CINXE.COM
Elastic for telecommunications | Elastic
<!DOCTYPE html><html lang="en-us"><head><meta charSet="utf-8"/><title>Elastic for telecommunications | Elastic</title><link rel="apple-touch-icon" sizes="57x57" href="/apple-icon-57x57.png"/><link rel="apple-touch-icon" sizes="60x60" href="/apple-icon-60x60.png"/><link rel="apple-touch-icon" sizes="72x72" href="/apple-icon-72x72.png"/><link rel="apple-touch-icon" sizes="76x76" href="/apple-icon-76x76.png"/><link rel="apple-touch-icon" sizes="114x114" href="/apple-icon-114x114.png"/><link rel="apple-touch-icon" sizes="120x120" href="/apple-icon-120x120.png"/><link rel="apple-touch-icon" sizes="144x144" href="/apple-icon-144x144.png"/><link rel="apple-touch-icon" sizes="152x152" href="/apple-icon-152x152.png"/><link rel="apple-touch-icon" sizes="180x180" href="/apple-icon-180x180.png"/><link rel="apple-touch-icon" sizes="192x192" href="/apple-icon-192x192.png"/><link rel="icon" type="image/png" href="/favicon-32x32.png" sizes="32x32"/><link rel="shortcut icon" href="/favicon.ico" type="image/x-icon"/><link rel="icon" href="/favicon.ico" type="image/x-icon"/><link rel="apple-touch-icon-precomposed" sizes="64x64" href="/favicon_64x64_16bit.png"/><link rel="apple-touch-icon-precomposed" sizes="32x32" href="/favicon_32x32.png"/><link rel="apple-touch-icon-precomposed" sizes="16x16" href="/favicon_16x16.png"/><meta name="application-name" content="Elastic"/><link rel="icon" type="image/png" href="/android-chrome-192x192.png" sizes="192x192"/><link rel="icon" type="image/png" href="/favicon-96x96.png" sizes="96x96"/><link rel="icon" type="image/png" href="/favicon-16x16.png" sizes="16x16"/><link rel="icon" type="image/png" href="/favicon-48x48.png" sizes="48x48"/><link rel="manifest" href="/manifest.json" crossorigin="use-credentials"/><meta name="msapplication-TileColor" content="#ffffff"/><meta name="localized" content="true"/><meta name="msapplication-TileImage" content="/mstile-144x144.png"/><meta name="description" content="Learn about the Search & Data Platform for Telecommunications from Elastic that enables this sector to transform operations in the 5G era, gain deeper insight into key performance indicators, enhance ..."/><meta property="og:title" content="Elastic for telecommunications"/><meta property="og:description" content="Learn about the Search & Data Platform for Telecommunications from Elastic that enables this sector to transform operations in the 5G era, gain deeper insight into key performance indicators, enhance ..."/><meta property="og:image" content="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltef153c426256a863/67bf728c938bf57bf4f9ae01/report-cover-solving-business-challenges-telco-it.png"/><meta name="twitter:widgets:csp" content="on"/><meta name="twitter:card" content="summary_large_image"/><meta name="twitter:site" content="@elastic"/><meta name="twitter:image" content="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltef153c426256a863/67bf728c938bf57bf4f9ae01/report-cover-solving-business-challenges-telco-it.png"/><meta name="twitter:title" content="Elastic for telecommunications"/><meta name="twitter:description" content="Learn about the Search & Data Platform for Telecommunications from Elastic that enables this sector to transform operations in the 5G era, gain deeper insight into key performance indicators, enhance ..."/><script type="application/ld+json">{"@context":"http://schema.org","type":"WebPage","headline":"Telco - Achieve real-time, high- resolution insights at telco scale","url":"/industries/telecommunications"}</script><meta name="baidu-site-verification" content="ksp2qKCW7Y"/><meta name="naver-site-verification" content="936882c1853b701b3cef3721758d80535413dbfd"/><meta name="yandex-verification" content="d8a47e95d0972434"/><meta name="viewport" content="width=device-width, initial-scale=1"/><meta name="theme-color" content="#00a9e5"/><meta name="robots" content="index,follow"/><link rel="canonical" href="https://www.elastic.co/industries/telecommunications"/><meta name="optimizely-fullstack-flags"/><link rel="dns-prefetch" href="https://cdn.optimizely.com"/><link rel="dns-prefetch" href="https://www.googletagmanager.com"/><link rel="dns-prefetch" href="https://clearbit.com"/><link rel="dns-prefetch" href="https://quora.com"/><link rel="preconnect" href="https://sjrtp2.marketo.com"/><link rel="preconnect" href="https://www.google.com"/><link rel="preconnect" href="https://www.facebook.com"/><link rel="preconnect" href="https://www.google-analytics.com"/><script type="application/javascript">(function(w,d,s,l,i){w[l]=w[l]||[];w[l].push({'gtm.start': new Date().getTime(),event:'gtm.js'});var f=d.getElementsByTagName(s)[0], j=d.createElement(s),dl=l!='dataLayer'?'&l='+l:'';j.async=true;j.src='https://www.googletagmanager.com/gtm.js?id='+i+dl;f.parentNode.insertBefore(j,f); })(window,document,'script','dataLayer','GTM-58RLH5');</script><script type="application/javascript">(function(w,d,s,l,i){w[l]=w[l]||[];w[l].push({"gtm.start": new Date().getTime(),event:"gtm.js"});var f=d.getElementsByTagName(s)[0], j=d.createElement(s),dl=l!="dataLayer"?"&l="+l:"";j.async=true;j.src= "https://www.googletagmanager.com/gtm.js?id="+i+dl;f.parentNode.insertBefore(j,f); })(window,document,"script","dataLayer","GTM-KNJMG2M");</script><link rel="preconnect" href="https://logx.optimizely.com"/><link rel="preconnect" href="https://search.elastic.co"/><link rel="preload" as="script" href="https://cdn.optimizely.com/js/18132920325.js"/><script type="text/javascript" src="https://cdn.optimizely.com/js/18132920325.js"></script><link href="https://fonts.googleapis.com/earlyaccess/notosansjapanese.css" rel="stylesheet preload"/><link href="https://info.elastic.co/js/forms2/css/forms2-theme-plain.css" rel="stylesheet preload"/><link href="https://info.elastic.co/js/forms2/css/forms2.css" rel="stylesheet preload"/><meta name="next-head-count" content="63"/><link rel="preload" href="/_next/static/css/848376ea2064b368.css" as="style"/><link rel="stylesheet" href="/_next/static/css/848376ea2064b368.css" data-n-g=""/><link rel="preload" href="/_next/static/css/cc96b92625c11a10.css" as="style"/><link rel="stylesheet" href="/_next/static/css/cc96b92625c11a10.css" data-n-p=""/><link rel="preload" href="/_next/static/css/00b4045520c1e71f.css" as="style"/><link rel="stylesheet" href="/_next/static/css/00b4045520c1e71f.css" data-n-p=""/><link rel="preload" href="/_next/static/css/45edebee533634bf.css" as="style"/><link rel="stylesheet" href="/_next/static/css/45edebee533634bf.css" data-n-p=""/><noscript data-n-css=""></noscript><script defer="" nomodule="" src="/_next/static/chunks/polyfills-c67a75d1b6f99dc8.js"></script><script src="/_next/static/chunks/webpack-5148e588555dde77.js" defer=""></script><script src="/_next/static/chunks/framework-f8115f7fae64930e.js" defer=""></script><script src="/_next/static/chunks/main-e0c5d542deb1c114.js" defer=""></script><script src="/_next/static/chunks/pages/_app-6f1882f10fa7b91d.js" defer=""></script><script src="/_next/static/chunks/94803-bededac2ac605716.js" defer=""></script><script src="/_next/static/chunks/78369-ec2165c0ca6d5d93.js" defer=""></script><script src="/_next/static/chunks/46066-934084ce72f338b5.js" defer=""></script><script src="/_next/static/chunks/12539-07e8e7ad1ecfc11a.js" defer=""></script><script src="/_next/static/chunks/63942-27b12f1e1aa13324.js" defer=""></script><script src="/_next/static/chunks/83815-e7369f199afe76a8.js" defer=""></script><script src="/_next/static/chunks/16271-72b27ce65f9bbac4.js" defer=""></script><script src="/_next/static/chunks/34827-27464bedac54c891.js" defer=""></script><script src="/_next/static/chunks/33562-651dc66677ed1457.js" defer=""></script><script src="/_next/static/chunks/98102-ccdb05f69597b878.js" defer=""></script><script src="/_next/static/chunks/66885-605d512f62ac3c81.js" defer=""></script><script src="/_next/static/chunks/77723-33e1b2a09288ac17.js" defer=""></script><script src="/_next/static/chunks/pages/default_detail-6fc749c508acaeaa.js" defer=""></script><script src="/_next/static/Lxlpn6lP1AzvlD3efONO4/_buildManifest.js" defer=""></script><script src="/_next/static/Lxlpn6lP1AzvlD3efONO4/_ssgManifest.js" defer=""></script><style id="__jsx-1189744782">.elastic-logo{align-items:center;display:flex;flex-shrink:0;width:100px;outline:none;}@media (min-width:767px){.elastic-logo{width:120px;}}.elastic-logo:focus-visible{outline:2px solid var(--button-primary-active-offset-color);border-radius:4px;}</style><style id="__jsx-3447688935">.icon g{fill:#000;transition:fill 0.2s ease 0s;}.icon.iconDark g{fill:#fff;}</style><style id="__jsx-1596590093">.button{text-shadow:none;box-shadow:none;}.button:hover{background:none;text-decoration:none;}.button:focus,.button:focus-visible{text-decoration:none;}.button.btn-small{height:40px;min-height:40px;}.button.btn-large{min-width:200px;min-height:60px;padding:8px 24px;}.button.icon{align-items:center;display:inline-flex;gap:8px;}.button.icon-left{flex-direction:row-reverse;}.btn-primary,.btn-secondary,.btn-secondary-inverted,input.btn-primary,a.btn-primary:not([href]):not([tabindex]){display:inline-flex;min-height:50px;height:auto;justify-content:center;align-items:center;min-width:140px;padding:8px 24px;text-align:center;text-decoration:none;box-shadow:none;border:2px solid;border-radius:4px;-webkit-transition:all 100ms ease-in;transition:all 100ms ease-in;}.btn-primary,a.btn-primary:not([href]):not([tabindex]){color:var(--button-primary-color);background-color:var(--button-primary-bg);border-color:var(--button-primary-border-color);}.btn-primary:hover,.btn-primary.hover,a.btn-primary:not([href]):not([tabindex]):hover,a.btn-primary:not([href]):not([tabindex]) .hover{color:var(--button-primary-hover-color);background-color:var(--button-primary-hover-bg);border-color:var(--button-primary-hover-border-color);}.btn-primary:focus,.btn-primary:focus-visible,a.btn-primary:not([href]):not([tabindex]):focus,a.btn-primary:not([href]):not([tabindex]):focus-visible{color:var(--button-primary-color);}.btn-primary:focus-visible,a.btn-primary:not([href]):not([tabindex]):focus-visible{color:var(--button-primary-active-color);outline:2px solid var(--button-primary-active-offset-color);outline-offset:2px;border-color:var(--button-primary-active-border-color);}.btn-secondary,a.btn-secondary:not([href]):not([tabindex]){color:var(--button-secondary-color);background-color:var(--button-secondary-bg);border-color:var(--button-secondary-border-color);}.btn-secondary:hover,.btn-secondary.hover,a.btn-secondary:not([href]):not([tabindex]):hover,a.btn-secondary:not([href]):not([tabindex]) .hover{color:var(--button-secondary-hover-color);background-color:var(--button-secondary-hover-bg);border-color:var(--button-secondary-hover-border-color);}.btn-secondary:focus,.btn-secondary:focus-visible,a.btn-secondary:not([href]):not([tabindex]):focus,a.btn-secondary:not([href]):not([tabindex]):focus-visible{color:var(--button-secondary-color);}.btn-secondary:focus-visible,a.btn-secondary:not([href]):not([tabindex]):focus-visible{color:var(--button-secondary-active-color);outline:2px solid var(--button-secondary-active-offset-color);outline-offset:2px;border-color:var(--button-secondary-active-border-color);}.btn-secondary-inverted{background:white !important;border-color:var(--button-primary-border-color);color:var(--button-primary-border-color);}.btn-secondary-inverted:hover{color:var(--button-primary-border-color) !important;}.btn-secondary-inverted:hover{color:var(--button-primary-border-color) !important;}.btn-description,.btn-tertiary,.cta-link,a.btn-tertiary:not([href]):not([tabindex]){cursor:pointer;display:inline-block;text-decoration:none;color:var(--button-tertiary-color);padding-right:27px;}.btn-description svg,.btn-tertiary svg,.cta-link svg,a.btn-tertiary:not([href]):not([tabindex]) svg{width:27px;margin-right:-27px;-webkit-transition:all 100ms ease-in;transition:all 100ms ease-in;top:50%;top:50%;left:8px;position:relative;height:inherit;}.btn-description svg path,.btn-tertiary svg path,.cta-link svg path,a.btn-tertiary:not([href]):not([tabindex]) svg path{stroke:var(--button-tertiary-color);}.btn-description:hover,.btn-tertiary:hover,.cta-link:hover,a.btn-tertiary:not([href]):not([tabindex]):hover{color:var(--button-tertiary-hover-color);}.btn-description:hover svg,.btn-tertiary:hover svg,.cta-link:hover svg,a.btn-tertiary:not([href]):not([tabindex]):hover svg{left:14px;}.btn-description:hover svg path,.btn-tertiary:hover svg path,.cta-link:hover svg path,a.btn-tertiary:not([href]):not([tabindex]):hover svg path{stroke:var(--button-tertiary-hover-color);}.btn-description:focus,.btn-description:focus-visible,.btn-tertiary:focus,.btn-tertiary:focus-visible,.cta-link:focus,.cta-link:focus-visible,a.btn-tertiary:not([href]):not([tabindex]):focus,a.btn-tertiary:not([href]):not([tabindex]):focus-visible{color:var(--button-tertiary-color);}.btn-description:focus-visible,.btn-tertiary:focus-visible,.cta-link:focus-visible,a.btn-tertiary:not([href]):not([tabindex]):focus-visible{text-decoration:none;color:var(--button-tertiary-hover-color);outline:2px solid var(--button-tertiary-active-offset-color);outline-offset:4px;border-radius:4px;padding-right:12px;}.btn-description:focus-visible svg,.btn-tertiary:focus-visible svg,.cta-link:focus-visible svg,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg{stroke:var(--button-tertiary-hover-color);}.btn-description:focus-visible svg path,.btn-tertiary:focus-visible svg path,.cta-link:focus-visible svg path,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg path{stroke:var(--button-tertiary-hover-color);}#header-alert .btn-tertiary svg path{stroke:var(--color-dark-ink);}.btn-text-link.no-underline{text-decoration:none;}.btn-text-link:hover{text-decoration:underline;}.btn-text-link.btn-small{font-size:14px;}.btn-text-link.lighter-ink{color:var(--color-lighter-ink);}@media only screen and (max-width:720px){.cta{align-items:center !important;}.btn-tertiary{margin-top:10px;}}.btn-tertiary{background:transparent !important;font-size:16px !important;font-weight:600 !important;line-height:24px !important;height:auto !important;width:auto !important;text-align:left !important;border:none !important;color:var(--button-tertiary-color);border-radius:0 !important;display:inline-block !important;vertical-align:middle !important;}.btn-tertiary .btn-copy{display:inline;line-height:24px !important;vertical-align:middle !important;}.btn-tertiary svg{display:inline-block !important;vertical-align:middle !important;margin-top:4px !important;line-height:24px !important;fill:none !important;top:auto !important;}#navigation_container .button.btn-tertiary{background:transparent !important;font-size:16px !important;font-weight:600 !important;line-height:24px !important;height:auto !important;width:auto !important;text-align:left !important;border:none !important;padding:12px 0 0 0 !important;margin:0 !important;color:#0B64DD !important;border-radius:0 !important;display:inline-block !important;vertical-align:middle !important;white-space:wrap;}#navigation_container .button.btn-tertiary .btn-copy{display:inline;line-height:24px !important;vertical-align:middle !important;}#navigation_container .button.btn-tertiary svg{display:inline-block !important;vertical-align:middle !important;margin-top:4px !important;height:24px !important;width:24px !important;line-height:24px !important;fill:none !important;}#navigation_container .button.btn-tertiary svg path{stroke:#0B64DD !important;}#navigation_container .button.btn-tertiary:hover{color:#094DAB !important;}#navigation_container .button.btn-tertiary:hover svg path{stroke:#094DAB !important;}#navigation_container .button.btn-secondary{background:transparent !important;}#navigation_container .button.btn-secondary:hover{color:white !important;}#navigation_container .button.btn-small{font-size:14px !important;font-weight:600;}@media only screen and (max-width:720px){#navigation_container .button.btn-secondary-inverted:hover{color:var(--button-primary-bg) !important;}}</style><style id="__jsx-1868079691">.render-newNav .newNav{display:block;}.render-newNav .oldNav{display:none;}.render-oldNav .newNav{display:none;}.render-oldNav .oldNav{display:block;}</style><style id="__jsx-3416596397">h1.topic-heading.jsx-3416596397,h2.topic-heading.jsx-3416596397{color:var(--topic-heading-color);}h1.topic-heading.authordesignation.jsx-3416596397,h2.topic-heading.authordesignation.jsx-3416596397{color:var(--topic-heading-color);}h1.topic-heading.teal.jsx-3416596397,h2.topic-heading.teal.jsx-3416596397{color:var(--color-light-teal);}h1.topic-heading.black.jsx-3416596397,h2.topic-heading.black.jsx-3416596397{color:var(--color-black);}</style><style id="__jsx-1955866259">.title-wrapper h1,.title-wrapper h2,.title-wrapper h3,.title-wrapper h4,.title-wrapper h5,.title-wrapper h6,.title-wrapper .h1,.title-wrapper .h2,.title-wrapper .h3,.title-wrapper .h4,.title-wrapper .h5,.title-wrapper .h6{margin:0;box-sizing:border-box;display:block;position:relative;}.title-wrapper h1 a,.title-wrapper h2 a,.title-wrapper h3 a,.title-wrapper h4 a,.title-wrapper h5 a,.title-wrapper h6 a,.title-wrapper .h1 a,.title-wrapper .h2 a,.title-wrapper .h3 a,.title-wrapper .h4 a,.title-wrapper .h5 a,.title-wrapper .h6 a{font-weight:400;text-decoration:none;font-weight:unset;}.title-wrapper h1 a:hover,.title-wrapper h2 a:hover,.title-wrapper h3 a:hover,.title-wrapper h4 a:hover,.title-wrapper h5 a:hover,.title-wrapper h6 a:hover,.title-wrapper .h1 a:hover,.title-wrapper .h2 a:hover,.title-wrapper .h3 a:hover,.title-wrapper .h4 a:hover,.title-wrapper .h5 a:hover,.title-wrapper .h6 a:hover{text-decoration:none;}.blog h2,.press-detail .press-content h2{margin-top:64px;}.blog h3,.blog h4,.blog h5,.blog h6,.press-detail .press-content h3,.press-detail .press-content h4,.press-detail .press-content h5,.press-detail .press-content h6{margin-top:32px;}</style><style id="__jsx-388436971">.cta-group .btn-tertiary{margin-bottom:8px;}.cta-group .d-flex.flex-column a{width:100% !important;}.cta-group .icon{max-height:16px;max-height:16px;}.cta-group .is-second-cta-inline{margin-left:16px !important;}</style><style id="__jsx-1383953900">.title-text-one-column .icon-topic-heading .icon-32,.title-text-two-column .icon-topic-heading .icon-32{margin:0 16px 16px 0;max-height:32px;max-width:32px;}.title-text-one-column .title-text-desc,.title-text-two-column .title-text-desc{margin-bottom:8px;}.title-text-one-column p:last-child,.title-text-two-column p:last-child{margin-bottom:0;}.title-text-one-column .title-text-footer .inline-flex-align-items-baseline,.title-text-two-column .title-text-footer .inline-flex-align-items-baseline{display:flex;flex-direction:row;flex-wrap:wrap;align-items:baseline;}.title-text-one-column .title-text-footer .inline-flex-align-items-baseline .text-link,.title-text-two-column .title-text-footer .inline-flex-align-items-baseline .text-link{margin-left:16px;}.title-text-one-column .title-text-footer .justify-content-center a .btn-tertiary,.title-text-two-column .title-text-footer .justify-content-center a .btn-tertiary{display:flex;align-items:center;}@media screen and (max-width:767px){.icon-topic-heading.d-flex .topic-heading{padding-bottom:16px;}}</style><style id="__jsx-682499841">@media screen and (max-width:576px){card-deck-spotlight .content{text-align:center;order:2;}card-deck-spotlight .content .title{margin-top:32px;}card-deck-spotlight .content .cta-group{justify-content:center !important;}}</style><style id="__jsx-802606770">.illustration-icon-grid-container ul:not(.illustration-icon-grid-2x2) .logo{height:64px;margin-bottom:16px;}.illustration-icon-grid-item-content .arrow-down,.illustration-icon-grid-item-content .arrow-up{width:24px;margin-right:16px;}.illustration-icon-grid-item-content .statistics-title-container{display:flex;flex-direction:row;justify-content:center;}.illustration-icon-grid-item-content .statistics-title-container .arrow-down{display:flex;align-items:flex-end;}.illustration-icon-grid-item-content .statistics-title-container .arrow-down img{position:relative;bottom:20%;}.illustration-icon-grid-item-content .statistics-title-container .arrow-up{display:flex;align-items:flex-start;}.illustration-icon-grid-item-content .statistics-title-container .arrow-up img{position:relative;bottom:-25%;}.illustration-icon-grid-item-content .statistics-title-container-80px{display:flex;flex-direction:row;margin-bottom:16px;}.illustration-icon-grid-items .btn-tertiary{padding-top:16px;margin-bottom:8px;}.illustration-icon-grid-items .one-column{position:relative;display:flex;flex-direction:column;}.illustration-icon-grid-items .two-column{position:relative;display:grid;column-gap:32px;grid-template-columns:128px 1fr;}.illustration-icon-grid-items .grid-image-left .grid-image{text-align:left;}.illustration-icon-grid-items .grid-image-center .grid-image{text-align:center;}.illustration-icon-grid-items .paragraph-left .paragraph{text-align:left;}.illustration-icon-grid-items .paragraph-center .paragraph{text-align:center;}.illustration-icon-grid-items .title-heading-left .statistics-title,.illustration-icon-grid-items .title-heading-left .title-wrapper{text-align:left;}.illustration-icon-grid-items .title-heading-center .statistics-title,.illustration-icon-grid-items .title-heading-center .title-wrapper{text-align:center;}.illustration-icon-grid-items .topic-heading-left .topic-heading{text-align:left;}.illustration-icon-grid-items .topic-heading-center .topic-heading{text-align:center;}.illustration-icon-grid-items .illustration-icon-grid-item-top .icon-32{width:32px;height:32px;margin-bottom:16px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .icon-64{width:64px;height:64px;margin-bottom:16px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .image-xsmall{width:128px;height:128px;margin-bottom:16px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper{overflow:hidden;position:relative;margin-bottom:32px;border-radius:10px;border:1px solid var(--color-dark-gray);}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper .thumbnail{border-radius:10px;object-fit:cover;position:relative;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper .thumbnail-hover:hover img{transform:scale(1.1);transition:transform 250ms ease-in-out,-webkit-transform 250ms ease-in-out;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-default{min-height:129px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-128{max-width:128px;width:128px;}.illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-128 img{height:75px;}.illustration-icon-grid-items .illustration-icon-grid-item-footer{width:100%;}.illustration-icon-grid-items .illustration-icon-grid-item-footer .inline-flex-align-items-baseline{display:flex;flex-direction:row;flex-wrap:wrap;align-items:baseline;}.illustration-icon-grid-items .illustration-icon-grid-item-footer .inline-flex-align-items-baseline .text-link{margin-left:16px;}.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .thumbnail-wrapper{margin:0 32px 32px 0;}.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .icon-32,.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .icon-64{margin-right:16px;}.illustration-icon-grid-2x2 .illustration-icon-grid-items .illustration-icon-grid-item-top .logo{height:auto;width:128px;}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{width:100%;}.illustration-icon32-clickable-list .illustration-icon-grid-item,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item{cursor:pointer;position:relative;-webkit-transform:translateY(0px);-moz-transform:translateY(0px);-ms-transform:translateY(0px);transform:translateY(0px);-moz-transition:all 0.4s;-webkit-transition:all 0.4s;-o-transition:all 0.4s;-ms-transition:all 0.4s;transition:all 0.4s;}.illustration-icon32-clickable-list .illustration-icon-grid-item:after,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item:after{opacity:0;filter:alpha(opacity=0);-moz-transition:all 0.4s;-webkit-transition:all 0.4s;-o-transition:all 0.4s;-ms-transition:all 0.4s;transition:all 0.4s;}.illustration-icon32-clickable-list .illustration-icon-grid-item:hover:after,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item:hover:after{opacity:1;filter:alpha(opacity=100);}.illustration-icon32-clickable-list .illustration-icon-grid-item-top,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top{display:flex;flex-wrap:nowrap;align-items:flex-start;}.illustration-icon32-clickable-list .illustration-icon-grid-item-top .icon-32,.illustration-icon32-clickable-list .illustration-icon-grid-item-top .icon-64,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top .icon-32,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top .icon-64{margin-right:16px;}.illustration-icon32-clickable-list li,.illustration-icon32-clickable-list-3-per-row li{padding:16px;border-radius:10px;}.illustration-icon32-clickable-list li:hover,.illustration-icon32-clickable-list-3-per-row li:hover{border-right:1px none var(--color-white);border-left:1px none var(--color-white);background-color:var(--color-white);box-shadow:0 10px 20px 0 rgba(152,162,179,0.15),0 2px 6px 0 rgba(152,162,179,0.25);}.illustration-icon64-grid-5x1-container .one-column{align-items:center;}.illustration-icon64-grid-5x1-container .illustration-icon-grid-item-content h5{font-size:1.125rem;line-height:1.375rem;font-weight:700;text-align:center;}@media screen and (max-width:991px){.two-column{flex-direction:column;align-items:flex-start;}.illustration-icon-grid-container .logo{height:64px;margin-bottom:16px;}.statistics-title-container .arrow-down img{bottom:13% !important;}.statistics-title-container .arrow-up img{bottom:-18% !important;}}@media screen and (max-width:576px){.illustration-icon-grid-items{display:flex;flex-direction:column;}.illustration-icon-grid-items .two-column{display:block;}}</style><style id="__jsx-2381115616">.card-deck-container.container-border,.illustration-icon-grid-container.container-border{border:1px solid var(--carddeck-container-border-color);}.card-deck-container .card-text-image .logo,.illustration-icon-grid-container .card-text-image .logo{height:64px;max-width:128px;margin:0px 16px 16px 0px;}.card-deck-container .card-text-image .logo-width-128px,.illustration-icon-grid-container .card-text-image .logo-width-128px{max-width:128px;margin:0px 16px 16px 0px;}.card-deck-container .card-paragraph ol,.card-deck-container .paragraph ol,.illustration-icon-grid-container .card-paragraph ol,.illustration-icon-grid-container .paragraph ol{padding-left:20px !important;}.card-deck-container .card-paragraph ol li,.card-deck-container .paragraph ol li,.illustration-icon-grid-container .card-paragraph ol li,.illustration-icon-grid-container .paragraph ol li{list-style-type:decimal;}.card-deck-container .card-paragraph ol li ol,.card-deck-container .paragraph ol li ol,.illustration-icon-grid-container .card-paragraph ol li ol,.illustration-icon-grid-container .paragraph ol li ol{margin:0px;}.card-deck-container .card-paragraph ol li ol li,.card-deck-container .paragraph ol li ol li,.illustration-icon-grid-container .card-paragraph ol li ol li,.illustration-icon-grid-container .paragraph ol li ol li{list-style-type:lower-alpha;}.card-outline-2-column .card.card-outline{background:var(--color-white);display:flex;flex-direction:row;}.illustration-icon-grid-items{display:grid;grid-auto-columns:1fr;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;grid-row-gap:16px;grid-column-gap:16px;margin-right:auto;margin-left:auto;}.illustration-icon-grid-items.illustration-icon-grid-4x1 .illustration-icon-grid-item,.illustration-icon-grid-items.illustration-icon32-split-grid-2x2 .illustration-icon-grid-item,.illustration-icon-grid-items .illustration-icon-grid-item-content{display:flex;flex-direction:column;position:relative;}.statistics-grid-2x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;width:78%;margin-left:auto;margin-right:auto;}.illustration-icon-grid-2x2{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.illustration-icon-grid-2x2 .two-column .illustration-icon-grid-item-content{display:flex;flex-direction:column;align-items:flex-start;justify-content:space-between;height:100%;}.illustration-icon-grid-3x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(3,1fr);grid-template-rows:auto;}.illustration-icon-grid-4x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(4,1fr);grid-template-rows:auto;}.illustration-icon32-clickable-list{grid-template-columns:repeat(4,1fr);}.illustration-icon32-clickable-list-3-per-row{grid-template-columns:repeat(3,1fr);}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:32px;grid-row-gap:32px;grid-template-rows:auto;}.illustration-icon32-clickable-list .illustration-icon-grid-item,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item{display:flex;flex-direction:column;justify-content:space-between;align-items:stretch;position:relative;}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{display:grid;grid-template-columns:0.6fr 1fr;grid-template-rows:auto;grid-column-gap:64px;grid-row-gap:64px;align-items:start;justify-items:start !important;}.illustration-clickable-list-split-grid-2x2-container .title-text-one-column.container,.illustration-icon32-split-grid-2x2-container .title-text-one-column.container{padding:0 !important;}.illustration-clickable-list-split-grid-2x2-container .illustration-icon32-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2{grid-column-gap:64px;grid-row-gap:64px;}.illustration-icon32-grid-2x2{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.illustration-icon32-grid-2x2-below-module-paragraph{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:32px;grid-row-gap:32px;grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.illustration-icon32-grid-2x2-showcase{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:64px repeat(2,1fr) 64px;grid-template-rows:auto;}.illustration-icon32-grid-2x2-showcase li:nth-child(odd){grid-column-start:2;}.illustration-icon32-grid-3x2{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(3,1fr);grid-template-rows:auto;}.illustration-icon64-grid-3x1{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:64px;grid-row-gap:64px;grid-template-columns:repeat(3,1fr);grid-template-rows:auto;}.illustration-icon64-grid-5x1-container{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-column-gap:32px;grid-row-gap:32px;grid-template-rows:auto;}.illustration-icon64-grid-5x1-container .one-column .illustration-icon-grid-item-content,.illustration-icon64-grid-5x1-container .one-column .illustration-icon-grid-item-top{display:flex;margin-right:auto;margin-left:auto;flex-direction:column;justify-content:flex-start;}.illustration-icon64-grid-5x1-3-per-row{grid-template-columns:repeat(3,1fr);}.illustration-icon64-grid-5x1{grid-template-columns:repeat(5,1fr);}@media screen and (max-width:991px){.illustration-icon-grid-4x1{grid-template-columns:repeat(3,1fr);}.illustration-icon-grid-2x2 .two-column{display:flex;flex-direction:column;}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{grid-template-columns:repeat(3,1fr);}.illustration-icon32-clickable-list .illustration-icon-grid-item-top,.illustration-icon32-clickable-list-3-per-row .illustration-icon-grid-item-top{flex-direction:column;}.illustration-icon32-grid-3x2,.illustration-icon64-grid-5x1-container{grid-column-gap:32px;grid-row-gap:32px;}.illustration-icon32-grid-2x2-showcase{grid-row-gap:32px;grid-template-columns:1fr;}.illustration-icon32-grid-2x2-showcase li:nth-child(odd){grid-column-start:initial;}.illustration-icon64-grid-5x1-container{grid-template-columns:repeat(3,1fr);}}@media screen and (max-width:980px){.statistics-grid-2x1{width:100%;}}@media screen and (max-width:767px){.illustration-icon-grid-2x2,.illustration-icon-grid-3x1,.illustration-icon-grid-4x1,.illustration-clickable-list-split-grid-2x2-container .illustration-clickable-list-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2,.illustration-icon32-grid-2x2,.illustration-icon32-grid-3x2,.illustration-icon64-grid-5x1-container{grid-column-gap:32px;grid-row-gap:32px;}.statistics-grid-2x1{grid-template-columns:repeat(1,1fr);}.illustration-icon-grid-2x2{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-icon-grid-2x2 .two-column .illustration-icon-grid-item-content{height:auto;}.illustration-icon-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.illustration-icon-grid-4x1{grid-template-columns:1fr 1fr;grid-template-rows:repeat(2,auto);}.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{grid-template-columns:1fr 1fr;grid-template-rows:repeat(3,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-template-columns:1fr;grid-template-rows:auto auto;}.illustration-clickable-list-split-grid-2x2-container .illustration-clickable-list-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2{grid-template-columns:1fr 1fr;grid-template-rows:repeat(1,auto);}.illustration-icon32-grid-2x2{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-icon32-grid-3x2{grid-template-columns:1fr 1fr;grid-template-rows:repeat(3,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-row-gap:32px;}.illustration-icon64-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.illustration-icon64-grid-5x1-container{grid-template-columns:1fr 1fr 1fr;grid-template-rows:repeat(3,auto);}}@media screen and (max-width:575px){.card-grid-2x1{grid-template-columns:1fr;grid-template-rows:repeat(2,auto);}.card-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.card-grid-4x1{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}}@media screen and (max-width:479px){.illustration-icon32-clickable-list,.illustration-icon32-clickable-list-3-per-row{grid-template-columns:1fr;grid-template-rows:repeat(6,auto);}.illustration-icon-grid-4x1{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-icon32-grid-3x2{grid-template-columns:1fr;grid-template-rows:repeat(6,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-row-gap:16px;}.illustration-clickable-list-split-grid-2x2-container .illustration-icon32-split-grid-2x2,.illustration-icon32-split-grid-2x2-container .illustration-icon32-split-grid-2x2{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}.illustration-clickable-list-split-grid-2x2-container,.illustration-icon32-split-grid-2x2-container{grid-template-columns:1fr;grid-template-rows:auto auto;}.illustration-icon64-grid-5x1-container{grid-template-columns:1fr 1fr;grid-template-rows:repeat(2,auto);}}</style><style id="__jsx-1653982606">.image.jsx-1653982606 img.full-width.jsx-1653982606{width:100vw;}.image.jsx-1653982606 figure.jsx-1653982606 figcaption.jsx-1653982606{margin:8px 0 0;}.image.jsx-1653982606 figure.jsx-1653982606 figcaption.jsx-1653982606 p.jsx-1653982606{margin-bottom:0;}</style><style id="__jsx-89852744">.vidyard-player-embed.jsx-89852744{display:none;}.overflow.jsx-89852744{width:auto;max-height:500px;}</style><style id="__jsx-2477493165">.video iframe{height:100% !important;}.video .shadow-light{overflow:hidden;}</style><style id="__jsx-1443386464">.card-list{display:flex;}.card-list .card-wrapper{flex:1;position:relative;height:fit-content;}@media (min-width:576px){.card-list .card-wrapper{height:unset;}}.card-list .badge{text-transform:uppercase;font-weight:600;line-height:1.8333333333;letter-spacing:0.1em;color:#fff;text-align:center;margin-bottom:-12px;width:100%;padding:12px 0 24px;border-top-left-radius:10px;border-top-right-radius:10px;}@media (min-width:576px){.card-list .badge{position:absolute;transform:translateY(-75%);margin-bottom:0;}}.card-list .card-container.card{height:100%;background:#fff;display:flex;flex-direction:column;justify-content:space-between;overflow:hidden;margin:0px;-moz-transition:all 0.4s ease;-webkit-transition:all 0.4s ease;-o-transition:all 0.4s ease;-ms-transition:all 0.4s ease;transition:all 0.4s ease;}.card-list .card-container.card:hover{-moz-box-shadow:0px 5px 24px rgba(0,0,0,0.12);-webkit-box-shadow:0px 5px 24px rgba(0,0,0,0.12);-o-box-shadow:0px 5px 24px rgba(0,0,0,0.12);-ms-box-shadow:0px 5px 24px rgba(0,0,0,0.12);box-shadow:0px 5px 24px rgba(0,0,0,0.12);}.card-list .card-container.card .card-topic-heading.pill{background:var(--color-light-teal);padding:6px 16px;display:inline-block;border-radius:42px;margin-bottom:24px;}.card-list .card-container.card .card-topic-heading.pill h2{padding:0;color:var(--color-dark-teal);}.card-list .card-container.card .card-icon-heading{display:flex;align-items:center;}.card-list .card-container.card .card-icon-heading h2{padding-bottom:0;}.card-list .card-container.card .card-header{background:none;padding:0;border-bottom:0px none;display:-moz-box;display:-ms-flexbox;display:-webkit-flex;display:flex;}.card-list .card-container.card .card-title{color:var(--headings-color);margin-bottom:0;word-break:break-word;}.card-list .card-container.card .card-paragraph{color:var(--body-color);}.card-list .card-container.card .card-paragraph .pricing{margin-top:16px;}.card-list .card-container.card .card-paragraph .pricing p{margin-bottom:4px;}.card-list .card-container.card .card-paragraph .pricing h4{font-weight:700;font-size:1.75rem;padding-bottom:4px;}.card-list .card-container.card .card-icon-heading .icon-32,.card-list .card-container.card .card-image .icon-32{width:32px;height:32px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading .icon-64,.card-list .card-container.card .card-image .icon-64{width:64px;height:64px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading .image-xsmall,.card-list .card-container.card .card-image .image-xsmall{width:128px;height:128px;margin-bottom:16px;}.card-list .card-container.card .card-icon-heading .logo,.card-list .card-container.card .card-image .logo{height:64px;max-width:120px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading .logo-small,.card-list .card-container.card .card-image .logo-small{height:64px;max-width:120px;margin:0px 16px 16px 0px;}.card-list .card-container.card .card-icon-heading.thumbnail-wrapper,.card-list .card-container.card .card-image.thumbnail-wrapper{margin-bottom:32px;border:1px solid var(--color-dark-gray);}.card-list .card-container.card .card-icon-heading.thumbnail-wrapper img.thumbnail,.card-list .card-container.card .card-image.thumbnail-wrapper img.thumbnail{border-radius:10px;}.card-list .card-container.card.paragraph-left .card-paragraph{text-align:left;}.card-list .card-container.card.paragraph-center .card-paragraph{text-align:center;}.card-list .card-container.card.title-heading-left .title-wrapper{text-align:left;}.card-list .card-container.card.title-heading-center .title-wrapper{text-align:center;}.card-list .card-container.card.topic-heading-left .topic-heading{text-align:left;}.card-list .card-container.card.topic-heading-center .topic-heading{text-align:center;}.card-list .card-container.card .card-footer{background:none !important;padding:0px;border:0px;}.card-list .card-container.card .card-footer .btn-tertiary{padding-top:16px;margin-bottom:8px;}.card-list .card-container.card .card-footer .cta-arrow a img{width:27px;height:20px;transition:all 500ms cubic-bezier(0.19,1,0.22,1);}.card-list .card-container.card .card-footer .inline-flex-align-items-baseline{display:flex;flex-direction:row;flex-wrap:wrap;align-items:baseline;}.card-list .card-container.card .card-footer .inline-flex-align-items-baseline .text-link{margin-left:16px;}.card-list .card-container.card .card-footer .d-flex.flex-column a{width:100%;}.card-list .card-container.card .card-footer .cta-arrow{text-align:left !important;}.card-list .card-container.card .card-footer .btn-primary.icon-left,.card-list .card-container.card .card-footer .btn-secondary.icon-left,.card-list .card-container.card .card-footer .text-link.icon-left{display:flex;flex-direction:row-reverse;}.card-list .card-container.card .card-footer .btn-primary.icon-right,.card-list .card-container.card .card-footer .btn-secondary.icon-right,.card-list .card-container.card .card-footer .text-link.icon-right{display:flex;flex-direction:row;}.card-list .card-container.card .card-footer .btn-primary.icon-left img,.card-list .card-container.card .card-footer .btn-secondary.icon-left img,.card-list .card-container.card .card-footer .text-link.icon-left img{padding-right:8px;}.card-list .card-container.card .card-footer .btn-primary.icon-right img,.card-list .card-container.card .card-footer .btn-secondary.icon-right img,.card-list .card-container.card .card-footer .text-link.icon-right img{padding-left:8px;}.card-border{position:absolute;border-style:none;border-width:1px;}.card-border.card-border-top{left:0px;top:0px;right:0px;bottom:auto;height:6px;max-height:6px;}.card-list .card-container.card-ghost{border:0px;border-bottom:1px solid var(--color-dark-gray) !important;box-shadow:none !important;cursor:pointer;}.card-list .card-container.card-ghost .card-title a,.card-list .card-container.card-ghost .card-title a:visited{text-decoration:none;color:inherit;}.card-list .card-container.card-ghost .card-title h3{text-decoration:none;}.card-list .card-container.card-ghost .card-footer{padding-bottom:32px;}.card-list .card-container.card-ghost .thumbnail-wrapper{overflow:hidden;position:relative;border-radius:10px;}.card-list .card-container.card-ghost .thumbnail-wrapper .thumbnail{transition:transform 250ms ease-in-out,-webkit-transform 250ms ease-in-out;width:100%;height:unset;object-fit:cover;position:relative;z-index:0;min-height:129px;}.card-list .card-container.card-ghost:hover img.thumbnail{transform:scale(1.1);}.card-list .card-container.card-ghost:hover .card-title h3{text-decoration:underline;}.card-list .card-container.card-ghost:hover .card-paragraph p{opacity:0.8;text-decoration:none;}.card-container.card-outline{border:1px solid var(--color-dark-gray) !important;}.card-container.card-outline-none{border:0px !important;}.card-content-left .card-title,.card-content-left .card-paragraph,.card-content-left .topic-heading{text-align:left;}.card-content-center .card-title,.card-content-center .card-paragraph,.card-content-center .topic-heading{text-align:center;}.card-image-left .card-image{text-align:left;}.card-image-center .card-image{text-align:center;}@media screen and (max-width:991){.card-container.card .card-footer .inline-flex-align-items-baseline{flex-direction:column;align-items:none;}.card-container.card .card-footer .inline-flex-align-items-baseline a{width:100%;}}</style><style id="__jsx-887545163">.carousel .carousel-two-column__tab-labels-left .carousel-heading .heading{font-family:'MierB','Inter',Arial,sans-serif;font-size:1rem;line-height:1.5rem;font-weight:400;}.carousel .carousel-two-column__tab-labels-left .carousel-heading:hover{margin-left:-2px;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab-list{border-bottom:0;border-left:1px solid var(--color-dark-gray);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab{padding:8px 16px;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab:hover{margin-bottom:0px;border-left:2px solid var(--color-black);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected{border-left:2px solid var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected:hover{border-color:var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected .carousel-heading{margin-left:-2px;}.carousel .carousel-two-column__tab-labels-left-accordion .carousel-heading{color:var(--color-black);cursor:pointer;padding:16px 16px 0 16px;position:relative;}.carousel .carousel-two-column__tab-labels-left-accordion .carousel-heading .heading{font-family:'MierB','Inter',Arial,sans-serif;padding-bottom:16px;font-size:1rem;line-height:1.5rem;font-weight:400;padding-right:24px;}.carousel .carousel-two-column__tab-labels-left-accordion .carousel-body{padding:0px 16px 16px;}.carousel .carousel-two-column__tab-labels-left-accordion .d-lg-none.carousel-asset{margin:32px 8px;}.carousel .carousel-two-column__tab-labels-left-accordion .react-tabs__tab{cursor:pointer;margin:-1px 0px 0px 0px;padding:0;border-top:1px solid #D4DAE5;border-bottom:1px solid #D4DAE5;border-left:2px solid transparent;}.carousel .carousel-two-column__tab-labels-left-accordion .react-tabs__tab--selected{background-color:var(--color-white);box-shadow:0 10px 20px 10px rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25);cursor:text;border-top:1px none var(--color-dark-gray);border-bottom:1px none var(--color-dark-gray);border-left:2px solid var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left-accordion .react-tabs__tab--selected .arrow:after{top:26px;-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}.carousel .carousel-two-column__tab-labels-left-accordion .arrow:after{content:"";height:12px;position:absolute;right:19px;top:20px;width:12px;border-top:1px solid var(--color-elastic-blue);border-left:1px solid var(--color-elastic-blue);-webkit-transform:rotate(-135deg);-moz-transform:rotate(-135deg);-ms-transform:rotate(-135deg);transform:rotate(-135deg);-moz-transition:transform 0.4s;-webkit-transition:transform 0.4s;-o-transition:transform 0.4s;-ms-transition:transform 0.4s;transition:transform 0.4s;}.carousel .carousel-two-column__tab-labels-left-accordion .close-acc .arrow:after{top:20px;-webkit-transform:rotate(-135deg);-moz-transform:rotate(-135deg);-ms-transform:rotate(-135deg);transform:rotate(-135deg);}.carousel .carousel-two-column__tab-labels-left-accordion .up-arrow:after{top:26px;-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}.carousel .show{display:block;}.carousel .hidden{display:none;}@media screen and (max-width:767px){.carousel .carousel-two-column__tab-labels-left .carousel-heading:hover{margin-left:0px !important;}.carousel .carousel-two-column__tab-labels-left .carousel-tabs{display:flex;align-content:center;justify-content:center;margin-bottom:16px;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab{border-left:none !important;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab-list{display:flex;flex-direction:row;justify-content:center;flex-wrap:wrap;border-left:none !important;border-bottom:1px solid var(--color-dark-gray) !important;width:100%;}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected{border-left:none !important;border-bottom:2px solid var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected:hover{border-color:var(--color-elastic-blue);}.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected .carousel-heading{margin-left:0px !important;}}</style><style id="__jsx-579451128">.default-detail section.hasBackground:nth-last-child(2)+.layout,.default-detail section.bg-light-gray:nth-last-child(2)+.layout,.default-detail div.bg-light-gray:nth-last-child(2)+.layout,.default-detail section.bg-developer-blue:nth-last-child(2)+.layout,.default-detail div.bg-developer-blue:nth-last-child(2)+.layout,.default-detail section.bg-light-gray:nth-last-child(2)+.layout,.default-detail section.bg-developer-blue:nth-last-child(2)+.layout{height:0;}.default-detail .quote .flex-items-wrapper .img-fluid{max-height:64px;}.default-detail .social-card .card{overflow:visible;}.default-detail #dl_calculator embed{height:100vh !important;}.default-detail #dl_calculator .customizable_chart_header{width:100% !important;}.default-detail p.note{font-size:0.75rem;color:var(--color-ink);font-weight:normal;margin-bottom:8px;text-transform:none;}.default-detail .footer-cta .mkto-form-wrapper.inline.center{display:flex;justify-content:center;}.default-detail .title-text-one-column h3{margin:40px 0px 0px;}.default-detail .title-text-one-column h3:first-child{margin-top:20px;}.default-detail .icon-grid+.image,.default-detail .icon-grid+.features{margin-top:-50px;}.default-detail .pricing{margin-bottom:-40px;}.default-detail .image-text-grid .card-deck .card .title-text-cta.card-body{display:flex;flex-direction:column;}.default-detail .editorial-molecule:hover .title-link .title{text-decoration:underline;}@media screen and (max-width:991px) and (min-width:481px){.listing-sidebar .sidebar-wrapper .sidebar .tab-column{display:flex;flex-direction:column;}.right-column{padding-top:64px;}.editorial-molecule{border-bottom:1px solid var(--color-dark-gray);padding-bottom:64px;}}@media screen and (max-width:767px) and (min-width:481px){.editorial-molecule .molecule{display:flex;flex-direction:row;}.editorial-molecule .molecule .thumbnail{height:max-content !important;}.editorial-molecule .molecule .title-link{margin:0;}}@media screen and (max-width:480px){.editorial-molecule{border-bottom:1px solid var(--color-dark-gray);padding-bottom:48px;}.right-column{padding-top:48px;}}@media screen and (max-width:375px){.default-detail .common-container{max-width:255px;word-break:break-word;}}</style><style id="__jsx-2923087917">@charset "UTF-8";html,body{-webkit-font-smoothing:antialiased;position:relative;color:var(--body-color);}h1,h2,h3,h4,h5,h6,.h1,.h2,.h3,.h4,.h5,.h6{margin:0;box-sizing:border-box;display:block;position:relative;}h1 a,h2 a,h3 a,h4 a,h5 a,h6 a,.h1 a,.h2 a,.h3 a,.h4 a,.h5 a,.h6 a{font-weight:400;text-decoration:none;font-weight:unset;}h1 a:hover,h2 a:hover,h3 a:hover,h4 a:hover,h5 a:hover,h6 a:hover,.h1 a:hover,.h2 a:hover,.h3 a:hover,.h4 a:hover,.h5 a:hover,.h6 a:hover{text-decoration:none;font-weight:unset;}h1 a:hover:hover,h2 a:hover:hover,h3 a:hover:hover,h4 a:hover:hover,h5 a:hover:hover,h6 a:hover:hover,.h1 a:hover:hover,.h2 a:hover:hover,.h3 a:hover:hover,.h4 a:hover:hover,.h5 a:hover:hover,.h6 a:hover:hover{text-decoration:none;}p{margin:0 0 8px 0;}strong,b{font-weight:700;}i,em{font-style:italic;}sub{position:relative;top:0.5em;font-size:0.8em;}sup{position:relative;top:-0.5em;font-size:0.8em;}hr{border-color:var(--color-dark-gray);}hr.custom-2{border-width:2px;}small{line-height:26px;font-size:12px;font-weight:400;}ul,ul li{background:none;list-style-type:none;margin:0;padding:0;}ul ul,ul li ul{margin-top:4px;}ul.list-green,ul.list-black,ul.list_arrows,.service-list ul,.title-text ul,.main-content-wrapper ul,.video-detail ul,.webinar-archive ul,.course-tabs .course-tab-list .react-tabs__tab-panel ul,.course-tabs .course-accordion ul,.title-text-desc ul{list-style:none;margin-top:8px;margin-bottom:8px;}ul.list-green li,ul.list-black li,ul.list_arrows li,.service-list ul li,.title-text ul li,.main-content-wrapper ul li,.video-detail ul li,.webinar-archive ul li,.course-tabs .course-tab-list .react-tabs__tab-panel ul li,.course-tabs .course-accordion ul li,.title-text-desc ul li{list-style:none;font-weight:normal;padding-left:15px;margin:0 0 8px 15px;}ul.list-green li:before,ul.list-black li:before,ul.list_arrows li:before,.service-list ul li:before,.title-text ul li:before,.main-content-wrapper ul li:before,.video-detail ul li:before,.webinar-archive ul li:before,.course-tabs .course-tab-list .react-tabs__tab-panel ul li:before,.course-tabs .course-accordion ul li:before,.title-text-desc ul li:before{content:"•";color:var(--color-dark-teal);display:inline-block;margin-left:-20px;width:20px;}ul.list-green li p,ul.list-black li p,ul.list_arrows li p,.service-list ul li p,.title-text ul li p,.main-content-wrapper ul li p,.video-detail ul li p,.webinar-archive ul li p,.course-tabs .course-tab-list .react-tabs__tab-panel ul li p,.course-tabs .course-accordion ul li p,.title-text-desc ul li p{display:inline;}ul.list-icon-check{list-style:none;}ul.list-icon-check li{list-style:none;font-weight:normal;padding-left:24px;margin:0 0 10px 5px;position:relative;}ul.list-icon-check li:before{border:1px solid var(--color-elastic-teal);border-width:0 2px 2px 0;content:"";height:13px;left:0;position:absolute;top:4px;width:8px;-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);-webkit-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}ol{margin-top:8px;margin-bottom:8px;padding-left:32px;}ol li{margin-bottom:8px;}ol li ol{margin:16px 0;}ol.lower-alpha{list-style-type:lower-alpha;}ol.upper-roman{list-style-type:upper-roman;}.blog .container ul:not(.card-grid),.webinar-wrap ul{list-style:none;}.blog .container ul:not(.card-grid) li,.webinar-wrap ul li{list-style:none;font-weight:normal;padding-left:15px;margin:0 0 10px 20px;}.blog .container ul:not(.card-grid) li:before,.webinar-wrap ul li:before{content:"•";color:var(--color-dark-teal);display:inline-block;margin-left:-20px;width:20px;}.blog .container ul.no-bullets{list-style:none;}.blog .container ul.no-bullets li{list-style:none;font-weight:normal;padding:0;margin-left:0 !important;}.blog .container ul.no-bullets li:before{content:"";}.featured-list li{list-style-type:none;margin-top:80px;margin-bottom:80px;}.featured-list li p{margin-bottom:0;}.featured-list li:first-child{margin-top:60px;}.featured-list li img{margin-right:auto;margin-left:auto;}table,dl,dt,dd,tbody,tfoot,thead,tr,th,td{line-height:26px;word-break:keep-all;}.table-responsive{margin-top:32px;width:100%;}.table-responsive table,.table-responsive table td{border:1px solid var(--color-light-gray);}.table-responsive table th,.table-responsive table td th{text-align:center;font-weight:600;}.table-responsive table td,.table-responsive table td td{padding:10px;}.table-responsive th,.table-responsive td{padding:16px;}.table-center-text th,.table-left-text th{border-bottom:2px solid var(--color-dark-gray);background-color:var(--color-white) !important;font-weight:bold;font-size:14px;line-height:24px;}.table-center-text tr:nth-child(odd),.table-left-text tr:nth-child(odd){background-color:var(--color-light-gray);}.table-left-text tr td{text-align:left;}.table-center-text tr td{text-align:center;}.table-left-text-label-column th{border-bottom:2px solid var(--color-dark-gray);background-color:var(--color-white) !important;font-weight:bold;}.table-left-text-label-column tr:nth-child(odd){background-color:var(--color-light-gray);}.table-left-text-label-column tr th:nth-child(2),.table-left-text-label-column tr td:nth-child(2){border-left:2px solid var(--color-dark-gray) !important;}.table-left-text-label-column td:first-child{font-weight:bold;text-align:left;}.table-merged-cells{border:1px solid var(--color-dark-gray);text-align:center;}.table-merged-cells td{border:1px solid var(--color-dark-gray);background-color:var(--color-white) !important;}.table-merged-cells th{background-color:var(--color-light-gray) !important;border:1px solid var(--color-dark-gray);}blockquote{border-left:5px solid var(--color-elastic-teal);padding-left:20px;line-height:32px;font-size:20px;font-weight:400;}.clearfix:before,.clearfix:after{content:" ";display:table;}.clearfix:after{clear:both;}.common-container{width:100%;max-width:748px;margin-right:auto;margin-left:auto;}.full-width-features{padding-left:15px;padding-right:15px;width:100%;}.paragraph-caption,.paragraph-caption p{font-size:12px;font-style:normal;font-weight:400;line-height:130%;margin:16px 0 8px 0;text-decoration:none;}.nowrap{color:#fff;font-size:18px;white-space:nowrap;}.unscroll{position:fixed;width:100%;}code{display:inline;white-space:normal;}code pre{box-sizing:border-box;-moz-box-sizing:border-box;webkit-box-sizing:border-box;display:inline-block;white-space:pre-wrap;white-space:-moz-pre-wrap;white-space:-pre-wrap;white-space:-o-pre-wrap;word-wrap:break-word;width:100%;overflow-x:auto;-webkit-border-radius:0px;-moz-border-radius:0px;-ms-border-radius:0px;border-radius:0px;}pre{box-sizing:border-box;-moz-box-sizing:border-box;webkit-box-sizing:border-box;display:inline-block;white-space:pre-wrap;white-space:-moz-pre-wrap;white-space:-pre-wrap;white-space:-o-pre-wrap;word-wrap:break-word;width:100%;overflow-x:auto;}pre.prettyprint{background-color:#f0f0f0;font-size:15px;margin-bottom:15px;padding:10px;word-break:break-word !important;white-space:pre-wrap !important;border-top:0px none;border-right:0px none;border-bottom:0px none;border-left:3px solid #39BDB1;-webkit-border-radius:0px;-moz-border-radius:0px;-ms-border-radius:0px;border-radius:0px;}span[data-type=inlineCode]{display:inline;white-space:normal;font-size:87.5%;color:var(--color-dark-pink);word-break:break-word;font-family:SFMono-Regular,Menlo,Monaco,Consolas,"Liberation Mono","Courier New",monospace;}.literal{background:#f0f0f0;color:#555;display:inline;padding:0 5px;vertical-align:middle;width:auto;white-space:normal;}.grey-bg{background:#f7f7f7;}.white-bg{background-color:#fff;}.bdr-btm-e0e0e0{border-bottom:1px solid #ccc;}.bdr-btm-ccc{border-bottom:1px solid #ccc;}.intro-paragraph{line-height:29px;font-size:18px;}.intro-paragraph p{line-height:29px;font-size:18px;}.white-box{background-color:#fff;box-shadow:0px 10px 20px 0px rgba(152,162,179,0.15),0px 2px 6px 0px rgba(152,162,179,0.25);padding:20px;}.form-control:focus{-moz-box-shadow:none;-webkit-box-shadow:none;-o-box-shadow:none;-ms-box-shadow:none;box-shadow:none;}.note{margin-bottom:20px;color:#f00;font-weight:600;text-transform:uppercase;}.quotes{height:120px;opacity:0.5;filter:alpha(opacity=50);}.grey-border-box{-webkit-box-align:center;align-items:center;-webkit-box-pack:justify;justify-content:space-between;width:100%;max-width:825px;border:1px solid rgb(212,218,229);border-radius:10px;background:rgb(255,255,255);padding:16px;font-size:14px;line-height:24px;}.grey-border-box p{font-size:14px;line-height:24px;}.grey-border-box a{line-height:26px;font-size:16px;}.grey-border-box .white-block{display:-moz-box;display:-ms-flexbox;display:-webkit-flex;display:flex;}.grey-border-box .white-block span{color:#0078a0;display:inline-block;line-height:60px;text-align:center;width:60px;height:60px;font-size:24px;font-weight:600;border-top:1px solid #0078a0;border-right:1px solid #0078a0;border-bottom:1px solid #0078a0;border-left:1px solid #0078a0;-webkit-border-radius:50%;-moz-border-radius:50%;-ms-border-radius:50%;border-radius:50%;}.skip-links{position:absolute;top:8px;left:8px;z-index:9999;}.skip-links .euiSkipLink{color:#fff;padding:8px 24px;font-size:0.875rem;font-weight:bold;line-height:1.5;min-height:40px;border:2px solid #0B64DD;border-radius:5px;text-decoration:none;position:relative;}.skip-links .euiSkipLink:hover{color:#005A9E;}.skip-links .euiSkipLink:focus{color:#fff;text-decoration:none;}@media screen and (min-width:992px){.statistics-title{color:var(--color-blurple);font-size:140px;line-height:130%;}.statistics-title-percent{color:var(--color-blurple);font-size:70px;line-height:200%;}.statistics-title-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:80px;line-height:80%;}.statistics-title-percent-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:50px;line-height:90%;}}@media screen and (max-width:991px){.statistics-title{color:var(--color-blurple);font-size:110px;line-height:105%;}.statistics-title-percent{color:var(--color-blurple);font-size:55px;line-height:150%;}.statistics-title-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:80px;line-height:80%;}.statistics-title-percent-80px{color:var(--color-blurple);font-family:'Space Mono',monospace;font-size:50px;line-height:90%;}}@media screen and (max-width:767px){.grey-border-box{display:block;}.grey-border-box .col{display:block;float:none;width:100%;}.grey-border-box .white-block{border-bottom:1px solid #ccc;border-right:0 none;-webkit-border-radius:6px 6px 0 0;-moz-border-radius:6px 6px 0 0;-ms-border-radius:6px 6px 0 0;border-radius:6px 6px 0 0;padding-bottom:55px;}.grey-border-box .product-icon{position:relative;top:50%;margin-bottom:-52px;right:0;bottom:0;left:50%;z-index:100;-webkit-transform:translate(-50%,-50%);-moz-transform:translate(-50%,-50%);-ms-transform:translate(-50%,-50%);transform:translate(-50%,-50%);}}img.greyscale{filter:url("data:image/svg+xml;utf8,<svg xmlns='http://www.w3.org/2000/svg'><filter ….2525 0 0 0.2525 0.2525 0.2525 0 0 0 0 0 1 0'/></filter></svg>#greyscale");filter:url("data:image/svg+xml;utf8,<svg xmlns='http://www.w3.org/2000/svg'><filter id='greyscale'><feColorMatrix type='matrix' values='0.3333 0.3333 0.3333 0 0 0.3333 0.3333 0.3333 0 0 0.3333 0.3333 0.3333 0 0 0 0 0 1 0'/></filter></svg>#greyscale");filter:grey;-webkit-filter:greyscale(100%);-webkit-backface-visibility:hidden;}.shadow-light{-moz-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;-webkit-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;-o-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;-ms-box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;box-shadow:0 10px 20px 0 rgba(152,162,179,0.1),0 2px 6px 0 rgba(152,162,179,0.25) !important;}.shadow-dark{-moz-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;-webkit-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;-o-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;-ms-box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;box-shadow:0 10px 20px 0 rgba(83,89,102,0.1),0 2px 6px 0 rgba(83,89,102,0.25) !important;}figure{margin:0;text-align:center;}figure i,.border-circle{background-position:center center;background-repeat:no-repeat;background-size:120% auto;display:block;height:170px;margin:0 auto;overflow:hidden;width:170px;border-top:6px solid #ccc;border-right:6px solid #ccc;border-bottom:6px solid #ccc;border-left:6px solid #ccc;-webkit-border-radius:340px;-moz-border-radius:340px;-ms-border-radius:340px;border-radius:340px;}figcaption{text-align:center;font-size:14px;line-height:24px;font-style:italic;}.circle-bg{background:#fff;-webkit-border-radius:104px;-moz-border-radius:104px;-ms-border-radius:104px;border-radius:104px;-moz-box-shadow:0px 2px 5px rgba(0,0,0,0.2);-webkit-box-shadow:0px 2px 5px rgba(0,0,0,0.2);-o-box-shadow:0px 2px 5px rgba(0,0,0,0.2);-ms-box-shadow:0px 2px 5px rgba(0,0,0,0.2);box-shadow:0px 2px 5px rgba(0,0,0,0.2);width:104px;height:104px;position:relative;display:inline-block;z-index:1;}.circle-bg img{bottom:0;height:70%;left:0;margin:auto;position:absolute;right:0;top:0;width:70%;}.circle-bg:before{content:" ";vertical-align:middle;height:100%;}.circle-bg .graph-img-center{left:6px;}.image-32-icon{height:32px !important;margin:0 0 16px !important;width:32px !important;}.image-64-icon{height:64px !important;margin:0 auto 16px !important;width:64px !important;}.onlyFadeIn{-webkit-animation:onlyFadeIn 1s;animation:onlyFadeIn 1s;}@-webkit-keyframes onlyFadeIn{0%{opacity:0;}100%{opacity:1;}}@keyframes onlyFadeIn{0%{opacity:0;}100%{opacity:1;}}.img-overflow{max-width:100%;height:auto;}@media (min-width:992px){.img-overflow{max-width:unset;max-height:500px;}}.embed-container iframe,.video iframe{border:0;height:287px;width:100%;}.play-icon{bottom:0;display:block;height:50px;left:0;margin:auto;position:absolute;right:0;top:0;z-index:2;}.video-thumb{position:relative;display:inline-block;max-width:100%;border-radius:10px;overflow:hidden;}.video-thumb .play-btn{bottom:0;height:64px;left:0;margin:auto;position:absolute;right:0;top:0;width:64px;}@media screen and (max-width:600px){.video-thumb{max-width:295px;}}.video-content-wrapper h3{color:var(--color-dark-blue);}.video-content-wrapper h3 a{color:var(--color-dark-blue);}.right-arrow{background-image:url(/static-res/images/right-blue-arrow.png);background-repeat:no-repeat;background-position:right 4px;padding-right:25px !important;color:#00a9e5;font-size:16px;display:inline-block;}.right-arrow:hover{color:#00a9e5;}.right-arrow .upgrade-icon{background-image:url(/static-res/images/refresh-icon.svg);background-repeat:no-repeat;background-position:0px 0px;display:inline-block;height:17px;padding-left:28px;vertical-align:middle;}.right-arrow:before{content:" ";vertical-align:middle;height:100%;}.right-arrow .graph-img-center{left:6px;}.checkmark{height:63px;width:63px;}.position-relative{position:relative;}.position-absolute{position:absolute;}@media screen and (min-width:768px) and (max-width:991px){.container{max-width:100% !important;}}@media screen and (max-width:767px){.container{width:100%;max-width:unset;}.common-container{width:100%;}.no-gutters{margin-right:0;margin-left:0;}.no-gutters>[class*=col-]{padding-right:0;padding-left:0;}}@media screen and (max-width:480px){.table-responsive table,.table-responsive table td{border:1px solid #ccc;}.table-responsive table th,.table-responsive table td th{text-align:center;font-weight:600;font-size:13px;}.table-responsive table td,.table-responsive table td td{padding:5px;font-size:13px;line-height:18px;}.table-responsive table td p a{font-size:13px;line-height:18px;}}a{color:var(--link-color);-webkit-transition:all 300ms ease-in-out;transition:all 300ms ease-in-out;text-decoration:underline;font-weight:600;}a:hover,a:focus{color:var(--link-hover-color);text-decoration:underline;box-shadow:none !important;}a.whiteurl{color:var(--color-white);}a.stretched-link:before{position:absolute;top:0;right:0;bottom:0;left:0;z-index:1;pointer-events:auto;content:"";background:transparent !important;background-color:rgba(0,0,0,0);}.btn-tertiary,.cta-link,a.btn-tertiary:not([href]):not([tabindex]){cursor:pointer;display:inline-block;text-decoration:none;color:var(--button-tertiary-color);font-weight:600;}.btn-tertiary svg,.cta-link svg,a.btn-tertiary:not([href]):not([tabindex]) svg{-webkit-transition:all 100ms ease-in;transition:all 100ms ease-in;left:8px;position:relative;height:inherit;}.btn-tertiary svg path,.cta-link svg path,a.btn-tertiary:not([href]):not([tabindex]) svg path{stroke:var(--button-tertiary-color);}.btn-tertiary:hover,.cta-link:hover,a.btn-tertiary:not([href]):not([tabindex]):hover{text-decoration:none;color:var(--button-tertiary-hover-color);}.btn-tertiary:hover svg,.cta-link:hover svg,a.btn-tertiary:not([href]):not([tabindex]):hover svg{left:14px;}.btn-tertiary:hover svg path,.cta-link:hover svg path,a.btn-tertiary:not([href]):not([tabindex]):hover svg path{stroke:var(--button-tertiary-hover-color);}.btn-tertiary:focus-visible,.cta-link:focus-visible,a.btn-tertiary:not([href]):not([tabindex]):focus-visible{text-decoration:none;color:var(--button-tertiary-hover-color);outline:2px solid var(--button-tertiary-active-offset-color);outline-offset:4px;border-radius:4px;padding-right:12px;}.btn-tertiary:focus-visible svg,.cta-link:focus-visible svg,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg{stroke:var(--button-tertiary-hover-color);}.btn-tertiary:focus-visible svg path,.cta-link:focus-visible svg path,a.btn-tertiary:not([href]):not([tabindex]):focus-visible svg path{stroke:var(--button-tertiary-hover-color);}.gdpr-text{margin-top:10px;}.gdpr-text p{font-size:12px;line-height:18px;opacity:1;}#marketo-fe-form{position:relative;}#marketo-fe-form .mktoForm{position:relative;width:100% !important;}#marketo-fe-form .mktoForm .mktoOffset{display:none;}#marketo-fe-form .mktoForm .mktoLabel,#marketo-fe-form .mktoForm legend{font-size:14px;font-weight:600;line-height:24px !important;text-align:left;width:auto !important;padding-top:0;margin-left:0;float:none;display:block;margin-bottom:4px;}#marketo-fe-form .mktoForm .mktoLabel[for=tempCheckBoxforForm]{margin-left:23px;width:calc(100% - 23px) !important;font-weight:normal;}#marketo-fe-form .mktoForm p,#marketo-fe-form .mktoForm #gdpr{opacity:1;margin-bottom:8px;}#marketo-fe-form .mktoForm .mktoFormCol{width:100%;min-height:unset;margin-bottom:0 !important;}#marketo-fe-form .mktoForm .mktoFieldWrap{margin-right:0px !important;width:100%;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=hidden]{display:none;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url]{-webkit-appearance:none;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url],#marketo-fe-form .mktoForm .mktoFieldWrap select{width:100% !important;color:var(--color-ink);height:50px;line-height:40px !important;min-width:190px;padding:8px !important;font-size:14px;font-weight:400;border:1px solid var(--color-dark-gray);border-radius:0;position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url]:focus,#marketo-fe-form .mktoForm .mktoFieldWrap select:focus{border-bottom:2px solid var(--color-elastic-blue);outline:none !important;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url].mktoInvalid,#marketo-fe-form .mktoForm .mktoFieldWrap select.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=text].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=email].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=number].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap input[type=url].mktoInvalid:focus,#marketo-fe-form .mktoForm .mktoFieldWrap select.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap select{background-color:#fff;position:relative;line-height:normal !important;padding:8px 32px 8px 8px !important;appearance:none;-webkit-appearance:none;-moz-appearance:none;-ms-appearance:none;background-image:url("/static-res/images/svg/icon-down-arrow-16-blue.svg");background-repeat:no-repeat;background-position:98% 50%;background-size:16px;}#marketo-fe-form .mktoForm .mktoFieldWrap textarea{border:1px solid var(--color-dark-gray);font-size:14px;height:6em;width:100% !important;padding:8px 16px;margin-bottom:32px;padding:8px 16px;position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap textarea:focus{outline:none;border-bottom:2px solid var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap textarea.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#marketo-fe-form .mktoForm .mktoFieldWrap textarea.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]{height:auto !important;width:16px !important;position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]:after{background-color:var(--color-white);content:"";height:17px;left:-2px;position:absolute;top:-2px;width:17px;border-top:1px solid var(--color-dark-gray);border-right:1px solid var(--color-dark-gray);border-bottom:1px solid var(--color-dark-gray);border-left:1px solid var(--color-dark-gray);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]:checked:after{background-color:var(--color-elastic-blue);border-color:var(--color-elastic-blue);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox]:checked:before{content:"";height:12px;left:3px;position:absolute;top:-2px;width:7px;z-index:1;border-right:2px solid rgb(255,255,255);border-bottom:2px solid rgb(255,255,255);-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}#marketo-fe-form .mktoForm .mktoFieldWrap input[type=checkbox][disabled]:after{border-color:#f8f9fb;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoRadioList{position:relative;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoRadioList label{margin-left:28px;margin-bottom:16px;line-height:14px;}#marketo-fe-form .mktoForm .mktoFieldWrap::-webkit-input-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap::-moz-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap:-ms-input-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap:-moz-placeholder{font-size:14px;line-height:24px;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoCheckboxList{margin:16px 0px 10px 0px;width:100% !important;z-index:1;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoCheckboxList>label{font-size:14px;margin-bottom:8px;margin-left:32px;min-height:25px;margin-top:-2px;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoHtmlText{width:100% !important;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoGutter.mktoHasWidth{display:none;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError{left:0;right:unset !important;bottom:unset !important;position:relative !important;z-index:0;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError .mktoErrorArrowWrap{display:none;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError .mktoErrorMsg{background-image:none !important;background-color:transparent !important;border:none !important;max-width:unset !important;box-shadow:none !important;text-shadow:none !important;color:var(--color-dark-orange) !important;font-size:14px !important;line-height:24px !important;margin-top:4px !important;padding-left:0;clear:both;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoError .mktoErrorMsg .mktoErrorDetail{display:inline !important;}#marketo-fe-form .mktoForm .mktoOffset,#marketo-fe-form .mktoForm .mktoRequiredField .mktoAsterix{display:none;}#marketo-fe-form .mktoForm .mktoButtonRow{width:100%;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap{margin-left:unset !important;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton{background:var(--color-elastic-blue);color:var(--color-white);display:inline-block;font-size:16px;font-weight:600;font-family:"MierB","Inter",Arial,sans-serif;height:50px;line-height:30px;margin:0;min-width:150px;padding:0 16px !important;text-align:center;text-transform:none;width:100%;border-top:1px solid var(--color-elastic-blue);border-right:1px solid var(--color-elastic-blue);border-bottom:1px solid var(--color-elastic-blue);border-left:1px solid var(--color-elastic-blue);-webkit-border-radius:4px !important;-moz-border-radius:4px !important;-ms-border-radius:4px !important;border-radius:4px !important;-moz-transition:all 200ms ease-in;-webkit-transition:all 200ms ease-in;-o-transition:all 200ms ease-in;-ms-transition:all 200ms ease-in;transition:all 200ms ease-in;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:hover{background:var(--color-dark-blue);border-color:var(--color-dark-blue);outline:none !important;}#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:active,#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:focus,#marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton:active:focus{border-color:var(--color-light-blue);outline:none !important;}.error-message{color:var(--color-dark-orange);font-size:14px;}#fallback-form{position:relative;}#fallback-form .fallback-form-title{font-weight:600;padding-bottom:10px;}#fallback-form .debug{border:1px solid red;color:red;position:absolute;top:-20px;display:none;}#fallback-form .input-wrapper p{font-size:12px;line-height:18px;}#fallback-form form.fallback{position:relative;text-align:left;max-width:100%;}#fallback-form form.fallback .input-wrapper input{width:100%;outline:none;}#fallback-form form.fallback .input-wrapper input[type=text],#fallback-form form.fallback .input-wrapper input[type=email],#fallback-form form.fallback .input-wrapper input[type=number],#fallback-form form.fallback .input-wrapper input[type=tel],#fallback-form form.fallback .input-wrapper input[type=url],#fallback-form form.fallback .input-wrapper select{width:100% !important;color:var(--color-ink);height:50px;max-height:50px;line-height:40px !important;min-width:190px;padding-left:8px !important;padding-right:8px !important;font-size:14px;font-weight:400;border-radius:0;border:1px solid var(--color-dark-gray);}#fallback-form form.fallback .input-wrapper input[type=text]:focus,#fallback-form form.fallback .input-wrapper input[type=email]:focus,#fallback-form form.fallback .input-wrapper input[type=number]:focus,#fallback-form form.fallback .input-wrapper input[type=tel]:focus,#fallback-form form.fallback .input-wrapper input[type=url]:focus,#fallback-form form.fallback .input-wrapper select:focus{border-bottom:2px solid var(--color-elastic-blue);outline:none !important;}#fallback-form form.fallback .input-wrapper input[type=text].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=email].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=number].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=tel].mktoInvalid,#fallback-form form.fallback .input-wrapper input[type=url].mktoInvalid,#fallback-form form.fallback .input-wrapper select.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#fallback-form form.fallback .input-wrapper input[type=text].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=email].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=number].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=tel].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper input[type=url].mktoInvalid:focus,#fallback-form form.fallback .input-wrapper select.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper textarea{border:1px solid var(--color-dark-gray);height:4.5em;width:100% !important;margin-bottom:32px;}#fallback-form form.fallback .input-wrapper textarea:focus{outline:none;border-bottom:2px solid var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper textarea.mktoInvalid{border-bottom:2px solid var(--color-dark-orange);}#fallback-form form.fallback .input-wrapper textarea.mktoInvalid:focus{border-bottom:2px solid var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper input[type=checkbox]{height:auto !important;position:relative;width:16px !important;}#fallback-form form.fallback .input-wrapper input[type=checkbox]:after{background-color:var(--color-white);content:"";height:16px;left:0;position:absolute;top:0;width:16px;border-top:1px solid var(--color-dark-gray);border-right:1px solid var(--color-dark-gray);border-bottom:1px solid var(--color-dark-gray);border-left:1px solid var(--color-dark-gray);}#fallback-form form.fallback .input-wrapper input[type=checkbox]:checked:after{background-color:var(--color-elastic-blue);border-color:var(--color-elastic-blue);}#fallback-form form.fallback .input-wrapper input[type=checkbox]:checked:before{content:"";height:12px;left:5px;position:absolute;top:0px;width:7px;z-index:1;border-right:2px solid rgb(255,255,255);border-bottom:2px solid rgb(255,255,255);-webkit-transform:rotate(45deg);-moz-transform:rotate(45deg);-ms-transform:rotate(45deg);transform:rotate(45deg);}#fallback-form form.fallback .input-wrapper::-webkit-input-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback .input-wrapper::-moz-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback .input-wrapper:-ms-input-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback .input-wrapper:-moz-placeholder{font-size:14px;line-height:24px;}#fallback-form form.fallback label{font-size:14px;font-weight:600;line-height:24px !important;text-align:left;width:100% !important;margin-bottom:0;margin-top:24px;}#fallback-form form.fallback .asterix{font-weight:700;color:var(--color-dark-orange);}#fallback-form form.fallback .submit-form{cursor:pointer;min-width:140px;width:max-content;padding-right:16px;padding-left:16px;-webkit-transition:all 200ms ease-in;transition:all 200ms ease-in;background-color:var(--color-elastic-blue);color:var(--color-white);height:50px;font-weight:700;text-align:center;letter-spacing:0.025em;margin:0;border:1px solid var(--color-elastic-blue);border-radius:4px;cursor:pointer;}#fallback-form form.fallback .submit-form:hover{background:var(--color-dark-blue);border-color:var(--color-dark-blue);}#fallback-form form.fallback .submit-form:active{border-color:var(--color-light-blue);}#fallback-form form.fallback .submit-form:focus{box-shadow:none;}.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap,.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap{margin-bottom:24px;}.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=url],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=text],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=email],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=number],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=tel],.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap input[type=url]{height:40px !important;}.mkto-form-wrapper.long-form #marketo-fe-form .mktoForm .mktoFieldWrap select,.marketo-form.long-form #marketo-fe-form .mktoForm .mktoFieldWrap select{height:auto !important;}.mkto-form-wrapper.inline #marketo-fe-form{position:relative;width:100%;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm{width:100% !important;padding:0px;position:relative;display:inline-flex;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoOffset,.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoAsterix{display:none;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol{margin-bottom:0 !important;float:none;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap{width:100%;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoHtmlText{display:none !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoHtmlText p{margin:0 !important;line-height:0 !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap input[type=email],.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap select{min-width:289px;width:100% !important;max-width:350px !important;margin-top:4px;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError{position:absolute !important;padding-bottom:unset;bottom:-52px !important;width:max-content;z-index:99 !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorArrowWrap{display:block;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorArrowWrap .mktoErrorArrow{background:rgba(255,255,255,0.9);border:1px solid var(--color-dark-orange) !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorMsg{border:1px solid var(--color-dark-orange) !important;color:var(--color-dark-orange) !important;padding:8px !important;background:rgba(255,255,255,0.9) !important;border-radius:0 !important;width:auto !important;margin-top:7px !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow{margin-top:4px;margin-left:16px;width:max-content !important;align-self:flex-end;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap{margin-left:0px !important;}.mkto-form-wrapper.inline .success-message{max-width:455px;width:100%;margin:0 auto;}.mkto-form-wrapper.inline.fallback{width:100%;max-width:455px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback{display:inline-flex;align-items:end;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper input,.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper select{min-width:307px;width:100% !important;max-width:350px !important;margin-top:4px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper{margin-top:4px;margin-left:16px;}.mkto-form-wrapper.inline.center #marketo-fe-form{margin-left:auto;margin-right:auto;}.mkto-form-wrapper.inline.center #marketo-fe-form .mktoForm{justify-content:center;}.mkto-form-wrapper.inline.center.fallback{max-width:455px !important;margin-left:auto;margin-right:auto;}.mkto-form-wrapper.inline.center.fallback #fallback-form{text-align:center;}.mkto-form-wrapper.inline.center .error-message{margin-top:16px;}@media screen and (max-width:1200px){.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap input[type=email],.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap select{min-width:270px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback{width:100%;margin:0;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper input,.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper select{min-width:270px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper{width:100%;}}@media screen and (max-width:991px){.react-tabs .react-tabs__tab{font-size:14px;}.mkto-form-wrapper.inline{margin-left:auto;margin-right:auto;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm{position:relative;display:block;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap{width:100%;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap input[type=email],.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap select{width:100% !important;max-width:unset !important;min-width:unset;margin-top:0;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError{width:auto;position:relative !important;top:8px;bottom:unset !important;padding-bottom:0;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorMsg{padding:0 !important;width:auto !important;border:none !important;background:transparent !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoFormCol .mktoFieldWrap .mktoError .mktoErrorArrowWrap{display:none !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow{margin-top:16px;margin-left:0;width:100% !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap{margin-left:0px !important;}.mkto-form-wrapper.inline #marketo-fe-form .mktoForm .mktoButtonRow .mktoButtonWrap .mktoButton{width:100% !important;}.mkto-form-wrapper.inline.fallback{max-width:455px;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback{display:block;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper input,.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .input-wrapper select{width:100% !important;max-width:unset !important;min-width:unset;margin-top:0;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper{margin:16px 0 0 0;}.mkto-form-wrapper.inline.fallback #fallback-form form.fallback .button-wrapper .submit-form{width:100% !important;}}.success-message{background:var(--color-white);color:var(--color-dark-teal) !important;border:1px solid var(--color-dark-teal) !important;padding:8px;text-align:center;}.success-message a{color:var(--color-dark-teal) !important;}.filter-wrapper{padding:32px 0px;}.filter-wrapper .header{display:flex;justify-content:space-between;border-bottom:1px solid var(--color-dark-gray);}.filter-wrapper .filter-row{width:100%;display:grid;grid-column-gap:32px;grid-row-gap:32px;grid-template-columns:1fr 1fr 1fr 1fr;align-items:baseline;}.filter-wrapper .filter-row .filter-column{width:100%;}.filter-wrapper .filter-row .filter-label{font-size:14px;font-weight:600;margin-bottom:5px;}@media screen and (max-width:991px){.filter-wrapper .container{padding:0 15px;}}@media screen and (max-width:768px){.filter-wrapper .header{padding-bottom:8px;}.filter-wrapper .container{padding:0 15px;}.filter-wrapper .filter-row{grid-template-columns:1fr 1fr;grid-template-rows:auto auto;}}@media screen and (max-width:575px){.filter-wrapper .header{display:flex;flex-direction:column;}.filter-wrapper .filter-row{grid-template-columns:1fr;}.filter-wrapper .filter-row .filter-column{margin:0 auto;width:300px;}}.card-small-padding{padding:8px;}.card-medium-padding{padding:16px;}.card-large-padding{padding:32px;}.card-xlarge-padding{padding:40px;}.card-xxlarge-padding{padding:48px;}.card-grid{display:-ms-grid;display:grid;grid-auto-columns:1fr;grid-template-columns:repeat(2,1fr);grid-template-rows:auto auto;grid-row-gap:32px;grid-column-gap:32px;}.card-grid-1x1{margin-right:auto;margin-left:auto;gap:32px;}@media (min-width:992px){.card-grid-1x1{gap:64px;}}.card-grid-1x1,.card-grid-1x1-sidebar{display:grid;justify-content:stretch;grid-auto-columns:1fr;grid-template-areas:".";grid-template-columns:1fr;grid-template-rows:auto;}.card-grid-1x1.col-sm-8,.card-grid-1x1-sidebar.col-sm-8{padding:0px;}.card-grid-1x1 .card-footer div:first-child,.card-grid-1x1-sidebar .card-footer div:first-child{margin-right:24px;}.card-grid-2x1{display:grid;margin-right:auto;margin-left:auto;justify-content:stretch;grid-auto-columns:1fr;grid-template-areas:".";grid-template-columns:repeat(2,1fr);grid-template-rows:auto;}.card-grid-2x1 .card-footer.align-self-left div:first-child{margin-right:24px;}.card-grid-3x1{display:grid;margin-right:auto;margin-left:auto;padding-left:0px;justify-content:stretch;grid-template-areas:".";grid-template-columns:repeat(3,1fr);grid-auto-columns:1fr;grid-template-rows:auto;}.card-grid-3x1 .card-footer.align-self-left div:first-child{margin-right:24px;}.card-grid-4x1{display:grid;margin-right:auto;margin-left:auto;justify-content:stretch;grid-column-gap:32px;grid-row-gap:32px;grid-template-columns:repeat(4,1fr);grid-template-rows:auto;}@media screen and (max-width:991px){.card-grid-3x1{grid-auto-flow:row;grid-template-areas:".";grid-template-columns:1fr 1fr;grid-template-rows:repeat(2,auto);}.card-grid-4x1{grid-row-gap:32px;grid-template-columns:1fr 1fr;grid-template-rows:auto auto;}}@media screen and (max-width:768px){.card-grid-3x1,.card-grid-4x1{grid-template-columns:1fr 1fr;}}@media screen and (max-width:575px){.card-grid-2x1{grid-template-columns:1fr;grid-template-rows:repeat(2,auto);}.card-grid-3x1{grid-template-columns:1fr;grid-template-rows:repeat(3,auto);}.card-grid-4x1{grid-template-columns:1fr;grid-template-rows:repeat(4,auto);}}.react-tabs .react-tabs__tab{cursor:pointer;margin-bottom:-2px;padding:0px 16px;margin-left:0;margin-right:0;}.react-tabs .react-tabs__tab h2{color:var(--color-black);font-size:16px;line-height:24px;padding-bottom:16px;font-weight:400;}.react-tabs .react-tabs__tab:focus{outline:0px none;}.react-tabs .react-tabs__tab:hover{border-bottom:2px solid var(--color-ink);}.react-tabs .react-tabs__tab--selected{color:var(--color-elastic-blue);cursor:text;display:block;margin-bottom:-2px;border-bottom:4px solid var(--carousel-tab-hover-border-color);}.react-tabs .react-tabs__tab--selected h2{color:var(--color-elastic-blue);}.react-tabs .react-tabs__tab--selected:hover{border-color:var(--color-elastic-blue);}.react-tabs .react-tabs__tab-panel{display:none;}.react-tabs .react-tabs__tab-panel--selected{display:block;}.instruction-module .react-tabs ul{border-bottom:0;}.instruction-module .react-tabs .top-tabs .react-tabs__tab{color:rgb(52,55,65);font-weight:400;height:40px;line-height:40px;margin:0px;padding:0px;text-align:center;text-transform:unset;width:200px;border-width:1px;border-style:solid;border-color:rgb(0,120,160);display:flex;justify-content:center;align-items:center;}.instruction-module .react-tabs .top-tabs .react-tabs__tab h2{padding-bottom:2px;}.instruction-module .react-tabs .top-tabs .react-tabs__tab--selected{background-color:var(--color-elastic-blue);}.instruction-module .react-tabs .top-tabs .react-tabs__tab--selected h2{color:#FFFFFF !important;}.instruction-module .react-tabs .vertical-tabs .react-tabs__tab h2{font-size:18px;line-height:22px;font-family:Inter,arial,sans-serif;}@media screen and (min-width:768px){.react-tabs .vertical-tabs .react-tabs__tab-list{border-bottom:0;border-left:1px solid var(--color-dark-gray);}.react-tabs .vertical-tabs .react-tabs__tab{margin-bottom:0;border-left:2px solid transparent;padding:8px 16px;}.react-tabs .vertical-tabs .react-tabs__tab h2{padding:5px 0;}.react-tabs .vertical-tabs .react-tabs__tab:hover{border-bottom:0;border-left:2px solid var(--color-ink);}.react-tabs .vertical-tabs .react-tabs__tab--selected{border-bottom:0;border-left:2px solid var(--color-elastic-blue);}.react-tabs .vertical-tabs .react-tabs__tab--selected:hover{border-left:2px solid var(--color-elastic-blue);}}@media screen and (max-width:767px){.code-carousel .react-tabs .react-tabs__tab-list{display:flex;flex-wrap:wrap;flex-direction:unset;margin-bottom:10px;}.code-carousel .react-tabs .react-tabs__tab{border-bottom:2px solid transparent;}.code-carousel .react-tabs .react-tabs__tab:hover{border-bottom:2px solid var(--color-ink);}.code-carousel .react-tabs .react-tabs__tab--selected{border-bottom:2px solid var(--carousel-tab-border-color);}.code-carousel .react-tabs .react-tabs__tab--selected:hover{border-bottom:4px solid var(--carousel-tab-hover-border-color);}}.carousel .carousel-one-column .react-tabs__tab,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab{color:var(--carousel-tab-color);cursor:pointer;margin-left:0;margin-right:0;position:relative;font-size:16px;line-height:22px;font-weight:700;font-style:normal;}.carousel .carousel-one-column .react-tabs__tab:focus,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab:focus{outline:0px none;}.carousel .carousel-one-column .react-tabs__tab h2,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab h2{color:var(--carousel-tab-color);font-size:16px;line-height:24px;font-weight:400;padding:0px;}.carousel .carousel-one-column .react-tabs__tab--selected,.carousel .carousel-two-column__tab-labels-left .react-tabs__tab--selected{cursor:text;display:block;cursor:text;}.carousel .carousel-one-column .carousel-asset .card-deck-container-block.container,.carousel .carousel-one-column .carousel-asset .illustration-icon-grid-container-block.container,.carousel .carousel-two-column__tab-labels-left .carousel-asset .card-deck-container-block.container,.carousel .carousel-two-column__tab-labels-left .carousel-asset .illustration-icon-grid-container-block.container{padding:0px;}.carousel .carousel-asset-code .carousel-asset-code-block{background-image:url(https://assets.website-files.com/5d35f5b2989a23dd99c4cb9a/5dd5be9fcd567c46f05e5544_image-dots-browser-16-colored.svg);background-repeat:no-repeat;background-position:32px 32px;background-color:var(--color-light-gray);height:500px;overflow-y:scroll;padding:40px 32px 32px;position:relative;-moz-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);-webkit-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);-o-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);-ms-box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);box-shadow:0 10px 20px 0 rgba(152,162,179,0.25);}.carousel .carousel-asset-code .carousel-asset-code-block .react-tabs__tab-panel{height:484px;overflow:auto;width:100%;}.carousel .carousel-asset-code .prettyprint{background-color:var(--color-light-gray);border:0px none !important;left:0;margin:20px auto 0;padding:16px;position:absolute;right:0;width:675px;}.carousel .carousel-asset-code .prettyprint ol li{background:none;}.carousel .carousel-asset-code .prettyprint .linenums{color:#999;display:contents;}.carousel .carousel-asset-code .prettyprint code{display:inline-block;left:0;overflow:hidden;position:relative;vertical-align:top;white-space:pre-wrap;width:90%;word-break:break-word;}.carousel .carousel-description{width:auto;max-width:854px;text-align:center;padding:0px 16px;margin-right:auto;margin-left:auto;}.carousel .icon-text-card-deck .container{padding-left:0px !important;padding-right:0px !important;}.carousel .icon-text-card.card .card-body{text-align:left;}.carousel .icon-text-card.card .card-body h3{font-size:24px;line-height:28px;}.carousel .icon-text-card.card .card-footer{text-align:left;}.carousel .icon-text-card.card .card-footer .card-footer{margin-top:16px !important;}@media screen and (max-width:991px) and (min-width:768px){.carousel .card.icon-text-card{width:100%;}}@media screen and (max-width:768px){.carousel .carousel .description{width:100%;margin:32px auto 8px auto;}}@media screen and (max-width:575px){.carousel .react-tabs__tab h2{font-size:14px !important;line-height:24px !important;}.carousel .icon-text-card-deck{margin:auto;}}.training .rail>div{position:relative;}.euiComboBox .euiFormControlLayoutIcons{position:absolute !important;}.euiComboBox .euiFormControlLayoutCustomIcon--clickable{border:0;background-color:transparent;padding:0;}.euiComboBox .euiFormControlLayoutClearButton{display:flex;justify-content:center;align-items:center;border:1px solid #98A2B3;}.css-1yifmy7-euiBadge-hollow{display:flex;align-items:center;}.euiBadge__iconButton.css-iqdgtj-euiBadge__iconButton-right{border:0;background:transparent;padding:0;}.euiComboBoxOptionsList__rowWrap{border-radius:6px;}.euiComboBoxOptionsList__rowWrap .euiFilterSelectItem{border:0;background:#fff;border-bottom:1px solid #EEF2F7;font-size:14px;font-weight:400;display:flex;align-items:center;}.euiComboBoxOptionsList__rowWrap .euiFilterSelectItem-isFocused{background-color:rgba(0,119,204,0.1);}@media (max-width:767px){.horizontal-scroll-table{width:100vw;overflow-x:auto;}}.comparison-table{max-width:830px;margin:0 auto;}.comparison-table thead{border-bottom:4px solid #000;}.comparison-table th{text-transform:uppercase;font-weight:700;letter-spacing:0.1em;padding:1rem 1.5rem;text-align:center;}.comparison-table td{padding:1rem 1.5rem;}.comparison-table td:not(:first-child){text-align:center;}.comparison-table tbody{font-size:0.875rem;}.comparison-table tbody tr{border-bottom:1px solid #ccc;}.comparison-table tfoot td{width:100%;color:#ccc;}.pricing-card.bg-dark-teal,.list.bg-dark-teal{--bullet-color:var(--color-dark-teal);}.pricing-card.bg-yellow,.list.bg-yellow{--bullet-color:var(--color-yellow);}.pricing-card.bg-elastic-teal,.list.bg-elastic-teal{--bullet-color:var(--color-elastic-teal);}.pricing-card.bg-pink,.list.bg-pink{--bullet-color:var(--color-pink);}.pricing-card.bg-blurple,.list.bg-blurple{--bullet-color:var(--color-blurple);}.list.dark-teal{--bullet-color:var(--color-dark-teal);}.list.yellow{--bullet-color:var(--color-yellow);}.list.elastic-teal{--bullet-color:var(--color-elastic-teal);}.list.pink{--bullet-color:var(--color-pink);}.list.blurple{--bullet-color:var(--color-blurple);}.serverless-pricing-table{width:100%;border-spacing:32px 0;table-layout:fixed;height:1px;}.serverless-pricing-table h4{letter-spacing:-0.04em;line-height:1.1;}.serverless-pricing-table tr{height:100%;}@media (min-width:767px){.serverless-pricing-table tr{border-bottom:1px solid var(--color-dark-gray);}}.serverless-pricing-table tr:last-child{border:none;}@media (max-width:767px){.serverless-pricing-table tr:not(:first-of-type){display:none;visibility:hidden;}}.serverless-pricing-table th{padding:0 0.5rem;}.serverless-pricing-table th:first-child{padding:0 1rem 1.5rem;}.serverless-pricing-table th:last-child{padding-right:0;}.serverless-pricing-table td,.serverless-pricing-table th{padding:0 0.5rem;vertical-align:top;height:100%;}.serverless-pricing-table td:first-child,.serverless-pricing-table th:first-child{padding:1.5rem 1rem 0 1.5rem;}@media (max-width:767px){.serverless-pricing-table td:first-child,.serverless-pricing-table th:first-child{border-bottom:none;padding:0;margin:0;}}.serverless-pricing-table td:last-child,.serverless-pricing-table th:last-child{padding-right:0;}@media (max-width:767px){.serverless-pricing-table td,.serverless-pricing-table th{display:block;height:initial;padding:0;margin:0 0 1.5rem;border-bottom:1px solid var(--color-dark-gray);}}.serverless-pricing-table td.feature-label,.serverless-pricing-table th.feature-label{font-family:'MierB','Inter',Arial,sans-serif;font-size:1.25rem;font-weight:700;letter-spacing:-0.02em;padding:1.5rem 1rem 1.5rem 1.5rem;}.serverless-pricing-table td.feature-label span:last-child,.serverless-pricing-table th.feature-label span:last-child{margin-top:6px;display:block;font-weight:normal;}.serverless-pricing-table td.feature,.serverless-pricing-table th.feature{vertical-align:middle;text-align:center;}.serverless-pricing-table td.feature .card-content,.serverless-pricing-table th.feature .card-content{padding:24px 0;height:100%;display:flex;flex-direction:column;justify-content:center;}.serverless-pricing-table td.feature .card-content *,.serverless-pricing-table th.feature .card-content *{vertical-align:middle;}.serverless-pricing-table .card-content{border-left:1px solid var(--color-dark-gray);border-right:1px solid var(--color-dark-gray);background:#fff;padding:0 0.5rem;}.serverless-pricing-table .card-content__container{padding:0 0.5rem 1.5rem;display:flex;flex-flow:column nowrap;align-items:center;justify-content:space-between;}.serverless-pricing-table .card-content__container p{margin:0;}.serverless-pricing-table .card-content__container .button{width:max-content;margin:0 auto;align-self:end;}.serverless-pricing-table .card-content__content{flex:1;display:grid;}.serverless-pricing-table .card-content.header{display:flex;flex-flow:column nowrap;justify-content:space-between;}.serverless-pricing-table .button-unstyled{padding:8px 24px;min-height:50px;display:inline-block;border:2px solid transparent;width:max-content;margin:0 auto;align-self:end;}.serverless-pricing-table .header{padding:0;}.serverless-pricing-table .card-content__header,.serverless-pricing-table .card-content__includes{padding:0 0.5rem;}.serverless-pricing-table .card-content__includes{padding:2rem 0.5rem;border-top:1px solid var(--color-dark-gray);}.serverless-pricing-table .border-bottom{border-bottom:1px solid var(--color-dark-gray);border-bottom-left-radius:16px;border-bottom-right-radius:16px;}.serverless-pricing-table .borderless-bottom{border-bottom:none;}.serverless-pricing-table .pricing-card{border-top-left-radius:16px;border-top-right-radius:16px;height:100%;padding-top:16px;}.serverless-pricing-table .pricing-card .card-label{padding:0.875rem 0;}.serverless-pricing-table .pricing-card .header{height:100%;border-top-left-radius:16px;border-top-right-radius:16px;border-top:1px solid var(--color-dark-gray);}.serverless-pricing-table .topic-heading{color:var(--color-light-ink);font-size:1rem;font-weight:700;line-height:22px;letter-spacing:0.1em;text-transform:uppercase;}.serverless-pricing-table .price{font-family:'MierB','Inter',Arial,sans-serif;font-size:1.75rem;font-weight:700;letter-spacing:-0.04em;margin-top:8px;}.serverless-pricing-table .list{max-width:250px;width:max-content;margin:0 auto;text-align:left;text-indent:-1.5rem;}.serverless-pricing-table .list li{font-weight:normal;margin-bottom:0.75rem;}.serverless-pricing-table .list li:before{content:"✓";position:relative;top:-2px;left:0;display:inline-block;background-color:var(--bullet-color,black);border-radius:50%;border-style:none;height:16px;width:16px;font-size:0.75rem;line-height:normal;color:#fff;padding-top:0;padding-left:3px;margin-right:0.5rem;text-indent:0;}.mobile-container{border-top:1px solid var(--color-dark-gray);margin:2rem 0 0;padding:1rem 0 0;}@media (min-width:767px){.mobile-container{display:none;visibility:hidden;}}.mobile-container__item{margin:1rem 0;}.mobile-container .topic-heading{padding-bottom:0.25rem;}.mobile-container__price-heading{font-weight:normal;}.mobile-container__price{font-weight:700;}.card-content--stretch .card-content__includes{min-height:373px;}.feature .pricing{margin:0 0 1rem;}.optional-eyebrow{display:block;font-size:1rem;text-transform:uppercase;color:var(--color-dark-teal);letter-spacing:0.1rem;}.pill>.topic-heading{font-size:0.875rem;}#LbltempCheckBoxforForm{padding-left:20px;}#marketo-fe-form .mktoForm .mktoFieldWrap .mktoCheckboxList{margin:0;}#LbltempCheckbox1{padding-left:20px;}#tempCheckbox1{margin-top:5px;}</style></head><body><noscript><iframe src="https://www.googletagmanager.com/ns.html?id=GTM-58RLH5" height="0" width="0" style="display:none;visibility:hidden"></iframe></noscript><div id="__next" data-reactroot=""><div class="progress-container"><div class="progress-bar" id="myBar"></div></div><div class="skip-links"><style data-emotion="css bivm3i-euiSkipLink-euiScreenReaderOnly">.css-bivm3i-euiSkipLink-euiScreenReaderOnly{-webkit-transition:none!important;transition:none!important;}.css-bivm3i-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:none!important;animation:none!important;}.css-bivm3i-euiSkipLink-euiScreenReaderOnly:not(:focus):not(:active):not(:focus-within){position:absolute;inset-block-start:auto;inset-inline-start:-10000px;inline-size:1px;block-size:1px;clip:rect(0 0 0 0);-webkit-clip-path:inset(50%);clip-path:inset(50%);overflow:hidden;margin:-1px;}</style><style data-emotion="css 1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly">.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly{color:#FFF;background-color:#07C;outline-color:#000;-webkit-transition:none!important;transition:none!important;}@media screen and (prefers-reduced-motion: no-preference){.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly{-webkit-transition:-webkit-transform 250ms ease-in-out,background-color 250ms ease-in-out;transition:transform 250ms ease-in-out,background-color 250ms ease-in-out;}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:hover:not(:disabled){-webkit-transform:translateY(-1px);-moz-transform:translateY(-1px);-ms-transform:translateY(-1px);transform:translateY(-1px);}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:active:not(:disabled){-webkit-transform:translateY(1px);-moz-transform:translateY(1px);-ms-transform:translateY(1px);transform:translateY(1px);}}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:none!important;animation:none!important;}.css-1ya6sd9-fill-primary-euiSkipLink-euiScreenReaderOnly:not(:focus):not(:active):not(:focus-within){position:absolute;inset-block-start:auto;inset-inline-start:-10000px;inline-size:1px;block-size:1px;clip:rect(0 0 0 0);-webkit-clip-path:inset(50%);clip-path:inset(50%);overflow:hidden;margin:-1px;}</style><style data-emotion="css 1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly">.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly{display:inline-block;-webkit-appearance:none;-moz-appearance:none;-ms-appearance:none;appearance:none;cursor:pointer;white-space:nowrap;max-inline-size:100%;vertical-align:middle;font-weight:500;padding:0 12px;block-size:32px;line-height:32px;font-size:1.0000rem;line-height:1.4286rem;min-inline-size:112px;border-radius:4px;color:#FFF;background-color:#07C;outline-color:#000;-webkit-transition:none!important;transition:none!important;}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:hover:not(:disabled),.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-text-decoration:underline;text-decoration:underline;}@media screen and (prefers-reduced-motion: no-preference){.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly{-webkit-transition:-webkit-transform 250ms ease-in-out,background-color 250ms ease-in-out;transition:transform 250ms ease-in-out,background-color 250ms ease-in-out;}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:hover:not(:disabled){-webkit-transform:translateY(-1px);-moz-transform:translateY(-1px);-ms-transform:translateY(-1px);transform:translateY(-1px);}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);animation:euiButtonActive 250ms cubic-bezier(.34, 1.61, .7, 1);}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:active:not(:disabled){-webkit-transform:translateY(1px);-moz-transform:translateY(1px);-ms-transform:translateY(1px);transform:translateY(1px);}}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:focus{-webkit-animation:none!important;animation:none!important;}.css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly:not(:focus):not(:active):not(:focus-within){position:absolute;inset-block-start:auto;inset-inline-start:-10000px;inline-size:1px;block-size:1px;clip:rect(0 0 0 0);-webkit-clip-path:inset(50%);clip-path:inset(50%);overflow:hidden;margin:-1px;}</style><a href="#main-content" rel="noreferrer" class="euiSkipLink css-1vo6hom-euiButtonDisplay-s-defaultMinWidth-s-fill-primary-euiSkipLink-euiScreenReaderOnly"><style data-emotion="css 1km4ln8-euiButtonDisplayContent">.css-1km4ln8-euiButtonDisplayContent{block-size:100%;inline-size:100%;display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-box-pack:center;-ms-flex-pack:center;-webkit-justify-content:center;justify-content:center;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;vertical-align:middle;gap:8px;}</style><span class="css-1km4ln8-euiButtonDisplayContent"><span class="eui-textTruncate">Skip to main content</span></span></a></div><header class="jsx-1868079691 primary header-wrapper render-oldNav"><div data-component-theme="" class="oldNav Index_navigation__kp9_7" id="navigation_container"><div class="Index_navigation_container__AMYLs"><div data-component-theme="" class="Index_navigation_header__KYvRr"><a class="brand" href="/"><span class="jsx-1189744782 elastic-logo"><span class="jsx-1189744782 sr-only">Elastic</span><svg width="117" height="40" viewBox="0 0 117 40" fill="none" xmlns="http://www.w3.org/2000/svg" class="jsx-1189744782"><g class="jsx-1189744782"><path d="M40.1527 20.9588C40.1527 17.5986 38.0653 14.6457 34.9257 13.5087C35.0615 12.7959 35.1294 12.0831 35.1294 11.3534C35.1294 5.09121 30.0382 -1.52588e-05 23.793 -1.52588e-05C20.1273 -1.52588e-05 16.7331 1.74797 14.5948 4.70088C13.5426 3.88628 12.2529 3.44505 10.9122 3.44505C7.58591 3.44505 4.88757 6.14339 4.88757 9.46965C4.88757 10.1994 5.02333 10.9122 5.26092 11.574C2.13831 12.6941 0 15.6979 0 19.0411C0 22.4183 2.10437 25.3712 5.24395 26.5083C5.10819 27.2041 5.0403 27.9338 5.0403 28.6635C5.0403 34.9088 10.1146 39.983 16.3598 39.983C20.0255 39.983 23.4196 38.2181 25.5409 35.2651C26.5931 36.0967 27.8829 36.5549 29.2236 36.5549C32.5498 36.5549 35.2482 33.8566 35.2482 30.5303C35.2482 29.8006 35.1124 29.0878 34.8748 28.4259C37.9974 27.3059 40.1527 24.3021 40.1527 20.9588Z" fill="white" class="jsx-1189744782"></path><path d="M15.7824 17.2253L24.5732 21.2304L33.432 13.4578C33.5677 12.8129 33.6186 12.185 33.6186 11.5061C33.6186 6.04156 29.1723 1.59523 23.7077 1.59523C20.4324 1.59523 17.3946 3.20745 15.5448 5.9058L14.0684 13.5596L15.7824 17.2253Z" fill="#FED10A" class="jsx-1189744782"></path><path d="M6.68665 26.5253C6.55088 27.1702 6.49997 27.832 6.49997 28.5108C6.49997 33.9924 10.9633 38.4387 16.4448 38.4387C19.7371 38.4387 22.8088 36.8095 24.6587 34.0942L26.1181 26.4744L24.1665 22.7408L15.3417 18.7187L6.68665 26.5253Z" fill="#24BBB1" class="jsx-1189744782"></path><path d="M6.63518 11.3195L12.6598 12.745L13.9835 5.90583C13.1689 5.27791 12.1507 4.93849 11.0985 4.93849C8.48499 4.93849 6.34668 7.05983 6.34668 9.69029C6.34668 10.2503 6.4485 10.8104 6.63518 11.3195Z" fill="#EF5098" class="jsx-1189744782"></path><path d="M6.10983 12.762C3.42846 13.6444 1.54471 16.224 1.54471 19.0581C1.54471 21.8243 3.25875 24.2851 5.82133 25.2694L14.2728 17.6326L12.7284 14.3233L6.10983 12.762Z" fill="#1BA9F5" class="jsx-1189744782"></path><path d="M26.186 34.0942C27.0176 34.7221 28.0189 35.0785 29.0541 35.0785C31.6676 35.0785 33.8059 32.9571 33.8059 30.3267C33.8059 29.7497 33.7041 29.1896 33.5174 28.6805L27.5098 27.2719L26.186 34.0942Z" fill="#93C83E" class="jsx-1189744782"></path><path d="M27.4075 25.6937L34.0261 27.238C36.7245 26.3555 38.5912 23.776 38.5912 20.9249C38.5912 18.1757 36.8772 15.6979 34.3146 14.7306L25.6595 22.3165L27.4075 25.6937Z" fill="#0B64DD" class="jsx-1189744782"></path><path fill-rule="evenodd" clip-rule="evenodd" d="M60.3483 29.8175V9.96179H62.4187V29.8175H60.3483ZM56.1393 28.0865L56.937 28.0017L56.9879 29.6309C54.8835 29.9194 53.0846 30.0721 51.5912 30.0721C49.6056 30.0721 48.197 29.4951 47.3655 28.3411C46.5339 27.1871 46.1266 25.3882 46.1266 22.9614C46.1266 18.1077 48.0613 15.6809 51.9136 15.6809C53.7804 15.6809 55.172 16.207 56.0884 17.2422C57.0048 18.2775 57.463 19.9236 57.463 22.1468L57.3443 23.7251H48.214C48.214 25.2524 48.4855 26.3895 49.0456 27.1192C49.6056 27.8489 50.556 28.2223 51.9306 28.2223C53.3222 28.2562 54.7138 28.2053 56.1393 28.0865ZM55.3926 22.0959C55.3926 20.3988 55.1211 19.1939 54.578 18.4981C54.035 17.8023 53.1525 17.4459 51.9306 17.4459C50.7087 17.4459 49.7753 17.8192 49.1644 18.549C48.5534 19.2787 48.231 20.4667 48.214 22.0959H55.3926ZM75.5031 26.9665V20.1612C75.5031 18.6338 75.1468 17.4968 74.417 16.784C73.7042 16.0543 72.5672 15.6979 71.0059 15.6979H65.6941V17.5307H71.1417C71.8375 17.5307 72.3975 17.7344 72.8048 18.1417C73.2121 18.549 73.4157 19.2278 73.4157 20.1612V21.3491L69.0712 21.7564C67.6117 21.8922 66.5426 22.2995 65.8638 22.9274C65.1849 23.5553 64.8455 24.5566 64.8455 25.8973C64.8455 27.255 65.1849 28.2902 65.8468 29.0029C66.5087 29.7327 67.476 30.0891 68.7488 30.0891C70.4119 30.0891 72.0581 29.7836 73.7212 29.0539C74.3557 29.6588 75.3493 29.648 76.5572 29.6349H76.5574H76.5576H76.5579C76.7391 29.6329 76.925 29.6309 77.1154 29.6309L77.2172 27.798C77.2172 27.798 75.5031 27.6623 75.5031 26.9665ZM69.0882 28.3411C67.6796 28.3411 66.9838 27.4925 66.9838 25.7955C66.9838 25.0318 67.1535 24.4378 67.5269 24.0305C67.9002 23.6232 68.4942 23.3856 69.3258 23.3178L73.4157 22.9274V27.4925L72.7878 27.7132C71.5829 28.1374 70.344 28.3411 69.0882 28.3411ZM83.5982 17.5477C81.5956 17.5477 80.5774 18.2435 80.5774 19.6521C80.5774 20.297 80.815 20.7552 81.2732 21.0267C81.7314 21.2983 82.7836 21.5698 84.4297 21.8583C86.0759 22.1468 87.2299 22.5371 87.9088 23.0632C88.5876 23.5724 88.927 24.5397 88.927 25.9652C88.927 27.3908 88.4688 28.426 87.5524 29.0878C86.6359 29.7497 85.3122 30.0891 83.5473 30.0891C82.4102 30.0891 78.5918 29.6648 78.5918 29.6648L78.7106 27.8659C79.0533 27.8978 79.3815 27.9289 79.6954 27.9586C81.3864 28.1186 82.6624 28.2393 83.5642 28.2393C84.6334 28.2393 85.448 28.0696 86.008 27.7302C86.5681 27.3908 86.8566 26.8138 86.8566 26.0161C86.8566 25.2185 86.619 24.6754 86.1438 24.3869C85.6686 24.0984 84.6164 23.8269 82.9872 23.5724C81.358 23.3178 80.204 22.9444 79.5252 22.4353C78.8463 21.9432 78.5069 21.0098 78.5069 19.6691C78.5069 18.3284 78.9821 17.3271 79.9325 16.6822C80.8828 16.0374 82.0708 15.7149 83.4794 15.7149C84.5994 15.7149 88.5027 16.0034 88.5027 16.0034V17.8193C87.8189 17.7797 87.1764 17.7364 86.5804 17.6962C85.3867 17.6157 84.3792 17.5477 83.5982 17.5477ZM94.5436 17.7853H98.939V15.9694H94.5436V11.7437H92.4901V15.9864H90.5215V17.7853H92.4901V25.0657C92.4901 27.0344 92.7617 28.375 93.3217 29.0708C93.8817 29.7666 94.866 30.123 96.3085 30.123C96.9534 30.123 97.8868 30.0212 99.1257 29.8176L98.9899 28.1035L96.5291 28.2732C95.6636 28.2732 95.1206 28.0187 94.883 27.5265C94.6624 27.0344 94.5436 25.9822 94.5436 24.4039V17.7853ZM101.824 12.8469V10.454H103.895V12.8638L101.824 12.8469ZM101.824 29.8176V15.9864H103.895V29.8176H101.824ZM115.995 16.0373C114.535 15.8167 113.5 15.6979 112.889 15.6979C110.819 15.6979 109.342 16.241 108.443 17.2931C107.56 18.3453 107.119 20.1951 107.119 22.8256C107.119 25.4561 107.543 27.3228 108.358 28.4259C109.172 29.529 110.666 30.0891 112.821 30.0891C113.67 30.0891 114.959 29.9533 116.674 29.6987L116.589 27.9847L113.33 28.2393C111.667 28.2393 110.581 27.8489 110.055 27.0513C109.529 26.2537 109.274 24.8451 109.274 22.8256C109.274 20.8061 109.563 19.4145 110.123 18.6678C110.683 17.9211 111.752 17.5477 113.313 17.5477C114.009 17.5477 115.095 17.6326 116.572 17.8023L116.657 16.1222L115.995 16.0373Z" fill="#000" class="jsx-1189744782 elastic-logo__wordmark"></path></g></svg></span></a><div class=" Actions_actions__9PoiP "><div class="Actions_action__THZjm"><button type="button" aria-label="Press down to open menu." aria-expanded="false"><span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="20" height="20" fill="none"><g clip-path="url(#a)"><path d="M10 18.75c-1.57 0-3.125-3.89-3.125-8.75 0-4.86 1.556-8.75 3.125-8.75V0C7.428 0 5.625 4.506 5.625 10S7.428 20 10 20v-1.25ZM10 18.75c1.57 0 3.125-3.89 3.125-8.75 0-4.86-1.556-8.75-3.125-8.75V0c2.572 0 4.375 4.506 4.375 10S12.572 20 10 20v-1.25Z"></path><path d="M3.125 7.5h13.75V6.25H3.125V7.5ZM3.125 13.75h13.75V12.5H3.125v1.25Z"></path><path fill-rule="evenodd" d="M20 10c0 5.523-4.477 10-10 10S0 15.523 0 10 4.477 0 10 0s10 4.477 10 10ZM1.25 10a8.75 8.75 0 1 0 17.5 0 8.75 8.75 0 0 0-17.5 0Z" clip-rule="evenodd"></path></g><defs><clipPath id="a"><path d="M0 0h20v20H0z"></path></clipPath></defs></svg></span><span class="Actions_ButtonText__L0fen">EN</span></button><div class="Dropdown_Dropdown__pUJPf Dropdown_Dropdown--modalOnMobile__olFVq"><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><ul><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Deutsch</a></li><li class="Actions_DropdownItem__z0FcS Actions_DropdownItemActive__0GjNS"><a class="Actions_DropdownLink__evluL">English</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Español</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Français</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">日本語</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">한국어</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">简体中文</a></li><li class="Actions_DropdownItem__z0FcS"><a class="Actions_DropdownLink__evluL">Português</a></li></ul></div></div></div></div><div class="Actions_action__THZjm"><button type="button"><svg xmlns="http://www.w3.org/2000/svg" width="20" height="20" fill="none" class="jsx-3447688935 icon"><g fill-rule="evenodd" stroke-width=".417" clip-path="url(#a)" clip-rule="evenodd" class="jsx-3447688935"><path d="M8.332 1.99a6.346 6.346 0 1 0 0 12.693 6.346 6.346 0 0 0 0-12.693Zm-7.5 6.346a7.5 7.5 0 1 1 15 0 7.5 7.5 0 0 1-15 0Z" class="jsx-3447688935"></path><path d="m14.124 13.336 5.041 5.041-.792.792-5.041-5.04.792-.793Z" class="jsx-3447688935"></path></g><defs class="jsx-3447688935"><clipPath id="a" class="jsx-3447688935"><path d="M0 0h20v20H0z" class="jsx-3447688935"></path></clipPath></defs></svg><span class="Actions_ButtonText__L0fen Actions_ButtonTextHidden__r8BOX">Search</span></button></div><div class="Actions_action__THZjm"><a href="https://cloud.elastic.co"><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="20" height="20" fill="none"><g clip-path="url(#a)"><path fill-rule="evenodd" d="M6.252 5.416a3.75 3.75 0 1 1 7.5 0 3.75 3.75 0 0 1-7.5 0ZM10.002 0a5.417 5.417 0 0 0-3.336 9.685 8.215 8.215 0 0 0-3.384 2.245C1.602 13.782.625 16.5.625 20h1.667c0-3.196.888-5.478 2.225-6.951 1.331-1.469 3.18-2.215 5.275-2.215 2.094 0 3.943.746 5.275 2.215 1.336 1.473 2.225 3.755 2.225 6.951h1.666c0-3.501-.977-6.219-2.657-8.071A8.204 8.204 0 0 0 13.2 9.79 5.417 5.417 0 0 0 10.002 0Z" clip-rule="evenodd"></path><path d="M1.668 20.003h16.667v-1.667H1.668v1.667Z"></path></g><defs><clipPath id="a"><path d="M0 0h20v20H0z"></path></clipPath></defs></svg><span class="Actions_ButtonText__L0fen Actions_ButtonTextHidden__r8BOX">Login</span></a></div><button type="button" aria-expanded="false" class=" Control_navigation-control__dMg2m "><span class="Control_navigation-control_text__wyRQe">Toggle Navigation</span><span class="Control_navigation-control_icon__2h1YW"><span></span><span></span><span></span></span></button></div><div style="top:72px" class="Buttons_navigationButtons__QJmSA"><a class="button btn-primary btn-small" href="https://cloud.elastic.co/registration"><span class="jsx-1596590093 btn-copy">Start free trial</span></a><a class="button btn-secondary-inverted btn-small" href="/contact"><span class="jsx-1596590093 btn-copy">Contact Sales</span></a></div><div style="top:72px" class="Index_navigation_flyout__73xqL"><div class="Index_navigation_flyout_content___3G_7"><nav class="Items_navigation-items__lSmFz" aria-label="Primary navigation"><div class="Items_dropdownWrapper__hJFj3" style="width:100%;height:200px"></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Platform, press down to open menu." aria-expanded="false">Platform<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm Items_spotlight-feature___wj__"><div class=" Card_nav-card__Gb2bd Card_ghost-card__kC3tT "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/platform"><h2 class="h5">The Search AI Company</h2></a><a class="Card_custom-link__semnr" href="/platform"><div class="Card_card-image__34JYo"><div class=" Card_thumbnail-wrapper__8kCr1 "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltb72b02d269f3201a/6643847599f5a8667dc35ac7/nav-platform.png" class="Card_img-fluid__EqrlH" alt="Search, Security, Observability"/></div></div></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a><a class="Card_custom-link__semnr" href="/platform"></a></div><div class="Card_card-body__81rqO"><div><p>Build tailored experiences with Elastic.</p></div><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/platform" tabindex="-1"><span class="jsx-1596590093 btn-copy">Elastic Search AI Platform overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><hr class="Card_nav-divider__yt_19"/><div><p><strong>Scale your business with Elastic Partners</strong></p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="https://partners.elastic.co/findapartner/" tabindex="-1">Find a partner<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/partners/become-a-partner" tabindex="-1">Become a partner<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/partners" tabindex="-1"><span class="jsx-1596590093 btn-copy">Partner overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt0090c6239e64faf8/62aa0980c949fd5059e8aebc/logo-stack-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">ELK Stack</h2></div><div class="Card_card-body__81rqO"><div><p>Search and analytics, data ingestion, and visualization – all at your fingertips.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/kibana" tabindex="-1">Kibana<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch" tabindex="-1">Elasticsearch<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/integrations" tabindex="-1">Integrations<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/elastic-stack" tabindex="-1"><span class="jsx-1596590093 btn-copy">ELK Stack overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><hr class="Card_nav-divider__yt_19"/><div><p><strong>By developers, for developers</strong></p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/vector-database" tabindex="-1">Try the world's most used vector database<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/blog/search-ai-lake-elastic-cloud-serverless" tabindex="-1">Scale with the low-latency Search AI Lake<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/community" tabindex="-1">Join our community<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div></div><div class="Items_Section__vJ9lm"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltdb0f38c35ae455dc/5d07f086877575d0584760a3/logo-cloud-24-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Elastic Cloud</h2></div><div class="Card_card-body__81rqO"><div><p>Unlock the power of real-time insights with Elastic on your preferred cloud provider.</p></div><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/cloud" tabindex="-1"><span class="jsx-1596590093 btn-copy">Elastic Cloud overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="/cloud/serverless" tabindex="-1">Elastic Cloud Serverless<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/pricing/serverless-search" tabindex="-1">Elastic Cloud Serverless pricing<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/cloud/serverless/search-ai-lake" tabindex="-1">Search AI Lake<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div></div></div></div></div></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Solutions, press down to open menu." aria-expanded="false">Solutions<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm Items_spotlight-feature___wj__"><div class=" Card_nav-card__Gb2bd Card_ghost-card__kC3tT "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/generative-ai"><h2 class="h5">Generative AI</h2></a><a class="Card_custom-link__semnr" href="/generative-ai"></a><a class="Card_custom-link__semnr" href="/generative-ai"></a><a class="Card_custom-link__semnr" href="/generative-ai"></a><a class="Card_custom-link__semnr" href="/generative-ai"></a></div><div class="Card_card-body__81rqO"><div><p>Prototype and integrate with LLMs faster using search AI.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/cloud/serverless/search-ai-lake" tabindex="-1">Search AI Lake<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/ai-assistant" tabindex="-1">Elastic AI Assistant<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/rag" tabindex="-1">Retrieval Augmented Generation<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="/blog/category/generative-ai" tabindex="-1">Generative AI blogs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/search-labs/tutorials" tabindex="-1">Search Labs tutorials<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/community" tabindex="-1">Elastic Community<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/generative-ai" tabindex="-1"><span class="jsx-1596590093 btn-copy">Generative AI overview </span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div><div class="Items_Section__vJ9lm Items_grid-column__BSkh1"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/enterprise-search"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt549f7d977c2a88f4/5d082d34616162aa5a85707d/logo-enterprise-search-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/enterprise-search"><h2 class="h5">Search</h2></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a><a class="Card_custom-link__semnr" href="/enterprise-search"></a></div><div class="Card_card-body__81rqO"><div><p>Discover a world of AI possibilities — built with the power of search.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/elasticsearch/vector-database" tabindex="-1">Vector database<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/relevance" tabindex="-1">Relevance<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/search-applications" tabindex="-1">Search applications<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/ecommerce" tabindex="-1">Ecommerce<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/site-search" tabindex="-1">Website search<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/workplace-search" tabindex="-1">Workplace search<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/enterprise-search/customer-support" tabindex="-1">Customer support<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/search-labs" tabindex="-1">Search Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/enterprise-search" tabindex="-1"><span class="jsx-1596590093 btn-copy">Search overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/security"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltf58b7c8e04706979/5e20f1a8132ead1155e8d0a4/logo-security-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/security"><h2 class="h5">Security</h2></a><a class="Card_custom-link__semnr" href="/security"></a><a class="Card_custom-link__semnr" href="/security"></a><a class="Card_custom-link__semnr" href="/security"></a><a class="Card_custom-link__semnr" href="/security"></a></div><div class="Card_card-body__81rqO"><div><p>Protect, investigate, and respond to cyber threats with AI-driven security analytics.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/security/siem" tabindex="-1">SIEM<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/security/ai" tabindex="-1">AI for the SOC<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/security/cyber-threat-research" tabindex="-1">Threat Research<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/security-labs" tabindex="-1">Security Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/security" tabindex="-1"><span class="jsx-1596590093 btn-copy">Security overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/observability"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltbf6ba0d0e0e1e5ab/5e20f19a2aa8e40a75136318/logo-observability-32-color.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/observability"><h2 class="h5">Observability</h2></a><a class="Card_custom-link__semnr" href="/observability"></a><a class="Card_custom-link__semnr" href="/observability"></a><a class="Card_custom-link__semnr" href="/observability"></a><a class="Card_custom-link__semnr" href="/observability"></a></div><div class="Card_card-body__81rqO"><div><p>Unify app and infrastructure visibility to proactively resolve issues.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/observability/log-monitoring" tabindex="-1">Log monitoring and analytics<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/opentelemetry" tabindex="-1">OpenTelemetry<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/application-performance-monitoring" tabindex="-1">Application performance monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/infrastructure-monitoring" tabindex="-1">Infrastructure monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/synthetic-monitoring" tabindex="-1">Synthetic monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/real-user-monitoring" tabindex="-1">Real user monitoring<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/universal-profiling" tabindex="-1">Universal Profiling<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/observability/aiops" tabindex="-1">AIOps<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/observability-labs" tabindex="-1">Observability Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/observability" tabindex="-1"><span class="jsx-1596590093 btn-copy">Observability overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div></div></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Customers, press down to open menu." aria-expanded="false">Customers<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/customers"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltacc5e178e52f430e/647ccc7b6be35fb5eabd2100/icon-checkmark-decorative-border.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/customers"><h2 class="h5">By solution</h2></a><a class="Card_custom-link__semnr" href="/customers"></a><a class="Card_custom-link__semnr" href="/customers"></a></div><div class="Card_card-body__81rqO"><div><p>See how customers search, solve, and succeed — all on one Search AI Platform.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/customers/success-stories?usecase=enterprise-search&industry=All" tabindex="-1">Search<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/customers/success-stories?usecase=security-analytics&industry=All" tabindex="-1">Security<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/customers/success-stories?usecase=elastic-observability&industry=All" tabindex="-1">Observability<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/customers" tabindex="-1"><span class="jsx-1596590093 btn-copy">All customer stories</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><a class="Card_custom-link__semnr" href="/industries"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt9f634b6f74878698/647ccc625637890f19859454/icon-briefcase.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div></a><a class="Card_custom-link__semnr" href="/industries"><h2 class="h5">Industries</h2></a><a class="Card_custom-link__semnr" href="/industries"></a><a class="Card_custom-link__semnr" href="/industries"></a></div><div class="Card_card-body__81rqO"><div><p>Exceed customer expectations and go to market faster.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/industries/public-sector" tabindex="-1">Public sector<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/financial-services" tabindex="-1">Financial services<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/telecommunications" tabindex="-1">Telecommunications<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/retail-ecommerce" tabindex="-1">Retail<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/industries/manufacturing" tabindex="-1">Manufacturing<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div><div class="Card_card-footer__OfpS8"><div class="d-flex flex-column"><a class="button Card_dropdown-link__qZWTu Card_dropdown-link__spaced___Q1m0 Card_btn-tertiary__f8UEk btn-tertiary" href="/industries" tabindex="-1"><span class="jsx-1596590093 btn-copy">Industries overview</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div><div class="Items_Section__vJ9lm Items_spotlight-feature___wj__"><div class=" Card_nav-card__Gb2bd undefined "><div class="Card_card-header__dLhyK"><h2 class="Card_topic-heading___KyPp">Customer spotlight</h2></div><div><div class="Spotlight_spotlight-card__Qi_WV"><div class="Spotlight_card-image__4S6cS"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt652fec920f2b1a14/650c1d87aa86c13fa1cc288c/logo-nav-dropdown-48x48-cisco.svg" alt="" class=""/></div><div class="Spotlight_card-body___rb9E"><p>Cisco saves 5,000 support engineer hours per month</p><a class="button Spotlight_stretched-link__2M98R btn-tertiary" href="/customers/cisco" tabindex="-1"><span class="jsx-1596590093 btn-copy">Read more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div><div class="Spotlight_spotlight-card__Qi_WV"><div class="Spotlight_card-image__4S6cS"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blte788c0f923f209a3/668c49f5534bb913eb26e9e8/logo-dropdown-48x48-sitecore.svg" alt="" class=""/></div><div class="Spotlight_card-body___rb9E"><p>Sitecore automates 96 percent of security workflows with Elastic</p><a class="button Spotlight_stretched-link__2M98R btn-tertiary" href="/customers/sitecore-security" tabindex="-1"><span class="jsx-1596590093 btn-copy">Read more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div><div class="Spotlight_spotlight-card__Qi_WV"><div class="Spotlight_card-image__4S6cS"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt90a52ed02808cbc1/650c1dadb25642d90add1e4e/logo-nav-dropdown-48x48-comcast.svg" alt="" class=""/></div><div class="Spotlight_card-body___rb9E"><p>Comcast transforms customer experiences with Elastic Observability</p><a class="button Spotlight_stretched-link__2M98R btn-tertiary" href="/customers/comcast" tabindex="-1"><span class="jsx-1596590093 btn-copy">Read more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div></div></div></div><div><button class="Items_navigation-items_item__7YSef navigation-item" aria-label="Resources, press down to open menu." aria-expanded="false">Resources<svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" fill="currentColor" viewBox="0 0 16 16"><path fill-rule="evenodd" d="M1.646 4.646a.5.5 0 0 1 .708 0L8 10.293l5.646-5.647a.5.5 0 0 1 .708.708l-6 6a.5.5 0 0 1-.708 0l-6-6a.5.5 0 0 1 0-.708z"></path></svg></button><div class="Dropdown_Dropdown__pUJPf "><div class="Dropdown_DropdownContent__tGePQ"><button class="Dropdown_DropdownClose__wx62b" disabled=""><span class="Dropdown_DropdownClose_text__IoOgP">Close panel</span><svg class="icons_icon__n3nWe" xmlns="http://www.w3.org/2000/svg" width="16" height="16" viewBox="0 0 16 16" fill="none"><path fill-rule="evenodd" clip-rule="evenodd" d="M6.58586 8.00008L0.292969 14.293L1.70718 15.7072L8.00008 9.41429L14.293 15.7072L15.7072 14.293L9.41429 8.00008L15.7072 1.70718L14.293 0.292969L8.00008 6.58586L1.70718 0.292969L0.292969 1.70718L6.58586 8.00008Z"></path></svg></button><div class="Dropdown_DropdownSections__G_B5O"><div class="Items_Section__vJ9lm Items_grid-column__BSkh1"><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Research</h2></div><div class="Card_card-body__81rqO"><div><p>Stay at the forefront of innovation with technical tips from the experts.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/search-labs" tabindex="-1">Search Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/security-labs" tabindex="-1">Security Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://www.elastic.co/observability-labs" tabindex="-1">Observability Labs<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Build</h2></div><div class="Card_card-body__81rqO"><div><p>Code with other developers to create a better Elastic, together.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/community" tabindex="-1">Community<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="https://discuss.elastic.co" tabindex="-1">Forum<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/downloads" tabindex="-1">Downloads<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/guide" tabindex="-1">Documentation<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Learn</h2></div><div class="Card_card-body__81rqO"><div><p>Unleash the possibilities of your data and grow your skill set.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/getting-started" tabindex="-1">Getting started<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/learn" tabindex="-1">Elastic resources<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/consulting" tabindex="-1">Consulting services<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/training" tabindex="-1">Trainings & certifications<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div><div class=" Card_nav-card__Gb2bd Card_icon-card__IEL2U "><div class="Card_card-header__dLhyK"><div class="Card_card-image__34JYo"><div class=" Card_icon__VSCRq "><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg" class="Card_img-fluid__EqrlH" alt=""/></div></div><h2 class="h5">Connect</h2></div><div class="Card_card-body__81rqO"><div><p>Keep informed about the latest tech and news from Elastic.</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/blog" tabindex="-1">Blog<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/events" tabindex="-1">Events<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul><hr class="Card_nav-divider__yt_19"/><div><p>Have questions?</p></div><ul><li><a class="Card_dropdown-link__qZWTu" href="/contact?storm=global-header-en" tabindex="-1">Contact sales<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li><li><a class="Card_dropdown-link__qZWTu" href="/support" tabindex="-1">Get support<svg width="27" height="14" viewBox="0 0 27 14" fill="none" xmlns="http://www.w3.org/2000/svg"><path d="M0 7H25" stroke="#0B64DD" stroke-width="2"></path><path d="M19 1L25 7L19 13" stroke="#0B64DD" stroke-width="2"></path></svg></a></li></ul></div></div></div></div></div></div></div><a class="Items_navigation-items_item__7YSef navigation-item" href="/pricing">Pricing</a><a class="Items_navigation-items_item__7YSef navigation-item" href="https://www.elastic.co/docs">Docs</a></nav></div></div></div></div></div><div class="newNav Navigation_navigation__fV7hy" data-theme="light"><div class="Masthead_masthead__BdzP7" data-theme="light"><div data-component="Container" class="Container_container__MtYF0 Container_container--gutter-sm__7pTAU Container_container--width-lg___3B8A"><div class="Masthead_masthead__content__9ozlx"><div class="Marquee_marquee__GjfGB"><p class="Marquee_marquee__tag__6fqKH"><svg data-component="Icon" class="Icon_icon__dSH3_" width="10" height="10" aria-hidden="true" xmlns="http://www.w3.org/2000/svg" fill="none"><path fill="#DD0A73" d="M10 5a5 5 0 0 0-5 5 5 5 0 0 0-5-5 5 5 0 0 0 5-5 5 5 0 0 0 5 5"></path></svg>New</p><a href="https://www.elastic.co/portfolio/operationalizing-generative-ai-strategic-guide">Read more</a></div><div class="Masthead_masthead__links__FIs_o"><a href="https://www.elastic.co/about">About us</a><a href="https://www.elastic.co/partners">Partners</a><a href="https://www.elastic.co/support">Support</a>|<a href="https://cloud.elastic.co/login"><svg xmlns="http://www.w3.org/2000/svg" fill="none" viewBox="0 0 24 24" stroke-width="1.5" stroke="currentColor" aria-hidden="true" data-slot="icon" height="16" width="16"><path stroke-linecap="round" stroke-linejoin="round" d="M15.75 6a3.75 3.75 0 1 1-7.5 0 3.75 3.75 0 0 1 7.5 0ZM4.501 20.118a7.5 7.5 0 0 1 14.998 0A17.933 17.933 0 0 1 12 21.75c-2.676 0-5.216-.584-7.499-1.632Z"></path></svg>Login</a></div></div></div></div><div data-component="Container" class="Container_container__MtYF0 Container_container--gutter-sm__7pTAU Container_container--width-lg___3B8A Navigation_navigation__container__tRrDy"><a class="Logo_logo__dlgEX" href="https://www.elastic.co/"><svg width="117" height="40" viewBox="0 0 117 40" fill="none" xmlns="http://www.w3.org/2000/svg"><g clip-path="url(#clip0_3472_2853)"><path d="M40.1527 20.9588C40.1527 17.5986 38.0653 14.6457 34.9257 13.5087C35.0615 12.7959 35.1294 12.0832 35.1294 11.3534C35.1294 5.09122 30.0382 0 23.7929 0C20.1273 0 16.7331 1.74799 14.5948 4.70089C13.5426 3.8863 12.2529 3.44506 10.9122 3.44506C7.58591 3.44506 4.88757 6.14341 4.88757 9.46967C4.88757 10.1994 5.02333 10.9122 5.26092 11.574C2.13831 12.6941 0 15.6979 0 19.0412C0 22.4183 2.10437 25.3712 5.24395 26.5083C5.10819 27.2041 5.0403 27.9338 5.0403 28.6636C5.0403 34.9088 10.1145 39.983 16.3598 39.983C20.0255 39.983 23.4196 38.2181 25.5409 35.2652C26.5931 36.0967 27.8829 36.5549 29.2236 36.5549C32.5498 36.5549 35.2482 33.8566 35.2482 30.5303C35.2482 29.8006 35.1124 29.0878 34.8748 28.426C37.9974 27.3059 40.1527 24.3021 40.1527 20.9588Z"></path><path d="M15.7826 17.2248L24.5735 21.2299L33.4322 13.4573C33.568 12.8124 33.6189 12.1845 33.6189 11.5056C33.6189 6.04106 29.1725 1.59473 23.708 1.59473C20.4326 1.59473 17.3949 3.20695 15.5451 5.90529L14.0686 13.5591L15.7826 17.2248Z"></path><path d="M6.68643 26.5253C6.55067 27.1702 6.49976 27.832 6.49976 28.5109C6.49976 33.9924 10.9631 38.4387 16.4446 38.4387C19.7369 38.4387 22.8086 36.8095 24.6584 34.0942L26.1179 26.4744L24.1663 22.7408L15.3415 18.7188L6.68643 26.5253Z"></path><path d="M6.63518 11.3195L12.6598 12.745L13.9835 5.90581C13.1689 5.27789 12.1507 4.93848 11.0985 4.93848C8.48499 4.93848 6.34668 7.05982 6.34668 9.69028C6.34668 10.2503 6.4485 10.8103 6.63518 11.3195Z"></path><path d="M6.11005 12.7617C3.42867 13.6442 1.54492 16.2237 1.54492 19.0579C1.54492 21.8241 3.25896 24.2848 5.82155 25.2691L14.273 17.6323L12.7286 14.323L6.11005 12.7617Z"></path><path d="M26.186 34.0937C27.0176 34.7216 28.0189 35.078 29.0541 35.078C31.6676 35.078 33.8059 32.9567 33.8059 30.3262C33.8059 29.7492 33.7041 29.1892 33.5174 28.6801L27.5098 27.2715L26.186 34.0937Z"></path><path d="M27.4074 25.6936L34.026 27.2379C36.7243 26.3554 38.5911 23.7759 38.5911 20.9248C38.5911 18.1755 36.8771 15.6978 34.3145 14.7305L25.6594 22.3164L27.4074 25.6936Z"></path><path d="M56.1395 28.0863L56.9371 28.0014L56.988 29.6306C54.8836 29.9191 53.0847 30.0718 51.5913 30.0718C49.6057 30.0718 48.1971 29.4948 47.3656 28.3408C46.534 27.1868 46.1267 25.3879 46.1267 22.9611C46.1267 18.1075 48.0614 15.6807 51.9137 15.6807C53.7805 15.6807 55.1721 16.2068 56.0885 17.242C57.005 18.2772 57.4632 19.9233 57.4632 22.1465L57.3444 23.7248H48.2141C48.2141 25.2521 48.4856 26.3892 49.0457 27.1189C49.6057 27.8487 50.5561 28.222 51.9307 28.222C53.3223 28.256 54.7139 28.2051 56.1395 28.0863ZM55.3927 22.0956C55.3927 20.3985 55.1212 19.1936 54.5781 18.4978C54.0351 17.802 53.1526 17.4456 51.9307 17.4456C50.7088 17.4456 49.7754 17.819 49.1645 18.5487C48.5535 19.2785 48.2311 20.4664 48.2141 22.0956H55.3927Z"></path><path d="M60.3481 29.8177V9.96191H62.4186V29.8177H60.3481Z"></path><path d="M75.5031 20.1615V26.9668C75.5031 27.6626 77.2171 27.7984 77.2171 27.7984L77.1153 29.6312C75.6558 29.6312 74.4509 29.75 73.7212 29.0542C72.058 29.7839 70.4119 30.0894 68.7487 30.0894C67.4759 30.0894 66.5086 29.733 65.8467 29.0033C65.1849 28.2905 64.8455 27.2553 64.8455 25.8977C64.8455 24.557 65.1849 23.5557 65.8637 22.9278C66.5425 22.2999 67.6117 21.8926 69.0712 21.7568L73.4157 21.3495V20.1615C73.4157 19.2282 73.212 18.5493 72.8047 18.142C72.3974 17.7347 71.8374 17.5311 71.1416 17.5311H65.694V15.6982H71.0058C72.5671 15.6982 73.7042 16.0546 74.417 16.7844C75.1467 17.4971 75.5031 18.6342 75.5031 20.1615ZM66.9838 25.7958C66.9838 27.4929 67.6796 28.3414 69.0881 28.3414C70.344 28.3414 71.5828 28.1378 72.7878 27.7135L73.4157 27.4929V22.9278L69.3257 23.3181C68.4942 23.386 67.9002 23.6236 67.5268 24.0309C67.1535 24.4382 66.9838 25.0321 66.9838 25.7958Z"></path><path d="M83.5981 17.5477C81.5955 17.5477 80.5773 18.2435 80.5773 19.6521C80.5773 20.2969 80.8149 20.7552 81.2731 21.0267C81.7313 21.2982 82.7835 21.5697 84.4297 21.8582C86.0758 22.1467 87.2298 22.5371 87.9087 23.0632C88.5875 23.5723 88.9269 24.5396 88.9269 25.9652C88.9269 27.3907 88.4687 28.4259 87.5523 29.0878C86.6359 29.7496 85.3121 30.089 83.5472 30.089C82.4101 30.089 78.5917 29.6648 78.5917 29.6648L78.7105 27.8659C80.8997 28.0695 82.495 28.2392 83.5641 28.2392C84.6333 28.2392 85.4479 28.0695 86.0079 27.7301C86.568 27.3907 86.8565 26.8137 86.8565 26.0161C86.8565 25.2184 86.6189 24.6754 86.1437 24.3869C85.6685 24.0984 84.6163 23.8269 82.9871 23.5723C81.3579 23.3177 80.2039 22.9444 79.5251 22.4353C78.8463 21.9431 78.5068 21.0097 78.5068 19.669C78.5068 18.3283 78.982 17.3271 79.9324 16.6822C80.8827 16.0373 82.0707 15.7148 83.4793 15.7148C84.5994 15.7148 88.5026 16.0033 88.5026 16.0033V17.8192C86.4492 17.7004 84.7691 17.5477 83.5981 17.5477Z"></path><path d="M98.9392 17.7857H94.5438V24.4043C94.5438 25.9826 94.6626 27.0348 94.8832 27.5269C95.1208 28.0191 95.6639 28.2736 96.5294 28.2736L98.9901 28.1039L99.1259 29.818C97.887 30.0216 96.9536 30.1234 96.3087 30.1234C94.8662 30.1234 93.8819 29.767 93.3219 29.0712C92.7619 28.3754 92.4903 27.0348 92.4903 25.0662V17.7857H90.5217V15.9868H92.4903V11.7441H94.5438V15.9699H98.9392V17.7857Z"></path><path d="M101.824 12.847V10.4541H103.895V12.8639L101.824 12.847ZM101.824 29.8177V15.9866H103.895V29.8177H101.824Z"></path><path d="M112.889 15.6982C113.5 15.6982 114.535 15.817 115.995 16.0377L116.656 16.1225L116.572 17.8026C115.095 17.6329 114.009 17.5481 113.313 17.5481C111.752 17.5481 110.683 17.9214 110.123 18.6681C109.563 19.4148 109.274 20.8064 109.274 22.8259C109.274 24.8455 109.529 26.254 110.055 27.0517C110.581 27.8493 111.667 28.2396 113.33 28.2396L116.589 27.9851L116.673 29.6991C114.959 29.9537 113.67 30.0894 112.821 30.0894C110.666 30.0894 109.172 29.5294 108.358 28.4263C107.543 27.3232 107.119 25.4564 107.119 22.8259C107.119 20.1955 107.56 18.3457 108.443 17.2935C109.342 16.2413 110.819 15.6982 112.889 15.6982Z"></path></g><defs><clipPath id="clip0_3472_2853"><rect width="116.674" height="40" fill="white"></rect></clipPath></defs></svg></a><nav aria-label="Main" data-orientation="horizontal" dir="ltr" class="NavDropdown_navDropdown__agBDs"><div class="NavDropdown_navDropdown__overlay__p8ZvY"></div><div style="position:relative"><ul data-orientation="horizontal" class="NavDropdown_navDropdown__list__qy1xV" dir="ltr"><li><button id="-trigger-LEGACY_REACT_AUTO_VALUE" data-state="closed" aria-expanded="false" aria-controls="-content-LEGACY_REACT_AUTO_VALUE" class="NavDropdown_navDropdown__trigger__Jj_Al" data-radix-collection-item="">Products</button></li><li><button id="-trigger-LEGACY_REACT_AUTO_VALUE" data-state="closed" aria-expanded="false" aria-controls="-content-LEGACY_REACT_AUTO_VALUE" class="NavDropdown_navDropdown__trigger__Jj_Al" data-radix-collection-item="">Solutions</button></li><li><button id="-trigger-LEGACY_REACT_AUTO_VALUE" data-state="closed" aria-expanded="false" aria-controls="-content-LEGACY_REACT_AUTO_VALUE" class="NavDropdown_navDropdown__trigger__Jj_Al" data-radix-collection-item="">Why Elastic?</button></li><li><button id="-trigger-LEGACY_REACT_AUTO_VALUE" data-state="closed" aria-expanded="false" aria-controls="-content-LEGACY_REACT_AUTO_VALUE" class="NavDropdown_navDropdown__trigger__Jj_Al" data-radix-collection-item="">Resources</button></li><a class="NavDropdown_navDropdown__trigger__Jj_Al" href="https://www.elastic.co/pricing">Pricing</a><a class="NavDropdown_navDropdown__trigger__Jj_Al" href="https://www.elastic.co/docs">Docs</a></ul></div></nav><div class="Navigation_navigation__actions__TEAR7"><div class="SearchInput_searchInput__ynnEJ"><div class="SearchInput_searchInput__glow__irOA9"></div><button class="SearchInput_searchInput__button__aVQ2G" type="button"><svg data-component="Icon" class="SearchInput_searchInput__icon__gWuuf Icon_icon__dSH3_" width="22" height="21" aria-hidden="true" xmlns="http://www.w3.org/2000/svg" fill="none"><path fill="currentColor" fill-rule="evenodd" d="M1.934 8.933a5.75 5.75 0 0 1 8.628 7.567l2.969 2.97a.75.75 0 0 1-1.06 1.06L9.5 17.56a5.75 5.75 0 0 1-7.567-8.627M6 8.75a4.25 4.25 0 1 0 0 8.5 4.25 4.25 0 0 0 0-8.5" clip-rule="evenodd"></path><path fill="currentColor" d="M18 4a4 4 0 0 0-4 4 4 4 0 0 0-4-4 4 4 0 0 0 4-4 4 4 0 0 0 4 4M22 10a3 3 0 0 0-3 3 3 3 0 0 0-3-3 3 3 0 0 0 3-3 3 3 0 0 0 3 3"></path></svg><span>Search</span></button></div><button data-component="Button" class="Button_button__iy3n8 Button_button--primary__Y48gQ Button_button--md__S_OuH" type="button"><span>Start free trial</span></button><button data-component="Button" class="Button_button__iy3n8 Button_button--secondary__BjlK0 Button_button--md__S_OuH" type="button"><span>Contact sales</span></button></div></div></div><div class="newNav Navigation_navigation__placeholder__Bm_GK"></div></header><main id="main-content" role="main"><div class="jsx-579451128 default-detail"><link rel="stylesheet" href="/static-res/styles/css/vendors/prettify.css" class="jsx-579451128"/><script type="text/javascript" src="/static-res/js/prettify.js" class="jsx-579451128"></script><section aria-labelledby="the-power-of-data-and-generative-ai-for-telco" data-component-theme="" class="jsx-3636536621 Hero_hero__iEZMX position-relative Hero_twoColumn___DJDO hero"><div class=""><div class="Patterns_patterns__3u_in container z-0"><div class="Patterns_left__g_wcp"><img src="/static-res/images/hero/generic-c-light-left.svg" alt=""/></div><div class="Patterns_right__kW4Ma"><img src="/static-res/images/hero/generic-c-light-right.svg" alt=""/></div></div></div><div class=""><div class="Hero_heroContent__S5fut justify-content-between"><div class="container"><div class="layout layout-06"></div><div class="row"><div class="col-12 col-sm-8 offset-sm-2 col-lg-5 offset-lg-0 d-flex"><div class="Hero_content__VSxmz align-self-center"><h2 class="topic-heading">Telecommunications</h2><div class="jsx-1955866259 title-wrapper"><h1 tag="H1" id="the-power-of-data-and-generative-ai-for-telco" class="jsx-1955866259 h2">The power of data and generative AI for telco</h1></div><div class="Hero_description__nrqhU paragraph-large"><p>Most (88%) telco executives say they either already have or plan to implement generative AI (GenAI) at their organizations.</p><p>But getting GenAI right depends on how well you can access, search, and analyze all your data, no matter its format or location.</p><p>Explore insights on data and AI from telco leaders.</p></div><div class="Hero_ctaList__efelZ mt-5"><div class="Hero_cta__zIL_f"><a class="button btn-primary" href="/resources/portfolio/report/solving-business-challenges-data-ai-telecommunications"><span class="jsx-1596590093 btn-copy">Read the study</span></a></div><div class="Hero_cta__zIL_f"><a class="button btn-tertiary" href="/telecommunications/unlocking-the-power-of-generative-ai"><span class="jsx-1596590093 btn-copy">Download brief</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div><div class="col-12 col-sm-10 offset-sm-1 col-lg-6 offset-lg-1"><div class="Hero_asset__rLCmZ"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltef153c426256a863/67bf728c938bf57bf4f9ae01/report-cover-solving-business-challenges-telco-it.png" class="shadow-light" alt=""/></div></div></div><div class="layout layout-05"></div></div></div></div></section><div class="layout layout-07"></div><div style="border-radius:" data-component-theme="" class="jsx-2381115616 illustration-icon-grid-container"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><h2 class="topic-heading">Break down network and business silos</h2><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="reimagine-telecom-with-unified-visibility" class="jsx-1955866259 h3">Reimagine telecom with unified visibility</h2></div><div class="title-text-desc paragraph-large"><p>Leading telecom providers worldwide trust Elastic to expand their digital services footprint by helping them deliver the next-gen telecom experiences. With proven solutions built on a single search intelligence platform, Elastic enables actionable insights into networks, support systems, and customer behavior that align with business objectives.</p></div><div class="title-text-footer"><div class="cta-group align-items-center justify-content-center text-center"><div><a class="button mt-4 btn-tertiary" href="/industries/telecommunications/enable-real-time-insights-at-telco-scale"><span class="jsx-1596590093 btn-copy">Download the guide</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div><div class="jsx-2381115616 container"><div class="layout layout-05"></div><ul class="illustration-icon-grid-items illustration-icon-grid-3x1"><li class="jsx-802606770 illustration-icon-grid-item one-column grid-image-left"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt80f78dbbb85f42a0/6492440bb9a07659f19282d1/illustration-people-channels-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="manage-distributed-networks" class="jsx-1955866259 h5">Manage distributed networks</h3></div></div><div><div class="paragraph paragraph-medium"><p>Hear from the Elastic industry team on how telecom companies are managing their core networks with Elastic.</p></div></div><div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/elasticon/archive/2021/global/enable-real-time-insights-at-scale-for-telco-to-solve"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></li><li class="jsx-802606770 illustration-icon-grid-item one-column grid-image-left"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7e1a162341d630e8/6540a0b262f244001b7d9257/illustration-cloud-services-security-posture-target-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="scale-efficiently-in-the-cloud" class="jsx-1955866259 h5">Scale efficiently in the cloud</h3></div></div><div><div class="paragraph paragraph-medium"><p>Find out how a leading telecom provider realized a <strong>283% ROI</strong> with a payback period of <strong>1.7 years</strong> after deploying Elastic Cloud. </p></div></div><div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/global-telecom-provider-realized-283-percent-roi-with-elastic-cloud"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></li><li class="jsx-802606770 illustration-icon-grid-item one-column grid-image-left"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9d6b5f42b0641e4a/6492528b0f2d9b16c2ed693a/illustration-security-lock-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="prevent-frauds-and-cyber-attacks" class="jsx-1955866259 h5">Prevent frauds and cyber attacks</h3></div></div><div><div class="paragraph paragraph-medium"><p>Download the total economic impact study from Forrester Consulting, which spotlights the combined benefits of protecting and observing applications and services. </p></div></div><div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/elastic-stack/2021-total-economic-impact-elastic-observability-security?elektra=products-security-siem&storm=cta1&rogue=forrester-tei-gic"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></li></ul></div></div><div class="layout layout-07"></div><section class="QuotesCarousel_quotesCarousel__toTDc"><div class="QuotesCarousel_quotesCarouselSection__8HAJ5 pt-9"><div class="container"><div class="row"><div class="col-12 col-md-10 offset-md-1"><div class="slick-slider slick-initialized" dir="ltr"><button type="button" data-role="none" class="slick-arrow slick-prev" style="display:block"> <!-- -->Previous</button><div class="slick-list"><div class="slick-track" style="width:900%;left:-100%"><div data-index="0" class="slick-slide slick-active slick-current" tabindex="-1" aria-hidden="false" style="outline:none;width:11.11111111111111%;position:relative;left:0;opacity:1;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">When we started using Elasticsearch, we recognized its promise. We could see that this would be part of our future. Our engineers were able to get the full stack up and running in just thirty minutes. It was simple. It was well thought out.</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Krishna Reddy<!-- -->, <!-- -->Director, Verizon</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div><div data-index="1" class="slick-slide" tabindex="-1" aria-hidden="true" style="outline:none;width:11.11111111111111%;position:relative;left:-11px;opacity:0;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">The Elastic Stack represents the backbone of the digital transformation project to give us visibility to Entel as a whole.</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Oscar Narváez<!-- -->, <!-- -->Tools & Analytic Monitoring Team Leader, Entel</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div><div data-index="2" class="slick-slide" tabindex="-1" aria-hidden="true" style="outline:none;width:11.11111111111111%;position:relative;left:-22px;opacity:0;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">We are now able to explore our data in new and different ways, within one scalable platform and move to a model where we’re innovating and optimizing rather than monitoring and maintaining.</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Álvaro Aldana<!-- -->, <!-- -->Global Video Monitoring Technical Lead, Telefónica</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div><div data-index="3" class="slick-slide" tabindex="-1" aria-hidden="true" style="outline:none;width:11.11111111111111%;position:relative;left:-33px;opacity:0;transition:opacity 500ms ease, visibility 500ms ease"><div><div tabindex="-1" style="width:100%;display:inline-block"><div><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/bltd5a35b9717d7a1af/5e05050d12af1140b8e779c9/icon-quote-64-pink.svg" alt="icon-quote" class="QuotesCarousel_logo64__pmSml"/><div class="QuotesCarousel_quoteContent__Wc_px"><p class="QuotesCarousel_paragraph__eE7i0">It is not every day that sales and marketing says, ‘Give the folks in IT whatever they need’. But, with the Elastic system we gave them, that’s exactly what happened for us.</p></div><div class="mt-6 d-flex justify-content-center flex-wrap"><div class="jsx-1955866259 title-wrapper"><h6 tag="H6" id="" class="jsx-1955866259 "><span class="QuotesCarousel_quoteHyphen__NF5TT">Jeremy Foran<!-- -->, <!-- -->Technology Specialist, BAI Communications</span></h6></div></div><div class="mb-2 pt-4 QuotesCarousel_quotesCta__bkVZc"></div></div></div></div></div></div></div><button type="button" data-role="none" class="slick-arrow slick-next" style="display:block"> <!-- -->Next</button><div style="padding:56px 0" class="slick-dots"><ul style="margin:0"> <li class="slick-active"><button>1</button></li><li class=""><button>2</button></li><li class=""><button>3</button></li><li class=""><button>4</button></li> </ul></div></div></div></div></div></div></section><div class="layout layout-07"></div><section aria-labelledby="monetize-5g" data-component-theme="" class="jsx-3636536621 TextImageVideo_textImageVideo__UWP8e module-gb"><div class="TextImageVideo_contentRow__4wUqk" data-component-theme=""><div class="container"><div class="row d-flex justify-content-between reverseLayout"><div class="content col-12 col-md-5 col-sm-6 align-self-center position-relative TextImageVideo_textContainer__4pma1"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="monetize-5g" class="jsx-1955866259 title h4">Monetize 5G</h2></div><div class="TextImageVideo_imageContent__Bu10U paragraph-medium"><p>Get more out of data by breaking down silos to deliver telco-as-a-service. Fine-tune network and cloud parameters to deliver guaranteed quality of service for network slicing. </p></div></div><div class="TextImageVideo_assetWrapper__FPCDO col-12 col-sm-6"><div class="TextImageVideo_asset__Snh_h"><div class="jsx-1653982606 image"><figure class="jsx-1653982606"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt2036df43444fee8c/627c5c017198441d81b4dff0/illustration-currency-value-scale-1216x860.png" alt="Illustration" class="jsx-1653982606 TextImageVideo_imageVideo__uZ4gh img-fluid"/></figure></div></div></div></div></div></div><div class="TextImageVideo_contentRow__4wUqk mt-10" data-component-theme=""><div class="container"><div class="row d-flex justify-content-between reverseLayout"><div class="content col-12 col-md-5 col-sm-6 align-self-center position-relative TextImageVideo_textContainer__4pma1"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="automate-workflows" class="jsx-1955866259 title h4">Automate workflows</h2></div><div class="TextImageVideo_imageContent__Bu10U paragraph-medium"><p>Automate workflows in business and operational support systems. Implement ML-based rules for the DevSecOps continuum, even as data and software continue to grow. </p></div></div><div class="TextImageVideo_assetWrapper__FPCDO col-12 col-sm-6"><div class="TextImageVideo_asset__Snh_h"><div class="jsx-1653982606 image"><figure class="jsx-1653982606"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blted380dfa0efceadf/627c5c3b220ab5285f52d685/illustration-dev-sec-ops-cloud-automations-1216x840.png" alt="Illustration" class="jsx-1653982606 TextImageVideo_imageVideo__uZ4gh img-fluid"/></figure></div></div></div></div></div></div><div class="TextImageVideo_contentRow__4wUqk mt-10" data-component-theme=""><div class="container"><div class="row d-flex justify-content-between reverseLayout"><div class="content col-12 col-md-5 col-sm-6 align-self-center position-relative TextImageVideo_textContainer__4pma1"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="protect-your-brand" class="jsx-1955866259 title h4">Protect your brand</h2></div><div class="TextImageVideo_imageContent__Bu10U paragraph-medium"><p>Integrate seamlessly with legacy and next-generation solutions to elevate the collective IQ of your team. Use a single source of truth throughout the organization. </p></div></div><div class="TextImageVideo_assetWrapper__FPCDO col-12 col-sm-6"><div class="TextImageVideo_asset__Snh_h"><div class="jsx-1653982606 image"><figure class="jsx-1653982606"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt648ad5b483eade22/627c5c878e09542a15b92080/illustration-site-search-heart-magnifying-glass-light-1216x840.png" alt="Illustration" class="jsx-1653982606 TextImageVideo_imageVideo__uZ4gh img-fluid"/></figure></div></div></div></div></div></div></section><div class="layout layout-07"></div><section aria-labelledby="the-power-of-generative-ai-for-telco" data-component-theme="" class="jsx-3636536621 image-video module-gb"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><h2 class="topic-heading">Generative AI telecommunications use cases</h2><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="the-power-of-generative-ai-for-telco" class="jsx-1955866259 h3">The power of generative AI for telco</h2></div><div class="title-text-desc paragraph-large"><p>Generative AI has the ability to transform the telecommunications industry. Watch this video series to learn about generative AI telecommunications use cases, the value this new technology can bring to customers and employees, and key considerations for getting started. Keep watching to see an example generative AI demo for telecommunications employees.</p></div><div class="title-text-footer"><div class="cta-group align-items-center justify-content-center text-center"><div><a class="button mt-4 btn-tertiary" href="/contact?baymax=rtp&rogue=eswt-1165-b#sales"><span class="jsx-1596590093 btn-copy">Contact us</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div><div class="layout layout-05"></div><div class="container"><div class="row"><div class="col-12 col-md-10 offset-md-1 mx-auto text-center"><div class="jsx-2477493165 video"><div class="jsx-2477493165 shadow-light"><figure class="jsx-89852744 vidyard-embed "><img src="https://play.vidyard.com/UgRhyVZFAhbbcahHa2JbyA.jpg" data-uuid="UgRhyVZFAhbbcahHa2JbyA" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="0" data-muted="0" data-loop="0" data-disable_analytics="0" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></div></div></section><div class="layout layout-07"></div><div style="border-radius:" data-component-theme="" class="jsx-2381115616 card-deck-container"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h2 id="customer-case-studies" class="jsx-1955866259 h3">Customer case studies</h2></div><div class="title-text-desc paragraph-large"><p>Read some of our customer success stories to learn how the Elastic Search AI Platform helped them achieve results that matter.</p></div><div class="title-text-footer"><div class="cta-group align-items-center justify-content-center text-center"><div><a class="button mt-4 btn-tertiary" href="/customers/success-stories?industry=telecommunications"><span class="jsx-1596590093 btn-copy">See all the case studies</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div><div class="jsx-2381115616 container"><div class="layout layout-05"></div><ul class="card-deck-items card-grid card-grid-4x1" data-component-theme="light"><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2662337af018e508/5ea9e29503f6e72ff388c17c/logoparade-verizon.svg" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Cutting costs and increasing customer satisfaction. Reduced MTTR by 10x. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/customers/verizon-wireless"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4a293e73e2cfb29d/5eb44f9ec83f71298799eee5/logoparade-entel.svg" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Future-proofing the business. Reduced MTTR by 80%. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/customers/entel"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf190f51b9f6622ca/617c2fc1a2b4ac1067d76acc/logoparade-deutsche-telekom.png" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Monitoring voice data traffic. Unified fault, performance, and predictive management. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/blog/telecommunications-observability-elastic-stack-monitoring-voice-traffic-data"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li><li class="jsx-1443386464 card-list"><div style="border-radius:10px" class="jsx-1443386464 card-wrapper"><div style="border-radius:10px" data-component-theme="light" class="jsx-1443386464 card-container card card-outline-none shadow-light card-image-center card-large-padding card-content-center"><div class="card-border card-border-top bg-elastic-blue"></div><div class="card-top"><div><div class="card-topic-heading"><h2 class="topic-heading">Customer spotlight</h2></div></div><div><div class="card-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc37e388c34332f02/5ef387f9704e3d1cf536f9f6/logoparade-furuno.svg" class="img-fluid logo" alt=""/></div></div><div><div class="card-paragraph"><p>Optimizing satellite communications at sea. Improved mean time to knowledge by 94%. </p></div></div></div><div class="card-footer"><div><div class="inline-flex-align-items-baseline justify-content-center text-center"><a class="button stretched-link btn-tertiary" href="/customers/furuno"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></li></ul></div></div><div class="layout layout-07"></div><section aria-labelledby="drive-customer-centricity" data-component-theme="" class="jsx-3636536621 carousel carousel-container carousel-two-column"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="drive-customer-centricity" class="jsx-1955866259 h3">Drive customer centricity</h2></div><div class="title-text-desc paragraph-large"><p>Implement proactive customer service. Answer questions in real -time. Build customer trust through secure operations. </p></div></div></div></div><div class="layout layout-05"></div><div class="jsx-887545163 container"><div class="carousel-two-column__tab-labels-left-accordion row" data-rttabs="true"><div class="jsx-887545163 carousel-tabs col-12 col-lg-4"><ul class="react-tabs__tab-list" role="tablist"><li class="react-tabs__tab react-tabs__tab--selected" role="tab" id="react-tabs-98" aria-selected="true" aria-disabled="false" aria-controls="react-tabs-99" tabindex="0" data-rttab="true"><div class="jsx-887545163 carousel-content"><div class="jsx-887545163 carousel-heading"><a class="jsx-887545163 stretched-link"></a><div class="jsx-887545163 heading">Provide a zero-touch experience</div><div class="jsx-887545163 arrow down"></div></div><div data-selectab="0" class="jsx-887545163 carousel-body show"><div class="jsx-887545163 carousel-text"><div class="jsx-887545163 paragraph-medium"><p>Use ML, vector search, and NLP for predictive and proactive analytics, eliminating any friction during the customer journey. See how to reduce churn and maximize customer lifetime value.</p></div></div><div class="jsx-887545163 d-lg-none carousel-asset-container carousel-asset-video"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/i4ZV9akMs7rjoCyWaDtffj.jpg" data-uuid="i4ZV9akMs7rjoCyWaDtffj" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="1" data-muted="1" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></li><li class="react-tabs__tab" role="tab" id="react-tabs-100" aria-selected="false" aria-disabled="false" aria-controls="react-tabs-101" data-rttab="true"><div class="jsx-887545163 carousel-content"><div class="jsx-887545163 carousel-heading"><a class="jsx-887545163 stretched-link"></a><div class="jsx-887545163 heading">Improve service quality</div><div class="jsx-887545163 arrow down"></div></div><div data-selectab="1" class="jsx-887545163 carousel-body hidden"><div class="jsx-887545163 carousel-text"><div class="jsx-887545163 paragraph-medium"><p>Map network performance metrics and system KPIs to customer behavior. Learn how to correlate all data sources to see how service quality impacts revenue.</p></div></div><div class="jsx-887545163 d-lg-none carousel-asset-container carousel-asset-video"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/QjtXkVijeo3xuuEK163fm5.jpg" data-uuid="QjtXkVijeo3xuuEK163fm5" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="1" data-muted="1" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></li><li class="react-tabs__tab" role="tab" id="react-tabs-102" aria-selected="false" aria-disabled="false" aria-controls="react-tabs-103" data-rttab="true"><div class="jsx-887545163 carousel-content"><div class="jsx-887545163 carousel-heading"><a class="jsx-887545163 stretched-link"></a><div class="jsx-887545163 heading">Enable real-time situational awareness</div><div class="jsx-887545163 arrow down"></div></div><div data-selectab="2" class="jsx-887545163 carousel-body hidden"><div class="jsx-887545163 carousel-text"><div class="jsx-887545163 paragraph-medium"><p>Reduce MTTR with relevant real-time insights. Find out how to associate alerts and performance metrics to achieve business objectives.</p></div></div><div class="jsx-887545163 d-lg-none carousel-asset-container carousel-asset-video"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/tjnE7MReeY843DLoeteWiM.jpg" data-uuid="tjnE7MReeY843DLoeteWiM" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="1" data-muted="1" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div></div></div></li></ul></div><div class="jsx-887545163 carousel-asset-container col-12 col-lg-8 d-none d-lg-block"><div class="carousel-asset carousel-asset-video react-tabs__tab-panel--selected" role="tabpanel" id="react-tabs-99" aria-labelledby="react-tabs-98"><figure class="jsx-89852744 vidyard-embed shadow-light "><img src="https://play.vidyard.com/i4ZV9akMs7rjoCyWaDtffj.jpg" data-uuid="i4ZV9akMs7rjoCyWaDtffj" data-v="4" data-chapter="1" data-type="inline" data-referring_url="" disablepictureinpicture="" data-autoplay="0" data-hidden_controls="1" data-muted="1" data-loop="1" data-disable_analytics="1" alt="Video thumbnail" class="jsx-89852744 vidyard-player-embed "/></figure></div><div class="carousel-asset carousel-asset-video" role="tabpanel" id="react-tabs-101" aria-labelledby="react-tabs-100"></div><div class="carousel-asset carousel-asset-video" role="tabpanel" id="react-tabs-103" aria-labelledby="react-tabs-102"></div></div></div></div></section><div class="layout layout-07"></div><section aria-labelledby="data-driven-innovations-for-sustainable-networks" data-component-theme="" class="jsx-3636536621 TextImageVideo_textImageVideo__UWP8e module-gb"><div class="TextImageVideo_contentRow__4wUqk" data-component-theme=""><div class="container"><div class="row d-flex justify-content-between reverseLayout"><div class="content col-12 col-md-5 col-sm-6 align-self-center position-relative TextImageVideo_textContainer__4pma1"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="data-driven-innovations-for-sustainable-networks" class="jsx-1955866259 title h4">Data-driven innovations for sustainable networks</h2></div><div class="TextImageVideo_imageContent__Bu10U paragraph-medium"><p>Achieve your sustainability goals with data-led insights into network performance, capacity demand, power consumption, resource allocation, vendor availability, and more. </p></div></div><div class="TextImageVideo_assetWrapper__FPCDO col-12 col-sm-6"><div class="TextImageVideo_asset__Snh_h"><div class="jsx-1653982606 image"><figure class="jsx-1653982606"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt98b4abc7d98a433c/6181816f7a41520f2aabcbc0/hero-hbp-telco-white-bg-2x.png" alt="Illustration" class="jsx-1653982606 TextImageVideo_imageVideo__uZ4gh img-fluid"/></figure></div></div></div></div></div></div></section><div class="layout layout-07"></div><div style="border-radius:" data-component-theme="" class="jsx-2381115616 illustration-icon-grid-container"><div class="jsx-1383953900 title-text-one-column"><div class="jsx-1383953900 container"><div class="col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h2 tag="H2" id="enhancing-connectivity-experiences-in-related-industries" class="jsx-1955866259 h3">Enhancing connectivity experiences in related industries</h2></div><div class="title-text-desc paragraph-large"><p>Expand to new verticals and industries with an intelligent data-led approach. Build partnerships to bring new capabilities that can drive innovation in connectivity-based services across industries.</p></div><div class="title-text-footer"><div class="cta-group align-items-center justify-content-center text-center"><div><a class="button mt-4 btn-tertiary" href="/industries/telecommunications/enable-real-time-insights-at-telco-scale"><span class="jsx-1596590093 btn-copy">Download the guide</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></div></div></div><div class="jsx-2381115616 container"><div class="layout layout-05"></div><ul class="illustration-icon-grid-items illustration-icon-grid-3x1"><li class="jsx-802606770 illustration-icon-grid-item one-column grid-image-left"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7f1f4dcf2f803a4b/649361202c4f8721501b2910/illustration-search-analytics-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="automotive" class="jsx-1955866259 h5">Automotive</h3></div></div><div><div class="paragraph paragraph-medium"><p>Learn how Elastic is ensuring a secured connected car experience.</p></div></div><div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/blog/elastic-announces-tisax-certification-security-connected-vehicles"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></li><li class="jsx-802606770 illustration-icon-grid-item one-column grid-image-left"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt10dd644478e9944f/648bcd6dcb6702268b15831d/illustration-task-automation-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="manufacturing" class="jsx-1955866259 h5">Manufacturing</h3></div></div><div><div class="paragraph paragraph-medium"><p>Find out how Elastic is helping industries with digital transformation.</p></div></div><div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/industries/manufacturing"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></li><li class="jsx-802606770 illustration-icon-grid-item one-column grid-image-left"><div class="illustration-icon-grid-item-main"><div class="illustration-icon-grid-item-top grid-image-left"><div><div class="grid-image"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt70efe238ed6f0f32/648bcbfc48a8ff0b3a476e4f/illustration-shopping-cart-128.svg" class="image-xsmall" alt=""/></div></div><div></div><div></div><div></div></div><div class="illustration-icon-grid-item-content"><div></div><div><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="retail" class="jsx-1955866259 h5">Retail</h3></div></div><div><div class="paragraph paragraph-medium"><p>Discover how retail giants are driving brand loyalty using Elastic.</p></div></div><div></div></div></div><div class="illustration-icon-grid-item-footer"><div></div><div></div><div></div><div><div class="d-flex flex-column justify-content-start text-start"><a class="button btn-tertiary" href="/industries/retail-ecommerce"><span class="jsx-1596590093 btn-copy">Learn more</span><svg class="icon-embed" width="27" height="15"><use href="/static-res/images/generic-icons.svg#cta-arrow"></use></svg></a></div></div></div></li></ul></div></div><div class="layout layout-07"></div><section aria-labelledby="elastic-cloud-your-way" data-component-theme="" id="footer-cta" class="jsx-3636536621 FooterCTA_footerCta__ET7NV"><div class="FooterCTA_footerCtaWrapper__LpSzU py-9 container-border-radius-top bg-dark-ink" data-component-theme="dark"><div class="container"><div class="row"><div class="FooterCTA_titleTextSection__3NglX col-md-8 offset-md-2 text-center"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="elastic-cloud-your-way" class="jsx-1955866259 ">Elastic Cloud, your way</h3></div><div class="paragraph-medium"><p>Purchase through your marketplace of choice to consolidate your cloud bill and leverage your existing cloud spending commitments. See all the regions we support on our <a href="/cloud/regions">regions page</a>. </p></div><div class="FooterCTA_ctaGroup___3dhk"></div></div></div></div><section class="FooterCTACards_footerCtaCards__69efo"><div class="container"><div class="FooterCTACards_cardSection__K9E_m mt-8" style="grid-template-columns:repeat(4, 1fr)"><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="aws-marketplace" class="jsx-1955866259 h5">AWS Marketplace</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>Elastic Cloud on AWS gives users the ability to run prebuilt SaaS solutions for search, observability, and security. Start a free trial.</p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://aws.amazon.com/marketplace/pp/Elasticsearch-Inc-Elasticsearch-Service-on-Elastic/B01N6YCISK" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="azure-marketplace" class="jsx-1955866259 h5">Azure Marketplace</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>Elastic on Microsoft Azure gives you the ability to deploy Elasticsearch directly within the Azure portal. </p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="google-marketplace" class="jsx-1955866259 h5">Google Marketplace</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>Deploy on Google Cloud so you can derive powerful, real-time insights from your data in minutes. </p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div><div class="FooterCTACards_cardContent__6vOAB"><div class="FooterCTACards_cardTitle__MVQki"><div class="jsx-1955866259 title-wrapper"><h3 tag="H3" id="elastic-cloud-trial" class="jsx-1955866259 h5">Elastic Cloud trial</h3></div></div><div class="FooterCTACards_cardBody__mgdS5 paragraph-medium"><p>We handle the maintenance and upkeep, so you can focus on gaining the insights that help you run your business. </p></div><div class="mt-6 FooterCTACards_ctaArrow__2NqlT"><a href="https://cloud.elastic.co/registration" class="stretched-link"><img class="img-fluid" src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt5a7c7b570189ea07/5f2550947f3b7908db02fc89/arrow-white.svg" alt="arrow-white"/></a></div></div></div></div></section></div></section></div></main><div id="elastic-footer"></div><footer class="Footer_footer__Q5T55" aria-label="footer"><div class="Footer_footerWrapper__yhyD_ bg-dark-ink" data-component-theme="dark"><div class="container"><div class="row Footer_footerTop__2eyMt"><div class="Footer_footerNav__LFrAZ"><div><div><div class="Footer_logo__EaWBg"><a href="/"><img src="https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf8467a95eaa27e4a/6638d7da0d02e4e98155aaa3/logo-tagline_secondary_all_white-177.svg" alt="Elastic home"/></a></div></div><div><div class="Footer_followUs__Y4Nvp"><div><h2 class="topic-heading">Follow us</h2></div><ul class="Footer_socialIconList__eaA5a"><li class="LinkedIn"><a id="footer_linkedin" href="https://www.linkedin.com/company/elastic-co"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blte7cfb1a091901ce1/5eb00c925751b2150e57a9d6/footer-icon-linkedin.svg" alt="Elastic's LinkedIn page"/></a></li><li class="YouTube"><a id="footer_youtube" href="https://www.youtube.com/user/elasticsearch"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt7c28b18be98b1af8/5eb00ca908d37e6d82ef7655/footer-icon-youtube.svg" alt="Elastic's YouTube page"/></a></li><li class="Facebook"><a id="footer_facebook" href="https://www.facebook.com/elastic.co"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt75566c5278ad68da/5eb00c59d238e314f259fbea/footer-icon-facebook.svg" alt="Elastic's Facebook page"/></a></li><li class="Twitter"><a id="footer_twitter" href="https://www.twitter.com/elastic"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt341fed86979a9fbb/5eb00c76b8a6356e4ddc1180/footer-icon-twitter.svg" alt="Elastic's Twitter page"/></a></li><li class="GitHub"><a id="" href="https://github.com/elastic"><img src="https://static-www.elastic.co/v3/assets/bltefdd0b53724fa2ce/blt6ef5841a45696d80/64ca2a6fc530871313bc3822/icon-footer-github.svg" alt="Elastic's GitHub page"/></a></li></ul></div></div></div><div class="Footer_rightSide__zawr1"><ul class="Footer_desktopNav__gXs3Z"><li><h2 class="topic-heading">About us</h2><div class="Footer_innerNav__tQcnP"><a href="/about/">About Elastic</a><a href="/about/leadership">Leadership</a><a href="/careers/diversity-and-inclusion">DE&I</a><a href="/blog">Blog</a><a href="/about/press">Newsroom</a></div></li><li><h2 class="topic-heading">Join us</h2><div class="Footer_innerNav__tQcnP"><a href="/careers">Careers</a><a href="https://jobs.elastic.co/#/">Career portal</a><a href="/careers/how-we-hire">How we hire</a></div></li></ul><ul class="Footer_desktopNav__gXs3Z"><li><h2 class="topic-heading">Partners</h2><div class="Footer_innerNav__tQcnP"><a href="https://partners.elastic.co/findapartner/">Find a partner</a><a href="https://login.elastic.co/login/partner">Partner login</a><a href="https://partners.elastic.co/English/register_email.aspx">Request access</a><a href="/partners/become-a-partner">Become a partner</a></div></li><li><h2 class="topic-heading">Trust & Security</h2><div class="Footer_innerNav__tQcnP"><a href="/trust">Trust center</a><a href="https://secure.ethicspoint.com/domain/media/en/gui/74447/index.html">EthicsPoint portal</a><a href="/trust/business-integrity#international-trade-compliance—eccn-information">ECCN report</a><a href="mailto:ethics@elastic.co">Ethics email</a></div></li></ul><ul class="Footer_desktopNav__gXs3Z"><li><h2 class="topic-heading">Investor relations</h2><div class="Footer_innerNav__tQcnP"><a href="https://ir.elastic.co/home/default.aspx">Investor resources</a><a href="https://ir.elastic.co/governance/corporate-governance/default.aspx">Governance</a><a href="https://ir.elastic.co/financials/quarterly-results/default.aspx">Financials</a><a href="https://ir.elastic.co/stock/stock-quote/default.aspx">Stock</a></div></li><li><h2 class="topic-heading">Excellence Awards</h2><div class="Footer_innerNav__tQcnP"><a href="/blog/2022-elastic-excellence-awards-winners">Previous winners</a><a href="/elasticon">ElasticON Tour</a><a href="/events/sponsor">Become a sponsor</a><a href="/events/">All events</a></div></li></ul><div class="Footer_mobileNav__Dvl0g"><div><div data-accordion-component="Accordion" class="accordion"><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-1067785" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-1067785" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">About us</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-1067785" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/about/">About Elastic</a><a href="/about/leadership">Leadership</a><a href="/careers/diversity-and-inclusion">DE&I</a><a href="/blog">Blog</a><a href="/about/press">Newsroom</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-1067786" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-1067786" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Join us</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-1067786" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/careers">Careers</a><a href="https://jobs.elastic.co/#/">Career portal</a><a href="/careers/how-we-hire">How we hire</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-1067787" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-1067787" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Partners</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-1067787" hidden=""><div class="Footer_innerNav__tQcnP"><a href="https://partners.elastic.co/findapartner/">Find a partner</a><a href="https://login.elastic.co/login/partner">Partner login</a><a href="https://partners.elastic.co/English/register_email.aspx">Request access</a><a href="/partners/become-a-partner">Become a partner</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-1067788" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-1067788" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Trust & Security</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-1067788" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/trust">Trust center</a><a href="https://secure.ethicspoint.com/domain/media/en/gui/74447/index.html">EthicsPoint portal</a><a href="/trust/business-integrity#international-trade-compliance—eccn-information">ECCN report</a><a href="mailto:ethics@elastic.co">Ethics email</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-1067789" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-1067789" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Investor relations</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-1067789" hidden=""><div class="Footer_innerNav__tQcnP"><a href="https://ir.elastic.co/home/default.aspx">Investor resources</a><a href="https://ir.elastic.co/governance/corporate-governance/default.aspx">Governance</a><a href="https://ir.elastic.co/financials/quarterly-results/default.aspx">Financials</a><a href="https://ir.elastic.co/stock/stock-quote/default.aspx">Stock</a></div></div></div><div data-accordion-component="AccordionItem" class="accordion__item"><div data-accordion-component="AccordionItemHeading" role="heading" class="accordion__heading" aria-level="3"><div class="accordion__button" id="accordion__heading-raa-1067790" aria-disabled="false" aria-expanded="false" aria-controls="accordion__panel-raa-1067790" role="button" tabindex="0" data-accordion-component="AccordionItemButton"><h2 class="topic-heading p-0">Excellence Awards</h2><div class="accordion__arrow"><svg class="icon-embed" width="14" height="9"><use href="/static-res/images/generic-icons.svg#chevron"></use></svg></div></div></div><div data-accordion-component="AccordionItemPanel" class="accordion__panel" id="accordion__panel-raa-1067790" hidden=""><div class="Footer_innerNav__tQcnP"><a href="/blog/2022-elastic-excellence-awards-winners">Previous winners</a><a href="/elasticon">ElasticON Tour</a><a href="/events/sponsor">Become a sponsor</a><a href="/events/">All events</a></div></div></div></div></div></div></div></div></div><div class="row Footer_footerBottom__iA_rq"><div class="Footer_footnoteContainer__y0YTd"><div class="Footer_legalLinkContainer__0vR8C"><div class="text-start"><ul class="Footer_legalLinks__5LXti"><li class="Trademarks"><a href="/legal/trademarks">Trademarks</a></li><li class="Terms of Use"><a href="/legal/terms-of-use">Terms of Use</a></li><li class="Privacy"><a href="/legal/privacy-statement">Privacy</a></li><li class="Sitemap"><a href="/sitemap">Sitemap</a></li></ul><div class="Footer_copyrightDate__1vxFm"><p>© <span class="copyright-year"></span>. Elasticsearch B.V. All Rights Reserved</p></div></div></div><div class="Footer_footnote__z5kru"><p>Elastic, Elasticsearch and other related marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries.</p><p>Apache, Apache Lucene, Apache Hadoop, Hadoop, HDFS and the yellow elephant logo are trademarks of the <a href="https://www.apache.org/">Apache Software Foundation</a> in the United States and/or other countries. All other brand names, product names, or trademarks belong to their respective owners.</p></div></div></div></div></div></footer></div><script id="__NEXT_DATA__" type="application/json">{"props":{"pageProps":{"entry":{"uid":"blt3014d2e874448b7b","_version":31,"locale":"en-us","ACL":{},"anchor_bar":[],"content_gallery":{"title_l10n":"","cta":{"cta_title_l10n":"","url":""}},"content_promos":[],"created_at":"2021-10-29T17:19:38.916Z","created_by":"blt3044324473ef223b70bc674c","footer_cta_reference":[{"uid":"blta325059ea4759f18","_version":11,"locale":"en-us","ACL":{},"created_at":"2021-10-28T23:33:28.947Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[],"icon_text_card":[{"title_l10n":"AWS Marketplace","_metadata":{"uid":"csd722b679339ac543"},"image":null,"subtitle_l10n":"\u003cp\u003eElastic Cloud on AWS gives users the ability to run prebuilt SaaS solutions for search, observability, and security. Start a free trial.\u003c/p\u003e","url":"https://aws.amazon.com/marketplace/pp/Elasticsearch-Inc-Elasticsearch-Service-on-Elastic/B01N6YCISK","paragraph_l10n":"\u003cp\u003eElastic Cloud on AWS gives users the ability to run prebuilt SaaS solutions for search, observability, and security. Start a free trial.\u003c/p\u003e","cta":{"url":"https://aws.amazon.com/marketplace/pp/Elasticsearch-Inc-Elasticsearch-Service-on-Elastic/B01N6YCISK"}},{"title_l10n":"Azure Marketplace","_metadata":{"uid":"cs4da0faa45278212c"},"image":null,"subtitle_l10n":"\u003cp\u003eElastic on Microsoft Azure gives you the ability to deploy Elasticsearch directly within the Azure portal. \n\u003c/p\u003e","url":"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview","paragraph_l10n":"\u003cp\u003eElastic on Microsoft Azure gives you the ability to deploy Elasticsearch directly within the Azure portal. \n\u003c/p\u003e","cta":{"url":"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?tab=Overview"}},{"title_l10n":"Google Marketplace","_metadata":{"uid":"cs64d53f53f55c755b"},"image":null,"subtitle_l10n":"\u003cp\u003eDeploy on Google Cloud so you can derive powerful, real-time insights from your data in minutes. \n\u003c/p\u003e","url":"https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co","paragraph_l10n":"\u003cp\u003eDeploy on Google Cloud so you can derive powerful, real-time insights from your data in minutes. \n\u003c/p\u003e","cta":{"url":"https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co"}},{"title_l10n":"Elastic Cloud trial","_metadata":{"uid":"csfa27fa0008f446d8"},"image":null,"subtitle_l10n":"\u003cp\u003eWe handle the maintenance and upkeep, so you can focus on gaining the insights that help you run your business.\n\u003c/p\u003e","url":"https://cloud.elastic.co/registration","paragraph_l10n":"\u003cp\u003eWe handle the maintenance and upkeep, so you can focus on gaining the insights that help you run your business.\n\u003c/p\u003e","cta":{"url":"https://cloud.elastic.co/registration"}}],"paragraph_l10n":"\u003cp\u003ePurchase through your marketplace of choice to consolidate your cloud bill and leverage your existing cloud spending commitments. See all the regions we support on our \u003ca href=\"/cloud/regions\"\u003eregions page\u003c/a\u003e.\n\u003c/p\u003e","tags":[],"title":"Industries - Elastic Cloud, your way","title_l10n":"Elastic Cloud, your way","updated_at":"2025-02-26T00:19:41.912Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2025-02-26T00:19:45.170Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"hero":[{"uid":"blte1d75184d7761b6b","title":"Telco - Generative AI for telco","product_name":"","icon":null,"logo":null,"topic_heading_l10n":"Telecommunications","title_l10n":"The power of data and generative AI for telco","subtitle_l10n":"","paragraph_l10n":"\u003cp\u003eMost (88%) telco executives say they either already have or plan to implement generative AI (GenAI) at their organizations.\u003c/p\u003e\u003cp\u003eBut getting GenAI right depends on how well you can access, search, and analyze all your data, no matter its format or location.\u003c/p\u003e\u003cp\u003eExplore insights on data and AI from telco leaders.\u003c/p\u003e","cta":[{"type":null,"cta_title_l10n":"Read the study","_metadata":{"uid":"cs1ebd4f98f9af345d"},"url":"/resources/portfolio/report/solving-business-challenges-data-ai-telecommunications","cta_icon":{"type":null,"file":null,"position":"right"},"cta_footnote_l10n":""},{"type":null,"cta_title_l10n":"Download brief","_metadata":{"uid":"cs3e19c9151776381e"},"url":"/telecommunications/unlocking-the-power-of-generative-ai","cta_icon":{"type":null,"file":null,"position":null},"cta_footnote_l10n":""}],"download_cta":{"cta_title_l10n":"","url":""},"image":{"uid":"bltef153c426256a863","_version":1,"title":"report-cover-solving-business-challenges-telco-it.png","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2025-02-26T19:59:08.575Z","updated_at":"2025-02-26T19:59:08.575Z","content_type":"image/png","file_size":"393031","filename":"report-cover-solving-business-challenges-telco-it.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-26T21:22:54.493Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltef153c426256a863/67bf728c938bf57bf4f9ae01/report-cover-solving-business-challenges-telco-it.png"},"shadow":true,"vidyard":{"video_id":"","uuid":"","video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false},"two_column_layout":true,"overflow":false,"spacing_top":null,"spacing_bottom":null,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-10-29T17:14:08.863Z","updated_at":"2025-02-26T19:59:10.148Z","ACL":{},"_version":12,"logos_below_cta":{"logos":[],"topic_heading_l10n":""},"image_alt_text_l10n":"","asset_border_radius":null,"callout":[],"content_blocks":[],"styles":{"container_background":null,"modules_background":null,"pattern_type":"generic","show_divider":false,"enable_display_font_size":false},"publish_details":{"time":"2025-02-26T21:22:54.395Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"layout_spacing":null,"modular_blocks":[{"card":{"title_l10n":"Gain complete visibility into next-gen networks","_metadata":{"uid":"cs9c5e405c8ecfb371"},"card_reference":[{"uid":"blt28508c8455e6e7bb","_version":9,"locale":"en-us","ACL":{},"below_card_modular_blocks":[],"card_deck_style":{"type":"illustration text grid 3x1","background_color":"","border_color":"","border_direction":null,"border_radius":"10px","component_container_background_color":"","padding":null,"per_row":null,"shadow":null,"shadow_hover":null,"image_alignment":"left align","paragraph_alignment":null,"text_alignment":null,"title_heading_alignment":null,"topic_heading_alignment":null,"image_border_color":"","image_border_style":"","image_border_width":"","image_filter":"","component_container_border_radius":"","component_container_padding":null},"card_modular_blocks":[{"card":{"title_l10n":"Manage distributed networks","_metadata":{"uid":"cs7e4239ee51ab7956"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":4,"is_dir":false,"uid":"blt80f78dbbb85f42a0","ACL":{},"content_type":"image/svg+xml","created_at":"2020-05-20T21:59:14.555Z","created_by":"blt3044324473ef223b70bc674c","description":"","file_size":"143706","filename":"illustration-people-channels-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-people-channels-128.svg","updated_at":"2023-06-21T00:27:55.582Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-23T21:09:49.629Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt80f78dbbb85f42a0/6492440bb9a07659f19282d1/illustration-people-channels-128.svg"},"_metadata":{"uid":"csdc3d345d254a4d96"},"alt_text_l10n":""}},{"title":{"title_l10n":"Manage distributed networks","_metadata":{"uid":"cse7defe7314327098"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eHear from the Elastic industry team on how telecom companies are managing their core networks with Elastic.\u003c/p\u003e","_metadata":{"uid":"cs7c9109b516c9b601"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs39c3acad2c9099eb"},"icon_direction":null,"title_l10n":"Learn more","url":"/elasticon/archive/2021/global/enable-real-time-insights-at-scale-for-telco-to-solve"}],"_metadata":{"uid":"csd2c3f48d51b4222a"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Scale efficiently in the cloud","_metadata":{"uid":"cscf922e7447b3f17d"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":3,"is_dir":false,"uid":"blt7e1a162341d630e8","ACL":{},"content_type":"image/svg+xml","created_at":"2021-11-09T01:14:12.535Z","created_by":"blt3044324473ef223b70bc674c","description":"","file_size":"215851","filename":"illustration-cloud-services-security-posture-target-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-cloud-services-security-posture-target-128.svg","updated_at":"2023-10-31T06:37:38.699Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-31T06:38:32.301Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7e1a162341d630e8/6540a0b262f244001b7d9257/illustration-cloud-services-security-posture-target-128.svg"},"_metadata":{"uid":"cs72b8bcc62132a7dd"},"alt_text_l10n":""}},{"title":{"title_l10n":"Scale efficiently in the cloud","_metadata":{"uid":"cs31cd71d76b6550c7"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eFind out how a leading telecom provider realized a \u003cstrong\u003e283% ROI\u003c/strong\u003e with a payback period of \u003cstrong\u003e1.7 years\u003c/strong\u003e after deploying Elastic Cloud.\n\u003c/p\u003e","_metadata":{"uid":"cs5d3feb25fcbf6d81"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs3484a42b628487dc"},"icon_direction":null,"title_l10n":"Learn more","url":"/global-telecom-provider-realized-283-percent-roi-with-elastic-cloud"}],"_metadata":{"uid":"csd405155fdc8bde60"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Prevent frauds and cyber attacks","_metadata":{"uid":"csc21a4fae3bf54a8c"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"uid":"blt9d6b5f42b0641e4a","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-04-06T18:54:07.840Z","updated_at":"2023-06-21T01:29:47.083Z","content_type":"image/svg+xml","file_size":"226206","filename":"illustration-security-lock-128.svg","title":"illustration-security-lock-128.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"parent_uid":"blt19bfea3747fb788b","description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-21T22:12:46.803Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9d6b5f42b0641e4a/6492528b0f2d9b16c2ed693a/illustration-security-lock-128.svg"},"_metadata":{"uid":"cs8d4aec9c1f1dd4f9"},"alt_text_l10n":""}},{"title":{"title_l10n":"Prevent frauds and cyber attacks","_metadata":{"uid":"cs256114f807e8efd0"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eDownload the total economic impact study from Forrester Consulting, which spotlights the combined benefits of protecting and observing applications and services.\n\u003c/p\u003e","_metadata":{"uid":"csc4a27af8c88ca1df"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs75f839f799590082"},"icon_direction":null,"title_l10n":"Learn more","url":"/elastic-stack/2021-total-economic-impact-elastic-observability-security?elektra=products-security-siem\u0026storm=cta1\u0026rogue=forrester-tei-gic"}],"_metadata":{"uid":"cs9c207489ce5eb864"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}}],"created_at":"2021-11-04T18:18:19.225Z","created_by":"blt3044324473ef223b70bc674c","spotlight_modular_blocks":[],"tags":[],"title":"Telco - Reimagine telecom with unified visibility","title_text":{"topic_heading_l10n":"Break down network and business silos","title_l10n":"Reimagine telecom with unified visibility","paragraph_l10n":"\u003cp\u003eLeading telecom providers worldwide trust Elastic to expand their digital services footprint by helping them deliver the next-gen telecom experiences. With proven solutions built on a single search intelligence platform, Elastic enables actionable insights into networks, support systems, and customer behavior that align with business objectives.\u003c/p\u003e","modular_blocks":[{"cta":{"alignment":"center align","width":null,"list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs7226500fc3ee2b01"},"icon_direction":null,"title_l10n":"Download the guide","url":"/industries/telecommunications/enable-real-time-insights-at-telco-scale"}],"_metadata":{"uid":"cs70051163f644a476"},"footnote_l10n":""}}],"style":{"dark_mode":"","layout":null,"left_align_text":false,"two_column_layout":false,"title_heading_size":"H2"}},"updated_at":"2023-06-23T21:01:35.441Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2023-10-31T06:38:23.158Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}},{"generic_body":{"title_l10n":"Quotes","_metadata":{"uid":"cs268156aee0c184ee"},"reference":[{"_version":2,"locale":"en-us","uid":"bltded191d0f483ccb0","ACL":{},"created_at":"2022-03-07T16:33:38.636Z","created_by":"blt3e52848e0cb3c394","enable_thumbnails":false,"quote_reference":[{"title":"Krishna Reddy, Director, Verizon","topic_heading_l10n":"","logo":null,"logo_left_aligned":null,"quote_l10n":"When we started using Elasticsearch, we recognized its promise. We could see that this would be part of our future. Our engineers were able to get the full stack up and running in just thirty minutes. It was simple. It was well thought out.","quote_author_l10n":"Krishna Reddy","quote_details_l10n":"Director, Verizon","quote_banner_pattern":["bltfdf1762f0006d947"],"cta":[],"image":null,"quote":"","quote_author":"","quote_details":"","tags":[],"locale":"en-us","uid":"blt0c2d53840e09d463","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2022-03-07T16:33:24.193Z","updated_at":"2022-03-07T16:50:02.351Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:00:45.264Z","user":"blt3e52848e0cb3c394"}},{"title":"Oscar Narváez, Tools \u0026 Analytic Monitoring Team Leader, Entel","topic_heading_l10n":"","logo":null,"logo_left_aligned":null,"quote_l10n":"The Elastic Stack represents the backbone of the digital transformation project to give us visibility to Entel as a whole.","quote_author_l10n":"Oscar Narváez","quote_details_l10n":"Tools \u0026 Analytic Monitoring Team Leader, Entel","quote_banner_pattern":["bltfdf1762f0006d947"],"cta":[],"image":null,"quote":"","quote_author":"","quote_details":"","tags":[],"locale":"en-us","uid":"bltbc03cf31818e8577","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2022-03-07T16:50:34.402Z","updated_at":"2022-03-07T16:50:34.402Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:00:45.272Z","user":"blt3e52848e0cb3c394"}},{"title":"Álvaro Aldana, Global Video Monitoring Technical Lead, Telefónica","topic_heading_l10n":"","logo":null,"logo_left_aligned":null,"quote_l10n":"We are now able to explore our data in new and different ways, within one scalable platform and move to a model where we’re innovating and optimizing rather than monitoring and maintaining.","quote_author_l10n":"Álvaro Aldana","quote_details_l10n":"Global Video Monitoring Technical Lead, Telefónica","quote_banner_pattern":["bltfdf1762f0006d947"],"cta":[],"image":null,"quote":"","quote_author":"","quote_details":"","tags":[],"locale":"en-us","uid":"blte50772f6f6899119","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2022-03-07T16:51:15.807Z","updated_at":"2022-03-07T16:51:15.807Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:00:45.280Z","user":"blt3e52848e0cb3c394"}},{"title":"Jeremy Foran, Technology Specialist, BAI Communications","topic_heading_l10n":"","logo":null,"logo_left_aligned":null,"quote_l10n":"It is not every day that sales and marketing says, ‘Give the folks in IT whatever they need’. But, with the Elastic system we gave them, that’s exactly what happened for us.","quote_author_l10n":"Jeremy Foran","quote_details_l10n":"Technology Specialist, BAI Communications","quote_banner_pattern":["bltfdf1762f0006d947"],"cta":[],"image":null,"quote":"","quote_author":"","quote_details":"","tags":[],"locale":"en-us","uid":"blta8b9874e9587956b","created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-07T16:52:07.961Z","updated_at":"2022-03-07T22:05:45.826Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T14:00:45.288Z","user":"blt3e52848e0cb3c394"}}],"tags":[],"title":"Telco","updated_at":"2022-03-07T16:52:28.844Z","updated_by":"blt3e52848e0cb3c394","_content_type_uid":"quotes_carousel","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-17T16:09:10.998Z","user":"blt3044324473ef223b70bc674c"}}]}},{"generic_body":{"title_l10n":"Text Image River layout - Monetize 5G","_metadata":{"uid":"csfa1ce75ced4cf135"},"reference":[{"_content_type_uid":"text_image_video","uid":"blt8f75ffaac647cdaa","_version":2,"locale":"en-us","ACL":{},"created_at":"2022-08-12T11:48:53.944Z","created_by":"blt3e52848e0cb3c394","do_not_alternate":false,"enable_overflow":false,"module":[{"icon":{"type":null,"file":null,"alt_text":""},"_metadata":{"uid":"cs4d31b9bfb3b79c5f"},"topic_heading_l10n":"","title_l10n":"Monetize 5G","paragraph_l10n":"\u003cp\u003eGet more out of data by breaking down silos to deliver telco-as-a-service. Fine-tune network and cloud parameters to deliver guaranteed quality of service for network slicing.\n\u003c/p\u003e","paragraph_list":{"group":[],"paragraph_l10n":""},"cta":{"alignment":"left align","width":"block","list":[]},"reference":[{"_content_type_uid":"image_reference","_version":1,"locale":"en-us","uid":"blt3465eb0478e2d9e1","ACL":{},"alt_text_l10n":"Illustration","caption_l10n":"","created_at":"2022-08-12T11:45:25.352Z","created_by":"blt3e52848e0cb3c394","image":{"_version":1,"is_dir":false,"uid":"blt2036df43444fee8c","ACL":{},"content_type":"image/png","created_at":"2022-05-12T00:59:45.323Z","created_by":"blt3044324473ef223b70bc674c","file_size":"93082","filename":"illustration-currency-value-scale-1216x860.png","parent_uid":null,"tags":[],"title":"illustration-currency-value-scale-1216x860.png","updated_at":"2022-05-12T00:59:45.323Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T01:16:27.617Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2036df43444fee8c/627c5c017198441d81b4dff0/illustration-currency-value-scale-1216x860.png"},"mobile_image":null,"shadow":false,"tags":[],"title":"illustration-currency-value-scale-1216x860.png","updated_at":"2022-08-12T11:45:25.352Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-12T11:45:35.733Z","user":"blt3e52848e0cb3c394"}}],"below_paragraph_reference":[],"below_component_reference":[],"pattern":null,"border_radius":""},{"icon":{"type":null,"file":null,"alt_text":""},"_metadata":{"uid":"csaff3f65fbdebc5f7"},"topic_heading_l10n":"","title_l10n":"Automate workflows","paragraph_l10n":"\u003cp\u003eAutomate workflows in business and operational support systems. Implement ML-based rules for the DevSecOps continuum, even as data and software continue to grow.\n\u003c/p\u003e","paragraph_list":{"group":[],"paragraph_l10n":""},"cta":{"alignment":"left align","width":"block","list":[]},"reference":[{"_content_type_uid":"image_reference","_version":1,"locale":"en-us","uid":"blt0a2b52e4f6ed2f9c","ACL":{},"alt_text_l10n":"Illustration","caption_l10n":"","created_at":"2022-08-12T11:46:54.698Z","created_by":"blt3e52848e0cb3c394","image":{"_version":1,"is_dir":false,"uid":"blted380dfa0efceadf","ACL":{},"content_type":"image/png","created_at":"2022-05-12T01:00:43.222Z","created_by":"blt3044324473ef223b70bc674c","file_size":"140388","filename":"illustration-dev-sec-ops-cloud-automations-1216x840.png","parent_uid":null,"tags":[],"title":"illustration-dev-sec-ops-cloud-automations-1216x840.png","updated_at":"2022-05-12T01:00:43.222Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T01:16:27.609Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blted380dfa0efceadf/627c5c3b220ab5285f52d685/illustration-dev-sec-ops-cloud-automations-1216x840.png"},"mobile_image":null,"shadow":false,"tags":[],"title":"illustration-dev-sec-ops-cloud-automations-1216x840.png","updated_at":"2022-08-12T11:46:54.698Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-12T11:47:01.741Z","user":"blt3e52848e0cb3c394"}}],"below_paragraph_reference":[],"below_component_reference":[],"pattern":null,"border_radius":""},{"icon":{"type":null,"file":null,"alt_text":""},"_metadata":{"uid":"cs8267b6abc65af8e5"},"topic_heading_l10n":"","title_l10n":"Protect your brand","paragraph_l10n":"\u003cp\u003eIntegrate seamlessly with legacy and next-generation solutions to elevate the collective IQ of your team. Use a single source of truth throughout the organization.\n\u003c/p\u003e","paragraph_list":{"group":[],"paragraph_l10n":""},"cta":{"alignment":"left align","width":"block","list":[]},"reference":[{"_content_type_uid":"image_reference","_version":1,"locale":"en-us","uid":"bltcd2cd6f4b12f8fa9","ACL":{},"alt_text_l10n":"Illustration","caption_l10n":"","created_at":"2022-08-12T11:48:16.160Z","created_by":"blt3e52848e0cb3c394","image":{"_version":1,"is_dir":false,"uid":"blt648ad5b483eade22","ACL":{},"content_type":"image/png","created_at":"2022-05-12T01:01:59.045Z","created_by":"blt3044324473ef223b70bc674c","file_size":"87334","filename":"illustration-site-search-heart-magnifying-glass-light-1216x840.png","parent_uid":null,"tags":[],"title":"illustration-site-search-heart-magnifying-glass-light-1216x840.png","updated_at":"2022-05-12T01:01:59.045Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T01:16:27.602Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt648ad5b483eade22/627c5c878e09542a15b92080/illustration-site-search-heart-magnifying-glass-light-1216x840.png"},"mobile_image":null,"shadow":false,"tags":[],"title":"illustration-site-search-heart-magnifying-glass-light-1216x840.png","updated_at":"2022-08-12T11:48:16.160Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-12T11:48:23.648Z","user":"blt3e52848e0cb3c394"}}],"below_paragraph_reference":[],"below_component_reference":[],"pattern":null,"border_radius":""}],"reverse_layout":true,"styles":{"background_color":null,"background_color_even_rows":false},"tags":[],"title":"Telco - Monetize 5G...","title_text":{"icon_next_to_topic_heading":{"file":null,"type":null},"topic_heading_l10n":"","title_l10n":"","paragraph_l10n":"","modular_blocks":[],"style":{"layout":null,"left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2025-02-20T12:25:57.986Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-02-20T12:26:06.935Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}},{"generic_body":{"title_l10n":"Video | The power of generative AI for telco","_metadata":{"uid":"cs4c6f28ef9a76f318"},"reference":[{"_content_type_uid":"image_video","uid":"blt7eb4c80cb7aaa672","_version":11,"locale":"en-us","ACL":{},"component_theme":{"color":null,"theme_type":null,"module_color":null,"container_color":null,"container_border_radius":null,"container_style":null,"divider_top":null,"divider_bottom":null,"spacer_top":null,"spacer_bottom":null},"created_at":"2023-12-04T21:11:37.006Z","created_by":"blt3044324473ef223b70bc674c","logo_bar_reference":[],"reference":[{"_content_type_uid":"video_reference","uid":"blt7af39ad71430720f","_version":1,"locale":"en-us","ACL":{},"border_radius":null,"caption_l10n":"","created_at":"2023-12-04T21:11:24.584Z","created_by":"blt3044324473ef223b70bc674c","footnote_l10n":"","hide_controls":false,"image":null,"loop":false,"looping_animation":false,"mute":false,"play_count":"","shadow":true,"tags":[],"title":"UgRhyVZFAhbbcahHa2JbyA","type":"vidyard","updated_at":"2023-12-04T21:11:24.584Z","updated_by":"blt3044324473ef223b70bc674c","video":null,"video_url_l10n":"","vidyard":[{"_version":1,"locale":"en-us","uid":"blt816389ca16566528","ACL":{},"created_at":"2023-12-04T21:10:18.478Z","created_by":"blt3044324473ef223b70bc674c","disable_analytics":false,"player_id":"","tags":[],"title":"UgRhyVZFAhbbcahHa2JbyA","updated_at":"2023-12-04T21:10:18.478Z","updated_by":"blt3044324473ef223b70bc674c","uuid":"UgRhyVZFAhbbcahHa2JbyA","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T21:10:22.325Z","user":"blt3044324473ef223b70bc674c"}}],"publish_details":{"time":"2023-12-04T21:11:29.519Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags":[],"title":"Industries - Telecommunications - The power of generative AI for telco","title_text":{"icon_next_to_topic_heading":{"file":null,"type":null},"topic_heading_l10n":"Generative AI telecommunications use cases","title_l10n":"The power of generative AI for telco","paragraph_l10n":"\u003cp\u003eGenerative AI has the ability to transform the telecommunications industry. Watch this video series to learn about generative AI telecommunications use cases, the value this new technology can bring to customers and employees, and key considerations for getting started. Keep watching to see an example generative AI demo for telecommunications employees.\u003c/p\u003e","modular_blocks":[{"cta":{"alignment":"center align","width":null,"list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs5a20218e3624e75a"},"icon_direction":null,"title_l10n":"Contact us","url":"/contact?baymax=rtp\u0026rogue=eswt-1165-b#sales"}],"_metadata":{"uid":"cse88196102408cb9f"},"footnote_l10n":""}}],"style":{"dark_mode":"","layout":"one-column","left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2023-12-07T18:22:26.710Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2023-12-07T18:42:01.658Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}},{"card":{"title_l10n":"Telco - Customer Case Studies","_metadata":{"uid":"csec68fc4651bfecf5"},"card_reference":[{"uid":"blt32f6af2ba600a729","_version":8,"locale":"en-us","ACL":{},"below_card_modular_blocks":[],"card_deck_style":{"type":"no outline card","border_radius":"10px","padding":"card-large","per_row":"4","shadow":"shadow-light","shadow_hover":null,"image_alignment":"center align","paragraph_alignment":null,"text_alignment":"center align","title_heading_alignment":null,"topic_heading_alignment":null,"border":"elastic-blue","component_container_border_radius":"","component_container_padding":null,"component_container_show_border":false,"container_background_color":null,"size_title_heading":null},"card_modular_blocks":[{"card":{"title_l10n":"Verizon","_metadata":{"uid":"cs99e13e70d1b79e08"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cs810876ac10f75bd8"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"uid":"blt2662337af018e508","ACL":{},"_version":1,"content_type":"image/svg+xml","created_at":"2020-04-29T20:24:53.111Z","created_by":"blt3044324473ef223b70bc674c","file_size":"5322","filename":"logoparade-verizon.svg","is_dir":false,"tags":[],"title":"logoparade-verizon.svg","updated_at":"2022-02-11T21:01:14.609Z","updated_by":"blt3044324473ef223b70bc674c","parent_uid":"blt6d22b227aff4713c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-09T20:04:29.183Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2662337af018e508/5ea9e29503f6e72ff388c17c/logoparade-verizon.svg"},"_metadata":{"uid":"csa263da7e57005655"},"alt_text_l10n":"Verizon logo"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eCutting costs and increasing customer satisfaction. Reduced MTTR by 10x. \n\u003c/p\u003e","_metadata":{"uid":"cs49ae72586213f967"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs65fac216e5ecc468"},"icon_direction":null,"title_l10n":"Learn more","url":"/customers/verizon-wireless"}],"_metadata":{"uid":"csa1b35d0bca848f0f"}}}],"style":{"border":null,"badge_l10n":""}}},{"card":{"title_l10n":"Entel","_metadata":{"uid":"csf2fad47c03c58f69"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cs9585212638c61dbd"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"_version":1,"is_dir":false,"uid":"blt4a293e73e2cfb29d","ACL":{},"content_type":"image/svg+xml","created_at":"2020-05-07T18:12:46.971Z","created_by":"blt3044324473ef223b70bc674c","file_size":"9312","filename":"logoparade-entel.svg","tags":[],"title":"logoparade-entel.svg","updated_at":"2022-02-11T21:00:41.866Z","updated_by":"blt3044324473ef223b70bc674c","parent_uid":"blt6d22b227aff4713c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-09T20:05:53.647Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4a293e73e2cfb29d/5eb44f9ec83f71298799eee5/logoparade-entel.svg"},"_metadata":{"uid":"cs2b3fe1d33a71bdb7"},"alt_text_l10n":"Entel logo"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eFuture-proofing the business. Reduced MTTR by 80%. \n\u003c/p\u003e","_metadata":{"uid":"cseee2db3b723d1e78"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs35a51f213e787a53"},"icon_direction":null,"title_l10n":"Learn more","url":"/customers/entel"}],"_metadata":{"uid":"cs41172f698eaee944"}}}],"style":{"border":null,"badge_l10n":""}}},{"card":{"title_l10n":"Deutsche Telekom","_metadata":{"uid":"csf97c4af48536631b"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cs3fcf31f8c8bb5111"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"_version":1,"is_dir":false,"uid":"bltf190f51b9f6622ca","ACL":{},"content_type":"image/png","created_at":"2021-10-29T17:30:41.720Z","created_by":"blt3044324473ef223b70bc674c","file_size":"3336","filename":"logoparade-deutsche-telekom.png","tags":[],"title":"logoparade-deutsche-telekom.png","updated_at":"2022-02-11T20:59:36.510Z","updated_by":"blt3044324473ef223b70bc674c","parent_uid":"blt6d22b227aff4713c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-11T16:44:54.296Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf190f51b9f6622ca/617c2fc1a2b4ac1067d76acc/logoparade-deutsche-telekom.png"},"_metadata":{"uid":"cs72cb80deb3c2df4b"},"alt_text_l10n":"Deutsche Telekom logo"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eMonitoring voice data traffic. Unified fault, performance, and predictive management.\n\u003c/p\u003e","_metadata":{"uid":"csb19d1383058a08ba"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs381cb2d427195389"},"icon_direction":null,"title_l10n":"Learn more","url":"/blog/telecommunications-observability-elastic-stack-monitoring-voice-traffic-data"}],"_metadata":{"uid":"csb8e51a9e16779329"}}}],"style":{"border":null,"badge_l10n":""}}},{"card":{"title_l10n":"Furuno","_metadata":{"uid":"csdc7fd4643b9d72e9"},"modular_blocks":[{"topic_heading":{"topic_heading_l10n":"Customer spotlight","_metadata":{"uid":"cse0f6e1cd0656eed7"},"style":null,"image":{"type":null,"file":null,"alt_text_l10n":""}}},{"image":{"type":"logo","file":{"uid":"bltc37e388c34332f02","_version":1,"parent_uid":"blt6d22b227aff4713c","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-24T17:06:01.983Z","updated_at":"2022-02-11T21:00:29.757Z","content_type":"image/svg+xml","file_size":"4019","filename":"logoparade-furuno.svg","title":"logoparade-furuno.svg","ACL":{},"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-17T22:59:42.824Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc37e388c34332f02/5ef387f9704e3d1cf536f9f6/logoparade-furuno.svg"},"_metadata":{"uid":"csee2de453b413e506"},"alt_text_l10n":"Furuno logo"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eOptimizing satellite communications at sea. Improved mean time to knowledge by 94%. \n\u003c/p\u003e","_metadata":{"uid":"cs80852e2f1f4fc773"}}},{"cta":{"alignment":"center align","width":"inline","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"csec755e8263dd0c9b"},"icon_direction":null,"title_l10n":"Learn more","url":"/customers/furuno"}],"_metadata":{"uid":"csd710e886c549416f"}}}],"style":{"border":null,"badge_l10n":""}}}],"created_at":"2021-10-28T20:58:18.950Z","created_by":"blt3044324473ef223b70bc674c","spotlight_modular_blocks":[],"tags":[],"title":"Telco - Customer case studies","title_text":{"topic_heading_l10n":"","title_l10n":"Customer case studies","paragraph_l10n":"\u003cp\u003eRead some of our customer success stories to learn how the Elastic Search AI Platform helped them achieve results that matter.\u003c/p\u003e","modular_blocks":[{"cta":{"alignment":"center align","width":null,"list":[{"type":"tertiary","icon_type":null,"title_l10n":"See all the case studies","_metadata":{"uid":"cs63c3fb764ffa0969"},"url":"/customers/success-stories?industry=telecommunications"}],"_metadata":{"uid":"cse0e2e8f3074dcc27"},"footnote_l10n":""}}],"style":{"layout":null,"left_align_text":false,"two_column_layout":false,"title_heading_size":null},"icon_next_to_topic_heading":{"file":null,"type":null}},"updated_at":"2025-02-26T00:20:38.435Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2025-02-26T00:20:43.727Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}},{"carousel":{"title_l10n":"Drive customer centricity","_metadata":{"uid":"csd56890297a833be0"},"location":null,"reference":[{"_content_type_uid":"carousel","_version":4,"locale":"en-us","uid":"bltd1399b525e402efd","ACL":{},"carousel_modular_blocks":[{"video":{"tab_title_l10n":"Provide a zero-touch experience","_metadata":{"uid":"cs63d406057af67430"},"tab_url":"","tab_paragraph_l10n":"\u003cp\u003eUse ML, vector search, and NLP for predictive and proactive analytics, eliminating any friction during the customer journey. See how to reduce churn and maximize customer lifetime value.\u003c/p\u003e","source":{"file":null,"vidyard_uuid":"i4ZV9akMs7rjoCyWaDtffj"},"settings":{"data_chapter":"","hide_controls":true,"loop_video":true,"muted":true,"shadow":true,"play_count":"auto"}}},{"video":{"tab_title_l10n":"Improve service quality","_metadata":{"uid":"cs2420858cbf6ddce4"},"tab_url":"","tab_paragraph_l10n":"\u003cp\u003eMap network performance metrics and system KPIs to customer behavior. Learn how to correlate all data sources to see how service quality impacts revenue.\u003c/p\u003e","source":{"file":null,"vidyard_uuid":"QjtXkVijeo3xuuEK163fm5"},"settings":{"data_chapter":"","hide_controls":true,"loop_video":true,"muted":true,"shadow":true,"play_count":"auto"}}},{"video":{"tab_title_l10n":"Enable real-time situational awareness","_metadata":{"uid":"cs2aa866dbe4b06258"},"tab_url":"","tab_paragraph_l10n":"\u003cp\u003eReduce MTTR with relevant real-time insights. Find out how to associate alerts and performance metrics to achieve business objectives.\u003c/p\u003e","source":{"file":null,"vidyard_uuid":"tjnE7MReeY843DLoeteWiM"},"settings":{"data_chapter":"","hide_controls":true,"loop_video":true,"muted":true,"shadow":true,"play_count":"auto"}}}],"created_at":"2022-09-20T21:31:54.939Z","created_by":"blt36e890d06c5ec32c","style":{"type":"two-column, tab labels left, tab description - accordion","width":"10 column","carousel_container_background_color":"","carousel_container_border_radius":"","carousel_container_padding":null,"carousel_container_shadow":null,"tab_label_opacity":null},"tags":[],"title":"Telco - Drive customer centricity","title_text":{"topic_heading_l10n":"","title_l10n":"Drive customer centricity","paragraph_l10n":"\u003cp\u003eImplement proactive customer service. Answer questions in real -time. Build customer trust through secure\u0026nbsp;operations.\n\u003c/p\u003e","modular_blocks":[],"style":{"dark_mode":"","layout":null,"left_align_text":false,"title_heading_size":"H2","two_column_layout":false},"icon_next_to_topic_heading":{"file":null,"type":null}},"updated_at":"2022-11-29T09:38:59.653Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-29T09:39:03.346Z","user":"blt3e52848e0cb3c394"}}]}},{"generic_body":{"title_l10n":"Text Image - Data-driven innovations for sustainable networks","_metadata":{"uid":"cs7335c9464ad96e70"},"reference":[{"_content_type_uid":"text_image_video","uid":"blt895bf87e9a5aa7f3","_version":2,"locale":"en-us","ACL":{},"created_at":"2022-08-12T13:34:28.167Z","created_by":"blt3e52848e0cb3c394","do_not_alternate":false,"enable_overflow":false,"module":[{"icon":{"type":null,"file":null,"alt_text":""},"_metadata":{"uid":"csecb657e880733552"},"topic_heading_l10n":"","title_l10n":"Data-driven innovations for sustainable networks","paragraph_l10n":"\u003cp\u003eAchieve your sustainability goals with data-led insights into network performance, capacity demand, power consumption, resource allocation, vendor availability, and more.\n\u003c/p\u003e","paragraph_list":{"group":[],"paragraph_l10n":""},"cta":{"alignment":"left align","width":"block","list":[]},"reference":[{"_content_type_uid":"image_reference","_version":1,"locale":"en-us","uid":"blt69a8eb85039c2963","ACL":{},"alt_text_l10n":"Illustration","caption_l10n":"","created_at":"2022-08-12T13:34:06.873Z","created_by":"blt3e52848e0cb3c394","image":{"_version":1,"is_dir":false,"uid":"blt98b4abc7d98a433c","ACL":{},"content_type":"image/png","created_at":"2021-11-02T18:20:31.601Z","created_by":"blt3044324473ef223b70bc674c","file_size":"162386","filename":"hero-hbp-telco-white-bg-2x.png","parent_uid":null,"tags":[],"title":"hero-hbp-telco-white-bg-2x.png","updated_at":"2021-11-02T18:20:31.601Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-03T23:19:54.666Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt98b4abc7d98a433c/6181816f7a41520f2aabcbc0/hero-hbp-telco-white-bg-2x.png"},"mobile_image":null,"shadow":false,"tags":[],"title":"hero-hbp-telco-white-bg-2x.png","updated_at":"2022-08-12T13:34:06.873Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-12T13:34:17.818Z","user":"blt3e52848e0cb3c394"}}],"below_paragraph_reference":[],"below_component_reference":[],"pattern":null,"border_radius":""}],"reverse_layout":true,"styles":{"background_color":null,"background_color_even_rows":false},"tags":[],"title":"Telco - Data-driven innovations for sustainable networks","title_text":{"icon_next_to_topic_heading":{"file":null,"type":null},"topic_heading_l10n":"","title_l10n":"","paragraph_l10n":"","modular_blocks":[],"style":{"layout":null,"left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2025-02-20T12:16:33.190Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-02-20T12:16:38.206Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}},{"card":{"title_l10n":"Enhancing connectivity experiences in related industries","_metadata":{"uid":"csbb3747c0e93beaf2"},"card_reference":[{"_version":4,"locale":"en-us","uid":"blt81bbe1b9a70c2007","ACL":{},"below_card_modular_blocks":[],"card_deck_style":{"type":"illustration text grid 3x1","background_color":"","border_color":"","border_direction":null,"border_radius":"10px","component_container_background_color":"","component_container_border_radius":"","component_container_padding":null,"padding":null,"per_row":null,"shadow":null,"shadow_hover":null,"image_alignment":"left align","paragraph_alignment":null,"text_alignment":null,"title_heading_alignment":null,"topic_heading_alignment":null,"image_border_color":"","image_border_style":"","image_border_width":"","image_filter":""},"card_modular_blocks":[{"card":{"title_l10n":"Automotive","_metadata":{"uid":"cse4e6ecf6606b4df9"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":2,"is_dir":false,"uid":"blt7f1f4dcf2f803a4b","ACL":{},"content_type":"image/svg+xml","created_at":"2019-06-17T23:01:50.218Z","created_by":"blt3044324473ef223b70bc674c","description":"","file_size":"167776","filename":"illustration-search-analytics-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-search-analytics-128.svg","updated_at":"2023-06-21T20:44:16.520Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-23T19:52:46.049Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7f1f4dcf2f803a4b/649361202c4f8721501b2910/illustration-search-analytics-128.svg"},"_metadata":{"uid":"cs18a317885c6ef633"},"alt_text_l10n":""}},{"title":{"title_l10n":"Automotive","_metadata":{"uid":"cs222c1b859127cf05"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eLearn how Elastic is ensuring a secured connected car experience.\u003c/p\u003e","_metadata":{"uid":"cs84371ff286c8f5aa"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs4e368d3237bd9022"},"icon_direction":null,"title_l10n":"Learn more","url":"/blog/elastic-announces-tisax-certification-security-connected-vehicles"}],"_metadata":{"uid":"cs51f77c3c2c6b9ebc"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Manufacturing","_metadata":{"uid":"cs6653d51015c63eea"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"uid":"blt10dd644478e9944f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-05-12T01:15:09.525Z","updated_at":"2023-06-16T02:48:13.602Z","content_type":"image/svg+xml","file_size":"226211","filename":"illustration-task-automation-128.svg","title":"illustration-task-automation-128.svg","ACL":{},"_version":2,"parent_uid":null,"is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-21T22:12:47.275Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt10dd644478e9944f/648bcd6dcb6702268b15831d/illustration-task-automation-128.svg"},"_metadata":{"uid":"csa697911f478dd182"},"alt_text_l10n":""}},{"title":{"title_l10n":"Manufacturing","_metadata":{"uid":"cs5bd7024bcd9074de"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eFind out how Elastic is helping industries with digital transformation.\u003c/p\u003e","_metadata":{"uid":"csde679be67134b780"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs18a7e3ef84072ce0"},"icon_direction":null,"title_l10n":"Learn more","url":"/industries/manufacturing"}],"_metadata":{"uid":"csb1c7d5cdf53da807"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}},{"card":{"title_l10n":"Retail","_metadata":{"uid":"cs9d9ddbc2ee21e8a5"},"modular_blocks":[{"image":{"type":"image-xsmall","file":{"_version":2,"is_dir":false,"uid":"blt70efe238ed6f0f32","ACL":{},"content_type":"image/svg+xml","created_at":"2020-02-13T23:46:17.100Z","created_by":"blt3044324473ef223b70bc674c","description":"","file_size":"156304","filename":"illustration-shopping-cart-128.svg","parent_uid":"blt19bfea3747fb788b","tags":[],"title":"illustration-shopping-cart-128.svg","updated_at":"2023-06-16T02:42:04.496Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-22T02:15:52.360Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt70efe238ed6f0f32/648bcbfc48a8ff0b3a476e4f/illustration-shopping-cart-128.svg"},"_metadata":{"uid":"cs15ddbcc9fa4dab73"},"alt_text_l10n":""}},{"title":{"title_l10n":"Retail","_metadata":{"uid":"cs13347a5b03f86f48"},"url":"","size_title":null}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eDiscover how retail giants are driving brand loyalty using Elastic.\u003c/p\u003e","_metadata":{"uid":"csd3fdffce6a21b2b6"}}},{"cta":{"alignment":"left align","width":"block","list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs370c7031d4d5ae5d"},"icon_direction":null,"title_l10n":"Learn more","url":"/industries/retail-ecommerce"}],"_metadata":{"uid":"csad59fa1bafa3554e"}}}],"style":{"background_color":"","border_color":"","border_direction":null}}}],"created_at":"2022-05-12T01:15:59.876Z","created_by":"blt3044324473ef223b70bc674c","spotlight_modular_blocks":[],"tags":[],"title":"Telco - Enhancing connectivity experiences in related industries","title_text":{"topic_heading_l10n":"","title_l10n":"Enhancing connectivity experiences in related\u0026nbsp;industries","paragraph_l10n":"\u003cp\u003eExpand to new verticals and industries with an intelligent data-led approach. Build partnerships to bring new capabilities that can drive innovation in connectivity-based services across industries.\u003c/p\u003e","modular_blocks":[{"cta":{"alignment":"center align","width":null,"list":[{"type":"tertiary","file":null,"_metadata":{"uid":"cs4123d899c5075819"},"icon_direction":null,"title_l10n":"Download the guide","url":"/industries/telecommunications/enable-real-time-insights-at-telco-scale"}],"_metadata":{"uid":"csf18253d1d1715174"},"footnote_l10n":""}}],"style":{"dark_mode":"","layout":null,"left_align_text":false,"title_heading_size":"H2","two_column_layout":false}},"updated_at":"2023-06-23T19:48:44.125Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-23T22:11:30.737Z","user":"blt36e890d06c5ec32c"}}]}}],"module_header":null,"seo":{"seo_title_l10n":"Elastic for telecommunications","seo_description_l10n":"Learn about the Search \u0026 Data Platform for Telecommunications from Elastic that enables this sector to transform operations in the 5G era, gain deeper insight into key performance indicators, enhance the customer experience, reduce the cost of customer acquisition, and protect the brand from outages or security incidents.","seo_image":null,"canonical_tag":"","noindex":false,"nofollow":false},"social_media":{"topic_heading_l10n":"","display_social_media_module":false},"structured_data":{"data_l10n":""},"tags":[],"tags_content_type":[],"tags_elastic_stack":[],"tags_industry":[],"tags_language":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":null,"title":"Telco - Achieve real-time, high- resolution insights at telco scale","updated_at":"2025-02-26T00:12:44.425Z","updated_by":"blt3044324473ef223b70bc674c","url":"/industries/telecommunications","publish_details":{"time":"2025-02-26T21:22:53.609Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},"locale":"","videos":[[{"uid":"bltd96ca5e8ce3b1d50","_version":12,"locale":"en-us","ACL":{},"created_at":"2025-03-26T09:26:57.534Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"2025 ElasticON Tour Syndey On Demand","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eElasticON Sydney 2025 was a groundbreaking event focused on \u003cstrong\u003eSupercharging \u0026lt;anything\u0026gt; with Search AI.\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhile the event itself has come to a close, the opportunity to learn and grow doesn't have to. We're offering on-demand access to exclusive sessions, insights, and innovations from some of the brightest minds in the industry. Whether you missed the event or want to relive the highlights, dive into a wealth of valuable content now. The action packed day highlighted the breadth of our technologies, strength of our community, and the depth of our customer and partner relationships.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cstrong\u003eLearn the latest advancements in Elastic:\u003c/strong\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eSearch:\u003c/strong\u003e Build generative AI applications faster than ever before. Deploy and scale across any environment (whether you're on-prem, in the cloud, or somewhere in between)\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eObservability:\u003c/strong\u003e Accelerate problem resolution and improve operational efficiency with Elastic's full stack Search AI-powered observability — fast, contextual, and intelligent observability across the broadest data sources.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eSecurity:\u003c/strong\u003e Detect sooner, investigate faster, and remediate before threats have a chance with Search AI-driven security analytics on the Elastic Search AI Platform.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-03-06T03:30:00.000Z","presenter":["blt99b00fd2496f838e","blt56500a97294fab28","blt6d194548ac42b2dc","bltd8c662f02c05199b","blt9f1e1cacd8fbd682","blt478d09976ac97420","blt98833041240bcd05","blt447838d009a3e1f4","blt0896400660d3af74","blt2430c9dcf8b77248","blt4997fec702d2a043","blt3f40228a9a953e07","bltfe527589b3edba86","bltc02c6104e3bb74eb","blt33c7df8b6c6cc48d","blt2843c397def9f319","blt849afd8f13e08832","blt6c6a8b2857cf88e8"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"2025 ElasticON Tour Sydney On Demand","seo_description_l10n":"This on-demand access is to access exclusive sessions, insights, and innovations from some of the brightest minds in the industry. ","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":["blta3fd0168b354a680","blt3d820a0eae1c9158"],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[{"uid":"bltc3a97789fa82c0a5","_content_type_uid":"tags_event_delivery"}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":["blt25a1df5963785e04"],"tags_role":["blt945c4bcb7423a5db","bltc7c3b39e2e489f59","blte90f70f3321c02eb"],"tags_stage":["blt07282f7110d8ad35"],"tags_technical_level":["blt09c5429e20d2ba41"],"tags_topic":["blt99b075caf3df4ca7","bltc76ab818663a30de","bltd2296d539450bf20"],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"2025 ElasticON Tour Sydney On Demand","token":"k36ytdcznt","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-29T16:02:38.085Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/2025-elasticon-tour-sydney-on-demand","video_type":[{"_version":6,"locale":"en-us","uid":"bltdcadaef5bdccac7e","ACL":{},"created_at":"2018-09-14T22:03:35.691Z","created_by":"blt5c97f327f30903e707c39c30","cta_title_l10n":"Watch now","key":"webinar_recorded","tags":[],"title":"Webinar (Archived)/Video (Gated)","title_l10n":"Customer Success Story","updated_at":"2024-03-01T14:32:53.729Z","updated_by":"bltd4a1665034acc830","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-07-18T20:32:05.528Z","user":"blt36e890d06c5ec32c"}}],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-29T16:02:45.010Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf0bcaadf262656d4","_version":27,"locale":"en-us","ACL":{},"created_at":"2025-03-18T06:58:19.061Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"2025 ElasticON Tour Singapore On Demand","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eTo skip ahead or choose which session you'd like to watch, click on the drop down menu in the top left corner of the playlist and see all the videos in the playlist.\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eElasticON Singapore 2025 was a groundbreaking event focused on \u003cstrong\u003eSupercharging \u0026lt;anything\u0026gt; with Search AI\u003c/strong\u003e.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhile the event itself has come to a close, the opportunity to learn and grow doesn't have to. We're offering on-demand access to exclusive sessions, insights, and innovations from some of the brightest minds in the industry. Whether you missed the event or want to relive the highlights, dive into a wealth of valuable content now. The action packed day highlighted the breadth of our technologies, strength of our community, and the depth of our customer and partner relationships.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eLearn the latest advancements in Elastic:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eSearch:\u003c/strong\u003e Build generative AI applications faster than ever before. Deploy and scale across any environment (whether you're on-prem, in the cloud, or somewhere in between)\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eObservability:\u003c/strong\u003e Accelerate problem resolution and improve operational efficiency with Elastic's full stack Search AI-powered observability — fast, contextual, and intelligent observability across the broadest data sources.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eSecurity:\u003c/strong\u003e Detect sooner, investigate faster, and remediate before threats have a chance with Search AI-driven security analytics on the Elastic Search AI Platform.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-03-04T00:00:00.000Z","presenter":["blt4990cfe37610ed0f","blt2430c9dcf8b77248","bltacd296962b184324","blte077751d388a38eb","blt598430dd66dec40d","blt8059b98a363c4188","bltd5fa52ed63b5c368","bltc2ab0be4acd23ab3","bltd4bc606cc96f4705","blt961d8d8769dbda90","blt31907cc8d673f59c","bltcdeff3671846f191","bltaed173dcaf595e32","bltbe8d6059b59aa777","blt0555a58731a0323f","blt69ada0b40c53529a","blt6bf9ccfdc624f123","blt5d2e8b61a6606cc4","blt2a4c77b305324183"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"ElasticON Tour Singapore On Demand","seo_description_l10n":"Missed out or interested in reliving the experience? Gain access to exclusive content from our diverse range of speakers.","seo_keywords_l10n":"Elasticsearch, Security","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":["blt25a1df5963785e04"],"tags_role":["blt945c4bcb7423a5db","bltc7c3b39e2e489f59","blte90f70f3321c02eb"],"tags_stage":["blt07282f7110d8ad35"],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"2025 ElasticON Tour Singapore On Demand","token":"jpxkje13y9","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T03:14:58.021Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/2025-elasticon-tour-singapore-on-demand","video_type":[{"_version":6,"locale":"en-us","uid":"bltdcadaef5bdccac7e","ACL":{},"created_at":"2018-09-14T22:03:35.691Z","created_by":"blt5c97f327f30903e707c39c30","cta_title_l10n":"Watch now","key":"webinar_recorded","tags":[],"title":"Webinar (Archived)/Video (Gated)","title_l10n":"Customer Success Story","updated_at":"2024-03-01T14:32:53.729Z","updated_by":"bltd4a1665034acc830","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-07-18T20:32:05.528Z","user":"blt36e890d06c5ec32c"}}],"vidyard":{"uuid":"WVWDemuLAMZsoTmUGzhyyf","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T03:15:04.019Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbf1a84ce72d54061","_version":7,"locale":"en-us","ACL":{},"created_at":"2025-02-11T22:32:54.367Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"ElasticON San Francisco 2024 | Adobe","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eJoin Elastic's Steve Kearns and Adobe's Varsha Chandan and Jordan Moore to explore how the latest platform innovations and AI integration can streamline development and issue diagnosis.\u003c/p\u003e\n\u003ch4\u003eHighlights\u003c/h4\u003e\n\u003cul\u003e\n \u003cli\u003eUncovering how the latest platform innovations simplify building and scaling Elastic solutions\u003c/li\u003e\n \u003cli\u003eLeveraging AI and Elasticsearch to reduce time and costs associated with developer tools\u003c/li\u003e\n \u003cli\u003eDiagnosing issues more efficiently using AI and Elasticsearch\u003c/li\u003e\n \u003cli\u003eThe role of AI in enhancing developer productivity\u003c/li\u003e\n \u003cli\u003eFuture milestones for evolving development tools with AI\u003c/li\u003e\n \u003cli\u003eHow Elastic’s platform innovations support your organization's scaling needs\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch4\u003eWant to stay in the loop on all things Elastic?\u003c/h4\u003e\n\u003cp\u003e\u003ca href=\"/events?tab=1\" target=\"_self\"\u003eJoin us\u003c/a\u003e at our upcoming events or check out \u003ca href=\"/events/elasticon/archive\" target=\"_self\"\u003eElasticON's video archive\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"/community\" target=\"_self\"\u003eGet connected\u003c/a\u003e to find help from the Elastic community.\u003c/p\u003e","presentation_date":"2025-02-10T16:00:00.000Z","presenter":["blta88061c105b8011d","blt6d541ad58e5164d9","blt3c68347d16e32c8b"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"ElasticON San Francisco 2024 | Adobe","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":true},"tags":[],"tags_elastic_stack":["blt6f3b5313b04c2729"],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":["bltccf54d4afac13158","blt0c39553861919e12","blt25a1df5963785e04"],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"ElasticON 2024/2025 - ElasticON San Francisco 2024 | Adobe","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-02-12T18:40:08.694Z","updated_by":"blt3044324473ef223b70bc674c","url":"/events/elasticon/archive/adobe","video_type":[{"title":"Video","key":"short_video","tags":[],"locale":"en-us","uid":"blt0d07966d0c7cc2b8","created_by":"blt5c97f327f30903e707c39c30","updated_by":"blt5c97f327f30903e707c39c30","created_at":"2018-09-14T22:03:52.264Z","updated_at":"2018-09-14T22:03:52.264Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-25T13:26:41.920Z","user":"blt0ac59771801e2eb09befe680"}}],"vidyard":{"uuid":"xJCsxzyiRjnD33NJsuBGaP","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-02-13T20:40:19.072Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],859],"imgAltContent":[[{"_version":1,"locale":"en-us","uid":"bltffa924ac55d9696b","ACL":{},"alt_text_l10n":"Google Cloud","created_at":"2022-09-26T22:03:17.978Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Google Cloud","updated_at":"2022-09-26T22:03:17.978Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.258Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt3b58313da82f767d","ACL":{},"alt_text_l10n":"Alibaba Cloud","created_at":"2022-09-26T22:02:31.046Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Alibaba Cloud","updated_at":"2022-09-26T22:03:01.894Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.247Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt75d785f1e5852fe1","ACL":{},"alt_text_l10n":"Tencent Cloud","created_at":"2022-09-26T22:02:54.706Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Tencent Cloud","updated_at":"2022-09-26T22:02:54.706Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.236Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt828d5ebb9468b886","ACL":{},"alt_text_l10n":"Amazon Web Services (AWS)","created_at":"2022-09-26T22:02:47.627Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Amazon Web Services (AWS)","updated_at":"2022-09-26T22:02:47.627Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.225Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt09fba657c7a83bc5","ACL":{},"alt_text_l10n":"Microsoft Azure","created_at":"2022-09-26T22:02:15.107Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Microsoft Azure","updated_at":"2022-09-26T22:02:15.107Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-26T22:03:30.214Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4c95fef51f752b47","ACL":{},"alt_text_l10n":"Elastic Enterprise Search","created_at":"2022-07-14T22:29:34.849Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Elastic Enterprise Search","updated_at":"2022-07-14T22:29:34.849Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-07-14T22:29:39.368Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta2ea276c30401c0c","ACL":{},"alt_text_l10n":"Kibana","created_at":"2022-07-14T22:26:18.479Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Kibana","updated_at":"2022-07-14T22:26:18.479Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-07-14T22:26:22.908Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2ecbc48c40dda5d6","ACL":{},"alt_text_l10n":"Application Performance Monitoring (APM)","created_at":"2022-07-13T19:59:06.363Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Application Performance Monitoring (APM)","updated_at":"2022-07-13T19:59:06.363Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-07-13T19:59:17.766Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt12a7b7945c143771","ACL":{},"alt_text_l10n":"Tom Kaplan","created_at":"2022-06-30T22:50:23.776Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Tom Kaplan","updated_at":"2022-06-30T22:50:23.776Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-30T22:50:26.858Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6e3875f2cb65b010","ACL":{},"alt_text_l10n":"Elastic Observability","created_at":"2022-06-23T22:18:01.526Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Elastic Observability","updated_at":"2022-06-23T22:18:01.526Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T22:18:06.080Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt806c6156aefec893","ACL":{},"alt_text_l10n":"Elastic Cloud","created_at":"2022-06-23T22:17:46.694Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Elastic Cloud","updated_at":"2022-06-23T22:17:46.694Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T22:17:51.494Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltea2a3342595c2256","ACL":{},"alt_text_l10n":"Flavio Knob","created_at":"2022-06-23T22:00:36.284Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Flavio Knob","updated_at":"2022-06-23T22:00:36.284Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T22:00:43.176Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdec86286dc507b12","ACL":{},"alt_text_l10n":"Shay Banon","created_at":"2022-06-23T21:58:54.908Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Shay Banon","updated_at":"2022-06-23T21:58:54.908Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-23T21:59:02.660Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt802af40f16c86cee","ACL":{},"alt_text_l10n":"Zurich Insurance Group","created_at":"2022-05-12T21:58:07.477Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zurich Insurance Group","updated_at":"2022-05-12T21:58:07.477Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.478Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt402e8602dc31c98d","ACL":{},"alt_text_l10n":"Zero Latency","created_at":"2022-05-12T21:58:07.296Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zero Latency","updated_at":"2022-05-12T21:58:07.296Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.056Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6eef21f967aadca5","ACL":{},"alt_text_l10n":"Zendesk","created_at":"2022-05-12T21:58:07.117Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zendesk","updated_at":"2022-05-12T21:58:07.117Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.262Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta9e0832242418c91","ACL":{},"alt_text_l10n":"Zalando","created_at":"2022-05-12T21:58:06.905Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Zalando","updated_at":"2022-05-12T21:58:06.905Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.728Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt92ffc7d5a0af27ba","ACL":{},"alt_text_l10n":"Yokogawa","created_at":"2022-05-12T21:58:06.721Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yokogawa","updated_at":"2022-05-12T21:58:06.721Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.114Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt50dee827c9ddca6c","ACL":{},"alt_text_l10n":"Yodle","created_at":"2022-05-12T21:58:06.549Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yodle","updated_at":"2022-05-12T21:58:06.549Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.200Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdc0636418b1728e2","ACL":{},"alt_text_l10n":"Yatego","created_at":"2022-05-12T21:58:06.337Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yatego","updated_at":"2022-05-12T21:58:06.337Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.068Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5141742ca3495e1c","ACL":{},"alt_text_l10n":"Yale University","created_at":"2022-05-12T21:58:06.152Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Yale University","updated_at":"2022-05-12T21:58:06.152Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.210Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt323409da7387c039","ACL":{},"alt_text_l10n":"XPO Logistics","created_at":"2022-05-12T21:58:05.961Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: XPO Logistics","updated_at":"2022-05-12T21:58:05.961Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.608Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbe0e7fa7c33dd6b0","ACL":{},"alt_text_l10n":"Xoom","created_at":"2022-05-12T21:58:05.779Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Xoom","updated_at":"2022-05-12T21:58:05.779Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.642Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6cc45a194dc90b06","ACL":{},"alt_text_l10n":"Xing","created_at":"2022-05-12T21:58:05.594Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Xing","updated_at":"2022-05-12T21:58:05.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.243Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt069c2ae8a045d1d9","ACL":{},"alt_text_l10n":"WuerthPhoenix","created_at":"2022-05-12T21:58:05.416Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: WuerthPhoenix","updated_at":"2022-05-12T21:58:05.416Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.050Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7df5c993ca47e99f","ACL":{},"alt_text_l10n":"Workday","created_at":"2022-05-12T21:58:05.218Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Workday","updated_at":"2022-05-12T21:58:05.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.441Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt36b939810c148804","ACL":{},"alt_text_l10n":"Wirecard","created_at":"2022-05-12T21:58:05.048Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wirecard","updated_at":"2022-05-12T21:58:05.048Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.672Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt84bce2c969eb32c8","ACL":{},"alt_text_l10n":"Will County Sheriff's Office","created_at":"2022-05-12T21:58:04.866Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Will County Sheriff's Office","updated_at":"2022-05-12T21:58:04.866Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.939Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt203415bcc35d284f","ACL":{},"alt_text_l10n":"Wikimedia","created_at":"2022-05-12T21:58:04.681Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wikimedia","updated_at":"2022-05-12T21:58:04.681Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.381Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf37fef07b73c3850","ACL":{},"alt_text_l10n":"Wemakeprice","created_at":"2022-05-12T21:58:04.491Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wemakeprice","updated_at":"2022-05-12T21:58:04.491Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.092Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb548a39f7e8d1177","ACL":{},"alt_text_l10n":"Wellcome Collection","created_at":"2022-05-12T21:58:04.307Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Wellcome Collection","updated_at":"2022-05-12T21:58:04.307Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.570Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt73707e9fbe08c997","ACL":{},"alt_text_l10n":"Weimob","created_at":"2022-05-12T21:58:04.132Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Weimob","updated_at":"2022-05-12T21:58:04.132Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.341Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3289a157b9290c23","ACL":{},"alt_text_l10n":"Warner Brothers","created_at":"2022-05-12T21:58:03.957Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Warner Brothers","updated_at":"2022-05-12T21:58:03.957Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.617Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt25be0810c6784170","ACL":{},"alt_text_l10n":"Walgreens","created_at":"2022-05-12T21:58:03.791Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Walgreens","updated_at":"2022-05-12T21:58:03.791Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.454Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt821f24cb81673931","ACL":{},"alt_text_l10n":"Voxpopme","created_at":"2022-05-12T21:58:03.612Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Voxpopme","updated_at":"2022-05-12T21:58:03.612Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf8e3add699994943","ACL":{},"alt_text_l10n":"Volvo","created_at":"2022-05-12T21:58:03.433Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Volvo","updated_at":"2022-05-12T21:58:03.433Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.838Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8b25ae0c5b27150d","ACL":{},"alt_text_l10n":"VITAS","created_at":"2022-05-12T21:58:03.246Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: VITAS","updated_at":"2022-05-12T21:58:03.246Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.015Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt041a600f9a4123bd","ACL":{},"alt_text_l10n":"Vimeo","created_at":"2022-05-12T21:58:03.079Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Vimeo","updated_at":"2022-05-12T21:58:03.079Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.008Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcfd649f747a6e232","ACL":{},"alt_text_l10n":"Verizon Business","created_at":"2022-05-12T21:58:02.898Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Verizon Business","updated_at":"2022-05-12T21:58:02.898Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.979Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14e12ede074158c9","ACL":{},"alt_text_l10n":"VELTRA","created_at":"2022-05-12T21:58:02.710Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: VELTRA","updated_at":"2022-05-12T21:58:02.710Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.192Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7ea26ad5fc793765","ACL":{},"alt_text_l10n":"Vandis","created_at":"2022-05-12T21:58:02.535Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Vandis","updated_at":"2022-05-12T21:58:02.535Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.465Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2203ed64e9786c6c","ACL":{},"alt_text_l10n":"USGS","created_at":"2022-05-12T21:58:02.367Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: USGS","updated_at":"2022-05-12T21:58:02.367Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.426Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltccc935fe8a1f29ba","ACL":{},"alt_text_l10n":"USAA","created_at":"2022-05-12T21:58:02.019Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: USAA","updated_at":"2022-05-12T21:58:02.019Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.959Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5de4351d329c977","ACL":{},"alt_text_l10n":"U.S. Census Bureau","created_at":"2022-05-12T21:58:01.828Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: U.S. Census Bureau","updated_at":"2022-05-12T21:58:01.828Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.700Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt70b7be1d1e8ccb44","ACL":{},"alt_text_l10n":"University of Washington","created_at":"2022-05-12T21:58:01.647Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: University of Washington","updated_at":"2022-05-12T21:58:01.647Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.303Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2010c4f7bec1f9ad","ACL":{},"alt_text_l10n":"University of Oxford","created_at":"2022-05-12T21:58:01.474Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: University of Oxford","updated_at":"2022-05-12T21:58:01.474Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.364Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9bdf058039e5089b","ACL":{},"alt_text_l10n":"UCLA","created_at":"2022-05-12T21:58:01.296Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: UCLA","updated_at":"2022-05-12T21:58:01.296Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.607Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt46f1e819a511f5d1","ACL":{},"alt_text_l10n":"Uber","created_at":"2022-05-12T21:58:01.109Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Uber","updated_at":"2022-05-12T21:58:01.109Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.137Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04691d5f3c58841e","ACL":{},"alt_text_l10n":"Twilio","created_at":"2022-05-12T21:58:00.926Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Twilio","updated_at":"2022-05-12T21:58:00.926Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.018Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blted80a9d45fb0acfd","ACL":{},"alt_text_l10n":"TV2","created_at":"2022-05-12T21:58:00.757Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: TV2","updated_at":"2022-05-12T21:58:00.757Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.032Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8c9425f16c9672","ACL":{},"alt_text_l10n":"Travelport","created_at":"2022-05-12T21:58:00.576Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Travelport","updated_at":"2022-05-12T21:58:00.576Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.627Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt003b6fde98d77510","ACL":{},"alt_text_l10n":"Transit Wireless","created_at":"2022-05-12T21:58:00.405Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Transit Wireless","updated_at":"2022-05-12T21:58:00.405Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:52.981Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2f85af70aca589e9","ACL":{},"alt_text_l10n":"Tinder","created_at":"2022-05-12T21:58:00.229Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tinder","updated_at":"2022-05-12T21:58:00.229Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.580Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt75dd759b88e10d4f","ACL":{},"alt_text_l10n":"Ticketmaster","created_at":"2022-05-12T21:58:00.042Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ticketmaster","updated_at":"2022-05-12T21:58:00.042Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.378Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta48036c82747cd11","ACL":{},"alt_text_l10n":"Thought Machine","created_at":"2022-05-12T21:57:59.850Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Thought Machine","updated_at":"2022-05-12T21:57:59.850Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.667Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaf0d546ca9881f6b","ACL":{},"alt_text_l10n":"Thomson Reuters","created_at":"2022-05-12T21:57:59.666Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Thomson Reuters","updated_at":"2022-05-12T21:57:59.666Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.754Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2f7c0e2579506913","ACL":{},"alt_text_l10n":"TheLadders","created_at":"2022-05-12T21:57:59.482Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: TheLadders","updated_at":"2022-05-12T21:57:59.482Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.571Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9144d7bae77f3980","ACL":{},"alt_text_l10n":"The Warehouse Group","created_at":"2022-05-12T21:57:59.291Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The Warehouse Group","updated_at":"2022-05-12T21:57:59.291Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.107Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf24dd4413895a40b","ACL":{},"alt_text_l10n":"The New York TImes","created_at":"2022-05-12T21:57:59.107Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The New York TImes","updated_at":"2022-05-12T21:57:59.107Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.076Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8429054e58ba5b24","ACL":{},"alt_text_l10n":"The Home Depot","created_at":"2022-05-12T21:57:58.927Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The Home Depot","updated_at":"2022-05-12T21:57:58.927Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.524Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4d9b0dc0b5f353fe","ACL":{},"alt_text_l10n":"The Guardian","created_at":"2022-05-12T21:57:58.746Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: The Guardian","updated_at":"2022-05-12T21:57:58.746Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.181Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt834b83b884bd1cc3","ACL":{},"alt_text_l10n":"Texas A\u0026M - College of Engineering","created_at":"2022-05-12T21:57:58.568Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Texas A\u0026M - College of Engineering","updated_at":"2022-05-12T21:57:58.568Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.517Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8894252579fd84","ACL":{},"alt_text_l10n":"Terradue","created_at":"2022-05-12T21:57:58.388Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Terradue","updated_at":"2022-05-12T21:57:58.388Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.620Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d90e6427c85ef91","ACL":{},"alt_text_l10n":"Tencent Cloud Meeting","created_at":"2022-05-12T21:57:58.202Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tencent Cloud Meeting","updated_at":"2022-05-12T21:57:58.202Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.065Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaeee5f2a21417391","ACL":{},"alt_text_l10n":"Telefónica","created_at":"2022-05-12T21:57:58.017Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Telefónica","updated_at":"2022-05-12T21:57:58.017Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.747Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt25c843667d1ed774","ACL":{},"alt_text_l10n":"TechCrunch","created_at":"2022-05-12T21:57:57.825Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: TechCrunch","updated_at":"2022-05-12T21:57:57.825Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.463Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9b529fc1222a4f36","ACL":{},"alt_text_l10n":"Tanium","created_at":"2022-05-12T21:57:57.658Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tanium","updated_at":"2022-05-12T21:57:57.658Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.594Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6305a55e7e7805bd","ACL":{},"alt_text_l10n":"Tango","created_at":"2022-05-12T21:57:57.474Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Tango","updated_at":"2022-05-12T21:57:57.474Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.552Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt825c87c4454c6156","ACL":{},"alt_text_l10n":"T-Mobile","created_at":"2022-05-12T21:57:57.290Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: T-Mobile","updated_at":"2022-05-12T21:57:57.290Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.504Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltca9187c8910c9b75","ACL":{},"alt_text_l10n":"Symantec","created_at":"2022-05-12T21:57:57.109Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Symantec","updated_at":"2022-05-12T21:57:57.109Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.933Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1328cc5ce7eb909b","ACL":{},"alt_text_l10n":"Swiss Life","created_at":"2022-05-12T21:57:56.925Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Swiss Life","updated_at":"2022-05-12T21:57:56.925Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.137Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2a813038618cda91","ACL":{},"alt_text_l10n":"SWIFT","created_at":"2022-05-12T21:57:56.742Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SWIFT","updated_at":"2022-05-12T21:57:56.742Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.459Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1d7a2be5c14c39d2","ACL":{},"alt_text_l10n":"SurveyMonkey","created_at":"2022-05-12T21:57:56.566Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SurveyMonkey","updated_at":"2022-05-12T21:57:56.566Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.324Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdc3097f3b5d94d31","ACL":{},"alt_text_l10n":"Sunhotels","created_at":"2022-05-12T21:57:56.390Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sunhotels","updated_at":"2022-05-12T21:57:56.390Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.857Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltead29dd9cb2c5198","ACL":{},"alt_text_l10n":"Stormfish","created_at":"2022-05-12T21:57:56.200Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Stormfish","updated_at":"2022-05-12T21:57:56.200Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.005Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt80fa85da43cd7f60","ACL":{},"alt_text_l10n":"St. Mary's University","created_at":"2022-05-12T21:57:56.027Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: St. Mary's University","updated_at":"2022-05-12T21:57:56.027Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.485Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt847355fe381f7d05","ACL":{},"alt_text_l10n":"Sprint","created_at":"2022-05-12T21:57:55.841Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sprint","updated_at":"2022-05-12T21:57:55.841Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.530Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd67becbdb7ec9752","ACL":{},"alt_text_l10n":"Spring","created_at":"2022-05-12T21:57:55.663Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Spring","updated_at":"2022-05-12T21:57:55.663Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.012Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte6bcf470301e8002","ACL":{},"alt_text_l10n":"Sovren","created_at":"2022-05-12T21:57:55.478Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sovren","updated_at":"2022-05-12T21:57:55.478Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.960Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5ecfdd579f982fb0","ACL":{},"alt_text_l10n":"Southern Glazer's Wine \u0026 Spirits","created_at":"2022-05-12T21:57:55.292Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Southern Glazer's Wine \u0026 Spirits","updated_at":"2022-05-12T21:57:55.292Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.474Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b10befcb9bdb126","ACL":{},"alt_text_l10n":"SoundCloud","created_at":"2022-05-12T21:57:55.107Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SoundCloud","updated_at":"2022-05-12T21:57:55.107Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8baf1d9627f2de05","ACL":{},"alt_text_l10n":"Softbank Payment Service","created_at":"2022-05-12T21:57:54.920Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Softbank Payment Service","updated_at":"2022-05-12T21:57:54.920Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.037Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7cdcf30b6d665e85","ACL":{},"alt_text_l10n":"Softbank Corp.","created_at":"2022-05-12T21:57:54.730Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Softbank Corp.","updated_at":"2022-05-12T21:57:54.730Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.429Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt25e04f53c93351fb","ACL":{},"alt_text_l10n":"Snaptrip","created_at":"2022-05-12T21:57:54.537Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Snaptrip","updated_at":"2022-05-12T21:57:54.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.474Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4da985a0ca92072e","ACL":{},"alt_text_l10n":"SMD-AM","created_at":"2022-05-12T21:57:54.359Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SMD-AM","updated_at":"2022-05-12T21:57:54.359Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.191Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3cbfcef99ac81d47","ACL":{},"alt_text_l10n":"Smarter City Solutions","created_at":"2022-05-12T21:57:54.179Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Smarter City Solutions","updated_at":"2022-05-12T21:57:54.179Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt330fa677d395c5ea","ACL":{},"alt_text_l10n":"Slack","created_at":"2022-05-12T21:57:54.008Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Slack","updated_at":"2022-05-12T21:57:54.008Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.627Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt85b53964d1493804","ACL":{},"alt_text_l10n":"Sky","created_at":"2022-05-12T21:57:53.820Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sky","updated_at":"2022-05-12T21:57:53.820Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.968Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt792089b53ea0fda5","ACL":{},"alt_text_l10n":"Sitecore","created_at":"2022-05-12T21:57:53.650Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Sitecore","updated_at":"2022-05-12T21:57:53.650Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.408Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta1154eb7fbf7a01e","ACL":{},"alt_text_l10n":"Shopify","created_at":"2022-05-12T21:57:53.473Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Shopify","updated_at":"2022-05-12T21:57:53.473Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6b707f858a7d0f22","ACL":{},"alt_text_l10n":"Shopback","created_at":"2022-05-12T21:57:53.294Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Shopback","updated_at":"2022-05-12T21:57:53.294Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.236Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9069c20f7952e8e0","ACL":{},"alt_text_l10n":"SEEK","created_at":"2022-05-12T21:57:53.122Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SEEK","updated_at":"2022-05-12T21:57:53.122Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.092Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0a642541e26e5754","ACL":{},"alt_text_l10n":"Science Warehouse","created_at":"2022-05-12T21:57:52.945Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Science Warehouse","updated_at":"2022-05-12T21:57:52.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.078Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta8f6f46f2f41f207","ACL":{},"alt_text_l10n":"SAP Concur","created_at":"2022-05-12T21:57:52.769Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: SAP Concur","updated_at":"2022-05-12T21:57:52.769Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.721Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt611c1ca06db3dc55","ACL":{},"alt_text_l10n":"Salesforce","created_at":"2022-05-12T21:57:52.588Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Salesforce","updated_at":"2022-05-12T21:57:52.588Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.515Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd8146b2d7dae5e77","ACL":{},"alt_text_l10n":"Safehouse","created_at":"2022-05-12T21:57:52.412Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Safehouse","updated_at":"2022-05-12T21:57:52.412Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.047Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte7dc3c618676f8ff","ACL":{},"alt_text_l10n":"RSN","created_at":"2022-05-12T21:57:52.073Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: RSN","updated_at":"2022-05-12T21:57:52.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.970Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt862651b8bcbe5d28","ACL":{},"alt_text_l10n":"Royal Bank of Canada","created_at":"2022-05-12T21:57:51.901Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Royal Bank of Canada","updated_at":"2022-05-12T21:57:51.901Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.981Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt580fc883510ef9b8","ACL":{},"alt_text_l10n":"RockNSM","created_at":"2022-05-12T21:57:51.733Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: RockNSM","updated_at":"2022-05-12T21:57:51.733Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.421Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaf0f913e34900622","ACL":{},"alt_text_l10n":"Roanoke College","created_at":"2022-05-12T21:57:51.568Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Roanoke College","updated_at":"2022-05-12T21:57:51.568Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.517Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2bb106357877cd1f","ACL":{},"alt_text_l10n":"Rightmove","created_at":"2022-05-12T21:57:51.384Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Rightmove","updated_at":"2022-05-12T21:57:51.384Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.479Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcb4b07e8c157bb46","ACL":{},"alt_text_l10n":"Renault","created_at":"2022-05-12T21:57:51.202Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Renault","updated_at":"2022-05-12T21:57:51.202Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.945Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt57db4d6f8b0bd4d2","ACL":{},"alt_text_l10n":"RedOwl Analytics","created_at":"2022-05-12T21:57:51.024Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: RedOwl Analytics","updated_at":"2022-05-12T21:57:51.024Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.412Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt22a59d21263ab48e","ACL":{},"alt_text_l10n":"Recruit","created_at":"2022-05-12T21:57:50.840Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Recruit","updated_at":"2022-05-12T21:57:50.840Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.434Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb67d20daef2bd6cf","ACL":{},"alt_text_l10n":"Rabobank","created_at":"2022-05-12T21:57:50.658Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Rabobank","updated_at":"2022-05-12T21:57:50.658Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.576Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3ce9488bcc7d69d8","ACL":{},"alt_text_l10n":"Quorum","created_at":"2022-05-12T21:57:50.475Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Quorum","updated_at":"2022-05-12T21:57:50.475Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.030Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt201cf8fc99ccc108","ACL":{},"alt_text_l10n":"Quizlet","created_at":"2022-05-12T21:57:50.292Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Quizlet","updated_at":"2022-05-12T21:57:50.292Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.372Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt05c374fa27ed03f2","ACL":{},"alt_text_l10n":"QTnet","created_at":"2022-05-12T21:57:50.108Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: QTnet","updated_at":"2022-05-12T21:57:50.108Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.041Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfcf7f1893b604a3c","ACL":{},"alt_text_l10n":"PSCU","created_at":"2022-05-12T21:57:49.943Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: PSCU","updated_at":"2022-05-12T21:57:49.943Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.855Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf81259efba44d4e3","ACL":{},"alt_text_l10n":"PSA","created_at":"2022-05-12T21:57:49.773Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: PSA","updated_at":"2022-05-12T21:57:49.773Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.819Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdcecac78674dc8ab","ACL":{},"alt_text_l10n":"Procter \u0026 Gamble","created_at":"2022-05-12T21:57:49.600Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Procter \u0026 Gamble","updated_at":"2022-05-12T21:57:49.600Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.869Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc9770a10c8eb80d3","ACL":{},"alt_text_l10n":"Postbank Systems","created_at":"2022-05-12T21:57:49.423Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Postbank Systems","updated_at":"2022-05-12T21:57:49.423Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.919Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6ee38ddf72b99fd5","ACL":{},"alt_text_l10n":"POSCO","created_at":"2022-05-12T21:57:49.242Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: POSCO","updated_at":"2022-05-12T21:57:49.242Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.256Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc07f288d971d6a3","ACL":{},"alt_text_l10n":"Polyconseil","created_at":"2022-05-12T21:57:49.065Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Polyconseil","updated_at":"2022-05-12T21:57:49.065Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.607Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaca3afd83df0dfc0","ACL":{},"alt_text_l10n":"Pfizer","created_at":"2022-05-12T21:57:48.882Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Pfizer","updated_at":"2022-05-12T21:57:48.882Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.741Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8e6bf57acd69142a","ACL":{},"alt_text_l10n":"Perched","created_at":"2022-05-12T21:57:48.711Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Perched","updated_at":"2022-05-12T21:57:48.711Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.078Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7ea0a788aea89f4f","ACL":{},"alt_text_l10n":"Perceivant","created_at":"2022-05-12T21:57:48.545Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Perceivant","updated_at":"2022-05-12T21:57:48.545Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.458Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b3b7f5e67bc9c5c","ACL":{},"alt_text_l10n":"Penske Media","created_at":"2022-05-12T21:57:48.373Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Penske Media","updated_at":"2022-05-12T21:57:48.373Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.254Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt64ce098751f354e3","ACL":{},"alt_text_l10n":"PedidosYa","created_at":"2022-05-12T21:57:48.192Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: PedidosYa","updated_at":"2022-05-12T21:57:48.192Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.584Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0ae045b430090a68","ACL":{},"alt_text_l10n":"Paylocity","created_at":"2022-05-12T21:57:48.010Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Paylocity","updated_at":"2022-05-12T21:57:48.010Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.095Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt072fb0b05b3f5c88","ACL":{},"alt_text_l10n":"Oui.SNCF","created_at":"2022-05-12T21:57:47.822Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Oui.SNCF","updated_at":"2022-05-12T21:57:47.822Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.060Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt908e97f524a30cdf","ACL":{},"alt_text_l10n":"OTTO Motors","created_at":"2022-05-12T21:57:47.645Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: OTTO Motors","updated_at":"2022-05-12T21:57:47.645Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.100Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e8fb5f9325f7d39","ACL":{},"alt_text_l10n":"OTTO","created_at":"2022-05-12T21:57:47.458Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: OTTO","updated_at":"2022-05-12T21:57:47.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.452Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7028ca66c7171d26","ACL":{},"alt_text_l10n":"Orange","created_at":"2022-05-12T21:57:47.274Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Orange","updated_at":"2022-05-12T21:57:47.274Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.286Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt943a44fd55656c43","ACL":{},"alt_text_l10n":"Optum","created_at":"2022-05-12T21:57:47.092Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Optum","updated_at":"2022-05-12T21:57:47.092Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.559Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt70df0dd6d4bd5b34","ACL":{},"alt_text_l10n":"Opsys","created_at":"2022-05-12T21:57:46.909Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Opsys","updated_at":"2022-05-12T21:57:46.909Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.311Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta63a0bcbab92e09e","ACL":{},"alt_text_l10n":"OLX","created_at":"2022-05-12T21:57:46.721Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: OLX","updated_at":"2022-05-12T21:57:46.721Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.702Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3ff81397984cb94d","ACL":{},"alt_text_l10n":"Oak Ridge National Laboratory","created_at":"2022-05-12T21:57:46.532Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Oak Ridge National Laboratory","updated_at":"2022-05-12T21:57:46.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.048Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4664222954f06060","ACL":{},"alt_text_l10n":"NYU Libraries","created_at":"2022-05-12T21:57:46.338Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NYU Libraries","updated_at":"2022-05-12T21:57:46.338Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.110Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0bcaaf2444d7c3f8","ACL":{},"alt_text_l10n":"Nvidia","created_at":"2022-05-12T21:57:46.164Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nvidia","updated_at":"2022-05-12T21:57:46.164Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaf36c3eb65d37ab5","ACL":{},"alt_text_l10n":"NSHC","created_at":"2022-05-12T21:57:45.981Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NSHC","updated_at":"2022-05-12T21:57:45.981Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.530Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltab39a95c4172e622","ACL":{},"alt_text_l10n":"NS1","created_at":"2022-05-12T21:57:45.794Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NS1","updated_at":"2022-05-12T21:57:45.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.735Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8c31a221acd52c5a","ACL":{},"alt_text_l10n":"NS Solutions Corporation","created_at":"2022-05-12T21:57:45.608Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NS Solutions Corporation","updated_at":"2022-05-12T21:57:45.608Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.056Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6709b8541d0815c5","ACL":{},"alt_text_l10n":"Nikkei","created_at":"2022-05-12T21:57:45.419Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nikkei","updated_at":"2022-05-12T21:57:45.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.621Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6f4074f98dbae885","ACL":{},"alt_text_l10n":"Night Shift Development","created_at":"2022-05-12T21:57:45.243Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Night Shift Development","updated_at":"2022-05-12T21:57:45.243Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.268Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9dcff8c1b1377e8f","ACL":{},"alt_text_l10n":"Networked Insights","created_at":"2022-05-12T21:57:45.065Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Networked Insights","updated_at":"2022-05-12T21:57:45.065Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.614Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6bf7aa642cb8e9a","ACL":{},"alt_text_l10n":"Netshoes","created_at":"2022-05-12T21:57:44.892Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Netshoes","updated_at":"2022-05-12T21:57:44.892Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.584Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd76633804a42c942","ACL":{},"alt_text_l10n":"Netflix","created_at":"2022-05-12T21:57:44.711Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Netflix","updated_at":"2022-05-12T21:57:44.711Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.027Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltca8f8783e97bea1f","ACL":{},"alt_text_l10n":"NetApp","created_at":"2022-05-12T21:57:44.532Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NetApp","updated_at":"2022-05-12T21:57:44.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.925Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt17fc47c5abbe4c1c","ACL":{},"alt_text_l10n":"NEHGS","created_at":"2022-05-12T21:57:44.350Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NEHGS","updated_at":"2022-05-12T21:57:44.350Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.230Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3e54ba54127d24bd","ACL":{},"alt_text_l10n":"NCIS Cyber Directorate","created_at":"2022-05-12T21:57:44.164Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NCIS Cyber Directorate","updated_at":"2022-05-12T21:57:44.164Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4bbc68ebaf30099a","ACL":{},"alt_text_l10n":"Naver","created_at":"2022-05-12T21:57:43.999Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Naver","updated_at":"2022-05-12T21:57:43.999Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.163Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf7afe5d3cdaa6862","ACL":{},"alt_text_l10n":"Nature Conservancy","created_at":"2022-05-12T21:57:43.807Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nature Conservancy","updated_at":"2022-05-12T21:57:43.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.811Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8e437a5b95b79df9","ACL":{},"alt_text_l10n":"Nativo","created_at":"2022-05-12T21:57:43.619Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Nativo","updated_at":"2022-05-12T21:57:43.619Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.072Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc40c312e4aca253b","ACL":{},"alt_text_l10n":"NASA JPL","created_at":"2022-05-12T21:57:43.435Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: NASA JPL","updated_at":"2022-05-12T21:57:43.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.685Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt358748740d7f2c04","ACL":{},"alt_text_l10n":"Mozilla","created_at":"2022-05-12T21:57:43.253Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mozilla","updated_at":"2022-05-12T21:57:43.253Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.636Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt31e1ed6c97e40da4","ACL":{},"alt_text_l10n":"MM Karton","created_at":"2022-05-12T21:57:43.063Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MM Karton","updated_at":"2022-05-12T21:57:43.063Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.598Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt73e9101810d88831","ACL":{},"alt_text_l10n":"Mindcurv","created_at":"2022-05-12T21:57:42.880Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mindcurv","updated_at":"2022-05-12T21:57:42.880Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.352Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltede68c6a1588ba41","ACL":{},"alt_text_l10n":"Miles \u0026 More","created_at":"2022-05-12T21:57:42.695Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Miles \u0026 More","updated_at":"2022-05-12T21:57:42.695Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.041Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9e2ce1c18cb74ecd","ACL":{},"alt_text_l10n":"Microsoft","created_at":"2022-05-12T21:57:42.521Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Microsoft","updated_at":"2022-05-12T21:57:42.521Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.627Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte084cb4a80073efd","ACL":{},"alt_text_l10n":"MetaWater","created_at":"2022-05-12T21:57:42.337Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MetaWater","updated_at":"2022-05-12T21:57:42.337Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.910Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdbde9d57a2f32119","ACL":{},"alt_text_l10n":"Merck","created_at":"2022-05-12T21:57:42.144Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Merck","updated_at":"2022-05-12T21:57:42.144Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.061Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt817ff69c8eabf6bd","ACL":{},"alt_text_l10n":"MercadoLibre","created_at":"2022-05-12T21:57:41.964Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MercadoLibre","updated_at":"2022-05-12T21:57:41.964Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.491Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0836ceb141cc4194","ACL":{},"alt_text_l10n":"Megazone","created_at":"2022-05-12T21:57:41.767Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Megazone","updated_at":"2022-05-12T21:57:41.767Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.069Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0d829f7f8e82e424","ACL":{},"alt_text_l10n":"McQueen Solutions","created_at":"2022-05-12T21:57:41.596Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: McQueen Solutions","updated_at":"2022-05-12T21:57:41.596Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.120Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt20421599022f8375","ACL":{},"alt_text_l10n":"Mayo Clinic","created_at":"2022-05-12T21:57:41.418Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mayo Clinic","updated_at":"2022-05-12T21:57:41.418Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.392Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt43dd0149d9e9e8cd","ACL":{},"alt_text_l10n":"Maryland Innovation and Security Institute","created_at":"2022-05-12T21:57:41.233Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Maryland Innovation and Security Institute","updated_at":"2022-05-12T21:57:41.233Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.091Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcf91fc612ef4515c","ACL":{},"alt_text_l10n":"Martin's Point Health Care","created_at":"2022-05-12T21:57:41.056Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Martin's Point Health Care","updated_at":"2022-05-12T21:57:41.056Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.973Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte42b299c5ef7c0d4","ACL":{},"alt_text_l10n":"MAPP","created_at":"2022-05-12T21:57:40.871Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: MAPP","updated_at":"2022-05-12T21:57:40.871Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.928Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf745937643d7f8b","ACL":{},"alt_text_l10n":"Mapbox","created_at":"2022-05-12T21:57:40.684Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Mapbox","updated_at":"2022-05-12T21:57:40.684Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.901Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltddc2f5ef86908dde","ACL":{},"alt_text_l10n":"Machine Zone","created_at":"2022-05-12T21:57:40.506Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Machine Zone","updated_at":"2022-05-12T21:57:40.506Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.879Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt937b6ee4d5531347","ACL":{},"alt_text_l10n":"Lyft","created_at":"2022-05-12T21:57:40.156Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Lyft","updated_at":"2022-05-12T21:57:40.156Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.140Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14588035404bcd09","ACL":{},"alt_text_l10n":"LiveChat","created_at":"2022-05-12T21:57:39.966Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: LiveChat","updated_at":"2022-05-12T21:57:39.966Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt70261775a4428c78","ACL":{},"alt_text_l10n":"Linklaters","created_at":"2022-05-12T21:57:39.778Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Linklaters","updated_at":"2022-05-12T21:57:39.778Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.280Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14331a9b21f8fa8b","ACL":{},"alt_text_l10n":"LINE","created_at":"2022-05-12T21:57:39.604Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: LINE","updated_at":"2022-05-12T21:57:39.604Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.165Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt619a625bd0ac77cf","ACL":{},"alt_text_l10n":"Lexer","created_at":"2022-05-12T21:57:39.426Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Lexer","updated_at":"2022-05-12T21:57:39.426Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.534Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt71b9283f80a8a0d4","ACL":{},"alt_text_l10n":"Lenovo","created_at":"2022-05-12T21:57:39.244Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Lenovo","updated_at":"2022-05-12T21:57:39.244Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.323Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc05b1bec86155ae5","ACL":{},"alt_text_l10n":"Kyruus","created_at":"2022-05-12T21:57:39.061Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kyruus","updated_at":"2022-05-12T21:57:39.061Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.657Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt13159e22be69f396","ACL":{},"alt_text_l10n":"Kroger","created_at":"2022-05-12T21:57:38.891Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kroger","updated_at":"2022-05-12T21:57:38.891Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.128Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f8585834b922051","ACL":{},"alt_text_l10n":"KPN","created_at":"2022-05-12T21:57:38.702Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: KPN","updated_at":"2022-05-12T21:57:38.702Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.497Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dc9b2d8d5ad4db7","ACL":{},"alt_text_l10n":"KeyBank","created_at":"2022-05-12T21:57:38.523Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: KeyBank","updated_at":"2022-05-12T21:57:38.523Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.538Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8280878e34b0ff93","ACL":{},"alt_text_l10n":"Kaidee","created_at":"2022-05-12T21:57:38.352Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kaidee","updated_at":"2022-05-12T21:57:38.352Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.511Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1391191d97d992d9","ACL":{},"alt_text_l10n":"Kadokawa CONNECTED","created_at":"2022-05-12T21:57:38.177Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Kadokawa CONNECTED","updated_at":"2022-05-12T21:57:38.177Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.146Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9fd830e07c9cc6fb","ACL":{},"alt_text_l10n":"Just Eat","created_at":"2022-05-12T21:57:37.992Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Just Eat","updated_at":"2022-05-12T21:57:37.992Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.637Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb8a4fdac0ae40a61","ACL":{},"alt_text_l10n":"JPL","created_at":"2022-05-12T21:57:37.813Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: JPL","updated_at":"2022-05-12T21:57:37.813Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.600Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb0964f9f16c25eb5","ACL":{},"alt_text_l10n":"John Deere","created_at":"2022-05-12T21:57:37.639Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: John Deere","updated_at":"2022-05-12T21:57:37.639Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.550Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6f6f3d4eb227c066","ACL":{},"alt_text_l10n":"Jobrapido","created_at":"2022-05-12T21:57:37.456Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Jobrapido","updated_at":"2022-05-12T21:57:37.456Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.275Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte60c478b182f1e28","ACL":{},"alt_text_l10n":"Jaguar","created_at":"2022-05-12T21:57:37.279Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Jaguar","updated_at":"2022-05-12T21:57:37.279Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.951Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd2ef43ebefe90c5e","ACL":{},"alt_text_l10n":"ITV","created_at":"2022-05-12T21:57:37.101Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ITV","updated_at":"2022-05-12T21:57:37.101Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.005Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c7be770d8ac5cdd","ACL":{},"alt_text_l10n":"International University","created_at":"2022-05-12T21:57:36.929Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: International University","updated_at":"2022-05-12T21:57:36.929Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.510Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt236abef8892fda2c","ACL":{},"alt_text_l10n":"Intercontinental Hotel Group","created_at":"2022-05-12T21:57:36.751Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Intercontinental Hotel Group","updated_at":"2022-05-12T21:57:36.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.445Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1f4671bf6cb5fe6f","ACL":{},"alt_text_l10n":"Instructables","created_at":"2022-05-12T21:57:36.568Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Instructables","updated_at":"2022-05-12T21:57:36.568Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.335Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7eed649ba201444d","ACL":{},"alt_text_l10n":"Ingram Micro","created_at":"2022-05-12T21:57:36.394Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ingram Micro","updated_at":"2022-05-12T21:57:36.394Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.471Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2a69653c47f14806","ACL":{},"alt_text_l10n":"ING Spain","created_at":"2022-05-12T21:57:36.205Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ING Spain","updated_at":"2022-05-12T21:57:36.205Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.447Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt735dbf124107fc63","ACL":{},"alt_text_l10n":"InfoTrack","created_at":"2022-05-12T21:57:36.021Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: InfoTrack","updated_at":"2022-05-12T21:57:36.021Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.329Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc03d0bc199e594fc","ACL":{},"alt_text_l10n":"Influence Health","created_at":"2022-05-12T21:57:35.839Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Influence Health","updated_at":"2022-05-12T21:57:35.839Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.650Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt42dbb5d3325bf8e6","ACL":{},"alt_text_l10n":"IEEE Globalspec","created_at":"2022-05-12T21:57:35.664Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: IEEE Globalspec","updated_at":"2022-05-12T21:57:35.664Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.065Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5fe54212c803d01b","ACL":{},"alt_text_l10n":"IBM","created_at":"2022-05-12T21:57:35.485Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: IBM","updated_at":"2022-05-12T21:57:35.485Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.506Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt004e9806914497f1","ACL":{},"alt_text_l10n":"IACT Corporation","created_at":"2022-05-12T21:57:35.300Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: IACT Corporation","updated_at":"2022-05-12T21:57:35.300Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:52.992Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1ce9add6379481b4","ACL":{},"alt_text_l10n":"i3 Systems, Inc.","created_at":"2022-05-12T21:57:35.104Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: i3 Systems, Inc.","updated_at":"2022-05-12T21:57:35.104Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.299Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4c773c89346597c4","ACL":{},"alt_text_l10n":"Hoshino Resorts","created_at":"2022-05-12T21:57:34.928Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Hoshino Resorts","updated_at":"2022-05-12T21:57:34.928Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.172Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt89acbe4ef0c352dc","ACL":{},"alt_text_l10n":"HolidayCheck","created_at":"2022-05-12T21:57:34.757Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: HolidayCheck","updated_at":"2022-05-12T21:57:34.757Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.987Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte994377bd1a2b0ab","ACL":{},"alt_text_l10n":"Hitachi Solutions, Ltd.","created_at":"2022-05-12T21:57:34.576Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Hitachi Solutions, Ltd.","updated_at":"2022-05-12T21:57:34.576Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.994Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt736af6f2540ccf24","ACL":{},"alt_text_l10n":"Hill AFB","created_at":"2022-05-12T21:57:34.383Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Hill AFB","updated_at":"2022-05-12T21:57:34.383Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.335Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt46881cdd850dfb82","ACL":{},"alt_text_l10n":"HELK","created_at":"2022-05-12T21:57:34.192Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: HELK","updated_at":"2022-05-12T21:57:34.192Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.120Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5bf86d044dacd94c","ACL":{},"alt_text_l10n":"Harel Insurance","created_at":"2022-05-12T21:57:34.015Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Harel Insurance","updated_at":"2022-05-12T21:57:34.015Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.431Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf8ae2ebe361b971e","ACL":{},"alt_text_l10n":"HappyFresh","created_at":"2022-05-12T21:57:33.832Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: HappyFresh","updated_at":"2022-05-12T21:57:33.832Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.825Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2827c97eb54874db","ACL":{},"alt_text_l10n":"H-E-B","created_at":"2022-05-12T21:57:33.650Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: H-E-B","updated_at":"2022-05-12T21:57:33.650Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.482Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16962bead1ff5c2f","ACL":{},"alt_text_l10n":"GuideStar","created_at":"2022-05-12T21:57:33.462Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GuideStar","updated_at":"2022-05-12T21:57:33.462Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.216Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3637ab36d3cf00bd","ACL":{},"alt_text_l10n":"Grubhub","created_at":"2022-05-12T21:57:33.285Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Grubhub","updated_at":"2022-05-12T21:57:33.285Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.663Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2174aaedb55466c3","ACL":{},"alt_text_l10n":"Groupon","created_at":"2022-05-12T21:57:33.105Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Groupon","updated_at":"2022-05-12T21:57:33.105Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.400Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt643e844c65ad43d6","ACL":{},"alt_text_l10n":"Green Man Gaming","created_at":"2022-05-12T21:57:32.921Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Green Man Gaming","updated_at":"2022-05-12T21:57:32.921Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.570Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt162646657593d87d","ACL":{},"alt_text_l10n":"Grab","created_at":"2022-05-12T21:57:32.733Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Grab","updated_at":"2022-05-12T21:57:32.733Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.195Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf02966382eca42b1","ACL":{},"alt_text_l10n":"Goldman Sachs","created_at":"2022-05-12T21:57:32.542Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Goldman Sachs","updated_at":"2022-05-12T21:57:32.542Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.059Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte4e89304a7574f1e","ACL":{},"alt_text_l10n":"GoDaddy","created_at":"2022-05-12T21:57:32.353Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GoDaddy","updated_at":"2022-05-12T21:57:32.353Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3620a9aafb8449c6","ACL":{},"alt_text_l10n":"Glomex","created_at":"2022-05-12T21:57:32.179Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Glomex","updated_at":"2022-05-12T21:57:32.179Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.654Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb08f8eea0cc7c703","ACL":{},"alt_text_l10n":"Globo.com","created_at":"2022-05-12T21:57:32.009Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Globo.com","updated_at":"2022-05-12T21:57:32.009Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.544Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt89d994d63cf310fc","ACL":{},"alt_text_l10n":"GitHub","created_at":"2022-05-12T21:57:31.841Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GitHub","updated_at":"2022-05-12T21:57:31.841Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7441d533eec880d6","ACL":{},"alt_text_l10n":"General Mills","created_at":"2022-05-12T21:57:31.651Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: General Mills","updated_at":"2022-05-12T21:57:31.651Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.358Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf288a36717eaaef8","ACL":{},"alt_text_l10n":"GDIT","created_at":"2022-05-12T21:57:31.463Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: GDIT","updated_at":"2022-05-12T21:57:31.463Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.084Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteee3e8992031a364","ACL":{},"alt_text_l10n":"Future Architect","created_at":"2022-05-12T21:57:31.270Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Future Architect","updated_at":"2022-05-12T21:57:31.270Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.050Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2d7d2bd434299759","ACL":{},"alt_text_l10n":"Furuno","created_at":"2022-05-12T21:57:31.079Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Furuno","updated_at":"2022-05-12T21:57:31.079Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.520Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35a9a1a7c28fdd8d","ACL":{},"alt_text_l10n":"Fujitsu","created_at":"2022-05-12T21:57:30.890Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fujitsu","updated_at":"2022-05-12T21:57:30.890Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.645Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1aa6cbe99dcac236","ACL":{},"alt_text_l10n":"Forcura","created_at":"2022-05-12T21:57:30.703Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Forcura","updated_at":"2022-05-12T21:57:30.703Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.238Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt781b08c2db99e45f","ACL":{},"alt_text_l10n":"Fitbit","created_at":"2022-05-12T21:57:30.516Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fitbit","updated_at":"2022-05-12T21:57:30.516Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.396Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dbf4c42724f2ea0","ACL":{},"alt_text_l10n":"FireEye","created_at":"2022-05-12T21:57:30.340Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: FireEye","updated_at":"2022-05-12T21:57:30.340Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.528Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd769a34479b15e33","ACL":{},"alt_text_l10n":"FICO","created_at":"2022-05-12T21:57:30.160Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: FICO","updated_at":"2022-05-12T21:57:30.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.034Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8a38ad997b77bbc2","ACL":{},"alt_text_l10n":"Fermilab","created_at":"2022-05-12T21:57:29.984Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fermilab","updated_at":"2022-05-12T21:57:29.984Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.005Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc76231546962bffb","ACL":{},"alt_text_l10n":"Feedzai","created_at":"2022-05-12T21:57:29.811Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Feedzai","updated_at":"2022-05-12T21:57:29.811Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.896Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt690eeda44c18819d","ACL":{},"alt_text_l10n":"Fastenal","created_at":"2022-05-12T21:57:29.633Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fastenal","updated_at":"2022-05-12T21:57:29.633Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.229Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2b7bf262bf551aec","ACL":{},"alt_text_l10n":"Fandango","created_at":"2022-05-12T21:57:29.452Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fandango","updated_at":"2022-05-12T21:57:29.452Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.469Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc929f4008f714e59","ACL":{},"alt_text_l10n":"Fairfax Media","created_at":"2022-05-12T21:57:29.092Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Fairfax Media","updated_at":"2022-05-12T21:57:29.092Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.912Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e7fd96603032488","ACL":{},"alt_text_l10n":"Facebook","created_at":"2022-05-12T21:57:28.890Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Facebook","updated_at":"2022-05-12T21:57:28.890Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.446Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd0d93313722dd2e1","ACL":{},"alt_text_l10n":"EZFarm","created_at":"2022-05-12T21:57:28.708Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: EZFarm","updated_at":"2022-05-12T21:57:28.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.986Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltecdc5cc97bf234bc","ACL":{},"alt_text_l10n":"Eventbrite","created_at":"2022-05-12T21:57:28.522Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Eventbrite","updated_at":"2022-05-12T21:57:28.522Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.023Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt56b906ebb6f676cb","ACL":{},"alt_text_l10n":"eStruxture Data","created_at":"2022-05-12T21:57:28.349Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eStruxture Data","updated_at":"2022-05-12T21:57:28.349Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.403Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt657193c765ffef39","ACL":{},"alt_text_l10n":"ESRI","created_at":"2022-05-12T21:57:28.158Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ESRI","updated_at":"2022-05-12T21:57:28.158Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.602Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdb9a794bae332d96","ACL":{},"alt_text_l10n":"Erste Group","created_at":"2022-05-12T21:57:27.979Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Erste Group","updated_at":"2022-05-12T21:57:27.979Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.054Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt49a78b721edd1534","ACL":{},"alt_text_l10n":"EO Media Group","created_at":"2022-05-12T21:57:27.793Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: EO Media Group","updated_at":"2022-05-12T21:57:27.793Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.153Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt77a0596e546d62e8","ACL":{},"alt_text_l10n":"Entel","created_at":"2022-05-12T21:57:27.618Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Entel","updated_at":"2022-05-12T21:57:27.618Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.390Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta6070c11de65133d","ACL":{},"alt_text_l10n":"Engadget","created_at":"2022-05-12T21:57:27.428Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Engadget","updated_at":"2022-05-12T21:57:27.428Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.691Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt311889e3633908f5","ACL":{},"alt_text_l10n":"EnergyIQ","created_at":"2022-05-12T21:57:27.242Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: EnergyIQ","updated_at":"2022-05-12T21:57:27.242Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.589Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9aad212543bb93b8","ACL":{},"alt_text_l10n":"Energisa","created_at":"2022-05-12T21:57:27.064Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Energisa","updated_at":"2022-05-12T21:57:27.064Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.581Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt78fdbcfeb35ca451","ACL":{},"alt_text_l10n":"Emirates NBD","created_at":"2022-05-12T21:57:26.883Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Emirates NBD","updated_at":"2022-05-12T21:57:26.883Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.402Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc3603d7c93395084","ACL":{},"alt_text_l10n":"Emerson","created_at":"2022-05-12T21:57:26.707Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Emerson","updated_at":"2022-05-12T21:57:26.707Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.678Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5e1a095dd42f4098","ACL":{},"alt_text_l10n":"Ellie Mae","created_at":"2022-05-12T21:57:26.531Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ellie Mae","updated_at":"2022-05-12T21:57:26.531Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.465Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc53d4bcfc5b07995","ACL":{},"alt_text_l10n":"Eleven Paths (Telefonica)","created_at":"2022-05-12T21:57:26.359Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Eleven Paths (Telefonica)","updated_at":"2022-05-12T21:57:26.359Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.692Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0abc351d0de4b19c","ACL":{},"alt_text_l10n":"eDreams","created_at":"2022-05-12T21:57:26.182Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eDreams","updated_at":"2022-05-12T21:57:26.182Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.086Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b0869c1257af6f","ACL":{},"alt_text_l10n":"ECS","created_at":"2022-05-12T21:57:26.002Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ECS","updated_at":"2022-05-12T21:57:26.002Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.041Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8511898223432dbb","ACL":{},"alt_text_l10n":"ECI","created_at":"2022-05-12T21:57:25.826Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: ECI","updated_at":"2022-05-12T21:57:25.826Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.948Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf0f3f31d0d252c86","ACL":{},"alt_text_l10n":"eBay Korea","created_at":"2022-05-12T21:57:25.640Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eBay Korea","updated_at":"2022-05-12T21:57:25.640Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.067Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta32be99cd1d4c367","ACL":{},"alt_text_l10n":"eBay","created_at":"2022-05-12T21:57:25.460Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: eBay","updated_at":"2022-05-12T21:57:25.460Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.661Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcbb2d798784eba3d","ACL":{},"alt_text_l10n":"E*Trade","created_at":"2022-05-12T21:57:25.277Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: E*Trade","updated_at":"2022-05-12T21:57:25.277Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.951Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt71288564a765a1cd","ACL":{},"alt_text_l10n":"DVLA","created_at":"2022-05-12T21:57:25.100Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DVLA","updated_at":"2022-05-12T21:57:25.100Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.317Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c67ffa73de8934b","ACL":{},"alt_text_l10n":"DramaFever","created_at":"2022-05-12T21:57:24.925Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DramaFever","updated_at":"2022-05-12T21:57:24.925Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.501Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt708bd1d551d6b5fa","ACL":{},"alt_text_l10n":"Docker","created_at":"2022-05-12T21:57:24.742Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Docker","updated_at":"2022-05-12T21:57:24.742Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.292Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6e40de2e7d79f3d1","ACL":{},"alt_text_l10n":"Direa","created_at":"2022-05-12T21:57:24.559Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Direa","updated_at":"2022-05-12T21:57:24.559Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.249Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta5d3c8b15d9cc43e","ACL":{},"alt_text_l10n":"DigitalOcean","created_at":"2022-05-12T21:57:24.386Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DigitalOcean","updated_at":"2022-05-12T21:57:24.386Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.684Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c63efdfda661ff3","ACL":{},"alt_text_l10n":"Devsisters","created_at":"2022-05-12T21:57:24.187Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Devsisters","updated_at":"2022-05-12T21:57:24.187Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.491Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2e89075a711e951a","ACL":{},"alt_text_l10n":"Devon Energy","created_at":"2022-05-12T21:57:24.012Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Devon Energy","updated_at":"2022-05-12T21:57:24.012Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.561Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt555807c9e4f92ae9","ACL":{},"alt_text_l10n":"Deutsche Telekom","created_at":"2022-05-12T21:57:23.832Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Deutsche Telekom","updated_at":"2022-05-12T21:57:23.832Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.380Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1478f1de8a987884","ACL":{},"alt_text_l10n":"DerbySoft","created_at":"2022-05-12T21:57:23.641Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DerbySoft","updated_at":"2022-05-12T21:57:23.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7b357913affc0bed","ACL":{},"alt_text_l10n":"Dell","created_at":"2022-05-12T21:57:23.447Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Dell","updated_at":"2022-05-12T21:57:23.447Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.416Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc2d2aadf8e1e6b14","ACL":{},"alt_text_l10n":"Delhivery","created_at":"2022-05-12T21:57:23.257Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Delhivery","updated_at":"2022-05-12T21:57:23.257Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.664Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9e137cb171447e0f","ACL":{},"alt_text_l10n":"Deezer","created_at":"2022-05-12T21:57:23.073Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Deezer","updated_at":"2022-05-12T21:57:23.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.620Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb769ee6a691fbb71","ACL":{},"alt_text_l10n":"DC Thomson","created_at":"2022-05-12T21:57:22.894Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: DC Thomson","updated_at":"2022-05-12T21:57:22.894Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.591Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7c1101be396cf896","ACL":{},"alt_text_l10n":"Cybozu, Inc.","created_at":"2022-05-12T21:57:22.708Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cybozu, Inc.","updated_at":"2022-05-12T21:57:22.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.423Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc74a3827872a4c74","ACL":{},"alt_text_l10n":"Cyber Security Innovations","created_at":"2022-05-12T21:57:22.531Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cyber Security Innovations","updated_at":"2022-05-12T21:57:22.531Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.713Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8bb6b5af5b7b8ab4","ACL":{},"alt_text_l10n":"Ctrip","created_at":"2022-05-12T21:57:22.336Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ctrip","updated_at":"2022-05-12T21:57:22.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.049Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt855d52164e1ca9e5","ACL":{},"alt_text_l10n":"Ctcue","created_at":"2022-05-12T21:57:22.155Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Ctcue","updated_at":"2022-05-12T21:57:22.155Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.955Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt653cdbbf95e42227","ACL":{},"alt_text_l10n":"CSX","created_at":"2022-05-12T21:57:21.976Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CSX","updated_at":"2022-05-12T21:57:21.976Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.593Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf6120d8cf05815aa","ACL":{},"alt_text_l10n":"CSG","created_at":"2022-05-12T21:57:21.793Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CSG","updated_at":"2022-05-12T21:57:21.793Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.786Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt3833e1f60ec9cd27","ACL":{},"alt_text_l10n":"Crimson Macaw","created_at":"2022-05-12T21:57:21.613Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Crimson Macaw","updated_at":"2022-05-12T21:57:21.613Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.690Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb0f71917411c7165","ACL":{},"alt_text_l10n":"Credit Suisse","created_at":"2022-05-12T21:57:21.439Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Credit Suisse","updated_at":"2022-05-12T21:57:21.439Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.557Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt763ca652cfdf4199","ACL":{},"alt_text_l10n":"CreatorIQ","created_at":"2022-05-12T21:57:21.249Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CreatorIQ","updated_at":"2022-05-12T21:57:21.249Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt14270cff94d0b91e","ACL":{},"alt_text_l10n":"Creationline, Inc.","created_at":"2022-05-12T21:57:21.072Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Creationline, Inc.","updated_at":"2022-05-12T21:57:21.072Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.155Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt38a79e3bbce1f126","ACL":{},"alt_text_l10n":"Cox Communications","created_at":"2022-05-12T21:57:20.875Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cox Communications","updated_at":"2022-05-12T21:57:20.875Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.011Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfe9e34bbd7d78d8b","ACL":{},"alt_text_l10n":"COS (Center for Open Science)","created_at":"2022-05-12T21:57:20.676Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: COS (Center for Open Science)","updated_at":"2022-05-12T21:57:20.676Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.862Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt67635abc692a4f85","ACL":{},"alt_text_l10n":"Concur","created_at":"2022-05-12T21:57:20.476Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Concur","updated_at":"2022-05-12T21:57:20.476Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.220Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7d294d29cb60c6d9","ACL":{},"alt_text_l10n":"Compare Group","created_at":"2022-05-12T21:57:20.296Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Compare Group","updated_at":"2022-05-12T21:57:20.296Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt85db1d2488eba1ba","ACL":{},"alt_text_l10n":"Collector Bank","created_at":"2022-05-12T21:57:20.118Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Collector Bank","updated_at":"2022-05-12T21:57:20.118Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.974Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt6647ff4f98fcda00","ACL":{},"alt_text_l10n":"Cogenta","created_at":"2022-05-12T21:57:19.940Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cogenta","updated_at":"2022-05-12T21:57:19.940Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.611Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteb40080095a4594e","ACL":{},"alt_text_l10n":"City of Wilson","created_at":"2022-05-12T21:57:19.764Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: City of Wilson","updated_at":"2022-05-12T21:57:19.764Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:18.014Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd1a19a3c02b08c5d","ACL":{},"alt_text_l10n":"City of Portland","created_at":"2022-05-12T21:57:19.575Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: City of Portland","updated_at":"2022-05-12T21:57:19.575Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.992Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fd0299de109ba7a","ACL":{},"alt_text_l10n":"Citigroup","created_at":"2022-05-12T21:57:19.384Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Citigroup","updated_at":"2022-05-12T21:57:19.384Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.351Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd6ae3e1628e85d5d","ACL":{},"alt_text_l10n":"Citi","created_at":"2022-05-12T21:57:19.194Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Citi","updated_at":"2022-05-12T21:57:19.194Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:10.019Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt612c38ebc6aaeac5","ACL":{},"alt_text_l10n":"Citadel Group","created_at":"2022-05-12T21:57:19.018Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Citadel Group","updated_at":"2022-05-12T21:57:19.018Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.524Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd21340b32a621fa2","ACL":{},"alt_text_l10n":"Cisco Talos","created_at":"2022-05-12T21:57:18.825Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cisco Talos","updated_at":"2022-05-12T21:57:18.825Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.998Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt74ba0723cf3acde8","ACL":{},"alt_text_l10n":"Cisco","created_at":"2022-05-12T21:57:18.647Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cisco","updated_at":"2022-05-12T21:57:18.647Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.370Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b781258dfabe57b","ACL":{},"alt_text_l10n":"Cigna","created_at":"2022-05-12T21:57:18.463Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cigna","updated_at":"2022-05-12T21:57:18.463Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.272Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ba98de9d8529e9","ACL":{},"alt_text_l10n":"CESICAT","created_at":"2022-05-12T21:57:18.289Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CESICAT","updated_at":"2022-05-12T21:57:18.289Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.100Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt93f0545de609d110","ACL":{},"alt_text_l10n":"Cerner","created_at":"2022-05-12T21:57:18.101Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Cerner","updated_at":"2022-05-12T21:57:18.101Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt946a82b512625e87","ACL":{},"alt_text_l10n":"CERN","created_at":"2022-05-12T21:57:17.916Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CERN","updated_at":"2022-05-12T21:57:17.916Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.572Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt74881ced4bba1ecc","ACL":{},"alt_text_l10n":"CERDEC/ARL","created_at":"2022-05-12T21:57:17.746Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CERDEC/ARL","updated_at":"2022-05-12T21:57:17.746Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.364Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1d7430456e9b649d","ACL":{},"alt_text_l10n":"CenturyLink","created_at":"2022-05-12T21:57:17.565Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CenturyLink","updated_at":"2022-05-12T21:57:17.565Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.313Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf531210bbf79c6b1","ACL":{},"alt_text_l10n":"CDL","created_at":"2022-05-12T21:57:17.376Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CDL","updated_at":"2022-05-12T21:57:17.376Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.774Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5d0a4c86b8d4954b","ACL":{},"alt_text_l10n":"CCTV","created_at":"2022-05-12T21:57:17.193Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CCTV","updated_at":"2022-05-12T21:57:17.193Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.440Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt155c6a13a1192d47","ACL":{},"alt_text_l10n":"CBC","created_at":"2022-05-12T21:57:17.006Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: CBC","updated_at":"2022-05-12T21:57:17.006Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.201Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcdfb889ec34061e0","ACL":{},"alt_text_l10n":"Car2Go","created_at":"2022-05-12T21:57:16.813Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Car2Go","updated_at":"2022-05-12T21:57:16.813Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.967Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc09b7e8e2c46e8d","ACL":{},"alt_text_l10n":"Capgemini","created_at":"2022-05-12T21:57:16.610Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Capgemini","updated_at":"2022-05-12T21:57:16.610Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.614Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f4378332e14f4ff","ACL":{},"alt_text_l10n":"Calgary Catholic School District","created_at":"2022-05-12T21:57:16.429Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Calgary Catholic School District","updated_at":"2022-05-12T21:57:16.429Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.483Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4af3ad2ac3c3183","ACL":{},"alt_text_l10n":"BulbAmerica","created_at":"2022-05-12T21:57:16.253Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BulbAmerica","updated_at":"2022-05-12T21:57:16.253Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.673Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt485687ae13b195d4","ACL":{},"alt_text_l10n":"Builtón","created_at":"2022-05-12T21:57:16.079Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Builtón","updated_at":"2022-05-12T21:57:16.079Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.145Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4377f94ab453f551","ACL":{},"alt_text_l10n":"Brolly","created_at":"2022-05-12T21:57:15.893Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Brolly","updated_at":"2022-05-12T21:57:15.893Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.082Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt37b9a3c07ffd3720","ACL":{},"alt_text_l10n":"Broaderbiz","created_at":"2022-05-12T21:57:15.699Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Broaderbiz","updated_at":"2022-05-12T21:57:15.699Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:10.681Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt709029231c67f216","ACL":{},"alt_text_l10n":"BPCE","created_at":"2022-05-12T21:57:15.516Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BPCE","updated_at":"2022-05-12T21:57:15.516Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.298Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte7e9d2f9abbc46b7","ACL":{},"alt_text_l10n":"Box","created_at":"2022-05-12T21:57:15.332Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Box","updated_at":"2022-05-12T21:57:15.332Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.979Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafb6f5a7c73517cb","ACL":{},"alt_text_l10n":"BNP Paribas","created_at":"2022-05-12T21:57:15.153Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BNP Paribas","updated_at":"2022-05-12T21:57:15.153Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.537Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb540438bbf4d409f","ACL":{},"alt_text_l10n":"BMW","created_at":"2022-05-12T21:57:14.980Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BMW","updated_at":"2022-05-12T21:57:14.980Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:02.563Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte35818ea37d72c17","ACL":{},"alt_text_l10n":"Blizzard","created_at":"2022-05-12T21:57:14.794Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Blizzard","updated_at":"2022-05-12T21:57:14.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.919Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc85fdfe39b77a46b","ACL":{},"alt_text_l10n":"Blackboard","created_at":"2022-05-12T21:57:14.591Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Blackboard","updated_at":"2022-05-12T21:57:14.591Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:09.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt85654053179804f2","ACL":{},"alt_text_l10n":"Bell Canada","created_at":"2022-05-12T21:57:14.402Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Bell Canada","updated_at":"2022-05-12T21:57:14.402Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:44.962Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04c206a2d77e2285","ACL":{},"alt_text_l10n":"BBC","created_at":"2022-05-12T21:57:14.217Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BBC","updated_at":"2022-05-12T21:57:14.217Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.030Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt46b48334c1d6c20d","ACL":{},"alt_text_l10n":"Bayer AG","created_at":"2022-05-12T21:57:13.999Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Bayer AG","updated_at":"2022-05-12T21:57:13.999Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.128Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt636f03b12f2bb3b3","ACL":{},"alt_text_l10n":"Bankwest","created_at":"2022-05-12T21:57:13.810Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Bankwest","updated_at":"2022-05-12T21:57:13.810Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.561Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1b3ccf9eb3002a02","ACL":{},"alt_text_l10n":"BAI Communications","created_at":"2022-05-12T21:57:13.632Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BAI Communications","updated_at":"2022-05-12T21:57:13.632Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:02.261Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltff7d14eebe21b05e","ACL":{},"alt_text_l10n":"BAI Canada","created_at":"2022-05-12T21:57:13.447Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: BAI Canada","updated_at":"2022-05-12T21:57:13.447Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.876Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c13e25327497cbb","ACL":{},"alt_text_l10n":"Azusa Pacific University","created_at":"2022-05-12T21:57:13.253Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Azusa Pacific University","updated_at":"2022-05-12T21:57:13.253Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.111Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt15d10999daa2ed8b","ACL":{},"alt_text_l10n":"AXA","created_at":"2022-05-12T21:57:13.054Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: AXA","updated_at":"2022-05-12T21:57:13.054Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:28:53.209Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt55ab8e95f71a5f34","ACL":{},"alt_text_l10n":"AutoScout24","created_at":"2022-05-12T21:57:12.863Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: AutoScout24","updated_at":"2022-05-12T21:57:12.863Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.393Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta8dbc4948d248385","ACL":{},"alt_text_l10n":"Autopilot","created_at":"2022-05-12T21:57:12.685Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Autopilot","updated_at":"2022-05-12T21:57:12.685Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.715Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt386af3ac08b15991","ACL":{},"alt_text_l10n":"Audi","created_at":"2022-05-12T21:57:12.500Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Audi","updated_at":"2022-05-12T21:57:12.500Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:18.999Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltde3c1eebe9ad8d75","ACL":{},"alt_text_l10n":"Auchan","created_at":"2022-05-12T21:57:12.323Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Auchan","updated_at":"2022-05-12T21:57:12.323Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:17.888Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt61a9adf7a1aab195","ACL":{},"alt_text_l10n":"Asian Food Network","created_at":"2022-05-12T21:57:12.147Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Asian Food Network","updated_at":"2022-05-12T21:57:12.147Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.543Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt931f215db4b59ccb","ACL":{},"alt_text_l10n":"Asana","created_at":"2022-05-12T21:57:11.963Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Asana","updated_at":"2022-05-12T21:57:11.963Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.132Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5d64e6e409dc810c","ACL":{},"alt_text_l10n":"Argos","created_at":"2022-05-12T21:57:11.771Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Argos","updated_at":"2022-05-12T21:57:11.771Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:26.455Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfcb527a0f1c9c706","ACL":{},"alt_text_l10n":"Amadeus","created_at":"2022-05-12T21:57:11.589Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Amadeus","updated_at":"2022-05-12T21:57:11.589Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.846Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7395586303b839e1","ACL":{},"alt_text_l10n":"Albert Heijn","created_at":"2022-05-12T21:57:11.400Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Albert Heijn","updated_at":"2022-05-12T21:57:11.400Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:37.347Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt436c743cba2a1055","ACL":{},"alt_text_l10n":"Airbus","created_at":"2022-05-12T21:57:11.210Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Airbus","updated_at":"2022-05-12T21:57:11.210Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.074Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8eb07a7b73362111","ACL":{},"alt_text_l10n":"Aginic","created_at":"2022-05-12T21:57:11.024Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Aginic","updated_at":"2022-05-12T21:57:11.024Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.085Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9ae02cf3417e4758","ACL":{},"alt_text_l10n":"Adobe","created_at":"2022-05-12T21:57:10.804Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Adobe","updated_at":"2022-05-12T21:57:10.804Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:51.587Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltf7320970545338ed","ACL":{},"alt_text_l10n":"Acuris","created_at":"2022-05-12T21:57:10.605Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Acuris","updated_at":"2022-05-12T21:57:10.605Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.793Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt53f2913cbc90ba00","ACL":{},"alt_text_l10n":"Activision","created_at":"2022-05-12T21:57:10.393Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Activision","updated_at":"2022-05-12T21:57:10.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:19.220Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltff00d74491dc28fe","ACL":{},"alt_text_l10n":"Achmea","created_at":"2022-05-12T21:57:10.206Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: Achmea","updated_at":"2022-05-12T21:57:10.206Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:30:23.869Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8b6181c39233bbf8","ACL":{},"alt_text_l10n":"11 Street","created_at":"2022-05-12T21:57:09.968Z","created_by":"blt36e890d06c5ec32c","tags":[],"title":"Customer: 11 Street","updated_at":"2022-05-12T21:57:09.968Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T22:29:45.028Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt403fcb9d8bef2f46","ACL":{},"alt_text_l10n":"Accenture","created_at":"2022-05-02T23:19:23.213Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Accenture","updated_at":"2022-05-12T21:47:24.400Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.797Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt8ea9cb7b1a5037c3","ACL":{},"alt_text_l10n":"Walmart Technology","created_at":"2022-05-02T23:19:22.836Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Walmart Technology","updated_at":"2022-05-12T21:47:01.930Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.809Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt7cd2eb6ff7674511","ACL":{},"alt_text_l10n":"Barclays","created_at":"2022-05-02T23:19:23.027Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Barclays","updated_at":"2022-05-12T21:46:58.490Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.820Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltcbcd7d1617610b47","ACL":{},"alt_text_l10n":"U.S. Department of Defense","created_at":"2022-05-02T23:19:23.405Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: U.S. Department of Defense","updated_at":"2022-05-12T21:46:44.810Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.833Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltd336b041dee3d8a9","ACL":{},"alt_text_l10n":"Air Force Mission Defense Teams","created_at":"2022-05-02T23:19:23.595Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Air Force Mission Defense Teams","updated_at":"2022-05-12T21:46:15.144Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.844Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt998fd1d1b1b796c4","ACL":{},"alt_text_l10n":"Ricoh","created_at":"2022-05-02T23:19:22.641Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Ricoh","updated_at":"2022-05-12T21:45:49.498Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.861Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt382da83ade79fb34","ACL":{},"alt_text_l10n":"U.S. Air Force","created_at":"2022-05-02T23:19:22.451Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: U.S. Air Force","updated_at":"2022-05-12T21:45:46.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.875Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltaf56ebc9f2d1fe5f","ACL":{},"alt_text_l10n":"Volkswagon","created_at":"2022-05-02T23:19:22.245Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Volkswagon","updated_at":"2022-05-12T21:45:42.535Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.887Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltc8f2519ccfc962b7","ACL":{},"alt_text_l10n":"Indiana University","created_at":"2022-05-02T23:19:23.788Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Customer: Indiana University","updated_at":"2022-05-12T21:45:24.150Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T21:47:36.901Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"blt39c3aa1b28dd2d91","ACL":{},"alt_text_l10n":"Application Performance Monitoring charts and graphs","created_at":"2022-03-18T21:02:28.349Z","created_by":"blt36e890d06c5ec32c","file":"blt8f7cd5151ef586ed","tags":[],"title":"Application Performance Monitoring charts and graphs","updated_at":"2022-04-01T19:07:18.369Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-04-01T19:07:31.659Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb1647f200956d5b9","ACL":{},"alt_text_l10n":"Elastic","created_at":"2022-03-22T18:19:39.827Z","created_by":"blt36e890d06c5ec32c","file":null,"tags":[],"title":"Elastic logo","updated_at":"2022-03-22T18:19:39.827Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-22T18:20:04.165Z","user":"blt36e890d06c5ec32c"}}]],"blogEntries":[[{"uid":"blta3be4cdd6afa6af0","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blta14bb0509c1528d3"],"body_l10n":"\u003cp\u003eToday we are pleased to announce the release of \u003cspan class=\"strong emphasis\"\u003e\u003cstrong\u003eElasticsearch 5.5.0\u003c/strong\u003e\u003c/span\u003e, based on \u003cspan class=\"strong emphasis\"\u003e\u003cstrong\u003eLucene 6.6.0\u003c/strong\u003e\u003c/span\u003e. This is the latest stable release, and is already available for deployment on \u003ca href=\"/cloud\" target=\"_top\"\u003eElastic Cloud\u003c/a\u003e, our Elasticsearch-as-a-service platform. This release includes a security fix for users of Elasticsearch X-Pack Security.\u003c/p\u003e\n\u003cp\u003eLatest stable release in 5.x:\u003c/p\u003e\n \u003cul class=\"list-green\"\u003e\n \u003cli\u003e\u003ca href=\"/downloads/elasticsearch\" target=\"_top\"\u003eDownload Elasticsearch 5.5.0\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/guide/en/elasticsearch/reference/5.5/release-notes-5.5.0.html\" target=\"_top\"\u003eElasticsearch 5.5.0 release notes\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/guide/en/elasticsearch/reference/5.5/breaking-changes-5.5.html\" target=\"_top\"\u003eElasticsearch 5.5 breaking changes\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/guide/en/x-pack/current/xpack-change-list.html\" target=\"_top\"\u003eX-Pack 5.5.0 release notes\u003c/a\u003e\u003c/li\u003e\n \u003c/ul\u003e\n\u003cp\u003eYou can read about all the changes in the release notes linked above, but there are a few changes which are worth highlighting:\u003c/p\u003e\n\u003cdiv class=\"section\"\u003e\n \u003cdiv class=\"titlepage\"\u003e\n \u003cdiv\u003e\n \u003cdiv\u003e\n \u003ch2 class=\"title\"\u003e\u003ca id=\"_sensitive_information_leak_esa_2017_10\"\u003e\u003c/a\u003eSensitive Information Leak (ESA-2017-10)\u003c/h2\u003e\n \u003c/div\u003e\n \u003c/div\u003e\n \u003c/div\u003e\n \u003cp\u003eElasticsearch X-Pack Security versions 5.0.0 to 5.4.3, when enabled, can result in the Elasticsearch _nodes API leaking sensitive configuration information, such as the paths and passphrases of SSL keys that were configured as part of an authentication realm. This could allow an authenticated Elasticsearch user to improperly view these details.\u003c/p\u003e\n \u003cp\u003eAll users of X-Pack security should upgrade to version 5.5.0. This update will prevent the _nodes API from returning sensitive settings. If you cannot upgrade, any sensitive settings can be hidden by using the X-Pack \u003ca href=\"https://www.elastic.co/guide/en/x-pack/current/security-troubleshooting.html#_literal_settings_literal\" target=\"_top\"\u003ehide_settings configuration option\u003c/a\u003e.\u003c/p\u003e\n \u003cp\u003e\u003cspan class=\"strong emphasis\"\u003e\u003cstrong\u003eCVE-ID:\u003c/strong\u003e\u003c/span\u003e CVE-2017-8442\u003c/p\u003e\n\u003c/div\u003e\n\u003cdiv class=\"section\"\u003e\n \u003cdiv class=\"titlepage\"\u003e\n \u003ch2 class=\"title\"\u003e\u003c/h2\u003e\n \u003ch2\u003eWindows MSI Installer release\u003c/h2\u003eWith this release of the Elastic stack, we're proud to announce the first release of the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.5/windows.html\"\u003eWindows MSI Installer for Elasticsearch\u003c/a\u003e. The installer provides a graphical user interface with a step-by-step wizard to guide users through the process of getting started with Elasticsearch on Windows:\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt82f0227e69882940/67c982a1045f58a85ec01543/msi_installer_configuration.png\" alt=\"Elasticsearch Node Configuration using the Windows Installer\" /\u003e\u003c/p\u003e\n \u003cp\u003eIn addition, it supports \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.5/windows.html#msi-command-line-options\"\u003emany command line options\u003c/a\u003e for flexible, silent installations. Please \u003ca href=\"https://www.elastic.co/downloads/elasticsearch\"\u003edownload the Windows Installer for Elasticsearch 5.5.0\u003c/a\u003e and try it out, and look out for a blog post coming soon with more details.\u003c/p\u003e\n \u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n \u003ch2 class=\"title\"\u003e\u003ca id=\"_icu_collation_keyword_fields\"\u003e\u003c/a\u003eICU Collation Keyword Fields\u003c/h2\u003e\n \u003c/div\u003e\n \u003cp\u003eCollations are used for sorting documents in a language-specific word order. The icu_collation_keyword field type allows you to convert a string (e.g. a surname) into bytes which represent the sort order for that string in a particular language. These bytes are indexed as a single token, just like the keyword field, and stored in doc values for fast sorting. Multiple collation fields can exist for the same string. For instance, the following will allow sorting in English order and in German “phonebook” order:\u003c/p\u003e\n \u003cdiv class=\"pre_wrapper\"\u003e\u003cpre class=\"programlisting\"\u003ePUT my_index\u003cbr /\u003e{\u003cbr /\u003e \"mappings\": {\u003cbr /\u003e \"user\": {\u003cbr /\u003e \"properties\": {\u003cbr /\u003e \"name\": {\u003cbr /\u003e \"type\": \"text\",\u003cbr /\u003e \"fields\": {\u003cbr /\u003e \"de_phonebook\": {\u003cbr /\u003e \"type\": \"icu_collation_keyword\",\u003cbr /\u003e \"index\": false,\u003cbr /\u003e \"language\": \"de\",\u003cbr /\u003e \"country\": \"DE\",\u003cbr /\u003e \"variant\": \"@collation=phonebook\"\u003cbr /\u003e },\u003cbr /\u003e \"en\": {\u003cbr /\u003e \"type\": \"icu_collation_keyword\",\u003cbr /\u003e \"index\": false,\u003cbr /\u003e \"language\": \"en\",\u003cbr /\u003e \"country\": \"US\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n \u003c/div\u003e\n\u003c/div\u003e\n\u003cdiv class=\"section\"\u003e\n \u003cdiv class=\"titlepage\"\u003e\n \u003cdiv\u003e\n \u003cdiv\u003e\n \u003ch2 class=\"title\"\u003e\u003ca id=\"_other_changes\"\u003e\u003c/a\u003eOther Changes\u003c/h2\u003e\n \u003c/div\u003e\n \u003c/div\u003e\n \u003c/div\u003e\n \u003cdiv\u003e\n \u003cul type=\"disc\"\u003e\n \u003cli\u003eA new ip_range field types (similar to date and numeric range fields) enables the indexing of IPv6 ranges, and allows these ranges to be queried with a range.\u003c/li\u003e\n \u003cli\u003eThe index.mapping.single_type setting will help you to prepare for the \u003ca href=\"https://www.elastic.co/blog/index-type-parent-child-join-now-future-in-elasticsearch\" target=\"_top\"\u003eone-type-per-index\u003c/a\u003e change coming in 6.0.\u003c/li\u003e\n \u003cli\u003eTerms aggregations which are sorted on a sub-aggregation will use less memory than before.\u003c/li\u003e\n \u003cli\u003eThe circuit breaker used by aggregations was allocating memory before accounting for the requested memory, which could result in an OOM exception.\u003c/li\u003e\n \u003c/ul\u003e\n \u003c/div\u003e\n \u003cp\u003ePlease \u003ca href=\"/downloads/elasticsearch\" target=\"_top\"\u003edownload Elasticsearch 5.5.0\u003c/a\u003e, try it out, and let us know what you think on Twitter (\u003ca href=\"https://twitter.com/elastic\" target=\"_top\"\u003e@elastic\u003c/a\u003e) or in our \u003ca href=\"https://discuss.elastic.co/c/elasticsearch\" target=\"_top\"\u003eforum\u003c/a\u003e. You can report any problems on the \u003ca href=\"https://github.com/elastic/elasticsearch/issues\" target=\"_top\"\u003eGitHub issues page\u003c/a\u003e.\u003c/p\u003e\n\u003c/div\u003e","category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:26:59.612Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt30c5a99357a6b177","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:09:49.974Z","updated_at":"2018-10-11T05:09:49.974Z","content_type":"image/jpeg","file_size":"93929","filename":"elasticsearch-blog-banner.jpg","title":"elasticsearch-blog-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:11:51.718Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt30c5a99357a6b177/5bbedb1d69d3fcaf5dbc0610/elasticsearch-blog-banner.jpg"},"markdown_l10n":"","publish_date":"2017-07-06T17:06:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch 5.5.0 released","seo_description_l10n":"Today we are pleased to announce the release of Elasticsearch 5.5.0, based on Lucene 6.5.1. This is the latest stable release, and is already available for deployment on Elastic Cloud, our Elasticsearch-as-a-service platform. This release includes a security fix for users of Elasticsearch X-Pack Security.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltb28316c9f63647c9","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:09:47.572Z","updated_at":"2018-10-11T05:09:47.572Z","content_type":"image/jpeg","file_size":"44060","filename":"elasticsearch-blog-thumb.jpg","title":"elasticsearch-blog-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:11:51.718Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb28316c9f63647c9/5bbedb1b560fdc4d0c8e6946/elasticsearch-blog-thumb.jpg"},"title":"Elasticsearch 5.5.0 released","title_l10n":"Elasticsearch 5.5.0 released","updated_at":"2025-03-10T12:39:35.255Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elasticsearch-5-5-0-released","publish_details":{"time":"2025-03-10T12:39:38.924Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9691b2ebd7a2765d","_version":15,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["bltc623bbbd9c0cfca4"],"body_l10n":"\u003cp\u003e\u003c/p\u003e\n\u003ch1\u003eKibana UI Update for July 15-19\u003c/h1\u003e\n\u003ch2\u003e\u003cspan\u003e\u003c/span\u003e\u003c/h2\u003e\n\u003ch2\u003eHiring\u003c/h2\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/01f01f5c1\"\u003e\u003cspan\u003eKibana Applications Security Engineer\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/24ddf24d1\"\u003e\u003cspan\u003eKibana - Senior JavaScript Engineer\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/a12f57d31\"\u003e\u003cspan\u003eKibana - Platform JavaScript Engineer (Node.js)\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://jobs.elastic.co/jobs/kibana/distributed-amer-or-western-europe/director-sr-director-product-management-kibana/1571633#/\"\u003e\u003cspan\u003eDirector / Sr Director Product Management - Kibana\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/7f51db4a1\"\u003e\u003cspan\u003eKibana - Visualisations Engineer\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2 dir=\"ltr\"\u003eSecurity\u003c/h2\u003e\n\u003ch3 dir=\"ltr\"\u003eNew Platform\u003c/h3\u003e\n\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe final changes to move \u003ca href=\"https://github.com/elastic/kibana/pull/39446\"\u003eauthentication to the new platform\u003c/a\u003e have been made, and will most likely have merged to master before you read this update.\u003c/p\u003e\n\u003ch3 dir=\"ltr\"\u003eAllow feature privileges which are excluded from base privileges\u003c/h3\u003e\n\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eTo enable ML and Reporting to \u003ca href=\"https://github.com/elastic/kibana/issues/37709#issuecomment-504145906\"\u003etransition to Kibana Privileges\u003c/a\u003e, we’re adding the ability for \u003ca href=\"https://github.com/elastic/kibana/pull/41300\"\u003efeature privileges to be excluded from the base privileges\u003c/a\u003e. This will allow users to grant access to ML and Reporting using the “custom” feature privileges during the 7.x timeframe.\u003c/p\u003e\n\u003ch2 dir=\"ltr\"\u003ePlatform\u003c/h2\u003e\n\u003ch3 dir=\"ltr\"\u003eNew Platform\u0026nbsp;\u003c/h3\u003e\n\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe \u003ca href=\"https://github.com/elastic/kibana/pull/39767\"\u003eroute handler interface RFC\u003c/a\u003e is pending final feedback from application teams. Mikhail has begin implementation, but we’re still accepting any final concerns before proceeding. All blocking issues for the security plugin’s migration have been solved.\u003c/p\u003e\n\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWe are in the process of \u003ca href=\"https://github.com/elastic/kibana/pull/41468\"\u003eadopting New platform Elasticsearch API to the legacy format\u003c/a\u003e to simplify further migration to the elasticesearch-js client. It shouldn't affect you unless you already use New Platform callAsCurrentUser / callAsInternalUser.\u003c/p\u003e\n\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/39891\"\u003eMigrating the Saved Object Client (SOC) to the new platform\u003c/a\u003e has turned out to be a bit more involved than we originally anticipated, but no critical roadblocks. We expect to begin review next week.\u003c/p\u003e\n\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWe’ve been iterating on the \u003ca href=\"https://github.com/elastic/kibana/pull/41251\"\u003eContextService\u003c/a\u003e this week to make consuming it much more ergonomic. This should be reviewed and merged next week which will unblock the last stages of the ApplicationService and HttpService.\u003c/p\u003e\n\u003ch2\u003eStack Services\u003c/h2\u003e\n\u003ch3\u003eAlerting Service\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003emerged\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eChange action config / params schema from joi to @kbn/config-schema \u003ca href=\"https://github.com/elastic/kibana/pull/40694\"\u003e#40694\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eCreates structured result of running an action \u003ca href=\"https://github.com/elastic/kibana/pull/41160\"\u003e#41160\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eRenders email action message text as html from markdown \u003ca href=\"https://github.com/elastic/kibana/pull/41187\"\u003e#41187\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003cspan\u003ein progress\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eAdd security support for alerts and actions\u0026nbsp; \u003ca href=\"https://github.com/elastic/kibana/pull/41389\"\u003e#41389\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eAdd an index action as built-in action\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eTask manager error handling enhancements \u003ca href=\"https://github.com/elastic/kibana/pull/39829\"\u003e#39829\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eTelemetry\u003c/h3\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eMove UI telemetry into a library\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eUpdate mappings\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eDiscuss 6 months plan\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eLocalization\u0026nbsp;\u003c/h3\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eAutomate label extraction and email sending to translators\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003e[merged] Use .i18nrc.json as the source of truth and enhance tooling\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eTesting German and French locales\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eDiscuss 6 months plan\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003eOperations\u003c/h2\u003e\n\u003cp\u003e\u003cspan\u003eWe finished the essential test suites for the static filesystem and will start the refactoring phase and fine tuning next. The old member-access rule from tslint was also enabled on typescript-eslint as the support for it was finally added.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan\u003ePrs:\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eEnable @typescript-eslint/explicit-member-accessibility rule \u003ca href=\"https://github.com/elastic/kibana/pull/41422\"\u003e#41422\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003eApp Architecture\u003c/h2\u003e\n\u003ch3\u003eEmbeddables \u0026amp; Actions\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eNow that \u003ca href=\"https://github.com/elastic/kibana/pull/39126\"\u003ethe final PR\u003c/a\u003e has merged with the initial embeddables API, we have been working toward \u003ca href=\"https://github.com/elastic/kibana/pull/41272\"\u003eprepping the API and dashboard embeddable container\u003c/a\u003e for migration to the new platform.\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\n\u003ch3\u003eOther\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eWe merged a fix for \u003ca href=\"https://github.com/elastic/kibana/pull/40855\"\u003ea long-standing bug\u003c/a\u003e affecting visualizations that were using the \"other\" bucket functionality for terms aggregations.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan\u003eWe opened a PR to add a \u003ca href=\"https://github.com/elastic/kibana/pull/41246\"\u003e@kbn/utility-types package\u003c/a\u003e for us to use in TypeScript across Kibana.\u003c/span\u003e\u003c/p\u003e\n\u003ch2\u003eKibana App (Visualizations, Sharing, Discover, Reporting)\u003c/h2\u003e\n\u003ch3\u003eNew visual editor Lens\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eThis week we thought about the basic structure of Lens and decided to add the concept of “layers”. This makes it possible to combine data tables of different queries (and even index patterns) in a single chart. The resulting PR touches a lot of places and is not merged yet, but will make charts possible as shown in the screenshot below.\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt75fc16ea1f691a7a/5d3621d5241468159d6fb2c0/image6.png\" data-sys-asset-uid=\"blt75fc16ea1f691a7a\" alt=\"image6.png\" /\u003e\n\u003cp\u003e\u003cspan\u003eBesides that we worked on showing Lens visualizations on dashboards by implementing the embeddable API and continued to improve performance.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003ch3\u003eElastic Charts\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eVersion 8.0.2 is out with some breaking changes and new features:\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eYou can now override the computed color of all the series of a specific type (all the lines for example) or of a series component using the fill/stroke attribute of the style. See \u003ca href=\"https://github.com/elastic/elastic-charts/pull/258\"\u003e#258\u003c/a\u003e for more details.\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0f904d5852050e64/5d36221e7414f11598138c00/image5.png\" data-sys-asset-uid=\"blt0f904d5852050e64\" alt=\"image5.png\" style=\"float: left;margin: 0px;text-align: left;\" /\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdb45ea071296b15e/5d36222fe0aa25161afed894/image2.png\" data-sys-asset-uid=\"bltdb45ea071296b15e\" alt=\"image2.png\" /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan\u003eThis also means that we introduced a breaking change: the previous Theme includes also the fill/stroke attributes for the series styles: with this change, specifying a fill or stroke at theme level means to override and use the same color on every series that belongs to that overridden attribute.\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan\u003eWe are also in the process to clean and restyle the legend. The first pass was to remove the redundancy of icons on the legend removing the eyeOpen/eyeClosed icons showing them only when necessary. We have now a bit more space for the series title.\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9a548df23fb2ee42/5d3622739778bb113bf137fc/image3.png\" data-sys-asset-uid=\"blt9a548df23fb2ee42\" alt=\"image3.png\"/\u003e\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan\u003eWe also fixed the last two issues missing before replacing the Discover chart with elastic-charts, covering some edge cases when displaying a single bar.\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003eDiscover\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003ePR for deangularizing kbnTableHeader is ready for review \u003ca href=\"https://github.com/elastic/kibana/pull/41259\"\u003e#41259\u003c/a\u003e\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan\u003eBefore deangularizing kbnTableRow kbnDocViews has to be finished, so this is the next step.\u003c/span\u003e\u003c/p\u003e\n\u003ch2\u003eCanvas\u003c/h2\u003e\n\u003ch3\u003eEmbeddables in Canvas\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eWe have decided to tackle the embeddables in Canvas en masse, and by enabling this exciting new feature, Canvas adoption, relevance, and flexibility will increase.\u0026nbsp; From existing users to prospective customers, Canvas will allow everyone to quickly create and brand personalized content faster and easier with an extra dose of fantabulousness.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan\u003eCanvas is currently in fast-follow mode behind the Kibana App Architecture team to enable existing shared visualizations like Maps in Canvas using the new embeddable architecture\u0026nbsp; for the 7.4 release.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt27a9d1d4fc9fdc02/5d3622889778bb113bf13802/image8.png\" data-sys-asset-uid=\"blt27a9d1d4fc9fdc02\" alt=\"image8.png\" /\u003e\u003c/p\u003e\n\u003ch2\u003eDesign\u003c/h2\u003e\n\u003ch3\u003eGraph\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eSurprise. We’re doing some exploration on what the graph visualizations could look like. We don’t anticipate jumping too deeply into this project during 7.4, but it’s on our radar and will get some more attention over the next few minors.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3a49754366bb39ac/5d362298e0aa25161afed89a/image9.png\" data-sys-asset-uid=\"blt3a49754366bb39ac\" alt=\"image9.png\" /\u003e\u003c/p\u003e\n\n\u003ch3\u003eMenu systems in the top nav exploration\u003c/h3\u003e\n\u003cp\u003e\u003cspan\u003eOne recurring pattern we’ve seen in the design team is that the apps are trying to put together various OS style “bar navs” to deal with their controls. We’re considering creating an actual nested menu system to deal with it. This would give folks a little more reliable way to deal with these sorts of situations and make our app to app experience a little more uniform.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7adf249c7f302b80/5d3622b40bbb1819f4df9086/image4.png\" data-sys-asset-uid=\"blt7adf249c7f302b80\" alt=\"image4.png\" /\u003e\u003c/p\u003e\n\u003ch3\u003eCharting lib removed from EUI (breaking change)\u003c/h3\u003e\n\u003cp\u003eWe merged \u003ca href=\"https://github.com/elastic/eui/pull/2108\"\u003ea PR in EUI to remove the charting library\u003c/a\u003e. Since this is a breaking change, we also went through and end of lifed a bunch of Sass mixins and the K6 themes.\u003c/p\u003e","category":[],"created_at":"2019-07-22T18:45:57.251Z","created_by":"blta9b9246b12e194b5","disclaimer":[],"full_bleed_image":{"uid":"bltaca1d2dd5b24785e","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2019-04-30T22:22:10.007Z","updated_at":"2019-04-30T22:22:10.007Z","content_type":"image/png","file_size":"97644","filename":"kibana_training_thumbnail.png","title":"kibana_training_thumbnail.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T11:00:00.000Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaca1d2dd5b24785e/5cc8ca924c5fe8936416626f/kibana_training_thumbnail.png"},"markdown_l10n":"","publish_date":"2019-07-22T17:23:36.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"Good progress on features and enhancements: Alerting, Maps, Elastic charts, Lens, Canvas, embeddables, and EUI.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt10b0272b11c24025","created_by":"blta9b9246b12e194b5","updated_by":"blta9b9246b12e194b5","created_at":"2019-07-22T20:10:10.482Z","updated_at":"2019-07-22T20:10:10.482Z","content_type":"image/jpeg","file_size":"100125","filename":"Screen_Shot_2019-07-22_at_3.08.00_PM.jpg","title":"Screen_Shot_2019-07-22_at_3.08.00_PM.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-07-22T21:31:14.627Z","user":"blta9b9246b12e194b5"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt10b0272b11c24025/5d361822c780b1161fc589b3/Screen_Shot_2019-07-22_at_3.08.00_PM.jpg"},"title":"Keeping up with Kibana: This week in Kibana for July 19th, 2019","title_l10n":"Keeping up with Kibana: This week in Kibana for July 19th, 2019","updated_at":"2025-03-10T12:36:34.054Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/keeping-up-with-kibana-2019-07-19","publish_details":{"time":"2025-03-10T12:36:38.139Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta3ff2ebac8b6a24a","_version":19,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt85b0e579ed18da50"],"body_l10n":"\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003ch2\u003e\u003cstrong\u003eKibana UI Update\u003c/strong\u003e\u003c/h2\u003e\n\u003ch3\u003e\u003cstrong\u003eHiring\u003c/strong\u003e\u003c/h3\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/24ddf24d1\"\u003e\u003cstrong\u003eKibana - Senior JavaScript Engineer\u003c/strong\u003e\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/a12f57d31\"\u003e\u003cstrong\u003eKibana - Platform JavaScript Engineer (Node.js)\u003c/strong\u003e\u003c/a\u003e\u003c/li\u003e\u003ca href=\"https://grnh.se/7f51db4a1\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/a\u003e\n \u003cli\u003e\u003ca href=\"https://grnh.se/7f51db4a1\"\u003e\u003cstrong\u003eKibana - Visualisations Engineer\u003c/strong\u003e\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch3\u003e\u003cstrong\u003eThis week's highlight:\u0026nbsp;new Lens visualization is coming!\u003c/strong\u003e\u003c/h3\u003e\n\u003cp\u003eLens has been merged! You can now see Lens visualization type in Visualize app on master and 7.x. We are continuing to work on bug fixes and small improvements in preparation for Beta, but would love for you to try it out and send us your feedback!\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcd5883a47968ebcb/5d8a92aba3629438cf51ec8f/lens_preview.gif\" data-sys-asset-uid=\"bltcd5883a47968ebcb\" alt=\"lens_preview.gif\" /\u003e\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eSecurity\u003c/strong\u003e\u003c/h3\u003e\n\u003ch4\u003e\u003cstrong\u003eSpace specific default routes\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eThe \u003ca href=\"https://github.com/elastic/kibana/pull/45382\"\u003eprerequisite PR\u003c/a\u003e which migrates portions of the Spaces plugin to the new platform merged last week. This makes the \u003ca href=\"https://github.com/elastic/kibana/pull/44678\"\u003eactual implementation\u003c/a\u003e much easier, which we’ll be focusing on this week.\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eSAML redirect and hash based routing\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eThe changes have been made to no longer rely upon RelayState for this feature, and the configurable URL length limits have been implemented. The \u003ca href=\"https://github.com/elastic/kibana/pull/44513\"\u003ePR\u003c/a\u003e is ready for the next round of reviews this week.\u0026nbsp;\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003ePlatform\u003c/strong\u003e\u003c/h3\u003e\n\u003cp\u003eThis week we completed nearly all of our blocker audits with plugin teams. We have a couple left to tie up this week and are primarily focused on execution now. So far, we have not identified any pressing new blockers that were previously unknown, which is good.\u003c/p\u003e\n\u003cp\u003eThis week we completed \u003ca href=\"https://github.com/elastic/kibana/pull/43610\"\u003emigrating the global banner UI\u003c/a\u003e to the New Platform. We also fixed a \u003ca href=\"https://github.com/elastic/kibana/pull/46167\"\u003ecouple\u003c/a\u003e \u003ca href=\"https://github.com/elastic/kibana/pull/45918\"\u003ebugs\u003c/a\u003e in the New Platform. This week, work is expected to complete on migrating the SavedObjectClient on the server and the \u003ca href=\"https://github.com/elastic/kibana/pull/44922\"\u003elicensing plugin on the client\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eFor the New Platform migration, 7 PRs were merged by plugin teams this week, 6 by the App Arch team and 1 by the Security team.\u003c/p\u003e\n\u003ch3\u003eGeo-Maps App\u003c/h3\u003e\n\u003cp\u003eMaps now cancels out-dated Elasticsearch requests when users change search criteria, remove a layer, or leave the map before existing requests resolve.\u003c/p\u003e\n\u003cp\u003eMigrated tooltips from Mapbox tooltips to EuiPopover. This is useful for embedded maps. Mapbox tooltips are constrained to the bounds of the panel while EuiPopovers are only constrained to the bounds of the screen, allowing tooltips to expand outside of small embedded panels.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1dd4884c701c5fba/5d8a93608a24c40d20cca0ab/map_tooltips.png\" data-sys-asset-uid=\"blt1dd4884c701c5fba\" alt=\"map_tooltips.png\" /\u003e\u003c/p\u003e\n\u003ch3\u003eGeo-Elastic Maps Service\u003c/h3\u003e\n\u003cp\u003eWe continue to curate and test subdivision boundaries of Eastern European countries. Currently in review are subdivisions for Serbia and Montenegro.\u0026nbsp;\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eApp Architecture\u003c/strong\u003e\u003c/h3\u003e\n\u003ch4\u003eNew Platform Migration\u003c/h4\u003e\n\u003cp\u003eWe made \u003ca href=\"https://github.com/elastic/kibana/pull/45532\"\u003eprogress\u003c/a\u003e on \u003ca href=\"https://github.com/elastic/kibana/pull/45498\"\u003emoving\u003c/a\u003e filter, time filter, and query services to the new platform. agg_config and agg_configs were \u003ca href=\"https://github.com/elastic/kibana/pull/45877\"\u003emoved\u003c/a\u003e to agg_types in preparation for the final move to data plugin.\u0026nbsp; We also worked on refactoring \u003ca href=\"https://github.com/elastic/kibana/pull/45874\"\u003evisualization\u003c/a\u003e \u003ca href=\"https://github.com/elastic/kibana/pull/45869\"\u003etypes\u003c/a\u003e.\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eKibana App (Visualizations, Sharing, Discover, Reporting)\u003c/strong\u003e\u003c/h3\u003e\n\u003ch4\u003e\u003cstrong\u003eLens\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eWe merged Lens into master and 7.x!\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eElastic Charts\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eIt’s now safe to call a React re-render on \u003ca href=\"https://github.com/elastic/elastic-charts/issues/376\"\u003eonBrushEnd events\u003c/a\u003e. We added the possibility to hide duplicate axes created by the user based on ticks labels, position and axis title.\u003c/p\u003e\n\u003cp\u003eOn version 13.0.0 we also introduced a small \u003cstrong\u003ebreaking change\u003c/strong\u003e, on the Theme type, introducing the visibility property on the tickLineStyle them property (see \u003ca href=\"https://github.com/elastic/elastic-charts/pull/374\"\u003e#374\u003c/a\u003e for details).\u003c/p\u003e\n\u003cp\u003eWe keep working on the \u003ca href=\"https://github.com/elastic/elastic-charts/pull/281\"\u003erefactoring\u003c/a\u003e of the library removing MobX state manager in favour of Redux (to align with other existing products and apps and to clean and improve the current data processing flow).\u003c/p\u003e\n\u003cp\u003eWe made progress on the pie chart implementation. Now the slice labelling is in good shape, we are working on adding more test coverage.We will finally integrate this work when the \u003ca href=\"https://github.com/elastic/elastic-charts/pull/281\"\u003erefactoring and the new chart type API\u003c/a\u003e is merged.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt498dd88600e965a3/5d8a93aab67b660d1bee2108/chart_preview.png\" data-sys-asset-uid=\"blt498dd88600e965a3\" alt=\"chart_preview.png\" /\u003e\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eGraph\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eLast week de-angularization of the search bar \u003ca href=\"https://github.com/elastic/kibana/pull/45351\"\u003e#45351\u003c/a\u003e including KQL support \u003ca href=\"https://github.com/elastic/kibana/pull/45364\"\u003e#45364\u003c/a\u003e was merged along with minor cleanups and restructurings \u003ca href=\"https://github.com/elastic/kibana/pull/45770\"\u003e#45770\u003c/a\u003e \u003ca href=\"https://github.com/elastic/kibana/pull/45782\"\u003e#45782\u003c/a\u003e. Graph now also has a readme that explains the setup and most commonly used commands.\u003c/p\u003e\n\u003cp\u003eDe-angularization of the field manager \u003ca href=\"https://github.com/elastic/kibana/pull/45384\"\u003e#45384\u003c/a\u003e and a new welcome screen when no workspace is configured \u003ca href=\"https://github.com/elastic/kibana/pull/45547\"\u003e#45547\u003c/a\u003e are currently in progress - thanks a lot for the input from the design team!.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta2d5e472b826d7ba/5d8a93d32d73960d2a506ecf/graph_getting_started.png\" data-sys-asset-uid=\"blta2d5e472b826d7ba\" alt=\"graph_getting_started.png\" /\u003e\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eDiscover\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eDe-angularization of the doc view was merged \u003ca href=\"https://github.com/elastic/kibana/pull/44660\"\u003e#44660\u003c/a\u003e. With the merge of \u003ca href=\"https://github.com/elastic/kibana/pull/44212\"\u003e#44212\u003c/a\u003e sorting by time field when indices mix the format \u003cstrong\u003edate\u003c/strong\u003e and \u003cstrong\u003edate_nanos \u003c/strong\u003eworks correctly. Currently in the works: De-angularizing the left side panel. And there’s a\u0026nbsp; brand new slack channel: #kibana-discover\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eCanvas\u003c/strong\u003e\u003c/h3\u003e\n\u003cp\u003eThe Canvas team is still heads down working on adding localization to the entire Canvas app.\u0026nbsp;\u0026nbsp;\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eDesign\u003c/strong\u003e\u003c/h3\u003e\n\u003ch4\u003e\u003cstrong\u003eAccessibility\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eAccessibility is always a focus for us and we have created a video around building and testing for accessibility with EUI.\u0026nbsp;\u003ca href=\"https://www.youtube.com/watch?v=iDXoEe8NkrE\u0026feature=youtu.be\"\u003eAvailable here.\u003c/a\u003e\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eEUI Data Grid\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eEuiDataGrid can now detect schema types and auto-applies formatting rules based on that. It can also be given styles on a per-cell basis.\u003c/p\u003e\n\u003cp\u003eThere is also progress around selecting and viewing a cell’s content.\u0026nbsp; The format of the popover will match the schema of the content for the cell, allowing for longer content and better readability.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1ac9697f5192bce5/5d8a945d27cc7a38ca73743c/data_grid.png\" data-sys-asset-uid=\"blt1ac9697f5192bce5\" alt=\"data_grid.png\" /\u003e\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eMaps + Compressed Forms\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eThe Maps application received the newly merged compressed forms to make for a clear and super slick UI.\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eDashboard workflow\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eWe’re exploring ways to tighten up the workflow between the Dashboard and the growing number of applications that provide content for dashboards (Visualize, Lens, Maps, etc).\u003c/p\u003e\n\u003ch4\u003e\u003cstrong\u003eColor Stops component\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eThe Color Stops component received some more attention recently and is becoming more and more polished.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3d9abe2e7d5f2e72/5d8a947ff0e07b2dd96a5100/color_stops_component.png\" data-sys-asset-uid=\"blt3d9abe2e7d5f2e72\" alt=\"color_stops_component.png\" /\u003e\u003c/p\u003e\n\u003ch3\u003e\u003cstrong\u003eStack Services\u003c/strong\u003e\u003c/h3\u003e\n\u003ch4\u003e\u003cstrong\u003eAlerting\u003c/strong\u003e\u003c/h4\u003e\n\u003cp\u003eWe built a performance improvement into Task Manager parallelizing the way in which Task Manager claims ownership of tasks.\u0026nbsp; He ran a performance assessment of this improvement, measuring a marked improvement in task performance, but not quite as good as we need for alerting.\u0026nbsp; He is now working on an alternative approach based off of Mike's past work on the subject.\u0026nbsp; Mike merged throttling support for alerts: \u003ca href=\"https://github.com/elastic/kibana/pull/41919\"\u003e#41919\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003eHe also added an API to update API key (change ownership): \u003ca href=\"https://github.com/elastic/kibana/pull/45925\"\u003e#45925\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003eThe \"alertId\" and \"alertInstanceId\" properties are now accessible in templated alert action params in\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/pull/45803\"\u003e#45803\u003c/a\u003e.\u0026nbsp; New tests testing access across spaces have been put in place: \u003ca href=\"https://github.com/elastic/kibana/pull/45892\"\u003e#45892\u003c/a\u003e.\u0026nbsp;A new discuss issue for alert muting is created: \u003ca href=\"https://github.com/elastic/kibana/issues/46034\"\u003e#46034\u003c/a\u003e.\u0026nbsp; Patrick continued work on the event log in\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/issues/45083\"\u003e#45083\u003c/a\u003e\u0026nbsp;and\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/pull/45081\"\u003e#45081\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eThat's all for this week.\u003cbr /\u003e- Kibana team\u003c/p\u003e","category":[],"created_at":"2019-09-24T21:55:54.169Z","created_by":"blte688eb02cfbb5524","disclaimer":[],"full_bleed_image":{"uid":"blt0ba64554b53df4df","ACL":{},"_version":1,"content_type":"image/png","created_at":"2019-10-18T22:04:10.512Z","created_by":"bltf6ab93733e4e3a73","file_size":"27476","filename":"kibana-weekly-blog-banner.png","is_dir":false,"parent_uid":null,"tags":[],"title":"kibana-weekly-blog-banner.png","updated_at":"2019-10-18T22:04:10.512Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-18T22:04:17.945Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ba64554b53df4df/5daa36dadf78486c826db921/kibana-weekly-blog-banner.png"},"markdown_l10n":"","publish_date":"2019-09-25T17:30:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Lens visualization is now available; we are continuing to migrate to the new platform; Graph getting started experience improvements and more!","seo_description_l10n":"Keeping up with Kibana: This week in Kibana for September 23th, 2019\nThe Kibana team has merged Lens visualization; we are continuing to migrate to the new platform; Graph getting started experience improvements and more!","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blta6ce6c7fc47ff2cb","ACL":{},"_version":1,"content_type":"image/png","created_at":"2019-10-18T22:04:10.428Z","created_by":"bltf6ab93733e4e3a73","file_size":"22849","filename":"kibana-weekly-blog-thumb.png","is_dir":false,"parent_uid":null,"tags":[],"title":"kibana-weekly-blog-thumb.png","updated_at":"2019-10-18T22:04:10.428Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-18T22:04:32.538Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta6ce6c7fc47ff2cb/5daa36da2dc72966da7451aa/kibana-weekly-blog-thumb.png"},"title":"Keeping up with Kibana: This week in Kibana for September 23rd, 2019","title_l10n":"Keeping up with Kibana: This week in Kibana for September 23rd, 2019","updated_at":"2025-03-10T12:35:17.420Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/keeping-up-with-kibana-2019-09-23","publish_details":{"time":"2025-03-10T12:35:21.374Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3e9a03c6f511ba22","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"","author":[],"body_l10n":"\u003cp\u003eLogstash has been missing a way to receive data through HTTP requests, but not anymore!\u003c/p\u003e\u003cp\u003eThe \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-http.html\"\u003elogstash-input-http\u003c/a\u003e\u0026nbsp;plugin is now available for everyone! Also, starting with \u003ca href=\"https://www.elastic.co/blog/logstash-1-5-2-released\"\u003eLogstash 1.5.2\u003c/a\u003e, it is included as one of the default plugins that are distributed with the official release.\u003c/p\u003e\u003ch2\u003eSo what exactly does the logstash-input-http plugin do?\u003c/h2\u003e\u003cp\u003eWhen you configure this plugin in the input section, it will launch a HTTP server and create events from requests sent to this endpoint. This means you can send notification data to Logstash using webhooks, thereby integrating your existing applications with Logstash’s rich plugin ecosystem!\u003c/p\u003e\u003ch2\u003eHow do I use this plugin?\u003c/h2\u003e\u003cp\u003eBy default it will bind the webserver to all hosts (\"0.0.0.0\") and open the TCP port 8080 but it's possible configure these settings:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003einput {\u003cbr /\u003e http {\u003cbr /\u003e host =\u0026gt; \"127.0.0.1\" # default: 0.0.0.0\u003cbr /\u003e port =\u0026gt; 31311 # default: 8080\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThat's all you need!\u003c/p\u003e\u003ch3\u003eWhat about security?\u003c/h3\u003e\u003cp\u003eYou can configure basic authentication by setting a username and password. All requests done to Logstash will then have to set the right credentials or receive a 401 response. Only correctly authenticated requests will produce an event inside of Logstash. For SSL, it is necessary to specify the path to a \u003ca href=\"https://docs.oracle.com/cd/E19509-01/820-3503/ggfen/index.html\"\u003eJava Keystore\u003c/a\u003e that contains the certificate that clients use to validate the server. Here's an example:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003einput {\u003cbr /\u003e port =\u0026gt; 3332\u003cbr /\u003e user =\u0026gt; myuser\u003cbr /\u003e password =\u0026gt; \"$tr0ngP4ssWD!\"\u003cbr /\u003e ssl =\u0026gt; on\u003cbr /\u003e keystore =\u0026gt; \"/tmp/mykeystore.jks\"\u003cbr /\u003e keystore_password =\u0026gt; \"keystore_pass\"\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch2\u003eOK, now show me this plugin in action!\u003c/h2\u003e\u003cp\u003eStep 1 - starting Logstash with http input:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ebin/logstash -e \"input { http { } } output { stdout { codec =\u0026gt; rubydebug} }\"\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eStep 2 - That's it!\u003c/p\u003e\u003cp\u003eTo test it, let's issue two requests:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e% curl -XPUT 'http://127.0.0.1:8080/twitter/tweet/1' -d 'hello' \u003cbr /\u003e% curl -H \"content-type: application/json\" -XPUT 'http://127.0.0.1:8080/twitter/tweet/1' -d '{\u003cbr /\u003e \"user\" : \"kimchy\",\u003cbr /\u003e \"post_date\" : \"2009-11-15T14:12:12\",\u003cbr /\u003e \"message\" : \"trying out Elasticsearch\"\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eResult in Logstash:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e \"message\" =\u0026gt; \"hello\",\u003cbr /\u003e \"@version\" =\u0026gt; \"1\",\u003cbr /\u003e \"@timestamp\" =\u0026gt; \"2015-05-29T14:49:00.392Z\",\u003cbr /\u003e \"headers\" =\u0026gt; {\u003cbr /\u003e \"content_type\" =\u0026gt; \"application/x-www-form-urlencoded\",\u003cbr /\u003e \"request_method\" =\u0026gt; \"PUT\",\u003cbr /\u003e \"request_path\" =\u0026gt; \"/twitter/tweet/1\",\u003cbr /\u003e \"request_uri\" =\u0026gt; \"/twitter/tweet/1\",\u003cbr /\u003e \"http_version\" =\u0026gt; \"HTTP/1.1\",\u003cbr /\u003e \"http_user_agent\" =\u0026gt; \"curl/7.37.1\",\u003cbr /\u003e \"http_host\" =\u0026gt; \"127.0.0.1:8080\",\u003cbr /\u003e \"http_accept\" =\u0026gt; \"*/*\",\u003cbr /\u003e \"content_length\" =\u0026gt; \"5\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e{\u003cbr /\u003e \"user\" =\u0026gt; \"kimchy\",\u003cbr /\u003e \"post_date\" =\u0026gt; \"2009-11-15T14:12:12\",\u003cbr /\u003e \"message\" =\u0026gt; \"trying out Elasticsearch\",\u003cbr /\u003e \"@version\" =\u0026gt; \"1\",\u003cbr /\u003e \"@timestamp\" =\u0026gt; \"2015-05-29T14:49:04.105Z\",\u003cbr /\u003e \"headers\" =\u0026gt; {\u003cbr /\u003e \"content_type\" =\u0026gt; \"application/json\",\u003cbr /\u003e \"request_method\" =\u0026gt; \"PUT\",\u003cbr /\u003e \"request_path\" =\u0026gt; \"/twitter/tweet/1\",\u003cbr /\u003e \"request_uri\" =\u0026gt; \"/twitter/tweet/1\",\u003cbr /\u003e \"http_version\" =\u0026gt; \"HTTP/1.1\",\u003cbr /\u003e \"http_user_agent\" =\u0026gt; \"curl/7.37.1\",\u003cbr /\u003e \"http_host\" =\u0026gt; \"127.0.0.1:8080\",\u003cbr /\u003e \"http_accept\" =\u0026gt; \"*/*\",\u003cbr /\u003e \"content_length\" =\u0026gt; \"110\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eYou can see that in the second request, since the content-type was application/json, the body was deserialized and expanded to the event root (notice the fields \"user\", \"post_date\" and \"message\").\u003c/p\u003e\u003ch2\u003eShow me more concrete examples of how to use it!\u003c/h2\u003e\u003cp\u003eBecause, real world examples make everything clearer!\u003c/p\u003e\u003ch3\u003eElastic\u0026nbsp;Watcher Integration\u003c/h3\u003e\u003cp\u003eIn this section, we’ll show you how to integrate \u003ca href=\"https://www.elastic.co/what-is/elasticsearch-alerting\"\u003eElastic\u0026nbsp;Watcher\u003c/a\u003e -- the new Elasticsearch plugin for alerting and notification -- with Logstash. \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/logstash-integration.html#_using_logstash_for_watch_actions\"\u003eSending\u003c/a\u003e notifications to Logstash via this input provides you a powerful toolset to further transform notifications and use Logstash’s rich collection of \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/output-plugins.html\"\u003eoutputs\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eImagine that you have indices with Apache logs, and now we want to get a periodic update of how many requests are resulting in a 404 (Not Found) response.\u003c/p\u003e\u003cp\u003eThe required steps for this are:\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/watcher/current/installing-watcher.html\"\u003eInstalling\u003c/a\u003e Watcher\u003c/li\u003e\u003cli\u003eCreating a new notification on Watcher that every minute reports the number of events that have a 404 response status\u003c/li\u003e\u003cli\u003eStart Logstash with the HTTP input\u003c/li\u003e\u003cli\u003eSend data to Elasticsearch and watch updates on Logstash\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eHere we go!\u003c/p\u003e\u003ch4\u003e1. Installing Watcher\u003c/h4\u003e\u003cpre class=\"prettyprint\"\u003ecd elasticsearch-1.5.2\u003cbr /\u003ebin/plugin -i elasticsearch/watcher/latest\u003cbr /\u003ebin/plugin -i elasticsearch/license/latest\u003cbr /\u003ebin/elasticsearch # restart the server\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003e2. Creating a watch\u003c/h4\u003e\u003cp\u003eThe Watcher plugin for elasticsearch provides an API to create and manipulate scheduled tasks, or \"watches\". A \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/introduction.html#_watcher_concepts\"\u003eWatch\u003c/a\u003e will query the data in the elasticsearch cluster according to its schedule, look for certain scenarios (like the presence of an error event) and execute actions. Examples of \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/customizing-actions.html\"\u003eactions\u003c/a\u003e are sending an email, writing a document to an index, calling an outside HTTP endpoint, and more..\u003c/p\u003e\u003cp\u003eFor this test, I created a simple watch that:\u003c/p\u003e\u003cul\u003e\u003cli\u003eevery minute\u003c/li\u003e\u003cli\u003ecounts number of HTTP requests that resulted in a 404\u003c/li\u003e\u003cli\u003eposts result to http://localhost:8080\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThis is the resulting JSON document I need to send to Watcher:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e \"trigger\" : {\u003cbr /\u003e \"schedule\" : { \"cron\" : \"0 0/1 * * * ?\" }\u003cbr /\u003e },\u003cbr /\u003e \"input\" : {\u003cbr /\u003e \"search\" : {\u003cbr /\u003e \"request\" : {\u003cbr /\u003e \"indices\" : [\u003cbr /\u003e \"logstash*\"\u003cbr /\u003e ],\u003cbr /\u003e \"body\" : {\u003cbr /\u003e \"query\" : {\u003cbr /\u003e \"term\": { \"response\": 404 }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"actions\" : {\u003cbr /\u003e \"my_webhook\" : {\u003cbr /\u003e \"webhook\" : {\u003cbr /\u003e \"auth\" : {\u003cbr /\u003e \"basic\" : {\u003cbr /\u003e \"username\" : \"guest\",\u003cbr /\u003e \"password\" : \"guest\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"method\" : \"POST\",\u003cbr /\u003e \"host\" : \"127.0.0.1\",\u003cbr /\u003e \"port\" : 8080,\u003cbr /\u003e \"path\": \"/{{ctx.watch_id}}\",\u003cbr /\u003e \"body\" : \"{{ctx.payload.hits.total}}\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eTo install this watch you need to create it in Elasticsearch by executing a PUT request:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ecurl -XPUT 'http://localhost:9200/_watcher/watch/my-watch' -d @create_webhook.json\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003e3. Logstash setup\u003c/h4\u003e\u003cpre class=\"prettyprint\"\u003ewget http://download.elastic.co/logstash/logstash/logstash-1.5.2.tar.gz\u003cbr /\u003etar -zxf logstash-1.5.2.tar.gz\u003cbr /\u003ecd logstash-1.5.2\u003cbr /\u003ebin/logstash -e \"input { http { } } output { stdout { codec =\u0026gt; rubydebug} }\"\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003e4. Results\u003c/h4\u003e\u003cp\u003eAfter launching an ingestion process in another terminal, Logstash starts receiving 1 notification per minute in the form of a HTTP POST:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e% bin/logstash -e \"input { http { } } output { stdout { codec =\u0026gt; rubydebug} }\" \u003cbr /\u003eLogstash startup completed\u003cbr /\u003e{\u003cbr /\u003e \"message\" =\u0026gt; \"330\",\u003cbr /\u003e \"@version\" =\u0026gt; \"1\",\u003cbr /\u003e \"@timestamp\" =\u0026gt; \"2015-06-02T12:53:00.037Z\",\u003cbr /\u003e \"headers\" =\u0026gt; {\u003cbr /\u003e \"content_type\" =\u0026gt; \"application/x-www-form-urlencoded\",\u003cbr /\u003e \"request_method\" =\u0026gt; \"POST\",\u003cbr /\u003e \"request_path\" =\u0026gt; \"/my-watch\",\u003cbr /\u003e \"request_uri\" =\u0026gt; \"/my-watch?\",\u003cbr /\u003e \"http_version\" =\u0026gt; \"HTTP/1.1\",\u003cbr /\u003e \"http_authorization\" =\u0026gt; \"Basic Z3Vlc3Q6Z3Vlc3Q=\",\u003cbr /\u003e \"http_accept_charset\" =\u0026gt; \"UTF-8\",\u003cbr /\u003e \"http_cache_control\" =\u0026gt; \"no-cache\",\u003cbr /\u003e \"http_pragma\" =\u0026gt; \"no-cache\",\u003cbr /\u003e \"http_user_agent\" =\u0026gt; \"Java/1.8.0_20\",\u003cbr /\u003e \"http_host\" =\u0026gt; \"127.0.0.1:8080\",\u003cbr /\u003e \"http_accept\" =\u0026gt; \"text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2\",\u003cbr /\u003e \"http_connection\" =\u0026gt; \"keep-alive\",\u003cbr /\u003e \"content_length\" =\u0026gt; \"12\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e{\u003cbr /\u003e \"message\" =\u0026gt; \"3103\",\u003cbr /\u003e \"@version\" =\u0026gt; \"1\",\u003cbr /\u003e \"@timestamp\" =\u0026gt; \"2015-06-02T12:54:00.030Z\",\u003cbr /\u003e \"headers\" =\u0026gt; {\u003cbr /\u003e \"content_type\" =\u0026gt; \"application/x-www-form-urlencoded\",\u003cbr /\u003e \"request_method\" =\u0026gt; \"POST\",\u003cbr /\u003e \"request_path\" =\u0026gt; \"/my-watch\",\u003cbr /\u003e \"request_uri\" =\u0026gt; \"/my-watch?\",\u003cbr /\u003e \"http_version\" =\u0026gt; \"HTTP/1.1\",\u003cbr /\u003e \"http_authorization\" =\u0026gt; \"Basic Z3Vlc3Q6Z3Vlc3Q=\",\u003cbr /\u003e \"http_accept_charset\" =\u0026gt; \"UTF-8\",\u003cbr /\u003e \"http_cache_control\" =\u0026gt; \"no-cache\",\u003cbr /\u003e \"http_pragma\" =\u0026gt; \"no-cache\",\u003cbr /\u003e \"http_user_agent\" =\u0026gt; \"Java/1.8.0_20\",\u003cbr /\u003e \"http_host\" =\u0026gt; \"127.0.0.1:8080\",\u003cbr /\u003e \"http_accept\" =\u0026gt; \"text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2\",\u003cbr /\u003e \"http_connection\" =\u0026gt; \"keep-alive\",\u003cbr /\u003e \"content_length\" =\u0026gt; \"13\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e{\u003cbr /\u003e \"message\" =\u0026gt; \"6071\",\u003cbr /\u003e \"@version\" =\u0026gt; \"1\",\u003cbr /\u003e \"@timestamp\" =\u0026gt; \"2015-06-02T12:55:00.031Z\",\u003cbr /\u003e \"headers\" =\u0026gt; {\u003cbr /\u003e \"content_type\" =\u0026gt; \"application/x-www-form-urlencoded\",\u003cbr /\u003e \"request_method\" =\u0026gt; \"POST\",\u003cbr /\u003e \"request_path\" =\u0026gt; \"/my-watch\",\u003cbr /\u003e \"request_uri\" =\u0026gt; \"/my-watch?\",\u003cbr /\u003e \"http_version\" =\u0026gt; \"HTTP/1.1\",\u003cbr /\u003e \"http_authorization\" =\u0026gt; \"Basic Z3Vlc3Q6Z3Vlc3Q=\",\u003cbr /\u003e \"http_accept_charset\" =\u0026gt; \"UTF-8\",\u003cbr /\u003e \"http_cache_control\" =\u0026gt; \"no-cache\",\u003cbr /\u003e \"http_pragma\" =\u0026gt; \"no-cache\",\u003cbr /\u003e \"http_user_agent\" =\u0026gt; \"Java/1.8.0_20\",\u003cbr /\u003e \"http_host\" =\u0026gt; \"127.0.0.1:8080\",\u003cbr /\u003e \"http_accept\" =\u0026gt; \"text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2\",\u003cbr /\u003e \"http_connection\" =\u0026gt; \"keep-alive\",\u003cbr /\u003e \"content_length\" =\u0026gt; \"13\"\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eA more complex example\u003c/h3\u003e\u003cp\u003eNow that we know how to trigger notification events from Watcher, we can leverage the plugin ecosystem in Logstash to escalate notifications depending in a certain criteria. This following config will:\u003c/p\u003e\u003cul\u003e\u003cli\u003econtinuously update the number of 404 requests in \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-outputs-statsd.html\"\u003estatsd\u003c/a\u003e\u003c/li\u003e\u003cli\u003eif the count reaches 10000 then send a message to \u003ca href=\"https://www.elastic.co/guide/en/watcher/2.4/configuring-hipchat.html\"\u003eHipChat\u003c/a\u003e, or\u003c/li\u003e\u003cli\u003eif reaches 40000, notify \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-outputs-pagerduty.html\"\u003ePagerDuty\u003c/a\u003e.\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003einput {\u003cbr /\u003e http { }\u003cbr /\u003e}\u003cbr /\u003efilter {\u003cbr /\u003e if [headers][request_path] == \"/my-watch\" {\u003cbr /\u003e mutate { convert =\u0026gt; [\"message\", \"integer\" ] }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003eoutput {\u003cbr /\u003e if [headers][request_path] == \"/my-watch\" {\u003cbr /\u003e if [message] \u0026gt; 40000 { # way too many, notify pagerduty\u003cbr /\u003e pagerduty {\u003cbr /\u003e description =\u0026gt; \"%{host} - Apache: Very high number of 404\"\u003cbr /\u003e details =\u0026gt; {\u003cbr /\u003e \"timestamp\" =\u0026gt; \"%{@timestamp}\"\u003cbr /\u003e \"message\" =\u0026gt; \"%{message}\"\u003cbr /\u003e }\u003cbr /\u003e service_key =\u0026gt; \"apikeyforlogstashservice\"\u003cbr /\u003e incident_key =\u0026gt; \"logstash/apacheservice\"\u003cbr /\u003e }\u003cbr /\u003e } else if [message] \u0026gt; 10000 { # unusual amount, notify devs in hipchat\u003cbr /\u003e hipchat {\u003cbr /\u003e from =\u0026gt; \"logstash\"\u003cbr /\u003e room_id =\u0026gt; \"dev\"\u003cbr /\u003e token =\u0026gt; \"[api key]\"\u003cbr /\u003e format =\u0026gt; \"Very high number of 404 requests: %{message}\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e # always update count of 404 in statsd\u003cbr /\u003e statsd { gauge =\u0026gt; [ \"http.status.404\", \"%{message}\" ] }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThat's it! Next is an example using GitHub instead of Watcher as the source of notifications.\u003c/p\u003e\u003ch3\u003eReceiving updates from GitHub\u003c/h3\u003e\u003cp\u003eGitHub allows you to receive commit \u003ca href=\"https://help.github.com/articles/receiving-email-notifications-for-pushes-to-a-repository/\"\u003enotifications\u003c/a\u003e, so let's receive those in Logstash through the HTTP input plugin. The steps I needed to accomplish this were:\u003c/p\u003e\u003col\u003e\u003cli\u003eCreating a VM with Logstash and launching an instance with the HTTP input plugin\u003c/li\u003e\u003cli\u003eSetting up the \u003ca href=\"https://help.github.com/articles/receiving-email-notifications-for-pushes-to-a-repository/\"\u003eGitHub webhook\u003c/a\u003e on a repository that will post notifications to the VM\u003c/li\u003e\u003cli\u003eDoing a commit on the repository to see the flow in action!\u003c/li\u003e\u003c/ol\u003e\u003ch4\u003e1. Logstash setup\u003c/h4\u003e\u003cp\u003eI created a VM on Amazon with TCP port 9200 open:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0050381633805b61/67c97b253661f25efecca582/introducing-the-logstash-http-input-plugin-vm-amazon.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003eThen setup and start logstash:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ewget http://download.elastic.co/logstash/logstash/logstash-1.5.2.tar.gz\u003cbr /\u003etar -zxf logstash-1.5.2.tar.gz\u003cbr /\u003ecd logstash-1.5.2\u003cbr /\u003ebin/logstash -e \"input { http { port =\u0026gt; 9200 } } output { stdout { codec =\u0026gt; rubydebug} }\"\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWhy a VM? I needed Logstash to be accessible from the internet, and exposing a port on my home network router was complicated..\u003c/p\u003e\u003ch4\u003e2. Github webhook setup\u003c/h4\u003e\u003cp\u003eI created a GitHub repo under my account called \u003ca href=\"https://github.com/jsvd/test-repo\"\u003etest-repo\u003c/a\u003e. There I set up a webhook and pointed it at the VM:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4ebe72cf822118aa/67c97b61959e4ed286e4d954/introducing-the-logstash-http-input-plugin-webhook.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003ch4\u003e3. Generating events\u003c/h4\u003e\u003cp\u003eLet's generate 1 commit so GitHub will notify Logstash:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003egit clone https://github.com/jsvd/test-repo\u003cbr /\u003ecd test-repo\u003cbr /\u003eecho 1 \u0026gt;\u0026gt; a\u003cbr /\u003egit commit -a -m \"new commit\"\u003cbr /\u003egit push\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003e4. Result\u003c/h4\u003e\u003cp\u003eOn the VM, Logstash received (output shortened for readability, \u003ca href=\"https://gist.github.com/jsvd/bef30e62b0b9bd599615\"\u003efull output here\u003c/a\u003e):\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e$ bin/logstash -e \"input { http { port =\u0026gt; 9200 } } output { stdout { codec =\u0026gt; rubydebug} }\"\u003cbr /\u003e{\u003cbr /\u003e \"ref\" =\u0026gt; \"refs/heads/master\",\u003cbr /\u003e \"before\" =\u0026gt; \"22dc008b4a9a612ff3fc55b02fabd551a582e271\",\u003cbr /\u003e \"after\" =\u0026gt; \"9046cd06b307dec789248a72c9f36630decc037a\",\u003cbr /\u003e \"created\" =\u0026gt; false,\u003cbr /\u003e \"deleted\" =\u0026gt; false,\u003cbr /\u003e \"forced\" =\u0026gt; false,\u003cbr /\u003e \"base_ref\" =\u0026gt; nil,\u003cbr /\u003e \"compare\" =\u0026gt; \"https://github.com/jsvd/test-repo/compare/22dc008b4a9a...9046cd06b307\",\u003cbr /\u003e \"commits\" =\u0026gt; [\u003cbr /\u003e [0] {\u003cbr /\u003e \"id\" =\u0026gt; \"9046cd06b307dec789248a72c9f36630decc037a\",\u003cbr /\u003e \"distinct\" =\u0026gt; true,\u003cbr /\u003e \"message\" =\u0026gt; \"new commit\",\u003cbr /\u003e \"timestamp\" =\u0026gt; \"2015-06-02T14:58:14+01:00\",\u003cbr /\u003e \"url\" =\u0026gt; \"https://github.com/jsvd/test-repo/commit/9046cd06b307dec789248a72c9f36630decc037a\",\u003cbr /\u003e \"author\" =\u0026gt; {\u003cbr /\u003e \"name\" =\u0026gt; \"Joao Duarte\",\u003cbr /\u003e \"email\" =\u0026gt; \"XXXXXXXXXXXX\",\u003cbr /\u003e \"username\" =\u0026gt; \"jsvd\"\u003cbr /\u003e },\u003cbr /\u003e \"committer\" =\u0026gt; {\u003cbr /\u003e \"name\" =\u0026gt; \"Joao Duarte\",\u003cbr /\u003e \"email\" =\u0026gt; \"XXXXXXXXXXXX\",\u003cbr /\u003e \"username\" =\u0026gt; \"jsvd\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ],\u003cbr /\u003e \"head_commit\" =\u0026gt; {\u003cbr /\u003e \"id\" =\u0026gt; \"9046cd06b307dec789248a72c9f36630decc037a\",\u003cbr /\u003e \"distinct\" =\u0026gt; true,\u003cbr /\u003e \"message\" =\u0026gt; \"new commit\",\u003cbr /\u003e \"timestamp\" =\u0026gt; \"2015-06-02T14:58:14+01:00\",\u003cbr /\u003e \"url\" =\u0026gt; \"https://github.com/jsvd/test-repo/commit/9046cd06b307dec789248a72c9f36630decc037a\",\u003cbr /\u003e \"author\" =\u0026gt; {\u003cbr /\u003e \"name\" =\u0026gt; \"Joao Duarte\",\u003cbr /\u003e \"email\" =\u0026gt; \"XXXXXXXXXXXX\",\u003cbr /\u003e \"username\" =\u0026gt; \"jsvd\"\u003cbr /\u003e },\u003cbr /\u003e \"committer\" =\u0026gt; {\u003cbr /\u003e \"name\" =\u0026gt; \"Joao Duarte\",\u003cbr /\u003e \"email\" =\u0026gt; \"XXXXXXXXXXXX\",\u003cbr /\u003e \"username\" =\u0026gt; \"jsvd\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003eThis input plugin opens up an incredible amount of possible scenarios since a lot of applications use webhooks and know how to export data using HTTP requests.\u003c/p\u003e\u003cp\u003eI'm already thinking of a ton of ideas where I can leverage this plugin, how are you going to use it?\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T12:12:48.786Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","publish_date":"2015-07-09T13:38:51.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":null,"title":"Introducing the Logstash HTTP input plugin","title_l10n":"Introducing the Logstash HTTP input plugin","updated_at":"2025-03-10T12:33:32.016Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/introducing-logstash-input-http-plugin","publish_details":{"time":"2025-03-10T12:33:35.378Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc420a7ae65dd972e","_version":29,"locale":"en-us","ACL":{},"abstract_l10n":"Provide your SOC team with a unified, pre-built SIEM detection rule experience.","author":["blt038f616a5d7994a3","blt1ed10b221239128a","bltc1a27bf09861513f"],"body_l10n":"\u003cp\u003eWith the release of \u003ca href=\"https://www.elastic.co/blog/elastic-security-7-6-0-released\" target=\"_self\"\u003eElastic Security 7.6\u003c/a\u003e, we've announced our creation of\u0026nbsp;a modern detection engine that provides SOC teams with a unified SIEM rule experience through\u0026nbsp;Elastic SIEM detections.\u0026nbsp;The\u0026nbsp;detection engine draws from a purpose-built set of Elasticsearch analytics engines\u0026nbsp;and runs on a new distributed execution platform in Kibana.\u0026nbsp;In this post, we provide a brief overview of the flow of detections in Elastic SIEM and discuss the new UI and backend features that help these detections work seamlessly for our users.\u003c/p\u003e\n\u003cp\u003eBefore we jump into detections, a quick note: if you are ready to try the SIEM app, check out our \u003ca href=\"https://www.elastic.co/blog/elastic-siem-for-small-business-and-home-1-getting-started\" target=\"_self\"\u003eSIEM for small businesses and at home\u0026nbsp;blog series\u003c/a\u003e. The series\u0026nbsp;covers getting set up on the cloud with our free \u003ca href=\"https://www.elastic.co/products/elasticsearch/service\" target=\"_self\"\u003etrial of Elasticsearch Service\u003c/a\u003e, using Beats to securely collect and stream data from your systems to the SIEM, and more. (It’s far easier than you would think!) We also offer a \u003ca href=\"https://www.elastic.co/guide/en/siem/guide/7.6/install-siem.html\" target=\"_self\"\u003egetting started guide\u0026nbsp;for hybrid deployments\u003c/a\u003e.\u003c/p\u003e\n\u003ch2\u003eUI workflow for signal management\u003c/h2\u003e\n\u003cp\u003eThe bread and butter of Elastic SIEM detections\u0026nbsp;are signals, which are Elasticsearch documents created when a signal detection rule's conditions are satisfied. In the simplest case, one signal document is created for each event matching the query defined in the rule. The signal document contains a copy of the fields from the matching document, and is kept in a separate signals index. The original events are not modified when a signal is created.\u003c/p\u003e\n\u003cp\u003eSignals are surfaced in the SIEM app. When a practitioner first sees a new signal, it is in an open state. After analysis and determining the next steps, the practitioner changes it to a closed state. All of these changes can be managed in the Detections view in the SIEM app.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt828482255973f9c4/5e669becc39d9b5d36c3d124/siem_detections_histogram_sorted_risk_score.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eThe signal\u0026nbsp;count histogram shows open signals and enables quick comparisons across key attributes:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eScore, severity, type, name, or MITRE ATT\u0026amp;CK™ tactic name\u0026nbsp;\u003c/li\u003e\n \u003cli\u003eSource or destination IP address\u003c/li\u003e\n \u003cli\u003eEvent action or \u003ca href=\"https://www.elastic.co/guide/en/ecs/1.4/ecs-allowed-values-event-category.html\" target=\"_self\"\u003ecategory\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003eHost or user name\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltebdcb7c7316b8bb7/5e669d474e03445d41facf35/siem_detections_signal_histogram.gif\" /\u003e\u003c/p\u003e\n\u003cp\u003eInvestigating signals in the Timeline is the next step:\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4e14d9a0b0452596/5e669de00b333d44908d0e40/siem_detections_signals_timeline_view_in_timeline_with_id.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eIf you did not specify a timeline template when\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/siem/guide/7.6/rules-ui-create.html#create-rule-ui\" target=\"_self\"\u003ecreating a rule\u003c/a\u003e, the Timeline is populated with a signal document. If you did specify a timeline template, the Timeline will be populated with what the user saved, speeding up investigations for certain types of rules.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4ddf4e3f1426a1a2/5e669dad6d9a795c6ecf10d4/siem_detections_signals_timeline_view_in_timeline_with_template.png\" /\u003e\u003c/p\u003e\n\u003cp\u003ePractitioners can view alerts from external alerting systems, such as\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/introducing-elastic-endpoint-security\" target=\"_self\"\u003eElastic Endpoint Security\u003c/a\u003e, Suricata, or Zeek, in the dedicated `External alerts` tab. Many organizations also implement rules generating signals for high-value external alerts so that they can benefit from the enhanced investigative workflow for signals.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt761ddf4865c94d43/5e669f706a12c038f19ec035/siem_detections_external_alerts_tab.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eOnce a signal or set of signals has been investigated to the analyst’s satisfaction, they can close the signals individually or in bulk. Signals can also be reopened, if necessary. We’re working on ways to automate the closing of signals in future releases.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltda92d9e0aceff2b7/5e669fc018b328555145dd83/siem_detections_signals_close_signal_hover.png\" /\u003e\u003c/p\u003e\n\u003ch2\u003eUI workflow for creation of rules\u003c/h2\u003e\n\u003cp\u003eFor signals to start showing up, detections need rules to run! Creating a rule for\u0026nbsp;SIEM detections is simple and straightforward. It comes down to three basic steps:\u003c/p\u003e\n\u003cp\u003e1) Generate the query to be used each time the rule runs. This query can be Lucene syntax, \u003ca href=\"https://www.elastic.co/guide/en/kibana/7.6/kuery-query.html\" target=\"_self\"\u003eKQL\u003c/a\u003e, a saved search, or the query can be imported from a saved timeline (with many more options for rule queries currently under development for future release):\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1a892690f4dc394/5e66a04363a80b5c6fc5a1bf/siem_detections_create_rule_custom_query.png\" /\u003e\u003c/p\u003e\n\u003cp\u003e2) Add some information describing the rule (title, description, etc.):\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt950d4ac86c74a8c6/5e66a09b6d9a795c6ecf10da/siem_detections_create_about_rule.png\" /\u003e\u003c/p\u003e\n\u003cp\u003e3) Schedule the interval the rule should run at and any\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/siem/guide/7.6/rules-ui-create.html#create-rule-ui\" target=\"_self\"\u003eadditional look-back time\u003c/a\u003e\u0026nbsp;for sanity checks. We generally recommend some amount of look-back time to allow for delays that may occur in a given user's ingestion pipeline. We also recommend some look-back time as the rules are not guaranteed to run exactly at their scheduled interval and therefore might be delayed between runs. An overloaded task manager worker queue or insufficient \u003ca href=\"https://www.elastic.co/blog/advanced-tuning-finding-and-fixing-slow-elasticsearch-queries\" target=\"_self\"\u003ecomputing resources\u003c/a\u003e\u0026nbsp;can cause these delays.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7175ab0a1e156ec1/5e66a0cc329c6c3829894d56/siem_detections_create_rule_schedule.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eThese three things are the basic components that make up a detections rule. We also provide settings to classify this rule according to MITRE ATT\u0026amp;CK tactics and techniques, as well as\u0026nbsp;links to additional references.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltadabd5e1e1fac099/5e66a11f63a80b5c6fc5a1c5/siem_detections_create_advanced_settings_blank_timeline.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eUsers can also perform actions on existing rules individually or in bulk, such as duplicate (for customizations), deactivate, export, and delete rules. We also have a guide for more information on\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/siem/guide/7.6/rules-ui-create.html\" target=\"_self\"\u003egeneral rule management\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd9fc55f1c8850ce7/5e66a1540b333d44908d0e52/siem_detections_rules_deactivate_selected.png\" /\u003e\u003c/p\u003e\n\u003ch2\u003ePrebuilt rules\u003c/h2\u003e\n\u003cp\u003eRules can be difficult to develop and are time intensive to test. Because of this, detections started with 92 prebuilt rules developed by the Intelligence \u0026amp; Analytics team at Elastic Security\u0026nbsp;and\u0026nbsp;have\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/securing-our-own-endpoints-with-elastic-security\" target=\"_self\"\u003ebeen used extensively at Elastic in a production environment\u003c/a\u003e. New\u0026nbsp;rules that respond to the latest critical threats are\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/playing-defense-against-gamaredon-group\" target=\"_self\"\u003econtinuously being developed\u003c/a\u003e. Getting them loaded and ready to run is as easy as a click of a button! You can read more about using and tuning the pre-built rules\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/siem/guide/7.6/prebuilt-rules.html\" target=\"_self\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte20be84367f8f502/5e66a17e18b328555145dd8b/siem_detections_signal_rules_load_prebuilt_rules_screen.png\" /\u003e\u003c/p\u003e\n\u003ch2\u003eDetections implementation details\u003c/h2\u003e\n\u003cp\u003eShortly after\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/alerting-in-the-elastic-stack\" target=\"_self\"\u003eAlerting in the Elastic Stack\u003c/a\u003e\u0026nbsp;made its way into Kibana to provide support for alerts as first-class entities, Elastic SIEM utilized alerting for the foundation of detections. Behind the UI, detections uses an\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/siem/guide/7.6/rule-api-overview.html\" target=\"_self\"\u003eAPI\u003c/a\u003e\u0026nbsp;layered on top of the\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/legacy/plugins/alerting/README.md\" target=\"_self\"\u003eAlerting API\u003c/a\u003e. The SIEM detections API brings convenience, workflows (such as opening and closing signals), the domain specifics of security (such as MITRE ATT\u0026amp;CK identification), and\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/kibana/7.6/kuery-query.html\" target=\"_self\"\u003eKQL Support\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfc2a6219ce8d8cd5/5e66a1a418b328555145dd91/siem_detections_rules_define_rule_saved_query.png\" /\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eRules run behind the scenes by creating an API Key\u0026nbsp;and then utilizing that API Key to make requests on behalf of the user using\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.6/search-request-body.html#request-body-search-search-after\" target=\"_self\"\u003esearch after\u003c/a\u003e\u0026nbsp;to find matching events and\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.6/docs-bulk.html\" target=\"_self\"\u003ebulk create\u003c/a\u003e\u0026nbsp;to copy the information from the event into a signal document in the signal index. A signal is made up of the rule details and the details of the original event document matched by the rule.\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfc78b7cafe4517d9/5e66a1bf0b6249392652ce1d/siem_detections_api_key_screen.png\" /\u003e\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003eIf more than 100 matching documents are found in a single rule execution, only the last 100 matches —\u0026nbsp;by descending `@timestamp` sort order —\u0026nbsp;are copied to the signals index. The signals index is automatically created per Kibana space the first time you visit the signal detection rules page. The index name format is `.siem-signals-\u003cspace name\u003e`. For the default space or, if spaces are not enabled, the signals index name will be `.siem-signals-default`. Each signals index created for each space has an index\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/legacy/plugins/siem/server/lib/detection_engine/routes/index/signals_policy.json\" target=\"_self\"\u003elifecycle management\u003c/a\u003e\u0026nbsp;setting of 50 GB or 30 days before it rolls over.\u0026nbsp; Signals'\u0026nbsp;indices\u0026nbsp;are retained indefinitely.\u003c/space\u003e\n\u003c/p\u003e\n\u003cp\u003eThe mapping of the SIEM signals index is a combination of\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/legacy/plugins/siem/server/lib/detection_engine/routes/index/ecs_mapping.json\" target=\"_self\"\u003eElastic Common Schema (ECS)\u003c/a\u003e\u0026nbsp;and a custom mapping of our definition of what a\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/legacy/plugins/siem/server/lib/detection_engine/routes/index/signals_mapping.json\" target=\"_self\"\u003esignal is\u003c/a\u003e. When a matching document is detected from the rule query, it will copy the fields over from the source indices\u0026nbsp;and the resulting signal fields will be searchable if the fields in the source document are compliant with\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/introducing-the-elastic-common-schema\" target=\"_self\"\u003eECS\u003c/a\u003e. If the fields from the source indices\u0026nbsp;are not part of ECS, they will still be stored in the signal’s `_source` and viewable within Timeline and other parts of the application. However, they will not be searchable.\u003c/p\u003e\n\u003ch2\u003eScalability\u003c/h2\u003e\n\u003cp\u003eThe detections UI is built atop the newly developed\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/legacy/plugins/alerting/README.md\" target=\"_self\"\u003eKibana Alerting framework\u003c/a\u003e\u0026nbsp;and the Kibana task manager. These two provide horizontal and vertical scaling capabilities, allowing flexibility that best suits whatever hardware is available at the time. Kibana\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/plugins/task_manager/server/README.md\" target=\"_self\"\u003etask manager workers\u003c/a\u003e\u0026nbsp;can be increased in number to take advantage of vertical scaling, or can be replicated across separate Kibana instances and scaled horizontally.\u003c/p\u003e\n\u003cp\u003eWhen multiple Kibana instances are running, the task managers will coordinate across the wire to balance the tasks across the instances. By updating the number of max_workers inside of the kibana.yml file from it’s default of 10, you can vertically scale up or down to appropriately allocate resources more efficiently per Kibana node.\u003c/p\u003e\n\u003ch2\u003eSignal deduplication\u003c/h2\u003e\n\u003cp\u003eWhen a rule is running, it generates signals based on the events that it finds that match the rule’s query. Sometimes duplicate signals can be created either by overlapping queries in separate rules or by a rule running twice in a row and catching the same signal due to a long additional look-back time. To prevent a duplicate signal from appearing in the signals table, we identify signals based on the index the source event is from, the source event’s document id, the source event’s version number, and the running rule’s id. By hashing on\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/blob/v7.6.0/x-pack/legacy/plugins/siem/server/lib/detection_engine/signals/utils.ts#L11-L19\" target=\"_self\"\u003ethese properties\u003c/a\u003e, we ensure only unique signals are added to the signals index.\u003c/p\u003e\n\u003ch2\u003eErrors\u003c/h2\u003e\n\u003cp\u003eSometimes errors will appear due to a syntax error in a rule’s query or some other issue during a rule’s execution period. We bubble these up in the errors tab on the rule details page. We plan to expand the visibility of rule execution information and general rule monitoring in the future.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltffc432e29392e581/5e66a1de0b6249392652ce23/siem_detections_error_string.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eAnd here we can see the failure history, which displays the last five errors that occurred during rule execution:\u003cbr /\u003e\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt92ce96e19860407b/5e66a1f6c39d9b5d36c3d13e/siem_detections_failure_history_tab.png\" /\u003e\u003c/p\u003e\n\u003ch2\u003eSIEM detections of tomorrow\u003c/h2\u003e\n\u003cp\u003eThe most exciting part of working on and releasing this Elastic SIEM detections beta is the early and continuous community feedback on the\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/c/siem\" target=\"_self\"\u003eElastic SIEM discussion forum\u003c/a\u003e\u0026nbsp;and our\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/issues?utf8=%E2%9C%93\u0026q=is%3Aopen+is%3Aissue+label%3ATeam%3ASIEM+detection\" target=\"_self\"\u003eopen feature tracking list\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eWe have big plans for making\u0026nbsp;detections even more powerful. Expanding rule queries to include aggregations, machine learning jobs, and EQL are just a few of them. If you think of something that is a great \u003ca href=\"https://www.elastic.co/what-is/siem\" target=\"_self\"\u003esecurity use case\u003c/a\u003e or want to ask a question or two about what is happening, please join us!\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-03-09T19:31:15.474Z","created_by":"bltfc54a1df6ec15d9e","disclaimer":["blta06a046e82d04210"],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"bltdbdbc176deb1b2e1","ACL":{},"content_type":"image/jpeg","created_at":"2020-01-24T21:38:05.636Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"182706","filename":"blog-banner-gears-steel.jpg","parent_uid":null,"tags":[],"title":"blog-banner-gears-steel.jpg","updated_at":"2020-11-25T18:39:33.932Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T18:39:36.297Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdbdbc176deb1b2e1/5fbea4e53cdbef7187cea40c/blog-banner-gears-steel.jpg"},"markdown_l10n":"","publish_date":"2020-03-11T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic SIEM detection engine with pre-built rules and analytics.","seo_description_l10n":"The Elastic SIEM detection Engine with pre-built rules and analytics provides SOC teams with a unified SIEM rule experience that draws from a purpose-built set of Elasticsearch analytics engines, and runs on a new distributed execution platform in Kibana.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltc84da5736cde2608","ACL":{},"content_type":"image/jpeg","created_at":"2020-01-24T21:38:05.708Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"130591","filename":"blog-thumb-gears-steel.jpg","parent_uid":null,"tags":[],"title":"blog-thumb-gears-steel.jpg","updated_at":"2020-11-25T18:39:15.354Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T18:39:27.266Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc84da5736cde2608/5fbea4d33cdbef7187cea40a/blog-thumb-gears-steel.jpg"},"title":"Elastic SIEM detections","title_l10n":"Elastic SIEM detections","updated_at":"2025-03-10T12:31:22.842Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-siem-detections","publish_details":{"time":"2025-03-10T12:31:26.503Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5db56c6fc846de6b","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt6122634fb71c4152"],"body_l10n":"\u003ch2\u003eStrap on your goggles...\u003c/h2\u003e\n\u003cp\u003eIn the movie \u003ca href=\"http://www.imdb.com/title/tt0093773/\" target=\"_blank\"\u003ePredator\u003c/a\u003e, the alien has a sophisticated thermal imaging system that allows him to single out his human prey by observing the heat differences between their bodies and the environment in which they are hiding.\u003c/p\u003e\n\u003cp\u003eThe new \u003ca href=\"/guide/en/elasticsearch/reference/current/search-aggregations-bucket-significantterms-aggregation.html\" target=\"_self\"\u003esignificant terms aggregation\u003c/a\u003e behaves like the Predator's vision, identifying interesting things that stand out from the background (not by observing heat differentials but by observing term frequency differentials). Terms of interest in a result set stand out clearly like the heat signal of a monosyllabic Austrian bodybuilder sweating behind a fern.\u003c/p\u003e\n\u003ch2\u003eRevealing the uncommonly common\u003c/h2\u003e\n\u003cp\u003eThe trick behind the significant terms aggregation is in spotting terms that are significantly more common in a result set than they are in the general background of data from which they are drawn. These are what you might call uncommonly common terms and examples of the real insights these can give include:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eThe words \"coil spring\" are revealed as a significant cause of the reported failures on a particular car model \u003cem\u003e(the most popular word in the car's fault reports is \"the\" but that is hardly significant)\u003c/em\u003e\u003c/li\u003e\n \u003cli\u003ePeople who liked the movie \"Talladega Nights\" also liked the movie \"Blades of Glory\" \u003cem\u003e(their most commonly-liked movie is \"Shawshank redemption\" but that is irrelevant as this is generally popular)\u003c/em\u003e\u003c/li\u003e\n \u003cli\u003eCredit cards reporting losses are shown to share a historical payment to an obscure website \u003cem\u003e(the most common payee in their transactions is typically not significant - big merchants such as iTunes are equally popular with non-compromised credit cards)\u003c/em\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eIn the following sections we present worked examples of just some of the useful applications of this new feature:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"#geo\" title=\"Geographic anomalies\" target=\"_self\"\u003eDetecting geographic anomalies\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"#fault\" title=\"Root cause analysis in fault reports\" target=\"_self\"\u003eRoot cause analysis in fault reports\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"#classifier\" title=\"Training classifiers\" target=\"_self\"\u003eTraining classifiers\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"#miscat\" title=\"Revealing badly categorised content\" target=\"_self\"\u003eRevealing badly categorised content\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"#credit\" title=\"Common point of compromise analysis\" target=\"_self\"\u003eDetecting credit card fraud\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"#recommend\" title=\"movie recommendations\" target=\"_self\"\u003eMaking product recommendations\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003chr /\u003e\n\u003ch3\u003e\u003ca id=\"geo\" href=\"#geo\" target=\"_self\"\u003e\u003c/a\u003eUse case: Geographic anomalies\u003c/h3\u003e\n\u003cp\u003eThis XKCD cartoon neatly summarises the issue with the typical forms of mapping analysis:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt18f33e2627493ce3/67c97a622c963b0bd61bdb1d/heatmap.png\" /\u003e\u003c/p\u003e\n\u003cp\u003eThe significant terms aggregation can help overcome this problem.\u003c/p\u003e\n\u003cp\u003eLet's first take all of the UK crime data for last year and break the reports down into geographic areas using the \u003ca href=\"/guide/en/elasticsearch/reference/current/search-aggregations-bucket-geohashgrid-aggregation.html\" target=\"_self\"\u003egeohash_grid aggregation\u003c/a\u003e and with a simple \u003ca href=\"/guide/en/elasticsearch/reference/current/search-aggregations-bucket-terms-aggregation.html\" target=\"_self\"\u003eterms aggregation\u003c/a\u003e like this:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/ukcrimes/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"aggregations\" : {\u003cbr /\u003e \"map\" : {\u003cbr /\u003e \"geohash_grid\" : { \u003cbr /\u003e \"field\":\"location\",\u003cbr /\u003e \"precision\":5,\u003cbr /\u003e },\u003cbr /\u003e \"aggregations\":{\u003cbr /\u003e \"most_popular_crime_type\":{\"terms\":{ \"field\" : \"crime_type\", \"size\" : 1}}\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eWe end up with an XKCD-style map effectively showing us a population distribution and the less-than useful insight that anti-social behaviour is the most popular crime type \u003cem\u003eeverywhere\u003c/em\u003e:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d8f43e9adc538716645/download?uid=blt849973d79f2b1af5?uid=blt849973d79f2b1af5\" width=\"300\" height=\"223\" style=\"width: 300;height: 223;\" /\u003e\u003c/p\u003e\n\u003cp\u003eHowever, if we use the significant_terms aggregation we can get a more interesting insight into the data and reveal the unusual occurrences of crime in each location:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/ukcrimes/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"aggregations\" : {\u003cbr /\u003e \"map\" : {\u003cbr /\u003e \"geohash_grid\" : { \u003cbr /\u003e \"field\":\"location\",\u003cbr /\u003e \"precision\":5,\u003cbr /\u003e },\u003cbr /\u003e \"aggregations\":{\u003cbr /\u003e \"weirdCrimes\":{\"significant_terms\":{\"field\" : \"crime_type\", \"size\":1}}\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eIf we show only the top scoring areas, we move away from focusing purely on the most populated areas and the most common crime and begin to find the anomalies in our data:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d8fd8edd48f769389db/download?uid=blt18d47854cf55f7dd?uid=blt18d47854cf55f7dd\" width=\"300\" height=\"208\" style=\"width: 300;height: 208;\" /\u003e\u003c/p\u003e\n\u003cp\u003eHere, we see a relatively remote area with a disproportionately large number of Possession of Weapon crimes. If we zoom in, we can see from the sky why this is the case - this is the location of Stansted airport where passengers are routinely searched as they transit through the airport. Other spots around the country have their own curiosities - the fields where drug-related crimes peak as part of annual music festivals, the year-round bicycle thefts from university towns like Cambridge, and the prisons where it would seem a crime conducted against a fellow criminal is not really a crime so is registered with the type Other.\u003c/p\u003e\n\u003ch3\u003e\u003ca id=\"fault\" href=\"#fault\" target=\"_self\"\u003e\u003c/a\u003eUse case: Root cause analysis\u003c/h3\u003e\n\u003cp\u003eThe \u003ca href=\"http://www.nhtsa.gov/\" target=\"_self\"\u003eNational Highway Traffic Safety Association\u003c/a\u003e maintains a database of car fault reports and, like many systems for fault reports, there is a product ID and a free-text description with each report. Using the significant_terms aggregation you can identify the common reasons for product failures by examining the free-text descriptions of each product.\u003c/p\u003e\n\u003ch4\u003eExample query\u003c/h4\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/nhtsa/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"aggregations\" : {\u003cbr /\u003e \"car_model\":{\u003cbr /\u003e \"terms\":{\"field\" : \"car_model\", \"size\" : 20},\u003cbr /\u003e \"aggregations\":{\u003cbr /\u003e \"reasons_for_failure\" : {\u003cbr /\u003e \"significant_terms\":{\"field\" : \"fault_description\", \"size\" : 20} \u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003ch4\u003eExample results\u003c/h4\u003e\u003cpre class=\"prettyprint noescape\"\u003e\"aggregations\": {\u003cbr /\u003e \"car_model\": {\u003cbr /\u003e \"buckets\": [\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"Taurus\",\u003cbr /\u003e \"doc_count\": 3967,\u003cbr /\u003e \"reasons_for_failure\": {\u003cbr /\u003e \"doc_count\": 3967,\u003cbr /\u003e \"buckets\": [\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"coil\",\u003cbr /\u003e \"doc_count\": 250,\u003cbr /\u003e \"score\": 0.544,\u003cbr /\u003e \"bg_count\": 1115\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"mounts\",\u003cbr /\u003e \"doc_count\": 178,\u003cbr /\u003e \"score\": 0.3969,\u003cbr /\u003e \"bg_count\": 777\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"spring\",\u003cbr /\u003e \"doc_count\": 261,\u003cbr /\u003e \"score\": 0.3668,\u003cbr /\u003e \"bg_count\": 1706\u003cbr /\u003e },\u003cbr /\u003e ...\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eTo make these keywords a more readable explanation of failures, a useful technique is to display the keywords in context (a technique commonly known by the acronym KWIC). This involves taking the keywords from the results shown above and constructing a terms query with highlighting. Here is an example javascript function to do just this:\u003c/p\u003e\n\u003ch4\u003eFetching \"keywords in context\" examples\u003c/h4\u003e\u003cpre class=\"prettyprint noescape\"\u003efunction getKWIC(car_model,buckets){ \u003cbr /\u003e var shouldClauses=[];\u003cbr /\u003e for(var i=0;i \u0026lt; buckets.length; i++)\u003cbr /\u003e {\u003cbr /\u003e //Get at least the top 5 significant keywords\u003cbr /\u003e if((shouldClauses.length \u0026gt; 5) || (buckets[i].score \u0026lt; 2)) {\u003cbr /\u003e shouldClauses.push( {\"term\" : { \"fault_description\" : { \u003cbr /\u003e \"value\" : buckets[i].key, \u003cbr /\u003e \"boost\" : buckets[i].score \u003cbr /\u003e } }});\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e var kwicQuery={\u003cbr /\u003e \"query\" :\u003cbr /\u003e {\u003cbr /\u003e \"bool\" : {\u003cbr /\u003e \"should\":shouldClauses,\u003cbr /\u003e \"must\":[{\"terms\":{\"car_model\":[car_model]}}]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\":30,\u003cbr /\u003e \"highlight\": {\u003cbr /\u003e \"pre_tags\" : [\"\u0026lt;span style=\"background-color: #f7f7a7;\"\u0026gt;\"],\u003cbr /\u003e \"post_tags\" : [\"\u0026lt;/span\u0026gt;\"], \u003cbr /\u003e \"fields\": {\"fault_description\":{\"matched_fields\": [\"fault_description\"] }}\u003cbr /\u003e } \u003cbr /\u003e };\u003cbr /\u003e dataForServer=JSON.stringify(kwicQuery);\u003cbr /\u003e var kwResultHtml=\"\";\u003cbr /\u003e $.ajax({\u003cbr /\u003e type: \"POST\",\u003cbr /\u003e url: '/nhtsa/_search',\u003cbr /\u003e dataType: 'json',\u003cbr /\u003e async: false,\u003cbr /\u003e data: dataForServer,\u003cbr /\u003e success: function (data) {\u003cbr /\u003e var hits=data.hits.hits;\u003cbr /\u003e for (h in hits){\u003cbr /\u003e //format results as html table rows \u003cbr /\u003e var snippets=hits[h].highlight.fault_description;\u003cbr /\u003e kwResultHtml+=\"\u0026lt;tr\u0026gt;\u0026lt;td\u0026gt;\";\u003cbr /\u003e for(snippet in snippets){\u003cbr /\u003e kwResultHtml+=\"\u0026lt;span\u0026gt;\"+snippets[snippet]+\"...\u0026lt;/span\u0026gt;\";\u003cbr /\u003e }\u003cbr /\u003e kwResultHtml+=\"\u0026lt;/td\u0026gt;\u0026lt;/tr\u0026gt;\";\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e });\u003cbr /\u003e return kwResultHtml; \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe results of our root-cause analysis might then appear as follows:\u003c/p\u003e\n\u003cp\u003e. AS A RESULT OF THE SITUATION, I INCURRED EXPENSE TO REPLACE THE \u003cstrong\u003eCOIL SPRINGS\u003c/strong\u003e, STRUTS AND UPPER \u003cstrong\u003eMOUNTS\u003c/strong\u003e; PLUS...AS I WAS BACKING UP THE FRONT DRIVERS SIDE \u003cstrong\u003eCOIL SPRING\u003c/strong\u003e BROKE, PUNCTURING THE TIRE. IT IS THE SAME... 2001 FORD TAURUS (48302 ODOMETER) REAR \u003cstrong\u003eCOIL SPRING\u003c/strong\u003e BROKE REPLACED \u003cstrong\u003eSPRINGS\u003c/strong\u003e WITH REAR STRUTS. *NM... WAS BROKE. FORD HAS HAD A HISTORY OF \u003cstrong\u003eCOIL SPRING\u003c/strong\u003e FAILURES AND SHOULD ISSUE A RECALL ON ALL \u003cstrong\u003eSPRINGS\u003c/strong\u003e. *TR...WHILE GETTING A SCHEDULED OIL CHANGE, THE DEALER NOTICED MY \u003cstrong\u003eCOIL SPRING\u003c/strong\u003e ON THE REAR PASSENGER SIDE... TRECALL CAMPAIGN 04V332000 CONCERNING \u003cstrong\u003eCOIL SPRINGS\u003c/strong\u003e. THE \u003cstrong\u003eCOIL SPRING\u003c/strong\u003e BROKE IN THREE PLACES. IT BLEW...\u003c/p\u003e\n\u003chr /\u003e\n\u003ch3\u003e\u003ca id=\"classifier\" href=\"#classifier\" target=\"_self\"\u003e\u003c/a\u003eUse case: Training a classifier\u003c/h3\u003e\n\u003cp\u003eMany systems classify documents by assigning tag or category fields. Classifying documents can be a tedious manual process and so in this example we will train a classifier to automatically spot keywords in new documents that suggest a suitable category.\u003c/p\u003e\n\u003cp\u003eBy using The Movie Database (TMDB) data we can search for movies that contain the term vampire in their description:\u003c/p\u003e\n\u003ch4\u003eExample query\u003c/h4\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/tmdb/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\" : {\u003cbr /\u003e \"match\" : {\"overview\":\"vampire\" }\u003cbr /\u003e },\u003cbr /\u003e \"aggregations\" : {\u003cbr /\u003e \"keywords\" : {\"significant_terms\" : {\"field\" : \"overview\"}}\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003ch4\u003eExample results\u003c/h4\u003e\u003cpre class=\"prettyprint noescape\"\u003e \"aggregations\": {\u003cbr /\u003e \"keywords\": {\u003cbr /\u003e \"doc_count\": 437,\u003cbr /\u003e \"buckets\": [\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"vampire\",\u003cbr /\u003e \"doc_count\": 437,\u003cbr /\u003e \"score\": 3790.9405,\u003cbr /\u003e \"bg_count\": 437\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"helsing\",\u003cbr /\u003e \"doc_count\": 17,\u003cbr /\u003e \"score\": 113.9480,\u003cbr /\u003e \"bg_count\": 22\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"dracula\",\u003cbr /\u003e \"doc_count\": 33,\u003cbr /\u003e \"score\": 98.3565,\u003cbr /\u003e \"bg_count\": 96\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"harker\",\u003cbr /\u003e \"doc_count\": 7,\u003cbr /\u003e \"score\": 42.5023,\u003cbr /\u003e \"bg_count\": 10\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"undead\",\u003cbr /\u003e \"doc_count\": 15,\u003cbr /\u003e \"score\": 31.9717,\u003cbr /\u003e \"bg_count\": 61\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"buffy\",\u003cbr /\u003e \"doc_count\": 4,\u003cbr /\u003e \"score\": 23.130071721937412,\u003cbr /\u003e \"bg_count\": 6\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"bloodsucking\",\u003cbr /\u003e \"doc_count\": 4,\u003cbr /\u003e \"score\": 19.8244,\u003cbr /\u003e \"bg_count\": 7\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"fangs\",\u003cbr /\u003e \"doc_count\": 5,\u003cbr /\u003e \"score\": 19.7094,\u003cbr /\u003e \"bg_count\": 11\u003cbr /\u003e }\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThese keywords could then be cherry-picked and added to a new terms query that is registered using the Percolate API to help identify new movies that should potentially be tagged as vampire movies. Note that much of the guesswork in selecting useful keywords is avoided.\u003c/p\u003e\n\u003chr /\u003e\n\u003ch3\u003e\u003ca id=\"miscat\" href=\"#miscat\" target=\"_self\"\u003e\u003c/a\u003eUse case: Finding mis-categorized content using the Like this but not this pattern\u003c/h3\u003e\n\u003cp\u003eFor systems that have a lot of pre-categorized content it can be useful to identify where the database maintainers have failed to categorize existing content properly. In this example we will start by looking at Reuters news articles tagged with the topic \"acquisitions\" and use significant_terms aggregation to learn some relevant keywords e.g.:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/reuters/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\" : {\u003cbr /\u003e \"match\" : {\"topics\":\"acq\" }\u003cbr /\u003e },\u003cbr /\u003e \"aggregations\" : {\u003cbr /\u003e \"keywords\":{\"significant_terms\" : {\"field\" : \"body\", \"size\" : 20}},\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe keywords that are revealed as relevant to the \"acquisition\" news category are as follows:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"aggregations\": {\u003cbr /\u003e \"keywords\": {\u003cbr /\u003e \"doc_count\": 2340,\u003cbr /\u003e \"buckets\": [\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"acquisition\",\u003cbr /\u003e \"doc_count\": 469,\u003cbr /\u003e \"score\": 0.973,\u003cbr /\u003e \"bg_count\": 704\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"acquire\",\u003cbr /\u003e \"doc_count\": 395,\u003cbr /\u003e \"score\": 0.927,\u003cbr /\u003e \"bg_count\": 535\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"shares\",\u003cbr /\u003e \"doc_count\": 842,\u003cbr /\u003e \"score\": 0.820,\u003cbr /\u003e \"bg_count\": 2258\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"stake\",\u003cbr /\u003e \"doc_count\": 363,\u003cbr /\u003e \"score\": 0.780,\u003cbr /\u003e \"bg_count\": 529\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"inc\",\u003cbr /\u003e \"doc_count\": 1220,\u003cbr /\u003e \"score\": 0.752,\u003cbr /\u003e \"bg_count\": 4390\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"merger\",\u003cbr /\u003e \"doc_count\": 298,\u003cbr /\u003e \"score\": 0.674,\u003cbr /\u003e \"bg_count\": 416\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key\": \"acquired\",\u003cbr /\u003e \"doc_count\": 327,\u003cbr /\u003e \"score\": 0.643,\u003cbr /\u003e \"bg_count\": 513\u003cbr /\u003e },\u003cbr /\u003e ...\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe next step is to construct a like this but not this query by:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eadding the significant category keywords to a should terms query and\u003c/li\u003e\n \u003cli\u003eadding the original category field criteria to a mustNot clause\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eas follows:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/reuters/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\" : {\u003cbr /\u003e \"bool\": {\u003cbr /\u003e \"mustNot\":[ {\"match\" : {\"topics\" : \"acq\" } }],\u003cbr /\u003e \"should\":[\u003cbr /\u003e { \"terms\":{\"body\":[\"acquisition\", \"acquire\",\"shares\",\"stake\",\"inc\",\"merger\"...]}}\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe results of this query are a relevance-ranked list of news articles that should have been tagged as articles about acquisitions but have somehow slipped through the net. Below is an example match which failed to record the \"acq\" topic tag:\u003c/p\u003e\n\u003cp\u003eSalomon Brothers \u003cstrong\u003eInc\u003c/strong\u003e said it has \u003cstrong\u003eacquired\u003c/strong\u003e 21,978 convertible subordinated debentures of Harcourt... Brace Jovanovich Inc, which it says could be converted into 21,978,000 common \u003cstrong\u003eshares\u003c/strong\u003e. In a filing... them into stock. Salomon said it would have a 35.8 pct \u003cstrong\u003estake\u003c/strong\u003e in Harcourt, based on 39.4 mln \u003cstrong\u003eshares\u003c/strong\u003e.... Harcourt has said that Salomon and Mutual Shares Corp, a New York investment firm, hold a combined... some or all of their current \u003cstrong\u003estake\u003c/strong\u003e in the market or in negotiated deals,\u003c/p\u003e\n\u003chr /\u003e\n\u003ch3\u003e\u003ca id=\"credit\" href=\"#credit\" target=\"_self\"\u003e\u003c/a\u003eUse case: detecting credit card fraud\u003c/h3\u003e\n\u003cp\u003eWhen a bank's customers phone the bank and complain that they have noticed unusual transactions on their account, the bank undertakes a common point of compromise analysis. The unusual transactions that were spotted might be payment for a hotel in a country the customer has not visited but this payment is the \u003cem\u003esymptom\u003c/em\u003e of the root problem and not the \u003cem\u003ecause\u003c/em\u003e. Somewhere in a customer's credit card history of payments a merchant has deliberately stolen their details (perhaps a card-skimmer installed in a petrol station) or accidentally lost their details (perhaps a website had its database hacked). Either way, this merchant represents a common point of compromise where potentially many card details were obtained and sold on the black market. For the bank, the objective is to identify the problem merchant (or merchants) and identify their customers who may be about to experience fraudulent payments.\u003c/p\u003e\n\u003cp\u003eThe starting query would be to take a selection of compromised cards and look at all of their transactions in the last few months and summarise who they've been paying:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003ecurl -XGET \"http://localhost:9200/transactions/_search\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"terms\": {\"payer\" : [59492167, 203701197, 365610456,....]}\u003cbr /\u003e },\u003cbr /\u003e \"aggregations\" : {\u003cbr /\u003e \"payees\":{ \u003cbr /\u003e \"significant_terms\":{\"field\":\"payee\"},\u003cbr /\u003e \"aggregations\":{ \"payers\":{\"terms\":{\"field\":\"payer\"}}}\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe set of payers in the query represent our unhappy customers and so the set of transactions that it matches will include a mix of happy payments but crucially the unhappy payments that led to their predicament. By using the significant_terms aggregation on the payee field, we can focus in on the merchants that appear in this fishy set of transactions disproportionately more than they would in a random sampling of predominantly happy customers. This helps tune out the popular merchants that are likely to be common with any random sample of customers and focus in on the likely points of compromise. For the selected fishy merchants, we have a child aggregation of payers so we can see just how many of our unhappy customers traded with this merchant and can visualize this as a social network diagram.\u003c/p\u003e\n\u003cp\u003eIf we only use the simpler terms aggregation we tend to focus on the popular merchants in our set and the culprit is not clear as it is hidden among the commonly common payees:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d900342dfd738265e83/download?uid=blt638dd473d7ac21f4?uid=blt638dd473d7ac21f4\" width=\"300\" height=\"222\" style=\"width: 300;height: 222;\" /\u003e\u003c/p\u003e\n\u003cp\u003eHowever when we use the significant_terms aggregation our focus shifts to the uncommonly common connector and the extra stats in the results mean we can report on what percentage of that merchant's transactions lie in this fishy set of transactions:\u003c/p\u003e\n\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d900342dfd738265e90/download?uid=blt7f823a24787177db?uid=blt7f823a24787177db\" width=\"300\" height=\"247\" style=\"width: 300;height: 247;\" /\u003e\u003c/p\u003e\n\u003cp\u003eNow the culprit is much clearer. The fishiest merchant here has 13 of his total of 72 transactions in the problem set, making him our strongest suggestion. The merchant with 3 out of his 19 transactions present in this set may appear simply because the bad merchant's customers are also likely to shop at this neighbouring store. Overlaying geographic and temporal information helps these sorts of investigations and is easy to do by adding extra child aggregations into our queries.\u003c/p\u003e\n\u003chr /\u003e\n\u003ch3\u003e\u003ca id=\"recommend\" href=\"#recommend\" target=\"_self\"\u003e\u003c/a\u003eUse case: product recommendation\u003c/h3\u003e\n\u003cp\u003eProduct recommendations are often driven by a \"people who liked this also like..\" type analysis of purchase data. The most powerful recommendation engines use complex algorithms and examine many features of the data but here we will use the significant_terms aggregation to provide reasonable results quickly using a simple set of data. In this example, we will use the publicly available \"MovieLens\" data. The first task is to index the user ratings data so that there is a single JSON document for each user listing all of the movie IDs they have liked (ratings of 4 stars or over):\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"user\": 6785,\u003cbr /\u003e \"movie\": [12, 3245, 4657, 7567, 55276, 56367...] \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eNow for any given movie we can query for all the people who liked that movie and summarise what other movies they like:\u003c/p\u003e\u003cpre class=\"prettyprint noescape\"\u003e{\u003cbr /\u003e \"query\": { \"terms\": { \"movie\": [46970]} },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"significantMovies\": { \"significant_terms\": { \"field\": \"movie\" }},\u003cbr /\u003e \"popularMovies\": { \"terms\": { \"field\": \"movie\" }}\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\n\u003cp\u003eThe above query first selects all fans of the movie with the ID 46970 (Talladega Nights) and then summarises their favourite movies using the terms aggregation to identify the most popular movies and the \u0026lt;code\u0026gt;significant_terms aggregation to find the more insightful \"uncommonly common\" movies.\u003c/p\u003e\n\u003cp\u003eThe results are as follows:\u003c/p\u003e\n\u003ctable class=\"legal-table\"\u003e\n \u003ctbody\u003e\n \u003ctr\u003e\n \u003cth colspan=\"2\"\u003e\n \u003cp\u003e\u003cbr /\u003eTop 3 movies liked by users who like \"Talladega Nights: The Ballad of Ricky Bobby\"\u003cbr /\u003e\u003c/p\u003e\n \u003c/th\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003cth\u003e\n \u003cp\u003e\u003cbr /\u003esignificant_terms\u003cbr /\u003e\u003c/p\u003e\n \u003c/th\u003e\n \u003cth\u003e\n \u003cp\u003e\u003cbr /\u003e(Popular) terms\u003cbr /\u003e\u003c/p\u003e\n \u003c/th\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cbr /\u003eBlades of Glory\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cbr /\u003eMatrix, The\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cbr /\u003eAnchorman: The Legend of Ron Burgundy\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cbr /\u003eShawshank Redemption, The\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003c/tr\u003e\n \u003ctr\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cbr /\u003eSemi-Pro\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003ctd\u003e\n \u003cp\u003e\u003cbr /\u003ePulp Fiction\u003cbr /\u003e\u003c/p\u003e\n \u003c/td\u003e\n \u003c/tr\u003e\n \u003c/tbody\u003e\n\u003c/table\u003e\n\u003cp\u003eThe terms aggregation looks to focus on movies that are universally popular (and arguably irrelevant) while the \u0026lt;code\u0026gt;significant_terms aggregation has focused in on movies that are particularly more popular with the fans of \"Talladega Nights\". The top 3 suggestions shown here all feature the star of Talladega Nights, Will Ferrell.\u003c/p\u003e\n\u003chr /\u003e\n\u003ch2\u003eConclusion\u003c/h2\u003e\n\u003cp\u003eThis post illustrates a sample of what can be done with significant_terms. I am excited to see what new insights people will gain from exploring their data using this new perspective. Let us know how you are using it and help us improve the analytic capabilities. Happy hunting!\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:19:32.394Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","publish_date":"2014-04-15T17:00:45.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"The new significant terms aggregation identifies interesting things that stand out from the background (not by observing heat differentials but by observing term frequency differentials).","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":null,"title":"Significant Terms Aggregation","title_l10n":"Significant Terms Aggregation","updated_at":"2025-03-10T12:29:06.387Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/significant-terms-aggregation","publish_details":{"time":"2025-03-10T12:29:14.670Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte3d29c6692d02d82","_version":25,"locale":"en-us","ACL":{},"abstract_l10n":"The Elastic Advent Calendar 2020 is now complete. Here's a recap of the final few days, as well as a summary from all 25 days.","author":["blt5b8d46bc024f3a05"],"body_l10n":"\u003cp\u003eWow, it's finally here! After 25 fantastic articles we've reached the end of the 2020 Elastic Advent series.\u003c/p\u003e\u003cp\u003eWe've covered\u0026nbsp;ECS, Synthetics, Monitoring Tekton tasks and pipelines, OpenTelemetry, log correlation with APM, Index patterns and tradeoffs for observability, Rank features, New data types, Phonetic search, Korean language search,\u0026nbsp;Elasticsearch Rust Client, Searchable snapshots, ESM, Workplace Search, App Search, Data import/export, Data visualisation, Kibana Lens, Kibana Maps, Free trainings, Preparing your certification, Preparing interviews,\u0026nbsp;and so much more. In the topics we've spoken in Chinese, English, French, German, Korean, Russian and Spanish.\u003c/p\u003e\u003cp\u003eWe hope you have enjoyed the posts, topics and information shared in them from our engineers. Here's a recap of the final few days, as well as a summary from all 25 days.\u003c/p\u003e\u003ch2\u003eThe 25 days of Elastic\u003c/h2\u003e\u003cp\u003e\u003cstrong\u003eDec 1 [english] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/254953\"\u003e\u003cstrong\u003eSynthetics: proactive problem detection\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\u0026nbsp;(Elasticsearch and Python - tools for a data scientist), by Ahil PonArul\u003c/strong\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eElastic is excited to introduce synthetic monitoring to our Uptime solution. This allows for more advanced uptime checks beyond basic pings. Combined with our new User Experience UI it also enables proactive problem detection.\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eThis is a step by step example of how to set Synthetics up, as well as integrate it with APM.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 2 [german] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-2nd-2020-de-aufgemerkt-zugehort-bessere-suchresultate-mit-phonetischer-suche/257045\"\u003e\u003cstrong\u003eAufgemerkt \u0026amp; zugehört! Bessere Suchresultate mit phonetischer Suche\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Alexander Reelsen\u0026nbsp;\u003c/strong\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003ePhonetische Suche ist eine Möglichkeit, nach ähnlichen klingenden Termen zu suchen, indem ein phonetischer Hash im invertierten Index gespeichert wird. In diesem Artikel schauen wir uns einige unterschiedliche phonetische Algorithmen in Elasticsearch an und wie diese die eigene Suche verbessern können.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 3 [english] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-3rd-2020-en-cross-version-elasticsearch-data-migration-with-esm/256516\"\u003e\u003cstrong\u003eCross version Elasticsearch data migration with ESM\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Medcl Zeng\u003c/strong\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eI heard that you are using Elasticsearch, that's great as, you know for search, it is the best choice, and it is evolving very fast. There are so many new and nice features coming up or already that i guess you can't wait to upgrade to the latest version, right?\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eThis blog post will explain how ESM could help to do your data migration.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 4 [english] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-4th-2020-en-validate-elastic-common-schema-ecs-fields-using-security-detection-rules/254805\"\u003e\u003cstrong\u003eValidate Elastic Common Schema (ECS) fields using Security Detection Rules\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Eric Beahan\u0026nbsp;\u003c/strong\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eThe Elastic Common Schema (ECS) provides an open, consistent model for structuring your data in the Elastic Stack. By normalizing data to a single common model, you can uniformly examine your data using interactive search, visualizations, and automated analysis.\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eElastic provides hundreds of\u0026nbsp;\u003ca href=\"https://www.elastic.co/integrations\"\u003eintegrations\u003c/a\u003e\u0026nbsp;that are ECS-compliant out-of-the-box, but ECS also allows you to normalize custom data sources. Normalizing a custom source can be an iterative and sometimes time-intensive process. However, we can use the Elastic Security Detection Engine to help quickly identify ECS non-compliance in our events.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 5 [français/english] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-5th-2020-fr-recherchez-tous-vos-documents-nimporte-ou-avec-workplace-search/254739\"\u003e\u003cstrong\u003eRecherchez tous vos documents, n'importe où, avec Workplace Search\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\u0026nbsp;|\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-5th-2020-en-searching-anything-anywhere-with-workplace-search/254740\"\u003e\u003cstrong\u003eSearching anything, anywhere with Workplace Search\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by David Pilato\u003c/strong\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eYou already know that\u0026nbsp;\u003ca href=\"https://www.elastic.co/workplace-search\"\u003eWorkplace Search\u003c/a\u003e\u0026nbsp;comes with\u0026nbsp;\u003ca href=\"https://www.elastic.co/workplace-search/content-sources\"\u003ea lot of connectors\u003c/a\u003e\u0026nbsp;which help you connect your enterprise document data sources and have a federated way to search across all that information. But what if a specific data source is not supported yet?\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eThis post will cover how you can create a custom data source to send your own data. We'll also cover an example of how this was used in the community\u0026nbsp;\u003ca href=\"https://fscrawler.readthedocs.io/\"\u003eFSCrawler project\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 6 [spanish/english] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-6th-es-cargando-datos-de-osm-en-elasticsearch/255082\"\u003e\u003cstrong\u003eCargando datos de OSM en Elasticsearch\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\u0026nbsp;|\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-6th-2020-en-uploading-data-from-osm-into-elasticsearch/255059\"\u003e\u003cstrong\u003eUploading data from OSM into Elasticsearch\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Jorge Sanz\u0026nbsp;\u003c/strong\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eOne of the most common issues for Elastic stack users that deal with geospatial data is how to upload geospatial data users is how to ingest data in Elasticsearch. You can check\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/kibana/7.10/import-geospatial-data.html\"\u003eKibana 7.10 docs\u003c/a\u003e\u0026nbsp;to learn about different ways to achieve this. Some time ago we wrote a\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/how-to-ingest-geospatial-data-into-elasticsearch-with-gdal\"\u003eblog post\u003c/a\u003e\u0026nbsp;that introduces ogr2ogr, a tool from the GDAL library that helps on ingesting data from dozens of formats into Elasticsearch.\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eIn this Advent Calendar post, we develop an example of this workflow using Docker to leverage the last version of the GDAL tool and OpenStreetMap as a popular source of Open Data Points of Interests.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 7 [français/english] —\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/dec-7th-2020-fr-utilisez-rally-comme-outil-dimport-export-de-donnees/256863\"\u003e\u003cstrong\u003eUtilisez Rally comme outil d'import/export de données\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\u0026nbsp;|\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/257820\"\u003e\u003cstrong\u003eUsing Rally as a data import/export tool\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Laurent Huet\u003c/strong\u003e\u003cspan style=\"background-color: initial;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eThis post will show you how you can use\u0026nbsp;\u003ca href=\"https://github.com/elastic/rally\"\u003eRally\u003c/a\u003e\u0026nbsp;to export data from one cluster to another.\u0026nbsp;The idea is to extract the whole data from one or more indices in a (big) flat file and reuse it later to easily import in another cluster.\u003c/p\u003e\u003cp rel=\"padding-left: 15pt;\" style=\"padding-left: 15pt;\"\u003eRally helps you do\u0026nbsp;that very easily.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 8 [russian/english]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/256527\"\u003eRank features для поиска в e-commerce\u003c/a\u003e\u0026nbsp;|\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/256525\"\u003eRank features for e-commerce search\u003c/a\u003e, by Mayya Sharipova\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eModern e-commerce search is expected to be fast, relevant and provide an opportunity for promoting certain results. This article demonstrates how\u0026nbsp;\u003cspan style=\"font-family: monospace;\"\u003erank_feature\u003c/span\u003e\u0026nbsp;and\u0026nbsp;\u003cspan style=\"font-family: monospace;\"\u003erank_features\u003c/span\u003e\u0026nbsp;types of elasticsearch can help in this goal. We will use an example of a commercial search engine for a shoes shop.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 9 [english]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/257377\"\u003eDon't let your Christmas tree Rust in a corner\u003c/a\u003e, by Sylvain Wallez\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eChristmas trees are part of what makes this time of the year so unique and brings sparkles in the eyes of children and adults alike. But what do you do with the tree once the party’s over? The best is to make sure it’s recycled and used as compost or firewood. Now how do you find where to dispose of your tree so that it will be correctly taken care of?\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eI live in Toulouse in the south of France, and the local authorities have not only set up a lot of collection places, but also published\u0026nbsp;\u003ca href=\"https://data.toulouse-metropole.fr/explore/dataset/collecte-des-sapins-de-noel/information/\"\u003etheir location as open data\u003c/a\u003e. It’s even listed on\u0026nbsp;\u003ca href=\"https://www.europeandataportal.eu/data/datasets/5dfc48ccdee7e752c18c3ede\"\u003eEuropean\u003c/a\u003e\u0026nbsp;open data. There’s a treasure trove of information there!\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eLet’s use this information to build a nice map in Kibana, and use the Rust client for Elasticsearch for that? Why Rust? Because it’s a great language that is growing in popularity, and this is an opportunity to experiment!\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 10 [spanish/english]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/dec-10th-2020-es-las-12-mejores-caracteristicas-de-mapas-desde-ga/256368\"\u003eLas 12 mejores características de Mapas desde GA\u003c/a\u003e\u0026nbsp;|\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/dec-10th-2020-es-las-12-mejores-caracteristicas-de-mapas-desde-ga/256368\"\u003eTop 12 new features in Maps since GA\u003c/a\u003e, by Nathan Reese\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eMaps was released as generally available (GA) in Kibana 7.3. Reaching production-ready is not the final destination, but just another stop on a long journey. Each Kibana point release includes so many incredible features that it’s hard to keep up with them all. So, as 2020 comes to an end, let's look back and revisit some of the most impactful features since going to GA.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 11 [english]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/dec-11th-2020-en-this-holiday-season-learn-new-elastic-skills/257072\"\u003eThis holiday season, learn new Elastic skills\u003c/a\u003e, by Pablo Musa\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eElastic has a lot of different products across multiple solutions. We make it as easy as possible for our users to benefit from our solutions, but it is still hard to master so many topics. To address that, Elastic invests a lot in creating the best possible content. And even though we create them in many formats, such as docs, blogs, webinars, ElasticON presentations, and training, it can still be daunting to learn so many different concepts. In this blog we will help you make the most of your holiday season by learning new skills.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 12 [spanish/english]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/257971\"\u003eTu infraestructura en un mapa\u003c/a\u003e\u0026nbsp;|\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/257864\"\u003eMapping your infrastructure\u003c/a\u003e, by Thomas Neirynck\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eThis post shows how you can use the Elastic Stack to map IoT, Security or Observability data. The data that is collected in these use-cases often do not explicitly contain a latitude or longitude. It is still possible to map this data in Kibana by using a “Term Join”.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 13 [english]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/257827\"\u003eMaking it personal: Tailoring content with signed search keys in App Search\u003c/a\u003e, by Orhan Toy\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eSigned search keys in Elastic App Search give you more control of a user's search experience. You can tailor the experience to show results you know are more relevant to the specific user while also letting you control what data the user can see and search over.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 14 [chinese]\u003c/strong\u003e\u0026nbsp;—\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/t/dec-14th-2020-cn-elastic/257010\"\u003e如何成为一名 Elastic 认证工程师\u003c/a\u003e, by Xiaoguo Liu\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e对 Elastic 认证的类别,培训及认证流程做了详细的介绍。针对中国地区的工程师如何应对 Elastic 认证做了详细的描述。\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 15 [english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258087\"\u003e\u003cstrong\u003ePreparing for an Elasticsearch Interview\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Aravind Putrevu\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eElasticsearch is the most popularly used data store for building a Search Engine, Centralized Logging, Observability, or Threat Hunting use cases.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eThat also means Elasticsearch is omnipresent in many organizations.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eIn this post, we'll see what are some important topics that you need to prepare for an Elasticsearch interview.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 16 [french/english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258847\"\u003e\u003cstrong\u003eMonitorer les tâches et pipelines Tekton avec Elastic Observability\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e | \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/257567\"\u003e\u003cstrong\u003eMonitoring Tekton Tasks and Pipelines with Elastic Observability\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Maxime Gréau\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eDo you know that Elastic performed 21 releases in 2020?\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eEach time a release is promoted, this is 500+ artifacts published to multiple public places (bucket, Docker registries, Maven Central, Rubygems, and so on) and available on Cloud at the same time. This complex process became a non-event thanks to our Unified Release workflow based on \u003cstrong\u003eTekton Tasks and Pipelines\u003c/strong\u003e and monitored with \u003ca href=\"https://www.elastic.co/observability\"\u003eElastic Observability\u003c/a\u003e.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eThis blog post shows how to run your first Tekton Task, and then how to install and use the Elastic Observability Solution to monitor many Tasks and Pipelines deployed within a cluster.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 17 [korean] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258379\"\u003e\u003cstrong\u003e한글 형태소 분석기 파헤치기\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Jongmin Kim\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eElasticsearch 에서는 Elastic 에서 공식으로 제공하는 한글 형태소 분석기인 nori 를 사용할 수 있습니다. 한글은 띄어쓰기가 없는 복합어가 대다수이기 때문에 의도하지 않은 대로 분석이 되는 경우가 많아 nori 를 사용하기 위해서는 목적에 맞는 사용자 사전을 등록해야 할 때가 많습니다.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 18 [english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/257788\"\u003e\u003cstrong\u003eSet up searchable snapshots in ECK\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Idan Moyal\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eSearchable snapshots, recently released as BETA in Elasticsearch 7.10, let you reduce your operating costs by using snapshots for resiliency rather than maintaining replica shards within a cluster.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eIn this blog we’ll demonstrate how to create a hot-cold topology using Elastic Cloud on Kubernetes (ECK). For the cold tier we will mount a snapshot using the new searchable snapshots API. The demonstration is carried out on Google Kubernetes Engine (GKE) and can easily be adjusted to other Kubernetes environments.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 19 [english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/257279\"\u003e\u003cstrong\u003eOpenTelemetry in Go Applications using Elastic APM\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Ricardo Ferreira\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eDistributed tracing technologies allow developers to virtually glue together disparate services to build a cohesive transaction that can be observed by folks in the operations team. This is super important because the distributed nature of modern cloud-native applications makes it hard for teams responsible for maintaining these applications up-and-running to rapidly perform RCA (Root Cause Analysis) of issues when they happen.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eThough tracing technologies are not necessarily new only in recent years it gained enough traction to become one of the three main pillars of an observability strategy—notably logs, metrics, and distributed tracing.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eTo speed up developer adoption, multiple standards such as \u003ca href=\"https://opentracing.io/\"\u003eOpenTracing\u003c/a\u003e and \u003ca href=\"https://opencensus.io/\"\u003eOpenCensus\u003c/a\u003e have been created throughout the years. However, it didn't make any sense to have multiple standards since this creates more harm than good. For this reason the standard \u003ca href=\"https://opentelemetry.io/\"\u003eOpenTelemetry\u003c/a\u003e was created out of the existing ones to be an observability framework for cloud-native software.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eIn this post, I will walk you through how to instrument applications written in \u003ca href=\"https://golang.org/\"\u003eGo\u003c/a\u003e to emit traces compatible with the OpenTelemetry specification, as well as how to send these traces to \u003ca href=\"https://www.elastic.co/apm\"\u003eElastic APM\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 20 [russian/english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258244\"\u003e\u003cstrong\u003eРазведочный анализ данных с Kibana\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e | \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258243\"\u003e\u003cstrong\u003eExploratory data visualization with Kibana\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Raya Fratkina\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003ePractitioners in the field of data visualizations often talk about 2 types of visualizations: exploratory vs explanatory. To quote Google definitions (the most authoritative source, of course), \"Exploratory data visualizations (EDVs) are the type of visualizations you assemble when you do not have a clue about what information lies within your data.”\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cspan style=\"background-color: initial;\"\u003eElastic stack is a great tool for such exploration since because of the flexible ways you can combine search, filtering, and aggregations to understand your data. In addition, you don't need to go through a costly process of defining a schema before you can start exploring.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 21 [english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258560\"\u003e\u003cstrong\u003eWhen neither logging nor code tracing is enough: Log Correlation with APM\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Emanuil Tolev\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eApplication Performance Monitoring and logging both provide critical insight into your ecosystem. When paired together for context, they can provide vital clues on how to resolve problems with your applications. This post assumes you’re familiar with what an \u003ca href=\"https://www.elastic.co/apm\"\u003eAPM (also known as “code tracing”) system\u003c/a\u003e does, what \u003ca href=\"https://www.elastic.co/log-monitoring\"\u003elog monitoring\u003c/a\u003e is, and the benefits of both. Elastic offers free solutions for both as part of \u003ca href=\"https://www.elastic.co/observability\"\u003eElastic Observability\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 22 [german] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/258155\"\u003e\u003cstrong\u003eIndex-Patterns und ihre Tradeoffs für Logs, Metriken und Traces\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Philipp Krenn\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eIndex patterns in the Elastic Stack for time-series data have been evolving. From single indices to daily ones, over rollovers, to the latest development, data streams. This post looks into each approach’s tradeoffs and how to use them with Beats, Elasticsearch, and Kibana.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 23 [spanish/english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/257209\"\u003e\u003cstrong\u003eNuevas incorporaciones a la familia de tipos keyword: constant_keyword y wildcard\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\u0026nbsp;| \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/257213\"\u003e\u003cstrong\u003eNew additions to the keyword family: constant_keyword and wildcard\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Imma Valls\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eWe’ve recently introduced two additional keyword types, \u003cspan style=\"font-family: monospace;\"\u003ewildcard\u003c/span\u003e and \u003cspan style=\"font-family: monospace;\"\u003econstant_keyword\u003c/span\u003e. In this post, we’ll try to briefly introduce them.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 24 [english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/255099\"\u003e\u003cstrong\u003eNew Kind on the Block, Kibana Lens!\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Rashmi Kulkarni\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eMillions of people already use Kibana for a wide range of purposes, but it was still a challenge for the average business user to quickly learn. Visualizations often require quite a bit of experimentation and several iterations to get the results “just right”. Visualizations in Kibana paired with the speed of Elasticsearch is up to the challenge, but it still requires advance planning or you’ll end up having to redo it a few times.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eThe new kid on the block, Kibana Lens, was designed to change this and we’re here to learn how to take advantage of this capability. So let’s get started! We are excited to announce that with the 7.10 release, Kibana Lens has officially become generally available. Lens is the easiest and most intuitive way to visualize data in Elasticsearch with a simple drag-and-drop interface that lets anyone instantly begin exploring data for insights, regardless of their previous Kibana experience.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDec 25 [english] — \u003c/strong\u003e\u003ca href=\"https://discuss.elastic.co/t/256691\"\u003e\u003cstrong\u003eSanta’s Little Helper - Workplace Search\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e, by Sean Story\u003c/strong\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eYou might have picked up on this from movies: Santa’s operation is pretty high tech.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eIt’s a big job, coordinating a massive workforce of Elves to ensure the timely delivery of billions of presents each year. This year, Santa is particularly excited to make use of Elastic’s Workplace Search for its first Christmas.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003eYou see, Santa and his team are working with a lot of data:\u003c/p\u003e\u003cul\u003e\u003cul\u003e\u003cli\u003eChildren all over the world are sending him letters and emails to let him know what their wish lists are.\u003c/li\u003e\u003cli\u003eHe’s got R\u0026amp;D designing and perfecting thousands of new toys each year.\u003c/li\u003e\u003cli\u003eThe assembly line teams require precise numbers to ensure that the right quantity of each toy gets produced.\u003c/li\u003e\u003cli\u003eHis fulfillment team has a mad scramble at the end to ensure that every single child gets the specific toy they wanted.\u003c/li\u003e\u003cli\u003eThe support desk has to field enormous request volumes on these new toys,\u003cul\u003e\u003cli\u003eFrom parents before the holiday (“Does this toy come with batteries included?”)\u003c/li\u003e\u003cli\u003eFrom children afterwards (“Are there any cheat codes?”).\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/ul\u003e\u003cp style=\"margin-left: 20px;\"\u003eIn years previous, this meant Santa had to hold a lot in his head - remembering how to log in to each of these separate data stores, how to search in them, and how to find the right subject-matter-experts for any given problem. But not this year!\u003c/p\u003e\u003ch2\u003eThank you!\u003c/h2\u003e\u003cp\u003eAll the of the topics will be kept on the\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/c/elastic-community-ecosystem/advent-calendar/61\"\u003eElastic Discuss Forums\u003c/a\u003e\u0026nbsp;so you can refer back to them at any time. And, as these are Discuss topics, you can also continue the conversation with the authors and other community members.\u003c/p\u003e\u003cp\u003eThanks for following this year's series, we hope it’s provided some useful inspiration for your use of the Elastic Stack. If you’d like us to repeat this, if you have ideas for next year or any other feedback, please let us know via\u0026nbsp;\u003ca href=\"https://twitter.com/elastic\"\u003eTwitter (@elastic)\u003c/a\u003e\u0026nbsp;or feel free to create a topic in our\u0026nbsp;\u003ca href=\"https://discuss.elastic.co/c/meta\"\u003eMeta category\u003c/a\u003e\u0026nbsp;with your comments.\u003c/p\u003e\u003cp\u003eWe look forward to building upon it for 2021!\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-12-09T16:34:43.339Z","created_by":"blte00f8f424214b2b071d3000b","disclaimer":[],"full_bleed_image":{"_version":4,"is_dir":false,"uid":"blt50965306ac555f89","ACL":{},"content_type":"image/png","created_at":"2020-11-30T17:49:30.902Z","created_by":"blte00f8f424214b2b071d3000b","description":"","file_size":"64112","filename":"blog-banner-advent-calendar-2020.png","parent_uid":"blta4175f15024ba632","tags":[],"title":"blog-banner-advent-calendar-2020.png","updated_at":"2020-12-02T15:23:27.057Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-02T15:23:33.503Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt50965306ac555f89/5fc7b16ffd99385ff600a8bd/blog-banner-advent-calendar-2020.png"},"markdown_l10n":"","publish_date":"2020-12-25T10:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"The Elastic Advent Calendar 2020 is now complete. Here's a recap of the final few days, as well as a summary from all 25 days.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}},{"title":"Visualizing","label_l10n":"Visualizing","keyword":"visualizing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt365f9ed2d77755c7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:12.101Z","updated_at":"2020-06-17T03:38:12.101Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:12.100Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:48:22.629Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte1906c436045dbef","ACL":{},"created_at":"2020-06-17T03:31:19.243Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"app-search","label_l10n":"App search","tags":[],"title":"App search","updated_at":"2020-07-06T22:20:20.511Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.547Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt3ff56eb3b9c58312","ACL":{},"created_at":"2020-06-17T03:33:18.405Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"business-analytics","label_l10n":"Business analytics","tags":[],"title":"Business analytics","updated_at":"2020-07-06T22:20:18.826Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.556Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt4607298d4fd82c81","ACL":{},"created_at":"2020-06-17T03:31:33.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"workplace-search","label_l10n":"Workplace search","tags":[],"title":"Workplace search","updated_at":"2020-07-06T22:19:56.394Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:53.167Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"blt84f07c69fc4bd896","ACL":{},"content_type":"image/png","created_at":"2020-11-30T18:12:03.681Z","created_by":"blte00f8f424214b2b071d3000b","description":"","file_size":"103335","filename":"blog-thumb-advent-calendar-2020.png","parent_uid":"blta4175f15024ba632","tags":[],"title":"blog-thumb-advent-calendar-2020.png","updated_at":"2020-12-02T15:22:53.210Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-02T15:22:45.943Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt84f07c69fc4bd896/5fc7b14dffb61e50a0fb1c1d/blog-thumb-advent-calendar-2020.png"},"title":"Elastic Advent Calendar, 2020: the full recap!","title_l10n":"Elastic Advent Calendar, 2020: the full recap!","updated_at":"2025-03-10T12:22:24.999Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-advent-calendar-2020-week-four","publish_details":{"time":"2025-03-10T12:22:28.883Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltda9158c9e34505d7","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["bltd275645e7a4890a4","blt096468343d241e0c"],"body_l10n":"\u003cp\u003eHard on the heels of our \u003ca href=\"https://www.elastic.co/blog/master-time-with-kibanas-new-time-series-visual-builder\"\u003efirst time series video tutorial\u003c/a\u003e, Chris Cowan is back with another video show off how powerful and versatile this new UI is. If you'd like to follow along, go ahead and download \u003ca href=\"https://www.elastic.co/downloads/beats/metricbeat\"\u003eMetricbeat\u003c/a\u003e to start ingesting metrics from your systems or services. You'll also want to make sure you have the latest version of \u003ca href=\"https://www.elastic.co/downloads/kibana\"\u003eKibana\u003c/a\u003e installed.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/59513a0a4b6c69cd2af4f1e5/download?uid=bltdf18bc128e3f72ff\" data-sys-asset-uid=\"bltdf18bc128e3f72ff\" alt=\"tsvb2-metric.png\" style=\"background-color: initial;\"/\u003e\u0026nbsp;\u003c/p\u003e\u003cp\u003eIn this video, you will learn to do the following:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eQuickly change visualization types with the same data\u003c/li\u003e\u003cli dir=\"ltr\"\u003eUse the overall functions to aggregate over the total time interval in single metric\u003c/li\u003e\u003cli dir=\"ltr\"\u003eTake advantage of the data formatter easily switch between data types\u003c/li\u003e\u003cli dir=\"ltr\"\u003eConditionally style a metric visualization based on the most recent value of your time series data\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eReady to dive in? Check out the video tutorial below.\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg style=\"width: 100%;margin: auto;display: block;\" class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/4vZEBRZ33apj1j1hqXKJCP.jpg\" data-uuid=\"4vZEBRZ33apj1j1hqXKJCP\" data-v=\"4\" data-type=\"inline\" width=\"100%\"/\u003e\u003c/div\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBe on the lookout for our next tutorial with the new time series visual builder!\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-18T15:27:05.738Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt6829556ec152d66d","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-15T06:36:24.325Z","updated_at":"2018-10-15T06:36:24.325Z","content_type":"image/png","file_size":"148873","filename":"tsvb2-banner.png","title":"tsvb2-banner.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T15:48:53.720Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6829556ec152d66d/5bc43568128146a006bd7ffe/tsvb2-banner.png"},"markdown_l10n":"","publish_date":"2017-06-26T18:56:08.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Kibana's New Time Series Visual Builder - Part 2","seo_description_l10n":"The second blog post in a series focused on utilizing Kibana's new visual builder for time series data","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt268bac530bbc816c","ACL":{},"_version":2,"content_type":"image/jpeg","created_at":"2018-10-15T06:36:40.789Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"86887","filename":"tsvb2-metric.jpg","is_dir":false,"parent_uid":null,"tags":[],"title":"tsvb2-metric.jpg","updated_at":"2019-12-20T17:19:55.363Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-12-20T17:20:02.725Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt268bac530bbc816c/5dfd02bbba09063e77b60236/tsvb2-metric.jpg"},"title":"Kibana's New Time Series Visual Builder - Part 2","title_l10n":"Kibana's New Time Series Visual Builder - Part 2","updated_at":"2025-03-10T12:20:58.408Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/kibanas-new-time-series-visual-builder-part-2","publish_details":{"time":"2025-03-10T12:21:03.950Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt893f37408794188a","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt8ba74c7c0a468fe7"],"body_l10n":"\u003cp\u003eEarlier this week, an \u003ca href=\"https://issues.apache.org/jira/browse/LOG4J2-1863\"\u003eadvisory\u003c/a\u003e was released detailing an object deserialization security flaw in the way Apache Log4j version 2 processes input data (\u003ca href=\"http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5645\"\u003eCVE-2017-5645\u003c/a\u003e). This flaw would give a remote attacker the ability to execute code of their choosing within the JVM process listening for Log4j events.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eIn a default Logstash install, the \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-log4j.html\"\u003eLog4j plugin\u003c/a\u003e is installed but not enabled. If you aren't explicitly using this plugin in your configuration, you are not affected by this issue.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWhen used in the Logstash pipeline, the Logstash log4j input plugin accepts Log4j version 1 data from remote applications. Often, any client is able to connect to Logstash because the connection offers no authentication. Given the very purpose of Logstash is to be an endpoint for receiving log data for an organization, it may not be practical to firewall the system as a form of protection. It is our expectation that Logstash will be easily reachable in most environments, and will accept whatever data is passed into it.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe currently known exploits for Java object deserialization do not work against default Logstash deployments, but the vulnerability is still present even without a known exploit. We recognize that this doesn’t necessarily mean a Logstash isn’t vulnerable to this flaw, it simply means we’re not aware of a weaponized exploit.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe Elastic Security Team does not believe the log4j input can be made 100% invulnerable \u0026nbsp;given the way it receives log data from arbitrary sources. By its very nature, object deserialization is difficult to secure and may be impossible to secure when parsing remote untrusted data. The general consensus in the security community is that if you must do object deserialization, it should only be done between systems that have a high level of trust. We do not have this level of trust with expected Logstash clients.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eRemediation\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWe have patched the version of Log4j shipped in Logstash against this particular attack using a variant of the patch from the updated version of Apache Log4j. Updates for Logstash will be included in a future release. This will improve the security of the Log4j input, but we continue to have reservations about its security given the prior paragraph.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eExisting Logstash v5.x and v2.4 users can upgrade the log4j input to receive this fix today by doing the following:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre\u003ebin/logstash-plugin update logstash-input-log4j\u003cbr /\u003e\u003c/pre\u003e\u003cpre\u003e% bin/logstash-plugin update logstash-input-log4j\u003cbr /\u003eUpdating logstash-input-log4j\u003cbr /\u003eUpdated logstash-input-log4j 3.0.3 to 3.0.5\u003cbr /\u003e\u003c/pre\u003e\u003ch3 dir=\"ltr\"\u003eDeprecation Notice\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBased on the reasons stated above, we are \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-log4j.html#_deprecation_notice\"\u003edeprecating\u003c/a\u003e the Log4j input. Our recommendation is for current Log4j input users to stop using log4j’s SocketAppender in their applications. For safe transport of log4j logs, users should configure log4j to write logs to disk and use \u003ca href=\"https://www.elastic.co/beats/filebeat\"\u003eFilebeat\u003c/a\u003e to forward to log information to Logstash. Setting up Filebeat to ship your local logs\u0026nbsp;is easy and we've provided migration steps\u0026nbsp;in \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-log4j.html\"\u003ethese\u0026nbsp;docs\u003c/a\u003e. This solution removes object deserialization from being used in an insecure manner. Additionally we have marked the Log4j plugin as deprecated and are going to remove Log4j support in Logstash 6.0.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eElastic would like to thank Marcio Almeida de Macedo of Red Team at Telstra for alerting us of this issue.\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:42:22.529Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt72cb93c2ccbd7da1","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:10:16.462Z","updated_at":"2018-10-11T05:10:16.462Z","content_type":"image/jpeg","file_size":"71338","filename":"blog-logstash-banner.jpg","title":"blog-logstash-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-05T13:08:20.494Z","user":"blt7e7f06f6a2518594"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt72cb93c2ccbd7da1/5bbedb3852d7ede27f815278/blog-logstash-banner.jpg"},"markdown_l10n":"","publish_date":"2017-04-20T15:29:09.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":null,"title":"The future of Log4j input in Logstash","title_l10n":"The future of Log4j input in Logstash","updated_at":"2025-03-10T12:19:39.829Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/log4j-input-logstash","publish_details":{"time":"2025-03-10T12:19:43.872Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt02181a30a463cdfd","_version":16,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog, learn how you can use Elastic machine learning to create your own ProblemChild framework to detect living-off-the-land (LOtL) activity in Windows process event data.","author":["bltc909a862477f6ea3","blt591d741e6afdef2f","blta95689a58b2be971"],"body_l10n":"\u003cp\u003eWhen it comes to malware attacks, one of the more common techniques is “living off the land” (LOtL). Utilizing standard tools or features that already exist in the target environment allows these attacks to blend into the environment and avoid detection. While these techniques can appear normal in isolation, they start looking suspicious when observed in the parent-child context. This is where the ProblemChild framework can help.\u0026nbsp;\u003c/p\u003e\u003cp\u003eIn this blog, we will talk about how you can use \u003ca href=\"https://www.elastic.co/what-is/elasticsearch-machine-learning\"\u003eElastic machine learning\u003c/a\u003e to create your own ProblemChild framework to detect LOtL activity in Windows process event data (we will be referring to Windows process events as just “events” throughout this blog). We will talk in detail about the following:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eExtracting features from event metadata\u003c/li\u003e\u003cli aria-level=\"1\"\u003eTraining a supervised model to classify events as malicious vs. benign\u003c/li\u003e\u003cli aria-level=\"1\"\u003eUsing the trained model to enrich event data at ingest time\u003c/li\u003e\u003cli aria-level=\"1\"\u003ePicking out the most unusual events for analysts to triage\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eIf you would like to follow along with this blog, we recommend starting a \u003ca href=\"https://cloud.elastic.co/registration\"\u003efree 14-day Elastic trial\u003c/a\u003e. All the supporting materials for this blog are also available in the \u003ca href=\"https://github.com/elastic/examples/tree/master/Machine%20Learning/ProblemChild\"\u003eexamples repository\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eBackground\u003c/h2\u003e\u003cp\u003eLiving-off-the-land binaries (LOLBins) are Microsoft-signed binaries that come pre-installed on the operating system. These binaries can sometimes have unexpected features outside of their core functionality, which attackers can leverage. For example, the task scheduler in Windows, which allows an admin to create, delete, run, and schedule tasks on a local computer. However, attackers may leverage the binary to bypass User Account Control (UAC) and escalate privileges. The use of these binaries complicates the discovery of the attack, since adversary behavior is mixed with traditional benign operating system activity.\u003c/p\u003e\u003cp\u003eThings get a little interesting when viewed from a parent-child lens, since unusual child processes spawned by a parent process can indicate malicious activity. For example, \u003cem\u003e\u003cstrong\u003eword.exe\u003c/strong\u003e\u003c/em\u003e spawning powershell.exe could indicate a Spearphishing Attachment. Current solutions to detect LOtL attacks using parent-child relationships include writing rules and heuristics. While these solutions work well, they can sometimes be either too rigid or too lax and do not generalize well. There is also a significant amount of manual effort that goes into writing them.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWith ProblemChild, the goal remains the same: we hope to provide better generalization with the added advantage of ranking and prioritizing events for further investigation using machine learning.\u003c/p\u003e\u003ch2\u003eThe ProblemChild framework\u003c/h2\u003e\u003cp\u003eProblemChild uses data frame analytics available in the Elastic Stack to build a supervised model to classify events as malicious or benign using features extracted from event metadata. It then uses anomaly detection to pick out “high priority” events for further analysis from those detected as malicious by the supervised model.\u003c/p\u003e\u003ch3\u003eData\u003c/h3\u003e\u003cp\u003eFor the supervised model, we gathered Windows process event metadata from a variety of sources like the \u003ca href=\"https://github.com/splunk/attack_data\"\u003eSplunk Attack data\u003c/a\u003e, \u003ca href=\"https://github.com/splunk/botsv1\"\u003eSplunk botsv1\u003c/a\u003e, \u003ca href=\"https://github.com/redcanaryco/atomic-red-team\"\u003eRed Canary Atomic Red Team\u003c/a\u003e, and several internal databases. An example of a raw sample used in training is as follows:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{ \u003cbr /\u003e \"timestamp_utc\": \"2019-06-14 15:31:17Z\", \u003cbr /\u003e \"pid\": 372, \u003cbr /\u003e \"integrity_level\": \"system\", \u003cbr /\u003e \"elevation_type\": \"default\", \u003cbr /\u003e \"signature_status\": \"trusted\", \u003cbr /\u003e \"serial_event_id\": 1007, \u003cbr /\u003e \"elevated\": true, \u003cbr /\u003e \"signature_signer\": \"Microsoft Windows Publisher\", \u003cbr /\u003e \"event_subtype_full\": \"already_running\", \u003cbr /\u003e \"command_line\": \"C:\\\\Windows\\\\System32\\\\svchost.exe -k LocalSystemNetworkRestricted -p\", \u003cbr /\u003e \"parent_process_name\": \"services.exe\", \u003cbr /\u003e \"ppid\": 620, \u003cbr /\u003e \"sha256\": \"7fd065bac18c5278777ae44908101cdfed72d26fa741367f0ad4d02020787ab6\", \u003cbr /\u003e \"user_name\": \"SYSTEM\", \u003cbr /\u003e \"process_path\": \"C:\\\\Windows\\\\System32\\\\svchost.exe\", \u003cbr /\u003e \"user_sid\": \"S-1-5-18\", \u003cbr /\u003e \"timestamp\": 132049998770000000, \u003cbr /\u003e \"process_name\": \"svchost.exe\", \u003cbr /\u003e \"original_file_name\": \"svchost.exe\", \u003cbr /\u003e \"parent_process_path\": \"C:\\\\Windows\\\\System32\\\\services.exe\", \u003cbr /\u003e \"unique_pid\": 1007, \u003cbr /\u003e \"md5\": \"8a0a29438052faed8a2532da50455756\", \u003cbr /\u003e \"sha1\": \"a1385ce20ad79f55df235effd9780c31442aa234\", \u003cbr /\u003e \"unique_ppid\": 1006, \u003cbr /\u003e \"event_type_full\": \"process_event\", \u003cbr /\u003e \"opcode\": 3, \u003cbr /\u003e \"user_domain\": \"NT AUTHORITY\" \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cfigcaption\u003eSample raw document containing Windows process event metadata\u003c/figcaption\u003e\u003ch3\u003eFeature engineering\u003c/h3\u003e\u003cp\u003eSince we wanted to focus on identifying LOtL activity using parent-child context, we started by extracting features that capture information about the process itself, its parent, and surrounding contextual information (e.g., elevation level, system user, etc.) from the raw event metadata (shown above) as follows:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eProcess name\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eParent process name\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eCommandline arguments\u003c/li\u003e\u003cli aria-level=\"1\"\u003eProcess path\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eParent process path\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eEvent subtype\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eWhether event is elevated\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eElevation type\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eIntegrity level\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eNormalized process path\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eWhether process is signed\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eWhether signer is trusted\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eWhether user is running as system\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eFilename mismatch\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eWhether process name ends with exe\u0026nbsp;\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAll of the feature engineering was done using processors already available in the Elastic Stack or using custom scripts written in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/modules-scripting-painless.html\"\u003ePainless\u003c/a\u003e, which were then used in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/script-processor.html\"\u003escript processors\u003c/a\u003e. A high-level breakdown of the featurization process is as follows:\u003c/p\u003e\u003cp\u003eSince the model supports Windows process events for the Elastic Endpoint Security integration, Elastic Endgame, and Winlogbeat, we first use a script processor to standardize\u0026nbsp;the field names across the different agents. We did this so the model always has the same set of input fields, regardless of the agent type.\u003c/p\u003e\u003cp\u003eWe then used script processors to build features that were derived from the common set of fields.\u003c/p\u003e\u003cp\u003eExample: The following script processor sets the feature feature_ends_with_exe to true if the process name associated with the event ends with \".exe\" and false otherwise.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{ \u003cbr /\u003e \"script\": { \u003cbr /\u003e \"lang\": \"painless\", \u003cbr /\u003e \"source\": \"\"\" \u003cbr /\u003e if(ctx.feature_process_name.contains(\".exe\")) { \u003cbr /\u003e ctx.feature_ends_with_exe = true \u003cbr /\u003e } \u003cbr /\u003e else { \u003cbr /\u003e ctx.feature_ends_with_exe = false \u003cbr /\u003e } \u003cbr /\u003e \"\"\" \u003cbr /\u003e } \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cfigcaption\u003eExample of using script processors for feature extraction\u003c/figcaption\u003e\u003cp\u003eWe noticed that minor variations like change in case, usernames, certain special characters (mainly \", /, \\), and appearance of random numbers/hexadecimal values in fields like commandline arguments and process paths were affecting the performance of our models, and needed to be normalized and/or obfuscated. We also found that replacing certain Windows directories with appropriate tokens, for example replacing\u0026nbsp;windows/system32 and windows/syswow64 with the token win_system_dir, further improved model performance. These normalizations and obfuscations were done using\u0026nbsp;the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/lowercase-processor.html\"\u003elowercase\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/gsub-processor.html\"\u003egsub\u003c/a\u003e processors available in the Elastic Stack.\u003c/p\u003e\u003cp\u003eExample: The following processor replaces text matched by the pattern defined in the pattern field with the string 'process_id' in the feature_command_line field.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{ \u003cbr /\u003e \"gsub\": { \u003cbr /\u003e \"field\": \"feature_command_line\", \u003cbr /\u003e \"pattern\": \"[0-9a-f]{4,}-[0-9a-f]{4,}-[0-9a-f]{4,}-[0-9a-f-]{4,}\", \u003cbr /\u003e \"replacement\": \"process_id\" \u003cbr /\u003e } \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cfigcaption\u003eExample of using pre-built Elastic Stack processors for normalization of features\u003c/figcaption\u003e\u003cp\u003eFinally, we used a series of script processors to extract n-gram features from process and parent process names and paths and commandline arguments. After experimenting with different n-gram lengths, we concluded that bigrams were the most optimum fit and provided the best trade-off between dimensionality of the feature set and model performance.\u003c/p\u003e\u003cp\u003eExample: The following processor generates bigrams for the field feature_process_name.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{ \u003cbr /\u003e \"script\": { \u003cbr /\u003e \"id\": \"ngram-extractor\", \u003cbr /\u003e \"params\": { \u003cbr /\u003e \"ngram_count\": 2, \u003cbr /\u003e \"field\": \"feature_process_name\", \u003cbr /\u003e \"max_length\": 100 \u003cbr /\u003e } \u003cbr /\u003e } \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cfigcaption\u003eScript processor for extracting n-grams\u003c/figcaption\u003e\u003cp\u003eAll the processors mentioned so far were a part of an ingest pipeline used to featurize raw events from the source index and re-index them. Please refer to the \u003ca href=\"https://github.com/elastic/examples/tree/master/Machine%20Learning/ProblemChild\"\u003eexamples repository\u003c/a\u003e for detailed instructions on featurization and the relevant configurations, scripts, etc. An example of features created by the ingest pipeline is as follows:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{ \u003cbr /\u003e \"feature_command_line_2-gram_feature10\" : \"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature53\" : \".e\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature54\" : \"ex\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature55\" : \"xe\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature56\" : \"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature49\" : \"ka\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature48\" : \"\"\"\\k\"\"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature47\" : \"\"\"r\\\"\"\", \u003cbr /\u003e \"feature_command_line\" : \"kaps.exe -u\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature46\" : \"er\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature45\" : \"le\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature44\" : \"ll\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature43\" : \"il\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature42\" : \"ki\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature41\" : \"\"\"\\k\"\"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature40\" : \"\"\"s\\\"\"\", \u003cbr /\u003e \"feature_running_as_system\" : false, \u003cbr /\u003e \"feature_process_signer_trusted\" : true, \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature46\" : \"er\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature47\" : \"\"\"r\\\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature48\" : \"\"\"\\k\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature49\" : \"ka\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature42\" : \"ki\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature43\" : \"il\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature44\" : \"ll\", \u003cbr /\u003e \"feature_process_parent_executable\" : \"\"\"c:\\win_system_dir\\drivers\\rivetnetworks\\killer\\kaps.exe\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature45\" : \"le\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature50\" : \"ap\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature51\" : \"ps\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature52\" : \"s.\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature56\" : \"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature55\" : \"xe\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature54\" : \"ex\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature53\" : \".e\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature52\" : \"s.\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature51\" : \"ps\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature50\" : \"ap\", \u003cbr /\u003e \"feature_process_name\" : \"kaps.exe\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature29\" : \"iv\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature28\" : \"ri\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature27\" : \"\"\"\\r\"\"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature26\" : \"\"\"s\\\"\"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature25\" : \"rs\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature24\" : \"er\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature23\" : \"ve\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature22\" : \"iv\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature21\" : \"ri\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature20\" : \"dr\", \u003cbr /\u003e \"feature_process_name_2-gram_feature4\" : \".e\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature4\" : \".e\", \u003cbr /\u003e \"feature_process_name_2-gram_feature5\" : \"ex\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature3\" : \"s.\", \u003cbr /\u003e \"feature_process_name_2-gram_feature6\" : \"xe\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature2\" : \"ps\", \u003cbr /\u003e \"feature_process_name_2-gram_feature7\" : \"\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature1\" : \"ap\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature7\" : \"\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature6\" : \"xe\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature5\" : \"ex\", \u003cbr /\u003e \"feature_ends_with_exe\" : true, \u003cbr /\u003e \"feature_process_executable_2-gram_feature39\" : \"ks\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature38\" : \"rk\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature37\" : \"or\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature36\" : \"wo\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature35\" : \"tw\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature34\" : \"et\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature33\" : \"ne\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature32\" : \"tn\", \u003cbr /\u003e \"feature_process_name_2-gram_feature0\" : \"ka\", \u003cbr /\u003e \"feature_process_parent_name_2-gram_feature0\" : \"ka\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature31\" : \"et\", \u003cbr /\u003e \"feature_process_name_2-gram_feature1\" : \"ap\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature30\" : \"ve\", \u003cbr /\u003e \"feature_process_name_2-gram_feature2\" : \"ps\", \u003cbr /\u003e \"feature_process_name_2-gram_feature3\" : \"s.\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature17\" : \"32\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature18\" : \"\"\"2\\\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature19\" : \"\"\"\\d\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature3\" : \"wi\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature13\" : \"st\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature2\" : \"\"\"\\w\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature14\" : \"te\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature5\" : \"nd\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature15\" : \"em\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature4\" : \"in\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature16\" : \"m3\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature7\" : \"ow\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature6\" : \"do\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature10\" : \"\"\"\\s\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature9\" : \"\"\"s\\\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature11\" : \"sy\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature8\" : \"ws\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature12\" : \"ys\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature1\" : \"\"\":\\\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature0\" : \"c:\", \u003cbr /\u003e \"feature_process_signed\" : true, \u003cbr /\u003e \"feature_elevation_type\" : \"limited\", \u003cbr /\u003e \"feature_integrity_level\" : \"medium\", \u003cbr /\u003e \"feature_elevated\" : false, \u003cbr /\u003e \"feature_process_executable_2-gram_feature19\" : \"\"\"\\d\"\"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature18\" : \"\"\"2\\\"\"\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature17\" : \"32\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature16\" : \"m3\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature15\" : \"em\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature14\" : \"te\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature13\" : \"st\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature12\" : \"ys\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature11\" : \"sy\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature10\" : \"\"\"\\s\"\"\", \u003cbr /\u003e \"feature_process_executable\" : \"\"\"c:\\win_system_dir\\drivers\\rivetnetworks\\killer\\kaps.exe\"\"\", \u003cbr /\u003e \"feature_filename_mismatch\" : false, \u003cbr /\u003e \"feature_process_executable_2-gram_feature8\" : \"ws\", \u003cbr /\u003e \"feature_command_line_2-gram_feature4\" : \".e\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature7\" : \"ow\", \u003cbr /\u003e \"feature_command_line_2-gram_feature3\" : \"s.\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature6\" : \"do\", \u003cbr /\u003e \"feature_command_line_2-gram_feature6\" : \"xe\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature5\" : \"nd\", \u003cbr /\u003e \"feature_command_line_2-gram_feature5\" : \"ex\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature39\" : \"ks\", \u003cbr /\u003e \"feature_command_line_2-gram_feature0\" : \"ka\", \u003cbr /\u003e \"feature_command_line_2-gram_feature2\" : \"ps\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature9\" : \"\"\"s\\\"\"\", \u003cbr /\u003e \"feature_command_line_2-gram_feature1\" : \"ap\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature35\" : \"tw\", \u003cbr /\u003e \"feature_normalized_ppath\" : \"win_system_dir\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature36\" : \"wo\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature37\" : \"or\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature38\" : \"rk\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature31\" : \"et\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature32\" : \"tn\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature33\" : \"ne\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature34\" : \"et\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature40\" : \"\"\"s\\\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature41\" : \"\"\"\\k\"\"\", \u003cbr /\u003e \"feature_event_action\" : \"creation_event\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature0\" : \"c:\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature4\" : \"in\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature3\" : \"wi\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature2\" : \"\"\"\\w\"\"\", \u003cbr /\u003e \"feature_process_parent_name\" : \"kaps.exe\", \u003cbr /\u003e \"feature_process_executable_2-gram_feature1\" : \"\"\":\\\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature28\" : \"ri\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature29\" : \"iv\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature24\" : \"er\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature25\" : \"rs\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature26\" : \"\"\"s\\\"\"\", \u003cbr /\u003e \"label\" : 0, \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature27\" : \"\"\"\\r\"\"\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature20\" : \"dr\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature21\" : \"ri\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature22\" : \"iv\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature23\" : \"ve\", \u003cbr /\u003e \"feature_process_parent_executable_2-gram_feature30\" : \"ve\", \u003cbr /\u003e \"feature_command_line_2-gram_feature8\" : \" -\", \u003cbr /\u003e \"feature_command_line_2-gram_feature7\" : \"e \", \u003cbr /\u003e \"feature_command_line_2-gram_feature9\" : \"-u\" \u003cbr /\u003e }\u003cbr /\u003e\u003c/pre\u003e\u003cfigcaption\u003eExample of features created by the featurization ingest pipeline\u003c/figcaption\u003e\u003cp\u003eThe nice thing about data frame analytics is that it automatically encodes boolean and categorical features (even features like n-grams), thus eliminating the need for you to manually convert these features into numerical values for the model. It also examines the features and automatically selects the most important features for classification.\u003c/p\u003e\u003ch3\u003eTraining the supervised model\u003c/h3\u003e\u003cp\u003eThe next step was to train a classification model based on the features extracted above. We used the data frame analytics UI to create the classification job. A snippet of what the process looks like in the UI is shown below:\u003c/p\u003e\u003cdiv id=\"video\" class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/JsS5MVj5VfBkvttTYjs8vS.jpg\" data-uuid=\"JsS5MVj5VfBkvttTYjs8vS\" data-v=\"4\" data-type=\"inline\" style=\"width: 100%;display: block;\" width=\"100%\"/\u003e\u003c/div\u003e\u003cbr /\u003e\u003cp\u003eAn overview of the process shown in the video is as follows:\u003c/p\u003eChoose the source index pattern for your jobChoose the job type as “Classification”Choose the dependent variable as the field containing the ground truth labelSet the training percentage: we recommend that you take an iterative approach to training. Start with a smaller training percentage, evaluate the performance and decide if you need to train on more data. A training percentage of ~55 worked for us. We didn’t see any gains in performance beyond this percentage for our datasetKeep only the fields required for training and exclude the rest by unchecking the boxes next to the fields. We only retained the following fields:\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltedbd4d01d04ceb62/60997d163705f74a9ffbd72d/1-training-features-blog-problemchild.png\" data-sys-asset-uid=\"bltedbd4d01d04ceb62\" width=\"374\" height=\"247\" style=\"display: block;margin: auto;width: 374;height: 247;\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eList of features to include in training (* indicates all features matching the pattern)\u003c/figcaption\u003eSet the number of feature importance values you would like to see once the model has trained: We chose 20Set a prediction field name of your choice: We chose y_predSet an appropriate job name and description under job ID and description respectivelySet a destination index and click “Continue”, followed by “Create”\u003ch3\u003eEvaluating the trained model\u003c/h3\u003e\u003cp\u003eOnce the model has trained, you can navigate to the data frame analytics results UI to analyze the performance of the model on the test set. The UI displays the confusion matrix, a key metric in evaluating the overall model performance. Additionally, you can also view a data table of the results, which shows how the model performed on individual data points in the dataset. You can toggle between the training and testing results by using the Training/Testing filters to the top right in the UI.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt72dec584e23e18c9/60997d3e01ff5a556925c83e/2-confusion-matrix-blog-problemchild.png\" data-sys-asset-uid=\"blt72dec584e23e18c9\" alt=\"2-confusion-matrix-blog-problemchild.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eConfusion matrix for our testing dataset\u003c/figcaption\u003e\u003cfigcaption\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt37ad98090151cb78/60997d8c43430a55689b20fb/3-individual-results-blog-problemchild.png\" data-sys-asset-uid=\"blt37ad98090151cb78\" alt=\"3-individual-results-blog-problemchild.png\"/\u003e\u003cbr /\u003eData table of individual results\u003c/figcaption\u003e\u003cp\u003eWe focused mainly on the confusion matrix for model evaluation. The confusion matrix displays the percentage of data points that were classified as true positives\u003cstrong\u003e \u003c/strong\u003e(malicious events that the model identified as malicious and that were actually malicious) and true negatives (benign events that the model identified as benign and that were actually benign). The matrix also displays the percentage of events that the model misclassified as malicious (false positives) and vice versa (false negatives).\u003c/p\u003e\u003cp\u003eAs seen in the figure above, our model had a 98% true positive rate on the testing data, which is pretty good, considering malicious process events are generally tricky to identify. The false positive rate was low, which is also a good sign. This means that the model will not generate a large number of alerts if deployed to production in our environment.\u003c/p\u003e\u003cp\u003eOne thing to note here is that the performance of your model could look very different from ours based on the training data. You might need to tune your model, increase the training percentage, add more training data or features, etc.\u003c/p\u003e\u003ch3\u003eEnriching incoming events on ingest\u003c/h3\u003e\u003cp\u003eOnce you have a model you like, you can use it to enrich incoming events with a prediction of whether or not the event is likely to be malicious, along with a probability score of how confident the model is in its prediction.\u003c/p\u003e\u003cp\u003eThis can be done by configuring an ingest pipeline for the new events with an \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/inference-processor.html\"\u003einference processor\u003c/a\u003e. However, for the trained model to make predictions, the incoming events need to be featurized using the same set of processors as discussed in the Feature Engineering section of this blog. Hence the ingest pipeline for these new events consists of all the processors mentioned previously, with the inference processor added after all the feature generating processors. A snippet of an enriched document looks as follows:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc54c85ecb5df5c3f/60997da043430a55689b20ff/4-enriched-document-blog-problemchild.png\" data-sys-asset-uid=\"bltc54c85ecb5df5c3f\" width=\"428\" height=\"464\" style=\"display: block;margin: auto;width: 428;height: 464;\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cfigcaption\u003eAn example of an enriched document\u003c/figcaption\u003e\u003cp\u003eThe complete ingest pipeline configuration and additional configuration details can be found in the \u003ca href=\"https://github.com/elastic/examples/blob/master/Machine%20Learning/ProblemChild/problemchild_inference.json\"\u003eexamples repository\u003c/a\u003e. You might also note that the document shown above does not have any of the features created by the featurization processors. This is because the ingest pipeline here contains a \u003ca href=\"https://github.com/elastic/examples/blob/master/Machine%20Learning/ProblemChild/problemchild_inference.json#L262-L271\"\u003escript processor\u003c/a\u003e that removes all the features created for inference, as well as any other superfluous features, once inference is done. Of course, you can choose to keep the features in by excluding this script processor from the ingest pipeline.\u003c/p\u003e\u003cp\u003eAn additional feature that you can configure to complement the supervised model is a blocklist. The blocklist can be used to catch known offenders in your environment that the trained model might miss based on certain keywords present in the commandline arguments. This is configured as a \u003ca href=\"https://github.com/elastic/examples/blob/master/Machine%20Learning/ProblemChild/blocklist.json\"\u003escript\u003c/a\u003e invoked by a \u003ca href=\"https://github.com/elastic/examples/blob/master/Machine%20Learning/ProblemChild/problemchild_inference.json#L250-L261\"\u003escript processor\u003c/a\u003e after the inference processor in the ingest pipeline. A starter list of keywords is provided in the \u003ca href=\"https://github.com/elastic/examples/blob/master/Machine%20Learning/ProblemChild/blocklist_keywords.txt\"\u003eexamples repository\u003c/a\u003e. You can also add to the list, but make sure to update the blocklist script processor in your ingest pipeline if you do.\u003c/p\u003e\u003cp\u003eAs mentioned at the beginning of this blog, the ProblemChild framework is currently built only for Windows process events. There are other operating systems (macOS, Linux) as well as different types of events (network, registry) for each OS. It would be ideal to make the ingest pipeline execute conditionally only when the incoming document contains the desired fields. For this, we used a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/pipeline-processor.html\"\u003epipeline processor\u003c/a\u003e and checked for specific fields in the document before deciding whether or not to direct it to the ingest pipeline. A sample of such a processor is as follows:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT _ingest/pipeline/problemchild_pipeline \u003cbr /\u003e{ \u003cbr /\u003e \"description\": \"A pipeline of pipelines for ProblemChild detection\", \u003cbr /\u003e \"processors\": [ \u003cbr /\u003e { \u003cbr /\u003e \"pipeline\": { \u003cbr /\u003e \"if\": \"ctx.containsKey('event') \u0026amp;\u0026amp; ctx['event'].containsKey('kind') \u0026amp;\u0026amp; ctx['event'].containsKey('category') \u0026amp;\u0026amp; ctx['event']['kind'] == 'event' \u0026amp;\u0026amp; ctx['event']['category'].contains('process') \u0026amp;\u0026amp; ctx.containsKey('host') \u0026amp;\u0026amp; ctx['host'].containsKey('os') \u0026amp;\u0026amp; (ctx['host']['os'].containsKey('family') || ctx['host']['os'].containsKey('type') || ctx['host']['os'].containsKey('platform')) \u0026amp;\u0026amp; (ctx['host']['os']['type'] == 'windows' || ctx['host']['os']['type'] == 'Windows' || ctx['host']['os']['family'] == 'windows' || ctx['host']['os']['family'] == 'Windows' || ctx['host']['os']['platform'] == 'windows' || ctx['host']['os']['platform'] == 'Windows') \u003cbr /\u003e \"name\": \"problemchild_inference\" \u003cbr /\u003e } \u003cbr /\u003e } \u003cbr /\u003e ] \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cfigcaption\u003eA conditional pipeline of pipelines to detect only on Windows process events\u003c/figcaption\u003e\u003cp\u003eFor a production use case, you might want to consider some error handling for the above pipeline as well.\u003c/p\u003e\u003ch3\u003eAnomaly detection for second-order analytics\u003c/h3\u003e\u003cp\u003eWith ProblemChild, our goal was to not only classify malicious events, but go a step further and identify the creme de la creme of the malicious events. In environments working with a large amount of data, even a small false positive rate can result in a large number of alerts. Picking out the rarest events for analysts can help them prioritize events and catalyze the triage process.\u003c/p\u003e\u003cp\u003eThe Elastic Stack has an anomaly detection module, which we leveraged to build an additional layer of analytics on top of our supervised model results. We made use of the rare detector to create anomaly detection jobs to identify rare processes spawned by a particular parent process/user/host, as well as the high_count detector to identify groups of suspicious processes spawned by a particular parent process/user/host. The \u003ca href=\"https://github.com/elastic/examples/tree/master/Machine%20Learning/ProblemChild/job_configs\"\u003econfigurations\u003c/a\u003e and \u003ca href=\"https://github.com/elastic/examples/tree/master/Machine%20Learning/ProblemChild/datafeeds\"\u003edatafeeds\u003c/a\u003e required to set up these jobs can be found in the examples repository as well.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThe Anomaly Explorer is a good place to view anomalies detected by your anomaly detection jobs. You can see an overall visualization of anomalies across a given time period, as well as an individual breakdown of the anomalies with the associated anomaly score and relevant context in the form of \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/current/ml-influencers.html\"\u003einfluencers\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt57eda0230cd38e80/60997dfa7ee89a47ff539fbe/5-swimlane-view-blog-problemchild.png\" data-sys-asset-uid=\"blt57eda0230cd38e80\" alt=\"5-swimlane-view-blog-problemchild.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eSwimlane view of overall anomalies\u003c/figcaption\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt02d67d720bb2d9fb/60997e20ce885c5a4f282048/6-drill-down-blog-problemchild.png\" data-sys-asset-uid=\"blt02d67d720bb2d9fb\" alt=\"6-drill-down-blog-problemchild.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eIndividual drill-down of anomalies\u003c/figcaption\u003e\u003cp\u003eYou can also go a step further and convert these unsupervised machine learning jobs into rules to generate actual detections. We will talk more about this in a future blog post.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003eIn this blog post, we trained a classification model to identify malicious Windows process events and used anomaly detection to further uncover rare events. We will also be releasing our models and configurations for ProblemChild in the \u003ca href=\"https://github.com/elastic/detection-rules/releases/\"\u003edetection-rules\u003c/a\u003e repository. Watch that space for future updates to ProblemChild. Also, stay tuned for a future blog post to find out how to use these in \u003ca href=\"https://www.elastic.co/siem\"\u003ethe Elastic SIEM app\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eIn the meantime, experience the latest version of \u003ca href=\"https://www.elastic.co/elasticsearch/service\"\u003eElasticsearch Service\u003c/a\u003e on Elastic Cloud and follow along with this blog to build the ProblemChild framework from scratch on your Windows process event data. Also be sure to take advantage of our \u003ca href=\"https://www.elastic.co/training/elastic-security-quick-start\"\u003eQuick Start training\u003c/a\u003e to set yourself up for success. Happy experimenting!\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-05-10T18:16:21.583Z","created_by":"bltc87e8bcd2aefc255","disclaimer":[],"full_bleed_image":{"uid":"blt4444e17c9e0df2d2","ACL":{},"_version":1,"content_type":"image/jpeg","created_at":"2020-12-29T20:04:45.763Z","created_by":"bltf6ab93733e4e3a73","file_size":"127027","filename":"blog-banner-yellow-network-security.jpg","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-29T20:04:40.359Z","user":"bltf6ab93733e4e3a73"},"tags":[],"title":"blog-banner-yellow-network-security.jpg","updated_at":"2020-12-29T20:04:45.763Z","updated_by":"bltf6ab93733e4e3a73","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4444e17c9e0df2d2/5feb8bdda7955d1a6a89196b/blog-banner-yellow-network-security.jpg"},"markdown_l10n":"","publish_date":"2021-05-18T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"ProblemChild: Detecting living-off-the-land attacks using the Elastic Stack","seo_description_l10n":"In this blog post, we train a classification model to identify malicious Windows process events and used anomaly detection to further uncover rare events. We are also releasing our models and configurations for ProblemChild in the detection-rules repository.","noindex":false,"canonical_tag":""},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltec42e5a5aed1ee3f","ACL":{},"_version":1,"content_type":"image/jpeg","created_at":"2020-12-29T20:04:25.909Z","created_by":"bltf6ab93733e4e3a73","file_size":"188409","filename":"blog-thumb-yellow-network-security.jpg","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-29T20:04:40.348Z","user":"bltf6ab93733e4e3a73"},"tags":[],"title":"blog-thumb-yellow-network-security.jpg","updated_at":"2020-12-29T20:04:25.909Z","updated_by":"bltf6ab93733e4e3a73","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec42e5a5aed1ee3f/5feb8bc91166ce7d2ed1aaba/blog-thumb-yellow-network-security.jpg"},"title":"ProblemChild: Detecting living-off-the-land attacks using the Elastic Stack","title_l10n":"ProblemChild: Detecting living-off-the-land attacks using the Elastic Stack","updated_at":"2025-03-10T12:18:20.662Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/problemchild-detecting-living-off-the-land-attacks","publish_details":{"time":"2025-03-10T12:18:24.865Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2e20e38579b749da","_version":13,"locale":"en-us","ACL":{},"abstract_l10n":"In this series of blogs we will provide an overview of our architecture, what data we send to our clusters, how and why we use Cross Cluster Search with the Security and Machine Learning (ML) applications, and how we tune, manage and notify.","author":["blt06048a64b0c2b959"],"body_l10n":"\u003cp\u003eThe Elastic Infosec Detections and Analytics team is responsible for building, tuning, and maintaining the security detections used to protect all Elastic systems. Within Elastic we call ourselves Customer Zero and \u003ca href=\"https://www.elastic.co/blog/elastic-on-elastic-how-infosec-deploys-infrastructure-and-stays-up-to-date-with-eck\"\u003ewe strive to always use the newest versions\u003c/a\u003e of our products.\u0026nbsp;\u003c/p\u003e\u003cp\u003eIn this series of blog posts we will provide an overview of our architecture, what data we send to our clusters, how and why we use Cross Cluster Search with the Security and Machine Learning (ML) applications, and how we tune, manage and notify analysts for those alerts.\u003c/p\u003e\u003cp\u003eIn the \u003ca href=\"https://www.elastic.co/blog/elastic-on-elastic-deep-dive-into-our-siem-architecture\"\u003eprevious blog post\u003c/a\u003e we provided an overview of our internal Elastic infrastructure that we use in Infosec and how we use Cross Cluster Search to connect multiple clusters into a single interface for Security Analysts. In this blog post we will go into more detail about the specific types of data we collect.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eTypes of data searchable in our SIEM\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt75786479af524e1d/6132317ecc95cf70fa047d1c/blog-elastic-siem-1.png\" data-sys-asset-uid=\"blt75786479af524e1d\" alt=\"blog-elastic-siem-1.png\"/\u003e\u003c/p\u003e\u003cstrong\u003e\u003c/strong\u003e\u003ch2\u003e\u003cstrong\u003eAuditbeat Cluster\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eWe use \u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/auditbeat-overview.html\"\u003eAuditbeat\u003c/a\u003e to monitor activity on all of our Linux servers and containers. We use the \u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/auditbeat-module-auditd.html\"\u003eauditd\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/auditbeat-module-system.html\"\u003eSystem Module\u003c/a\u003e to collect process execution, logins, network connections, system information, and the \u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/auditbeat-module-file_integrity.html\"\u003eFile Integrity Module\u003c/a\u003e for monitoring of critical files. We use several \u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/filtering-and-enhancing-data.html\"\u003eprocessors\u003c/a\u003e in the auditbeat config to filter and enhance the data as we as it's collected.\u0026nbsp;\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eWe use \u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/drop-event.html\"\u003edrop_event\u003c/a\u003e processors to filter out known good events from being logged. This lets us keep our costs down when centrally logging events from cloud systems. The drop_event process lets you write complex filters to remove your noisiest events before they ever logged.\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/add-process-metadata.html\"\u003eadd_process_metadata\u003c/a\u003e is used to add the parent process information to process events. Many of the Security app detections use parent-child process relationships to identify strange behavior so having this processor is critical.\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/add-cloud-metadata.html\"\u003eadd_cloud_metadata\u003c/a\u003e adds the cloud information to each event making it easier to identify which cloud provider, region, and account a system belongs to.\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/add-docker-metadata.html\"\u003eadd_docker_metadata\u003c/a\u003e to add container ID, name, and labels to the event.\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/auditbeat/7.13/include-fields.html\"\u003einclude_fields\u003c/a\u003e lets you add custom fields to a config. We use it to add custom ‘config.version’ and ‘team’ fields to the events so we can easily identify the owner of the system and any systems using an older version of the auditbeat config.\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003e\u003cstrong\u003eFilebeat Cluster\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eOur \u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/index.html\"\u003eFilebeat\u003c/a\u003e cluster is where we use Filebeat to collect logs from the many third party systems we use at Elastic. Some of the third party services have built in Filebeat modules that make it very easy to to configure and collect the events in ECS formatting. The following built in Filebeat modules are being used:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-okta.html\"\u003eOkta Module\u003c/a\u003e collects events from the Okta API and it is used for many of our detections and investigations. We use Okta for Single Sign On to many applications in Elastic so having these logs is critical to identifying who accessed what.\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-o365.html\"\u003eOffice 365 Module\u003c/a\u003e is useful for security to monitor access to documents, and Azure AD authentication.\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-nginx.html\"\u003eNginx module\u003c/a\u003e collects access logs from the proxies in front of our critical web services. This can be very useful for tracking access or alerting on strange activity and web attacks.\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-google_workspace.html\"\u003eGoogle Workspace\u003c/a\u003e module collects events from Gmail, Google Drive, and other Google services\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-gcp.html\"\u003eGoogle Cloud Module\u003c/a\u003e to build alerts and investigate activity in GCP\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-aws.html\"\u003eAWS Module\u003c/a\u003e to build alerts and investigate activity in AWS\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/7.13/filebeat-module-azure.html\"\u003eAzure Module\u003c/a\u003e to build alerts and investigate activity in Azure\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eSometimes a built-in Filebeat module doesn’t exist so the SecEng team will have to build custom scripts and configurations for Filebeat to collect the information we need. The following logs are being collected in this way:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eQualys - a script retrieves the results from our Qualys scans from the service and then converts the results from XML to json where it is then ingested by Filebeat. In addition to visualizing and alerting for Vulnerability Management, the Qualys data can be used to enrich other events. For example, if we see an alert for an exploit, and according to Qualys the host is vulnerable to that exploit we can elevate the priority of the investigation.\u003c/li\u003e\u003cli aria-level=\"1\"\u003eGithub - The Github events API is used to collect events about activity in all Elastic Owned repositories.\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eHackerOne - Submitted reports from our bug bounty program.\u003c/li\u003e\u003cli aria-level=\"1\"\u003eShodan - The Shodan API is used to gather information for our Threat Intel team tracking exposure of Elastic clusters.\u003c/li\u003e\u003cli aria-level=\"1\"\u003eRecordedFuture - Threat Intel feeds ingested for enriching events.\u003c/li\u003e\u003cli aria-level=\"1\"\u003eJamf - Inventory information about our Fleet of Mac systems. This makes it easier to find the registered owner of the system.\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eLastPass - Activity from our corporate LastPass subscription.\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003e\u003cstrong\u003eMonitoring Cluster\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eA \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.13/monitor-elasticsearch-cluster.html\"\u003eMonitoring Cluster\u003c/a\u003e cluster is used to collect monitoring information from all of the other clusters. This information is used to audit activity on the other clusters and our Endgame SMPs as well as to monitor the performance on those clusters. Metricbeat, Filebeat, and Auditbeat logs from all of the other clusters are stored on this cluster.\u0026nbsp;\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003eEndgame Cluster\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eWe use Endgame to \u003ca href=\"https://www.elastic.co/blog/securing-our-own-endpoints-with-elastic-security\"\u003esecure all of the workstations\u003c/a\u003e used by Elasticians around the globe. In addition to being amazing at preventing attacks, Endgame can easily be configured to stream events to an Elastic cluster where we can use the machine learning and detection engine capabilities as well. Streaming the events to our SIEM lets us see the entire picture of activity on Elastic systems with the workstation events in the same dashboards and visualizations as the Okta SSO, Google Workspace, and other events.\u0026nbsp;\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003eFleet Cluster\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eOur fleet cluster is where we manage the Elastic Agent and its new integrations such as Endpoint Security and OSquery. With Fleet you can deploy Elastic Agent to systems to collect observability data and have the ability to deploy and remove \u003ca href=\"https://www.elastic.co/guide/en/fleet/current/fleet-overview.html#configuring-integrations\"\u003eintegrations\u003c/a\u003e to the Elastic Agents to collect additional data as needed.\u003c/p\u003e\u003cp\u003eBecause we are using Endgame for endpoint protection on our workstations we are not yet using the Endpoint Security fleet integration at scale. As the Endpoint Security integration reaches feature parity with Endgame we will be migrating our systems off of Endgame and onto Endpoint Security. We cannot deploy Endgame and Endpoint Security to the same systems at the same time because they are not compatible with each other. All of the other Elastic Agent integrations can be used with Endgame.\u003c/p\u003eThe primary Fleet integration we use at this time is the \u003ca href=\"https://www.elastic.co/about/press/elastic-announces-osquery-management-integration-for-unified-data-analysis-to-address-cyber-threats\"\u003eOSQuery Manager\u003c/a\u003e integration. The OSQuery Manager lets us schedule and run live OSQuery queries to actively gather information from our fleet of systems. \u003ca href=\"https://osquery.io/\"\u003eOSQuery\u003c/a\u003e is an open source project that enables analysts to directly query their systems to gather information such as running processes, installed applications, disk encryption status, named pipes, installed Chrome extensions, and over 250 other types of queries. For a more in depth dive on how we use OSquery Manager at Elastic we presented this Webcast with the SANS institute: \u003cspan style=\"font-size: 11pt;font-family: Arial;color: #000000;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003ca href=\"https://www.sans.org/webcasts/operationalize-osquery-at-scale-with-elastic/\"\u003ehttps://www.sans.org/webcasts/operationalize-osque...\u003c/a\u003e\u003c/span\u003e\u003ch2\u003e\u003cstrong\u003eMalware Sandbox\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eThis cluster is another Fleet server but this one is used only for deploying Elastic Agent to analyst VMs to instrument them as a \u003ca href=\"https://www.elastic.co/blog/how-to-build-a-malware-analysis-sandbox-with-elastic-security\"\u003eMalware Analysis Sandbox\u003c/a\u003e. Rather than having each analyst maintain their own cluster for this the SecEng team created a single managed cluster that all of us can use to manage log collection from our Sandbox VMs. The ability to manage Fleet and to add and remove agents and policies dynamically requires Super User privileges on the cluster so this activity needs to be a separate cluster from the production clusters. With CCS All of the analysts can see the logs from this cluster which means we can have one Analyst detonate and analyze the malware on their sandbox but everyone has access to the events that were created. These events can then be added to a case and we can use the indicators of compromise from the sandbox to quickly search through our live data for any evidence of compromise.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eCustomer Zero continued\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eIn this post we walked through the types of searchable data in a single Elastic SIEM interface and how we use that data for Security Detection, Incident Response, Threat Hunting, Threat Intelligence, Compliance Auditing, and Vulnerability Management.\u003c/p\u003e\u003cp\u003eBe sure to check back for our Third part of this series which will show you how we configure the Security app and Detection Rules to work with Cross Cluster Search.\u0026nbsp;\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-09-02T20:05:08.380Z","created_by":"blt1e57c6588ae1816e","disclaimer":[],"full_bleed_image":{"uid":"blt1264ab51dcf8cbce","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-27T22:46:09.488Z","updated_at":"2020-07-27T22:46:09.488Z","content_type":"image/png","file_size":"14352","filename":"blog-banner-security-pattern-color.png","title":"blog-banner-security-pattern-color.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-27T22:46:19.680Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1264ab51dcf8cbce/5f1f5931804fa40c94d9c6c5/blog-banner-security-pattern-color.png"},"markdown_l10n":"","publish_date":"2021-09-07T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic on Elastic Series: Data collected to the Infosec SIEM","seo_description_l10n":"In this series of blogs we will provide an overview of our architecture, what data we send to our clusters, how and why we use Cross Cluster Search with the Security and Machine Learning (ML) applications, and how we tune, manage and notify.","noindex":false,"canonical_tag":""},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt7275b59d6d8d38ce","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-07T21:42:22.214Z","updated_at":"2020-07-07T21:42:22.214Z","content_type":"image/png","file_size":"12109","filename":"blog-thumb-security-pattern-color.png","title":"blog-thumb-security-pattern-color.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-27T22:18:32.010Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7275b59d6d8d38ce/5f04ec3eab218d2b0111496e/blog-thumb-security-pattern-color.png"},"title":"Elastic on Elastic Series: Data collected to the Infosec SIEM","title_l10n":"Elastic on Elastic Series: Data collected to the Infosec SIEM","updated_at":"2025-03-10T12:17:12.398Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-on-elastic-data-collected-to-the-infosec-siem","publish_details":{"time":"2025-03-10T12:17:15.838Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt914a89de909d1093","_version":19,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blte305d0d8f427e122"],"body_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e\u003c/span\u003eElasticsearch is a very versatile platform that supports a variety of use cases and provides great flexibility around data organisation and replication strategies. This flexibility can, however, sometimes make it hard to determine up-front how to best organize your data into indices and shards, especially if you are new to the Elastic Stack. While suboptimal choices will not necessarily cause problems when first starting out, they have the potential to cause performance problems as data volumes grow over time. The more data the cluster holds, the more difficult it also becomes to correct the problem, as reindexing of large amounts of data can sometimes be required.\u003c/p\u003e\u003cp\u003eWhen we come across users that are experiencing performance problems, it is not uncommon that this can be traced back to issues around how data is indexed and number of shards in the cluster. This is especially true for use-cases involving multi-tenancy and/or use of time-based indices. When discussing this with users, either in person at events or meetings or via our \u003ca href=\"https://discuss.elastic.co\" target=\"_self\"\u003eforum\u003c/a\u003e, some of the most common questions are “How many shards should I have?” and “How large should my shards be?”\u003c/p\u003e\u003cp\u003eThis blog post aims to help you answer these questions and provide practical guidelines for use cases that involve the use of time-based indices (e.g., logging or security analytics) in a single place.\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eWhat is a shard?\u003c/h2\u003e\u003cp\u003eBefore we start, we need to establish some facts and terminology that we will need in later sections.\u003c/p\u003e\u003cp\u003eData in Elasticsearch is organized into \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/2.x/_add_an_index.html\" target=\"_self\"\u003eindices\u003c/a\u003e. Each index is made up of one or more shards. Each shard is an instance of a Lucene index, which you can think of as a self-contained search engine that indexes and handles queries for a subset of the data in an Elasticsearch cluster.\u003c/p\u003e\u003cp\u003eAs data is written to a shard, it is periodically published into new immutable Lucene segments on disk, and it is at this time it becomes available for querying. This is referred to as a refresh. How this works is described in greater detail in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/inside-a-shard.html\" target=\"_self\"\u003eElasticsearch: the Definitive Guide\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eAs the number of segments grow, these are periodically consolidated into larger segments. This process is referred to as \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.5/index-modules-merge.html\" target=\"_self\"\u003emerging\u003c/a\u003e. As all segments are immutable, this means that the disk space used will typically fluctuate during indexing, as new, merged segments need to be created before the ones they replace can be deleted. Merging can be quite resource intensive, especially with respect to disk I/O.\u003c/p\u003e\u003cp\u003eThe shard is the unit at which Elasticsearch distributes data around the cluster. The speed at which Elasticsearch can move shards around when rebalancing data, e.g. following a failure, will depend on the size and number of shards as well as network and disk performance.\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/training/elasticsearch-engineer\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eBecome an Elasticsearch Engineer\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cem\u003e: Learn to build your own custom search application using Elasticsearch on the back end.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-weight: 700;\"\u003e\u003cem\u003eTIP:\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-weight: 700;\"\u003e\u003cem\u003e\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(49, 133, 155);\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003eAvoid having very large shards as this can negatively affect the cluster's ability to recover from failure. There is no fixed limit on how large shards can be, but a shard size of 50GB is often quoted as a limit that has been seen to work for a variety of use-cases.\u003c/em\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003ch2 dir=\"ltr\"\u003eIndex by retention period\u003c/h2\u003e\u003cp\u003eAs segments are immutable, \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/2.x/update-doc.html\" target=\"_self\"\u003eupdating a document\u003c/a\u003e requires Elasticsearch to first find the existing document, then mark it as deleted and add the updated version. \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/2.x/delete-doc.html\" target=\"_self\"\u003eDeleting a document\u003c/a\u003e also requires the document to be found and marked as deleted. For this reason, deleted documents will continue to tie up disk space and some system resources until they are merged out, which can consume a lot of system resources.\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cem\u003eRelated: \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/lucenes-handling-of-deleted-documents\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eLucene's handling of deleted documents\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003eElasticsearch allows complete indices to be deleted very efficiently directly from the file system, without explicitly having to delete all records individually. This is by far the most efficient way to delete data from Elasticsearch.\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eTry to use \u003c/em\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/2.x/time-based.html\" target=\"_self\"\u003e\u003cem\u003etime-based indices\u003c/em\u003e\u003c/a\u003e\u003cem\u003e for managing data retention whenever possible. Group data into indices based on the retention period. Time-based indices also make it easy to vary the number of primary shards and replicas over time, as this can be changed for the next index to be generated. This simplifies adapting to changing data volumes and requirements.\u003c/em\u003e\u003c/p\u003e\u003chr/\u003e\u003ch2 dir=\"ltr\"\u003eAre indices and shards not free?\u003c/h2\u003e\u003cp\u003eFor each Elasticsearch index, information about mappings and state is stored in the cluster state. This is kept in memory for fast access. Having a large number of indices and shards in a cluster can therefore result in a large cluster state, especially if mappings are large. This can become slow to update as all updates need to be done through a single thread in order to guarantee consistency before the changes are distributed across the cluster.\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eIn order to reduce the number of indices and avoid large and sprawling mappings, consider storing data with similar structure in the same index rather than splitting into separate indices based on where the data comes from. It is important to find a good balance between the number of indices and shards, and the mapping size for each individual index. Because the \u003c/em\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/2.x/finite-scale.html#finite-scale\" target=\"_blank\"\u003e\u003cem\u003ecluster state\u003c/em\u003e\u003c/a\u003e\u003cem\u003e is loaded into the heap on every node (including the masters), and the amount of heap is directly proportional to the number of indices, fields per index and shards, it is important to also monitor the heap usage on master nodes and make sure they are sized appropriately. \u0026nbsp;\u003c/em\u003e\u003c/p\u003e\u003chr/\u003e\u003cp\u003eEach shard has data that need to be kept in memory and use heap space. This includes data structures holding information at the shard level, but also at the segment level in order to define where data reside on disk. The size of these data structures is not fixed and will vary depending on the use-case.\u003c/p\u003e\u003cp\u003eOne important characteristic of the segment related overhead is however that it is not strictly proportional to the size of the segment. This means that larger segments have less overhead per data volume compared to smaller segments. The difference can be substantial.\u003c/p\u003e\u003cp\u003eIn order to be able to store as much data as possible per node, it becomes important to manage heap usage and reduce the amount of overhead as much as possible. The more heap space a node has, the more data and shards it can handle.\u003c/p\u003e\u003cp\u003eIndices and shards are therefore not free from a cluster perspective, as there is some level of resource overhead for each index and shard.\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eSmall shards result in small segments, which increases overhead. Aim to keep the average shard size between at least a few GB and a few tens of GB. For use-cases with time-based data, it is common to see shards between 20GB and 40GB in size.\u003c/em\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eAs the overhead per shard depends on the segment count and size, forcing smaller segments to merge into larger ones through a \u003c/em\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.5/indices-forcemerge.html\" target=\"_self\"\u003e\u003cem\u003eforcemerge\u003c/em\u003e\u003c/a\u003e\u003cem\u003e operation can reduce overhead and improve query performance. This should ideally be done once no more data is written to the index. Be aware that this is an expensive operation that should ideally be performed during off-peak hours.\u003c/em\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eThe number of shards you can hold on a node will be proportional to the amount of heap you have available, but there is no fixed limit enforced by Elasticsearch. A good rule-of-thumb is to ensure you keep the number of shards per node below 20 per GB heap it has configured. A node with a 30GB heap should therefore have a maximum of 600\u0026nbsp;shards, but the further below this limit you can keep it the better. This will generally help the cluster stay in good health. \u003c/em\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e\u003cem\u003e\u003cstrong\u003e(Editor’s note: As of 8.3, we have drastically reduced the heap usage per shard, thus updating the rule of thumb in this blog. Please follow \u003c/strong\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/size-your-shards.html#field-count-recommendation\" target=\"_self\"\u003e\u003cem\u003e\u003cstrong\u003edocumentation\u003c/strong\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003cstrong\u003e for 8.3+ versions of Elasticsearch.)\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003chr/\u003e\u003ch2 dir=\"ltr\"\u003eHow does shard size affect performance?\u003c/h2\u003e\u003cp\u003eIn Elasticsearch, each query is executed in a single thread per shard. Multiple shards can however be processed in parallel, as can multiple queries and aggregations against the same shard.\u003c/p\u003e\u003cp\u003eThis means that the minimum query latency, when no caching is involved, will depend on the data, the type of query, as well as the size of the shard. Querying lots of small shards will make the processing per shard faster, but as many more tasks need to be queued up and processed in sequence, it is not necessarily going to be faster than querying a smaller number of larger shards. Having lots of small shards can also reduce the query throughput if there are multiple concurrent queries.\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eThe best way to determine the maximum shard size from a query performance perspective is to \u003c/em\u003e\u003ca href=\"https://www.elastic.co/elasticon/conf/2016/sf/quantitative-cluster-sizing\" target=\"_self\"\u003e\u003cem\u003ebenchmark using realistic data and queries\u003c/em\u003e\u003c/a\u003e\u003cem\u003e. Always benchmark with a query and indexing load representative of what the node would need to handle in production, as optimizing for a single query might give misleading results.\u003c/em\u003e\u003c/p\u003e\u003chr/\u003e\u003ch2 dir=\"ltr\"\u003eHow do I manage shard size?\u003c/h2\u003e\u003cp\u003eWhen using time-based indices, each index has traditionally been associated with a fixed time period. Daily indices are very common, and often used for holding data with short retention period or large daily volumes. These allow retention period to be managed with good granularity and makes it easy to adjust for changing volumes on a daily basis. Data with a longer retention period, especially if the daily volumes do not warrant the use of daily indices, often use weekly or monthly indices in order to keep the shard size up. This reduces the number of indices and shards that need to be stored in the cluster over time.\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003eTIP: If using time-based indices covering a fixed period, adjust the period each index covers based on the retention period and expected data volumes in order to reach the target shard size.\u003c/em\u003e\u003c/p\u003e\u003chr/\u003e\u003cp\u003eTime-based indices with a fixed time interval works well when data volumes are reasonably predictable and change slowly. If the indexing rate can vary quickly, it is very difficult to maintain a uniform target shard size.\u003c/p\u003e\u003cp\u003eIn order to be able to better handle this type of scenarios, the \u003ca href=\"https://www.elastic.co/blog/managing-time-based-indices-efficiently\" target=\"_self\"\u003eRollover and Shrink APIs\u003c/a\u003e were introduced. These add a lot of flexibility to how indices and shards are managed, specifically for time-based indices.\u003c/p\u003e\u003cp\u003eThe \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.5/indices-rollover-index.html\" target=\"_self\"\u003erollover index API\u003c/a\u003e makes it possible to specify the number of documents an index should contain and/or the maximum period documents should be written to it. Once one of these criteria has been exceeded, Elasticsearch can trigger a new index to be created for writing without downtime. Instead of having each index cover a specific time-period, it is now possible to switch to a new index at a specific size, which makes it possible to more easily achieve an even shard size for all indices.\u003c/p\u003e\u003cp\u003eIn cases where data might be updated, there is no longer a distinct link between the timestamp of the event and the index it resides in when using this API, which may make updates significantly less efficient as each update may need to be preceded by a search.\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eIf you have time-based, immutable data where volumes can vary significantly over time, consider using the rollover index API to achieve an optimal target shard size by dynamically varying the time-period each index covers. This gives great flexibility and can help avoid having too large or too small shards when volumes are unpredictable.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\u003chr/\u003e\u003cp\u003eThe \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.5/indices-shrink-index.html\" target=\"_self\"\u003eshrink index API\u003c/a\u003e allows you to shrink an existing index into a new index with fewer primary shards. If an even spread of shards across nodes is desired during indexing, but this will result in too small shards, this API can be used to reduce the number of primary shards once the index is no longer indexed into. This will result in larger shards, better suited for longer term storage of data.\u003cbr /\u003e\u003c/p\u003e\u003chr/\u003e\u003cp style=\"margin-left: 20px;\"\u003e\u003cem\u003e\u003cstrong\u003eTIP: \u003c/strong\u003e\u003c/em\u003e\u003cem\u003eIf you need to have each index cover a specific time period but still want to be able to spread indexing out across a large number of nodes, consider using the shrink API to reduce the number of primary shards once the index is no longer indexed into. This API can also be used to reduce the number of shards in case you have initially configured too many shards.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e\u003chr/\u003e\u003ch2 dir=\"ltr\"\u003eConclusions\u003c/h2\u003e\u003cp\u003eThis blog post has provided tips and practical guidelines around how to best manage data in Elasticsearch. If you are interested in learning more, \"Elasticsearch: the definitive guide\" contains a section about \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/2.x/scale.html\" target=\"_self\"\u003edesigning for scale\u003c/a\u003e, which is well worth reading even though it is a bit old.\u003c/p\u003e\u003cp\u003eA lot of the decisions around how to best distribute your data across indices and shards will however depend on the use-case specifics, and it can sometimes be hard to determine how to best apply the advice available. For more in-depth and personal advice you can engage with us \u003ca href=\"https://www.elastic.co/subscriptions\" target=\"_self\"\u003ecommercially through a subscription\u003c/a\u003e and let our Support and Consulting teams help accelerate your project. If you are happy to discuss your use-case in the open, you can also get help from \u003ca href=\"https://www.elastic.co/community\" target=\"_self\"\u003eour community\u003c/a\u003e and through our public \u003ca href=\"https://discuss.elastic.co\" target=\"_self\"\u003eforum\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003ca href=\"https://www.elastic.co/webinars/manage-elasticsearch-clusters-at-scale-with-ece\" target=\"_self\"\u003eLearn how to manage Elasticsearch at scale.\u003c/a\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003cem\u003eThis post was originally published on September 18, 2017. It was updated on December 16, 2022.\u003c/em\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:29:21.156Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltc81257aac79bef06"],"full_bleed_image":{"title":"elasticsearch-sharding-fullbleed.jpg","uid":"blt3f6104a62d496acf","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:39:23.517Z","updated_at":"2019-01-05T09:39:23.517Z","content_type":"image/jpeg","file_size":"154326","filename":"elasticsearch-sharding-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:27:44.371Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3f6104a62d496acf/5c307b4bc599e1696624125c/elasticsearch-sharding-fullbleed.jpg"},"markdown_l10n":"","publish_date":"2022-12-16T15:46:16.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"elasticsearch-sharding-thumbnail.jpg","uid":"blta55fe6273ba821f9","created_by":"sys_blt57a423112de8a853","updated_by":"blt3e52848e0cb3c394","created_at":"2019-01-05T09:39:18.994Z","updated_at":"2019-05-03T16:52:27.589Z","content_type":"image/jpeg","file_size":"62749","filename":"elasticsearch-sharding-thumbnail.jpg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-03T16:52:44.630Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta55fe6273ba821f9/5c307b46a253ae3e67bc86df/elasticsearch-sharding-thumbnail.jpg"},"title":"How many shards should I have in my Elasticsearch cluster?","title_l10n":"How many shards should I have in my Elasticsearch cluster?","updated_at":"2025-03-10T12:16:06.559Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/how-many-shards-should-i-have-in-my-elasticsearch-cluster","publish_details":{"time":"2025-03-10T12:16:12.880Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte3b7793de7eb5bf0","_version":43,"locale":"en-us","ACL":{},"abstract_l10n":"Today, we are excited to announce the introduction of Elastic Endpoint Security.","author":["blt4990cfe37610ed0f"],"body_l10n":"\u003cp\u003eToday we are excited to announce the introduction of \u003ca href=\"/endpoint-security\"\u003eElastic Endpoint Security\u003c/a\u003e, based on Elastic’s acquisition of Endgame, a pioneer and \u003ca href=\"https://www.endgame.com/mitre-attck-coverage\"\u003eindustry-recognized leader\u003c/a\u003e in endpoint threat prevention, detection, and response based on the MITRE ATT\u0026amp;CK™ matrix. Elastic is combining \u003ca href=\"/siem\"\u003eSIEM\u003c/a\u003e and endpoint security into a single solution to enable organizations to automatically and flexibly respond to threats in real time, whether in the cloud, on-premises, or in hybrid environments. Also announced today, Elastic is eliminating per-endpoint pricing.\u003c/p\u003e\u003cp\u003e“Two key trends in endpoint security —\u0026nbsp;the importance of a strong analytics back-end and the rise of the MITRE ATT\u0026amp;CK framework as a lingua franca —\u0026nbsp;help make the case for greater emphasis on threat hunting and incident response use cases,” said Fernando Montenegro, Principal Analyst at 451 Research. “Elastic’s acquisition of Endgame fits well within these trends, and the combination of SIEM and endpoint security should enable organizations to pursue efficiencies around those use cases.”\u003c/p\u003e\u003cp\u003eEndgame has been validated by numerous independent testing organizations, including NSS Labs, SE Labs, MITRE, and others as having both the strongest preventions and detections available. This was recently illustrated by its performance in \u003ca href=\"https://www.av-comparatives.org/tests/business-security-test-august-september-2019-factsheet/\"\u003ethe AV Comparatives Independent Anti-Virus Test\u003c/a\u003e, where Endgame demonstrated exceptional protection against real-world threats, preventing 99.7% of malware with no cloud connectivity required.\u003c/p\u003e\u003cp\u003eAdditionally, Elastic Endpoint Security brings one of the \u003ca href=\"https://www.endgame.com/blog/technical-blog/heres-how-we-do-numbers\"\u003estrongest sources of endpoint security data\u003c/a\u003e, raw endpoint event data, and alerts to the Elastic Stack, joining the existing logging, security, APM, and infrastructure event collection. With the average threat dwell time exceeding 100 days, shipping, scaling, and storing data efficiently in Elasticsearch makes searching through all of this disparate security-related data practical, easy, and fast. Accordingly, endpoint security is a natural fit for the Elastic Stack to provide prevention against threats and the fastest detection and response to stop attacks at the earliest stages possible.\u003c/p\u003e\u003cp\u003e“Users deserve more from the tools they deploy. That’s why we are providing immediate value today through the simplicity of a single stack to search, store, analyze, and\u0026nbsp;secure\u0026nbsp;your data,” said Shay Banon, founder and chief executive officer of Elastic. “This is an exciting step toward realizing our vision for applying search to multiple use cases, as we are now able to offer users the best threat hunting solution with the best endpoint protection.”\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc6d5cb9a33c0de89/5d9fe365b517f10ef0a935d0/screenshot-elastic-siem-endpoint-security-data-elasticsearch-2-optimized.jpg\" data-sys-asset-uid=\"bltc6d5cb9a33c0de89\" alt=\"screenshot-elastic-siem-endpoint-security-data-elasticsearch-2-optimized.jpg\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eOur journey into SIEM and endpoint security\u003c/h2\u003e\u003cp\u003eTools working in isolation can’t safeguard an organization, and the data that those tools collect isn’t actionable without a centralized management console. Security teams are faced with siloed data, slow query times, and compromised analysis that lacks relevance and context. Organizations already know they need to work in real time; they need to ingest and store all types of data in a way that is unbounded; and they need to produce relevant results and automatically operationalize them into existing and new security workflows.\u003c/p\u003e\u003cp\u003eNearly two years ago, we embarked on a mission to help organizations evolve their security efforts. While the Elastic Stack has been adopted and is used as a security solution for use cases like threat hunting, fraud detection, and security monitoring, we wanted to make it even easier for users to deploy our products for security. We first worked in collaboration with our community to develop the Elastic Common Schema (ECS) to provide an easy way to normalize data from disparate sources from network and host data. Then we launched \u003ca href=\"/siem\"\u003eElastic SIEM\u003c/a\u003e, the world’s first free and open SIEM... but we didn’t stop there.\u003c/p\u003e\u003cp\u003eNow, when you deploy a data collection agent for Elastic SIEM, you can protect the endpoint simultaneously and remove the inefficiency of multiple solutions that can’t respond in time to prevent damage and loss.\u003c/p\u003e\u003cp\u003e“Stopping attacks as early as possible is the goal. That requires the best preventions and the highest fidelity detections on the endpoint. The combination of Endgame’s leading endpoint protection technology with Elastic SIEM creates an interactive workspace for SecOps and threat hunting teams to stop attacks and protect their organizations,” said Nate Fick, formerly CEO of Endgame and now general manager of Elastic Security.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1f87637fb7870298/5d9fe27bf8ca980f8717f6f8/screenshot-resolver-trickbot-enrichments-showing-defender-shutdown-endgame-2-optimized.png\" data-sys-asset-uid=\"blt1f87637fb7870298\" alt=\"screenshot-resolver-trickbot-enrichments-showing-defender-shutdown-endgame-2-optimized.png\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eThe end of endpoint pricing\u003c/h2\u003e\u003cp\u003eIn addition to combining the world’s first free and open SIEM with the best endpoint protection technology, Elastic is eliminating per-endpoint pricing.\u003c/p\u003e\u003cp\u003e“Why should users need to count the number of devices they need to protect? Or choose how many days of threat intelligence data they can afford to retain?” added Banon. “We want organizations to have the best protection, use it everywhere, and not be penalized with per-endpoint pricing.”\u003c/p\u003e\u003cp\u003eElastic customers pay for resource capacity for any solution they use\u0026nbsp;—\u0026nbsp;Elastic Logs, APM, SIEM, App Search, Site Search, Enterprise Search, and now Endpoint Security —\u0026nbsp;with a consistent and transparent pricing framework. This ensures organizations can capture maximum value from their data. With Elastic Endpoint Security, customers get full protection for as many endpoints as they need, and full data collection and shipping without having to compromise.\u003c/p\u003e\u003ch2\u003eSecurity leaders comment on Elastic Endpoint Security\u003c/h2\u003e\u003cp\u003e\u003cstrong\u003eTexas A\u0026amp;M University, Andrew Stokes, Assistant Director and Information Security Officer\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e“We value speed of response and the ability to learn from and analyze our historical data. Elastic Endpoint Security has dramatically dropped our mean time to remediate from seven days to 30 minutes over legacy antivirus, and the Elastic Stack has provided an unparalleled way to store, analyze, and react to data well beyond any competitor in the market. Combining Elastic Endpoint Security and the Elastic Stack into a single, intelligence-led platform will further simplify and automate our security operations.”\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eOptiv, Anthony Diaz, Divisional Vice President, Emerging Services\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\"Elastic is bringing together the integration of a next-generation SIEM, robust visualization engine and a best-in-class endpoint product all backed by the world's leading search technology. This combination provides a foundation for enterprises to combat the growing complexity of cyber threats. Elastic's vision for bringing together these components in an open ecosystem is a revolutionary, yet practical idea that helps organizations of all sizes maximize all of their data to manage their cyber security needs.\"\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eInfotrack, Sebastian Mill, Chief Technology Officer, Global Development\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e“At InfoTrack, we’ve come to realize just how valuable endpoint data can be for gaining visibility into our operations and making sure our infrastructure remains secure. Toward these goals, our innovation team has already been scoping Auditbeat into our environments, but introducing Elastic Endpoint Security takes it to a whole new level. We are intrigued by the ability to stop threats with Elastic Endpoint Security while pairing security event data with some Elastic machine learning-powered anomaly detection. It will be a killer setup.\"\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eSANS Institute, John Pescatore, Director, Emerging Security Trends\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e“When SANS surveyed SOC managers about the tools they wish new SOC hires were skilled in the Elastic (ELK) Stack was one of the top ones mentioned. The components of the ELK stack are used both by SOC analysts and application developers. Having strong EDR capability integrated into the endpoint side of the standard packages deployed by DevOps and CI/CD pipelines can be a real game changer in visibility, detection and prevention of cyber attacks.”\u003c/p\u003e\u003ch2\u003eResources\u003c/h2\u003e\u003cp\u003eIf you want to see Elastic Endpoint Security in action and hear more about our developments, please join us at one of our \u003ca href=\"/elasticon/\"\u003eElastic{ON} Tour\u003c/a\u003e stops in the US, EMEA, or Asia Pacific.\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/security/endpoint-security\" target=\"_self\"\u003eElastic Endpoint Security solutions page\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.endgame.com/resource/product-info/pdf/endgame-endpoint-protection-platform\"\u003eElastic Endpoint documentation\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/siem\"\u003eElastic SIEM solutions page\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/guide/en/siem/guide/current/index.html\"\u003eElastic SIEM documentation\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://discuss.elastic.co/c/siem\"\u003eElastic SIEM community forum\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/webinars/introducing-elastic-siem\"\u003eElastic SIEM webinar recording\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-10-11T15:53:54.978Z","created_by":"bltfefb9f3ab4fd6abcade87a28","disclaimer":["blt20299652b018eb23"],"full_bleed_image":{"uid":"blt20c12adf8ada039c","created_by":"bltfefb9f3ab4fd6abcade87a28","updated_by":"bltfefb9f3ab4fd6abcade87a28","created_at":"2019-10-11T15:53:24.790Z","updated_at":"2019-10-11T15:53:24.790Z","content_type":"image/png","file_size":"71723","filename":"endgame-blog-post.png","title":"endgame-blog-post.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-15T12:31:55.041Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt20c12adf8ada039c/5da0a574daf87c13de87f23f/endgame-blog-post.png"},"markdown_l10n":"","publish_date":"2019-10-15T13:30:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":["endpoint","endgame"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blte41b0699a34eac99","ACL":{},"created_at":"2023-11-06T20:38:53.624Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"edr","label_l10n":"EDR","tags":[],"title":"EDR","updated_at":"2023-11-06T20:38:53.624Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:26.559Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt6ba71b4a02e74776","created_by":"bltfefb9f3ab4fd6abcade87a28","updated_by":"bltfefb9f3ab4fd6abcade87a28","created_at":"2019-10-11T15:53:19.573Z","updated_at":"2019-10-11T15:53:19.573Z","content_type":"image/png","file_size":"49569","filename":"endgame-blog-thumbnail.png","title":"endgame-blog-thumbnail.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-15T12:31:55.041Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ba71b4a02e74776/5da0a56ff8ca980f8717fcb6/endgame-blog-thumbnail.png"},"title":"Introducing Elastic Endpoint Security","title_l10n":"Introducing Elastic Endpoint Security","updated_at":"2025-03-10T12:14:50.692Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/introducing-elastic-endpoint-security","publish_details":{"time":"2025-03-10T12:14:53.940Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt34fc51955689b63a","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["bltd8c9152eb9be7946"],"body_l10n":"\u003cp\u003eKibana provides powerful ways to search and visualize data stored in Elasticsearch. For the purpose of visualizations, Kibana looks for fields defined in Elasticsearch mappings and presents them as options to the user building a chart. But what happens if you forget to define an important value as a separate field in your schema? Or what if you want to combine two fields and treat them as one? This is where Kibana scripted fields come into play.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eScripted fields have actually been around since the early days of Kibana 4. At the time they were introduced, the only way to define them relied on \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.0/modules-scripting-expression.html\" target=\"_self\"\u003eLucene Expressions\u003c/a\u003e,\u0026nbsp;a scripting language in Elasticsearch which deals exclusively with numeric values. As a result, the power of scripted fields was limited to a subset of use cases. In 5.0, Elasticsearch introduced \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.0/modules-scripting-painless.html\" target=\"_self\"\u003ePainless\u003c/a\u003e, a safe and powerful scripting language that allows operating on a variety of data types, and as a result, scripted fields in Kibana 5.0 are that much more powerful.\u003c/p\u003e\u003cp\u003eIn the rest of this blog, we'll walk you through how to create scripted fields for common use cases. We'll do so by relying on a dataset from \u003ca href=\"https://www.elastic.co/guide/en/kibana/5.0/tutorial-load-dataset.html\" target=\"_self\"\u003eKibana Getting Started tutorial\u003c/a\u003e\u0026nbsp;and use an instance of Elasticsearch and Kibana running in \u003ca href=\"https://cloud.elastic.co/\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e, which you can spin up for free.\u003c/p\u003e\u003cp\u003eThe following video walks you through how to spin up a personal Elasticsearch and Kibana\u0026nbsp;instance in Elastic Cloud and load a sample\u0026nbsp;dataset\u0026nbsp;into it.\u0026nbsp;\u003cbr /\u003e\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/6gWkzXXhT69tUa7uRtvJ96.jpg\" data-uuid=\"6gWkzXXhT69tUa7uRtvJ96\" data-v=\"4\" data-type=\"inline\" width=\"677\"/\u003e\u003c/div\u003e\u003ch2\u003eHow scripted fields work\u003c/h2\u003e\u003cp\u003eElasticsearch allows you to specify scripted fields on every request. Kibana improves on this by allowing you to define a scripted field once in the Management section, so it can be used in multiple places in the UI going forward. Note that while Kibana stores scripted fields alongside its other configuration in the .kibana index, this configuration is Kibana-specific, and Kibana scripted fields are not exposed to API users of Elasticsearch.\u003c/p\u003e\u003cp\u003eWhen you go to define a scripted field in Kibana, you'll be given a choice of scripting language, allowing you to pick from all the languages installed on the Elasticsearch nodes that have dynamic scripting enabled. By default that is \"expression\" and \"painless\" in 5.0 and just \"expression\" in 2.x. You can install other scripting languages and enable dynamic scripting for them, but it is not recommended because they cannot be sufficiently \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-scripting-security.html\" target=\"_self\"\u003esandboxed\u003c/a\u003e\u0026nbsp;and have been deprecated.\u003c/p\u003e\u003cp\u003eScripted fields operate on one Elasticsearch document at a time, but can reference multiple fields in that document. As a result, it is appropriate to use scripted fields to combine or transform fields within a single document, but not perform calculations based on on multiple documents (e.g. time-series math). Both Painless and Lucene expressions operate on fields stored in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/doc-values.html\" target=\"_self\"\u003edoc_values\u003c/a\u003e.\u0026nbsp;So for string data, you will need to have the string to be stored in data type keyword. Scripted fields based on Painless also cannot operate directly on _source.\u003c/p\u003e\u003cp\u003eOnce scripted fields are defined in \"Management\", user can interact with them the same way as with other fields in the rest of Kibana. Scripted fields automatically show up in the Discover field list and are available in Visualize for the purposes of creating visualizations. Kibana simply passes scripted field definitions to Elasticsearch at query time for evaluation. The resulting dataset is combined with other results coming back from Elasticsearch and presented to the user in a table or a chart.\u003c/p\u003e\u003cp\u003eThere are a couple of known limitations when working with scripted fields at the time of writing this blog. You can apply most Elasticsearch aggregations available in Kibana visual builder to scripted fields, with the most notable exception of the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-aggregations-bucket-significantterms-aggregation.html\" target=\"_self\"\u003esignificant terms aggregation\u003c/a\u003e. You can also filter on scripted fields via the filter bar in Discover, Visualize, and Dashboard, although you have to take care to write proper scripts that return well-defined values, as we show below. It is also important to refer to the \"Best Practices\" section below to ensure you do not destabilize your environment, when using scripted fields.\u003c/p\u003e\u003cp\u003eThe following video shows\u0026nbsp;how to use Kibana to create scripted fields.\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/SKHYsZcKZHq9u7GTNGWPaL.jpg\" data-uuid=\"SKHYsZcKZHq9u7GTNGWPaL\" data-v=\"4\" data-type=\"inline\" width=\"677\"/\u003e\u003c/div\u003e\u003ch2\u003eScripted field examples\u003c/h2\u003e\u003cp\u003eThis section presents a few examples of Lucene expressions and Painless scripted fields in Kibana in common scenarios. As mentioned above, these examples were developed on top of a dataset from \u003ca href=\"https://www.elastic.co/guide/en/kibana/5.0/tutorial-load-dataset.html\" target=\"_self\"\u003eKibana Getting Started tutorial\u003c/a\u003e\u0026nbsp;and assume you are using Elasticsearch and Kibana 5.1.1, as there are a couple of known issues related to filtering and sorting on certain types of scripted fields in earlier versions.\u003c/p\u003e\u003cp\u003eFor the most part, scripted fields should work out of the box, as Lucene expressions and Painless are enabled by default in Elasticsearch 5.0. The only exception are scripts that require regex-based parsing of fields, which will require you to set the following setting in elasticsearch.yml to turn on regex matching for Painless: script.painless.regex.enabled: true\u003c/p\u003e\u003ch3\u003ePerform a calculation on a single field\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e: Calculate kilobytes from bytes\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e:\u0026nbsp;expressions\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e:\u0026nbsp;number\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003e doc['bytes'].value / 1024\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNote: Keep in mind that Kibana scripted fields work on a single document at a time only, so there is no way to do time-series math in a scripted field.\u003cbr /\u003e\u003c/p\u003e\u003ch3\u003eDate math resulting in number\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e:\u0026nbsp;Parse date into hour-of-day\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e: expressions\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e:\u0026nbsp;number\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eLucene expressions provide a whole host of \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.0/modules-scripting-expression.html#_date_field_api\" target=\"_self\"\u003edate manipulation functions\u003c/a\u003e\u0026nbsp;out-of-the-box. However, since Lucene expressions only return numerical values, we'll have to use Painless to return a string-based day-of-week (below).\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e doc['@timestamp'].date.hourOfDay\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNote: Script above will return 1-24\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003edoc['@timestamp'].date.dayOfWeek\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNote: Script above will return 1-7\u003c/p\u003e\u003ch3\u003eCombine two string values\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e:\u0026nbsp;Combine source and destination or first and last name\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e:\u0026nbsp;painless\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e:\u0026nbsp;string\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003e doc['geo.dest.keyword'].value + ':' + doc['geo.src.keyword'].value\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNote: Because scripted fields need to operate on fields in doc_values, we are using .keyword versions of strings above.\u003c/p\u003e\u003ch3\u003eIntroducing logic\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e: Return label \"big download\" for any document with bytes over 10000\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e: painless\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e: string\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003e if (doc['bytes'].value \u0026gt; 10000) { \u003cbr /\u003e return \"big download\";\u003cbr /\u003e}\u003cbr /\u003ereturn \"\";\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eNote: When introducing logic, ensure that every execution path has a well-defined return statement and a well-defined return value (not null). For instance, above scripted field will fail with a compile error when used in Kibana filters\u0026nbsp;without the return\u0026nbsp;statement at the end or if the statement returns null. Also keep in mind that breaking up logic into functions is not supported within Kibana scripted fields.\u0026nbsp;\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eReturn substring\u003cbr /\u003e\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e: Return the part after the last slash in the URL\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e: painless\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e: string\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003e def path = doc['url.keyword'].value;\u003cbr /\u003eif (path != null) {\u003cbr /\u003e int lastSlashIndex = path.lastIndexOf('/');\u003cbr /\u003e if (lastSlashIndex \u0026gt; 0) {\u003cbr /\u003e return path.substring(lastSlashIndex+1);\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003ereturn \"\";\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eNote: Whenever possible, avoid using regex expressions to extract substrings, as indexOf() operations are less resource-intensive and less error-prone.\u0026nbsp;\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eMatch a string using regex, and take action on a match\u003cbr /\u003e\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e: Return a string \"error\" if a substring \"error\" is found in field \"referer\", otherwise return a string \"no error\".\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e: painless\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e: string\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003eif (doc['referer.keyword'].value =~ /error/) { \u003cbr /\u003ereturn \"error\"\u003cbr /\u003e} else {\u003cbr /\u003ereturn \"no error\"\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eNote: Simplified regex syntax is useful for conditionals based on a regex match.\u0026nbsp;\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eMatch a string and return that match\u003cbr /\u003e\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e: Return domain, the string after the last dot in the \"host\" field.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e: painless\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e: string\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003edef m = /^.*\\.([a-z]+)$/.matcher(doc['host.keyword'].value);\u003cbr /\u003eif ( m.matches() ) {\u003cbr /\u003e return m.group(1)\u003cbr /\u003e} else {\u003cbr /\u003e return \"no match\"\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eNote: Defining an object via the regex matcher() functions allows you to extract groups of characters that matched the regex and return them.\u0026nbsp;\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eMatch a number and return that match\u003cbr /\u003e\u003c/h3\u003e\u003cul\u003e\u003cli\u003eExample: Return the first octet of the IP address (stored as a string) and treat it as a number.\u003c/li\u003e\u003cli\u003eLanguage: painless\u003c/li\u003e\u003cli\u003eReturn type: number\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003e def m = /^([0-9]+)\\..*$/.matcher(doc['clientip.keyword'].value);\u003cbr /\u003eif ( m.matches() ) {\u003cbr /\u003e return Integer.parseInt(m.group(1))\u003cbr /\u003e} else {\u003cbr /\u003e return 0\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eNote: It is important to return the right data type in a script. Regex match returns a string, even if a number is matched, so you should explicitly convert it to an integer on return.\u0026nbsp;\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eDate math resulting in strings\u003cbr /\u003e\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eExample\u003c/strong\u003e: Parse date into day-of-week into string\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLanguage\u003c/strong\u003e: painless\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReturn type\u003c/strong\u003e: string\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003eLocalDateTime.ofInstant(Instant.ofEpochMilli(doc['@timestamp'].value), ZoneId.of('Z')).getDayOfWeek().getDisplayName(TextStyle.FULL, Locale.getDefault())\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eNote: Since Painless supports all of Java's native types, it provides access to native functions around those types, such as \u003ca href=\"https://docs.oracle.com/javase/8/docs/api/java/time/LocalDateTime.html#getDayOfWeek--\" target=\"_self\"\u003eLocalDateTime()\u003c/a\u003e, useful in performing more advanced date math.\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eBest practices\u003cbr /\u003e\u003c/h2\u003e\u003cp dir=\"ltr\"\u003eAs you see, the Painless scripted language provides powerful ways of extracting useful information out of arbitrary fields stored in Elasticsearch via Kibana scripted fields. However, with great power comes great responsibility.\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\"\u003eBelow we outline a few best practices around using Kibana scripted fields.\u003c/p\u003e\u003cul\u003e\u003cli\u003eAlways use a development environment to experiment with scripted fields. Because scripted fields are immediately active after you save them in the Management section of Kibana (e.g. they appear in the Discover screen for that index pattern for all users), you should not develop scripted fields directly in production. We recommend that you try your syntax first in a development environment, evaluate the impact of scripted fields on realistic data sets and data volumes in staging, and only then promote them to production.\u0026nbsp;\u003c/li\u003e\u003cli\u003eOnce you gain confidence that the scripted field provides value to your users, consider modifying your ingest to extract the field at index time for new data. This will save Elasticsearch processing at query time and will result in faster response times for Kibana users. You can also use the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.0/docs-reindex.html\" target=\"_self\"\u003e_reindex\u003c/a\u003e API in Elasticsearch to re-index existing data.\u003c/li\u003e\u003c/ul\u003e\u003ca href=\"https://www.elastic.co/webinars/hidden-gems-in-kibana\" target=\"_self\"\u003e\u003cspan\u003eDiscover how to get the most out of you data using Kibana like a pro.\u003c/span\u003e\u003c/a\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:38:19.704Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"bltbf74335e81fdbea7","ACL":{},"_version":1,"content_type":"image/png","created_at":"2021-01-13T23:55:05.856Z","created_by":"bltde77f2161b811714","file_size":"39216","filename":"blog-banner-generic-elastic.png","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-14T14:09:24.839Z","user":"blt36e890d06c5ec32c"},"tags":[],"title":"blog-banner-generic-elastic.png","updated_at":"2021-01-13T23:55:05.856Z","updated_by":"bltde77f2161b811714","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf74335e81fdbea7/5fff8859e4028c63a64d9be2/blog-banner-generic-elastic.png"},"markdown_l10n":"","publish_date":"2016-12-13T17:45:34.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt226f04bb0dd0936b","ACL":{},"created_at":"2023-11-06T20:46:35.144Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"personalization","label_l10n":"Personalization","tags":[],"title":"Personalization","updated_at":"2023-11-06T20:46:35.144Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:12.713Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":null,"title":"Using Painless in Kibana scripted fields","title_l10n":"Using Painless in Kibana scripted fields","updated_at":"2025-03-10T12:13:28.735Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/using-painless-kibana-scripted-fields","publish_details":{"time":"2025-03-10T12:13:33.998Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt64b3445f5e84599f","_version":24,"locale":"en-us","ACL":{},"abstract_l10n":"Windows access token manipulation attacks are well known and abused from an offensive perspective, but rely on an extensive body of arcane Windows security internals. In this blog post, we demystify how access tokens work in Windows environments.","author":["bltc2baef8dab82b56d"],"body_l10n":"\u003cp\u003eThis blog series is aimed at giving defense practitioners a thorough understanding of Windows access tokens for the purposes of detection engineering.\u0026nbsp;\u003c/p\u003e\u003cp\u003eHere in Part 1, we'll cover key concepts in Windows Security.\u0026nbsp;The desired outcome is to help defenders understand how access tokens work in Windows environments.\u0026nbsp;In Part 2 of the\u0026nbsp;series, we’ll build on the concepts outlined in Part 1\u0026nbsp;and cover\u0026nbsp;how attackers abuse legitimate Windows \u003ca href=\"https://attack.mitre.org/techniques/T1134/\"\u003efunctionality\u003c/a\u003e to move laterally and compromise entire Active Directory domains in depth.\u003c/p\u003e\u003cp\u003eAs a note of caution, this blog has deliberately attempted to abstract away the workings of specific Windows network authentication protocols (e.g., NTLM and Kerberos) and Security Support Providers (e.g., CredSSP, Negotiate, etc.). As a consequence, there may be instances where behavior unique to these protocols/packages differs with the behavior described below (i.e., Kerberos constrained delegation). Additionally, this blog owes a huge debt of gratitude to \u003cem\u003eProgramming Windows Security\u003c/em\u003e by Keith Brown which is a fantastic resource for learning more about fundamental Windows security concepts.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eLogon sessions and access tokens\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eThe key concept to grasp in order to understand authentication in Windows environments is the relationship between \u003cstrong\u003elogon sessions\u003c/strong\u003e and \u003cstrong\u003eaccess tokens\u003c/strong\u003e. A logon session is used to represent the \u003cem\u003epresence\u003c/em\u003e of a user on a machine and begins when a user is successfully authenticated and ends when the user logs off.\u003c/p\u003e\u003cp\u003eFor example, when a user physically logs on to a Windows workstation (i.e., interactively), they supply a username and password, which is then checked by the \u003ca href=\"https://docs.microsoft.com/en-us/windows-server/security/windows-authentication/credentials-processes-in-windows-authentication\"\u003eLocal Security Authority\u003c/a\u003e (LSA). If the account is a local account (i.e., only valid on that specific computer) the LSA will check the credentials against its own security database. In the case of a Windows Active Directory domain environment, the authentication attempt is referred to the closest domain controller (DC) which will process the request and authenticate the user.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc5d931ae03cda6fb/5f3c5f2b6bbc05271064339a/1-windows-logon-session-access-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"bltc5d931ae03cda6fb\" alt=\"1-windows-logon-session-access-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 1 - Windows logon process for an interactive user\u003c/figcaption\u003e\u003cp\u003eOnce the user has been successfully authenticated, the LSA will create a new \u003cstrong\u003elogon session\u003c/strong\u003e and produce an \u003cstrong\u003eaccess token\u003c/strong\u003e, as shown above.\u003csup\u003e1\u003c/sup\u003e\u0026nbsp;A logon session can have multiple access tokens associated with it, but an access token can only ever be linked to one logon session (which is typically the successful logon attempt that generated it).\u003csup\u003e2\u003c/sup\u003e\u0026nbsp;Windows has legitimate functionality which can be used to change the logon session (and hence cached credentials) that your current token is associated with. This will be covered in more detail in part 2.\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003eEvery new logon session is identifiable via a 64 bit locally unique identifier (LUID), referred to as the logon ID, and every access token must contain an Authentication Id (or AuthId) parameter that identifies the origin/linked logon session via this LUID. This is highlighted in the diagram below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5e0d9d711f5c3946/5f3c5f38752d292b6ca4e530/2-authid-parameter-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"blt5e0d9d711f5c3946\" alt=\"2-authid-parameter-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 2 - Every access token is linked to a sole logon session, which is identifiable via the AuthID parameter. The AuthID field contains a 64 bit LUID, or logon ID, which identifies the \u003cstrong\u003eorigin\u003c/strong\u003e logon session.\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThe main function of an access token is to act as a “volatile repository for security settings associated with the logon session” which can be adjusted and modified on the fly.\u003csup\u003e2\u003c/sup\u003e\u0026nbsp;In this sense, access tokens act as a \u003cstrong\u003eproxy\u003c/strong\u003e or \u003cstrong\u003estand-in\u003c/strong\u003e for the logon session and so when making security decisions, Windows developers never interact with the logon session itself (which is “hidden” away in lsass), but with an access token which \u003cstrong\u003erepresents\u003c/strong\u003e it (and hence predominantly via the Windows access token API).\u0026nbsp;\u003c/p\u003e\u003cp\u003eTherefore, a developer can copy existing tokens (\u003ca href=\"https://docs.microsoft.com/en-gb/windows/win32/api/securitybaseapi/nf-securitybaseapi-duplicatetokenex?redirectedfrom=MSDN\"\u003eDuplicateTokenEx\u003c/a\u003e), modify the security settings for a given token (\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-gettokeninformation\"\u003eGet\u003c/a\u003e/\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-settokeninformation\"\u003eSetTokenInformation\u003c/a\u003e) etc.\u0026nbsp;to their heart's content, but these tokens are still just abstractions representing the security settings from the\u003cem\u003e originating\u003c/em\u003e logon session.\u003c/p\u003e\u003cp\u003eMost importantly, the access token represents the \u003cstrong\u003esecurity context\u003c/strong\u003e of the user. The security context can be defined as the privileges and permissions that a user has on a specific workstation (and across the network). An access token caches a number of \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/access-tokens\"\u003eattributes\u003c/a\u003e which determine its security context, such as:\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe security identifier (SID) for the user\u003c/li\u003e\u003cli\u003eGroup memberships\u003c/li\u003e\u003cli\u003ePrivileges held\u003c/li\u003e\u003cli\u003eA logon ID which \u003cem\u003ereferences\u003c/em\u003e the\u003cstrong\u003e origin\u003c/strong\u003e logon session\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eFor example, the screenshot below shows the cached security attributes for an access token using James Forshaw’s \u003ca href=\"https://github.com/googleprojectzero/sandbox-attacksurface-analysis-tools\"\u003eTokenViewer\u003c/a\u003e:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcbe78d08b45c817d/5f3c5f43327a6201d7ebc9cf/3-cached-security-attributes-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"bltcbe78d08b45c817d\" alt=\"3-cached-security-attributes-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 3 -\u0026nbsp;TokenViewer revealing the cached security attributes stored in an access token\u003c/figcaption\u003e\u003cp\u003e\u003cspan\u003eAs discussed previously, the Authentication ID parameter, which is the key link between an access token and the logon session that it represents, contains a 64 bit LUID (logon ID) which identifies the origin logon session that this access token is associated with. Note also\u0026nbsp;that it is possible to infer a number of other conclusions about the state of this token, e.g., it is a primary token, it is not elevated (medium integrity),\u0026nbsp;\u003cspan\u003eand the user is an administrator (\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winnt/ne-winnt-token_elevation_type\"\u003eElevation Type\u003c/a\u003e = limited means the token is a ‘filtered’ admin token and hence UAC is enabled)\u003c/span\u003e.\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWhenever a thread \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/interaction-between-threads-and-securable-objects\"\u003eattempts to access a securable object\u003c/a\u003e managed by the Windows kernel, such as a process, thread, handle, semaphore, token, etc., Windows will perform an \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-accesscheck\"\u003eaccess check\u003c/a\u003e. To perform this check, Windows needs three pieces of information\u003csup\u003e2\u003c/sup\u003e:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eWho\u003c/strong\u003e is requesting access?\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eWhat\u003c/strong\u003e are their intentions with the object?\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eWho\u003c/strong\u003e can access the object?\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eHence, Windows will first check the token associated with the calling thread and look at the authorization attributes cached in it (e.g., user sid, group memberships, privileges etc.). Secondly, Windows will look at the desired \u003ca href=\"https://docs.microsoft.com/en-gb/windows/win32/secauthz/access-rights-and-access-masks\"\u003eaccess\u003c/a\u003e requested by the thread. In the Windows security model you \u003cstrong\u003emust\u003c/strong\u003e state your intentions upfront; for performance reasons an access check only occurs \u003cem\u003eonce\u003c/em\u003e and no further checks are performed on any additional handle operations (unless a user attempts to perform an action that the handle did not have rights to, e.g., write to a read-only handle).\u0026nbsp;Thirdly, Windows will retrieve the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/security-descriptors\"\u003esecurity descriptor\u003c/a\u003e for the target object. The security descriptor contains a discretionary access control list (\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/access-control-lists\"\u003eDACL\u003c/a\u003e) which specifies what users/groups have access to the object and the \u003cem\u003etype \u003c/em\u003eof access granted.\u0026nbsp;\u003c/p\u003e\u003cp\u003eBased on these three sources of information, Windows can give a boolean answer to whether a principal has access to a given object. This is why every process \u003cstrong\u003emust\u003c/strong\u003e have a primary token; it is the user that is “charged” for any objects that process attempts to access.\u003csup\u003e2\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eAs a note, some \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/privilege-constants\"\u003eprivileges\u003c/a\u003e can be thought of as simply enabling a user to bypass/skip the access check in the kernel for a given object. For example, if a token has the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openprocess\"\u003eSeDebugPrivilege\u003c/a\u003e privilege enabled, the Windows kernel will skip the DACL checks for any process and thread objects (hence why it is so powerful).\u003csup\u003e3\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eFollowing successful authentication from an interactive logon, Windows will execute the user’s shell (normally explorer.exe) on behalf of the newly logged-on user. The operating system performs this action by using the newly minted access token to spawn explorer.exe as that user via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-createprocessasusera\"\u003eCreateProcessAsUserA\u003c/a\u003e. This function takes a handle to a token and spawns a new process as the user specified in the token (i.e., in a \u003cem\u003edifferent\u003c/em\u003e security context).\u003c/p\u003e\u003cp\u003eTypically, every process created by the user is a child of the shell process (i.e., explorer.exe)\u003csup\u003e4\u003c/sup\u003e\u0026nbsp;and every new process will (by default) run in the \u003cstrong\u003esame\u003c/strong\u003e security context as its parent; hence the child process will inherit its parent’s access token upon creation.\u003csup\u003e5\u003c/sup\u003e\u0026nbsp;Therefore, \u003cem\u003eall\u003c/em\u003e processes will inherit their \u003cem\u003eown\u003c/em\u003e local copy of an access token.\u003c/p\u003e\u003cp\u003eAs stated previously, access tokens act as a local “volatile repository” for the security settings associated with the logon session. As each process has its \u003cem\u003eown\u003c/em\u003e local copy of an access token, a process can modify the volatile security settings stored in its copy without affecting other processes.\u003csup\u003e2\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eFor example, a browser such as Chrome may want to create a \u003cem\u003erestricted\u003c/em\u003e version of its access token in order to effectively \u003ca href=\"https://chromium.googlesource.com/chromium/src/+/master/docs/design/sandbox.md\"\u003esandbox\u003c/a\u003e the application in the event an attacker is able to exploit the browser and obtain arbitrary code execution on the compromised machine. As a consequence of the sandbox, any actions performed by the attacker will be restricted and help prevent further damage. As previously discussed, \u003cem\u003eall\u003c/em\u003e access checks in Windows make decisions based on the attributes stored in the calling thread’s token, and so by ‘hardening’ the token a developer can restrict its access.\u003c/p\u003e\u003cp\u003eThe key point is that Chrome can modify its local copy of the token \u003cem\u003ewithout\u003c/em\u003e affecting other applications. This can be achieved via APIs such as \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-adjusttokengroups\"\u003eAdjustTokenGroups\u003c/a\u003e/\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-adjusttokenprivileges\"\u003eAdjustTokenPrivileges\u003c/a\u003e, which can be used to \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/enabling-and-disabling-privileges-in-c--\"\u003edisable\u003c/a\u003e dangerous groups and privileges, respectively. Alternatively, a new restricted copy of a specified access token can be created with \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-createrestrictedtoken\"\u003eCreateRestrictedToken\u003c/a\u003e.\u0026nbsp;As an example, the relevant functionality in the chromium source code can be \u003ca href=\"https://github.com/chromium/chromium/blob/4e88a3c4fa53bf4d3622d07fd13f3812d835e40f/sandbox/win/src/restricted_token.cc#L65\"\u003efound here\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eThis is so important because, as discussed above, access tokens are the \u003cstrong\u003ecore\u003c/strong\u003e component of the Windows security model and so by being able to change the information cached in them, a developer can limit \u003cstrong\u003ewhat\u003c/strong\u003e securable objects a token can touch and hence restrict its access across a system.\u003c/p\u003e\u003cp\u003eThe diagram below summarizes the logon process and an example\u0026nbsp;access check for an interactive user, \u003cstrong\u003eASTRO\\cosmo\u003c/strong\u003e:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7b021068d99d5ea2/5f3c5f8760261e2e581f214f/4-logon-process-access-control-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"blt7b021068d99d5ea2\" alt=\"4-logon-process-access-control-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 4 -\u0026nbsp;An overview of the Windows logon process and access checks for an interactive logon\u003c/figcaption\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eNetwork authentication\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eHaving covered local authentication and access control, what happens under the hood when a user needs to access some resource located across the network? For example, a user could attempt to view the available shares on another host by running the following command:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb93047fd50346e0/5f3c5f93327a6201d7ebc9d3/5-attempt-available-shares-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"blteb93047fd50346e0\" alt=\"5-attempt-available-shares-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 5 -\u0026nbsp;Attempt to view available shares on the remote domain controller, \\\\MISTAKENOT-DC-1\u003c/figcaption\u003e\u003cp\u003eThe user’s logon session is \u003cstrong\u003eunique\u003c/strong\u003e to their workstation (as is their access token and privileges) and they cannot simply send their access token over the wire. The token would be meaningless as it \u003cem\u003edoes not\u003c/em\u003e correspond to a valid logon session on the remote host. Furthermore, this authentication mechanism would be an obvious target for replay attacks.\u003csup\u003e2\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eIn this case, the user needs to \u003cstrong\u003ere-authenticate\u003c/strong\u003e and establish a \u003cstrong\u003enew\u003c/strong\u003e logon session on the remote machine (assuming the user has access). For an interactive logon (and actually all other logon types like service, batch, etc.,\u0026nbsp;\u003cem\u003eexcept\u003c/em\u003e network\u003csup\u003e6\u003c/sup\u003e) Windows will \u003cem\u003e\u003cstrong\u003eautomatically\u003c/strong\u003e\u003c/em\u003e cache the credentials as part of the Windows single sign-on (SSO) mechanism.\u003csup\u003e7\u003c/sup\u003e\u0026nbsp;This is the intended design of the Windows SSO mechanism and prevents the user from having to constantly re-enter their password when accessing network resources.\u003c/p\u003e\u003cp\u003eAs a consequence, access tokens which link back to these types of logon sessions \u003cem\u003ecan\u003c/em\u003e authenticate to remote hosts and Windows will \u003cstrong\u003eautomatically\u003c/strong\u003e authenticate on the users behalf whenever a network resource is accessed by a thread or process.\u003csup\u003e8\u003c/sup\u003e\u0026nbsp;Note that Windows will \u003cstrong\u003ealways\u003c/strong\u003e use the credentials cached in the logon session that the access token is linked to when authenticating remotely\u0026nbsp;(e.g., Windows will find the token’s linked logon session, via the AuthId, and use the credentials cached for that logon session, as shown below).\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt985c90d304c8a2e9/5f3d9001004c131277a52a66/access-token-linked-session-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"blt985c90d304c8a2e9\" alt=\"access-token-linked-session-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003cspan\u003e\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 6 - Relationship between an access token, its linked logon session, and the credentials cached for that logon session\u003c/figcaption\u003e\u003cp\u003eTherefore, in order to establish a new logon session, the SMB server will need to authenticate the client over the network. In Windows domains, network authentication is typically performed via \u003ca href=\"https://docs.microsoft.com/en-us/windows-server/security/kerberos/kerberos-authentication-overview\"\u003eKerberos\u003c/a\u003e or the legacy challenge-response protocol \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthn/microsoft-ntlm\"\u003eNTLM\u003c/a\u003e. Irrespective of the network authentication protocol used, on receiving an authentication request the target host will forward the credential information to the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthn/key-distribution-center\"\u003eDC\u003c/a\u003e and, following successful authentication, establish a new \u003cem\u003enetwork\u003c/em\u003e login session for the user (i.e.,\u0026nbsp;\u003cstrong\u003ethis login\u003c/strong\u003e “\u003cstrong\u003erepresents a remote client”\u003c/strong\u003e).\u003csup\u003e2\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eNetwork logins \u003cstrong\u003edo not\u003c/strong\u003e cache credentials and therefore you cannot use this token to authenticate to another remote host.\u003csup\u003e9\u003c/sup\u003e\u0026nbsp;This is commonly referred to as the ‘double hop’ problem. Note that due to the inherent \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthn/microsoft-ntlm\"\u003edesign\u003c/a\u003e of the NTLM challenge response protocol (e.g., the client encrypts a challenge with the user’s NTLM hash) it fundamentally does not support credential delegation.\u003c/p\u003e\u003cp\u003eMost importantly from the server’s perspective, following the successful authentication of the remote user, it is presented with a newly minted\u003cem\u003e \u003c/em\u003e\u003cstrong\u003eaccess token\u003c/strong\u003e which represents the network logon of the remote client. The diagram below illustrates this process:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc34cb1078b03baab/5f3c5fa0752d292b6ca4e534/6-network-logon-blog-windows-tokens-for-defenders.png\" data-sys-asset-uid=\"bltc34cb1078b03baab\" alt=\"6-network-logon-blog-windows-tokens-for-defenders.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 7 - The network authentication process when a user attempts to access a remote resource, such as an SMB file share\u003c/figcaption\u003e\u003cp\u003eThis neatly leads to the second key concept for Windows access tokens: \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/com/impersonation\"\u003e\u003cstrong\u003eimpersonation\u003c/strong\u003e\u003c/a\u003e. As previously mentioned, access tokens encode a wealth of information about the security context of the user and enable a handy way for developers to make “localized” changes to this context \u003cem\u003ewithout\u003c/em\u003e affecting other processes.\u003csup\u003e2\u003c/sup\u003e\u0026nbsp;However, in \u003cstrong\u003emulti-threaded\u003c/strong\u003e applications, problems and difficult-to-debug race conditions may arise if different threads start enabling/disabling different privileges or modifying default token DACLs.\u003csup\u003e2 10\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eAs a result, Windows has a feature called impersonation. By default \u003cem\u003eall\u003c/em\u003e threads will inherit the same security context as their process’s primary token. However, impersonation allows a thread to switch to a \u003cem\u003edifferent\u003c/em\u003e security context.\u0026nbsp;Specifically, it enables threads to have their own local copy of a token; known as an impersonation token.\u0026nbsp;This is the best way to remember the distinction between primary and impersonation tokens, in that impersonation tokens are always applied to threads, whereas primary tokens are associated with processes. In this way, the SMB server can handle each incoming client request in a separate thread and impersonate the access token representing the remote client.\u003c/p\u003e\u003cp\u003eAlso note that switching security context has two implications. The first is that\u0026nbsp;\u003cstrong\u003elocally\u003c/strong\u003e the thread is now impersonating a different access token, and hence any \u003cstrong\u003elocal\u003c/strong\u003e access checks will be performed using this new token. Secondly, as this impersonated token may be linked to a \u003cstrong\u003edifferent \u003c/strong\u003elogon session (and therefore potentially have \u003cem\u003edifferent\u003c/em\u003e cached credentials (if a non-network login)) the thread’s security context \u003cstrong\u003eremotely\u003c/strong\u003e is also \u003cem\u003edifferent\u003c/em\u003e. Furthermore, as we shall see in the next blog post in this series, do not always assume that the cached credentials stored in lsass \u003cstrong\u003ematch\u003c/strong\u003e the user specified in the token.\u003c/p\u003e\u003cp\u003eIn summary, from the perspective of a listening server process (say an SMB file server), the following steps must occur following a connection request from a remote client:\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe user is authenticated and a new logon session is created (\u003cstrong\u003eNETWORK_ONLY\u003c/strong\u003e)\u003c/li\u003e\u003cli\u003eThe server process is presented with a handle to an impersonation token which links back to the remote client’s new\u003cstrong\u003e network logon session\u003c/strong\u003e\u003c/li\u003e\u003cli\u003eThe server can use this token to impersonate the client to perform work on their behalf\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThis approach has the added benefit of making use of the existing Windows’ access control model, as all actions performed while impersonating are under the security context of the user’s identity (hence any local access check decisions will use the information cached in the impersonated user’s token). Therefore, if that user does not already have access to a specific file on a share, they will be denied access.\u003c/p\u003e\u003cp\u003eFor most of Windows’ key IPC mechanisms (e.g., named pipes, RPC, COM) this process is handled automatically. The server needs only to call the appropriate API in order to obtain a handle to the remote clients’ security context (i.e., access token) and start impersonating the client via functions such as\u003csup\u003e2\u003c/sup\u003e:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-impersonateloggedonuser\"\u003eImpersonateLoggedOnUser\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/combaseapi/nf-combaseapi-coimpersonateclient\"\u003eCoImpersonateClient\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/rpcdce/nf-rpcdce-rpcimpersonateclient\"\u003eRpcImpersonateClient\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/namedpipeapi/nf-namedpipeapi-impersonatenamedpipeclient\"\u003eImpersonateNamedPipeClient\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://docs.microsoft.com/en-gb/windows/win32/api/ddeml/nf-ddeml-ddeimpersonateclient\"\u003eDdeImpersonateClient\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003e\u003cstrong\u003eConclusion\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eHopefully this has been an informative overview of some key concepts in Windows Security. Stay tuned for Part 2 of this blog series, where we’ll build on the concepts outlined above and cover in more depth how attackers abuse legitimate Windows \u003ca href=\"https://attack.mitre.org/techniques/T1134/\"\u003efunctionality\u003c/a\u003e to move laterally and compromise entire Active Directory domains, and how you can detect and respond to access token manipulation within your environment.\u003c/p\u003e\u003cp\u003eReady for holistic data protection with \u003ca href=\"https://www.elastic.co/security\"\u003eElastic Security\u003c/a\u003e? Try it free today, or experience our latest version on \u003ca href=\"https://www.elastic.co/elasticsearch/service\"\u003eElasticsearch Service\u003c/a\u003e on Elastic Cloud.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eReferences\u003c/h2\u003e\u003col\u003e\u003cli\u003e\u003cspan\u003eWith \u003ca href=\"https://docs.microsoft.com/en-us/windows/security/identity-protection/user-account-control/how-user-account-control-works\"\u003eUAC\u003c/a\u003e enabled, Windows actually creates two tokens for an administrative user: a filtered user token and a ‘linked’ administrative token. Therefore, this is a slightly simplified description. For more info see: \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://www.tiraniddo.dev/2017/05/reading-your-way-around-uac-part-1.html\"\u003ehttps://www.tiraniddo.dev/2017/05/reading-your-way...\u003c/a\u003e\u003c/span\u003e / \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://www.tiraniddo.dev/2017/05/reading-your-way-around-uac-part-2.html\"\u003ehttps://www.tiraniddo.dev/2017/05/reading-your-way...\u003c/a\u003e / \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://www.tiraniddo.dev/2017/05/reading-your-way-around-uac-part-3.html\"\u003ehttps://www.tiraniddo.dev/2017/05/reading-your-way...\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003cem\u003eProgramming Windows Security\u003c/em\u003e, Keith Brown\u003c/span\u003e\u003ca href=\"https://www.tiraniddo.dev/2017/05/reading-your-way-around-uac-part-3.html\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eThis can be verified by looking at PsOpenProcess/Thread in IDA and looking for a call to SePrivilegeCheck.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eThere are many exceptions where this obviously isn’t the case, such as when OS services will execute an app on behalf of the user;\u0026nbsp;e.g., metro apps/calc in Windows 10, process creation services such as Sec Logon, Task Scheduler, WMI, etc.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eThis is true even if the thread is currently impersonating a different security context (as we will cover in the next blog post in this series). See James Forshaw’s presentation on Process Failure Modes for more info: / \u003ca href=\"https://drive.google.com/file/d/0B5sMkPVXQnfPaVB6T2N3Mk5UX28/view\"\u003ehttps://drive.google.com/file/d/0B5sMkPVXQnfPaVB6T2N3Mk5UX28/view\u003c/a\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eA full list of the available logon types can be found here under dwLogonType: \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-logonusera\"\u003ehttps://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-logonusera\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003ca href=\"https://clymb3r.wordpress.com/2013/11/03/powershell-and-token-impersonation/\"\u003ehttps://clymb3r.wordpress.com/2013/11/03/powershel...\u003c/a\u003e\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eIt is worth noting that this design, along with insecure legacy protocols such as NTLM, have had a long history of security issues, such as NTLM relaying, and are often still difficult to fully mitigate in complex enterprise environments.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003eFor example, if during a penetration test you run mimikatz on an SMB file share for a large enterprise you will see a huge number of network logins corresponding to remote clients browsing the share with no cached credentials.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003cspan\u003eN.B The default DACL for a token specifies the default DACL that is applied to any securable object that a thread/process running with that token creates at runtime.\u003c/span\u003e\u003cbr /\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-08-18T23:12:31.228Z","created_by":"bltc87e8bcd2aefc255","disclaimer":[],"full_bleed_image":{"uid":"blt2bc2ee0d053197c6","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-01T23:00:35.030Z","updated_at":"2020-07-01T23:00:35.030Z","content_type":"image/png","file_size":"79461","filename":"blog-banner-security-laptop.png","title":"blog-banner-security-laptop.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T15:16:43.194Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2bc2ee0d053197c6/5efd15937a4c912976093ae3/blog-banner-security-laptop.png"},"markdown_l10n":"","publish_date":"2020-08-20T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Introduction to Windows tokens for security practitioners","seo_description_l10n":"Windows access token manipulation attacks are well known and abused from an offensive perspective, but rely on an extensive body of arcane Windows security internals. In this blog post, we demystify how access tokens work in @Windows environments.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltb35dc0df9e2855a5","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-01T23:00:22.154Z","updated_at":"2020-07-01T23:00:22.154Z","content_type":"image/png","file_size":"73829","filename":"blog-thumb-security-laptop.png","title":"blog-thumb-security-laptop.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T15:16:43.194Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb35dc0df9e2855a5/5efd1586e22ca44fde3b8201/blog-thumb-security-laptop.png"},"title":"Introduction to Windows tokens for security practitioners","title_l10n":"Introduction to Windows tokens for security practitioners","updated_at":"2025-03-10T12:10:07.513Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/introduction-to-windows-tokens-for-security-practitioners","publish_details":{"time":"2025-03-10T12:10:11.122Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta36a5e1b52930f7c","_version":23,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticsearch 7.10.0 is here! Featuring searchable snapshots which is the beginning journey to searchable S3, stored field compression to save up to 10% on index size, Event Query Language for security use cases, and more.","author":["blt59e7f7049d793705"],"body_l10n":"\u003cp\u003eWe're pleased to announce the release of Elasticsearch 7.10.0, based on Apache Lucene 8.7.0. Version 7.10 is the latest stable release of Elasticsearch and is now available for deployment via \u003ca href=\"/elasticsearch/service\" target=\"_self\"\u003eElasticsearch Service\u003c/a\u003e on \u003ca href=\"/cloud\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e or via \u003ca href=\"/downloads/elasticsearch\" target=\"_self\"\u003edownload\u003c/a\u003e for use in your own environment(s).\u003c/p\u003e\u003cp\u003eIf you're ready to roll up your sleeves and get started, we have the links you need:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/cloud/\" target=\"_self\"\u003eStart Elasticsearch on Elastic Cloud\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/downloads/elasticsearch\" target=\"_self\"\u003eDownload Elasticsearch\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/release-notes-7.10.0.html\" target=\"_self\"\u003eElasticsearch 7.10.0 release notes\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/breaking-changes-7.0.html\" target=\"_self\"\u003eElasticsearch 7.10.0 breaking changes\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eWith today's release, our \u003ca href=\"/enterprise-search\" target=\"_self\"\u003eElastic Enterprise Search\u003c/a\u003e, \u003ca href=\"/observability\" target=\"_self\"\u003eElastic Observability\u003c/a\u003e, and \u003ca href=\"/security\" target=\"_self\"\u003eElastic Security\u003c/a\u003e solutions also received significant updates. To learn more about these updates\u0026nbsp;you might consider giving our main\u003ca href=\"/blog/whats-new-elastic-7-10-0-searchable-snapshots-lens-user-experience-monitoring\" target=\"_self\"\u003e Elastic 7.10 release\u003c/a\u003e blog a read.\u003c/p\u003e\u003ch2\u003eStore more and spend less with searchable snapshots\u003c/h2\u003e\u003cp\u003eData is growing at an exponential rate across many organizations. This is especially true for time series data like logs, metrics, traces, and security events used to observe and protect your systems. In time-series data, the most recent data ingested into Elasticsearch is what's valuable. This data drives alerting, machine learning detection, devops workflows, and monitoring security events. But keeping all of this data on high-performance instances can become very expensive if not economically feasible.\u003c/p\u003e\u003cp\u003eTo address this, we began looking at the lifecycle of data. Using features like \u003ca href=\"/blog/elastic-stack-6-6-0-released\" target=\"_self\"\u003eindex lifecycle management\u003c/a\u003e helped move data from high-performance, high-cost \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/data-tiers.html\" target=\"_self\"\u003e\"hot\" nodes to lower cost \"warm\" nodes\u003c/a\u003e with less performant disks. But what if your organization asked you to keep years of data? Could you answer the question of how many unique visitors visited your site year over year on Cyber Monday? Or how many systems a user accessed over a 5 year period for a security forensic investigation? To keep this much data on warm nodes still requires a significant financial investment. This has prompted many organizations to store some data as\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/snapshots-take-snapshot.html\" target=\"_self\"\u003esnapshots\u003c/a\u003e. This isn't a perfect solution, as you still need to take the time to restore the data from a snapshot whenever you need to search.\u003c/p\u003e\u003cp\u003eIntroducing... \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/searchable-snapshots.html\" target=\"_self\"\u003esearchable snapshots\u003c/a\u003e, a new beta feature which allows you to directly search your snapshots without a restore, on low cost object stores such as AWS S3, Microsoft Azure Storage, or Google Cloud Storage without a significant impact to search performance. Balance the cost, performance and capabilities to meet your storage and search needs.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/ZsDF2rsBhcof1LcdsmZBth.jpg\" data-uuid=\"ZsDF2rsBhcof1LcdsmZBth\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"1\" style=\"width: 677;margin-top: auto;margin-right: auto;margin-bottom: auto;margin-left: auto;display: block;\" width=\"677\"/\u003e\u003c/p\u003e\u003cp\u003eSearchable snapshots power a new data tier called the\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/data-tiers.html#cold-tier\" target=\"_self\"\u003ecold tier\u003c/a\u003e. The cold tier, also in beta, is designed to dramatically reduce storage costs for your read-only data by reducing your cluster storage by up to 50% without a significant impact to performance. It maintains the same level of reliability and redundancy as your hot and warm tiers, with full support for the automatic recovery you have come to expect from Elasticsearch. Are you craving more information? Check out this \u003ca href=\"/blog/introducing-elasticsearch-searchable-snapshots\" target=\"_self\"\u003esearchable snapshots introduction\u003c/a\u003e blog for more information.\u003c/p\u003e\u003ch2\u003eBolstering Elasticsearch's security chops with EQL\u003c/h2\u003e\u003cp\u003eIn 7.9, we \u003ca href=\"/blog/whats-new-elasticsearch-7-9-0\" target=\"_self\"\u003eannounced\u003c/a\u003e Event Query Language (EQL), a new experimental query language. \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.x/eql-search-api.html\" target=\"_self\"\u003eEQL\u003c/a\u003e\u0026nbsp;has been used for years within Endgame to help you get a holistic view of a system for threat investigation, identification, and prevention. These same unique capabilities used within the security space have now been brought to Elasticsearch, and in 7.10, EQL in Elasticsearch is now in beta for use cases such as observability and other time-series data.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7b3c6e098bd9c247/5fa9b95342256d5ffdf419bd/eql-final.gif\" data-sys-asset-uid=\"blt7b3c6e098bd9c247\" alt=\"eql-final.gif\"/\u003e\u003c/p\u003e\u003cp\u003eA great way to understand EQL is to consider a home security analogy. Entering the house through any doorway to the home is not considered suspicious even if it's late at night. However, a person entering the house from the front door and from the back door at the same time raises questions because it would be impossible to be in two places at once. It may also be suspicious if someone enters the house after failing to use 90 different keys to open the front door in under a minute \u0026lt;wink\u0026gt;.\u003c/p\u003e\u003cp\u003eEQL is designed to easily take an event (front door opening) and correlate other events or sequence of events (entering through the back door or window, forced entry, etc), to draw conclusions on the state of the system. These events can be correlated over a span of time to find new insights such as 90 previously failed attempts before gaining entry to the home. You can read an introduction to EQL\u0026nbsp;\u003ca href=\"/blog/introducing-event-query-language\" target=\"_self\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eElasticsearch 7.10 will be smaller, in a big way\u003c/h2\u003e\u003cp\u003eOur initial benchmarks have reported space reductions of up to 10% using a new stored field compression! This is big news, especially for organizations paying for storing and maintaining petabytes of data. Indices created by our \u003ca href=\"/observability\" target=\"_self\"\u003eElastic Observability\u003c/a\u003e and \u003ca href=\"/security\" target=\"_self\"\u003eElastic Security\u003c/a\u003e solutions will see the greatest savings due to the repetitive nature of the data they typically hold. To learn more about stored field compression and how you can save up to 10% on index size, be on the look out for stored field compression blog overview being released shortly.\u003c/p\u003e\u003ch2\u003eElasticsearch performance improvements\u003c/h2\u003e\u003cp\u003eElastic has been on a mission to continually improve search aggregation performance and memory efficiencies. In \u003ca href=\"/blog/elasticsearch-7-8-0-released\" target=\"_self\"\u003e7.8\u003c/a\u003e, we reduced aggregation memory consumption by maintaining serialized results, and in \u003ca href=\"/blog/whats-new-elasticsearch-7-9-0\" target=\"_self\"\u003e7.9\u003c/a\u003e we increased the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/search-settings.html#search-settings-max-buckets\" target=\"_self\"\u003esearch.max_buckets\u003c/a\u003e limit to 65,535. The Elasticsearch team has continued this work in 7.10, specifically targeting the coordinator node and the request-level circuit breaker to improve performance and memory tracking of \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/search-aggregations-metrics-cardinality-aggregation.html\" target=\"_self\"\u003ecardinality\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/search-aggregations-bucket.html\" target=\"_self\"\u003ebucket aggregation\u003c/a\u003e. \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/search-aggregations-bucket-datehistogram-aggregation.html\" target=\"_self\"\u003eDate histogram aggregation\u003c/a\u003e performance has also been improved by 50% by precomputing date ranges.\u003c/p\u003e\u003ch2\u003eElasticsearch functional and usability enhancements\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt94e1cb58b5fbb532/5fa9b9ef42256d5ffdf419c9/quote-heraclitus-no-person-ever-steps-in-the-same-river-twice.png\" data-sys-asset-uid=\"blt94e1cb58b5fbb532\" alt=\"quote-heraclitus-no-person-ever-steps-in-the-same-river-twice.png\"/\u003e\u003c/p\u003e\u003ch3\u003ePoint in time reader\u003c/h3\u003e\u003cp\u003eNo person ever steps in the same river twice, since it's not the same river and it's not the same person... unless you have \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/point-in-time-api.html\" target=\"_self\"\u003epoint in time reader\u003c/a\u003e. When querying an index in Elasticsearch, you are essentially searching for data at a given point of time. If your query returns the top 10% results, how do you query the other 90%? With an index that is constantly changing as in most observability and security use cases, sending another query will return a different result because the index or data has already changed. Point in time reader gives you the ability to repeatedly query an index at the state it was at at a given point in time. The point in time reader already serves the EQL query language, and we expect to use it for many other use cases in the future.\u003cbr /\u003e\u003c/p\u003e\u003ch3\u003eCase insensitivity\u003c/h3\u003e\u003cp\u003eIn 7.10 we have added a\u0026nbsp;case insensitivity\u0026nbsp;parameter to term, prefix and wildcard queries. This change makes it much easier to search for e.g. ‘china’ or ‘China’. Security and observability use cases frequently require case insensitive search, and the introduction of the case insensitive parameter to the query will alleviate the need to use regular expressions to indicate a criteria that includes all possible capitalization permutations.\u003c/p\u003e\u003ch3\u003eUnsigned 64 bits integer\u003c/h3\u003e\u003cp\u003eThe time for \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/number.html#number\" target=\"_self\"\u003e64 bit integers\u003c/a\u003e is now! Elasticsearch now supports unsigned 64 bit integers. This new numeric type supports very large positive integers from 0 to 264-1. This is particularly useful for system-generated data, such as counters from routers or Windows registry events. Note that aggregations will still work on the nearest double. This is great news if you work with finance, security and network performance data.\u003c/p\u003e\u003ch3\u003eVersion data type\u003c/h3\u003e\u003cp\u003eHow can you search across software versions where the numeric value is semantic? \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/version.html\" target=\"_self\"\u003eVersion datatype\u003c/a\u003e is a specialization of the keyword field to handle software version values and to support specialized precedence rules for them based on semantic versioning. For example, major, minor, and patch versions are sorted numerically (\"2.1.0\" \u0026lt; \"2.4.1\" \u0026lt; \"2.11.2\"), and pre-release versions are sorted before releases (\"1.0.0-alpha \u0026lt; \"1.0.0\").\u003c/p\u003e\u003ch3\u003eNew aggregations\u003c/h3\u003e\u003cp\u003eIn addition to the aggregations we added in \u003ca href=\"/blog/elasticsearch-7-8-0-released\" target=\"_self\"\u003e7.8\u003c/a\u003e, we are introducing two new aggregations! Histograms: \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/search-aggregations-metrics-max-aggregation.html#search-aggregations-metrics-max-aggregation-histogram-fields\" target=\"_self\"\u003emin/max aggregations on histogram fields\u003c/a\u003e, and hard bounds for histogram aggregations. The histogram datatype is useful for handling high volume numeric data, which is frequently aggregated where it is produced, allowing for a more space-efficient Elasticsearch index. For example, Elastic APM could roll up histogram data or sum it up in one structure to reduce the amount of data being sent from the APM agent into Elasticsearch. Being able to aggregate on the histogram enables supports new scenarios.\u003c/p\u003e\u003cp\u003eThe 2nd aggregation is \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/search-aggregations-metrics-rate-aggregation.html\" target=\"_self\"\u003erate metrics aggregation\u003c/a\u003e, which is used inside a date_histogram and calculates the rate of occurrences of a specified field within a bucket of a date_histogram aggregation. Previously, it was harder to calculate the rate, but since rate is a basic piece of information when analyzing time series data, we thought it would be valuable to make it easier. This is one of many such adaptations we are making to verify that it is easy and intuitive to use the Elasticsearch generic search and analytics engine on time series data.\u003c/p\u003e\u003ch3\u003eNew ingest node pipeline UI\u003c/h3\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1155c42dc8e2f74/5fa9ba656f82405d9a4aaa81/ingest_node_pipelines_demo.gif\" data-sys-asset-uid=\"bltc1155c42dc8e2f74\" alt=\"ingest_node_pipelines_demo.gif\"/\u003e\u003c/p\u003e\u003cp\u003eIt is easier to debug your ingest flow with the new ingest node pipeline UI. Added visual cues and pipeline tests allow you to easily step through the execution flow. Viewing error messages from the output can help you identify what actions are needed to ensure your documents will work properly with your ingest processors.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eMachine Learning\u003c/h2\u003e\u003ch3\u003eAUC ROC metric for evaluating your classification machine learning models\u003c/h3\u003e\u003cp\u003eWe have added area under the curve of receiver operating characteristic (AUC ROC) as an evaluation metric for classification analysis. This is a common evaluation metric to know how well your models perform.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch3\u003eCustom feature processor in data frame analytics\u003c/h3\u003e\u003cp\u003eNew field in data frame analytics allows you to supply your own feature transformations and processors that are applied before training, which are applied automatically at inference time. This allows you to do a last step feature transformation for any data row before giving it to analytics.\u003c/p\u003e\u003ch2\u003eThat's All Folks…\u003c/h2\u003e\u003cp\u003e7.10 is a huge release for Elasticsearch and we couldn't cover all of it within this blog. Be sure to check out more by reading the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.10/release-highlights.html\" target=\"_self\"\u003erelease highlights\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eReady to get your hands dirty? Spin up a 14-day free trial of \u003ca href=\"/cloud/\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e or \u003ca href=\"/downloads/elasticsearch\" target=\"_self\"\u003edownload Elasticsearch\u003c/a\u003e today. Try it out, and be sure to let us know what you think on Twitter (\u003ca href=\"https://twitter.com/elastic\" target=\"_self\"\u003e@elastic\u003c/a\u003e) or in \u003ca href=\"https://discuss.elastic.co/c/elasticsearch\" target=\"_self\"\u003eour forum\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2020-11-05T23:51:41.746Z","created_by":"blt34e7f499d15c5bd0","disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt524d5ee0222d5354","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:36.948Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"54225","filename":"blog-banner-release-elasticsearch.png","parent_uid":null,"tags":[],"title":"blog-banner-release-elasticsearch.png","updated_at":"2021-01-26T17:45:10.329Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-03T15:47:40.504Z","user":"bltde77f2161b811714"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt524d5ee0222d5354/601055260cb0aa0ffcdd590e/blog-banner-release-elasticsearch.png"},"markdown_l10n":"","publish_date":"2020-11-11T17:04:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch 7.10.0 released","seo_description_l10n":"Elasticsearch 7.10.0 is here! Featuring searchable snapshots which is the beginning journey to searchable S3, stored field compression to save up to 10% on index size, Event Query Language for security use cases, and more.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"blt8c2b608c10eb1fd8","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:42.964Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"51730","filename":"blog-thumb-release-elasticsearch.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-elasticsearch.png","updated_at":"2022-02-11T21:03:50.956Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.895Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c2b608c10eb1fd8/601055106215cf0f9a18d799/blog-thumb-release-elasticsearch.png"},"title":"Elasticsearch 7.10.0 released","title_l10n":"Elasticsearch 7.10.0 released","updated_at":"2025-03-10T12:06:56.183Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/whats-new-elasticsearch-7-10-0-searchable-snapshots-store-more-for-less","publish_details":{"time":"2025-03-10T12:07:00.829Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltde557cd7dddc2b40","_version":24,"locale":"en-us","ACL":{},"abstract_l10n":"This blog teaches security practitioners how attackers abuse legitimate Windows functionalities to move laterally and compromise Active Directory domains.","author":["bltc2baef8dab82b56d"],"body_l10n":"\u003cp\u003eIn our previous blog post on \u003ca href=\"https://www.elastic.co/blog/introduction-to-windows-tokens-for-security-practitioners\"\u003eWindows access tokens for security practitioners\u003c/a\u003e, we covered:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eThe relationship between logon sessions and access tokens\u003c/li\u003e\u003cli aria-level=\"1\"\u003eHow network authentication works in Windows environments\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eHaving covered some of the key concepts in Windows security, we will now build on this knowledge and start to look at how attackers can abuse legitimate Windows functionality to move laterally and compromise Active Directory domains.\u003c/p\u003e\u003cp\u003eThis blog has deliberately attempted to abstract away the workings of specific Windows network authentication protocols (e.g., NTLM and Kerberos) where possible. As a consequence, there may be instances where behaviour unique to these protocols differs with the behavior described below. It also assumes some basic understanding of the Kerberos authentication protocol\u003csup\u003e1\u003c/sup\u003e.\u003c/p\u003e\u003cp\u003eAdditionally, the material covered in this blog series was used for a BlackHat 2020 presentation, “Detecting Access Token Manipulation”. The presentation can be found \u003ca href=\"https://www.youtube.com/watch?v=RMVyYvt0bLY\"\u003ehere\u003c/a\u003e and the slides \u003ca href=\"https://i.blackhat.com/USA-20/Thursday/us-20-Burgess-Detecting-Access-Token-Manipulation.pdf\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eAccess Token Manipulation (ATT\u0026amp;CK technique: T1134)\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eHaving explained the basic principles of how logon sessions and access tokens work in \u003ca href=\"https://www.elastic.co/blog/introduction-to-windows-tokens-for-security-practitioners\"\u003eour previous blog post\u003c/a\u003e, both locally and for distributed applications, this section will explain how attackers can abuse access tokens and target the fundamental trust relationships in Windows domains to compromise entire networks. The aim of this section is to describe access token manipulation \u003ca href=\"https://attack.mitre.org/techniques/T1134/\"\u003etechniques\u003c/a\u003e used by attackers within the \u003cem\u003econtext\u003c/em\u003e of a simulated compromise.\u0026nbsp;\u003c/p\u003e\u003cp\u003eAs a note, there is already an extensive body of excellent research on access token manipulation (which will be linked to liberally throughout this post). This blog attempts to build on this body of knowledge via considering access token manipulation from a different approach, namely through the relationship between access tokens, logon sessions and cached credentials. In the author's opinion, any description of token manipulation without considering these relationships represents only the tip of the iceberg. As a consequence, this blog’s definition of access token manipulation is perhaps much broader than commonly understood.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eInitial compromise\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eIn the event that an attacker obtains a foothold in a network via spear phishing, they will typically end up with a shell running in the \u003cem\u003esecurity context\u003c/em\u003e of the compromised user. This could be achieved via spawning a new process or injecting directly into memory (depending on the payload), but the end result is the same: the attacker’s code is running in a process which has an access token belonging to the compromised user.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThis means that any \u003cstrong\u003elocal access checks \u003c/strong\u003ewill use the compromised user’s access token and any \u003cstrong\u003eremote authentication attempts\u003c/strong\u003e will use the compromised user’s cached credentials\u003csup\u003e2\u003c/sup\u003e. Hence, the attacker can, both locally and across the network, perform \u003cem\u003eall\u003c/em\u003e the actions that the compromised user can. For example, if any internal web applications use Windows SSO, an attacker will be able to access them as if they were the user.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eToken Manipulation: The ‘Art of the possible’\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eTypically, an attacker will want to move from the compromised endpoint to another host \u003cem\u003eas quickly as possible\u003c/em\u003e\u003csup\u003e3\u003c/sup\u003e. When considering \u003cstrong\u003elateral movement\u003c/strong\u003e from a token manipulation perspective, the attacker effectively has three options\u003csup\u003e4\u003c/sup\u003e, each of which is constrained by the fundamental relationship between access tokens, logon sessions, and cached credentials, as illustrated below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdcd5a4e605d40114/6075bee21898af75a401bc49/1-access-tokens-logon-sessions-blog-access-token-manipulation.png\" data-sys-asset-uid=\"bltdcd5a4e605d40114\" alt=\"1-access-tokens-logon-sessions-blog-access-token-manipulation.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 1 - The relationship between access tokens, logon sessions and cached credentials\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eIf an attacker wants to move laterally via Windows SSO then all of these three links must be in place (e.g., they have a handle to a token which is linked to a logon session backed by their target credentials). Otherwise, an attacker’s freedom of movement relies on either \u003cstrong\u003ecreating\u003c/strong\u003e new links (e.g., new logon sessions) or \u003cstrong\u003emodifying\u003c/strong\u003e existing ones (e.g., changing cached credentials or the logon session that their access token points to). These constraints are discussed in more detail in the three options below:\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003e1. Steal the token of an already logged-on privileged user (non-network logon)\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eIf another privileged user is already logged on to the compromised host, an attacker can escalate their privileges and obtain a handle to an access token representing this user. Irrespective of whether the attacker impersonates the stolen token or starts a new process, if that token is linked to a \u003cem\u003enon-network\u003c/em\u003e logon session, it will have cached credentials, and hence the attacker can auth off the box to another host\u003csup\u003e5\u003c/sup\u003e. Hence, this technique allows an attacker to use another user’s credentials to access remote hosts across the network (via Windows SSO), and therefore pivot without needing to dump credentials\u003csup\u003e6\u003c/sup\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eAs a note, token manipulation attacks generally relate to two distinct objectives: moving laterally (which this blog is concerned with) and local privilege escalation\u003csup\u003e7\u003c/sup\u003e. Token theft \u003cem\u003etends\u003c/em\u003e to be associated with the latter (e.g., stealing/impersonating a token for the purpose of bypassing \u003cstrong\u003elocal access checks,\u003c/strong\u003e rather than for the purpose of using the cached credentials for remote authentication) and so this blog will not discuss it in any further detail, but the following resources are useful further reading:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://posts.specterops.io/understanding-and-defending-against-access-token-theft-finding-alternatives-to-winlogon-exe-80696c8a73b\"\u003ehttps://posts.specterops.io/understanding-and-defending-against-access-token-theft-finding-alternatives-to-winlogon-exe-80696c8a73b\u003c/a\u003e\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/\"\u003ehttps://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/\u003c/a\u003e\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003ca href=\"https://labs.f-secure.com/assets/BlogFiles/mwri-security-implications-of-windows-access-tokens-2008-04-14.pdf\"\u003ehttps://labs.f-secure.com/assets/BlogFiles/mwri-security-implications-of-windows-access-tokens-2008-04-14.pdf\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003e\u003cstrong\u003e2. Create a new logon session with stolen credentials and impersonate the returned token or spawn a new process with it\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eIn this case, there is no privileged user already logged on (and hence no corresponding \u003cstrong\u003euseful\u003c/strong\u003e access token/logon session), but the attacker still needs to find a way to \u003cem\u003echange their security context\u003c/em\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eHence, the attacker must find credentials elsewhere and use these stolen credentials to create a \u003cstrong\u003enew\u003c/strong\u003e logon session as the compromised user. \u003ca href=\"https://www.elastic.co/blog/introduction-to-windows-tokens-for-security-practitioners\"\u003eAs Windows will automatically cache credentials for certain logon types\u003c/a\u003e, the attacker can now obtain a newly minted access token which is backed up by the stolen credentials. Once the attacker has a handle to a token representing the compromised user, they can authenticate off the box making use of the standard Windows SSO process.\u0026nbsp;\u003c/p\u003e\u003cp\u003eTypically, plain text credentials are found by attackers via either \u003ca href=\"https://github.com/EmpireProject/Empire/blob/master/data/module_source/credentials/Invoke-Kerberoast.ps1\"\u003eKerberoasting\u003c/a\u003e or searching for unsecured plain text credentials across all accessible resources, such as network shares, Sharepoint, internal wikis, enterprise GitHub, Zendesk, etc.\u003csup\u003e8\u003c/sup\u003e\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003e3. Change the cached credentials associated with their current access token to stolen credentials (e.g., legitimately via an API or “illegitimately” by \u003c/strong\u003e\u003cem\u003e\u003cstrong\u003edirectly modifying\u003c/strong\u003e\u003c/em\u003e\u003cstrong\u003e lsass memory)\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eIn this scenario, rather than create a new logon session, the attacker modifies the cached credentials associated with their current access token (and hence logon session). As we shall see, many Windows \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/rpc/security-support-providers-ssps-\"\u003eSecurity Support Providers\u003c/a\u003e (SSPs) provide native ways to do this (and which \u003cstrong\u003edo not\u003c/strong\u003e\u003cem\u003e \u003c/em\u003erequire elevated privileges).\u0026nbsp;\u003c/p\u003e\u003cp\u003eAlternatively, attackers can go the “direct” route and \u003cstrong\u003emanually\u003c/strong\u003e modify cached credentials stored in lsass. This requires elevated privileges in order to obtain a write handle (e.g., \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/procthread/process-security-and-access-rights\"\u003ePROCESS_VM_WRITE\u003c/a\u003e) to lsass via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openprocess\"\u003eOpenProcess\u003c/a\u003e. This is typical of pass-the-hash type attacks as we shall cover later on.\u003c/p\u003e\u003ch2\u003eAccess Token Manipulation\u0026nbsp;attacks\u003c/h2\u003e\u003cp\u003eThis blog post will look at four common techniques\u0026nbsp;used by attackers (all of which can be classified as variations of option 3 above):\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eThe NETONLY flag\u003c/li\u003e\u003cli aria-level=\"1\"\u003ePass-The-Ticket\u003c/li\u003e\u003cli aria-level=\"1\"\u003ePass-The-Hash\u003c/li\u003e\u003cli aria-level=\"1\"\u003eOverpass-The-Hash\u003c/li\u003e\u003c/ul\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003e1. The NETONLY flag\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eThe Windows API provides the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-logonuserw\"\u003eLogonUser\u003c/a\u003e function to create a new logon session for a given user (or principal)\u003csup\u003e9\u003c/sup\u003e:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eBOOL LogonUserW(\u003cbr /\u003e LPCWSTR lpszUsername,\u003cbr /\u003e LPCWSTR lpszDomain,\u003cbr /\u003e LPCWSTR lpszPassword,\u003cbr /\u003e DWORD dwLogonType,\u003cbr /\u003e DWORD dwLogonProvider,\u003cbr /\u003e PHANDLE phToken\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe key parameter to take note of here is the \u003cstrong\u003edwLogonType\u003c/strong\u003e, which specifies the \u003cem\u003etype\u003c/em\u003e of logon to perform. For example, in the case of a user physically logging into their workstation, it will be set to \u003cstrong\u003eLOGON32_LOGON_INTERACTIVE\u003c/strong\u003e. The logon type specified will determine the \u003cem\u003etype\u003c/em\u003e and \u003cem\u003eprivileges\u003c/em\u003e of the token returned.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFor example, in the case of an interactive logon, LogonUserW will return a primary access token, and, if UAC is \u003cem\u003eenabled\u003c/em\u003e, this token will be a filtered token (meaning it will be medium integrity and \u003ca href=\"https://docs.microsoft.com/en-us/windows/security/identity-protection/user-account-control/how-user-account-control-works\"\u003eunelevated\u003c/a\u003e). This has one exception: if the user is a local administrator account (e.g., a *-500 \u003ca href=\"https://support.microsoft.com/en-gb/help/243330/well-known-security-identifiers-in-windows-operating-systems\"\u003eSID\u003c/a\u003e) Windows will automatically return an elevated token\u003csup\u003e10\u003c/sup\u003e.\u003c/p\u003e\u003cp\u003eIn the case of a network logon (\u003cstrong\u003eLOGON32_LOGON_NETWORK\u003c/strong\u003e), an \u003cem\u003eimpersonation\u003c/em\u003e token is returned (as typically this would be used by a server to perform work on the remote clients behalf). Furthermore, if the user is in the local administrators group, the token is elevated and has \u003cem\u003eall\u003c/em\u003e privileges enabled\u003csup\u003e11\u003c/sup\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThese permutations of LogonUser\u0026nbsp;are captured in the table below:\u003c/p\u003e\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003edwLogonType\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eToken returned\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eCache credentials?\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eIs returned token elevated? (if admin)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eInteractive (\u003cstrong\u003eLOGON32_LOGON_INTERACTIVE\u003c/strong\u003e)\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePrimary\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eYes\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNo (UAC applies)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eInteractive (Local admin account, e.g., rid-500)\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePrimary\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eYes\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eYes\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eNetwork (\u003cstrong\u003eLOGON32_LOGON_NETWORK\u003c/strong\u003e)\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eImpersonation\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNo\u003csup\u003e12\u003c/sup\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eYes (+ \u003cem\u003eall\u003c/em\u003e privileges enabled)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eNetwork (Local admin account, e.g., rid-500\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eImpersonation\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNo\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDepends on remote UAC settings\u003csup\u003e13\u003c/sup\u003e\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cfigcaption\u003eTable 1 - The permutations of LogonUser for the corresponding dwLogonType\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThe key point is that LogonUser returns a handle to a \u003cstrong\u003enewly minted token\u003c/strong\u003e, which can now be used for impersonation.\u0026nbsp;\u003c/p\u003e\u003cp\u003eIf the token returned is a \u003cstrong\u003eprimary\u003c/strong\u003e token it must first be converted in to an impersonation token via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-duplicatetokenex\"\u003eDuplicateTokenEx\u003c/a\u003e by passing a \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winnt/ne-winnt-token_type\"\u003eTokenType\u003c/a\u003e of TokenImpersonate\u003csup\u003e14\u003c/sup\u003e:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eBOOL DuplicateTokenEx(\u003cbr /\u003e HANDLE hExistingToken,\u003cbr /\u003e DWORD dwDesiredAccess,\u003cbr /\u003e LPSECURITY_ATTRIBUTES lpTokenAttributes,\u003cbr /\u003e SECURITY_IMPERSONATION_LEVEL ImpersonationLevel,\u003cbr /\u003e TOKEN_TYPE TokenType,\u003cbr /\u003e PHANDLE phNewToken\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003eThe \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-setthreadtoken\"\u003eSetThreadToken\u003c/a\u003e function can then be used to assign the returned impersonation token to the current thread:\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eBOOL SetThreadToken(\u003cbr /\u003e PHANDLE Thread,\u003cbr /\u003e HANDLE Token\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAlternatively, the Windows API provides the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-impersonateloggedonuser\"\u003eImpersonateLoggedOnUser\u003c/a\u003e function, which will allow the calling thread to impersonate the \u003cem\u003esecurity context\u003c/em\u003e of the user represented by the token passed:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eBOOL ImpersonateLoggedOnUser(\u003cbr /\u003e HANDLE hToken\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eImpersonateLoggedOnUser has the added benefit that it will automatically check the type of the token passed and convert it to an impersonation token (via \u003ca href=\"https://docs.microsoft.com/en-us/windows-hardware/drivers/ddi/ntifs/nf-ntifs-ntduplicatetoken\"\u003eNtDuplicateToken\u003c/a\u003e) if a primary token was passed (as this token type\u003cem\u003e \u003c/em\u003ecannot\u003cem\u003e \u003c/em\u003ebe used by a thread to impersonate)\u003csup\u003e15\u003c/sup\u003e.\u003c/p\u003e\u003cp\u003eNote that from a defense evasion perspective, both these impersonation APIs are lightweight wrappers over the undocumented syscall \u003ca href=\"http://undocumented.ntinternals.net/UserMode/Undocumented%20Functions/NT%20Objects/Thread/NtSetInformationThread.html\"\u003eNtSetInformationThread\u003c/a\u003e (e.g., called with a \u003ca href=\"https://www.geoffchappell.com/studies/windows/km/ntoskrnl/api/ps/psquery/class.htm\"\u003eThreadInformationClass\u003c/a\u003e of \u003ca href=\"http://undocumented.ntinternals.net/index.html?page=UserMode/Undocumented%20Functions/NT%20Objects/Thread/THREAD_INFORMATION_CLASS.html\"\u003eThreadImpersonationToken\u003c/a\u003e). Therefore, they are a good target for attackers to use direct syscalls to bypass user-mode hooks via techniques such as \u003ca href=\"https://github.com/jthuraisamy/SysWhispers\"\u003ehttps://github.com/jthuraisamy/SysWhispers\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eFurthermore, it is important to stress that Windows has strict rules around impersonation. These are listed below and taken from the MSDN page for \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-impersonateloggedonuser\"\u003eImpersonateLoggedOnUser\u003c/a\u003e:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eAll impersonate functions, including ImpersonateLoggedOnUser allow the requested impersonation if one of the following is true:\u003cbr /\u003e - The requested impersonation level of the token is less than SecurityImpersonation, such as SecurityIdentification or SecurityAnonymous\u003cbr /\u003e - The caller has the SeImpersonatePrivilege privilege.\u003cbr /\u003e - A process (or another process in the caller’s logon session) created the token using explicit credentials through LogonUser or LsaLogonUser function.\u003cbr /\u003eThe authenticated identity is the same as the caller\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAdditionally, the impersonated token’s integrity level must also be less or equal to the calling process’s integrity level or else the impersonation call will also fail\u003csup\u003e16\u003c/sup\u003e. Therefore, assuming an \u003cstrong\u003eunelevated\u003c/strong\u003e attacker logs on an admin user \u003cem\u003einteractively\u003c/em\u003e via stolen credentials, and UAC is enabled, they will receive an unelevated (e.g., filtered) token back and hence will have no issues impersonating the returned user and moving laterally, etc.\u003cbr /\u003e\u003c/p\u003e\u003ch4\u003e“The curious /NETONLY flag”\u003csup\u003e17\u003c/sup\u003e\u003c/h4\u003e\u003cp\u003eAn attacker may find however that attempting to log on a user with stolen credentials \u003cstrong\u003efails.\u003c/strong\u003e This may be due to a multitude of reasons, such as the credentials are valid, but the account does not have permissions to log onto that specific workstation / they’re only valid in a different domain, etc.\u003cstrong\u003e \u003c/strong\u003eFurthermore,\u003cstrong\u003e \u003c/strong\u003ethe attacker may also want to avoid logging in a highly privileged account entirely, as this may appear highly anomalous in certain contexts (e.g., a domain admin logging on to a low privileged business user’s host should be incredibly suspicious).\u003csup\u003e18\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eIn this scenario the \u003cstrong\u003eLOGON32_LOGON_NEW_CREDENTIALS\u003c/strong\u003e flag comes to the attacker’s rescue. If an attacker calls the LogonUserW function with this flag and passes a valid set of credentials (say found from sniffing around on file shares), Windows will enable the caller to duplicate their current token but make it point to a \u003cstrong\u003enew\u003c/strong\u003e logon session, referred to as a New Credentials logon session, which caches the stolen credentials. As a result, the user still has the same security context \u003cem\u003elocally \u003c/em\u003e(e.g., they still have a copy of the \u003cstrong\u003esame\u003c/strong\u003e access token; it just points to a \u003cstrong\u003enew\u003c/strong\u003e logon session),\u0026nbsp;however, any attempts to authenticate remotely will supply the new credentials passed in the call to LogonUserW\u003csup\u003e19\u003c/sup\u003e. This is illustrated in the diagram below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt48a9085f9cadcc41/6075bf781898af75a401bc4d/2-logon-new-credentials-blog-access-token-manipulation.gif\" data-sys-asset-uid=\"blt48a9085f9cadcc41\" alt=\"2-logon-new-credentials-blog-access-token-manipulation.gif\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 2 - How the LOGON32_LOGON_NEW_CREDENTIALS flag works under the hood\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eHence, the \u003cstrong\u003eLOGON32_LOGON_NEW_CREDENTIALS\u003c/strong\u003e flag provides a native mechanism to make your current access token point to a \u003cem\u003edifferent\u003c/em\u003e logon session and hence \u003cem\u003edifferent \u003c/em\u003ecredentials.\u003csup\u003e20\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eNote, that calling LogonUserW with the LOGON32_LOGON_NEW_CREDENTIALS flag \u003cstrong\u003edoes not\u003c/strong\u003e validate the credentials when the call is made (they can be complete junk), but are only validated by a Domain Controller at the time of any remote authentication requests.\u0026nbsp;\u003c/p\u003e\u003cp\u003eAs a further example, a quick review of the \u003ca href=\"https://github.com/cobbr/Covenant/blob/5b90f203c2e42c0f0e5607653c71f6fc452adaab/Covenant/Data/Tasks/SharpSploit.Credentials.yaml#L13-L48\"\u003ecode\u003c/a\u003e for the ‘MakeToken’ task from the open source .NET C2 framework Covenant reveals exactly the same approach: it takes a username/password combination and creates a new logon session/token with them via passing the \u003cstrong\u003eLOGON32_LOGON_NEW_CREDENTIALS\u003c/strong\u003e flag before proceeding to impersonate the returned token.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFurthermore, you can replicate the exact same behaviour with \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-createprocesswithlogonw\"\u003eCreateProcessWithLogonW\u003c/a\u003e by passing a dwLogonFlags of \u003cstrong\u003eLOGON_NETCREDENTIALS_ONLY\u003c/strong\u003e.\u003csup\u003e21\u003c/sup\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eBOOL CreateProcessWithLogonW( \u003cbr /\u003e LPCWSTR lpUsername,\u003cbr /\u003e LPCWSTR lpDomain,\u003cbr /\u003e LPCWSTR lpPassword,\u003cbr /\u003e DWORD dwLogonFlags,\u003cbr /\u003e LPCWSTR lpApplicationName,\u003cbr /\u003e LPWSTR lpCommandLine,\u003cbr /\u003e DWORD dwCreationFlags,\u003cbr /\u003e LPVOID lpEnvironment,\u003cbr /\u003e LPCWSTR lpCurrentDirectory,\u003cbr /\u003e LPSTARTUPINFOW lpStartupInfo,\u003cbr /\u003e LPPROCESS_INFORMATION lpProcessInformation\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe key difference is that this involves spawning a new process with the returned token, as opposed to the intra process impersonation discussed previously. In fact, the built in Windows utility, runas, is a simple wrapper around CreateProcessWithLogonW and the \u003cstrong\u003e/NETONLY\u003c/strong\u003e flag provides a native way to spawn a new process with different network-only credentials, as demonstrated below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc8ce4c6cedfdd854/6075c0c249eb2079fbffc7b4/3-using-the-runas-blog-access-token-manipulation.png\" data-sys-asset-uid=\"bltc8ce4c6cedfdd854\" alt=\"3-using-the-runas-blog-access-token-manipulation.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 3 - Example of using the runas /NETONLY flag to spawn a new process as the user astro\\cosmo but with \u003cem\u003edifferent\u003c/em\u003e cached credentials.\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eIn exactly the same way as previously described, the new command prompt appears locally to be running as the same user (i.e., the attributes cached in the token are the same for any \u003cstrong\u003elocal\u003c/strong\u003e access checks; hence whoami returns ‘astro\\cosmo’), but any remote authentication attempts will be performed using the stolen credentials for the ‘ASTRO\\Administrator’ user.\u0026nbsp;\u003c/p\u003e\u003cp\u003eThese logon sessions can be viewed using SysInternals’ \u003ca href=\"https://docs.microsoft.com/en-us/sysinternals/downloads/logonsessions\"\u003eLogonSessions\u003c/a\u003e tool. Logon sessions that were created with the NewCredentials flag can be determined by the Logon type field as shown below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf1ed1a3700d155ad/6075c154f684ae78caa308cc/4-logon-session-blog-access-token-manipulation.png\" data-sys-asset-uid=\"bltf1ed1a3700d155ad\" alt=\"4-logon-session-blog-access-token-manipulation.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 4 - Example of a NewCredentials logon session which is typically generated by the NETONLY flag\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eFurthermore, anomalous NewCredentials logon sessions (e.g., produced via the NETONLY gadget) leave artifacts in the Windows event logs. These can be identified via the event id 4642 and a LogonType of 9. An example is shown in the image below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte4598ff799d5c1a9/6075c1bdd0dd26715b4a7bb8/5-windows-event-log-blog-access-token-manipulation.png\" data-sys-asset-uid=\"blte4598ff799d5c1a9\" alt=\"5-windows-event-log-blog-access-token-manipulation.png\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 5 - Example of a Windows Event Log for Event ID 4624 which is typically generated by the NETONLY flag\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eNote that the original user is shown by the SubjectUserName field and the specified network only credentials (e.g., the credentials passed) are displayed in the TargetOutboundUser/DomainName fields.\u003csup\u003e22\u003c/sup\u003e\u003c/p\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003ch4\u003e\u003cstrong\u003eAuto-elevation\u003c/strong\u003e\u003c/h4\u003e\u003cp\u003eOne further quirk from a local privilege escalation perspective is that for rid-500 accounts, \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-createprocesswithlogonw\"\u003eCreateProcessWithLogonW\u003c/a\u003e will automatically elevate the returned token for interactive logons (e.g. it will ignore UAC). Therefore, \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-createprocesswithlogonw\"\u003eCreateProcessWithLogonW\u003c/a\u003e can be passed a local/domain admin account in order to execute an \u003cstrong\u003eelevated process from a medium/unelevated context\u003c/strong\u003e.\u003c/p\u003e\u003cp\u003eThis behavior can be verified using runas. For example, when runas is used to spawn a process using a local admin account (e.g., runas /user:\"Administrator\" cmd.exe), the resulting process will be elevated (e.g., high integrity). However, when a non rid-500 account is used (but which is still in the local administrators group) the resulting process will be unelevated (e.g., it will be a filtered token / medium integrity).\u003c/p\u003e\u003cp\u003eNotice that this behaviour is consistent with the permutations listed for LogonUserW in Table 1. Therefore, an unelevated attacker could also log on a (non rid-500) admin user as a network logon and receive an elevated token with all privileges enabled.\u003c/p\u003e\u003cp\u003eHowever, as per the impersonation rules previously outlined, the attacker should not actually be able to \u003cem\u003edo anything\u003c/em\u003e with this token as any attempts to impersonate the elevated token should fail, as it has a higher integrity level than the caller. Nevertheless, it is actually possible to duplicate the elevated token, lower the integrity level of the copied token to medium (NB ‘isElevated’ is still true)\u003csup\u003e23\u003c/sup\u003e, and start impersonating the elevated token from an unelevated/medium integrity context\u003csup\u003e24\u003c/sup\u003e. Hence, from an impersonation token perspective, you can bypass the default Windows behaviour of only elevating certain accounts and impersonate an elevated token irrespective of whether the account is a rid-500 account or not.\u003c/p\u003e\u003ch4\u003e\u003cstrong\u003eProcess creation\u003c/strong\u003e\u003c/h4\u003e\u003cp\u003eNote, that by default, when you create a child process it inherits your primary token \u003cem\u003eeven\u003c/em\u003e if you are currently impersonating another security context\u003csup\u003e25\u003c/sup\u003e. For example, if you are impersonating a SYSTEM token and you call \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-createprocessa\"\u003eCreateProcess\u003c/a\u003e(), it will \u003cstrong\u003estill\u003c/strong\u003e inherit a copy of the primary process token (rather than inheriting the SYSTEM security context of the thread).\u003csup\u003e26\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eTherefore, if an attacker wishes to spawn a new process in a \u003cem\u003edifferent security context,\u003c/em\u003e\u0026nbsp;they must either:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eUse CreateProcessWithLogonW with explicit credentials (as previously discussed)\u0026nbsp;\u003c/li\u003e\u003cli aria-level=\"1\"\u003eCall either \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-createprocesswithtokenw\"\u003eCreateProcessWithTokenW\u003c/a\u003e or \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-createprocessasuserw\"\u003eCreateProcessAsUserW\u003c/a\u003e and pass a handle to a token (e.g., with the token returned from LogonUser or more commonly via a stolen token)\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eBoth of these functions can be passed a handle to a token which represents the security context of the new process.\u003csup\u003e27\u003c/sup\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eBOOL CreateProcessWithTokenW(\u003cbr /\u003e HANDLE hToken,\u003cbr /\u003e DWORD dwLogonFlags,\u003cbr /\u003e LPCWSTR lpApplicationName,\u003cbr /\u003e LPWSTR lpCommandLine,\u003cbr /\u003e DWORD dwCreationFlags,\u003cbr /\u003e LPVOID lpEnvironment,\u003cbr /\u003e LPCWSTR lpCurrentDirectory,\u003cbr /\u003e LPSTARTUPINFOW lpStartupInfo,\u003cbr /\u003e LPPROCESS_INFORMATION lpProcessInformation\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cpre class=\"prettyprint\"\u003eBOOL CreateProcessAsUserW(\u003cbr /\u003e HANDLE hToken,\u003cbr /\u003e LPCWSTR lpApplicationName,\u003cbr /\u003e LPWSTR lpCommandLine,\u003cbr /\u003e LPSECURITY_ATTRIBUTES lpProcessAttributes,\u003cbr /\u003e LPSECURITY_ATTRIBUTES lpThreadAttributes,\u003cbr /\u003e BOOL bInheritHandles,\u003cbr /\u003e DWORD dwCreationFlags,\u003cbr /\u003e LPVOID lpEnvironment,\u003cbr /\u003e LPCWSTR lpCurrentDirectory,\u003cbr /\u003e LPSTARTUPINFOW lpStartupInfo,\u003cbr /\u003e LPPROCESS_INFORMATION lpProcessInformation\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eFor example, CreateProcessAsUserW is typically used by the operating system itself to spawn the user’s shell following a successful logon (it is also used by the Secondary Logon service when a user calls creatProcessWithLogonW). In this sense, it allows a user to “inject a process into the logon session of their choice”\u003csup\u003e28\u003c/sup\u003e. As a note, both of these APIs are wrappers around \u003ca href=\"https://doxygen.reactos.org/d9/dd7/dll_2win32_2kernel32_2client_2proc_8c.html#a13a0f94b43874ed5a678909bc39cc1ab\"\u003eCreateProcessInternalW\u003c/a\u003e (located in KernelBase.dll).\u003c/p\u003e\u003cp\u003eThe key difference here is that the caller must have certain privileges to call these two APIs\u003csup\u003e29\u003c/sup\u003e. From an attackers perspective though the goal here is the same; obtain code execution in the security context of the target user for the purposes of moving laterally.\u003c/p\u003e\u003cp\u003eOne interesting quirk is that the PowerShell Empire framework was forced to take this process spawning approach (which is arguably much noisier from a detection perspective) due to limitations with how PowerShell handles impersonation and multi-threading, as the notes \u003ca href=\"https://github.com/PowerShellMafia/PowerSploit/blob/c7985c9bc31e92bb6243c177d7d1d7e68b6f1816/Exfiltration/Invoke-TokenManipulation.ps1#L10-L17\"\u003ehere\u003c/a\u003e explain in more detail.\u003c/p\u003e\u003cp\u003eIn any case, the workflow for using process spawning token manipulation techniques remains the same. Once the attacker has obtained a handle to the token (via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openprocess\"\u003eOpenProcess\u003c/a\u003e/\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openprocesstoken\"\u003eOpenProcessToken\u003c/a\u003e if primary token, or \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openthread\"\u003eOpenThread\u003c/a\u003e/\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openthreadtoken\"\u003eOpenThreadToken\u003c/a\u003e in the case of a thread impersonating) the attacker must call DuplicateTokenEx to create a local (primary) copy of the target token, and then supply this copy to either the CreateProcessWithTokenW or CreateProcessAsUserW functions.\u003c/p\u003e\u003cp\u003eNote that again in this case, attackers are only interested in privileged logon sessions which are \u003cstrong\u003enon network logins\u003c/strong\u003e, as network logins \u003cem\u003edo not\u003c/em\u003e cache credentials and so \u003cstrong\u003ecannot\u003c/strong\u003e\u003cem\u003e \u003c/em\u003eauthenticate to other hosts.\u003cbr /\u003e\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003e2. Pass-The-Ticket\u003c/strong\u003e\u003c/h3\u003e\u003cbr /\u003eWindows provides a native method to perform a very similar technique to the NETONLY flag using \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthn/kerberos-ssp-ap\"\u003eKerberos\u003c/a\u003e\u003csup\u003e30\u003c/sup\u003e. This technique is even more powerful in the sense that it doesn’t require an attacker to create a new logon session, but rather arbitrarily change the cached Kerberos credentials (e.g., TGT) associated with their logon session (and hence current access token), as demonstrated below:\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt681818873a2effeb/6075c3b21898af75a401bc5b/6-pass-the-ticket-blog-access-token-manipulation.gif\" data-sys-asset-uid=\"blt681818873a2effeb\" alt=\"6-pass-the-ticket-blog-access-token-manipulation.gif\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 6 - How the Pass-the-ticket attack works under the hood. In this example, the user, ASTRO\\cosmo, applies the stolen TGT of the ASTRO\\Administrator user to their current logon session.\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eIn order to start interacting with the Kerberos SSP and manage the Kerberos ticket cache, a process can call \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/ntsecapi/nf-ntsecapi-lsacallauthenticationpackage\"\u003eLsaCallAuthenticationPackage\u003c/a\u003e (located in Sspicl.dll):\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eNTSTATUS LsaCallAuthenticationPackage( \u003cbr /\u003e HANDLE LsaHandle,\u003cbr /\u003e ULONG AuthenticationPackage,\u003cbr /\u003e PVOID ProtocolSubmitBuffer,\u003cbr /\u003e ULONG SubmitBufferLength,\u003cbr /\u003e PVOID *ProtocolReturnBuffer,\u003cbr /\u003e PULONG ReturnBufferLength,\u003cbr /\u003e PNTSTATUS ProtocolStatus\u003cbr /\u003e);\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNote that the user will need to have previously called \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/ntsecapi/nf-ntsecapi-lsaconnectuntrusted\"\u003eLsaConnectUntrusted\u003c/a\u003e in order to obtain a connection handle to the LSA server and \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/ntsecapi/nf-ntsecapi-lsalookupauthenticationpackage\"\u003eLsaLookupAuthenticationPackage\u003c/a\u003e to find the id of the kerberos package (MICROSOFT_KERBEROS_NAME_A). Additionally, inspection of these functions in IDA (again they can be located in Sspicl.dll) will reveal that they are connecting to the Lsa via \u003cstrong\u003eRPC.\u003c/strong\u003e\u003csup\u003e31\u003c/sup\u003e.\u003c/p\u003e\u003cp\u003eThrough LsaCallAuthenticationPackage, a user can make a number of sensitive requests, although the exact requests available to the user depend on whether they are elevated or not. For example, an \u003cstrong\u003eunelevated\u003c/strong\u003e user can perform basic ticket management actions\u003csup\u003e32\u003c/sup\u003e, such as enumerating their current active tickets, purging the ticket cache, and \u003cstrong\u003eapplying arbitrary tickets to their current logon session\u003c/strong\u003e\u003csup\u003e33\u003c/sup\u003e. Hence, this effectively enables a user to change the credentials cached with their current logon session and therefore specify \u003cstrong\u003earbitrary \u003c/strong\u003e\u003cem\u003e\u003cstrong\u003enetwork only\u003c/strong\u003e\u003c/em\u003e\u003cstrong\u003e credentials\u003c/strong\u003e.\u003c/p\u003e\u003cp\u003eAdditionally, from an elevated context\u003csup\u003e34\u003c/sup\u003e an attacker can enumerate and dump tickets (e.g., credentials) belonging to other users, therefore providing similar functionality to mimikatz without\u003cem\u003e \u003c/em\u003eneeding to open a handle to lsass\u003csup\u003e35\u003c/sup\u003e.\u003c/p\u003e\u003cp\u003eA full list of the types of messages that can be sent to the Kerberos authentication package can be found \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/ntsecapi/ne-ntsecapi-kerb_protocol_message_type\"\u003ehere\u003c/a\u003e. In order to change the current TGT associated with a given logon session, the \u003cstrong\u003eKerbSubmitTicketMessage\u003c/strong\u003e can be passed, which uses the following message struct:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eTypedef struct _KERB_SUBMIT_TKT_REQUEST {\u003cbr /\u003e KERB_PROTOCOL_MESSAGE_TYPE MessageType;\u003cbr /\u003e LUID LogonId;\u003cbr /\u003e ULONG Flags;\u003cbr /\u003e KERB_CRYPTO_KEY32 Key;\u003cbr /\u003e ULONG KerbCredSize;\u003cbr /\u003e ULONG KerbCredOffset;\u003cbr /\u003e} KERB_SUBMIT_TKT_REQUEST, *PKERB_SUBMIT_TKT_REQUEST\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eTherefore, for a KerbSubmitTicketMessage, the ProtocolSubmitBuffer parameter simply points to a block of memory consisting of a KERB_SUBMIT_TKT_REQUEST struct followed immediately by an \u003ca href=\"https://www.ietf.org/rfc/rfc4120.txt\"\u003eASN\u003c/a\u003e encoded Kerberos ticket (which is the ticket to be applied to the specified logon session). The relevant code in mimikatz for submitting KerbSubmitTicketMessage requests can be found \u003ca href=\"https://github.com/gentilkiwi/mimikatz/blob/fe4e98405589e96ed6de5e05ce3c872f8108c0a0/mimikatz/modules/kerberos/kuhl_m_kerberos.c#L100-L127\"\u003ehere\u003c/a\u003e and in Rubeus \u003ca href=\"https://github.com/GhostPack/Rubeus/blob/732303e2f182d25e81ae25b4351782b2d0f061d0/Rubeus/lib/LSA.cs#L779-L878\"\u003ehere\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFollowing the call to LsaCallAuthenticationPackage, the user’s TGT has now been updated to the stolen ticket. From this point forward, any attempts to access network resources by any process/thread which is linked to the user’s access token/interactive logon session will \u003cstrong\u003eautomatically\u003c/strong\u003e authenticate over Kerberos using the stolen TGT (e.g., by requesting different service tickets/TGS for resources across the domain).\u0026nbsp;\u003c/p\u003e\u003cp\u003eNote, that a user can only have \u003cstrong\u003eone \u003c/strong\u003eTGT associated with their current logon session. Hence, applying a new ticket will wipe the user’s previous ticket. What if an attacker would like to preserve their current TGT? In this case, once again the NETONLY flag comes to the rescue - an attacker can create a \u003ca href=\"https://github.com/GhostPack/Rubeus#asktgt\"\u003e“sacrificial” NETONLY process\u003c/a\u003e via CreateProcessWithLogonW with arbitrary/junk credentials. This will create a new dummy process and, most importantly, a new logon session (and hence access token) to which a stolen TGT can be applied (and hence preserve the user’s current ticket)\u003csup\u003e36\u003c/sup\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOne important conclusion to draw from this technique for defense practitioners, is that as \u003cem\u003eall\u003c/em\u003e the activity is performed via LsaCallAuthenticationPackage (and hence over RPC), it does not require any \u003cstrong\u003edirect\u003c/strong\u003e interaction with lsass (N.B. direct here refers to opening a handle to lsass via OpenProcess). Furthermore, for this specific use case (ptt), all the activity is via local RPC \u003cem\u003euntil\u003c/em\u003e an attacker attempts to authenticate to a remote host (which will generate new logons).\u0026nbsp;\u003c/p\u003e\u003cp\u003eAs a further example, the README for \u003ca href=\"https://github.com/GhostPack/Rubeus#example-credential-extraction\"\u003eRubeus\u003c/a\u003e includes the following statement:\u0026nbsp;\u003c/p\u003e\u003cp\u003e“Rubeus doesn't have any code to touch LSASS (and none is intended), so its functionality is limited to extracting Kerberos tickets through use of the LsaCallAuthenticationPackage() API”\u0026nbsp;\u003c/p\u003e\u003cp\u003eTherefore, any detection logic which is predicated on handle access to lsass (e.g. via a \u003ca href=\"https://docs.microsoft.com/en-us/windows-hardware/drivers/ddi/wdm/nc-wdm-pob_pre_operation_callback\"\u003eObjectPreCallback\u003c/a\u003e kernel routine for a specified \u003cstrong\u003eprocess\u003c/strong\u003e or \u003cstrong\u003ethread\u003c/strong\u003e handle operation, or a user mode hook on OpenProcess/NtOpenProcess) could miss this activity. Hence, it is a potential blind spot for, say, defenders relying on Sysmon process access events to alert on suspicious process handle access.\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003e3. Pass-the-hash (PtH)\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eThe last two techniques this blog will cover are examples of an attacker changing the cached credentials associated with their current access token/logon session “illegitimately” by \u003cstrong\u003edirectly\u003c/strong\u003e \u003cstrong\u003emodifying\u003c/strong\u003e lsass memory. In the PtH scenario, the attacker’s access token is unchanged and points to the same logon session, however the associated cached credentials are directly overwritten to a stolen hash. From this point, any remote authentication attempts will use the stolen hash, as demonstrated below:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt363d7ac13b31f2a2/6075c4ac2999957477a782ca/7-under-the-hood-blog-access-token-manipulation.gif\" data-sys-asset-uid=\"blt363d7ac13b31f2a2\" alt=\"7-under-the-hood-blog-access-token-manipulation.gif\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 7 - How the PtH attack works under the hood. In this example, the legitimate hash of the user, ASTRO\\cosmo, is overwritten in-memory with the NTLM hash belonging to the ASTRO\\Administrator user.\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eIn this sense, both PtH and OPtH can be thought as \u003cem\u003efunctionally\u003c/em\u003e identical to the NETONLY technique previously discussed.\u003c/p\u003e\u003cp\u003eThe typical workflow of a PtH attack is:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eOpen a write handle to lsass (e.g. via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openprocess\"\u003eOpenProcess\u003c/a\u003e/\u003ca href=\"http://undocumented.ntinternals.net/UserMode/Undocumented%20Functions/NT%20Objects/Process/NtOpenProcess.html\"\u003eNtOpenProcess\u003c/a\u003e with a desired access of \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/procthread/process-security-and-access-rights\"\u003ePROCESS_VM_WRITE\u003c/a\u003e)\u003c/li\u003e\u003cli aria-level=\"1\"\u003eEnumerate the linked list of logon sessions\u003c/li\u003e\u003cli aria-level=\"1\"\u003eLocate the logon session of interest and identify the required authentication package (In the case of PtH/NTLM this is the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthn/msv1-0-authentication-package\"\u003eMSV1_0 authentication\u003c/a\u003e package)\u003c/li\u003e\u003cli aria-level=\"1\"\u003eUpdate the associated cached credentials\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eNote that these techniques often rely on parsing and modifying \u003cstrong\u003eundocumented\u003c/strong\u003e Windows structures. This is not something that will be covered in this blog, but more information on how this is performed can be found \u003ca href=\"https://www.slideshare.net/rootedcon/hernan-ochoa-wce-internals-rootedcon-2011\"\u003ehere\u003c/a\u003e and \u003ca href=\"https://blog.xpnsec.com/exploring-mimikatz-part-1/\"\u003ehere\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eHence, once the cached credentials are updated in memory, they will \u003cstrong\u003eautomatically\u003c/strong\u003e be used to authenticate remotely, as per the usual Windows SSO design, when any process/thread running as that token attempts to access a remote resource.\u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp\u003eNote, that in this simple case, there have been \u003cstrong\u003eno\u003c/strong\u003e additional logon session / access tokens created. However, in a similar fashion to pass-the-ticket attacks, these tools will also frequently need to create new junk NETONLY processes/logon sessions in order to preserve existing credentials or to apply stolen credentials to.\u0026nbsp;\u003c/p\u003e\u003cp\u003eAs a note, in order to obtain a write handle to lsass, malware will typically take two approaches:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003eAcquire SeDebugPrivilege\u003csup\u003e37\u003c/sup\u003e\u003c/li\u003e\u003cli aria-level=\"1\"\u003eSteal and impersonate a SYSTEM token\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThe first approach was discussed in part one of this blog series, however the latter approach is a typical example of stealing/impersonating a token \u003cstrong\u003efor the purpose of bypassing local access checks\u003c/strong\u003e (e.g. \u003ca href=\"https://github.com/GhostPack/Rubeus/blob/4c9145752395d48a73faf326c4ae57d2c565be7f/Rubeus/lib/Helpers.cs#L55-L107\"\u003estealing a SYSTEM token\u003c/a\u003e with a specific privilege enabled e.g. SeTcbPrivilege). A SYSTEM token is commonly obtained via \u003ca href=\"https://posts.specterops.io/understanding-and-defending-against-access-token-theft-finding-alternatives-to-winlogon-exe-80696c8a73b\"\u003estealing the primary token from winlogon\u003c/a\u003e.\u003c/p\u003e\u003ch3\u003e\u003cstrong\u003e4. Overpass-the-hash (OPtH)\u003c/strong\u003e\u003c/h3\u003e\u003cp\u003eThe Overpass-the-hash technique applies the same concept as pass-the-hash with one key difference: it converts a hash into a fully fledged TGT ticket.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWhen a user first logs on to a Windows workstation, as part of the Kerberos authentication process, the user’s password hash is used to encrypt a timestamp in order to validate the user’s identity to the Domain Controller / Key Distribution Center (KDC) and receive a TGT. Overpass-the-hash modifies these cached hashes\u003csup\u003e38\u003c/sup\u003e\u0026nbsp;in memory and then kicks off the normal Kerberos authentication protocol (AS-REQ/AS_REP etc.) in order to obtain \u003cstrong\u003ea fully fledged TGT\u003c/strong\u003e for a stolen hash.\u003csup\u003e39\u003c/sup\u003e\u003c/p\u003e\u003cp\u003eThis technique can be performed via mimikatz’ pth command (which is misleadingly labelled pth when it is actually performing overpass-the-hash under the hood):\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003emimikatz # sekurlsa::pth /user:Administrator /domain:ASTRO.testlab /ntlm: c0f969f35beb20e8f09ce86ef42ccd51\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThis essentially performs the same steps as PtH, except it targets the Kerberos SSP (and hence kerberos.dll).\u003csup\u003e40\u003c/sup\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3f0ec627cce8ca30/6075c51c66e3a310e06c57c6/8-opth-attack-blog-access-token-manipulation.gif\" data-sys-asset-uid=\"blt3f0ec627cce8ca30\" alt=\"8-opth-attack-blog-access-token-manipulation.gif\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eFigure 8 - How the OPtH attack works under the hood. In this example, the legitimate hash of the user, ASTRO\\cosmo, is overwritten in-memory with the hash belonging to the ASTRO\\Administrator user, kicking off the normal Kerberos authentication process.\u003c/figcaption\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eAs this technique once again involves wiping the current TGT associated with the user’s logon session, an attacker can use a NETONLY process (with an associated dummy logon session) to preserve their current TGT, which is exactly how mimikatz \u003ca href=\"https://github.com/gentilkiwi/mimikatz/blob/72b83acb297f50758b0ce1de33f722e70f476250/mimikatz/modules/sekurlsa/kuhl_m_sekurlsa.c#L947-L961\"\u003eperforms\u003c/a\u003e overpass-the-hash by default.\u0026nbsp;\u003c/p\u003e\u003cp\u003eFirstly, it spawns a new process in a suspended state via CreateProcessWithLogonW with the LOGON_NETCREDENTIALS_ONLY flag. It then obtains a handle to the primary token of this suspended process and retrieves the authentication id for the \u003cem\u003enew\u003c/em\u003e dummy logon session via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-gettokeninformation\"\u003eGetTokenInformation\u003c/a\u003e. This function is used to query information cached in the token via the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winnt/ne-winnt-token_information_class\"\u003eTOKEN_INFORMATION_CLASS\u003c/a\u003e enum, which in this case is \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winnt/ns-winnt-token_statistics\"\u003eTokenStatistics\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eHaving obtained the authentication id, mimikatz can now start enumerating the linked list of logon sessions within lsass, looking for the newly created logon session. Once it has found the target logon session (via the authentication id), it can then proceed to update the Kerberos credentials associated with it. Once the credentials are updated, the token (whose corresponding logon session is now linked to the stolen hash) can be converted to an impersonation token via DuplicateTokenEx and impersonated via SetThreadToken as we have seen previously.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOnce again at this stage, any attempts an attacker makes to access resources across the network will use the domain\\user and password hash combination provided as arguments to mimikatz for authentication. Therefore, all remote interactions will be performed with the access and privileges of the stolen credentials.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eConclusion\u003c/strong\u003e\u003c/h2\u003eThe purpose of this two-part blog series was to explain how fundamental concepts in Windows Security work under the hood and to show how attackers abuse these features in order to compromise Windows domains. This blog has demonstrated that irrespective of what tools or what authentication provider is abused, attackers act under a set of constraints that result in the same anomalous signals for access token manipulation (e.g., anomalous network only logins). These constraints are determined by the fundamental relationship between access tokens, logon sessions and cached credentials.\u003cp\u003e\u003c/p\u003e\u003cp\u003eReady for holistic data protection with \u003ca href=\"https://www.elastic.co/security\"\u003eElastic Security\u003c/a\u003e? Try it free today, or experience our latest version on \u003ca href=\"https://www.elastic.co/elasticsearch/service\"\u003eElasticsearch Service\u003c/a\u003e on Elastic Cloud.\u0026nbsp;And take advantage of our\u0026nbsp;\u003ca href=\"https://www.elastic.co/training/elastic-security-quick-start\"\u003eQuick Start training\u003c/a\u003e\u0026nbsp;to set yourself up for success.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eReferences\u003c/h2\u003e\u003cp\u003e1. \u0026nbsp;\u0026nbsp;For a recap of how Kerberos authentication works see Programming Windows Security, Keith Brown or \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://posts.specterops.io/kerberosity-killed-the-domain-an-offensive-kerberos-overview-eb04b1402c61\"\u003ehttps://posts.specterops.io/kerberosity-killed-the...\u003c/a\u003e. Additionally, Rubeus, which is a toolkit for interacting with Kerberos, has an extremely informative \u003ca href=\"https://github.com/GhostPack/Rubeus#readme\"\u003ereadme\u003c/a\u003e, which is recommended for further reading.\u003c/p\u003e\u003cp\u003e2. Remember, Windows will automatically authenticate with the credentials cached in the logon session whenever a user attempts to access a network resource as per the Windows SSO mechanism. Cached credentials here can refer to any authentication provider (e.g. NTLM hashes or Kerberos tickets). NB this assumes the user is interactively logged in (non-network).\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e3. \u0026nbsp;This is typically to avoid losing a foothold due to incident response or host isolation.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e4. \u0026nbsp;This is obviously only applicable to attacker activity on a compromised host, as opposed to an attacker executing code from another source e.g. remotely via \u003ca href=\"https://github.com/SecureAuthCorp/impacket\"\u003eimpacket\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e5. \u0026nbsp;\u003ca href=\"https://clymb3r.wordpress.com/2013/11/03/powershell-and-token-impersonation/\"\u003ehttps://clymb3r.wordpress.com/2013/11/03/powershel...\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e6. \u0026nbsp;See the ‘steal_token’ command from Cobalt Strike as an example of this technique: \u003ca href=\"https://www.cobaltstrike.com/help-beacon\"\u003ehttps://www.cobaltstrike.com/help-beacon\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e7. \u0026nbsp;\u003ca href=\"https://github.com/PowerShellMafia/PowerSploit/blob/c7985c9bc31e92bb6243c177d7d1d7e68b6f1816/Exfiltration/Invoke-TokenManipulation.ps1#L31-L44\"\u003eThis\u003c/a\u003e comment from the archived PowerSploit framework should also provide further clarification on this distinction between token theft for local privilege escalation vs lateral movement.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e8. \u0026nbsp;Alternatively, attackers can also go the password spraying route or attempt to use NTLM sniffing/replaying attacks via tools such as \u003ca href=\"https://github.com/SpiderLabs/Responder\"\u003eresponder\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e9. \u0026nbsp;Note that both LogonUserA/W are simple wrappers around \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthn/logonuserexexw\"\u003eLogonUserExExW\u003c/a\u003e in SspiCli.dll\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e10. \u0026nbsp;In exactly the same way, \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-createprocesswithlogonw\"\u003eCreateProcessWithLogonW\u003c/a\u003e can be passed a local admin account (rid-500) to execute an elevated process from a medium/unelevated context.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e11. \u0026nbsp;There are remote UAC registry \u003ca href=\"https://support.microsoft.com/en-gb/help/951016/description-of-user-account-control-and-remote-restrictions-in-windows\"\u003eoptions\u003c/a\u003e which can modify this behaviour.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e12. \u0026nbsp;There is an additional logon type, LOGON32_LOGON_NETWORK_CLEARTEXT, which is essentially a network logon but with cached credentials. See Programming Windows Security, Keith Brown for more information.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e13. \u0026nbsp;See for more info:\u003cbr /\u003e\u003c/p\u003e\u003ca href=\"https://blueteamer.blogspot.com/2018/12/disabling-uac-remote-restrictions-to.html\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003ca href=\"https://blueteamer.blogspot.com/2018/12/disabling-uac-remote-restrictions-to.html\"\u003ehttps://blueteamer.blogspot.com/2018/12/disabling-...\u003c/a\u003e\u003cbr /\u003e\u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://support.microsoft.com/en-gb/help/951016/description-of-user-account-control-and-remote-restrictions-in-windows\"\u003ehttps://support.microsoft.com/en-gb/help/951016/de...\u003c/a\u003e\u003cbr /\u003e\u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://labs.f-secure.com/blog/enumerating-remote-access-policies-through-gpo/\"\u003ehttps://labs.f-secure.com/blog/enumerating-remote-...\u003c/a\u003e\u003cp\u003e14. \u0026nbsp;NB there is also a \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-duplicatetoken\"\u003eDuplicateToken\u003c/a\u003e function but this only returns an impersonation token.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e15. \u0026nbsp;This can be verified by examining the function in IDA. Alternatively, check \u003ca href=\"https://doxygen.reactos.org/d1/d72/dll_2win32_2advapi32_2sec_2misc_8c.html#aed5dfd166fea98c3ac188fbbc8f88190\"\u003ehere\u003c/a\u003e on ReactOS.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e16. \u0026nbsp;This summary is a slight simplification of impersonation security. For a more thorough overview see James Forshaw’s “Introduction to Logical Privilege Escalation on Windows” slides (p26): \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://conference.hitb.org/hitbsecconf2017ams/materials/D2T3%20-%20James%20Forshaw%20-%20Introduction%20to%20Logical%20Privilege%20Escalation%20on%20Windows.pdf\"\u003ehttps://conference.hitb.org/hitbsecconf2017ams/mat...\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e17. \u0026nbsp;This title is taken from an excellent blog by Raphael Mudge: \u003ca href=\"https://blog.cobaltstrike.com/2015/12/16/windows-access-tokens-and-alternate-credentials/\"\u003eWindows Access Tokens and Alternate Credentials\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e18. \u0026nbsp;This is typically the main reason why option 2 is not commonly used by attackers.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e19. \u0026nbsp;Hence, running ‘whoami’ will still show the same user (as the token is still the same), despite the duplicated token having different network credentials. This is a common source of confusion when using Cobalt Strike’s \u003ca href=\"https://www.cobaltstrike.com/help-beacon\"\u003emake_token\u003c/a\u003e command (which performs the same technique as described under the hood).\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e20. \u0026nbsp;The Windows RPC/COM APIs also enable a user to specify network-only credentials. For example, this can be achieved for RPC by calling \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/rpcdce/nf-rpcdce-rpcbindingsetauthinfoexw\"\u003eRpcBindingSetAuthInfoExW\u003c/a\u003e and passing a SEC_WINNT_AUTH_IDENTITY structure via the AuthIdentity parameter. For more information see Programming Windows Security, Keith Brown and \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/wmisdk/setting-authentication-using-c-\"\u003ehttps://docs.microsoft.com/en-us/windows/win32/wmisdk/setting-authentication-using-c-\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e21. \u0026nbsp;While the two flags have different names, their meaning is the same; these credentials are only to be used on the network.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e22. \u0026nbsp;Note there are still \u003ca href=\"https://github.com/EmpireProject/Empire/blob/master/data/module_source/credentials/Invoke-CredentialInjection.ps1#L77-L82\"\u003eways\u003c/a\u003e around creating suspicious event logs for anomalous logon sessions.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e23. \u0026nbsp;This is a James Forshaw trick - see the following blog for more detail: \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://www.tiraniddo.dev/2017/05/reading-your-way-around-uac-part-3.html\"\u003ehttps://www.tiraniddo.dev/2017/05/reading-your-way...\u003c/a\u003e. Additionally, \u003ca href=\"https://github.com/googleprojectzero/sandbox-attacksurface-analysis-tools\"\u003eTokenViewer\u003c/a\u003e is an excellent tool for experimenting with this type of technique.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e24. \u0026nbsp;With this resulting impersonation token it is possible to write a file to System32 etc.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e25. \u0026nbsp;There still may be legitimate reasons for impersonating prior to calling an API though, such as to obtain a privilege you don’t currently have before calling an API which requires it (although note some APIs do automatically enable privileges).\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e26. \u0026nbsp;There are a few ways around this. For example, you can spawn a process as the child of a SYSTEM process by obtaining a handle to a SYSTEM process via OpenProcess with the \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/procthread/process-security-and-access-rights\"\u003ePROCESS_CREATE_PROCESS\u003c/a\u003e access right. This HANDLE can then be passed to \u003ca href=\"https://undocumented.ntinternals.net/index.html?page=UserMode%2FUndocumented%20Functions%2FNT%20Objects%2FProcess%2FNtCreateProcess.html\"\u003eNtCreateProcess\u003c/a\u003e as the ParentProcess parameter. This can also be achieved via the PROC_THREAD_ATTRIBUTE_PARENT_PROCESS parameter and CreateProcess: \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://gist.github.com/xpn/a057a26ec81e736518ee50848b9c2cd6\"\u003ehttps://gist.github.com/xpn/a057a26ec81e736518ee50...\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e27. \u0026nbsp;Bizarrely, CreateProcessWithTokenW takes a dwLogonFlags argument despite also requiring a handle to an existing token, which by definition, should already have a corresponding logon session. It seems likely that this is something to do with loading the user profile.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e28. \u0026nbsp;Programming Windows Security, Keith Brown\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e29. \u0026nbsp;Specifically, SE_IMPERSONATE_NAME for CreateProcessWithTokenW and SE_INCREASE_QUOTA_NAME (\u0026amp;) SE_ASSIGNPRIMARYTOKEN_NAME (if token is not assignable) for CreateProcessAsUserW\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e30. \u0026nbsp;A recap of Kerberos authentication can be found \u003ca href=\"https://posts.specterops.io/kerberosity-killed-the-domain-an-offensive-kerberos-overview-eb04b1402c61\"\u003ehere\u003c/a\u003e and see the following for more information on kerberos related attacks: \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://www.blackhat.com/docs/us-14/materials/us-14-Duckwall-Abusing-Microsoft-Kerberos-Sorry-You-Guys-Don't-Get-It.pdf\"\u003ehttps://www.blackhat.com/docs/us-14/materials/us-1...\u003c/a\u003e, , \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://github.com/GhostPack/Rubeus#readme\"\u003ehttps://github.com/GhostPack/Rubeus#readme\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e31. \u0026nbsp;\u003ca href=\"https://googleprojectzero.blogspot.com/2019/12/calling-local-windows-rpc-servers-from.html\"\u003ehttps://googleprojectzero.blogspot.com/2019/12/cal...\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e32. \u0026nbsp;E.g. the native Windows tool \u003ca href=\"https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/klist\"\u003eklist\u003c/a\u003e offers similar functionality and is clearly a wrapper around LsaCallAuthenticationPackage.\u003c/p\u003e\u003cp\u003e33. \u0026nbsp;Note that an unelevated user can only apply tickets to their own logon session; elevated privileges are needed to apply a TGT to a different logon session.\u003c/p\u003e\u003cp\u003e34. \u0026nbsp;There are some caveats/subtleties to this statement which are better answered by the Rubeus \u003ca href=\"https://github.com/GhostPack/Rubeus#example-credential-extraction\"\u003ereadme\u003c/a\u003e. In short though, the caller needs to register an LSA connection via \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/ntsecapi/nf-ntsecapi-lsaregisterlogonprocess\"\u003eLsaRegisterLsaProcess\u003c/a\u003e which requires the SeTcbPrivilege privilege (i.e. the caller is part of the trusted computing base).\u003c/p\u003e\u003cp\u003e35. \u0026nbsp;As an observation, you can also talk to the msv1_0 authentication package via LsaCallAuthenticationPackage and send the following message types: \u003cspan\u003e\u003c/span\u003e\u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/api/ntsecapi/ne-ntsecapi-msv1_0_protocol_message_type\"\u003ehttps://docs.microsoft.com/en-us/windows/win32/api...\u003c/a\u003e, although I have not investigated whether it is also possible to retrieve NTLM credentials through this interface.\u003c/p\u003e\u003cp\u003e36. \u0026nbsp;For more information see the Rubeus github repository \u003ca href=\"https://github.com/GhostPack/Rubeus\"\u003ereadme\u003c/a\u003e, which has a fantastic write up of lots of kerberos related functionality and opsec considerations.\u003c/p\u003e\u003cp\u003e37. \u0026nbsp;See \u003ca href=\"https://docs.microsoft.com/en-us/windows/win32/secauthz/enabling-and-disabling-privileges-in-c--\"\u003ehere\u003c/a\u003e for an example of enabling a privilege\u003c/p\u003e\u003cp\u003e38. \u0026nbsp;This can be verified by looking at PsOpenProcess/Thread in IDA and looking for a call to SePrivilegeCheck.\u003c/p\u003e\u003cp\u003e39. \u0026nbsp;Note, that acquiring SeDebugPrivilege tends to be very noisy from a detection logic perspective.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e40. \u0026nbsp;Note the hash/key can be rc4_hmac (e.g. NTLM), aes128_hmac, aes256_hmac etc.. see \u003ca href=\"https://www.slideshare.net/gentilkiwi/abusing-microsoft-kerberos-sorry-you-guys-dont-get-it/18\"\u003ehere\u003c/a\u003e for more.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e41. \u0026nbsp;See for more detail: \u003ca href=\"https://www.blackhat.com/docs/us-14/materials/us-14-Duckwall-Abusing-Microsoft-Kerberos-Sorry-You-Guys-Don%27t-Get-It.pdf\"\u003ehttps://www.blackhat.com/docs/us-14/materials/us-1...\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e42. \u0026nbsp;As a note, Rubeus’ \u003ca href=\"https://github.com/GhostPack/Rubeus#asktgt\"\u003easktgt\u003c/a\u003e functionality performs a variant of overpass-the-hash via building raw AS-REQ traffic for a given hash from an unelevated context and without needing to touch lsass.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-04-13T16:27:47.029Z","created_by":"bltc87e8bcd2aefc255","disclaimer":[],"full_bleed_image":{"uid":"blt2bc2ee0d053197c6","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-01T23:00:35.030Z","updated_at":"2020-07-01T23:00:35.030Z","content_type":"image/png","file_size":"79461","filename":"blog-banner-security-laptop.png","title":"blog-banner-security-laptop.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T15:16:43.194Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2bc2ee0d053197c6/5efd15937a4c912976093ae3/blog-banner-security-laptop.png"},"markdown_l10n":"","publish_date":"2021-04-20T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How attackers abuse Access Token Manipulation (ATT\u0026CK T1134)","seo_description_l10n":"This blog teaches security practitioners how attackers abuse legitimate Windows functionalities to move laterally and compromise Active Directory domains.","noindex":false,"canonical_tag":""},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltb35dc0df9e2855a5","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-07-01T23:00:22.154Z","updated_at":"2020-07-01T23:00:22.154Z","content_type":"image/png","file_size":"73829","filename":"blog-thumb-security-laptop.png","title":"blog-thumb-security-laptop.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T15:16:43.194Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb35dc0df9e2855a5/5efd1586e22ca44fde3b8201/blog-thumb-security-laptop.png"},"title":"How attackers abuse Access Token Manipulation (ATT\u0026CK T1134)","title_l10n":"How attackers abuse Access Token Manipulation (ATT\u0026CK T1134)","updated_at":"2025-03-10T12:05:21.654Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/how-attackers-abuse-access-token-manipulation","publish_details":{"time":"2025-03-10T12:05:25.598Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt29a413bc0dbf6a52","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"At Elastic, we :heart: APIs. PSD2 regulation is forcing banks to share their precious data through APIs, so why not get ahead with Elastic?","author":["blt8bf5cf20b113d800"],"body_l10n":"\u003cp\u003eAt Elastic, we :heart: APIs because developers love to work with them to get things done. APIs also have the power to change (or disrupt) an industry quickly and decisively, as is the case with The Revised Payment Service Directive (PSD2). APIs make it possible to seemlessly switch from Web browsers to apps, to deploy content to any platform, and to find the best deals among thousands of suppliers. PSD2 sets out to standardize APIs between EU banks and abolish the existing lock-ins that still exist in the industry. Because while financial institutions are closer to the forefront of the innovation curve than almost any other industry, the point can be made that this has not resulted in wide-spread open access to the core banking ecosystems - namely accounts and transactions. PSD2 is a directive from the European Union that will make banks open up access to their, otherwise private, core banking functions in ways that we have not seen before. PSD2 legislation introduces a breadth of opportunity for retail banks, while also introducing new risk. The Elastic Stack plays a vital role in many of the world’s banks today, and that will especially be true for PSD2 architectures.\u003c/p\u003e\u003ch2\u003eA Primer on PSD2 Regulation\u003c/h2\u003e\u003cp\u003eIn a nutshell, PSD2 stipulates that:\u003c/p\u003e\u003col\u003e\u003cli\u003eBanks have to allow a secure way for customer to authorize a third party provider to (1) have direct access to account and transactions data, (2) make and authorize payments via APIs.\u003c/li\u003e\u003cli\u003eCustomers have to be able to trust the privacy and security of their information, hence multi-factor authentication (at least two factors) and granular authorization controls (“entitlements”) have to be in place.\u003c/li\u003e\u003cli\u003eMember states have until 2018 to create local legislation for PSD2, to come into force likely end of 2018 or early 2019, along with penalties for non-compliance.\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eMuch in-depth content has been written about PSD2 since its inception. For a more thorough discussion of PSD2 we refer you to those resources. The rest of this blog will focus on the strategic choices that banks will need to make, and how PSD2 impacts banking architectures.\u003c/p\u003e\u003ch2\u003eStrategic Overview\u003c/h2\u003e\u003cp\u003eWe need to give you a couple of new acronyms to make sense of PSD2. Warning: they don't really roll off the tongue.\u003c/p\u003e\u003cdl\u003e\u003cdt\u003eASPSP\u003c/dt\u003e\u003cdd\u003eAccount Service Payment Service Providers, the core capability of retail banks.\u003c/dd\u003e\u003c/dl\u003e\u003cdl\u003e\u003cdt\u003ePISP\u003c/dt\u003e\u003cdd\u003ePayment Initiation Service Provider, a party in between the customer and the bank, and initiates a transaction. Can be a non-bank entity, like the retailer.\u003c/dd\u003e\u003c/dl\u003e\u003cdl\u003e\u003cdt\u003eAISP\u003c/dt\u003e\u003cdd\u003eAccount Information Service Provider, also known as “the cross-bank service” where customers can get a consolidated picture of their finances.\u003c/dd\u003e\u003c/dl\u003e\u003cdl\u003e\u003cdt\u003eXS2A\u003c/dt\u003e\u003cdd\u003eAccess to Account. The legislative API calls that grant AISPs access to transaction data.\u003c/dd\u003e\u003c/dl\u003e\u003cp\u003eSome things in life are inevitable, while others are entirely optional. Retail banks in the EU have to align their strategy along a range of options that lead from a compliant utility-like bank on one end, to a one-stop shop for anything related to consumer finance on the other end. A bank may choose to simply conform to the PSD2 legislation and continue much like it did before. But there is value to be found in going beyond the compliance of integration and open up financial services on top of XS2A. Value such as using your bank’s platform to consume other banks’ APIs and give them the complete picture of their financial status. Or, implement APIs that go beyond XS2A, like for requesting loans, giving advice around savings, or finding businesses where your users can spend their money on new, shiny things.\u003c/p\u003e\u003cp\u003eFintech players are disrupting business in all areas: investing, paying, and saving. And they are creating new ones like cryptocurrencies. Users love fintech because they provide their services using qualities that users have come to expect from Google, Facebook, Amazon and the likes: everything online and 24/7, using data intelligently to minimize users actions and maximize value, and have a tremendous user experience through UIs and APIs.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cblockquote\u003eAlong the spectrum of strategic options, banks may decide to be a lean, utility-like provider of payments and account services. Or, at the other end of the spectrum, provide a world-class experience that users will use as the focal point of all their financial dealings.\u003c/blockquote\u003e\u003cp\u003eSo, banks that operate in the European Union can strategize on three axes:\u003c/p\u003e\u003col\u003e\u003cli\u003eAPI Consumption: Stick to the position in the payments infrastructure that they have today, or additionally consume APIs from other ASPSPs to become an AISP that people crowd around?\u003c/li\u003e\u003cli\u003eAPI Exposure: Expose just the necessary APIs (as required), or additionally expose many more value-adding services through them?\u003c/li\u003e\u003cli\u003eUser Experience: Do you want to invest in best web and mobile user experience that is available in the market?\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc903651b9cc1934b/5f970af4432f517518d3f821/blog-psd2-1.png\" width=\"703\" height=\"447\" alt=\"The retail banking world before and after PSD2\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 703;height: 447;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eInteractions with our clients indicate that most banks, if not all, opt to go beyond the requirements that PSD2 demands of them to become a single open ecosystem between merchants, banks and users.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9b347f0ce3dd373d/5f970af983a0a3620dd3a055/blog-psd2-2.png\" width=\"616\" height=\"468\" alt=\"A simplified communication schema of today's payment systems, and in a PSD2 world\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 616;height: 468;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eA simplified architecture of a PSD2-compliant retail banking ecosystem already shows the important role that APIs will play. A big change is that more APIs will have to be opened up to more external parties. Apart from the obvious security concerns, this also means that you will no longer control the usage of your own APIs, other parties will use them as well.\u003c/p\u003e\u003ch2\u003eHaving and sharing actionable data will be the Norm for AISPs\u003c/h2\u003e\u003cp\u003eAISPs (we’ll repeat: Account Information Service Providers) add value to customers by ‘knowing it all’. To become an AISP, a bank must have a complete picture of a user’s financial transactions and accounts. On top of that, an AISP should know what the user wants to achieve, what merchants the user likes, all with user consent (GDPR, anyone?). On top of that, AISPs should strive to have the best experiences (that includes user interfaces, alerts, brand image, trustworthiness) to get in a position of advising the user. Luckily, APIs also help out to get data from merchants and ASPSPs into the AISP.\u003c/p\u003e\u003cp\u003eReal-time query engines are able to react and predict to users, transactions, and the like. Having offline batch processing is a great way to extract intelligence out of data in some cases, but to get that intelligence online, a fast data store is needed with millisecond response times.\u003c/p\u003e\u003cp\u003eEuropean banks have been experimenting with personal finance features on their platforms for years. But they have always been based on the partial picture of the user’s finances, and were arguably not as functional a users have come to expect in recent years. With PSD2, we expect a surge of new personal finance tools that will be completely automated, intelligent and responsive. It requires real-time analytics and natural language processing (NLP) at scale, such as aggregations, fuzzy queries, multi-language, and predictions.\u003c/p\u003e\u003ch2\u003ePSD2 Architectures\u003c/h2\u003e\u003cp\u003eBanks already operate using internal APIs that connect modern, scalable front-end applications to core account and payment systems. Typically, the core banking systems are legacy systems that don’t scale effortlessly, so they offload part of their responsibilities to various modern data stores to save cycles on the core systems. PSD2-compliant architectures will have to make those APIs accessible to 3rd parties that are, at best, under the bank’s influence, not control. This means that the APIs will make or break access to bank’s most basic functions.\u003c/p\u003e\u003ch3\u003eA Shopping List for PSD2 Architectures\u003c/h3\u003e\u003cp\u003eA PSD2-compliant architecture requires at least these major components:\u003c/p\u003e\u003col\u003e\u003cli\u003eAn API to the fast access layer with proper scaling, throttling, and security in place.\u003c/li\u003e\u003cli\u003eA fast access layer to offload the core banking applications and provide cheap, scalable data services to the API layer.\u003c/li\u003e\u003cli\u003eCore banking applications, often legacy systems that are already in place. ACID-compliance, a relational nature and its license models usually hinder scalability.\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/observability\" target=\"_self\"\u003eAn observability platform\u003c/a\u003e for all of the above, and the focus of the rest of this blog.\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eThe rest of this blog will focus on executing an API-first banking strategy, starting out with running PSD2-compliant APIs and moving ahead as an AISP to provide users the single, intelligent interface to all their personal finance needs. Part II will focus on a logging platform to monitor the PSD2 architecture.\u003c/p\u003e\u003ch2\u003eThe Elastic Stack\u003c/h2\u003e\u003cp\u003eThe Elastic Stack is a use-case agnostic data platform that is very well-suited for running high-traffic, API-driven environments like this one. It excels especially when the mere serving of key/value pairs is not enough. Elastic’s analytic functionalities for both structured as well as unstructured data are necessary for serving dashboards, advisories, transaction histories, integrating with 3rd party data stores and the likes. Elastic makes data come alive, it’s far beyond a bunch of documents waiting to be called by their ID. Often the Core Banking Apps are not suited for the scale that banks will be faced with due to technical and licensing issues. Elastic has scalability built-in from its first lines of code, and there are great benefits to its licensing model which is based on number of logical nodes, not the amount of queries, users or ingested data.\u003c/p\u003e\u003cp\u003eThe rest of this blog will focus on executing an API-first banking strategy, starting out with running PSD2-compliant APIs and moving ahead as an AISP to provide users the single, intelligent interface to all their personal finance needs. Part II will focus on a logging platform to monitor the PSD2 architecture.\u003c/p\u003e\u003ch2\u003eThe Elastic Stack for Smart Banking Data Platforms\u003c/h2\u003e\u003cp\u003eThe Elastic Stack is perfectly suited to run not just your classical search and logging use cases, but also for serving business data via APIs. In a nutshell, an PSD2-enabled bank that also will become an AISP will need the following high-level architecture. In pink, the minimum PSD2 components. In green, an incomplete list of differentiating value-adding services (once interbanking and intermerchant APIs are in place, the list of imaginable value-adding services becomes huge).\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdef8417de3a1eefa/5f970af8545bdb56ce4903bc/blog-psd2-3.png\" width=\"755\" height=\"499\" alt=\"The Elastic Stack for Smart Banking Data Platforms\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 755;height: 499;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe think that successfully running value-adding platforms successfully, banks will require excellence in these key areas:\u003c/p\u003e\u003col\u003e\u003cli\u003eSecurity and Privacy: This includes corporate and legislative requirements such as encryption, authorizations, audit logging, privacy, and data separation.\u003c/li\u003e\u003cli\u003eMonitoring and Alerting: The ability to know current and historical status of the service, and be informed of any serious deviations from what is considered normal. The ability to view the inner workings of a system is also called observability.\u003c/li\u003e\u003cli\u003eQuality of Service: The ability to throttle in case of overloads, to protect underlying systems from DoS attacks and to allow the enforcement of Fair Use policies.\u003c/li\u003e\u003cli\u003eEasy, far-reaching scalability: Scaling the platforms should be simple and painless.\u003c/li\u003e\u003cli\u003eReal-time answers: Answer calls fast to support the needs and expectations of users, throughout the user experience.\u003c/li\u003e\u003cli\u003eSelf-learning and self-service: Getting useful intelligence out of the data without having to foresee and manages what exactly is relevant (because who would know beforehand how security breaches or outages might unfold?) requires abilities to find anomalies, create advanced dashboards, and a raw data store. Consumers are expected to mix and match layouts of dashoards and apps to their needs, but they will only do so if the data and UX are very intuitive to work with.\u003c/li\u003e\u003c/ol\u003e\u003ch3\u003eElastic Architecture for Data Platforms\u003c/h3\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3c8065fff0095f2f/5f970af8878c0d548cdc1361/blog-psd2-4.png\" width=\"734\" height=\"471\" alt=\"The Elastic Stack for Smart Banking Data Platforms Architecture\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 734;height: 471;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThe Elastic Stack is a complete suite of products for running API architectures:\u003c/p\u003e\u003cul\u003e\u003cli\u003eLogstash is a dynamic data collection pipeline with an extensible plugin ecosystem and strong Elasticsearch synergy. It can read from slower, write-optimized primary data stores such as RDBMSs. Ingestion can be batch-oriented or near real-time.\u003c/li\u003e\u003cli\u003eElasticsearch is a distributed, REST API enabled, JSON-based search and analytics engine designed for horizontal scalability, maximum reliability, and easy management.\u003c/li\u003e\u003cli\u003eKibana gives shape to your data and is the extensible user interface for configuring and managing all aspects of the Elastic Stack.\u003c/li\u003e\u003cli\u003eX-Pack is a single extension that integrates handy features — security, alerting, monitoring, reporting, graph exploration, and machine learning.\u003c/li\u003e\u003cli\u003eThe APIs sit on top of the Stack, as well as custom UIs like mobile apps or websites.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eThe Elastic Stack logical architecture for APIs combines all these products into an end to end platform with accompanying services, like Consulting and Expert Support. As you have probably read a bunch of times by now, Elastic :heart: APIs. That is why the Elastic Stack products natively supports REST API endpoints for easy integration into any architecture.\u003c/p\u003e\u003ch3\u003eServing PSD2 API Requests\u003c/h3\u003e\u003cp\u003eElasticsearch natively supports REST API endpoints, likely the same technology that will dominate the PSD2 landscape. Expect millisecond response times to queries, in an encrypted, authenticated and authorized ecosystem, including audit logging (GDPR anyone?).\u003c/p\u003e\u003cp\u003eOf course, banks already run private APIs similar to PSD2’s public ones to connect their customers to their data on mobile apps, web browsers, kiosks, or ATMs. Consolidating these private and public APIs is going to make banks more cost-efficient and agile (less code to manage).\u003c/p\u003e\u003ch3\u003eStepping Up Your Game as an AISP\u003c/h3\u003e\u003cp\u003eElastic’s most unique feature for AISPs is the ability to not just store and serve data safely and on immense scale, but to get meaningful, actionable insights from that data. We expect that users will be searching for the AISP that provides that best combination of data intelligence and user experience and handle most day-to-day finances with that AISP. Kibana shows off Elasticsearch’s aggregations and time-series features nicely. Custom UIs can utilize the same features and implement a completely custom presentation.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd49eddf9206e585b/5f970af4fe49b57a83a141c8/blog-psd2-5.png\" width=\"413\" height=\"464\" alt=\"A Kibana screenshot of real-time payments analytics\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 413;height: 464;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eScalability is important when you set out to store a breadth of customer-centric financial information. Elasticsearch’s code is setup to be scalable from its very beginnings, resulting in a system that can handle millions of concurrent reads and writes per second. It allows AISPs to provide services with 3rd party data just as easily as with internal data.\u003c/p\u003e\u003ch3\u003eImplementing a Customer Financial Advisory\u003c/h3\u003e\u003cp\u003eHaving a time-series of financial transactions of a customer enables an AISP to provide relevant and timely information to their users. Disregard, for a moment, that having an army of analysts look at all data in an AISP to turn it into meaningful information would be cost-prohibitive, i.e. very expensive. What could they possibly come up with? Customers might want to know when they slowly increase their spending in certain categories, like groceries. Or, they might be interested to hear about how their bank can help them redecorate their homes or buy a new car. If privacy regulation allows, an AISP could also aggregate and sell anonymized market insights to governments and commercial sectors. Facebook already acquired a European payments license.\u003c/p\u003e\u003cp\u003eGoing back to the army of analysts. Elastic is investing heavily in new ways to look at data that exists in the open source Stack. Two of them are particulary interesting to behavioral intelligence. X-Pack Machine Learning is a technology that does unsupervised anomaly detection on time-series data. It builds up a sense of “normal” by looking at historical data and by looking at peer data, and then weeds out false positives to give you only relevant, actionable insights. This is your army of analysts.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt70ed1e67a7adc4ef/5f970af8209f0756c89d3cd7/blog-psd2-6.gif\" width=\"770\" height=\"433\" alt=\"X-Pack Machine Learning GIF\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 770;height: 433;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eSome good reads on X-Pack Machine Learning are:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/products/x-pack/machine-learning\"\u003ePage: Elastic X-Pack Machine Learning\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/videos/machine-learning-lab-3-detect-outliers-in-a-population\"\u003eVideo: Outlier Detection with Machine Learning\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eTraversing Relevant Connections\u003c/h3\u003e\u003cp\u003eX-Pack Graph is a technology that presents connections in data as a graph. It weeds out irrelevant, ‘boring’ connections by comparing subsets of data with their peers. For instance, because the total population has a certain percentage of their money spent on, say, cappuccinos, we might want to explore which subset of the population spends more than average on cappuccinos? This is trivial even with SQL-era aggregations. But now answer this: if I want to sell more cappuccinos, which other products or services should I relate my marketing to so that I reach new audience that would gladly buy more cappuccinos if given the opportunity? What is uncommonly common about people that drink uncommon amounts of cappuccinos that can help me propel my business to the right locations, the right products, using the right brand message? And how can I get these insights as self-service analytics? Graph will help to get meaningful relations from data using wisdom of the crowd algorithms.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2f0a0dab9edbf71a/5f970af545fa7d72ddd1dbc6/blog-psd2-7.png\" width=\"705\" height=\"412\" alt=\"X-Pack Graph demo\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 705;height: 412;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eSome good reads on X-Pack Graph are:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/products/x-pack/graph\"\u003ePage: Elastic X-Pack Graph\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/videos/deep-dive-new-graph-capabilities-elastic-stack-mark-harwood\"\u003eVideo: Graph Deep Dive with Mark Harwood\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/using-elastic-graph-and-kibana-to-analyze-panama-papers\"\u003eBlog: Using Elastic Graph + Kibana to Analyze Panama Papers\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003e‘Orchestration as a Service’ with Cloud Enterprise\u003c/h3\u003e\u003cp\u003eElastic Cloud is our public SaaS service running on AWS. Using that technology and our expertise, we set out to bring the Elastic Cloud experience to any data center. And that’s what we did with Elastic Cloud Enterprise (ECE). As organizations adopt Elastic across use cases and departments, ECE keeps your focus on building value-adding services on top of your Elastic clusters.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3eb1e0be94bc6949/5f970af42425cd7a8af684a4/blog-psd2-8.gif\" width=\"889\" height=\"498\" alt=\"Elastic Cloud Enterprise demo\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);width: 889;height: 498;display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe would love to talk about ECE some more, but this blog is not meant as a comprehensive discussion of Elastic Cloud Enterprise. Luckily, those resources already exist. Some good reads on ECE are:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/cloud/enterprise\"\u003ePage: Elastic Cloud Enterprise\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/elastic-cloud-enterprise-launch-demo\"\u003eWebinar: Elastic Cloud Enterprise Demo\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eHuh? I thought Elastic was for Monitoring: Logs, Metrics and Traces!\u003c/h2\u003e\u003cp\u003eElastic has been synonymous with logging for years. Indeed, many global financial institutions ingest logs, metrics and traces of their IT infrastructure to an Elastic platform. That platform then provides dashboards, time-series analytics, anomaly detecting using X-Pack Machine Learning, real-time alerting, fraud detection, root-cause analysis and other services with that data. Part II of this series will focus on running Elastic for monitoring APIs.\u003c/p\u003e\u003cp\u003eIcons made by Freepik from flaticon.com\u003c/p\u003e\u003cdiv\u003e\u003c/div\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:22:51.061Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf7e0361d38ceea67"],"full_bleed_image":{"title":"psd2-architectures-elasticsearch-fullbleed.jpg","uid":"blte6583088ad57a933","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T10:09:29.607Z","updated_at":"2019-01-05T10:09:29.607Z","content_type":"image/jpeg","file_size":"165387","filename":"psd2-architectures-elasticsearch-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T19:59:56.128Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte6583088ad57a933/5c30825929d13af10bc2ac92/psd2-architectures-elasticsearch-fullbleed.jpg"},"markdown_l10n":"","publish_date":"2017-09-14T17:13:50.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"psd2-architectures-elasticsearch-fullbleed.jpg","uid":"blte6583088ad57a933","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T10:09:29.607Z","updated_at":"2019-01-05T10:09:29.607Z","content_type":"image/jpeg","file_size":"165387","filename":"psd2-architectures-elasticsearch-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T19:59:56.128Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte6583088ad57a933/5c30825929d13af10bc2ac92/psd2-architectures-elasticsearch-fullbleed.jpg"},"title":"PSD2: Modern Banking API Architectures with the Elastic Stack","title_l10n":"PSD2: Modern Banking API Architectures with the Elastic Stack","updated_at":"2025-03-10T12:01:46.891Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/psd2-architectures-with-the-elastic-stack","publish_details":{"time":"2025-03-10T12:01:54.027Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3ff2488406803b3c","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt613ce7bc42d2579c"],"body_l10n":"\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eWelcome to Keeping up with Kibana! This is a series of posts on new developments in the Kibana project and any related learning resources and events.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eWe had a Kibana all-hands meeting this week. Each team gave a presentation on the main projects they are working on. The all-hands meeting provides the team a good opportunity to understand what we’re doing across the team and to get aligned on the priorities, plans, and timelines. Going forward, we will have an all-hands every 5 weeks.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eTypeScript support\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eThe Platform team has begun to work on first-class\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/18780\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #1155cc;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eTypeScript \u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003esupport in Kibana. Supporting TypeScript is necessary for rolling out the new Kibana Platform roadmap and for supporting greenfield plugin development, such as the Infra app. There won’t \u0026nbsp;be an immediate impact on the team because ECMAScript will continue to compile as it always has. Once support of TypeScript is complete, the Platform team will communicate about the roll out and usage. \u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eLaying the foundation for a new platform\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eThe Platform team has completed a \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/9675\" style=\"text-decoration: none;\" rel=\"text-decoration:none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #1155cc;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003enew platform\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e rollout roadmap and is working on the foundation for rolling out the new platform.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eKibana localization\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eOur \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/17201\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #1155cc;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003elocalization\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e project is making progress. We’re finishing up the technical guide and starting to build the Angular wrapper.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eMaking progress in security\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eThe Security team is moving fast with \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/18178\" style=\"text-decoration: none;\" rel=\"text-decoration:none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #1155cc;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eRBAC\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e. We’re finalizing the internal design, writing tests, and beginning to document the changes. The team continues to make progress on the Spaces implementation and began Reactifying the Role management page.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eFocusing on accessibility\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.656;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eThe Design team is making big progress on the \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/11534\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #1155cc;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eAccessibility \u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eproject.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.656;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.656;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eTesting\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.656;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eWe’re almost ready for our 6.3 release! QA continues to test 6.3.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003ePlatform\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cul style=\"margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eMake schema async, and plugin discovery expose raw package jsons\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18926\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#18926\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eFunctional test runner changes through kbn-test package\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18568\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#18568\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eFix timing issue with esArchiver that causes it to fail when a snapshot is in progress\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18624\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#18624\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 14pt;margin-bottom: 4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eSharing\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cul style=\"margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eClean up time range handling in embeddables \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/17718\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e17718\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eChange KuiContextMenu to EuiContextMenu \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/17621\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e17621\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eDisplay disabled control when index pattern no longer exists \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18931\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e18931\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eFix arrows used to modify control order \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18929\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e18929\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 14pt;margin-bottom: 4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eVisualizations\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cul style=\"margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eAllow splitting series on multiple fields (\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/17855\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#17855\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e)\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: italic;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eAdd EditorOptionsGroup component (for Reactifying the existing editors) (\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18812\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#18812\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e,\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/18917\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#18917\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e)\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: italic;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eDon't deep clone vis in courier request handler (\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/19069\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#19069\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e)\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: italic;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eFix missing value display for number fields (\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/16644\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#16644\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e)\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\" style=\"list-style-type: disc;font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: italic;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre;margin-left: 11pt;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eReplace _term order in terms agg by _key (due to deprecation in ES) (\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/19032\" style=\"text-decoration: none;\"\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: underline;webkit-text-decoration-skip: none;text-decoration-skip-ink: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e#19032\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;font-family: Arial;color: #666666;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003e)\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 14pt;margin-bottom: 4pt;\"\u003e\u003cspan style=\"font-size: 13.999999999999998pt;font-family: Arial;color: #434343;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eManagement\u003c/strong\u003e\u003c/span\u003e\u003c/h4\u003e\u003ch4 dir=\"ltr\" style=\"line-height: 1.656;margin-top: 14pt;margin-bottom: 4pt;\" rel=\"line-height:1.656;margin-top:14pt;margin-bottom:4pt;\"\u003e\u003cspan style=\"font-weight: normal;\"\u003e\u003c/span\u003e\u003c/h4\u003e","category":[],"created_at":"2019-04-01T13:12:05.689Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"parent_uid":null,"uid":"blt711fba4b0341c251","created_by":"blt0a74c5872964bd5e889a6b79","updated_by":"blt0a74c5872964bd5e889a6b79","created_at":"2018-11-16T05:37:37.473Z","updated_at":"2018-11-16T05:37:37.473Z","content_type":"image/png","file_size":"95050","filename":"our-source-code-as-you-are.png","title":"our-source-code-as-you-are.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T19:59:05.130Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt711fba4b0341c251/5bee57a1153999e837012b00/our-source-code-as-you-are.png"},"markdown_l10n":"","publish_date":"2018-05-22T16:31:33.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"New developments in the Kibana project include: TypeScript support, new platform roadmap, Kibana localization progress, RBAC progress in security, accessibility project update, platform, sharing, visualization and management updates.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"blt0ba59e988f7aec63","ACL":{},"content_type":"image/png","created_at":"2019-02-19T18:16:15.632Z","created_by":"blt5c97f327f30903e707c39c30","description":"","file_size":"48267","filename":"customer-bpce-image1.png","parent_uid":null,"tags":[],"title":"customer-bpce-image1.png","updated_at":"2023-01-11T13:35:45.245Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-11T13:35:52.984Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ba59e988f7aec63/63bebb310dc3963ccff8aa76/customer-bpce-image1.png"},"title":"Keeping up with Kibana: This week in Kibana for May 14, 2018","title_l10n":"Keeping up with Kibana: This week in Kibana for May 14, 2018","updated_at":"2025-03-10T11:55:06.636Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/keeping-up-with-kibana-2018-05-14","publish_details":{"time":"2025-03-10T11:55:10.703Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbbc0b11f65d7a6e8","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt85b0e579ed18da50"],"body_l10n":"\u003ch4\u003eWelcome to Keeping up with Kibana! This is a series of posts on new developments in the Kibana project and any related learning resources and events.\u003c/h4\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eOne-click sample data\u003c/h2\u003e\u003cp\u003eThe highlight of this week is the new Sample Data set on the home page. This new feature\u0026nbsp;allows for a one-click getting started experience users new to Kibana. Users can load a constructed Flight data set that includes a pre-packaged dashboard and\u0026nbsp;experiment with Kibana without having to go through the process of loading data themselves. Here is what it looks like after loading:\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3f0968e7e0277ca2/5c30595925a401fc6fe4f515/Screen_Shot_2018-05-30_at_12.48.57_PM.png\" data-sys-asset-uid=\"blt3f0968e7e0277ca2\" alt=\"Screen Shot 2018-05-30 at 12.48.57 PM.png\" style=\"width: 979;height: 514;\" width=\"979\" height=\"514\"/\u003e\u003c/p\u003e\u003cp\u003eClicking the \"Launch\" button shows the pre-packaged dashboard:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdf94568915cdff18/5c3059563fdf8ce26f0c08e3/Screen_Shot_2018-05-30_at_12.49.58_PM.png\" data-sys-asset-uid=\"bltdf94568915cdff18\" alt=\"Screen Shot 2018-05-30 at 12.49.58 PM.png\" style=\"width: 975;height: 513;\" width=\"975\" height=\"513\"/\u003e\u003c/p\u003e\u003cp\u003eSee\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/pull/17807\"\u003e17807\u003c/a\u003e\u0026nbsp;for more details.\u003c/p\u003e\u003ch2\u003eCanvas technology preview\u003c/h2\u003e\u003cp\u003eCanvas is getting a facelift!\u003c/p\u003e\u003cp\u003eIn the oncoming weeks, we're converting all our UI components to EUI (Elastic's in-house UI framework). Most recently we merged a few changes to the workpad header as well as workpad \u0026amp; page settings for the next release!\u0026nbsp;Here's a sample of what's in store:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd58705ce446a50c4/5c305965ebb7714d660270c4/May28_canvas_facelift.png\" data-sys-asset-uid=\"bltd58705ce446a50c4\" alt=\"May28 canvas facelift.png\"/\u003e\u003c/p\u003e\u003cp\u003eWe are also working on new layout engine that will let you easily move, resize and rotate elements in Canvas. The version we have now is just ok, but we've been working on an all new version that is looking \u003cem\u003eamazing\u003c/em\u003e. The first iteration of it will be functionality identical to the current system, with the addition of keyboard commands, but our team has built all sorts of awesome stuff under the covers. Like these rad 3D transforms:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2004309c7b6ede6c/5c305963ca40458566ef6749/May28-canvas_layout_engine.gif\" data-sys-asset-uid=\"blt2004309c7b6ede6c\" alt=\"May28-canvas layout engine.gif\" style=\"width: 688;height: 335;\" width=\"688\" height=\"335\"/\u003e\u003c/p\u003e\u003cp\u003eCheck out more Canvas news \u003ca href=\"http://canvas.elastic.co/\"\u003ehere\u003c/a\u003e\u003c/p\u003e\u003ch2\u003eOther enhancements and bug fixes\u003c/h2\u003e\u003ch4\u003eSecurity\u003c/h4\u003e\u003cp\u003eSpaces:\u0026nbsp; we are making progress on Reactifying the existing role management screen.\u003c/p\u003e\u003cp\u003eRBAC: We’re in the process of splitting out the platform specific PRs that enable RBAC. A\u0026nbsp;number of them have been merged, others are still in review, and a few more are soon to come.\u003c/p\u003e\u003cul\u003e\u003cli\u003eIntroduced the concept of SavedObjectRepository which will assist with implementing spaces and securing the SavedObjectsClient for RBAC \u003ca href=\"https://github.com/elastic/kibana/pull/19013\"\u003e#19013\u003c/a\u003e\u003c/li\u003e\u003cli\u003eImplemented consistent multi-type SavedObjectsClient.find which is currently used by saved objects management and will allow us to secure it for RBAC \u003ca href=\"https://github.com/elastic/kibana/pull/19231\"\u003e#19231\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eDesign\u003c/h4\u003e\u003cp\u003eOn the EUI front, we are making good progress making EUI fully compatible with React 16.3. We have also added the much requested \u003ca href=\"https://github.com/elastic/eui/pull/872\"\u003eButton Groups / Toggles\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eWe also:\u003c/p\u003e\u003cul\u003e\u003cli\u003eUpdated EuiSearchBar to React 16.3 lifecycle \u003ca href=\"https://github.com/elastic/eui/pull/863\"\u003e#863\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFixed EuiComboBox focus trap \u003ca href=\"https://github.com/elastic/eui/pull/866\"\u003e#866\u003c/a\u003e\u003c/li\u003e\u003cli\u003eAdded support for custom props for rows in EuiBasicTable and EuiInMemoryTable. \u003ca href=\"https://github.com/elastic/eui/pull/869\"\u003e#869\u003c/a\u003e\u003c/li\u003e\u003cli\u003eMade\u0026nbsp;\u003ca href=\"https://github.com/elastic/eui/pulls?utf8=%E2%9C%93\u0026q=is%3Apr+is%3Aclosed+merged%3A%3E%3D2018-05-19\"\u003e15 more small changes\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003ePlatform\u003c/h4\u003e\u003cul\u003e\u003cli\u003eOption to run Kibana from build for CI \u003ca href=\"https://github.com/elastic/kibana/pull/19125\"\u003e#19125\u003c/a\u003e\u003c/li\u003e\u003cli\u003eRemoved custom tslint overrides for kbn-system-loader \u003ca href=\"https://github.com/elastic/kibana/pull/19336\"\u003e#19336\u003c/a\u003e\u003c/li\u003e\u003cli\u003eRemoved custom tslint overrides for kbn-pm \u003ca href=\"https://github.com/elastic/kibana/pull/19335\"\u003e#19335\u003c/a\u003e\u003c/li\u003e\u003cli\u003eRemoved the tslint requirement to prefix interfaces with an `I` \u003ca href=\"https://github.com/elastic/kibana/pull/19402\"\u003e#19402\u003c/a\u003e\u003c/li\u003e\u003cli\u003eUpgraded eslint-plugin-no-unsanitized to support runtime `import`, which we’ll need for application bundles in the new platform \u003ca href=\"https://github.com/elastic/kibana/pull/19315\"\u003e#19315\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eOperations\u003c/h4\u003e\u003cp style=\"margin-left: 20px;\"\u003eAdded validation of the current node version \u003ca href=\"https://github.com/elastic/kibana/pull/19154\"\u003e#19154\u003c/a\u003e\u003c/p\u003e\u003ch4\u003eSharing enhancements and bug fixes\u003c/h4\u003e\u003cul\u003e\u003cli\u003eConverted Dashboard “Add Panel” to EUI PR 17374\u003c/li\u003e\u003cli\u003eFixed copy to clipboard IE bug PR 19281\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eVisualizations bug fixes\u003c/h4\u003e\u003cul\u003e\u003cli\u003eAxis Labels Filter - better geometry assessment \u003ca href=\"https://github.com/elastic/kibana/pull/16130\"\u003e#16130\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFixed rendering markdown when updating open in new tab setting \u003ca href=\"https://github.com/elastic/kibana/pull/19356\"\u003e#19356\u003c/a\u003e\u003c/li\u003e\u003cli\u003eDon't show toast warning in filter agg \u003ca href=\"https://github.com/elastic/kibana/pull/19255\"\u003e#19255\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFixed flaky load discover search \u003ca href=\"https://github.com/elastic/kibana/pull/19265\"\u003e#19265\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eManagement\u003c/h4\u003e\u003cul\u003e\u003cli\u003eAccount for cluster level settings for Watcher UI \u003ca href=\"https://github.com/elastic/kibana/pull/19121\"\u003e#19121\u003c/a\u003e\u003c/li\u003e\u003cli\u003eSaved objects UI in React! \u003ca href=\"https://github.com/elastic/kibana/pull/17426\"\u003e#17426\u003c/a\u003e, \u003ca href=\"https://github.com/elastic/kibana/pull/19193\"\u003e#19193\u003c/a\u003e\u003c/li\u003e\u003cli\u003eEnsure index patterns leverage existing optimistic concurrency \u003ca href=\"https://github.com/elastic/kibana/pull/18937\"\u003e#18937\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eUntil next week,\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eKibana Team\u003c/strong\u003e\u003c/p\u003e","category":[],"created_at":"2019-04-01T13:12:00.114Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt29843bb98ba59a2a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:37:11.833Z","updated_at":"2018-10-11T05:37:11.833Z","content_type":"image/jpeg","file_size":"71803","filename":"blog-kibana-banner.jpg","title":"blog-kibana-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T15:49:05.384Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt29843bb98ba59a2a/5bbee187eb7e90a514e6e46b/blog-kibana-banner.jpg"},"markdown_l10n":"","publish_date":"2018-05-28T16:31:33.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"New One click sample data has been added to Kibana. Many updates made to Canvas. Also changes to security, design, visualizations, management and other applications within Kibana.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":3,"is_dir":false,"uid":"blt0ba59e988f7aec63","ACL":{},"content_type":"image/png","created_at":"2019-02-19T18:16:15.632Z","created_by":"blt5c97f327f30903e707c39c30","description":"","file_size":"48267","filename":"customer-bpce-image1.png","parent_uid":null,"tags":[],"title":"customer-bpce-image1.png","updated_at":"2023-01-11T13:35:45.245Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-11T13:35:52.984Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ba59e988f7aec63/63bebb310dc3963ccff8aa76/customer-bpce-image1.png"},"title":"Keeping up with Kibana: This week in Kibana for May 28, 2018","title_l10n":"Keeping up with Kibana: This week in Kibana for May 28, 2018","updated_at":"2025-03-10T11:54:09.582Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/keeping-up-with-kibana-2018-05-28","publish_details":{"time":"2025-03-10T11:54:13.258Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt495b203e24e8e651","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"We are deprecating support for ciphers that are considered weak and will update the list of ciphers supported to connect to Elasticsearch Service to include the Mozilla Intermediate ciphers after January 30, 2022.","author":["blte2d7fdc8a799bffb"],"body_l10n":"\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAt Elastic Cloud we are committed to offering our customers the most secure way to run their workloads in the cloud. With the goal of being “secure by default,” we are deprecating ciphers that are considered weak and insecure. Going forward, we will only support ciphers that are included in the \u003ca href=\"https://wiki.mozilla.org/Security/Server_Side_TLS#Intermediate_compatibility_.28recommended.29\"\u003eMozilla intermediate\u003c/a\u003e list. (edit: we are adding AES128-GCM-SHA256\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAES256-GCM-SHA384 to this list for Windows 11 compatibility).\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThis change is scheduled to take effect after Jan 30th 2022. If you only have deployments in Azure regions, this change does not affect you.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eWe will communicate a precise date closer to the change.\u003c/p\u003e\u003ch3\u003eWhat are the changes?\u003c/h3\u003e\u003cp\u003eWe are updating the list of ciphers supported for clients connecting to their Elasticsearch clusters, Kibana, or other components on Elasticsearch Service. The changes are basically on two fronts:\u003c/p\u003e\u003cul\u003e\u003cli aria-level=\"1\"\u003e\u003cem\u003eWe will deprecate certain ciphers that are considered weak by modern encryption standards. The ciphers we are going to stop supporting in all regions are:\u0026nbsp;\u003c/em\u003e\u003cul\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-ECDSA-AES128-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-AES128-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-ECDSA-AES256-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-AES256-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-DES-CBC3-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eAES128-SHA256\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eAES128-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eAES256-SHA1\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eDES-CBC3-SHA\u003c/em\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli aria-level=\"1\"\u003e\u003cem\u003eWe are \u003c/em\u003e\u003cem\u003e\u003cstrong\u003eonly\u003c/strong\u003e\u003c/em\u003e\u003cem\u003e going to support the ciphers that are included in the \u003c/em\u003e\u003ca href=\"https://wiki.mozilla.org/Security/Server_Side_TLS#Intermediate_compatibility_.28recommended.29\"\u003e\u003cem\u003eMozilla intermediate\u003c/em\u003e\u003c/a\u003e\u003cem\u003e list of ciphers and are considered a security best practice. In addition to the ciphers in the Mozilla intermediate list we have also added AES128-GCM-SHA256 and AES256-GCM-SHA384 (see list below) for Windows 11 compatibility. We will remove these at a later point of time.\u003c/em\u003e\u003cul\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-AES128-GCM-SHA256\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-ECDSA-AES256-GCM-SHA384\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-AES256-GCM-SHA384\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-ECDSA-CHACHA20-POLY1305\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-CHACHA20-POLY1305\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-AES-128-CBC-SHA\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-ECDSA-AES128-SHA256\u003c/em\u003e\u003c/li\u003e\u003cli aria-level=\"2\"\u003e\u003cem\u003eECDHE-RSA-AES128-SHA256\u003c/em\u003e\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"2\"\u003e\u003cem\u003eAES128-GCM-SHA256\u003c/em\u003e\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"2\"\u003e\u003cem\u003eAES256-GCM-SHA384\u003c/em\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cbr /\u003e\u003cli\u003e\u003cp\u003eEdit: We have added ECDHE-ECDSA-AES128-GCM-SHA256, AES128-GCM-SHA256 and AES256-GCM-SHA384 to the list of supported ciphers since the last update.\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cul\u003e\u003c/ul\u003e\u003c/ul\u003e\u003ch3\u003eWhat is the impact on me?\u003c/h3\u003e\u003cp\u003eIf you use clients that \u003cstrong\u003edo not\u003c/strong\u003e currently support at least one of the ciphers from the list of ciphers to be supported, you will need to update your clients to do so. This is important to be able to communicate with your cluster or any endpoints on Elastic Cloud (Kibana, APM Server, etc.) once the cipher list is updated.\u003c/p\u003e\u003ch3\u003eWhat should I do if I have clients that are using outdated ciphers?\u003c/h3\u003e\u003cp\u003eIf there are many teams at your organization using various clients, we recommend sending them a note on the upcoming changes encouraging them to update their clients. If you still don’t know what to do, reach out to \u003ca href=\"mailto:support@elastic.co\"\u003esupport@elastic.co\u003c/a\u003e.\u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003ch3 dir=\"ltr\"\u003eHow do I test which ciphers my clients support?\u0026nbsp;\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003eThese changes are already in effect in the following regions, you can test your clients by creating a small test deployment in any one of these regions. If your deployments are in one of these regions only, the changes don’t impact you.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003eAWS\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- af-south-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- ca-central-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- eu-north-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- eu-south-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- eu-west-3\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- me-south-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- ap-east-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- ap-south-1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- ap-northeast-2\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003eGCP\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- asia-east1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- asia-northeast1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- asia-northeast3\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- asia-southeast1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- australia-southeast1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- northamerica-northeast1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- southamerica-east1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- us-east1\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- us-east4\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: #24292e;background-color: transparent;font-weight: 400;font-style: normal;font-variant: normal;text-decoration: none;vertical-align: baseline;white-space: pre-wrap;\"\u003e- us-west2\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eWhat will happen if I do nothing?\u003c/h3\u003e\u003cp\u003eThe TLS handshake involves a client and a server negotiating a cipher supported by both parties. If you are running clients that support none of the ciphers that will be supported after the change, such clients will not be able to establish a connection with your Elasticsearch cluster or other Elastic Cloud endpoints (Kibana, APM Server, etc.), leading to downtime. \u003cstrong\u003eWe strongly recommend updating such clients.\u003c/strong\u003e\u0026nbsp;\u003c/p\u003e\u003cp\u003eAll ESS customers will be contacted by email about these changes, we will send regular email reminders and status page updates closer to the dates when the changes will roll out.\u003c/p\u003e","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2021-06-23T18:52:23.380Z","created_by":"bltd9bd8e1ce5969ea6","disclaimer":[],"full_bleed_image":{"_version":1,"is_dir":false,"uid":"blte1ff01b854421089","ACL":{},"content_type":"image/png","created_at":"2021-02-24T15:35:54.554Z","created_by":"bltf6ab93733e4e3a73","file_size":"57519","filename":"blog-banner-cloud-blue.png","parent_uid":null,"tags":[],"title":"blog-banner-cloud-blue.png","updated_at":"2021-02-24T15:35:54.554Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-24T15:36:06.706Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte1ff01b854421089/6036725a946aa93dbe5995e0/blog-banner-cloud-blue.png"},"markdown_l10n":"","publish_date":"2021-07-07T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Changes to support for ciphers used to connect to Elasticsearch Service","seo_description_l10n":"","noindex":false,"canonical_tag":""},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt231f19497aaf4242","ACL":{},"content_type":"image/png","created_at":"2021-02-24T15:35:54.852Z","created_by":"bltf6ab93733e4e3a73","file_size":"113075","filename":"blog-thumb-cloud-blue.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-blue.png","updated_at":"2022-02-11T21:03:14.508Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:40.632Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt231f19497aaf4242/6036725a259b2810197dbbf3/blog-thumb-cloud-blue.png"},"title":"Changes to support for ciphers used to connect to Elasticsearch Service","title_l10n":"Changes to support for ciphers used to connect to Elasticsearch Service","updated_at":"2025-03-10T11:53:03.411Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/notice-cipher-changes-ess","publish_details":{"time":"2025-03-10T11:53:07.267Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb2412645e995337e","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"Every ElasticON is packed with user stories, roadmaps, deep dives, and Q\u0026A with Elastic experts. Join us for the free, virtual event October 5-7 2021.","author":["blt9396b940ff8a6007"],"body_l10n":"\u003cp\u003eThis has been the year of solving: From rapid digital transformation emboldened by the hybrid workplace to substantial cybersecurity attacks disrupting infrastructure, solvers were ready at the front lines.\u003c/p\u003e\u003cp\u003eElastic has been the platform for solvers who are addressing exceptional challenges including: \u003ca href=\"https://www.elastic.co/blog/de-watergroep-and-devoteam-build-elastic-observability-pipeline-to-deliver-water-to-millions\"\u003edelivering water to 3 million customers\u003c/a\u003e, \u003ca href=\"https://www.elastic.co/customers/zurich-insurance-group\"\u003edriving insurance innovation\u003c/a\u003e, and \u003ca href=\"https://www.elastic.co/customers/emirates-nbd\"\u003esecuring billions in customer assets\u003c/a\u003e. And this year’s ElasticON Global 2021 theme, “Solve,” celebrates all of those working to solve the world’s most complex problems every day–from here on Earth, to the cloud, and even to \u003ca href=\"https://www.elastic.co/elasticon/global/agenda?solutionProduct=null\u0026type=null\u0026technicalLevel=null\u0026day=day-2\" target=\"_blank\"\u003eMars\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eJoin your fellow solvers at \u003ca href=\"https://events.elastic.co/elasticon/global/register\"\u003ethe virtual event\u003c/a\u003e. Whether you're new to the Elastic community or an ElasticON alumnus, we welcome you to learn more about how to turn data to action using our three solutions built on a single stack.\u0026nbsp;\u003c/p\u003e\u003cp\u003ePrepare for \u003ca href=\"https://www.elastic.co/elasticon/global/agenda?solutionProduct=null\u0026type=null\u0026technicalLevel=null\u0026day=day-3\u0026sol=null\u0026typ=null\u0026lev=null\"\u003ethree action-packed days\u003c/a\u003e with inspirational keynotes, product roadmaps and demos, customer success stories, and expert advice.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eDay 1\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eElastic Observability: Unified, actionable, frictionless\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eElastic Security: Limitless XDR. Unbounded security\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eElastic Enterprise Search: Solve with speed, scale, and relevance, out of the box\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/elasticon/global/agenda?solutionProduct=null\u0026type=null\u0026technicalLevel=null\u0026day=day-1 \"\u003eAnd more ...\u003c/a\u003e\u003cspan\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eDay 2\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eRethinking Observability with Elastic Machine Learning and statistics\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eGet the crawl rolling: Indexing with the Elastic web crawler\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eMicroservice choreography and triaging errors with Elastic Observability and the Elastic Stack\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/elasticon/global/agenda?solutionProduct=null\u0026type=null\u0026technicalLevel=null\u0026day=day-2 \" target=\"_blank\"\u003eAnd more ...\u003c/a\u003e\u003cspan\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eDay 3\u003c/strong\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eExploring Enterprise Search with Elastic on Microsoft Azure: A hands-on lab learning experience\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eCapture the Bug with Elastic Observability\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eCapture the Flag with Elastic Security\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003e\u003ca href=\"https://www.elastic.co/elasticon/global/agenda?solutionProduct=null\u0026type=null\u0026technicalLevel=null\u0026day=day-3 \" target=\"_blank\"\u003eAnd more ...\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eFrom keynotes to fireside chats, attendees are sure to be inspired.\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eConference highlights\u003c/h1\u003eWe’ve got\u0026nbsp; you covered — from \u003ca href=\"https://www.elastic.co/enterprise-search\"\u003eenterprise search\u003c/a\u003e to \u003ca href=\"https://www.elastic.co/observability\"\u003eincreased observability\u003c/a\u003e, or \u003ca href=\"https://www.elastic.co/security\"\u003etighter security\u003c/a\u003e to \u003ca href=\"https://www.elastic.co/cloud/\"\u003ecloud accessibility\u003c/a\u003e. Whatever you’re interested in learning about, we’ve curated a wealth of specific content designed to help you drive innovation and deliver more reliable solutions at scale.\u0026nbsp;\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eAn opening keynote from Elastic founder and CEO Shay Banon and chief product officer Ashutosh Kulkarni on the power of an open community and ecosystem, plus what innovations are on the horizon over the next year for the unified Elastic Search Platform.\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eA fireside chat with Microsoft EVP, Cloud + AI, Scott Guthrie, and Shay Banon focused on the companies’ joint commitment to cloud innovation and how they are helping organizations remove barriers to technology adoption and deliver greater value to customers.\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eA fireside chat with chef, culinary innovator, and founder of World Central Kitchen, José Andrés, who will speak about his mission to use the power of food to nourish communities and strengthen economies around the world during times of crisis and beyond.\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eA fireside chat with Diana Trujillo, flight director, and robotic arm system domain lead for the Mars Perseverance mission, who will speak about the hard work, dedication, and passion it took to realize her dream of becoming an aerospace engineer at NASA’s Jet Propulsion Laboratory.\u003cspan\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eYou’ll have access to more than \u003ca href=\"https://www.elastic.co/elasticon/global/speakers\"\u003e100 technical sessions\u003c/a\u003e offering key learnings and insights from Elastic customers, partners, and experts, including Adobe, General Motors, IBM, Microsoft, SAP, Twitter, and others.\u003cbr /\u003e\u003cbr /\u003eWe’ve even got a virtual exhibit hall where you can chat live with fellow participants, access exclusive promotions, and meet with ElasticON Global sponsors including presenting sponsor, Microsoft Azure, along with ClearQuery, Google Cloud, Novetta, Pure Storage, SVA System Vertrieb Alexander GmbH, Swimlane, and Teleport.\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eExcellence Awards\u003c/h1\u003e\u003cp\u003eThe Elastic Excellence Awards program will recognize philanthropic, innovative, and transformative projects and the people behind them. This year awards will be given in eight categories:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eCause Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eEnterprise Search Business Transformation Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eObservability Business Transformation Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eSecurity Business Transformation Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eSolve with Search Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eInnovation Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003ePublic Sector Award\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eCertified Professional of the Year\u003c/li\u003e\u003c/ul\u003e\u003ch1 dir=\"ltr\"\u003eSkills workshops and trainings\u0026nbsp;\u003c/h1\u003e\u003cp\u003eDevelop new skills through technical workshops and live, instructor-led training courses to help prepare you for certification exams. Participants can access discounted pricing for three Elastic courses: Elastic Observability Engineer, Elasticsearch Engineer, and Data Analysis with Kibana. Courses are offered multiple days and times, \u003ca href=\"https://www.elastic.co/elasticon/global/agenda?solutionProduct=null\u0026type=null\u0026technicalLevel=null\u0026day=day-0\"\u003eso find the best spot for you\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eSolve with us\u003c/h1\u003e\u003cp\u003eWe hope to see you there and if you still have questions, learn more about \u003ca href=\"https://www.elastic.co/elasticon/global/why-attend\"\u003ewhat ElasticON Global can do for you\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eBuilding on past philanthropic efforts, Elastic will make a donation to World Central Kitchen and Girlstart on behalf of every person participating in ElasticON Global. Additional donation opportunities will be made available to attendees during the event.\u003c/p\u003e\u003ca href=\"https://events.elastic.co/elasticon/global/register\"\u003eRegister to join us\u003c/a\u003e! Level-up your skills and inspire innovation with some of the world’s leading solvers.","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2021-09-21T20:30:24.370Z","created_by":"blt1e57c6588ae1816e","disclaimer":[],"full_bleed_image":{"uid":"blta1cbddeb4726a1df","ACL":{},"_version":1,"content_type":"image/png","created_at":"2021-01-12T16:26:17.549Z","created_by":"bltf6ab93733e4e3a73","file_size":"77773","filename":"blog-banner-megaphone-logo.png","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-12T16:26:00.903Z","user":"bltf6ab93733e4e3a73"},"tags":[],"title":"blog-banner-megaphone-logo.png","updated_at":"2021-01-12T16:26:17.549Z","updated_by":"bltf6ab93733e4e3a73","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta1cbddeb4726a1df/5ffdcda9e4028c63a64d9380/blog-banner-megaphone-logo.png"},"markdown_l10n":"","publish_date":"2021-09-22T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Join us at ElasticON Global: Elastic’s free, virtual user conference October 5-7","seo_description_l10n":"Every ElasticON is packed with user stories, roadmaps, deep dives, and Q\u0026A with Elastic experts. Join us for the free, virtual event October 5-7 2021.","noindex":false,"canonical_tag":""},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt05b074fc2dd9b6f2","ACL":{},"content_type":"image/png","created_at":"2021-01-12T16:26:17.534Z","created_by":"bltf6ab93733e4e3a73","file_size":"53698","filename":"blog-thumb-megaphone-logo.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-megaphone-logo.png","updated_at":"2022-02-11T21:04:12.027Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:03.242Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt05b074fc2dd9b6f2/5ffdcda97f3df4662710b21b/blog-thumb-megaphone-logo.png"},"title":"Join us at ElasticON Global: Elastic’s free, virtual user conference October 5-7","title_l10n":"Join us at ElasticON Global: Elastic’s free, virtual user conference October 5-7","updated_at":"2025-03-10T11:51:52.995Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/join-us-at-elasticon-global-elastics-free-virtual-user-conference-October-5-7","publish_details":{"time":"2025-03-10T11:51:57.509Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd1501b9c0a3fc477","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["bltcf0a69ce766b1421"],"body_l10n":"\u003cp\u003eEver want to search your database entities from Elasticsearch?\u0026nbsp;Now you can use Logstash\u0026nbsp;to do just that!\u0026nbsp;In this blog we introduce the \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-jdbc.html\"\u003eJDBC input\u003c/a\u003e, which has been created to import data from any database that supports the JDBC interface. Below, we show you few examples of using this plugin.\u003c/p\u003e\u003ch2\u003eGetting Started\u003c/h2\u003e\u003ch3\u003eInstallation\u003c/h3\u003e\u003cpre class=\"prettyprint\"\u003ebin/plugin install logstash-input-jdbc\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003e\u003cbr /\u003e\u003c/h3\u003e\u003ch3\u003eDriver Support\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.8327272415161155;margin-top: 0pt;margin-bottom: 11pt;\"\u003ePopular databases like Oracle, Postgresql, and MySQL have compatible JDBC drivers that can be used with this input. This plugin does not come packaged with any of these JDBC drivers out of the box, but is straightforward to download. You can then configure the plugin to use the desired jdbc driver library. The setting jdbc_driver_library and jdbc_driver_class are used to load the library path and the driver's class name.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.8327272415161155;margin-top: 0pt;margin-bottom: 11pt;\" rel=\"line-height:1.8327272415161155;margin-top:0pt;margin-bottom:11pt;\"\u003eLets get started with the examples!\u003c/p\u003e\u003ch2\u003eExample 1: Simple Postgres Input\u003c/h2\u003e\u003cp\u003eHere is an example of how you get started reading from a local \u003ca href=\"http://postgresql.org\"\u003ePostgresql\u003c/a\u003e\u0026nbsp;database. As a prerequisite,\u0026nbsp;\u003ca href=\"https://jdbc.postgresql.org/download.html\"\u003edownload\u003c/a\u003e\u0026nbsp;the Postgresql JDBC drivers to use with the plugin.\u003c/p\u003e\u003ch3\u003eSetting Up The\u0026nbsp;Database\u003c/h3\u003e\u003cp\u003eBefore we get started, let's create a table called contacts and populate it with some contacts!\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ecreate table contacts (\u003cbr /\u003e\u0026lt;p\u0026gt;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;uid serial,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;email VARCHAR(80) not null,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;first_name VARCHAR(80) NOT NULL,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;last_name VARCHAR(80) NOT NULL\u003cbr /\u003e);\u003cbr /\u003eINSERT INTO contacts(email, first_name, last_name) VALUES('jim@example.com', 'Jim', 'Smith');\u003cbr /\u003eINSERT INTO contacts(email, first_name, last_name) VALUES(null, 'John', 'Smith');\u003cbr /\u003eINSERT INTO contacts(email, first_name, last_name) VALUES('carol@example.com', 'Carol', 'Smith');\u003cbr /\u003eINSERT INTO contacts(email, first_name, last_name) VALUES('sam@example.com', 'Sam', null);\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAfter this runs, here are the contents in the database in table form.\u003c/p\u003e\u003ctable\u003e\u003cthead\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003eEmail \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eFirst Name \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eLast Name \u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/thead\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003enull \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJohn \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSmith \u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003ecarol@example.com \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eCarol \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSmith \u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003esam@example.com \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSam \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSmith \u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003ejim@example.com \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJim \u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSmith\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003ch3\u003eLogstash Configuration\u003c/h3\u003e\u003cp\u003eWe can go ahead and output all these events to the console with this sample\u0026nbsp;Logstash\u0026nbsp;configuration:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e# file: simple-out.conf\u003cbr /\u003einput {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;# Postgres jdbc connection string to our database, mydb\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_connection_string =\u0026gt; \"jdbc:postgresql://localhost:5432/mydb\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;# The user we wish to execute our statement as\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_user =\u0026gt; \"postgres\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;# The path to our downloaded jdbc driver\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_driver_library =\u0026gt; \"/path/to/postgresql-9.4-1201.jdbc41.jar\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;# The name of the driver class for Postgresql\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_driver_class =\u0026gt; \"org.postgresql.Driver\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;# our query\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;statement =\u0026gt; \"SELECT * from contacts\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;}\u003cbr /\u003e}\u003cbr /\u003eoutput {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;stdout { codec =\u0026gt; json_lines }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNow we can run Logstash and see the results!\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p style=\"line-height: 22.3999996185303px; color: rgb(57, 57, 57); font-family: Arial, Helvetica, Verdana, Tahoma, sans-serif; white-space: normal;\"\u0026gt;$\u0026nbsp;logstash-1.5.3/bin/logstash -f simple-out.conf\u0026nbsp;\u0026lt;/p\u0026gt;\u0026lt;p style=\"line-height: 22.3999996185303px; color: rgb(57, 57, 57); font-family: Arial, Helvetica, Verdana, Tahoma, sans-serif; white-space: normal;\"\u0026gt;Logstash startup completed\u0026lt;/p\u0026gt;\u0026lt;p style=\"line-height: 22.3999996185303px; color: rgb(57, 57, 57); font-family: Arial, Helvetica, Verdana, Tahoma, sans-serif; white-space: normal;\"\u0026gt;{\"uid\":1,\"email\":null,\"first_name\":\"hello\",\"last_name\":null,\"@version\":\"1\",\"@timestamp\":\"2015-07-29T21:03:18.958Z\"}\u003cbr /\u003e{\"uid\":2,\"email\":\"jim@example.com\",\"first_name\":\"Jim\",\"last_name\":\"Smith\",\"@version\":\"1\",\"@timestamp\":\"2015-07-29T21:03:18.959Z\"}\u003cbr /\u003e{\"uid\":3,\"email\":null,\"first_name\":\"John\",\"last_name\":\"Smith\",\"@version\":\"1\",\"@timestamp\":\"2015-07-29T21:03:18.959Z\"}\u003cbr /\u003e{\"uid\":4,\"email\":\"carol@example.com\",\"first_name\":\"Carol\",\"last_name\":\"Smith\",\"@version\":\"1\",\"@timestamp\":\"2015-07-29T21:03:18.959Z\"}\u003cbr /\u003e{\"uid\":5,\"email\":\"sam@example.com\",\"first_name\":\"Sam\",\"last_name\":null,\"@version\":\"1\",\"@timestamp\":\"2015-07-29T21:03:18.961Z\"}\u0026lt;/p\u0026gt;\u0026lt;p style=\"line-height: 22.3999996185303px; color: rgb(57, 57, 57); font-family: Arial, Helvetica, Verdana, Tahoma, sans-serif; white-space: normal;\"\u0026gt;Logstash shutdown completed\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAwesome, we read data from Postgresql!\u003c/p\u003e\u003cp\u003eUp next,\u0026nbsp;we will demonstrate two examples of how you may use this plugin in the context of Elasticsearch.\u003c/p\u003e\u003ch3\u003eExample 2:\u0026nbsp;Synchronizing Data In Your Table To Elasticsearch\u003c/h3\u003e\u003cp\u003eIn the case that we are using our database as an input source for Elasticsearch, we may\u0026nbsp;be interested in keeping our existing documents\u0026nbsp;in-sync with our data as the database undergoes updates.\u0026nbsp;In this case, we can simply index our rows in Elasticsearch with unique ids such that any\u0026nbsp;time we re-index them, they will just update. This way, we prevent Elasticsearch from assigning\u0026nbsp;a new ID for each record and generating duplicates!\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p\u0026gt;# file: contacts-index-logstash.conf\u003cbr /\u003einput {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_connection_string =\u0026gt; \"jdbc:postgresql://localhost:5432/mydb\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_user =\u0026gt; \"postgres\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_validate_connection =\u0026gt; true\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_driver_library =\u0026gt; \"/path/to/postgresql-9.4-1201.jdbc41.jar\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_driver_class =\u0026gt; \"org.postgresql.Driver\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;statement =\u0026gt; \"SELECT * from contacts\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;}\u003cbr /\u003e}\u003cbr /\u003eoutput {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;elasticsearch {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;protocol =\u0026gt; http\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;index =\u0026gt; \"contacts\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;document_type =\u0026gt; \"contact\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;document_id =\u0026gt; \"%{uid}\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;host =\u0026gt; \"ES_NODE_HOST\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;}\u003cbr /\u003e}\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eLet's do a quick check to see that \"Sam\" was indexed into Elasticsearch\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p\u0026gt;curl ES_NODE_HOST:9200/contacts/contact/5?pretty\u003cbr /\u003e{\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_index\" : \"contacts\",\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_type\" : \"contact\",\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_id\" : \"5\",\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_version\" : 1,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"found\" : true,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_source\":{\"uid\":5,\"email\":\"sam@example.com\",\"first_name\":\"Sam\",\"last_name\":null,\"@version\":\"1\",\"@timestamp\":\"2015-07-29T22:12:20.146Z\"}\u003cbr /\u003e}\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eSo far we just saw how to use a query to fetch results from a database query, but what if\u0026nbsp;we want to update our index with new changes? What if some of our contacts changed emails,\u0026nbsp;or we want to update someone's last name? Here is a sequence of changes that we can apply to\u0026nbsp;our table and later verify the behavior we want in the resulting Elasticsearch index.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p\u0026gt;UPDATE contacts SET last_name = 'Smith' WHERE email = 'sam@example.com';\u003cbr /\u003eUPDATE contacts SET email = 'john@example.com' WHERE uid = 3;\u003cbr /\u003eINSERT INTO contacts(email, first_name, last_name) VALUES('new@example.com', 'New', 'Smith');\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eNow we can run Logstash with the same configuration. When we do the same query as before, we will\u0026nbsp;\u003c/p\u003e\u003cp\u003enotice that our document containing Sam has been updated and @version is now 2\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p\u0026gt;curl ES_NODE_HOST:9200/contacts/contact/5?pretty\u003cbr /\u003e{\u0026lt;/p\u0026gt;\u0026lt;p\u0026gt;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_index\" : \"contacts\",\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_type\" : \"contact\",\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_id\" : \"5\",\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_version\" : 2,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"found\" : true,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"_source\":{\"uid\":5,\"email\":\"sam@example.com\",\"first_name\":\"Sam\",\"last_name\":\"Smith\",\"@version\":\"1\",\"@timestamp\":\"2015-07-29T22:12:56.980Z\"}\u003cbr /\u003e}\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eUsing this method, we can re-index our table into Elasticsearch without ending up with duplicates. One thing to note is that we are not able to capture deletes to documents under this scheme.\u003c/p\u003e\u003ch2\u003eExample 3: MusicBrainz Demo\u003c/h2\u003e\u003cp\u003e\u003ca href=\"http://musicbrainz.org\"\u003eMusicBrainz\u003c/a\u003e is an open music database containing up-to-date information\u0026nbsp;about artists, their works, and everything in-between. You can learn\u0026nbsp;more at\u0026nbsp;\u003ca href=\"http://musicbrainz.org\"\u003ehttp://musicbrainz.org\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eMusicBrainz graciously\u0026nbsp;hosts a biweekly\u0026nbsp;data dump of their database \u003ca href=\"http://ftp.musicbrainz.org/pub/musicbrainz/data/fullexport/\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003eThis data is\u0026nbsp;1.8GB with information about\u0026nbsp;around 18\u0026nbsp;million tracks\u003c/p\u003e\u003ch3\u003eHow to get the MusicBrainz data\u003c/h3\u003e\u003cp\u003eYou must first run your own mirror of the MusicBrainz database. This can\u0026nbsp;be achieved using a tool called \u003ca href=\"https://bitbucket.org/lalinsky/mbslave\"\u003embslave\u003c/a\u003e. The project's repo has instructions on syncing with the data-dump.\u003c/p\u003e\u003ch3\u003eFormulating a query to load\u003c/h3\u003e\u003cp\u003eNow that we have all of this wealth of music data in an accessible database, we can choose a subset of the data we wish to index into Elasticsearch.\u0026nbsp;We may be interested in exploring the data about artists and their releases. Here is a\u0026nbsp;SQL query to fetch a few attributes belonging to artists and their releases:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p\u0026gt;SELECT\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release_group.gid AS album_id,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release_group.type AS album_primary_type_id,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release_group_primary_type.name AS album_primary_type_name,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release.name AS release_name,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;artist.name AS artist_name,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;artist.gid AS artist_gid,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;artist_credit.id AS artist_credit_id,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;artist.type AS artist_type_id,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;artist_type.name AS artist_type_name,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;artist.begin_date_year artist_begin_date_year,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;area.name AS artist_country_name,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release_country.date_year AS release_year,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release_country.date_month AS release_month,\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;release_country.date_day AS release_day\u003cbr /\u003eFROM\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;musicbrainz.artist\u003cbr /\u003eINNER JOIN musicbrainz.artist_credit_name\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON artist_credit_name.artist = artist.id\u003cbr /\u003eINNER JOIN musicbrainz.artist_credit\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON artist_credit.id = artist_credit_name.artist_credit\u003cbr /\u003eINNER JOIN musicbrainz.release_group\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON release_group.artist_credit = artist_credit.id\u003cbr /\u003e\u0026lt;span\u0026gt;\u0026lt;/span\u0026gt;INNER JOIN musicbrainz.release\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON release.release_group = release_group.id\u003cbr /\u003eINNER JOIN musicbrainz.release_country\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON release.id = release_country.release\u003cbr /\u003eINNER JOIN musicbrainz.artist_type\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON artist.type = artist_type.id\u003cbr /\u003eINNER JOIN musicbrainz.area\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON artist.area = area.id\u003cbr /\u003eINNER JOIN musicbrainz.release_group_primary_type\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;ON release_group_primary_type.id = release_group.type\u003cbr /\u003e\u0026lt;span\u0026gt;\u0026lt;/span\u0026gt;WHERE\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;((release_country.date_year IS NOT NULL) AND\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;(release_country.date_month IS NOT NULL) AND\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;(release_country.date_day IS NOT NULL))\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eUsing Logstash to Query The Database and Index Into Elasticsearch\u003cspan\u003e\u003c/span\u003e\u003c/h3\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;p\u0026gt;input {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_driver_library =\u0026gt; \"/path/to/driver.jar\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_driver_class =\u0026gt; \"org.postgresql.Driver\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_url =\u0026gt; \"jdbc://postgresql\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;jdbc_user =\u0026gt; \"musicbrainz\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;statement_filepath =\u0026gt; \"query.sql\"\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;}\u003cbr /\u003e}\u0026lt;/p\u0026gt;\u0026lt;p\u0026gt;output {\u003cbr /\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;elasticsearch { protocol =\u0026gt; http }\u0026lt;/p\u0026gt;\u0026lt;p\u0026gt;}\u0026lt;/p\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eIn this case, we have such a complex query that we chose to leverage the\u0026nbsp;statement_filepath parameter option.\u0026nbsp;\u003c/p\u003e\u003ch3\u003eExploring Data in Kibana\u003c/h3\u003e\u003cp\u003eOne great feature of migrating a part of the data into Elasticsearch is the ability to generate great insightful visualizations using Kibana. For starters, let's see how many musical releases are introduced year over year!\u003c/p\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c9512798d8e381fd7c7/download?uid=blt34ee9177b75fa356?uid=blt34ee9177b75fa356\" data-sys-asset-uid=\"blt246e03b110fd12f5\" width=\"572\" height=\"431\" style=\"width: 572;height: 431;\"/\u003e\u003c/p\u003e\u003cp style=\"text-align: center;\"\u003e(image:\u0026nbsp;Number of releases per year from 1900 to 2010)\u003c/p\u003e\u003cp\u003eSeeing general counts is a nice starter, but we can explore much more! For example, these releases have artists, countries, and release types associated with them. In the following Kibana dashboard we can see the 20 artists with the most number of releases associated to them. We can also visualize the differences between album, EP, and singles releases across the various producing countries.\u003c/p\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c950342dfd738263266/download?uid=blt736a3d8684d25830?uid=blt736a3d8684d25830\" data-sys-asset-uid=\"blt6c481a1036436dc9\" width=\"562\" height=\"327\" style=\"width: 562;height: 327;\"/\u003e\u003c/p\u003e\u003cp\u003eWe can drill\u0026nbsp;into our donut visualization and filter for\u0026nbsp;EPs that were produced by artists from the United Kingdom.\u003cbr /\u003e\u003c/p\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c9558208ba076e281b6/download?uid=blt56470000d74aa90f?uid=blt56470000d74aa90f\" data-sys-asset-uid=\"blt66b13a43b0cd13f9\" width=\"611\" height=\"336\" style=\"width: 611;height: 336;\"/\u003e\u003c/p\u003e\u003cp\u003eYou may recognize some of these artists, while others may be new to you. Musicbrainz collects data about so many artists, there is always something new to discover!\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eMore Information\u003c/h2\u003e\u003cp\u003eThis post only begins to explore the integrations and features the JDBC plugin includes. For more information, check out the\u0026nbsp;plugin's \u003ca href=\"https://www.elastic.co/guide/en/logstash/current/plugins-inputs-jdbc.html\"\u003edocumentation\u003c/a\u003e. We would love your feedback on our \u003ca href=\"https://discuss.elastic.co/c/logstash\"\u003eforum\u003c/a\u003e; if you think you’ve found a bug in this plugin, please submit an \u003ca href=\"https://github.com/logstash-plugins/logstash-input-jdbc/issues\"\u003eissue\u003c/a\u003e.\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T12:42:07.657Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt2ff68c6d90c2b030","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:04:26.332Z","updated_at":"2018-10-09T10:04:26.332Z","content_type":"image/jpeg","file_size":"18637","filename":"insert-into-logstash-jdbc-input-plugin-database-full-bleed.jpg","title":"insert-into-logstash-jdbc-input-plugin-database-full-bleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-07T05:49:55.472Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2ff68c6d90c2b030/5bbc7d2a20bcc78f36235c29/insert-into-logstash-jdbc-input-plugin-database-full-bleed.jpg"},"markdown_l10n":"","publish_date":"2015-08-03T08:10:10.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltae953c1ebbd1cada","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:03:50.268Z","updated_at":"2018-10-09T10:03:50.268Z","content_type":"image/png","file_size":"80299","filename":"insert-into-logstash-jdbc-input-plugin-database-thumbnail.png","title":"insert-into-logstash-jdbc-input-plugin-database-thumbnail.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-07T05:49:55.472Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltae953c1ebbd1cada/5bbc7d06becc14715d488b9a/insert-into-logstash-jdbc-input-plugin-database-thumbnail.png"},"title":"INSERT INTO LOGSTASH SELECT DATA FROM DATABASE","title_l10n":"INSERT INTO LOGSTASH SELECT DATA FROM DATABASE","updated_at":"2025-03-10T11:50:05.036Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/logstash-jdbc-input-plugin","publish_details":{"time":"2025-03-10T11:50:08.800Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt931f5da4602bc388","_version":22,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security has been updated and our users are not affected by SolarWinds’ recent security advisory regarding a supply-chain attack on the Orion management platform. Identify potential attacks using new and existing rules in this post.","author":["bltb5fbc25dec714531"],"body_l10n":"\u003ch2\u003eExecutive summary\u003c/h2\u003e\u003cul\u003e\u003cli\u003eElastic Security’s malware prevention technology, used by both Elastic Endgame and the endpoint security capabilities within Elastic Security, has been updated and is not affected by attacks described in this disclosure\u003c/li\u003e\u003cli\u003eExisting Elastic Security rules (listed below) can help identify potential attacks\u003c/li\u003e\u003cli\u003eNew Elastic Security rules (listed below) can help detect new threats\u003c/li\u003e\u003cli\u003eRecommended searches/threat hunts are listed below for Elastic Security (Elastic Endgame recommendations can be found on our \u003ca href=\"https://support.elastic.co/customers/s/login/\"\u003esupport portal\u003c/a\u003e)\u003c/li\u003e\u003cli\u003eUsers can leverage\u0026nbsp;Elastic ML models to detect potential C2 from the SUNBURST attack\u003c/li\u003e\u003cli\u003eUsers are invited to work directly with our protection engineers in our \u003ca href=\"https://github.com/elastic/detection-rules\"\u003epublic rules repo\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eBackground\u003c/h2\u003e\u003cp\u003eOn December 13, \u003ca href=\"https://www.solarwinds.com/securityadvisory\"\u003eSolarWinds released a security advisory\u003c/a\u003e\u0026nbsp;regarding a successful supply-chain attack on the Orion management platform. The attack affects Orion versions 2019.4 HF 5 through 2020.2.1, software products released between March and June of 2020. Likewise, on December 13, \u003ca href=\"https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html\"\u003eFireEye released information about a global campaign involving SolarWinds supply-chain compromise\u003c/a\u003e that affected some versions of Orion software.\u003c/p\u003e\u003cp\u003eMany details of the intrusion have not been made public, and this content may be later updated as additional information becomes known. Elastic provides this information for users in the free tier, and recommends subscription customers refer to the \u003ca href=\"https://support.elastic.co/customers/s/login/\"\u003esupport portal\u003c/a\u003e for additional information about licensed features.\u003c/p\u003e\u003ch2\u003eMalware protection\u003c/h2\u003e\u003cp\u003eWe have updated our MalwareScore protection, used by both Elastic Endgame and Elastic Security. This update includes blocklist entries for known bad file hashes, providing essential prevention capability to mitigate deployed SolarWinds client software containing malicious code. Users should receive this update automatically.\u003c/p\u003e\u003ch2\u003eFree and open behavioral detections\u003c/h2\u003e\u003cp\u003eWe have reviewed public materials disclosed by SolarWinds and FireEye to ensure we have as up-to-date an understanding of tactics, techniques, and procedures (TTPs) as possible. Additionally, Elastic reviewed \u003ca href=\"https://www.volexity.com/blog/2020/12/14/dark-halo-leverages-solarwinds-compromise-to-breach-organizations/\"\u003econtent published by Volexity\u003c/a\u003e\u0026nbsp;describing post-exploitation activities observed during professional services engagements. While information about how the adversary responsible has leveraged this supply-chain compromise is limited, materials published by FireEye and Volexity indicate attempts to obtain lasting operational control by targeting directory services and other forms of authentication with a particular emphasis on information access.\u003c/p\u003e\u003cp\u003eThe following existing behavioral detections for the Elastic Security solution may identify evidence of successful post-exploitation:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/rules/azure/persistence_user_added_as_owner_for_azure_service_principal.toml\"\u003eUser Added as Owner for Azure Service Principal\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/rules/azure/persistence_mfa_disabled_for_azure_user.toml\"\u003eMulti-Factor Authentication Disabled for an Azure User\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/86b1a56c1bfb42da504923e70bef788177967985/rules/microsoft-365/credential_access_microsoft_365_brute_force_user_account_attempt.toml\"\u003eAttempts to Brute Force a Microsoft 365 User Account\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/73e2690ec0683c3b77d54458da56c5d8b1c41092/rules/microsoft-365/credential_access_microsoft_365_potential_password_spraying_attack.toml\"\u003ePotential Password Spraying of Microsoft 365 User Accounts\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/rules/azure/initial_access_consent_grant_attack_via_azure_registered_application.toml\"\u003ePossible Consent Grant Attack via Azure-Registered Application\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/rules/azure/credential_access_key_vault_modified.toml\"\u003eAzure Key Vault Modified\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/538aa80bba56535bb32eaab6cad9ef44d959ea30/rules/windows/defense_evasion_process_termination_followed_by_deletion.toml\"\u003eProcess Termination followed by Deletion\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/e6645a8be9f70397b096928f28c49899d69adf04/rules/windows/defense_evasion_clearing_windows_event_logs.toml\"\u003eClearing Windows Event Logs\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAdditionally, new behavioral rules are being released for the following activities:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/3b583cebade7de127f90dcbb7a93b9e083048b3c/rules/windows/collection_email_powershell_exchange_mailbox.toml\"\u003eExporting Exchange MailBox via PowerShell\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/3b583cebade7de127f90dcbb7a93b9e083048b3c/rules/windows/defense_evasion_solarwinds_backdoor_service_disabled_via_registry.toml\"\u003eSolarWinds Process Disabling Services via Registry\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/3b583cebade7de127f90dcbb7a93b9e083048b3c/rules/windows/execution_apt_solarwinds_backdoor_child_cmd_powershell.toml\"\u003eCommand Execution via SolarWinds Process\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/3b583cebade7de127f90dcbb7a93b9e083048b3c/rules/windows/execution_apt_solarwinds_backdoor_unusual_child_processes.toml\"\u003eSuspicious SolarWinds Child Process\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/7.11/rules/azure/initial_access_azure_active_directory_powershell_signin.toml\"\u003eAzure Active Directory PowerShell Sign-in\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/7.11/rules/azure/defense_evasion_azure_service_principal_addition.toml\"\u003eAzure Service Principal Addition\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/5e8b86a84eb9d5291ae64ec440254ca3ae274808/rules/windows/command_and_control_sunburst_c2_activity_detected.toml\"\u003eSUNBURST Command and Control Activity Detected\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/7.11/rules/azure/defense_evasion_azure_application_credential_modification.toml\"\u003eAzure Application Credential Modification\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/rules/windows/execution_scheduled_task_powershell_source.toml\"\u003eOutbound Scheduled Task Activity via PowerShell\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eElastic Security users may find value in enabling additional \u003ca href=\"https://github.com/elastic/detection-rules\"\u003edetection-rules\u003c/a\u003e in \u003cem\u003eall\u003c/em\u003e categories, prioritizing triage and analysis of results related to SolarWinds client software.\u003c/p\u003e\u003cp\u003eUsers should note that the detection-rules command-line interface (\u003ca href=\"https://github.com/elastic/detection-rules/blob/main/CLI.md\"\u003eCLI\u003c/a\u003e) is required to import rules, and the import-rules function can import rules in several formats either individually or from a directory.\u003c/p\u003e\u003ch2\u003eThreat hunting using Elastic\u003c/h2\u003e\u003cp\u003eUsers who have deployed the Elastic endpoint may find that hunts focused on the following are important leads to prioritize based on public reporting:\u003c/p\u003e\u003ch3\u003eDisabling services via the Windows registry\u003c/h3\u003e\u003ch4\u003eEQL\u003c/h4\u003e\u003cpre\u003eregistry where registry.path : \"HKLM\\\\SYSTEM\\\\*ControlSet*\\\\Services\\\\*\\\\Start\" and registry.data.strings == \"4\" and not (process.name : \"services.exe\" and user.domain: \"NT AUTHORITY\")\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eKQL\u003c/h4\u003e\u003cpre\u003eregistry.path:HKLM\\\\System\\\\*ControlSet*\\\\Services\\\\*\\\\Start and registry.data.strings:\"4\" and not (process.name:\"services.exe\" and user.domain:\"NT AUTHORITY\")\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eUnusual descendants of the SolarWinds client\u003c/h3\u003e\u003ch4\u003eEQL\u003c/h4\u003e\u003cpre\u003eprocess where event.type in (\"start\",\"process_started\") and process.parent.name:(\"SolarWinds.BusinessLayerHost.exe\",\"SolarWinds.BusinessLayerHostx64.exe\")\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eKQL\u003c/h4\u003e\u003cpre\u003eevent.category:process and event.type:start and process.parent.name:(\"SolarWinds.BusinessLayerHost.exe\" or \"SolarWinds.BusinessLayerHostx64.exe\")\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eCreation of executable files by the SolarWinds client\u003c/h3\u003e\u003ch4\u003eEQL\u003c/h4\u003e\u003cpre\u003efile where process.name in (\"SolarWinds.BusinessLayerHost.exe\", \"SolarWinds.BusinessLayerHostx64.exe\") and file.name : (\"*.dll*\", \"*.exe*\", \"*.ps1*\", \"*.jpg*\", \"*.png*\")\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eKQL\u003c/h4\u003e\u003cpre\u003eevent.category:file and event.type:creation and file.extension:(dll or DLL or exe or EXE or ps1 or PS1 or jpg or JPG or png or PNG) and process.name:(\"SolarWinds.BusinessLayerHost.exe\" or \"SolarWinds.BusinessLayerHostx64.exe\")\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eUnexpected network communications by the SolarWinds client\u003c/h3\u003e\u003ch4\u003eEQL\u003c/h4\u003e\u003cpre\u003enetwork where network.protocol == \"http\" and process.name: (\"SolarWinds.BusinessLayerHostx64.exe\", \"ConfigurationWizard.exe\", \"NetflowDatabaseMaintenance.exe\", \"NetFlowService.exe\", \"SolarWinds.Administration.exe\", \"SolarWinds.BusinessLayerHost.exe\", \"SolarWinds.Collector.Service.exe\" , \"SolarwindsDiagnostics.exe\") and wildcard(http.request.body.content, \"POST*/swip/Upload.ashx*\", \"PUT*/swip/Upload.ashx*\", \"GET*/swip/SystemDescription*\", \"HEAD*/swip/SystemDescription*\", \"GET*/swip/Events*\", \"HEAD*/swip/Events*\") and not wildcard(http.request.body.content, \"POST*solarwinds.com*\", \"PUT*solarwinds.com*\", \"GET*solarwinds.com*\", \"HEAD*solarwinds.com*\")\u003cbr /\u003e\u003c/pre\u003e\u003ch4\u003eKQL\u003c/h4\u003e\u003cpre\u003eevent.category:network and event.type:protocol and network.protocol:http and process.name:(ConfigurationWizard.exe or NetFlowService.exe or NetflowDatabaseMaintenance.exe or SolarWinds.Administration.exe or SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe or SolarWinds.Collector.Service.exe or SolarwindsDiagnostics.exe) and http.request.body.content:(((*/swip/Upload.ashx* and (POST* or PUT*)) or (*/swip/SystemDescription* and (GET* or HEAD*)) or (*/swip/Events* and (GET* or HEAD*))) and not *solarwinds.com*)\u003cbr /\u003e\u003c/pre\u003e\u003ch2\u003eFor our users leveraging machine learning\u003c/h2\u003e\u003cp\u003eMachine learning is a critical capability when tracking down and detecting unknown threats. Elastic Security ships prebuilt jobs and rules that can jumpstart security teams across any organization. In this case, SUNBURST detection was not the exception. In \u003ca href=\"https://www.elastic.co/blog/supervised-and-unsupervised-machine-learning-for-dga-detection\"\u003ethis blog\u003c/a\u003e, Elastic users can find step-by-step instructions to leverage one of the latest additions to our fleet: a model that combines supervised and unsupervised learning for effectively detect Domain Generation Algorithm (DGA) activity in organizations.\u003c/p\u003e\u003ch2\u003eNext steps\u003c/h2\u003e\u003cp\u003eElastic will update our malware protection signer allowlist to remove an allowlist entry for SolarWinds Worldwide, LLC. As a result, SolarWinds users may see malware alerts for software signed by SolarWinds. These may be false positives.\u003c/p\u003e\u003cp\u003eElastic Security's researchers are monitoring this situation for any updates. As new information emerges, we will evaluate and create additional protections as needed.\u003c/p\u003e\u003cp\u003eElastic recommends users follow all applicable guidance from SolarWinds in addition to the guidance provided in this document. Users of SolarWinds products should also review reference materials for associated network-based indicators and conduct searches to identify potential evidence of prior or ongoing compromise. Elastic users can easily search for atomic indicators without learning a new query language.\u003c/p\u003e","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2020-12-15T17:54:09.183Z","created_by":"bltc87e8bcd2aefc255","disclaimer":["bltc28183b66ccd29e9"],"full_bleed_image":{"uid":"bltdee39bad4d3c7965","ACL":{},"_version":1,"content_type":"image/jpeg","created_at":"2020-12-15T21:34:00.574Z","created_by":"bltf6ab93733e4e3a73","file_size":"145965","filename":"blog-banner-digital-red-shield.jpg","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-15T21:34:07.114Z","user":"bltf6ab93733e4e3a73"},"tags":[],"title":"blog-banner-digital-red-shield.jpg","updated_at":"2020-12-15T21:34:00.574Z","updated_by":"bltf6ab93733e4e3a73","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdee39bad4d3c7965/5fd92bc869cce544cffa72f0/blog-banner-digital-red-shield.jpg"},"markdown_l10n":"","publish_date":"2020-12-15T22:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Security provides free and open protections for SUNBURST","seo_description_l10n":"Elastic Security has been updated and our users are not affected by SolarWinds’ recent security advisory regarding a supply-chain attack on the Orion management platform. Identify potential attacks using new and existing rules in this post.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt58039093428c8670","ACL":{},"_version":1,"content_type":"image/jpeg","created_at":"2020-12-15T21:33:59.500Z","created_by":"bltf6ab93733e4e3a73","file_size":"191083","filename":"blog-thumb-digital-red-shield.jpg","is_dir":false,"parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-15T21:34:07.129Z","user":"bltf6ab93733e4e3a73"},"tags":[],"title":"blog-thumb-digital-red-shield.jpg","updated_at":"2020-12-15T21:33:59.500Z","updated_by":"bltf6ab93733e4e3a73","url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt58039093428c8670/5fd92bc77c43e43bf41983af/blog-thumb-digital-red-shield.jpg"},"title":"Elastic Security provides free and open protections for SUNBURST","title_l10n":"Elastic Security provides free and open protections for SUNBURST","updated_at":"2025-03-10T11:49:02.298Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-security-provides-free-and-open-protections-for-sunburst","publish_details":{"time":"2025-03-10T11:49:05.847Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte3b1bc93c2634e11","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt494a7006515ea7c6"],"body_l10n":"\u003cp\u003eThe Elasticsearch engineering team is busy working on features for Elasticsearch 6.0. One of the changes that is coming in Elasticsearch 6.0 is \u003cem\u003estrict content-type checking\u003c/em\u003e.\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eWhat’s changing?\u003c/h1\u003e\u003cp dir=\"ltr\"\u003eStarting from Elasticsearch 6.0, all REST requests that include a body must also provide the correct content-type for that body.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIn earlier releases of Elasticsearch, the content-type was optional, and if it was missing or not recognised, then the server would \u003cem\u003esniff\u003c/em\u003e the content and make an educated guess regarding the content-type. That will no longer happen in Elasticsearch 6.0 - every incoming request needs to have the correct content-type for the body it contains.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eThis ability to enforce strict content-type checking has existed since Elasticsearch 5.3 via the http.content_type.required \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/5.3/modules-http.html#_settings_2\"\u003econfiguration setting\u003c/a\u003e. In 5.x it is optional, and defaults to \u003ctt\u003efalse\u003c/tt\u003e, in Elasticsearch 6.0, that setting defaults to \u003ctt\u003etrue\u003c/tt\u003e, and there is no way to disable it.\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eWhy are we changing this?\u003c/h1\u003e\u003cp dir=\"ltr\"\u003eWe know that the content-type sniffing has been quite convenient when using basic HTTP tools such as curl. Many of us are quite accustomed to searching a cluster by running something like this:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ecurl 'http://localhost:9200/_search' -d'\u003cbr /\u003e{\u003cbr /\u003e \"query\" : {\u003cbr /\u003e \"match_all\" : {}\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eBut, we need to make that sort of operation slightly more verbose, and include the content-type, in the interests of \u003cem\u003e\u003cstrong\u003eclarity\u003c/strong\u003e\u003c/em\u003e and \u003cem\u003e\u003cstrong\u003esecurity\u003c/strong\u003e\u003c/em\u003e.\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eClarity\u003c/h2\u003e\u003cp dir=\"ltr\"\u003eAs Elasticsearch has evolved we’ve made a conscious decision to favour reliability and predictability over leniency. And while being lenient with content-types has been convenient, it also produced some surprising results.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eFor example, if you tried to send plain text content to an API that didn’t support it, then you would usually receive a clear error like this:\u003c/p\u003e\u003cblockquote style=\"font-family: monospace;font-style: normal;font-size: 100%;\"\u003eContent-Type header [text/plain] is not supported\u003c/blockquote\u003e\u003cp dir=\"ltr\"\u003eBut under the covers Elasticsearch was doing its best to try and guess what you might have meant. So, if your body started with “\u003ctt\u003e{\u003c/tt\u003e” then it would guess that your content was actually JSON, but when it tried to parse that, it would fail and the error message would look more like:\u003c/p\u003e\u003cblockquote style=\"font-family: monospace;font-style: normal;font-size: 100%;\"\u003eUnexpected character ('a' (code 97)): was expecting double-quote to start field name\u003c/blockquote\u003e\u003cp dir=\"ltr\"\u003eAnd, while most of our APIs support YAML formatted requests, the content-type sniffing required that the body start with a start-of-document marker (“\u003ctt\u003e---\u003c/tt\u003e”), which is not what users expected.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eWhen it comes to content-type, we’ve come to the conclusion that “Say what you mean” provides a more reliable and predictable outcome, than guessing. Being explicit is the safer, clearer and more consistent approach.\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eSecurity\u003c/h2\u003e\u003cp dir=\"ltr\"\u003eStrict checking of content-type is also useful as a layer of protection against \u003cem\u003eCross Site Request Forgery\u003c/em\u003e attacks.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eBecause the Elasticsearch REST API uses simple HTTP requests, what’s easy to do with curl, is often easy to do with your web browser. If your internal network allows it, you can point your favourite browser at the \u003ctt\u003e/_cluster/settings\u003c/tt\u003e endpoint on one of your Elasticsearch nodes and see the settings for your cluster.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eUnfortunately, if an attacker has the right knowledge about your internal network and Elasticsearch cluster, they can craft a malicious webpage that would use that same technique to perform unwanted updates to your cluster. Web browsers implement a number of security policies that help protect from such attacks, and part of that protection is to place limits on the content-types that may be used when sending data to remote servers.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eAs an example, consider this very simple web page:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;html\u0026gt;\u003cbr /\u003e \u0026lt;body\u0026gt;\u003cbr /\u003e \u0026lt;script src=\"https://code.jquery.com/jquery-3.2.1.min.js\"\u003cbr /\u003e type=\"text/javascript\"\u0026gt;\u0026lt;/script\u0026gt;\u003cbr /\u003e \u0026lt;script type=\"text/javascript\"\u0026gt;\u003cbr /\u003e $(function() {\u003cbr /\u003e $.ajax({\u003cbr /\u003e url: \"http://localhost:9200/visitors/doc/\",\u003cbr /\u003e type:'POST',\u003cbr /\u003e data: JSON.stringify({ browser: navigator.userAgent,\u003cbr /\u003e date: new Date() }),\u003cbr /\u003e contentType: 'text/plain'\u003cbr /\u003e });\u003cbr /\u003e });\u003cbr /\u003e \u0026lt;/script\u0026gt;\u003cbr /\u003e \u0026lt;/body\u0026gt;\u003cbr /\u003e\u0026lt;/html\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eIf you run an out-of-the-box install of Elasticsearch 5 on your local computer, and then open up that page in your web browser, it will add a new document in your Elasticsearch cluster that stores your browser’s \u003cem\u003eUser Agent\u003c/em\u003e and the time that you loaded the page. That’s not so scary, but with minimal changes we could make that same page overwrite or delete existing documents.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIf you try run that code in your browser, you will find that there an error message is displayed in the development console. Here’s what it looks like in Google Chrome:\u003c/p\u003e\u003cblockquote style=\"font-family: monospace;font-style: normal;font-size: 100%;\"\u003eXMLHttpRequest cannot load http://localhost:9200/visitors/doc/. No 'Access-Control-Allow-Origin' header is present on the requested resource.\u003c/blockquote\u003e\u003cp dir=\"ltr\"\u003eThat error is due to the \u003cem\u003eSame Origin Policy\u003c/em\u003e\u003csup id=\"footref-1\"\u003e\u0026nbsp;\u003c/sup\u003e\u003ca href=\"#footnote-1\"\u003e\u003csup id=\"footref-1\"\u003e1\u003c/sup\u003e\u003c/a\u003e that is one of the security features of the web. By default, a web page loaded from one site may only access content from that same site. This policy prevented our sample web page from reading the JSON that was sent as a response when it stored the document in Elasticsearch.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eBut why does the browser even allow us to send data to the Elasticsearch server if we’re not allowed to read the result? The answer lies in a second browser feature called \u003cem\u003eCross Origin Resource Sharing\u003c/em\u003e (CORS)\u003csup id=\"footref-2\"\u003e\u0026nbsp;\u003c/sup\u003e\u003ca href=\"#footnote-2\"\u003e\u003csup id=\"footref-2\"\u003e2\u003c/sup\u003e\u003c/a\u003e. While the \u003cem\u003eSame Origin Policy\u003c/em\u003e acts as a very useful default to securing the web, there are also many times where it is helpful for two otherwise independent sites to be able to share resources. CORS defines a mechanism by which a site can optionally grant other sites access to its resources.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eDue to the history of the web, and the way it has evolved over time, CORS assumes that some types of requests can always be \u003cem\u003esent\u003c/em\u003e safely. For example, web browsers have always allowed cross-origin form submission - a form on my web page can be configured to send its data to your server. If the browser determines that a cross-origin request meets certain requirements, then it will declare it to be \u003cem\u003esafe\u003c/em\u003e and will send that request off to the third-party server. It is only when the response comes back from that server, that the browser checks to see whether the original web page is allowed to access the provided content.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIn our example above, the request sets the content-type to be \u003ctt\u003etext/plain\u003c/tt\u003e which browsers treat as a safe value\u003csup id=\"footref-3\"\u003e\u0026nbsp;\u003c/sup\u003e\u003ca href=\"#footnote-3\"\u003e\u003csup id=\"footref-3\"\u003e3\u003c/sup\u003e\u003c/a\u003e, so the requests is sent off to the Elasticsearch server. When Elasticsearch responds, the browser looks for special CORS-related headers, so that it can decide whether the calling script is allowed to process the content of the response. By default, an Elasticsearch server does not include any of those CORS headers in the response, so the cross-origin request fails, and our web-page is prevented from seeing the results of the POST. But by then the damage has already been done - the request was sent to the Elasticsearch cluster and the document has been stored.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eThe strict content-type checking in Elasticsearch 6.0 helps prevent that damage. The Index API that is being used in this example does not support a content-type of \u003ctt\u003etext/plain\u003c/tt\u003e, so Elasticsearch 6.0 will reject the request without performing any updates.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eWe might attempt to work around those content-type checks by changing our test page to send a valid Content-Type such as JSON.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\u0026lt;html\u0026gt;\u003cbr /\u003e \u0026lt;body\u0026gt;\u003cbr /\u003e \u0026lt;script src=\"https://code.jquery.com/jquery-3.2.1.min.js\"\u003cbr /\u003e type=\"text/javascript\"\u0026gt;\u0026lt;/script\u0026gt;\u003cbr /\u003e \u0026lt;script type=\"text/javascript\"\u0026gt;\u003cbr /\u003e $(function() {\u003cbr /\u003e $.ajax({\u003cbr /\u003e url: \"http://localhost:9200/visitors/doc/\",\u003cbr /\u003e type:'POST',\u003cbr /\u003e data: JSON.stringify({ browser: navigator.userAgent,\u003cbr /\u003e date: new Date() }),\u003cbr /\u003e contentType: 'application/json'\u003cbr /\u003e });\u003cbr /\u003e });\u003cbr /\u003e \u0026lt;/script\u0026gt;\u003cbr /\u003e \u0026lt;/body\u0026gt;\u003cbr /\u003e\u0026lt;/html\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\"\u003eHowever, the CORS security policy does not treat \u003ctt\u003eapplication/json\u003c/tt\u003e as a \u003cem\u003esafe\u003c/em\u003e content-type, so the browser performs what is known as a \u003cem\u003epreflight\u003c/em\u003e request. That request is sent to the same URL on the Elasticsearch server, but the HTTP method is set to \u003ctt\u003eOPTIONS\u003c/tt\u003e and no data is sent in the request body. Once again the web browser looks for the special CORS response headers, and since Elasticsearch doesn’t send them, the cross-origin request is refused and the \u003ctt\u003ePOST\u003c/tt\u003e body is never sent to the Elasticsearch server.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eBy enforcing strict content-type checks in Elasticsearch 6.0, we reduce the risk of \u003cem\u003eCross Site Request Forgery\u003c/em\u003e attacks and help protect against accidental or malicious destruction of data.\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eWhat do I need to do?\u003c/h1\u003e\u003cp dir=\"ltr\"\u003eFor most users there’s nothing you need to do - everything has been taken care of.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eAll the components of the Elastic Stack, as well as our official REST clients will send the correct content-type for each request - just make sure that you’re on a recent version. If you are using a third-party client, or one that you built yourself, then you’ll need to check whether that client sends a valid content-type for each request.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIf you regularly use \u003ctt\u003ecurl\u003c/tt\u003e or another command line tool to send data into Elasticsearch, you’ll need to add the Content-Type header to any request that contains a body. For curl, that means adding -H'Content-Type: application/json' to the command line of any request that has a JSON body\u003csup id=\"footref-4\"\u003e\u0026nbsp;\u003c/sup\u003e\u003ca href=\"#footnote-4\"\u003e\u003csup id=\"footref-4\"\u003e4\u003c/sup\u003e\u003c/a\u003e.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIf you’re interested in testing your application or client library, we’ve released \u003ca href=\"https://www.elastic.co/blog/elasticsearch-6-0-0-alpha2-released\"\u003e6.0.0-alpha2\u003c/a\u003e, and it includes content-type checking. Alternatively, you can turn on strict content-type checking in recent versions of Elasticsearch 5 (see below).\u003c/p\u003e\u003ch1 dir=\"ltr\" rel=\"line-height:1.38;margin-top:20pt;margin-bottom:6pt;\"\u003eWhat about Elasticsearch 5.x?\u003c/h1\u003e\u003cp dir=\"ltr\"\u003eI mentioned earlier that you can enable strict content-type checking in recent releases of Elasticsearch 5 by enabling the http.content_type.required configuration option. Given the security reasons mentioned above, you should consider whether that is something that would be of value to you right now.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIf you’re deploying a brand new Elasticsearch cluster, it’s probably a good idea to require strict content-types from the start. It will be one less thing to worry about when you do upgrade to 6.x, and it gives you an added layer of protection against \u003cem\u003eCross Site Request Forgery\u003c/em\u003e attacks.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIf you have an existing Elasticsearch installation, then turning on that setting may be a little trickier - you need to know that all of your clients are sending the correct content-type. But if you can tackle that problem now that will get you one step closer to being able to migrate to Elasticsearch 6 when it is officially available.\u003c/p\u003e\u003ch1 dir=\"ltr\"\u003eConclusion\u003c/h1\u003e\u003cp dir=\"ltr\"\u003eThis is not a decision that we made lightly. We had a lot of conversation about it, and considered various options. We recognise that the old content sniffing approach was convenient, but we feel strongly that this change is a necessary one to help provide stable, reliable and predictable features in Elasticsearch.\u003c/p\u003e\u003chr/\u003e\u003cp id=\"footnote-1\" style=\"margin: 0 1em;\"\u003e\u003ca href=\"#footref-1\" style=\"font-size: 80%;min-width: 1.2em;display: inline-block;\"\u003e1.\u003c/a\u003e\u0026nbsp;\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy\"\u003ehttps://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy\u003c/a\u003e\u003c/p\u003e\u003cp id=\"footnote-2\" style=\"margin: 0 1em;\"\u003e\u003ca href=\"#footref-2\" style=\"font-size: 80%;min-width: 1.2em;display: inline-block;\"\u003e2.\u003c/a\u003e\u0026nbsp;\u003ca href=\"https://developer.mozilla.org/en-US/docs/Web/HTTP/Access_control_CORS\"\u003ehttps://developer.mozilla.org/en-US/docs/Web/HTTP/Access_control_CORS\u003c/a\u003e\u003c/p\u003e\u003cp id=\"footnote-3\" style=\"margin: 0 1em;\"\u003e\u003ca href=\"#footref-3\" style=\"font-size: 80%;min-width: 1.2em;display: inline-block;\"\u003e3.\u003c/a\u003e\u0026nbsp;\u003ca href=\"https://fetch.spec.whatwg.org/#cors-safelisted-request-header\"\u003ehttps://fetch.spec.whatwg.org/#cors-safelisted-request-header\u003c/a\u003e\u003c/p\u003e\u003cp id=\"footnote-4\" style=\"margin: 0 1em;\"\u003e\u003ca href=\"#footref-4\" style=\"font-size: 80%;min-width: 1.2em;display: inline-block;\" rel=\"font-size:90%;min-width:1.2em;display:inline-block\"\u003e4.\u003c/a\u003e\u0026nbsp;If you’re copying examples from our documentation, you’ll find that the the \u003cspan style=\"color: #00a9e5;\"\u003eCOPY AS CURL\u003c/span\u003e button automatically includes this option.\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:04:32.243Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"bltffd625cb0946c2c3","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-15T06:56:34.505Z","updated_at":"2018-10-15T06:56:34.505Z","content_type":"image/jpeg","file_size":"185571","filename":"content-typewriter-header.jpg","title":"content-typewriter-header.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:51:51.966Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltffd625cb0946c2c3/5bc43a22ee56595935433902/content-typewriter-header.jpg"},"markdown_l10n":"","publish_date":"2017-07-25T14:44:30.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"Elasticsearch 6.0 will enforce strict content-type checking. All REST requests that include a body must also provide the correct Content-Type header.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt048e5e01aa446692","ACL":{},"created_at":"2023-11-06T20:38:02.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"devsecops","label_l10n":"DevSecOps","tags":[],"title":"DevSecOps","updated_at":"2023-11-06T20:38:02.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.187Z","user":"blt4b2e1169881270a8"}},{"title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltfb7ae09ed75b8f86","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-15T06:56:29.805Z","updated_at":"2018-10-15T06:56:29.805Z","content_type":"image/jpeg","file_size":"115735","filename":"content-typewriter-thumb.jpg","title":"content-typewriter-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:51:51.966Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfb7ae09ed75b8f86/5bc43a1db126b38913d73917/content-typewriter-thumb.jpg"},"title":"Strict Content-Type Checking for Elasticsearch REST Requests","title_l10n":"Strict Content-Type Checking for Elasticsearch REST Requests","updated_at":"2025-03-10T11:47:13.936Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/strict-content-type-checking-for-elasticsearch-rest-requests","publish_details":{"time":"2025-03-10T11:47:30.925Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7d113691929d2058","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["bltc2297dffec6bba68"],"body_l10n":"\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eQuestion: How many engineers does it take to change a light bulb?\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAnswer: The light bulb works fine on the system in my office...\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eOK. It isn’t a great joke. But it’s the perfect setup for discussing an important topic here at Elastic: How do busy engineers, often working on large and gnarly projects, handle the small issues — like changing a metaphorical light bulb — that inevitably pop up from time to time?\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe answer: Fix-It Friday.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe Elasticsearch code is housed in a public repository \u003ca href=\"https://github.com/elastic/elasticsearch\"\u003eon GitHub\u003c/a\u003e and accessible to anyone. When a user finds bugs, spots missing features, or wants to make a specific request, they can flag it using the issues tab by simply submitting a new issue. The process is open and transparent — just the way we like it.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eEach day, someone on the Elasticsearch team is assigned to a role called support dev help. In this role, the engineer has the dual duty of aiding the Elastic support team while looking for fresh issues in the Elasticsearch repository. When a new issue arises, the engineer will add a label to help the team prioritize when to tackle it, and how much effort it might take to solve it.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eHowever, not all issues have a simple diagnosis, nor an easy fix.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“If there’s enough information, but it’s not clear that the issue is something we really want to handle due to policy, or maybe the person handling the ticket doesn’t have enough knowledge in the issue area to make a decision on it, then we can mark the ticket ‘discuss’ and it goes into the queue for Fix-It Friday,” said Colin Goodheart-Smithe, Elasticsearch Software Engineer. \u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eElasticsearch Team Lead Clint Gormley created the Fix-It Friday initiative a little over three years ago as a time when these small issues were given to engineers to solve. That ambitious concept didn’t last very long. The team quickly learned that small issues often turned out to be big ones in disguise. (Think: the filament in the light bulb looks dead, but in reality the electricity is out.) So, the scope of Fix-It Friday evolved into a get together for discussing user requests and finding solutions. Since the Elastic team is distributed, the meetup also became a weekly opportunity to get off Slack and email and get focused on a team video call.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“It’s a good time,” said Gormley, “getting a group with such a wide range of expertise in one virtual room — it’s amazing.”\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAbout 10 issues are discussed during a typical one hour Fix-It Friday session. Issues are later fixed and implemented or de-escalated. When asked whether there was a particular issue from a Fix-It Friday meeting that jumped out at him, or that he thought was quirky or fun, Gormley laughed. “We’ve only been through 12,000 issues or something ….”\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBut one seemingly small bug hiding something larger did spring to mind. Users reported heavy queries submitted to Elasticsearch never timing out, and Gormley recalled queries which ran for hours.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“Usually, our queries run milliseconds, so if one runs for an hour, you know you have a problem,” he explained.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIn these situations users, thinking nothing is happening, run the query again. So, instead of one \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-wildcard-query.html\"\u003ewildcard query\u003c/a\u003e running for an hour, they actually have two — or more. This isn’t exactly an issue that could break anything, but it had the potential to slow results and reduce resources. The issue was marked for discussion at a Fix-It Friday session. After a lengthy debate, Elastic engineers considered adding a default timeout, meaning in one hour’s time, the query got canceled. It seemed like a good idea at first. But with several eyeballs on the issue, another perspective developed.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eData is stored in indexes mapped out to shards, which are situated on different machines. When you run a query, it reaches out to all the shards, gathering the results and providing those results to the user. But what happens if one of the shards is missing due to a dying node on the shard, or when it gets disconnected from the network, causing the heavy query to fail? Should Elasticsearch show an exception? Or show only the results from the available shards?\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eUsers performing a simple search might be happy with getting results only from available shards. But users performing analytics would want to know that they’re receiving partial results. For the timeout option, Elastic engineers decided that a silent timeout (when you do not get a notification that the query stopped running) was out of the question. They also considered throwing an exception so that the user knew something was wrong with the query. But what of other circumstances, such as a missing shard, that can create partial results? Should that throw a hard exception too? In the end, they decided to add a global and per-request setting to toggle this behavior. The timeout discussion turned out to be too large a decision for one engineer to make on their own.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“From a user perspective it’s important that we actually look at these things,” said Gormley. “Our users are very involved. If they’ve taken the time to write a decent issue, we owe it to them to respond appropriately.”\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThis is where the value of Fix-It Friday really comes into play — it’s a broadening of the collective Elastic mind. For engineers, Fix-It Friday is a chance to break from the day-to-day and think about new issues in different ways, providing an opportunity to meditate on an problem that may not be their particular focus but is part of the larger product. In the end, Fix-It Friday isn’t about simply fixing bugs, or fielding requests — it’s about widening the scope of what Elastic can do.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“It's about making decisions,” said Elasticsearch Software Engineer Adrien Grand. “It’s about which direction we want to take.”\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“You see people asking us to add features that work on small datasets but won’t scale,” said Gormley. “If we make something as a small-scale solution, inevitably someone will want to use it on the big scale and it will fail. That kind of stuff is important for new devs to know so that they can make these decisions later on. There’s an ethos to how we develop; guiding principles of what to add, and what not to add.”\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eHowever, Gormley added, nothing is set in stone.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“That willingness to change minds is an important part of the Elastic culture.”\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e“As usual in open source,” added Adrien Grand, “no is temporary, but yes is forever.”\u003c/p\u003e","category":[{"uid":"bltc253e0851420b088","_version":4,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:45:23.873Z","created_by":"sys_blt57a423112de8a853","key":"culture","label_l10n":"Culture","tags":[],"title":"Culture","updated_at":"2024-05-10T13:44:28.145Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.214Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:04:00.950Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"Fix-It-Friday-Solving-Issues.jpg","uid":"blt207e3803f666e598","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:18:33.139Z","updated_at":"2019-01-05T09:18:33.139Z","content_type":"image/jpeg","file_size":"191702","filename":"Fix-It-Friday-Solving-Issues.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-22T18:02:55.445Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt207e3803f666e598/5c30766933d6423967f5b5f0/Fix-It-Friday-Solving-Issues.jpg"},"markdown_l10n":"","publish_date":"2017-12-22T17:40:59.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"black-and-white-code-programming-tech-79290.jpg","uid":"bltea769ac573ee2244","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:18:36.498Z","updated_at":"2019-01-05T09:18:36.498Z","content_type":"image/jpeg","file_size":"69779","filename":"black-and-white-code-programming-tech-79290.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-22T18:02:55.445Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltea769ac573ee2244/5c30766cebb7714d66027174/black-and-white-code-programming-tech-79290.jpg"},"title":"Solving the Small but Important Issues with Fix-It Fridays","title_l10n":"Solving the Small but Important Issues with Fix-It Fridays","updated_at":"2025-03-10T11:45:45.006Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/solving-the-small-but-important-issues-with-fix-it-fridays","publish_details":{"time":"2025-03-10T11:45:48.432Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1d36e81324226831","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Want to submit your first pull request (PR) to Elastic? In this post, we outline how we use pull requests, how to submit, and the process when we receive one.","author":["bltc2297dffec6bba68"],"body_l10n":"\u003cp\u003eGetting things done at Elastic is a collaborative effort.\u003c/p\u003e\u003cp\u003eOur engineers work around the clock (quite literally for a \u003ca href=\"https://www.elastic.co/about/our-source-code\"\u003edistributed company\u003c/a\u003e) developing new products and features. It’s an immense amount of work, requiring fine attention to detail. But no matter how careful we are, we’re not perfect, and with any open source project as complex as ours, we still need the community's help to make it better.\u003c/p\u003e\u003cp\u003eIn \u003ca href=\"https://www.elastic.co/blog/solving-the-small-but-important-issues-with-fix-it-fridays\"\u003eSolving the Small but Important Issues with Fix-It Fridays\u003c/a\u003e, we discussed how contributions from our community are the driving factor of our continued success in developing our products. One of the great benefits of being an open source project is that we have a large community of developers looking out for bugs and eagerly waiting for a chance to squash them.\u003c/p\u003e\u003cp\u003eIf you’re a new member to the community and want to submit your first pull request (PR), or have questions about how the process works, you’ve come to the right place! In this post, we’ll provide an overview of how pull requests work for Elastic, what the process is when we receive one, and how to avoid common mistakes that might prevent your contribution from being implemented.\u003c/p\u003e\u003ch2\u003eSo, how do I submit a pull request?\u003c/h2\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt20df7811154eb06b/5fa98bde42256d5ffdf418b1/blog-how-we-pull-1.png\" style=\"border: none;transform: rotate(0.00rad);webkit-transform: rotate(0.00rad);\" width=\"624\" height=\"275\"/\u003e\u003c/p\u003e\u003cp\u003eBefore you submit a PR, you need to create a fork in a GITHUB repository and make your code changes. This is usually done under your own GitHub account, which creates a copy of the source repository for you. All of our projects live in their own GitHub repository. A full list of our repositories are available on the \u003ca href=\"https://github.com/elastic\"\u003eElastic organization page\u003c/a\u003e on GitHub.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOnce you’ve created a fork of a repository and changed the code, you’ll be asked if you want to create a PR to push the suggested changes to the master branch of the product repository. For example, \u003ca href=\"https://github.com/elastic/elasticsearch\"\u003ethe Elasticsearch repository\u003c/a\u003e seen below. To keep things simple, we'll show examples from the Elasticsearch repository throughout this post.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt236f36ccc109c964/5fa98bd64a4abb73ff79c618/blog-how-we-pull-2.png\" style=\"border: none;transform: rotate(0.00rad);webkit-transform: rotate(0.00rad);\" width=\"624\" height=\"336\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc7e6969602ebde49/5fa98bde6f82405d9a4aa965/blog-how-we-pull-3.png\" style=\"border: none;transform: rotate(0.00rad);webkit-transform: rotate(0.00rad);\" width=\"624\" height=\"84\"/\u003e\u003c/p\u003e\u003cp\u003eWhen you click on the “New pull request”, you’ll be greeted by our \u003ca href=\"https://github.com/elastic/elasticsearch/blob/master/.github/PULL_REQUEST_TEMPLATE.md\"\u003epull request template\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7f6935bae5ef3748/5fa98bd646f622769b5ec879/blog-how-we-pull-4.png\" style=\"border: none;transform: rotate(0.00rad);webkit-transform: rotate(0.00rad);\" width=\"624\" height=\"247\"/\u003e\u003c/p\u003e\u003cp\u003eThis template will give you the guidance that will help your PR get through the first review, so be sure to read through it since each product has its own set of criteria and documentation.\u003c/p\u003e\u003cp\u003eMake sure to avoid these common mistakes when submitting:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eSubmitting duplicates -\u003c/strong\u003e First, search for open PRs that already address the bug your code is attempting to fix. Duplicates are usually denied.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eNot including tests -\u003c/strong\u003e A PR that includes code changes should include a test that illustrates the new code’s behavior. Ideally, this test should reproduce the problem the PR is fixing so that the test fails without the code, and passes when the code is applied.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eMaster branch\u0026nbsp;only -\u003c/strong\u003e Make sure that any PR which changes code is made against the master branch in the relevant directory.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eOnce you’ve completed all the requirements spelled out in the template, click “Create Pull Requests”. Now the ball is in our court.\u003c/p\u003e\u003ch2\u003eTriaging and labeling\u003c/h2\u003e\u003cp\u003eThe first step we take is to make sure the PR meets the requirements of a good request (as mentioned above), and if it does, to tag the PR with a label so that it ends up in the right hands for further investigation. Labels might include \u0026gt;bug, \u0026gt;feature, etc. Once the pull request has a label, it is assigned to the proper subteam to handle. From that point, dealing with the request is the responsibility of the team in charge of that area.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3cb04a52dd873501/5fa98bde65bdd35303e00a60/blog-how-we-pull-5.png\" style=\"border: none;transform: rotate(0.00rad);webkit-transform: rotate(0.00rad);\" width=\"624\" height=\"409\"/\u003e\u003c/p\u003e\u003ch2\u003eBeginning the process\u003c/h2\u003e\u003cp\u003eOnce the PR is labelled it is picked up by one of our developers. We try to get back to the requester as soon as possible and we ask that you have patience when submitting the PR as handling the request properly may take some time due to level and depth of requests coming in around the clock.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eSubmitting documentation changes\u003c/h2\u003e\u003cp\u003eNote: We also receive a lot of PRs that modify or request changes to our docs. This process is a lot simpler than code changes — all that’s required is to click “edit” on the Elastic docs page, make changes, and submit the request. There’s no need to fork a project and no tests required. We label these PRs “\u0026gt;doc” and handle them as quickly as possible.\u003c/p\u003e\u003ch2\u003eOften, there’s more work to be done\u003c/h2\u003e\u003cp\u003eA PR often needs to be adapted before it’s ready to merge. At this point, the PR becomes a collaborative space where discussion takes place, changes are proposed, and further commits are made.\u003c/p\u003e\u003cp\u003eDuring the review process we run tests against the PR, and the results can be seen on GitHub. Sometimes, the test will fail when the changes in the PR are applied, even if the submitted tests worked. This isn’t the end of the line though. We’ll help the contributor fix the contributed code so that all tests pass.\u003c/p\u003e\u003cp\u003eCode style, as well as code and naming conventions, is something we also look at in this stage. Users who submit pull requests should expect that their code will go through at least one review round. Code is never perfect (nope, not even ours!) and ready to merge when submitted — so expect some collaboration along the way.\u003c/p\u003e\u003ch2\u003eHow long will it take to commit my PR?\u003c/h2\u003e\u003cp\u003ePRs vary in the time it takes to handle them. A simple line of code might be handled swiftly, but complex code changes will go through multiple rounds of review. If you feel that your PR has sat for a long time without any action, it’s OK to ping the ticket as a reminder it’s still active.\u003c/p\u003e\u003ch2\u003eCommitting the code\u003c/h2\u003e\u003cp\u003eWhen everything is ready to go, the reviewers will add a comment with the approval action — which may be a LGTM (\"Looks Good To Me\") comment, or something along those lines. After the PR is accepted, an Elastic developer will merge the pull request into the master branch and then back port the change to the development branches as necessary.\u003c/p\u003e\u003cp\u003eSo, that’s how it works — in a nutshell. Of course, pull requests vary. The process may be simple, or difficult. The only way you’ll know the process in depth is to roll up your sleeves and get in there, elbow deep.\u003c/p\u003e\u003cp\u003eReady to submit your first PR? Have a look through the \u003ca href=\"https://github.com/elastic\"\u003eElastic repositories available on GitHub\u003c/a\u003e, familiarize yourself with the guidelines, and give it a go. If you have any further questions about the process then head over to our \u003ca href=\"https://discuss.elastic.co/\"\u003eDiscuss forums\u003c/a\u003e, create a topic, and we'll be happy to help.\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:50:26.808Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"Debug.jpg","uid":"blt82a39e38e1a5ae8a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:43:07.565Z","updated_at":"2019-02-04T06:43:07.565Z","content_type":"image/jpeg","file_size":"80335","filename":"Debug.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T00:25:37.436Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt82a39e38e1a5ae8a/5c57defba209c1ca0be9dcd9/Debug.jpg"},"markdown_l10n":"","publish_date":"2018-09-10T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How We Handle Pull Requests at Elastic","seo_description_l10n":"Want to submit your first pull request (PR) to Elastic? In this post, we outline how we use pull requests, how to submit, and the process when we receive one.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"Code request.jpg","uid":"blt9455447ab8242933","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:43:13.822Z","updated_at":"2019-02-04T06:43:13.822Z","content_type":"image/jpeg","file_size":"128256","filename":"Code_request.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T00:25:37.436Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9455447ab8242933/5c57df0165157fdb0b6c6329/Code_request.jpg"},"title":"How We Handle Pull Requests at Elastic","title_l10n":"How We Handle Pull Requests at Elastic","updated_at":"2025-03-10T11:44:35.547Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/how-we-handle-pull-requests-at-elastic","publish_details":{"time":"2025-03-10T11:44:40.964Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt47e67819b1cc33ac","_version":21,"locale":"en-us","ACL":{},"abstract_l10n":"In 7.11, we’re thrilled to release the beta of runtime fields, Elastic's implementation of schema on read. You now have the best of both — the performance and scale you expect from schema on write, combined with the flexibility with schema on read.","author":["blt59e7f7049d793705"],"body_l10n":"\u003cp\u003eWe’re pleased to announce Elasticsearch 7.11.0, based on Apache Lucene 8.7.0.\u003c/p\u003e\u003cp\u003eVersion 7.11 is the latest stable release of Elasticsearch and is now available for deployment via \u003ca href=\"https://www.elastic.co/products/elasticsearch/service\"\u003eElasticsearch Service on Elastic Cloud\u003c/a\u003e or via \u003ca href=\"https://www.elastic.co/downloads/elasticsearch\"\u003edownload\u003c/a\u003e for use in your own environment(s).\u003c/p\u003e\u003cp\u003eReady to roll up your sleeves and get started? We have the links you need:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/cloud/\"\u003eStart Elasticsearch on Elastic Cloud\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/downloads/elasticsearch\"\u003eDownload Elasticsearch\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/release-notes-7.11.0.html\"\u003eElasticsearch 7.11.0 release notes\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/breaking-changes-7.0.html\"\u003eElasticsearch 7.11.0 breaking changes\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eWith today’s release, our \u003ca href=\"https://www.elastic.co/enterprise-search\"\u003eElastic Enterprise Search\u003c/a\u003e, \u003ca href=\"https://www.elastic.co/observability\"\u003eElastic Observability\u003c/a\u003e, and \u003ca href=\"https://www.elastic.co/security\"\u003eElastic Security\u003c/a\u003e solutions also received updates. To learn more, check out our main \u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-7-11-0-searchable-snapshots-schema-on-read\"\u003eElastic 7.11\u0026nbsp;release\u003c/a\u003e blog or read the \u003ca href=\"https://elastic.co/blog/whats-new-elastic-enterprise-search-7-11-0-web-crawler-box-content-source\"\u003eElastic Enterprise Search blog\u003c/a\u003e, \u003ca href=\"https://elastic.co/blog/whats-new-elastic-observability-7-11-0-apm-service-overview-page-ecs-logging-library-ga\"\u003eElastic Observability blog\u003c/a\u003e, and \u003ca href=\"https://elastic.co/blog/whats-new-elastic-security-7-11-0-cloud-host-detections-accessible-UI\"\u003eElastic Security blog\u003c/a\u003e for more details.\u003c/p\u003e\u003ch2\u003eKnown Issue\u003c/h2\u003e\u003cp\u003eInstallations of Elasticsearch 7.11.0 with an\u0026nbsp;Active Directory or LDAP realm configured will fail to start. A fix will be released in 7.11.1. For more details, please see the\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/release-notes-7.11.0.html#known-issues-7.11.0\"\u003e7.11.0 release notes\u003c/a\u003e.\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.x/release-notes-7.11.0.html#known-issues-7.11.0\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003c/p\u003e\u003ch2\u003eSchema on read for Elasticsearch is here\u003c/h2\u003e\u003cp\u003eYou’ve read that right: schema on read is here for Elasticsearch 7.11. You can now get the best of both worlds on a single platform — the performance and scale you expect from schema on write, combined with the flexibility and data discovery of schema on read. We call the feature that delivers schema on read \u003cstrong\u003eruntime fields\u003c/strong\u003e,\u003cstrong\u003e \u003c/strong\u003eand it's now in beta.\u003c/p\u003e\u003cp\u003eRuntime fields let you define and evaluate fields at query time, which opens a wide range of new use cases. If you need to adapt to a changing log format or fix an index mapping, use runtime fields to change the schema on the fly without reindexing your data. Or if you are indexing new data and don’t have intimate knowledge of what it contains, you can use runtime fields to discover this data and define your schema without impacting others.\u003c/p\u003e\u003cp\u003eNo matter the use case, runtime fields reduce the time to get value from your data.\u003c/p\u003e\u003ch3\u003eBetter together\u003c/h3\u003e\u003cp\u003eElasticsearch is known for being a fast distributed search and analytics engine because we use schema on write. With schema on write, fields are written to disk at ingest time, so you need to plan what fields you want in advance and test to ensure you’re happy with the results.\u003c/p\u003e\u003cp\u003eThe payoff is fast queries, which is why schema on write is still the default mechanism within Elasticsearch for indexing and searching data. With schema on read, there is added flexibility as it doesn’t require as much planning and testing, which comes in handy when you don’t know your data or when you realize after indexing you want to\u0026nbsp;do things differently.\u003cbr /\u003e\u003cbr /\u003eWhat’s unique about our implementation of schema on read is that we’ve built runtime fields on the same Elastic Stack — the same architecture, the same tools, and the same interfaces you are already using. There are no new datastores, languages, or components, and there’s no additional procedural overhead.\u0026nbsp; Using both of these mechanisms complement each other, giving you performance with schema on write and flexibility with schema on read.\u003c/p\u003e\u003cp\u003eBe sure to read more on the \u003ca href=\"https://www.elastic.co/blog/introducing-elasticsearch-runtime-fields\"\u003eruntime fields blog\u003c/a\u003e and if you’re ready to dig in, check out the \u003ca href=\"https://elastic.co/blog/getting-started-with-elasticsearch-runtime-fields\"\u003etechnical blog\u003c/a\u003e.\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/rSvmFXHwD4Fy39EKPYBKob.jpg\" data-uuid=\"rSvmFXHwD4Fy39EKPYBKob\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"1\" disable_analytics=\"1\" style=\"width: 100%;margin: auto;display: block;\" width=\"100%\"/\u003e\u003c/div\u003e\u003ch2\u003eYour data is good as cold with searchable snapshots and cold tier both generally available\u003c/h2\u003e\u003cp\u003eIn Elasticsearch 7.10 we \u003ca href=\"https://www.elastic.co/blog/whats-new-elasticsearch-7-10-0-searchable-snapshots-store-more-for-less\"\u003eannounced\u003c/a\u003e \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/searchable-snapshots.html\"\u003esearchable snapshots\u003c/a\u003e, a new capability that brings S3 and other object stores to life. Searchable snapshots let you directly search the data stored in your snapshots as well as the new cold tier, which can reduce your data storage costs by up to 50% over the existing warm tier. Storing more data at a reduced cost provides an easy and fast way to get a deeper level of data insight.\u003c/p\u003e\u003cp\u003eData is a differentiator to how business and operations run. With exponential data growth, it becomes economically unfeasible to store and search all of your data on expensive compute with SSD drives.\u003c/p\u003e\u003cp\u003eThe typical solution over time is to \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/index-lifecycle-management.html\"\u003emove your data\u003c/a\u003e to a different data tier consisting of less performant disks and compute, and eventually migrating read-only data to snapshots stored on low-cost object storage (such as AWS S3). If you want to search data stored in snapshots, you first need to manually restore the data back to the cluster. This takes time and effort.\u003c/p\u003e\u003cp\u003eBut with searchable snapshots, you can directly search these snapshots without the need to “rehydrate” your data.\u003c/p\u003e\u003cp\u003eThe cold tier stores your read-only data locally, but it backs the indices with snapshots stored in S3, Azure, Google Cloud, or other low-cost object stores for resiliency. This removes the need to store replicas of your data locally, effectively doubling the density of your local storage nodes. Using the cold tier, you can retain more data locally at a large scale for a significantly reduced cost — all with the same level of reliability, redundancy, and automatic recovery you’ve come to expect from Elasticsearch.\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/8AjEgtqGRTz5R6F7B7kFJV.jpg\" data-uuid=\"8AjEgtqGRTz5R6F7B7kFJV\" data-v=\"4\" data-type=\"inline\" data-autoplay=\"1\" data-loop=\"1\" data-disable_analytics=\"1\" data-hidden_controls=\"1\" data-muted=\"1\" disable_analytics=\"1\" style=\"width: 100%;margin: auto;display: block;\" width=\"100%\"/\u003e\u003c/div\u003e\u003cp\u003eWith the cold tier, you no longer need to choose which piece of observability data to delete to save money. Imagine searching year over year on application performance without needing to restore your data first from backups. Or gain increased insight by combining observability data with business intelligence to make intuitive data-driven decisions.\u003c/p\u003e\u003cp\u003eArm threat hunters and security analysts with years of high-volume security data sources now made easily accessible through searchable snapshots. Collect additional security-related data at greater scale and keep it accessible for longer than previously practical or economical. Performing large security forensic investigations has become a lot easier and less time consuming with data stored on the cold tier.\u003c/p\u003e\u003cp\u003eWhile we are excited with these new capabilities, our journey does not stop here. We’re currently developing a frozen tier, which takes things a step further and allows you to store and search your data directly on the object store. Removing the need to store data locally at all can reduce your storage costs by an even bigger margin.\u003c/p\u003e\u003cp\u003eThis means you’ll be able to search nearly an unlimited amount of data, on demand, with costs approaching that of just storing data on S3.\u003c/p\u003e\u003cp\u003eSearchable snapshots and the cold tier are now generally available for self-managed users. Both are also available in Elastic Cloud along with a cold slider. If you’d like to know more details, please visit the \u003ca href=\"https://www.elastic.co/elasticsearch/elasticsearch-searchable-snapshots\"\u003esearchable snapshots page\u003c/a\u003e or read our \u003ca href=\"https://www.elastic.co/blog/introducing-elasticsearch-searchable-snapshots\"\u003ededicated blog\u003c/a\u003e.\u003c/p\u003e\u003ch3\u003eThreat detection in action with EQL, now generally available\u003c/h3\u003e\u003cp\u003eEvent query language or EQL has come a long way in helping with threat investigation, identification, and prevention. For those not familiar with EQL, it’s a sequential correlation language that allows you to view multiple events within a system, draw conclusions to give a better perspective of that system, and observe these sequences over a span of time.\u003c/p\u003e\u003cp\u003eSince our announcement in 7.9, we’ve been continuously developing and maturing EQL to assist in threat detection. Let’s walk through one example of how EQL can help identify a MITRE ATT\u0026amp;CK™: Spearphishing (T1193); PowerShell (T1086).\u003c/p\u003e\u003cp\u003eIn this attack there is a scriptable child process such as a PowerShell, VBScript or cmd.exe within an MS Office product such as Word, Excel, or Powerpoint.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eEQL\u003c/strong\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eprocess where\u003cbr /\u003e process.parent.name in (\u003cbr /\u003e \"WINWORD.EXE\", \"EXCEL.EXE\", \"POWERPNT.EXE\"\u003cbr /\u003e )\u003cbr /\u003e and process.name in (\u003cbr /\u003e \"powershell.exe\", \"cscript.exe\", \"wscript.exe\", \"cmd.exe\"\u003cbr /\u003e )\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eEQL will then use these previous sequence correlations over a span of time to identify the validity.\u003c/p\u003e\u003cp\u003eIn this EQL query we are asking “Did MS Office create a VBScript and then execute over a max span of 5 minutes?”\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003esequence with maxspan=5m\u003cbr /\u003e [file where file.extension == \"exe\"\u003cbr /\u003e and process.name in (\"WINWORD.EXE\") \u003cbr /\u003e ] by file.path\u003cbr /\u003e [process where true] by process.executable\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe power in EQL is that it allows you to match a sequence of events of various types. It’s similar to other query languages, which helps reduce the learning curve. And it’s built for security — specifically threat hunting and behavior detection.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eFind the path with geo_line aggregation\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eThe new geo_line aggregation aggregates all the geo_point values within a bucket into a LineString ordered by the chosen sort field (usually timestamp). This feature is useful when you have a set of locations of an object, and you want the path that the object travelled.\u003c/p\u003e\u003cp\u003eAn example of a use case is in shipping logistics. You can collect GPS coordinates of your freight trucks on a regular interval, sort by the timestamp of each such location document, and draw a line that represents the path the truck traveled.\u003c/p\u003e\u003ch2\u003eTrack security configuration changes with a new security_config_change event.type\u003c/h2\u003e\u003cp\u003eAs an administrator, making security changes like adding a user or a user role is trivial, but troubleshooting access issues or auditing these changes was impossible.\u003c/p\u003e\u003cp\u003eWith the new event.type security_config_change, adding a user or a role is now tracked in the audit log. With this change, there is no need to log the entire payload to audit details of changes to security settings because they are now available with a dedicated event type.\u003c/p\u003e\u003cp\u003eHere’s an example of what is logged when the Put User API is invoked to create or update a native user:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\"type\":\"audit\", \"timestamp\":\"2020-12-30T22:10:09,749+0200\", \"node.id\":\"0RMNyghkQYCc_gVd1G6tZQ\", \"event.type\":\"security_config_change\", \"event.action\":\"put_user\", \"request.id\":\"VIiSvhp4Riim_tpkQCVSQA\", \"put\":{\"user\":{\"name\":\"user1\",\"enabled\":false,\"roles\":[\"admin\",\"other_role1\"],\"full_name\":\"Jack Sparrow\",\"email\":\"jack@blackpearl.com\",\"has_password\":true,\"metadata\":{\"cunning\":10}}}}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eFor additional information or examples, be sure to check out the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/audit-event-types.html\"\u003eaudit event types documentation\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eA UI is worth a thousand API calls\u003c/h2\u003e\u003cp\u003eElasticsearch UI enhancements are one of the many examples of how Elastic continues to provide a better user experience. Here are some of the major UI enhancements in 7.11.\u003c/p\u003e\u003ch3\u003eAutocomplete for Pain|less\u003c/h3\u003e\u003cp\u003eNot an expert in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/modules-scripting-painless.html\"\u003ePainless scripting\u003c/a\u003e? Can’t quite remember the correct syntax? Not a problem with the new autocomplete UI for painless scripts. With helpful autocomplete syntax suggestions, including mapped fields and source, and inline error reporting, you save time and frustration with scripting in Painless. You can find this new UI everywhere painless is used in \u003ca href=\"https://www.elastic.co/kibana\"\u003eKibana\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt620fdd16631e4074/6019946361513a1aa7473ea4/blog-elasticsearch-7-11-painless.gif\" data-sys-asset-uid=\"blt620fdd16631e4074\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch3\u003eSearchable snapshots in ILM UI\u003c/h3\u003e\u003cp\u003eIf you are a longtime user of Elasticsearch, you know that \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/index-lifecycle-management.html\"\u003eindex lifecycle management\u003c/a\u003e has come a long way when it comes to moving data and having the ability to configure it within the UI. With the recent addition of data tiers and searchable snapshots, you now have the ability to configure hot and cold phases and searchable snapshots within the ILM policies UI.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8215515f87c37212/6019948254849c183a1c044b/blog-elasticsearch-7-11-searchable-snaps.gif\" data-sys-asset-uid=\"blt8215515f87c37212\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch3\u003eRuntime fields editor in the index template\u003c/h3\u003e\u003cp\u003eThe beta release of runtime fields delivers schema on read to Elasticsearch, which opens many new workflows. One of the ways to define runtime fields is during the creation of an index template. With the index template mapping editor, you can explore the possibilities by creating and editing runtime fields in your index template mappings.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltde04630fed53b29f/6019949f0f1c0c1aa6f87f02/blog-elasticsearch-7-11-runtime-fields.gif\" data-sys-asset-uid=\"bltde04630fed53b29f\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch3\u003eTransform adds a new type: Latest in machine learning\u003c/h3\u003e\u003cp\u003eTransforms in 7.11 has added another type focused on allowing you to copy the most recent documents to a new index. This new type of Transform is called Latest and works by identifying one or more fields as a unique key and a date field for sorting, then creating an index that can be updated with the most recent document.\u003c/p\u003e\u003cp\u003eScenarios where this becomes especially useful include where companies are trying to keep track of the latest purchase their customers have made or in a monitoring setting where tracking the latest event coming from a host is critical.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1c552014dfa6c0f2/601994b629a02c49ba1f431d/blog-elasticsearch-7-11-transform.jpg\" data-sys-asset-uid=\"blt1c552014dfa6c0f2\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eThat's all folks…\u003cspan\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e7.11 is another monumental release for Elasticsearch, and we couldn't cover all of it within this blog. Be sure to check out more in the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.11/release-highlights.html\"\u003erelease highlights\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eReady to get your hands dirty and try some of the new functionalities? Spin up a \u003ca href=\"https://cloud.elastic.co/registration\"\u003efree 14-day trial of Elastic Cloud\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/downloads/elasticsearch\"\u003edownload Elasticsearch\u003c/a\u003e today. Try it out and be sure to let us know what you think on Twitter (\u003ca href=\"https://twitter.com/elastic\"\u003e@elastic\u003c/a\u003e), in \u003ca href=\"https://discuss.elastic.co/c/elasticsearch\"\u003eour forum\u003c/a\u003e, or join us on our \u003ca href=\"https://join.slack.com/t/elasticstack/shared_invite/zt-l83t3arq-0ivqSOe2S6IBiRGBb6ollg\"\u003ecommunity slack channel.\u003c/a\u003e\u003c/p\u003e","category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-02-02T14:59:55.237Z","created_by":"blt34e7f499d15c5bd0","disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt524d5ee0222d5354","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:36.948Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"54225","filename":"blog-banner-release-elasticsearch.png","parent_uid":null,"tags":[],"title":"blog-banner-release-elasticsearch.png","updated_at":"2021-01-26T17:45:10.329Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-03T15:47:40.504Z","user":"bltde77f2161b811714"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt524d5ee0222d5354/601055260cb0aa0ffcdd590e/blog-banner-release-elasticsearch.png"},"markdown_l10n":"","publish_date":"2021-02-10T17:03:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch 7.11.0 released","seo_description_l10n":"In Elasticsearch 7.11, we’re thrilled to release the beta of runtime fields, Elastic's implementation of schema on read. You now have the best of both — the performance and scale you expect from schema on write, combined with the flexibility with schema on read.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"blt8c2b608c10eb1fd8","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:42.964Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"51730","filename":"blog-thumb-release-elasticsearch.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-elasticsearch.png","updated_at":"2022-02-11T21:03:50.956Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.895Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c2b608c10eb1fd8/601055106215cf0f9a18d799/blog-thumb-release-elasticsearch.png"},"title":"Elasticsearch 7.11.0 released: Adding flexibility with schema on read","title_l10n":"Elasticsearch 7.11.0 released: Adding flexibility with schema on read","updated_at":"2025-03-10T11:42:21.599Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/whats-new-elasticsearch-7-11-0-schema-on-read-is-here","publish_details":{"time":"2025-03-10T11:42:25.025Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt23fc1bf24f8f6102","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"The 6.4 release of Kibana includes new features highlighted by the addition of sample data, the Elastic Maps service, experimental API docs, scripted field and saved object changes and many redesigned UIs.","author":["blt4ca268ce71bf38df"],"body_l10n":"\u003cp\u003eWelcome to the 6.4.0 release of Kibana!\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/downloads/kibana\"\u003eDownload Kibana 6.4.0\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/guide/en/kibana/6.4/release-notes-6.4.0.html\"\u003eKibana 6.4.0 release notes\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eYou can get all the details\u0026nbsp;in the release notes linked above, but there are a few changes which are worth highlighting:\u003c/p\u003e\u003cul\u003e\u003cli\u003eOne-click sample data\u003c/li\u003e\u003cli\u003eImproved workflow for inspecting data\u003c/li\u003e\u003cli\u003eNew Beta tutorials\u003c/li\u003e\u003cli\u003eSaved Objects refresh\u003c/li\u003e\u003cli\u003eScripted fields preview\u003c/li\u003e\u003cli\u003eCustom rules for fine tuning machine learning results\u003c/li\u003e\u003cli\u003eImproved usability for managing machine learning jobs\u003c/li\u003e\u003cli\u003eResponse time anomalies with machine learning in APM\u003c/li\u003e\u003cli\u003eNew query bar for searching and filtering APM data\u003c/li\u003e\u003cli\u003eLanding page for Elastic Maps Service\u003c/li\u003e\u003cli\u003eApply Vega\u0026nbsp;filters to dashboard context\u0026nbsp;\u003c/li\u003e\u003cli\u003eExperimental API docs\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eOne-click sample data\u003c/h2\u003e\u003cp\u003eTo improve the getting started experience, Kibana has a sample data set that enables you to take Kibana for a test ride without having to go through the process of loading data yourself.\u0026nbsp; With one click, you can install a Flight data set and start interacting with Kibana visualizations in seconds.\u003c/p\u003e\u003cp\u003eTo access the sample data, go to the Kibana home page and click the link next to Sample Data.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltad181a4693ba62f4/5fa98f3097f9f35d942e9b6f/blog-kibana-6-4-0-1.png\" width=\"624\" height=\"431\" style=\"width: 624;height: 431;\"/\u003e\u003c/p\u003e\u003ch2\u003eImproved workflow for inspecting data\u003c/h2\u003e\u003cp\u003eIf you’ve used a spy panel in the past to inspect the data behind a visualization, you’ll notice that this feature's been given a facelift.\u0026nbsp; It’s also easier to access--you can inspect visualizations from multiple places in the UI.\u0026nbsp; On a dashboard, open the panel menu for a visualization and select Inspect.\u0026nbsp; In the visualization editor, click Inspect in the menu bar.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt584eb9c28891e07a/5fa98f2ffaf76f509e12e9a1/blog-kibana-6-4-0-2.png\" width=\"624\" height=\"484\" style=\"width: 624;height: 484;\"/\u003e\u003c/p\u003e\u003ch2\u003eAdditional tutorials for adding data to Kibana\u003c/h2\u003e\u003cp\u003eYou’ll find new Beta tutorials on the Add Data page. The majority of these tutorials are\u0026nbsp;for Metricbeat modules that fetch metrics from services.\u0026nbsp; They include the Beta label to indicate that they are a pre-release of the software.\u003c/p\u003e\u003cp\u003eTo access the tutorials, go to the Kibana home page. In Add Data to Kibana, find the data type you’re interested in and click its button to view a list of available tutorials.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt84b67115b20d1bec/5fa98f2809ed4c6f277eb608/blog-kibana-6-4-0-3.png\" width=\"624\" height=\"483\" style=\"width: 624;height: 483;\"/\u003e\u003c/p\u003e\u003ch2\u003eSaved Objects design refresh\u003c/h2\u003e\u003cp\u003eSaved Objects in Management has a new look. The updated page provides the same features in terms of filtering, importing, exporting, and deleting of saved objects, plus three main improvements:\u003c/p\u003e\u003cul\u003e\u003cli\u003eYou can now import and export index patterns.\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eImporting saved objects has a more user-friendly workflow.\u003c/li\u003e\u003cli\u003eA new Relationship view allows you to view how other objects use an object, so you know the impact of deleting it.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4179e635d6dd971f/5fa98f30fd99385ff6003cd4/blog-kibana-6-4-0-4.png\" width=\"624\" height=\"431\" style=\"width: 624;height: 431;\"/\u003e\u003c/p\u003e\u003ch2\u003ePreview your scripted fields\u003c/h2\u003e\u003cp\u003eIndex patterns in Management now allows you to test run a \u003ca href=\"/guide/en/kibana/6.4/scripted-fields.html\"\u003escript\u003c/a\u003e to see if your scripted fields work as intended. If your results require more context, you can easily include more fields in the test run.\u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp\u003eTo try out this feature, open Index patterns \u0026gt; Scripted fields.\u0026nbsp; Add or edit a scripted field and click Get help with syntax and preview the results or your script.\u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp\u003eScripts are validated on save.\u0026nbsp; You can’t save a script that won't compile.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta372f5567cfe6b0f/5fa98f293cdbef7187ce5539/blog-kibana-6-4-0-5.png\" width=\"624\" height=\"483\" style=\"width: 624;height: 483;\"/\u003e\u003c/p\u003e\u003ch2\u003eCustom rules for fine tuning machine learning results\u003c/h2\u003e\u003cp\u003eIf you want to fine tune your machine learning results (for example, to skip anomalies related to certain servers), you can now create custom rules in Kibana. Custom rules instruct anomaly detectors to change their behavior based on domain-specific knowledge that you provide. \u003ca href=\"/guide/en/elastic-stack-overview/6.4/ml-rules.html\"\u003eSee machine learning custom rules\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc7e99eb0822567d3/5fa98f2972a3526f28dba3c0/blog-kibana-6-4-0-6.jpg\" width=\"624\" height=\"567\" style=\"width: 624;height: 567;\"/\u003e\u003c/p\u003e\u003ch2\u003eImproved usability for managing machine learning jobs\u003c/h2\u003e\u003cp\u003eThe Machine Learning \u0026gt; Job Management page has a new look, which comes with better searching, filtering, and multi-select options, enabling you to manage multiple jobs with fewer clicks.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41678ad943916efd/5fa98f274a4abb73ff79c62c/blog-kibana-6-4-0-7.jpg\" width=\"624\" height=\"327\" style=\"width: 624;height: 327;\"/\u003e\u003c/p\u003e\u003ch2\u003eResponse time anomalies with machine learning in APM\u003c/h2\u003e\u003cp\u003eThe APM UI now integrates with machine learning to show anomalies in response times on transactions. This makes catching unexpected behavior in your services much easier by annotating critical anomalies on top of the response times graph. It’s a one-click setup in the APM UI to get the job running. Please note that the feature is beta in 6.4.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt22adc819dfed8db9/5fa98f2f65bdd35303e00a74/blog-kibana-6-4-0-8.png\" width=\"624\" height=\"244\" style=\"width: 624;height: 244;\"/\u003e\u003c/p\u003e\u003ch2\u003eNew query bar for searching and filtering APM data\u003c/h2\u003e\u003cp\u003eAdding a query will instantly apply to the data shown in graphs and tables, making the scope of the data immediately more focused. It comes with a handy autocomplete that helps find the fields and even provides suggestions to the data they include. This way you can easily filter for transaction response times higher than 2000 ms, a particular user ID, or even a response status code. Please note that the feature is beta in 6.4.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3dc749bd93ee47f4/5fa98f2fffb61e50a0faad3d/blog-kibana-6-4-0-9.png\" width=\"624\" height=\"264\" style=\"width: 624;height: 264;\"/\u003e\u003c/p\u003e\u003ch2\u003eLanding page for Elastic Maps Service\u003c/h2\u003e\u003cp\u003eThe Elastic Maps Service powers all geospatial visualizations for Kibana by serving up basemaps tiles and vector boundary layers, key features that are essential for visualizing geodata. The new landing page allows you to preview the data that is published by Elastic Maps Service, either as a map or as data.\u0026nbsp;\u003c/p\u003e\u003cp\u003eYou can do a text search for feature properties, or use your mouse to see the available properties for each feature. You can also use the landing page to download the vector data that is hosted by the Elastic Maps Service.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt401af1bedc075263/5fa98f2f4e40cf53001f50b9/blog-kibana-6-4-0-10.png\" width=\"624\" height=\"468\" style=\"width: 624;height: 468;\"/\u003e\u003c/p\u003e\u003ch2\u003eApply Vega filters to dashboard context\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 14px;\"\u003eVega now allows modifying filters and the time range in Kibana, by adding utility functions, that can be called in your signal handlers. Check the \u003ca href=\"https://github.com/elastic/kibana/pull/17586\"\u003ePR description\u003c/a\u003e for a description of the functions.\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eExperimental API docs\u003c/h2\u003e\u003cp\u003eThis release adds documentation for these experimental APIs:\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe \u003ca href=\"/guide/en/kibana/6.4/api.html\"\u003eKibana role management API\u003c/a\u003e enables you to control access to Kibana features and saved objects.\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eThe \u003ca href=\"/guide/en/kibana/6.4/logstash-configuration-management-api.html\"\u003eLogstash configuration management API\u003c/a\u003e allows you to programmatically integrate with the Logstash configuration management feature.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eKibana also provides documentation for the \u003ca href=\"/guide/en/kibana/6.4/saved-objects-api.html\"\u003esaved objects API\u003c/a\u003e, which allows you to manage Kibana saved objects, including dashboards, visualizations, and index patterns.\u003c/p\u003e","category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:18:25.275Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt29843bb98ba59a2a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:37:11.833Z","updated_at":"2018-10-11T05:37:11.833Z","content_type":"image/jpeg","file_size":"71803","filename":"blog-kibana-banner.jpg","title":"blog-kibana-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T15:49:05.384Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt29843bb98ba59a2a/5bbee187eb7e90a514e6e46b/blog-kibana-banner.jpg"},"markdown_l10n":"","publish_date":"2018-08-23T16:04:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"The 6.4 release of Kibana includes new features highlighted by the addition of sample data, the Elastic Maps service, experimental API docs, scripted field and saved object changes and many redesigned UIs.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt83342df3b2b2883d","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-10T10:13:19.103Z","updated_at":"2018-10-10T10:13:19.103Z","content_type":"image/png","file_size":"125966","filename":"kibana-image.png","title":"kibana-image.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:19:39.373Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt83342df3b2b2883d/5bbdd0bf6d5c9db27fe9985d/kibana-image.png"},"title":"Kibana 6.4.0 Released","title_l10n":"Kibana 6.4.0 Released","updated_at":"2025-03-10T11:40:44.957Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/kibana-6-4-0-released","publish_details":{"time":"2025-03-10T11:40:50.401Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7a2b3ad49e3f0772","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Introducing Index Sorting in Elasticsearch 6.0! Users can enjoy improved query time performance by storing documents on disk in a specific order at index time.","author":["bltdabf9b8408da96f6","blt92817206712cedcd"],"body_l10n":"\u003cp\u003eIn Elasticsearch 6.0 we’re introducing a new feature called Index Sorting. Users can now optimize Elasticsearch indexes to store documents on disk in a specific order. We’re very excited for Index Sorting, as it’s another useful tool in optimizing Elasticsearch performance!\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThrough this article, we’ll dive into a number of areas:\u003c/p\u003e\u003cul\u003e\u003cli\u003eLucene’s Index Sorting functionality\u003c/li\u003e\u003cli\u003eExamples where Index Sorting will improve query performance\u003c/li\u003e\u003cli\u003eCaveats to consider in using Index Sorting for time series data\u003c/li\u003e\u003cli\u003ePerformance considerations\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eIndex Sorting in Lucene\u003c/h2\u003e\u003ch3\u003eLucene’s IndexSorter\u003c/h3\u003e\u003cp\u003eMany years ago, Lucene introduced an offline tool known as the \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-2482\"\u003eIndexSorter\u003c/a\u003e. The IndexSorter copied a source index to a new destination index, and ordered the documents on disk based on a user specified order. At that time, because it was not possible to update the destination index directly, users of this feature had to re-build a sorted view every time new documents were added to the source index. The IndexSorter was the first attempt to provide a way to sort documents on disk, not at search time, but at index time.\u003c/p\u003e\u003cp\u003eWith index sorting, a new concept called “early termination” was introduced. Suppose for instance that you want to retrieve N documents sorted by date (date being a field in the index). If the index is sorted on disk by this date field it would be possible to “stop” the request after visiting the first N documents that match the query (since they are already in the order the user specified). This is what we call “early termination”. Early termination of a query can bring significant improvement to search response times, especially for sort-based queries, and led to the increased popularity of the IndexSorter tool among Lucene users. The static nature of the tool prevented its usage for indices with a lot of updates, which is why it was eventually replaced with a solution that allows incremental updates. Instead of doing a one-time sort of a static index, a new solution was proposed to sort documents at merge time.\u003c/p\u003e\u003ch3\u003eLucene improvements\u003c/h3\u003e\u003cp\u003eOriginally, Lucene indexed documents in the order they were received, and assigned each document an incremental (and internal) document id (assigned on a per segment basis). The first document indexed in a segment had a document id of 0, and so on. At search time, each segment is visited in document id order, to retrieve documents that match a user query. In order to retrieve the best N documents for a query, Lucene needs to visit every document matching the query across all segments. If the query matches millions of documents, retrieving only the best N would still require millions of documents to be visited.\u003c/p\u003e\u003cp\u003eA Lucene index creates a new segment whenever a refresh is triggered. This new segment contains all the documents that were added after the last refresh. When the segment is flushed it becomes visible to the searcher and new documents can appear in search results. Because refreshes occur constantly, the number of segments can easily explode in an index. Segment merges happen in the background to limit the number of segments from growing too large. Merges are triggered based on a policy that selects segments eligible for merging, the selected segments are then merged in a new segment that replaces the old segments. By default, the segment merge process copies documents from different segments to a new segment based on their internal document ids. In order to replace the static tool (the IndexSorter mentioned above), a \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-4752\"\u003enew merge policy was introduced\u003c/a\u003e to allow index sorting for dynamic indices that reorders documents during the merge process based on a configurable order (the value of a field for instance). This new design was a huge step in the right direction, and allowed an index to be sorted on the fly and to use this information on a per-segment basis. Some segments are sorted (segments created by a merge) and some are not (the newly flushed segments). At merge time, the unsorted segments are first “sorted” and then merged with other sorted segments.\u003c/p\u003e\u003cp\u003eThis merge policy that lived in a module was then moved to a top-level option on the IndexWriterConfig to make index sorting a \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-6766\"\u003efirst class citizen\u003c/a\u003e in Lucene.\u003c/p\u003e\u003cp\u003eThough some benchmarks showed that the cost of sorting at merge time can divide the total throughput of indexation by a factor of 2:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta924260b54220c12/5fa9877924612d7400da3968/blog-index-sort-6-1.png\" width=\"624\" height=\"212\" alt=\"Screen Shot 2017-08-10 at 10.16.39 AM.png\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);\"/\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://home.apache.org/~mikemccand/lucenebench/sparseResults.html#index_throughput\"\u003ehttps://home.apache.org/~mikemccand/lucenebench/sp...\u003c/a\u003e\u003c/p\u003e\u003cp\u003eThe reason for the reduction in indexing performance is simple: re-sorting segments has a cost, causing merge time and memory consumption for these indices to increase by a large factor.\u003c/p\u003e\u003cp\u003eSince re-sorting multiple segments at a time is costly, we decided to sort documents earlier in the indexation process. Instead of waiting for merge times to sort multiple segments, we’ve moved the sorting to flush time (when the segments are first created): \u003ca href=\"https://issues.apache.org/jira/browse/LUCENE-7579\"\u003eLUCENE-7579.\u003c/a\u003e If all segments are already sorted, merging can occur using a simple merge-sort strategy, which is much faster. This new strategy was first introduced in Lucene 6.5 and increased the throughput benchmarks by almost 65% (see annotation V).\u003c/p\u003e\u003cp\u003eAs you can see in this story index sorting had a lot of history in Lucene but until now it was not available in Elasticsearch. Thanks to all these optimizations, we’ve decided to unlock this feature in Elasticsearch 6.0 and we’re really excited to show how this feature can help you to optimize your use case with this new release!\u003c/p\u003e\u003ch2\u003eIndex Sorting in Action\u003c/h2\u003e\u003ch3\u003eEarly termination of search queries\u003c/h3\u003e\u003cp\u003eIt’s very common in applications to query for the top X results, sorted by value Y (top player scores, new users, latest events, etc.). In most cases, Elasticsearch will not have enough information to quickly gather the first X results and sort them until the entire data set has been examined. Doc values make this process more efficient, however, in the cases where the dataset is extremely large, a lot more values will be examined and compared than are needed by the user.\u003c/p\u003e\u003cp\u003eWith the introduction of index sorting in Elasticsearch 6.0, we can now specify the ordering of documents on disk, allowing Elasticsearch to short circuit and return queries more efficiently. For instance, if we’re creating a leaderboard for a video game company to track the top 3 player scores (and we have a very large number of players!), we can instruct Elasticsearch to store documents in the order of their player score, allowing us to compute the leaderboard much more efficiently.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb218fa68545af041/5fa98780ffb61e50a0faacfb/blog-index-sort-6-2.jpg\" width=\"624\" height=\"187\" alt=\"leaderboard.jpg\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e// Get the top 3 player scores (based on the number of points)\u003cbr /\u003eGET scores/score/_search\u003cbr /\u003e{\u003cbr /\u003e \"size\": 3,\u003cbr /\u003e \"sort\": [\u003cbr /\u003e { \"points\": \"desc\" }\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eDepending on the version of Elasticsearch, and on usage of index sorting, we can store the documents on disk very efficiently for the query above:\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;font-family: Arial;color: rgb(0, 0, 0);background-color: transparent;vertical-align: baseline;white-space-collapse: preserve;text-wrap-mode: wrap;\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/599b0598949407fa18d59c85/download?uid=blt3a1f0c3350489703\" data-sys-asset-uid=\"blt3a1f0c3350489703\" alt=\"first_diag.png\"/\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThe query above will still need to return a count for the number of results (and requires a little extra work). We can remove this requirement with the new option \"track_total_hits\"\u0026nbsp;set to false:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e// Get the top 3 player scores (based on the number of points)\u003cbr /\u003eGET scores/score/_search\u003cbr /\u003e{\u003cbr /\u003e \"size\": 3,\u003cbr /\u003e \"track_total_hits\" : false,\u003cbr /\u003e \"sort\": [\u003cbr /\u003e { \"points\": \"desc\" }\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe now have a very efficient leaderboard query for top player scores, using a sorted index.\u003c/p\u003e\u003ch3\u003e\u003c/h3\u003e\u003ch3\u003eSpecifying an index sorting order in Elasticsearch 6.0\u003c/h3\u003e\u003cp\u003eTo continue with our example above (creating a leaderboard of top player scores), we will need to tell Elasticsearch how to order the documents on disk. We can do this by providing a definition in the settings for the index:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT scores\u003cbr /\u003e{\u003cbr /\u003e \"settings\" : {\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"sort.field\" : \"points\", \u003cbr /\u003e \"sort.order\" : \"desc\" \u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"mappings\": {\u003cbr /\u003e \"score\": {\u003cbr /\u003e \"properties\": {\u003cbr /\u003e \"points\": {\u003cbr /\u003e \"type\": \"long\"\u003cbr /\u003e },\u003cbr /\u003e \"playerid\": {\u003cbr /\u003e \"type\": \"keyword\"\u003cbr /\u003e },\u003cbr /\u003e \"game\" : {\u003cbr /\u003e \"type\" : \"keyword\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe example above will sort documents on disk by the points field (in descending order). This is helpful for the simple query above (for top 3 player scores).\u0026nbsp;\u003c/p\u003e\u003ch3\u003eGrouping documents within an index by similar structure\u003c/h3\u003e\u003cp\u003eThere are many advantages to storing documents sorted by a similar type. For instance, if there is an index named “scores”, some scores may come from the game “Joust”, and include specific fields such as “top-speed” and “farthest-jump”, a score for a different game, such as “Dragon’s Lair” may include fields for “sword-fight-score” and “goblins-killed”:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e// Score for the game \"Joust\"\u003cbr /\u003e{\u003cbr /\u003e \"game\" : \"joust\",\u003cbr /\u003e \"playerid\" : \"1234\",\u003cbr /\u003e \"top-speed\" : 212,\u003cbr /\u003e \"farthest-jump\" : 49\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cpre class=\"prettyprint\"\u003e// Score for the game \"Dragon’s Lair\"\u003cbr /\u003e{\u003cbr /\u003e \"game\" : \"dragons-lair\",\u003cbr /\u003e \"playerid\" : \"5678\",\u003cbr /\u003e \"sword-fight-score\" : 89,\u003cbr /\u003e \"goblins-killed\" : 3\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eStoring the documents on disk sorted by game will help place similar documents (with similar field names) together. The advantages to this are query speed (although it’s important to remember this really depends on the query) and compression. Storing similar fields closer together may lead to better compression, and Elasticsearch (and in turn Lucene) is able to store the deltas more efficiently:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT scores\u003cbr /\u003e{\u003cbr /\u003e \"settings\" : {\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"sort.field\" : \"game\", \u003cbr /\u003e \"sort.order\" : \"desc\" \u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eMore efficient AND conjunctions\u003c/h3\u003e\u003cp\u003eUsing index sorting to locate documents on disk in a specific order can also \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/index-modules-index-sorting-conjunctions.html\"\u003eimprove AND conjunctions\u003c/a\u003e, complex queries with many conditions.\u003c/p\u003e\u003cp\u003eLet’s continue with our video game example, when a player joins a game, they must be paired up with another player in the same region, skill level, and course. A sample query to find similar players for starting a new match may look similar to the following (get 10 players within the \"EU\"\u0026nbsp;region, playing \"Dragon’s Lair\", with a skill rating of 9, and at the \"Castle\" map):\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eGET players/player/_search\u003cbr /\u003e{\u003cbr /\u003e \"size\": 3,\u003cbr /\u003e \"track_total_hits\" : false,\u003cbr /\u003e \"query\" : { \u003cbr /\u003e \"bool\" : {\u003cbr /\u003e \"filter\" : [\u003cbr /\u003e { \"term\" : { \"region\" : \"eu\" } },\u003cbr /\u003e { \"term\" : { \"game\" : \"dragons-lair\" } },\u003cbr /\u003e { \"term\" : { \"skill-rating\" : 9 } },\u003cbr /\u003e { \"term\" : { \"map\" : \"castle\" } } \u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eLet's look at how the Elasticsearch may gather the results needed for the query:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/599616921eff86ee22016a11/download?uid=blt9aa0104633a60b1f\" data-sys-asset-uid=\"blt9aa0104633a60b1f\" alt=\"new_query_without.png\"/\u003e\u003c/p\u003e\u003cp\u003eNow, let's specify the ordering of the documents on disk to improve our query above:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT players\u003cbr /\u003e{\u003cbr /\u003e \"settings\" : {\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"sort.field\" : [\"region\", \"game\", \"skill-rating\", \"map\"], \u003cbr /\u003e \"sort.order\" : [\"asc\", \"asc\", \"asc\", \"asc\"] \u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"mappings\": {\u003cbr /\u003e \"player\": {\u003cbr /\u003e \"properties\": {\u003cbr /\u003e \"playerid\": {\u003cbr /\u003e \"type\": \"keyword\"\u003cbr /\u003e },\u003cbr /\u003e \"region\": {\u003cbr /\u003e \"type\": \"keyword\"\u003cbr /\u003e },\u003cbr /\u003e \"skill-rating\" : {\u003cbr /\u003e \"type\" : \"integer\"\u003cbr /\u003e },\u003cbr /\u003e \"game\" : {\u003cbr /\u003e \"type\" : \"keyword\"\u003cbr /\u003e },\u003cbr /\u003e \"map\" : {\u003cbr /\u003e \"type\" : \"keyword\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe can now see the documents are placed closer together:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/5996174b2d8186e8071aa7e5/download?uid=blt79a4bd69300b6a4c\" data-sys-asset-uid=\"blt79a4bd69300b6a4c\" alt=\"new_query_with2.png\"/\u003e\u003c/p\u003e\u003cp\u003eBy using a sorted index, we can locate the documents with\u0026nbsp;similar field\u0026nbsp;values closer together, making our query to find players for a given match more efficient.\u003c/p\u003e\u003ch3\u003eWhen index sorting isn't a good fit\u003c/h3\u003e\u003cp\u003eStoring sorted values on disk requires a lot more work at index time from Elasticsearch than storing unsorted values. In some cases the performance overhead of index sorting can decrease write performance by as much as 40-50%. For this reason it is very important to determine if the application should be optimized for query performance or write performance. Optimizing an application for write performance (and taking the hit on query performance) will most likely mean index sorting is not a good option.\u003c/p\u003e\u003cp\u003eYou can check the throughput for indexation with and without index sorting. As mentioned above, the performance hit will vary widely and depend on your use case. For example, the geonames Elasticsearch benchmark shows a very small performance hit for Index Sorting (the blue line labeled “Append Sorted”):\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltabbe6b882b3ff86d/5fa9878142256d5ffdf418a3/blog-index-sort-6-3.png\" width=\"624\" height=\"340\" alt=\"Screen Shot 2017-08-10 at 1.11.12 PM.png\" style=\"width: 624;height: 340;\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://elasticsearch-benchmarks.elastic.co/index.html#tracks/geonames/nightly/30d\"\u003ehttps://elasticsearch-benchmarks.elastic.co/index....\u003c/a\u003e\u003c/p\u003e\u003cp\u003eAlternatively, the “NYC Taxis” benchmark shows a large drop in indexing performance with index sorting:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte19365eb5b04302c/5fa9877a09ed4c6f277eb5f6/blog-index-sort-6-4.png\" width=\"624\" height=\"339\" alt=\"Screen Shot 2017-08-10 at 1.12.42 PM.png\" style=\"width: 624;height: 339;\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://elasticsearch-benchmarks.elastic.co/index.html#tracks/nyc-taxis/nightly/30d\"\u003ehttps://elasticsearch-benchmarks.elastic.co/index....\u003c/a\u003e\u003c/p\u003e\u003cp\u003eIn system design, there are tradeoffs at almost every level, with index sorting, the tradeoff we’re considering is less efficient writes (as the document must be sorted) for faster queries (in specific scenarios) vs more efficient writes and slower queries (as the results must be sorted at query time).\u003c/p\u003e\u003cp\u003eSimilar to any new feature, it is very important to test index sorting with your specific use case and dataset.\u003c/p\u003e\u003ch2\u003eWe’re not finished\u003c/h2\u003e\u003cp\u003eThis is only the beginning, we’ll continue to improve index sorting for a larger range of use cases!\u003c/p\u003e\u003cp\u003eHopefully this article gives you a good overview of index sorting as a great new tool to consider in your Elasticsearch 6.0 toolbox. In addition to this blog post, the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/index-modules-index-sorting.html\"\u003edocumentation on Index Sorting\u003c/a\u003e can be a great resource to bookmark. If you want to try out the new index sorting functionality, download \u003ca href=\"https://www.elastic.co/blog/elasticsearch-6-0-0-beta1-released\"\u003e6.0.0-beta1\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/blog/elastic-pioneer-program-6-0\"\u003ebecome a pioneer\u003c/a\u003e!\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:27:33.905Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt2687e8f094c63672","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-15T07:15:30.543Z","updated_at":"2018-10-15T07:15:30.543Z","content_type":"image/png","file_size":"4275","filename":"sorting-leaderboard.png","title":"sorting-leaderboard.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:46:10.577Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2687e8f094c63672/5bc43e929264e07113847db5/sorting-leaderboard.png"},"markdown_l10n":"","publish_date":"2017-08-21T15:56:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt8aa2f12f523f80cb","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-15T07:15:20.246Z","updated_at":"2018-10-15T07:15:20.246Z","content_type":"image/png","file_size":"2670","filename":"index-sorting-img.png","title":"index-sorting-img.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:46:10.577Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8aa2f12f523f80cb/5bc43e88c93e69af7fbf97f6/index-sorting-img.png"},"title":"Introducing Index Sorting in Elasticsearch 6.0","title_l10n":"Introducing Index Sorting in Elasticsearch 6.0","updated_at":"2025-03-10T11:37:54.792Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/index-sorting-elasticsearch-6-0","publish_details":{"time":"2025-03-10T11:37:59.015Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt93b70002148168a5","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"This is Part II of a series on PSD2 in which we will focus on creating “observability” in a public API architecture.","author":["blt8bf5cf20b113d800"],"body_l10n":"\u003cp\u003eAt Elastic, we :heart: APIs because developers love to work with them to get things done. APIs also have the power to change (or disrupt) an industry quickly and decisively, as is the case with The Revised Payment Service Directive (PSD2). APIs make it possible to seemlessly switch from Web browsers to apps, to deploy content to any platform, and to find the best deals among thousands of suppliers. PSD2 sets out to standardize APIs between EU banks and abolish the existing lock-ins that still exist in the industry. Because while financial institutions are closer to the forefront of the innovation curve than almost any other industry, the point can be made that this has not resulted in wide-spread open access to the core banking ecosystems - namely accounts and transactions. PSD2 is a directive from the European Union that will make banks open up access to their, otherwise private, core banking functions in ways that we have not seen before. PSD2 legislation introduces a breadth of opportunity for retail banks, while also introducing new risk. The Elastic Stack plays a vital role in many of the world’s banks today, and that will especially be true for PSD2 architectures.\u003c/p\u003e\u003cp\u003eThis is Part II of a series on PSD2 in which we will focus on creating “observability” in a public API architecture, that is to say at all times knowing the status of the business service, its anomalies that require attention and all historical raw data around individual users and requests. \u003ca href=\"/blog/psd2-architectures-with-the-elastic-stack\"\u003ePart I\u003c/a\u003e focuses on using the Elastic Stack for running next-generation retail banking APIs and also gives a general introduction of PSD2 regulation and strategic options for EU retail banks.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cdl\u003e\u003cdt\u003eObservability\u003c/dt\u003e\u003cdd\u003e“Seeing” all that is happening in a complex architecture. Three distinct but related types of data emerged: Logs, Traces, and Metrics.\u003c/dd\u003e\u003c/dl\u003e\u003cdl\u003e\u003cdt\u003eLogs\u003c/dt\u003e\u003cdd\u003eRecords of discrete events. Often a combination of text and numerical data. Examples: an API request, a transaction error.\u003c/dd\u003e\u003c/dl\u003e\u003cdl\u003e\u003cdt\u003eTraces\u003c/dt\u003e\u003cdd\u003eInformation related to a specific request. Examples: database queries related to a request, or a stack trace of a microservice. Traces look a lot like Logs, but are more verbose and specific to a single action. For simplicity, we will group Traces and Logs together in this article.\u003c/dd\u003e\u003c/dl\u003e\u003cdl\u003e\u003cdt\u003eMetrics\u003c/dt\u003e\u003cdd\u003eRecords of observations on a timeline interval. Aggregatable into higher-level KPIs and usually numerical. Examples: CPU usage, number of transactions.\u003c/dd\u003e\u003c/dl\u003e\u003ch2\u003eA Shopping List\u003c/h2\u003e\u003cp\u003eAt Elastic we get to see many customers running production, value-add installations, the successful deployments provide the business with a platform to leverage for insight. The commonality that can be extracted from these installations include but are not limited to:\u003c/p\u003e\u003col\u003e\u003cli dir=\"ltr\"\u003e\u003cstrong\u003eSecurity and Privacy: \u003c/strong\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cstrong\u003eThis includes corporate and legislative requirements around audit logging, privacy, multi-tenancy, encryption at e and data separation. Running public APIs that give access to funds and transaction histories will be a prima target for bad actors.\u003c/strong\u003e\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cstrong\u003eMonitoring and Alerting: \u003c/strong\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003eThe ability to know current and historical status of the service, and be informed of any serious deviations from what is considered normal. We expect SLAs to apply to these services that will demand intelligent monitoring of the whole architecture. \u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003eCorrelation of metrics and logs is vital\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003e to quickly understand what actions to take.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cstrong\u003eQuality of Service: \u003c/strong\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003eThe ability to throttle in case of overloads, to protect itself from DDoS attacks and to allow the enforcement of Fair Use policies on the public APIs.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cstrong\u003eEasy, far-reaching scalability: \u003c/strong\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003eScaling the platforms should be simple and painless.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cstrong\u003eReal-time answers: \u003c/strong\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003eAnswer calls fast to support the needs and expectations of users, throughout the solution.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cstrong\u003eSelf-learning and self-service: \u003c/strong\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 400;vertical-align: baseline;white-space: pre-wrap;\"\u003eGetting useful intelligence out of the data without having to foresee and manages what exactly is relevant (because who would know beforehand how security breaches or outages might unfold?) requires abilities to find anomalies, create advanced dashboards, and a raw data store. It also requires tooling that enables non-techies to get what they need through self-service BI.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\" rel=\"line-height:1.38;margin-top:18pt;margin-bottom:6pt;\"\u003eThe Elastic Stack for Logging and Metrics\u003c/h2\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/59e4cf4265db43d1714179e5/download?uid=blt01bc63a2f3bcb482\" data-sys-asset-uid=\"blt01bc63a2f3bcb482\" alt=\"Screen Shot 2017-10-16 at 17.24.21.png\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eAt the highest level, Elastic is functioning as the data platform for all logs, metrics, and traces that are generated in the Elastic data platform. A separate cluster will ensure separation of resources and data. Data agents generate and collect relevant data into a pipeline that transforms the data before ingesting it into a permanent data store. From ingestion, that data is immediately available for automated and manual analytics: machine learning, dashboarding, ad-hoc queries, and the likes.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eThe Elastic Stack for Logging and Metrics\u003c/h2\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/59e4cfafaa78dca571c320be/download?uid=blt24506b4eaeaacc3c\" data-sys-asset-uid=\"blt24506b4eaeaacc3c\" alt=\"Screen Shot 2017-10-16 at 17.26.10.png\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eMore specifically, the logical architecture looks like pictured above. The Elastic Stack offers a complete suite of products for API observability architectures:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eBeats\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e is a platform for lightweight shippers that send data from edge machines to Logstash and Elasticsearch.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eLogstash\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e is a dynamic data collection pipeline with an extensible plugin ecosystem and strong Elasticsearch synergy.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eElasticsearch\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e is a distributed, REST API enabled, JSON-based search and analytics engine designed for horizontal scalability, maximum reliability, and easy management.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eKibana\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e gives shape to your data and is the extensible user interface for configuring and managing all aspects of the Elastic Stack.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eX-Pack\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e is a single extension that integrates handy features — security, alerting, monitoring, reporting, graph exploration, and machine learning\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eThe Elastic Stack logical architecture for Observability combines all these products into an end to end platform with accompanying services, like Consulting and Expert Support. As you have probably read a bunch of times by now, Elastic :heart: APIs. That is why the Elastic Stack products natively supports REST API endpoints for easy integration into any architecture.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eKeeping an Eye on Things, All Things\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cstrong\u003eLog events\u003c/strong\u003e are composed of documents in the 1st Normal Form (1NF), usually with a timestamp. 1NF is important to achieve linear scalability: it is not feasible to arbitrarily join multiple datasets of hundreds of terabytes while the user or a real-time process is waiting for the answer. Of course, it’s a good idea to join those datasets at time of ingestion! That still allows us to scale to billions of events per day without slowing down.\u003c/p\u003e\u003cp\u003eMillions of similar events will stream into the Elastic platform using the Elastic Beats data agent towards Logstash, Elastic’s data processing product. Logstash will be able to enrich, lookup, filter and transform the data in transit before storing it in Elasticsearch. After Logstash, the same document might look like this. It has relevant information added to it that will help the observability of what is actually happening on our APIs. Bold fields added by Logstash. There is ample opportunity to add in any business logic.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:5pt;margin-bottom:0pt;\"\u003eA simplified, enriched event log describing a single API call, in JSON format, after enrichment with GeoIP information and a threat score:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e[{\u003cbr /\u003e \"timestamp\": \"2018-01-05T18:25:43.512Z\",\u003cbr /\u003e \"http_method\": \"GET\",\u003cbr /\u003e \"request\": \"transactions/latest\",\u003cbr /\u003e \"result\": 200,\u003cbr /\u003e \"error\": null,\u003cbr /\u003e \"ip\": \"123.123.123.123\",\u003cbr /\u003e \"geoip_fields\": {\u003cbr /\u003e \"country_iso_code\": \"NL\",\u003cbr /\u003e \"city_name\": \"Rotterdam\",\u003cbr /\u003e \"location\": { \"lat\": 51.922755, \"lon\": 4.479196 }\u003cbr /\u003e // other fields omitted\u003cbr /\u003e }\u003cbr /\u003e \"user\": \"Alice\",\u003cbr /\u003e \"user_last_login\": \"2018-01-01T16:40:09.938Z\",\u003cbr /\u003e \"threat_score\": 0.042,\u003cbr /\u003e \"authentication_method\": \"app_fingerprint\",\u003cbr /\u003e ... // other fields omitted\u003cbr /\u003e}]\u003cbr /\u003e\u003c/pre\u003e\u003cblockquote\u003eWhen we pre-filter, pre-aggregate or otherwise remove data before our data store, we will, by definition, lose an unknown amount of information.\u003c/blockquote\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eElasticsearch will take billions of logs and metrics to provide you an unobstructed view of what is actually happening, in real-time. Kibana sits on top of the stack to discover data and manage Elastic components. This is where scalability becomes important. When we pre-filter, pre-aggregate or otherwise remove data before our data store, we will, by definition, lose observability. Luckily, the Elastic Stack can take on any workload, even if you turn out to be the largest retail bank of the globe.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003ePoint Solutions for Logs, Metrics, Metrics\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eA number of point solutions for a subset of the desired functionality are available, often closed source and not seldom including a form of vendor lock-in. Apart from added complexity in buying, deploying and operating multiple systems where one can suffice, the real problem is the additional overhead of having to deal with multiple ‘truths’ at the same time. While attackers are rampaging through the system, or outages are hampering performance, your SecOps and DevOps might be manually correlating the “logging solution” output, with the “metrics solution” output, possibly demanding another tool to overlay on the said point solutions. And while some integration options are usually available, some of these \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003esolutions\u003c/span\u003e do not expose their raw data willingly.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eElastic clears these issues completely, by bringing together what should be together.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eScaling Up Within Budget\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eSo, now that we have established the need to \u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003esave all data\u003c/span\u003e and keep it in a real-time data store for enough time to be able to train Machine Learning jobs, understand longer-term patterns of behavior, and investigate interesting events. \u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eNo one knows what data will become valuable later.\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eHow do we keep costs at bay? Elastic has support for several advanced strategies:\u003c/p\u003e\u003col\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eMulti-tier (or hot/warm) architecture:\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e allocate data in tiers (hot, warm, tapid?) and designate data nodes to exist in one of those tiers. It allows read and write separation (only hot data gets written to), and most importantly an option to store more data on a warm node, allowing a slight performance degradation for older data while saving infrastructure costs at the same time.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eIncrease compression\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e on older data\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eOptimize data for Warm Archive:\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e this goes a bit ‘under the hood’, but there are a number of actions you can take on your older shards to optimze them for reading in a Warm zone: Merge Segments, Shrink to less Shards\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eA multi-tier data architecture looks like this:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/59e4d0fda32c30ab71e2c356/download?uid=blt11c66e6503b522c1\" data-sys-asset-uid=\"blt11c66e6503b522c1\" alt=\"Screen Shot 2017-10-16 at 17.31.48.png\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eMonitoring a World-Class API Service\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 5pt;\"\u003eAll these provide their own perspective on what is happening in the system. So it helps to keep them in the same place. This is where the agnostic nature of Elastic shines: it really does not limit the types of data that can be used on it. You can happily aggregate metrics into KPIs on dashboards, alongside frequent errors taken from log files, with stack traces on the same data store so that DevOps Engineers can dive into anything interesting in seconds.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 5pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfcec5c8ee8f6289d/5fa9833665bdd35303e00a28/blog-psd2-2-1.png\" width=\"526\" height=\"278\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eKibana makes it possible for everyone to create the most relevant perspective on the data, and share those visualizations, dashboards, graphs and machine learning jobs with the organization. Or just keep it for themselves.\u003c/p\u003e\u003ch3 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 4pt;\"\u003eThe (Un)known (Un)knowns with X-Pack Machine Learning\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eSelf-learning anomaly detection is all about tackling both \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003eknowns\u003c/span\u003e and \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003eunknowns\u003c/span\u003e. We believe that even if nobody has predicted something \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003ecould\u003c/span\u003e happening, does not mean it’s not relevant if it \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003edoes\u003c/span\u003e. At the same time, you probably have other things to do than create alerts for anything that you know \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003ecould\u003c/span\u003e happen.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eSolutions for…\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eKnown knowns: \u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003eif an API gets overloaded, we will be in a lot of trouble. We know exactly what to look for, and when to let the alarms go off.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eKnown unknowns:\u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e we know that users will use our APIs today, but we do not know how many. We can use history to guide us, but we cannot be exact. If we see something “out of the ordinary”, it’s probably worth a look by a human. At least we know what KPIs and metrics are relevant.\u003c/span\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;font-weight: 700;vertical-align: baseline;white-space: pre-wrap;\"\u003eUnknown unknowns: \u003c/span\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003ewe acknowledge that something might popup at any moment that disrupts our systems, our business. Like a new security vulnerability. We cannot predict which KPIs or metrics will be relevant, but we do know that as long as wel have good observability, the data will have the information we need. If we only know what to look for.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eKnown knowns we can easily cover with X-Pack Alerting. It uses pre-defined boundaries of what is “OK” and what is “not OK.” It will respond in real-time to anything in the known known department. The other two need something more.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eEnter X-Pack Machine Learning. It will learn from history to predict the future, and tell you when something is not right, including the associated probabilities. It covers both known unknowns and unknown unknowns by looking holistically at all the data. At the same time, it’s so easy that a kid can use it, freeing up time from your people with the “sexiest jobs of the 21st century” (Harvard Business Review) to work on other, more complex challenges.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb06d502ff8a4103/5fa98336ffb61e50a0faacdd/blog-psd2-2-2.gif\" width=\"624\" height=\"351\" alt=\"machine-learning-final.gif\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch3 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 16pt;margin-bottom: 5pt;\"\u003eTraces, or action-specific logs\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eAnd of course, you’ll be able to dive into anything interesting or suspicious. Across your infrastructure and application stack. Any information that you have made available about a single request (or many!) is right in front of you.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;text-align: center;\"\u003e\u003cspan style=\"font-size: 10pt;background-color: transparent;vertical-align: baseline;white-space-collapse: preserve;text-wrap-mode: wrap;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte713a5eca5f2fcf3/5fa9833742256d5ffdf41887/blog-psd2-2-3.png\" width=\"624\" height=\"236\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);display: block;margin: auto;\"/\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eWe would love to talk to you some more, but our time is running out. Some good reads on IT Operations Analytics with the Elastic Stack:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.elastic.co/blog/using-elasticsearch-and-machine-learning-for-it-operations\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eBlog: Using Elastic and Machine Learning for IT Operations\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.elastic.co/webinars/elastic-for-operational-analytics\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eWebinar: Elastic for Operational Analytics\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.elastic.co/elasticon/tour/2015/amsterdam/connecting-the-dots-with-elasticsearch-tracing-of-events-within-ing\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eTalk: Tracing of Events within ING Bank\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.youtube.com/watch?v=mqEqBN0_Lnc\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eVideo: 8 Minutes on IT Operations with Machine Learning Demo\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 16pt;margin-bottom: 4pt;\"\u003eFinding Bad Guys\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIn security as well as with IT operations, we can utilize X-Pack Machine Learning to find unusual patterns in all of our data, with quantitative and qualitative algorithms.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2906e295760102a9/5fa9833009ed4c6f277eb5ce/blog-psd2-2-4.png\" width=\"624\" height=\"268\" style=\"width: 624;height: 268;\"/\u003e\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:5pt;margin-bottom:0pt;\"\u003eShould we spot suspicious activity, we can utilize X-Pack Graph to create connections between data points and traverse the logs using algorithms that put the \u003cspan style=\"font-size: 11pt;background-color: transparent;font-style: italic;vertical-align: baseline;white-space: pre-wrap;\"\u003erelevance\u003c/span\u003e first, the popularity second. This is an excellent way to weed out noise that could otherwise interfere with our observability.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:5pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;text-align: center;\"\u003e\u003cspan style=\"font-size: 10pt;background-color: transparent;vertical-align: baseline;white-space-collapse: preserve;text-wrap-mode: wrap;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt16dd1da81d53cac6/5fa9832f46f622769b5ec843/blog-psd2-2-5.png\" width=\"395\" height=\"340\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);display: block;margin: auto;\"/\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eWe would love to talk to you some more, but this blog is not meant as a comprehensive discussion of how to do API Security Analytics. Luckily, such resources already exist. Some good reads on Security Analytics with the Elastic Stack:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.elastic.co/blog/integrating-elasticsearch-with-arcsight-siem-part-6\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eBlog Series: Integrating Elastic with ArcSight SIEM\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.elastic.co/webinars/automated-anomaly-detection-with-machine-learning\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eWebinar: Automated Anomaly Detecting with Machine Learning\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.youtube.com/watch?v=Qd9UZWxbLFw\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eVideo: 6 Minutes on Security Analytics with Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 16pt;margin-bottom: 4pt;\"\u003eExpand Your Horizon with APM\u003c/h3\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eAdding APM (Application Performance Monitoring) to the Elastic Stack is a natural next step in providing our users with end-to-end monitoring, from logging, to server-level metrics, to application-level metrics, all the way to the end-user experience in the browser or client. It allows for more visibility of the operations of your APIs. APM is currenty in Alpha and hence not quite ready for production today. However, as new, exciting innovations go, it’s worth taking a look at it today!\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5bdbcb0b4be6ea9a/5fa98337fd99385ff6003c78/blog-psd2-2-6.png\" width=\"624\" height=\"353\" style=\"border-width: initial;border-style: none;transform: rotate(0rad);display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003eSome good reads on the upcoming APM module of the Elastic Stack:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003e\u003ca href=\"https://www.elastic.co/blog/starting-down-the-path-for-elastic-apm\"\u003e\u003cspan style=\"font-size: 11pt;background-color: transparent;text-decoration-line: underline;vertical-align: baseline;white-space: pre-wrap;\"\u003eBlog: Starting Down the Path of APM for the Elastic Stack\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 5pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 9pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003eIcons made by Freepik from flaticon.com\u003c/span\u003e\u003c/p\u003e\u003cdiv\u003e\u003cspan style=\"font-size: 9pt;background-color: transparent;vertical-align: baseline;white-space: pre-wrap;\"\u003e\u003cbr /\u003e\u003c/span\u003e\u003c/div\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:28:18.934Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"psd2-architectures-elasticsearch-fullbleed.jpg","uid":"blte6583088ad57a933","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T10:09:29.607Z","updated_at":"2019-01-05T10:09:29.607Z","content_type":"image/jpeg","file_size":"165387","filename":"psd2-architectures-elasticsearch-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T19:59:56.128Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte6583088ad57a933/5c30825929d13af10bc2ac92/psd2-architectures-elasticsearch-fullbleed.jpg"},"markdown_l10n":"","publish_date":"2017-10-24T16:57:49.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"psd2-architectures-elasticsearch-fullbleed.jpg","uid":"blte6583088ad57a933","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T10:09:29.607Z","updated_at":"2019-01-05T10:09:29.607Z","content_type":"image/jpeg","file_size":"165387","filename":"psd2-architectures-elasticsearch-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T19:59:56.128Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte6583088ad57a933/5c30825929d13af10bc2ac92/psd2-architectures-elasticsearch-fullbleed.jpg"},"title":"PSD2: Monitoring Modern Banking API Architectures with the Elastic Stack, Part II","title_l10n":"PSD2: Monitoring Modern Banking API Architectures with the Elastic Stack, Part II","updated_at":"2025-03-10T11:35:51.180Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/psd2-architectures-with-the-elastic-stack-part-ii","publish_details":{"time":"2025-03-10T11:35:57.678Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1869f3e94e545dd7","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"How Elastic engineers and staffers are supporting the Unicode Consortium's Adopt-a-Character program, and why you should donate!","author":["blt2494922cd45b66e9","bltd3e6819c090469cd"],"body_l10n":"\u003cp\u003eThe \u003ca href=\"http://unicode.org/\" target=\"_blank\"\u003eUnicode Consortium\u003c/a\u003e is a non-profit corporation founded in 1991. Its goals include standardizing and supporting the languages of the world and allowing people to use any language on their computers and smartphones.\u003c/p\u003e\u003cp\u003eThis work is essential for the software we build at Elastic. Unicode does more than just list out all the characters. They describe how to parse text, how to sort in different languages, and so much more to support all human languages.\u003c/p\u003e\u003cp\u003eThe Unicode Consortium's \u003ca href=\"http://blog.unicode.org/2015/12/unicode-launches-adopt-character.html\" target=\"_blank\"\u003eAdopt-a-Character program\u003c/a\u003e raises money to support a variety of important missions. Conserving the world's living languages is a huge task, and includes working with language experts, technologists, and cultural leaders, all in order to support minority languages on computers.\u003c/p\u003e\u003cp\u003eAccording to Unicode, close to 98 percent of our world's living languages are digitally disadvantaged. This means that operating systems, web browsers and mobile applications don't support them. So the Adopt-a-Character donations help Unicode — a neutral organization\u0026nbsp;interested in language conservation and technological standardization — to drive the work to correct this. They plan to focus use of the funds on adding characters for both modern and historic disadvantaged languages, and to support internationalization for those languages (\u003ca href=\"http://cldr.unicode.org/\" target=\"_blank\"\u003eCLDR\u003c/a\u003e and \u003ca href=\"https://en.wikipedia.org/wiki/International_Components_for_Unicode\" target=\"_blank\"\u003eICU\u003c/a\u003e).\u003c/p\u003e\u003cp\u003eWhen Elastic Founder and CTO \u003ca href=\"https://twitter.com/kimchy\"\u003eShay Banon\u003c/a\u003e found out about the adoption program, he had a cool idea: why not allow every engineer at Elastic (as well as other teammates within the company) to choose and adopt a character?\u003c/p\u003e\u003cp\u003eBesides supporting a good cause, it tells us a bit about every engineer on our team! Here's what we chose:\u003c/p\u003e\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003cth width=\"25%\"\u003e\u003cp\u003e\u003cstrong\u003eCharacter Adopted\u003c/strong\u003e \u003c/p\u003e\u003c/th\u003e\u003cth width=\"75%\"\u003e\u003cp\u003e\u003cstrong\u003eWho and Why\u003c/strong\u003e\u003c/p\u003e\u003c/th\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7212798d8e381ffc2d/download?uid=bltde28a09b63a94dd6?uid=bltde28a09b63a94dd6\" data-sys-asset-uid=\"blt1e18067c622301b4\" alt=\"gold-007B.png\"/\u003e and \u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d71d8edd48f769384a0/download?uid=blte01bbb4961d8c5b9?uid=blte01bbb4961d8c5b9\" data-sys-asset-uid=\"bltb6083c2951d50b29\" alt=\"gold-007D.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eElastic loves the curly braces — and it's a great cause. :) (Suggested by Brandon Mensing, Product Management, Strategy)\u003cbr /\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d77d8edd48f7693859d/download?uid=blt2952366a472080f9?uid=blt2952366a472080f9\" data-sys-asset-uid=\"blt83d45881ff25800c\" alt=\"elastic-unicode-curly-braces-awards.jpg\" width=\"420\" height=\"252\" style=\"width: 420;padding: 10px;height: 252;\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d710342dfd73826593d/download?uid=blt45c49c27b6f6fc81?uid=blt45c49c27b6f6fc81\" data-sys-asset-uid=\"blt609f2112e9376e9e\" alt=\"globe-with-meridians.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eRyan Schneider, Education Engineer: I adopted this emoji as it relates to one of the strongest ideals of our company which is its distributed culture that gives us the talent, camaraderie, and strengths that drive our products. The other globe emojis were tempting, but they specifically faced the globe on one particular region which showed bias. Our true distributed nature spans the entire globe.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7112798d8e381ffc17/download?uid=blt559b5193ef9487cc?uid=blt559b5193ef9487cc\" data-sys-asset-uid=\"bltd6808972b14f1160\" alt=\"doughnut.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eTyler Fontaine, Support Engineer: Because mmm donut.\u003cbr /\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d71d8edd48f769384af/download?uid=blt058137609964e359?uid=blt058137609964e359\" data-sys-asset-uid=\"blt7fb14070324790cb\" alt=\"donut.gif\" style=\"width: 300;padding: 10px;\" width=\"300\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eScene from \u003ca href=\"http://www.fox.com/the-simpsons/full-episodes\" target=\"_blank\"\u003eThe Simpsons\u003c/a\u003e. Copyright © 2016 by FOX Broadcasting Company. All Rights Reserved.\u003c/figcaption\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7158208ba076e2a77d/download?uid=blt4d855d9093c0a535?uid=blt4d855d9093c0a535\" data-sys-asset-uid=\"blt5c804b9e3d416402\" alt=\"monkey-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eThe Elastic \u003ca href=\"https://www.elastic.co/blog/elastic-support-speaking-code-and-human\"\u003eSupport\u003c/a\u003e Team, because we're loveable Support Monkeys.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d720342dfd738265949/download?uid=bltd34116f962b70102?uid=bltd34116f962b70102\" data-sys-asset-uid=\"blt2a39c5a9c48b14c4\" alt=\"coffee.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNik Everett, Software Engineer: Because coffee keeps us going.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7243e9adc538716152/download?uid=blt5ff3cf7f6416ad60?uid=blt5ff3cf7f6416ad60\" data-sys-asset-uid=\"blt23b2de9ff85d755c\" alt=\"for-all.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eTyler Hannan: Back before I realized I could make money in software, I was a theoretical mathematics \u0026amp; philosophy student. I was also … um … \"involved\" in the type of art that is placed in large swatches in abandoned buildings and/or trains and, more often, in galleries. Because we were a bunch of theoretical mathematicians making street art, we signed each piece with one consistent maths symbol. One that encapsulated the purpose, and name, of our little crew.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d723dc542cb38c0a9cd/download?uid=blt1996a4de20afb752?uid=blt1996a4de20afb752\" data-sys-asset-uid=\"blt2495500f93e9445a\" alt=\"hand-with-finger-raised.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eRobert Muir, Software Engineer: The money really does go to a good cause to fund important work on the world's languages. Besides that, you get a cool tweet from unicode. I did adopt this specific character because of this controversial \u003ca href=\"http://www.buzzfeed.com/charliewarzel/inside-emojigeddon-the-fight-over-the-future-of-the-unicode\" target=\"_blank\"\u003earticle\u003c/a\u003e. TL;DR: \"We're devoting the funds raised from the program to help flesh out support for digitally disadvantaged languages. And it's proved to be successful largely because of emoji.\"\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7212798d8e381ffc32/download?uid=blt3815d2ffd38717d7?uid=blt3815d2ffd38717d7\" data-sys-asset-uid=\"blt158ac3e1da2e6596\" alt=\"upside-down-smiley.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSpencer Alger, JavaScript Developer: I just adopted the upside-down smiley, because it's silly and simple and I love using it.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d72d8edd48f769384c3/download?uid=bltbc7e21bf1bbccc10?uid=bltbc7e21bf1bbccc10\" data-sys-asset-uid=\"bltd67987aebb047f7a\" alt=\"panda-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNicolas Ruflin, Software Engineer: I adopted it because who doesn't like Pandas? A Panda always helps to keep a conversation friendly.\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d723dc542cb38c0a9db/download?uid=blt9261c7a33ea9cc69?uid=blt9261c7a33ea9cc69\" data-sys-asset-uid=\"blt7959d19b242daf1f\" alt=\"horns.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eRuss Cam, Software Engineer: Because rock'n'roll!\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d720342dfd73826596e/download?uid=bltdf847b831d7a6a1a?uid=bltdf847b831d7a6a1a\" data-sys-asset-uid=\"bltb2af5fbc76790412\" alt=\"wind-blowing.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eRobin Clarke, Helper-outer: Because \"best winds\" is the best way to say goodbye.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d723dc542cb38c0a9ec/download?uid=bltb438dc19805374db?uid=bltb438dc19805374db\" data-sys-asset-uid=\"blte78dbe3ed02590a9\" alt=\"penguin.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJakob Reiter, Support Engineer: I've adopted the penguin, as it represents GNU/Linux and I probably wouldn't be working here, if I hadn't been introduced to GNU/Linux almost 13 years ago when I started my career in IT.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7258208ba076e2a7a6/download?uid=blt4814050ff96728c8?uid=blt4814050ff96728c8\" data-sys-asset-uid=\"blt6aadbd8ff30efb15\" alt=\"thumbs-up.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJoão Duarte, Log Whisperer: because this is the correct response to \"Can you all see this?\" when screen sharing in Zoom. Also I've always been a fan of nonverbal communication so I use thumbs up a lot!\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7243e9adc53871616e/download?uid=blt794d2a2cae8670df?uid=blt794d2a2cae8670df\" data-sys-asset-uid=\"bltb0baaccaec9d31b8\" alt=\"burrito.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eTudor Golubenco, Software Engineer: Because I like to use it as a reaction meaning \"thanks\". Plus, it's tasty.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d729e7a83165490e6f2/download?uid=blt00b2febc208d717b?uid=blt00b2febc208d717b\" data-sys-asset-uid=\"bltb19f2db4b72f6227\" alt=\"keyboard.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMartijn Laarman, Software Developer: Because without one who knows where I'd be? :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d723dc542cb38c0a9f1/download?uid=bltf91453ebab5c448e?uid=bltf91453ebab5c448e\" data-sys-asset-uid=\"bltb47800c3764cffc8\" alt=\"shield.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAndrei Stefan, Support Engineer: Adopted because, well… \u003ca href=\"https://www.elastic.co/products/shield\"\u003esecurity\u003c/a\u003e. ;-)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7358208ba076e2a7b3/download?uid=blteeab566308e40b0d?uid=blteeab566308e40b0d\" data-sys-asset-uid=\"blt52badb091381ce95\" alt=\"yellow-ribbon.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJongmin Kim, Developer Evangelist: This yellow ribbon is tied on my backpack. This has been done by many people in my local area in remembrance of the sinking of Sewol Ferry on 16 April 2014, which claimed 476 victims including 375 high school students. And also for remembrance of all people who have been victims of all kinds of situations like industrial accidents, natural disasters, and wars.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7343e9adc538716179/download?uid=blt9eee0eb563cebf12?uid=blt9eee0eb563cebf12\" data-sys-asset-uid=\"bltd1bb65d0018de425\" alt=\"black-spade-suit.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePete Dyson, Support Engineer: I adopted the black spade suit. So the story behind it is that I met my wife playing online poker :) She was in Berlin and I was in Brisbane, Australia. And through some crazy aligned planets thing, she now lives in Australia and we're married with three crazy kids. So I also have one of these tattooed on my left arm, an ace of spades playing card... which I got on my 28th birthday on the 28th of Feb 2008.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d730342dfd73826597e/download?uid=blt4aa4a15df17136aa?uid=blt4aa4a15df17136aa\" data-sys-asset-uid=\"blt95aa516bd9bdadaf\" alt=\"baby-bottle.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSteve Kearns, Sr. Director, Product Management: After 5+ years of having a unicode character poster on the wall of my cubicle while learning the intricacies of various human languages and search, it's nice to be able to give back. I adopted because I'm expecting a baby in the next few days! Target release date is May 2, but releases rarely go according to plan ;) Editor's note: The release was pushed back to May 10, and mom and baby are healthy.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d73d8edd48f769384e4/download?uid=blt7b4b809238502bd7?uid=blt7b4b809238502bd7\" data-sys-asset-uid=\"blt289b33e251115b84\" alt=\"horse-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAdrien Grand, Software Engineer: I adopted the horse face because unicorns are overrated.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d733dc542cb38c0aa00/download?uid=blt98444c60ce195108?uid=blt98444c60ce195108\" data-sys-asset-uid=\"blt80e633e0059f23bf\" alt=\"checkered-flag.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDaniel Mitterdorfer, Software Engineer: I have adopted the chequered flag\u0026nbsp;(U+1F3C1)\u0026nbsp;as I have been into car racing since I was a small boy.\u0026nbsp;That’s why I have also named our benchmarking tool for Elasticsearch \"\u003ca href=\"https://www.elastic.co/blog/announcing-rally-benchmarking-for-elasticsearch\"\u003eRally\u003c/a\u003e.\" But unfortunately, there is no Unicode character for a rally car yet. :(\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d739985d589763790c0/download?uid=blt2fbeeb538ff43bec?uid=blt2fbeeb538ff43bec\" data-sys-asset-uid=\"blt4af4c5cc20c6a109\" alt=\"ear-of-maize.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eCourt Ewing, Tech Lead Kibana: I've adopted U+1F33D (ear of maize) because I live in the middle of Amish country and our local tech community has sort of adopted that emoji as its own thing. It now carries a million different unofficial meanings for us — we could probably have entire discussions exclusively with the corn emoji. This Adopt-a-Character program is awesome.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d733dc542cb38c0aa15/download?uid=blta7e8b719419e2a49?uid=blta7e8b719419e2a49\" data-sys-asset-uid=\"blt6c218d7ae9875ad0\" alt=\"soft-ice-cream.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAli Beyad, Software Engineer: I've adopted U+1F366 (soft ice cream) … because I asked my 4 year old daughter which one she would pick and that is what she sagaciously chose.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d733dc542cb38c0aa10/download?uid=blt164f16fa878dea21?uid=blt164f16fa878dea21\" data-sys-asset-uid=\"blt87d6f4efce5f7889\" alt=\"frog-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDavid Pilato, Developer Evangelist: I'm still wondering why I choose U+1F438 ???\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d73d8edd48f769384f5/download?uid=bltf33c3a7e6b16015d?uid=bltf33c3a7e6b16015d\" data-sys-asset-uid=\"blt5e4606ba7dcf287f\" alt=\"raised-fist-type-4.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePeter Kim, Chief Coffee Connoisseur: I adopted the raised fist to support the struggle of oppressed peoples around the world against all forms of injustice. From Wikipedia: The raised fist is a symbol of solidarity and support. It is also used as a salute to express unity, strength, defiance, or resistance. The salute dates back to ancient Assyria as a symbol of resistance in the face of violence.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7343e9adc53871618a/download?uid=blt30c3c6ea9a0c824b?uid=blt30c3c6ea9a0c824b\" data-sys-asset-uid=\"blt65f4e4e6cc7c3fb1\" alt=\"rooster.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJay Greenberg, Support Engineer: I have adopted the rooster for obvious reasons.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d73d8edd48f769384fb/download?uid=blta8beb0df5345991f?uid=blta8beb0df5345991f\" data-sys-asset-uid=\"bltb5b3b5d7c6036ad3\" alt=\"dragon.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eLee Drengenberg, Software Engineer: I got this instead of an actual tattoo.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7358208ba076e2a7d0/download?uid=bltb393abcfa2fb2e02?uid=bltb393abcfa2fb2e02\" data-sys-asset-uid=\"bltee8ea5ca88b107ff\" alt=\"gem-stone.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eGuy Boertje, Software Engineer: I chose U+1F48E, gem or diamond. This is for all Elastic \"diamonds\" that I share this amazing ride with. \"Diamond geezer\" is a relatively new London slang term. In London today, a geezer is a person who is \"one of us\" or \"a good sort\" — usually male. Diamond was added to refine it to a \"the best of us,\" \"the best of sorts\". Now it's shortened to simply \"diamond\" as in \"You are a real diamond\" — not gender specific though. \"Geezer\" was used before for someone who can operate narrowly on either side of the law — a skallywag, a dodgy sort or someone that \"knows people that know people\". Obviously Elastic has none of these. In US English, I believe geezer refers to an old man, but this is clearly wrong. :-)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d733dc542cb38c0aa2b/download?uid=bltad06dd97d68984dd?uid=bltad06dd97d68984dd\" data-sys-asset-uid=\"blt16775e4e3d075d61\" alt=\"cricket-bat-ball.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eShaunak Kashyap, Developer: I chose it for my favorite sport, watching and playing. Plus I'm pretty sure that one isn't going to have too many takers. :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7312798d8e381ffc62/download?uid=bltf372d1e243a87201?uid=bltf372d1e243a87201\" data-sys-asset-uid=\"blt96f7ccb78662867e\" alt=\"alien.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eCostin Leau, Software Engineer: I picked it because I do believe that space is the final frontier. And hope that not too far in the future humanity will be exploring other planets, visiting other galaxies, discover ubik and maybe, just maybe meeting extra-terrestrial (and why not, friendly) life forms.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7458208ba076e2a7e3/download?uid=bltb6425998851dc955?uid=bltb6425998851dc955\" data-sys-asset-uid=\"blta85b4cf3d507a581\" alt=\"snowboarder.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMatt Bargar, Software Engineer: I adopted it because I wanted to be a professional snowboarder when I grew up. Alas, I was born in Ohio.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7443e9adc53871619f/download?uid=bltcd4d59995c97f68d?uid=bltcd4d59995c97f68d\" data-sys-asset-uid=\"bltbf8b3fde77c08327\" alt=\"screaming.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eColin Surprenant, Software Engineer: I chose it because this is probably the finance team's reaction upon receiving all of our funky expense reports. :P\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d74d8edd48f7693850c/download?uid=bltc9f2dfc9342fbd07?uid=bltc9f2dfc9342fbd07\" data-sys-asset-uid=\"blt06a3b547f0a0c87a\" alt=\"ChPKrsSU4AAwNHa.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eUri Boness, Elastic Co-Founder: 'Cause I hate talking / explaining core values.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d749985d589763790ef/download?uid=blt4d893051200a9632?uid=blt4d893051200a9632\" data-sys-asset-uid=\"blt9248c6d83d4865b6\" alt=\"magnifying-glass.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAlex Brasetvik, Software Engineer: I adopted this — You know, for search … (Wish there had been a skydiver emoji.)\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d749e7a83165490e725/download?uid=blt66fe87e62bcb4285?uid=blt66fe87e62bcb4285\" data-sys-asset-uid=\"blt7c02c36f36a9f1f6\" alt=\"roasted-sweet-potato.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAaron Bull Schaefer, Infrastructure Engineer: I've chosen the good ole' roasted sweet potato (U+1F360) as they are not only delicious, but rich in complex carbohydrates, dietary fiber, and beta-carotene, with a dash of potentially healthy (not yet studied) resin glycosides having antibacterial and antifungal properties. As if that weren't enough, :sweet_potato: is one of my favorite exclamatory reactions to messages in Slack.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d743dc542cb38c0aa33/download?uid=blt69e71eaa2d80a277?uid=blt69e71eaa2d80a277\" data-sys-asset-uid=\"blt3f35a548b958e21b\" alt=\"bug.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJason Bryan, Support Engineer: I have adopted the bug (U+1F41B) to pay tribute to the bug gods and because the pupa stage is terribly underrated.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d740342dfd7382659ad/download?uid=blt35335c98236c55a1?uid=blt35335c98236c55a1\" data-sys-asset-uid=\"blt3bc0266571787a3c\" alt=\"speaker-with-sound-waves.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSteve Mayzak, VP Worldwide Solutions Architecture: I adopted this one for my love of music and bass!\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d743dc542cb38c0aa38/download?uid=bltf14f6251e651434e?uid=bltf14f6251e651434e\" data-sys-asset-uid=\"blt8914e321f01d5cd4\" alt=\"heat-waves.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePaul Echeverri, Senior Technical Writer: I adopted it because I love hot water and hot springs of all sorts.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7443e9adc5387161ab/download?uid=bltc2d2f487528272f2?uid=bltc2d2f487528272f2\" data-sys-asset-uid=\"blt1dc8afb5fe034513\" alt=\"raised-hand-vulcan.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNicholas Lim, Services Engineer: Adopted this on two counts: I \u0026lt;3 Spock and my resounding wish is for everyone to \"Live long and prosper.\"\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d749e7a83165490e737/download?uid=blt4118e6f3ef3fd3b0?uid=blt4118e6f3ef3fd3b0\" data-sys-asset-uid=\"blte733243ab9ef12bf\" alt=\"spider.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMedcl Zeng, Developer Evangelist: I adopt this spider, which is the hard-working agent for the internet.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfb7f10cd843a4079/5fa95ae172a3526f28dba26c/runner.png\" data-sys-asset-uid=\"bltfb7f10cd843a4079\" alt=\"runner.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eChristian Strzadala, Software Engineer: I've adopted this as I do run a fair bit.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d749985d589763790ff/download?uid=blt19af81bd84561f34?uid=blt19af81bd84561f34\" data-sys-asset-uid=\"blt99f27dd99efb6d1c\" alt=\"chet.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJordan Zimmerman, Cloud Engineer: I adopted U+05D7, the Hebrew letter Chet. When followed by a yud it is the word \"life\" (chai): חי. I'm such a softy. חי makes the number 18 so, many Jews always add $18 when giving money gifts.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d740342dfd7382659bc/download?uid=bltfe6bab322db2ac39?uid=bltfe6bab322db2ac39\" data-sys-asset-uid=\"blte71bd5cd05f1ecd8\" alt=\"snowboarder.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eBaha Azarmi, Solutions Architect: I adopted U+1F3C2 … Well, you know why :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d759e7a83165490e746/download?uid=blt0b66da1d4f1a95fb?uid=blt0b66da1d4f1a95fb\" data-sys-asset-uid=\"blte55370e500dd3a26\" alt=\"desert.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eChristian Zumbiehl, Professional Services: I chose this one because I am fascinated by deserts and I see the cactus as a model of persistence.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7443e9adc5387161c3/download?uid=bltde165e5c18cf878d?uid=bltde165e5c18cf878d\" data-sys-asset-uid=\"blt826c7f3fc99d807e\" alt=\"fermata.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eChristoph Büscher, Software Engineer: I adopted a character from music notation. The fermata is used to indicate to hold a note a bit longer than usual, to give it more space and attention because it's really good.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d74d8edd48f76938531/download?uid=bltbc0c2272c6850215?uid=bltbc0c2272c6850215\" data-sys-asset-uid=\"blt0e6d7e0b1ccdcb01\" alt=\"black-question-mark.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eKurt Hurtado, Software Engineer: I adopted 'BLACK QUESTION MARK ORNAMENT' (U+2753 ). At Elastic, we always ask \"WHY?\"... it's an important part of our culture. Also, when I teach classes on the Elastic Stack, I love getting questions from attendees. I learn best myself when I'm asking questions.\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d740342dfd7382659cc/download?uid=blta346b43a971de6e9?uid=blta346b43a971de6e9\" data-sys-asset-uid=\"blte114275f1441906a\" alt=\"pepper.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eTim Sullivan, UI Engineer: I adopted it because it looks a lot like the kind of Thai chilis that my wife grows at home. We're both huge fans of chili and spicy food, and it's something that we've always had in common.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7143e9adc538716144/download?uid=bltad017cf2260f03af?uid=bltad017cf2260f03af\" data-sys-asset-uid=\"blt0ad01ddd70ff6d7c\" alt=\"monkey.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJay Modi, Security Engineer: I adopted it because, well, I like monkeys.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d75d8edd48f76938538/download?uid=blt7c98986c0e2b1ed2?uid=blt7c98986c0e2b1ed2\" data-sys-asset-uid=\"blt211c3369b40c4b85\" alt=\"unicodeBronze-2601.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eHenry Pak, Solutions Architect: Adopted it because\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7543e9adc5387161cb/download?uid=blt310c85ce06ef2313?uid=blt310c85ce06ef2313\" data-sys-asset-uid=\"bltab64ec4155a2c782\" alt=\"There_is_no_cloud.jpg\" style=\"width: 300;padding: 10px;\" width=\"300\"/\u003e\u003c/p\u003e\u003cfigcaption\u003eScene from \u003ca href=\"http://www.warnerbros.com/matrix\" target=\"_blank\"\u003eThe Matrix\u003c/a\u003e. Copyright © 1999 by Warner Bros. All Rights Reserved.\u003c/figcaption\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d75d8edd48f76938545/download?uid=bltae8ab14e0277716b?uid=bltae8ab14e0277716b\" data-sys-asset-uid=\"blt017e485daabe393c\" alt=\"sparkles.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eKosho Owa, Solutions Architect: I have adopted it because it can make anything shiny.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7543e9adc5387161d6/download?uid=bltc7b5f669823a9b15?uid=bltc7b5f669823a9b15\" data-sys-asset-uid=\"bltcf5fd791f19c5e88\" alt=\"books.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDeb Adair, Technical Writer: I adopted books. You know, for docs!\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d759e7a83165490e756/download?uid=bltd5cadf3af89349f1?uid=bltd5cadf3af89349f1\" data-sys-asset-uid=\"blt3f9f9d205141e544\" alt=\"water-wave.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSherry Ger, Support Engineer: I adopted that because it is how it feels in support!\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d750342dfd7382659da/download?uid=blt7a5f9c5144f52ad6?uid=blt7a5f9c5144f52ad6\" data-sys-asset-uid=\"blt922f4a814e0c8546\" alt=\"cjk-radical-j-simplified.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eShay Banon, the dude abides: I have adopted U+2EEF, it was my first tattoo (followed 30 minutes later by my second one). Why it was my first tattoo is a different story :)\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7558208ba076e2a813/download?uid=blt7ca9b67a4f8f0559?uid=blt7ca9b67a4f8f0559\" data-sys-asset-uid=\"blt01f32c2233eb72d2\" alt=\"japanese-beginner.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAaron Mildenstein, Software Engineer: I adopted U+1F530 because, well, Japan. This symbol goes on the back of cars with new drivers, kind of like a \"beginner on board\" identification. It fits with my \"untergeek\" nickname and reminds me to always keep learning as though I were a beginner.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d759985d58976379130/download?uid=blt3242cbd2e2bd855c?uid=blt3242cbd2e2bd855c\" data-sys-asset-uid=\"blt33eada05c9424905\" alt=\"tiger-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePhilipp Krenn, Developer Advocate: I've adopted U+1F42F. I'm just like a big cat that likes to sleep whenever possible, I love Hobbes from Calvin and Hobbes, and it has been my emoji in many chats.\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d750342dfd7382659e7/download?uid=blt52fb82ef354966e1?uid=blt52fb82ef354966e1\" data-sys-asset-uid=\"blt806be65eca7ecc61\" alt=\"racing-car.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eKevin Kluge, VP of Engineering: I adopted U+1F3CE. It looks like a Ferrari F1 car. I've been following F1 and rooting for \u003ca href=\"http://formula1.ferrari.com/en/\"\u003eFerrari\u003c/a\u003e for a long time. I also do some amateur car racing as my primary hobby, when work and family allow. :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d753dc542cb38c0aa6d/download?uid=bltf4eee27e4cdca478?uid=bltf4eee27e4cdca478\" data-sys-asset-uid=\"blt81eba3fc643f166a\" alt=\"peace-dove.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eGabriel Moskovicz, Engineer: I adopted U+1F54A, the dove of peace. Pretty sure it is self-explanatory. :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d759e7a83165490e764/download?uid=blt0936fddec8128a79?uid=blt0936fddec8128a79\" data-sys-asset-uid=\"blt1d45db4515bbb6cb\" alt=\"cjk-unified-ideograph-96ea.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJason Tedor, Software Engineer: I adopted U+96EA because my wife's name is 深雪 meaning \"deep snow\" and it also seemed fitting since I'm from Alaska.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d769985d5897637914e/download?uid=bltc0572ea4e21c1e8c?uid=bltc0572ea4e21c1e8c\" data-sys-asset-uid=\"bltd59b58156947e084\" alt=\"snow-capped-mountains.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMark Harwood, Software Engineer: I adopted \"snow-capped mountain\" — they've always been a big part of my family. I married my wife on top of one :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d753dc542cb38c0aa7d/download?uid=blt6aa2b7bd14401308?uid=blt6aa2b7bd14401308\" data-sys-asset-uid=\"bltdde5b8b851ebdf91\" alt=\"wolf-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eChris Earle, Monitoring Lead: I adopted U+1F43A because I love dogs and that reminds me of German Shepherds, which is my favorite breed. It looks more like a Husky or Wolf in some other emoji formats and they're pretty cool too.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7612798d8e381ffcd4/download?uid=blta0527d25f72f7c47?uid=blta0527d25f72f7c47\" data-sys-asset-uid=\"blt73c73c3708953fce\" alt=\"tree.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDeDe Morton, Sr. Technical Writer: I adopted the tree (U+1F333) for the rich imagery of being rooted while also reaching towards the sky … for the connections that we have to the people we love and to the past and future through our ancestors and children … for the fruit that nourishes us … and for the air that we breathe.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d760342dfd7382659f8/download?uid=blt9124a764f9bcf33e?uid=blt9124a764f9bcf33e\" data-sys-asset-uid=\"blt0ffacb8c955e96be\" alt=\"hangul-choseong-khieukh.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eBohyun Kim, Senior Product Manager: I adopted a Korean consonant, since it gets used the most when I type in Korean. This character has the sound of [kʰ] which can sound like a soft laughing sound when they're spoken in a series (e.g. 'ㅋㅋㅋㅋ' translates to ‘kkkk').\u0026nbsp;So when I find something really funny, I will type this about 20 times :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d769e7a83165490e775/download?uid=blt02f3dce62f78d37a?uid=blt02f3dce62f78d37a\" data-sys-asset-uid=\"blt0582572fefd0c594\" alt=\"light-bulb.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eBoaz Leskes, Software Engineer: It's the best of part of any serious programming/debugging session.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d769985d5897637914f/download?uid=blt3a62d2b2cbb85abc?uid=blt3a62d2b2cbb85abc\" data-sys-asset-uid=\"bltbfd7f46c026d7738\" alt=\"glowing-star.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eColin Goodheart-Smithe, Software Engineer: I adopted it because I studied nuclear astrophysics at university so I learnt all about (and have since forgotten all about) stars.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7643e9adc538716204/download?uid=blt16f292f289480fa0?uid=blt16f292f289480fa0\" data-sys-asset-uid=\"blt9c9a2b6b469a73ab\" alt=\"rocket.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMartijn van Groningen, Software Engineer: I've adopted U+1F680 because rockets are cool.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7612798d8e381ffce2/download?uid=bltc839914af6fb07cb?uid=bltc839914af6fb07cb\" data-sys-asset-uid=\"bltb89cc11ba830d3d5\" alt=\"noodles-bowl.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003ePius Fung, Support Engineer: I adopted because I can eat noodles 365 days a year. :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d76d8edd48f76938571/download?uid=blt2afaff6846554fae?uid=blt2afaff6846554fae\" data-sys-asset-uid=\"blt6c63af8cff2c145b\" alt=\"mountain.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eSuyog Rao, Team Lead: Adopted U+26F0. You know, for the love of mountains and outdoors. :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7658208ba076e2a846/download?uid=blt5e14aeb1ea947631?uid=blt5e14aeb1ea947631\" data-sys-asset-uid=\"blt742c069de6ce874c\" alt=\"lion-face.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAntonio Bonuccelli, Elastic Support: Adopting a lion face ‘cause it's an endangered species and it is also my zodiac sign. :-)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d76d8edd48f76938579/download?uid=blt8ea7407bcefda290?uid=blt8ea7407bcefda290\" data-sys-asset-uid=\"blt39e864fb4a141fb5\" alt=\"person-with-praying-hands.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDrew Raines, Software Developer:\u0026nbsp;I adopted \u003cem\u003eperson with folded hands, type-6\u003c/em\u003e as homage to the four pair in my home. This image embodies two beautiful things: transracial adoption and prayer. I grew up a white boy in the American south. My children are black Africans. Adoption has allowed me to incarnate into the black experience. I watch as they get disciplined before their white peers. I educate them how to talk to the police for fear they won’t come home one night when they’re teenagers. But I have hope in the God who adopted me, who\u0026nbsp;promised to \u003cem\u003eproclaim liberty to the captives\u003c/em\u003e and \u003cem\u003eset at liberty those who are oppressed\u003c/em\u003e (Lk 4). While we wait for that day, he told us to pray. Hate is not someone else’s problem. It’s in me. Left to my own, I wouldn’t need any lessons on how to judge people or think I’m better than they are. A hater like I am cannot just talk to a perfect God with impunity. Jesus Christ incarnated into the human experience, bearing the punishment that I deserve for rejecting God and hating my neighbor, and defeated the domain of darkness whence all hate comes so that, in part, I could \u003cem\u003epray\u003c/em\u003e. It’s soil in which I plant my hope that his promise is true. So I do it. For my family, for my neighbor, for you.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d760342dfd738265a11/download?uid=bltc5dfdf9168089b67?uid=bltc5dfdf9168089b67\" data-sys-asset-uid=\"blt2425f07f415de27b\" alt=\"artist-palette.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMarcelo Rodriguez, Support Engineer: I adopted it for the inner artist in all of us and our Engineering All-Hands reminded me that what we do is more of an art than a science.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d760342dfd738265a16/download?uid=blt79863b8fe0f54725?uid=blt79863b8fe0f54725\" data-sys-asset-uid=\"bltf5315a584576654e\" alt=\"minidisc.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAndrew Cholakian, Software Engineer: I adopted it because I always wanted a MiniDisc player but could never afford one. Now I have one foreevvvveerrrrr.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d763dc542cb38c0aaa0/download?uid=blt6230686c402ad543?uid=blt6230686c402ad543\" data-sys-asset-uid=\"blt40dc430ecec45180\" alt=\"raised-hand.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eUri Cohen, product guy: I adopted raised hand with part between middle and ring fingers, type-4 for three reasons: 1) Because it's the Vulcan salute, and I highly appreciate good reason behind everything I do (albeit not at the expense of emotions). 2) It's also (and that's where Leonard Nimoy borrowed it from) how Cohens, which stands for priests in Hebrew, raise their hands in the \u003ca href=\"https://en.wikipedia.org/wiki/Priestly_Blessing\"\u003etraditional priest blessing\u003c/a\u003e in synagogue. I am not religious, at least not in the traditional way, but being a Cohen is part of my heritage. The type 4 is, well, because it's the closest to my skin tone :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7643e9adc538716212/download?uid=bltb06ec706bb04e8e7?uid=bltb06ec706bb04e8e7\" data-sys-asset-uid=\"blt037bb4055f64788d\" alt=\"party-popper.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eNicolás Bevacqua, UI Engineer: I adopted party popper because I'm a huge fan of this emoji. It makes me feel so good every time I add one of these into a message, for some reason!\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d769985d58976379161/download?uid=bltefbdab3999c3298e?uid=bltefbdab3999c3298e\" data-sys-asset-uid=\"blt6c67f7939aaac2af\" alt=\"boom.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eMiguel Bosin, Support Engineer: I adopted because this is what I felt when I joined Elastic and met the impressive (in many senses) people I have met so far.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d763dc542cb38c0aaa1/download?uid=bltf8ebcf1141631444?uid=bltf8ebcf1141631444\" data-sys-asset-uid=\"blt52b18024cbaf6f1e\" alt=\"baseball.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJason Dickson, Content Coordinator: I adopted U+26BE because it reminds me of watching baseball with my grandfather and attending San Jose Giants games with my wife and friends.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7758208ba076e2a851/download?uid=bltd01944aaea3cf041?uid=bltd01944aaea3cf041\" data-sys-asset-uid=\"blt8427fd2bb62b517c\" alt=\"movie-camera.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eBen Ferrer, Video Content Creator: I've always had a camera in my hand since I was a kid, and cinematography has been my passion for quite awhile.\u003c/p\u003e\u003cbr /\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d77d8edd48f7693858b/download?uid=bltc43946eb525e2cb1?uid=bltc43946eb525e2cb1\" data-sys-asset-uid=\"blt7feafead69eaaef8\" alt=\"white-rat.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eTanya Bragin, member of the Product team: I thought of adopting this when I was texting with my husband about our three-year-old daughter. She is German, and a diminutive name often used in Germany for little girls is inexplicably \"Maeuschen,\" which means \"little mouse.\" So when we text each other, we often use this character to describe Alina. I decided to adopt this emoji to signify my unbounded love for her, and the amazing experience it has been for me being a parent and raising a child.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d7743e9adc538716224/download?uid=blt985f5f04353ad667?uid=blt985f5f04353ad667\" data-sys-asset-uid=\"blte5f181176a893ddc\" alt=\"top-hat.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eJames Baiera, Software Engineer: I've adopted the top hat emoji. Years ago, some old friends gave me the nickname \"Jimmy the Hat,\" due in part because I always wear a hat (though not a top hat). Also because my first name is Jimmy. It's an exceedingly clever nickname that has stuck with me since.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp align=\"center\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d773dc542cb38c0aaaf/download?uid=blt0f722798a4163f07?uid=blt0f722798a4163f07\" data-sys-asset-uid=\"blt8a31d24b3b138392\" alt=\"floppy-disk.png\"/\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eDimitrios Liappis, Infrastructure Engineer: I adopted the floppy disk emoji\u0026nbsp;\u003ca href=\"http://www.unicode.org/emoji/charts/emoji-list.html#1f4be\" target=\"_blank\"\u003e\u003cbr /\u003e\u003c/a\u003e(U+1F4BE) because this is what got me started with computers and I still fondly take care of devices that can read them. :)\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cbr /\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eLuisa Antonio, Marketing Coordinator: I chose the laughing face emoji because laughing on a daily basis is a must for me. A good sense of humor goes a long way in life\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003eSoon to be added: The Elastic \u003ca href=\"https://www.elastic.co/training\"\u003eEducation\u003c/a\u003e\u0026nbsp;Team will be\u0026nbsp;adopting the owl\u0026nbsp;(U+1F989) from Unicode 9.0\u0026nbsp;at\u0026nbsp;bronze level.\u0026nbsp;As seen in the \u003ca href=\"http://www.latimes.com/business/technology/la-fi-tn-new-emoji-unicode-9-20160602-snap-story.html\"\u003eLos Angeles Times last week\u003c/a\u003e, the owl is one of a set of\u0026nbsp;brand-new emojis coming soon to a screen near you!\u0026nbsp;The Unicode Consortium is\u0026nbsp;close to allowing adoption of Unicode 9.0 characters with their website update in the coming weeks. Check back and you can\u0026nbsp;be first to adopt one of the awesome new emojis!\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003eIn case you're wondering, adopting wasn't required and all adoption fees were eligible for reimbursement by Elastic. And here's an example of the cool certificates that a Bronze-level sponsor may choose to receive:\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d729985d58976379092/download?uid=blt0e158b6c742c14b6?uid=blt0e158b6c742c14b6\" data-sys-asset-uid=\"blt51e21fa6f3050fd5\" alt=\"Elastic-Baha-Unicode-Consortium.jpg\" width=\"624\"/\u003e\u003c/p\u003e\u003cp\u003eElastic commends the Unicode Consortium for all the work it is doing, and we encourage everyone reading this to visit the \u003ca href=\"http://unicode.org/\" target=\"_blank\"\u003eUnicode Consortium\u003c/a\u003e site and its \u003ca href=\"http://unicode.org/consortium/adopt-a-character.html\" target=\"_blank\"\u003eAdopt-a-Character program\u003c/a\u003e, and make a donation to sponsor your favorite character today!\u003c/p\u003e","category":[{"uid":"bltc253e0851420b088","_version":4,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:45:23.873Z","created_by":"sys_blt57a423112de8a853","key":"culture","label_l10n":"Culture","tags":[],"title":"Culture","updated_at":"2024-05-10T13:44:28.145Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.214Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:18:56.195Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt9b9e21e089f315b8","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:10:37.770Z","updated_at":"2018-10-11T05:10:37.770Z","content_type":"image/jpeg","file_size":"205625","filename":"blog-unicode-sponsor-banner.jpg","title":"blog-unicode-sponsor-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:16:11.924Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9b9e21e089f315b8/5bbedb4d6a851d9f7f70c82b/blog-unicode-sponsor-banner.jpg"},"markdown_l10n":"","publish_date":"2016-06-07T14:20:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch Loves the Unicode Adopt-a-Character Program","seo_description_l10n":"Shay Banon found out about the Unicode Consortium's Adopt-a-Character program, and he had a cool idea: why not allow every engineer at Elastic (as well as other teammates within the company) to choose and adopt a character?","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt389c921db479034d","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:10:30.572Z","updated_at":"2018-10-11T05:10:30.572Z","content_type":"image/jpeg","file_size":"75873","filename":"blog-unicode-sponsor-thumb.jpg","title":"blog-unicode-sponsor-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T18:16:11.924Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt389c921db479034d/5bbedb4663ed239936a7df03/blog-unicode-sponsor-thumb.jpg"},"title":"Adopt-a-Character Program and the Unicode Consortium :-)","title_l10n":"Adopt-a-Character Program and the Unicode Consortium :-)","updated_at":"2025-03-10T11:34:44.388Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-love-for-the-adopt-a-character-program-and-the-unicode-consortium","publish_details":{"time":"2025-03-10T11:34:48.061Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt202b6cb6e7511b42","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"Create a threshold alert in Elasticsearch using a simple and easy Kibana UI.","author":["blt7df598857705e791","blt84d458550c3f5c4e"],"body_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/elasticon/conf/2017/sf/opening-keynote\"\u003eSimple things should be simple\u003c/a\u003e was one of the themes at Elastic{ON} ‘17, our annual user conference where we connect with our users. During and prior to the user conference,\u0026nbsp;we received many requests for a simple and easy to use UI to create alerts. As it turns out, creating a single UI to work effectively for all types of alerts is pretty hard. For example, a UI that can create an alert when the\u0026nbsp;average CPU utilization goes over 50%\u0026nbsp;looked\u0026nbsp;pretty different from a UI that can create an\u0026nbsp;alert when there are many concurrent logins from the same IP address.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eSince it is hard to build a universal UI for all types of alerts, we decided to tackle the UI for the most commonly requested alert first: a simple, threshold\u0026nbsp;alert that is triggered\u0026nbsp;when a metric goes above or below a given threshold.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBefore we can get into examples, make sure that you have the minimum of version of 6.0.0-beta 2 of \u003ca href=\"https://www.elastic.co/downloads/elasticsearch#preview-release\"\u003eElasticsearch\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/downloads/kibana#preview-release\"\u003eKibana\u003c/a\u003e installed with \u003ca href=\"https://www.elastic.co/downloads/x-pack#preview-release\"\u003eX-Pack\u003c/a\u003e installed on both. Also, ensure that you have Elasticsearch configured with a user with \u003ca href=\"https://www.elastic.co/guide/en/kibana/6.0/watcher-security.html\"\u003esufficient rights\u003c/a\u003e. Now, we need some interesting data with which to build our alerts. \u003ca href=\"https://www.elastic.co/beats/metricbeat\"\u003eMetricbeat\u003c/a\u003e is a great beat for monitoring system and user processes on a machine. To set up Metricbeat, refer to our documentation \u003ca href=\"https://www.elastic.co/guide/en/beats/metricbeat/6.0/metricbeat-installation.html\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eOnce Metricbeat is installed and running, open up a browser and navigate to Kibana. Click on the Management app in the side navigation bar, and then click on Watcher under the Elasticsearch heading.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd79cd0b30bd5c1d6/5fa958d509ed4c6f277eb496/blog-threshold-alert-1.png\" width=\"624\" height=\"348\" style=\"width: 624;height: 348;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eNow, click on the ‘Create New Watch’ button and select ‘Threshold Alert’. This will bring you to the new threshold alert UI.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIn the ‘Create a new threshold alert’ panel, configure the name, index, time field and the trigger interval. This will reveal the condition panel with a simple condition already populated, as well as a visualization of the data that the condition is based upon.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0d576f8480155b0a/5fa958dc6f82405d9a4aa796/blog-threshold-alert-2.png\" width=\"624\" height=\"163\" style=\"width: 624;height: 163;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eFor our first example, we want a threshold alert that is triggered when the maximum of the total CPU usage on a machine ever goes above 50% during the past 5 minutes. This is a very common type of alerts because it can help understand when and where the spikes are happening to take an action. We will choose 50% as a threshold value. Modify the condition expression so that it matches the image below.\u0026nbsp;As you change the expression, the visualization is updated automatically to show the threshold value and data as red and blue lines respectively.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt054cca82200a0818/5fa958dbffb61e50a0faab99/blog-threshold-alert-3.png\" width=\"615\" height=\"301\" style=\"width: 615;height: 301;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr class=\"kix-line-break\"/\u003eNow that we have configured the condition to trigger the\u0026nbsp;alert, let’s configure what we want to happen when that condition is met. In this case, we want to send an E-mail to the person to which it matters most. Click on the ‘Add new action’ select box, and choose ‘E-mail’. A sample configuration for an e-mail action is shown below.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb2d144ab6cb6a27/5fa958dc97f9f35d942e99c0/blog-threshold-alert-4.png\" width=\"624\" height=\"259\" style=\"width: 624;height: 259;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eNote that you can use \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-template.html#search-template\"\u003emustache\u003c/a\u003e syntax to access the {{ctx}} object which contains information about the alert when it triggers. We are using that here to embed the max CPU value into the body of our e-mail. If you have an \u003ca href=\"https://www.elastic.co/guide/en/x-pack/6.0/actions-email.html#configuring-email\"\u003ee-mail account configured in Elasticsearch\u003c/a\u003e, then you can click on the ‘Test fire an e-mail now’ and watcher will send out a sample e-mail.\u003c/p\u003e\u003cp\u003eClick on the ‘Save’ button to save your new alert. There is now a threshold alert running on your Elasticsearch cluster.\u003c/p\u003e\u003cp\u003eWant to see this feature in a live demo?\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 478px;margin-bottom: 15px;\"\u003e\u003cimg style=\"width: 100%;margin: auto;display: block;\" class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/Pzht5TWZYmh74gvk38QPUg.jpg\" data-uuid=\"Pzht5TWZYmh74gvk38QPUg\" data-v=\"4\" data-type=\"inline\" width=\"100%\"/\u003e\u003c/div\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBut of course there’s more, like what’s coming up next. We have plans to allow you to use Kibana's saved searches to be the input for a threshold alert since those are fairly common and currently used in other areas of Kibana. We also plan to build out more UIs for other alerting use cases, such as comparing today’s value with last week’s value and alerting when the change goes\u0026nbsp;beyond a certain threshold.\u003c/p\u003e\u003cbr /\u003eGo use this feature\u0026nbsp;and check out our \u003ca href=\"https://www.elastic.co/guide/en/kibana/6.0/watcher-ui.html\"\u003edocumentation\u003c/a\u003e for more details. As you dive into the 6.0 preview releases, we'd love to hear your feedback as part of our \u003ca href=\"https://www.elastic.co/blog/elastic-pioneer-program-6-0\" target=\"_blank\"\u003ePioneer Program\u003c/a\u003e. Your insights make\u0026nbsp;our software better!","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:22:15.395Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf7e0361d38ceea67"],"full_bleed_image":{"title":"Screen Shot 2017-09-12 at 4.37.01 PM.png","uid":"blt8c93fdb27c9974d3","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:41:23.178Z","updated_at":"2019-01-05T09:41:23.178Z","content_type":"image/png","file_size":"114006","filename":"Screen_Shot_2017-09-12_at_4.37.01_PM.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:28:26.145Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c93fdb27c9974d3/5c307bc34657a057675ba7c4/Screen_Shot_2017-09-12_at_4.37.01_PM.png"},"markdown_l10n":"","publish_date":"2017-09-13T09:30:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"Screen Shot 2017-09-12 at 3.40.08 PM.png","uid":"bltec7f90943d63b5af","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:41:38.908Z","updated_at":"2019-01-05T09:41:38.908Z","content_type":"image/png","file_size":"97060","filename":"Screen_Shot_2017-09-12_at_3.40.08_PM.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T21:28:26.145Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec7f90943d63b5af/5c307bd233d6423967f5b62c/Screen_Shot_2017-09-12_at_3.40.08_PM.png"},"title":"Creating a threshold alert in Elasticsearch is simpler than ever.","title_l10n":"Creating a threshold alert in Elasticsearch is simpler than ever.","updated_at":"2025-03-10T11:32:38.423Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/creating-a-threshold-alert-in-elasticsearch-is-simpler-than-ever","publish_details":{"time":"2025-03-10T11:32:42.629Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb8713a9f8f7f14a0","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"This step-by-step set of instructions will walk you through setting up an Elastic Cloud account, creating and securing your Elasticsearch cluster, and more.","author":["bltfcef00cc055272b5"],"body_l10n":"\u003ctable style=\"background: #FFFFD2;\"\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cstrong\u003eDON'T PANIC.\u0026nbsp;\u003c/strong\u003eThis article contains instructions for Elasticsearch 2.x\u0026nbsp;and Kibana Version 4.x, but still works. An updated version for 5.x can be found \u003ca href=\"/blog/getting-started-with-hosted-elasticsearch-v5-and-a-sample-dataset\"\u003ehere\u003c/a\u003e.\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003eGetting an Elasticsearch environment up and running has never been easier. With Elastic Cloud, you can launch your cluster and start ingesting data in literally minutes. See how in this \u003ca href=\"https://youtu.be/MNkdXSzt96E\" target=\"_blank\"\u003e3-minute video\u003c/a\u003e. This step-by-step set of instructions will walk you through setting up an Elastic Cloud account, creating and securing a Elasticsearch cluster, importing data, and visualizing it in Kibana. So, let's get started.\u003c/p\u003e\u003ch2\u003eLog into Elastic Cloud\u0026nbsp;\u003c/h2\u003e\u003col\u003e\u003cli\u003eGo to \u003cspan style=\"font-size: 14.6667px;text-decoration: underline;vertical-align: baseline;white-space: pre-wrap;background-color: transparent;\"\u003e\u003c/span\u003e\u003ca href=\"https://cloud.elastic.co\" target=\"_blank\"\u003ehttps://cloud.elastic.co\u003c/a\u003e in your browser and sign up for an account.\u0026nbsp;\u003c/li\u003e\u003cli\u003eYou will receive a confirmation email. Open it and follow the instructions to start your trial.\u003c/li\u003e\u003cli\u003eLog into your\u0026nbsp;Elastic Cloud account\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eCreate your first\u0026nbsp;hosted\u0026nbsp;Elasticsearch cluster\u003c/h2\u003e\u003col\u003e\u003cli\u003eOnce you have signed in, go to the Cluster tab to create your cluster.\u0026nbsp;\u003c/li\u003e\u003cli\u003eSelect cluster size. I will select a cluster with 4GB memory and 64GB storage\u0026nbsp;\u003c/li\u003e\u003cli\u003eChoose a region that is close to your location. I am choosing US West.\u0026nbsp;\u003c/li\u003e\u003cli\u003eSelect replication. I am choosing only one Datacenter location.\u0026nbsp;\u003c/li\u003e\u003cli\u003eClick on\u0026nbsp;Create to provision your cluster.\u0026nbsp;\u0026nbsp;Provisioning will start and you will receive a notification once it's complete.\u003c/li\u003e\u003c/ol\u003e\u003cul\u003e\u003c/ul\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d6b0342dfd73826582d/download?uid=bltfd5f7b26de739143?uid=bltfd5f7b26de739143\" data-sys-asset-uid=\"blt4b2a517253f115d3\" alt=\"Cloud-CreateCluster.gif\"/\u003e\u003c/p\u003e\u003cspan\u003e\u003c/span\u003e\u003ch2\u003eSecure your Cluster\u003c/h2\u003e\u003cp\u003eNext, let's configure cluster access and security.\u003c/p\u003e\u003col\u003e\u003cli\u003eClick on the Configure Shield link on the Overview page.\u0026nbsp;\u003c/li\u003e\u003cli\u003eCreate additional users and/or configure existing usernames and passwords. I will create\u0026nbsp;a new user,\u0026nbsp;sa_admin\u003c/li\u003e\u003cli\u003eIf you added new users, configure their roles. I will configure sa_admin\u0026nbsp;user with admin role\u0026nbsp;\u003c/li\u003e\u003cli\u003eCopy the usernames and password before hitting the Save. This is important because the passwords are hashed once you save the config. Save your credentials in a secure vault. Or a Post-it note\u0026nbsp;😉.\u0026nbsp;\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt43820ebc23d53bf6/5f9b1f1b6178a9645452b84e/blog-cloud-sandbox-2.png\" data-sys-asset-uid=\"blt43820ebc23d53bf6\" alt=\"blog-cloud-sandbox-2.png\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cp\u003eYou can update your passwords or add additional users using the same process.\u0026nbsp;You may also use the new security API that is included in 2.3.1 by following the\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/shield/2.3/shield-rest.html#shield-users-rest\" target=\"_blank\"\u003einstructions in our documentation\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eEnable Kibana\u003c/h2\u003e\u003col\u003e\u003cli\u003eTo enable Kibana, go to the Configuration link and go to the Kibana 4 section.\u0026nbsp;\u003c/li\u003e\u003cli\u003eSelect Enable from the dropdown list, then click Update. \u0026nbsp;The displayed\u0026nbsp;endpoint is how you access Kibana - it is unique for your cluster.\u0026nbsp;\u003c/li\u003e\u003cli\u003eClick on the link and to open Kibana in a new tab.\u0026nbsp;\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eLog into Kibana with username \u0026amp; password configured in the previous step.\u0026nbsp;\u003c/li\u003e\u003c/ol\u003e\u003col\u003e\u003c/ol\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4d6c12798d8e381ffb16/download?uid=blt8bccaf94c539ea49?uid=blt8bccaf94c539ea49\" data-sys-asset-uid=\"blte360d26fdf492cc1\" alt=\"Cloud-Kibana.gif\"/\u003e\u003c/p\u003e\u003ch2\u003eElasticsearch Endpoint\u003cspan\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003eOnce you are logged into Kibana, you will first see the Discovery tab.\u0026nbsp;However, there is no data to visualize.\u0026nbsp;Next, we will work on ingesting data into Elasticsearch.\u0026nbsp;Let's gather some information so we can be successful.\u0026nbsp;\u003c/p\u003e\u003col\u003e\u003cli\u003eGo to the Overview link in the Elastic Cloud console. The listed endpoints are used for API access for your cluster.\u0026nbsp;\u003c/li\u003e\u003cli\u003eClick on the https link, this will show the cluster. Copy the https URL;\u0026nbsp;this will be used in the following steps. \u003cspan style=\"font-size: 14.6667px;font-family: Arial;color: rgb(0, 0, 0);vertical-align: baseline;white-space: pre-wrap;background-color: transparent;\"\u003e\u003c/span\u003e\u0026nbsp;\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaff9614bcb37eb68/5f9b1f3c83a0a3620dd3b42c/blog-cloud-sandbox-4.png\" data-sys-asset-uid=\"bltaff9614bcb37eb68\" alt=\"blog-cloud-sandbox-4.png\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003ch2\u003eImport Data\u003c/h2\u003e\u003cp\u003eNow, let’s get some data into our Elasticsearch cluster to see the Elastic Stack in action. If you don’t have a sample dataset handy, use one from the various data samples in our\u0026nbsp;\u003ca href=\"https://github.com/elastic/examples\" target=\"_blank\"\u003eGitHub Examples Repo.\u003c/a\u003e I will be using the \u003ca href=\"https://github.com/elastic/examples/tree/master/Common%20Data%20Formats/apache_logs\" target=\"_blank\"\u003eApache logs sample\u003c/a\u003e\u0026nbsp;and \u003ca href=\"https://www.elastic.co/downloads/logstash\" target=\"_blank\"\u003eLogstash\u003c/a\u003e\u0026nbsp;(download your system version). To ingest the logs into our hosted Elasticsearch cluster, we will need to modify the elasticsearch output of the \u003ca href=\"https://github.com/elastic/examples/blob/master/Common%20Data%20Formats/apache_logs/logstash/apache_logstash.conf\" target=\"_blank\"\u003eLogstash config included in the example\u003c/a\u003e.\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e1. Download the repository, and change to the directory that contains the\u0026nbsp;apache_logstash.conf\u0026nbsp;file. Be sure to replace hosts endpoint in the config\u0026nbsp;with your own cluster endpoint (copied in the previous step)\u003cbr /\u003e2. Modify username and password to the user account with write access configured Secure Elasticsearch section. I will be using sa_admin user\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eelasticsearch {\u003cbr /\u003e hosts =\u0026gt; \"https://e66e6e11692c749cc8e09f25e1af4efa.us-west-1.aws.found.io:9243/\"\u003cbr /\u003e user =\u0026gt; \"sa_admin\"\u003cbr /\u003e password =\u0026gt; \"my_f@ncy_p@55w0rd\"\u003cbr /\u003e index =\u0026gt; \"apache_elastic_example\"\u003cbr /\u003e template =\u0026gt; \"./apache_template.json\"\u003cbr /\u003e template_name =\u0026gt; \"apache_elastic_example\"\u003cbr /\u003e template_overwrite =\u0026gt; true \u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp style=\"margin-left: 20px;\"\u003e3. Run the following command to index the data into Elasticsearch via\u0026nbsp;Logstash:\u003c/p\u003e\u003col\u003e\u003c/ol\u003e\u003cpre class=\"prettyprint\"\u003ecat ../apache_logs | \u0026lt;Logstash_Install_Dir\u0026gt;/bin/logstash -f apache_logstash.conf\u003cbr /\u003e\u003c/pre\u003e\u003cp style=\"margin-left: 20px;\"\u003e4. You can verify your data exists in Elasticsearch by going to ES_ENDPOINT/apache_elastic_example/_count, where ES_ENDPOINT is the Elasticsearch endpoint URL.\u0026nbsp;You should see the count as 10000.\u003c/p\u003e\u003col\u003e\u003c/ol\u003e\u003cpre class=\"prettyprint\"\u003e{\"count\":10000,\"_shards\":{\"total\":1,\"successful\":1,\"failed\":0}}\u003cbr /\u003e\u003c/pre\u003e\u003cp style=\"margin-left: 20px;\"\u003e5. You can verify the health of your cluster by going to\u0026nbsp;ES_ENDPOINT/_cat/indices.\u0026nbsp;You should see your apache_elastic_example index listed along with its\u0026nbsp;statistics:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ehealth status index pri rep docs.count docs.deleted store.size pri.store.size\u003cbr /\u003eyellow open .kibana 1 1 2 0 19.1kb 19.1kb\u003cbr /\u003eyellow open apache_elastic_example 1 1 10000 0 7.3mb 7.3mb\u003cbr /\u003e\u003c/pre\u003e\u003ch2\u003eVisualize Data\u003c/h2\u003e\u003cp\u003eNow let's access your Kibana instance and continue with the example\u0026nbsp;instructions to visualize our data.\u003c/p\u003e\u003col\u003e\u003cli\u003eGo to Indices options under the Settings tab and add the apache_elastic_example index to Kibana\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/597a55668fbeeb9e0c70eec2/download?uid=blt090db32089b5e739\" data-sys-asset-uid=\"blt090db32089b5e739\" alt=\"kibana-index.png\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e2.\u0026nbsp;You can look at your data by selecting apache_elastic_example index on the Discovery tab.\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 14.6667px;font-family: Arial;color: rgb(0, 0, 0);vertical-align: baseline;white-space: pre-wrap;background-color: transparent;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/uploads/597a5a41e8291db20cf37569/download?uid=bltabeb130913ba393c\" data-sys-asset-uid=\"bltabeb130913ba393c\" alt=\"another_example.png\"/\u003e\u003c/p\u003e\u003cp style=\"margin-left: 20px;\"\u003e3. Import the examples dashboard by clicking\u0026nbsp;on Settings\u0026nbsp;\u0026gt;\u0026nbsp;Objects\u0026nbsp;\u0026gt;\u0026nbsp;Import and selecting the\u0026nbsp;\u003ca href=\"https://github.com/elastic/examples/blob/master/Common%20Data%20Formats/apache_logs/logstash/apache_kibana-4.json\" target=\"_blank\"\u003eapache_kibana-4.json\u003c/a\u003e\u0026nbsp;file.\u0026nbsp;You can view this dashboard by clicking on the view button (eye icon) or by going to the Dashboards tab and clicking the Load Saved Dashboard button.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaa1b0173cc5b053b/5f9b1f5b878c0d548cdc27c2/blog-cloud-sandbox-7.png\" data-sys-asset-uid=\"bltaa1b0173cc5b053b\" alt=\"blog-cloud-sandbox-7.png\" style=\"display: block;margin: auto;\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eNow you have some sample Apache log data in Elasticsearch and you can begin to get some insight and more importantly value from your logs. You can continue exploring\u0026nbsp;with other sample datasets from the \u003ca href=\"https://github.com/elastic/examples\" target=\"_blank\"\u003eExamples repo\u003c/a\u003e\u0026nbsp; and the\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/kibana/4.5/getting-started.html#tutorial-load-dataset\" target=\"_blank\"\u003eKibana getting started guide\u003c/a\u003e \u0026nbsp;or\u0026nbsp;start sending your own data by using Logstash or Beats.\u003c/p\u003e\u003cp\u003eHere are some other useful links to help you on the journey of using the Elastic Stack on Cloud.\u003c/p\u003e\u003cul\u003e\u003cli\u003eCloud\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/cloud/current/index.html\u003c/a\u003e\u003c/li\u003e\u003cli\u003eKibana\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/kibana/4.5/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/kibana/4.5/index.html\u003c/a\u003e\u003c/li\u003e\u003cli\u003eSecurity\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/shield/2.3/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/shield/2.3/index.html\u003c/a\u003e\u003c/li\u003e\u003cli\u003eElasticsearch\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/2.4/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/elasticsearch/reference/2.4/index.html\u003c/a\u003e\u003c/li\u003e\u003cli\u003eBeats\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/beats/libbeat/1.3/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/beats/libbeat/1.3/index.html\u003c/a\u003e\u003c/li\u003e\u003cli\u003eLogstash\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/logstash/2.4/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/logstash/2.4/index.html\u003c/a\u003e\u003c/li\u003e\u003cli\u003eThe Definitive Guide \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/index.html\" target=\"_blank\"\u003ehttps://www.elastic.co/guide/en/elasticsearch/guide/current/index.html\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eOr, you can continue your Training with some official classes by some world class Education Engineers:\u0026nbsp;\u003ca href=\"https://www.elastic.co/training\" target=\"_blank\"\u003ehttps://www.elastic.co/training\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eEditor's Note\u0026nbsp;(July 27, 2017): We've updated some links and content to direct to more current resources (e.g., GitHub repos and documentation)\u0026nbsp;and reflect more accurate information.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:01:52.721Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt2fe033ff23dccbec","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T06:33:32.976Z","updated_at":"2018-10-11T06:33:32.976Z","content_type":"image/jpeg","file_size":"208693","filename":"elastic-cloud-tutorial-full-bleed.jpg","title":"elastic-cloud-tutorial-full-bleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T18:14:58.935Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2fe033ff23dccbec/5bbeeebceb7e90a514e6e4b3/elastic-cloud-tutorial-full-bleed.jpg"},"markdown_l10n":"","publish_date":"2016-06-01T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Cloud Tutorial: Getting Started with a sample dataset","seo_description_l10n":"This step-by-step set of instructions will walk you through setting up an Elastic Cloud account, creating and securing a Elasticsearch cluster, importing data, and visualizing it in Kibana.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt9249a7101bf25edc","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T13:36:09.265Z","updated_at":"2018-10-09T13:36:09.265Z","content_type":"image/jpeg","file_size":"103281","filename":"elastic-cloud-tutorial.jpg","title":"elastic-cloud-tutorial.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T18:14:58.935Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9249a7101bf25edc/5bbcaec90e6edaf014d23bee/elastic-cloud-tutorial.jpg"},"title":"Tutorial: Getting Started with Elastic Cloud with a Sample Dataset","title_l10n":"Tutorial: Getting Started with Elastic Cloud with a Sample Dataset","updated_at":"2025-03-10T11:15:21.806Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/building-cloud-sandbox-with-sample-data-v2","publish_details":{"time":"2025-03-10T11:15:25.258Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb788399e560fae32","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt4ca268ce71bf38df"],"body_l10n":"\u003ch4\u003eWelcome to Keeping up with Kibana! This is a series of posts on new developments in the Kibana project and any related learning resources and events.\u003c/h4\u003e\u003cp\u003eThe Kibana team continues to move forward on its large initiatives. We’re throwing more resources against getting Canvas to beta. Dave is joining the team for the next two weeks to help polish up the design and get it looking at its best. We’re already making sizable progress there and Catherine’s done a great job migrating to EUI components. With all this early effort Canvas will be our first plugin to use Kibana 7’s styling entirely.\u003c/p\u003e\u003cp\u003eThe security team continues their tear of moving Kibana to a role-based access control world. While still early, we’re close on merging some first-phase PRs that will allow us to move to stage 2 of adding individual workspaces to the app. Once that’s in this will let teams segment their content into buckets viewable by certain roles. This should help all of our larger customers who have trouble organizing their 1000s of Kibana saved objects across hundreds of consumers.\u003c/p\u003e\u003cp\u003eWe’re also making progress on moving our visualization libraries into EUI where they can be cohesively styled and made more reusable. That team is also very close to merging in a new inspector, which should greatly improve the experience of seeing the data behind each visualization when viewed through a dashboard.\u003c/p\u003e\u003ch3\u003eCanvas\u003c/h3\u003e\u003cp\u003eThe team continues to focus on features and fixes related to Beta release and eventual migration to the X-Pack codebase.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc5d59108544638e2/5f9b21e31f9166620ed86f01/blog-Keeping-up-with-Kibana-2018-06-18.png\" data-sys-asset-uid=\"bltc5d59108544638e2\" alt=\"blog-Keeping-up-with-Kibana-2018-06-18.png\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003eRelease with support for Elastic SQL (in version 2002) \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/443\"\u003e#443\u003c/a\u003e \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/642\"\u003e#642\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eMore work for Reporting; correctly handle element done events\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana-canvas/pull/641\"\u003e#641\u003c/a\u003e\u003c/li\u003e\u003cli\u003eAdded temporary SCSS build for Design to use, pending SCSS support in Kibana \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/670\"\u003e#670\u003c/a\u003e\u003c/li\u003e\u003cli\u003eAdded legend config to pie charts \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/672\"\u003e#672\u003c/a\u003e\u003c/li\u003e\u003cli\u003eHide stack traces on errors when in Production mode \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/666\"\u003e#666\u003c/a\u003e\u003c/li\u003e\u003cli\u003eMore EUI work \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/650\"\u003e#650\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFixed issue when deleting the only workpad \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/682\"\u003e#682\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFixed issue where errros wrapped in Boom were causing unhandled Promise rejections \u003ca href=\"https://github.com/elastic/kibana-canvas/pull/673\"\u003e#673\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eDesign\u003c/h3\u003e\u003cp\u003eThe design team continuing on mocks for Beats central management. Caroline is working through designs for a new Visualizations editor which we’ll be showing off soon. Chandler closed a bunch of blockers around tables and tabs in EUI and built out a service for fixed position popovers that should solve our positioning woes in EUI soon. Dave started work on \u003ca href=\"http://snid.es/1M1q2u2k1Q17\"\u003ecleaning up Canvas\u003c/a\u003e and hopes to have it looking sharp in the next couple weeks. We’re also working toward getting a \u003ca href=\"https://github.com/elastic/eui/pull/921\"\u003esuper selector component\u003c/a\u003e added to EUI soon.\u003c/p\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003eRefactor EuiTabbedContent to track its selected tab by name \u003ca href=\"https://github.com/elastic/eui/pull/931\"\u003e#931\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eCustom column sort values for EuiInMemoryTable \u003ca href=\"https://github.com/elastic/eui/pull/929\"\u003e#929\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFlyout alterations \u003ca href=\"https://github.com/elastic/eui/pull/925\"\u003e#925\u003c/a\u003e\u003c/li\u003e\u003cli\u003eFix default sort comparator to logically handle null/undefined values \u003ca href=\"https://github.com/elastic/eui/pull/922\"\u003e#922\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eDiscovery\u003c/h3\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003e[Context view] Incrementally increase context time window \u003ca href=\"https://github.com/elastic/kibana/pull/16878\"\u003e#16878\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eAllow overwriting filters when adding via `queryFilter` \u003ca href=\"https://github.com/elastic/kibana/pull/19754\"\u003e#19754\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eGeo\u003c/h3\u003e\u003cp\u003eThe team focused on the Elastic Map Service landing page and fixing the Sophox application we use to produce our vector data layers. Work continues on the \u003ca href=\"https://github.com/elastic/kibana/issues/19582\"\u003ePhase 1\u003c/a\u003e of the GIS App first seen at Elastic{on}.\u003c/p\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003eEMS Landing Page can be now configured to use staging or production manifests. \u003ca href=\"https://github.com/elastic/ems-landing-page/pull/11\"\u003ehttps://github.com/elastic/ems-landing-page/pull/1...\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/ems-landing-page/pull/11\"\u003e\u003cbr /\u003e\u003c/a\u003eMinimize JavaScript for EMS landing page \u003ca href=\"https://github.com/elastic/ems-landing-page/pull/6\"\u003ehttps://github.com/elastic/ems-landing-page/pull/6\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eManagement\u003c/h3\u003e\u003cp\u003eThe team focused on wrapping up phase 1 of index lifecycle management and phase 1 of rollup support in Kibana.\u0026nbsp; Additionally, some cleanup work is still being done on console.\u003c/p\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/kibana/pull/19760\"\u003ehttps://github.com/elastic/kibana/pull/19760\u003c/a\u003e adds documentation links to console\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eOperations\u003c/h3\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003eRemove node version validator from git pre-commit hook script \u003ca href=\"https://github.com/elastic/kibana/pull/19950\"\u003e#19950\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eRemove devDependencies from licenses report by default allowing to include dem with --dev flag\u003ca href=\"https://github.com/elastic/kibana/pull/19626\"\u003e#19626\u003c/a\u003e\u003c/li\u003e\u003cli\u003eChanged eslint extends order in order to allow kibana eslint rules to be more important than the ones from prettier \u003ca href=\"https://github.com/elastic/eui/pull/927\"\u003e#927\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eQA\u003c/h3\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003eFix for timelion flaky tests PR: \u003ca href=\"https://github.com/elastic/kibana/pull/19996\"\u003e19996\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eConverted management tests to ES6 format PR: \u003ca href=\"https://github.com/elastic/kibana/pull/19870\"\u003e19870\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eSecurity\u003c/h3\u003e\u003cp\u003eThe first phase of our RBAC project is out for review! This phase is the first step to controlling access to Kibana using custom application permissions, as opposed to direct access to the Kibana index. We put some final touches on this PR, which allows us to introduce this feature in a backwards compatible manner, without requiring any changes to the kibana.yml configuration. This all sets us up nicely for our upcoming second phase, which introduces Spaces (\u003ca href=\"https://github.com/elastic/kibana/issues/18948\"\u003e#18948\u003c/a\u003e)!\u003c/p\u003e\u003cp\u003eSpeaking of Spaces, we collaborated with the Design Team this week to prototype a new UI for managing Kibana privileges within individual spaces. We also added the ability to customize the “avatar” for each space.\u003c/p\u003e\u003ch3\u003eSharing\u003c/h3\u003e\u003ch5\u003ePRs\u003c/h5\u003e\u003cul\u003e\u003cli\u003eFix gaps in sample data: \u003ca href=\"https://github.com/elastic/kibana/issues/19912\"\u003ehttps://github.com/elastic/kibana/issues/19912\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/elastic/kibana/issues/19912\"\u003e\u003cbr /\u003e\u003c/a\u003eAccessibility fixes:\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/pull/19838\"\u003ehttps://github.com/elastic/kibana/pull/19838\u003c/a\u003e,\u0026nbsp;\u003ca href=\"https://github.com/elastic/kibana/issues/19830\"\u003ehttps://github.com/elastic/kibana/issues/19830\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch3\u003eVisualizations\u003c/h3\u003e\u003cp\u003eExplicit passing of filters and queries (#19172) has been merged. We now no longer rely on inheritance between the application and individual visualizations to apply global filters/queries. Every application (like dashboard) is now required to pass in all global context (filters, queries) explicitly to any visualization. That will allow for panel individual filters/queries and also cleans up some quiet old tech-debts.\u003c/p\u003e\u003cp\u003eThe last blocking issues on the new Inspector are nearly resolved and our work on the new XYAxis chart component (\u003ca href=\"https://github.com/elastic/eui/issues/536\"\u003eeui/#536\u003c/a\u003e) is moving forward. We've also started adding extension points into the Editor that are required to support roll-up indexes in the visualization editor.\u003c/p\u003e\u003ch3\u003ePRs\u003c/h3\u003e\u003cul\u003e\u003cli\u003eRefactoring Markdown lifecycle methods to React 16.3 \u003ca href=\"https://github.com/elastic/kibana/pull/19436\"\u003e(#19436\u003c/a\u003e)\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e","category":[],"created_at":"2019-04-01T13:13:30.163Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt29843bb98ba59a2a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:37:11.833Z","updated_at":"2018-10-11T05:37:11.833Z","content_type":"image/jpeg","file_size":"71803","filename":"blog-kibana-banner.jpg","title":"blog-kibana-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-18T15:49:05.384Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt29843bb98ba59a2a/5bbee187eb7e90a514e6e46b/blog-kibana-banner.jpg"},"markdown_l10n":"","publish_date":"2018-06-18T16:31:33.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"Canvas adds support for Elastic SQL. The first phase of role-based access control is out for review.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"canvas.png","uid":"bltbf64f655ce7bbd44","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T07:00:17.079Z","updated_at":"2019-01-05T07:00:17.079Z","content_type":"image/png","file_size":"61177","filename":"canvas.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-30T19:59:05.130Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf64f655ce7bbd44/5c30560193d9791a70cd73fb/canvas.png"},"title":"Keeping up with Kibana: This week in Kibana for June 18th, 2018","title_l10n":"Keeping up with Kibana: This week in Kibana for June 18th, 2018","updated_at":"2025-03-10T11:13:02.103Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/Keeping-up-with-Kibana-2018-06-18","publish_details":{"time":"2025-03-10T11:13:05.615Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6a34c8b32c6d194b","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"A new visualization type in Kibana lets you create custom visualizations using Vega, an open source, JSON-based, declarative language.","author":["bltab86dacd5699378c"],"body_l10n":"\u003cp\u003e\u003cem\u003eInterested in a\u0026nbsp;walkthrough of Vega-based visualizations in Kibana? \u003c/em\u003e\u003ca href=\"/webinars/creating-custom-kibana-visualizations-with-vega-plugin\"\u003e\u003cem\u003eCheck out this video\u003c/em\u003e\u003c/a\u003e\u003cem\u003e.\u003c/em\u003e\u003c/p\u003e\u003cp\u003eBeginning with Kibana 6.2, users can now go beyond the built-in visualizations offered. This new visualization type lets users create custom visualizations without developing their own plugin using an open source JSON-based declarative language called \u003ca href=\"https://vega.github.io/vega/examples/\"\u003eVega\u003c/a\u003e, or its simpler version called \u003ca href=\"https://vega.github.io/vega-lite/examples/\"\u003eVega-Lite\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eUnlike other visualizations, the Vega vis is a blank canvas on which you, the developer, can draw visual elements based on one or more data sources including custom URLs. For example, you can design a Sankey diagram of the network traffic patterns. This Sankey visualization will be demonstrated in the \u003ca href=\"/blog/sankey-visualization-with-vega-in-kibana\"\u003enext blog post\u003c/a\u003e.\u003c/p\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt457ad68e7663aa65/5f971b5945fa7d72ddd1dbfe/blog-custom-vega-1.png\" width=\"624\" height=\"311\" style=\"width: 624;height: 311;\"/\u003e\u003c/p\u003e\u003ch2\u003eHello World Scatter Plot with Vega-Lite\u003c/h2\u003e\u003cp\u003eOur first example will be drawing a scatter plot from the sample Logstash data using the simpler Vega-Lite language.\u003c/p\u003e\u003ch3\u003eData\u003c/h3\u003e\u003cp\u003eThe first step of any Vega visualization is to get the right data using Elasticsearch query language. We will use 3 fields from the sample Logstash data. The data was generated using \u003ca href=\"https://github.com/elastic/makelogs#makelogs\"\u003emakelogs utility\u003c/a\u003e. This query can be tried in the “dev tools” tab to see the full result structure. We will use the same query as part of the Vega code below.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eGET logstash-*/_search\u003cbr /\u003e{\u003cbr /\u003e \"size\": 10,\u003cbr /\u003e \"_source\": [\"@timestamp\", \"bytes\", \"extension\"]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe output is an array of these elements inside the { hits: { hits: [...] }} structure:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{ \"hits\": { \"hits\": [\u003cbr /\u003e {\u003cbr /\u003e \"@timestamp\": \"2018-02-01T18:05:55.363Z\",\u003cbr /\u003e \"bytes\": 2602,\u003cbr /\u003e \"extension\": \"jpg\"\u003cbr /\u003e },\u003cbr /\u003e ...\u003cbr /\u003e] }}\u003cbr /\u003e\u003c/pre\u003e\u003ch3\u003eDrawing\u003c/h3\u003e\u003cp\u003eNow create a new Vega visualization. If the Vega vis is not listed, ensure lab visualizations in \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/advanced-options.html\"\u003eadvanced settings\u003c/a\u003e (visualize:enableLabs) are enabled. Delete the default code, and paste this instead. Vega vis is written using JSON superset called \u003ca href=\"https://hjson.org/\"\u003eHJSON\u003c/a\u003e.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e $schema: https://vega.github.io/schema/vega-lite/v2.json\u003cbr /\u003e data: {\u003cbr /\u003e # URL object is a context-aware query to Elasticsearch\u003cbr /\u003e url: {\u003cbr /\u003e # The %-enclosed keys are handled by Kibana to modify the query\u003cbr /\u003e # before it gets sent to Elasticsearch. Context is the search\u003cbr /\u003e # filter as shown above the dashboard. Timefield uses the value \u003cbr /\u003e # of the time picker from the upper right corner.\u003cbr /\u003e %context%: true\u003cbr /\u003e %timefield%: @timestamp\u003cbr /\u003e index: logstash-*\u003cbr /\u003e body: {\u003cbr /\u003e size: 10000\u003cbr /\u003e _source: [\"@timestamp\", \"bytes\", \"extension\"]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e # We only need the content of hits.hits array\u003cbr /\u003e format: {property: \"hits.hits\"}\u003cbr /\u003e }\u003cbr /\u003e # Parse timestamp into a javascript date value\u003cbr /\u003e transform: [\u003cbr /\u003e {calculate: \"toDate(datum._source['@timestamp'])\", as: \"time\"}\u003cbr /\u003e ]\u003cbr /\u003e # Draw a circle, with x being the time field, and y - number of bytes\u003cbr /\u003e mark: circle\u003cbr /\u003e encoding: {\u003cbr /\u003e x: {field: \"time\", type: \"temporal\"}\u003cbr /\u003e y: {field: \"_source.bytes\", type: \"quantitative\"}\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt672e9a61067273f6/5f971b5989353a72dcaeae99/blog-custom-vega-2.png\" width=\"490\" height=\"364\" style=\"width: 490;height: 364;\"/\u003e\u003c/p\u003e\u003cp\u003eWe should make a few more cleanups and improvements:\u003c/p\u003e\u003cul\u003e\u003cli\u003eDisable X axis title by adding\u0026nbsp;axis: { title: null } to x encoding\u003c/li\u003e\u003cli\u003eSet Y axis title with axis: { title: \"Transferred bytes\" }\u003c/li\u003e\u003cli\u003eMake dots different color and shape depending on the extension field: add this to encodings:\u003c/li\u003e\u003c/ul\u003e\u003cpre class=\"prettyprint\"\u003ecolor: {field:\"_source.extension\", type:\"nominal\", legend: {title:\"File type\"}}\u003cbr /\u003eshape: {field:\"_source.extension\", type:\"nominal\"}\u003cbr /\u003e\u003c/pre\u003e\u003ch2 style=\"text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt124f340e20cfaf62/5f971b5e1f9166620ed85bdc/blog-custom-vega-3.png\" width=\"499\" height=\"366\" style=\"width: 499;height: 366;\"/\u003e\u003c/h2\u003e\u003cp\u003eWe could even change the visualization entirely by putting extension as the y axis, and using size. Replace all of encodings with these:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ex: {field: \"time\", type: \"temporal\", axis: {title: null}}\u003cbr /\u003ey: {field: \"_source.extension\", type: \"nominal\", axis: {title: null}}\u003cbr /\u003esize: {field: \"_source.bytes\", type: \"quantitative\", legend: null}\u003cbr /\u003ecolor: {field: \"_source.extension\", type: \"nominal\", legend: null}\u003cbr /\u003e\u003c/pre\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt27a9b03a8013629d/5f971b59432f517518d3f851/blog-custom-vega-4.png\" style=\"border: medium none;transform: rotate(0rad);\" width=\"464\" height=\"376\"/\u003e\u003c/p\u003e\u003ch2\u003eBuilding Trend Indicator with Vega\u003c/h2\u003e\u003cp\u003eFor the Vega example, let’s build a very simple trend indicator to compare the number of events in the last 10 minutes vs the 10 minutes before that.\u003c/p\u003e\u003cp style=\"text-align: center;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2a3fb28f33e54cf3/5f971b59cb9eba781f084e21/blog-custom-vega-5.png\" style=\"border: medium none;transform: rotate(0rad);\" width=\"624\" height=\"119\"/\u003e\u003c/p\u003e\u003cp\u003eWe can ask Elasticsearch for the 10 min aggregates, but those aggregates would be aligned on 10 minute boundaries, rather than being the “last 10 minutes”. Instead, we will ask for the last 20 aggregates, 1 minute each, excluding the current (incomplete) minute. The extended_bounds param ensures that even when there is no data, we still get a count=0 result for each bucket. Try running this query in the Dev Tools tab - copy/paste it, and hit the green play button.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eGET logstash-*/_search\u003cbr /\u003e{\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"time_buckets\": {\u003cbr /\u003e \"date_histogram\": {\u003cbr /\u003e \"field\": \"@timestamp\",\u003cbr /\u003e \"interval\": \"1m\",\u003cbr /\u003e \"extended_bounds\": { \"min\": \"now-20m/m\", \"max\": \"now-1m/m\" }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"range\": {\u003cbr /\u003e \"@timestamp\": { \"gte\": \"now-20m/m\", \"lte\": \"now-1m/m\" }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\": 0\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe result would be\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e // ... skipping some meta information ...\u003cbr /\u003e \"aggregations\": {\u003cbr /\u003e \"time_buckets\": {\u003cbr /\u003e \"buckets\": [\u003cbr /\u003e {\u003cbr /\u003e \"key_as_string\": \"2018-02-09T00:52:00.000Z\",\u003cbr /\u003e \"key\": 1518137520000,\u003cbr /\u003e \"doc_count\": 1\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"key_as_string\": \"2018-02-09T00:53:00.000Z\",\u003cbr /\u003e \"key\": 1518137580000,\u003cbr /\u003e \"doc_count\": 3\u003cbr /\u003e },\u003cbr /\u003e // ... 18 more objects\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eAnd the actual Vega spec with inline comments:\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e{\u003cbr /\u003e # Schema indicates that this is Vega code\u003cbr /\u003e $schema: https://vega.github.io/schema/vega/v3.0.json\u003cbr /\u003e # All our data sources are listed in this section\u003cbr /\u003e data: [\u003cbr /\u003e {\u003cbr /\u003e name: values\u003cbr /\u003e # when url is an object, it is treated as an Elasticsearch query\u003cbr /\u003e url: {\u003cbr /\u003e index: logstash-*\u003cbr /\u003e body: {\u003cbr /\u003e aggs: {\u003cbr /\u003e time_buckets: {\u003cbr /\u003e date_histogram: {\u003cbr /\u003e field: @timestamp\u003cbr /\u003e interval: 1m\u003cbr /\u003e extended_bounds: {min: \"now-20m/m\", max: \"now-1m/m\"}\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e query: {\u003cbr /\u003e range: {\u003cbr /\u003e @timestamp: {gte: \"now-20m/m\", lte: \"now-1m/m\"}\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e size: 0\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e # We only need a specific array of values from the response\u003cbr /\u003e format: {property: \"aggregations.time_buckets.buckets\"}\u003cbr /\u003e # Perform these transformations on each of the 20 values from ES\u003cbr /\u003e transform: [\u003cbr /\u003e # Add \"row_number\" field to each value -- 1..20\u003cbr /\u003e {\u003cbr /\u003e type: window\u003cbr /\u003e ops: [\"row_number\"]\u003cbr /\u003e as: [\"row_number\"]\u003cbr /\u003e }\u003cbr /\u003e # Break results into 2 groups, group #0 with row_number 1..10,\u003cbr /\u003e # and group #1 with row numbers being 11..20\u003cbr /\u003e {type: \"formula\", expr: \"floor((datum.row_number-1)/10)\", as: \"group\"}\u003cbr /\u003e # Group 20 values into an array of two elements, one for\u003cbr /\u003e # each group, and sum up the doc_count fields as \"count\"\u003cbr /\u003e {\u003cbr /\u003e type: aggregate\u003cbr /\u003e groupby: [\"group\"]\u003cbr /\u003e ops: [\"sum\"]\u003cbr /\u003e fields: [\"doc_count\"]\u003cbr /\u003e as: [\"count\"]\u003cbr /\u003e }\u003cbr /\u003e # At this point \"values\" data source should look like this:\u003cbr /\u003e # [ {group:0, count: nnn}, {group:1, count: nnn} ]\u003cbr /\u003e # Check this with F12 or Cmd+Opt+I (browser developer tools),\u003cbr /\u003e # and run this in console:\u003cbr /\u003e # console.table(VEGA_DEBUG.view.data('values'))\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e {\u003cbr /\u003e # Here we create an artificial dataset with just a single empty object\u003cbr /\u003e name: results\u003cbr /\u003e values: [\u003cbr /\u003e {}\u003cbr /\u003e ]\u003cbr /\u003e # we use transforms to add various dynamic values to the single object\u003cbr /\u003e transform: [\u003cbr /\u003e # from the 'values' dataset above, get the first count as \"last\",\u003cbr /\u003e # and the one before that as \"prev\" fields.\u003cbr /\u003e {type: \"formula\", expr: \"data('values')[0].count\", as: \"last\"}\u003cbr /\u003e {type: \"formula\", expr: \"data('values')[1].count\", as: \"prev\"}\u003cbr /\u003e # Set two boolean fields \"up\" and \"down\" to simplify drawing\u003cbr /\u003e {type: \"formula\", expr: \"datum.last\u0026gt;datum.prev\", as: \"up\"}\u003cbr /\u003e {type: \"formula\", expr: \"datum.last\u0026lt;datum.prev\", as: \"down\"}\u003cbr /\u003e # Calculate the change as percentage, with special handling of 0\u003cbr /\u003e {\u003cbr /\u003e type: formula\u003cbr /\u003e expr: \"if(datum.last==0, if(datum.prev==0,0,-1), (datum.last-datum.prev)/datum.last)\"\u003cbr /\u003e as: percentChange\u003cbr /\u003e }\u003cbr /\u003e # Calculate which symbol to show - up or down arrow, or a no-change dot\u003cbr /\u003e {\u003cbr /\u003e type: formula\u003cbr /\u003e expr: if(datum.up,'🠹',if(datum.down,'🠻','🢝'))\u003cbr /\u003e as: symbol\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e # Marks is a list of all drawing elements.\u003cbr /\u003e # For this graph we only need a single text mark.\u003cbr /\u003e marks: [\u003cbr /\u003e {\u003cbr /\u003e type: text\u003cbr /\u003e # Text mark executes once for each of the values in the results,\u003cbr /\u003e # but results has just one value in it. We could have also used it\u003cbr /\u003e # to draw a list of values.\u003cbr /\u003e from: {data: \"results\"}\u003cbr /\u003e encode: {\u003cbr /\u003e update: {\u003cbr /\u003e # Combine the symbol, last value, and the formatted percentage\u003cbr /\u003e # change into a string\u003cbr /\u003e text: {\u003cbr /\u003e signal: \"datum.symbol + ' ' + datum.last + ' ('+ format(datum.percentChange, '+.1%') + ')'\"\u003cbr /\u003e }\u003cbr /\u003e # decide which color to use, depending on the value\u003cbr /\u003e # being up, down, or unchanged\u003cbr /\u003e fill: {\u003cbr /\u003e signal: if(datum.up, '#00ff00', if(datum.down, '#ff0000', '#0000ff'))\u003cbr /\u003e }\u003cbr /\u003e # positioning the text in the center of the window\u003cbr /\u003e align: {value: \"center\"}\u003cbr /\u003e baseline: {value: \"middle\"}\u003cbr /\u003e xc: {signal: \"width/2\"}\u003cbr /\u003e yc: {signal: \"height/2\"}\u003cbr /\u003e # Make the size of the font adjust with the size of the visualization\u003cbr /\u003e fontSize: {signal: \"min(width/10, height)/1.3\"}\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThis is the first of many for the Vega blog post series! Be on the lookout for our next post where we’ll \u003ca href=\"/blog/sankey-visualization-with-vega-in-kibana\"\u003ecreate a Sankey chart\u003c/a\u003e. And make sure to \u003ca href=\"/webinars/creating-custom-kibana-visualizations-with-vega-plugin\"\u003echeck out this video walkthrough of Kibana visualizations with Vega\u003c/a\u003e.\u003c/p\u003e","category":[{"uid":"bltb79594af7c5b4199","_version":3,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:05.640Z","created_by":"blt3044324473ef223b70bc674c","key":"product","label_l10n":"Product","tags":[],"title":"Product","updated_at":"2024-05-10T13:44:20.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.527Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:02:23.376Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"blog-vega-fb.jpg","uid":"blt8e4a071e6ba82b81","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T13:48:18.560Z","updated_at":"2019-02-04T13:48:18.560Z","content_type":"image/jpeg","file_size":"153196","filename":"blog-vega-fb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T00:38:13.818Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8e4a071e6ba82b81/5c5842a2516e21cf0b2a124c/blog-vega-fb.jpg"},"markdown_l10n":"","publish_date":"2018-02-20T18:31:07.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":["vega"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"blog-vega-thumb.jpg","uid":"blt17a214e3e183063e","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T07:04:08.921Z","updated_at":"2019-01-05T07:04:08.921Z","content_type":"image/jpeg","file_size":"42461","filename":"blog-vega-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T00:38:13.818Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17a214e3e183063e/5c3056e8aab458d30b314274/blog-vega-thumb.jpg"},"title":"Custom Vega Visualizations in Kibana 6.2","title_l10n":"Custom Vega Visualizations in Kibana 6.2","updated_at":"2025-03-10T11:08:14.291Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/custom-vega-visualizations-in-kibana","publish_details":{"time":"2025-03-10T11:08:21.041Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb4b1e73e35d30243","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"This blog post talks about how you can use Reporting and Watcher integration on Elastic Cloud to schedule the delivery of PDF reports.","author":["bltc511a9eb9519c0e7"],"body_l10n":"\u003cp\u003eEverybody gets a report!\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eWe recently \u003ca href=\"https://www.elastic.co/blog/reporting-2-4-0-released\"\u003ereleased\u003c/a\u003e the first version of Reporting for Kibana which gives users the ability to generate a PDF report from saved Kibana dashboards. \u0026nbsp;By leveraging \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/introduction.html\"\u003eWatcher\u003c/a\u003e’s email action, you can send PDF reports regularly, or only when certain events have occurred.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIn this blog post, I will demonstrate the power of Reporting and Watcher integration and how we are dogfooding this in house. \u0026nbsp;For our example use case, we are sending bi-weekly PDF reports to our systems team manager if there are any helpdesk tickets filed by internal employees mentioning a specific keyword.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eTo get up and running quickly, I have set up an instance on \u003ca href=\"https://www.elastic.co/cloud/as-a-service\"\u003eElastic Cloud\u003c/a\u003e because it is \u003cem\u003eso\u003c/em\u003e easy to get Elasticsearch (with authentication via \u003ca href=\"https://www.elastic.co/guide/en/shield/current/index.html\"\u003eShield\u003c/a\u003e) and Kibana running on the latest and greatest versions. \u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe following example below was created against ES 2.4.0 with Kibana 4.6.1 (when Reporting was originally released).\u0026nbsp;There have been changes in Cloud and Reporting since then. \u0026nbsp; I have added notes in the sections below related to the changes in our products since the original release.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eStep 1: \u0026nbsp;Populate the Data\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eFirst step is simply to populate Elasticsearch with the data you are reporting against. \u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWe track helpdesk tickets internally using Salesforce’s Service Cloud. \u0026nbsp;In this case, I have written a custom Logstash salesforce plugin using the \u003ca href=\"https://github.com/ejholmes/restforce\"\u003erestforce\u003c/a\u003e ruby gem to join object data related to posts, emails and chatter comments from various objects so we can get tickets with the full feed history intact.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eStep 2: \u0026nbsp;Install the Reporting Plugin\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"margin-top: 0pt;margin-bottom: 0pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003e\u003cstrong\u003e(Starting in 5.0+, Reporting is now installed with X-Pack on Elastic Cloud. \u0026nbsp;It is no longer necessary to install the Reporting plugin separately).\u003c/strong\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eReporting is built on top of Kibana, so you will have to set up Kibana and \u003ca href=\"https://www.elastic.co/guide/en/reporting/current/getting-started.html\"\u003einstall the Reporting plugin\u003c/a\u003e. \u0026nbsp;If you are running on Elastic Cloud, the Reporting plugin is already installed for you when you enable Kibana :)\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3eec3bae4c04e1ff/5f88649c4671ee30c689e87c/report-1.png\" height=\"91\" width=\"84\" style=\"width: 84;height: 91;\"/\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"margin-top: 18pt;margin-bottom: 6pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003eStep 3: \u0026nbsp;Secure Your\u0026nbsp;Data\u003c/h2\u003e\u003ch2 dir=\"ltr\" style=\"margin-top: 18pt;margin-bottom: 6pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003e\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBecause the data for my use case can potentially be sensitive, I have enabled Shield in my Elastic Cloud instance (“configure Shield”) for authentication. \u0026nbsp;From the Elastic Cloud instance,\u0026nbsp;simply\u0026nbsp;click on the link and then configure the users and roles accordingly. \u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2b013e82631ad8f6/5f88649aa50ed742e7fcc321/report-2.png\" height=\"40\" width=\"546\" style=\"width: 546;height: 40;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eYou can create\u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/shield/current/reporting.html#reporting\"\u003eusers with a reporting role\u003c/a\u003e\u0026nbsp;for report generation purposes.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eNote: \u0026nbsp;When installing Kibana in your local environment and enabling security via Shield, keep in mind that Reporting on 2.4 requires the \u003ca href=\"https://www.elastic.co/guide/en/shield/current/kibana.html#kibana\"\u003eKibana Shield plugin\u003c/a\u003e, and the Kibana Shield plugin in turn requires \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/production.html#enabling-ssl\"\u003eSSL to be enabled\u003c/a\u003e in Kibana. \u0026nbsp;Starting in 5.0+, we no longer require SSL to be enabled in Kibana to use the Kibana Shield plugin (certainly, you may still want to enable SSL for production deployments). \u0026nbsp;Since I am running on Elastic Cloud, SSL is already enabled by default. Yay!\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eStep 4: \u0026nbsp;Create a Dashboard and View the Report\u003c/h2\u003e\u003cp dir=\"ltr\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\" style=\"margin-top: 0pt;margin-bottom: 0pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003e\u003cstrong\u003e(For 5.0+, refer to the Reporting\u0026nbsp;\u003c/strong\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/5.5/xpack-reporting.html\" target=\"_blank\"\u003e\u003cstrong\u003edocumentation\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\u0026nbsp;for the latest screens and instructions).\u003c/strong\u003e\u003c/p\u003e\u003cp dir=\"ltr\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\" style=\"margin-top: 0pt;margin-bottom: 0pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eCurrently, you can only generate a PDF report against a dashboard if the dashboard is an existing/saved object in Kibana.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt292a06e83bc57255/5f88649c1252ff30caf61f59/report-3.png\" height=\"388\" width=\"466\" style=\"width: 466;height: 388;\"/\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eOnce you have created the desired dashboard, click on the “Generate Report” icon (rightmost icon).\u0026nbsp; This will give you a button to generate a Printable PDF report. \u0026nbsp;Clicking on the button will issue a one-time reporting request to the reporting queue. \u0026nbsp;\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt59100050e2c2a73e/5f88649aace59e4b82917b68/report-4.png\" height=\"60\" width=\"624\" style=\"width: 624;height: 60;\"/\u003e\u003c/p\u003e\u003cp\u003eWhen the report is ready, you can locate the report in the list of generated reports from \u003cstrong\u003eSettings \u0026gt; Reporting \u003c/strong\u003eand download it using\u0026nbsp;the corresponding action icon.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8840b3777b0c45f8/5f88649cf9d3bf27fac3be21/report-5.png\" height=\"141\" width=\"624\" style=\"width: 624;height: 141;\"/\u003e\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"margin-top: 18pt;margin-bottom: 6pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003eStep 5: \u0026nbsp;Create a Watch to Send the Report\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cstrong\u003e(On 5.0+, Watcher comes packaged with X-pack which is automatically installed on Elastic Cloud. \u0026nbsp;In the above example, it uses the \"http\" attachment type of the email action which applies to Reporting 4.6 and 5.0. \u0026nbsp;Starting in 5.1+, we now have a specialized \"\u003c/strong\u003e\u003ca href=\"https://www.elastic.co/guide/en/x-pack/5.5/actions-email.html#configuring-email\" target=\"_blank\"\u003e\u003cstrong\u003ereporting\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e\"\u0026nbsp;attachment type specifically for integration between Alerting/Watcher and Reporting. \u0026nbsp;Refer to Reporting \u003c/strong\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/5.5/automating-report-generation.html#automating-report-generation\" target=\"_blank\"\u003e\u003cstrong\u003edocumentation\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e for detailed steps.)\u003c/strong\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eFollow the Watcher installation steps to \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/installing-watcher.html\"\u003einstall the Watcher plugin\u003c/a\u003e. \u0026nbsp; Since I am using an Elastic Cloud instance, it’s a simple check of the watcher option under the Plugins section and it will install it for you!\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltea7d61fcb64f04cb/5f88649a1f5f6d4173b501d6/report-6.png\" height=\"63\" width=\"624\" style=\"width: 624;height: 63;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eOnce Watcher is installed and the Watcher service is running, create the watch using the \u003ca href=\"https://www.elastic.co/guide/en/sense/current/index.html\"\u003eSense\u003c/a\u003e editor or curl equivalent, etc.. \u0026nbsp;If you are running on the Elastic Cloud, Sense editor is pre-installed with Kibana. \u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/reporting/current/getting-started.html#automating-report-generation\"\u003eWatcher + Reporting integration\u003c/a\u003e uses Watcher’s email action with attachment capability to trigger report generation and subsequently send the resulting PDF file to the recipients specified.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBefore creating the watch, \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/email-services.html#email-account\"\u003econfigure a valid smtp server\u003c/a\u003e for Watcher to use for sending emails. \u0026nbsp;On Elastic Cloud, you do not have to set up a smtp server and will use the one provided by the Cloud environment \u0026nbsp;(however, remember to \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/watcher.html#watcher-whitelist\"\u003ewhitelist\u003c/a\u003e the email addresses for the recipients of your reports).\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cstrong\u003eUse case:\u003c/strong\u003e \u0026nbsp;Our systems manager has been receiving reports that customers have trouble attaching files to\u0026nbsp;Salesforce Service Cloud support cases. \u0026nbsp;He would like to get a bi-weekly analytics report over 6 months of data on tickets filed against the Service Cloud (our support system) only if there are tickets created related to attachments within the past 2 weeks.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe watch below queries the helpdesk ticket data to see if there are any tickets filed against the support system by internal employees within the past 2 weeks, and if these tickets mention attachments in their feeds (which can be\u0026nbsp;posts, emails, or comments on either). \u0026nbsp;If so, the watch will fire and request the saved dashboard to be generated as a PDF report to be sent to the systems manager.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT _watcher/watch/reporting\u003cbr /\u003e{\u003cbr /\u003e \"trigger\": {\u003cbr /\u003e \"schedule\": {\u003cbr /\u003e \"interval\": \"14d\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"input\": {\u003cbr /\u003e \"search\": {\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"indices\": \"sfcases\",\u003cbr /\u003e \"body\": {\u003cbr /\u003e \"size\": 0,\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"bool\": {\u003cbr /\u003e \"must\": [\u003cbr /\u003e {\u003cbr /\u003e \"query_string\": {\u003cbr /\u003e \"query\": \"Ticket_Category:support AND Feeds:attachment\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ],\u003cbr /\u003e \"filter\": [\u003cbr /\u003e {\u003cbr /\u003e \"range\": {\u003cbr /\u003e \"CreatedDate\": {\u003cbr /\u003e \"gte\": \"now-14d\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e {\u003cbr /\u003e \"term\": {\u003cbr /\u003e \"Ticket_Category\": \"support\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"condition\": {\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"inline\": \"if (ctx.payload.hits.total \u0026gt;0) return true; else return false;\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"actions\": {\u003cbr /\u003e \"email_admin\": {\u003cbr /\u003e \"email\": {\u003cbr /\u003e \"to\": \"'John Smith \u0026lt;email_address@elastic.co\u0026gt;'\",\u003cbr /\u003e \"subject\" : \"[Report][Helpdesk] Service Cloud Attachment Tickets\",\u003cbr /\u003e \"body\" : \"There are new helpdesk tickets created within the past 2 weeks against the Service Cloud with feeds related to attachments. Please review the bi-weekly PDF report attached.\",\u003cbr /\u003e \"attachments\": {\u003cbr /\u003e \"helpdesk_attachment_tickets.pdf\": {\u003cbr /\u003e \"http\": {\u003cbr /\u003e \"content_type\": \"application/pdf\",\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"method\": \"POST\",\u003cbr /\u003e \"headers\": {\u003cbr /\u003e \"kbn-xsrf\": \"reporting\"\u003cbr /\u003e },\u003cbr /\u003e \"read_timeout\": \"300s\",\u003cbr /\u003e \"scheme\": \"https\",\u003cbr /\u003e \"auth\": {\u003cbr /\u003e \"basic\": {\u003cbr /\u003e \"username\": \"reporting_user\",\u003cbr /\u003e \"password\": \"password\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"url\": \"https://\u0026lt;elastic_cloud_instance_id\u0026gt;.us-east-1.aws.found.io/api/reporting/generate/dashboard/Support-(Dashboard)-Service-Cloud-Internal-Case-Analytics?_g=(refreshInterval:(display:Off,pause:!f,value:0),time:(from:now-6M,mode:quick,to:now))\u0026amp;_a=(filters:!(),options:(darkTheme:!f),panels:!((col:7,id:%27Support-(Pie)-By-Status%27,panelIndex:3,row:3,size_x:3,size_y:2,type:visualization),(col:4,id:%27Support-(Pie)-By-Severity-Level%27,panelIndex:4,row:3,size_x:3,size_y:2,type:visualization),(col:3,id:%27Support-(Bar)-Date-Histogram%27,panelIndex:9,row:1,size_x:10,size_y:2,type:visualization),(col:10,id:%27Support-(Pie)-Origin%27,panelIndex:12,row:3,size_x:3,size_y:2,type:visualization),(col:1,id:%27Support-(Bar)-Owner%27,panelIndex:15,row:5,size_x:6,size_y:4,type:visualization),(col:7,id:%27Support-(Bar)-Contacts%27,panelIndex:16,row:5,size_x:6,size_y:4,type:visualization),(col:1,id:%27Support-(Pie)-Ticket-Category%27,panelIndex:17,row:3,size_x:3,size_y:2,type:visualization),(col:1,id:%27Support-(Metric)-Total-%23-of-Internal-Cases%27,panelIndex:19,row:1,size_x:2,size_y:2,type:visualization),(col:1,columns:!(CaseNumber,Contact,Subject,Priority,Status),id:%27Case-View-(Internal)%27,panelIndex:20,row:9,size_x:12,size_y:4,sort:!(CreatedDate,desc),type:search)),query:(query_string:(analyze_wildcard:!t,query:%27Ticket_Category:support%20AND%20Feeds:attachment%27)),title:%27Support%20-%20(Dashboard)%20Service%20Cloud%20Internal%20Case%20Analytics%27,uiState:(P-15:(vis:(legendOpen:!t)),P-4:(spy:(mode:(fill:!f,name:!n)),vis:(legendOpen:!t)),P-9:(vis:(legendOpen:!f))))\u0026amp;sync\"\u0026lt;/elastic_cloud_instance_id\u0026gt;\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe \u003cstrong\u003erequest.url\u003c/strong\u003e\u0026nbsp;string in the watch’s email action is copied from the Generation URL\u0026nbsp;entry from above (screenshot in Step 4) which will be used by Watcher to generate the report on the fly. \u0026nbsp;Currently, report generation is synchronous, which means that it is important to set the \u003cstrong\u003erequest.read_timeout\u003c/strong\u003e\u0026nbsp;to a timeout that is longer than the time it takes to generate the report. \u0026nbsp;Otherwise, Watcher tasks can start to queue up.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eFor more detailed explanation of the other settings in the email action, refer to the Reporting \u003ca href=\"https://www.elastic.co/guide/en/reporting/current/getting-started.html#automating-report-generation\"\u003edocumentation\u003c/a\u003e.\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"margin-top: 18pt;margin-bottom: 6pt;line-height: 1.38;background-color: rgb(255, 255, 255);\"\u003eStep 6: \u0026nbsp;Check Out the Report\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eHere is the resulting\u0026nbsp;Watcher alert email sent by Elastic Cloud with the PDF report:\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e---------- Forwarded message ----------\u003cbr /\u003eFrom: Watcher Alert \u0026lt;noreply@watcheralert.found.io\u0026gt;\u003cbr /\u003eDate: Thu, Sep 15, 2016 at 12:43 PM\u003cbr /\u003eSubject: [Report][Helpdesk] Service Cloud Attachment Tickets\u003cbr /\u003eTo: 'John Smith \u0026lt;email_address@elastic.co\u0026gt;\u003cbr /\u003eThere are new helpdesk tickets created within the past 2 weeks against the Service Cloud with feeds related to attachments. Please review the bi-weekly PDF report attached.\u003cbr /\u003e\u0026lt;\u0026lt; helpdesk_attachment_tickets.pdf (211K) \u0026gt;\u003cbr /\u003e--\u003cbr /\u003eThis email is sent via a Watcher alert on a Found hosted cluster. Your email address was previously whitelisted. To stop receiving any Watcher alert, click: \u0026lt;\u0026lt;a href=\"http://email.watcheralert.found.io/u/eJwNxDEOwyAMAMDXwEZkDIF68JA_ZOoSEQMtUtVEhP6_ueEyx1wh6Ma9nEcf7fvawCDYYICMnVdLyi0e7yBMSP6p3-xsTLaE-JAqexXcEQiJhPLs0KesO5_tdykP5ZOu0WSSQw9WuPwBv48fcg\"\u0026gt;\u0026lt;span\u0026gt;\u0026lt;/span\u0026gt;\u0026lt;/a\u0026gt;http://email.watcheralert.found.io/u/…..\u0026gt;\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAnd here are a few example screens from the generated PDF report received by the systems manager. \u0026nbsp;How cool is that!\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt84b71e13e6aa4416/5f88649b3db5122648cbcd27/report-7.png\" height=\"274\" width=\"459\" style=\"width: 459;height: 274;\"/\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf77e4f1b0e5d33dc/5f88649a271ecf4a1a644e21/report-8.png\" height=\"543\" width=\"457\" style=\"width: 457;height: 543;\"/\u003e\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc458f9de1f9727c/5f886499dcf0e74b7cbf661e/report-9.png\" height=\"126\" width=\"462\" style=\"width: 462;height: 126;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eImagine the possibilities! \u0026nbsp;Give it a try and don’t forget to view the\u0026nbsp;\u003ca href=\"https://www.elastic.co/webinars/reporting-and-alerting-overview-and-demo?baymax=rtp\u0026elektra=products\u0026iesrc=ctr\"\u003eReporting Webinar\u003c/a\u003e video\u0026nbsp;to learn more about the new reporting capabilities :)\u003c/p\u003e\u003cdiv\u003e\u003cbr /\u003e\u003c/div\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:39:19.293Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt6991d59444b0d068","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-10T10:34:21.679Z","updated_at":"2018-10-10T10:34:21.679Z","content_type":"image/jpeg","file_size":"84336","filename":"blog-reporting-fullbleed.jpg","title":"blog-reporting-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T23:33:28.734Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6991d59444b0d068/5bbdd5adcca23e4e0cc6b469/blog-reporting-fullbleed.jpg"},"markdown_l10n":"","publish_date":"2016-10-03T16:46:20.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"You get a report! You get a report!","seo_description_l10n":"This blog post talks about how you can use Reporting and Watcher integration on Elastic Cloud to schedule the delivery of PDF reports.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt23c1099fc18829f9","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-10T10:34:16.927Z","updated_at":"2018-10-10T10:34:16.927Z","content_type":"image/jpeg","file_size":"43645","filename":"blog-reporting-thumb.jpg","title":"blog-reporting-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T23:33:28.734Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt23c1099fc18829f9/5bbdd5a8587df1a314bc77a9/blog-reporting-thumb.jpg"},"title":"You get a report! You get a report!","title_l10n":"You get a report! You get a report!","updated_at":"2025-03-10T11:06:06.158Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/you_get_a_report_you_get_a_report","publish_details":{"time":"2025-03-10T11:06:10.451Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc7bb0b96acd395fe","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"In this integration, we explore NHL Play-by-Play data in Elasticsearch \u0026 Kibana, then dive into creating a custom WMS tile server for a hockey rink backdrop.","author":["blt6e6b2409dd184f91"],"body_l10n":"\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cstrong\u003eNote:\u0026nbsp;For a more detailed and flexible approach\u0026nbsp;using geo-referenced vectors, the reader should follow the steps outlined \u003c/strong\u003e\u003ca href=\"https://www.elastic.co/blog/operational-analytics-with-elasticsearch-at-elasticon-2017-part-2\"\u003e\u003cstrong\u003ein this blog post\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003eThe National Hockey League (NHL) provides public access to each game’s play-by-play data, in convenient JSON format (see \u003ca href=\"https://assets.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt59f1e2e912ab70b1/5f516abcb553152466d1c1c0/PlayByPlay.json\"\u003esample doc\u003c/a\u003e* for 1 game), which we can ingest into Elasticsearch with minimal effort. \u0026nbsp;In this blog post, we will explore approximately 73 thousand plays made (so far) in the 2016-2017 NHL Season.\u003c/p\u003e\u003cp\u003eEach play contains the following information: \u0026nbsp;\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eTime of Play\u003c/li\u003e\u003cli dir=\"ltr\"\u003eType of Play (Goal, Shot, Hit, Penalty, Fight)\u003c/li\u003e\u003cli dir=\"ltr\"\u003eWho made the play\u003c/li\u003e\u003cli dir=\"ltr\"\u003eWho else was involved in the play\u003c/li\u003e\u003cli dir=\"ltr\"\u003eWho was on the ice at the time of the play\u003c/li\u003e\u003cli dir=\"ltr\"\u003eX,Y coordinates of play location on the ice.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eA text description of the play.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eUsing Kibana dashboard with some basic visualizations, we can drill down on a specific game. \u0026nbsp;\u0026nbsp;Let’s see a timeline of plays, colour coded by type and split by team, then some pie charts of each play, also split by team. \u0026nbsp;\u0026nbsp;The first pie shows us that only the Ducks scored in this game. \u0026nbsp;\u003cem\u003eGogliano\u003c/em\u003e and \u003cem\u003eSilfverberg\u003c/em\u003e made this a 2-0 win over the Stars.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt15712bc88f5738df/5f8861f11529bb3239a1f1bd/kibana-nhl-1.png\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003cbr /\u003eA hockey rink is 200 Feet by 85 Feet, which conveniently equates closely to longitude and latitude (180 by 90). \u0026nbsp;\u0026nbsp;In the case that your data does not equate naturally, you could use Logstash to translate the coordinates to a compatible longitude and latitude range. \u0026nbsp;The following visualization shows the location of all goals scored, but something’s not right - Latitude and Longitude is a nice coordinate hack, but we need the correct backdrop.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6b48cc6ffe994e1e/5f8861f12f59ae27f3d60e40/kibana-nhl-2.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eAs of \u003ca href=\"https://www.elastic.co/blog/kibana_4.2_beta2\"\u003eKibana 4.2, we added support for custom map tiles\u003c/a\u003e, so we can turn our world into a hockey rink (for those of us who haven’t already).\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eSidney Crosby’s Shot Locations\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltebfafefc8f3d23cb/5f8861f14671ee30c689e83a/kibana-nhl-3.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eP.K. Subban’s Shot Locations\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb6807bdb86d1eb91/5f8861f1f6c586323f8b34d4/kibana-nhl-4.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 10pt;margin-bottom: 0pt;\"\u003eSetting up a custom Tile Server\u003c/h2\u003e\u003cp\u003eLet’s now outline the process used to load this custom map into the Kibana visualization. \u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eStep 1) Create a GeoTIFF version of the Arena image\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003egdal_translate -of GTiff -a_srs EPSG:4326 -a_ullr -105 45 105 -45 nhl_rink.gif nhl_rink_gtiff.tiff\u003cbr /\u003egdal_warp -t_srs EPSG:4326 nhl_rink_gtiff.tiff nhl_rink.tiff\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eThe \u003ca href=\"http://www.gdal.org/gdal_translate.html\"\u003egdal_translate\u003c/a\u003e and \u003ca href=\"http://www.gdal.org/gdalwarp.html\"\u003egdalwarp\u003c/a\u003e\u0026nbsp;commands are used in conjunction to encode longitude/latitude points into the image, and to “reproject”, or set control points.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eStep 2) Set up GeoServer\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"http://geoserver.org/\"\u003eGeoServer\u003c/a\u003e is a free and open-source \u003ca href=\"https://en.wikipedia.org/wiki/Web_Map_Service\"\u003eWMS\u003c/a\u003e server, which makes it compatible with Kibana. \u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;Downloading and installing this software onto your favourite platform is easy, and results in a Web Front end that you can log into to manage your tile service. \u0026nbsp;\u0026nbsp;Once the server is running, you can log into via \u003cem\u003ehttp://\u0026lt;hostname\u0026gt;:8080/geoserver.\u003c/em\u003e\u0026nbsp; \u0026nbsp;\u0026nbsp;In the screenshots, we are working with GeoServer 2.7.2.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eStep 3) Create a new Workspace\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eFrom the Data-\u0026gt;Workspaces menu, click “Add new Workspace”. \u0026nbsp;\u0026nbsp;In this example, we name it “NHL”, and also set the Namespace URI to “NHL” \u0026nbsp;\u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eStep 4) Import the GeoTIFF into Data Stores.\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eFrom the Data-\u0026gt;Stores menu, click “Add new Store”. \u0026nbsp;\u0026nbsp;\u0026nbsp;Select GeoTIFF. \u0026nbsp;\u0026nbsp;Select the Workspace you just created, and set a datasource name. \u0026nbsp;For this example, we use the DS name “nhl_rink_ds”. \u0026nbsp;\u0026nbsp;\u0026nbsp;Browse to select your nhl_rink.tiff file, and press Save.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte2afbd188247962c/5f8861ee271ecf4a1a644e09/kibana-nhl-5.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eStep 5) Create the WMS Layer\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eFrom the Data-\u0026gt;Layers menu, click “Add new Resource”. \u0026nbsp;\u0026nbsp;\u0026nbsp;Select your newly created data source (NHL:nhl_rink_ds). \u0026nbsp;\u0026nbsp;By default, the Layer will be named the same as the store image name, without the file extension. (nhl_rink). \u0026nbsp;Click Publish (which then opens up the Layer Settings) then Click Save.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt233dbd7b50c72fb1/5f8861f03db5122648cbccfb/kibana-nhl-6.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThat’s it, your tile service is ready to go!\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eStep 6) Configure Kibana to use the new tile server\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eFinally, create a tile map visualization in Kibana and configure a custom WMS compliant map server.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1e10ee39fdbd4513/5f8861ef1f5f6d4173b501b4/kibana-nhl-7.png\" alt=\"Screen Shot 2017-01-11 at 1.37.32 PM.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003ctable style=\"font-size: 14px;\"\u003e\u003ctbody\u003e\u003ctr style=\"height: 0px;\"\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWMS url\u003c/p\u003e\u003c/td\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003ehttp://\u0026lt;hostname\u0026gt;:8080/geoserver/NHL/wms\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr style=\"height: 0px;\"\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWMS layers\u003c/p\u003e\u003c/td\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003enhl_rink\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr style=\"height: 0px;\"\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWMS version\u003c/p\u003e\u003c/td\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003e1.1.0\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr style=\"height: 0px;\"\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWMS format\u003c/p\u003e\u003c/td\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eimage/png\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr style=\"height: 0px;\"\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWMS attribution\u003c/p\u003e\u003c/td\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eMy NHL Data\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr style=\"height: 0px;\"\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWMS styles\u003c/p\u003e\u003c/td\u003e\u003ctd style=\"border-color: rgb(0, 0, 0);padding: 7px;\"\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.2;margin-top: 0pt;margin-bottom: 0pt;\"\u003eraster\u0026nbsp; \u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 10pt;margin-bottom: 0pt;\"\u003eExploring Further\u003c/h2\u003e\u003cp\u003eConsider the possibilities for drawing conclusions about the data set:\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003eWhich goalies are vulnerable to shots from certain players shooting from certain locations?\u003c/li\u003e\u003cli\u003eWho is drawing the most penalties (Aggregating by p2name.raw where type.raw:penalty)?\u003c/li\u003e\u003cli\u003eTime Series Analysis in\u0026nbsp;\u003ca href=\"https://www.elastic.co/blog/timelion-timeline\"\u003eTimelion\u003c/a\u003e to show relationships between stats\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eTry Importing the data into Elasticsearch yourself: \u0026nbsp;\u003ca href=\"https://github.com/elastic/examples/tree/master/Exploring%20Public%20Datasets/nhl\"\u003eFind the source code with instructions on GitHub.\u003c/a\u003e\u003c/p\u003e\u003cp\u003eAs always, we appreciate your feedback, so feel free to ping us on \u003ca href=\"https://discuss.elastic.co/\"\u003eDiscuss\u003c/a\u003e\u0026nbsp;or\u0026nbsp;\u003ca href=\"https://twitter.com/elastic\"\u003eTwitter\u003c/a\u003e. \u0026nbsp;Or, if you want to kick it up a notch and meet us in person, please come to our big user conference Elastic{ON} in March 2017!\u003cbr /\u003e\u003c/p\u003e\u003chr/\u003e\u003cp\u003e* - The game data was previously available from\u0026nbsp;http://live.nhl.com/GameData/20142015/2014021136/PlayByPlay.json\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T11:38:24.031Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"Screen Shot 2017-01-18 at 10.22.50 AM.png","uid":"blt4760580d9e4fc357","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T08:38:26.436Z","updated_at":"2019-02-04T08:38:26.436Z","content_type":"image/png","file_size":"108969","filename":"Screen_Shot_2017-01-18_at_10.22.50_AM.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T22:41:25.987Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4760580d9e4fc357/5c57fa0265ace9e30b31635b/Screen_Shot_2017-01-18_at_10.22.50_AM.png"},"markdown_l10n":"","publish_date":"2017-01-24T14:36:08.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"title":"Screen Shot 2017-01-18 at 10.24.17 AM.png","uid":"blt752a10e825e961d3","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T08:38:20.925Z","updated_at":"2019-02-04T08:38:20.925Z","content_type":"image/png","file_size":"120083","filename":"Screen_Shot_2017-01-18_at_10.24.17_AM.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T22:41:25.987Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt752a10e825e961d3/5c57f9fca209c1ca0be9dd4f/Screen_Shot_2017-01-18_at_10.24.17_AM.png"},"title":"Kibana and a Custom Tile Server for NHL Data","title_l10n":"Kibana and a Custom Tile Server for NHL Data","updated_at":"2025-03-10T11:02:13.734Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/kibana-and-a-custom-tile-server-for-nhl-data","publish_details":{"time":"2025-03-10T11:02:18.175Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfc289dfab4213783","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticsearch engineer Boaz Leskes gave a guest lecture to 100 students from the VU University of Amsterdam on the Life of a Cocument in Elasticsearch.","author":["blt7d550e7b21fc20a2"],"body_l10n":"\u003cp\u003eJust when you think you’ve graduated from university, there’s always something that pulls you right back in. We all remember the fun of exams, the deadlines, the never ending books, the long days, and of course, the partying. And then there’s that amazing moment when you finally graduate and say goodbye to university. But who would’ve thought that going back to school could actually be quite interesting?\u003c/p\u003e\u003cp\u003eWe’re happy to say that we got invited to give a guest lecture at the VU University in Amsterdam to teach computer science and engineering students the basics of Elasticsearch. \u003ca href=\"https://twitter.com/bleskes\"\u003eBoaz Leskes\u003c/a\u003e, one of our core software engineers, was the lucky one to give this presentation to around 100 students. Surprisingly enough only two students have heard about Elasticsearch and Lucene before but guess what, that was about to change...\u003c/p\u003e\u003cp\u003eBoaz explained the lifecycle of a single document in Elasticsearch (see slides below\u0026nbsp;from his presentation at Elastic{ON}15). The talk\u0026nbsp;covered many different aspects including what happens when you index a single document in Elasticsearch and how Elasticsearch ensures a document is replicated and found across the whole cluster reliably.\u003c/p\u003e\u003cdiv style=\"height: 478px;margin-bottom: 20px;\"\u003e\u003ciframe width=\"100%\" height=\"478\" src=\"//speakerdeck.com/player/3097bd6f3f3e450a8415f49e7c17bf75\" class=\"video-iframe\" frameborder=\"0\" allowfullscreen=\"\"\u003e\u003cspan id=\"selection-marker-1\" class=\"redactor-selection-marker\"\u003e\u003c/span\u003e\u003c/iframe\u003e\u003c/div\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAfter some term descriptions to lay the ground Boaz got the students’ attention and he even started cracking his jokes as he usually does to get them even more ‘awake’. And yes, they were actually answering some of his questions and they were pretty good at it!\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAt this point, the students were captured including the one sitting in front of me who wrote down pretty much every sentence Boaz said. Boaz continued with his talk and explained more about the how, when and where a document is stored and processed in\u0026nbsp;Elasticsearch. At the end of his presentation, it was question time! Despite a tough start being confronted with a\u0026nbsp;completely new topic, students\u0026nbsp;were asking a lot of good questions.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe two students with the best questions got offered an Elasticsearch book at the end - no, it’s not just a \u003ca href=\"https://speakerdeck.com/bleskes/life-of-a-document-in-elasticsearch?slide=6\"\u003eJSON document within the presentation\u003c/a\u003e, the book actually exists. :)\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAll in all the guest lecture was a great success, at least from our perspective. Let’s hope the students see it the same way!\u0026nbsp;And in my opinion, going back to school was totally worth it!\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan\u003e\u003c/span\u003eIf you are interested, Boaz’ presentation slides can be downloaded from\u0026nbsp;\u003ca href=\"https://speakerdeck.com/bleskes/life-of-a-document-in-elasticsearch\"\u003ehere\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003eApplause, Applause!\u003cbr /\u003e\u003c/p\u003e","category":[],"created_at":"2019-04-18T15:19:50.541Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"_version":3,"is_dir":false,"uid":"blt9390c3a66f9a7673","ACL":{},"content_type":"image/png","created_at":"2019-09-04T15:43:09.575Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"73492","filename":"blog-banner-generic-black.png","parent_uid":null,"tags":[],"title":"blog-banner-generic-black.png","updated_at":"2020-11-25T17:47:29.005Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T17:47:21.551Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9390c3a66f9a7673/5fbe98b142256d5ffdf46887/blog-banner-generic-black.png"},"markdown_l10n":"","publish_date":"2015-11-27T16:18:43.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Goes Back To School","seo_description_l10n":"Boaz gave a guest lecture to 100 students from the VU University of Amsterdam on the Life of a document in Elasticsearch.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":4,"is_dir":false,"uid":"blt906fe334a8bd62cc","ACL":{},"content_type":"image/png","created_at":"2019-12-05T18:00:18.530Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"32572","filename":"blog-thumb-generic-black.png","parent_uid":null,"tags":[],"title":"blog-thumb-generic-black.png","updated_at":"2020-11-25T17:48:14.349Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-11-25T17:48:07.076Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt906fe334a8bd62cc/5fbe98de4e40cf53001fa2a4/blog-thumb-generic-black.png"},"title":"Elastic Goes Back To School","title_l10n":"Elastic Goes Back To School","updated_at":"2025-03-10T10:57:17.179Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-goes-back-to-school","publish_details":{"time":"2025-03-10T10:57:20.703Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltadf3df28c911c68c","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blta3a0ef5d1f46fd39"],"body_l10n":"\u003cp\u003e\u003cem\u003e“Alert me when my Elasticsearch cluster state is red!\"\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003eYou asked, we heard.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eSome of our users have been creating Watches based on the data that X-Pack monitoring collects to get real-time alerts. We then thought,\u0026nbsp;‘Wouldn’t it be nice if we created some Watches for the common cluster problems and make everyone’s life easier?’\u003c/p\u003e\u003cp dir=\"ltr\"\u003eSo we did. We worked hard to automatically surface potential issues within your Elastic Stack. We hope you like it!\u003c/p\u003e\u003cp dir=\"ltr\"\u003eFor this first-class feature in X-Pack monitoring, we leveraged X-Pack alerting via Watcher to periodically query the monitoring data, identify issues and provide alerts for critical issues.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eWhen you click on the Monitoring app, you will see any active Cluster Alerts as part of the overview of your Elastic Stack.\u003c/p\u003e\u003cp dir=\"ltr\"\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfcbb7b1b0900aac0/5f878677f9d3bf27fac3b90c/es-cluster-alerts-blog-image.gif?disposition=inline\" width=\"918\" height=\"703\" style=\"width: 918;height: 703;\"/\u003e\u003c/p\u003e\u003cp dir=\"ltr\"\u003eUnder Top Cluster Alerts, we see that “Elasticsearch cluster status is yellow” with a link to allocate missing replica shards. Clicking the link takes you to the index listing page, which has information about indices that have unassigned shards. There needs to be more than one node in a cluster so that replica shards could be assigned. To resolve this issue, we need to add a second node to join this single-node cluster. Anything that makes the Elasticsearch health turn green will make this Cluster Alert go away - most of the time, that means adding another node to host the replica shards.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eIn the 5.4 release, we’re shipping with the following four Watches to get this rolling:\u003c/p\u003e\u003cul\u003e\u003cli\u003eYellow or red Elasticsearch cluster state\u003c/li\u003e\u003cli\u003eMismatching versions of Elasticsearch nodes\u003c/li\u003e\u003cli\u003eMismatching versions of different Kibana instances\u003c/li\u003e\u003cli\u003eMismatching versions of Logstash nodes in your cluster\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\"\u003eIn future releases, we plan to provide alerts for X-Pack license expiration approaching, Elasticsearch shards approaching maximum size limits, CPU, memory, and disk utilization, and the holy grail: nodes joining and leaving the cluster. We know that one size does not fit all, we plan on working on customizable thresholds in the future.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eWe are also actively working to enable E-mail configuration from Kibana for the built-in Watches. In the future, we will let you set notifications via Slack, HipChat, PagerDuty, Jira and Webhook integrations.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eWhen you're on vacation on a beautiful beach, you can fully enjoy your time and relax knowing that your Elastic Stack issues will be kept under close watch with Cluster Alerts in X-Pack monitoring.\u003c/p\u003e\u003cp dir=\"ltr\"\u003eTo try out this new feature, get started today with \u003ca href=\"https://www.elastic.co/start\"\u003ethe latest release\u003c/a\u003e with a trial license, where you can take a full advantage of all \u003ca href=\"https://www.elastic.co/subscriptions\"\u003eX-Pack features\u003c/a\u003e.\u0026nbsp;If you have any questions or requests, please let us know via our \u003ca href=\"https://discuss.elastic.co/c/x-pack\"\u003eX-Pack discuss\u003c/a\u003e forum.\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-18T15:15:30.655Z","created_by":"sys_blt57a423112de8a853","disclaimer":["bltf7e0361d38ceea67"],"full_bleed_image":{"uid":"bltd1357fd2c4876f68","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2019-05-02T02:45:25.809Z","updated_at":"2019-05-02T02:45:25.809Z","content_type":"image/jpeg","file_size":"62402","filename":"beach-pier-lone-man-boat-sand-banner.jpg","title":"beach-pier-lone-man-boat-sand-banner.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T02:45:36.946Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd1357fd2c4876f68/5cca59c54c5fe893641667c8/beach-pier-lone-man-boat-sand-banner.jpg"},"markdown_l10n":"","publish_date":"2017-05-30T20:56:53.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt970bec35974cf578","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2019-05-02T02:45:20.723Z","updated_at":"2019-05-02T02:45:20.723Z","content_type":"image/jpeg","file_size":"44240","filename":"beach-pier-lone-man-boat-sand-thumb.jpg","title":"beach-pier-lone-man-boat-sand-thumb.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T02:45:36.946Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt970bec35974cf578/5cca59c0683c75ef655381d1/beach-pier-lone-man-boat-sand-thumb.jpg"},"title":"Cluster Alerts for Elasticsearch Issues: Cluster Alerts in X-Pack Monitoring","title_l10n":"Cluster Alerts for Elasticsearch Issues: Cluster Alerts in X-Pack Monitoring","updated_at":"2025-03-10T10:55:50.761Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elasticsearch-cluster-alerts-for-issues-from-xpack-monitoring","publish_details":{"time":"2025-03-10T10:55:54.967Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfcbdb493b8e32695","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt5a853ed84ea8bcc8"],"body_l10n":"\u003cp\u003eToday we are proud to announce the general availability of Elastic Application Performance Monitoring (APM) Server on top of the Elasticsearch Service. Elastic APM provides rich insights into application performance and visibility for distributed workloads, while the Elasticsearch Service simplifies provision and management. Elastic APM on Elasticsearch Service supports a number of languages including Java, Go, Ruby, Python, and Javascript.\u003c/p\u003e\u003cp\u003eThese new \u003ca href=\"/blog/elastic-apm-6-6-0-released\"\u003eElastic APM 6.6\u003c/a\u003e abilities pair with the other powerful features already available on the Elasticsearch service including:\u003c/p\u003e\u003cul\u003e\u003cli\u003eAutomated anomaly detection for APM data with machine learning\u003c/li\u003e\u003cli\u003eFaster troubleshooting with alerting on top of APM data\u003c/li\u003e\u003cli\u003eCost-effective hot-warm architecture with built-in index curation\u003c/li\u003e\u003cli\u003eCentralizing logs, metrics, and APM data\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eExisting Elasticsearch Service users can add APM Servers to any existing or new deployment with version 6.3 and above.\u003c/p\u003e\u003ch2\u003eAdd\u0026nbsp;APM Server to your deployment... for free\u003c/h2\u003e\u003cp\u003eAs an easy way to try Elastic APM on Elasticsearch Service, we are also including a 512 MB APM Server\u0026nbsp;instance with all new 6.6+ deployments and\u0026nbsp;as part of the \u003ca href=\"https://www.elastic.co/blog/elasticsearch-service-on-elastic-cloud-introduces-new-pricing-with-reduced-costs\"\u003efree allowance\u003c/a\u003e\u0026nbsp;announced last year. This new addition to the free allowance joins the existing 1 GB machine learning node and 1 GB Kibana instance. With this instance of APM Server, you can start instrumenting your applications and send hundreds of events per second before needing to scale up.\u003c/p\u003e\u003cp\u003eIf you are a current user of the Elasticsearch Service, upgrade your deployment and start up your own APM server to take it for a spin. If you aren't a current user, sign up for a\u0026nbsp;\u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup\"\u003e14-day free trial of Elasticsearch Service\u003c/a\u003e\u0026nbsp;and give the whole stack a whirl.\u003c/p\u003e","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2019-04-01T13:47:36.151Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"_version":2,"is_dir":false,"uid":"blt524d5ee0222d5354","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:36.948Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"54225","filename":"blog-banner-release-elasticsearch.png","parent_uid":null,"tags":[],"title":"blog-banner-release-elasticsearch.png","updated_at":"2021-01-26T17:45:10.329Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-03T15:47:40.504Z","user":"bltde77f2161b811714"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt524d5ee0222d5354/601055260cb0aa0ffcdd590e/blog-banner-release-elasticsearch.png"},"markdown_l10n":"","publish_date":"2019-01-29T19:01:54.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":["newsletter"],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"blt8c2b608c10eb1fd8","ACL":{},"content_type":"image/png","created_at":"2019-01-05T05:57:42.964Z","created_by":"sys_blt57a423112de8a853","description":"","file_size":"51730","filename":"blog-thumb-release-elasticsearch.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-release-elasticsearch.png","updated_at":"2022-02-11T21:03:50.956Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.895Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c2b608c10eb1fd8/601055106215cf0f9a18d799/blog-thumb-release-elasticsearch.png"},"title":"Introducing Elastic APM on Elasticsearch Service","title_l10n":"Introducing Elastic APM on Elasticsearch Service","updated_at":"2025-03-10T10:54:18.859Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/introducing-elastic-apm-on-elasticsearch-service","publish_details":{"time":"2025-03-10T10:54:22.040Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltec0223f5e225d370","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Our Cloud service experienced issues with managing memory for the clusters. This blog is a postmortem of the incident.","author":["blt553467a41584839d","blt2b6896ceeb9a2141"],"body_l10n":"\u003cp\u003eElastic Cloud is on the tail end of eliminating a mix of memory issues that has caused problems for a lot of low-memory nodes, and in some rare cases even large nodes. Following the memory problems, we experienced connectivity issues on a handful of servers in eu-west-1 that affected any cluster with at least one node on these impacted servers.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eAfter investigation, we found that there were a number of small problems that, when combined, created larger issues. \u0026nbsp;This post attempts to summarise the breadth of things that all contributed to the problems, and the extent of testing we’re ramping up to avoid repeating our mistakes. You might learn a thing or two about Linux, Docker, memory accounting, glibc, JVM-settings, Netty, and Elasticsearch as well. We sure have.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"font-size: 24px;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cspan style=\"font-size: 30px;\"\u003e\u003cstrong\u003eScope\u0026nbsp;of the memory problem\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eElastic Cloud runs tens of thousands of Elasticsearch nodes. These nodes run on servers with memory ranging from 30-244 GiB and 4-32 cores, which we call our “allocator pool”. A single server can host a lot of Elasticsearch nodes, each running in containers getting a reserved slice of memory and a (boostable) slice of the CPU. The servers run a small number of different kernel and Docker versions, and we’ll get back to why.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe memory issues can be categorised as:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eHigh memory pressure from Elasticsearch causing increased GC-load and latencies, and eventually the JVM running out of heap space. There were several things that could lead to this.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eGrowth in the JVM’s non-heap memory, eating away memory intended for page cache and possibly causing kernel-level OOM-reaping.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eBecause we used long-running containers, kernel memory was being incorrectly accounted, causing the kernel to kill processes in a container almost as soon as the node started.\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAll of these could affect a single node, but just one would be sufficient to make the node unreliable.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWhenever a process is restarted due to memory issues, we log the event and notify the account owner and operational contacts (rate limiting to max one email per 6 hours). While Elasticsearch keeps getting more careful against running out of memory, it’s not uncommon for an overloaded cluster to run out of memory.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThus, we know that in the period we had the most issues, approximately 1% of the running clusters were affected. That’s a lot of clusters, but as most mitigations affect every cluster and some required restarting Elasticsearch and/or upgrading, we needed to proceed carefully to not cause any problems to the majority of nodes not having any issues.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cspan style=\"font-size: 30px;\"\u003e\u003cstrong\u003eOn environment variety\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eElastic Cloud is based on the acquisition of Found, which launched a hosted Elasticsearch service in 2012. Having managed lots of containers since before Docker even existed and container schedulers were buzzwords, we have a lot of experience in how container-features can cause Linux to crash, or sometimes worse, cause nodes to slow down to a crawl. Even the 4.4 kernel series in Ubuntu LTS recently had OOM-issues.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWith the exception of security patches, we’re typically very slow when it comes to upgrading Linux and Docker: issues with these components can severely hurt our reliability or create significant ops workload \u0026nbsp;to clean up containers that are not being created or destroyed correctly. Docker is a fast-moving technology, and generally only the most recent versions receive security patches. This makes it important to keep up, and we were gradually increasing the numbers of servers running more recent versions as we gained confidence in it.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eOur server fleet is also composed of servers of varying size. Smaller servers limit the blast radius if there’s an issue, while larger servers are necessary to host the beefier clusters. Depending on available capacity during provisioning, a small 1GB node can end up on a massive server. A node will be allotted the same CPU time regardless of the numbers of cores available, so performance differences are small between servers. There are settings that rely \u0026nbsp;on the core count, however, and we didn’t properly cover all the bases of settings that look at cores. This could pose problems for a small node landing on a large server.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eHaving run the 3.19-series of the kernel for a long time without issues, it took some time before we suspected it could be the issue. This will be described more later, but we’ve found that \u0026nbsp;Docker ≥1.12 has problems on Linux \u0026lt;4.4.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eTo start with, we turned every stone related to Elasticsearch and the JVM.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cspan style=\"font-size: 30px;\"\u003e\u003cstrong\u003eElasticsearch, Lucene, and the JVM\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eElasticsearch needs both heap space and page cache to perform well. A cluster with 1 GB memory on Cloud gets a little less than half the memory for heap space, to leave memory for page cache and non-heap JVM usage.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThere were a few issues in the early 5.0s that could cause a small node to quickly OOM as segments grew large enough to consume the available buffer space the S3 snapshotter could use, which was changed to 100 MB. This would be about 20% of a 1GB nodes available space, quickly leading to issues. That was quickly identified and remedied and every cluster was upgraded to apply the fix.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eHowever, we still saw Elasticsearch 5.x use a lot more non-heap memory than 2.x, which we eventually attributed to Elasticsearch 5 upgrading to Netty 4. Disabling Netty’s pooled allocator and recycler further reduced non-heap memory.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan\u003e\u003c/span\u003eThat still wasn’t enough, some nodes kept on OOM-ing – but now by the kernel’s OOM-reaper, which triggers if a process in a container with limited memory exceeds its memory. Increased non-heap usage would normally result in performance reductions, and not processes getting killed by the kernel OOM-reaper. So we knew we still had an issue.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan\u003e\u003c/span\u003eWe found more tweaks that improved the memory usage issues:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eUpgrading to JVM 8 turned tiered compilation on by default, something not really necessary for Elasticsearch. This would eat up 48MB memory for additional code caches.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eglibc’s memory allocator could waste a lot of memory on servers with many cores. A colleague coming in from Prelert has described the interactions of the \u003ca href=\"http://info.prelert.com/blog/java-8-and-virtual-memory-on-linux\"\u003eJVM and virtual memory on Linux\u003c/a\u003e as they relate to that change, which could waste a lot of memory for a small node running on a large server.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eThere were a number of small fixes in Elasticsearch between 5.0.0 and 5.2.2 that helped with memory usage. \u0026nbsp;\u0026nbsp;For example, not \u003ca href=\"https://github.com/elastic/elasticsearch/pull/22711\"\u003eclosing a stream\u003c/a\u003e could leak memory.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eWe reduced the number of JVM allocated GC threads. \u0026nbsp;\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eWe are also expanding our test suites to include tests that specifically address long running containers under load, and measure memory usage.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cspan style=\"font-size: 30px;\"\u003e\u003cstrong\u003eKernel and Docker bugs\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAfter much debugging, we found that specific combinations of kernel version and Docker version create a major problem with memory accounting. \u0026nbsp;In our case, combining kernel version 3.19 with Docker version 1.12 exposed this bug. \u0026nbsp;We had been running the 3.19 kernel for a long time, and it wasn’t immediately obvious that the kernel was a contributing factor to memory issues.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe core of the issue is that Docker 1.12 turns on kmem accounting. \u0026nbsp;In 3.x versions of the Linux kernel, this causes problems because of a \u003ca href=\"https://lwn.net/Articles/628829/\"\u003eslab shrinker issue\u003c/a\u003e. \u0026nbsp;In a nutshell, this causes the kernel to think that there is more kernel memory used than there actually is, and it starts killing processes to reclaim memory. \u0026nbsp;Eventually it kills the JVM, which obviously hurts the cluster. \u0026nbsp;There is a fix for the slab shrinker issue in kernel versions \u0026gt;= 4.0. \u0026nbsp;Our testing led us to combine kernel version 4.4 with Docker 1.12. \u0026nbsp;This combination solved the kmem accounting problems.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cspan style=\"font-size: 30px;\"\u003e\u003cstrong\u003eLooking forward\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAs you can see, there were a number of issues that combined to create a kind of “perfect storm” of memory issues. \u0026nbsp;We are now at a point where we’re convinced we’ve identified all of the major issues and are a long way toward addressing them throughout our fleet.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe total number of affected clusters in our SaaS environment was around 1%. \u0026nbsp;While this seems like a small number, we’re committed to reaching out to affected customers and offering explanations and help. \u0026nbsp;Although this issue affected clusters of all sizes, smaller clusters were the fastest to be affected due to the already limited amount of memory. \u0026nbsp;Since trial customers tend to run smaller clusters, we’ll be contacting trial customers who were active during the affected time period and offering new or extended trials.\u003c/p\u003e\u003cbr /\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:39:16.155Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt30e796ddb40ad174","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T08:33:06.391Z","updated_at":"2018-10-11T08:33:06.391Z","content_type":"image/jpeg","file_size":"104582","filename":"banner-the-thinker-blue.jpg","title":"banner-the-thinker-blue.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T22:21:44.731Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt30e796ddb40ad174/5bbf0ac2becc14715d4891de/banner-the-thinker-blue.jpg"},"markdown_l10n":"","publish_date":"2017-03-03T17:09:51.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Memory issues we'll remember","seo_description_l10n":"Our Cloud service experienced issues with managing memory for the clusters. This blog is a postmortem of the incident.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltbe725cb027423d89","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T08:33:08.804Z","updated_at":"2018-10-11T08:33:08.804Z","content_type":"image/jpeg","file_size":"45012","filename":"thumb-the-thinker-blue.jpg","title":"thumb-the-thinker-blue.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T22:21:44.731Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbe725cb027423d89/5bbf0ac4192fad64364a513b/thumb-the-thinker-blue.jpg"},"title":"Memory Issues We'll Remember","title_l10n":"Memory Issues We'll Remember","updated_at":"2025-03-10T10:53:01.322Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/memory-issues-well-remember","publish_details":{"time":"2025-03-10T10:53:05.977Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0f12ec44e37dd19a","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"I wanted to visualize the weather outside. So I built a way using some hobby hardware, Elasticsearch \u0026 Kibana.","author":["blt960dc480f767f8f4"],"body_l10n":"\u003cp\u003eI’m far from a meteorologist. I’m a hacker with a garage/office that I spend way too much time in. I have a bias toward things that feel like data. A friend told me that I was maybe being a bit of a garage troll; I am tucked away from the sun and warmth. I decided that I needed to figure out if she was right.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThis was a perfect opportunity to dive into the Internet of Playful Things: Arduino for my weather measurements, Elasticsearch for storage, and Kibana for viewing and analysis. With off-the-shelf parts, open source libraries and a Saturday afternoon available, I got to work.\u003c/p\u003e\u003cp\u003eIn true DIY blog post fashion, here’s the finished product. I’m far too impatient to test with weeks and weeks worth of data. In order to speed up my testing, I raided the freezer and bathroom for some supplies...\u003c/p\u003e\u003cdiv class=\"video embed-container\" style=\"height: 319.725px;\"\u003e\u003cimg class=\"vidyard-player-embed\" src=\"https://play.vidyard.com/E8MPU4HroDPfJmKKCrUFYe.jpg\" data-uuid=\"E8MPU4HroDPfJmKKCrUFYe\" data-v=\"4\" data-type=\"inline\" style=\"width: 100%;margin: auto;display: block;\" width=\"100%\"/\u003e\u003c/div\u003e\u003cp\u003e\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eI choose the ESP8266 more and more often lately. It’s a microcontroller with WiFi capabilities that can be used by itself or with most other platforms. Folks have built compatibility layers for Node.js, Python, and Arduino with it. It has become a very popular device because of its price and capabilities. For only a couple bucks, you can add WiFi to any hobby hardware project. For about sixteen dollars, you can get a battery-powered Arduino and node/lua-compatible development board. For this project I chose a board from \u003ca href=\"https://www.adafruit.com/product/2821\"\u003eAdafruit\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eElasticsearch and Kibana provide a very tidy combination for storing and visualizing the sensor data coming out of my hardware. Prebuilt modules from Adafruit make creating your own wireless weather station simple.\u003c/p\u003e\u003ch2\u003eThings you’ll need\u003c/h2\u003e\u003cp\u003eElectronics\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.adafruit.com/product/2821\"\u003eAdafruit Feather HUZZAH or another ESP8266 dev board\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.adafruit.com/products/1603\"\u003eAdafruit BMP180 Temperature/Pressure/Altitude Sensor\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eTools\u003c/p\u003e\u003cul\u003e\u003cli\u003eSoldering Iron\u003c/li\u003e\u003cli\u003eHookup Wire\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eNice to have\u003c/p\u003e\u003cul\u003e\u003cli\u003e3.7v Lithium Battery - \u003ca href=\"https://www.adafruit.com/products/1603?q=lithium\u0026\"\u003elike these\u003c/a\u003e\u003c/li\u003e\u003cli\u003eBreadboard - \u003ca href=\"https://www.adafruit.com/products/64\"\u003ehalf size is just right\u003c/a\u003e\u003c/li\u003e\u003cli\u003eJumper Wires - \u003ca href=\"https://www.adafruit.com/products/1957\"\u003elike these\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eComputer\u003c/p\u003e\u003cul\u003e\u003cli\u003eArduino Software (with some extra libraries and examples, detailed below)\u003c/li\u003e\u003cli\u003eElasticsearch + Kibana\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eFor Elasticsearch and Kibana, you can setup an instance on \u003ca href=\"https://www.elastic.co/cloud/as-a-service\"\u003eElastic Cloud\u003c/a\u003e or you’ll need to share a network with your devices and use a local instance of both.\u003c/p\u003e\u003ch2\u003eHardware Build\u003c/h2\u003e\u003cp\u003eI recommend using a breadboard for most prototypes and temporary projects. The first step is to solder the header pins onto the board. Adafruit ships most of its modules without the pins soldered on. If you haven’t soldered before, there are lots of really good guides to getting started. SparkFun has \u003ca href=\"https://learn.sparkfun.com/tutorials/how-to-solder---through-hole-soldering\"\u003ea nice guide\u003c/a\u003e. If you’re getting really into it you should dig into the \u003ca href=\"http://workmanship.nasa.gov/lib/insp/2%20books/frameset.html\"\u003eNASA Workmanship Standards\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eA note on soldering and tools:\u003c/p\u003e\u003cp\u003eMost guides on how to solder are written by people who do it a lot. Like most other hobbies and professions, using good tools will make the job easier. It’s also expensive. All you really need to get started is an iron, solder, and something to cut and strip wires with. Get better tools as you need them. My \u003ca href=\"http://www.oaklandlibrary.org/locations/tool-lending-library/tool-list-lending-guidelines\"\u003elocal library will loan the tools\u003c/a\u003e, yours might too. You might also have a \u003ca href=\"https://wiki.hackerspaces.org/List_of_Hacker_Spaces\"\u003elocal hackerspace\u003c/a\u003e which may be able to assist with tools, equipment, and techniques.\u003c/p\u003e\u003cp\u003eMy first toolset, which got me through about 10 years of experimenting.\u003c/p\u003e\u003cp\u003e\u003cimg alt=\"blog-2-weather-station.jpg\" data-sys-asset-uid=\"blt9733f1e16e3536ab\" src=\"https://api.contentstack.io/v2/assets/57bb09cb1251899a28dc2012/download?uid=blt9733f1e16e3536ab\"/\u003e\u003c/p\u003e\u003cp\u003eThis sensor board uses SPI to communicate with the microcontroller. The ESP8266 has SPI support, so we hook up Data (SDA) and Clock (SCL) lines to the SDA and SCL lines of each board for communication.\u003c/p\u003e\u003cp\u003eWe also hook up the 3v and Ground (GND) lines to power sensor board. That’s it! 4 wires is all we need.\u003c/p\u003e\u003cp\u003e\u003cimg alt=\"blog-3-weather-station.jpg\" data-sys-asset-uid=\"blt040cf6db92ab8fcf\" src=\"https://api.contentstack.io/v2/assets/57bb09d21251899a28dc2018/download?uid=blt040cf6db92ab8fcf\"/\u003e\u003c/p\u003e\u003ch2\u003eArduino Software\u003c/h2\u003e\u003cp\u003eIf you haven’t already, download and install the Arduino IDE and ESP8266 Board Package. \u003ca href=\"https://learn.adafruit.com/adafruit-feather-huzzah-esp8266/using-arduino-ide\"\u003eFollow this guide if you need help\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eYou’ll also need to install the libraries below.\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://github.com/PaulStoffregen/Time\"\u003eNTP\u003c/a\u003e - NTP is the network time protocol, it’s how we get the clock day/time from the internet to generate timestamps.\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/adafruit/Adafruit_Sensor\"\u003eAdafruit Unified Sensor Library\u003c/a\u003e \u003ca href=\"https://learn.adafruit.com/using-the-adafruit-unified-sensor-driver/introduction\"\u003e(More information)\u003c/a\u003e\u003c/li\u003e\u003cli\u003eAdafruit \u003ca href=\"https://github.com/adafruit/Adafruit_BMP085_Unified\"\u003eBMP085U\u003c/a\u003e Sensor Library (this also covers the BMP180 sensor we are using)\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003ca href=\"https://www.arduino.cc/en/Guide/Libraries\"\u003eUse this guide\u003c/a\u003e if you need help installing Arduino Libraries.\u003c/p\u003e\u003cp\u003eHaving WiFi makes it very easy to publish directly to Elasticsearch via the HTTP interface. The only real challenge was getting the Arduino code to generate an Elasticsearch compatible timestamp. I think that we’ve got a clever and straight-forward solution, by combining the arduino `mils()` function with an NTP generated unix timestamp.\u003c/p\u003e\u003cp\u003eChange the SSID and password in the sketch below and you should be ready to start.\u003c/p\u003e\u003ch2\u003eConfiguring Elasticsearch\u003c/h2\u003e\u003cp\u003eBefore we start sending data we’re going to prime Elasticsearch to index the documents we’re sending. Make sure to check the Elasticsearch URL (my `response = requests.put` line) to match your Elasticsearch endpoint.\u003c/p\u003e\u003cp\u003eI’m using Python and the requests library, but you can use whatever tool you’re familiar with.\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eimport requests\u003cbr /\u003eimport json\u003cbr /\u003edata = {\u003cbr /\u003e \"mappings\": {\u003cbr /\u003e \"reading\": {\u003cbr /\u003e \"properties\": {\u003cbr /\u003e \"temperature\": {\"type\": \"float\"},\u003cbr /\u003e \"pressure\": {\"type\": \"float\"},\u003cbr /\u003e \"timestamp\": {\"type\": \"date\"},\u003cbr /\u003e },\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003eresponse = requests.put('http://localhost:9200/weather', data=json.dumps(data))\u003cbr /\u003etry:\u003cbr /\u003e assert response.status_code is 200\u003cbr /\u003eexcept AssertionError:\u003cbr /\u003e raise AssertionError(\"Your mapping was not created\", response)\u003cbr /\u003e# You could use this snippet to delete your old data if you have an error.\u003cbr /\u003e#response = requests.delete('http://localhost:9200/weather')\u003cbr /\u003e#try:\u003cbr /\u003e# assert response.status_code is 200\u003cbr /\u003e#except AssertionError:\u003cbr /\u003e# raise AssertionError(\"Your mapping was not deleted\", response)\u003cbr /\u003e\u003c/pre\u003e\u003ch2\u003eSending Data\u003c/h2\u003e\u003cp\u003eModify the \u003ca href=\"#sketch1\"\u003esketch\u003c/a\u003e as mentioned above, and upload it to your device. It should start sending data to your Elasticsearch instance. You can verify in the Serial Monitor under `Tools -\u0026gt; Serial Monitor`. Make sure that the baud rate is set to 115200.\u003c/p\u003e\u003ch2\u003eConfiguring Kibana\u003c/h2\u003e\u003cp\u003eOpen your Kibana instance, click “Settings” and add a new pattern. If you type “weather” into the index pattern, it should autofill the timestamp.\u003c/p\u003e\u003cp\u003eMine looks like this:\u003c/p\u003e\u003cp\u003e\u003cimg alt=\"blog-4-weather-station.png\" data-sys-asset-uid=\"blt6055beb7b47ea60a\" src=\"https://api.contentstack.io/v2/assets/57bb09d81251899a28dc201f/download?uid=blt6055beb7b47ea60a\"/\u003e\u003c/p\u003e\u003cp\u003eOnce you create a new index, you can click `Visualize` to start making graphs.\u003c/p\u003e\u003cp\u003eHere’s one I created. Start with the settings I have in the screenshot and then experiment to find what you like.\u003c/p\u003e\u003cp\u003e\u003cimg alt=\"blog-5-weather-station.png\" data-sys-asset-uid=\"bltdcbcc5191d4eec35\" src=\"https://api.contentstack.io/v2/assets/57bb09de7791d1a8275e38f5/download?uid=bltdcbcc5191d4eec35\"/\u003e\u003c/p\u003e\u003cp\u003e\u003ca name=\"sketch1\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003c/p\u003e\u003ch2\u003eArduino Code Listing\u003c/h2\u003e\u003cpre class=\"prettyprint\"\u003e /*\u003cbr /\u003e * Simple HTTP get webclient test\u003cbr /\u003e */\u003cbr /\u003e#include \u0026lt;ESP8266WiFi.h\u0026gt;\u003cbr /\u003e#include \u0026lt;Wire.h\u0026gt;\u003cbr /\u003e#include \u0026lt;Adafruit_Sensor.h\u0026gt;\u003cbr /\u003e#include \u0026lt;Adafruit_BMP085_U.h\u0026gt;\u003cbr /\u003e#include \u0026lt;TimeLib.h\u0026gt;\u003cbr /\u003e#include \u0026lt;WiFiUdp.h\u0026gt;\u003cbr /\u003eAdafruit_BMP085_Unified bmp = Adafruit_BMP085_Unified(10085);\u003cbr /\u003estatic const char ntpServerName[] = \"us.pool.ntp.org\"; \u003cbr /\u003e// Setup your wifi SSID and password here.\u003cbr /\u003econst char* ssid = \"CanIGetAWiFi\";\u003cbr /\u003econst char* password = \"n0youCan7\";\u003cbr /\u003econst int timeZone = 0; // UTC\u003cbr /\u003e// Variables needed for NTP\u003cbr /\u003e// Elasticsearch needs us to generate timestamps for the data in order to make date histograms in Kibana.\u003cbr /\u003eWiFiUDP Udp;\u003cbr /\u003eunsigned int localPort = 8888; // local port to listen for UDP packets\u003cbr /\u003etime_t getNtpTime();\u003cbr /\u003evoid printDigits(int digits);\u003cbr /\u003evoid sendNTPpacket(IPAddress \u0026amp;address);\u003cbr /\u003e// This is the IP address, or DNS name of my Elasticsearch instance.\u003cbr /\u003econst char* host = \"192.168.1.215\";\u003cbr /\u003econst int port = 9200;\u003cbr /\u003eint motion;\u003cbr /\u003e// Variables\u003cbr /\u003efloat temperature;\u003cbr /\u003eString timestamp;\u003cbr /\u003etime_t start_time;\u003cbr /\u003euint32_t t_ms;\u003cbr /\u003euint32_t start_mills;\u003cbr /\u003eString run_mills;\u003cbr /\u003eint milis_chars;\u003cbr /\u003evoid setup() {\u003cbr /\u003e Serial.begin(115200);\u003cbr /\u003e delay(100);\u003cbr /\u003e // We start by connecting to a WiFi network\u003cbr /\u003e Serial.println();\u003cbr /\u003e Serial.print(\"Connecting to \");\u003cbr /\u003e Serial.println(ssid);\u003cbr /\u003e WiFi.begin(ssid, password);\u003cbr /\u003e while (WiFi.status() != WL_CONNECTED) {\u003cbr /\u003e delay(500);\u003cbr /\u003e Serial.print(\".\");\u003cbr /\u003e }\u003cbr /\u003e Serial.println(\"\");\u003cbr /\u003e Serial.println(\"WiFi connected\"); \u003cbr /\u003e Serial.println(\"IP address: \");\u003cbr /\u003e Serial.println(WiFi.localIP());\u003cbr /\u003e Serial.println(\"Setting up NTP\");\u003cbr /\u003e Udp.begin(localPort);\u003cbr /\u003e Serial.print(\"Local port: \");\u003cbr /\u003e Serial.println(Udp.localPort());\u003cbr /\u003e Serial.println(\"waiting for sync\");\u003cbr /\u003e setSyncProvider(getNtpTime);\u003cbr /\u003e setSyncInterval(300);\u003cbr /\u003e start_time = now();\u003cbr /\u003e Serial.println(\"Pressure Sensor Test\"); Serial.println(\"\");\u003cbr /\u003e /* Initialise the sensor */\u003cbr /\u003e if(!bmp.begin())\u003cbr /\u003e {\u003cbr /\u003e /* There was a problem detecting the BMP085 ... check your connections */\u003cbr /\u003e Serial.print(\"Ooops, no BMP180 detected ... Check your wiring!\");\u003cbr /\u003e while(1);\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003evoid loop() { \u003cbr /\u003e // Measure pressure \u0026amp; temperature from BMP sensor\u003cbr /\u003e // Modified from https://learn.adafruit.com/bmp085/using-the-bmp085-api-v2\u003cbr /\u003e sensors_event_t event;\u003cbr /\u003e bmp.getEvent(\u0026amp;event);\u003cbr /\u003e float pressure = event.pressure;\u003cbr /\u003e float temperature;\u003cbr /\u003e bmp.getTemperature(\u0026amp;temperature);\u003cbr /\u003e // Use WiFiClient class to create TCP connections, connect to the Elasticsearch instance.\u003cbr /\u003e WiFiClient client;\u003cbr /\u003e if (!client.connect(host, port)) {\u003cbr /\u003e Serial.println(\"connection failed\");\u003cbr /\u003e return;\u003cbr /\u003e }\u003cbr /\u003e run_mills = String(millis());\u003cbr /\u003e milis_chars = run_mills.length();\u003cbr /\u003e // To generate a millisecond unix timestamp, we first get the second timestamp, and add to it, the last three characters of the arduino/relative millisecond timestamp\u003cbr /\u003e timestamp = String(now()) + run_mills.charAt(milis_chars-3) + run_mills.charAt(milis_chars-2) + run_mills.charAt(milis_chars-1);\u003cbr /\u003e // With such a simple document, we're just going to use a string to generate the JSON to send to Elasticsearch\u003cbr /\u003e String data = \"{pressure: \"+String(pressure)+\", temperature: \"+String(temperature)+\", timestamp: \"+ timestamp +\"}\";\u003cbr /\u003e // We can inspect the data being sent over the Serial line, in the Arduino IDE.\u003cbr /\u003e Serial.println(data);\u003cbr /\u003e // We now create a URI for the request\u003cbr /\u003e // This is the index of the Elasticsearch document we're creating\u003cbr /\u003e String url = \"/weather/reading\";\u003cbr /\u003e // \u003cbr /\u003e client.print(String(\"POST \") + url + \" HTTP/1.1\\r\\n\" +\u003cbr /\u003e // If you're using Shield, you'll need to generate an authentication header\u003cbr /\u003e \"Content-Length: \" + data.length() + \"\\r\\n\" +\u003cbr /\u003e \"\\r\\n\" + data);\u003cbr /\u003e // We need this delay in here to give the WiFi Time\u003cbr /\u003e delay(50);\u003cbr /\u003e // Read all the lines of the reply from server and print them to Serial\u003cbr /\u003e while(client.available()){\u003cbr /\u003e String line = client.readStringUntil('\\r');\u003cbr /\u003e Serial.print(line);\u003cbr /\u003e }\u003cbr /\u003e Serial.println();\u003cbr /\u003e}\u003cbr /\u003e/* Copied from https://github.com/PaulStoffregen/Time/blob/master/examples/TimeNTP_ESP8266WiFi/TimeNTP_ESP8266WiFi.ino#L99 */\u003cbr /\u003e/*-------- NTP code ----------*/\u003cbr /\u003econst int NTP_PACKET_SIZE = 48; // NTP time is in the first 48 bytes of message\u003cbr /\u003ebyte packetBuffer[NTP_PACKET_SIZE]; //buffer to hold incoming \u0026amp; outgoing packets\u003cbr /\u003etime_t getNtpTime()\u003cbr /\u003e{\u003cbr /\u003e IPAddress ntpServerIP; // NTP server's ip address\u003cbr /\u003e while (Udp.parsePacket() \u0026gt; 0) ; // discard any previously received packets\u003cbr /\u003e Serial.println(\"Transmit NTP Request\");\u003cbr /\u003e // get a random server from the pool\u003cbr /\u003e WiFi.hostByName(ntpServerName, ntpServerIP);\u003cbr /\u003e Serial.print(ntpServerName);\u003cbr /\u003e Serial.print(\": \");\u003cbr /\u003e Serial.println(ntpServerIP);\u003cbr /\u003e sendNTPpacket(ntpServerIP);\u003cbr /\u003e uint32_t beginWait = millis();\u003cbr /\u003e while (millis() - beginWait \u0026lt; 1500) {\u003cbr /\u003e int size = Udp.parsePacket();\u003cbr /\u003e if (size \u0026gt;= NTP_PACKET_SIZE) {\u003cbr /\u003e Serial.println(\"Receive NTP Response\");\u003cbr /\u003e Udp.read(packetBuffer, NTP_PACKET_SIZE); // read packet into the buffer\u003cbr /\u003e unsigned long secsSince1900;\u003cbr /\u003e // convert four bytes starting at location 40 to a long integer\u003cbr /\u003e secsSince1900 = (unsigned long)packetBuffer[40] \u0026lt;\u0026lt; 24;\u003cbr /\u003e secsSince1900 |= (unsigned long)packetBuffer[41] \u0026lt;\u0026lt; 16;\u003cbr /\u003e secsSince1900 |= (unsigned long)packetBuffer[42] \u0026lt;\u0026lt; 8;\u003cbr /\u003e secsSince1900 |= (unsigned long)packetBuffer[43];\u003cbr /\u003e return secsSince1900 - 2208988800UL + timeZone * SECS_PER_HOUR;\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e Serial.println(\"No NTP Response :-(\");\u003cbr /\u003e return 0; // return 0 if unable to get the time\u003cbr /\u003e}\u003cbr /\u003e// send an NTP request to the time server at the given address\u003cbr /\u003evoid sendNTPpacket(IPAddress \u0026amp;address)\u003cbr /\u003e{\u003cbr /\u003e // set all bytes in the buffer to 0\u003cbr /\u003e memset(packetBuffer, 0, NTP_PACKET_SIZE);\u003cbr /\u003e // Initialize values needed to form NTP request\u003cbr /\u003e // (see URL above for details on the packets)\u003cbr /\u003e packetBuffer[0] = 0b11100011; // LI, Version, Mode\u003cbr /\u003e packetBuffer[1] = 0; // Stratum, or type of clock\u003cbr /\u003e packetBuffer[2] = 6; // Polling Interval\u003cbr /\u003e packetBuffer[3] = 0xEC; // Peer Clock Precision\u003cbr /\u003e // 8 bytes of zero for Root Delay \u0026amp; Root Dispersion\u003cbr /\u003e packetBuffer[12] = 49;\u003cbr /\u003e packetBuffer[13] = 0x4E;\u003cbr /\u003e packetBuffer[14] = 49;\u003cbr /\u003e packetBuffer[15] = 52;\u003cbr /\u003e // all NTP fields have been given values, now\u003cbr /\u003e // you can send a packet requesting a timestamp:\u003cbr /\u003e Udp.beginPacket(address, 123); //NTP requests are to port 123\u003cbr /\u003e Udp.write(packetBuffer, NTP_PACKET_SIZE);\u003cbr /\u003e Udp.endPacket();\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cimg alt=\"blog-6-weather-station.jpg\" data-sys-asset-uid=\"bltcfb2a4739572e401\" src=\"https://api.contentstack.io/v2/assets/57bb09e71251899a28dc202f/download?uid=bltcfb2a4739572e401\"/\u003e\u003c/p\u003e\u003cp\u003eIt turned out that the temperature alone wasn’t enough to dissuade my friend that I’ve been spending too much time inside the house. That being said, setting up this experiment couldn’t have been easier and I’m really looking forward to using WiFi-enabled microcontrollers to send readings to Elasticsearch for further experiments.\u003c/p\u003e\u003cp\u003eI also got this sweet live gif of myself with a hair dryer and a popsicle on this temperature sensor, so there’s that.\u003c/p\u003e\u003cp\u003e\u003cimg alt=\"blog-7-weather-station.gif\" data-sys-asset-uid=\"bltb7b317058e3f4f13\" src=\"https://api.contentstack.io/v2/assets/57bb0a771251899a28dc2049/download?uid=bltb7b317058e3f4f13\"/\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://twitter.com/issackelly\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://twitter.com/issackelly\"\u003eIssac Kelly\u003c/a\u003e is an Engineer and Designer in Oakland, CA.\u003c/p\u003e","category":[{"title":"User Stories (not in use)","key":"customers","tags":[],"locale":"en-us","uid":"blt26ff0a1ade01f60d","created_by":"sys_blt57a423112de8a853","updated_by":"blt3044324473ef223b70bc674c","created_at":"2018-08-27T12:42:07.232Z","updated_at":"2024-05-10T13:44:13.133Z","ACL":{},"_version":4,"label_l10n":"Customers","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-15T21:04:11.996Z","user":"blt36e890d06c5ec32c"}}],"created_at":"2019-04-01T13:40:01.214Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"blt57d8676269e9a5a6","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-10T10:27:35.705Z","updated_at":"2018-10-10T10:27:35.705Z","content_type":"image/png","file_size":"202128","filename":"blog-hero-weather-station.png","title":"blog-hero-weather-station.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T23:58:01.776Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt57d8676269e9a5a6/5bbdd417bb1e335136d9ec2e/blog-hero-weather-station.png"},"markdown_l10n":"","publish_date":"2016-08-25T13:53:34.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"An Arduino-Based Home Weather Station Built with Arduino, Elasticsearch, and Kibana","seo_description_l10n":"I wanted to visualize the weather outside. So I built a way to do it using some hobby hardware, Elasticsearch, and Kibana.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8d9878a192a994c7","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-10T10:27:38.411Z","updated_at":"2018-10-10T10:27:38.411Z","content_type":"image/png","file_size":"100314","filename":"blog-thumbnail-weather-station.png","title":"blog-thumbnail-weather-station.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T23:58:01.776Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8d9878a192a994c7/5bbdd41a117bd0dc7fcc606c/blog-thumbnail-weather-station.png"},"title":"An Arduino-Based Home Weather Station on the Elastic Stack","title_l10n":"An Arduino-Based Home Weather Station on the Elastic Stack","updated_at":"2025-03-10T10:51:44.265Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/arduino-based-home-weather-station-on-the-elastic-stack","publish_details":{"time":"2025-03-10T10:51:49.501Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt53538aa46a21e49d","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic{ON}Tour was a sell-out Elastic user conference held in Munich on Nov 10, 2015. This year Elastic raised €16K to support Django Girls awesome programs.","author":["bltbf7b8e4eaf437b73"],"body_l10n":"\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4cf60342dfd738264356/download?uid=blta07409776f340069?uid=blta07409776f340069\" data-sys-asset-uid=\"bltb9dccc8472d13e3c\" alt=\"Djangogirls.png\" width=\"129\" height=\"129\" style=\"width: 129;height: 129;float: right;margin: 0 0 20px 20px;text-align: right;\"/\u003e\u003ca href=\"https://djangogirls.org/\" target=\"_blank\"\u003eDjango Girls\u003c/a\u003e is a non-profit organization that empowers and helps women to organize free, one-day programming workshops by providing tools, resources and support. It was born in Berlin in July 2014 and started by two Olas:\u0026nbsp;\u003ca href=\"http://twitter.com/olasitarska\" target=\"_blank\"\u003eSitarska\u003c/a\u003e\u0026nbsp;and\u0026nbsp;\u003ca href=\"http://twitter.com/asendecka\" target=\"_blank\"\u003eSendecka\u003c/a\u003e. Today, Django Girls is a volunteer run organization with hundreds of people contributing to bring more women into the Python \u0026amp; Django communities.\u003c/p\u003e\u003cp\u003eThis summer, Django Girls celebrated its \u003ca href=\"http://love.djangogirls.org/\" target=\"_blank\"\u003efirst year anniversary\u003c/a\u003e: nearly one hundred event have happened since its inception. Growing that quickly has been amazing but also a bit scary: to make it more sustainable, the support team decided to recruit someone to help them. I was lucky enough to be selected and I started working for Django Girls in September.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOne of the perks of being the Django Girls Awesomeness Ambassador is receiving cool emails. Some of these emails include those from future organizers really excited about their workshops, as well as from attendees and coaches who just want to say thank you. When we received an email from \u003ca href=\"https://www.elastic.co/\" target=\"_blank\"\u003eElastic\u003c/a\u003e expressing interest in supporting the Django Girls mission, I was only starting the job and I have to say, I was as excited as our organizers: sponsorship for Django Girls and going to Munich to run a booth, count me in! I started to prepare a booth, think about what to say to people and what swag to bring with me. A few days before going to Munich, we received another email from Elastic saying they managed to raise almost\u0026nbsp;15,000 € for us (see slide below from the event presentation. I went to Munich still not believing that all this money was for us! “Of course it is!”, said Livia, my contact from Elastic and she asked me what we planned to do with it.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4cf658208ba076e2921d/download?uid=bltd9c90d33e4b36832?uid=bltd9c90d33e4b36832\" data-sys-asset-uid=\"blt7f9baad69197d864\" alt=\"Munich Tour.jpg\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eFig. 1 Impression from the main stage at Elastic{ON} Tour Munich\u003c/em\u003e\u003c/p\u003e\u003cp\u003eI'm especially excited, because thanks to the Elastic sponsorship my future as a Awesomeness Ambassador is secured: currently, most of the money Django Girls Foundation receives covers my role in the organization. My job is to make the life of the \u003ca href=\"https://github.com/DjangoGirls/wiki/blob/master/general/people.md\" target=\"_blank\"\u003esupport team\u003c/a\u003e easier so they can work on other projects: a \u003ca href=\"http://yaypython.com/\" target=\"_blank\"\u003eprogramming book\u003c/a\u003e, cool \u003ca href=\"https://www.youtube.com/channel/UC0hNd2uW8jTR5K3KBzRuG2A\" target=\"_blank\"\u003evideos for people who can’t attend our workshop\u003c/a\u003e, etc. My main job is to stay on top of the Django Girls inbox and make sure that anyone who asks for help will be answered swiftly with the necessary support, especially making sure everyone is happy and that planned events are happening as scheduled. I also help maintain our website and resources: our \u003ca href=\"http://tutorial.djangogirls.org\" target=\"_blank\"\u003etutorial\u003c/a\u003e and its translations, \u003ca href=\"https://djangogirls.org/resources/\" target=\"_blank\"\u003edocumentations\u003c/a\u003e, \u003ca href=\"https://github.com/DjangoGirls/resources\" target=\"_blank\"\u003eposters and swag\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eOn top of securing the existence of the Awesomeness Ambassador position, we also plan to use this money on two cool initiatives. The first one is sending swag boxes to organizers full of stickers, buttons and tattoos - it will be our “Django Girls Organizer Starter Kit”. If you haven’t heard about us already, you have to look at \u003ca href=\"https://www.flickr.com/photos/djangogirls/\" target=\"_blank\"\u003epictures\u003c/a\u003e of our events: we want a positive learning atmosphere and all these little details contribute to it.\u003c/p\u003e\u003cp\u003eThe second initiative is working on the inaugural Django Girls Summit! Yes, the Summit! We are extremely excited about this plan. We want to organize a two day unconference where organizers could meet and share their experiences about \u0026nbsp;Django Girls workshops: what was hard, how they handled problems, how they find sponsors and so on and so on. We imagine it as a place where people who are making Django Girls what it is now could meet in person and learn from each other. We are really excited about this and can’t wait to start planning it!\u003c/p\u003e\u003cp\u003eThank you again Elastic for the visibility you’ve gave to our organization, for the booth at Munich and for this awesome sponsorship. You have been with us from almost the very beginning, supporting us on many different levels: as mentors, supporters and sponsors. Thank you for being awesome!\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp style=\"text-align: right;\"\u003e\u003cem\u003eLucie Daeye, is the Django Girls Awesomess Ambassador since September 2015 and organizer of Pyladies Paris. She was doing a PhD in Geography and Korean studies when decided to switch career to become a developer.\u003c/em\u003e\u003c/p\u003e\u003cp style=\"text-align: right;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem \u003e\u003cbr italic=\"[object Object]\"/\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem \u003e\u003cbr italic=\"[object Object]\"/\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eThe original blog post has been published a few days ago\u0026nbsp;\u003c/em\u003e\u003ca href=\"http://blog.djangogirls.org/post/135185350903/meet-our-new-sponsor-elastic\" target=\"_blank\"\u003e\u003cem\u003ehere\u003c/em\u003e\u003c/a\u003e\u003cem\u003e.\u003c/em\u003e\u003cbr /\u003e\u003c/p\u003e","category":[{"uid":"bltc253e0851420b088","_version":4,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:45:23.873Z","created_by":"sys_blt57a423112de8a853","key":"culture","label_l10n":"Culture","tags":[],"title":"Culture","updated_at":"2024-05-10T13:44:28.145Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.214Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:32:02.903Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":null,"markdown_l10n":"","publish_date":"2015-12-15T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Django Girls review of Elastic{ON} Tour Munich","seo_description_l10n":"Elastic{ON}Tour was a sell-out Elastic user conference held in Munich on Nov 10, 2015. This year Elastic raised €16K to support Django Girls awesome programs. Read their review here.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt796d7e3e5965fd1b","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T11:20:53.918Z","updated_at":"2018-10-09T11:20:53.918Z","content_type":"image/png","file_size":"38195","filename":"logo-django-girls-720x420.png","title":"logo-django-girls-720x420.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T03:15:09.002Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt796d7e3e5965fd1b/5bbc8f15c863b8e614126a29/logo-django-girls-720x420.png"},"title":"Django Girls review of Elastic{ON} Tour Munich","title_l10n":"Django Girls review of Elastic{ON} Tour Munich","updated_at":"2025-03-10T10:43:21.392Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/django-girls-review-of-elasticon-tour-munich","publish_details":{"time":"2025-03-10T10:43:25.442Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt314e43bf8d382077","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt619a4d5c39ed775a"],"body_l10n":"\u003cp\u003eGaining actionable insights from continuously produced data in real-time is a common requirement for many businesses today. A wide-spread use case for real-time data processing is dashboarding. A typical architecture to support such a use case is based on a data stream processor, a data store with low latency read/write access, and a visualization framework.\u003c/p\u003e\u003cp class=\"normal\"\u003eIn this blog post, we demonstrate how to build a real-time dashboard solution for stream data analytics using Apache Flink, Elasticsearch, and Kibana. The following figure depicts our system architecture.\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4ced43e9adc538714ad1/download?uid=bltae1ce211c170912e?uid=bltae1ce211c170912e\" data-sys-asset-uid=\"blt7e4ec8c4f4708211\" alt=\"Real-time-dashboard-for-stream-data analytics.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eIn our architecture, Apache Flink executes stream analysis jobs that ingest a data stream, apply transformations to analyze, transform, and model the data in motion, and write their results to an Elasticsearch index. Kibana connects to the index and queries it for data to visualize. All components of our architecture are open source systems under the Apache License 2.0. We show how to implement a Flink DataStream program that analyzes a stream of taxi ride events and writes its results to Elasticsearch and give instructions on how to connect and configure Kibana to visualize the analyzed data in real-time.\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eWhy use Apache Flink for stream processing?\u003c/h2\u003e\u003cp class=\"normal\"\u003eBefore we dive into the details of implementing our demo application, we discuss some of the features that make Apache Flink an outstanding stream processor. Apache Flink 0.10, which was recently released, comes with a competitive set of stream processing features, some of which are unique in the open source domain.\u0026nbsp;The most important ones are:\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cstrong\u003eSupport for event time and out of order streams: \u003c/strong\u003eIn reality, streams of events rarely arrive in the order that they are produced, especially streams from distributed systems and devices. Until now, it was up to the application programmer to correct this “time drift”, or simply ignore it and accept inaccurate results, as streaming systems (at least in the open source world) had no support for \u003cem\u003eevent time\u003c/em\u003e (i.e., processing events by the time they happened in the real world). Flink 0.10 is the first open source engine that supports out of order streams and which is able to consistently process events according to their timestamps.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eExpressive and easy-to-use APIs in Scala and Java: \u003c/strong\u003eFlink's DataStream API ports many operators which are well known from batch processing APIs such as map, reduce, and join to the streaming world. In addition, it provides stream-specific operations such as window, split, and connect. First-class support for user-defined functions eases the implementation of custom application behavior. The DataStream API is available in Scala and Java.\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003e\u003cstrong\u003eSupport for sessions and unaligned windows:\u003c/strong\u003e Most streaming systems have some concept of \u003cem\u003ewindowing\u003c/em\u003e, i.e., a grouping of events based on some function of time. Unfortunately, in many systems these windows are hard-coded and connected with the system’s internal checkpointing mechanism. Flink is the first open source streaming engine that completely decouples windowing from fault tolerance, allowing for richer forms of windows, such as sessions.\u003cspan\u003e\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eConsistency, fault tolerance, and high availability: \u003c/strong\u003eFlink guarantees consistent state updates in the presence of failures (often called “exactly-once processing”), and consistent data movement between selected sources and sinks (e.g., consistent data movement between Kafka and HDFS). Flink also supports worker and master failover, eliminating any single point of failure.\u0026nbsp;\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003e\u003cstrong\u003eLow latency and high throughput:\u003c/strong\u003e We have clocked Flink at \u003ca href=\"http://data-artisans.com/high-throughput-low-latency-and-exactly-once-stream-processing-with-apache-flink/\" target=\"_blank\"\u003e1.5 million events per second per core\u003c/a\u003e, and have also observed latencies in the \u003ca href=\"http://data-artisans.com/high-throughput-low-latency-and-exactly-once-stream-processing-with-apache-flink/\" target=\"_blank\"\u003e25 millisecond range\u003c/a\u003e for jobs that include network data shuffling. Using a tuning knob, Flink users can navigate the latency-throughput trade off, making the system suitable for both high-throughput data ingestion and transformations, as well as ultra low latency (millisecond range) applications.\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003e\u003cstrong\u003eConnectors and integration points:\u003c/strong\u003e Flink integrates with a wide variety of open source systems for data input and output (e.g., HDFS, Kafka, Elasticsearch, HBase, and others), deployment (e.g., YARN), as well as acting as an execution engine for other frameworks (e.g., Cascading, Google Cloud Dataflow). The Flink project itself comes bundled with a Hadoop MapReduce compatibility layer, a Storm compatibility layer, as well as libraries for machine learning and graph processing.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eDeveloper productivity and operational simplicity: \u003c/strong\u003eFlink runs in a variety of environments. Local execution within an IDE significantly eases development and debugging of Flink applications. In distributed setups, Flink runs at massive scale-out. The YARN mode allows users to bring up Flink clusters in a matter of seconds. Flink serves monitoring metrics of jobs and the system as a whole via a well-defined REST interface. A build-in web dashboard displays these metrics and makes monitoring of Flink very convenient.\u003cspan\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp class=\"normal\"\u003eThe combination of these features makes Apache Flink a unique choice for many stream processing applications.\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eBuilding a demo application with Flink, Elasticsearch, and Kibana\u003c/h2\u003e\u003cp class=\"normal\"\u003eOur demo ingests a stream of taxi ride events and identifies places that are popular within a certain period of time, i.e., we compute every 5 minutes the number of passengers that arrived at each location within the last 15 minutes by taxi. This kind of computation is known as a sliding window operation. We share a \u003ca href=\"https://github.com/dataArtisans/flink-streaming-demo/blob/master/src/main/scala/com/dataartisans/flink_demo/examples/SlidingArrivalCount.scala\" target=\"_blank\"\u003eScala implementation\u003c/a\u003e of this application (among others) on \u003ca href=\"https://github.com/dataArtisans/flink-streaming-demo\" target=\"_blank\"\u003eGithub\u003c/a\u003e. You can easily run the application from your IDE by cloning the repository and importing the code. The \u003ca href=\"https://github.com/dataArtisans/flink-streaming-demo\" target=\"_blank\"\u003erepository's README\u003c/a\u003e file provides more detailed instructions.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eAnalyze the taxi ride event stream with Apache Flink\u003c/h2\u003e\u003cp class=\"normal\"\u003eFor the demo application, we generate a stream of taxi ride events from a\u003ca href=\"http://www.nyc.gov/html/tlc/html/about/trip_record_data.shtml\"\u003e\u003cbr /\u003e\u003c/a\u003e\u003ca href=\"http://www.nyc.gov/html/tlc/html/about/trip_record_data.shtml\" target=\"_blank\"\u003epublic dataset of the New York City Taxi and LimousineCommission\u003c/a\u003e (TLC). The data set consists of records about taxi trips in New York City from 2009 to 2015. We took some of this data and converted it into a data set of taxi ride events by splitting each trip record into a ride start and a ride end event. The events have the following schema:\u0026nbsp;\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003erideId: Long\u003cbr /\u003etime: DateTime // start or end time\u003cbr /\u003eisStart: Boolean // true = ride start, false = ride end\u003cbr /\u003elocation: GeoPoint // lon/lat of pick-up or drop-off location\u003cbr /\u003epassengerCnt: short\u003cbr /\u003etravelDist: float // -1 on start events\u003cbr /\u003e\u003c/pre\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003eWe implemented a custom SourceFunction to serve a DataStream[TaxiRide] from the ride event data set. In order to generate the stream as realistically as possible, events are emitted by their timestamps. Two events that occurred ten minutes after each other in reality are ingested by Flink with a ten minute lag. A speed-up factor can be specified to “fast-forward” the stream, i.e., with a speed-up factor of 2.0, these events are served five minutes apart. Moreover,\u0026nbsp;the source function adds a configurable random delay to each event to simulate the real-world jitter. Given this stream of taxi ride events, our task is to compute every five minutes the number of passengers that arrived within the last 15 minutes at locations in New York City by taxi.\u003c/p\u003e\u003cp class=\"normal\"\u003eAs a first step we obtain a StreamExecutionEnvironment and set the TimeCharacteristic to EventTime. Event time mode guarantees consistent results even in case of historic data or data which is delivered out-of-order.\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003eval env = StreamExecutionEnvironment.getExecutionEnvironment\u003cbr /\u003eenv.setStreamTimeCharacteristic(TimeCharacteristic.EventTime)\u003cbr /\u003e\u003c/pre\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003eNext, we define the data source that generates a DataStream[TaxiRide] with at most 60 seconds serving delay (events are out of order by max. 1 minute) and a speed-up factor of 600 (10 minutes are served in 1 second).\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003e// Define the data source\u003cbr /\u003eval rides: DataStream[TaxiRide] = env.addSource(new TaxiRideSource(\u003cbr /\u003e “./data/nycTaxiData.gz”, 60, 600.0f))\u003cbr /\u003e\u003c/pre\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003eSince we are only interested in locations that people travel to (and not where they come from) and because the original data is a little bit messy (locations are not always correctly specified), we apply a few filters to first cleanse the data.\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003eval cleansedRides = rides\u003cbr /\u003e // filter for ride end events\u003cbr /\u003e .filter( !_.isStart )\u003cbr /\u003e // filter for events in NYC\u003cbr /\u003e .filter( r =\u0026gt; NycGeoUtils.isInNYC(r.location) )\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003eThe location of a taxi ride event is defined as a pair of continuous longitude/latitude values. We need to map them into a finite set of regions in order to be able to aggregate events by location. We do this by defining a grid of approx. 100x100 meter cells on the area of New York City. We use a utility function to map event locations to cell ids and extract the passenger count as follows:\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003e// map location coordinates to cell Id, timestamp, and passenger count\u003cbr /\u003eval cellIds: DataStream[(Int, Long, Short)] = cleansedRides\u003cbr /\u003e .map { r =\u0026gt;\u003cbr /\u003e ( NycGeoUtils.mapToGridCell(r.location), r.time.getMillis, r.passengerCnt )\u003cbr /\u003e }\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003eAfter these preparation steps, we have the data that we would like to aggregate. Since we want to compute the passenger count for each location (cell id), we start by keying (partitioning by key) the stream by cell id (_._1). Subsequently, we define a sliding time window and run a \u0026lt;code\u0026gt;WindowFunction\u0026lt;/code\u0026gt;; by calling apply():\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003eval passengerCnts: DataStream[(Int, Long, Int)] = cellIds\u003cbr /\u003e // key stream by cell Id\u003cbr /\u003e .keyBy(_._1)\u003cbr /\u003e // define sliding window on keyed stream\u003cbr /\u003e .timeWindow(Time.minutes(15), Time.minutes(5))\u003cbr /\u003e // count events in window\u003cbr /\u003e .apply { (\u003cbr /\u003e cell: Int,\u003cbr /\u003e window: TimeWindow,\u003cbr /\u003e events: Iterable[(Int, Short)],\u003cbr /\u003e out: Collector[(Int, Long, Int)]) =\u0026gt;\u003cbr /\u003e out.collect( ( cell, window.getEnd, events.map( _._2 ).sum ) )\u003cbr /\u003e }\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003eThe timeWindow()\u0026nbsp;operation groups stream events into finite sets of records on which\u0026nbsp;a window or aggregation function can be applied. For our application, we call apply() to process the windows using a WindowFunction. The WindowFunction\u0026nbsp;receives four parameters, a Tuple that contains the key of the window, a Window object that contains details such as the start and end time of the window, an Iterable\u0026nbsp;over all elements in the window, and a Collector to collect the records emitted by the WindowFunction. We want to count the number of passengers that arrive within the window’s time bounds. Therefore, we have to emit a single record that contains the grid cell id, the end time of the window, and the sum of the passenger counts which is computed by extracting the individual passenger counts from the iterable (events.map( _._2)) and summing them (.sum).\u0026nbsp;\u003cbr /\u003eFinally, we translate the cell id back into a GeoPoint (referring to the center of the cell) and print the result stream to the standard output. The final env.execute() call takes care of submitting the program for execution.\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003eval cntByLocation: DataStream[(Int, Long, GeoPoint, Int)] = passengerCnts \u003cbr /\u003e// map cell Id back to GeoPoint\u003cbr /\u003e.map( r =\u0026gt; (r._1, r._2, NycGeoUtils.getGridCellCenter(r._1), r._3 ) )\u003cbr /\u003ecntByLocation\u003cbr /\u003e// print to console\u003cbr /\u003e.print()\u003cbr /\u003eenv.execute(“Total passenger count per location”)\u003cbr /\u003e\u003c/pre\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003eIf you followed the \u003ca href=\"https://github.com/dataartisans/flink-streaming-demo\" target=\"_blank\"\u003einstructions to import the demo code\u003c/a\u003e into your IDE, you can run the \u003ca href=\"https://github.com/dataArtisans/flink-streaming-demo/blob/master/src/main/scala/com/dataartisans/flink_demo/examples/SlidingArrivalCount.scala\" target=\"_blank\"\u003eSlidingArrivalCount.scala\u003c/a\u003e program by executing its main() methods. You will see Flink’s log messages and the computed results being printed to the standard output.\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eYou might wonder why the the program produces results much faster than once every five minutes per location. This is due to the event time processing mode. Since all time-based operations (such as windows) are based on the timestamps of the events, the program becomes independent of the speed at which the data is served. This also means that you can process historic data which is read at full speed from some data store and data which is continuously produced with exactly the same program.\u003c/p\u003e\u003cp class=\"normal\"\u003eOur streaming program will run for a few minutes until the packaged data set is completely processed but you can terminate it at any time. As a next step, we show how to write the result stream into an Elasticsearch index.\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003ePrepare the Elasticsearch\u003c/h2\u003e\u003cp class=\"normal\" style=\"line-height: 22.4px;color: rgb(57, 57, 57);font-family: Arial, Helvetica, Verdana, Tahoma, sans-serif;font-weight: normal;\"\u003e\u003co:p\u003eT\u003c/o:p\u003ehe Flink Elasticsearch connector depends on Elasticsearch 1.7.3. Follow these steps to setup Elasticsearch and to create an index.\u0026nbsp;\u003c/p\u003e\u003col\u003e\u003cli\u003eDownload Elasticsearch 1.7.3 as .tar (or .zip) archive \u003ca href=\"https://www.elastic.co/downloads/past-releases/elasticsearch-1-7-3\" target=\"_blank\"\u003ehere\u003c/a\u003e.\u003c/li\u003e\u003cli\u003eExtract the archive file:\u003cbr /\u003etar xvfz elasticsearch-1.7.3.tar.gz\u003cbr /\u003e\u003c/li\u003e\u003cli\u003e\u003cspan\u003e\u003c/span\u003eEnter the extracted directory and start Elasticsearch\u003cbr /\u003e\u003cpre class=\"prettyprint\"\u003ecd elasticsearch-1.7.3\u003cbr /\u003e./bin/elasticsearch\u003cbr /\u003e\u003c/pre\u003e\u003c/li\u003e\u003cli\u003eCreate an index called “nyc-idx”: \u0026nbsp;\u003cbr /\u003ecurl -XPUT \"http://localhost:9200/nyc-idx\"\u003c/li\u003e\u003cli\u003eCreate an index mapping called “popular-locations”:\u0026nbsp;\u003cpre class=\"prettyprint\" style=\"font-size: 12.6px;\"\u003ecurl -XPUT \"http://localhost:9200/nyc-idx/_mapping/popular-locations\" -d'\u003cbr /\u003e{\u003cbr /\u003e \"popular-locations\" : {\u003cbr /\u003e \"properties\" : {\u003cbr /\u003e \"cnt\": {\"type\": \"integer\"},\u003cbr /\u003e \"location\": {\"type\": \"geo_point\"},\u003cbr /\u003e \"time\": {\"type\": \"date\"}\u003cbr /\u003e }\u003cbr /\u003e } \u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp class=\"normal\"\u003eThe \u003ca href=\"https://github.com/dataArtisans/flink-streaming-demo/blob/master/src/main/scala/com/dataartisans/flink_demo/examples/SlidingArrivalCount.scala\" target=\"_blank\"\u003eSlidingArrivalCount.scala\u003c/a\u003e program is prepared to write data to the Elasticsearch index you just created but requires a few parameters to be set at the beginning of the main() function. Please set the parameters as follows:\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003eval writeToElasticsearch = true \u003cbr /\u003eval elasticsearchHost = // look up the IP address in the Elasticsearch logs\u003cbr /\u003eval elasticsearchPort = 9300\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eNow, everything is set up to fill our index with data. When you run the program by executing the main() method again, the program will write the resulting stream to the standard output as before but also insert the records into the nyc-idx Elasticsearch index.\u003c/p\u003e\u003cp\u003eIf you later want to clear the nyc-idx index, you can simply drop the mapping by running\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ecurl -XDELETE 'http://localhost:9200/nyc-idx/popular-locations'\u003cbr /\u003e\u003c/pre\u003e\u003cp class=\"normal\"\u003eand create the mapping again with the previous command.\u003cbr /\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eVisualizing the results with Kibana\u003c/h2\u003e\u003cp class=\"normal\"\u003eIn order to visualize the data that is inserted into Elasticsearch, we install Kibana 4.1.3 which is compatible with Elasticsearch 1.7.3. The setup is basically the same as for Elasticsearch.\u003c/p\u003e\u003cp class=\"normalCxSpMiddle\" style=\"margin-left: 36.0pt;mso-add-space: auto;text-indent: -18.0pt;mso-list: l0 level1 lfo1;\"\u003e1.\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; Download Kibana 4.1.3 for your environment \u003ca href=\"https://www.elastic.co/downloads/past-releases/kibana-4-1-3\" target=\"_blank\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003cp class=\"normalCxSpMiddle\" style=\"margin-left: 36.0pt;mso-add-space: auto;text-indent: -18.0pt;mso-list: l0 level1 lfo1;\"\u003e2.\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; Extract the archive file.\u003c/p\u003e\u003cp class=\"normalCxSpMiddle\" style=\"margin-left: 36.0pt;mso-add-space: auto;text-indent: -18.0pt;mso-list: l0 level1 lfo1;\"\u003e3.\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; Enter the extracted folder and start Kibana by running the start script: ./bin/kibana\u003c/p\u003e\u003cp class=\"normalCxSpMiddle\" style=\"margin-left: 36.0pt;mso-add-space: auto;text-indent: -18.0pt;mso-list: l0 level1 lfo1;\"\u003e4.\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp; Open \u003ca href=\"http://localhost:5601\" target=\"_blank\"\u003ehttp://localhost:5601\u003c/a\u003e in your browser to access Kibana.\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eNext we need to configure an index pattern. Enter the index name “nyc-idx” and click on “Create”. Do not uncheck the “Index contains time-based events” option. Now, Kibana knows about our index and we can start to visualize our data.\u003cbr /\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eFirst click on the “Discover” button at the top of the page. You will find that Kibana tells you “No results found”.\u003cbr /\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eThis is because Kibana restricts time-based events by default to the last 15 minutes. Since our taxi ride data stream starts on January, 1st 2013, we need to adapt the time range that is considered by Kibana. This is done by clicking on the label “Last 15 Minutes” in the top right corner and entering an absolute time range starting at 2013-01-01 and ending at 2013-01-06.\u003cbr /\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eWe have told Kibana where our data is and the valid time range and can continue to visualize the data. For example we can visualize the arrival counts on a map. Click on the “Visualize” button at the top of the page, select “Tile map”, and click on “From a new search”.\u003cbr /\u003eSee the following screenshot for the tile map\u0026nbsp;\u003cspan style=\"0: 0;1: :;2: ;3: l;4: ;;5: 1;6: :;7: ;8: i;9: ;;10: 2;11: :;12: ;13: n;14: ;;15: 3;16: :;17: ;18: e;19: ;;20: 4;21: :;22: ;23: -;24: ;;25: 5;26: :;27: ;28: h;29: ;;30: 6;31: :;32: ;33: e;34: ;;35: 7;36: :;37: ;38: i;39: ;;40: 8;41: :;42: ;43: g;44: ;;45: 9;46: :;47: ;48: h;49: ;;50: 1;51: 0;52: :;53: ;54: t;55: ;;56: 1;57: 1;58: :;59: ;60: :;61: ;;62: 1;63: 2;64: :;65: ;66: ;67: ;;68: 1;69: 3;70: :;71: ;72: 2;73: ;;74: 1;75: 4;76: :;77: ;78: 2;79: ;;80: 1;81: 5;82: :;83: ;84: .;85: ;;86: 1;87: 6;88: :;89: ;90: 4;91: ;;92: 1;93: 7;94: :;95: ;96: p;97: ;;98: 1;99: 8;100: :;101: ;102: x;103: ;;104: 1;105: 9;106: :;107: ;108: ;;109: ;;\"\u003econfiguration (left-hand side).\u003cbr /\u003e\u003cbr /\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4cedd8edd48f76936e3f/download?uid=bltf1f62db73d923fd0?uid=bltf1f62db73d923fd0\" data-sys-asset-uid=\"blted7add5609e867dc\" alt=\"Kibana-map-configuration.png\" style=\"max-width: 100%;\"/\u003e\u0026nbsp;\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003eAnother interesting visualization is to plot the number of arriving passengers over time. Click on “Visualize” at the top, select “Vertical bar chart”, and select “From a new search”. Again, have a look at the following screenshot for an example for how to configure the chart.\u003cbr /\u003e\u003cbr /\u003e\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4ced58208ba076e290cf/download?uid=blt6c4b8b02175e1150?uid=blt6c4b8b02175e1150\" data-sys-asset-uid=\"blt10c054ec93365faa\" alt=\"Kibana-verticl-bar-chart.png\" style=\"max-width: 100%;\"/\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003cbr /\u003eKibana offers many more chart types and visualization options which are out of the scope of this post. You can easily play around with this setup, explore Kibana’s features, and implement your own Flink DataStream programs to analyze taxi rides in New York City.\u003cbr /\u003e\u003cbr /\u003e\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003ch2\u003e\u003ca name=\"h.sk7gnkn852yk\"\u003e\u003cbr /\u003e\u003c/a\u003eWe’re done and hope you had some fun\u003c/h2\u003e\u003cp class=\"normal\"\u003eIn this blog post we demonstrated how to build a real-time dashboard application with Apache Flink, Elasticsearch, and Kibana. By supporting event-time processing, Apache Flink is able to produce meaningful and consistent results even for historic data or in environments where events arrive out-of-order. The expressive DataStream API with flexible window semantics results in significantly less custom application logic compared to other open source stream processing solutions. Finally, connecting Flink with Elasticsearch and visualizing the real-time data with Kibana is just a matter of a few minutes. We hope you enjoyed running our demo application and had fun playing around with the code.\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003cem\u003eFabian Hueske is a PMC member of Apache Flink. He is contributing to Flink \u0026nbsp;\u003c/em\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4cee9e7a83165490d14f/download?uid=blt0942cc226cc2c30c?uid=blt0942cc226cc2c30c\" data-sys-asset-uid=\"blt6e5b5c42df586968\" alt=\"fabian_2.jpg\" width=\"170\" height=\"170\" style=\"width: 170;height: 170;float: right;margin: 0px;text-align: right;\"/\u003e\u003cem\u003esince its earliest days when it started as research project as part of his PhD studies at TU Berlin. Fabian did internships with IBM Research, SAP Research, and Microsoft Research and is a co-founder of data Artisans, a Berlin-based start-up devoted to foster Apache Flink. He is interested in distributed data processing and query optimization.\u003c/em\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e\u003cp class=\"normal\"\u003e\u003co:p\u003e\u003c/o:p\u003e\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T13:17:56.437Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"data-artisans-kibana-architecture-full-bleed.jpg","uid":"blt8ce3612c276e15af","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:43:37.854Z","updated_at":"2019-02-04T06:43:37.854Z","content_type":"image/jpeg","file_size":"103634","filename":"data-artisans-kibana-architecture-full-bleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T03:20:51.318Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8ce3612c276e15af/5c57df1902ac90e80ba0a8cc/data-artisans-kibana-architecture-full-bleed.jpg"},"markdown_l10n":"","publish_date":"2015-12-07T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Building real-time dashboard applications with Apache Flink, Elasticsearch, and Kibana","seo_description_l10n":"This blog post shows how to build a real-time dashboard solution for stream data analytics using Apache Flink, Elasticsearch, and Kibana.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt0a824b431b273457","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:33:59.571Z","updated_at":"2018-10-09T10:33:59.571Z","content_type":"image/jpeg","file_size":"27109","filename":"data-artisans-logo.jpeg","title":"data-artisans-logo.jpeg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T03:20:51.318Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0a824b431b273457/5bbc8417b160bf6a367eb817/data-artisans-logo.jpeg"},"title":"Building real-time dashboard applications with Apache Flink, Elasticsearch, and Kibana","title_l10n":"Building real-time dashboard applications with Apache Flink, Elasticsearch, and Kibana","updated_at":"2025-03-10T10:42:06.957Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/building-real-time-dashboard-applications-with-apache-flink-elasticsearch-and-kibana","publish_details":{"time":"2025-03-10T10:42:11.648Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt21db21b485e789be","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"The new Singapore region for Elasticsearch Service is our 4th GCP region in Asia Pacific and our 12th GCP region globally.","author":["blta469eec733f1f129"],"body_l10n":"\u003cp\u003eWe are pleased to share the news that the Google Cloud Platform Singapore (asia-southeast1)\u0026nbsp;region for the Elasticsearch Service on Elastic Cloud is now available! This is our 12th GCP region globally and our 4th GCP region in Asia Pacific.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eExisting users can simply \u003ca href=\"https://cloud.elastic.co\"\u003elog in\u003c/a\u003e to start using the GCP Singapore region on our Elasticsearch Service immediately. New users can \u003ca href=\"https://www.elastic.co/gcp\"\u003esign up\u003c/a\u003e\u0026nbsp;for a free 14-day trial to try it out.\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eElasticsearch Service brings you the best search, observability, and security solutions. Get access to features such as machine learning and index lifecycle management. Build visualizations intuitively with Kibana Lens and put your creative mark on them with Canvas. And with our use case-ready deployment templates, provisioning, configuring, and scaling your deployments is a breeze.\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eGo deeper with Google and the Elasticsearch Service\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWe \u003ca href=\"https://www.elastic.co/blog/elastic-and-google-team-up-to-bring-a-more-native-elasticsearch-service-experience-on-google-cloud\"\u003epartner with Google\u003c/a\u003e to bring the Elasticsearch Service to GCP. Elastic will continue to introduce new GCP regions for the Elasticsearch Service to complement our joint engineering work on native GCP console integration.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eElastic and GCP customers can also subscribe to the Elasticsearch Service via the \u003ca href=\"https://console.cloud.google.com/marketplace/details/endpoints/elasticsearch-service.gcpmarketplace.elastic.co\"\u003eGCP Marketplace\u003c/a\u003e. If you're a marketplace customer, integrated billing consolidates usage charges into your existing GCP bill. These charges are deductible from prepaid GCP agreements.\u0026nbsp;\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eGet started with the Elasticsearch Service in GCP Singapore\u003c/h2\u003e\u003cp dir=\"ltr\"\u003eIf you are looking to move an existing cluster or deployment, be sure to check out our documentation about \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-migrate-data.html\"\u003emigrating your Elasticsearch data\u003c/a\u003e, with more details in our \u003ca href=\"https://www.elastic.co/webinars/migrating-your-elasticsearch-data-to-elastic-cloud\"\u003emigrating Elasticsearch data webinar\u003c/a\u003e. If you still have questions, \u003ca href=\"https://www.elastic.co/contact\"\u003ewe're here to help\u003c/a\u003e.\u003c/p\u003e\u003cdiv\u003e\u003cbr /\u003e\u003c/div\u003e","category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2020-03-17T21:04:39.826Z","created_by":"blt09675795f3a8cdd57c4f255b","disclaimer":[],"full_bleed_image":{"uid":"blt940496fcf44f1298","created_by":"blt09675795f3a8cdd57c4f255b","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-03-17T21:43:08.357Z","updated_at":"2021-01-12T21:14:14.424Z","content_type":"image/png","file_size":"42527","filename":"blog-banner-cloud-gcp-region.png","title":"blog-banner-cloud-gcp-region.png","ACL":{},"_version":4,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-12T21:14:16.512Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt940496fcf44f1298/5ffe1126fee93e550328c4ab/blog-banner-cloud-gcp-region.png"},"markdown_l10n":"","publish_date":"2020-03-18T21:04:08.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch Service is now available on Google Cloud Platform (GCP) in Singapore","seo_description_l10n":"The new Singapore region for Elasticsearch Service is our 4th GCP region in Asia Pacific and our 12th GCP region globally.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":5,"is_dir":false,"uid":"blt83d6e1208fcdaef9","ACL":{},"content_type":"image/png","created_at":"2020-03-17T21:42:17.536Z","created_by":"blt09675795f3a8cdd57c4f255b","description":"","file_size":"36615","filename":"blog-thumb-cloud-gcp-region.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-gcp-region.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.418Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt83d6e1208fcdaef9/5ffe112b7f3df4662710b33e/blog-thumb-cloud-gcp-region.png"},"title":"Elasticsearch Service is now available on Google Cloud Platform (GCP) in Singapore","title_l10n":"Elasticsearch Service is now available on Google Cloud Platform (GCP) in Singapore","updated_at":"2025-03-10T10:40:20.255Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elasticsearch-service-is-now-available-on-google-cloud-platform-gcp-in-singapore","publish_details":{"time":"2025-03-10T10:40:24.074Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta29d3aee29c50bfa","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blte305d0d8f427e122"],"body_l10n":"\u003cp\u003eElasticsearch supports a wide range of use-cases across our user base, and more and more of these rely on fast indexing to quickly get large amounts of data into Elasticsearch. Even though Elasticsearch is fast and index performance is continually improved, it is still possible to overwhelm it. At that point you typically see parts of bulk requests getting rejected. In this blog post we will look at the causes and how to avoid it.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThis is the second installment in a series of blog posts where we look at and discuss your common questions. The first installment discussed and provided guidelines around \"\u003ca href=\"/blog/how-many-shards-should-i-have-in-my-elasticsearch-cluster\"\u003eHow many shards one should aim to have in an Elasticsearch cluster?\u003c/a\u003e\"\u003c/p\u003e\u003ch2\u003eWhat happens when a bulk indexing request is sent to Elasticsearch?\u003c/h2\u003e\u003cp\u003eLet’s start at the beginning and look at what happens behind the scenes when a bulk indexing request is sent to Elasticsearch.\u003c/p\u003e\u003cp\u003eWhen a bulk request arrives at a node in the cluster, it is, in its entirety, put on the bulk queue and processed by the threads in the bulk thread pool. The node that receives the request is referred to as the coordinating node as it manages the life of the request and assembles the response. This can be a node dedicated to just coordinating requests or one of the data nodes in the cluster.\u003c/p\u003e\u003cp\u003eA bulk request can contain documents destined for multiple indices and shards. The first processing step is therefore to split it up based on which shards the documents need to be routed to. Once this is done, each bulk sub-request is forwarded to the data node that holds the corresponding primary shard, and it is there enqueued on that node’s bulk queue. If there is no more space available on the queue, the coordinating node will be notified that the bulk sub-request has been rejected.\u003c/p\u003e\u003cp\u003eThe bulk thread pool processes requests from the queue and documents are forwarded to replica shards as part of this processing. Once the sub-request has completed, a response is sent to the coordinating node.\u003c/p\u003e\u003cp\u003eOnce all sub-requests have completed or been rejected, a response is created and returned to the client. It is possible, and even likely, that only a portion of the documents within a bulk request might have been rejected.\u003c/p\u003e\u003cp\u003eThe reason Elasticsearch is designed with request queues of limited size is to protect the cluster from being overloaded, which increases stability and reliability. If there were no limits in place, clients could very easily bring a whole cluster down through bad or malicious behaviour. The limits that are in place have been set based on our extensive experience supporting Elasticsearch for different types of use-cases.\u003c/p\u003e\u003cp\u003eWhen using the HTTP interface, requests that results in at least a partial rejection will return with response code 429, 'Too many requests'. The principle also applies when the transport protocol is used, although the protocol and interface naturally is different. Applications and clients may report these errors back to the user in different ways, and some may even attempt to handle this automatically by retrying any rejected documents.\u003c/p\u003e\u003ch2\u003eHow can we test this in practice?\u003c/h2\u003e\u003cp\u003eIn order to illustrate the practical impact of this behaviour, we devised a simple test where we use \u003ca href=\"https://github.com/elastic/rally\"\u003eour benchmarking tool Rally\u003c/a\u003e to run bulk indexing requests against a couple of \u003ca href=\"/cloud\"\u003eElastic Cloud clusters\u003c/a\u003e with varying number of data nodes. Configuration and instructions on how to run Rally is available in \u003ca href=\"https://gist.github.com/cdahlqvist/2f368e8a874259b5cf4ca28b8a75d454\"\u003ethis gist\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eThe same indexing workload was run against three different Elastic Cloud clusters. We have been indexing with one replica shard configured wherever possible. The clusters consisted of one, two and three data nodes respectively, with each data node having 8GB RAM (4GB heap for Elasticsearch, 4GB native memory). Invoking the GET /_nodes/thread_pool API we could see that each data node by default had a fixed bulk thread pool size of two with a queue size of 200:\u003c/p\u003e\u003cpre\u003e%\u0026gt; curl -XGET http://\u0026lt;es_url\u0026gt;:\u0026lt;es_port\u0026gt;/_nodes/thread_pool\u0026lt;/es_port\u0026gt;\u0026lt;/es_url\u0026gt;\u003cbr /\u003e\"bulk\": {\u003cbr /\u003e\"type\": \"fixed\",\u003cbr /\u003e\"min\": 2,\u003cbr /\u003e\"max\": 2,\u003cbr /\u003e\"queue_size\": 200\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eDuring the test we indexed into a varying number of shards (2, 4, 8, 16, and 32) using a varying number of concurrent clients (8, 16, 24, 32, 48, and 64) for each cluster. For every combination of shard and client count we indexed 6.4 million documents with a batch size of 100 documents and another 6.4 million documents with a batch size of 200 documents. This means that in total we attempted to index 384 million documents per cluster.\u003c/p\u003e\u003cp\u003eFor this test we treat the clusters as a black box, and perform the analysis from the client’s perspective. To limit the scope we will also not look at the impact of various configurations on performance as that is a quite large topic on its own.\u003c/p\u003e\u003cp\u003eAll the generated, detailed metrics were sent to a separate Elastic Cloud instance for analysis using Kibana. For each request Rally measures how many the documents in the bulk request were rejected and successful. Based on this data we can classify each request as successful, partially rejected, and fully rejected. A few requests also timed out, and these have also been included for completeness.\u003c/p\u003e\u003cp\u003eUnlike Beats and Logstash, Rally does not retry failed indexing requests, so each has the same number of requests executed but the final number of documents indexed varied from run to run depending on the volume of rejections.\u003c/p\u003e\u003ch2\u003eHow bulk rejection frequency depend on shard count, clients count, and data node count?\u003c/h2\u003e\u003cp\u003eBulk rejections occur when the bulk queues fill up. The number of queue slots that get used depends both on the number of concurrent requests, and the number of shards being indexed into. To measure this correlation we have added a calculated metric, \u003cstrong\u003eclient shard concurrency\u003c/strong\u003e, to each run. This is defined as \u003cem\u003ethe number of shards being indexed into\u003c/em\u003e, multiplied by \u003cem\u003ethe number of concurrent indexing threads\u003c/em\u003e, and indicates how many queue slots would be needed to hold all bulk sub-requests.\u003c/p\u003e\u003cp\u003eIn the graph below, we show how the percentage of requests that result in partial or full rejections, depends on the client shard concurrency for the three different clusters.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3cfc31f3fdd1b884/5e613b0b18d3347ceffbbb41/bulk-rejection-blog-1.png\" data-sys-asset-uid=\"blt3cfc31f3fdd1b884\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cdiv\u003e\u003cp\u003eFor clusters with one or two nodes we can see that appearance of bulk rejections start when the client shard concurrency level is somewhere between 192 and 256. This makes sense as each node has a bulk queue size of 200. For the cluster with 3 nodes we can see that it is able to handle even higher level of client shard concurrency without any bulk rejections appearing.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOnce we get over this limit, we start seeing partial bulk rejections, where at least one sub-request has managed to get queued and processed. A relatively small portion of requests also result on full rejections as the concurrency level increases, especially for the single node cluster.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWhen we compare the single and two node clusters, we can see that the percentage of fully successful requests increases slightly and that there are fewer full rejections. This is expected, as the total bulk queue across the cluster is twice as large and requests are sent to all data nodes. Even though the total bulk queue size is twice as large across the cluster, the 2 node cluster does not appear able to handle twice the client shard concurrency of the single node cluster. This is likely due to the fact that distribution is not perfect and that the introduction of replica shards have resulted in each indexing operation requiring more work and being slower as a result. An important thing to note is also that all partial rejections are treated as equals in this graph. The number of rejected documents is not shown and does indeed vary depending on the cluster size, but we will shortly look at that in greater detail.\u0026nbsp;\u003c/p\u003e\u003cp\u003eWhen we go to three data nodes, we see a more marked improvement, and receive requests without any rejections at high levels of concurrency. We also only see full rejections for the highest concurrency levels.\u003c/p\u003e\u003cp\u003eIf we instead plot the average portion of rejected documents per request as a function of shard and client count for the three clusters, we get the following graphs.\u003c/p\u003e\u003cp\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf49d04d4bd8150d/5e613aed18d3347ceffbbb3b/bulk-rejection-blog-2.png\" data-sys-asset-uid=\"bltbf49d04d4bd8150d\" style=\"display: block;margin: auto;\"/\u003e\u003c/p\u003e\u003cdiv\u003e\u003c/div\u003e\u003cp\u003eHere we can see that the percentage of rejected events grows with increased concurrency levels for all cluster sizes. We can also see that the rejection levels drop across the board with the more data nodes we add, which is expected.\u003c/p\u003e\u003cp\u003eEarlier we saw that partial rejections started at approximately the same time for both one and two node clusters. If we now look at these graphs, we can see that the portion of rejected documents grows faster for the single node cluster compared to the one with two data nodes. This means that even though we saw a similar level of partially rejected requests, the larger cluster had more documents indexed per request.\u003c/p\u003e\u003ch2\u003eCan’t I just get around this by increasing the bulk queue size?\u003c/h2\u003e\u003cp\u003eOne of the most common reactions when faced with bulk rejections is to increase the size of the bulk queue. Why not set it to a really large value so you do not have to worry about this again?\u003c/p\u003e\u003cp\u003eIncreasing the size of the queue is not likely to improve the indexing performance or throughput of your cluster. Instead it would just make the cluster queue up more data in memory, which is likely to result in bulk requests taking longer to complete. The more bulk requests there are in the queue, the more precious heap space will be consumed. If the pressure on the heap gets too large, it can cause a lot of other performance problems and even cluster instability.\u003c/p\u003e\u003cp\u003eAdjusting the queue sizes is therefore strongly discouraged, as it is like putting a temporary band-aid on the problem rather than actually fixing the underlying issue. So what else can we do improve the situation?\u003c/p\u003e\u003ch2\u003eCan coordinating only nodes help?\u003c/h2\u003e\u003cp\u003eBy introducing coordinating only nodes, the data nodes will be able to focus on processing sub-requests, as the request itself will not take up a slot on their bulk queue. This is generally good, but the actual benefit of this arrangement is likely to vary from use-case to use-case. In many use cases it does relatively little difference, and we see lots of successful indexing heavy use cases that do not use dedicated coordinating nodes.\u003c/p\u003e\u003ch2\u003eWhat conclusions can we draw?\u003c/h2\u003e\u003cp\u003eAs always, there is not necessarily any good one-size-fits-all solution, and the way to address bulk rejections will vary from use-case to use-case. If you see bulk rejections, try to understand why they are taking place and whether it is a single node or the whole cluster that is affected.\u003c/p\u003e\u003cp\u003eIf the cluster is unable to cope with the load, ensure that all nodes are sharing the load evenly. If this does not help, it may be necessary to scale the cluster out or up. This will increase capacity and make it less likely that queues are filled up. Increasing the bulk queue size is only likely to postpone the problems, and may actually make them worse.\u003c/p\u003e\u003cp\u003eAlso remember that rejected requests do not always mean that all documents were unsuccessful. Make sure you inspect the full response and retry the appropriate documents. Logstash and Beats already do this by default.\u003c/p\u003e\u003cp\u003eWe hope this has given you a better understand of how it works. If you have any further questions, there are \u003ca href=\"/community\"\u003emany ways to engage with us\u003c/a\u003e, including through \u003ca href=\"https://discuss.elastic.co/\"\u003eour forum\u003c/a\u003e.\u003c/p\u003e\u003c/div\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T10:05:32.006Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"title":"elasticsearch-cluster-bulk-rejections-fullbleed.jpg","uid":"blt418d869df45a88bb","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:29:36.877Z","updated_at":"2019-01-05T09:29:36.877Z","content_type":"image/jpeg","file_size":"145061","filename":"elasticsearch-cluster-bulk-rejections-fullbleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T19:54:39.309Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt418d869df45a88bb/5c3079006e9992e16f529a4f/elasticsearch-cluster-bulk-rejections-fullbleed.jpg"},"markdown_l10n":"","publish_date":"2017-11-22T17:13:16.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"title":"elasticsearch-cluster-bulk-rejections-thumbnail.jpg","uid":"blt44b8ccc839f287db","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T09:29:32.644Z","updated_at":"2019-01-05T09:29:32.644Z","content_type":"image/jpeg","file_size":"63921","filename":"elasticsearch-cluster-bulk-rejections-thumbnail.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-02T19:54:39.309Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt44b8ccc839f287db/5c3078fcb2b2be79676e84cc/elasticsearch-cluster-bulk-rejections-thumbnail.jpg"},"title":"Why am I seeing bulk rejections in my Elasticsearch cluster?","title_l10n":"Why am I seeing bulk rejections in my Elasticsearch cluster?","updated_at":"2025-03-10T10:39:05.401Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/why-am-i-seeing-bulk-rejections-in-my-elasticsearch-cluster","publish_details":{"time":"2025-03-10T10:39:10.554Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte6fa4df46b3ae6b5","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt34ee8792416ba5d6"],"body_l10n":"\u003ch2\u003eWe are hiring\u003c/h2\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://grnh.se/62cf75441\"\u003eKibana - Senior Product Designer\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://grnh.se/24ddf24d1\"\u003eKibana - Senior JavaScript Engineer\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://grnh.se/a12f57d31\"\u003eKibana - Platform JavaScript Engineer (Node.js)\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://grnh.se/cf4410401\"\u003eKibana - Principal Product Manager Maps\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://grnh.se/aef19e931\"\u003eKibana - Senior/Principal Product Manager Analytics\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003ePlatform\u003c/h2\u003e\u003ch3\u003eChanges for developers:\u003c/h3\u003e\u003cul\u003e\u003cli\u003eA new \u003ca href=\"https://github.com/elastic/kibana/pull/56636\"\u003e\u003cspan style=\"font-family: monospace;\"\u003egetServerInfo()\u003c/span\u003e API\u003c/a\u003e is available for plugins that need to know Kibana’s public URL.\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eApp Architecture\u003c/h2\u003e\u003ch3\u003eSearch bar default behaviors\u003c/h3\u003e\u003cp\u003eUsing \u003cspan style=\"font-family: monospace;\"\u003eSearchBar\u003c/span\u003e or \u003cspan style=\"font-family: monospace;\"\u003eTopNavMenu\u003c/span\u003e? We got some news for you!\u003c/p\u003e\u003cp\u003eBoth components now ship with \u003ca href=\"https://github.com/elastic/kibana/pull/56160\"\u003epre-wired default behaviors\u003c/a\u003e, so you don't have to write any additional code to utilize filter and query state management, auto refresh settings or saved query workflow.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eTo enable, pass in \u003cspan style=\"font-family: monospace;\"\u003euseDefaultBehavious=\"true\"\u003c/span\u003e to the component, as well as an (optional) initial state, remove your own management code and you should be good to go.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eTo get notifications on state changes (for example to sync with a state container), you still have to use a combination of observables and callbacks, as \u003ca href=\"https://github.com/elastic/kibana/pull/56160/files#diff-945c21bd7ac7af10525d33c7e544c4c2R581\"\u003eseen here\u003c/a\u003e. Update for that is \u003ca href=\"https://github.com/elastic/kibana/issues/57168\"\u003ecoming soon\u003c/a\u003e.\u003c/p\u003e\u003ch3\u003ePlugin Generator\u003c/h3\u003e\u003cp\u003eIf you wish to generate a new Kibana Platform plugin, check out the \u003ca href=\"https://github.com/elastic/kibana/pull/55281\"\u003eupdated Plugin Generator tool\u003c/a\u003e. It is now up to date with the most recent plugin structure and guidelines.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-family: monospace;\"\u003enode scripts/generate_plugin \"My Plugin\" -i\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003ePlease post feedback and suggestions on the outstanding \u003ca href=\"https://github.com/elastic/kibana/issues/56652\"\u003eimprovements issue\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e","category":[],"created_at":"2020-02-11T19:07:28.952Z","created_by":"bltc9d62ae104284d62","disclaimer":[],"full_bleed_image":{"uid":"blt0ba64554b53df4df","ACL":{},"_version":1,"content_type":"image/png","created_at":"2019-10-18T22:04:10.512Z","created_by":"bltf6ab93733e4e3a73","file_size":"27476","filename":"kibana-weekly-blog-banner.png","is_dir":false,"parent_uid":null,"tags":[],"title":"kibana-weekly-blog-banner.png","updated_at":"2019-10-18T22:04:10.512Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-18T22:04:17.945Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ba64554b53df4df/5daa36dadf78486c826db921/kibana-weekly-blog-banner.png"},"markdown_l10n":"","publish_date":"2020-02-11T21:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"kibana weekly update contains platform migration, and maps feature enhancements","seo_description_l10n":"In this week's Kibana Engineer update we look at the update to Maps icon styling features and some platform updates","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blta6ce6c7fc47ff2cb","ACL":{},"_version":1,"content_type":"image/png","created_at":"2019-10-18T22:04:10.428Z","created_by":"bltf6ab93733e4e3a73","file_size":"22849","filename":"kibana-weekly-blog-thumb.png","is_dir":false,"parent_uid":null,"tags":[],"title":"kibana-weekly-blog-thumb.png","updated_at":"2019-10-18T22:04:10.428Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-10-18T22:04:32.538Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta6ce6c7fc47ff2cb/5daa36da2dc72966da7451aa/kibana-weekly-blog-thumb.png"},"title":"Keeping up with Kibana: This week in Kibana for February 11th, 2020","title_l10n":"Keeping up with Kibana: This week in Kibana for February 11th, 2020","updated_at":"2025-03-10T10:37:58.311Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/keeping-up-with-kibana-2020-02-11","publish_details":{"time":"2025-03-10T10:38:01.571Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf8998749005e56e3","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt4f911b4247a9427a"],"body_l10n":"\u003cp\u003eLast week, \u003ca href=\"https://www.elastic.co/blog/staying-in-control-with-moving-averages-part-1\"\u003ewe introduced how to build a simple Control Chart\u003c/a\u003e using the new moving_avg pipeline aggregations. \u0026nbsp;The demonstration used a very simple dataset, where the trend was very flat, and the spike was very obvious. \u0026nbsp;In fact, it was so obvious you could probably catch it with a simple threshold.\u003c/p\u003e\u003cp\u003eThis week, we'll show how the same control chart can be used in more tricky scenarios, such as constantly increasing linear trends, or cyclic/seasonal data\u003c/p\u003e\u003ch2 dir=\"ltr\" rel=\"line-height:1.38;margin-top:10pt;margin-bottom:0pt;\"\u003eLinear Trends\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe example from last week was very simple, and a threshold set by eye would have been sufficient. \u0026nbsp;For example, you could easily determine the ideal mean, calculate three standard deviations yourself, and alert when it goes above that point. \u0026nbsp;This works well for flat trends, but what if your data happens to have a constant linear trend?\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eJust\u0026nbsp;as a refresher, here is the aggregation we built last week:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\" style=\"font-size: 12.6000003814697px;\"\u003e{\u003cbr /\u003e \"size\": 0,\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"date_histo\": {\u003cbr /\u003e \"histogram\": {\u003cbr /\u003e \"field\": \"tick\",\u003cbr /\u003e \"interval\": \"hour\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"stats\": {\u003cbr /\u003e \"extended_stats\": {\u003cbr /\u003e \"field\": \"value\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"movavg_mean\": {\u003cbr /\u003e \"moving_avg\": {\u003cbr /\u003e \"buckets_path\": \"stats.avg\",\u003cbr /\u003e \"window\": 24,\u003cbr /\u003e \"model\": \"ewma\",\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"alpha\": 0.1 \u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"movavg_std\": {\u003cbr /\u003e \"moving_avg\": {\u003cbr /\u003e \"buckets_path\": \"stats.std_deviation\",\u003cbr /\u003e \"window\": 24,\u003cbr /\u003e \"model\": \"ewma\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"shewhart_ucl\": {\u003cbr /\u003e \"bucket_script\": {\u003cbr /\u003e \"buckets_path\": {\u003cbr /\u003e \"mean\": \"movavg_mean.value\",\u003cbr /\u003e \"std\": \"movavg_std.value\"\u003cbr /\u003e },\u003cbr /\u003e \"script\": \"mean + (3 * std)\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eLet's re-use that same aggregation on some data with a constant linear trend, which includes the same spike on Thursday. \u0026nbsp;Without changing anything, we'll see:\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003ca href=\"https://api.contentstack.io/v2/assets/575e4c9c3dc542cb38c084f9/download?uid=blt1e5f788806ad9d40?uid=blt1e5f788806ad9d40\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c9c3dc542cb38c084f9/download?uid=blt1e5f788806ad9d40?uid=blt1e5f788806ad9d40\" data-sys-asset-uid=\"blt59216816fa960ad9\" width=\"689\" height=\"149\" style=\"width: 689;height: 149;\"/\u003e\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eSmoothed average: purple\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eMax value: yellow\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eUpper control limit: green\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAs you can see, a\u0026nbsp;simple threshold would no longer work; it would be triggered due to the natural growth of the values. \u0026nbsp;There are several ways you could work around it (plot a linear threshold trigger, diff against yesterday, etc). \u0026nbsp;But the control chart handles this scenario in stride without modification\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBecause the threshold is generated dynamically based on the \"local\" data in the moving averages, the constant linear trend is no problem and everything just works.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eCyclic Trends\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eCyclic trends are even more fun. \u0026nbsp;Imagine your data has some seasonality. \u0026nbsp;In this case, I just plotted a random sine wave, but you'll see this cyclic behavior everywhere in real data: \u0026nbsp;sales numbers, server utilization, queue lengths, etc. \u0026nbsp;Cycles can be very tricky for simpler spike detection algorithms. \u0026nbsp;The algorithm needs to differentiate between the natural peaks and real spikes.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIf we apply the exact same aggregation as before, we get a decent chart:\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://api.contentstack.io/v2/assets/575e4c9cd8edd48f7693603f/download?uid=blte63ebbbcb7a64d8e?uid=blte63ebbbcb7a64d8e\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c9cd8edd48f7693603f/download?uid=blte63ebbbcb7a64d8e?uid=blte63ebbbcb7a64d8e\" data-sys-asset-uid=\"bltdd73a9e465e66522\" width=\"696\" height=\"150\" style=\"width: 696;height: 150;\"/\u003e\u003c/a\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cem\u003eSmoothed average: purple\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eMax value: yellow\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eUpper control limit: green\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eYou'll notice a problem though. \u0026nbsp;The maximum values in yellow consistently \"trip\" the threshold (in green) on the leading edge. \u0026nbsp;It looks like the green threshold lags behind the data, and never quite anticipates the upcoming cycle. \u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe problem is the moving average model. \u0026nbsp;Simpler models like linear and ewma always display a certain amount of lag, and in particular struggle with cyclic data. \u0026nbsp;The lag was present in all the previous examples (go look), it just usually isn’t a problem with non-seasonal data.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eInstead, we should use holt_winters, a moving average model that includes terms that can account for seasonality. \u0026nbsp;Let's replace the two previous moving averages with this:\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e\"movavg_mean\": {\u003cbr /\u003e \"moving_avg\": {\u003cbr /\u003e \"buckets_path\": \"stats.avg\",\u003cbr /\u003e \"window\": 200,\u003cbr /\u003e \"model\": \"holt_winters\",\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"period\": 69\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e},\u003cbr /\u003e\"movavg_std\": {\u003cbr /\u003e \"moving_avg\": {\u003cbr /\u003e \"buckets_path\": \"stats.std_deviation\",\u003cbr /\u003e \"window\": 150,\u003cbr /\u003e \"model\": \"holt_winters\",\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"period\": 69\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e},\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eYou'll notice a few changes. \u0026nbsp;Obviously, we swapped ewma for holt_winters. \u0026nbsp;Next, we changed the window size. \u0026nbsp;Holt-Winters requires a larger window so that it can more accurately model seasonal behavior. \u0026nbsp;Finally, we specified how large the \"period\" of the data is. \u0026nbsp;In this case, it is roughly 62 hours from peak to peak. \u0026nbsp;Holt-Winters has more parameters that are tunable, but we are going to rely on the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/master/search-aggregations-pipeline-movavg-aggregation.html#movavg-minimizer\"\u003eautomatic minimization\u003c/a\u003e to choose those for us.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe graph that we get out looks much better:\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://api.contentstack.io/v2/assets/575e4c9cd8edd48f7693603a/download?uid=blt0c6c71d33f680ac4?uid=blt0c6c71d33f680ac4\"\u003e\u003cimg src=\"https://api.contentstack.io/v2/assets/575e4c9cd8edd48f7693603a/download?uid=blt0c6c71d33f680ac4?uid=blt0c6c71d33f680ac4\" data-sys-asset-uid=\"bltc28ae47c3a2fd1f6\" width=\"724\" height=\"151\" style=\"width: 724;height: 151;\"/\u003e\u003c/a\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cem\u003eSmoothed average: purple\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eMax value: yellow\u003c/em\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cem\u003eUpper control limit: green\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThe threshold now lines up with the data perfectly, and we correctly detect the spike (and nothing else). \u0026nbsp;You will notice a new anomaly though. \u0026nbsp;Exactly one period after the first spike a new spike exists where there wasn’t one previously. \u0026nbsp;And if you look closely, you'll see a tiny spike two periods afterwards which is also new.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThis is an artifact from Holt-Winters. \u0026nbsp;Forecasts are built based on past seasonal data, and since the past data\u0026nbsp;had a spike, you'll see traces of that in future forecasts. \u0026nbsp;This artifact can be diminished slightly by increasing the window length, and in general isn't usually large enough to trigger a \"threshold breach\".\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eExtra Credit: Configuring a Watcher alert\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIf you have Watcher installed -- \u003ca href=\"/what-is/elasticsearch-alerting\"\u003ean alerting and notification plugin for Elasticsearch\u003c/a\u003e -- it is trivial to add a watch which will alert you when a spike has been detected. \u0026nbsp;We will define a watch that checks every hour (finer granularity is unnecessary, since the data is only logged at 1hr intervals). \u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThen we plop in our aggregation, and setup some email and logging notifications and define the condition. \u0026nbsp;The condition is simply checking to see if the maximum value is greater than the upper control limit.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ecurl -XPUT 'http://localhost:9200/_watcher/watch/log_error_watch' -d '{\u003cbr /\u003e \"trigger\": {\u003cbr /\u003e \"schedule\": {\u003cbr /\u003e \"interval\": \"1hr\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"input\": {\u003cbr /\u003e \"search\": {\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"indices\": [\"reactor_logs\"],\u003cbr /\u003e \"body\": {\u003cbr /\u003e \"size\": 0,\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"histo\": {\u003cbr /\u003e \"date_histogram\": {\u003cbr /\u003e \"field\": \"tick\",\u003cbr /\u003e \"interval\": \"hour\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"stats\": {\u003cbr /\u003e \"extended_stats\": {\u003cbr /\u003e \"field\": \"value\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"movavg_mean\": {\u003cbr /\u003e \"moving_avg\": {\u003cbr /\u003e \"buckets_path\": \"stats.avg\",\u003cbr /\u003e \"window\": 24,\u003cbr /\u003e \"model\": \"ewma\",\u003cbr /\u003e \"settings\": {\u003cbr /\u003e \"alpha\": 0.1\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"movavg_std\": {\u003cbr /\u003e \"moving_avg\": {\u003cbr /\u003e \"buckets_path\": \"stats.std_deviation\",\u003cbr /\u003e \"window\": 24,\u003cbr /\u003e \"model\": \"ewma\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"shewhart_ucl\": {\u003cbr /\u003e \"bucket_script\": {\u003cbr /\u003e \"buckets_path\": {\u003cbr /\u003e \"mean\": \"movavg_mean.value\",\u003cbr /\u003e \"std\": \"movavg_std.value\"\u003cbr /\u003e },\u003cbr /\u003e \"script\": \"mean + (3 * std)\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"condition\": {\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"inline\": \"def lastBucket = ctx.payload.aggregations.histo.buckets.last(); return lastBucket.stats.max \u0026gt; lastBucket.shewhart_ucl.value\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"actions\": {\u003cbr /\u003e \"log_error\": {\u003cbr /\u003e \"logging\": {\u003cbr /\u003e \"text\": \"Reactor Meltdown!\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"send_email\": { \u003cbr /\u003e \"email\": {\u003cbr /\u003e \"to\": \"user@example.com\", \u003cbr /\u003e \"subject\": \"Watcher Notification - Reactor Meltdown!\",\u003cbr /\u003e \"body\": \"Reactor is melting down, please investigate. :)\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}'\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWith this in place, Watcher will email you as soon as the upper control limit has been reached. \u0026nbsp;It is fairly trivial to extend this to log/alert on “warnings”, such as when values exceed two standard deviations instead of three, or has remained above the mean for more than 10 consecutive hours. \u0026nbsp;The sky is the limit!\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\"\u003eConclusion\u003c/h2\u003e\u003cp\u003eI hope this article was interesting. \u0026nbsp;Most folks are acquainted with the smoothing capabilities of moving averages;\u0026nbsp; they are great for smoothing out noise so you can see the more general trend. \u0026nbsp;But they can also be the building blocks for much richer functionality, such as finding anomalous data points in a dynamic dataset. \u0026nbsp;It's fairly remarkable how powerful simple, statistical techniques can be in practice.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBecause of the new functionality in pipeline aggregations, all of this functionality can now be expressed in Elasticsearch itself. \u0026nbsp;And when coupled with Watcher, you can build robust alerting and notifications directly from your data, without having to pipe it to an external system first.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIn the future, we'll be looking at how you can forecast into the future with moving averages, other methods for anomaly detection and more. \u0026nbsp;Stay tuned!\u003c/p\u003e\u003cdiv\u003e\u003cbr /\u003e\u003c/div\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T12:48:47.627Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"bltc1071980bd992b5e","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:05:36.712Z","updated_at":"2018-10-09T10:05:36.712Z","content_type":"image/jpeg","file_size":"75535","filename":"staying-in-control-with-moving-averages-full-bleed.jpg","title":"staying-in-control-with-moving-averages-full-bleed.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T03:09:49.300Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1071980bd992b5e/5bbc7d706c9763b95d07a74e/staying-in-control-with-moving-averages-full-bleed.jpg"},"markdown_l10n":"","publish_date":"2015-08-12T14:37:11.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":null,"title":"Staying in Control with Moving Averages - Part 2","title_l10n":"Staying in Control with Moving Averages - Part 2","updated_at":"2025-03-10T10:35:51.491Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/staying-in-control-with-moving-averages-part-2","publish_details":{"time":"2025-03-10T10:35:54.946Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0184c325196e29b4","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"","author":["blt4f911b4247a9427a"],"body_l10n":"\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWelcome to the third and final installment of this series on building a statistical anomaly detector in Elasticsearch. \u0026nbsp;As a quick recap, let’s look at what we’ve built so far:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eIn Part 1, we \u003ca href=\"https://www.elastic.co/blog/implementing-a-statistical-anomaly-detector-part-1\"\u003econstructed a pipeline aggregation that crunched millions of data points\u003c/a\u003e to generate\u0026nbsp;the top 90th percentile of\u0026nbsp;\"surprise\" values. \u0026nbsp;It did this by\u0026nbsp;constructing a time-series per\u0026nbsp;(metric, query) tuple, calculating the surprise of that tuple, then finding the top 90th percentile of surprise for each metric.\u003c/li\u003e\u003cli dir=\"ltr\"\u003eIn Part 2, we \u003ca href=\"https://www.elastic.co/blog/implementing-a-statistical-anomaly-detector-part-2\"\u003eused Timelion to graph the 90th percentile surprise over time\u003c/a\u003e. \u0026nbsp;We then used Timelion’s flexible syntax to construct a dynamic threshold\u0026nbsp;three standard deviations above the moving average of the surprise. \u0026nbsp;When the surprise passed this threshold, we showed it on the chart with a bar\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eToday, we’ll take what we built in Part 1 and 2 and automate it completely using\u0026nbsp;\u003ca href=\"https://www.elastic.co/what-is/elasticsearch-alerting\"\u003eWatcher\u003c/a\u003e, Elastic’s real-time alerting and notification plugin for Elasticsearch.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWith Watcher’s ability to use mustache templating and groovy scripting, it is a remarkably powerful alerting engine. \u0026nbsp;We can encode the entire Atlas system in just two watches. \u0026nbsp;The first watch will generate all of the surprise data (just like Part 1) while the second watch will create the threshold and check for anomalies (like Timelion in Part 2).\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eLet’s get started!\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eData Collection Watch\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe first watch’s job is to collect the top 90th surprise values for each metric on an hourly basis, emulating the data collection process we built in Part 1. \u0026nbsp;This means we can leverage most of the hard work from that section (e.g. the pipeline aggregation).\u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eFirst, here is the entire watch (then we’ll break it down piece-by-piece):\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT _watcher/watch/atlas\u003cbr /\u003e{\u003cbr /\u003e \"trigger\":{\u003cbr /\u003e \"schedule\":{\u003cbr /\u003e \"hourly\" : { \"minute\" : 0 }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"input\":{\u003cbr /\u003e \"search\":{\u003cbr /\u003e \"request\":{\u003cbr /\u003e \"indices\":\"data\",\u003cbr /\u003e \"types\": \"data\",\u003cbr /\u003e \"body\":{\u003cbr /\u003e \"query\":{\u003cbr /\u003e \"filtered\":{\u003cbr /\u003e \"filter\":{\u003cbr /\u003e \"range\":{\u003cbr /\u003e \"hour\":{\u003cbr /\u003e \"gte\":\"now-24h\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\":0,\u003cbr /\u003e \"aggs\":{\u003cbr /\u003e \"metrics\":{\u003cbr /\u003e \"terms\":{\u003cbr /\u003e \"field\":\"metric\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\":{\u003cbr /\u003e \"queries\":{\u003cbr /\u003e \"terms\":{\u003cbr /\u003e \"field\":\"query\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\":{\u003cbr /\u003e \"series\":{\u003cbr /\u003e \"date_histogram\":{\u003cbr /\u003e \"field\":\"hour\",\u003cbr /\u003e \"interval\":\"hour\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\":{\u003cbr /\u003e \"avg\":{\u003cbr /\u003e \"avg\":{\u003cbr /\u003e \"field\":\"value\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"movavg\":{\u003cbr /\u003e \"moving_avg\":{\u003cbr /\u003e \"buckets_path\":\"avg\",\u003cbr /\u003e \"window\":24,\u003cbr /\u003e \"model\":\"simple\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"surprise\":{\u003cbr /\u003e \"bucket_script\":{\u003cbr /\u003e \"buckets_path\":{\u003cbr /\u003e \"avg\":\"avg\",\u003cbr /\u003e \"movavg\":\"movavg\"\u003cbr /\u003e },\u003cbr /\u003e \"script\":\"(avg - movavg).abs()\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"largest_surprise\":{\u003cbr /\u003e \"max_bucket\":{\u003cbr /\u003e \"buckets_path\":\"series.surprise\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"ninetieth_surprise\":{\u003cbr /\u003e \"percentiles_bucket\":{\u003cbr /\u003e \"buckets_path\":\"queries\u0026gt;largest_surprise\",\u003cbr /\u003e \"percents\":[\u003cbr /\u003e 90.0\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"extract\":[\u003cbr /\u003e \"aggregations.metrics.buckets.ninetieth_surprise\",\u003cbr /\u003e \"aggregations.metrics.buckets.key\"\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"actions\":{\u003cbr /\u003e \"index_payload\":{\u003cbr /\u003e \"transform\":{\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"file\": \"hourly\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"index\" : \"atlas\",\u003cbr /\u003e \"doc_type\" : \"data\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eIt’s long, but don’t panic! \u0026nbsp;A lot of it is repeated code from Part 1. \u0026nbsp;Let’s start looking at the individual components:\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT _watcher/watch/atlas\u003cbr /\u003e{\u003cbr /\u003e \"trigger\":{\u003cbr /\u003e \"schedule\":{\u003cbr /\u003e \"hourly\" : { \"minute\" : 0 }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe first thing in our request is the HTTP command. \u0026nbsp;Watches are stored inside your cluster, so we execute a PUT command to the _watcher endpoint and add a new watch called “atlas”. \u0026nbsp;Next, we schedule the watch to run with a\u0026nbsp;“trigger”. \u0026nbsp;Triggers allow watches to run on schedules, much like a cronjob. \u0026nbsp;We are going to use an \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/trigger.html#schedule-hourly\"\u003ehourly trigger\u003c/a\u003e, which fires every hour\u0026nbsp;on the hour.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAfter our trigger, we define the \"input\" to the watch:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e \"input\":{\u003cbr /\u003e \"search\":{\u003cbr /\u003e \"request\":{\u003cbr /\u003e \"indices\":\"data\",\u003cbr /\u003e \"types\": \"data\",\u003cbr /\u003e \"body\":{...},\u003cbr /\u003e \"extract\":[\u003cbr /\u003e \"aggregations.metrics.buckets.ninetieth_surprise\",\u003cbr /\u003e \"aggregations.metrics.buckets.key\"\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eInputs provide the data that a watch uses to make decisions. \u0026nbsp;There are a variety of inputs available, \u0026nbsp;but we’ll use a search input. \u0026nbsp;This input\u0026nbsp;executes an arbitrary Elasticsearch query and allows a watch to use the response for later processing. \u0026nbsp;The “request” parameter defines the details about the request: the indices/types to query and the request body (which is the pipeline aggregation we built in Part 1). \u0026nbsp;Combined with the trigger, our watch will execute the large pipeline agg against the raw data every hour.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe “extract” parameter lets us extract\u0026nbsp;details that we are interested in, to simplify further processing in the watch. \u0026nbsp;It is conceptually very similar to filter_path, merely a filtering mechanism to reduce response verbosity. \u0026nbsp;Here we are using it to extract the five top-90th percentile surprises and their keys.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eFinally we define an \"action\":\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e \"actions\":{\u003cbr /\u003e \"index_payload\":{\u003cbr /\u003e \"transform\":{\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"file\": \"hourly\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"index\" : {\u003cbr /\u003e \"index\" : \"atlas\",\u003cbr /\u003e \"doc_type\" : \"data\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe action is executed after the query has run, and defines the \"output\" of a watch. \u0026nbsp;\u003ca href=\"https://www.elastic.co/guide/en/watcher/current/actions.html\"\u003eActions\u003c/a\u003e can send emails, send messages to Slack, post to custom webhooks, etc. \u0026nbsp;For our purposes, we actually want to put data back inside Elasticsearch. \u0026nbsp;We need to index the results of the pipeline aggregation so we can alert on it. \u0026nbsp;To do that, we setup an index_payload action which will index documents back into Elasticsearch for us.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBut before we can index anything, we need to convert the JSON aggregation response into a set of indexable\u0026nbsp;documents. \u0026nbsp;That is done via the transform\u0026nbsp;script hourly.groovy which resides on our node (in the config/scripts/ directory). \u0026nbsp;It looks like this:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003edef docs = [];\u003cbr /\u003efor(item in ctx.payload.aggregations.metrics.buckets) {\u003cbr /\u003e def doc = [\u003cbr /\u003e metric : item.key,\u003cbr /\u003e value : item.ninetieth_surprise.values[\"90.0\"],\u003cbr /\u003e execution_time: ctx.execution_time\u003cbr /\u003e ];\u003cbr /\u003e docs \u0026lt;\u0026lt; doc;\u003cbr /\u003e}\u003cbr /\u003ereturn [ _doc : docs ];\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIts function is very simple: iterate over the 90th percentile buckets and create an array holding the key, the value and the execution time. \u0026nbsp;Then append that to a bulk array and return it when done iterating over the buckets.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe returned array is in the Bulk API syntax, which Watcher will insert into the “atlas” index under the “data” type. \u0026nbsp;Once this watch is added to the cluster, Elasticsearch will begin collecting hourly surprise metrics just like we did in the simulator. \u0026nbsp;Perfect! \u0026nbsp;Let’s write the watch that finds anomalies now.\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eAnomaly Detection Watch\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe goal of this watch is to replicate what we did in Part 2 with Timelion. \u0026nbsp;Namely, it needs to construct a threshold that is three standard deviations above the moving average of the 90th surprise...per metric. \u0026nbsp;Then it needs to raise some kind of alert if that threshold is broken.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThis watch follows a similar layout as the last one, but has a bit more custom logic. \u0026nbsp;The whole watch looks like this:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003ePUT _watcher/watch/atlas_analytics\u003cbr /\u003e{\u003cbr /\u003e \"trigger\": {\u003cbr /\u003e \"schedule\": {\u003cbr /\u003e \"hourly\" : { \"minute\" : 5 }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"input\": {\u003cbr /\u003e \"search\": {\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"indices\": \"atlas\",\u003cbr /\u003e \"types\": \"data\",\u003cbr /\u003e \"body\": {\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"filtered\": {\u003cbr /\u003e \"filter\": {\u003cbr /\u003e \"range\": {\u003cbr /\u003e \"execution_time\": {\u003cbr /\u003e \"gte\": \"now-6h\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\": 0,\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"metrics\": {\u003cbr /\u003e \"terms\": {\u003cbr /\u003e \"field\": \"metric\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"series\": {\u003cbr /\u003e \"date_histogram\": {\u003cbr /\u003e \"field\": \"execution_time\",\u003cbr /\u003e \"interval\": \"hour\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"avg\": {\u003cbr /\u003e \"avg\": {\u003cbr /\u003e \"field\": \"value\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"series_stats\": {\u003cbr /\u003e \"extended_stats\": {\u003cbr /\u003e \"field\": \"value\",\u003cbr /\u003e \"sigma\": 3\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"extract\": [\u003cbr /\u003e \"aggregations.metrics.buckets\"\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"condition\": {\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"file\": \"analytics_condition\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"transform\": {\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"file\": \"analytics_transform\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"actions\": {\u003cbr /\u003e \"index_payload\": {\u003cbr /\u003e \"logging\": {\u003cbr /\u003e \"text\": \"{{ctx.alerts}}\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"email_alert\" : {\u003cbr /\u003e \"email\": {\u003cbr /\u003e \"to\": \"'John Doe \u0026lt;john.doe@example.com\u0026gt;'\",\u003cbr /\u003e \"subject\": \"Atlas Alerts Triggered!\",\u003cbr /\u003e \"body\": \"Metrics that appear anomalous: {{ctx.alerts}}\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp\u003eWe'll walk through it step-by-step again. \u0026nbsp;Similar to the first watch,\u0026nbsp;we PUT the watch into the cluster with a specific name (“atlas_analytics”) and setup an hourly schedule for it to run. However, the schedule is offset by five minutes this time to allow the first watch time to complete.\u003c/p\u003e\u003cp\u003eWe also use a search input again:\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e \"input\": {\u003cbr /\u003e \"search\": {\u003cbr /\u003e \"request\": {\u003cbr /\u003e \"indices\": \"atlas\",\u003cbr /\u003e \"types\": \"data\",\u003cbr /\u003e \"body\": {\u003cbr /\u003e \"query\": {\u003cbr /\u003e \"filtered\": {\u003cbr /\u003e \"filter\": {\u003cbr /\u003e \"range\": {\u003cbr /\u003e \"execution_time\": {\u003cbr /\u003e \"gte\": \"now-6h\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"size\": 0,\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"metrics\": {\u003cbr /\u003e \"terms\": {\u003cbr /\u003e \"field\": \"metric\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"series\": {\u003cbr /\u003e \"date_histogram\": {\u003cbr /\u003e \"field\": \"execution_time\",\u003cbr /\u003e \"interval\": \"hour\"\u003cbr /\u003e },\u003cbr /\u003e \"aggs\": {\u003cbr /\u003e \"avg\": {\u003cbr /\u003e \"avg\": {\u003cbr /\u003e \"field\": \"value\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"series_stats\": {\u003cbr /\u003e \"extended_stats\": {\u003cbr /\u003e \"field\": \"value\",\u003cbr /\u003e \"sigma\": 3\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"extract\": [\u003cbr /\u003e \"aggregations.metrics.buckets\"\u003cbr /\u003e ]\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThis search is a little different. \u0026nbsp;First, it is querying /atlas/data instead of /data/data;\u0026nbsp;this watch is aggregating the results of the previous watch instead of\u0026nbsp;the raw data. \u0026nbsp;The query is also filtering to\u0026nbsp;just the last\u0026nbsp;six hours which\u0026nbsp;allows us to scope the time frame to a specific window.\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAn\u0026nbsp;aggregation is used\u0026nbsp;to build a date_histogram per metric (e.g. a time-series per metric). \u0026nbsp;Inside each series we calculate the average and standard deviation (making sure to ask the stats agg for three standard deviations via the sigma parameter). \u0026nbsp;Finally, we extract out just the buckets because we don’t care about the rest of the response.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan\u003e\u003c/span\u003eYou’ll notice that in Part 2 we used a moving average and standard deviation to calculate this data, while here it is a plain average / stddev. \u0026nbsp;Why is that? \u0026nbsp;Because this watch executes every hour, the window of time will naturally slide across the data.\u0026nbsp;Unlike the Timelion implementation -- which had to display all points of time in one graph -- we are only concerned with generating the data points for this hour, so a simple avg works fine.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan\u003e\u003c/span\u003eSo at this point, our watch has all the required information to flag an anomaly...but we need to run some custom logic to tie it together. \u0026nbsp;That’s what happens next, in the condition clause:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e \"condition\": {\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"file\": \"analytics_condition\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eA condition is a \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/condition.html\"\u003egatekeeper to the action\u003c/a\u003e: if the condition evaluates true, the action is run. \u0026nbsp;Our condition uses another groovy script, analytics_condition.groovy:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003edef docs = [];\u003cbr /\u003edef status = false;\u003cbr /\u003efor(item in ctx.payload.aggregations.metrics.buckets) {\u003cbr /\u003e def std_upper = Double.valueOf(item.series_stats.std_deviation_bounds.upper);\u003cbr /\u003e def avg = Double.valueOf(item.series.buckets.last().avg.value);\u003cbr /\u003e if (std_upper == Double.NaN || avg == Double.NaN) {\u003cbr /\u003e continue;\u003cbr /\u003e }\u003cbr /\u003e if (avg \u0026gt; std_upper) {\u003cbr /\u003e status = true;\u003cbr /\u003e break;\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003ereturn status;\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThe script is really very simple: extract the standard deviation upper bound (which is provided by the aggregation natively) and the average, then see if the average is greater than the upper bound. \u0026nbsp;If the average is indeed greater, set a flag and return true\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAt this point, if the condition returned false is returned empty, the watch ends: nothing is anomalous. \u0026nbsp;But if it returns true, we continue onwards to the transform clause:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e \"transform\": {\u003cbr /\u003e \"script\": {\u003cbr /\u003e \"file\": \"analytics_transform\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eTransformations can be used to \u003ca href=\"https://www.elastic.co/guide/en/watcher/current/transform.html\"\u003emodify, enrich and manipulate data\u003c/a\u003e. \u0026nbsp;We’ll use the transformation to tidy up the data so that a list of alerts can be embedded in an email easily. \u0026nbsp;Again, we use a groovy script to do the transformation, this one called analytics_transform.groovy:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003edef alerts = [];\u003cbr /\u003efor(item in ctx.payload.aggregations.metrics.buckets) {\u003cbr /\u003e def std_upper = Double.valueOf(item.series_stats.std_deviation_bounds.upper);\u003cbr /\u003e def avg = Double.valueOf(item.series.buckets.last().avg.value);\u003cbr /\u003e if (Double.isNaN(std_upper) || Double.isNaN(avg)) {\u003cbr /\u003e continue;\u003cbr /\u003e }\u003cbr /\u003e if (avg \u0026gt; std_upper) {\u003cbr /\u003e alerts \u0026lt;\u0026lt; item.id;\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003ereturn [alerts: alerts];\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eLook familiar? \u0026nbsp;This is basically the same as the analytics_condition.groovy script used in the condition clause. \u0026nbsp;The only difference is that any anomalous metrics are appended to an array, instead of changing a flag. \u0026nbsp;The array is then returned, which we can use in our final email action:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cpre class=\"prettyprint\"\u003e \"actions\": {\u003cbr /\u003e \"index_payload\": {\u003cbr /\u003e \"logging\": {\u003cbr /\u003e \"text\": \"{{ctx.alerts}}\"\u003cbr /\u003e }\u003cbr /\u003e },\u003cbr /\u003e \"email_alert\" : {\u003cbr /\u003e \"email\": {\u003cbr /\u003e \"to\": \"'John Doe \u0026lt;john.doe@example.com\u0026gt;'\",\u003cbr /\u003e \"subject\": \"Atlas Alerts Triggered!\",\u003cbr /\u003e \"body\": \"Metrics that appear anomalous: {{ctx.alerts}}\"\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e }\u003cbr /\u003e}\u003cbr /\u003e\u003c/pre\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIn the last part of the watch, we perform two actions. \u0026nbsp;First, we log the anomalies (for debugging purposes). \u0026nbsp;We also define an email_alert, which will fire off an email. \u0026nbsp;The body of the email can use mustache for templating, which is how we can embed the list of alerts (via {{ctx.alerts}}, the array we built in the transformation step)\u003c/p\u003e\u003ch2 dir=\"ltr\" style=\"line-height: 1.38;margin-top: 18pt;margin-bottom: 6pt;\"\u003eConclusion\u003c/h2\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAnd that’s it! \u0026nbsp;The watches are long, but relatively straightforward when you work through them step-by-step. \u0026nbsp;All the difficult work was done in Part 1 and\u0026nbsp;2...moving the logic into Watcher is mostly\u0026nbsp;trivial.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eOnce these watches are enabled, the cluster will automatically start monitoring and alerting on an hourly basis. \u0026nbsp;It is very tunable because watches can be modified at any time via API calls. You could make the interval shorter or longer, extend the amount of data in each aggregation pass, modify any of the aggregation settings, change the types of moving averages in the pipeline agg, introduce entirely new metrics,\u0026nbsp;etc. \u0026nbsp;It is a very easy system to tweak even once it is live and in production.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cspan\u003e\u003c/span\u003eI hope you’ve enjoyed this three-part series. \u0026nbsp;It was a very fun project to work on, and really helped me understand the power that pipeline aggregations, Timelion and Watcher bring to the table (especially when combined). \u0026nbsp;Until next time!\u003c/p\u003e","category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2019-04-01T12:52:43.018Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"full_bleed_image":{"uid":"bltfda3d7019e246c37","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:54:31.474Z","updated_at":"2018-10-09T10:54:31.474Z","content_type":"image/jpeg","file_size":"103567","filename":"timelion-dashboard-anomaly-detector.jpg","title":"timelion-dashboard-anomaly-detector.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T03:14:46.139Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfda3d7019e246c37/5bbc88e7bb1e335136d9e8f2/timelion-dashboard-anomaly-detector.jpg"},"markdown_l10n":"","publish_date":"2015-12-16T16:11:21.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Implementing a Statistical Anomaly Detector in Elasticsearch - Part 3","seo_description_l10n":"In the final article of this three-part series, we build a fully automated anomaly detector using Watcher to send email alerts.","canonical_tag":"","noindex":false},"tags":[],"tags_campaigns":[],"tags_culture":[],"tags_elastic_stack":[],"tags_event_type":[],"tags_industry":[],"tags_partner":[],"tags_role":[],"tags_stage":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt12f7710e8fc6bd66","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:43:42.568Z","updated_at":"2018-10-09T10:43:42.568Z","content_type":"image/svg+xml","file_size":"5225","filename":"graph-watcher.svg","title":"graph-watcher.svg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-04T03:14:46.139Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt12f7710e8fc6bd66/5bbc865e63ed239936a7db02/graph-watcher.svg"},"title":"Implementing a Statistical Anomaly Detector in Elasticsearch - Part 3","title_l10n":"Implementing a Statistical Anomaly Detector in Elasticsearch - Part 3","updated_at":"2025-03-10T10:34:39.377Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/implementing-a-statistical-anomaly-detector-part-3","publish_details":{"time":"2025-03-10T10:34:43.420Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1821],"blogV2entries":[[{"uid":"blt20773f2febac2588","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"To efficiently observe across a mix of modern cloud and legacy systems, government agencies need observability tools that are open, flexible, and scalable. OpenTelemetry (OTel) is fast becoming a pivotal part of that flexible toolset.","author":["blt6d82d216763f3c7c"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-31T16:58:58.823Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5afa7b8fefe7e6b3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePublic sector organizations today face unique challenges in maintaining and optimizing their IT infrastructure and prioritizing efficiency and interoperability. With a mix of modern cloud and legacy systems, ensuring consistent performance, reliability, and security is paramount. To effectively observe across these environments, government agencies need observability tools that are open, flexible, and scalable. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/opentelemetry\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenTelemetry (OTel)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is fast becoming a pivotal part of that flexible toolset.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eWatch the webinar:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/opentelemetry-in-public-sector-using-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eObservability in the open: OTel for public sector\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"},{"title_l10n":"The rise of OpenTelemetry","_metadata":{"uid":"cs22db8247450ad2c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/opentelemetry\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenTelemetry\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, a Cloud Native Computing Foundation (CNCF) project, is rapidly changing how organizations collect and process observability data. The open source initiative provides a comprehensive set of APIs, libraries, agents, and instrumentation to support the generation, transmission, and processing of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/telemetry-data\"\u003e\u003cspan style='font-size: 12pt;'\u003etelemetry data\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (such as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/3-pillars-of-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003emetrics, logs, and traces\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e) in a single, unified schema. These open standards help organizations eliminate vendor lock-in and promote interoperability among observability platforms and tools, which is particularly crucial for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic sector organizations\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that often deal with diverse technology stacks and don’t want to be tied to proprietary solutions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOTel's significance lies in its ability to provide a consistent, vendor-agnostic approach to data collection. This leads to improved system reliability and uptime, which are critical for delivering essential public services. The standardized telemetry data also enhances accountability, audit trails, and compliance. Moreover, as an open source project, OTel offers a cost-effective solution for telemetry collection.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Observability in the public sector","_metadata":{"uid":"cs1dfdd23c1a6202c9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePublic sector organizations are increasingly shifting from traditional monitoring to observability to gain deeper insights into their complex systems. Traditional monitoring, which involves tracking predefined metrics and logs, often falls short in dynamic environments. Observability, on the other hand, captures comprehensive system data, enabling real-time analysis and troubleshooting, often leveraging AI and machine learning (ML).\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor end-to-end \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eobservability\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, data from the three pillars — \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/log-files\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003elogs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/traces#traces-metrics-logs-and-profiles\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emetrics\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/traces\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003etraces\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — are essential. This holistic view allows application and operations teams to understand the internal state of systems, diagnose issues effectively, and ensure high operational performance. However, many public sector organizations grapple with a fragmented tool landscape, including legacy systems and a mix of cloud environments, leading to complexity and increased costs. This is further complicated by compliance regulations, privacy requirements, and security controls required for sensitive data and mission-critical systems.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs549107098df7a4b7"}}},{"banner":{"reference":[{"uid":"bltc7b3a60e8abc4ce9","_content_type_uid":"banner"}],"_metadata":{"uid":"csafbbeef29dbd5451"}}},{"title_text":{"title_text":[{"title_l10n":"Open architecture and standards","_metadata":{"uid":"cs6e5c603e5bf44787"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdopting open architecture and industry standards is crucial for public sector entities to create sustainable, efficient, and supportable technology environments. OpenTelemetry, as an open source standard, ensures a consistent approach to capturing telemetry data from diverse applications and infrastructure. This \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/us-federal-agencies-opentelemetry\"\u003e\u003cspan style='font-size: 12pt;'\u003estandardization\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is vital for organizations managing a mix of in-house applications and commercial off-the-shelf (COTS) products.\u003cbr /\u003e\u003cbr /\u003eElastic's integration with OTel provides a solution to many observability challenges. With native support for OTel data feeds and fully supported distributions of OTel agents, agencies can integrate a wide range of data sources and gain real-time insights using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. This provides a supported method of collecting data in an industry-standard way for observability over modern and legacy systems.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs12ec0c67d2f6cec7"}}},{"title_text":{"title_text":[{"title_l10n":"Backend capabilities and analyst experiences","_metadata":{"uid":"cs93642111de5e7a75"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs government organizations adopt OpenTelemetry for data collection, the capabilities of the backend data storage and analytics component become increasingly important. Elastic provides a distributed, scalable, and flexible platform that can handle the large data volumes generated by government agencies. This distributed nature ensures high availability, allows data to be stored where it makes sense, and enables scaling without performance compromises.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic also focuses on providing unified experiences for end users, providing IT teams with dashboards and workflows that enable seamless data correlation and presentation. Analysts can gain a holistic view of their systems, troubleshoot issues efficiently, and switch between different views without worrying about the underlying data format or source.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"AI and machine learning for enhanced observability","_metadata":{"uid":"cs746fd3e851dc3562"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo further enhance observability, Elastic integrates \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/machine-learning\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI and ML capabilities\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. By combining OTel data collection with ML tools, organizations can expedite problem detection and resolution. The Elastic Search AI Platform offers out-of-the-box ML features for anomaly detection and automated metadata analysis, reducing the cognitive load on analysts and enabling them to focus on strategic tasks.\u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/ai-assistant\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cbr /\u003e\u003cbr /\u003eElastic's AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e also plays a crucial role in improving analyst workflows. By leveraging \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style='font-size: 12pt;'\u003enatural language processing\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, the AI Assistant can answer questions, generate queries, and surface relevant information from knowledge bases, helping analysts resolve issues faster.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Reusability for cybersecurity","_metadata":{"uid":"cs7a289ef8452ad655"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe use of OpenTelemetry tools isn’t limited to just observability use cases. With ever increasing data required for system visibility and performance, there is significant opportunity for security teams to use data collected for observability as part of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/cybersecurity\"\u003e\u003cspan style='font-size: 12pt;'\u003ecybersecurity\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e operations.\u003cbr /\u003e\u003cbr /\u003eElastic provides out-of-the-box security analytics views, dashboards, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/threat-hunting\"\u003e\u003cspan style='font-size: 12pt;'\u003ethreat hunting workflows\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. By unifying observability and security data, analysts can quickly determine if an issue is related to infrastructure, application defects, or security breaches.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic Observability: A powerful backend","_metadata":{"uid":"cs87f63265c0b1a73b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic's Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e provides the robust foundation for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Known for its speed, flexibility, and scalability, Elastic enables real-time analysis of large data volumes, including AI powered analyst experiences.\u003cbr /\u003e\u003cbr /\u003eElastic Observability offers a comprehensive suite of tools for full-stack observability, empowering organizations to achieve end-to-end visibility into \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/application-performance-monitoring\"\u003e\u003cspan style='font-size: 12pt;'\u003eapplication performance\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and availability. Elastic is also a major contributor to the OpenTelemetry project, having donated the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/ecs/current/ecs-reference.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Common Schema\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, APM Agent SDKs, and its Universal Profiling Agent. Elastic provides native support for OpenTelemetry data, allowing for direct ingestion of traces, metrics, and logs without conversion. This tight integration simplifies data collection and enables seamless workflows within the Elastic Search AI Platform.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The future of observability","_metadata":{"uid":"cse959fd9a1e6f9060"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs public sector organizations continue to focus on modernization and efficiency, OTel's flexibility and adaptability will be critical. Integrating OTel with platforms like Elastic enables organizations to leverage real-time, intelligent insights and enhance predictive maintenance.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy combining \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/opentelemetry\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability with OpenTelemetry\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, public sector organizations can achieve a robust, agile, and efficient observability solution that is scalable, cost-effective, and future-proof. This empowers them to deliver reliable and efficient services to citizens while ensuring compliance with regulatory requirements.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eWant to learn more?\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTune in to the webinar, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/opentelemetry-in-public-sector-using-elastic\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eObservability in the open: OTel for public sector\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, for an overview of OTel. We’ll cover all the practical considerations, value-adds, and efficiencies of OTel for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/civilian\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003egovernment\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/education\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eeducation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/defense\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edefense\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRead the white paper: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/opentelemetry-using-elastic\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOpenTelemetry in public sector using Elastic\u003c/span\u003e\u003c/a\u003e\u003cu\u003e\u003c/u\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cu\u003e\u003c/u\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cu\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/u\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cu\u003e\u003c/u\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cu\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/u\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cu\u003e\u003c/u\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cu\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/u\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3c4342d66ca285cc"}}}],"publish_date":"2025-03-31","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4eb0f5c53cfcb73a","ACL":{},"created_at":"2023-11-06T20:43:57.712Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-source-standards","label_l10n":"Open source/standards","tags":[],"title":"Open source/standards","updated_at":"2023-11-06T20:43:57.712Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:21.485Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt17630d07558c63f6","ACL":{},"created_at":"2023-11-06T21:33:01.038Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"state-local-government","label_l10n":"State \u0026 local government","tags":[],"title":"State \u0026 local government","updated_at":"2023-11-06T21:33:01.038Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.342Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt7043145c7ebd03fc","_version":1,"title":"Blog Header Image_ Simplifying public sector observability with OpenTelemetry and Elastic176952.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-31T16:56:01.110Z","updated_at":"2025-03-31T16:56:01.110Z","content_type":"image/jpeg","file_size":"110663","filename":"Blog_Header_Image_Simplifying_public_sector_observability_with_OpenTelemetry_and_Elastic176952.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-31T17:15:17.883Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7043145c7ebd03fc/67eac92107ba261f790be0d9/Blog_Header_Image_Simplifying_public_sector_observability_with_OpenTelemetry_and_Elastic176952.jpg"},"title":"Simplifying public sector observability with OpenTelemetry and Elastic","title_l10n":"Simplifying public sector observability with OpenTelemetry and Elastic","updated_at":"2025-03-31T20:27:09.796Z","updated_by":"bltd9765be97bbed20c","url":"/blog/simplifying-public-sector-observability","publish_details":{"time":"2025-03-31T20:27:18.595Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb99c86e7bf8954a3","_version":73,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic recognized as a Visionary in the 2022 Gartner® Magic Quadrant™ for APM and Observability for the second consecutive year! Find out the details on how we scored among the top three vendors for 5 out of 6 critical use cases.","author":["bltde0a0be05534cebf"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2022-05-26T14:22:05.635Z","created_by":"blt469f34057b68c377","markdown_l10n":"\n","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa5328db5d00de694"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe are excited to announce that Elastic has been recognized as a Visionary in the \u003ca href=\"/explore/devops-observability/2022-gartner-magic-quadrant-apm\" target=\"_blank\"\u003e2022 Gartner Magic Quadrant for APM and Observability\u003c/a\u003e for the second year in a row. In addition, the Elastic solution scored among the Top 3 vendors in five out of six use cases in the \u003ca href=\"/explore/devops-observability/2022-gartner-critical-capabilities-apm\" target=\"_blank\"\u003e2022 Gartner Critical Capabilities for APM and Observability\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eElastic recognized for its completeness of vision and ability to execute\u003c/h2\u003e\u003cp\u003eWe believe Elastic's recognition in this report, based on our “ability to execute” and “completeness of vision”, provides validation to our efforts to deliver new and innovative full-stack observability capabilities on a single platform.\u003c/p\u003e\u003cp\u003eWe are grateful to our customers who continue to adopt \u003ca href=\"/observability\" target=\"_blank\"\u003eElastic Observability\u003c/a\u003e to ingest business and operational data, break down silos, and enable end-to-end hybrid and multi-cloud visibility. Elastic’s ability to visualize and analyze all data in context and correlate across logs, metrics, and traces, combined with sophisticated out-of-the-box machine learning and anomaly detection, enables faster problem detection and resolution.\u003c/p\u003e\u003cp\u003eRecent Elastic Observability releases have demonstrated sustained momentum in the following areas:\u003c/p\u003e\u003cul\u003e\u003cli\u003eAutomated root cause analysis with innovative AIOps capabilities such as APM correlations and anomaly detection\u003c/li\u003e\u003cli\u003ePowerful and interactive analytics capabilities allowing queries across multiple dimensions, connecting business and operational KPIs, and the ability to answer the “unknown unknowns”\u003c/li\u003e\u003cli\u003eOver 200+ out-of-the-box integrations delivering frictionless data ingest with native cloud provider integrations for AWS, Azure, and Google Cloud, as well as cloud-native observability for AWS Lambda and Kubernetes\u003c/li\u003e\u003cli\u003eA unified Elastic Agent with centralized management and support for metrics, logs, traces, and endpoint security data collection\u003c/li\u003e\u003cli\u003eTraceability of the software delivery lifecycle with observability for CI/CD pipeline tools such as Jenkins, Maven, and Ansible\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs88d97d4fe27ba3a5"}}},{"image":{"image":{"uid":"blt44b350bc960cf375","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-06-13T15:51:20.088Z","updated_at":"2022-06-13T15:51:20.088Z","content_type":"image/png","file_size":"506841","filename":"2022_Gartner_MQ_for_APM_graphic_-_Small.png","title":"2022_Gartner_MQ_for_APM_graphic_-_Small.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-13T16:36:39.152Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt44b350bc960cf375/62a75cf8482ba357e65db33a/2022_Gartner_MQ_for_APM_graphic_-_Small.png"},"_metadata":{"uid":"cs706ee2b3bd9eaba9"},"caption_l10n":"","alt_text_l10n":"2022 Gartner Magic Quadrant for APM and Observability, Elastic Observability as Visionary","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"Elastic scored among top three vendors for 5 out of 6 use cases","_metadata":{"uid":"cs972666851c2e320a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElastic scored among the top 3 vendors in the following five use cases:\u003c/p\u003e\u003col\u003e\u003cli\u003eIT Operations\u003c/li\u003e\u003cli\u003eDevOps/AppDev\u003c/li\u003e\u003cli\u003eSRE/Platform Operations\u003c/li\u003e\u003cli\u003eApplication Owner/Line of Business\u003c/li\u003e\u003cli\u003eDigital Experience Monitoring\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eIn addition, Elastic is ranked sixth for the Security Operations use case.\u003c/p\u003e\u003cp\u003eWe believe Elastic’s strategic platform investments to deliver observability and observability capabilities on a unified platform align strongly with the market convergence of these functions.\u003c/p\u003e"}],"_metadata":{"uid":"csc77bbbd809be9990"}}},{"image":{"image":{"uid":"blta9d0d975985edb7c","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-06-13T15:30:39.011Z","updated_at":"2022-06-13T15:30:39.011Z","content_type":"image/png","file_size":"117591","filename":"Figure1.png","title":"Figure1.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-13T16:36:39.161Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta9d0d975985edb7c/62a7581f05f1d157f3a8a34b/Figure1.png"},"_metadata":{"uid":"cs0d5ead1d42f64861"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Building lasting value for customers","_metadata":{"uid":"cs2ade86ce48c92c6d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn our upcoming customer ROI value study, \u003cem\u003eResults that Matter,\u003c/em\u003e Elastic surveyed more than 1,400 customers to understand the key benefit areas, capabilities, and value they achieve with the Elastic Platform.\u003c/p\u003e\u003cp\u003eObservability customers indicated a 67% increase in developer and IT staff productivity, 66% improvement in MTTx metrics, and they were able to accelerate the time to market of new features by 61%. In addition, Observability customers reported an overall improvement in system resilience of 60%.\u003c/p\u003e\u003cp\u003eThese results show how organizations can increase productivity, accelerate innovation, and improve the digital experience for their customers while ensuring the delivery of mission-critical services with Elastic Observability.\u003c/p\u003e\u003cp\u003eAccording to Simon Ansell, Senior Director of Design, Engineering and Quality IT at Jaguar Land Rover, Elastic Observability gives his team the opportunity to \u003ca href=\"/customers/jaguar-land-rover\" target=\"_blank\" isblock=\"true\"\u003e\u003cu\u003edetect and fix root cause events quickly\u003c/u\u003e\u003c/a\u003e across business units and with minimal IT or developer support.\u003c/p\u003e\u003cp\u003e“Elasticsearch gives us the ability to spot all the transactions between our suppliers and our JLR plants, ensuring that transactions are synchronized, and data quality is maintained. By optimizing the data transmissions, we can help engineering become more efficient and further optimize our supply chain”, Ansell adds.\u003c/p\u003e\u003cp\u003eElastic reviews on \u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring/vendor/elasticsearch\" target=\"_self\" isblock=\"true\"\u003eGartner Peer Insights\u003c/a\u003e also include the following comments:\u003c/p\u003e\u003cp\u003e\u003cem\u003e“Complete observability solution, well documented, and with clear licensing mode and expenses. It covers the main observability pillars: monitoring, centralized logs, APM, and uptime.”\u003c/em\u003e (\u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring/vendor/elasticsearch/product/elastic-elk-stack/review/view/4008922\" target=\"_blank\" isblock=\"true\"\u003e\u003cu\u003eRead the full review\u003c/u\u003e\u003c/a\u003e)\u003c/p\u003e\u003cp\u003e\u003cem\u003e- Project Manager in the IT Services Industry\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e“I don't know how it would be possible to manage large scale production deployments without a tool like this, without the metrics, correlation, and monitoring provided by the Elastic Stack we would be blind [to] the operation of our systems and severely limited in our ability to respond to issues in a timely manner.\"\u003c/em\u003e (\u003ca href=\"https://www.gartner.com/reviews/market/application-performance-monitoring/vendor/elasticsearch/product/elastic-observability/review/view/3675358\" target=\"_blank\" isblock=\"true\"\u003eRead the full review\u003c/a\u003e)\u003c/p\u003e\u003cp\u003e\u003cem\u003e- Technical Advisor in the Public Sector\u003c/em\u003e\u003c/p\u003e\u003ch2\u003eElastic Observability continues to drive innovation\u003c/h2\u003e\u003cp\u003eAs an active contributor to the CNCF, Elastic embraces and supports open-source standards including native support for OpenTelemetry. Our flexible deployment models allow customers to operate the observability solution closer to their workloads in the cloud or on premises, enabling data sovereignty while lowering the total cost of ownership. Elastic Observability continues to simplify the ingestion of telemetry data, using one-click integrations via the unified Elastic Agent, including central management and policy configurations at scale.\u003c/p\u003e\u003cp\u003e\u003cem\u003e“We believe this recognition validates Elastic’s investments in the power of the Elastic Search platform and our Observability solution across logs, traces, metrics, AIOps, and OpenTelemetry, which continues to enable digital businesses to delight their customers.”\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003e- Sajai Krishnan, GM Elastic Observability\u003c/em\u003e\u003c/p\u003e\u003cp\u003eIf you’d like to share your own experience with Elastic Observability on the Gartner Peer Insights review site, please do so at \u003ca href=\"https://gtnr.io/vi0wXUUVs\" target=\"_self\" isblock=\"true\"\u003ehttps://gtnr.io/vi0wXUUVs\u003c/a\u003e. For your time, you can receive a $25 gift card or have it donated to a charity.\u003c/p\u003e\u003cp\u003e\u003ca href=\"/explore/devops-observability/2022-gartner-magic-quadrant-apm\" target=\"_blank\" isblock=\"true\"\u003eDownload the 2022 Gartner APM and Observability Magic Quadrant report\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"/explore/devops-observability/2022-gartner-critical-capabilities-apm\" target=\"_blank\" isblock=\"true\"\u003eDownload the 2022 Garter Critical Capabilities for APM and Observability report\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eGartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eGartner and Magic Quadrant are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eGartner, “Magic Quadrant for APM and Observability,” By \u003c/em\u003e\u003ca href=\"https://www.gartner.com/analyst/76263\" target=\"_self\" isblock=\"true\"\u003e\u003cem\u003ePadraig Byrne\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, \u003c/em\u003e\u003ca href=\"https://www.gartner.com/analyst/62373\" target=\"_self\" isblock=\"true\"\u003e\u003cem\u003eGregg Siegfried\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, \u003c/em\u003e\u003ca href=\"https://www.gartner.com/analyst/97569\" target=\"_self\" isblock=\"true\"\u003e\u003cem\u003eMrudula Bangera\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, June 2022.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eGartner, \"Critical Capabilities for APM and Observability\", By \u003c/em\u003e\u003ca href=\"https://www.gartner.com/analyst/62373\" target=\"_self\" isblock=\"true\"\u003e\u003cem\u003eGregg Siegfried\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, \u003c/em\u003e\u003ca href=\"https://www.gartner.com/analyst/97569\" target=\"_self\" isblock=\"true\"\u003e\u003cem\u003eMrudula Bangera\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, \u003c/em\u003e\u003ca href=\"https://www.gartner.com/analyst/76263\" target=\"_self\" isblock=\"true\"\u003e\u003cem\u003ePadraig Byrne\u003c/em\u003e\u003c/a\u003e\u003cem\u003e, June 2022.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eThis graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Elastic.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003eGartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cem\u003ePEER INSIGHTS is a trademark and service mark, of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.\u003c/em\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs12ad444ebb1e06a4"}}}],"publish_date":"2022-06-13","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic recognized as a visionary in the 2022 Gartner® Magic Quadrant™ for APM and Observability for the second consecutive year","seo_description_l10n":"We are excited to announce that Elastic has been recognized as a Visionary in the 2022 Gartner APM and Observability Magic Quadrant for the second year in a row. The Elastic Observability solution scored among the Top 3 vendors in five out of six use cases in the 2022 Gartner Critical Capabilities for APM and Observability.\n","seo_image":{"uid":"blt3603a9dd70034139","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-06-13T13:23:34.109Z","updated_at":"2022-06-13T13:23:34.109Z","content_type":"image/png","file_size":"70099","filename":"2022Gartner-APM-Observability-Elastic-twitter.png","title":"2022Gartner-APM-Observability-Elastic-twitter.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-13T16:36:39.171Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3603a9dd70034139/62a73a56a18b205191cf8a30/2022Gartner-APM-Observability-Elastic-twitter.png"},"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt04299f9a7e625037","ACL":{},"created_at":"2023-11-06T20:39:42.024Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"gartner","label_l10n":"Gartner","tags":[],"title":"Gartner","updated_at":"2023-11-06T20:39:42.024Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.182Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf93d7e3164a8ca89","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-06-13T13:24:14.438Z","updated_at":"2022-06-13T13:24:14.438Z","content_type":"image/png","file_size":"92846","filename":"2022-Gartner-APM-Observability-Elastic-LinkedIn.png","title":"2022-Gartner-APM-Observability-Elastic-LinkedIn.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-13T16:36:39.178Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf93d7e3164a8ca89/62a73a7ec4d59b57e0c24e66/2022-Gartner-APM-Observability-Elastic-LinkedIn.png"},"title":"Elastic recognized as a Visionary in the 2022 Gartner® Magic Quadrant™ for APM and Observability for the second consecutive year","title_l10n":"Elastic recognized as a Visionary in the 2022 Gartner® Magic Quadrant™ for APM and Observability for the second consecutive year","updated_at":"2025-03-31T14:45:27.272Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-observability-2022-gartner-magic-quadrant-critical-capabilities-apm","publish_details":{"time":"2025-03-31T14:45:33.012Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcd6bb781e50ce12d","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"We will present and use elastic-package tool which is the official developer tool, used to create your own integrations that will be run by the Elastic Agent.","author":["blt11e8f14bb30068bc"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-10-25T16:48:11.043Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd04ed0d57cb2e4c1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this getting starting guide you will learn how elastic-package can help you quickly start a full Elastic Stack.\u003c/p\u003e\u003cp\u003eElastic-package is an open source tool that will help you shorten your development time by providing pre-built commands. For example it will help you lint, format, test, build, and promote your packages.\u003c/p\u003e\u003cp\u003eEach and every developer that wants to contribute by creating their own \u003ca href=\"https://www.elastic.co/integrations\"\u003eintegrations\u003c/a\u003e should use elastic-package. It will provide a ready-to-code environment.\u003c/p\u003e\u003ch2\u003eGetting started with elastic-package\u003c/h2\u003e\u003cp\u003eAs a developer you can use elastic-package in two ways, the first one is through binary usage and the second one is by pulling elastic-package github repository.\u003c/p\u003e\u003cp\u003eFor binary usage, start by downloading the \u003ca href=\"https://github.com/elastic/elastic-package/releases\"\u003elatest version\u003c/a\u003e.\u003c/p\u003e\u003cp\u003ePull the archive that you need and unarchive it locally.\u003c/p\u003e"}],"_metadata":{"uid":"cs0dbbc06aead6317b"}}},{"code":{"code":"julienlind@MacBook-Pro Downloads % tar -xvf elastic-package_0.20.1_darwin_amd64.tar.gz","_metadata":{"uid":"cs4f40fb3097d57696"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7cc991071768031f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThen you can experiment with the elastic-package command line. First, try starting with the \"help\" command.\u003c/p\u003e\n\u003cp\u003e\u003cem\u003e(Note:It might improve your developer experience if you put the tool in your PATH. Edit your ~/.bashrc file and specify your executable PATH: “PATH=$PATH:$PATH_TO_MY_EXEC”)\u003c/em\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdc0d36f75977fa6c"}}},{"code":{"code":"julienlind@MacBook-Pro Downloads % elastic-package help\nelastic-package - Command line tool for developing Elastic Integrations\n\nUsage:\n elastic-package [command]\n\nAvailable Commands:\n build Build the package\n check Check the package\n clean Clean used resources\n completion generate the autocompletion script for the specified shell\n create Create package resources\n export Export package assets\n format Format the package\n help Help about any command\n install Install the package\n lint Lint the package\n profiles Manage stack config profiles\n promote Promote packages\n publish Publish the package to the Package Registry\n service Manage the service stack\n stack Manage the Elastic stack\n status Show package status\n test Run test suite for the package\n uninstall Uninstall the package\n version Show application version\n\nFlags:\n -h, --help help for elastic-package\n -v, --verbose verbose mode\n\nUse \"elastic-package [command] --help\" for more information about a command.","_metadata":{"uid":"cs0143a273661a0147"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs697f181305769603"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWith the github repository:\u003c/p\u003e"}],"_metadata":{"uid":"csa82ee846799d6178"}}},{"code":{"code":"julienlind@MacBook-Pro Downloads % git clone https://github.com/elastic/elastic-package.git\n\nCloning into 'elastic-package'...\nremote: Enumerating objects: 5188, done.\nremote: Counting objects: 100% (1356/1356), done.\nremote: Compressing objects: 100% (449/449), done.\nremote: Total 5188 (delta 1078), reused 936 (delta 901), pack-reused 3832\nReceiving objects: 100% (5188/5188), 13.41 MiB | 26.11 MiB/s, done.\nResolving deltas: 100% (2952/2952), done.\njulienlind@MacBook-Pro Downloads % cd elastic-package\njulienlind@MacBook-Pro elastic-package % make build\n[...]\njulienlind@MacBook-Pro elastic-package % elastic-package help","_metadata":{"uid":"csc4efc329b4086b25"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7a66f751109c2efa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\"make build”\" command will call \"go get\" which will result in creating a binary file in ~/go/bin . \u003c/p\u003e\n\u003cp\u003eThus here we assume that in your ~/.bashrc file you have specified your Golang executable path such as follow:\u003c/p\u003e\n\u003cp\u003ePATH=$PATH:$GOPATH/bin\u003c/p\u003e\u003ch2\u003eStart a local elastic stack in a few minutes\u003c/h2\u003e\n\u003cp\u003eHere, we assume that you do have \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html\"\u003eDocker desktop\u003c/a\u003e up and running on your computer.\u003c/p\u003e\n\u003cp\u003eOnce you do, simply use the “stack” command as in the example below:\u003c/p\u003e"}],"_metadata":{"uid":"cs29b529076997fce4"}}},{"code":{"code":"julienlind@MacBook-Pro elastic-package % elastic-package stack up","_metadata":{"uid":"cs15f4aec7529f385b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs68698f3c3f3dc0ab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen booting up a stack you will then be able to access all components locally and experiment with all available functionalities. If you encounter any problems add the -v option to allow verbose output. (Please note that having a low memory threshold can cause some issues with Docker settings.)\u003c/p\u003e\n\u003cp\u003e\"-d\" can also be used in order to run this in daemon mode.\u003c/p\u003e\n\u003cp\u003eYour local stack is now available with the following information:\u003c/p\u003e\n\u003cp\u003ePackage Registry: http://localhost:8080\u003cbr\u003e\nElasticsearch: http://localhost:9200\u003cbr\u003e\nFleet Server: http://localhost:8220\u003cbr\u003e\nkibana: \u003ca href=\"http://localhost:5601/\"\u003ehttp://localhost:5601\u003c/a\u003e\u003cbr\u003e\nlogin: elastic\u003cbr\u003e\npass: changeme\u003c/p\u003e\n\u003cp\u003eWhen you are done with your tests, be sure to run a \"stack down\" command to shut down everything.\u003c/p\u003e"}],"_metadata":{"uid":"cs86cc9ebe7335f381"}}},{"code":{"code":"julienlind@MacBook-Pro elastic-package % elastic-package stack down","_metadata":{"uid":"csc47e548f8529a0ad"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csde426df364931a99"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\"Stack up\" and \"stack down\" seem to be simple commands, but behind the scenes there are a lot of things happening. These commands start or close a set of dependent containers: elasticsearch, kibana, fleet, elastic agent and the package registry.\u003c/p\u003e\n\u003cp\u003eAll those containers are deployed inside the same Docker network in order to communicate between each other.\u003c/p\u003e\n\u003cp\u003eRunning \"docker ps\" command will help you discover what is running:\u003c/p\u003e"}],"_metadata":{"uid":"csc98696faeaf0019c"}}},{"code":{"code":"julienlind@MacBook-Pro elastic-package % docker ps\nCONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES\n1d92499e5f7b docker.elastic.co/beats/elastic-agent-complete:7.15.0-SNAPSHOT \"/usr/bin/tini -- /u…\" About a minute ago Up About a minute (healthy) elastic-package-stack_elastic-agent_1\n743bea1f53de docker.elastic.co/beats/elastic-agent-complete:7.15.0-SNAPSHOT \"/usr/bin/tini -- /u…\" 2 minutes ago Up About a minute (healthy) 127.0.0.1:8220-\u003e8220/tcp elastic-package-stack_fleet-server_1\n0f1205be9e12 docker.elastic.co/kibana/kibana:7.15.0-SNAPSHOT \"/bin/tini -- /usr/l…\" 2 minutes ago Up About a minute (healthy) 127.0.0.1:5601-\u003e5601/tcp elastic-package-stack_kibana_1\n56525b050da9 elastic-package-stack_package-registry \"./package-registry …\" 2 minutes ago Up About a minute (healthy) 127.0.0.1:8080-\u003e8080/tcp elastic-package-stack_package-registry_1\nb3587459cedc docker.elastic.co/elasticsearch/elasticsearch:7.15.0-SNAPSHOT \"/bin/tini -- /usr/l…\" 2 minutes ago Up About a minute (healthy) 127.0.0.1:9200-\u003e9200/tcp, 9300/tcp elastic-package-stack_elasticsearch_1","_metadata":{"uid":"csab03536fc546a066"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2e5566c96a620ee1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNow that you are familiar with elastic-package, you can think about \u003ca href=\"https://www.elastic.co/blog/use-elastic-package-to-create-and-bootstrap-a-new-elastic-integration\" target=\"_self\"\u003edeveloping your own integrations\u003c/a\u003e, and testing them locally, or on your elastic stack.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd0198530e5a79609"}}}],"publish_date":"2021-10-25T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltc1e6b31c57960d36","created_by":"bltc759967f917b6179af5f1988","updated_by":"bltc759967f917b6179af5f1988","created_at":"2020-06-10T18:24:15.869Z","updated_at":"2020-06-10T18:24:15.869Z","content_type":"image/png","file_size":"142598","filename":"elastic-integrations.png","title":"elastic-integrations.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-25T21:11:23.988Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1e6b31c57960d36/5ee1254ff2c45903a4be0c31/elastic-integrations.png"},"title":"How to quickly start a full Elastic Stack by using elastic-package","title_l10n":"How to quickly start a full Elastic Stack by using elastic-package","updated_at":"2025-03-28T17:22:30.119Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/getting-started-with-elastic-package","publish_details":{"time":"2025-03-28T17:22:35.197Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt48bb8f3504c29c30","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"Realizing business objectives and successful outcomes with our customers is at the core of what we do. In this series, learn some of the many ways Elastic Technical Account Managers partner with organizations to accomplish these goals.","author":["bltad40eff0cd58b113","bltfcef00cc055272b5"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-10-28T20:30:54.035Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc6b44c8335fc004c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/consulting\"\u003eElastic Consulting\u003c/a\u003e helps our customers drive impactful business outcomes. From preventing fraud in the financial space, to taking actions on botnets across eCommerce platforms. In this part of our series, Nikki Jones, Customer Success Lead, and Chad Pryor, Elastic Technical Account Manager (TAM), discuss the secret recipe for helping customers achieve success, and the value of the TAM/customer relationship.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eHow do Elastic Technical Account Managers support our customers? \u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eWe provide a personal connection, a bridge of success to enable our customers to derive the most value from their investment in our products and services. We are solution providers who proactively guide the technology landscape, help resolve challenges before they occur, and provide a gateway into the Elastic ecosystem so our customers can focus on the business outcomes most important to them.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eWe heard something about a secret recipe for success, care to share this with us?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eMy recipe is really quite simple: 1 cup customer success management, 1 cup architect, 1 cup product management, 1 cup project manager, 1 cup business development with a dash of customer advocacy. Bake into the voice of the customer.\u003c/p\u003e\n\u003cp\u003eWorking together cross functionally on projects throughout the customer journey to plan the technology roadmap, validate configurations, prevent issues before they happen and implement successfully, means we have happy customers.\u003c/p\u003e\u003cbr\u003e"}],"_metadata":{"uid":"cs38e1f43a9917a946"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7d649f3e32643f45","ACL":{},"content_type":"image/png","created_at":"2021-10-28T20:27:24.076Z","created_by":"blt1e57c6588ae1816e","file_size":"60262","filename":"blog-elastic-chadpryor.png","tags":[],"title":"blog-elastic-chadpryor.png","updated_at":"2021-10-28T20:27:24.076Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-29T15:00:00.509Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7d649f3e32643f45/617b07aca2b4ac1067d75c3a/blog-elastic-chadpryor.png"},"_metadata":{"uid":"cs14bac7936d53dafc"},"caption_l10n":"Chad Pryor, Technical Account Manager","alt_text_l10n":"Chad Pryor, Technical Account Manager","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs72742af3982c639c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003e\u003cem\u003eTell us how you became an Elastic Consultant?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eI had my first introduction to \u003ca href=\"https://www.elastic.co/elastic-stack/\"\u003eElasticsearch\u003c/a\u003e\n version 0.9 \u0026 1.0.1 at a previous company. I created a dashboard of\n multiple sources from the operations infrastructure to create a heat \nmap of incidents per service based on MTTR and cost of engineers. This \nallowed us to view the outages, their cost and availability. During the\n early days of Elasticsearch we were an extremely heavy user of Kibana, \nwith over 300 users. \u003c/p\u003e\n\u003cp\u003eThen I went to the first Elastic{ON} where I\n met the founders who were knowledgeable of the company I was working \nfor and knew a little about my use case. I knew Elastic was a place I \ncould throw my energy and creativity towards. It felt like a team and I \nloved the incredible nature of Search. So I submitted my resume and the \nrest is history.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eIn your words, what do you do for our customers? \u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eI\n act as a conduit between our Elastic technical resources and our \ncustomers' to help achieve business outcomes and strategize on the \ntechnology roadmap. A real highlight for me is helping our customers see\n the full potential of using our solutions and how to solve many \nbusiness challenges. Having regular meetings and asking the right \nquestions to facilitate better outcomes really maximizes their Elastic \ninvestment.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eWhat kind of business and technical challenges do you help our customers to solve?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eSome of the challenges we love to help solve include upgrade planning, product and feature guidance, and support of new features and adoption strategies. Also the Identification of pain points and feedback to Product teams is really important, as are support case reviews and improvements.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eWhat has been one the most interesting or coolest use cases you were involved in and why?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eOne customers’ team had been using Splunk to try and respond to bad bots across their e-commerce platform. The challenge for them was doing this in real time, so I worked with them to implement Watcher to take actions and identify the bad bots across multiple data streams and created an allow/deny list which enabled them to block bad bots in real time and in an automated way.\u003c/p\u003e\n\u003cp\u003eAnother customer in the financial space was looking to correlate business transactions with operational analytics. I worked very closely to enable the teams, helping them to create a Business KPI dashboard that was shared across multiple business units and used by Executives for real insights. Later I found this was further extended into their security space.\u003c/p\u003e\n\u003cp\u003eThis concept helped prevent fraud. Several of these team members went on to lead other Elastic Stack initiatives within their organization and were quickly promoted. They even spoke at one of our Elastic events. Go Team X!\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eHow do you think our customers view you and your relationship?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eI strive to be part of the team and become the center for all things Elastic. Knowing the challenges a customer faces while using our products is important for helping them be successful. Understanding many use cases within their industry helps provide guidance and strengthens the relationship. As new stakeholders become part of their team and the Elastic footprint evolves, I serve as a consistent point of contact helping provide a common language which enables us to Invest in their success and reach their goals.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eHow does it feel to help our customers succeed? \u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eIf you have ever assisted with a goal, closed a big deal, solved a nagging technical problem, mentored someone or helped someone grow into something more, you will know there is a sense of pride and accomplishment in that growth. That's how it feels to help our customers succeed. \u003c/p\u003e\u003ch3\u003eAligning with our customers' desired business outcomes to achieve success\u003c/h3\u003e\n\u003cp\u003e\"Our\n TAMs provide technical and strategic guidance at every stage in your \nElastic journey. They are an extension of your team and dedicated to \nhelping you achieve your business outcomes. Contact \u003ca href=\"https://www.elastic.co/consulting\"\u003eElastic Consulting\u003c/a\u003e to learn more about \u003ca href=\"https://www.elastic.co/consulting/embedded-services\"\u003eEmbedded Services\u003c/a\u003e and how we can help you maximize your Elastic investment.\"\u003c/p\u003e\u003cbr\u003e"}],"_metadata":{"uid":"cs7677134e956f9810"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt13aded2f2f2151e7","ACL":{},"content_type":"image/png","created_at":"2021-08-25T13:09:25.990Z","created_by":"blt1e57c6588ae1816e","file_size":"230941","filename":"blog-elastic-nikki-3.png","tags":[],"title":"blog-elastic-nikki-3.png","updated_at":"2021-08-25T13:09:25.990Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-29T15:00:00.171Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt13aded2f2f2151e7/612641054d39656a33b08da5/blog-elastic-nikki-3.png"},"_metadata":{"uid":"cs6da1d695697a8c87"},"caption_l10n":"Nikki Jones, Customer Success \u0026 Services Lead","alt_text_l10n":"Nikki Jones, Customer Success \u0026 Services Lead","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}}],"publish_date":"2021-11-01T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Helping Elastic Customers Succeed | Elastic TAMs partner with organizations to maximize their investments","seo_description_l10n":"Realizing business objectives and successful outcomes with our customers is at the core of what we do. In this series, learn some of the many ways Elastic Technical Account Managers partner with organizations to accomplish these goals. Interview with Chad Pryor.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt495cceb372618a03","created_by":"blt4349d9729d06d101","updated_by":"blt4349d9729d06d101","created_at":"2022-01-12T14:40:00.805Z","updated_at":"2022-01-12T14:40:00.805Z","content_type":"image/png","file_size":"31159","filename":"TAMblog.png","title":"TAMblog.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-12T14:40:08.739Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt495cceb372618a03/61dee8409efff26ae7598a77/TAMblog.png"},"title":"Helping Elastic Customers Succeed | Elastic TAMs partner with organizations to maximize their investments","title_l10n":"Helping Elastic Customers Succeed | Elastic TAMs partner with organizations to maximize their investments","updated_at":"2025-03-28T17:20:44.706Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/helping-elastic-customers-succeed-elastic-tams-partner-with-organizations-to-maximize-their-investments","publish_details":{"time":"2025-03-28T17:20:49.671Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8a2794067c9957c5","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"As news of Log4shell emerged, security teams all around the globe scrambled to detect, mitigate and contain the vulnerability. This blog highlights how teams can use the Elastic Search platform to detect Log4shell exploit attempts.","author":["blt47281ee31f9b7aa9"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-01-13T17:35:34.412Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd43605f56b7d2633"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eOverview\u003c/h2\u003e\n\u003cp\u003eFollowing the discovery of Log4Shell, a vulnerability in Log4J2, Elastic released a \u003ca href=\"https://www.elastic.co/blog/detecting-log4j2-with-elastic-security?ultron=log4js-exploit\u0026blade=announcement\u0026hulk=email\u0026mkt_tok=ODEzLU1BTS0zOTIAAAGBU8N1ZDYRbFq2QZ4ZK8tc2IbDatArsdI6WGcA2M90g4v02svJeqCXFeZ23R4TjeYii4KBGAkqMBgWc5IkxYrmefgwZBanjGQh8v66drUymiVSQFvs\"\u003eblog post\u003c/a\u003e describing how users of our platform can leverage Elastic Security to help defend their networks. We also released an \u003ca href=\"https://discuss.elastic.co/t/apache-log4j2-remote-code-execution-rce-vulnerability-cve-2021-44228-esa-2021-31/291476\"\u003eadvisory\u003c/a\u003e detailing how Elastic products and users are impacted.\u003c/p\u003e\n\u003cp\u003eIn this blog, we expand on these initial posts and highlight how the combination of security and observability solutions can provide deep visibility into the exploited vulnerability and arm security analysts with valuable data for root cause analysis.\u003c/p\u003e\u003ch2\u003eGaining the upper hand - combining Observability and Security data\u003c/h2\u003e\n\u003cp\u003eAlong with \u003ca href=\"https://www.elastic.co/security\"\u003eElastic Security\u003c/a\u003e, we provide a comprehensive \u003ca href=\"https://www.elastic.co/observability\"\u003eObservability\u003c/a\u003e suite within Kibana. Observability is primarily referring to the combination of application performance monitoring (APM), logs, and metrics — a traditionally untapped datasource in the world of security analytics and incident response.\u003c/p\u003e\n\u003cp\u003eSince Log4Shell is a vulnerability in \u003ca href=\"https://logging.apache.org/log4j/2.x/\"\u003eLog4j2\u003c/a\u003e, a Java logging library, we will be using our \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/java/current/index.html\"\u003eJava APM agent\u003c/a\u003e to demonstrate what a vulnerable instrumented application produces if Log4Shell is exploited. Our vulnerable application will also be producing logs, which can be correlated with the data produced by APM. This is a feature known as \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/java/current/log-correlation.html\"\u003ecorrelated logs and traces\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eServer setup: How are we collecting and shipping data?\u003c/h2\u003e\n\u003cp\u003eWe use the \u003ca href=\"https://www.elastic.co/guide/en/fleet/current/index.html\"\u003eElastic Agent\u003c/a\u003e to ship our system and application logs, system metrics, docker (podman) container metrics, and packet data. We’ll also use it to run \u003ca href=\"https://www.elastic.co/guide/en/kibana/master/osquery.html\"\u003eOsquery\u003c/a\u003e and our \u003ca href=\"https://www.elastic.co/endpoint-security/\"\u003eendpoint security integration\u003c/a\u003e with malware protections enabled.\u003c/p\u003e\n\u003cp\u003eOur vulnerable Java application[\u003ca href=\"https://github.com/christophetd/log4shell-vulnerable-app\"\u003e1\u003c/a\u003e] will be instrumented with the Elastic Java APM Agent.\u003c/p\u003e\n\u003cp\u003eElastic Agent and the Java APM agent are both connected to an Elastic cluster running on our \u003ca href=\"https://www.elastic.co/cloud/\"\u003eElasticsearch Service\u003c/a\u003e\u003c/p\u003eGuides are available for \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/java/current/setup.html\"\u003eAPM\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/guide/en/fleet/current/elastic-agent-installation.html\"\u003eElastic Agent\u003c/a\u003e."}],"_metadata":{"uid":"csd64563293251520c"}}},{"image":{"image":{"uid":"bltc2665e28dde7dc32","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:27:31.220Z","updated_at":"2022-01-13T17:27:31.220Z","content_type":"image/png","file_size":"126302","filename":"1-image.png","title":"1-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.188Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc2665e28dde7dc32/61e0610314ef402247ceb9cb/1-image.png"},"_metadata":{"uid":"csce9c0658b0f30325"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs84b0687acce12d6c"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eScenario: Application exploited\u003c/h2\u003e\n\u003cp\u003eLet’s walk through a hypothetical, but very real, situation many organizations went through. As the news of Log4Shell began to emerge, our vulnerable application was exposed and, unfortunately, exploited. \u003c/p\u003e\n\u003cp\u003eWe’ll now assume the role of a security analyst team who has just noticed a few alerts fire in Elastic Security. At this point, they do not know it is a Log4Shell exploit attempt — they will use the data and views available to them to investigate and get to the root cause.\u003c/p\u003e\u003ch2\u003eKicking off the investigation\u003c/h2\u003e\n\u003cp\u003eOur analyst team notices two alerts fire in very quick succession.\u003c/p\u003e"}],"_metadata":{"uid":"cs1401008ee1fb4edd"}}},{"image":{"image":{"uid":"bltd8f6dcc456ae5c65","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:28:00.353Z","updated_at":"2022-01-13T17:28:00.353Z","content_type":"image/png","file_size":"206278","filename":"2-image.png","title":"2-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.199Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd8f6dcc456ae5c65/61e06120bf9cb8387cc1e82d/2-image.png"},"_metadata":{"uid":"cs14813f4fac3bba8d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs08a80ac8aa108aba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe alerts state that a \u003cem\u003eSuspicious JAVA Child Process\u003c/em\u003e was detected, followed by a \u003cem\u003eMalware Prevention\u003c/em\u003e attempt.\u003c/p\u003e\n\u003cp\u003eUsing some of the views in Kibana, the analysts are able to get more details about the events in question.\u003c/p\u003e"}],"_metadata":{"uid":"cse8e3d1290f981848"}}},{"image":{"image":{"uid":"blt10235e2f1cf9a209","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:28:20.594Z","updated_at":"2022-01-13T17:28:20.594Z","content_type":"image/png","file_size":"357756","filename":"3-image.png","title":"3-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.208Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt10235e2f1cf9a209/61e06134bf9cb8387cc1e831/3-image.png"},"_metadata":{"uid":"cs7a71144d5fdd30f9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt58fb04c1e6fea6fe","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:28:31.048Z","updated_at":"2022-01-13T17:28:31.048Z","content_type":"image/png","file_size":"251425","filename":"4-image.png","title":"4-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.216Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt58fb04c1e6fea6fe/61e0613fdea73a236fc57b84/4-image.png"},"_metadata":{"uid":"cs15c0449a987bbc7b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb58a8ed99053d54e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOur analysts are able to see that java ran a process that eventually ended up downloading “Mozi.a” via wget. Thanks to the endpoint security integration, that file wasn’t able to run because it was determined to be malware.\u003c/p\u003e"}],"_metadata":{"uid":"cs7951e88127035a2d"}}},{"image":{"image":{"uid":"bltb20984f262de38e3","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:28:49.609Z","updated_at":"2022-01-13T17:28:49.609Z","content_type":"image/png","file_size":"243535","filename":"5-image.png","title":"5-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.228Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb20984f262de38e3/61e06151bf9cb8387cc1e835/5-image.png"},"_metadata":{"uid":"csaa084a919513b696"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csceaf85a1b23a88f8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBased on this knowledge, our analyst team determines that this is a true positive, and should be investigated further. \u003c/p\u003e\n\u003cp\u003eIn the Elastic Security overview page, they can see that a 0-day vulnerability in Log4j2 was recently announced and is actively being exploited.\u003c/p\u003e"}],"_metadata":{"uid":"csff241d900c871b07"}}},{"image":{"image":{"uid":"bltfd5c6543f9873969","created_by":"blt4349d9729d06d101","updated_by":"blt4349d9729d06d101","created_at":"2022-01-13T17:54:30.526Z","updated_at":"2022-01-13T17:54:30.526Z","content_type":"image/png","file_size":"1243099","filename":"image6log4jblog.png","title":"image6log4jblog.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.239Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfd5c6543f9873969/61e0675651bc1739fe79a103/image6log4jblog.png"},"_metadata":{"uid":"csafb5fdd0b9d25633"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0fddb46701b4a2fe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSince java was invoked to download and execute a malicious file, they decide to investigate further to see if that host in particular is running any vulnerable java applications.\u003c/p\u003e\n\u003cp\u003eUsing the Observability inventory view within Kibana, they check the processes currently running on the host and perform a search for “java.”\u003c/p\u003e"}],"_metadata":{"uid":"csd2e9040f9ce72e1b"}}},{"image":{"image":{"uid":"blt7631af4f9175891f","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:29:36.511Z","updated_at":"2022-01-13T17:29:36.511Z","content_type":"image/png","file_size":"542671","filename":"7-image.png","title":"7-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.249Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7631af4f9175891f/61e0618051bc1739fe79a0e1/7-image.png"},"_metadata":{"uid":"csb0229645490d395d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse857f50f059d9d27"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThey see a java process running with the same process id that was identified within the security alerts. However, they decide to dig a bit deeper to confirm that the vulnerable libraries are being used that are mentioned in the news feed. Using Osquery within the same view, they run a query to determine this, based on \u003ca href=\"https://blog.fleetdm.com/detect-log4j-with-osquery-and-fleet-e29c9de18ac9\"\u003ethe article\u003c/a\u003e they found shared by \u003ca href=\"https://fleetdm.com\"\u003efleetdm\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eWithin the Osquery results, they see that the java application in question is, in fact, using the Log4j2 library, as well as the JNDI lookup class:\u003c/p\u003e"}],"_metadata":{"uid":"cs0a28faae0019132d"}}},{"image":{"image":{"uid":"bltdc5714bd0277c799","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:30:02.465Z","updated_at":"2022-01-13T17:30:02.465Z","content_type":"image/png","file_size":"284041","filename":"8-image.png","title":"8-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.256Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc5714bd0277c799/61e0619a51bc1739fe79a0e5/8-image.png"},"_metadata":{"uid":"csdb2cdac8b6ce98c3"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse321c11e57a85adb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBased on these findings, they already had substantial evidence that the likelihood of Log4j2 being exploited in their application is very high. \u003c/p\u003e\n\u003cp\u003eDigging deeper, the analysts switch to the APM view in Kibana, checking the running services that are being instrumented. They notice the application in question based on the filtered host, the time range, and the service name they previously identified.\u003c/p\u003e"}],"_metadata":{"uid":"cscdff3ae867f09099"}}},{"image":{"image":{"uid":"blt915c692e616da5c9","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:30:23.103Z","updated_at":"2022-01-13T17:30:23.103Z","content_type":"image/png","file_size":"150695","filename":"9-image.png","title":"9-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.263Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt915c692e616da5c9/61e061af7c5435387a0c0ff5/9-image.png"},"_metadata":{"uid":"csbbc7357c3a9d01e5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs04b42bc073fa3360"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThey notice the following transaction was triggered for that service and click to discover more.\u003c/p\u003e"}],"_metadata":{"uid":"csd86d800716717690"}}},{"image":{"image":{"uid":"bltd261c16a21a796a4","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:30:39.143Z","updated_at":"2022-01-13T17:30:39.143Z","content_type":"image/png","file_size":"95897","filename":"10-image.png","title":"10-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.271Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd261c16a21a796a4/61e061bf8b16776549def57d/10-image.png"},"_metadata":{"uid":"csa133c0ef342ea309"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs685157b1057bfb37"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe transaction shows them that almost immediately after the request was received by the application, an additional GET request was made to another web server. Based on other traces for this application, this did not seem normal. They could see a backend service was added to their application service map for that time period. It was not present at any other time.\u003c/p\u003e"}],"_metadata":{"uid":"cs21cb5dd45721012e"}}},{"image":{"image":{"uid":"blt405ec542eaab10ea","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:31:45.397Z","updated_at":"2022-01-13T17:31:45.397Z","content_type":"image/png","file_size":"110689","filename":"11-image.png","title":"11-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.282Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt405ec542eaab10ea/61e06201ef206c6c5e494fe3/11-image.png"},"_metadata":{"uid":"csea4c7d753b976fb2"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"bltfa8aa7abb7c811fd","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:31:55.257Z","updated_at":"2022-01-13T17:31:55.257Z","content_type":"image/png","file_size":"891506","filename":"12-image.png","title":"12-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.293Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfa8aa7abb7c811fd/61e0620b14ef402247ceb9d1/12-image.png"},"_metadata":{"uid":"cs33fbf93f16f5d186"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs612cf052810ccd5c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAfter clicking on the first line in the trace, they view the metadata collected. They see a request header, “X-Api-Version,” was sent containing an unusual value, which also looked similar to requests seen in the news feed for Log4Shell:\u003c/p\u003e"}],"_metadata":{"uid":"cs1bf7407093899311"}}},{"image":{"image":{"uid":"blt9eced15eb785281c","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:32:13.785Z","updated_at":"2022-01-13T17:32:13.785Z","content_type":"image/png","file_size":"344547","filename":"13-image.png","title":"13-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.307Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9eced15eb785281c/61e0621d51bc1739fe79a0e9/13-image.png"},"_metadata":{"uid":"cs3c80c2ccf5f24352"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc1869a5938a8adef"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eClicking on the GET request in the transaction span, they see exactly what their application asked for in the request. They also see the stack trace that was generated.\u003c/p\u003e"}],"_metadata":{"uid":"cs148291a10647afce"}}},{"image":{"image":{"uid":"bltf7cdd2b534c97be7","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:32:38.739Z","updated_at":"2022-01-13T17:32:38.739Z","content_type":"image/png","file_size":"218972","filename":"14-image.png","title":"14-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.316Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf7cdd2b534c97be7/61e06236dbd06039fdcf89be/14-image.png"},"_metadata":{"uid":"csc6b13f166b3d0341"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt30087d0b20863b6b","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:33:11.233Z","updated_at":"2022-01-13T17:33:11.233Z","content_type":"image/png","file_size":"574609","filename":"15-image.png","title":"15-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.324Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt30087d0b20863b6b/61e062577c5435387a0c0ff9/15-image.png"},"_metadata":{"uid":"cse476bde40fae6aee"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc8fe3afa4c288d4a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOur analysts are able to observe that “ExploitAL8hS9wdf7.class” was downloaded via the java application from 10.88.0.1 on port 8888. From the stack trace, they see that the source was indeed the Log4j JNDI Manager lookup function.\u003c/p\u003e\n\u003cp\u003eThey also check for any application logs generated during this transaction, as their deployment also correlated logs and metrics.\u003c/p\u003e"}],"_metadata":{"uid":"cs13c3b7115d82e156"}}},{"image":{"image":{"uid":"bltb83d4b191bf24777","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:34:09.149Z","updated_at":"2022-01-13T17:34:09.149Z","content_type":"image/png","file_size":"168593","filename":"16-image.png","title":"16-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.331Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb83d4b191bf24777/61e0629114ef402247ceb9d9/16-image.png"},"_metadata":{"uid":"cs65907a6dbf2991cc"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs24f8326e5061c2cc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThey immediately notice that the same value they saw in the “X-Api-Version” request header was logged. Based on this, it seems like their application is logging this header by design. \u003c/p\u003e\n\u003cp\u003eThe contents of the header seem to be encoded with base64, so they decode the value:\u003c/p\u003e"}],"_metadata":{"uid":"cs03465c7f0103962a"}}},{"image":{"image":{"uid":"blt51d9f35981358c39","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-01-13T17:35:04.880Z","updated_at":"2022-01-13T17:35:04.880Z","content_type":"image/png","file_size":"102999","filename":"17-image.png","title":"17-image.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.338Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt51d9f35981358c39/61e062c8dea73a236fc57b8c/17-image.png"},"_metadata":{"uid":"cs4876037984bc5ed9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs861ea455d4b52872"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThey notice that the decoded contents are the same commands detected in the alerts they first began investigating in Elastic Security.\u003c/p\u003e\n\u003cp\u003eBased on all the above, they confirmed that their application seems to be vulnerable to Log4shell, and was indeed exploited.\u003c/p\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\n\u003cp\u003eAs security analysts, sometimes we forget the opportunity available to us at the intersection of Observability and Security. Observability data, even when we remember to use it, is usually available in a different system and not easily accessible.\u003c/p\u003e\n\u003cp\u003eHopefully, this blog has allowed you to understand the value of having security and observability data within the same platform. At Elastic, we know that it’s not always possible to instrument applications at this level. It’s not a trivial task. We’re working hard to address this and provide ways to allow organizations to be able to get this level of insight easily.\u003c/p\u003e\n\u003cp\u003eCheck out \u003ca href=\"https://www.youtube.com/watch?v=FO3jjKG6RiE\"\u003ea live recorded version\u003c/a\u003e of this investigation, as well as other details on Log4Shell and how it impacts Elastic products.\u003c/p\u003e\u003cbr\u003e\u003cbr\u003e\u003cbr\u003e\u003ch2\u003eReference material\u003c/h2\u003e\n\u003cp\u003e\u003ca href=\"https://www.lunasec.io/docs/blog/log4j-zero-day/\"\u003ehttps://www.lunasec.io/docs/blog/log4j-zero-day/\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://www.tenable.com/blog/cve-2021-44228-proof-of-concept-for-critical-apache-log4j-remote-code-execution-vulnerability\"\u003ehttps://www.tenable.com/blog/cve-2021-44228-proof-of-concept-for-critical-apache-log4j-remote-code-execution-vulnerability\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://www.crowdstrike.com/blog/log4j2-vulnerability-analysis-and-mitigation-recommendations/\"\u003ehttps://www.crowdstrike.com/blog/log4j2-vulnerability-analysis-and-mitigation-recommendations/\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://mbechler.github.io/2021/12/10/PSA_Log4Shell_JNDI_Injection/\"\u003ehttps://mbechler.github.io/2021/12/10/PSA_Log4Shell_JNDI_Injection/\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://www.greynoise.io/viz/query/?gnql=CVE-2021-44228\"\u003ehttps://www.greynoise.io/viz/query/?gnql=CVE-2021-44228\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://logging.apache.org/log4j/2.x/security.html#\"\u003ehttps://logging.apache.org/log4j/2.x/security.html#\u003c/a\u003e\u003c/p\u003e\u003cbr\u003e[1] The application used is a slightly modified version of \u003ca href=\"https://github.com/christophetd/log4shell-vulnerable-app\"\u003ehttps://github.com/christophetd/log4shell-vulnerable-app\u003c/a\u003e"}],"_metadata":{"uid":"csc7912a1e1104658f"}}}],"publish_date":"2022-01-13T21:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Investigate Log4Shell exploits with Elastic Security and Observability","seo_description_l10n":"As news of Log4shell emerged, security teams all around the globe scrambled to detect, mitigate and contain the vulnerability. This blog highlights how teams can use the Elastic Search platform to detect Log4shell exploit attempts.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blta5708fce04036d59","created_by":"blt4349d9729d06d101","updated_by":"blt4349d9729d06d101","created_at":"2021-12-20T20:50:12.662Z","updated_at":"2021-12-20T20:50:12.662Z","content_type":"image/png","file_size":"69276","filename":"log4jsecurityblog.png","title":"log4jsecurityblog.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-13T18:16:28.347Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta5708fce04036d59/61c0ec843d2b1760404ed2f4/log4jsecurityblog.png"},"title":"Investigate Log4Shell exploits with Elastic Security and Observability","title_l10n":"Investigate Log4Shell exploits with Elastic Security and Observability","updated_at":"2025-03-28T17:20:22.982Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/investigate-log4shell-exploits-with-elastic-security-and-observability","publish_details":{"time":"2025-03-28T17:20:28.688Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt53b99db0c7d6fc1d","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Explore the MSHTML exploitation chain from phishing through the loading of a popular information stealer, FORMBOOK. Additionally, we’ll uncover campaign testing infrastructure through a tradecraft oversight.","author":["bltc1a27bf09861513f"],"category":["bltb79594af7c5b4199"],"created_at":"2022-01-12T22:36:49.292Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2d5d377f7bb9b5ab"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe wanted to call out some great \u003ca href=\"https://news.sophos.com/en-us/2021/12/21/attackers-test-cab-less-40444-exploit-in-a-dry-run/\"\u003eadjacent research\u003c/a\u003e from the team at Sophoslabs Uncut that was released on December 21, 2021. Research groups frequently analyze similar (or in this case, identical) campaigns through their own unique lens. This is fantastic for the security community, as the campaign gets more eyes and different perspectives applied towards the same problem.\u003c/p\u003e\n\u003cp\u003eElastic researches exploits, vulnerabilities, and threats on an ongoing basis. Recently, we \u003ca href=\"https://elastic.github.io/security-research/intelligence/2022/01/01.formbook-adopts-cabless-approach/article/\"\u003epublished research\u003c/a\u003e that covers the FORMBOOK campaign that steals information through a phishing campaign and takes advantage of the MSHTML exploit chain. While researching the FORMBOOK campaign, the Elastic Security Intelligence \u0026 Analytics team found campaign phases as well as shared infrastructure through a tradecraft oversight. This allowed the different phases to be associated and show how the campaign evolved over time.\u003c/p\u003e\n\u003cp\u003eOn September 7, 2021, Microsoft confirmed a \u003ca href=\"https://nvd.nist.gov/vuln/detail/CVE-2021-40444\"\u003evulnerability\u003c/a\u003e for the browser rendering engine used in several applications such as those within the Microsoft Office suite. Within three days [\u003ca href=\"https://twitter.com/vxunderground/status/1436326057179860992?s=20\"\u003e1\u003c/a\u003e] [\u003ca href=\"https://github.com/lockedbyte/CVE-2021-40444\"\u003e2\u003c/a\u003e], proof-of-concept code was released, highlighting the maturity of the exploit development ecosystem and underscoring the importance of proactive threat hunting and patch management strategies.\u003c/p\u003e\n\u003cp\u003eIn a nutshell, the research shows the following:\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe speed at which vulnerability PoC’s are being released highlights the need to leverage threat hunting to identify post-exploitation events before patches can be applied\u003c/li\u003e\u003cli\u003eA FORMBOOK campaign was observed combining infrastructure that allowed testing and production phases to be linked together\u003c/li\u003e\u003cli\u003ePatching for the MSHTML exploit appears to be effective as the campaign shifted from attempting to use the exploit to a traditional phishing malware-attachment approach\u003c/li\u003e\u003cli\u003eThe campaign required a multi-process attack chain to load a DLL file onto victim systems\u003c/li\u003e\u003c/ul\u003e\u003cbr\u003e\u003cp\u003eThe \u003ca href=\"https://elastic.github.io/security-research/intelligence/2022/01/01.formbook-adopts-cabless-approach/article/\"\u003eElastic research\u003c/a\u003e on this campaign is comprehensive and includes a full overview and analysis, including information on testing infrastructure and the production phase. Elastic also shares how you can detect and defend \u003ca href=\"https://elastic.github.io/security-research/intelligence/2022/01/01.formbook-adopts-cabless-approach/article/\"\u003eagainst specific indicators \u003c/a\u003eof this campaign, along with associated indicators of compromise. \u003c/p\u003e\n\u003cp\u003eThis situation is developing as more research about FORMBOOK and its impact is still being identified. This campaign is in the early stages, so expect us to post more on this topic as we uncover the proper cybersecurity measures to take to protect your organization. \u003c/p\u003eIn the meantime, you can try Elastic Security with a free \u003ca href=\"https://cloud.elastic.co/registration?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=trail\"\u003e14-day trial of Elastic Cloud\u003c/a\u003e. Or \u003ca href=\"https://www.elastic.co/downloads/?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=download\"\u003edownload\u003c/a\u003e the self-managed version of the Elastic Stack for free."}],"_metadata":{"uid":"csc07f8c7f96e2e03e"}}}],"publish_date":"2022-01-24T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Protecting against CAB-less 40444 FORMBOOK information-stealing campaign","seo_description_l10n":"Explore the MSHTML exploitation chain from phishing through the loading of a popular information stealer. Additionally, we’ll uncover campaign testing infrastructure through a tradecraft oversight.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt741994bc79ce7bd9","created_by":"bltb93267ccd58e6ba5","updated_by":"bltb93267ccd58e6ba5","created_at":"2021-08-20T15:10:55.026Z","updated_at":"2021-08-20T15:10:55.026Z","content_type":"image/png","file_size":"103114","filename":"blog-security-laptop-720x420.png","title":"blog-security-laptop-720x420.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-08-20T15:11:00.220Z","user":"bltb93267ccd58e6ba5"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt741994bc79ce7bd9/611fc5ff6768907ea9764dba/blog-security-laptop-720x420.png"},"title":"Identifying exploits and adversary tradecraft of FORMBOOK information-stealing campaign","title_l10n":"Identifying exploits and adversary tradecraft of FORMBOOK information-stealing campaign","updated_at":"2025-03-28T17:19:56.931Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/identifying-exploits-and-adversary-tradecraft-of-formbook-information-stealing-campaign","publish_details":{"time":"2025-03-28T17:20:01.542Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt80ef6177b84d92c2","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog, we walk users through identifying beaconing malware in their environment using our beaconing identification framework.","author":["bltc909a862477f6ea3","blt99cfdb037f677a86","blta95689a58b2be971"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-12-16T23:00:07.218Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1e8af300a7861024"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe early stages of an intrusion usually include initial access, execution, persistence, and command-and-control (C2) beaconing. When structured threats use zero-days, these first two stages are often not detected. It can often be challenging and time-consuming to identify persistence mechanisms left by an advanced adversary as we saw in the \u003ca href=\"https://www.elastic.co/blog/elastic-security-provides-free-and-open-protections-for-sunburst\"\u003e2020 SUNBURST supply chain compromise\u003c/a\u003e. Could we then have detected SUNBURST in the initial hours or days by finding its C2 beacon?\u003c/p\u003e\u003cp\u003eThe potential for beaconing detection is that it can serve as an early warning system and help discover novel persistence mechanisms in the initial hours or days after execution. This allows defenders to disrupt or evict the threat actor before they can achieve their objectives. So, while we are not quite \"left of boom\" by detecting C2 beaconing, we can make a big difference in the outcome of the attack by reducing its overall impact.\u003c/p\u003e\u003cp\u003eIn this blog, we talk about a beaconing identification framework that we built using Painless and aggregations in the Elastic Stack. The framework can not only help threat hunters and analysts monitor network traffic for beaconing activity, but also provides useful indicators of compromise (IoCs) for them to start an investigation with. If you don’t have an Elastic Cloud cluster but would like to try out our beaconing identification framework, you can start a \u003ca href=\"https://cloud.elastic.co/registration\"\u003efree 14-day trial\u003c/a\u003e of Elastic Cloud.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eBeaconing — A primer\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eAn enterprise's defense is only as good as its firewalls, antivirus, endpoint detection and intrusion detection capabilities, and SOC (Security Operations Center) — which consists of analysts, engineers, operators administrators, etc. who work round the clock to keep the organization secure. Malware however, enters enterprises in many different ways and uses a variety of techniques to go undetected. An increasingly common method being used by adversaries nowadays to evade detection is to use C2 beaconing as a part of their attack chain, given that it allows them to blend into networks like a normal user.\u003c/p\u003e\u003cp\u003eIn networking, beaconing is a term used to describe a continuous cadence of communication between two systems. In the context of malware, beaconing is when malware periodically calls out to the attacker's C2 server to get further instructions on tasks to perform on the victim machine. The frequency at which the malware checks in and the methods used for the communications are configured by the attacker. Some of the common protocols used for C2 are HTTP/S, DNS, SSH, and SMTP, as well as common cloud services like Google, Twitter, Dropbox, etc. Using common protocols and services for C2 allows adversaries to masquerade as normal network traffic and hence evade firewalls.\u003c/p\u003e\u003cp\u003eWhile on the surface beaconing can appear similar to normal network traffic, it has some unique traits with respect to timing and packet size, which can be modeled using standard statistical and signal processing techniques.\u003c/p\u003e\u003cp\u003eBelow is an example of a Koadic C2 beacon, which serves the malicious payload using the DLL host process. As you can see, the payload beacons consistently at an interval of 10 minutes, and the source, as well as destination packet sizes, are almost identical.\u003c/p\u003e"}],"_metadata":{"uid":"cs83591b1e1b180d8f"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt3cf9ad051f23a469","ACL":{},"content_type":"image/png","created_at":"2021-12-16T22:52:34.157Z","created_by":"bltc87e8bcd2aefc255","file_size":"148583","filename":"1-koadic-beacon.png","parent_uid":null,"tags":[],"title":"1-koadic-beacon.png","updated_at":"2021-12-16T22:52:34.157Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3cf9ad051f23a469/61bbc332c52c5b292ce23623/1-koadic-beacon.png"},"_metadata":{"uid":"cs60209f0e1fadf3f5"},"caption_l10n":"Example of a Koadic C2 beacon","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa9f51e6c83bfe1ca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt might seem like a trivial task to catch C2 beaconing if all beacons were as neatly structured and predictable as the above. All one would have to look for is periodicity and consistency in packet sizes. However, malware these days is not as straightforward.\u003c/p\u003e"}],"_metadata":{"uid":"cs0968029198d33dad"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt6daaebfe0c310780","ACL":{},"content_type":"image/png","created_at":"2021-12-16T22:53:06.807Z","created_by":"bltc87e8bcd2aefc255","file_size":"130814","filename":"2-emotet-beacon.png","parent_uid":null,"tags":[],"title":"2-emotet-beacon.png","updated_at":"2021-12-16T22:53:06.807Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6daaebfe0c310780/61bbc352f8d92f2155890bae/2-emotet-beacon.png"},"_metadata":{"uid":"csa2528e41738fe23e"},"caption_l10n":"Example of an Emotet beacon","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs93e82f707682873d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eMost sophisticated malware nowadays adds a \"jitter\" or randomness to the beacon interval, making the signal more difficult to detect. Some malware authors also use longer beacon intervals. The beaconing identification framework we propose accounts for some of these elusive modifications to traditional beaconing behavior.\u003c/p\u003e\u003cstrong\u003e\u003ch2\u003eOur approach\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eWe’ve discussed a bit about the why and what — in this section we dig deeper into how we identify beaconing traffic. Before we begin, it is important to note that beaconing is merely a communication characteristic. It is neither good nor evil by definition. While it is true that malware heavily relies on beaconing nowadays, a lot of legitimate software also exhibits beaconing behaviour.\u003c/p\u003e\u003cp\u003eWhile we have made efforts to reduce false positives, this framework should be looked at as a means for beaconing identification to help reduce the search space for a threat hunt, not as a means for detection. That said, indicators produced by this framework, when combined with other IoCs, can potentially be used to detect on malicious activity.\u003c/p\u003e\u003cp\u003eThe beacons we are interested in comprise traffic from a single running process on a particular host machine to one or more external IPs. Given that the malware can have both short (order of seconds) and long (order of hours or days) check-in intervals, we will restrict our attention to a time window that works reasonably for both and attempt to answer the question: “What is beaconing in my environment right now or recently?” We have also parameterized the inputs to the framework to allow users to configure important settings like time window, etc. More on this in upcoming sections.\u003c/p\u003e\u003cp\u003eWhen dealing with large data sets, such as network data for an enterprise, you need to think carefully about what you can measure, which allows you to scale effectively. Scaling has several facets, but for our purposes, we have the following requirements: \u003c/p\u003e\u003col\u003e\u003cli\u003eWork can be parallelised over different shards of data stored on different machines\u003c/li\u003e\u003cli\u003eThe amount of data that needs to move around to compute what is needed must be kept manageable. \u003c/li\u003e\u003c/ol\u003e\u003cp\u003eMultiple approaches have been suggested for detecting beaconing characteristics, but not all of them satisfy these constraints. For example, a popular choice for detecting beacon timing characteristics is to measure the interval between events. This proves to be too inefficient to use on large datasets because the events can't be processed across multiple shards.\u003c/p\u003e\u003cp\u003eDriven by the need to scale, we chose to detect beaconing by bucketing the data in the time window to be analyzed. We gather the event count and average bytes sent and received in each bucket. These statistics can be computed in MapReduce fashion and values from different shards can be combined at the coordinating node of an Elasticsearch query.\u003c/p\u003e\u003cp\u003eFurthermore, by controlling the ratio between the bucket and window lengths, the data we pass per running process has predictable memory consumption, which is important for system stability. The whole process is illustrated diagrammatically below:\u003c/p\u003e"}],"_metadata":{"uid":"cs7b51d549ce13c72b"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt637220fb9bd76515","ACL":{},"content_type":"image/png","created_at":"2021-12-16T22:53:52.228Z","created_by":"bltc87e8bcd2aefc255","file_size":"255057","filename":"3-bucketing-data.png","parent_uid":null,"tags":[],"title":"3-bucketing-data.png","updated_at":"2021-12-16T22:53:52.228Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt637220fb9bd76515/61bbc380d628d527ff44068c/3-bucketing-data.png"},"_metadata":{"uid":"csb2a57f8d6bd3760e"},"caption_l10n":"Bucketing data for analysis","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdb5575dd4d432110"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eA key attribute of beaconing traffic is it often has similar netflow bytes for the majority of its communication. If we average the bytes over all the events that fall in a single bucket, the average for different buckets will in fact be even more similar. This is just the law of large numbers in action. A good way to measure similarity of several positive numbers (in our case these are average bucket netflow bytes) is using a statistic called the \u003ca href=\"https://en.wikipedia.org/wiki/Coefficient_of_variation\"\u003ecoefficient of variation\u003c/a\u003e (COV). This captures the average relative difference between the values and their mean. Because this is a relative value, a COV closer to 0 implies that values are tightly clustered around their mean.\u003c/p\u003e\n\u003cp\u003eWe also found that occasional spikes in the netflow bytes in some beacons were inflating the COV statistic. In order to rectify this, we simply discarded low and high percentile values when computing the COV, which is a standard technique for creating a robust statistic. We threshold the value of this statistic to be significantly less than one to detect this characteristic of beacons.\u003c/p\u003e\n\u003cp\u003eFor periodicity, we observed that signals displayed one of two characteristics when we viewed the bucket counts. If the period was less than the time bucket length (i.e. high frequency beacons), then the count showed little variation from bucket to bucket. If the period was longer than the time bucket length (i.e. low frequency beacons), then the signal had high autocorrelation. Let's discuss these in detail.\u003c/p\u003e\n\u003cp\u003eTo test for high frequency beacons, we use a statistic called \u003ca href=\"https://en.wikipedia.org/wiki/Index_of_dispersion\"\u003erelative variance\u003c/a\u003e (RV). The rate of many naturally occurring phenomena are well described by a \u003ca href=\"https://en.wikipedia.org/wiki/Poisson_distribution#Occurrence_and_applications\"\u003ePoisson distribution\u003c/a\u003e. The reason for this is that if events arrive randomly at a constant average rate and the occurrence of one event doesn’t affect the chance of others occurring, then their count in a fixed time interval must be Poisson distributed.\u003c/p\u003e\n\u003cp\u003eJust to underline this point, it doesn’t matter the underlying mechanisms for that random delay between events (making a coffee, waiting for your software to build, etc.)— if those properties hold, their rate distribution is always the same. Therefore, we expect that the bucket counts to be Poisson distributed for much of the traffic in our network, but not for beacons, which are much more regular. A feature of the Poisson distribution is that its variance is equal to its average, i.e. its RV is 1. Loosely, this means that if the RV of our bucket counts is closer to 0, the signal is more regular than a Poisson process.\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"https://en.wikipedia.org/wiki/Autocorrelation\"\u003eAutocorrelation\u003c/a\u003e is a useful statistic for understanding when a time series repeats itself. The basic idea behind autocorrelation is to compare the time series values to themselves after shifting them in time. Specifically, it is the covariance between the two sets of values (which is larger when they are more similar), normalized by dividing it by the square root of the variances of the two sets, which measures how much the values vary among themselves.\u003c/p\u003e\n\u003cp\u003eThis process is illustrated schematically below. We apply this to the time series comprising the bucket counts: if the signal is periodic then the time bucketed counts must also repeat themselves. The nice thing about autocorrelation from our perspective is that it is capable of detecting any periodic pattern. For example, the events don’t need to be regularly spaced but might repeat like two events occurring close to one another in time, followed by a long gap and so on.\u003c/p\u003e"}],"_metadata":{"uid":"csd267b637695db3f1"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt4120b5263fcc3275","ACL":{},"content_type":"image/png","created_at":"2021-12-16T22:54:25.426Z","created_by":"bltc87e8bcd2aefc255","file_size":"181062","filename":"4-diagramming-representation.png","parent_uid":null,"tags":[],"title":"4-diagramming-representation.png","updated_at":"2021-12-16T22:54:25.426Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4120b5263fcc3275/61bbc3a1c9ed2d27fb59ea77/4-diagramming-representation.png"},"_metadata":{"uid":"cs29c5ab29fd21047b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs07af511b7121651e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe don’t know the shift beforehand that will maximize the similarity between the two sets of values, so we search over all shifts for the maximum. This, in effect, is the period of the data — the closer its autocorrelation is to one, the closer the time series is to being truly periodic. We threshold the autocorrelation close to one to test for low frequency beacons.\u003c/p\u003e\u003cp\u003eFinally, we noted that most beaconing malware these days incorporates jitter. How does autocorrelation deal with this? Well first off, autocorrelation isn’t a binary measure — it is a sliding scale: the closer the value is to 1 the more similar the two sets of values are to one another. Even if they are not identical but similar it can still be close to one. In fact, we can do better than this by modelling how random jitter affects autocorrelation and undoing its effect. Provided the jitter isn’t too large, the process to do this turns out to be about as complex as just finding the maximum autocorrelation.\u003c/p\u003e\u003cp\u003eIn our implementation, we’ve made the percentage configurable, although one would always use a small-ish percentage to avoid flagging too much traffic as periodic. If you'd like to dig into the gory details of our implementation, all the artifacts are available as a GitHub \u003ca href=\"https://github.com/elastic/detection-rules/releases/tag/ML-Beaconing-20211216-1\"\u003erelease\u003c/a\u003e in our detection rules repository. \u003c/p\u003e\u003cstrong\u003e\u003ch2\u003eHow do we do this using Elasticsearch?\u003c/h2\u003e\u003c/strong\u003e\u003cp\u003eElasticsearch has some very powerful tools for ad hoc data analysis. The \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-aggregations-metrics-scripted-metric-aggregation.html\"\u003escripted metric aggregation\u003c/a\u003e is one of them. The nice thing about this aggregation is that it allows you to write custom Painless scripts to derive different metrics about your data. We used the aggregation to script out the beaconing tests.\u003c/p\u003e\u003cp\u003eIn a typical environment, the cardinality of the distinct processes running across endpoints is rather high. Trying to run an aggregation that partitions by every running process is therefore not feasible. This is where another feature of the Elastic Stack comes in handy. A \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/transforms.html\"\u003etransform\u003c/a\u003e is a complex aggregation which paginates through all your data and writes results to a destination index.\u003c/p\u003e\u003cp\u003eThere are various basic operations available in transforms, one of them being partitioning data at scale. In our case, we partitioned our network event logs by host and process name and ran our scripted metric aggregation against each host-process name pair. The transform also writes out various beaconing related indicators and statistics. A sample document from the resulting destination index is as follows:\u003c/p\u003e"}],"_metadata":{"uid":"cs5b950397b2c62b09"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt018aa108edab2cdf","ACL":{},"content_type":"image/png","created_at":"2021-12-16T22:55:15.604Z","created_by":"bltc87e8bcd2aefc255","file_size":"277524","filename":"5-sample-beaconing.png","parent_uid":null,"tags":[],"title":"5-sample-beaconing.png","updated_at":"2021-12-16T22:55:15.604Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt018aa108edab2cdf/61bbc3d3c52c5b292ce2362b/5-sample-beaconing.png"},"_metadata":{"uid":"csc89451f665d8fa93"},"caption_l10n":"Sample document produced by the beaconing transform","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs557c60046d3352d3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs you can see, the document contains valuable beaconing-related information about the process. First off, the \u003ccode\u003ebeacon_stats.is_beaconing\u003c/code\u003e indicator says whether or not we found the process to be beaconing. If it is, as in the case above, the document will also contain important metadata, such as the frequency of the beacon. The indicator \u003ccode\u003ebeacon_stats.periodic\u003c/code\u003e says whether or not the signal is a low-frequency beacon, while the indicator \u003ccode\u003ebeacon_stats.low_count_variation\u003c/code\u003e indicates whether or not it is a high-frequency beacon.\u003c/p\u003e\n\u003cp\u003eFurthermore, the indicators \u003ccode\u003ebeacon_stats.low_source_bytes_variation\u003c/code\u003e and \u003ccode\u003elow_destination_bytes_variation\u003c/code\u003e indicate whether or not the source and destination bytes sent during the beaconing communication were more or less uniform. Finally, you will also notice the \u003ccode\u003ebeaconing_score\u003c/code\u003e indicator, which is a value from 1-3, representing the number of beaconing tests satisfied by the process for that time period. \u003c/p\u003e\n\u003cp\u003eWriting such metadata out to an index also means that you can search for different facets of beaconing software in your environment. For example, if you want to search for low frequency beaconing processes in your environment, you would query for documents where the \u003ccode\u003ebeacon_stats.periodic\u003c/code\u003e indicator is \u003ccode\u003etrue\u003c/code\u003e and \u003ccode\u003ebeacon_stats.low_count_variation\u003c/code\u003e is \u003ccode\u003efalse\u003c/code\u003e. You can also build second order analytics on top of the indexed data, such as using \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/xpack-ml-anomalies.html\"\u003eanomaly detection\u003c/a\u003e to find rare beaconing processes, or using a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-aggregations-bucket-significantterms-aggregation.html\"\u003esignificant terms aggregation\u003c/a\u003e to detect lateral movement of beaconing malware in your environment. \u003c/p\u003e\n\u003cp\u003eFinally, we’ve included several dashboards for your threat hunters and analysts to use for monitoring beaconing activity in your environment. These can be found in the \u003ca href=\"https://github.com/elastic/detection-rules/releases/tag/ML-Beaconing-20211216-1\"\u003erelease package\u003c/a\u003e as well.\u003c/p\u003e\u003cstrong\u003e\u003ch2\u003eTuning parameters and filtering\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eAdvanced users can also tune important parameters to the scripted metric aggregation in the transforms, like jitter percentage, time window, etc. If you'd like to change the default parameters, all you would need to do is delete the transform, change the parameters, and restart it. The parameters you can tune are as follows:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ccode\u003enumber_buckets_in_range\u003c/code\u003e: The number of time buckets we split the time window into. You need enough to ensure you get reasonable estimates for the various statistics, but too many means the transform will use more memory and compute.\u003c/li\u003e\u003cli\u003e\u003ccode\u003etime_bucket_length\u003c/code\u003e: The length of each time bucket. This controls the time window, so the larger this value the longer the time window. You might set this longer if you want to check for very low frequency beacons. \u003c/li\u003e\u003cli\u003e\u003ccode\u003enumber_destination_ips\u003c/code\u003e: The number of destination IPs to gather in the results. Setting this higher increases the transform resource usage.\u003c/li\u003e\u003cli\u003e\u003ccode\u003emax_beaconing_bytes_cov\u003c/code\u003e: The maximum coefficient of variation in the payload bytes for the low source and destination bytes variance test. Setting this higher will increase the chance of detecting traffic as beaconing, so would likely increase \u003ca href=\"https://en.wikipedia.org/wiki/Precision_and_recall\"\u003erecall\u003c/a\u003e for malicious C2 beacons. However, it will also reduce the \u003ca href=\"https://en.wikipedia.org/wiki/Precision_and_recall\"\u003eprecision\u003c/a\u003e of the test.\u003c/li\u003e\u003cli\u003e\u003ccode\u003emax_beaconing_count_rv\u003c/code\u003e: The maximum relative variance in the bucket counts for the high frequency beacon test. As with \u003ccode\u003emax_beaconing_bytes_cov\u003c/code\u003e, we suggest tuning this parameter based on the kind of tradeoff you want between precision and recall.\u003c/li\u003e\u003cli\u003e\u003ccode\u003etruncate_at\u003c/code\u003e: The lower and upper fraction of bucket values discarded when computing \u003ccode\u003emax_beaconing_bytes_cov\u003c/code\u003e and \u003ccode\u003emax_beaconing_count_rv\u003c/code\u003e. This allows you to ignore occasional changes in traffic patterns. However, if you retain too small a fraction of the data, these tests will be unreliable.\u003c/li\u003e\u003cli\u003e\u003ccode\u003emin_beaconing_count_autocovariance\u003c/code\u003e: The minimum autocorrelation of the signal for the low frequency beacon test. Lowering this value will likely result in an increase in recall for malicious C2 beacons, at the cost of reduced test precision. As with some of the other parameters mentioned above, we suggest tuning this parameter based on the kind of tradeoff you want between precision and recall.\u003c/li\u003e\u003cli\u003e\u003ccode\u003emax_jitter\u003c/code\u003e: The maximum amount by which we assume that a periodic beacon is jittered, as a fraction of its period.\u003c/li\u003e\u003c/ul\u003e\n\u003cp\u003eYou can also make changes to the transform query. We currently look for beaconing activity over a 6h time range, but you can change this to a different time range. As mentioned previously, beaconing is not a characteristic specific to malware and a lot of legitimate, benign processes also exhibit beaconing-like activity.\u003c/p\u003e\n\u003cp\u003eIn order to curb the false positive rate, we have included a starter list of filters in the transform query to exclude known benign beaconing processes that we observed during testing, and a list of IPs that fall into two categories:\u003c/p\u003e\u003col\u003e\u003cli\u003eThe source IP is local and the destination is remote\u003c/li\u003e\u003cli\u003eFor certain Microsoft processes, the destination IP is in a Microsoft block\u003c/li\u003e\u003c/ol\u003e\n\u003cp\u003eYou can add to this list based on what you see in your environment. \u003c/p\u003e\u003cstrong\u003e\u003ch2\u003eEvaluation\u003c/h2\u003e\u003c/strong\u003e\n\u003cp\u003eIn order to measure the effectiveness of our framework as a reduced search space for beaconing activity, we wanted to test two aspects:\u003c/p\u003e\u003col\u003e\u003cli\u003eDoes the framework flag actual malicious beaconing activity?\u003c/li\u003e\u003cli\u003eBy how much does the framework reduce the search space for malicious beacons? \u003c/li\u003e\u003c/ol\u003e\n\u003cp\u003eIn order to test the performance on malware beacons, we ran the transform on some synthetic data as well as some real malware! We set up test ranges for Emotet and Koadic, and also tested it on NOBELIUM logs we had from several months ago. The results from the real malware tests are worth mentioning here.\u003c/p\u003e"}],"_metadata":{"uid":"cse885ceb23168abc4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltaaf3b71ba1b9f1ec","ACL":{},"content_type":"image/png","created_at":"2022-01-06T17:38:10.819Z","created_by":"bltc87e8bcd2aefc255","file_size":"327252","filename":"6-beaconing-metadata.png","parent_uid":null,"tags":[],"title":"6-beaconing-metadata.png","updated_at":"2022-01-06T17:38:10.819Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaaf3b71ba1b9f1ec/61d7290214048326a8098bc8/6-beaconing-metadata.png"},"_metadata":{"uid":"cs2f55d59826a9ebf0"},"caption_l10n":"Beaconing metadata for NOBELIUM","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csec0ec02b19b28c7d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor NOBELIUM, the beaconing transform catches the offending process, \u003ccode\u003erundll32.exe\u003c/code\u003e, as well as the two destination IPs, 192.99.221.77 and 83.171.237.173, which were among the main IoCs for NOBELIUM.\u003c/p\u003e\n\u003cp\u003eFor Koadic and Emotet as well, the transform was able to flag the process as well as the known destination IPs on which the test C2 listeners were running. The characteristics of each of the beacons were different. For example, Koadic was a straightforward, high-frequency beacon that satisfied all the beaconing criteria being checked in the transform i.e. periodicity, as well as low variation of source and destination bytes. Emotet was slightly trickier since it was a low frequency beacon with a high jitter percentage. But we were able to detect it due to the low variation in the source bytes of the beacon.\u003c/p\u003e\n\u003cp\u003eTo test the amount of reduction in search space, we ran the transform over three weeks on an internal cluster that was receiving network event logs from ~ 2k hosts during the testing period. We measured the reduction in search space based on the number of network event log messages, processes, and hosts an analyst or threat hunter would have to sift through before and after running the transform, in order to identify malicious beacons. The numbers are as follows:\u003c/p\u003e"}],"_metadata":{"uid":"cs190ce8bb1307ec4f"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt625476054e233d2c","ACL":{},"content_type":"image/png","created_at":"2022-01-06T17:40:09.917Z","created_by":"bltc87e8bcd2aefc255","file_size":"79456","filename":"7-search-space-reduction.png","parent_uid":null,"tags":[],"title":"7-search-space-reduction.png","updated_at":"2022-01-06T17:40:09.917Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt625476054e233d2c/61d729798d6b4f214f46bfaf/7-search-space-reduction.png"},"_metadata":{"uid":"cs7b6f849e3df3fa74"},"caption_l10n":"Search space reduction metrics as a result of the beaconing transform","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf7ce8b964aaba748"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhile the reduction in search space is obvious, another point to note is the scale of data that the transforms are able to churn through comfortably, which becomes an important aspect to consider, especially in production environments. Additionally, we have also released dashboards (available in the \u003ca href=\"https://github.com/elastic/detection-rules/releases/tag/ML-Beaconing-20211216-1\"\u003erelease package\u003c/a\u003e), which track metrics like prevalence of the beaconing processes, etc. that can help make informed decisions about further filtering of the search space. \u003c/p\u003e\n\u003cp\u003eWhile the released dashboards, and the statistics in the above table are based on cases where the \u003ccode\u003ebeacon_stats.is_beaconing\u003c/code\u003e indicator is \u003ccode\u003etrue\u003c/code\u003e i.e. beacons that satisfy either of the beaconing tests, threat hunters may want to further streamline their search by starting with the most obvious beaconing-like cases and then moving on to the less obvious ones. This can be done by filtering and searching by the \u003ccode\u003ebeacon_stats.beaconing_score\u003c/code\u003e indicator instead of \u003ccode\u003ebeacon_stats.is_beaconing\u003c/code\u003e, where a score of 3 indicates a typical beacon (satisfying tests for periodicity as well as low variation in packet bytes), and score of 1 indicates a less obvious beacon (satisfying only one of the three tests).\u003c/p\u003e\n\u003cp\u003eFor reference, we observed the following on our internal cluster:\u003c/p\u003e"}],"_metadata":{"uid":"cs31c18693929b64ec"}}},{"image":{"image":{"_version":3,"is_dir":false,"uid":"blt4691beda742c2543","ACL":{},"content_type":"image/png","created_at":"2022-01-06T17:43:53.565Z","created_by":"bltc87e8bcd2aefc255","description":"","file_size":"95258","filename":"Screen_Shot_2022-01-06_at_4.36.40_PM.png","parent_uid":null,"tags":[],"title":"8-streamlining-threat-hunting.png","updated_at":"2022-01-06T23:37:31.650Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4691beda742c2543/61d77d3b0d4d1813c7f4611c/Screen_Shot_2022-01-06_at_4.36.40_PM.png"},"_metadata":{"uid":"csaf4d8c673662a96b"},"caption_l10n":"Streamlining your threat hunt using the Beaconing Score indicator","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2252421542161151"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eWhat's next\u003c/h2\u003e\n\u003cp\u003eWe’d love for you to try out our beaconing identification framework and give us feedback as we work on improving it. If you run into any issues during the process, please reach out to us on our \u003ca href=\"https://ela.st/slack\"\u003ecommunity Slack channel\u003c/a\u003e, \u003ca href=\"https://discuss.elastic.co/c/security\"\u003ediscussion forums\u003c/a\u003e, or even our \u003ca href=\"https://github.com/elastic/detection-rules\"\u003eopen detections repository\u003c/a\u003e. Stay tuned for Part 2 of this blog, where we’ll cover going from identifying beaconing activity to actually detecting on malicious beacons!\u003c/p\u003eTry out our beaconing identification framework with a \u003ca href=\"https://cloud.elastic.co/registration\"\u003efree 14-day trial\u003c/a\u003e of Elastic Cloud."}],"_metadata":{"uid":"cs0a006b5dc03e3a47"}}}],"publish_date":"2022-01-13T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Identifying beaconing malware using Elastic","seo_description_l10n":"In this blog, we walk users through identifying beaconing malware in their environment using our beaconing identification framework.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt187bba664e7f49b2","ACL":{},"content_type":"image/png","created_at":"2022-01-26T14:52:00.647Z","created_by":"blt4349d9729d06d101","file_size":"36981","filename":"blog-thumbnail-securitymaze.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumbnail-securitymaze.png","updated_at":"2022-02-11T21:02:23.280Z","updated_by":"blt4349d9729d06d101","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt187bba664e7f49b2/61f16010fb66f771578d73fb/blog-thumbnail-securitymaze.png"},"title":"Identifying beaconing malware using Elastic","title_l10n":"Identifying beaconing malware using Elastic","updated_at":"2025-03-28T17:19:34.130Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/identifying-beaconing-malware-using-elastic","publish_details":{"time":"2025-03-28T17:19:38.962Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2daf81890b72a9c7","_version":41,"locale":"en-us","ACL":{},"abstract_l10n":"Unify all of your Kubernetes metrics, log, and trace data on a single platform and dashboard, Elastic. From the infrastructure to the application layer Elastic Observability makes it easier for you to understand how your cluster is performing.","author":["blt19aa6eaf05f480b6"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-10-24T16:26:05.501Z","created_by":"blt469f34057b68c377","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs38f12a0dfb7ad801"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs an operations engineer (SRE, IT manager, DevOps), you’re always struggling with how to manage technology and data sprawl. Kubernetes is becoming increasingly pervasive and a majority of these deployments will be in Amazon Elastic Kubernetes Service (EKS), Google Kubernetes Engine (GKE), or Azure Kubernetes Service (AKS). Some of you may be on a single cloud while others will have the added burden of managing clusters on multiple Kubernetes cloud services. In addition to cloud provider complexity, you also have to manage hundreds of deployed services generating more and more observability and telemetry data.\u003c/p\u003e\n\u003cp\u003eThe day-to-day operations of understanding the status and health of your Kubernetes clusters and applications running on them, through the logs, metrics, and traces they generate, will likely be your biggest challenge. But as an operations engineer you will need all of that important data to help prevent, predict, and remediate issues. And you certainly don’t need that volume of metrics, logs and traces spread across multiple tools when you need to visualize and analyze Kubernetes telemetry data for troubleshooting and support.\u003c/p\u003e\n\u003cp\u003eElastic Observability helps manage the sprawl of Kubernetes metrics and logs by providing extensive and centralized observability capabilities beyond just the logging that we are known for. Elastic Observability provides you with granular insights and context into the behavior of your Kubernetes clusters along with the applications running on them by unifying all of your metrics, log, and trace data through OpenTelemetry and APM agents.\u003c/p\u003e\n\u003cp\u003eRegardless of the cluster location (EKS, GKE, AKS, self-managed) or application, \u003ca href=\"/what-is/kubernetes-monitoring\" target=\"_self\"\u003eKubernetes monitoring\u003c/a\u003e is made simple with Elastic Observability. All of the node, pod, container, application, and infrastructure (AWS, GCP, Azure) metrics, infrastructure and application logs, along with application traces are available in Elastic Observability.\u003c/p\u003e\n\u003cp\u003eIn this blog we will show:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eHow \u003ca href=\"http://cloud.elastic.co\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e can aggregate and ingest metrics and log data through the Elastic Agent (easily deployed on your cluster as a DaemonSet) to retrieve logs and metrics from the host (system metrics, container stats) along with logs from all services running on top of Kubernetes.\u003c/li\u003e\n \u003cli\u003eHow Elastic Observability can bring a unified telemetry experience (logs, metrics,traces) across all your Kubernetes cluster components (pods, nodes, services, namespaces, and more).\u003c/li\u003e\n\u003c/ul\u003e"}],"_metadata":{"uid":"cs4aa09c1fdada6917"}}},{"image":{"image":{"uid":"bltce62a2d5f717362e","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-25T15:31:42.158Z","updated_at":"2022-10-25T15:31:42.158Z","content_type":"image/png","file_size":"61580","filename":"ManagingKubernetes-ElasticAgentIntegration-1.png","title":"ManagingKubernetes-ElasticAgentIntegration-1.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:53.981Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltce62a2d5f717362e/6358015e1012fd7700082e36/ManagingKubernetes-ElasticAgentIntegration-1.png"},"_metadata":{"uid":"cs33a3a28d05bb5bf2"},"caption_l10n":"Elastic Agent with Kubernetes Integration","alt_text_l10n":"Elastic Agent with Kubernetes Integration","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"Prerequisites and config","_metadata":{"uid":"cs6995396d6c696743"},"header_style":"H2","paragraph_l10n":"\n\u003cp\u003eIf you plan on following this blog, here are some of the components and details we used to set up this demonstration:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eEnsure you have an account on \u003ca href=\"http://cloud.elastic.co\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e and a deployed stack (\u003ca href=\"https://www.elastic.co/guide/en/elastic-stack/current/installing-elastic-stack.html\" target=\"_self\"\u003esee instructions here\u003c/a\u003e).\u003c/li\u003e\n \u003cli\u003eWhile we used GKE, you can use any location for your Kubernetes cluster.\u003c/li\u003e\n \u003cli\u003eWe used a variant of the ever so popular \u003ca href=\"https://github.com/GoogleCloudPlatform/microservices-demo\" target=\"_self\"\u003eHipsterShop\u003c/a\u003e demo application. It was originally written by Google to showcase Kubernetes across a multitude of variants available such as the \u003ca href=\"https://github.com/open-telemetry/opentelemetry-demo\" target=\"_self\"\u003eOpenTelemetry Demo App\u003c/a\u003e. To use the app, please go \u003ca href=\"https://github.com/bshetti/opentelemetry-microservices-demo/tree/main/deploy-with-collector-k8s\" target=\"_self\"\u003ehere\u003c/a\u003e and follow the instructions to deploy. You don’t need to deploy otelcollector for Kubernetes metrics to flow — we will cover this below.\u003c/li\u003e\n \u003cli\u003eElastic supports native ingest from Prometheus and FluentD, but in this blog, we are showing a direct ingest from Kubernetes cluster via Elastic Agent. There will be a follow-up blog showing how Elastic can also pull in telemetry from Prometheus or FluentD/bit.\u003c/li\u003e\n\u003c/ul\u003e\n\u003ch2\u003eWhat can you observe and analyze with Elastic?\u003c/h2\u003e\n\u003cp\u003eBefore we walk through the steps on getting Elastic set up to ingest and visualize Kubernetes cluster metrics and logs, let’s take a sneak peek at Elastic’s helpful dashboards.\u003c/p\u003e\n\u003cp\u003eAs we noted, we ran a variant of HipsterShop on GKE and deployed Elastic Agents with Kubernetes integration as a DaemonSet on the GKE cluster. Upon deployment of the agents, Elastic starts ingesting metrics from the Kubernetes cluster (specifically from kube-state-metrics) and additionally Elastic will pull all log information from the cluster.\u003c/p\u003e\n\n"},{"title_l10n":"Visualizing Kubernetes metrics on Elastic Observability","_metadata":{"uid":"cs4fce6eb81f491026"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eHere are a few Kubernetes dashboards that will be available out of the box (OOTB) on Elastic Observability.\u003c/p\u003e"}],"_metadata":{"uid":"cs99aa5fe8a735988a"}}},{"image":{"image":{"uid":"blt887d8ef07d307362","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-25T15:31:57.235Z","updated_at":"2022-10-25T15:31:57.235Z","content_type":"image/png","file_size":"191522","filename":"ManagingKubernetes-HipsterShopMetrics-2.png","title":"ManagingKubernetes-HipsterShopMetrics-2.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.010Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt887d8ef07d307362/6358016d7e515b5598d02ec6/ManagingKubernetes-HipsterShopMetrics-2.png"},"_metadata":{"uid":"cs86d8f5371048dd24"},"caption_l10n":"HipsterShop cluster metrics on Elastic Kubernetes overview dashboard ","alt_text_l10n":"HipsterShop cluster metrics on Elastic Kubernetes overview dashboard ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"image":{"image":{"uid":"blt214caae71b183c68","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:20:18.621Z","updated_at":"2022-10-27T20:20:18.621Z","content_type":"image/png","file_size":"377803","filename":"ManagingKubernetes-HipsterShopDashboard-3.png","title":"ManagingKubernetes-HipsterShopDashboard-3.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.035Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt214caae71b183c68/635ae802dc15735d5cd05e9a/ManagingKubernetes-HipsterShopDashboard-3.png"},"_metadata":{"uid":"csde5f3b262da7a191"},"caption_l10n":"HipsterShop default namespace pod dashboard on Elastic Observability","alt_text_l10n":"HipsterShop default namespace pod dashboard on Elastic Observability","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa89e770e8d9ee7bf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn addition to the cluster overview dashboard and pod dashboard, Elastic has several useful OOTB dashboards:\u003c/p\u003e\u003cul\u003e\u003cli\u003eKubernetes overview dashboard (see above)\u003c/li\u003e\u003cli\u003eKubernetes pod dashboard (see above)\u003c/li\u003e\u003cli\u003eKubernetes nodes dashboard\u003c/li\u003e\u003cli\u003eKubernetes deployments dashboard\u003c/li\u003e\u003cli\u003eKubernetes DaemonSets dashboard\u003c/li\u003e\u003cli\u003eKubernetes StatefulSets dashboards\u003c/li\u003e\u003cli\u003eKubernetes CronJob \u0026amp; Jobs dashboards\u003c/li\u003e\u003cli\u003eKubernetes services dashboards\u003c/li\u003e\u003cli\u003eMore being added regularly\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAdditionally, you can either customize these dashboards or build out your own.\u003c/p\u003e"},{"title_l10n":"Working with logs on Elastic Observability","_metadata":{"uid":"cs88b098d86b83c0c0"},"header_style":"H3","paragraph_l10n":""}],"_metadata":{"uid":"cs6d75c765e3246575"}}},{"image":{"image":{"uid":"blt8e1ec8f6ac8b30b3","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:12:43.733Z","updated_at":"2022-10-27T20:12:43.733Z","content_type":"image/png","file_size":"418686","filename":"ManagingKubernetes-Logging-4.png","title":"ManagingKubernetes-Logging-4.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.067Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8e1ec8f6ac8b30b3/635ae63be079731084befcf3/ManagingKubernetes-Logging-4.png"},"_metadata":{"uid":"csb3ccae5b74516b9f"},"caption_l10n":"Kubernetes container logs and Elastic Agent logs","alt_text_l10n":"Kubernetes container logs and Elastic Agent logs","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5dea0aee159d5dee"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs you can see from the screens above, not only can I get Kubernetes cluster metrics, but also all the Kubernetes logs simply by using the Elastic Agent in my Kubernetes cluster.\u003c/p\u003e"},{"title_l10n":"Prevent, predict, and remediate issues","_metadata":{"uid":"csa2008ae90dd56369"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eIn addition to helping manage metrics and logs, Elastic can help you detect and predict anomalies across your cluster telemetry. Simply turn on Machine Learning in Elastic against your data and watch it help you enhance your analysis work. As you can see below, Elastic is not only a unified observability location for your Kubernetes cluster logs and metrics, but it also provides extensive true machine learning capabilities to enhance your analysis and management.\u003c/p\u003e"}],"_metadata":{"uid":"csd45e29e97552940b"}}},{"image":{"image":{"uid":"bltc7cc079bb922a6a5","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:13:50.892Z","updated_at":"2022-10-27T20:13:50.892Z","content_type":"image/png","file_size":"186665","filename":"ManagingKubernetes-AnomalyDetection-5.png","title":"ManagingKubernetes-AnomalyDetection-5.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.091Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc7cc079bb922a6a5/635ae67e57082b10e8174b2f/ManagingKubernetes-AnomalyDetection-5.png"},"_metadata":{"uid":"cs0fb3f72365df1390"},"caption_l10n":"Anomaly detection across logs on Elastic Observability","alt_text_l10n":"Anomaly detection across logs on Elastic Observability","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"image":{"image":{"uid":"bltdea4ab144dd9094c","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-25T18:21:43.608Z","updated_at":"2022-10-25T18:21:43.608Z","content_type":"image/png","file_size":"217047","filename":"ManagingKubernetes-PodIssues-6.png","title":"ManagingKubernetes-PodIssues-6.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.114Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdea4ab144dd9094c/63582937eb4a5478dab71967/ManagingKubernetes-PodIssues-6.png"},"_metadata":{"uid":"csd47fe2bc78759718"},"caption_l10n":"Analyzing issues on a Kubernetes pod with Elastic Observability ","alt_text_l10n":"Analyzing issues on a Kubernetes pod with Elastic Observability ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9327f166a642a8bf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn the top graph, you see anomaly detection across logs and it shows something potentially wrong in the September 21 to 23 time period. Dig into the details on the bottom chart by analyzing a single kubernetes.pod.cpu.usage.node metric showing cpu issues early in September and again, later on in the month. You can do more complicated analyses on your cluster telemetry with Machine Learning using multi-metric analysis (versus the single metric issue I am showing above) along with population analysis.\u003c/p\u003e\n\u003cp\u003eElastic gives you better machine learning capabilities to enhance your analysis of Kubernetes cluster telemetry. In the next section, let’s walk through how easy it is to get your telemetry data into Elastic.\u003c/p\u003e\n\n"},{"title_l10n":"Setting it all up","_metadata":{"uid":"csee2bf2b94fd5c60f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLet’s walk through the details of how to get metrics, logs, and traces into Elastic from a HipsterShop application deployed on GKE.\u003c/p\u003e\n\u003cp\u003eFirst, pick your favorite version of Hipstershop — as we noted above, we used a variant of the \u003ca href=\"https://github.com/open-telemetry/opentelemetry-demo\" target=\"_self\"\u003eOpenTelemetry-Demo\u003c/a\u003e because it already has OTel. We slimmed it down for this blog, however (fewer services with some varied languages).\u003c/p\u003e\n"},{"title_l10n":"Step 0: Get an account on Elastic Cloud","_metadata":{"uid":"cs6d8e34b39a7ab2b3"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eFollow the instructions to \u003ca href=\"https://cloud.elastic.co/registration?fromURI=%2Fhome\" target=\"_self\"\u003eget started on Elastic Cloud\u003c/a\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"cs473b7a9ed880d206"}}},{"image":{"image":{"uid":"blt75e885c80b3ecaa2","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-24T13:21:29.749Z","updated_at":"2022-10-24T13:21:29.749Z","content_type":"image/png","file_size":"34780","filename":"ManagingKubernetes-FreeElasticCloud-7.png","title":"ManagingKubernetes-FreeElasticCloud-7.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.138Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt75e885c80b3ecaa2/635691591012fd7700081c6e/ManagingKubernetes-FreeElasticCloud-7.png"},"_metadata":{"uid":"cs3e36208b03b11aa2"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Step 1: Get a Kubernetes cluster and load your Kubernetes app into your cluster","_metadata":{"uid":"cs532635d8e4486cc2"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eGet your app on a Kubernetes cluster in your Cloud service of choice or local Kubernetes platform. Once your app is up on Kubernetes, you should have the following pods (or some variant) running on the \u003cspan data-type='inlineCode'\u003edefault\u003c/span\u003e namespace.\u003c/p\u003e"}],"_metadata":{"uid":"cs01f032326880b913"}}},{"code":{"code":"NAME READY STATUS RESTARTS AGE\nadservice-8694798b7b-jbfxt 1/1 Running 0 4d3h\ncartservice-67b598697c-hfsxv 1/1 Running 0 4d3h\ncheckoutservice-994ddc4c4-p9p2s 1/1 Running 0 4d3h\ncurrencyservice-574f65d7f8-zc4bn 1/1 Running 0 4d3h\nemailservice-6db78645b5-ppmdk 1/1 Running 0 4d3h\nfrontend-5778bfc56d-jjfxg 1/1 Running 0 4d3h\njaeger-686c775fbd-7d45d 1/1 Running 0 4d3h\nloadgenerator-c8f76d8db-gvrp7 1/1 Running 0 4d3h\notelcollector-5b87f4f484-4wbwn 1/1 Running 0 4d3h\npaymentservice-6888bb469c-nblqj 1/1 Running 0 4d3h\nproductcatalogservice-66478c4b4-ff5qm 1/1 Running 0 4d3h\nrecommendationservice-648978746-8bzxc 1/1 Running 0 4d3h\nredis-cart-96d48485f-gpgxd 1/1 Running 0 4d3h\nshippingservice-67fddb767f-cq97d 1/1 Running 0 4d3h","_metadata":{"uid":"csc41513058ada8933"}}},{"title_text":{"title_text":[{"title_l10n":"Step 2: Turn on \u003ca href=\"https://github.com/kubernetes/kube-state-metrics\" target=\"_self\"\u003ekube-state-metrics\u003c/a\u003e","_metadata":{"uid":"cs85b901c4c20ef037"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eNext you will need to turn on \u003ca href=\"https://github.com/kubernetes/kube-state-metrics\" target=\"_self\"\u003ekube-state-metrics\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eFirst:\u003c/p\u003e"}],"_metadata":{"uid":"cs07e1cbbcef92d293"}}},{"code":{"code":"git clone https://github.com/kubernetes/kube-state-metrics.git","_metadata":{"uid":"cs23f630d2eb2129c5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs13a23d118b8315c1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNext, in the kube-state-metrics directory under the examples directory, just apply the standard config.\u003c/p\u003e"}],"_metadata":{"uid":"cs62860c51339dd50d"}}},{"code":{"code":"kubectl apply -f ./standard","_metadata":{"uid":"cs99649bbb65ed214e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7d12941d6b9b1f61"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis will turn on kube-state-metrics, and you should see a pod similar to this running in \u003cspan data-type='inlineCode'\u003ekube-system\u003c/span\u003e namespace.\u003c/p\u003e"}],"_metadata":{"uid":"cs609cb460cce6b7c7"}}},{"code":{"code":"kube-state-metrics-5f9dc77c66-qjprz 1/1 Running 0 4d4h","_metadata":{"uid":"cs741920e897242b11"}}},{"title_text":{"title_text":[{"title_l10n":"Step 3: Install the Elastic Agent with Kubernetes integration","_metadata":{"uid":"cs3f85bc071eab6ea5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eAdd Kubernetes Integration:\u003c/strong\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cimg src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5a3ae745e98b9e37/635691670a58db35cbdbc0f6/ManagingKubernetes-Addk8sButton-8.png\"/\u003e\u003c/li\u003e\u003cli\u003eIn Elastic, go to integrations and select the Kubernetes Integration, and select to Add Kubernetes.\u003c/li\u003e\u003cli\u003eSelect a name for the Kubernetes integration.\u003c/li\u003e\u003cli\u003eTurn on \u003cspan data-type='inlineCode'\u003ekube-state-metrics\u003c/span\u003e in the configuration screen.\u003c/li\u003e\u003cli\u003eGive the configuration a name in the \u003cspan data-type='inlineCode'\u003enew-agent-policy-name\u003c/span\u003e text box.\u003c/li\u003e\u003cli\u003eSave the configuration. The integration with a policy is now created.\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eYou can read up on the agent policies and how they are used on the Elastic Agent \u003ca href=\"https://www.elastic.co/guide/en/fleet/current/agent-policy.html\" target=\"_self\"\u003ehere\u003c/a\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"cs03380db6618bdcba"}}},{"image":{"image":{"uid":"bltf87bc18a319c01fa","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:15:27.047Z","updated_at":"2022-10-27T20:15:27.047Z","content_type":"image/png","file_size":"164087","filename":"ManagingKubernetes-K8sIntegration-9.png","title":"ManagingKubernetes-K8sIntegration-9.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.165Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf87bc18a319c01fa/635ae6df1fb4e757e1110e96/ManagingKubernetes-K8sIntegration-9.png"},"_metadata":{"uid":"cs231f5b0eb428229a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"image":{"image":{"uid":"bltd5d9f1b51d094f55","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:15:46.032Z","updated_at":"2022-10-27T20:15:46.032Z","content_type":"image/png","file_size":"257086","filename":"ManagingKubernetes-FleetManagement-10.png","title":"ManagingKubernetes-FleetManagement-10.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.191Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd5d9f1b51d094f55/635ae6f2e079731084befd11/ManagingKubernetes-FleetManagement-10.png"},"_metadata":{"uid":"cscdca24893f401893"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5e0e362977d4dafe"},"header_style":"H2","paragraph_l10n":"\u003col\u003e\u003cli\u003eAdd Kubernetes integration.\u003c/li\u003e\u003cli\u003eSelect the policy you just created in the second.\u003c/li\u003e\u003cli\u003eIn the third step of Add Agent instructions, copy and paste or download the manifest.\u003c/li\u003e\u003cli\u003eAdd manifest to the shell where you have \u003cspan data-type='inlineCode'\u003ekubectl\u003c/span\u003e running, save it as \u003cspan data-type='inlineCode'\u003eelastic-agent-managed-kubernetes.yaml\u003c/span\u003e, and run the following command.\u003c/li\u003e\u003c/ol\u003e"}],"_metadata":{"uid":"cs854494792043aaa1"}}},{"code":{"code":"kubectl apply -f elastic-agent-managed-kubernetes.yaml","_metadata":{"uid":"cs4e7d8e0dbafe2d0d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8e834bb25ef282ce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou should see a number of agents come up as part of a DaemonSet in \u003cspan data-type='inlineCode'\u003ekube-system\u003c/span\u003e namespace.\u003c/p\u003e"}],"_metadata":{"uid":"cs44f8afd6eddb8d49"}}},{"code":{"code":"NAME READY STATUS RESTARTS AGE\nelastic-agent-qr6hj 1/1 Running 0 4d7h\nelastic-agent-sctmz 1/1 Running 0 4d7h\nelastic-agent-x6zkw 1/1 Running 0 4d7h\nelastic-agent-zc64h 1/1 Running 0 4d7h","_metadata":{"uid":"cs12f025e5096b0e10"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5a1217bb61e79984"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn my cluster, I have four nodes and four elastic-agents started as part of the DaemonSet.\u003c/p\u003e"},{"title_l10n":"Step 4: Look at Elastic out of the box dashboards (OOTB) for Kubernetes metrics and start discovering Kubernetes logs","_metadata":{"uid":"cs6186f455f175978a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eThat is it. You should see metrics flowing into all the dashboards. To view logs for specific pods, simply go into Discover in Kibana and search for a specific pod name.\u003c/p\u003e"}],"_metadata":{"uid":"cs2a0c925769ed7504"}}},{"image":{"image":{"uid":"blt887d8ef07d307362","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-25T15:31:57.235Z","updated_at":"2022-10-25T15:31:57.235Z","content_type":"image/png","file_size":"191522","filename":"ManagingKubernetes-HipsterShopMetrics-2.png","title":"ManagingKubernetes-HipsterShopMetrics-2.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.010Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt887d8ef07d307362/6358016d7e515b5598d02ec6/ManagingKubernetes-HipsterShopMetrics-2.png"},"_metadata":{"uid":"csa8349be3d014741c"},"caption_l10n":"HipsterShop cluster metrics on Elastic Kubernetes overview dashboard","alt_text_l10n":"HipsterShop cluster metrics on Elastic Kubernetes overview dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt214caae71b183c68","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:20:18.621Z","updated_at":"2022-10-27T20:20:18.621Z","content_type":"image/png","file_size":"377803","filename":"ManagingKubernetes-HipsterShopDashboard-3.png","title":"ManagingKubernetes-HipsterShopDashboard-3.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.035Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt214caae71b183c68/635ae802dc15735d5cd05e9a/ManagingKubernetes-HipsterShopDashboard-3.png"},"_metadata":{"uid":"cs98089015a23cd84e"},"caption_l10n":"Hipstershop default namespace pod dashboard on Elastic Observability","alt_text_l10n":"Hipstershop default namespace pod dashboard on Elastic Observability","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6359c296c8c2dd2e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAdditionally, you can browse all the pod logs directly in Elastic.\u003c/p\u003e"}],"_metadata":{"uid":"cs409fc85f468e73ee"}}},{"image":{"image":{"uid":"blte727271d2277b489","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:16:30.533Z","updated_at":"2022-10-27T20:16:30.533Z","content_type":"image/png","file_size":"725415","filename":"ManagingKurbenetes-PodLogs-11.png","title":"ManagingKurbenetes-PodLogs-11.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.217Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte727271d2277b489/635ae71e3bd922566d8d5ba7/ManagingKurbenetes-PodLogs-11.png"},"_metadata":{"uid":"cs45b3894f19a07452"},"caption_l10n":"frontendService and cartService logs","alt_text_l10n":"frontendService and cartService logs","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7d0acec67fa309f6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn the above example, I searched for frontendService and cartService logs.\u003c/p\u003e\n"},{"title_l10n":"Step 5: Bonus!","_metadata":{"uid":"cs412303701082f7aa"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eBecause we were using an OTel based application, Elastic can even pull in the application traces. But that is a discussion for another blog.\u003c/p\u003e\u003cp\u003eHere is a quick peek at what Hipster Shop’s traces for a front end transaction look like in Elastic Observability.\u003c/p\u003e"}],"_metadata":{"uid":"cs7702792a8070536e"}}},{"image":{"image":{"uid":"blt22f8bd674c6abd67","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-27T20:17:32.138Z","updated_at":"2022-10-27T20:17:32.138Z","content_type":"image/png","file_size":"163807","filename":"ManagingKubernetes-CheckOutTransaction-12.png","title":"ManagingKubernetes-CheckOutTransaction-12.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.243Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt22f8bd674c6abd67/635ae75c6eed4a5820f4af96/ManagingKubernetes-CheckOutTransaction-12.png"},"_metadata":{"uid":"csc0d73c002fedcd2a"},"caption_l10n":"Trace for Checkout transaction for HipsterShop","alt_text_l10n":"Trace for Checkout transaction for HipsterShop","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"Conclusion: Elastic Observability rocks for Kubernetes monitoring","_metadata":{"uid":"cs76b4dd3d5ac1cd6e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eI hope you’ve gotten an appreciation for how Elastic Observability can help you manage Kubernetes clusters along with the complexity of the metrics, log, and trace data it generates for even a simple deployment.\u003c/p\u003e\u003cp\u003eA quick recap of lessons and more specifically learned:\u003c/p\u003e\u003cul\u003e\u003cli\u003eHow \u003ca href=\"http://cloud.elastic.co\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e can aggregate and ingest telemetry data through the Elastic Agent, which is easily deployed on your cluster as a DaemonSet and retrieves metrics from the host, such as system metrics, container stats, and metrics from all services running on top of Kubernetes\u003c/li\u003e\u003cli\u003eShow what Elastic brings from a unified telemetry experience (Kubernenetes logs, metrics, traces) across all your Kubernetes cluster components (pods, nodes, services, any namespace, and more).\u003c/li\u003e\u003cli\u003eInterest in exploring Elastic’s ML capabilities which will reduce your \u003cstrong\u003eMTTHH \u003c/strong\u003e(mean time to happy hour)\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eReady to get started? \u003ca href=\"https://cloud.elastic.co/registration\" target=\"_self\"\u003eRegister\u003c/a\u003e and try out the features and capabilities I’ve outlined above.\u003c/p\u003e"}],"_metadata":{"uid":"cs162de4b0f728fb46"}}}],"publish_date":"2022-11-01","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"AWS","label_l10n":"AWS","keyword":"aws","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt5da20aee1a072f80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:30.685Z","updated_at":"2023-11-06T20:08:30.685Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:00:52.463Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt30356308fa9784a5","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-10-24T13:19:08.952Z","updated_at":"2022-10-24T13:19:08.952Z","content_type":"image/png","file_size":"38200","filename":"ManagingKubernetes-ElasticAgentIntegration-1.png","title":"ManagingKubernetes-ElasticAgentIntegration-1.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-01T15:45:54.270Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt30356308fa9784a5/635690ccb45ffc5dbc605ad3/ManagingKubernetes-ElasticAgentIntegration-1.png"},"title":"Managing your Kubernetes cluster with Elastic Observability","title_l10n":"Managing your Kubernetes cluster with Elastic Observability ","updated_at":"2025-03-28T17:19:08.311Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/kubernetes-cluster-metrics-logs-monitoring","publish_details":{"time":"2025-03-28T17:19:13.554Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt147856c2c61b7a59","_version":23,"locale":"en-us","ACL":{},"abstract_l10n":"We will use an official builder tool, elastic-package, to bootstrap a new integration in order to observe an unsupported product or service. We will configure it to collect available logs and metrics and run under the Elastic Agent.","author":["blt54b3d91f48035ccc"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-10-12T16:16:21.658Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs82ef73c2d9c19a2d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAt Elastic we use \u003ca href=\"https://www.elastic.co/blog/getting-started-with-elastic-package\" target=\"_self\"\u003eelastic-package\u003c/a\u003e on a daily basis to create and maintain Integrations. Today we’ll learn how to quickly bootstrap a new Elastic Integration using a built-in creator, and how to start observing the service.\u003c/p\u003e\n\u003cp\u003eElastic Integrations are a new way of using Elastic Agents to observe logs and metrics. By using Internet of Things smart devices, you can track data like electricity consumption, gas, or water usage in your household. However, there are countless IoT devices out there, and they all have proprietary apps or web pages to monitor data. What if you want to have a dashboard with all your IoT data in one place? That’s where Integrations come in.\u003c/p\u003e\n\u003cp\u003eSay you want to monitor your home’s water usage for leaks. An Elastic Integration makes this easy. Your IoT device has a REST endpoint with a data feed. By using an Elastic integration to create a smart pipeline to Kibana Alerts, you’ve got your service. Repeat as needed and you’ve got a dashboard to monitor your home. Further, with a small investment you can build IoT detectors on your own using any prototyping platform (for example Arduino) and basic electronic components (like water sensors).\u003c/p\u003e\n\u003cp\u003eThese Integrations don’t contain any Go code — all functionality is provided using YAML or JSON configuration. If writing configuration files sounds like an exhausting challenge, that’s where the built-in creator comes in, shortening the initial time for bootstrapping the package using an embedded package archetype.\u003c/p\u003e\n\u003cp\u003eIf you have never heard of Elastic Agent or Elastic Integrations and want to learn more before jumping in, \u003ca href=\"https://www.elastic.co/blog/elastic-agent-and-fleet-make-it-easier-to-integrate-your-systems-with-elastic\"\u003ethis blog post\u003c/a\u003e is a great place to start. Otherwise, let's dive in!\u003c/p\u003e\u003ch2\u003eReview observed service\u003c/h2\u003e\n\u003cp\u003eThe candidate for implementing a new package will be the IPFS Node application, a client to the decentralized peer-to-peer (P2P) network for storing and sharing data in a distributed file system. It uses content-addressing to uniquely identify each file. The application can run in both, daemon and console modes, and it exposes few network ports:\u003c/p\u003e\u003cul\u003e\u003cli\u003e4001 - default libp2p swarm port\u003c/li\u003e\u003cli\u003e5001 - API internal port, shouldn’t be exposed publicly\u003c/li\u003e\u003cli\u003e8080 - Gateway to serve content\u003c/li\u003e\u003c/ul\u003e\n\u003cp\u003eThe node application is also distributed as Docker image, which can be easily started:\u003c/p\u003e"}],"_metadata":{"uid":"csd60ae418d51ab3be"}}},{"code":{"code":"$ docker run --rm --name ipfs-node -p 127.0.0.1:5001:5001 ipfs/go-ipfs@sha256:f7e30972e35a839ea8ce00c060412face29aa31624fd2dc87a5e696f99835a91\n\nChanging user to ipfs\nipfs version 0.9.1\ngenerating ED25519 keypair...done\npeer identity: 12D3KooWR6NcsnsW7bzaMnfYWL9D8f411P351TnfTX2D9pxRY74t\ninitializing IPFS node at /data/ipfs\nto get started, enter:\n\n\tipfs cat /ipfs/QmQPeNsJPyVWPFDVHb77w8G42Fvo15z4bG2X8D2GhfbSXc/readme\n\nInitializing daemon...\ngo-ipfs version: 0.9.1-dc2715a\nRepo version: 11\nSystem version: amd64/linux\nGolang version: go1.15.2\n2021/09/27 13:01:00 failed to sufficiently increase receive buffer size (was: 208 kiB, wanted: 2048 kiB, got: 416 kiB). See https://github.com/lucas-clemente/quic-go/wiki/UDP-Receive-Buffer-Size for details.\nSwarm listening on /ip4/127.0.0.1/tcp/4001\nSwarm listening on /ip4/127.0.0.1/udp/4001/quic\nSwarm listening on /ip4/172.17.0.2/tcp/4001\nSwarm listening on /ip4/172.17.0.2/udp/4001/quic\nSwarm listening on /p2p-circuit\nSwarm announcing /ip4/127.0.0.1/tcp/4001\nSwarm announcing /ip4/127.0.0.1/udp/4001/quic\nSwarm announcing /ip4/172.17.0.2/tcp/4001\nSwarm announcing /ip4/172.17.0.2/udp/4001/quic\nAPI server listening on /ip4/0.0.0.0/tcp/5001\nWebUI: http://0.0.0.0:5001/webui\nGateway (readonly) server listening on /ip4/0.0.0.0/tcp/8080\nDaemon is ready","_metadata":{"uid":"cs67dd34c2156e8108"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs87b4d291eb684655"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this tutorial we will be interested in the API running on port 5001, which exposes following methods:\u003c/p\u003e\n\u003cul\u003e\u003cli\u003e\u003ccode\u003e/api/v0/stats/bw - get IPFS bandwidth information\u003c/code\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ccode\u003e/api/v0/repo/stat - get statistics for currently used repository\u003c/code\u003e\u003c/li\u003e\u003c/ul\u003e\n\n\u003cp\u003eBoth API methods respond to POST calls:\u003c/p\u003e"}],"_metadata":{"uid":"cs62966b7dcc86de0c"}}},{"code":{"code":"$ curl -X POST http://127.0.0.1:5001/api/v0/stats/bw\n{\"TotalIn\":18136337,\"TotalOut\":944694,\"RateIn\":34125.006805975005,\"RateOut\":4088.311294056906}\n\n$ curl -X POST http://127.0.0.1:5001/api/v0/repo/stat\n{\"RepoSize\":9321761,\"StorageMax\":10000000000,\"NumObjects\":95,\"RepoPath\":\"/data/ipfs\",\"Version\":\"fs-repo@11\"}","_metadata":{"uid":"cs39eaa5bb3d610991"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csccc9db1865dc9dd7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe goal of this exercise is to create an integration which scraps metrics from the described API and collects standard application logs from the ipfs-node.\n\u003c/p\u003e\u003ch2\u003eBootstrap new \"ipfs_node\" package\u003c/h2\u003e\n\u003cp\u003eLet's start with creating a new repository (or you can select your own place) to store the integration. Next, use the built-in creator and your new package:\u003c/p\u003e"}],"_metadata":{"uid":"cs7f7891b6bdae72bf"}}},{"code":{"code":"$ elastic-package create package\nCreate a new package\n? Package name: ipfs_node\n? Version: 0.0.1\n? Package title: IPFS Node\n? Description: Collect logs and metrics from IPFS node.\n? Categories: custom, network\n? Release: experimental\n? Kibana version constraint: ^7.15.0\n? Github owner: mtojek\nNew package has been created: ipfs_node\nDone","_metadata":{"uid":"csbd6265586dffd537"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs024a137f382e978c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe package has been created, but we also need three additional data streams - traffic (metrics), repository (metrics) and application (logs):\u003c/p\u003e"}],"_metadata":{"uid":"cs78ac66c90671cbb7"}}},{"code":{"code":"$ cd ipfs_node\n$ elastic-package create data-stream\nCreate a new data stream\n? Data stream name: traffic\n? Data stream title: Traffic\n? Type: metrics\nNew data stream has been created: traffic\nDone\n$ elastic-package create data-stream\nCreate a new data stream\n? Data stream name: repository\n? Data stream title: Repository\n? Type: metrics\nNew data stream has been created: repository\nDone\n$ elastic-package create data-stream\nCreate a new data stream\n? Data stream name: application\n? Data stream title: Application logs\n? Type: logs\nNew data stream has been created: application\nDone","_metadata":{"uid":"csf0b4a430b55323dd"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs350ec03e4da996a3"},"header_style":"H2","paragraph_l10n":"Once the creator finished its job, let’s check all files in the directory:"}],"_metadata":{"uid":"cs0736aa1601fbb7f8"}}},{"code":{"code":"$ tree\n.\n├── changelog.yml\n├── data_stream\n│ ├── application\n│ │ ├── agent\n│ │ │ └── stream\n│ │ │ └── stream.yml.hbs\n│ │ ├── elasticsearch\n│ │ │ └── ingest_pipeline\n│ │ │ └── default.yml\n│ │ ├── fields\n│ │ │ └── base-fields.yml\n│ │ └── manifest.yml\n│ ├── repository\n│ │ ├── agent\n│ │ │ └── stream\n│ │ │ └── stream.yml.hbs\n│ │ ├── fields\n│ │ │ └── base-fields.yml\n│ │ └── manifest.yml\n│ └── traffic\n│ ├── agent\n│ │ └── stream\n│ │ └── stream.yml.hbs\n│ ├── fields\n│ │ └── base-fields.yml\n│ └── manifest.yml\n├── docs\n│ └── README.md\n├── img\n│ ├── sample-logo.svg\n│ └── sample-screenshot.png\n└── manifest.yml\n\n17 directories, 15 files","_metadata":{"uid":"cs7fedd4611b759f44"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs34ba1f4608171ff9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe package root contains 3 different data streams (traffic, repository and application), a basic README file, a changelog file, and sample graphics (icon and screenshot). Every data stream contains a manifest, an agent's stream definition, field definitions and an optional stub for ingest pipeline.\u003c/p\u003e\u003ch2\u003eAdjust configuration of data streams\u003c/h2\u003e\n\u003cp\u003eNow it's time to fill all the templates. Let's modify the package manifest (manifest.yml) and replace default policy templates with following:\u003c/p\u003e"}],"_metadata":{"uid":"cs364bbaa77b105bb8"}}},{"code":{"code":"policy_templates:\n - name: application\n title: IPFS node logs and metrics\n description: Collect IPFS node logs and metrics\n inputs:\n - type: logfile\n title: Collect application logs\n description: Collecting application logs from IPFS node\n - type: http/metrics\n title: Collect application metrics\n description: Collecting repository and traffic metrics from IPFS node\n vars:\n - name: hosts\n type: text\n title: Hosts\n description: Base URL of the internal endpoint\n required: true\n default: http://localhost:5001","_metadata":{"uid":"cs2f179f0131951624"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs64098f7cc3bf1337"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe package manifest describes two kinds of inputs - \u003ccode\u003elogfile\u003c/code\u003e and \u003ccode\u003ehttp/metrics\u003c/code\u003e. The logfile input is a standard filebeat's input, which allows for reading entries from files, but HTTP metrics is a Beats module, which fetches data from external HTTP endpoints (it supports JSON format). In the package manifest there can be defined common variables, which apply to multiple data streams - in this case we can keep the base URL to the IPFS node.\u003c/p\u003e\n\u003cp\u003eLet's define data streams:\u003c/p\u003e\n\u003cul\u003e\u003cli\u003eapplication - read standard application logs\u003c/li\u003e\u003cli\u003erepository - read IPFS repository statistics\u003c/li\u003e\u003cli\u003etraffic - read bandwidth metrics for the node\u003c/li\u003e\u003c/ul\u003e\n\u003cp\u003e\u003cbr\u003eHere is the data stream manifest for \"application\" data stream:\u003c/p\u003e"}],"_metadata":{"uid":"csedf7a11e135973bc"}}},{"code":{"code":"title: \"Application logs\"\ntype: logs\nstreams:\n - input: logfile\n title: Standard logs\n description: Collect IPFS node application logs\n vars:\n - name: paths\n type: text\n title: Paths\n multi: true\n default:\n - /var/log/ipfs-node-*.log\n - /var/log/ipfs-debug-*.log","_metadata":{"uid":"cs20171e61eb813204"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs604d79a1450a4248"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt's relatively small and defines one variable - paths (location of log files). For the purpose of this exercise we will not introduce more variables and only focus on the basic lifecycle of an integration. Once you modified the \"application\" data stream manifest, adjust manifests for \"repository\" and \"traffic\".\u003c/p\u003e\n\u003cp\u003e\"Repository\" data stream manifest: \u003c/p\u003e"}],"_metadata":{"uid":"csd00f59ddada69c9e"}}},{"code":{"code":"title: \"Repository\"\ntype: metrics\nstreams:\n - input: http/metrics\n title: Repository metrics\n description: Collect repository metrics from IPFS node\n vars:\n - name: period\n type: text\n title: Period\n default: 10s","_metadata":{"uid":"cs3d2fdf3b69917a29"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs19d6ca79fd305043"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\"Traffic\" data stream manifest:\u003c/p\u003e"}],"_metadata":{"uid":"csf7960c77e4b1c4a8"}}},{"code":{"code":"title: \"Traffic\"\ntype: metrics\nstreams:\n - input: http/metrics\n title: Traffic metrics\n description: Collect bandwidth metrics from IPFS node\n vars:\n - name: period\n type: text\n title: Period\n default: 10s","_metadata":{"uid":"csce10fa735a130cf2"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0045e8789d970c6d"},"header_style":"H2","paragraph_l10n":"Both manifests define a single variable - period, which defines the delay between consecutive metrics fetch operations. All manifest files are used by Fleet UI (Kibana) to render configuration forms of the Integration:\n"}],"_metadata":{"uid":"csbcd68d4f9b8b5e78"}}},{"image":{"image":{"uid":"bltc2a5afbc3a75071b","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2021-10-13T22:30:12.483Z","updated_at":"2021-10-13T22:30:12.483Z","content_type":"image/png","file_size":"98511","filename":"elastic-package-integrations.1.png","title":"elastic-package-integrations.1.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-26T17:28:53.580Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc2a5afbc3a75071b/61675df419868352684e08f0/elastic-package-integrations.1.png"},"_metadata":{"uid":"cs0e2ed4780437ea2f"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8b182fb9f81afae5"},"header_style":"H2","paragraph_l10n":"Let's adjust the agent's stream configuration files. It's the configuration which is passed down to the Elastic Agent instance to reconfigure supervised \u003ccode\u003efilebeat\u003c/code\u003e and \u003ccode\u003emetricbeat\u003c/code\u003e processes. The agent stream for the \"application\" uses the standard file input:"}],"_metadata":{"uid":"cs8551684ec03a2a33"}}},{"code":{"code":"paths:\n{{#each paths as |path i|}}\n - {{path}}\n{{/each}}\nexclude_files: [\".gz$\"]\nprocessors:\n - add_locale: ~\n\nThe agent stream for the “repository” uses the HTTP module with enabled JSON metricset:\n\nmetricsets: [\"json\"]\nhosts:\n{{#each hosts}}\n - {{this}}/api/v0/repo/stat\n{{/each}}\nperiod: {{period}}\nmethod: \"POST\"\nnamespace: \"repository\"","_metadata":{"uid":"cse538e3c3903969ff"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs469c1fd361b16a9c"},"header_style":"H2","paragraph_l10n":"Similarly does the agent for “\"traffic\":"}],"_metadata":{"uid":"cseeb3bcbf6b2f3a5f"}}},{"code":{"code":"metricsets: [\"json\"]\nhosts:\n{{#each hosts}}\n - {{this}}/api/v0/stats/bw\n{{/each}}\nperiod: {{period}}\nmethod: \"POST\"\nnamespace: \"traffic\"","_metadata":{"uid":"csa0aad6cfc7098621"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs13f284d97ad81289"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe \"application\" data stream pushes logs to an \u003ca href=\"https://www.elastic.co/blog/should-i-use-logstash-or-elasticsearch-ingest-nodes\"\u003eingest pipeline\u003c/a\u003e which runs in Elasticsearch. It can transform logs in multiple ways - skip fields, add new fields, trim content, replace values conditionally, etc. For the purpose of this exercise we will not introduce a complex processing:\u003c/p\u003e\n\u003cp\u003edata_stream/application/elasticsearch/ingest_pipeline/default.yml\u003c/p\u003e"}],"_metadata":{"uid":"csb21ff5e519b514d9"}}},{"code":{"code":"---\ndescription: Pipeline for processing sample logs\nprocessors:\n - set:\n field: ecs.version\n value: '1.11.0'\n - trim:\n field: message\n - drop:\n description: 'Drop if the log message is empty'\n if: ctx.message == ''\non_failure:\n - set:\n field: error.message\n value: '{{ _ingest.on_failure_message }}'","_metadata":{"uid":"csfa4d9c5b69713dd3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs83de94d56caf36e3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe core package files are ready now, so it's a good moment to run few extra commands:\u003c/p\u003e\n\u003cp\u003e\u003ccode\u003eelastic-package format\u003c/code\u003e - to format the package source code\u003cbr\u003e\u003ccode\u003eelastic-package lint\u003c/code\u003e - to double-check if all files are inline with \u003ca href=\"https://github.com/elastic/package-spec\"\u003epackage-spec\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003ccode\u003eelastic-package build\u003c/code\u003e - to build the integration package (mind that this will create the build directory with a built package)\u003c/p\u003e\n\u003cp\u003eOnce every command passed successfully we can switch to testing. The elastic-package tool can boot up locally the Elastic stack for development and testing purposes. The stack consists of Docker containers for Elasticsearch, Kibana, Fleet Server and Elastic Agent. As all contantainers run in the same network, it's a good idea to run the IPFS node in a container belonging to the same Docker network.\u003c/p\u003e\n\u003cp\u003eCreate \u003ccode\u003e_dev/deploy/docker\u003c/code\u003e directory in the package root and add place following files:\u003c/p\u003e\n\u003cp\u003edocker-compose.yml\u003c/p\u003e"}],"_metadata":{"uid":"csc33002d4f05af27d"}}},{"code":{"code":"version: '2.3'\nservices:\n ipfs_node:\n build: .\n ports:\n - 5001\n volumes:\n - ${SERVICE_LOGS_DIR}:/var/log/ipfs","_metadata":{"uid":"csc737679629910681"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1000c7d536b2bd78"},"header_style":"H2","paragraph_l10n":"docker-entrypoint.sh"}],"_metadata":{"uid":"csa0e6986e7597703c"}}},{"code":{"code":"#!/bin/sh\n\n/usr/local/bin/start_ipfs daemon --migrate=true | tee /var/log/ipfs/ipfs-node-0.log","_metadata":{"uid":"cs6cd2388212687743"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8b6e21b51ec927cd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eDockerfile\u003c/p\u003e"}],"_metadata":{"uid":"cs7caac621ff554e17"}}},{"code":{"code":"FROM ipfs/go-ipfs@sha256:f7e30972e35a839ea8ce00c060412face29aa31624fd2dc87a5e696f99835a91\n\nRUN mkdir -p /var/log/ipfs\n\nADD docker-entrypoint.sh /\n\nENV IPFS_LOGGING \"info\"\n\nENTRYPOINT [\"/docker-entrypoint.sh\"]","_metadata":{"uid":"csbe1a2fdde3796d76"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2c545c0185eaecae"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe will use them in system tests to boot up an instance of an IPFS node in the Docker network and make it observable by Elastic Agent. Now it’s the time to boot the Elastic stack. Navigate to the package root and run the command:\u003c/p\u003e"}],"_metadata":{"uid":"cscb96b851a9b99f9c"}}},{"code":{"code":"elastic-package stack up -d","_metadata":{"uid":"cs715590a933419f06"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb409c6ac6a3e6c6c"},"header_style":"H2","paragraph_l10n":"The tool will discover the locally built package and include it in the Package Registry - see command output:"}],"_metadata":{"uid":"csb6a1e1447d1e9dba"}}},{"code":{"code":"Custom build packages directory found: /Users/marcin.tojek/go/src/github.com/mtojek/elastic-blog-posts/build/integrations\nPackages from the following directories will be loaded into the package-registry:\n- built-in packages (package-storage:snapshot Docker image)\n- /Users/marcin.tojek/go/src/github.com/mtojek/elastic-blog-posts/build/integrations","_metadata":{"uid":"csebb82d9bd004ba39"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4c78466d0c1ccc46"},"header_style":"H2","paragraph_l10n":"The instance of the Package Registry will include your prebuilt ipfs_node package and expose it under: \u003ca href=\"http://localhost:8080/search?package=ipfs_node\u0026experimental=1\"\u003ehttp://localhost:8080/search?package=ipfs_node\u0026experimental=1\u003c/a\u003e"}],"_metadata":{"uid":"cs1444e327994b52a7"}}},{"code":{"code":"[\n {\n \"name\": \"ipfs_node\",\n \"title\": \"IPFS Node\",\n \"version\": \"0.0.1\",\n \"release\": \"experimental\",\n \"description\": \"Collect logs and metrics from IPFS node.\",\n \"type\": \"integration\",\n \"download\": \"/epr/ipfs_node/ipfs_node-0.0.1.zip\",\n \"path\": \"/package/ipfs_node/0.0.1\",\n \"icons\": [\n {\n \"src\": \"/img/sample-logo.svg\",\n \"path\": \"/package/ipfs_node/0.0.1/img/sample-logo.svg\",\n \"title\": \"Sample logo\",\n \"size\": \"32x32\",\n \"type\": \"image/svg+xml\"\n }\n ],\n \"policy_templates\": [\n {\n \"name\": \"application\",\n \"title\": \"IPFS node logs and metrics\",\n \"description\": \"Collect IPFS node logs and metrics\"\n }\n ]\n }\n]","_metadata":{"uid":"cs2950838451b204b6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf4fefa20c806846d"},"header_style":"H2","paragraph_l10n":"Navigate to the local Kibana panel: \u003ca href=\"http://localhost:5601\"\u003ehttp://localhost:5601\u003c/a\u003e (login: elastic, password: changeme), visit the Integrations page and confirm that the IPFS node package is present. Click on the “Add IPFS node” button to see the configuration form (rendered from manifests):"}],"_metadata":{"uid":"cs91d530055ea23903"}}},{"image":{"image":{"uid":"bltdc57cceb5dc28ecf","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2021-10-13T22:40:07.349Z","updated_at":"2021-10-13T22:40:07.349Z","content_type":"image/png","file_size":"132033","filename":"elastic-package-integrations.2.png","title":"elastic-package-integrations.2.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-26T17:28:53.588Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc57cceb5dc28ecf/61676047494c2c12936fdc2a/elastic-package-integrations.2.png"},"_metadata":{"uid":"cs91941789788c3640"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8aba0663103ae862"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLet's prepare a few system tests to verify the package life. A system test consists of multiple steps (automatically executed by the test runner):\u003c/p\u003e\u003col\u003e\u003cli\u003eCreate a new policy defining the Integration.\u003c/li\u003e\u003cli\u003eAssign the policy to the agent.\u003c/li\u003e\u003cli\u003eWait until the agent pushes events to Elasticsearch.\u003c/li\u003e\u003cli\u003eVerify if events are correct.\u003c/li\u003e\u003c/ol\u003e\u003cbr\u003e\u003cp\u003eCreate one system test definition for \"application\" data stream in \u003ccode\u003edata_stream/application/_dev/test/system/test-default-config.yml\u003c/code\u003e:\u003c/p\u003e"}],"_metadata":{"uid":"csed2b49f8abf34445"}}},{"code":{"code":"vars: ~\ndata_stream:\n vars:\n paths:\n - \"{{SERVICE_LOGS_DIR}}/ipfs-node-*\"","_metadata":{"uid":"csf6f0119b6df28127"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csddf660a029f041a3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis system test definition defines the value for \"paths\" to observe. The SERVICE_LOGS_DIR env is a directory mounted in the Elastic Agent (source: service container with IPFS node).\u003c/p\u003e\n\u003cp\u003eCreate two system test definitions for \"repository\" data stream in \u003ccode\u003edata_stream/repository/_dev/test/system/test-default-config.yml\u003c/code\u003e and \u003ccode\u003edata_stream/traffic/_dev/test/system/test-default-config.yml\u003c/code\u003e (same content):\u003c/p\u003e"}],"_metadata":{"uid":"cs25d1110544e2ab89"}}},{"code":{"code":"vars:\n hosts:\n - http://{{Hostname}}:{{Port}}\ndata_stream:\n vars: ~","_metadata":{"uid":"cs92c3e5048cfb92bc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9b4cf615dfa0a42a"},"header_style":"H2","paragraph_l10n":"\u003cbr\u003e\u003cp\u003eLet's run all system tests and check results:\u003c/p\u003e"}],"_metadata":{"uid":"csde9e2952845904e0"}}},{"code":{"code":"elastic-package test system -v","_metadata":{"uid":"cs3f024d8907436b9c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs152edb17f90b9635"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt will take some time to run all tests, but the tool reports progress and current activity. After a few minutes it will end up with … a failure similar to this:\u003c/p\u003e"}],"_metadata":{"uid":"cs2d7c944917f29b50"}}},{"code":{"code":"2021/09/28 16:57:28 DEBUG deleting data in data stream...\n--- Test results for package: ipfs_node - START ---\nFAILURE DETAILS:\nipfs_node/traffic default:\n[0] field \"ecs.version\" is undefined\n[1] field \"http.traffic.RateIn\" is undefined\n[2] field \"http.traffic.RateOut\" is undefined\n[3] field \"http.traffic.TotalIn\" is undefined\n[4] field \"http.traffic.TotalOut\" is undefined\n[5] field \"service.address\" is undefined\n[6] field \"service.type\" is undefined","_metadata":{"uid":"cs00c5600844efe8cc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc5a54e12f05ffda5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe haven't added any field definition in data streams, so let's start with enabling the dependency manager to pull in ECS fields. Create the \u003ccode\u003e_dev/build/build.yml\u003c/code\u003e file in the package root:\u003c/p\u003e"}],"_metadata":{"uid":"cs455320937345e7d8"}}},{"code":{"code":"dependencies:\n ecs:\n reference: git@1.11","_metadata":{"uid":"csb0feb9827b01e6bd"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs138de3d3568d521c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003ePopulate fields directories with following files:\u003c/p\u003e\n\u003cp\u003edata_stream/application/fields/ecs.yml\u003c/p\u003e"}],"_metadata":{"uid":"cs2ad2f0a11c8626a9"}}},{"code":{"code":"- external: ecs\n name: ecs.version\n- external: ecs\n name: log.file.path\n- external: ecs\n name: message","_metadata":{"uid":"cs92c885a64bef03d5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8f18f7b21ba5b78c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003edata_stream/application/fields/fields.yml\u003c/p\u003e"}],"_metadata":{"uid":"cs5667b4a19d5320b6"}}},{"code":{"code":"- name: input.type\n type: keyword\n description: Input type\n- name: log.offset\n type: long\n description: Logfile offset","_metadata":{"uid":"csbb5e4f8dee511172"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7fb777f15ad61d2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003edata_stream/repository/fields/ecs.yml\u003c/p\u003e"}],"_metadata":{"uid":"csd8ee3732171535f4"}}},{"code":{"code":"- external: ecs\n name: ecs.version\n- external: ecs\n name: service.type\n- external: ecs\n name: error.message","_metadata":{"uid":"cs0d421003637f0d37"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cseb5c7649f25518f2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003edata_stream/repository/fields/fields.yml\u003c/p\u003e"}],"_metadata":{"uid":"csc4c16e852bf23524"}}},{"code":{"code":"- name: http.repository.NumObjects\n type: long\n description: Number of objects in the repository\n- name: http.repository.RepoPath\n type: keyword\n description: Path to the repository\n- name: http.repository.RepoSize\n type: long\n description: Size of the repository\n- name: http.repository.StorageMax\n type: long\n description: Max size of the storage\n- name: http.repository.Version\n type: keyword\n description: Storage version\n- name: service.address\n type: keyword\n description: Service address","_metadata":{"uid":"csabd2707d61d56f67"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb0b79d284a9698bd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003edata_stream/traffic/fields/ecs.yml\u003c/p\u003e"}],"_metadata":{"uid":"cse19700fde30697f0"}}},{"code":{"code":"- external: ecs\n name: ecs.version\n- external: ecs\n name: service.type\n- external: ecs\n name: error.message","_metadata":{"uid":"cs715df772bf0208b3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6cc1c262e29e6ec3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003edata_stream/traffic/fields/fields.yml\u003c/p\u003e"}],"_metadata":{"uid":"csf922e1074d150481"}}},{"code":{"code":"- name: http.traffic.RateIn\n type: scaled_float\n description: In network rate\n- name: http.traffic.RateOut\n type: scaled_float\n description: On network rate\n- name: http.traffic.TotalIn\n type: long\n description: Total in traffic\n- name: http.traffic.TotalOut\n type: long\n description: Total out traffic\n- name: service.address\n type: keyword\n description: Service address","_metadata":{"uid":"cs44f388fc9a566163"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs88f5ec5bf05cc14c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce all fields files are ready, let's rerun system tests, but this time enable --generate flag:\u003c/p\u003e"}],"_metadata":{"uid":"cs8be314e99a6cb790"}}},{"code":{"code":"elastic-package test system -v --generate","_metadata":{"uid":"cs96ed32b2b064ad58"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd3c7b2a07ff4481e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen system tests pass, the system test runner will store sample events from data streams containing real Elasticsearch documents. For example:\u003c/p\u003e\n\u003cp\u003edata_stream/traffic/sample_event.json\u003c/p\u003e"}],"_metadata":{"uid":"csa8d1cdc390d67ea8"}}},{"code":{"code":"{\n ...\n },\n \"http\": {\n \"traffic\": {\n \"RateIn\": 6143.101688596616,\n \"RateOut\": 2978.29294020491,\n \"TotalIn\": 160014,\n \"TotalOut\": 55738\n }\n },\n \"metricset\": {\n \"name\": \"json\",\n \"period\": 10000\n },\n \"service\": {\n \"address\": \"http://elastic-package-service_ipfs_node_1:5001/api/v0/stats/bw\",\n \"type\": \"http\"\n }\n}","_metadata":{"uid":"cs827ef0662ba38ee1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csda811b648105997d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs we proved that our integration collects data and even stored a few sample events, it’s recommended to present them in the README. The elastic-package provides basic rendering options to render the table with fields and sample events. Let’s create a README template (_dev/build/docs/README.md) in the package root:\u003c/p\u003e"}],"_metadata":{"uid":"csc97d46b84e05e832"}}},{"code":{"code":"# IPFS Node\n\nThis is a new integration created using the [elastic-package](https://github.com/elastic/elastic-package) tool.\n\n## Application logs\n\n{{event \"application\"}}\n\n{{fields \"application\"}}\n\n## Repository metrics\n\n{{event \"repository\"}}\n\n{{fields \"repository\"}}\n\n## Traffic metrics\n\n{{event \"traffic\"}}\n\n{{fields \"traffic\"}}","_metadata":{"uid":"cs3b8a49d8c9cfe267"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa1cb03943a08ffd9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eRebuild the package with \u003ccode\u003eelastic-package\u003c/code\u003c build and check rendered package README file in \u003ccode\u003edocs/README.md\u003c/code\u003e.\u003cbr\u003e\nCongratulations, you have just built your first integration.\u003c/p\u003e\n\n\u003ch2\u003eTroubleshooting the integration\u003c/h2\u003e\n\n\u003cp\u003eIt may happen that complex ingest configuration will require a few minutes of debugging. The elastic-package exposes a dedicated feature to dump all logs from the Elastic stack. With the stack up and running, run the following command:\u003c/p\u003e"}],"_metadata":{"uid":"cs9a2a42bd4b569b64"}}},{"code":{"code":"elastic-package stack dump","_metadata":{"uid":"csb7d47f469727504e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7106a85960a31c86"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe tool will pull logs from Docker containers including internal files and place together in the directory:\u003c/p\u003e"}],"_metadata":{"uid":"cs1d1ed1622dedf44a"}}},{"code":{"code":"$ tree elastic-stack-dump\nelastic-stack-dump\n└── logs\n ├── elastic-agent-internal\n │ ├── filebeat-json.log\n │ ├── filebeat-json.log-2021-09-28-15-16\n │ ├── filebeat-json.log-2021-09-28-15-17\n │ ├── metricbeat-json.log\n │ ├── metricbeat-json.log-2021-09-28-15-20\n │ └── metricbeat-json.log-2021-09-28-15-21\n ├── elastic-agent.log\n ├── elasticsearch.log\n ├── fleet-server-internal\n │ ├── fleet-server-json.log\n │ ├── fleet-server-json.log-2021-09-28-14-1\n │ └── fleet-server-json.log-2021-09-28-14-2\n ├── fleet-server.log\n ├── kibana.log\n └── package-registry.log\n\n3 directories, 26 files","_metadata":{"uid":"cs99080143ff448d3a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdf73dcb96efb0071"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLook around for possible errors, configuration issues or stack problems. If you notice that the Elastic Agent doesn't process any logs, it's worth looking into filebeat and metricbeat logs.\u003c/p\u003e\n\n\n\u003ch2\u003eBrowse metrics in Elasticsearch\u003c/h2\u003e\n\n\u003cp\u003eThere is an option to check documents processed by the Agent running during system tests. Restart system tests with an extra flag to defer cleanup by 5 minutes:\u003cbr\u003e\n\u003ccode\u003eelastic-package test system --data-streams repository --defer-cleanup 5m -v\u003c/code\u003e\u003c/p\u003e\n\n\u003cp\u003eObserve the output of elastic-package until you notice the \"waiting\" confirmation:\u003c/p\u003e"}],"_metadata":{"uid":"csa578a4ff71db0e63"}}},{"code":{"code":"2021/09/28 18:19:07 DEBUG Policy revision assigned to the agent (ID: cae28981-0d96-434d-aa3f-55a63e37f6f9)...\n2021/09/28 18:19:07 DEBUG checking for expected data in data stream...\n2021/09/28 18:19:07 DEBUG found 0 hits in metrics-ipfs_node.repository-ep data stream\n2021/09/28 18:19:08 DEBUG found 0 hits in metrics-ipfs_node.repository-ep data stream\n2021/09/28 18:19:09 DEBUG found 0 hits in metrics-ipfs_node.repository-ep data stream\n2021/09/28 18:19:10 DEBUG found 0 hits in metrics-ipfs_node.repository-ep data stream\n2021/09/28 18:19:11 DEBUG found 1 hits in metrics-ipfs_node.repository-ep data stream\n2021/09/28 18:19:11 DEBUG waiting for 5m0s before tearing down...","_metadata":{"uid":"cs8e70310d5a6bc5ea"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaf37a812e5fc4ad8"},"header_style":"H2","paragraph_l10n":"Feel free to review existing indices using Elasticsearch endpoint - \u003ca href=\"http://localhost:9200/_cat/indices\"\u003ehttp://localhost:9200/_cat/indices\u003c/a\u003e (login: elastic, password: changeme):"}],"_metadata":{"uid":"csb6ca7dae68912c80"}}},{"code":{"code":"green open .tasks aB4Wp5GtRGWtMomVKVIKvQ 1 0 2 0 13.8kb 13.8kb\nyellow open .ds-metrics-system.process.summary-default-2021.09.28-000001 XRf77R7XS2KKrqnffegb6w 1 1 1081 0 1.2mb 1.2mb\ngreen open .security-7 4VEaX_a0TEuNDDRWr4W14g 1 0 117 6 292.8kb 292.8kb\nyellow open .ds-metrics-ipfs_node.repository-ep-2021.09.28-000001 GlmMwE9-SAipRygU4sI88Q 1 1 8 0 237.7kb 237.7kb\nyellow open .ds-logs-ipfs_node.application-ep-2021.09.28-000001 -BWSONvSQxmJZCbF1GtmnQ 1 1 0 0 67.4kb 67.4kb\nyellow open .ds-metrics-elastic_agent.metricbeat-default-2021.09.28-000001 vWNedZJeQaeG35bO5UorDQ 1 1 2162 0 2mb 2mb\nyellow open .ds-metrics-system.uptime-default-2021.09.28-000001 7kfIHzAqTdSLQEhPc72sMw 1 1 1081 0 1.1mb 1.1mb\ngreen open .kibana-event-log-7.15.0-snapshot-000001 vqx_yozOSeekpJ_h2zdiCQ 1 0 2 0 11.9kb 11.9kb\ngreen open .fleet-policies-7","_metadata":{"uid":"csfdde8c09e0973acb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb03df70afbb7617b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLet's review documents in the \u003ccode\u003e.ds-metrics-ipfs_node.repository-ep-2021.09.28-000001\u003c/code\u003e index:\u003c/p\u003e\n\u003cp\u003e\u003ca href=\"http://localhost:9200/.ds-metrics-ipfs_node.repository-ep-2021.09.28-000001/_search?pretty=true\"\u003ehttp://localhost:9200/.ds-metrics-ipfs_node.repository-ep-2021.09.28-000001/_search?pretty=true\u003c/a\u003e (keep in mind that the link depends on the existing data stream, which might be different in your case)\u003c/p\u003e"}],"_metadata":{"uid":"cs181271e9af6ee0f9"}}},{"code":{"code":"{\n \"took\" : 2,\n \"timed_out\" : false,\n \"_shards\" : {\n \"total\" : 1,\n \"successful\" : 1,\n \"skipped\" : 0,\n \"failed\" : 0\n },\n \"hits\" : {\n \"total\" : {\n \"value\" : 21,\n \"relation\" : \"eq\"\n },\n \"max_score\" : 1.0,\n \"hits\" : [\n {\n \"_index\" : \".ds-metrics-ipfs_node.repository-ep-2021.09.28-000001\",\n \"_type\" : \"_doc\",\n \"_id\" : \"OuA0LXwBJVkAmqat6T4O\",\n \"_score\" : 1.0,\n \"_source\" : {\n \"agent\" : {\n \"hostname\" : \"docker-fleet-agent\",\n \"name\" : \"docker-fleet-agent\",\n \"id\" : \"cae28981-0d96-434d-aa3f-55a63e37f6f9\",\n \"type\" : \"metricbeat\",\n \"ephemeral_id\" : \"88e873e4-9bb2-4220-bfa4-e6bfcc0e6e04\",\n \"version\" : \"7.15.0\"\n },\n ...\n \"http\" : {\n \"repository\" : {\n \"RepoPath\" : \"/data/ipfs\",\n \"StorageMax\" : 1.0E10,\n \"Version\" : \"fs-repo@11\",\n \"RepoSize\" : 119295,\n \"NumObjects\" : 22\n }\n },\n \"metricset\" : {\n \"period\" : 10000,\n \"name\" : \"json\"\n },\n \"event\" : {\n \"duration\" : 3025800,\n \"agent_id_status\" : \"verified\",\n \"ingested\" : \"2021-09-28T16:20:14Z\",\n \"module\" : \"http\",\n \"dataset\" : \"ipfs_node.repository\"\n }\n }\n },\n…\n}","_metadata":{"uid":"csbbeadd1f24601c01"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscc3390fe3f53a1cc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThat's all folks! You managed to create your first integration, cover it with system tests and verify integrity with a real service (not mocked files). Feel free to build more Elastic Integrations and submit them to our repository, Elastic Integrations.\u003c/p\u003e\n\n\u003cp\u003eThe source code for this tutorial can be also found here.\u003c/p\u003e"}],"_metadata":{"uid":"cs7ba7960655c9709a"}}}],"publish_date":"2021-10-21T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Use elastic-package to create and bootstrap a new Elastic integration for IoT devices","seo_description_l10n":"We will use an official builder tool for Elastic Integration, elastic-package, to bootstrap a new integration to observe an unsupported product or service. We will configure it to collect available logs and metrics and run under the Elastic Agent.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt9c35d17afad9d20d","ACL":{},"content_type":"image/png","created_at":"2020-07-17T22:37:06.439Z","created_by":"bltf6ab93733e4e3a73","file_size":"72902","filename":"blog-thumb-rocket-launch.png","tags":[],"title":"blog-thumb-rocket-launch.png","updated_at":"2020-07-17T22:37:06.439Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-02-10T16:42:04.105Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9c35d17afad9d20d/5f122812c31823015df6ef0a/blog-thumb-rocket-launch.png"},"title":"Use elastic-package to create and bootstrap a new Elastic integration","title_l10n":"Use elastic-package to create and bootstrap a new Elastic integration","updated_at":"2025-03-28T17:17:16.391Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/use-elastic-package-to-create-and-bootstrap-a-new-elastic-integration","publish_details":{"time":"2025-03-28T17:17:21.567Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7ee407f6cbfd8682","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"The elastic-package tool provides different testing methods for Elastic Integrations - asset, pipeline, static and system tests. We'll review the most useful options based on existing integrations.","author":["blt54b3d91f48035ccc"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-10-28T16:08:06.901Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5957b2d1ce00fffa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs observed products and services evolve or their authors introduce new features, it’s essential to preserve compatibility between the product and the corresponding integration and detect inconsistencies as soon as possible.\u003c/p\u003e\n\u003cp\u003eAt Elastic, we use the \u003ca href=\"https://github.com/elastic/elastic-package\"\u003eelastic-package\u003c/a\u003e on a daily basis to create and maintain integrations. Today, we'll review existing testing methods for integrations and learn how to verify integrity between Elastic Agent and observed products.\u003c/p\u003e\n\u003cp\u003eReview following testing methods and adopt them in your integrations to increase test coverage for pipelines, manifests, fields, etc. Adopting at least a few of them will prevent hours of manual testing and bug hunting.\u003c/p\u003e\u003ch2\u003ePreparation for tests (cheatsheet)\u003c/h2\u003e\n\u003cp\u003eAll testing methods require the Elastic stack to be present for testing. Boot up the stack with the command:\u003c/p\u003e"}],"_metadata":{"uid":"csf38a6c2f6a2812eb"}}},{"code":{"code":"elastic-package stack up -d","_metadata":{"uid":"cs38671c62db2ed848"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb5d4f7a21ff19b8a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIf you want to reload the content of Elastic Package Registry (EPR), use the following command:\u003c/p\u003e"}],"_metadata":{"uid":"cs060c7893e6d06c90"}}},{"code":{"code":"elastic-package stack up -d --services package-registry","_metadata":{"uid":"csc6901a3bc073ace0"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs170f2cd898e0f736"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eKeep in mind that reloading makes sense only when you have rebuilt the package and would like to expose it with the EPR. It’s quicker than restarting the entire stack, but may be insufficient if Kibana caches the package revision (name and version).\u003c/p\u003e\n\u003cp\u003eThe test runner also requires environment variables to point to the stack endpoints (Kibana, Elasticsearch). Use this eval to populate these variables:\u003c/p\u003e"}],"_metadata":{"uid":"csf216001723e8b8d8"}}},{"code":{"code":"eval \"$(elastic-package stack shellinit)\"","_metadata":{"uid":"cs711ff7395172d009"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs84f3c58463c22960"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eAsset tests: verify if your integration can be installed successfully\u003c/h2\u003e\u003cp\u003eThe first described testing method is asset testing. The test runner uses an active Kibana instance to perform an installation procedure of the package. Build the package:\u003c/p\u003e"}],"_metadata":{"uid":"cs2f74d49be2ea90f0"}}},{"code":{"code":"elastic-package build","_metadata":{"uid":"cse78cce3af2f690bf"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs03d12aa936c746d2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNext, staying in the package root, boot up the Elastic stack or reload the Package Registry.\u003c/p\u003e\n\u003cp\u003eAsset testing can be performed with the following command (verbose mode):\u003c/p\u003e"}],"_metadata":{"uid":"cse88a6580397f62ba"}}},{"code":{"code":"elastic-package test asset -v","_metadata":{"uid":"cscba1dce5ef6c37ab"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbc239fce50f37590"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eHere is the sample output of asset tests running for NGINX Ingress Controller:\u003c/p\u003e"}],"_metadata":{"uid":"cs6186fbd620354d84"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt18663c6a5d39084d","ACL":{},"content_type":"image/png","created_at":"2021-10-28T17:48:53.250Z","created_by":"blt3044324473ef223b70bc674c","file_size":"831832","filename":"elastic-stack-package-1.png","parent_uid":null,"tags":[],"title":"elastic-stack-package-1.png","updated_at":"2021-10-28T17:48:53.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-05T17:00:00.638Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt18663c6a5d39084d/617ae28538150b1072a1d741/elastic-stack-package-1.png"},"_metadata":{"uid":"cs045ee8e99a7662dd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs10e020ffb2faa2cd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs you can see, the elastic-package installed the appropriate package first in Kibana (POST call) and then performed a set of checks to verify that all package elements are available. It can check different parts, especially Kibana saved objects (e.g., Kibana dashboards and visualizations), ingest pipelines or index templates (field mappings).\u003c/p\u003e\n\u003cp\u003eAsset tests are relatively fast and can give you an ultimate answer whether your package is installable. You could achieve same result with manual clicking through Fleet UI, but it's definitely doing this with the elastic-package and nearly impossible to miss any package components that should be installed.\u003c/p\u003e\n\u003ch2\u003ePipeline tests: unit tests for Elasticsearch ingest pipeline\u003c/h2\u003e\n\u003cp\u003eIf you're dealing with log files requiring additional transformation before storing them in the Elasticsearch, it's a good habit to prepare all representative files (including different formats) and use them to exercise the ingest pipeline.\u003c/p\u003e\n\u003cp\u003eA single pipeline test case contains a single input log file with an optional test config and expected output (documents ready to be stored in Elasticsearch). Let's review pipeline tests written for the NGINX Ingress Controller integration, the error data stream (error logs):\u003c/p\u003e"}],"_metadata":{"uid":"csf9d2995ad5cb81af"}}},{"code":{"code":"tree nginx_ingress_controller/data_stream/error/_dev/test/pipeline\n.\n├── test-error-raw.log\n├── test-error-raw.log-config.yml\n└── test-error-raw.log-expected.json\n\nThe test-error-raw.log file contains a small, representative sample of application logs:\nI1215 14:15:13.816334 8 main.go:256] \"Trying to discover Kubernetes version\"\nI1215 14:15:13.816854 8 round_trippers.go:449] Response Headers:\nF1215 14:16:33.326604 8 main.go:294] Error while initiating a connection to the Kubernetes API server. This could mean the cluster is misconfigured (e.g. it has invalid API server certificates or Service Accounts configuration). Reason: Get \"https://127.0.0.1:443/version?timeout=32s\": dial tcp 127.0.0.1:443: connect: connection refused\nRefer to the troubleshooting guide for more information: https://kubernetes.github.io/ingress-nginx/troubleshooting/\ngoroutine 1 [running]:\nk8s.io/klog/v2.stacks(0xc00000e001, 0xc0004fc6c0, 0x1cd, 0x228)\n k8s.io/klog/v2@v2.3.0/klog.go:996 +0xb9\nk8s.io/klog/v2.(*loggingT).output(0x28fb700, 0xc000000003, 0x0, 0x0, 0xc000344770, 0x28499eb, 0x7, 0x126, 0x0)\n k8s.io/klog/v2@v2.3.0/klog.go:945 +0x191\nk8s.io/klog/v2.(*loggingT).printf(0x28fb700, 0x3, 0x0, 0x0, 0x1c19509, 0x13f, 0xc00009ff08, 0x1, 0x1)\n k8s.io/klog/v2@v2.3.0/klog.go:733 +0x17a","_metadata":{"uid":"cs0b8d542aa068a120"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs42cdc282c1be2ec8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eA good representative sample should contain different candidates for ingestion - lines with timestamps and columns, multi-line entries, empty lines, etc. The more different log lines will be covered with pipeline tests, the higher support level will be achieved and more logs will be consumed successfully.\u003c/p\u003e\n\u003cp\u003eThe \u003ccode\u003etest-error-raw.log-config.yml\u003c/code\u003e file enables extra features which can change behavior of the test runner:\u003c/p\u003e"}],"_metadata":{"uid":"cs6b07f598dd5e0add"}}},{"code":{"code":"multiline:\n first_line_pattern: \"^[A-Z]{1}[0-9]{4} \"\nfields:\n event.timezone: \"GMT+1\"\n \"@timestamp\": \"2020-12-16T11:39:15.954Z\"\n tags:\n - preserve_original_event\ndynamic_fields:\n event.ingested: \".*\"","_metadata":{"uid":"csf30552ede7290c22"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csff3e938450ff25dc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor example it can define a first_line_pattern for multiline logs, additional fields to be added to input logs or mark some fields to be dynamic (can't be statically asserted).\u003c/p\u003e\n\u003cp\u003eThe last and mandatory file, \u003ccode\u003etest-error-raw.log-expected.json\u003c/code\u003e, stores expected results for a single pipeline test. The content of the file reflects documents to be collected and stored in Elasticsearch once is processed by an ingest pipeline:\u003c/p\u003e"}],"_metadata":{"uid":"cs12654574719c3da5"}}},{"code":{"code":"{\n \"expected\": [\n {\n \"nginx_ingress_controller\": {\n \"error\": {\n \"thread_id\": 8,\n \"source\": {\n \"line_number\": 489,\n \"file\": \"config.go\"\n }\n }\n },\n \"@timestamp\": \"2020-12-15T04:15:13.816036+01:00\",\n \"ecs\": {\n \"version\": \"1.11.0\"\n },\n \"log\": {\n \"level\": \"E\"\n },\n \"message\": \"Expected to load root CA config from /var/run/secrets/kubernetes.io/serviceaccount/ca.crt, but got err: open /var/run/secrets/kubernetes.io/serviceaccount/ca.crt: no such file or directory\",\n \"event\": {\n \"ingested\": \"2021-06-09T12:42:49.083062900Z\",\n \"original\": \"E1215 04:15:13.816036 8 config.go:489] Expected to load root CA config from /var/run/secrets/kubernetes.io/serviceaccount/ca.crt, but got err: open /var/run/secrets/kubernetes.io/serviceaccount/ca.crt: no such file or directory\",\n \"timezone\": \"GMT+1\",\n \"created\": \"2020-12-16T11:39:15.954Z\",\n \"kind\": \"event\",\n \"category\": [","_metadata":{"uid":"csa6ebeb8c6626fb0f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs50776b13d2ae4baf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt's advised to store both, input logs and expected results, under the version control system as the output of pipeline tests is represented in a form of diff:\u003c/p\u003e"}],"_metadata":{"uid":"cs430a977b23de5262"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt890e3f46ec4a28e5","ACL":{},"content_type":"image/png","created_at":"2021-10-28T17:53:36.526Z","created_by":"blt3044324473ef223b70bc674c","file_size":"220727","filename":"elastic-stack-package-2.png","tags":[],"title":"elastic-stack-package-2.png","updated_at":"2021-10-28T17:53:36.526Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-05T17:00:00.174Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt890e3f46ec4a28e5/617ae3a068a7871075fab174/elastic-stack-package-2.png"},"_metadata":{"uid":"cs46621793c8513edb"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd62815dac20dc1c3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003ePipeline testing can be performed with the following command (verbose mode):\u003c/p\u003e"}],"_metadata":{"uid":"csb5eab1ba13f08138"}}},{"code":{"code":"elastic-package test pipeline -v","_metadata":{"uid":"csc7b5d3f00441326f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5cf5d0b12b2decb2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eHere is the sample output of pipeline tests running for NGINX Ingress Controller:\u003c/p\u003e"}],"_metadata":{"uid":"cs5bcdeec7a3975927"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blta62b31b43619d09d","ACL":{},"content_type":"image/png","created_at":"2021-10-28T17:54:21.260Z","created_by":"blt3044324473ef223b70bc674c","file_size":"225829","filename":"elastic-stack-package-3.png","tags":[],"title":"elastic-stack-package-3.png","updated_at":"2021-10-28T17:54:21.260Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-05T17:00:00.625Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta62b31b43619d09d/617ae3cd00b7f610684661b1/elastic-stack-package-3.png"},"_metadata":{"uid":"cs0bfe0be08a850ec6"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csafa91e45ea71c795"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eStatic tests: make sure that static files are correct\u003c/h2\u003e\n\u003cp\u003eThe intention of static tests is verification of files not necessarily related with ingestion logic, but important from the user perspective.\u003c/p\u003e\n\u003cp\u003eAt the moment of writing (September 2021) static tests involve the field validator to check if sample event files (\u003ccode\u003esample_event.json\u003c/code\u003e) don’t expose any undocumented or incorrectly typed fields, which may confuse integration users. Field definitions are stored in data streams in \u003ccode\u003efields\u003c/code\u003e directory (see the MongoDB integration below):\u003c/p\u003e"}],"_metadata":{"uid":"cs6df3e6f1ee53a7ef"}}},{"code":{"code":"find . -name fields\n./data_stream/metrics/fields\n./data_stream/dbstats/fields\n./data_stream/collstats/fields\n./data_stream/status/fields\n./data_stream/replstatus/fields\n./data_stream/log/fields","_metadata":{"uid":"cs1acf899043fb5436"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7bdd07e992f0205d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eStatic testing can be performed with the following command (verbose mode):\u003c/p\u003e"}],"_metadata":{"uid":"cs6fe399ca6d4010bb"}}},{"code":{"code":"elastic-package test static -v","_metadata":{"uid":"csd580bcf1272bb046"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7e03bcbd5533cb41","ACL":{},"content_type":"image/png","created_at":"2021-10-28T17:56:09.515Z","created_by":"blt3044324473ef223b70bc674c","file_size":"306881","filename":"elastic-stack-package-4.png","tags":[],"title":"elastic-stack-package-4.png","updated_at":"2021-10-28T17:56:09.515Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-05T17:00:00.660Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7e03bcbd5533cb41/617ae439ca49a0105c0b6a0e/elastic-stack-package-4.png"},"_metadata":{"uid":"cs25b2c47413d3d451"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9117e1412b8e1ad7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this use case the test runner executed a set of static tests against all data streams defined in the MongoDB integration. It verified all sample_events.json files that were saved using \u003ccode\u003e--generate\u003c/code\u003e flag of the \u003ccode\u003etest system\u003c/code\u003e command.\u003c/p\u003e\n\u003ch2\u003eSystem tests: check data collection of the integration against a real service or product\u003c/h2\u003e\n\u003cp\u003eSystem tests are the most complicated ones compared with other available testing methods and they take time and resources to execute. The test runner simulates steps a real developer would do to enable an integration and collect data. It requires the entire Elastic stack to be up and running and connects a real service (dockerized) to the Docker stack network.\u003c/p\u003e\n\u003cp\u003eThe system test runner supports different kinds of observed services. The basic one is a standard Docker Compose service defined in \u003ccode\u003e_dev/deploy/docker\u003c/code\u003e, which runs one or two Docker containers. A good candidate for Docker service is NGINX web server exposing HTTP endpoints and healthcheck.\u003c/p\u003e\n\u003cp\u003eAnother kind is a Kubernetes deployment - the application is described using YAML definition files in \u003ccode\u003e_dev/deploy/k8s\u003c/code\u003e and installed by the test runner using \u003ccode\u003ekubectl\u003c/code\u003e. Apart from the Elastic stack it requires a kind cluster to be up and running. This service deployer is recommended for services deployed in the Kubernetes cluster or internal Kubernetes applications.\u003c/p\u003e\n\u003cp\u003eThere are integrations that monitor cloud services that can’t be dockerized by design (e.g DynamoDB, Amazon S3) and mocking won’t give best results. For such cases the way to go is the Terraform service deployer, which can read .tf files from \u003ccode\u003e_dev/deploy/tf\u003c/code\u003e and use Terraform to apply changes.\u003c/p\u003e\n\u003cp\u003eThe system test lifecycle starts with booting up observed services and waiting until it becomes healthy. Next, the system test runner assigns a new test policy to the Elastic Agent instance, based on the provided test configuration. Here is a basic configuration for the system test of the NGINX integration, \u003ccode\u003estubstatus\u003c/code\u003e data stream:\u003c/p\u003e\n\u003cp\u003edata_stream/stubstatus/_dev/test/system/test-default-config.yml\u003c/p\u003e"}],"_metadata":{"uid":"cs3ed9d6ef8f9207ef"}}},{"code":{"code":"vars:\n hosts:\n - http://{{Hostname}}:{{Port}}\ndata_stream:\n vars:\n server_status_path: /server-status","_metadata":{"uid":"csa0541a0db22deb7b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8480c7150eca66eb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe sample configuration contains definitions for policy template's variables and data stream's variables. As you can see there are placeholders defined for the \u003ccode\u003ehosts\u003c/code\u003e variable, these will be replaced with the internal Docker endpoint (service host and port).\u003c/p\u003e\n\u003cp\u003eThe test runner waits (and watches) until the agent instance picks up the policy and then starts observing the related data stream for new documents - this means that the agent collected some logs or metrics, optionally the ingest pipeline transformed them and data landed as documents in Elasticsearch.\u003c/p\u003e\n\u003cp\u003eThe system test runner fetches the latest documents and runs static tests on them to make sure they are aligned with the field schema.\u003c/p\u003e"}],"_metadata":{"uid":"csf4ad50813b3fb85b"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt0099e1a914123396","ACL":{},"content_type":"image/png","created_at":"2021-10-28T17:58:51.024Z","created_by":"blt3044324473ef223b70bc674c","file_size":"566284","filename":"elastic-stack-package-5.png","tags":[],"title":"elastic-stack-package-5.png","updated_at":"2021-10-28T17:58:51.024Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-05T17:00:00.459Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0099e1a914123396/617ae4db9ff3ae1079a918e0/elastic-stack-package-5.png"},"_metadata":{"uid":"csccf904bd25eb6b95"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csacb4b42e9f73ee35"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSystem testing can be performed with the following command (verbose mode):\u003c/p\u003e"}],"_metadata":{"uid":"cs4d7de783c600a1eb"}}},{"code":{"code":"elastic-package test system -v","_metadata":{"uid":"cs2c79567ddeca972c"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blta49ff9f4b07adcae","ACL":{},"content_type":"image/png","created_at":"2021-10-28T17:59:15.412Z","created_by":"blt3044324473ef223b70bc674c","file_size":"822287","filename":"elastic-stack-package-6.png","tags":[],"title":"elastic-stack-package-6.png","updated_at":"2021-10-28T17:59:15.412Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-05T17:00:00.718Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta49ff9f4b07adcae/617ae4f3a2b4ac1067d75b9a/elastic-stack-package-6.png"},"_metadata":{"uid":"cs12528be2e29a89ae"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csce9dff07415c9303"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eKeep in mind that it takes some time to run all system tests for all data streams if you have many ones or if the service container has long initialization. Nevertheless it's still a convenient testing method to adopt as it covers the entire end-to-end path of logs/metric data in Elastic Agent's based environments. \u003c/p\u003e\n\u003cp\u003eWith described testing methods an Integration developer can cover multiple parts of a package including ingest pipelines, fields, config policies and Kibana saved objects. All these methods have been developed in the CI-friendly way and can be executed automatically without any human interaction (this is the way we run tests for Integrations in Elastic). Feel free to introduce more tests to your integrations and detect inconsistencies with an observed product as soon as possible.\u003c/p\u003e"}],"_metadata":{"uid":"csb468f5d1964886fe"}}}],"publish_date":"2021-11-05T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Review testing methods for Elastic integrations using the elastic-package tool","seo_description_l10n":"The elastic-package tool provides different testing methods for Elastic Integrations - asset, pipeline, static and system tests. We'll review the most useful options based on existing integrations.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltc1e6b31c57960d36","created_by":"bltc759967f917b6179af5f1988","updated_by":"bltc759967f917b6179af5f1988","created_at":"2020-06-10T18:24:15.869Z","updated_at":"2020-06-10T18:24:15.869Z","content_type":"image/png","file_size":"142598","filename":"elastic-integrations.png","title":"elastic-integrations.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-25T21:11:23.988Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc1e6b31c57960d36/5ee1254ff2c45903a4be0c31/elastic-integrations.png"},"title":"Review testing methods for Elastic integrations using the elastic-package tool","title_l10n":"Review testing methods for Elastic integrations using the elastic-package tool","updated_at":"2025-03-28T17:16:58.090Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/review-testing-methods-for-elastic-integrations-using-the-elastic-package-tool","publish_details":{"time":"2025-03-28T17:17:03.126Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6a5c1b96f68fa450","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"Realizing business objectives and successful outcomes with our customers is at the core of what we do. In this series, learn some of the many ways Elastic Technical Account Managers partner with organizations to accomplish these goals.","author":["bltad40eff0cd58b113","blte41e3464cc3af85b"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-11-23T17:58:06.369Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf2571543b7d9dadd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFrom improving safety in planes to reducing times to detect and respond to threats, \u003ca href=\"https://www.elastic.co/consulting\"\u003eElastic Consulting\u003c/a\u003e helps our customers drive impactful business outcomes. \u003c/p\u003e\n\u003cp\u003eTechnical\n Account Managers (TAM) play an essential role in supporting our \ncustomers throughout their journey. In this latest post from our series,\n Nikki Jones, Customer Success Lead interviews Taha Derouiche, Elastic \nTAM. \u003c/p\u003e"}],"_metadata":{"uid":"csf2917cec9af33c3a"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt91e834ee19477d83","ACL":{},"content_type":"image/jpeg","created_at":"2021-11-23T17:57:00.940Z","created_by":"blt1e57c6588ae1816e","file_size":"240101","filename":"taha.jpg","parent_uid":null,"tags":[],"title":"taha.jpg","updated_at":"2021-11-23T17:57:00.940Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-24T18:00:00.094Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt91e834ee19477d83/619d2b6c9b3c850ceca03d3a/taha.jpg"},"_metadata":{"uid":"csfc810c19b7c46a7a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfadf33a81eafe421"},"header_style":"H2","paragraph_l10n":"\u003cstrong\u003e\u003cem\u003eCan you give an example of what kind of business challenges you help our customers solve, and what value you help them unlock?\u003c/em\u003e\u003c/strong\u003e\u003cbr\u003e\u003cbr\u003e\n\u003cp\u003eWe are a trusted advisor who is a recurring touch point for technical questions that really allow our customers to find greater value in their Elastic investment. This makes sure our customers are successful and that their business requirements are inline with the product roadmap and vision.\u003c/p\u003e\n\u003cp\u003eFor example, I recently worked with a digital e-commerce travel company to set up an Elastic SIEM to:\u003c/p\u003e\n\u003cul\u003e\u003cli\u003eReduce times to detect and respond to threats and increase forensic investigation capabilities\u003c/li\u003e\u003cli\u003eIncrease observability; build a reliable, extensible, and responsive security platform\u003c/li\u003e\u003cli\u003eFacilitate the onboarding and accelerate the ramp up of new users\u003c/li\u003e\u003c/ul\u003e\n\u003cp\u003e\u003cbr\u003e\u003c/p\u003e\n\u003cp\u003eDuring our regular strategic sessions, we started refining and tailoring the solution so that we could begin using Machine Learning \u0026 AI to enhance the user experience with detection rules. The discovery of this use case enabled the customer to improve their managed platform visibility and decrease the operational load the team was handling.\u003c/p\u003e\n\u003cp\u003eThis has also enabled other Machine Learning teams across that business to leverage the existing data, together with their other use cases.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eHow else have you helped our customers achieve their business goals?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eI work with an Aerospace company who is using Elasticsearch to index and scan all of the flight lanes operational manuals, to allow the aircraft maintenance engineers to improve safety in planes. We identify solutions by matching plane maintenance indicators to possible remediation solutions. Some signals are sent while the plane is still flying, this allows them to be serviced immediately after landing and makes sure engineers are ready on the ground, which also ensures traffic is not impacted by maintenance related delays.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eHow does it feel to help our customers succeed?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eMaking sure they are successful, and keeping a high cadence, and short feedback loop on their needs is a priority. It is very satisfying to be there for them and make sure their input is prioritised at the right levels and that we are setting the right level of expectations.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eHow do our customers view your relationship?\u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eOur customers want to have their business goals met, with clear indicators, and a predictable vision. We help to translate this through proactive sessions and interactions to keep our goals aligned in an actionable way.\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003e\u003cem\u003eCould you give us some examples of the types of business outcomes our customers are looking to achieve through your work together? \u003c/em\u003e\u003c/strong\u003e\u003c/p\u003e\n\u003cp\u003eIncreased confidence, having a counterpart to raise questions and concerns, and to validate some assumptions. Companies put a lot of effort into large projects and the more clarity they get, the more engaged they become. \u003c/p\u003e\u003ch3\u003eAligning with our customers' desired business outcomes to achieve success\u003c/h3\u003e\"Our TAMs provide technical and strategic guidance at every stage in your Elastic journey. They are an extension of your team and dedicated to helping you achieve your business outcomes. Contact \u003ca href=\"https://www.elastic.co/consulting\"\u003eElastic Consulting\u003c/a\u003e to learn more about \u003ca href=\"https://www.elastic.co/consulting/embedded-services\"\u003eEmbedded Services\u003c/a\u003e and how we can help you maximize your Elastic investment.\""}],"_metadata":{"uid":"cs0b644975e5690ea2"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt13aded2f2f2151e7","ACL":{},"content_type":"image/png","created_at":"2021-08-25T13:09:25.990Z","created_by":"blt1e57c6588ae1816e","file_size":"230941","filename":"blog-elastic-nikki-3.png","tags":[],"title":"blog-elastic-nikki-3.png","updated_at":"2021-08-25T13:09:25.990Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-29T15:00:00.171Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt13aded2f2f2151e7/612641054d39656a33b08da5/blog-elastic-nikki-3.png"},"_metadata":{"uid":"csbf8c697673248dc6"},"caption_l10n":"","alt_text_l10n":"Nikki Jones, Customer Success \u0026 Services Lead","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}}],"publish_date":"2021-11-24T06:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Helping Elastic Customers Succeed | How Elastic partners with organizations to maximise their investments","seo_description_l10n":"Realizing business objectives and successful outcomes with our customers is at the core of what we do. In this series, learn some of the many ways Elastic Technical Account Managers partner with organizations to accomplish these goals.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"Interview with Technical Account Manager, Taha Derouiche","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"bltde0200616937614f","ACL":{},"content_type":"image/png","created_at":"2021-01-12T15:23:30.320Z","created_by":"bltf6ab93733e4e3a73","file_size":"87431","filename":"blog-thumb-heart-engine.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-heart-engine.png","updated_at":"2022-02-11T21:04:31.036Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:26:52.407Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltde0200616937614f/5ffdbef2e4028c63a64d9312/blog-thumb-heart-engine.png"},"title":"Helping Elastic Customers Succeed | How Elastic partners with organizations to maximise their investments","title_l10n":"Helping Elastic Customers Succeed | How Elastic partners with organizations to maximise their investments","updated_at":"2025-03-28T17:16:39.679Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/helping-elastic-customers-succeed-how-elastic-partners-with-organizations-to-maximise-their-investments","publish_details":{"time":"2025-03-28T17:16:44.458Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4c63038d9805671e","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"The Osquery Manager integration for Elastic Agent helps teams better detect, investigate, and hunt for vulnerabilities and anomalous activities. Learn how to deploy Osquery Manager in this blog.","author":["blt22f454b4f18b8d95"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-12-14T18:46:07.420Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd873be4b783ee5f8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWith the Elastic 7.16 release, \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/osquery.html\"\u003eOsquery Manager\u003c/a\u003e is now generally available for Elastic Agent, making it easier than ever to deploy and run Osquery across your environments. By collecting \u003ca href=\"https://osquery.io/\"\u003eOsquery\u003c/a\u003e data and combining it with the power of the Elastic Stack, you can greatly expand your endpoint telemetry, enabling enhanced detection and investigation, and improved hunting for vulnerabilities and anomalous activities.\u003c/p\u003e\n\u003cp\u003eThis blog post gives a brief intro to the Osquery Manager integration for Elastic Agent and how it can be used in conjunction with Elastic Security. Included are examples that show how to operationalize the Osquery data with use cases such as building critical security alerts, querying isolated hosts during investigations, and monitoring for anomalous host activities with ML detections.\u003c/p\u003e\u003ch2\u003eHow does Osquery Manager work?\u003c/h2\u003e\u003ca href=\"https://osquery.io/\"\u003eOsquery\u003c/a\u003e is an open source tool that lets you query Operating Systems like a database using SQL. When you add the \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/osquery.html\"\u003eOsquery Manager\u003c/a\u003e integration to an \u003ca href=\"https://www.elastic.co/guide/en/fleet/current/agent-policy.html\"\u003eElastic Agent policy\u003c/a\u003e, Osquery is deployed to all agents assigned to that policy. Once that’s added, from Kibana, you can run live queries and schedule recurring queries for those agents to gather data from \u003ca href=\"https://osquery.io/schema/\"\u003ehundreds of tables\u003c/a\u003e across your entire enterprise. These capabilities help with real time incident response, threat hunting, and regular monitoring to detect vulnerability or compliance issues."}],"_metadata":{"uid":"cs3e9abc671b7889e3"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7798a49bc1bfba08","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:41:25.663Z","created_by":"bltc87e8bcd2aefc255","file_size":"118243","filename":"1-schedule-queries.png","parent_uid":null,"tags":[],"title":"1-schedule-queries.png","updated_at":"2021-12-14T18:41:25.663Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.399Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7798a49bc1bfba08/61b8e555c455652925b787df/1-schedule-queries.png"},"_metadata":{"uid":"cs745cb409ad67ec82"},"caption_l10n":"Run live queries","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blta36a97d483a6ebb6","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:41:49.519Z","created_by":"bltc87e8bcd2aefc255","file_size":"147455","filename":"2-it-compliance-details.png","parent_uid":null,"tags":[],"title":"2-it-compliance-details.png","updated_at":"2021-12-14T18:41:49.519Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.081Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta36a97d483a6ebb6/61b8e56dd73c783f9a3d157b/2-it-compliance-details.png"},"_metadata":{"uid":"cs9c959903e65051d2"},"caption_l10n":"Schedule queries","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7730b5eecd02bb9a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen you run live or scheduled queries, the results are automatically stored in an Elasticsearch index and can easily be \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/osquery.html#osquery-map-fields\"\u003emapped to the Elastic Common Schema\u003c/a\u003e, normalizing your data to a common set of fields to work with the SIEM app and enabling you to easily search, analyze, and visualize data across multiple sources. \u003c/p\u003e\u003ch2\u003eBuild security alerts for Osquery data\u003c/h2\u003e\n\u003cp\u003eOsquery surfaces a \u003ca href=\"https://osquery.io/schema/\"\u003ebroad swath of data\u003c/a\u003e about operating systems. When combined with the \u003ca href=\"https://www.elastic.co/security\"\u003eElastic Security\u003c/a\u003e solution, security teams are able craft queries that help them to detect threats within their environment, monitor for issues that matter the most to their organization, and then take action when there’s a problem.\u003c/p\u003e\n\u003cp\u003eAs an example, one issue to monitor is whether any of your systems have processes running where the executable is no longer on disk. This can be an indicator of a malicious process, for example, when malware deletes itself after execution to avoid detection. \u003c/p\u003e\n\u003cp\u003eYou can monitor this using Osquery across Windows, Linux, and Mac systems with a simple query:\u003c/p\u003e\n\u003cp\u003e\u003ccode\u003eSELECT * FROM processes;\u003c/code\u003e\u003c/p\u003e\n\u003cp\u003eThe response from the \u003ca href=\"https://osquery.io/schema/5.0.1#processes\"\u003eprocesses table\u003c/a\u003e includes several useful fields, like the name, \u003ccode\u003epid\u003c/code\u003e, and \u003ccode\u003epath\u003c/code\u003e of all running processes on the target systems, as well as whether the process path exists \u003ccode\u003eon_disk\u003c/code\u003e. If \u003ccode\u003eon_disk = 0\u003c/code\u003e for a process, that means the file is no longer on the disk and there may be an issue. This is a perfect use case for 1) scheduling a query to monitor for this across your fleet, and 2) creating an alert to notify you when a process is found that doesn’t have a binary on disk.\u003c/p\u003eWhile it’s possible to schedule a query that specifically checks for processes where no binary is on disk (for example, using \u003ccode\u003eSELECT name\u003c/code\u003e, \u003ccode\u003epath\u003c/code\u003e, \u003ccode\u003epid FROM processes WHERE on_disk = 0\u003c/code\u003e), it can be beneficial to schedule a broader query that retrieves \u003cem\u003eall\u003c/em\u003e fields for the processes table, because you can use that data to drive several cases you may want to monitor."}],"_metadata":{"uid":"cs91efd25470cdf424"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt47ee7a2c74db7e05","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:43:02.251Z","created_by":"bltc87e8bcd2aefc255","file_size":"58203","filename":"3-threat-detection-details.png","parent_uid":null,"tags":[],"title":"3-threat-detection-details.png","updated_at":"2021-12-14T18:43:02.251Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.198Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt47ee7a2c74db7e05/61b8e5b6c548b77c207db560/3-threat-detection-details.png"},"_metadata":{"uid":"cs4a5a26c1ef582c27"},"caption_l10n":"Scheduled query for all running processes","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs459c733b3b07ff1a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce this query is running regularly, you can then write a detection rule to alert you when query results include a process that’s missing a binary on disk. This example rule will alert if it finds any results for the running-processes query in the threat-detection pack where the on_disk field is 0.\u003c/p\u003e"}],"_metadata":{"uid":"cs49b38bdba10e8efd"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blted6c4a96ed50aaf8","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:43:35.235Z","created_by":"bltc87e8bcd2aefc255","file_size":"119881","filename":"4-running-process-without-binary.png","parent_uid":null,"tags":[],"title":"4-running-process-without-binary.png","updated_at":"2021-12-14T18:43:35.235Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.085Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blted6c4a96ed50aaf8/61b8e5d78ae3ee7d4c154be9/4-running-process-without-binary.png"},"_metadata":{"uid":"cs9f755689b7bcab2b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs26413050cc7b890a"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eQuery isolated hosts\u003c/h2\u003e\n\u003cp\u003eCombining Osquery with the \u003ca href=\"https://www.elastic.co/guide/en/security/current/es-overview.html\"\u003eEndpoint Security\u003c/a\u003e integration can take your security operations to the next level. With Endpoint Security enabled, when you are handling a security incident and suspect that a system has been compromised, you can \u003ca href=\"https://www.elastic.co/guide/en/security/current/host-isolation-ov.html\"\u003eisolate the host\u003c/a\u003e from your network to block communication and prevent lateral movement to other hosts. Isolating a host in this situation can give you time to investigate the issue and recover to a safe state. \u003c/p\u003e\n\u003cp\u003eWhile a host is isolated, it can still communicate with the Elastic Stack, and you can use Osquery to run live queries against the host to help with your investigation. For example, you can use it to help assess the impact and severity of the compromise or to confirm the issue has been resolved before releasing the host.\u003c/p\u003e"}],"_metadata":{"uid":"csbb35642bc67cc38b"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt594eaad526014424","ACL":{},"content_type":"image/gif","created_at":"2021-12-14T18:44:09.016Z","created_by":"bltc87e8bcd2aefc255","file_size":"1824389","filename":"5-monitoring-osquery.gif","parent_uid":null,"tags":[],"title":"5-monitoring-osquery.gif","updated_at":"2021-12-14T18:44:09.016Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.122Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt594eaad526014424/61b8e5f95b7db17e976062b0/5-monitoring-osquery.gif"},"_metadata":{"uid":"cs1f33037558a778e8"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0739893a1015e065"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eMonitor for anomalous host activities\u003c/h2\u003e\n\u003cp\u003eWith scheduled \u003ca href=\"https://github.com/osquery/osquery/tree/master/packs\"\u003equery packs\u003c/a\u003e, you can run a set of queries regularly to establish a baseline of behavior and activity on your hosts. The data you collect over time helps you to build an understanding of what normal operating conditions are like in your environment. For example, you can write queries to monitor for the applications users have installed, who logs into which systems, which programs run on startup, and many others. \u003c/p\u003e\n\u003cp\u003eWith \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/current/index.html\"\u003eElastic Machine Learning\u003c/a\u003e, you can create \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/current/ml-overview.html\"\u003eanomaly detection\u003c/a\u003e jobs for specific Osquery data that you’re collecting so that you can identify anomalous patterns in that data. \u003c/p\u003e\n\u003cp\u003eLet’s walk through an example that shows how to monitor for anomalous programs installed on Windows systems.\u003c/p\u003e\n\u003cp\u003eFirst, to establish a baseline, schedule a query to begin collecting all programs installed on your Windows systems. This query is set to run once a day and also maps a few Osquery values to ECS to standardize the data:\u003c/p\u003e"}],"_metadata":{"uid":"cs45e93943ea640b41"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt9f41511887e52558","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:44:37.914Z","created_by":"bltc87e8bcd2aefc255","file_size":"102651","filename":"6-edit-query.png","parent_uid":null,"tags":[],"title":"6-edit-query.png","updated_at":"2021-12-14T18:44:37.914Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.150Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f41511887e52558/61b8e61585b59c201581aba4/6-edit-query.png"},"_metadata":{"uid":"cs4b775f1c852cc153"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs53ec6c6aeb28f55a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNext, create a saved search that you’ll use later to create your anomaly detection job. The search is based on the \u003ccode\u003eaction_id\u003c/code\u003e of the scheduled query, which includes the pack name (\u003ccode\u003ewindows-hardening\u003c/code\u003e) and the query name (\u003ccode\u003ewindows-programs\u003c/code\u003e).\u003c/p\u003e"}],"_metadata":{"uid":"csdb5926a31099b90b"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt8972acc0d09962a2","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:45:08.465Z","created_by":"bltc87e8bcd2aefc255","file_size":"74312","filename":"7-discover-view.png","parent_uid":null,"tags":[],"title":"7-discover-view.png","updated_at":"2021-12-14T18:45:08.465Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.107Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8972acc0d09962a2/61b8e6349793463f93f419bb/7-discover-view.png"},"_metadata":{"uid":"csda907c2996b8840c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs201d8a9917883ad8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eUsing the saved search, you can now create a Machine Learning job that detects application anomalies in these search results. This job has a detector that looks for rare application names (package.name) in the Osquery results, and it is set to run continuously.\u003c/p\u003e"}],"_metadata":{"uid":"cs55e212ad34f2539c"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt1ce98bcab6ab017a","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:45:31.865Z","created_by":"bltc87e8bcd2aefc255","file_size":"161491","filename":"8-create-job.png","parent_uid":null,"tags":[],"title":"8-create-job.png","updated_at":"2021-12-14T18:45:31.865Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.105Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1ce98bcab6ab017a/61b8e64b130d6061708025c5/8-create-job.png"},"_metadata":{"uid":"cs9888806920be0c6c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab2a469de3d40a11"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eRunning this job helps to identify potential issues across your environment — for example, to find uncommon or unexpected applications that are installed on Windows workstations.\u003c/p\u003e"}],"_metadata":{"uid":"cs3240ce8741fdd82e"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7802382548a7fe6c","ACL":{},"content_type":"image/png","created_at":"2021-12-14T18:45:52.197Z","created_by":"bltc87e8bcd2aefc255","file_size":"85582","filename":"9-anomalies.png","parent_uid":null,"tags":[],"title":"9-anomalies.png","updated_at":"2021-12-14T18:45:52.197Z","updated_by":"bltc87e8bcd2aefc255","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-04T14:00:00.115Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7802382548a7fe6c/61b8e66085b59c201581aba8/9-anomalies.png"},"_metadata":{"uid":"csc03efa740af48b14"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7c71a93a001d21f7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhile outliers may be benign, they can also be an indicator of unwanted activity in your environment. Once you start capturing anomalies, you can write detection rules to alert on instances that merit investigation.\u003c/p\u003e\u003ch2\u003eGive Osquery Manager a try\u003c/h2\u003e\n\u003cp\u003eThe Osquery Manager integration gives you greater insight into the endpoints you’re monitoring with the Elastic Security solution and helps security teams to better detect, investigate, and hunt for vulnerabilities and anomalous activities. \u003c/p\u003eIf you want to give all this a try and see how easy it is to deploy Osquery Manager and start running queries, you can start a \u003ca href=\"https://cloud.elastic.co/registration\"\u003efree 14-day trial of Elastic\u003c/a\u003e. Please share any feedback on the \u003ca href=\"https://discuss.elastic.co/\"\u003eElastic Discuss forum\u003c/a\u003e or the \u003ca href=\"https://ela.st/slack\"\u003eElastic Stack Community on Slack\u003c/a\u003e."}],"_metadata":{"uid":"cs79cc1c1c20e1e68b"}}}],"publish_date":"2022-01-04T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Osquery Manager for Elastic","seo_description_l10n":"Easily deploy and run Osquery across your environments to gather valuable insight into your data. Reduce investigation time by identifying incident telemetry and isolate hosts as needed.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blte50385d14a2cee80","created_by":"bltf020187e3918e5de","updated_by":"bltf020187e3918e5de","created_at":"2021-11-04T07:42:30.648Z","updated_at":"2021-11-04T07:42:30.648Z","content_type":"image/png","file_size":"85196","filename":"apac-anomaly-detection-event-illo.png","title":"apac-anomaly-detection-event-illo.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-04T07:42:56.531Z","user":"bltf020187e3918e5de"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte50385d14a2cee80/61838ee6912a3c799bc4284f/apac-anomaly-detection-event-illo.png"},"title":"Gain the upper hand over adversaries with Osquery and Elastic","title_l10n":"Gain the upper hand over adversaries with Osquery and Elastic","updated_at":"2025-03-28T17:16:10.497Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/gain-upper-hand-over-adversaries-with-osquery-and-elastic","publish_details":{"time":"2025-03-28T17:16:16.042Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0f261ad95c4956c0","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Until today, there was no simple way to visualize how the flow of your eBPF program running in the kernel was. Hopefully, there is one starting today.","author":["bltbf89aefee1aed525"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-02-01T18:45:38.802Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs416c983dce47da33"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eI bet we all have heard so much about eBPF in recent years. Data shows that eBPF is quickly becoming the first choice for implementing tracing and security applications, and Elastic is also working relentlessly on supercharging our \u003ca href=\"/security\"\u003esecurity solutions\u003c/a\u003e (and more) with eBPF. \u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs6f7e874922e4adaa"},"header_style":"H2","paragraph_l10n":"However, one major challenge is that the eBPF ecosystem lacks tooling to make developers' lives easier. eBPF programs are written in C but compiled for a specific ISA later executed by the eBPF Virtual Machine. LLVM has a specific backend allowing us to write C and get eBPF ELF objects out. There are no tools helping developers to clearly understand which path their code took while running in the Linux kernel, which code regions, or, even better, code branches are uncovered, and maybe why.\n"},{"title_l10n":"","_metadata":{"uid":"csf1b94d9ec7dcc84d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"http://github.com/elastic/bpfcov\"\u003eThat's why I sat down and wrote bpfcov\u003c/a\u003e: a tool to gather source-based coverage info for our eBPF programs running in the Linux kernel. Whether they are getting loaded via \u003ccode\u003eBPF_PROG_TEST_RUN\u003c/code\u003e or by other ordinary means. Until today, there was no simple way to visualize how the flow of your eBPF program running in the kernel was. Hopefully, there is one starting today.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csd9af2a09fc2a81bd"},"header_style":"H2","paragraph_l10n":"So, let's jump straight into the topic."},{"title_l10n":"Source-based code coverage for eBPF","_metadata":{"uid":"cs23a662a6275b93de"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"","_metadata":{"uid":"csc8ac1622b4a9543f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eEveryone reading this post probably knows what the code coverage is. Common line-level coverage gives us a sense of what line is executed. In some cases, it even tells us how many times a line got executed. \u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs89daeda5548ea4cf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen building this tool, driven by my experience fighting with BPF, I knew I wanted something more. Line-level granularity is often too coarse. We do not want an approximation of what code actually executed.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csea2809ccd04c6ce8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe need something more precise to understand the execution path of our eBPF programs in the Linux kernel. We even want to know what part of an `if` conditional executed. Source-based code coverage is what I wanted for this reason.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs9c3d7612a44452ea"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSince it starts at code generation time in LLVM, it has the notion of regions of the code, branches, and so on. It even precisely counts things like short-circuited conditionals, thanks to the counter expression and arithmetics between them. It generates coverage summaries with very fined-grained code regions, helping us find grasps in the code and its execution flow.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs8f7e693bfeade132"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSo, given eBPF programs are usually written in C, couldn’t we just instrument them for \u003ca href=\"https://clang.llvm.org/docs/SourceBasedCodeCoverage.html\"\u003esource-based code coverage\u003c/a\u003e as we would commonly do with Clang for our C programs? I bet this is the first argument pumping into the head of many readers. It also was one of my thoughts when approaching this problem. Turns out that we definitely can, and we will do it. But it won’t work as is.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs1d20fe8a470f93c2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eTo understand why it won’t work, we need to keep in mind that BPF programs are compiled via Clang (thanks to the \u003ca href=\"https://github.com/llvm/llvm-project/tree/main/llvm/lib/Target/BPF\"\u003eLLVM BPF target\u003c/a\u003e) to BPF ELF object files, containing instructions specific to the chosen BPF instruction set, which need to be later loaded in the Linux kernel via the \u003ca href=\"https://www.kernel.org/doc/html/latest/userspace-api/ebpf/syscall.html\"\u003ebpf()\u003c/a\u003e syscall. Furthermore, it’s paramount to mention that the BPF programs will be verified by an in-kernel verifier and then executed by the BPF VM.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csc166b012c86faf92"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSuch a lifecycle and environment imposes a set of constraints that make it infeasible to get them working with the plain instrumentation that LLVM applies to get source-based code coverage. In fact, when compiling a C program for source-based coverage with the \u003ccode\u003e-fprofile-instr-generate\u003c/code\u003e and \u003ccode\u003e-fcoverage-mapping\u003c/code\u003e Clang flags, LLVM instruments it with a bunch of global variables and, in some cases, functions.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs1c2bf44d583ee7c3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eObserving the LLVM IR of a C program after compiling it with the \u003ccode\u003e-fprofile-instr-generate\u003c/code\u003e flag, we can notice that, LLVM…\u003c/p\u003e\n\u003cul\u003e\u003cli\u003edefines the counters, in the form of \u003ccode\u003e__profc_\u0026lt;function_name\u0026gt;\u003c/code\u003e private global arrays whose size is the number of counters needed to cover all the regions and branches of such a function\u003c/li\u003e\u003cli\u003emarks those counters to be into the `__llvm_prf_cnts` section of the ELF\u003c/li\u003e\u003cli\u003edefines (and initializes) \u003ccode\u003e__profd_\u0026lt;function_name\u0026gt;\u003c/code\u003e private global struct instances that contains an identifier of the function, the pointer to its counters, the pointer to the function itself, the number of the counters for the target function, and a bunch of other info needed to tie together the counters and the coverage mappings\u003c/li\u003e\u003cli\u003emarks the \u003ccode\u003e__profd_\u003c/code\u003e globals to end up into the \u003ccode\u003e__llvm_prf_data\u003c/code\u003e section of the ELF\u003c/li\u003e\u003cli\u003edefines (and initializes) a private constant (\u003ccode\u003e__llvm_prf_nm\u003c/code\u003e) containing the names of the target functions\u003c/li\u003e\u003cli\u003emarks the names constant to end up in the \u003ccode\u003e__llvm_prf_names\u003c/code\u003e section of the ELF\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"","_metadata":{"uid":"cs108db5a94c42c54c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe first issue to dismount here is that we can't have random ELF sections (like \u003ccode\u003e__llvm_prf_cnts\u003c/code\u003e, etc.) into valid BPF ELF files.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs1bb0bdede0a149fa"},"header_style":"H2","paragraph_l10n":"We know that we can have eBPF global constants with a scalar type like \u003ccode\u003e__profc_\u003c/code\u003e ones, at least on recent Linux kernels. At the same time, we know it's not wise to have global structs like \u003ccode\u003e__profd_\u003c/code\u003e or whatever loader for our eBPF programs we will write, as we'll need the struct definitions. Too clunky."},{"title_l10n":"","_metadata":{"uid":"cs58d0179f62eff06a"},"header_style":"H2","paragraph_l10n":"The \u003ccode\u003e-fprofile-instr-generate\u003c/code\u003e flag also generates a global constructor and a set of global functions, all prefixed with \u003ccode\u003e__llvm_profile\u003c/code\u003e, intended to set up the profiling runtime in the resulting binary so that when it dies or exits it will automatically generate a \u003ccode\u003eprofraw\u003c/code\u003e file."},{"title_l10n":"","_metadata":{"uid":"cs70e2cd2df54eb8e8"},"header_style":"H2","paragraph_l10n":"Here we meet another stumbling block to overcome. The BPF verifier will refuse our BPF ELF containing strange global functions, not to mention \"constructors\"..."},{"title_l10n":"","_metadata":{"uid":"cs6b5aa6b43204ded8"},"header_style":"H2","paragraph_l10n":"We need to get rid of them and replace their functionality with a feasible approach for BPF. Clearly, LLVM also patches our instructions in the right spots, by placing the counters and incrementing them. As you can see in the following annotated screenshot:"}],"_metadata":{"uid":"cs9ff8829d219f5f2e"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt1288e08485151449","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:13:35.853Z","created_by":"blt3044324473ef223b70bc674c","file_size":"441646","filename":"code-coverage-ebpf-programs-annotated-screenshot-llvm-patches-our-instructions.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-annotated-screenshot-llvm-patches-our-instructions.png","updated_at":"2022-02-01T18:13:35.853Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.618Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1288e08485151449/61f9784fd970ea1bb42ad274/code-coverage-ebpf-programs-annotated-screenshot-llvm-patches-our-instructions.png"},"_metadata":{"uid":"cs55a7274bf7e8680e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs36f493dbd5fc52e3"},"header_style":"H2","paragraph_l10n":"If you write an eBPF program incrementing a counter (defined as an eBPF global variable) you will notice that the resulting instructions will be like those here in the screenshot. It means we can keep these the way they are generated by LLVM and let it do all its magic without interfering at the instructions level. Finally, some good news!"},{"title_l10n":"","_metadata":{"uid":"cse9d4b2936575342e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eInstead, focusing on the \u003ccode\u003e-fcoverage-mapping\u003c/code\u003e Clang flag and inspecting the LLVM IR it outputs, we notice that it…\u003c/p\u003e\u003cul\u003e\u003cli\u003edefines (and initializes) \u003ccode\u003e__covrec_\u003c/code\u003e global (constant) structs, most notably containing the same ID that the \u003ccode\u003e__profd_\u003c/code\u003e variables contain, and a \u003ca href=\"https://en.wikipedia.org/wiki/LEB128\"\u003eLEB128\u003c/a\u003e encoded string containing all the region, branches, and generally the \u003ca href=\"https://llvm.org/docs/CoverageMappingFormat.html\"\u003ecoverage mapping\u003c/a\u003e info\u003c/li\u003e\u003cli\u003edefines (and initializes) a \u003ccode\u003e__llvm_coverage_mapping\u003c/code\u003e function containing meta info about the coverage mapping format (eg., the version), and the source file names\u003c/li\u003e\u003cli\u003emarks the \u003ccode\u003e__llvm_coverage_mapping\u003c/code\u003e variable to be put into the \u003ccode\u003e__llvm_covmap\u003c/code\u003e section of the ELF\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"","_metadata":{"uid":"cs6faa292867bb024b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this case, we have the same category of issues mentioned before.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csadc769cdf0dc86af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe need to keep at least the header of \u003ccode\u003e__llvm_coverage_mapping\u003c/code\u003e because it contains the coverage mappings version, which we need for generating a valid \u003ccode\u003eprofraw\u003c/code\u003e file. Also, we need to put it in a BPF.\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs5fb3446f6d57863a"},"header_style":"H2","paragraph_l10n":"Luckily, we can remove the \u003ccode\u003e__covrec_\u003c/code\u003e structs from the BPF ELF meant to be loaded in the kernel. We can keep them in a second BPF ELF that would be intended to be given to tools needing the coverage mappings for generating the coverage reports, just like \u003ccode\u003ellvm-cov\u003c/code\u003e does.\n"},{"title_l10n":"How it's done","_metadata":{"uid":"cs911b0b49fe96261d"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"libBPFCov.so - A LLVM pass","_metadata":{"uid":"cs6b7210e82ecb4c52"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eBy analyzing the resulting LLVM IR for source-based coverage instrumented programs, we should now have a better understanding of what we need to do for having it on eBPF programs running in the Linux kernel. We now know what to completely get rid of and do differently, and what we need to patch to make it loadable and usable by the BPF VM in the kernel.\u003c/p\u003e\n\u003cp\u003eThe plan is simple: get Clang to instrument a BPF LLVM intermediate representation for source-based code coverage, then patch it to model it into a valid representation for BPF ELF. How do we need to transform it?\u003c/p\u003e\n\u003cp\u003eFirst of all, we are so lucky we don’t have to mess with the actual BPF instructions — namely the counters increments. We can keep them the way they are. This is a huge win because we let LLVM keep track of the global state of the registers and we avoid a lot of work this way.\u003c/p\u003e\n\u003cp\u003eBut for sure we have to strip any profile initialization stuff that Clang creates, things like \u003ccode\u003e__llvm_profile_runtime\u003c/code\u003e and \u003ccode\u003e__llvm_profile_init\u003c/code\u003e - when present - are no good for the BPF VM in the kernel.\u003c/p\u003e\n\u003cp\u003eWe also want to ensure the global variables, whether constants or not, have the right visibility (ie., \u003ccode\u003edso_local\u003c/code\u003e) and linkage, to have them in the \u003ccode\u003elibbpf\u003c/code\u003e skeletons if we plan to use them.\u003c/p\u003e\n\u003cp\u003eFor the global structs that we need for generating the \u003ccode\u003eprofraw\u003c/code\u003e files, namely the \u003ccode\u003e__profd_\u003c/code\u003e variables, we just transform them into different and single global variables, one for each field. \u003c/p\u003e\n\u003cp\u003eFor example, this is what I did for the \u003ccode\u003e__profd_*\u003c/code\u003e variables which originally are a struct with 7 fields. For other global structs like the \u003ccode\u003e__covrec_\u003c/code\u003e ones, we can just strip them from the BPF ELF that is meant to be loaded in the kernel.\u003c/p\u003e\n\u003cp\u003eAnyway, the report generation phase (ie., \u003ccode\u003ellvm-cov\u003c/code\u003e or \u003ccode\u003ebpfcov out\u003c/code\u003e) will need them for knowing at which line and column a code region or a branch starts. For this reason, I decided to give the LLVM pass an option (enabled with the \u003ccode\u003estrip-initializers-only\u003c/code\u003e flag) that keeps them, so we can later create a BPF ELF that is only meant for this phase and not for loading.\u003c/p\u003e\n\u003cp\u003eThis BPF ELF will have \u003ccode\u003e.bpf.obj\u003c/code\u003e as an extension, rather than \u003ccode\u003e.bpf.o\u003c/code\u003e.\u003c/p\u003e\n\u003cp\u003eFinally, we know that \u003ca href=\"https://github.com/libbpf/libbpf\"\u003elibbpf\u003c/a\u003e supports (on recent Linux kernels) eBPF global variables, which are simply eBPF maps with one single value, and we are planning to use them. But, as already mentioned, it does not accept or recognize the ELF sections that the Clang instrumentation injects in the intermediate representation.\u003c/p\u003e\n\u003cp\u003eSo we need our LLVM pass to change them to \u003ca href=\"https://lore.kernel.org/bpf/20211021014404.2635234-8-andrii@kernel.org/\"\u003ecustom eBPF sections\u003c/a\u003e. The eBPF custom sections are in the form of \u003ccode\u003e.rodata.*\u003c/code\u003e or \u003ccode\u003e.data.*\u003c/code\u003e made to contain static and/or global data. We can change the section of the counters to be \u003ccode\u003e.data.profc\u003c/code\u003e. The section of the \u003ccode\u003e__llvm_prf_nm\u003c/code\u003e from \u003ccode\u003e_llvm_prf_names\u003c/code\u003e to \u003ccode\u003e.rodata.profn\u003c/code\u003e, and so on. You can find all this logic summarized in these \u003ca href=\"https://github.com/elastic/bpfcov/blob/5607ee6b5419cd72dfd9c17e00455188865f8766/lib/BPFCov.cpp#L660-L694\"\u003ebits of code\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eSo, assuming the following dummy eBPF program:\u003c/p\u003e"}],"_metadata":{"uid":"cs092767ecf955024e"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt27273abc3e684c98","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:22:59.347Z","created_by":"blt3044324473ef223b70bc674c","file_size":"112429","filename":"code-coverage-ebpf-programs-dummy-ebpf.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-dummy-ebpf.png","updated_at":"2022-02-01T18:22:59.347Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.612Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt27273abc3e684c98/61f97a835865427ee15b8b0b/code-coverage-ebpf-programs-dummy-ebpf.png"},"_metadata":{"uid":"cs505da65cc847b068"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs691076c666e50aac"},"header_style":"H2","paragraph_l10n":"I think that the following snippet tells everything about what we obtain from the \u003ccode\u003elibBPFCov.so\u003c/code\u003e LLVM pass:\n\n"}],"_metadata":{"uid":"cs24063bea78bb2569"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt76355cdd32316d3b","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:25:59.116Z","created_by":"blt3044324473ef223b70bc674c","file_size":"516806","filename":"code-coverage-ebpf-programs-snippet-everything-about-libbpfcovso-llvm-pass.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-snippet-everything-about-libbpfcovso-llvm-pass.png","updated_at":"2022-02-01T18:25:59.116Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.606Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt76355cdd32316d3b/61f97b37dc6df77ee044f786/code-coverage-ebpf-programs-snippet-everything-about-libbpfcovso-llvm-pass.png"},"_metadata":{"uid":"cs6831065737bd488f"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9b3c138551226a6c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor example, you may notice that we have 2 \u003ccode\u003e__profc_\u003c/code\u003e counters.\u003c/p\u003e\n\u003cp\u003eThe first is for the \u003ccode\u003eBPF_PROG\u003c/code\u003e macro that expands to a function, the second for the actual BPF raw tracepoint program \u003ccode\u003ehook_sys_enter\u003c/code\u003e. This one has size 3. That’s because the \u003ccode\u003ehook_sys_enter\u003c/code\u003e function has 3 main regions: the entry of the function, the \u003ccode\u003eif\u003c/code\u003e conditional, and the \u003ccode\u003efor\u003c/code\u003e cycle.\u003c/p\u003e\n\u003cp\u003eYou may also notice that the LLVM pass, for each one of the 2 functions we have, split the \u003ccode\u003e__profd_\u003c/code\u003e global structs into 7 different global variables in the \u003ccode\u003e.rodata.profd\u003c/code\u003e section.\u003c/p\u003e\n\u003cp\u003eSomeone who has an eye for it may also have noticed that the third field of \u003ccode\u003e__profd_\u003c/code\u003e — now \u003ccode\u003e__profd_something.2\u003c/code\u003e — does not contain anymore the address of its counters. I didn’t want (nor I could) to expose kernel addresses, so I put here the offset of the counters in their section (\u003ccode\u003e.data.profc\u003c/code\u003e).\u003c/p\u003e\n\u003cp\u003eFinally, you can also see that, as anticipated before, we completely deleted the \u003ccode\u003e__covrec_\u003c/code\u003e global constant structs from this IR that’s meant to generate a valid and loadable BPF ELF. While the instructions incrementing the counters in the correct spots are not touched at all. So we don’t need another screenshot to show them!\u003c/p\u003e\n\u003cp\u003eThe only missing moving part is how to generate a valid \u003ccode\u003eprofraw\u003c/code\u003e file. We stripped any logic for doing it. We know that for generating it we need all the globals we left in this LLVM intermediate representation. But we have no sane way to hook the exit or the stop of an eBPF program in the Linux kernel.\u003c/p\u003e\n\u003cp\u003eSuddenly, inspiration came: let’s pin the globals to the BPF file system so that we can decouple the process of generating the \u003ccode\u003eprofraw\u003c/code\u003e file from the running (and exiting) of the instrumented eBPF application!\u003c/p\u003e\n\u003cp\u003eAnd that’s what the \u003ccode\u003ebpfcov\u003c/code\u003e CLI does.\u003c/p\u003e\n\u003cp\u003eBefore moving to the next section, I suggest you go to the bpfcov repository and start building the pass to obtain \u003ccode\u003elibBPFCov.so\u003c/code\u003e. You can find the instructions on how to build it \u003ca href=\"https://github.com/elastic/bpfcov/blob/main/README.md#building\"\u003ehere\u003c/a\u003e.\u003c/p\u003e"},{"title_l10n":"Instrument your eBPF program","_metadata":{"uid":"cs42e1c4796cbb9df4"},"header_style":"H2","paragraph_l10n":"Now that we have built \u003ccode\u003elibBPFCov.so\u003c/code\u003e we can finally take action!\n\nInstrumenting an eBPF program for source-based coverage is not that different than compiling it normally with Clang and the BPF target.\n\nThe only difference is that we ask Clang to output LLVM IR (either in textual or binary form), run the \u003ccode\u003elibBPFCov.so\u003c/code\u003e pass on it (with \u003ccode\u003eopt\u003c/code\u003e), and finally compile it (with \u003ccode\u003ellc\u003c/code\u003e) to a BPF ELF.\n\n"}],"_metadata":{"uid":"cs4b6bb37fdceb88fe"}}},{"code":{"code":"bash\nclang -g -O2 \\\n -target bpf \\\n -D__TARGET_ARCH_x86 -I$(YOUR_INCLUDES) \\\n -fprofile-instr-generate -fcoverage-mapping \\\n -emit-llvm -S \\\n -c raw_enter.bpf.c -o raw_enter.bpf.ll\n\nopt -load-pass-plugin $(BUILD_DIR)/lib/libBPFCov.so -passes=\"bpf-cov\" \\\n -S raw_enter.bpf.ll -o raw_enter.bpf.cov.ll\n\nllc -march=bpf -filetype=obj -o cov/raw_enter.bpf.o raw_enter.bpf.cov.ll","_metadata":{"uid":"csc87ca53f859f966e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csee7f7fc6992886b7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou can see in the Makefile inside the \u003ccode\u003eexamples/src\u003c/code\u003e directory of the bpfcov GitHub repository how to automate those steps.\u003c/p\u003e\n\n\u003cp\u003eWe now have a valid and coverage instrumented BPF ELF: \u003ccode\u003ecov/raw_enter.bpf.o\u003c/code\u003e.\u003c/p\u003e\n\n\u003cp\u003eFrom now on, you can instruct your loader and userspace code to use it, so to obtain a binary (eg., \u003ccode\u003e/cov/raw_enter\u003c/code\u003e) that is your eBPF application.\u003c/p\u003e"},{"title_l10n":"Use it","_metadata":{"uid":"csefc697ee609a0ee6"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"bpfcov run + bpfcov gen","_metadata":{"uid":"csddc8d2a4dbb5d45b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eWhat's left to do? Just three steps:\u003c/p\u003e\n\u003col\u003e\n\u003cli\u003eRun our eBPF application with the bpfcov CLI run command\u003c/li\u003e\n\u003cli\u003eGenerate its \u003ccode\u003eprofraw\u003c/code\u003e file\u003c/li\u003e\n\u003cli\u003eGenerate beautiful source-based coverage reports\u003c/li\u003e\n\u003c/ol\u003e\n\u003cp\u003eSo, let's run our eBPF application with:\u003c/p\u003e"}],"_metadata":{"uid":"cs5df4287142d52a16"}}},{"code":{"code":"bash\nsudo ./bpfcov -v2 run cov/raw_enter","_metadata":{"uid":"cs9b0bc57d9f1a1d84"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs23488a17aff508bf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis command acts similar to strace. It will detect the \u003ccode\u003ebpf()\u003c/code\u003e syscalls with the \u003ccode\u003eBPF_MAP_CREATE\u003c/code\u003e command.\u003c/p\u003e\n\u003cp\u003eMeaning that it will detect the eBPF globals in the \u003ccode\u003e.profc\u003c/code\u003e, \u003ccode\u003e.profd\u003c/code\u003e, \u003ccode\u003e.profn\u003c/code\u003e, and \u003ccode\u003e.covmap\u003c/code\u003e custom eBPF sections and pin them to the BPF file system, as you can see in the following screenshot.\u003c/p\u003e"}],"_metadata":{"uid":"cs18d378b9b3cc8be0"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt343f22aa081b0b35","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:33:25.012Z","created_by":"blt3044324473ef223b70bc674c","file_size":"329374","filename":"code-coverage-ebpf-programs-detect-ebpf-globals.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-detect-ebpf-globals.png","updated_at":"2022-02-01T18:33:25.012Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.600Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt343f22aa081b0b35/61f97cf5c1f2271a3225de62/code-coverage-ebpf-programs-detect-ebpf-globals.png"},"_metadata":{"uid":"cs53c0df8e0068dec9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0be1482b14272617"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou may also notice that - since the LLVM pass annotated the counters correctly - \u003ccode\u003elibbpf\u003c/code\u003e can collect relocations for them…\u003c/p\u003e\n\u003cp\u003eAt this point, whether we stopped our eBPF application or it exited… We have eBPF maps pinned to our BPF file system. Let’s check it:\u003c/p\u003e"}],"_metadata":{"uid":"cs67e541c35fef892a"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt5a75c2954d242864","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:34:32.029Z","created_by":"blt3044324473ef223b70bc674c","file_size":"87207","filename":"code-coverage-ebpf-programs-ebpf-maps-pinned.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-ebpf-maps-pinned.png","updated_at":"2022-02-01T18:34:32.029Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.594Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5a75c2954d242864/61f97d38d8212f3e7b5e9a3e/code-coverage-ebpf-programs-ebpf-maps-pinned.png"},"_metadata":{"uid":"cs914b5f9c5ea83fd6"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa669482f44f7e080"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWonderful, we already know that the \u003ccode\u003ehook_sys_enter\u003c/code\u003e function executed one time, the \u003ccode\u003eif\u003c/code\u003e condition did not evaluate to true, while the \u003ccode\u003efor\u003c/code\u003e iterated nine times!\u003c/p\u003e\n\u003cp\u003eIt’s time to put the counters, the function names, the functions data, in a \u003ccode\u003eprofraw\u003c/code\u003e file now.\u003c/p\u003e\n\u003cp\u003eThis is why I created the \u003ccode\u003ebpfcov gen\u003c/code\u003e command exists: to dump the pinned maps in a \u003ccode\u003eprofraw\u003c/code\u003e file.\u003c/p\u003e"}],"_metadata":{"uid":"csa2f2ec1c1e0c272a"}}},{"code":{"code":"shell\nsudo ./bpfcov -v2 gen –unpin cov/raw_enter","_metadata":{"uid":"csaca08406c609a564"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt86e90993d73953bc","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:36:47.842Z","created_by":"blt3044324473ef223b70bc674c","file_size":"52076","filename":"code-coverage-ebpf-programs-bpfcovgen-command.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-bpfcovgen-command.png","updated_at":"2022-02-01T18:36:47.842Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.586Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86e90993d73953bc/61f97dbfd970ea1bb42ad284/code-coverage-ebpf-programs-bpfcovgen-command.png"},"_metadata":{"uid":"cs52aceb9ce9022ad5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf2295fbb3637e56c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAnd this is the resulting \u003ccode\u003eprofraw\u003c/code\u003e file for our instrumented eBPF program!\u003c/p\u003e\n\u003cp\u003eYou can see it’s made of four parts: a header, \u003ccode\u003e.rodata.profd\u003c/code\u003e, \u003ccode\u003e.data.profc\u003c/code\u003e (ie., the counters!), and the names (\u003ccode\u003e.rodata.profn\u003c/code\u003e), plus some padding for alignment…\u003c/p\u003e"}],"_metadata":{"uid":"cs4e88aa9e00beb12d"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt39920bda1252d59c","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:38:19.399Z","created_by":"blt3044324473ef223b70bc674c","file_size":"73952","filename":"code-coverage-ebpf-programs-profraw-file.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-profraw-file.png","updated_at":"2022-02-01T18:38:19.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.579Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt39920bda1252d59c/61f97e1b847be764b351bb28/code-coverage-ebpf-programs-profraw-file.png"},"_metadata":{"uid":"cs4c7746d145fd6817"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs32a7a457c591b4c5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe can now either use the existing LLVM tools (\u003ccode\u003ellvm-profdata\u003c/code\u003e and \u003ccode\u003ellvm-cov\u003c/code\u003e) with it or simply use the \u003ccode\u003eout\u003c/code\u003e subcommand.\u003c/p\u003e\n\u003cp\u003eThe \u003ccode\u003ebpfcov out\u003c/code\u003e command is an opinionated shortcut to generate HTML, JSON, or LCOV coverage reports even from multiple eBPF programs and their \u003ccode\u003eprofraw\u003c/code\u003e files.\u003c/p\u003e\n\u003cp\u003eIt is very convenient because it avoids us having to generate \u003ccode\u003eprofdata\u003c/code\u003e from the \u003ccode\u003eprofraw\u003c/code\u003e, calling \u003ccode\u003ellvm-cov\u003c/code\u003e with a bunch of long and different options. And it even works with multiple \u003ccode\u003eprofraw\u003c/code\u003e files coming from different eBPF applications…\u003c/p\u003e"}],"_metadata":{"uid":"csd3f1f13af592571f"}}},{"code":{"code":"shell\n./bpfcov out -o yey –f html \\\n cov/raw_enter.profraw …","_metadata":{"uid":"csb2256ea5034f67cb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf4cf3768fedfbe0a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt outputs a very nice HTML directory whose index file gives us summaries not only about function and line coverage but also and notably about region and branch coverages for our eBPF applications.\u003c/p\u003e"}],"_metadata":{"uid":"cs34c468b36f329a57"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt26ff757402407978","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:40:58.095Z","created_by":"blt3044324473ef223b70bc674c","file_size":"79727","filename":"code-coverage-ebpf-programs-coverage-report.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-coverage-report.png","updated_at":"2022-02-01T18:40:58.095Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.572Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt26ff757402407978/61f97eba19a2b06354d109fe/code-coverage-ebpf-programs-coverage-report.png"},"_metadata":{"uid":"csdef8f551cf1bf77e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs13202e3ec1884328"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBy clicking on any item in the table we end up visualizing very fine-grained, source-based coverage. A good example is the one in the following image:\u003c/p\u003e"}],"_metadata":{"uid":"cscdcfd5efa1fd6194"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt462d132dfef359ed","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:41:44.266Z","created_by":"blt3044324473ef223b70bc674c","file_size":"96492","filename":"code-coverage-ebpf-programs-source-based-coverage.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-source-based-coverage.png","updated_at":"2022-02-01T18:41:44.266Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.565Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt462d132dfef359ed/61f97ee8847be764b351bb30/code-coverage-ebpf-programs-source-based-coverage.png"},"_metadata":{"uid":"cs6d4bd75cc114dd02"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9d9ceece6e027cbd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFurthermore, it does work also on very complicated and real-life eBPF programs. For example, the following screenshot is a part of the coverage report obtained for a BPF LSM test (\u003ca href=\"https://github.com/torvalds/linux/blob/master/tools/testing/selftests/bpf/progs/lsm.c\"\u003eprogs/lsm.c\u003c/a\u003e, loaded by \u003ca href=\"https://github.com/torvalds/linux/blob/master/tools/testing/selftests/bpf/prog_tests/test_lsm.c\"\u003eprog_tests/test_lsm.c\u003c/a\u003e) living in the Linux kernel.\u003c/p\u003e"}],"_metadata":{"uid":"cs7ed64550c0c450b1"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7465c14ed8595511","ACL":{},"content_type":"image/png","created_at":"2022-02-01T18:42:36.954Z","created_by":"blt3044324473ef223b70bc674c","file_size":"120366","filename":"code-coverage-ebpf-programs-coverage-report-living-in-linux-kernel.png","parent_uid":null,"tags":[],"title":"code-coverage-ebpf-programs-coverage-report-living-in-linux-kernel.png","updated_at":"2022-02-01T18:42:36.954Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-01T18:52:33.554Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7465c14ed8595511/61f97f1c7ece8a1a37f715f1/code-coverage-ebpf-programs-coverage-report-living-in-linux-kernel.png"},"_metadata":{"uid":"csb3e6f0f6d953d08a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs660943e1e6112923"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThanks to this tool I can finally understand that over a total of eight executions of the \u003ccode\u003elsm/file_mprotect\u003c/code\u003e BPF LSM program on my kernel, its \u003ccode\u003eis_stack\u003c/code\u003e variable was true two times out of eight, because six times the \u003ccode\u003evma-\u0026gt;vm_end \u0026gt;= vma-\u0026gt;vm_mm-\u0026gt;start_stack\u003c/code\u003e branch condition (98:58) evaluated to false. \u003c/p\u003e\n\u003cp\u003eLine 100, using \u003ccode\u003eis_stack\u003c/code\u003e in another condition, confirms that it was indeed true two times out of six. And that, for this reason (first operand - 100:6 - \u003ccode\u003eis_stack\u003c/code\u003e being false six times), the following check (100:18) on \u003ccode\u003emonitored_pid\u003c/code\u003e was short-circuited and evaluated (to true, by the way) only two times.\u003c/p\u003e\n\u003cp\u003eWe finally have a tool helping us write and understand the way our eBPF programs run in the Linux kernel. I can’t stress enough how this is something I dreamt of so many times during the past few years I’ve been working with BPF…\u003c/p\u003e\n\u003cp\u003eHope that the eBPF community and ecosystem will find bpfcov useful and cool the same way I do.\u003c/p\u003e"},{"title_l10n":"Bits on the future","_metadata":{"uid":"cs0fdb95c3d068441b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe \u003ca href=\"https://ela.st/bpfcov\"\u003ebpfcov\u003c/a\u003e tool is open-source, and it will stay that way. It is still in its early days so it will probably need a bit more tests, examples, and fixes. Just like any new software out there.\u003c/p\u003e\n\u003cp\u003eI will soon publish another project showcasing the coverage of the kernel BPF selftests, using this tool. This means there are a lot of contribution opportunities. I’d invite you to take a look at \u003ca href=\"https://ela.st/bpfcov\"\u003eits source code\u003c/a\u003e and send patches! :)\u003c/p\u003e\n\u003cp\u003eAlso, in case you want to start using it on your eBPF applications and repositories, feel free to contact me for support. I’d love to help you to use it.\u003c/p\u003e\n\u003cp\u003eFrom a technical perspective these are the topics that are on top of my mind for its future:\u003c/p\u003e\u003cul\u003e\u003cli\u003eA project like bpfcov must have a logo!\u003c/li\u003e\u003cli\u003eWrite \u003ccode\u003ellvm-lit\u003c/code\u003e tests for the \u003ccode\u003elibBPFCov.so\u003c/code\u003e LLVM pass\u003c/li\u003e\u003cli\u003eSupport newer LLVM versions\u003c/li\u003e\u003cli\u003eWorkaround solutions to have it working on Linux kernels where BPF does not support custom eBPF sections and eBPF globals\u003c/li\u003e\u003cli\u003eCreate a versioning and release process\u003c/li\u003e\u003cli\u003ePublish artifacts on GitHub (\u003ccode\u003elibBPFCov.so\u003c/code\u003e, bpfcov CLI binary)\u003c/li\u003e\u003cli\u003eAdd more examples\u003c/li\u003e\u003cli\u003ePublish HTML reports of the example eBPF applications via GitHub pages\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Come see bpfcov at FOSDEM 2022","_metadata":{"uid":"cs46370fa89bf9558d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn case you made it to the end, and you still want to hear more details on building source-based coverage for eBPF, or you want to ask questions to its \u003ca href=\"https://twitter.com/leodido\"\u003eauthor\u003c/a\u003e, please join this \u003ca href=\"https://ela.st/bpfcov-fosdem-22\"\u003etalk at FOSDEM 2022\u003c/a\u003e on Feb 5.\u003c/p\u003e\n\u003cp\u003eYou can already take a look at the \u003ca href=\"https://ela.st/coverage-for-ebpf-programs-deck\"\u003etalk’s deck\u003c/a\u003e (while here you can find the \u003ca href=\"https://ela.st/bpfcov-slides-source\"\u003eslides in PDF and markdown format\u003c/a\u003e if you prefer).\u003c/p\u003e\n\u003cp\u003eWhile at \u003ca href=\"https://ela.st/bpfcov\"\u003eelastic/bpfcov\u003c/a\u003e you can take a look at the project. Don't forget to star it, if you don’t mind! :)\u003c/p\u003e"}],"_metadata":{"uid":"cs09a387fea2c6337d"}}}],"publish_date":"2022-02-03T14:30:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Code coverage for eBPF programs","seo_description_l10n":"","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9e37344acd64cf5a","ACL":{},"created_at":"2023-11-06T20:38:34.272Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ebpf","label_l10n":"eBPF","tags":[],"title":"eBPF","updated_at":"2023-11-06T20:38:34.272Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.250Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt2c53b53a84e578dd","ACL":{},"content_type":"image/png","created_at":"2021-05-05T15:04:29.365Z","created_by":"blt3e52848e0cb3c394","file_size":"161741","filename":"blog-security-detection-720x420.png","tags":[],"title":"blog-security-detection-720x420.png","updated_at":"2021-05-05T15:04:29.365Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-13T22:00:14.862Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2c53b53a84e578dd/6092b3fd5907c910150fa6ac/blog-security-detection-720x420.png"},"title":"Code coverage for eBPF programs","title_l10n":"Code coverage for eBPF programs","updated_at":"2025-03-28T17:15:45.345Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/code-coverage-for-ebpf-programs","publish_details":{"time":"2025-03-28T17:15:50.900Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt567e68c6fa19b449","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":" ","author":["blt8280a0fbfa4a6db2"],"category":[],"created_at":"2022-02-09T21:59:00.839Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse2e2fc8d207f3cd7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eMost developers believe that building reliable software involves writing good code, implementing enough testing, and using as many proven architecture patterns as possible. The assumption is that building things this way equals creating a flawless system. Sadly, in the software world, this is not true. Software reliability is not the same as software correctness. You may write good code, implement enough testing, and use as many proven architecture patterns as possible to end up with software deemed correct. But, the code may still blow up straight on the customer's face.\u003c/p\u003e\n\u003cp\u003eBuilding software reliability is something else, entirely. It requires developers to look at the code, not from the perspective of what it is supposed to do but what the code is effectively doing, with little room for guessing. Distributed tracing is a technique you can use to accomplish this, and we will dive into the details for this post.\u003c/p\u003e"}],"_metadata":{"uid":"cs30d6b6fefc4af4e0"}}},{"title_text":{"title_text":[{"title_l10n":"Looking for the code's perfect lap","_metadata":{"uid":"cs4f5f46647e11e507"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOne of the best things about the \u003ca href=\"https://sre.google/\"\u003eSRE\u003c/a\u003e culture is that developers become more conscious about the responsibility that lies in their hands. Instead of just writing code and building images that somebody else would use to build and deploy the system, they are responsible for overseeing the code move from pipeline to production. They need to ensure that the system is running as expected, which often means being on-call waiting for customers to complain about something. But they shouldn't need to wait until customers complain to take any action.\u003c/p\u003e\n\u003cp\u003eFord v Ferrari is an American sports drama film from 2019 directed by James Mangold that tells the history of how Ford managed to defeat Ferrari at the \u003ca href=\"https://en.wikipedia.org/wiki/1966_24_Hours_of_Le_Mans\"\u003e1966 24 Hours of Le Mans\u003c/a\u003e race in France. The plot follows a determined team of American and British engineers and designers, led by automotive designer Carroll Shelby and his British driver, Ken Miles. Although the movie is not only about him, Ken Miles was undoubtedly a vital element for the film. His character was inspired by the real \u003ca href=\"https://en.wikipedia.org/wiki/Ken_Miles\"\u003eKen Miles\u003c/a\u003e, a British race car driver, and mechanic who became famous for his exploits within motorsports. Ken Miles’ unconventional take on mechanical engineering for racing helped him win some of the biggest races in the world.\u003c/p\u003e\n\u003cp\u003eThere is a scene in the movie where Ken is talking with his son Peter Miles, where he’s trying to explain to the boy what it takes to win a race.\u003c/p\u003e\n\u003cp\u003e\"If you're going to push a piece of machinery to the limit and expect it to hold together, you have to have some sense of where that limit is. Look out there. Out there is the perfect lap. No mistakes. Every gear change, every corner. Perfect.\"\u003c/p\u003e\n\u003cp\u003eThe same applies to software engineering. It is somewhat impossible to get code running as expected if you have never tried the code in the right conditions that will determine if it may fail or not. After all, there's a difference between knowing the path and walking the path. When your code is executed in a staged environment, such as a unit testing platform, you assert if the code will satisfy the happy path scenarios that you hard-coded. Ultimately, this is going to assert the code's correctness. Another consideration is running the code in an environment that will reflect the many possible outcomes your code may have, such as a production environment. In that scenario, you are dealing with uncertainty.\u003c/p\u003e\n\u003cp\u003eFortunately, you can transform this uncertainty into predictability with distributed tracing. By using an instrument-first approach, which is building instrumentation as you write the code for your software, you can have your code expressing its execution in a way that you can truly assess whether or not it produces the correct output. You can verify scenarios like \"will the code behave the same if it runs not in one, but several Kubernetes pods?.\" You can think about this as a complex unit test case that could answer this question, but you didn't have to write it.\u003c/p\u003e\n\u003cp\u003eWhen your code is written along with instrumentation, you can start answering questions that may not have been asked during the system's design and implementation phases and ditch the embarrassment of not understanding your own code's behavior. You can use the production environment to debug your systems without the fear of breaking anything. Your code will be genuinely observable. But instrumenting the code alone doesn't do the magic. You also have to push your code to the limit.\u003c/p\u003e\n\u003cp\u003ePushing the code to its limits is about pursuing the unknown unknowns, instead of just known unknowns. Every release you build, every function refactored, every new dependency added, you ought to check how the code behaves along with other components, see when it breaks, and identify all the unforeseen conditions. Ultimately, your job is to look for the perfect lap.\u003c/p\u003e"}],"_metadata":{"uid":"cs3f043d21d7c40654"}}},{"image":{"image":{"uid":"blt1a4a05466a3a0d82","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:47:49.285Z","updated_at":"2022-02-09T21:47:49.285Z","content_type":"image/png","file_size":"163857","filename":"building-software-reliability-latency-distribution.png","title":"building-software-reliability-latency-distribution.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.396Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1a4a05466a3a0d82/62043685f38b14611e039fa9/building-software-reliability-latency-distribution.png"},"_metadata":{"uid":"cse3104c9f08264946"},"caption_l10n":"Figure 1: Timeline of a transaction instrumented using distributed tracing.","alt_text_l10n":"Figure 1: Timeline of a transaction instrumented using distributed tracing.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs719c4afd398f72a1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFigure 1 shows an example of a code instrumented using distributed tracing. The purpose of the instrumentation is to enable rich details of what the code did when executed and provide users with a way to investigate how long it took each part of the code. The beauty of this approach is that now, you no longer have to settle with hypotheses of which path your code may have taken. You now have a picture of the execution of your code.\u003c/p\u003e\n\u003cp\u003eIf code instrumentation is so great, why do developers avoid it as much as they can? You may ask. Presumably, code instrumentation is terrible for performance, and leaving the code with the instrumentation written in it will slow things down. It is essential to know a few things. First off, code instrumentation has evolved a lot in terms of performance overhead. The perception of being something slow came from technologies from the past. Furthermore, it can be disabled at any time via configuration.\u003c/p\u003e\u003cbr\u003eTherefore, developers no longer have to fear the performance impact of code instrumentation and perhaps the potential refactoring they would have to implement to remove the instrumentation from the code to fix the problem. You can leave the code untouched and disable the instrumentation as needed. Hopefully, knowing this trick may encourage developers to adopt an instrument-first approach during development. In fact, leaving the instrumentation on your code provides extra superpowers!\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eCode Instrumentation allows you to compare different releases from your system and the changes that may have affected performance, availability, and correctness. Since distributed tracing allows you to have a picture of the execution of your code, you can now compare the picture of each release and quickly see if, for example, the last committed code pushed on a Friday night broke anything.\u003c/p\u003e\n\u003cp\u003eTo illustrate this, let's say that after the last release, you started to have customers complaining about the performance of a transaction that usually takes less than a second to complete. You can use your observability backend to inspect the transactions done before the last release and check its execution, as shown in Figure 2.\u003c/p\u003e"}],"_metadata":{"uid":"cse87ea25fb097da27"}}},{"image":{"image":{"uid":"bltdbb4ebd3682adc18","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:48:37.782Z","updated_at":"2022-02-09T21:48:37.782Z","content_type":"image/png","file_size":"209543","filename":"building-software-reliability-timeline-backend-golang-java-frontend-react-143ms.png","title":"building-software-reliability-timeline-backend-golang-java-frontend-react-143ms.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.404Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdbb4ebd3682adc18/620436b58b1f312528798ae1/building-software-reliability-timeline-backend-golang-java-frontend-react-143ms.png"},"_metadata":{"uid":"cs158c906cadc80f48"},"caption_l10n":"Figure 2: Investigating the performance of a business transaction in a previous release.","alt_text_l10n":"Figure 2: Investigating the performance of a business transaction in a previous release.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1720db9889ccf3f5"},"header_style":"H2","paragraph_l10n":"Then, you can fast forward in time to inspect the transactions executed after the last release and compare the differences. As you can see in Figure 3, the last release introduced a new step called \u003cstrong\u003eadditionalMarkUp\u003c/strong\u003e in the transaction, which increased its overall execution time significantly to more than five seconds.\u003cbr\u003e"}],"_metadata":{"uid":"cs04803f1341c11e96"}}},{"image":{"image":{"uid":"blt34769be877225911","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:49:11.444Z","updated_at":"2022-02-09T21:49:11.444Z","content_type":"image/png","file_size":"214441","filename":"building-software-reliability-timeline-backend-golang-java-frontend-react-5164ms.png","title":"building-software-reliability-timeline-backend-golang-java-frontend-react-5164ms.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.424Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt34769be877225911/620436d7d6534f0c05718cb8/building-software-reliability-timeline-backend-golang-java-frontend-react-5164ms.png"},"_metadata":{"uid":"csefff31c44c65e573"},"caption_l10n":"Figure 3: Investigating the performance of a business transaction in the last release.","alt_text_l10n":"Figure 3: Investigating the performance of a business transaction in the last release.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf0103586773b3826"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis troubleshooting style is perfectly possible as long as the observability backend provides longer retention for the ingested traces, as you need to compare current data with past data. For example, with \u003ca href=\"/observability\"\u003eElastic Observability\u003c/a\u003e, you have the concept of \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/searchable-snapshots.html\"\u003eSearchable snapshots\u003c/a\u003e, where you can configure its persistence layer to handle more data density for historical data, using cheaper storage such as \u003ca href=\"https://aws.amazon.com/s3/\"\u003eAmazon S3\u003c/a\u003e, \u003ca href=\"https://azure.microsoft.com/en-us/services/storage/blobs/\"\u003eAzure Blob Storage\u003c/a\u003e, and \u003ca href=\"https://cloud.google.com/storage\"\u003eGoogle Cloud Storage\u003c/a\u003e. You can store more data without skyrocketing your storage costs.\u003c/p\u003e"}],"_metadata":{"uid":"csc3115a70f8981c5f"}}},{"image":{"image":{"uid":"blt73025d0628c93ae5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:50:07.100Z","updated_at":"2022-02-09T21:50:07.100Z","content_type":"image/gif","file_size":"33545093","filename":"building-software-reliability-hot-warm-cold.gif","title":"building-software-reliability-hot-warm-cold.gif","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.432Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt73025d0628c93ae5/6204370fc7047b4ac12ee87f/building-software-reliability-hot-warm-cold.gif"},"_metadata":{"uid":"csf16768882e57bae6"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9f87244be08e2c0a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBut observability is not just about debugging your code. The real value from observability comes when you use it to figure out where exactly in the system to look for code that needs debugging. You can achieve this superpower by adopting an instrument-first approach, where your code can become genuinely observable. What does it take to embrace the instrument-first approach? Well, you can start by learning how instrumentation works for the programming language used to build your services. Then, you can apply code instrumentation to the parts of code that are relevant to your customers.\u003c/p\u003e\n\u003cp\u003eSuppose you are designing an e-commerce system that allows customers to browse for products, put those products into a shopping cart, provide a way to pay for them, and, once paid, handle product shipment. This flow is what is relevant to your customers. In this case, this whole customer flow — also known as a business transaction — should be explicitly observable via distributed tracing.\u003c/p\u003e\n\u003cp\u003eRemember, though, distributed tracing is not a goal achieved overnight. The most successful observability implementations result from several iterations, where each step instruments another aspect of the code for the sake of tracing. In the first release of your software, you may not have noticed that a particular dependency is essential to the success of a given business transaction. You can ensure that the dependency is included in the next release, given its importance.\u003c/p\u003e\n\u003cp\u003eKnowing that you have an iterative process is important to remove the burden from your shoulders about expecting a perfect, distributed tracing implementation in your first attempt. It is OK to be incomplete. Distributed tracing is not a single-shot type of implementation. It is an ongoing, always incomplete, constant code refinement that developers must consider. If your code is still under development and changing, the same goes for your distributed tracing implementation. Remember, your code's perfect lap is out there. No mistakes. Every new release you build, every function refactored, every new dependency added. Perfect.\u003c/p\u003e"}],"_metadata":{"uid":"csce9a160c5d449ec6"}}},{"title_text":{"title_text":[{"title_l10n":"Four golden signals, one perspective","_metadata":{"uid":"csb794a04c5db0eb44"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\"You can't manage what you don't measure.\" This iconic statement is one of the most famous quotes found in books about business management. It’s also become well-known among folks responsible for maintaining systems online, such as SREs.\u003c/p\u003e\n\u003cp\u003eAs an SRE, you can't say that you manage a system if you don’t have a single clue about its current state. The best way to assess the system's current state is to continuously probe for data and build up metrics around it. Metrics can be used to evaluate how the system is going, which way it may be trending, and build knowledge about the system's behavior given past incidents. For example, you can investigate a past incident where your system was unavailable for thirty minutes and create a causation analysis that demonstrates that when it happened, the database's CPU spiked during the same time interval.\u003c/p\u003e\n\u003cp\u003eThis is known as monitoring, a practice that has been around for quite some time now. But the technologies used to implement it have matured significantly in the last few years, especially in the areas of time-series analysis and storage. Without monitoring, managing your system will be like driving a car with your eyes blindfolded — it will be only a matter of time before an accident happens. With monitoring correctly in place, the monitored system can be protected by having a human alerted when one of the metrics is problematic.\u003c/p\u003e\n\u003cp\u003eSuccessful monitoring is in the end, a matter of which metrics you decide to collect. Luckily, there’s no need to guess about which metrics to collect. Some lessons learned in SRE can provide you with a relatively great start.\u003c/p\u003e\n\u003cp\u003eOne key learning is regarding the \u003ca href=\"https://sre.google/sre-book/monitoring-distributed-systems/\"\u003efour golden signals\u003c/a\u003e. They represent the aspects of a system that really matter the most. Focusing on the aspects that matter the most is important as metric collection doesn't come for free. Collecting metrics always incur a slight overhead, whether in the source system where you pulled those metrics or storing the metrics. But, you have to start somewhere, and the four golden signals are a great starting point.\u003c/p\u003e\n\n\u003cul\u003e\n\t\u003cli\u003e\u003cstrong\u003eLatency\u003c/strong\u003e: The time it takes to service a request, which includes the monitoring of all successful or errored requests. Latency must be measured from individual services, collection of services, and end-to-end business transactions.\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eTraffic\u003c/strong\u003e: How much demand is being placed on your system, measured in a high-level system-specific metric. For example, this metric may be the number of transactions per second for a key-value storage system.\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eErrors\u003c/strong\u003e: The rate at which your services are failing. They can be explicit like the number of HTTP 500s, implicit, like the number of HTTP 200s with errors, or derived by policies like whatever requests don't complete in one second is considered an error.\u003c/li\u003e\n\t\u003cli\u003e\u003cstrong\u003eSaturation\u003c/strong\u003e: How \"full\" your service is. This can be measured in various ways, such as how much more load the system can handle and given a set of constrained resources — when approximately it will stop serving requests.\u003c/li\u003e\u003c/ul\u003e\n\t\u003cp\u003eBy focusing on the four golden signals, you can better assess the system's current state and what to do next. It’s an excellent first step to achieving software reliability. But it is not the only step. Previously, we discussed the concept of a business transaction. This is what customers see as most relevant. More important than monitoring the four golden signals from the system's perspective is monitoring the four golden signals from your customer's perspective.\u003c/p\u003e\n\u003cp\u003eAfter all, \"nines don't matter if users aren't happy.\" This quote was coined by \u003ca href=\"https://twitter.com/mipsytipsy\"\u003eCharity Majors\u003c/a\u003e, where she explains that you may have a highly available system with five-nines of availability, and customers could still not finish their transactions. Here’s where distributed tracing can truly bring value to your journey in building reliability for your software. Yes, keep an eye on the four golden signals, but let distributed tracing glue them together and help you understand the customer's business transactions. Don't just monitor the latency of your microservices. Instead, observe how their latencies affect a given business transaction.\u003c/p\u003e\n\u003cp\u003eYou can accomplish this by instrumenting your code with distributed tracing, which will act as a catalyst in unifying collected metrics with executed code. Figure 4 is a great example of this. Given a business transaction, you can see how the four golden signals can be visualized in the context of that transaction. This visualization is provided automatically. All you need to do is instrument the code and ingest the produced traces to the same backend where metrics are being stored; in this example, we have \u003ca href=\"/observability\"\u003eElastic Observability\u003c/a\u003e, which can automatically correlate the traces and the metrics.\u003c/p\u003e"}],"_metadata":{"uid":"cs2936ccb881f41c94"}}},{"image":{"image":{"uid":"bltce92a8563c028b19","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:52:42.094Z","updated_at":"2022-02-09T21:52:42.094Z","content_type":"image/png","file_size":"490055","filename":"building-software-reliability-opbeans-java-transactions.png","title":"building-software-reliability-opbeans-java-transactions.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.440Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltce92a8563c028b19/620437aa433b4e498f669925/building-software-reliability-opbeans-java-transactions.png"},"_metadata":{"uid":"cs5bd0bd46b0f0cc24"},"caption_l10n":"Figure 4: Visualizing the four golden signals from the perspective of a transaction.","alt_text_l10n":"Figure 4: Visualizing the four golden signals from the perspective of a transaction.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs747b9a013608f4a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen you focus on your customer's perspectives, you will rarely be caught by surprise if your systems start to fail for whatever reason. Thanks to distributed tracing, you can act upon what’s causing the issue, which it will efficiently point out. Then you can work towards building a fix as soon as possible. Without the customer perspective, you will be stuck forever in that war room trying to convince people that everything is okay because a given metric shows up as green — but everybody else will argue that nothing is working and you should do something about it.\u003c/p\u003e\n\u003cp\u003eLet’s call this the four golden signals, one perspective. This one perspective is the business transaction that your customers will be interacting with. It is the only perspective that really matters. The four golden signals must be derived from that perspective so that discussing them should always be in the context of a given business transaction.\u003c/p\u003e"}],"_metadata":{"uid":"cs416e1ea26b3e5242"}}},{"image":{"image":{"uid":"bltcf5513888f91cb28","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:53:14.466Z","updated_at":"2022-02-09T21:53:14.466Z","content_type":"image/png","file_size":"37066","filename":"building-software-reliability-business-transaction-latency-traffic-errors-saturation.png","title":"building-software-reliability-business-transaction-latency-traffic-errors-saturation.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.447Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcf5513888f91cb28/620437ca214fe9266428ccc0/building-software-reliability-business-transaction-latency-traffic-errors-saturation.png"},"_metadata":{"uid":"csea3bb4d586bba6c2"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs325a254ff4fcf59a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis model resembles the \u003ca href=\"https://www.cs.ubc.ca/~gregor/teaching/papers/4+1view-architecture.pdf\"\u003e\"4+1\" architecture view model\u003c/a\u003e from \u003ca href=\"https://twitter.com/pbpk\"\u003ePhilippe Kruchten\u003c/a\u003e. The idea is that the other aspects of the system are considered from the perspective of the system's user and the use cases around it. It is a proven way to ensure that all stakeholders are on the same page and energy will be focused on what matters.\u003c/p\u003e"}],"_metadata":{"uid":"cs3455012148817b8c"}}},{"title_text":{"title_text":[{"title_l10n":"We're not in Kansas anymore","_metadata":{"uid":"cs6bf51a937be89845"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe way developers build systems has changed significantly over the years. It is possible to observe this by looking at the evolution of distributed tracing. Its origins go back to 2002 with a prototype called Pinpoint developed by researchers from the University of California, Berkeley, and Stanford. Its goal was to identify the root causes of problems in internet services created using J2EE. All traces were based on single-machine requests and the context was stored in thread-local variables within the JVM.\u003c/p\u003e\n\u003cp\u003eAfter this step forward in J2EE, researchers at Microsoft Research Cambridge developed Magpie in 2004, a project focused on recording detailed end-to-end traces and annotating those traces with fine-grained information, focused on .NET-based systems. A bit more ambitious than Pinpoint, Magpie wanted to provide tracing for heterogeneous environments; however, they ended up relying on Microsoft's specific components, such as the Windows XP's event tracing for Windows, making it hard to use other platforms.\u003c/p\u003e\n\u003cp\u003eAs you can see, they both solved the problem of handling traces using inferences available on individual technology stacks. A reasonable expectation, given that at the time, most systems were created using a single technology stack and executed in a few, known by name, servers. In 2007, the University of California developed another project called X-Trace. Its purpose was to implement request tracing between distributed systems running on different computers. To accomplish this goal, the X-Trace project proposed a standardized way of propagating the trace context, so the distributed trace could be constructed with a more deterministic approach and be less dependent on specific technology stacks.\u003c/p\u003e\n\u003cp\u003eIn 2010, Google developed an internal system called Dapper, which was heavily inspired by Pinpoint, Magpie, and X-Trace, but focused on solving some operational problems found while using these projects at scale in production systems: the need for trace sampling, trade-offs surrounding runtime overheads, data security, and how to make traces accessible to users. At this point in time, we can agree that the world had already embraced the idea that distributed applications were a new reality.\u003c/p\u003e\n\u003cp\u003eFrom 2002 to 2010, there was an apparent revolution in how systems were built and how the world started to shift from monolith applications to distributed systems that communicate via APIs. All the work done in the distributed tracing space was ultimately, a reaction to the needs of developers. Business transactions were executed by code written in different programming languages, running on different machines, running with different runtimes, and sharing data over remote procedure calls. However, it may be worth detailing another change in the last decade. Since 2010, there has been another shift in how systems are built. We are currently in an era of highly distributed and deep systems.\u003c/p\u003e\n\u003cp\u003eYes, systems still communicate via APIs and share data over remote procedure calls. But JSON and XML are no longer the most popular data formats used, with binary technologies like Avro, Protobuf, and Parquet getting mainstream. Streaming systems such as Apache Kafka, Pulsar, and Flink are no longer only themes of specialized tech conferences for developers. Data flows implemented using Hadoop, Spark, and TensorFlow are the new mandate for complex artificial intelligence use cases. Bare metal hosts were replaced by VMs, which gave place to containers, and functions are getting popular as a unit of code deployment. As Dorothy commented in The Wizard of Oz, we're not in Kansas anymore.\u003c/p\u003e\n\u003cp\u003eFor instance, \u003ca href=\"https://en.wikipedia.org/wiki/Online_transaction_processing\"\u003eOLTP\u003c/a\u003e and \u003ca href=\"https://en.wikipedia.org/wiki/Online_analytical_processing\"\u003eOLAP\u003c/a\u003e systems were always different things in the past. Traditionally, developers would only implement data pipelines to offload transactional databases and run analytics workloads using specialized data warehouses. Data engineering has evolved from a niche data analytics skillset to a standard developers' expertise. Modern systems often rely on data pipelines for their backend and frontend layers. When they are executed, most business transactions leverage data served by these data pipelines. Therefore, data pipelines are now part of the standard business transaction, even though they are not directly part of the critical transaction path.\u003c/p\u003e\n\u003cp\u003eHow can we debug systems using this design? How can developers understand a business transaction if the flow is broken down into different contexts? These are questions developers ask themselves, and it is hard to build software reliability without answers. Distributed tracing still helps with this — but there is now a shared responsibility between developers and what distributed tracing can deliver.\u003c/p\u003e\n\u003cp\u003eFor starters, context propagation sometimes may not happen automatically. Developers may have to roll up their sleeves and write code to make this happen. For example, think about a flow where a transaction starts in one microservice written in \u003ca href=\"https://openjdk.java.net/\"\u003eJava\u003c/a\u003e that reads data from \u003ca href=\"https://redis.io/\"\u003eRedis\u003c/a\u003e and then publishes a message to \u003ca href=\"https://pulsar.apache.org/\"\u003eApache Pulsar\u003c/a\u003e. From the Java microservice perspective, the transaction has finished. But from the business transaction perspective, it is still pending. Other microservice written in \u003ca href=\"https://go.dev/\"\u003eGo\u003c/a\u003e will give continuity by reading the message off Pulsar and resuming the processing. The challenge is that the business transaction flow is broken down into different processes executed asynchronously.\u003c/p\u003e"}],"_metadata":{"uid":"csd6824570b7994a7c"}}},{"image":{"image":{"uid":"blt8f474579529a2906","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:54:26.414Z","updated_at":"2022-02-09T21:54:26.414Z","content_type":"image/png","file_size":"72573","filename":"building-software-reliability-spring-redis-pulsar.png","title":"building-software-reliability-spring-redis-pulsar.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.457Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8f474579529a2906/62043812d96fa00bff5ef79e/building-software-reliability-spring-redis-pulsar.png"},"_metadata":{"uid":"cs02000f3dcaa221d5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs357b98af417d1a79"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eModern observability technologies such as OpenTelemetry provide the tools, APIs, and SDKs for developers to handle scenarios like this. It is a solved problem. Yet, it requires developers to explicitly use them in their code, which is sometimes unpleasant. The unpleasantry comes from developers having to write extra code to solve a problem they didn't know they would have until they needed distributed tracing. The session \u003ca href=\"https://www.youtube.com/watch?v=XpEQTqaawyk\"\u003eBuilding Observable Streaming Systems with OpenTelemetry\u003c/a\u003e, which was presented on \u003ca href=\"https://2021.berlinbuzzwords.de/\"\u003eBerlin Buzzwords in 2021\u003c/a\u003e, shows an example of this scenario and how to implement context propagation manually.\u003c/p\u003e"}],"_metadata":{"uid":"cs47877cdf7ded7b03"}}},{"image":{"image":{"uid":"blt3cca754dbd2e18bd","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:54:57.836Z","updated_at":"2022-02-09T21:54:57.836Z","content_type":"image/png","file_size":"114160","filename":"building-software-reliability-trace-sample.png","title":"building-software-reliability-trace-sample.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.466Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3cca754dbd2e18bd/620438311e536a4ac08df6fc/building-software-reliability-trace-sample.png"},"_metadata":{"uid":"csf40fecd56106ac6c"},"caption_l10n":"Figure 5: Example of transaction whose context was propagated manually.","alt_text_l10n":"Figure 5: Example of transaction whose context was propagated manually.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs82a894bf08058424"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFurthermore, you may also have to understand how specific technology stacks will create their own traces. This is important because developers are increasingly using technology stacks to build up the layers of their systems. Service meshes are a good example. If you deploy a service mesh such as \u003ca href=\"https://istio.io/\"\u003eIstio\u003c/a\u003e with your system, this means that the service mesh will manage all the interprocess communication; therefore, you need to make sure that interactions will emit a trace so you can have visibility across the transactions. The same goes for Kubernetes. If your system connects to a database running in Kubernetes, you need to ensure that this interaction will also emit a relevant trace. So you need to configure your Kubernetes cluster accordingly.\u003c/p\u003e\n\u003cp\u003eTo build this level of tracing, you will need to understand in further detail how each technology stack provides you with extension points. Sometimes it is as easy as configuring their support for a particular distributed tracing technology. Sometimes, you may need to leverage the built-in plugin architecture and write an extension. For example, \u003ca href=\"https://plugins.jenkins.io/opentelemetry/\"\u003ethis Jenkins plugin\u003c/a\u003e allows developers to monitor your pipelines using OpenTelemetry. This project was created at Elastic by \u003ca href=\"https://twitter.com/cyrilleleclerc\"\u003eCyrille Le Clerc\u003c/a\u003e and eventually donated to the Jenkins project. Finally, sometimes you may need to build a custom version of the technology stack with distributed tracing included.\u003c/p\u003e\n\u003cp\u003eEventually, you may also need to get involved with some open source projects to get the tracing your system requires. Many projects provide a way for the community to discuss and decide the future of specific implementations. For example, the Apache Kafka project is adding support for client metrics and observability, as you can see in the \u003ca href=\"https://cwiki.apache.org/confluence/display/KAFKA/KIP-714%3A+Client+metrics+and+observability\"\u003eKIP-714\u003c/a\u003e. Ultimately, it is up to you to get involved with these projects and help shape the future of the implementation.\u003c/p\u003e"}],"_metadata":{"uid":"cs45ef59fc4ccc2ec7"}}},{"title_text":{"title_text":[{"title_l10n":"Simplifying your observability journey","_metadata":{"uid":"cse69cd2eb37ff71fc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFrom a practical standpoint, adopting observability is very challenging. The reality is that most developers still feel a bit lost about the concrete steps to adopt observability. The confusion is understandable, though. Different technologies over the years, multiple approaches, proprietary products versus open-source implementations, and the twisted ideas about what observability means from vendors. For example, if you ask a vendor whose main product is focused on time-series analysis, they will say that observability is only about metrics. Another vendor whose main product is focused on collecting and storing logs will say that observability is only about logs. The same goes for vendors focused on distributed tracing. To them, it is only about traces.\u003c/p\u003e\n\u003cp\u003eThe reality is that observability is way more than these different types of data, also known as signal types. Individually, they have their advantages and solve specific problems. A better way to look at observability is by unifying all the signal types into one cohesive context, which unlocks the ability of an organization to answer questions about its systems and services with confidence. The so-called three pillars of observability are nothing but a fallacy. Think about pipes and not pillars. If a new signal type rises in the future, make sure to collect it and combine it with the other signal types to build datasets that will answer the questions that matter — unknown unknowns.\u003c/p\u003e"}],"_metadata":{"uid":"cs397860797c9721b5"}}},{"image":{"image":{"uid":"blt973b940c9505789d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:55:49.278Z","updated_at":"2022-02-09T21:55:49.278Z","content_type":"image/png","file_size":"54590","filename":"building-software-reliability-traces-metrics-logs.png","title":"building-software-reliability-traces-metrics-logs.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.485Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt973b940c9505789d/62043865b7731b0ad7717f94/building-software-reliability-traces-metrics-logs.png"},"_metadata":{"uid":"csd63d37e592aaba4d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs047f7a9245cd49cf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBut how to build datasets from different signal types? Pragmatically speaking, this means that signal types must be collected in a standardized way, stored using specific schemas, and live in a kind of data store that allows them to be linked to each other. This isn't easy to solve, as each signal type has its peculiarities.\u003c/p\u003e\n\u003cp\u003eMetrics are time-series data that must be quickly aggregatable. Ingesting metrics at scale often leads to a problem in computing called high cardinality. The logs don't have a predefined schema by themselves. Looking for data in logs requires a data store with a flexible schema, less dependent on just queries, and more about doing searches. Traces are something else entirely; they are multidimensional data with many relationships. End-to-end traces are \u003ca href=\"https://en.wikipedia.org/wiki/Graph_(abstract_data_type)\"\u003egraphs\u003c/a\u003e and not just \u003ca href=\"https://en.wikipedia.org/wiki/Tree_(data_structure)\"\u003etrees\u003c/a\u003e, as a child span can have multiple parents, as well as forks. Finally, you need to be able to build visualizations on top of all these signal types so users can play with the data.\u003c/p\u003e\n\u003cp\u003eWhen you get caught up with the semantics of solving these data problems, you quickly lose interest in adopting observability. To be fair, as any person would. But you don't need to worry about these data concerns to adopt observability. Leave this responsibility to the vendors. For example, \u003ca href=\"/observability\"\u003eElastic Observability\u003c/a\u003e uses \u003ca href=\"/elasticsearch/\"\u003eElasticsearch\u003c/a\u003e and \u003ca href=\"/kibana/\"\u003eKibana\u003c/a\u003e to handle these data problems. It is a great platform to handle signal types like metrics, logs, traces, and many others. Whereas other vendors wrote their data stores and visualization engines from scratch. This shouldn't matter to you from the observability adoption standpoint.\u003c/p\u003e\n\u003cp\u003eBut data collection and ingestion are still your responsibility. It is a less complex problem, but it is still a challenge. Most of the issues related to the collection and ingestion of signal types are the proliferation of different technologies. It is not uncommon to see observability data collected requiring different agents to be installed. Specific agents for metrics, others for logs, and traces make maintaining systems and keeping them up and running more challenging. Along with these many agents, data buffering and transformation technologies are commonly needed before sending the signal types to the observability backends. Technologies such as \u003ca href=\"https://kafka.apache.org/\"\u003eApache Kafka\u003c/a\u003e, \u003ca href=\"/logstash/\"\u003eLogstash\u003c/a\u003e, and \u003ca href=\"https://www.fluentd.org/\"\u003eFluentD\u003c/a\u003e are recurring characters for such use cases.\u003c/p\u003e\n\u003cp\u003eHow does all of this complexity affect software reliability? The more tools you have to maintain every time you release a new system version, the slower and fragile your software delivery will become. It is not uncommon for developers to complain about the number of moving parts that need to be updated before a simple change occurs. For this reason, adopting observability heavily depends on how simple the implementation is. Whether you focus only on distributed tracing or adopting the other signal types to develop a more comprehensive solution, simplifying your observability journey is key.\u003c/p\u003e\n\u003cp\u003eStart by deciding which distributed tracing instrumentation technology you will adopt. There are many options, but each one has its advantages and disadvantages. While it is tricky to suggest one that can act as a bulletproof option, you can assume that adopting open standards should be the way to go. \u003ca href=\"https://opentelemetry.io/\"\u003eOpenTelemetry\u003c/a\u003e, which is a project created from the merger of \u003ca href=\"https://opentracing.io/\"\u003eOpenTracing\u003c/a\u003e and \u003ca href=\"https://opencensus.io/\"\u003eOpenCensus\u003c/a\u003e, is currently the best open standard to use for distributed tracing and many other observability needs, given its widespread acceptance and active community. It is also a \u003ca href=\"https://www.cncf.io/blog/2021/08/26/opentelemetry-becomes-a-cncf-incubating-project/\"\u003eCNCF incubating project\u003c/a\u003e. It supports different programming languages and ensures that the instrumentation code you write won't be wasted when you change your observability backend.\u003c/p\u003e\n\u003cp\u003eOpenTelemetry also provides a standard format for signal types along with specifications. As long as you use a compatible observability backend, you don't have to worry about data plumbing to store the signal types. Here's an example of code written in Go that leverages the OpenTelemetry APIs to produce traces.\u003c/p\u003e"}],"_metadata":{"uid":"cs408e5b2c46983026"}}},{"code":{"code":"func hello(writer http.ResponseWriter, request *http.Request) {\n \n ctx := request.Context()\n \n ctx, buildResp := tracer.Start(ctx, \"buildResponse\")\n response := buildResponse(writer)\n buildResp.End()\n \n // Create a custom span\n _, mySpan := tracer.Start(ctx, \"mySpan\")\n if response.isValid() {\n log.Print(\"The response is valid\")\n }\n mySpan.End()\n \n}","_metadata":{"uid":"cs24689a957737994f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csea74b1bccd37e52e"},"header_style":"H2","paragraph_l10n":"\u003cfigcaption\u003e\u003cp class=\"paragraph-medium paragraph-caption\"\u003e\u003cstrong\u003eListing 1\u003c/strong\u003e: Using the OpenTelemetry API for Go to produce traces.\u003c/p\u003e\u003c/figcaption\u003e"}],"_metadata":{"uid":"csc464c0ccfcf0db7c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse1868b5ec159fe42"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this example, the function hello() belongs to a microservice written in Go that exposes an API invoked via HTTP. When this API is invoked, the microservice will execute the hello() function responsible for producing the relevant traces, as shown in Figure 6.\u003c/p\u003e"}],"_metadata":{"uid":"csbc61c1321b122e30"}}},{"image":{"image":{"uid":"blt0219a5867a9718d4","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-02-09T21:57:37.187Z","updated_at":"2022-02-09T21:57:37.187Z","content_type":"image/png","file_size":"125568","filename":"building-software-reliability-trace-sample-latency-distribution.png","title":"building-software-reliability-trace-sample-latency-distribution.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.494Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0219a5867a9718d4/620438d1d6534f0c05718cc4/building-software-reliability-trace-sample-latency-distribution.png"},"_metadata":{"uid":"cseadb4901b85506b0"},"caption_l10n":"Figure 6: Visualizing the traces produced by the microservice in Go.","alt_text_l10n":"Figure 6: Visualizing the traces produced by the microservice in Go.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6b3cfb611ce9c203"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe complete source code of this example can be found on \u003ca href=\"https://github.com/riferrei/otel-with-golang\"\u003ethis GitHub repository\u003c/a\u003e. Keep in mind though, that the APIs and SDKs for each programming language will vary. The specification may be the same but each programming language has its own peculiarities. Visit the \u003ca href=\"https://opentelemetry.io/docs/instrumentation/\"\u003einstrumentation page\u003c/a\u003e on the OpenTelemetry website to find more information about the programming language of your choice.\u003c/p\u003e\n\u003cp\u003eAs for metrics, logs, and other signal types, the OpenTelemetry project is still in its early days. It will take a while until the community can leverage something production-ready. Meanwhile, you may need to use the tools offered by some vendors. For example, \u003ca href=\"/observability\"\u003eElastic Observability\u003c/a\u003e has the \u003ca href=\"https://www.elastic.co/guide/en/fleet/current/fleet-overview.html\"\u003eElastic Agent\u003c/a\u003e, a single, unified agent that you deploy to hosts or containers to collect data. The Elastic Agent considerably simplifies the effort necessary to collect signal types from different sources. The Elastic Agent also can be managed from a central location. This reduces the administrative overhead required to maintain your systems.\u003c/p\u003e\n\u003cp\u003eFinally, the usage of cloud-managed services can considerably reduce the operational overhead required for an observability backend. Whenever possible, offloading the burden of keeping the lights on for your observability backend may be beneficial in the long run and sometimes even cheaper. After all, saving money is not just about reducing infrastructure costs. It is also about letting your developers — arguably your most expensive assets — focus on business-critical tasks. At the same time, the operation of the observability backend is done by companies that only do that. \u003ca href=\"/cloud/\"\u003eElastic Cloud\u003c/a\u003e is an excellent example.\u003c/p\u003e\n\u003cp\u003eWith Elastic Cloud, you can benefit from having the engineers from Elastic take care of the cloud-manage service operation. At the same time, you can use Elastic Observability as a service, with the ability to deploy it in multiple cloud providers such as \u003ca href=\"https://aws.amazon.com/\"\u003eAWS\u003c/a\u003e, \u003ca href=\"https://azure.microsoft.com/en-us/\"\u003eAzure\u003c/a\u003e, and \u003ca href=\"https://cloud.google.com/\"\u003eGoogle Cloud\u003c/a\u003e. Starting with Elastic Observability is as easy as creating a deployment using the \u003ca href=\"https://cloud.elastic.co/home\"\u003eweb console\u003c/a\u003e, or, to make things even more fun, creating the deployment \u003ca href=\"https://registry.terraform.io/providers/elastic/ec/latest/docs\"\u003eprogrammatically using Terraform\u003c/a\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"cs666e457e6dd72af4"}}},{"title_text":{"title_text":[{"title_l10n":"Summary","_metadata":{"uid":"cs7cfac52a20498ace"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eReliability is the most fundamental feature of any product. After all, a system isn't beneficial if it's unavailable or nobody can use it. Building software reliability is, therefore, a constant flux of efforts focused on improving the design and operation of systems to make them more scalable, more reliable, and more efficient. Most software teams don't have the luxury of continuously focusing on optimization since innovation and delivering new features are equally important. Developing reliable software is then truly understanding what the code does from the moment it was written to when it is executed, without much room for guessing. And distributed tracing can help with this goal.\u003c/p\u003e\n\u003cp\u003eThis post discussed some key aspects that you need to consider to build software reliability with distributed tracing. It examined the importance of understanding your code's limits by pursuing the unknown unknowns using code instrumentation. It mentioned the importance of focusing on the four golden signals from the business transaction perspective. It discussed the importance of adopting an instrument-first approach to ensure your code will be genuinely observable. It highlighted the challenges of using distributed tracing with modern technology stacks. Finally, it provides you with considerations you need to worry about while adopting observability. Join me on March 3 in the virtual event, \u003ca href=\"https://www.elastic.co/virtual-events/building-software-reliability-with-distributed-tracing\"\u003eBuilding software reliability with distributed tracing\u003c/a\u003e, if you have any questions.\u003c/p\u003e\n\u003cp\u003eThere is no better way to start your distributed tracing journey than getting your hands dirty with an example. With \u003ca href=\"https://www.elastic.co/cloud/\"\u003eElastic Cloud\u003c/a\u003e, you can try \u003ca href=\"https://www.elastic.co/observability\"\u003eElastic Observability\u003c/a\u003e for free without needing a credit card. Create your account \u003ca href=\"https://cloud.elastic.co/registration?elektra=en-cloud-page\"\u003ehere\u003c/a\u003e. You can play with the examples written in \u003ca href=\"https://github.com/riferrei/otel-with-java\"\u003eJava\u003c/a\u003e and \u003ca href=\"https://github.com/riferrei/otel-with-golang\"\u003eGo\u003c/a\u003e to understand how the API works. If you need more information, you can subscribe to the \u003ca href=\"https://www.youtube.com/c/OfficialElasticCommunity\"\u003eElastic Community Channel\u003c/a\u003e, which has lots of tutorials, meetup recordings, and presentations to help you get started.\u003c/p\u003e"}],"_metadata":{"uid":"cs905378af19ede289"}}}],"publish_date":"2022-02-09T22:03:22.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Building Software Reliability with Distributed Tracing","seo_description_l10n":"Building software reliability requires a deep understanding of how your software's code executes without much room for guessing. Learn how distributed tracing can help with this while also terraforming the way for a much larger observability adoption.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"Building software reliability requires a deep understanding of how your software's code executes without much room for guessing. Learn how distributed tracing can help with this while also terraforming the way for a much larger observability adoption.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc2c6579373c53341","ACL":{},"created_at":"2021-07-12T21:53:13.753Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2021-07-12T21:53:13.753Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.194Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"parent_uid":null,"uid":"bltf57a751242bc5493","created_by":"bltfb089905b0c41028","updated_by":"bltfb089905b0c41028","created_at":"2022-01-28T22:11:49.094Z","updated_at":"2022-01-28T22:11:49.094Z","content_type":"image/png","file_size":"113641","filename":"illustration-protect-at-scale-social-1200x628.png","title":"illustration-protect-at-scale-social-1200x628.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-11T02:00:16.505Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf57a751242bc5493/61f46a2565ceda6b20b4b050/illustration-protect-at-scale-social-1200x628.png"},"title":"Building software reliability with distributed tracing","title_l10n":"Building software reliability with distributed tracing","updated_at":"2025-03-28T17:15:26.951Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/building-software-reliability-with-distributed-tracing","publish_details":{"time":"2025-03-28T17:15:32.454Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbf59002caa1ec5c1","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic observability features, using open standards, will enable automation teams to identify areas for process improvement and communicate business value.","author":["blt70064f34d44ea152"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-03-01T01:42:56.590Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1e7edb3aba9926c9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhile automating systems is seen as an imperative in boardrooms around the globe, automation teams — the teams on the ground — often lack the data to help them to industrialize their automation efforts and move from ad-hoc automation to strategic automation. \u003c/p\u003e\n\u003cp\u003eIn this automation-focused blog post, we will show how to instrument infrastructure automation with Elastic Observability. With Elastic Observability, automation teams can produce information that will help them identify areas for optimization, and develop dashboards that communicate business value to stakeholders and the c-suite.\u003c/p\u003e\n\u003cp\u003eWe will demonstrate how observability can help automation teams answer five critical questions to determine how their processes are performing, namely:\u003c/p\u003e\u003cul\u003e\u003cli\u003eHow are the performance of my automation services trending?\u003c/li\u003e\u003cli\u003eWhat are the specific issues and bottlenecks?\u003c/li\u003e\u003cli\u003eWhat is the general health of our automation capability?\u003c/li\u003e\u003cli\u003eIs automation saving my business time and increasing productivity?\u003c/li\u003e\u003cli\u003eAre teams using automation effectively and where can we optimize?\u003c/li\u003e\u003c/ul\u003e\u003cbr\u003e\u003cp\u003eWe will explore how we use the data to optimize automation and then look at how we configure Ansible command line as well as AWX (Tower) to extract the data. \u003c/p\u003e"}],"_metadata":{"uid":"cs08c5e4bc86016e6d"}}},{"title_text":{"title_text":[{"title_l10n":"Out of the box","_metadata":{"uid":"csc04f2bc9ff038167"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eThe pipeline instrumentation for Ansible is based on \u003ca href=\"https://opentelemetry.io/\"\u003eOpenTelemetry\u003c/a\u003e. This provides an open source approach to telemetry collection where the Elastic team is working with the Ansible community to provide Ansible visibility.\u003c/p\u003e\n\u003cp\u003eBy default the export publishes OpenTelemetry compliant data to \u003ca href=\"https://www.elastic.co/guide/en/apm/get-started/current/open-telemetry-elastic.html\"\u003eElastic Application Performance Monitoring\u003c/a\u003e (APM), which provides immediate insights into how automation flows are performing.\u003c/p\u003e"}],"_metadata":{"uid":"csfd327be5fa15a845"}}},{"title_text":{"title_text":[{"title_l10n":"Start with the end in mind: What does the data tell us about our pipelines and their performance?","_metadata":{"uid":"cs4b307218c085f685"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"How are the performance of my automation services trending?","_metadata":{"uid":"cs669fc30bcd19877f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eIn the example scenario we have automation flows and tests grouped by services, the Services view provides an overview of all the services that your team might be managing with insights into average runtime (Latency) and failure rate. \u003c/p\u003e"}],"_metadata":{"uid":"cs84b83a5259832fed"}}},{"image":{"image":{"uid":"bltf68797ed57e496e7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:35:02.392Z","updated_at":"2022-03-01T01:35:02.392Z","content_type":"image/png","file_size":"65487","filename":"ansible-automation-petclinic-account-test-environment.png","title":"ansible-automation-petclinic-account-test-environment.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.661Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf68797ed57e496e7/621d78460e638750b44cdc06/ansible-automation-petclinic-account-test-environment.png"},"_metadata":{"uid":"csacda2f1263d7c4ec"},"caption_l10n":"Services Overview","alt_text_l10n":"Services Overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbabd17f3eacbdceb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eDrilling down into a service provides information on the playbooks and tests that we run as part of this service as well as how our dependencies are performing.\u003c/p\u003e"}],"_metadata":{"uid":"cs19aa4284d1d8ca08"}}},{"image":{"image":{"uid":"blt3c44e63fb9e65b72","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:37:28.280Z","updated_at":"2022-03-01T01:37:28.280Z","content_type":"image/png","file_size":"78168","filename":"ansible-automation-transactions-dependencies.png","title":"ansible-automation-transactions-dependencies.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.679Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3c44e63fb9e65b72/621d78d86f0333490a0e6fda/ansible-automation-transactions-dependencies.png"},"_metadata":{"uid":"csf0ae000aa9c6b81a"},"caption_l10n":"Transactions and Dependencies","alt_text_l10n":"Transactions and Dependencies","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"What are the specific issues and bottlenecks?","_metadata":{"uid":"cs0c3ef10e61a3f48b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt seems that this has some work to do to improve the resilience of their automation, so they would drill down into a specific “Transaction” to see how the individual tasks run. In this example our Kubernetes environment took much longer than usual, but the transaction did not fail.\u003c/p\u003e"}],"_metadata":{"uid":"cs212c2429c1619eb2"}}},{"image":{"image":{"uid":"bltd9744210cddca1ab","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:37:54.315Z","updated_at":"2022-03-01T01:37:54.315Z","content_type":"image/png","file_size":"311701","filename":"ansible-automation-latency-distribution.png","title":"ansible-automation-latency-distribution.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.685Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd9744210cddca1ab/621d78f22f7a0b2e3f26c43e/ansible-automation-latency-distribution.png"},"_metadata":{"uid":"cs3da81a79eaa8620d"},"caption_l10n":"Transaction Span","alt_text_l10n":"Transaction Span","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7157dcd601a12881"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis automation however failed, and by clicking on the failed task we can immediately get more information on the Ansible task details as well as the error message.\u003c/p\u003e"}],"_metadata":{"uid":"cs1ff0007e587883e9"}}},{"image":{"image":{"uid":"blt6df2e4c41dd0a2e0","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:38:14.712Z","updated_at":"2022-03-01T01:38:14.712Z","content_type":"image/png","file_size":"126252","filename":"ansible-automation-timeline.png","title":"ansible-automation-timeline.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.692Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6df2e4c41dd0a2e0/621d7906c4c1b167484d2983/ansible-automation-timeline.png"},"_metadata":{"uid":"csf0cbf2c95b4269dc"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt1beeb9a25a82d60b","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:38:34.605Z","updated_at":"2022-03-01T01:38:34.605Z","content_type":"image/png","file_size":"217316","filename":"ansible-automation-metadata.png","title":"ansible-automation-metadata.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.699Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1beeb9a25a82d60b/621d791aba043c4a2c4a9c0d/ansible-automation-metadata.png"},"_metadata":{"uid":"csacd59e75b93ff014"},"caption_l10n":"Span details for a failed transaction","alt_text_l10n":"Span details for a failed transaction","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs585b8650934645dd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou might notice some interesting fields in the span details above. The Ansible Open Telemetry callback plugin appends labels to the OpenTelemetry data, and we can use these labels to build custom dashboards and queries. In fact we can add our own custom labels, in this example “manual_effort” and “team” to further refine our dashboards.\u003c/p\u003e\n\u003cp\u003eNow let us explore what type of higher level questions we can answer by instrumenting our automation flows. For this we will use dashboards to summarize data.\u003c/p\u003e"}],"_metadata":{"uid":"cs534d5c44443748d7"}}},{"title_text":{"title_text":[{"title_l10n":"What is the general health of our automation capability?","_metadata":{"uid":"cs5236d57c386b602e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe first set of questions I would like to answer is related to how much automation the teams do overall and when they run the automation. It would also be good to understand if the Ansible version is consistent over time. \u003c/p\u003e\n\u003cp\u003eMost of this information is available out of the box. The Ansible plugin has two variables that we use to group information by Team and also by Service:\u003c/p\u003e\u003cul\u003e\u003cli\u003eOTEL_SERVICE_NAME - This variable enables the Service Grouping for example our “Account Test Environment” service in the Service Overview view at the top. \u003c/li\u003e\u003cli\u003eOTEL_RESOURCE_ATTRIBUTES - this is a catch-all variable that enables us to set any custom attribute that would be useful. In our case we are logging “\u003cem\u003eteam name”\u003c/em\u003e and also “\u003cem\u003eexpected manual effort”\u003c/em\u003e. \u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs4d891c35e726ac40"}}},{"image":{"image":{"uid":"blt01c30b964d4565af","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:39:20.188Z","updated_at":"2022-03-01T01:39:20.188Z","content_type":"image/png","file_size":"383878","filename":"ansible-automation-1545-orchestrations.png","title":"ansible-automation-1545-orchestrations.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.706Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt01c30b964d4565af/621d79486f0333490a0e6fde/ansible-automation-1545-orchestrations.png"},"_metadata":{"uid":"csa5824e102ddfcdeb"},"caption_l10n":"Automation Overview","alt_text_l10n":"Automation Overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Is automation saving my business time and increasing productivity?","_metadata":{"uid":"cs2f75e166183e2934"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eCapturing the team names and also the expected manual effort per automation flow enables us to build dashboards that demonstrate how much manual effort the teams saved over time through automation. This dashboard adds the hours of manual effort per team over time and is management gold and enables organizations to justify the effort required to deploy, run and expand enterprise wide automation.\u003c/p\u003e"}],"_metadata":{"uid":"cs582fe8185e379ebe"}}},{"image":{"image":{"uid":"blt8970cddbcb6fd20c","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:39:44.518Z","updated_at":"2022-03-01T01:39:44.518Z","content_type":"image/png","file_size":"105288","filename":"ansible-automation-hours-saved-by-team.png","title":"ansible-automation-hours-saved-by-team.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.712Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8970cddbcb6fd20c/621d7960d83ad851e8a9d4c8/ansible-automation-hours-saved-by-team.png"},"_metadata":{"uid":"cs385a90156d51b0f2"},"caption_l10n":"Hours saved by Team","alt_text_l10n":"Hours saved by Team","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Are teams using automation effectively and where can we optimize?","_metadata":{"uid":"csec5cb96b6302be83"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe last set of questions we are looking at is to try and understand which modules teams use and also which modules they have issues with. \u003c/p\u003e\n\u003cp\u003eThe Ansible plugin captures the Ansible task level information and from this we can see that teams use more \u003cem\u003ecommand\u003c/em\u003e and \u003cem\u003eshell\u003c/em\u003e modules than Ansible good practices would encourage. This would be an opportunity for this team to optimize their work. It also shows that the team has a large number of failures due to how they use the \u003cem\u003eshell\u003c/em\u003e module with a summary of the top errors. Having this information readily available highlights areas for improvement and quick wins.\u003c/p\u003e"}],"_metadata":{"uid":"cs6c52519dc9172a8b"}}},{"image":{"image":{"uid":"blt8e08099ef6915307","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:40:17.539Z","updated_at":"2022-03-01T01:40:17.539Z","content_type":"image/png","file_size":"301428","filename":"ansible-automation-dashboard.png","title":"ansible-automation-dashboard.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.719Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8e08099ef6915307/621d798147e4d72e3e67f35c/ansible-automation-dashboard.png"},"_metadata":{"uid":"cs96ad4390b1ca364e"},"caption_l10n":"Automation Module Summary","alt_text_l10n":"Automation Module Summary","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Instrumenting Ansible: Zero playbook changes!","_metadata":{"uid":"cs0b532bd8bf3a25c4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe good news here is that instrumenting playbooks do not require any changes to the actual playbooks themselves. At a bare minimum it requires the ansible community package, three python dependencies, an entry in the ansible.cfg file and environment variables that point to the Elastic APM Server.\u003c/p\u003e\u003cbr\u003eThis section will cover the required changes at a high level, if you want to get into the details please refer to \u003ca href=\"https://github.com/yohanswanepoel/ansible_apm_test\"\u003ethis repository\u003c/a\u003e."},{"title_l10n":"Command line Ansible","_metadata":{"uid":"cse77dd9bc08a00f09"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eThe command line Ansible configuration requires four steps:\u003c/p\u003e\u003cul\u003e\u003cli\u003eInstall the Ansible community.general package\u003c/li\u003e\u003cli\u003eInstall the Python dependencies: opentelemetry-exporter-otlp\u003c/li\u003e\u003cli\u003eUpdate the ansible.cfg file and \u003ccode\u003ecallbacks_enabled = community.general.opentelemetry\u003c/code\u003e \u003c/li\u003e\u003cli\u003eSpecify OTEL_EXPORTER_OTLP_ENDPOINT as an environment variable\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Configuring AWX/Tower","_metadata":{"uid":"cs2280bed2bf014d6a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eThere is a slight nuance in where to apply the configuration when using AWX or Ansible Tower. AWX in this project runs on Kubernetes, so the settings and packages we require are in specific components.\u003c/p\u003e"},{"title_l10n":"Packages","_metadata":{"uid":"cs738501f788e8625e"},"header_style":"H4","paragraph_l10n":"\u003cp\u003eAWX requires an Execution Environment with the Ansible and Python packages installed. For this we used the \u003ca href=\"https://www.ansible.com/blog/introduction-to-ansible-builder\"\u003eAnsible Builder tool\u003c/a\u003e to create the container definition. \u003c/p\u003e\n\u003cp\u003eYou then upload the container to an image repository accessible by AWX and define an Execution Environment using the container you created. \u003c/p\u003e"},{"title_l10n":"Service details and environment variables","_metadata":{"uid":"csc39a6fe2cb4a3f1b"},"header_style":"H4","paragraph_l10n":"\u003cp\u003eTo inject the environment variables and service details you can use custom credential types and then assign the credentials to the Playbook template. This gives you the flexibility to reuse the endpoint details for Elastic APM and also standardize on custom fields for reporting purposes.\u003c/p\u003e"}],"_metadata":{"uid":"csd506c0c01135de97"}}},{"image":{"image":{"uid":"blt431eced8c44d88ba","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:42:06.070Z","updated_at":"2022-03-01T01:42:06.070Z","content_type":"image/png","file_size":"84444","filename":"ansible-automation-apm-endpoint.png","title":"ansible-automation-apm-endpoint.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.724Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt431eced8c44d88ba/621d79ee5c258851f3bc71c1/ansible-automation-apm-endpoint.png"},"_metadata":{"uid":"cs53271c08c58047db"},"caption_l10n":"APM Service Endpoint","alt_text_l10n":"APM Service Endpoint","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"bltf6a6d610f604b280","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-03-01T01:42:19.974Z","updated_at":"2022-03-01T01:42:19.974Z","content_type":"image/png","file_size":"119887","filename":"ansible-automation-apm-service-details.png","title":"ansible-automation-apm-service-details.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-01T01:49:07.730Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf6a6d610f604b280/621d79fb3837bf67467a9910/ansible-automation-apm-service-details.png"},"_metadata":{"uid":"cs3b5e2309595968c5"},"caption_l10n":"Custom Fields","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Ansible Config file","_metadata":{"uid":"cs2009b5c44487d22d"},"header_style":"H4","paragraph_l10n":"\u003cp\u003eThe easiest way to propagate the Ansible Config file setting is to include the anisble.cfg file in the root folder of the automation project that you use for the templates in.\u003c/p\u003e\n\u003cp\u003eThat is all there is to it. Once that is done the telemetry data for the playbooks you run in AWX will appear in Elastic providing you with great insights.\u003c/p\u003e"}],"_metadata":{"uid":"cs685183606c226e5e"}}},{"title_text":{"title_text":[{"title_l10n":"Summary","_metadata":{"uid":"cs24daa13357cbeb83"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn this blog post we demonstrated how instrumenting your Ansible automation can provide insights that will help you optimize and industrialize automation in your organization. We also showed how easy it is to instrument your Ansible automation flows. \u003c/p\u003e\u003cbr\u003ePlease reach out and share your thoughts on what insights you would like to drive from your automation. Learn \u003ca href=\"https://www.elastic.co/guide/en/apm/get-started/current/open-telemetry-elastic.html\"\u003emore here\u003c/a\u003e."}],"_metadata":{"uid":"cs6c7da6d86607d8e8"}}}],"publish_date":"2022-03-01T01:48:54.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"5 questions about Ansible that Elastic Observability can answer","seo_description_l10n":"Elastic observability features, using open standards and Ansible, will enable automation teams to identify areas for process improvement and communicate business value.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Python","label_l10n":"Python","keyword":"python","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6293a0df96e13ba7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:49:39.583Z","updated_at":"2023-11-06T20:49:39.583Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.836Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt22e723be0010edc0","ACL":{},"content_type":"image/png","created_at":"2021-02-24T15:45:28.502Z","created_by":"bltf6ab93733e4e3a73","file_size":"114517","filename":"blog-thumb-cloud-observability-midnight.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-observability-midnight.png","updated_at":"2022-02-11T21:03:14.508Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:46.214Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt22e723be0010edc0/603674987737ce7794e655ff/blog-thumb-cloud-observability-midnight.png"},"title":"5 questions about Ansible that Elastic Observability can answer","title_l10n":"5 questions about Ansible that Elastic Observability can answer","updated_at":"2025-03-28T17:15:03.754Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/5-questions-about-ansible-that-elastic-observability-can-answer","publish_details":{"time":"2025-03-28T17:15:08.411Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt165b804c2a3ada98","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security has verified a multi-stage malware attack targeting the Ukraine government: Operation Bleeding Bear. Learn more.","author":["bltc1a27bf09861513f"],"category":["bltb79594af7c5b4199"],"created_at":"2022-01-19T14:59:24.423Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5900298bf06e0d45"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElastic Security \u003ca href=\"https://elastic.github.io/security-research/malware/2022/01/01.operation-bleeding-bear/article/\"\u003ehas verified\u003c/a\u003e a new destructive malware targeting Ukraine: Operation Bleeding Bear.\u003c/p\u003e\n\u003cp\u003eOver the weekend, \u003ca href=\"https://www.microsoft.com/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/\"\u003eMicrosoft released\u003c/a\u003e details about this multi-stage and destructive malware campaign that the \u003ca href=\"https://twitter.com/ncsccUA/status/1482733473228013569?s=20\"\u003eUkrainian National Cyber Security Coordination Center\u003c/a\u003e has been referring to as Operation Bleeding Bear.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eElastic users are fully protected\u003c/strong\u003e from attacks like these through our advanced malware detection and Ransomware Protection capabilities, and the Elastic Security team continues to monitor these events. This case highlights the importance of prevention when it’s up against ransomware and malware with destructive capabilities.\u003c/p\u003e\n\u003cp\u003eIn this \u003ca href=\"https://elastic.github.io/security-research/malware/2022/01/01.operation-bleeding-bear/article/\"\u003efull-length article\u003c/a\u003e, we break down the involved malware providing new insights and highlighting behaviors that can be used to help identify this activity.\u003c/p\u003e\n\u003cp\u003eElastic Security researchers provide an overview of Operation Bleeding Bear, including how it wipes the Master Boot Record, uses tampering techniques such as disabling Windows Defender, leverages process hollowing, and corrupts files across the file system. We also outline \u003ca href=\"https://elastic.github.io/security-research/malware/2022/01/01.operation-bleeding-bear/article/\"\u003edefensive recommendations\u003c/a\u003e, specific Indicators of Compromise (IoCs) and a how-to-locate and remediate guide using Elastic Security and the MITRE ATT\u0026CK® framework — identifying malware components at each stage.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eExisting Elastic Security users can access these capabilities within the product. If you’re new to Elastic Security, take a look at our \u003ca href=\"https://www.elastic.co/training/free#quick-starts\"\u003eQuick Start guides\u003c/a\u003e (bite-sized training videos to get you started quickly). And you can always get started with a \u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-security-7-16-blog\"\u003efree 14-day trial of Elastic Cloud\u003c/a\u003e.\u003c/p\u003e\u003cbr\u003e"}],"_metadata":{"uid":"csc6cc03c78e0f94cd"}}}],"publish_date":"2022-01-19T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Security verifies new malware targeting Ukraine: Operation Bleeding Bear (WhisperGate)","seo_description_l10n":"Elastic Security has verified a multi-stage malware attack targeting the Ukraine government: Operation Bleeding Bear. Learn more in this article.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt8eb410499d8645b9","ACL":{},"content_type":"image/png","created_at":"2021-12-03T15:10:01.483Z","created_by":"blt4349d9729d06d101","file_size":"161741","filename":"blog-security-detection-720x420.png","parent_uid":null,"tags":[],"title":"blog-security-detection-720x420.png","updated_at":"2021-12-03T15:10:01.483Z","updated_by":"blt4349d9729d06d101","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-03T18:35:40.809Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8eb410499d8645b9/61aa334981fe8f3ca269a15f/blog-security-detection-720x420.png"},"title":"Elastic Security verifies new destructive malware targeting Ukraine: Operation Bleeding Bear","title_l10n":"Elastic Security verifies new destructive malware targeting Ukraine: Operation Bleeding Bear","updated_at":"2025-03-28T17:14:45.282Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-security-verifies-operation-bleeding-bear","publish_details":{"time":"2025-03-28T17:14:50.496Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2cb28e2119c3d8c4","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security підтвердила багатоетапну атаку з використанням зловмисного програмного забезпечення, спрямовану на уряд України: операцію Bleeding Bear («Кривавий ведмідь»). Докладніше.","author":["bltc1a27bf09861513f"],"category":[],"created_at":"2022-03-07T17:42:17.551Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csff916d09b407101a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElastic Security \u003ca href=\"https://elastic.github.io/security-research/malware/2022/01/01.operation-bleeding-bear/article/\"\u003eпідтвердила\u003c/a\u003e нову руйнівну атаку з використанням зловмисного ПЗ, спрямовану на Україну: операцію Bleeding Bear.\u003c/p\u003e\n\u003cp\u003eПротягом вихідних \u003ca href=\"https://www.microsoft.com/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/\"\u003eкорпорація Microsoft оприлюднила\u003c/a\u003e подробиці цієї багатоетапної руйнівної кампанії з використання зловмисного програмного забезпечення, яку \u003ca href=\"https://twitter.com/ncsccUA/status/1482733473228013569?s=20\"\u003eНаціональний координаційний центр кібербезпеки України\u003c/a\u003e називає «Операція Bleeding Bear».\u0026nbsp;\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eКористувачі Elastic повністю захищені\u003c/strong\u003e від подібних атак завдяки нашим розширеним можливостям виявлення зловмисного програмного забезпечення та захисту від програм-вимагачів, і команда Elastic Security продовжує відстежувати ці події. Цей випадок підкреслює важливість запобігання, коли мова йде про програми-вимагачі та зловмисне ПЗ з руйнівними можливостями.\u003c/p\u003e\n\u003cp\u003eУ \u003ca href=\"https://elastic.github.io/security-research/malware/2022/01/01.operation-bleeding-bear/article/\"\u003eповній статті\u003c/a\u003e ми аналізуємо залучене зловмисне програмне забезпечення, надаючи нові відомості та виявляючи шаблони поведінки, які можуть бути використані для ідентифікації такої активності.\u003c/p\u003e\n\u003cp\u003eДослідники Elastic Security здійснюють огляд операції Bleeding Bear, включаючи те, як під час неї стирається основний завантажувальний запис, використовуються методи фальсифікації, такі як вимкнення Захисника Windows, і підміна процесів, а також пошкоджуються файли у файловій системі. Ми також викладаємо \u003ca href=\"https://elastic.github.io/security-research/malware/2022/01/01.operation-bleeding-bear/article/\"\u003eрекомендації щодо захисту\u003c/a\u003e, конкретні індикатори компрометації та інструкції з локалізації та виправлення з використанням Elastic Security та платформи MITRE ATT\u0026CK® — ідентифікуючи компоненти зловмисного програмного забезпечення на кожному етапі.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eПоточні користувачі Elastic Security можуть отримати доступ до цих можливостей у продукті. Якщо ви новачок у Elastic Security, перегляньте наші \u003ca href=\"/training/free#quick-starts\"\u003eпосібники для швидкого початку\u003c/a\u003e (невеликі навчальні відео, щоб швидко розпочати роботу). І ви завжди можете розпочати роботу з \u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-security-7-16-blog\"\u003eбезкоштовною 14-денною пробною версією Elastic Cloud\u003c/a\u003e.\u003c/p\u003e\u003cbr\u003e"}],"_metadata":{"uid":"cs166256b79f2c5e4b"}}}],"publish_date":"2022-01-19T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Security підтверджує факт нових зловмисних програм, спрямованих на Україну: операція Bleeding Bear (WhisperGate)","seo_description_l10n":"Elastic Security підтвердила багатоетапну атаку з використанням зловмисного програмного забезпечення, спрямовану на уряд України: операцію Bleeding Bear («Кривавий ведмідь»). Дізнайтеся більше в цій статті.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt8eb410499d8645b9","ACL":{},"content_type":"image/png","created_at":"2021-12-03T15:10:01.483Z","created_by":"blt4349d9729d06d101","file_size":"161741","filename":"blog-security-detection-720x420.png","parent_uid":null,"tags":[],"title":"blog-security-detection-720x420.png","updated_at":"2021-12-03T15:10:01.483Z","updated_by":"blt4349d9729d06d101","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-03T18:35:40.809Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8eb410499d8645b9/61aa334981fe8f3ca269a15f/blog-security-detection-720x420.png"},"title":"Elastic Security verifies new destructive malware targeting Ukraine: Operation Bleeding Bear (in Ukrainian)","title_l10n":"Elastic Security підтверджує факт нових руйнівних зловмисних програм, спрямованих на Україну: операція Bleeding Bear","updated_at":"2025-03-28T17:14:29.552Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-security-verifies-operation-bleeding-bear-ukrainian","publish_details":{"time":"2025-03-28T17:14:34.220Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3a37ffedd9bda2e6","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"With the collection of osquery data combined with the power of Elastic Stack, users can greatly expand their endpoint telemetry, enabling enhanced detection and investigation and improving hunting for vulnerabilities and anomalous activities.","author":["blt7c76ea1dccaa833f"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-03-28T14:56:35.600Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3a0685551df9c0f1"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eAs of the Elastic 7.16 release, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-security-7-16-0\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003eOsquery Manager is generally available\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e for Elastic Agent, providing every user the ability to easily deploy and run osquery across their environments. With the collection of osquery data combined with the power of Elastic Stack, you can gr\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eeatly expand your endpoint telemetry, enabling enhanced detection and investigation and improving hunting for vulnerabilities and anomalous activities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThis blog post covers a brief introduction to osquery and the Osquery Manager integration for Elastic Agent, and provides a \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003ecomprehensive configuration guide for the Agent and its usage\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e for \u003ca href=\"https://www.elastic.co/security/threat-hunting\" target=\"_self\"\u003ethreat hunting\u003c/a\u003e for persistence on Windows endpoints.\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWhat is osquery?\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003ca href=\"https://osquery.io/\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003e\u003cstrong\u003eOsquery\u003c/strong\u003e\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e is an open source tool to monitor IT infrastructure. It lets you query your operating systems — supported systems are Windows, OS X (macOS), Linux, and FreeBSD — as if they were a relational database, in that you can explore your system data with SQL-like statements. It relies on an extensive \u003c/span\u003e\u003ca href=\"https://osquery.io/schema/5.1.0/#\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003eschema\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e to collect system operational information.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eFurthermore, osquery provides \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eosqueryd\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e to manage multiple hosts, run scheduled queries, and aggregate results and generate logs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eDeploying and scaling osquery in a multi-machine environment can easily become a struggle for many IT professionals. The\u0026nbsp; following figure shows that many steps are involved in the process:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cseda5c3fac7eaf74c"}}},{"image":{"image":{"uid":"blt42492000dcb9bc93","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:47:09.960Z","updated_at":"2022-03-28T14:47:09.960Z","content_type":"image/png","file_size":"689768","filename":"1-osquery-development-flow.png","title":"1-osquery-development-flow.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.315Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt42492000dcb9bc93/6241ca6deb32d94188d01ab6/1-osquery-development-flow.png"},"_metadata":{"uid":"csa5209cc53084bfaa"},"caption_l10n":"Figure 1: Osquery deployment flow","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0c4913a35de92af7"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWhile this might seem complex, the Elastic \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eOsquery Manager\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e integration supports an easy deployment across multiple endpoints and simplifies the collection of data and aggregation of data.\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eIt’s never been easier to implement osquery at scale\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe Osquery Manager integration simplifies the deployment shown in Figure 1 by adding it to the policy assigned to the agents running on your endpoints. Once deployed, it lets you run live queries and schedule recurring queries for those agents to gather data fro\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003em \u003c/span\u003e\u003ca href=\"https://osquery.io/schema/\"\u003ehundreds of tables\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e a\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003ecross your entire enterprise — all within a dedicated page in Kibana. The \u003c/span\u003e\u003ca href=\"https://osquery.io/schema\"\u003eextensive\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e schema provided by osquery helps with a variety of use cases, including security vulnerability detection, compliance monitoring, incident investigations, and more.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eLet’s see now how to use this integration for threat hunting.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eWindows advanced persistence techniques\u003c/strong\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003ePersistence is a tactic used by adversaries to maintain their access on a compromised machine.\u0026nbsp; Several techniques exist to achieve this tactic – an exhaustive list of those techniques are describe within the \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/tactics/TA0003/\"\u003e\u003cu\u003eMITRE ATT\u0026CK Matrix\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eSome of the most common techniques exploited by the attackers are:\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e1.\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003e Scheduled Task technique \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e(\u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1053/005/\"\u003e\u003cu\u003eMITRE T1053.005\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e): Adversaries may abuse the Windows Task Scheduler to perform task scheduling for initial or recurring execution of malicious code. Attackers often invent very convincing names for their scheduled tasks and this might pass unobserved by a less scrutinous eye.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e2. \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eServices Creation technique\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e (\u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1543/003/\"\u003e\u003cu\u003eMITRE T1543.003\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e): Adversaries may create or modify Windows services to repeatedly execute malicious payloads as part of persistence. When Windows boots up, it starts programs or applications called services that perform background system functions. We should investigate services whose executables are located in an unusual folder. AppData and its subfolders are a notorious example.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e3. \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eStartup Items technique\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e (\u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1547/001/\"\u003e\u003cu\u003eMITRE T1547.001\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e): Adversaries may achieve persistence by adding a program to a startup folder or referencing it with a Registry Run key. Adding an entry to the \"Run keys\" in the Registry or startup folder will cause the program referenced to be executed when a user logs in. Placing a program within a startup folder will also cause that program to execute when a user logs in.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe most common Run keys created by default on Windows systems are:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003eHKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003eHKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003eHKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003eHKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eBut Run keys may exist under multiple Windows registry hives, and if you want a comprehensive understanding on this subject, visit the official microsoft \u003c/span\u003e\u003ca href=\"https://docs.microsoft.com/en-us/documentation/\"\u003e\u003cu\u003edocumentation\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWith this brief introduction to some known persistence techniques, let's focus on the configuration of the Elastic Agent with the Osquery Manager integration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eElastic Agent: A quick refresh\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/fleet/current/fleet-overview.html\"\u003e\u003cu\u003eElastic Agent\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e provides a single, unified way to add monitoring for logs, metrics, and other types of data to a host. It can also protect hosts from security threats, query data from operating systems, and more. A single agent makes it easier and faster to deploy monitoring across your infrastructure. Each agent has a single policy that you can update to add integrations for new data sources, security protections, and more.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eElastic Agent can be deployed in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/fleet/current/fleet-overview.html\"\u003e\u003cu\u003eFleet\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e or standalone mode. With the former, you install Elastic Agent on each host you want to monitor and use Fleet in Kibana to define, configure, and manage your agents in a central location. It makes the management and upgrade of your agents considerably easier. Standalone mode lets you install Elastic Agent on each host you want to monitor and manually configure the agent locally on the system where it’s installed. You are responsible for managing and upgrading the agents. This approach is recommended for advanced users only.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eEvery Agent policy may contain multiple integrations depending on the type of data you want to collect from the endpoint where it is deployed.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eConfiguring Osquery Manager with Elastic Agent\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eLet’s see the full configuration cycle from deployment to installation of the Elastic Agent focusing on the Osquery Manager integration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eOnce your deployment is up and running, open the Kibana menu and browse to Fleet:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs014789428d67eb1c"}}},{"image":{"image":{"uid":"blt7d8ac8ded1b7e19a","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:48:08.720Z","updated_at":"2022-03-28T14:48:08.720Z","content_type":"image/png","file_size":"98403","filename":"2-kibana-fleet.png","title":"2-kibana-fleet.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.325Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7d8ac8ded1b7e19a/6241caa8a87d324d9a1526c9/2-kibana-fleet.png"},"_metadata":{"uid":"cs4a39aeae9b95fe7e"},"caption_l10n":"Figure 2: Kibana Fleet","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs81508bb4d4eb1ec1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eThe Agents section shows the running agents in your deployment along with their status and policy information. If you spin up a cloud instance, you will see that a preconfigured agent running the Elastic Cloud agent policy already includes a fleet server integration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eBefore adding your own agent, it's time to create a policy. You can rely on the available default policy, which comes with a prebuilt system integration. In this demo, however, we are going to create a new one. The creation wizard allows you to specify the policy name as well as enable the collection of monitoring data for troubleshooting purposes if needed.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd3426f8e2530177b"}}},{"image":{"image":{"uid":"bltbc7735cd92f72314","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:50:18.086Z","updated_at":"2022-03-28T14:50:18.086Z","content_type":"image/gif","file_size":"1343954","filename":"3-policy-creation.gif","title":"3-policy-creation.gif","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.332Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbc7735cd92f72314/6241cb2a78aaca403c23bbe3/3-policy-creation.gif"},"_metadata":{"uid":"csdfe5d7db505623f8"},"caption_l10n":"Figure 3: Policy creation","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse1ecb39265a1a61d"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eOnce the policy is created, you can start adding integrations to it. Every policy already contains the System integration that allows you to monitor your servers and collect system data like Windows event logs, Linux /var/log files, cpu, load, memory, network, process, and process_summary.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eWe can leave it to collect metrics from our host and then add new ones by clicking on the button \u003c/span\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003cstrong\u003eAdd Integrations\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e. From the integration catalog, search for the \u003c/span\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003cstrong\u003eOsquery Manager integration\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e and select it to add to your existing policy.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs179b7c2d699d501b"}}},{"image":{"image":{"uid":"blt3a034af22cab258a","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:50:54.587Z","updated_at":"2022-03-28T14:50:54.587Z","content_type":"image/gif","file_size":"2846540","filename":"4-add-osquery-manager.gif","title":"4-add-osquery-manager.gif","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.341Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3a034af22cab258a/6241cb4eea69f146914e88fa/4-add-osquery-manager.gif"},"_metadata":{"uid":"cscf442af4f811d543"},"caption_l10n":"Figure 4: Add Osquery Manager integration","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csabb7e8256759e31a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eOnce your policy is saved, it is time to assign it to the Agent — but it hasn’t yet been created. Let's follow the Agent installation wizard for downloading and installing the Agent files on the target system.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse3a588dbaaf5c65d"}}},{"image":{"image":{"uid":"blt301cc0f711b9fc46","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:51:20.920Z","updated_at":"2022-03-28T14:51:20.920Z","content_type":"image/gif","file_size":"882546","filename":"5-add-agent-wizard.gif","title":"5-add-agent-wizard.gif","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.349Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt301cc0f711b9fc46/6241cb686ede5e4690a3f51e/5-add-agent-wizard.gif"},"_metadata":{"uid":"csea343a5849211c0d"},"caption_l10n":"Figure 5: Add Agent wizard","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb58896135d05ddca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eIf the installation process is successful, you will see your agent listed as healthy in the Agents tab. Data is now being collected from your Endpoints.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfd25f015344ed66f"}}},{"image":{"image":{"uid":"bltc62ebef4908813a5","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:51:45.243Z","updated_at":"2022-03-28T14:51:45.243Z","content_type":"image/png","file_size":"127613","filename":"6-agent-deployment-status.png","title":"6-agent-deployment-status.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.357Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc62ebef4908813a5/6241cb8145a531453af5b57b/6-agent-deployment-status.png"},"_metadata":{"uid":"csce40b4e5cf65df3d"},"caption_l10n":"Figure 6: Agent deployment status","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9dc0ef40df158f78"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eRepeat this installation step for every endpoint you want to monitor. The same policy can be applied to multiple endpoints at the same time.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eHow does Osquery Manager work?\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWith Osquery in Kibana, you can:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eRun live queries for one or more agents\u003c/span\u003e\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eSchedule query packs to capture changes to OS state over time\u003c/span\u003e\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eView a history of past queries and their results\u003c/span\u003e\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eSave queries and build a library of queries for specific use cases\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe osquery page contains three sections:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eLive queries: To run live osqueries on the deployed agents running the osquery manager integration, you can select one or multiple agents at the same time on which you want to run the intended query. Or group them by Policy or running Platform.\u003c/span\u003e\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(33, 37, 41);\"\u003ePacks: You can create packs to organize sets of queries. This allows you to define multiple queries at the same time and schedule them to run at periodic intervals on one or more agents. For example, you might create one pack that checks for IT compliance-type issues, and another pack that monitors for evidence of malware.\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eSaved queries: Contains a list of queries that have been saved previously and can be reused \u003c/span\u003e\u003cspan style=\"color: rgb(32, 33, 36);\"\u003efor live queries or also within packs.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp style=\"text-align: left;\"\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd0ab41f56fe40cce"}}},{"image":{"image":{"uid":"bltda0241775f9a5e9c","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:52:18.476Z","updated_at":"2022-03-28T14:52:18.476Z","content_type":"image/png","file_size":"73586","filename":"7-kibana-osquery.png","title":"7-kibana-osquery.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.365Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltda0241775f9a5e9c/6241cba249b1d64d9bcd34d5/7-kibana-osquery.png"},"_metadata":{"uid":"cs4a35c281c025265a"},"caption_l10n":"Figure 7: Kibana osquery","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3a15cec8b1711005"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eIt's finally time to see how to use the Osquery Manager integration to threat hunt for persistence on Windows. For this demo I have deployed a local Windows 2019 Server with an Agent running the \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eSystem\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e and \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eOsquery Manager \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eintegration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWe are going to see how to perform threat hunting for the following two techniques:\u003c/span\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003ePersistence with Task Scheduler (MITRE T1053.005)\u003c/span\u003e\u003c/li\u003e\u003cli style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003ePersistence with Registry Run Keys (MITRE T1547.001)\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThreat hunting for persistence with Task Scheduler\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eOne possible persistence technique relies on the creation of scheduled tasks on Windows via task scheduler that would persist on system reboots. The presence of tasks that contain ambiguous names or a path to ambiguous executable files can represent an indicator of a malicious activity going on at the endpoint.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eAccording to the extended osquery schema, the \u003c/span\u003e\u003ca href=\"https://osquery.io/schema/5.1.0/#scheduled_tasks\"\u003e\u003cu\u003escheduled_tasks\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e table collects the list of scheduled tasks on the Windows endpoints and includes several useful fields like the name, path, or runtime information on any task. An example query to be run to retrieve these information is as follows:\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eSELECT name, action, path, state FROM scheduled_tasks;\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThrough this query, we are going to grab the list of scheduled tasks configured on our endpoint with enhanced details such as the path of the executable that is run by the scheduled task or the runtime information.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eIn the Kibana Osquery section, select the \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003elive queries\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e tab to execute the SQL statement on a selected number of Agents. The query returns the content of the \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003escheduled_tasks\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e table. We could look into this data to look for indicators of persistence. For instance, in my endpoint I can see a service named \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eWindowsUpdates\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e where the action references a \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003ePowershell\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e script on the ambiguous \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cem\u003eAppData\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e folder with a very suspicious name.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2f4bbc2a95d62311"}}},{"image":{"image":{"uid":"blt0220114d6dcd3407","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:52:57.109Z","updated_at":"2022-03-28T14:52:57.109Z","content_type":"image/gif","file_size":"7046180","filename":"8-scheduled-tasks-analysis.gif","title":"8-scheduled-tasks-analysis.gif","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.373Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0220114d6dcd3407/6241cbc99c74804c1596a818/8-scheduled-tasks-analysis.gif"},"_metadata":{"uid":"cs6810d411ab40c571"},"caption_l10n":"Figure 8: Scheduled tasks analysis","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs29cd7253801f5e50"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eQuery results are automatically stored in an Elasticsearch index and can easily be mapped to the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/ecs/current/index.html\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003eElastic Common Schema\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e to normalize your data to a common set of fields. This will greatly simplify your workflow within the Elastic Security app, enabling you to easily search, analyze, and visualize data across multiple sources.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eLater in this blog we will see how to operationalise this data by creating a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/detection-engine-overview.html\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003edetection rule\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e out of these queries.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eThreat hunting for persistence with Registry Run Keys\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eAs previously mentioned, adversaries may achieve persistence by referencing a program with a Registry Run key, such that it will cause the program referenced to be executed when a user logs in. Osquery schema provides a table named \u003c/span\u003e\u003ca href=\"https://osquery.io/schema/5.1.0/#registry\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003eregistry\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e that retrieves information from the Microsoft registry hive like the key, name, path, or type that can be used for threat hunting purposes. The following SQL statement can be used to search for all\u003c/span\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003cem\u003e Run\\RunOnce\u003c/em\u003e\u003c/span\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e keys values in the Registry Hive that could be exploited for persistence.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eselect * from registry where key like 'HKEY_USERS\\%\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run' or key like 'HKEY_USERS\\%\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\RunOnce' or key like 'HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run%\\%' ;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eThe retrieved table can be analyzed looking for ambiguous registry values containing suspicious paths or command executions. In my example, I discovered a Run key with data that specifies the establishment of a remote connection to a suspicious IP address.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs05edfadc3635b3be"}}},{"image":{"image":{"uid":"blt96c1026cdc5223ea","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:53:50.809Z","updated_at":"2022-03-28T14:53:50.809Z","content_type":"image/gif","file_size":"5610122","filename":"9-registry-table-analysis.gif","title":"9-registry-table-analysis.gif","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.379Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96c1026cdc5223ea/6241cbfe22e3ba45344ed7be/9-registry-table-analysis.gif"},"_metadata":{"uid":"cs396709417d4c6cbf"},"caption_l10n":"Figure 9: Registry table analysis","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2be7d55b8cb47cb0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eScaling your operations with Osquery Manager\u0026nbsp;\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eOsquery in Kibana provides a way to schedule queries to be run periodically via \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/master/osquery.html#osquery-schedule-query\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003ePack\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e. When adding a new Pack configuration, we can specify multiple queries to be executed at a certain interval and \u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);'\u003eoptionally map results or static values to fields in the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/ecs/1.12/ecs-reference.html\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003eElastic Common Schema\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(33, 37, 41);'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6a02c03832707ee6"}}},{"image":{"image":{"uid":"blt865ce2a4884fbff7","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:54:26.675Z","updated_at":"2022-03-28T14:54:26.675Z","content_type":"image/png","file_size":"158871","filename":"10-add-scheduled-queries.png","title":"10-add-scheduled-queries.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.386Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt865ce2a4884fbff7/6241cc22eb32d94188d01ac4/10-add-scheduled-queries.png"},"_metadata":{"uid":"cs7fa91d530cec007f"},"caption_l10n":"Figure 10: Add scheduled queries with Pack","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt112c58568dcfc790","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:54:45.773Z","updated_at":"2022-03-28T14:54:45.773Z","content_type":"image/png","file_size":"102095","filename":"11-pack-query.png","title":"11-pack-query.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.394Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt112c58568dcfc790/6241cc3545a531453af5b583/11-pack-query.png"},"_metadata":{"uid":"cs64927fce70eb5501"},"caption_l10n":"Figure 11: Pack query example","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6f6967c9ce1ea304"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(33, 37, 41);'\u003eFurthermore, you can import prebuilt configuration Packs. The official osquery \u003c/span\u003e\u003ca href=\"https://github.com/osquery/osquery\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003eGitHub repository\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(33, 37, 41);'\u003e contains some very good examples of packs that could be used for security monitoring use cases.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eBuild security alerts for osquery data\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(33, 37, 41);'\u003eCombining osquery with the Elastic Security solution will let you unleash all the power of the Elastic Stack.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(33, 37, 41);'\u003eFor instance, it is possible to rely on the results of a scheduled osquery with Packs and write a detection to alert when query results match a suspicious pattern. As an example, while hunting for persistence on Scheduled tasks, we could generate an alert whenever the returned results contain a path matching an executable in the AppData folder.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs147989ca56bff61a"}}},{"image":{"image":{"uid":"bltba486c2f41631bbd","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-03-28T14:55:13.225Z","updated_at":"2022-03-28T14:55:13.225Z","content_type":"image/png","file_size":"152947","filename":"12-suspicious-action.png","title":"12-suspicious-action.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-28T23:32:35.402Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltba486c2f41631bbd/6241cc516ede5e4690a3f528/12-suspicious-action.png"},"_metadata":{"uid":"csad5e3df2c4ac9c30"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs89bf32efb4d0d7d6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eGive Osquery Manager a try\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eThe \u003c/span\u003e\u003ca href=\"https://docs.elastic.co/en/integrations/osquery_manager\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003eOsquery Manager integration\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e gives you greater insight into the endpoints you’re monitoring with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='color:rgb(17, 85, 204);'\u003e\u003cu\u003eElastic Security\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e and helps security teams to better detect, investigate, and hunt for vulnerabilities and anomalous activities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003eIf you want to give all this a try and see how easy it is to deploy Osquery Manager and start running queries, you can start a \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003cu\u003efree 14-day trial of Elastic\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e. Please share any feedback on the \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co/\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003cu\u003eElastic Discuss forum\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e or the \u003c/span\u003e\u003ca href=\"https://ela.st/slack\"\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e\u003cu\u003eElastic Stack Community on Slack\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(0, 0, 0);'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbd99979902862349"}}}],"publish_date":"2022-03-30T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"A comprehensive guide on threat hunting for persistence with osquery","seo_description_l10n":"With the collection of osquery data combined with the power of Elastic Stack, users can greatly expand their endpoint telemetry, enabling enhanced detection and investigation and improving hunting for vulnerabilities and anomalous activities.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt741994bc79ce7bd9","created_by":"bltb93267ccd58e6ba5","updated_by":"bltb93267ccd58e6ba5","created_at":"2021-08-20T15:10:55.026Z","updated_at":"2021-08-20T15:10:55.026Z","content_type":"image/png","file_size":"103114","filename":"blog-security-laptop-720x420.png","title":"blog-security-laptop-720x420.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-08-20T15:11:00.220Z","user":"bltb93267ccd58e6ba5"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt741994bc79ce7bd9/611fc5ff6768907ea9764dba/blog-security-laptop-720x420.png"},"title":"A comprehensive guide on threat hunting for persistence with osquery","title_l10n":"A comprehensive guide on threat hunting for persistence with osquery","updated_at":"2025-03-28T17:14:12.138Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/comprehensive-guide-on-threat-hunting-for-persistence-with-osquery","publish_details":{"time":"2025-03-28T17:14:16.804Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt687480ab53d723ee","_version":13,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security’s developer support team has seen a surge in reports from customers about sluggish performance in our UI. Here's how we used Elastic Observability and its APM capabilities to look under the hood at what was really happening.","author":["bltb700a6129837fa7a"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-03-30T02:13:21.618Z","created_by":"bltac225ac457fe0293","markdown_l10n":"Elastic Security’s developer support team has recently seen a surge in reports from customers about sluggish performance in our UI. Our initial inspection of logs for troubleshooting provided some insights, but not enough for a true fix. Luckily, we have [Elastic Observability](https://www.elastic.co/observability/solution-overview) and its APM capabilities to dive in deeper and look under the hood at what was really happening within Elastic Security. And, more importantly, how we could improve its performance for customers. \n\nHere’s the story of how the Elastic Security engineering team optimized the performance of detection rules in order to improve security visibility. In this post, I would like to share some of the details on how we accomplished that goal with Elastic Observability.\n\n\n## The importance of detection rules for Elastic Security\n\nDetection rules are at the heart of [Elastic Security](https://www.elastic.co/security). Their job is to search Elasticsearch indices periodically (i.e. logs) for suspicious source events and notify SOC analysts when a rule’s conditions are met. \n\nElastic Security might execute hundreds and even thousands of detection rules in the background, so their performance is critical, as any slowness could lead to scan gaps and potentially missed alerts and threats.\n\nThe main focus was on reducing the median execution time of detection rules per Kibana instance for a given volume of data. Metrics related to memory or CPU usage were not considered since rule execution operations are I/O bound. \n\n\n## Challenges around measuring application performance\n\nOne challenge when testing the performance of detection rules is that they run on a schedule in the background. It makes them different from classic REST APIs, to which you can make a series of requests and measure the response time or use off-the-shelf tools such as ApacheBench. We needed a way to collect all the required performance-related metrics during rule execution.\n\nAs a team, we were already collecting some execution-related metrics such as total rule execution time and maximum read and write time. While these metrics could answer some questions and help identify rules that execute heavy queries, it was difficult to use this information for general performance testing and identification of bottlenecks.\n\nAnother challenge was the many layers of abstractions around the rule execution code. Many teams contribute to the detection engine and the core framework it’s built upon. As a result, when a developer calls a framework’s method, they are not always aware of the database requests being made under the hood since the framework is owned and maintained by other teams.\n\nThis makes performance optimizations particularly hard as all the complexity is hidden. To effectively track and understand the performance, the goal was to visualize what’s going on inside the rule executors and track every database request.\n\n\n## Baselining and measuring application performance\n\nBefore starting any optimization work, it was important to understand the current situation and collect relevant performance metrics. To endeavor on any optimizations without this context would be like shooting in the dark. \n\nWhen measuring performance, the first option that came to mind was to use standard Node.js tools like the Performance API and the built-in profiler. However, these tools are pretty low-level and require a substantial time investment to work with. We wanted something simpler and ready to use out of the box. Since Elastic Security and Elastic Observability are built on the same Elasticsearch platform and deliver the value of being able to secure and observe at the same time, we decided to try Elastic Observability. Elastic Observability can be set up to collect performance metrics in a matter of minutes and record important application events — like HTTP requests and database queries — without any prior configuration.\n\nWith the APM agent deployed, it was pretty easy to start collecting telemetry data right away. \n\n\n\n1. Provision Elastic Observability cloud cluster\n2. [Enable and configure Elastic node.js APM agent](https://www.elastic.co/guide/en/apm/agent/nodejs/current/index.html)\n\n\n(Note: Kibana comes integrated with the Elastic node.js APM agent for self-monitoring, [details here](https://github.com/elastic/kibana/blob/main/docs/developer/getting-started/debugging.asciidoc).)\n\nWe enabled about 500 detection rules to generate load and navigated to the APM section of Elastic Observability to see tracing details.\n\nWithin Elastic APM it was easy to find the rule execution transactions and the corresponding performance charts quickly.\n\n![enter image description here][5]\n\n![enter image description here][6]\n\nWith the out-of-the-box average rule execution latency and distribution as initial parameters and baseline, all consequent optimization work would be compared to these numbers.\n\n## The optimization process for Elastic Security \n\nOnce we had gathered the initial, baseline numbers, it was now time to start searching for optimization opportunities.\n\nBy default, the Elastic APM agent collects all outgoing requests and Elasticsearch queries. Distributed traces with rich contextual information about user, url, payload, and query details are also provided out of the box by Elastic Observability. \n\n![enter image description here][3]\n\nBy simply reviewing the trace, one can visualize the paths that the code follows under the hood making it possible to spot bottlenecks. For example, it was apparent which outgoing Elasticsearch queries were taking the longest to execute among the transactions. \n\nIt is also worth noting that code path uniformity should be considered when examining performance. The analyzed code may have logical conditions that significantly affect the number of operations performed. For example, cached data or exceptions lead to early execution termination. And if a mixture of transactions with different spans count falls into the analyzed sample, this can significantly skew the final results. So prepare in advance different execution paths and split the tests into homogeneous groups.\n\nTo provide even more information about the execution of a specific code path, we added custom instrumentation to executors with spans. Spans add contextual information to executed code blocks like name, labels, outcome, etc. That way, we could visualize actual business logic rather than raw method calls.\n\n![enter image description here][4]\n\nAfter identifying the slowest methods, it’s time to analyze code for performance problems. Some of the glaring issues identified were:\n\n1. Inefficient database calls - Analyzing spans highlighted a couple of database calls that request the same data from different places. This was easy to fix by reorganizing the code.\n2. Lack of parallelization - Some requests were being sent serially instead of being sent in parallel.\n3. Usage of refresh=wait_for - When writing documents we often included this parameter unnecessarily. This parameter makes every Elasticsearch write operation wait for an index update, which adds up to one extra second to every call.\n4. Lack of batching - Many documents were written in a row instead of buffering write operations and sending only one bulk write request to the database.\n\n\n\n## Results of application optimization with Elastic Observability\n\nSome of the issues surfaced were easy to fix, so I decided to take the initiative and corrected them right away. That first optimization pass led to a reduction in the average rule execution time of about 30%.\n\n![enter image description here][1]\n\n![enter image description here][2]\n\nThis investigation also sparked several inter-team discussions and has resulted in plans to invest even more time to make rule executors even faster. Optimizing application performance is a never-ending goal for developer teams but with Elastic Observability, we can approach this work systematically and with real data points. \n\n\n## Observability and Security on a unified platform\n\nAs oftentimes with software development, the identified performance issues could have been avoided. Instead of optimizing the performance of detection rules after the fact, a more proactive approach would have been preferable. Teams should consider increased instrumentation at the start of development work to collect performance data. With a proper observability solution in place, teams can incorporate performance review as part of their standard code review process proactively and fix performance issues in earlier development stages.\n\nThis optimization project was a great example of the better-together nature of the Elastic Security and Observability solutions. My knowledge and expertise around Elastic Security made it very easy for me to learn Elastic Observability, deploy the solution, and quickly find real answers. With Elastic, it’s easy to leverage your Elasticsearch expertise for both observability and security initiatives. And what better place to put that perspective into practice than right here at Elastic. \n\n\n---\n\nIf you’re new to Elastic and want to give both the Observability and Security solutions a spin, you can start a [free 14-day trial of Elastic](https://cloud.elastic.co/registration). Please share any feedback on the [Elastic Discuss forum](https://discuss.elastic.co/) or the [Elastic Stack Community on Slack](https://ela.st/slack).\n\n\n [1]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb692f34d2f944695/6243be578e98cf0ef87cccd8/image3.png\n [2]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt316a775aaf14f3b2/6243be7a81c9270edfaab4ed/image7.png\n [3]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41013d310ebd95db/6243be93cd71790ea006536f/image1.png\n [4]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd9d7c1e65088d4cc/6243bead96ee250ebe231a8b/image4.png\n [5]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt00c730d4e2ec2ffb/6243bee8cd71790ea0065373/image5.png\n [6]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt29177ba10ae80ba9/6243befe0909bc0eb039f8fe/image7.png","modular_blocks":[],"publish_date":"2022-03-30T01:56:17.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic on Elastic - Using Elastic Observability to optimize the performance of detection rules in Elastic Security","seo_description_l10n":"Get a behind the scenes look at how the Elastic Security team leveraged #ElasticObservability to optimize the performance of their security solution.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blte50385d14a2cee80","created_by":"bltf020187e3918e5de","updated_by":"bltf020187e3918e5de","created_at":"2021-11-04T07:42:30.648Z","updated_at":"2021-11-04T07:42:30.648Z","content_type":"image/png","file_size":"85196","filename":"apac-anomaly-detection-event-illo.png","title":"apac-anomaly-detection-event-illo.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-04T07:42:56.531Z","user":"bltf020187e3918e5de"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte50385d14a2cee80/61838ee6912a3c799bc4284f/apac-anomaly-detection-event-illo.png"},"title":"Elastic on Elastic - Using Elastic Observability to optimize the performance of detection rules in Elastic Security","title_l10n":"Elastic on Elastic - Using Elastic Observability to optimize the performance of detection rules in Elastic Security","updated_at":"2025-03-28T17:13:47.620Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/using-elastic-observability-to-optimize-the-performance-of-detection-rules-in-elastic-security","publish_details":{"time":"2025-03-28T17:13:53.630Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb1f2cd0ed2b7c893","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"The goals for our accessibility efforts go beyond compliance. We want all humans to feel empowered to understand and affect the world when they use Elastic products.","author":["blt05a3c381b672c006"],"category":["bltb79594af7c5b4199"],"created_at":"2022-03-31T18:29:56.871Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"When was the last time you visited a website and got frustrated because you had trouble using it? Maybe the site was using WebGL technology that your browser didn’t support, you couldn’t read its text due to it being so small. If you think back to these annoying experiences where you functionally could not navigate a site, chances are you’ve experienced inaccessibility in one form or another.\n\n![Venn diagram of the words frustrating and difficult, with the word inaccessible in the overlapping space.][1]\n\nThis is not to say that all frustrating experiences are inaccessible, but there are definitely overlaps between bad UX and inaccessibility.\n\nSpecifically, it focuses on people who have disabilities that impede their vision, hearing, and movement. Web accessibility means that websites, tools, and technologies are designed and developed so that people with disabilities can use them. More specifically, people can perceive, understand, navigate, and interact with the web.\n\n- **Perceivable:** Can users consume content on your site in different ways? For example, providing closed captions for a video.\n- **Operable:** Can the site function without confusion and without the use of a mouse or complex interactions?\n- **Understandable:** Can a user understand how the user interface of the site functions and the information on the site?\n- **Robust: **Can different assistive devices (screen readers, for example) understand the website?\n\n\nEach of these different principles have a success rating of either A, AA, or AAA. A l[evel requirement](https://www.levelaccess.com/wcag-a-and-wcag-aa-conformance/) must be met to prevent barriers for use by assistive technology. \n\n## **Goals of Accessibility in Kibana**\n\nThe goals for our accessibility efforts go beyond compliance. We want all humans to feel empowered to understand and affect the world when they use Elastic products. You can find our statement under [Accessibility](https://www.elastic.co/guide/en/kibana/master/accessibility.html) in the Kibana docs. Kibana aims to meet [WCAG 2.1 level AA](https://www.w3.org/WAI/WCAG21/quickref/?currentsidebar=%23col_customize\u0026levels=aaa\u0026technologies=server%2Csmil%2Cflash%2Csl) compliance. Currently, we can only claim to partially conform, meaning we do not fully meet all of the success criteria. However, we do try to take a broader view of accessibility, and go above and beyond the legal and regulatory standards to provide a good experience for all of our users.\n\nWe continue to look into ways to improve our products’ accessibility, including more comprehensive tools for testing during development and to catch regressions.\n\n## **Assessment approach**\n\n**Elastic assesses the accessibility of Kibana with the following approaches:**\n\n- Self-evaluation: Our employees are familiar with accessibility standards and review new designs and implemented features to confirm that they are accessible.\n- External evaluation: We engage external contractors to help us conduct an independent assessment and generate a formal VPAT. Please email accessibility@elastic.co if you’d like a copy.\n- Automated evaluation: We are starting to run [axe](https://www.deque.com/axe/) on every page. See our current progress in the [automated testing GitHub issue](https://github.com/elastic/kibana/issues/51456).\n\n\n### **Manual testing largely focuses on screen reader support and is done on:**\n\n- VoiceOver on MacOS with Safari, Chrome and Edge\n- NVDA on Windows with Chrome and Firefox\n\n\n[EUI](https://github.com/elastic/eui), or Elastic UI, is the component library that’s behind all of the UI that we create at Elastic. An accessibility focus at this foundational layer of our work ensures solid building blocks supporting every piece of UI we create. By consolidating all of our most used patterns in one area, we’re able to provide consistent experiences and [handle lots of accessibility concerns](https://github.com/elastic/eui/issues/2262) before the scores of implementing developers — from Kibana, to Elastic Cloud, to every other UI team, internal and external — even get to work.\n\n### **Some examples of small EUI accessibility bug fixes which went into the 7.16.0 release:**\n\n- [[EuiPopover] Allow content to be accessible during opening animation by thompsongl · Pull Request #5249 · elastic/eui · GitHub](https://github.com/elastic/eui/pull/5249)\n- [https://github.com/elastic/eui/pull/5241](https://github.com/elastic/eui/pull/5241)\n\n\n### **Example of Accessibility (often abbreviated to A11y) testing :**\n\n- Documentation for a11y testing in Kibana can be found [here](https://www.elastic.co/guide/en/kibana/master/development-tests.html#development-accessibility-tests).\n- Meta issue for accessibility testing in Kibana can be found [here](https://github.com/elastic/kibana/issues/51456).\n- An example of kibana a11y functional test can be found in this [file](https://github.com/elastic/kibana/blob/master/x-pack/test/accessibility/apps/index_lifecycle_management.ts) that contains a11y tests for the ILM plugin.\n\n\n\nDespite our best efforts to ensure accessibility in Kibana, there may be some limitations. Please [open an issue on GitHub](https://github.com/elastic/kibana/issues/new?labels=Project%3AAccessibility\u0026template=Accessibility.md\u0026title=%28Accessibility%29) if you observe an issue not [listed](https://github.com/elastic/kibana/issues?q=is%3Aissue+is%3Aopen+sort%3Aupdated-desc+label%3AProject%3AAccessibility).\n\n### **Known limitations are in the following areas:**\n\n- Charts: We have a clear plan for the first steps of making charts accessible. We’ve opened this [Charts accessibility ticket on GitHub](https://github.com/elastic/elastic-charts/issues/300) for tracking our progress.\n- Maps: Maps might pose difficulties to users with vision disabilities. We welcome your input on making our maps accessible. Go to the [Maps accessibility ticket on GitHub](https://github.com/elastic/kibana/issues/57271) to join the discussion and view our plans.\n- Tables: Although generally accessible and marked-up as standard HTML tables with column headers, tables rarely make use of row headers and have poor captions. You will see incremental improvements as various applications in Kibana adopt a new accessible component.\n- Color contrast: Modern Kibana interfaces generally do not have color contrast issues. However, older code might fall below the recommended contrast levels. As we continue to update our code, this issue will phase out naturally. We have recently added [textures](https://github.com/elastic/elastic-charts/issues/1061) in addition to colors to enhance readability and accessibility of charts.\n\n\n## **More Documentation**\n\n- [Elastic's accessibility journey: Mindset and tools](https://www.elastic.co/blog/elastic-accessibility-journey-mindset-and-tools)\n- [Accessibility Statement for Kibana](https://www.elastic.co/guide/en/kibana/master/accessibility.html)\n\n\n\n\n [1]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd83c0669d9bf0ca7/6245f9048d970d0e9927c913/unnamed-8.png","modular_blocks":[],"publish_date":"2022-03-31T18:56:47.000Z","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"","seo_image":null,"seo_title_l10n":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"},{"uid":"blt4bebb28f8e616e9a","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blte132c539e3832b05","ACL":{},"_version":2,"content_type":"image/png","created_at":"2020-02-11T15:56:18.503Z","created_by":"bltd934ac619651f9f7","description":"","file_size":"16654","filename":"accessibility-blog-thumb.png","is_dir":false,"parent_uid":null,"tags":[],"title":"accessibility-blog-thumb.png","updated_at":"2020-02-12T00:41:52.479Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-02-12T00:41:55.325Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte132c539e3832b05/5e4349d0c43f006b46274649/accessibility-blog-thumb.png"},"title":"P.O.U.R (Perceivable, Operable, Understandable, Robust) into Accessibility","title_l10n":"How Elastic approaches accessibility in Kibana","updated_at":"2025-03-28T17:13:27.400Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/how-elastic-approaches-accessibility-in-kibana","publish_details":{"time":"2025-03-28T17:13:31.944Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7908c045e17f761f","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"Deployment strategies like blue-green and canary allow building and shipping your software releases with control. But this doesn't mean that you are error-free. But you can minimize the damage by integrating Argos Rollout and Elastic Observability.","author":["blt8280a0fbfa4a6db2"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-04-01T02:13:50.367Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"_This blog post was written by [Daniel Hoang](https://twitter.com/dhpup), developer advocate from [Akuity](https://akuity.io/)._\n\nShipping complex applications at high velocity lead to increased failures. Longer pipelines, scattered microservices, and more code inherently lead to bigger complexity where small mistakes may cost you big time.\n\nWe can’t promise that this blog post will help you get rid of failed deployments, however, we can promise that automated verification of deployments using Argo Rollouts and Elastic Observability will minimize damage, and help you feel more confident when shipping complex applications to Kubernetes.\n\n\n### **What is Argo?**\n\nArgo is a collection of open-source tools for Kubernetes to run workflows, manage clusters, and do GitOps right. It’s also an open-source project that saw an incredible 115% year-on-year increase in in-production use according to [the 2021 CNCF Survey](https://www.cncf.io/reports/cncf-annual-survey-2021/).\n\n\nIn this blog post, we will take a glimpse at how to make the best out of combining Argo Rollouts and Elastic Observability and creating a fully controlled release. This guide is intended to help you understand what this type of implementation could look like with Argo CD, Argo Rollouts \u0026 Elastic Observability. You can always use other deployment tools or verification tools to achieve this as well.\n\nBefore we go into the setup of everything I want to share a bit about the tools we will be using today. Argo CD is a declarative, GitOps Continuous Delivery tool for Kubernetes. Argo Rollouts which is very key to this example is a drop-in replacement for a deployment that opens up complex deployment options like a canary and blue-green deployment. Elastic Observability is a platform available both on-premises and via Elastic Cloud that allows you to consolidate signal types like metrics, logs, and traces into a single unified view. We will be using its support to APM (Application Performance Management) for this setup.\n\n\n### **Application setup**\n\nFor this example, we will be using [the rollouts demo application from a GitHub repository](https://github.com/argoproj/rollouts-demo). [ ](https://github.com/argoproj/rollouts-demo)\n\nThis application has a great visual representation. Each block represents a response. The images we will be using today will be purple and bad-yellow, where purple represents an errorless application and bad-yellow represents an application with a 50% error response rate. \n\n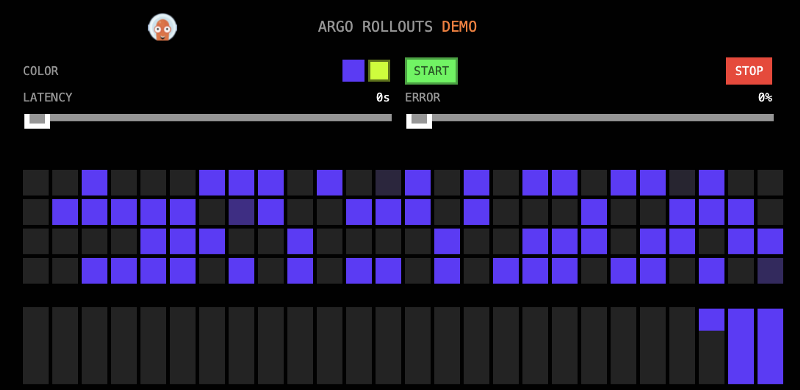\n\n### **Instrument the application with Elastic Observability**\n\nNow, why would you want to instrument your application with Elastic Observability? What we want to do is to provide reliability and insight into the pipeline so that developers can catch errors early and act upon them. Elastic Observability is a great tool to use to achieve this, especially in the context of Argo where your Kubernetes deployments can easily scale to massive proportions. With the added visibility teams can improve customers' experience and better adhere to SLAs and SLOs. The ultimate goal is to [build software reliability](https://www.elastic.co/blog/building-software-reliability-with-distributed-tracing). \n\nFor the purpose of this blog post, we will be using Elastic Cloud which is a SaaS-hosted version of Elastic. A quick start guide is available on [the Elastic Documentation website](https://www.elastic.co/guide/en/apm/guide/current/apm-quick-start.html):[ ](https://www.elastic.co/guide/en/apm/guide/current/apm-quick-start.html)\n\nOnce Elastic Cloud is up, we will need to add the Application Performance Monitoring integration. \n\nOnce that is done, you will need to instrument the application. \n\n**Install the agent**\n\nInstall the APM agent packages for Go.\n\n`go get go.elastic.co/apm`\n\n**Configure the agent**\n\nElastic Agents are unified agents that you deploy to hosts or containers to collect data and send it to the Elastic Stack, they can also be libraries that run inside of your application process depending on what programming language is used(In this case we’re using Go which this concept applies to.). APM services are created programmatically based on the executable file name or the `ELASTIC_APM_SERVICE_NAME` environment variable.\n\n Initialize using environment variables:\n\n Set the service name. Allowed characters: a-z, A-Z, 0-9, -, _, and space.\n\n If ELASTIC_APM_SERVICE_NAME is not specified, the executable name will be used.\n\n export ELASTIC_APM_SERVICE_NAME=\n\n Set custom APM Server URL. Default:[ http://localhost:8200.](http://localhost:8200.)\n\n export ELASTIC_APM_SERVER_URL=\n\n Use if APM Server requires a token\n\n export ELASTIC_APM_SECRET_TOKEN=\n\n**Instrument your application**\n\nInstrument your Go application by using one of the provided instrumentation modules or by using the tracer API directly.\n\nimport (\n\n\t\"net/http\"\n\n\t\"go.elastic.co/apm/module/apmhttp\"\n\n)\n\nfunc main() {\n\n\tmux := http.NewServeMux()\n\n\t...\n\n\thttp.ListenAndServe(\":8080\", apmhttp.Wrap(mux))\n\n}\n\nAlternatively, you could also instrument your application using [OpenTelemetry](https://opentelemetry.io/). Here is an [example in Go](https://github.com/riferrei/otel-with-golang) that shows you how to do this.\n\n\n### **Find the data**\n\nOnce we have the faulty application running we can start to see what data could be used for verification. In this case, it looks like the failed transaction rates are available so we'll go ahead and use that. \n\n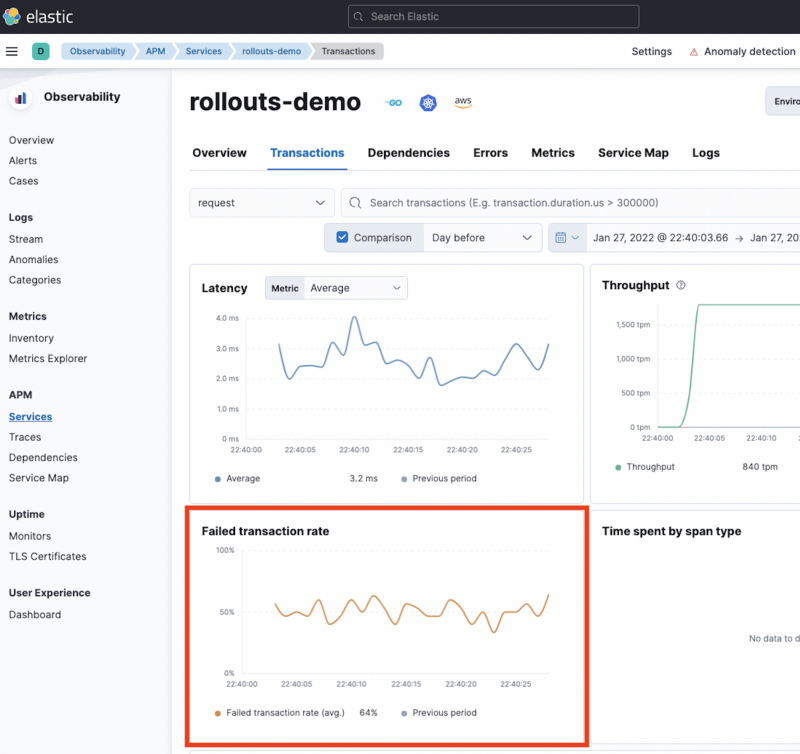![alt_text]\n\n\nAll of the data that you would normally query for in Kibana is actually exposed using the Elastic API. \n\n\n### **Build a test**\n\nAs you’re building a test you will need to determine what metrics would be the best to track based on your application. For this example, we can use a simple query that essentially shows the average of the response codes based on a timeframe. \n\n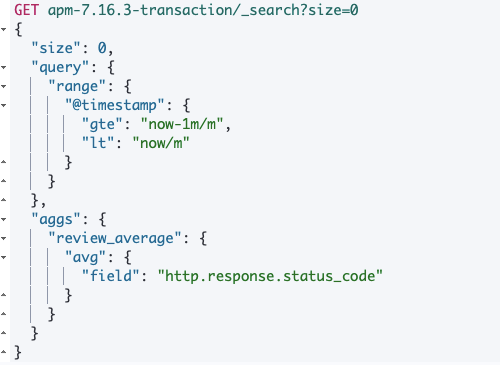\nElastic API Query Example\n\nYou will notice [in the Argo Rollouts docs](https://argoproj.github.io/argo-rollouts/features/analysis/) Elastic is not listed as an integration, however, we shouldn't worry about that because Argo Rollouts is flexible and there are ways to easily integrate various tools with it. [ ](https://argoproj.github.io/argo-rollouts/features/analysis/)\n\nWhat’s really great is that Argo Rollouts has an analysis method called a **Job **which allows you to use a Kubernetes job as your test. \n\nWhat I did next was I created a shell script test which queries for that average response code, and if it is greater than my set threshold it returns an exit code. Then I threw that test into a container to later run as part of a Kubernetes job. \n\n\n### **Next use Argo Rollouts**\n\nTo do this we will be replacing the deployment yaml with an Argo Rollouts yaml, this adds a new section `strategy` to define the progressive delivery option. You will see that we will be using a canary strategy and pausing for analysis at 20% of the new deployment. \\\n \\\nIn this example, we’re going to be rolling out this new version to 20% of production customers and based on their experience either rollback or rollout 100% to production. This would be a huge improvement if you’re currently pushing applications from 0-100% in production without any testing at all. However, this model does not work for every company, especially if you have stricter SLA models. If you fall under one of those companies, you may have to consider doing additional testing in other stages, use an atomic switch model like blue/green, or use a service mesh combined with load testing.\n\n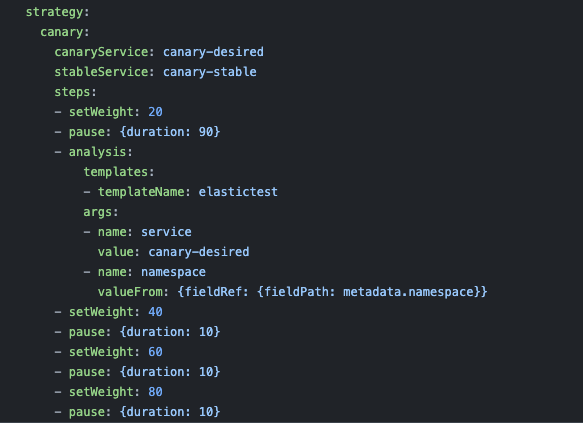\n\nFor the analysis step, you will also need to define a YAML. \n\nIn this step, I’ve defined the image containing the test, and the commands to execute the test. \n\n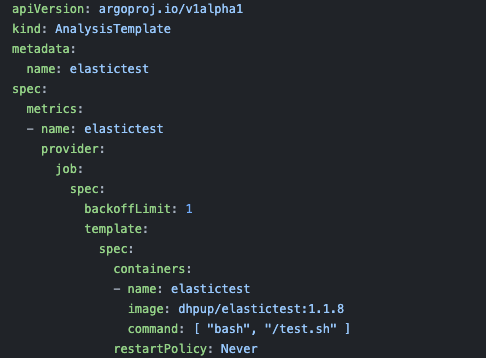\n\n### **Automated deployment verification \u0026 rollback**\n\nIn the picture below you can see it all in action. As the yellow version was slowly rolled out, we ran an analysis. Then, based on the failure of the analysis, we rolled completely back to the color purple. Success!\n\n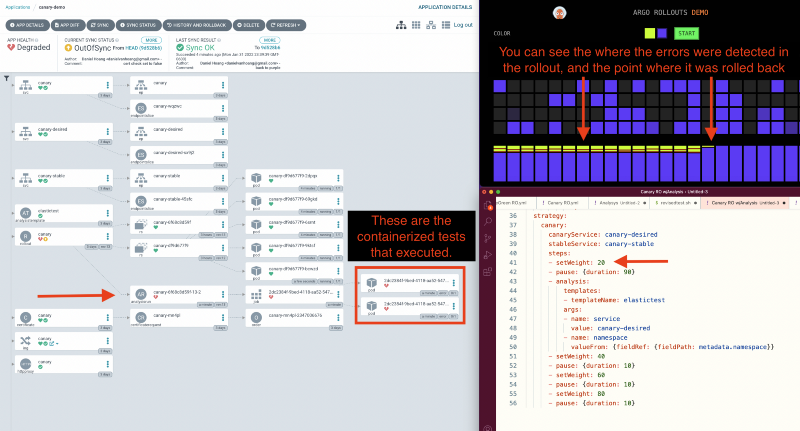\n\nCombining Argo Project with Elastic Observability is a combo that results in a very strong and capable [observability tool][1]. Both Elastic and Argo are extremely flexible in their implementation in terms of API access, and a variety of verification types. I hope this guide helps you in the next part of your CI/CD journey.\n\nIf you have any questions feel free to reach out to me on Twitter at [@dhpup](http://twitter.com/dhpup) or check out the [Argo Project website](https://argoproj.github.io/).\n\n\n [1]: https://www.elastic.co/observability","modular_blocks":[],"publish_date":"2022-03-31T07:00:00.000Z","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"Deployment strategies like blue-green and canary allow building and shipping your software releases with control. But this doesn't mean that you are error-free. But you can minimize the damage by integrating Argos Rollout and Elastic Observability.","seo_image":null,"seo_title_l10n":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"OpenTelemetry","label_l10n":"Open source/standards","keyword":"opentelemetry","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt069bd34528952802","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:44:13.512Z","updated_at":"2023-11-06T20:44:13.512Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.903Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt75ebbc12a186b316","created_by":"blt4349d9729d06d101","updated_by":"blt4349d9729d06d101","created_at":"2022-01-28T20:24:55.834Z","updated_at":"2022-01-28T20:24:55.834Z","content_type":"image/png","file_size":"43920","filename":"observability.png","title":"observability.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-31T23:17:09.534Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt75ebbc12a186b316/61f4511765ceda6b20b4b01e/observability.png"},"title":"How to automate verification of deployments with Argo Rollouts and Elastic Observability","title_l10n":"How to automate verification of deployments with Argo Rollouts and Elastic Observability","updated_at":"2025-03-28T17:13:08.957Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/automate-verification-of-deployments-with-argo-rollouts-and-elastic-observability","publish_details":{"time":"2025-03-28T17:13:14.407Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt285b751bcf9302dd","_version":25,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticsearch enhancements added in 7.15+, lowers data transfer and storage (DTS) and can lower your Elastic Cloud bills. Learn how our cloud observability team saved $100,000 and upgrade to 8.1 today.","author":["blt59e7f7049d793705"],"category":["bltb79594af7c5b4199"],"created_at":"2022-04-14T01:12:05.447Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"Let's start with the bottom line: When we upgraded to Elasticsearch 7.15 last year, our internal observability clusters saw a reduction in inter-node traffic from 464TB to 204.5TB per day. We monitored this reduction through subsequent upgrades and noticed its impact on our data transfer and storage costs. So here it is: upgrading saved Elastic $3,500 per day, or approximately $100,000 a month, or $1.2 million annually. We are excited to see these innovations directly lower the total cost of ownership and potentially save money for our customers. Here's a closer look at how we did it, and how you can, too.\n\n**Note:** As of the date of this blog post, the [latest Elastic release is 8.1][1] — however rest assured that if you're upgrading to the latest release, you're getting the data (and cost) savings present in 7.15, along with all the efficiencies and improvements we've since introduced.\n\n## Introducing Elastic’s own observability (O11y) clusters\n\nObserving production software, services, and infrastructure is critical to the success of any organization. That is why at Elastic, we use [Elastic Observability](https://www.elastic.co/observability) to ensure the availability of [Elastic Cloud](https://www.elastic.co/cloud/). Not only do our customers depend on this managed service for their observability, [security](https://www.elastic.co/security), and [search](https://www.elastic.co/enterprise-search/), but we also use Elastic Cloud for these same use cases.\n\nAll told, Elastic’s observability cluster comprises approximately 207 production clusters spanning 4 different cloud providers, hosting over 1.2 trillion documents. The 207 clusters can be broken up into 3 clusters in each [cloud region](https://www.elastic.co/guide/en/cloud/current/ec-reference-regions.html), where we gather, store, and analyze data like metrics, logs, and APM data. While this provides the benefits of restricting network traffic to regions and for isolation and security, it can be challenging to recognize patterns across a distributed platform. If there is an interesting data point in one region, how can you easily determine if the same data point is occurring in any of our other regions?\n\n![enter image description here][2]\n \nBy applying [cross-cluster search](https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-cross-cluster-search.html), the Elastic Cloud Observability team uses a single overview cluster that executes searches across all of the regional logging, metrics, and traces clusters. Cross-cluster search is both a scalable and seamless solution to keep up with the pace of Elastic Cloud’s regional expansion as our team monitors each new region. If you would like to know about our single overview cluster, you can read about it [here](https://www.elastic.co/blog/use-cross-cluster-search-elastic-cloud-observability). Or if you are curious about how we defined our SLI/SLO parameters for Elastic Cloud, you can check this ElasticON talk [here](https://www.elastic.co/blog/use-cross-cluster-search-elastic-cloud-observability).\n\n## Avoiding a network traffic jam \n\nWith the size and scale of the observability cluster monitoring Elastic Cloud, there is bound to be “some” network traffic. Other than the terabyte of logs, metrics, and trace data ingested per day, there is also roughly 464TB worth of inter-node traffic! This includes data being relocated between tiers defined by [index lifecycle management](https://www.elastic.co/guide/en/elasticsearch/reference/current/index-lifecycle-management.html) (ILM) and data sync between nodes that are located in different [availability zones](https://www.elastic.co/guide/en/cloud/current/ec-planning.html#ec-ha) to ensure high availability. Searches that are executed across multiple nodes of a cluster from the overview cluster also contribute to this network traffic. If you are familiar with the pricing from some of the major cloud providers, then you already know how data transfer and storage (DTS) network traffic charges can quickly add up. \n\nWith the enhancements made in [Elasticsearch 7.15](https://www.elastic.co/blog/whats-new-elasticsearch-kibana-cloud-7-15-0), inter-node traffic was reduced by more than half to 204.5TB — and with this significant reduction in DTS saved Elastic more than $3,500 dollars a day, $100,000 per month, or $1.2 million a year! \n\n## How we did it\n\nIn [Elasticsearch 7.15](https://www.elastic.co/blog/whats-new-elasticsearch-kibana-cloud-7-15-0) there were two critical changes to drastically reduce DTS:\n\n### 1. Network data compression\n\nThe first change was utilizing lz4, a lossless compression algorithm we used to compress indexing data. From our benchmarks shown below, we show negligible performance overhead for heavy-indexing use cases like logs, metrics, and time-series data while reducing inter-node traffic by more than 70%.\n\n![enter image description here][3]\n\nThis greatly reduced node traffic which helped ultimately reduced our DTS cost.\n\n### 2. New data relocation and recovery methods\n\nPrior to 7.15, data relocation between phases in ILM like hot and warm could be sent to different data nodes within the cluster. If nodes are located in different availability zones then a cost would be incurred for sending network data from node to node from the cloud provider.\n\n![enter image description here][4]\n\nIn 7.15, data relocation is handled by utilizing snapshot data. Communication between the data nodes and the snapshot storage doesn’t traverse different availability zones which reduces DTS costs.\n\nIn addition to data relocation, automatic shard recovery and resilience are improved by using snapshot data. Prior to 7.15 if a data node is added, replaced, removed, or simply unreachable, copies of data would be rebalanced across the remaining data nodes within the cluster to ensure resiliency. Shards would be copied from node to node via inter-node communication which would increase DTS.\n\n![enter image description here][5]\n\nUsing the same technology, 7.15 shards are now recovered from snapshot data stored on cloud object storage, avoiding communication from node to node that would otherwise increase DTS.\n\nIf you would like to know more about these changes in 7.15 and DTS reduction, I would highly recommend reading [reducing data transfer and storage DTS costs in Elastic Cloud.](http://www.elastic.co/blog/reduce-data-transfer-and-storage-dts-costs-in-elastic-cloud) There is great information on pricing and additional details about some of the technical changes in Elasticsearch.\n\n## Are you ready to experience life in the (network) fast lane?\n\nFor clusters with heavy indexing like Elastic’s internal observability cluster, we expected a significant drop in DTS which resulted in a reduced cloud bill. Simply upgrading to 7.15 (or a later version of Elastic) can help deliver similar cost benefits.\n\n We recommend you upgrade to the latest version of Elastic so you don’t miss out on all the new features from faster and more efficient search in[ Elasticsearch 7.16](https://www.elastic.co/blog/three-ways-improved-elasticsearch-scalability/), to [NLP and vector search](https://www.elastic.co/blog/whats-new-elastic-8-0-0?storm=nav-products-new) 8.0 — and even more speed and cost search benefits in 8.1 \n\nSound interesting? Try them out now on [Elastic Cloud](https://cloud.elastic.co/registration?blade=blog\u0026gambit=dts-blog) by upgrading your deployments today and enjoy these features. Or [sign up for a free 14-day trial](https://cloud.elastic.co/registration) and check out our blog for a [step-by-step guide on how to try it out](https://www.elastic.co/blog/getting-started-with-elastic-cloud).\n\n\n [1]: https://www.elastic.co/blog/whats-new-elastic-8-1-0\n [2]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd87cd8d97b628593/626b1039a1a1dd2aa9f6a44d/Internal_O11y_Clusters.PNG\n [3]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt66e8810877307575/625776507e7b344b2534ee8f/2.PNG\n [4]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9bb1d546fb9963cb/625776607e7b344b2534ee93/3.PNG\n [5]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt15514c14c246989f/6257766e2777714c51b305ac/4.PNG","modular_blocks":[],"publish_date":"2022-04-27T22:16:24.000Z","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"Elasticsearch enhancements added in 7.15+, lowers data transfer and storage (DTS) and can lower your Elastic Cloud bills. Learn how our cloud observability team saved $100,000 and upgrade to 8.1 today.","seo_image":null,"seo_title_l10n":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt736c21c9cc3bed67","ACL":{},"created_at":"2023-11-06T20:35:30.489Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-regions","label_l10n":"Cloud regions","tags":[],"title":"Cloud regions","updated_at":"2023-11-06T20:35:30.489Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.290Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt2978b11d0fd056a7","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2022-04-14T01:20:26.427Z","updated_at":"2022-04-14T01:20:26.427Z","content_type":"image/png","file_size":"103668","filename":"unnamed-10.png","title":"unnamed-10.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-04-27T22:26:20.526Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2978b11d0fd056a7/625776da00a8bb4b7796064a/unnamed-10.png"},"title":"Elastic on Elastic: How we saved $100,000/month by keeping our own software up to date","title_l10n":"Elastic on Elastic: How we saved $100,000/month by keeping our own software up to date","updated_at":"2025-03-28T17:12:43.604Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-observability-clusters-upgrade-latest-release-save-money","publish_details":{"time":"2025-03-28T17:12:51.669Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt68c977f2c007373d","_version":25,"locale":"en-us","ACL":{},"abstract_l10n":"A Shell evasion attack is a type of code injection attack in which the attacker injects malicious code into a benign program that has been started by an unsuspecting user. This evasion technique can be used to install malware on the target device.\n","author":["blt7b745b7af930dc8b"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-05-09T14:53:07.762Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5715b76493a78ca5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eCybersecurity strategies within cloud environments are often seen as a complicated landscape with rapidly developing technologies, architectures, and terms. Simultaneously, there are continuously motivated individuals and groups trying to utilize vulnerabilities for illicit uses such as to increase access to the data, install malware, disrupt services, and more.\u003c/p\u003e\u003cp\u003eMore recently, a series of observed threat actors have taken advantage of Shell Evasion tactics to evade detection and target unknowing victims — often to successful outcomes given the lack of visibility most organizations have within their infrastructure.\u003c/p\u003e\u003ch2\u003eShell evasion\u003c/h2\u003e\u003cp\u003eCybercriminals are increasingly using stealthy shells to stay undetected on their victims’ computers. A shell evasion attack technique can be used to install malware on the target device, or circumvent controls within the system by evading the detection of rule-based engines.\u003c/p\u003e\u003cp\u003eThe term \"shell evasion\" covers the different ways that attackers can slip around security controls by using false identities. This includes using social engineering, creating false websites, and hidden passageways outside of any defensive perimeter.\u003c/p\u003e\u003cp\u003eShell evasion techniques are used primarily to avoid detection by anti-malware or intrusion detection systems. One risk is that an attacker can use shell evasion techniques to slip past defenses undetected and gain access to highly sensitive information.\u003c/p\u003e\u003cp\u003eShell evasion attacks are a method used by astute adversaries that are attempting to get around computer systems by disguising themselves as benign executables and behaviors. Research has found that some of these attacks have been using malicious shell scripts to bypass anti-malware software and avoid detection.\u003c/p\u003e\u003cp\u003eIn shell evasion, programs are often developed to execute commands from within the shell. When executed, another process can be launched in the background without the user's knowledge. This can lead to data tampering and other types of hacking that make it unclear who is behind the attack. The vulnerability of shell evasion is often increased by limitations on what commands can be executed in a restricted mode.\u003c/p\u003e\u003ch2\u003eShell evasion attack vector\u003c/h2\u003e\u003cp\u003eThere are two main types of threats that can occur with Shell execution. The first is the execution threat, where an attacker forces the victim's system to execute a malicious command or script. The other type is the insider threat, where an authorized user executes a command without realizing it could be malicious or performs an undesired (not a standard use) of the command, leading to an evasion pattern from security monitoring tools.\u003c/p\u003e\u003cp\u003eThis blog highlights the use cases of spawning interactive shells from various Linux binaries in evasive manners from regular monitoring, leading to an insider threat pattern. An example insider threat scenario can be described as when an employee has access to systems, programs, or data and maliciously uses these privileged assets. This can include things such as altering records, deleting or modifying files and programs, installing software (which may or may not be malicious, or could be unauthorized software) on the company's systems, bypassing security controls via the shell evasion technique.\u003c/p\u003e\u003ch2\u003ePreventing shell evasion\u003c/h2\u003e\u003cp\u003eShell evasion can be easily misunderstood or misinterpreted as a shell vulnerability. In general, a vulnerability can always be prevented when upgraded to the patch version or by removing the use cases of the vulnerable library in the source code. It can also be prevented by temporarily suspending services that use the vulnerable library until a patch has been identified. But an evasion technique will continue to prevail if the use case is being adhered to by the library or system.\u003c/p\u003e\u003cp\u003eThe most common scenario of shell evasion is executing a Linux command outside of its expected behavior. Similar to a cpulimit command, which in normal scenarios is used to restrict CPU usage of a particular process, a Linux command is used for spawning an interactive shell with the right usage of the command. Therefore, preventing these use cases is highly unlikely, even with the best practices of secure engineering.\u003c/p\u003e\u003cp\u003eThe dimension of detecting Shell evasion takes precedence in such scenarios where prevention lies in a more idealistic way of training engineers with best practices of secure engineering.\u003c/p\u003e\u003ch2\u003eDetect shell evasions with Elastic Security 8.2\u003c/h2\u003e\u003cp\u003eIn \u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-security-8-2-0\" target=\"_blank\"\u003eElastic Security 8.2\u003c/a\u003e detection rules, a new category of GTFOBin shell evasion rules has been added to the platform. These rules give cloud users greater visibility in interactive shells being spawned from various Linux libraries. In the current release libraries, such as apt (including apt-get), awk, and its various forms — busybox, MySQL, ssh, and others — Linux libraries have been added to the detection rules to identify any user invoking shell via the shell evasion technique. The detection rules can be customized to fire alerts in a manner suitable for the monitored Linux infrastructure.\u003c/p\u003eOn a newly deployed \u003ca href=\"https://info.elastic.co/elasticsearch-service-trial-gic-security-14d.html\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e environment, navigate to the Elastic Security section and then to the Rules from the left navigation panel. There would be no rules currently in the new environment, like the below screenshot.\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6e114f9acb125b6c"}}},{"image":{"image":{"parent_uid":null,"uid":"bltee41bf882ce4b920","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:55:29.368Z","updated_at":"2022-05-09T16:55:29.368Z","content_type":"image/png","file_size":"91818","filename":"blog-elastic-shell-evasion-1.png","title":"blog-elastic-shell-evasion-1.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.408Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltee41bf882ce4b920/62794781b5ad5f2863c5cabb/blog-elastic-shell-evasion-1.png"},"_metadata":{"uid":"cs5d92eb75117f10bf"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs486504f52f37331c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBy clicking on the “Load Elastic prebuilt detection rules”, all Elastic configured rules available in this version would be now available for enabling.\u003c/p\u003e"}],"_metadata":{"uid":"csd55c32b279399b8a"}}},{"image":{"image":{"parent_uid":null,"uid":"blt17e8fc46cf543c39","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:55:48.475Z","updated_at":"2022-05-09T16:55:48.475Z","content_type":"image/png","file_size":"218360","filename":"blog-elastic-shell-evasion-2.png","title":"blog-elastic-shell-evasion-2.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.414Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17e8fc46cf543c39/627947947198441d81b3d8ec/blog-elastic-shell-evasion-2.png"},"_metadata":{"uid":"cs2670f895ae812a1f"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs28b56770399bc837"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIf the Elastic Cloud is a newly deployed environment, we can proceed to add endpoint security to this environment.\u003c/p\u003e"}],"_metadata":{"uid":"cs8c5db19528fe8185"}}},{"image":{"image":{"parent_uid":null,"uid":"bltb085ba008fa8253b","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:56:35.369Z","updated_at":"2022-05-09T16:56:35.369Z","content_type":"image/png","file_size":"114340","filename":"blog-elastic-shell-evasion-3.png","title":"blog-elastic-shell-evasion-3.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.418Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb085ba008fa8253b/627947c37198441d81b3d8f2/blog-elastic-shell-evasion-3.png"},"_metadata":{"uid":"cs5b4a4588f1c97444"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs01e547b9b0685764"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce the endpoint configuration is completed, we can proceed to add hosts.\u003c/p\u003e"}],"_metadata":{"uid":"cs0af0125fa15c4ae9"}}},{"image":{"image":{"parent_uid":null,"uid":"blt23516c2a417078ab","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:56:53.818Z","updated_at":"2022-05-09T16:56:53.818Z","content_type":"image/png","file_size":"110595","filename":"blog-elastic-shell-evasion-4.png","title":"blog-elastic-shell-evasion-4.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.427Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt23516c2a417078ab/627947d57198441d81b3d8f6/blog-elastic-shell-evasion-4.png"},"_metadata":{"uid":"csd81d65c08fd36e2c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs26358ef30f93f522"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eEnrolling agent is very intuitive and the steps for various OS installations are also provided.\u003c/p\u003e"}],"_metadata":{"uid":"cs81776b5c1101e25f"}}},{"image":{"image":{"parent_uid":null,"uid":"blt1203d8e66e6566d1","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:57:20.161Z","updated_at":"2022-05-09T16:57:20.161Z","content_type":"image/png","file_size":"171284","filename":"blog-elastic-shell-evasion-5.png","title":"blog-elastic-shell-evasion-5.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.431Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1203d8e66e6566d1/627947f05f7b601eaaec04de/blog-elastic-shell-evasion-5.png"},"_metadata":{"uid":"csbcefb7151b611eae"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"parent_uid":null,"uid":"blt7e5e5b14b2169ed4","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T18:55:43.836Z","updated_at":"2022-05-09T18:55:43.836Z","content_type":"image/png","file_size":"86876","filename":"blog-elastic-shell-evasion-6.png","title":"blog-elastic-shell-evasion-6.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.451Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7e5e5b14b2169ed4/627963af7198441d81b3d948/blog-elastic-shell-evasion-6.png"},"_metadata":{"uid":"cs17aceca49678f1c5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf882b8925d50f69c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe have now successfully added a host for the environment, enabling shell evasion detection rules.\u003c/p\u003e\u003cp\u003eNote: If there is an existing Elastic Cloud environment, please upgrade to the latest versions and then update the ruleset to the latest version, after these steps we can enable the shell evasion detection rules.\u003c/p\u003e\u003cp\u003eAn easy way to look for all shell evasion rules at once is to search via tags, and these rules are bundled under the GTFOBins tag.\u003c/p\u003e"}],"_metadata":{"uid":"cs6e28c613ad387bb2"}}},{"image":{"image":{"parent_uid":null,"uid":"blt6d4e9eea63b2e72e","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:57:53.039Z","updated_at":"2022-05-09T16:57:53.039Z","content_type":"image/png","file_size":"233357","filename":"blog-elastic-shell-evasion-7.png","title":"blog-elastic-shell-evasion-7.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.457Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6d4e9eea63b2e72e/62794811b5ad5f2863c5cabf/blog-elastic-shell-evasion-7.png"},"_metadata":{"uid":"cs29b64792f2d3d341"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs200bfc57c59fcee5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe can bulk enable all the rules at once, or a user can evaluate what suits his infrastructure best and enable only those select rules.\u003c/p\u003e"}],"_metadata":{"uid":"cs0a7217c8bfe033f9"}}},{"image":{"image":{"parent_uid":null,"uid":"blt028b3698cf6548e1","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:58:11.271Z","updated_at":"2022-05-09T16:58:11.271Z","content_type":"image/png","file_size":"135557","filename":"blog-elastic-shell-evasion-8.png","title":"blog-elastic-shell-evasion-8.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.462Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt028b3698cf6548e1/62794823a1a1dd2aa9f6fb72/blog-elastic-shell-evasion-8.png"},"_metadata":{"uid":"csbc95ef5a9ddc979b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse1ddde24d133e937"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAnalyze a sample rule and check the alerting features.\u003c/p\u003e\u003cp\u003eScenario 1: When a shell has been evoked using the env command, Elastic Security identifies such user activities and alerts the same.\u003c/p\u003e"}],"_metadata":{"uid":"cse7bda1466fcaf83a"}}},{"image":{"image":{"parent_uid":null,"uid":"bltbc82d5a86e811c1f","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:58:30.669Z","updated_at":"2022-05-09T16:58:30.669Z","content_type":"image/png","file_size":"180066","filename":"blog-elastic-shell-evasion-9.png","title":"blog-elastic-shell-evasion-9.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.467Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbc82d5a86e811c1f/627948360d4d8e1d7f112773/blog-elastic-shell-evasion-9.png"},"_metadata":{"uid":"csb892dd9991683676"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"parent_uid":null,"uid":"bltdc3d08e336d1a03f","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:58:45.281Z","updated_at":"2022-05-09T16:58:45.281Z","content_type":"image/png","file_size":"72577","filename":"blog-elastic-shell-evasion-10.png","title":"blog-elastic-shell-evasion-10.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.471Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc3d08e336d1a03f/627948450cffdf1eb136ce77/blog-elastic-shell-evasion-10.png"},"_metadata":{"uid":"cs7f41e270a3703ee1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"parent_uid":null,"uid":"bltd0d768595bc4715b","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:58:59.492Z","updated_at":"2022-05-09T16:58:59.492Z","content_type":"image/png","file_size":"105156","filename":"blog-elastic-shell-evasion-11.png","title":"blog-elastic-shell-evasion-11.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.477Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd0d768595bc4715b/62794853a1a1dd2aa9f6fb76/blog-elastic-shell-evasion-11.png"},"_metadata":{"uid":"cs1de1845b207b0a44"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd9741afe4ad2d741"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe session view of the of the command execution can be visualized with details.\u003c/p\u003e"}],"_metadata":{"uid":"cs2a57ec135d1d707a"}}},{"image":{"image":{"parent_uid":null,"uid":"bltad52a2ab1da9bc56","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:59:24.905Z","updated_at":"2022-05-09T16:59:24.905Z","content_type":"image/png","file_size":"121232","filename":"blog-elastic-shell-evasion-12.png","title":"blog-elastic-shell-evasion-12.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.481Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltad52a2ab1da9bc56/6279486c8e09542a15b81653/blog-elastic-shell-evasion-12.png"},"_metadata":{"uid":"cs4ebaf09f826a84fa"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs97624a46e93a4b6d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eScenario 2: When a shell has been evoked using the apt command, Elastic Security identifies such user activities and alerts the same.\u003c/p\u003e"}],"_metadata":{"uid":"cs8c7e09b8a87bfbde"}}},{"image":{"image":{"parent_uid":null,"uid":"blt090ac282e0715212","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T16:59:49.288Z","updated_at":"2022-05-09T16:59:49.288Z","content_type":"image/png","file_size":"200639","filename":"blog-elastic-shell-evasion-13.png","title":"blog-elastic-shell-evasion-13.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.485Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt090ac282e0715212/62794885a1a1dd2aa9f6fb7a/blog-elastic-shell-evasion-13.png"},"_metadata":{"uid":"csc656cabb8eba3196"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"parent_uid":null,"uid":"blt18aea1619c375334","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:00:20.643Z","updated_at":"2022-05-09T17:00:20.643Z","content_type":"image/png","file_size":"74275","filename":"blog-elastic-shell-evasion-14.png","title":"blog-elastic-shell-evasion-14.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.488Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt18aea1619c375334/627948a44886af2aa2be4285/blog-elastic-shell-evasion-14.png"},"_metadata":{"uid":"cs12a45aa9df214e27"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"parent_uid":null,"uid":"bltba71f5461b25f5e1","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:00:36.486Z","updated_at":"2022-05-09T17:00:36.486Z","content_type":"image/png","file_size":"117853","filename":"blog-elastic-shell-evasion-15.png","title":"blog-elastic-shell-evasion-15.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.492Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltba71f5461b25f5e1/627948b45f7b601eaaec04e4/blog-elastic-shell-evasion-15.png"},"_metadata":{"uid":"cs4754385ba4841c08"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0ce03336d3348ca0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe can investigate the alert in the timeline as well, for additional information. \u003c/p\u003e"}],"_metadata":{"uid":"cs0eaf5e66d28c45c7"}}},{"image":{"image":{"parent_uid":null,"uid":"blta932687271fbc266","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:00:56.503Z","updated_at":"2022-05-09T17:00:56.503Z","content_type":"image/png","file_size":"222116","filename":"blog-elastic-shell-evasion-16.png","title":"blog-elastic-shell-evasion-16.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.496Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta932687271fbc266/627948c84d9f892971293ccf/blog-elastic-shell-evasion-16.png"},"_metadata":{"uid":"cs2e0e6a8b01e40a51"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8fe4cf53d41047d1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe event can be further analyzed to identify if the user is executing any malicious or unauthorized code in the spawned interactive shell via the evasion technique\u003c/p\u003e"}],"_metadata":{"uid":"csb05bf01ec459531b"}}},{"image":{"image":{"parent_uid":null,"uid":"blt235da76688082e38","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:01:10.851Z","updated_at":"2022-05-09T17:01:10.851Z","content_type":"image/png","file_size":"150715","filename":"blog-elastic-shell-evasion-17.png","title":"blog-elastic-shell-evasion-17.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.500Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt235da76688082e38/627948d6deee7329767eac4f/blog-elastic-shell-evasion-17.png"},"_metadata":{"uid":"cscf05ca4e86c67d52"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb648b848ff8b67a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe can see the user has executed the date and whoami commands in the shell.\u003c/p\u003e\u003cp\u003eSimilar analysis can be provided by the sessions view.\u003c/p\u003e"}],"_metadata":{"uid":"cs8ad1359f276345d5"}}},{"image":{"image":{"parent_uid":null,"uid":"blt42156559eb06c4d2","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:01:28.338Z","updated_at":"2022-05-09T17:01:28.338Z","content_type":"image/png","file_size":"294876","filename":"blog-elastic-shell-evasion-18.png","title":"blog-elastic-shell-evasion-18.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.505Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt42156559eb06c4d2/627948e84886af2aa2be4289/blog-elastic-shell-evasion-18.png"},"_metadata":{"uid":"cs2b32a03377545fef"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse69e2609a7e473b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eDepending on the outcome of the analysis, we can decide the closure actions for this alert using the ‘more actions’ feature in the post analysis phase.\u003c/p\u003e"}],"_metadata":{"uid":"cs98da7a9979cac614"}}},{"image":{"image":{"parent_uid":null,"uid":"bltc4344bac4ca047d8","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:01:44.412Z","updated_at":"2022-05-09T17:01:44.412Z","content_type":"image/png","file_size":"66793","filename":"blog-elastic-shell-evasion-19.png","title":"blog-elastic-shell-evasion-19.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.508Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc4344bac4ca047d8/627948f80cffdf1eb136ce7b/blog-elastic-shell-evasion-19.png"},"_metadata":{"uid":"csd145b1198b530f7c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5be260d64d93e595"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eCumulative open /acknowledged or closed alerts can also be found in the ‘Alerts” section of the deployment.\u003c/p\u003e"}],"_metadata":{"uid":"cs45a74925db6473d5"}}},{"image":{"image":{"parent_uid":null,"uid":"bltb4fc8490b9d2e4c5","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-05-09T17:02:01.517Z","updated_at":"2022-05-09T17:02:01.517Z","content_type":"image/png","file_size":"106094","filename":"blog-elastic-shell-evasion-20.png","title":"blog-elastic-shell-evasion-20.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-09T23:48:39.513Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb4fc8490b9d2e4c5/6279490923c6cf2a1c3b2bc7/blog-elastic-shell-evasion-20.png"},"_metadata":{"uid":"cs09e7c6363bf80e3c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfdc95c3ecce54e8c"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eMITRE ATT\u0026CK\u003csup\u003e®\u003c/sup\u003e of Shell Evasion\u003c/h2\u003e\u003cp\u003eThe Shell evasion technique primarily defines the execution tactic of the adversary. The tactics and techniques details are referenced below.\u003c/p\u003e"}],"_metadata":{"uid":"cs65b9d074f59d47c8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9bc432705dba6c79"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003eTactics\u003c/h3\u003e\u003ctable class=\"table-responsive table-left-text\"\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/tactics/TA0002\" target=\"_self\"\u003eTA0002\u003c/a\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/tactics/TA0002\" target=\"_self\"\u003eExecution\u003c/a\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eThe adversary is trying to run malicious code.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003ch3\u003eTechniques / Sub Techniques\u003c/h3\u003e\u003cbr/\u003e\u003ctable class=\"table-responsive table-left-text\"\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1059\" target=\"_self\"\u003eT1059\u003c/a\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1059\" target=\"_self\"\u003eCommand and Scripting Interpreter\u003c/a\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAdversaries may abuse command and script interpreters to execute commands, scripts, or binaries. These interfaces and languages provide ways of interacting with computer systems and are a common feature across many different platforms. Most systems come with some built-in command-line interface and scripting capabilities, for example, macOS and Linux distributions include some flavor of \u003ca href=\"https://attack.mitre.org/techniques/T1059/004\" target=\"_self\"\u003eUnix Shell\u003c/a\u003e while Windows installations include the \u003ca href=\"https://attack.mitre.org/techniques/T1059/003\" target=\"_self\"\u003eWindows Command Shell\u003c/a\u003e and \u003ca href=\"https://attack.mitre.org/techniques/T1059/001\" target=\"_self\"\u003ePowerShell\u003c/a\u003e.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1059/004\" target=\"_self\"\u003e.004\u003c/a\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1059/004\" target=\"_self\"\u003eUnix Shell\u003c/a\u003e\u003c/p\u003e\u003c/td\u003e\u003ctd\u003e\u003cp\u003eAdversaries may abuse Unix shell commands and scripts for execution. Unix shells are the primary command prompt on Linux and macOS systems, though many variations of the Unix shell exist (e.g. sh, bash, zsh, etc.) depending on the specific OS or distribution. Unix shells can control every aspect of a system, with certain commands requiring elevated privileges.\u003c/p\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs48085a6ac25f823b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csba22a77bf6752b19"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eClosing summary\u003c/h2\u003e\u003cp\u003eCloud infrastructures are often proven to be complex to decipher not because of enormous resources (large nodes), but due to a lack of visibility on what happens in/between those resources. Shell evasion(s) can go unmonitored due to the lack of visibility in the infrastructure without proper monitoring tools to detect and capture these threats.\u003c/p\u003e\u003cp\u003eElastic Security equips teams with greater visibility to prevent, detect, and respond to all such events at cloud speed and scale — securing business operations with a unified, open platform.\u003c/p\u003e\u003cp\u003eYou can always get started with a \u003ca href=\"https://cloud.elastic.co/registration\" target=\"_self\"\u003efree 14-day trial of Elastic Cloud\u003c/a\u003e. Or \u003ca href=\"https://www.elastic.co/downloads/\" target=\"_self\"\u003edownload\u003c/a\u003e the self-managed version of the Elastic Stack for free.\u003c/p\u003e\u003cp\u003eReferences:\u003cbr/\u003e\u003cbr/\u003e[1] https://gtfobins.github.io/\u003c/p\u003e"}],"_metadata":{"uid":"cs832ee4b2031607bd"}}}],"publish_date":"2022-05-09","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Shell Evasion: An Insider Threat","seo_description_l10n":"Cloud users can gain unprecedented visibility and context into their data, along with cluster compliance, cloud workloads, and cloud architecture — all with Elastic Security. Through the unified solution, they can detect threats and respond quickly to secure their data, applications, users, and, ultimately, their business. The blog highlights the use cases of spawning interactive shells from various Linux binaries in evasive manners from regular monitoring, leading to an insider threat pattern.\n\n","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"bltf43c99d661aee915","ACL":{},"content_type":"image/png","created_at":"2021-01-12T16:54:39.941Z","created_by":"bltf6ab93733e4e3a73","file_size":"53874","filename":"blog-thumb-security-radar.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-security-radar.png","updated_at":"2022-02-11T21:04:12.027Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:03.892Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf43c99d661aee915/5ffdd44f1ae93152b725f4f4/blog-thumb-security-radar.png"},"title":"Shell Evasion: An Insider Threat","title_l10n":"Shell Evasion: An Insider Threat","updated_at":"2025-03-28T17:12:24.987Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/shell-evasion-an-insider-threat","publish_details":{"time":"2025-03-28T17:12:29.935Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt53d35879e7d57d2d","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Have you ever looked at your indices and would like more detail on what is driving storage consumption in your Elastic deployment?","author":["blt28ab9f00f648323c"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-03-15T22:56:47.416Z","created_by":"bltac225ac457fe0293","markdown_l10n":"Have you ever looked at your indices and wanted more detail on what is driving storage consumption in your Elastic deployment? Perhaps you have ingested custom data using default settings and would like to know where your data modeling efforts could make the largest impact? In this blog post we will look at how to use Elastic’s recently introduced [disk usage API](https://www.elastic.co/guide/en/elasticsearch/reference/current/indices-disk-usage.html) to answer such questions. \n\nHere at Elastic, when we work with our customers, one of the most common areas of improvement is index mapping configuration. A lack of mappings, or using the wrong types, can increase storage usage in your Elastic deployment. This post will help you understand what fields are most influential in driving your storage footprint and how you can optimize consumption through best-practice configuration. \n\n\n## Getting started\n\nIf you are not already using Elastic, create a deployment using our hosted Elasticsearch Service on [Elastic Cloud](https://www.elastic.co/cloud/elasticsearch-service/signup?baymax=docs-body\u0026elektra=docs). The deployment includes an Elasticsearch cluster for storing and searching your data, and a Kibana instance for visualizing and managing your data. For more information, see [spin up the Elastic Stack](https://www.elastic.co/guide/en/observability/current/spin-up-stack.html). I recommend using a development or staging environment for this exercise. \n\nYou will also need some data in an Elasticsearch index to analyze. If you have created a brand new cluster, you can add some sample data [using Kibana](https://www.elastic.co/guide/en/kibana/current/connect-to-elasticsearch.html). In my example, I have used some log data ingested using [Filebeat](https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-installation-configuration.html). \n\nIf you are using Elastic’s Beats or Elastic Agent to index data, chances are it will already be modeled according to Elastic’s best practices. This is of course fantastic, except it does make this exercise a bit less interesting. Fortunately we can easily discard our data model by copying it to an index without a mapping configuration. I picked one of my indices and executed the following reindex operation using Kibana dev tools:\n\n\n```\nPOST _reindex/\n{\n \"source\": {\n \"index\": \"filebeat-7.16.2-2022.01.06-000001\"\n }, \n \"dest\": {\n \"index\": \"nomapping-filebeat\"\n }\n}\n```\n\n\nNote that I have chosen a target index name that starts with a prefix that does not match any of Elastic’s standard index patterns. This ensures mappings are not automatically applied from one of my index templates. \n\nBy having two copies of the index, one with appropriate mappings and one without, we will be able to do a side by side comparison later in the blog post. \n\nThe final prerequisite is [jq](https://stedolan.github.io/jq/download/), which is a great tool for manipulating json. We will use jq to transform the API response into a list of documents, which we can easily ingest into Elasticsearch using Kibana. This will make the analysis of the API response easier using the Discover interface through Kibana.\n\n\n## Using the disk usage API\n\nCalling the [disk usage API](https://www.elastic.co/guide/en/elasticsearch/reference/8.0/indices-disk-usage.html) is simple, just go to Kibana dev tools and issue a request similar to:\n\n\n```\nPOST nomapping-filebeat/_disk_usage?run_expensive_tasks=true\n```\n\n\nNote the run_expensive_tasks parameter is required ,and by providing it I acknowledge that I am putting additional load on the cluster. This is also the reason for my earlier recommendation to do the exercise in a non-production cluster. \n\nHere is the top of my response:\n\n\n```\n{\n \"_shards\" : {\n \"total\" : 1,\n \"successful\" : 1,\n \"failed\" : 0\n },\n \"nomapping-filebeat\" : {\n \"store_size\" : \"23.3mb\",\n \"store_size_in_bytes\" : 24498333,\n \"all_fields\" : {\n \"total\" : \"22.7mb\",\n \"total_in_bytes\" : 23820161,\n \"inverted_index\" : {\n \"total\" : \"9.9mb\",\n \"total_in_bytes\" : 10413531\n },\n \"stored_fields\" : \"8mb\",\n \"stored_fields_in_bytes\" : 8404459,\n \"doc_values\" : \"3.1mb\",\n \"doc_values_in_bytes\" : 3284983,\n \"points\" : \"1.1mb\",\n \"points_in_bytes\" : 1237784,\n \"norms\" : \"468.1kb\",\n \"norms_in_bytes\" : 479404,\n \"term_vectors\" : \"0b\",\n \"term_vectors_in_bytes\" : 0\n }\n```\n\n\nThe response provides a breakdown of the storage usage of the index as a whole. We can see that the inverted index is the largest factor, followed by stored fields and doc values. \n\nLooking further down the response, I get a breakdown of each field, including the host.name field. \n\n\n```\n\"fields\" : {\n…\n\"host.name\" : {\n \"total\" : \"23.2kb\",\n \"total_in_bytes\" : 23842,\n \"inverted_index\" : {\n \"total\" : \"23.2kb\",\n \"total_in_bytes\" : 23842\n },\n…\n```\n\n\nWe could easily be satisfied with the API results. By using the CTRL-F function in the response tab and searching for “mb”, as in megabyte, we would quickly identify a few large fields in our index. Let’s take it one step further though and look at how we can quickly reformat the response and analyze it using Kibana.\n\n\n## Analyzing field disk usage in Kibana\n\nCopy paste the API result into your favorite text editor and save it as a file, in my case disk-usage-filebeat.json. Then run the command below, replacing _nomapping-filebeat_ with your index name and _disk-usage-filebeat.json_ with your recently saved file:\n\n\n```\njq -c '.[\"nomapping-filebeat\"].fields | to_entries | map({field: .key} + .value) | .[]' disk-usage-filebeat.json \u003e disk-usage-ld.json\n```\n\n\nThe command transforms the json into a list of objects, each including a field name and related usage data, and outputs newline delimited json. See [the jq manual ](https://stedolan.github.io/jq/manual/)for more information. \n\nWe can now upload the data using the [data visualizer](https://www.elastic.co/guide/en/machine-learning/current/ml-gs-visualizer.html), found under **Machine learning **in Kibana. Once you have navigated to the visualizer, click import file and upload your disk-usage-ld.json file. The resulting page should include fields similar to the screenshot below, matching the field analytics in the API response. \n\n![enter image description here][1]\n\nScroll down, click import and name your index where the disk usage data will be stored. Make sure to check the “create index pattern” tick box. \n\n![enter image description here][2]\n\nAs you can see I named my index disk-usage. On the next screen click** Index Pattern Management**. You can also navigate using the main menu: **Stack Management -\u003e Index Patterns**. \n\nWe will use the [formatting feature ](https://www.elastic.co/guide/en/kibana/current/managing-index-patterns.html#managing-fields)in Kibana to improve the readability of our byte fields. For each of the following fields click edit and select bytes as format:\n\n\n\n* doc_values_in_bytes\n* inverted_index.total_in_bytes\n* stored_fields_in_bytes`\n* total_in_bytes\n\n**Tip**: enter **bytes** in the search field to quickly find the fields, as in the following screenshot. \n\n\n![enter image description here][3]\n\nNow we are ready to visualize our field data. Navigate to **Discover **and select the **disk-usage **index pattern. Add the following columns: \n\n\n\n* field\n* stored_fields_in_bytes\n* inverted_index.total_in_bytes\n* doc_values_in_bytes\n* total_in_bytes\n\nSort on **total_in_bytes **in descending order.\n\n![enter image description here][4]\n\nAs you can see my largest field is **_source. **This is a built in field that [stores the original document](https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-source-field.html), and one we almost always want to keep. The next two fields are **host.mac **and **host.ip. **Looking further down we can also see** **the same fields with a **.keyword **suffix. As per Elasticsearch's [dynamic mapping defaults](https://www.elastic.co/guide/en/elasticsearch/reference/current/dynamic-field-mapping.html#dynamic-field-mapping), these fields have been set to text with a keyword multi-field. I also notice that the [text fields](https://www.elastic.co/guide/en/elasticsearch/reference/current/text.html)’ storage is taken up by the inverted index, which is used for search, while the [keyword fields](https://www.elastic.co/guide/en/elasticsearch/reference/current/keyword.html)’ are dominated by doc_values, which are used for aggregations and sorting. \n\nAdding the text and keyword sizes together, the total sizes are: \n\n\n\n* host.mac + host.mac.keyword = 5.3 MB\n* host.ip + host.ip.keyword = 3 MB\n\n\n## Comparing to Best Practice\n\nLets navigate to **Dev tools and take a **look at the original filebeat index. This index has the Elastic Common Schema mapping already applied out of the box.\n\nI retrieve the disk usage information from my original index using:\n\n\n```\nPOST filebeat-7.16.2-2022.01.06-000001/_disk_usage?run_expensive_tasks=true\n```\n\n\nFrom the response I read the following for the **host.ip **and **host.mac** fields:\n\n\n```\n\"host.ip\" : {\n \"total\" : \"1.3mb\"\n…\n\"host.mac\" : {\n \"total\" : \"492.1kb\",\n…\n```\n\n\nAs we can see, the storage usage is lower by a factor of 2-5. To take a look at the mapping, we can retrieve it using:\n\n\n```\nGET filebeat-7.16.2-2022.01.06-000001/_mapping/field/host.ip,host.mac\n```\n\n\nI can see that host.ip is mapped as ip and host.mac is mapped as keyword. In most cases, the type of data stored in these fields will be used for exact filtering, aggregations and sorting which means that having them mapped as a text field does not provide further value for analysis and takes up extra storage space in the cluster. \n\n\n## Conclusion and Next Steps\n\nIn this blog post we have seen how we can use the disk usage API to understand what fields are most expensive in terms of storage utilization. We formatted the API response using jq and imported it back into Elastic using the data visualizer so that we could analyze the data in Discover. We have also seen how having an appropriate mapping can dramatically reduce the storage footprint. So how do we optimize storage usage in our indexes?\n\n\n### Use Elastic Integrations\n\nBy using Elastic [integrations](https://www.elastic.co/integrations/data-integrations), either through Beats or Elastic Agent, field mappings will be automatically created for you as data is ingested. Please note that if you don’t send data to Elasticsearch directly, for example if you send Filebeat data via Logstash, you might need to load your index templates [manually](https://www.elastic.co/integrations/data-integrations).\n\n\n### Configure Mappings\n\nIf you are using custom data, you often need to configure your mappings manually. To make sure your mapping is applied, define it within an [index template](https://www.elastic.co/guide/en/elasticsearch/reference/current/index-templates.html) with the appropriate index patterns. \n\nMapping individual fields quickly becomes tedious. For most machine generated data we usually want to map most strings to the keyword type, so including a [dynamic template](https://www.elastic.co/guide/en/elasticsearch/reference/current/dynamic-templates.html) as the example below will save a lot of time. Don’t forget to add specific mappings for ips and for text meant for free text search, such as the standard field “message”. \n\n\n```\n\"mappings\": {\n \"dynamic_templates\": [\n {\n \"strings_as_keyword\" : {\n \"match_mapping_type\" : \"string\",\n \"mapping\" : {\n \"ignore_above\" : 1024,\n \"type\" : \"keyword\"\n }\n }\n }\n ]\n }\n```\n\n\nWhen naming and assigning types to your fields we recommend consulting the [Elastic Common Schema](https://www.elastic.co/guide/en/ecs/current/index.html). It will help you build a consistent data model and allow you to view your custom data in Kibana’s applications. \n\n\n### Implement Storage Tiers\n\nA slightly tangential, but important, tool to optimize your storage footprint is [data tiers](https://www.elastic.co/guide/en/elasticsearch/reference/current/data-tiers.html). By using data tiers you can move data to cheaper hardware as it ages. Our frozen tier even lets you [store data in blob storage](https://www.elastic.co/blog/introducing-elasticsearch-frozen-tier-searchbox-on-s3), which dramatically reduces costs and is designed for data that is rarely accessed or when slower query responses are acceptable. The easiest way to manage data tiers is by using Elastic Cloud, have a look at our [best practices for managing data](https://www.elastic.co/guide/en/cloud/current/ec-cloud-ingest-data.html) to get you started. \n\n\n [1]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta5acf9c533b23f1a/62311a5c785e150be52d509f/2.png\n [2]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb3b2d6a8280b509/62311a681bd2ea5415f0d194/3.png\n [3]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9bc173bc501ae5dc/62311a72b17dc223f2f2b8d6/4.png\n [4]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9309f9090a403eda/62311a95785e150be52d50a3/5.png","modular_blocks":[],"publish_date":"2022-03-15T22:45:38.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How to analyze and optimize the storage footprint of your Elastic deployment","seo_description_l10n":"Have you ever looked at your indices and would like more detail on what is driving storage consumption in your Elastic deployment? Perhaps you have ingested custom data using default settings and would like to know where your data modeling efforts could make the largest impact? In this blog post we will look at how to use the recently introduced disk usage API to answer such questions.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt7d4ad2c13a8a0253","ACL":{},"content_type":"image/png","created_at":"2021-02-24T15:35:54.863Z","created_by":"bltf6ab93733e4e3a73","file_size":"109478","filename":"blog-thumb-cloud-white.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-white.png","updated_at":"2022-02-11T21:03:14.508Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:40.515Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7d4ad2c13a8a0253/6036725ace4a0d12c3ec1c42/blog-thumb-cloud-white.png"},"title":"How to analyze and optimize the storage footprint of your Elastic deployment","title_l10n":"How to analyze and optimize the storage footprint of your Elastic deployment","updated_at":"2025-03-28T17:12:02.828Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/how-to-analyze-and-optimize-the-storage-footprint-of-your-elastic-deployment-disk-usage-api","publish_details":{"time":"2025-03-28T17:12:08.266Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1ac5a327c0a25af9","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how-to spin up ECK using terraform","author":["blt37871c8eba8cdb1e"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-05-20T13:46:40.200Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csadb14790fc35d5d2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOn this page, you will find a how-to spin up ECK using Terraform. The main idea is to have a Kubernetes cluster and ECK installed by running only 3 commands.\u003c/p\u003e\u003ch2\u003eDemo\u003c/h2\u003e\u003cp\u003eTo see the demo, please access \u003ca href=\"https://github.com/framsouza/eck-terraform\" target=\"_self\"\u003ehttps://github.com/framsouza/eck-terraform\u003c/a\u003e\u003c/p\u003e\u003ch2\u003eFeatures\u003c/h2\u003e\u003cp\u003eEvery feature will be deployed via Terraform:\u003c/p\u003e\u003cul\u003e\u003cli\u003eInstall GKE (Google Kubernetes Engine) cluster\u003c/li\u003e\u003cli\u003eIt will contain 1 node pool with 3 nodes (One in each zone) running on region europe-west1\u003c/li\u003e\u003cli\u003eIt contains a helm provider that will be responsible to install the ECK operator\u003c/li\u003e\u003cli\u003eElasticsearch cluster with 3 nodes\u003c/li\u003e\u003cli\u003eOne Kibana instance\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eRequirements\u003c/h2\u003e\u003cp\u003eBefore starting you should have the following commands installed:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.terraform.io/downloads\" target=\"_self\"\u003eterraform\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://cloud.google.com/sdk/docs/install\" target=\"_self\"\u003egcloud\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eLet's play\u003c/h2\u003e\u003cp\u003eAs you probably know, Terraform is an infrastructure as code tool, which means we can describe our infrastructure desire into a file and apply it via Terraform. Here, we are going to spin up a GKE cluster with 3 nodes running on europe-west1 region. The machines we are going to use is e2-standard-4 which will give us 4vCPU nad 16GB of memory in each node.\u003c/p\u003e\u003cp\u003eFirst, you have to authenticate into Google Cloud console, to so run the following command,\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003egcloud auth application-default login\u003c/span\u003e\u003c/p\u003e\u003cp\u003eOnce you are logged it, you should export 2 variables, the Kubernetes config path and the Google project you are going to use\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003eexport KUBE_CONFIG_PATH=~/.kube/config \u0026\u0026 export GOOGLE_PROJECT=\u0026lt;YOUR-PROJECT-NAME\u0026gt;\u003c/span\u003e\u003c/p\u003e\u003cp\u003eNow, you can run\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003eterraform init\u003c/span\u003e \u003c/p\u003e\u003cp\u003eIt will load the providers and configuration. Right after that, you should run\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003eterraform plan\u003c/span\u003e\u003c/p\u003e\u003cp\u003eIt will show you everything that will be created by Terraform, take a moment to check this output. Once you are ready, you just need to run:\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003eterraform apply -parallelism=1\u003c/span\u003e\u003c/p\u003e\u003cp\u003eIt will apply your changes in sequence. Once everything was applied, you will get an output similar to this,\u003c/p\u003e"}],"_metadata":{"uid":"cs92006cc01f4bff3c"}}},{"code":{"code":"Apply complete! Resources: 7 added, 0 changed, 0 destroyed.\n\nOutputs:\n\ngke_name = \"TO CONNECT TO KUBERNETES: gcloud container clusters get-credentials \u003cKUBERNETES-NAME\u003e --region europe-west1 --project \u003cYOUR-PROJECT-NAME\u003e\"\nkibana_endpoint = \"TO CONNECT TO KIBANA: kubectl port-forward svc/\u003cKIBANA-ENDPOINT\u003e 5601:5601\"\nkubernetes_name = \"fram-gke-eck\"","_metadata":{"uid":"csd1361a886198fde5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5e2d63dc35a6124d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce you \u003cspan data-type='inlineCode'\u003eport-foward\u003c/span\u003e your kibana service, you can easily access it on your browser via localhost.\u003c/p\u003e\u003ch2\u003eWrapping up\u003c/h2\u003e\u003cp\u003eNow, to clean up everything you just need to run\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003eterraform destroy\u003c/span\u003e\u003c/p\u003e\u003cp\u003eHappy terraform!\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch4\u003eKeep learning about ECK:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/eck-in-production-environment\" target=\"_self\"\u003eECK in production environment\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/using-eck-with-helm\" target=\"_self\"\u003eECK with helm\u003c/a\u003e\u003cbr/\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs9a5d6ee53509b960"}}}],"publish_date":"2022-05-24","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"Learn how-to spin up ECK using terraform","seo_image":null,"seo_title_l10n":"Installing ECK with Terraform on GCP"},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt23bfd15a9c05b228","ACL":{},"_version":1,"content_type":"image/png","created_at":"2020-01-28T19:51:35.869Z","created_by":"bltf6ab93733e4e3a73","file_size":"34449","filename":"eck-blog-thumb.png","is_dir":false,"parent_uid":null,"tags":[],"title":"eck-blog-thumb.png","updated_at":"2020-01-28T19:51:35.869Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-30T16:11:50.504Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt23bfd15a9c05b228/5e3090c7507d2f74fb78c86e/eck-blog-thumb.png"},"title":"Installing ECK with Terraform on GCP","title_l10n":"Installing ECK with Terraform on GCP","updated_at":"2025-03-28T17:11:39.220Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/installing-eck-with-terraform-on-gcp","publish_details":{"time":"2025-03-28T17:11:44.043Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt39c497413e6e41cc","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"Using ECK with helm-charts","author":["blt37871c8eba8cdb1e"],"category":["bltb79594af7c5b4199"],"created_at":"2022-05-20T13:46:41.067Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs380947f69a13e94f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIf you want a solution where you can run only 4 commands and have your \u003ca href=\"https://www.elastic.co/observability/kubernetes-monitoring\" target=\"_self\"\u003eKubernetes observability\u003c/a\u003e (logs \u0026amp; metrics, dashboards …) automatically set up, this guide is for you. Here we will use helm to spin up Elastic Stack on ECK (Elastic on Kubernetes), with automatically Kubernetes observability. We are going to run only 4 commands and we will have Elasticsearch, Kibana, Fleet \u0026amp; Elastic Agents (with System \u0026amp; Metrics of Kubernetes enabled). Once you follow this guide, at the end, you can access Kibana and quickly check your Kubernetes healthy, as the image below:\u003c/p\u003e"}],"_metadata":{"uid":"cs75f46c971e4935dd"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltb1a6d3e2b38b49cd","ACL":{},"content_type":"image/png","created_at":"2022-05-23T22:06:53.808Z","created_by":"blt1e57c6588ae1816e","file_size":"264897","filename":"blog-elastic-elk.png","parent_uid":null,"tags":[],"title":"blog-elastic-elk.png","updated_at":"2022-05-23T22:06:53.808Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T13:00:00.084Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb1a6d3e2b38b49cd/628c057db4fa6b61ed70c686/blog-elastic-elk.png"},"_metadata":{"uid":"cs77c8ad55adec6eab"},"caption_l10n":"","alt_text_l10n":"Once you follow this guide, at the end you can access Kibana and quickly check your Kubernetes healthy","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1b8ba9bf5d488784"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis page will give a generic way on how to set up ECK resources via helm. Keep in mind that you should adjust/add chart values that are relevant for your use case.\u003c/p\u003e\u003cp\u003e\u003cspan data-type='inlineCode'\u003estack/charts/elasticsearch/values.yml:\u003c/span\u003e You should adjust this file to meet your use cases requirements, using this chart you can enable dedicated notes for: \u003cspan data-type='inlineCode'\u003emaster, data, data_hot, data_cold, data_frozen, ingest\u003c/span\u003e nodes. If you don't want to use a dedicated node, a node will be created containing all the roles (default). If you want to create data dedicated nodes, make sure to also enable \u003cspan data-type='inlineCode'\u003emaster\u003c/span\u003e dedicated nodes.\u003c/p\u003e\u003cp\u003eBefore deploying Elasticsearch and Kibana make sure you deployed the ECK operator, the steps to do so in the following:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm repo add elastic https://helm.elastic.co\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm install elastic-operator elastic/eck-operator -n elastic-system --create-namespace\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eOnce you have the operator up and running, you should clone this repo and either spin up the \u003cspan data-type='inlineCode'\u003estack\u003c/span\u003e (which has dependencies Elasticsearch and Kibana) or you can choose to spin up only Elasticsearch (or only Kibana).\u003c/p\u003e\u003cp\u003eLet's assume you want to spin up the stack (Elasticsearch \u0026 Kibana), you should run the following:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm install elastic-stack ./stack\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eIn case you want to deploy only Elasticsearch:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm install \u0026lt;CHARTNAME\u0026gt; ./stack/charts/elasticsearch\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eIf you decide to spin up only Kibana, you should run:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm install \u0026lt;CHARTNAME\u0026gt; ./stack/charts/kibana\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eDone! With that you have Elasticsearch and Kibana up and running. Now we want to use Fleet and elastic agents to collect logs and metrics from our Kubernetes cluster where ECK is running. To do so, the \u003cspan data-type='inlineCode'\u003efleet- server\u003c/span\u003e chart has elastic-agent as a dependency.\u003c/p\u003e\u003cp\u003eTo install that, run the following:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm install \u0026lt;CHARTNAME\u0026gt; ./fleet-server\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eHappy Helming and Observability!\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch4\u003eKeep learning about ECK:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/eck-in-production-environment\" target=\"_self\"\u003eECK in production environment\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/installing-eck-with-terraform-on-gcp\" target=\"_self\"\u003eInstalling ECK with Terraform on GCP\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cbr/\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf03da7bc0acb2888"}}}],"publish_date":"2022-05-24","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"Using ECK with helm-charts","seo_image":null,"seo_title_l10n":"Using ECK with helm"},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt23bfd15a9c05b228","ACL":{},"_version":1,"content_type":"image/png","created_at":"2020-01-28T19:51:35.869Z","created_by":"bltf6ab93733e4e3a73","file_size":"34449","filename":"eck-blog-thumb.png","is_dir":false,"parent_uid":null,"tags":[],"title":"eck-blog-thumb.png","updated_at":"2020-01-28T19:51:35.869Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-30T16:11:50.504Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt23bfd15a9c05b228/5e3090c7507d2f74fb78c86e/eck-blog-thumb.png"},"title":"Using ECK with helm","title_l10n":"Using ECK with helm","updated_at":"2025-03-28T17:11:21.054Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/using-eck-with-helm","publish_details":{"time":"2025-03-28T17:11:26.083Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0a853e3237c8770b","_version":20,"locale":"en-us","ACL":{},"abstract_l10n":"Data analysts and developers can now ingest BigQuery data directly into Elastic, eliminating operational overhead and reducing the time spent on data ingestion to focus on building dashboards to uncover insights or running full-text search in Elastic","author":["bltf8910a8513017ea4","bltac9c8eef342a33ed","blt54cbb3c8904457dd"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-09-29T00:14:29.981Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa489251cbf249015"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eToday we’re excited to announce support for direct BigQuery data ingestion to the Elastic Stack. Now data analysts and developers can ingest data from Google BigQuery to the Elastic Stack with just a few clicks in the Google Cloud Console. By leveraging Dataflow templates, native integrations allow customers to simplify their data pipeline architecture, and eliminate operational overhead related to agent installation and management. \u003c/p\u003e\n\u003cp\u003eMany data analysts and developers use Google BigQuery as a data warehouse solution and the Elastic Stack as a search and dashboard visualization solution. To enhance the experience for both solutions, Google and Elastic have worked together to provide a simplified way to ingest data from BigQuery tables and views to the Elastic Stack. And all of this is possible with just a few clicks in the Google Cloud Console, without ever installing any data shippers or ETL (extract, transform, load) tools.\u003c/p\u003e\n\u003cp\u003eIn this blog post, we’ll cover how to get started with agentless data ingestion from Google BigQuery to the Elastic Stack.\u003c/p\u003e\n\u003ch2\u003eSimplify BigQuery + Elastic use cases\u003c/h2\u003e\n\u003cp\u003eBigQuery is a popular serverless data warehouse solution that makes it possible to centralize data from different sources, such as custom applications, databases, Marketo, NetSuite, Salesforce, web clickstreams, or even Elasticsearch. Users can do joins of datasets from different sources and then run SQL queries to analyze data. It’s common to utilize the output of BigQuery SQL jobs to create further views and tables in BigQuery, or create dashboards to share with other stakeholders and teams in your organization — which can be achieved with Kibana, Elastic’s native data visualization tool!\u003c/p\u003e\n\u003cp\u003eAnother key use case for BigQuery and the Elastic Stack is a full-text search. BigQuery users can ingest data into Elasticsearch and then query and analyze the search results using Elasticsearch APIs or Kibana. \u003c/p\u003e\u003ch2\u003eStreamline data ingest\u003c/h2\u003e\n\u003cp\u003eGoogle Dataflow is a serverless, asynchronous messaging service based on Apache Beam. Dataflow can be used instead of Logstash to ingest data directly from the Google Cloud Console. The Google and Elastic teams worked together to develop an out-of-the-box Dataflow template for pushing data from BigQuery to the Elastic Stack. This template replaces data processing such as data format transformation previously completed by Logstash in a serverless manner — with no other changes for users who previously used the Elasticsearch ingest pipeline.\u003c/p\u003e\n\u003cp\u003eIf you are using BigQuery and Elastic Stack today, you need to install a separate data processor like Logstash or a custom solution on a Google Compute Engine virtual machine (VM), and then use one of these data processors to send data from BigQuery to the Elastic Stack. Provisioning a VM and installing a data processor requires process and management overhead. Now you can skip this step and ingest data directly from BigQuery to Elastic using a dropdown menu in Dataflow. Removing friction is valuable to many users — especially when it can be done with a few clicks in the Google Cloud Console.\u003c/p\u003e\n\u003cp\u003eHere is a summary of data ingestion flow. The integration works for all users, regardless of whether you are using the Elastic Stack on Elastic Cloud, Elastic Cloud in the Google Cloud Marketplace, or a self-managed environment.\u003c/p\u003e"}],"_metadata":{"uid":"cs09c67b2bbf7898d3"}}},{"image":{"image":{"uid":"bltc88ebf1bb8406026","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-28T20:11:44.431Z","updated_at":"2021-09-28T20:11:44.431Z","content_type":"image/png","file_size":"27459","filename":"elastic-blog-bigquery.png","title":"elastic-blog-bigquery.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.758Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc88ebf1bb8406026/61537700bd88320e1278b77d/elastic-blog-bigquery.png"},"_metadata":{"uid":"csa6f29d684c262017"},"caption_l10n":"","alt_text_l10n":"BigQuery Dataflow","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4640b2ede7aea8c2"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eGet started\u003c/h2\u003e\n\u003cp\u003eTo illustrate how easy it is to integrate data from BigQuery to Elasticsearch, we'll use \u003ca href=\"https://console.cloud.google.com/marketplace/product/stack-exchange/stack-overflow\"\u003ea public dataset from the popular Q\u0026A forum Stack Overflow\u003c/a\u003e. Within just a few clicks you can ingest the data via the Dataflow batch job, and start searching and analyzing in Kibana.\u003c/p\u003e\n\u003cp\u003eWe used a table called \u003ccode\u003estackoverflow_posts\u003c/code\u003e under the BigQuery data set stackoverflow. It has several structured fields as columns like \u003ccode\u003epost body, title, comment_count,\u003c/code\u003e etc., which we’ll bring into Elasticsearch to perform free text search and aggregation.\u003c/p\u003e"}],"_metadata":{"uid":"csde0feb006367961c"}}},{"image":{"image":{"uid":"bltb2304d445ad8f950","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:25:35.468Z","updated_at":"2021-09-29T01:25:35.468Z","content_type":"image/png","file_size":"499102","filename":"elastic-blog-bigquery-2.png","title":"elastic-blog-bigquery-2.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.771Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb2304d445ad8f950/6153c08f0332d478b9d32e6a/elastic-blog-bigquery-2.png"},"_metadata":{"uid":"cs93ca40fbba38ad4f"},"caption_l10n":"","alt_text_l10n":"Google Cloud Platform","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs753f6a76b1df0738"},"header_style":"H2","paragraph_l10n":"Create a dataflow job from a template. Select the \u003cstrong\u003eBigQuery to Elasticsearch\u003c/strong\u003e template from the dropdown menu, which is one of Google’s provided templates."}],"_metadata":{"uid":"cs207c7ba3bf00a42d"}}},{"image":{"image":{"uid":"blt8a13c406ef657328","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:27:36.413Z","updated_at":"2021-09-29T01:27:36.413Z","content_type":"image/png","file_size":"268326","filename":"elastic-blog-bigquery-3.png","title":"elastic-blog-bigquery-3.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.784Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8a13c406ef657328/6153c10877d06a0c98360b37/elastic-blog-bigquery-3.png"},"_metadata":{"uid":"csdd2253162444692b"},"caption_l10n":"","alt_text_l10n":"Google Cloud Platform cloud-staging","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs705024374194a42d"},"header_style":"H2","paragraph_l10n":"Fill in the required parameters, including your Cloud ID and Base64-encoded API Key for Elasticsearch. Cloud ID can be found from Elastic Cloud UI as shown below. API Key can be created using the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/security-api-create-api-key.html\"\u003eCreate API key API\u003c/a\u003e."}],"_metadata":{"uid":"cs67552b6044d8b907"}}},{"image":{"image":{"uid":"blta09e250e3a47d5fc","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:29:03.899Z","updated_at":"2021-09-29T01:29:03.899Z","content_type":"image/png","file_size":"157870","filename":"elastic-blog-bigquery-4.png","title":"elastic-blog-bigquery-4.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.809Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta09e250e3a47d5fc/6153c15f9d27cf7da4ba365d/elastic-blog-bigquery-4.png"},"_metadata":{"uid":"cs424f404dec5482ce"},"caption_l10n":"","alt_text_l10n":"deployment parameters","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0ae2e247357e84b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor the \u003ccode\u003eElasticsearch index\u003c/code\u003e field, pick an index name where your data will be loaded. For example, we used the \u003ccode\u003estack-posts\u003c/code\u003e index. Table in BigQuery to read from in the form of: my-project:my-dataset.my-table. In our example it is \u003ccode\u003ebigquery-public-data:stackoverflow.stackoverflow_posts\u003c/code\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"csdfc2d10eee00ed54"}}},{"image":{"image":{"uid":"bltbdea1a890609a844","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:33:37.039Z","updated_at":"2021-09-29T01:33:37.039Z","content_type":"image/png","file_size":"325298","filename":"elastic-blog-bigquery-5.png","title":"elastic-blog-bigquery-5.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.833Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbdea1a890609a844/6153c271f725af79f53ff0db/elastic-blog-bigquery-5.png"},"_metadata":{"uid":"cs8cda003260a993bb"},"caption_l10n":"","alt_text_l10n":"create job from template","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0e5098e27147c80b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eClick \u003cstrong\u003eRun Job\u003c/strong\u003e to start the batch processing.\u003c/p\u003e\n\u003cp\u003eWithin a few minutes, you can see the data flowing into your Elasticsearch index. To visualize this data, create an index pattern by following the \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/index-patterns.html\"\u003edocumentation\u003c/a\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"csc42a38c9be19335e"}}},{"image":{"image":{"uid":"blt725d4952687e818f","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:35:27.723Z","updated_at":"2021-09-29T01:35:27.723Z","content_type":"image/png","file_size":"252407","filename":"elastic-blog-bigquery-6.png","title":"elastic-blog-bigquery-6.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.843Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt725d4952687e818f/6153c2dff725af79f53ff0e3/elastic-blog-bigquery-6.png"},"_metadata":{"uid":"cs40e96564180c9081"},"caption_l10n":"","alt_text_l10n":"Create index pattern","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5232bfa0c9bdf958"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAnd now, head over to Discover in Kibana and start searching your data!\u003c/p\u003e"}],"_metadata":{"uid":"csa965bbddb0de9466"}}},{"image":{"image":{"uid":"bltd4c28514d02849fd","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:36:21.294Z","updated_at":"2021-09-29T01:36:21.294Z","content_type":"image/png","file_size":"476118","filename":"elastic-blog-bigquery-7.png","title":"elastic-blog-bigquery-7.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.851Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd4c28514d02849fd/6153c3150332d478b9d32e7a/elastic-blog-bigquery-7.png"},"_metadata":{"uid":"cs30ba64a0ff434811"},"caption_l10n":"","alt_text_l10n":"Discover in Kibana","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs31aacdad7fc94fa8"},"header_style":"H2","paragraph_l10n":"Visualize the top five buckets for comment counts for your search query, or create a filter or a dashboard all through the power of \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/dashboard.html#lens\"\u003eKibana Lens\u003c/a\u003e."}],"_metadata":{"uid":"cscd3936221245c1e4"}}},{"image":{"image":{"uid":"blt0f7e16821d94e3da","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-29T01:39:40.064Z","updated_at":"2021-09-29T01:39:40.064Z","content_type":"image/png","file_size":"475548","filename":"elastic-blog-bigquery-8.png","title":"elastic-blog-bigquery-8.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-29T15:10:41.861Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0f7e16821d94e3da/6153c3dcbd88320e1278b874/elastic-blog-bigquery-8.png"},"_metadata":{"uid":"cs073b71b9759ebae6"},"caption_l10n":"","alt_text_l10n":"Kibana Lens","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf4c9effdf4b4af28"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eWrapping up\u003c/h2\u003eElastic is constantly making it easier and more frictionless for customers to run where they want and use what they want — and this streamlined integration with Google Cloud is the latest example of that. Elastic Cloud extends the value of the Elastic Stack, allowing customers to do more, faster, making it the best way to experience our platform. \u003ca href=\"https://cloud.google.com/dataflow/docs/guides/templates/provided-batch#bigquery-to-elasticsearch\" target=\"_self\"\u003eFor more information on the integration, visit Google’s documentation\u003c/a\u003e. To get started using Elastic on Google Cloud, visit the \u003ca href=\"https://console.cloud.google.com/marketplace/product/elastic-prod/elastic-cloud?utm_source=elastic\u0026utm_medium=elastic_blog\u0026utm_campaign=ingest_data_directly_from_google_bigquery_into_elastic_using_google_dataflow\" target=\"_self\"\u003eGoogle Cloud Marketplace\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/\" target=\"_self\"\u003eelastic.co\u003c/a\u003e."}],"_metadata":{"uid":"cs1885f5baedaa93c3"}}}],"publish_date":"2021-09-29T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Ingest data directly from Google BigQuery into Elastic using Google Dataflow","seo_description_l10n":"Data analysts and developers can now ingest BigQuery data directly into Elastic, eliminating operational overhead and reducing the time spent on data ingestion to focus on building dashboards to uncover insights or running full-text search in Elastic.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte0256e5390d036ed","ACL":{},"created_at":"2023-11-06T20:25:43.573Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-migration","label_l10n":"Cloud migration","tags":[],"title":"Cloud migration","updated_at":"2023-11-06T20:25:43.573Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:27.667Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8d7a0b617e08ab37","ACL":{},"created_at":"2023-11-06T21:36:18.085Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"workload-migration","label_l10n":"Workload migration","tags":[],"title":"Workload migration","updated_at":"2023-11-06T21:36:18.085Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.400Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltfda9e7f7ea98808b","ACL":{},"content_type":"image/png","created_at":"2020-01-10T22:30:09.095Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"44390","filename":"blog-thumb-cloud-gcp.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-gcp.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.262Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfda9e7f7ea98808b/5ffe114c7f3df4662710b340/blog-thumb-cloud-gcp.png"},"title":"Ingest data directly from Google BigQuery into Elastic using Google Dataflow","title_l10n":"Ingest data directly from Google BigQuery into Elastic using Google Dataflow","updated_at":"2025-03-28T17:10:59.502Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/ingest-data-directly-from-google-bigquery-into-elastic-using-google-dataflow","publish_details":{"time":"2025-03-28T17:11:05.166Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt075dad2d9f17fb69","_version":22,"locale":"en-us","ACL":{},"abstract_l10n":"Developers, SREs, and security analysts can now ingest data directly from Google Cloud Storage into Elastic using Google Dataflow, accelerating the time required for troubleshooting and analysis.","author":["bltf8910a8513017ea4","bltac9c8eef342a33ed","blt54cbb3c8904457dd"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-09-29T02:45:28.216Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfd2394a2b0ebc71f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eToday we’re excited to announce support for direct Google Cloud Storage (GCS) data ingestion to the Elastic Stack with Google Dataflow. Now developers, site reliability engineers (SREs), and security analysts can ingest data from GCS to the Elastic Stack with just a few clicks in the Google Cloud Console. \u003c/p\u003e\n\u003cp\u003eMany developers, SREs, and security analysts use GCS to store logs and events generated from applications and infrastructure in Google Cloud while also using the Elastic Stack to troubleshoot, monitor, or look for security anomalies from these applications and infrastructure. To enhance the experience for both solutions, Google and Elastic have worked together to provide an easy-to-use, low-friction way to ingest logs and events stored in GCS to the Elastic Stack. This allows you to simplify your data pipeline architecture, eliminate operational overhead, and reduce the time required for troubleshooting — all with just a few clicks in the Google Cloud Console, and without creating a custom data processor. \u003c/p\u003e\n\u003cp\u003eIn this blog post, we’ll cover how to get started with agentless data ingestion from GCS to the Elastic Stack using Google Dataflow.\u003c/p\u003e\u003ch2\u003eStreamline data ingest from GCS\u003c/h2\u003e\n\u003cp\u003eGoogle Cloud Storage is an object storage solution that is often compared to Amazon S3 or Azure Blob Storage. GCS is often used for data backup and archive, data analytics with no streaming requirements, or even hosting simple web pages and applications at attractive price points. A developer, SRE, or security analyst may decide to store application or infrastructure logs and events in GCS for backup or archive purposes. A Google Cloud user may also have a data pipeline where not all of the data is ingested into the Elastic Stack, with some stored in GCS for later analysis if necessary. \u003c/p\u003e\n\u003cp\u003eOnce the logs and events are in GCS, you have to decide on the ingestion method for third-party analytics solutions like Elastic. It would be ideal to be able to ingest data directly from GCS to the Elastic Stack with just a few clicks in the Google Cloud Console. This is now possible with a dropdown menu in Google Dataflow, a popular serverless data process product based on Apache Beam. Dataflow effectively pushes logs and events from GCS to the Elastic Stack. Currently, CSV file format is supported and we’ll be adding support for JSON soon.\u003c/p\u003e\n\u003cp\u003eHere is the summary of the data ingestion flow. The integration works for all users, whether you’re using the Elastic Stack on Elastic Cloud, Elastic Cloud in the Google Cloud Marketplace, or a self-managed environment. \u003c/p\u003e"}],"_metadata":{"uid":"cs929630b489400a8e"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltd90012c091d42541","ACL":{},"content_type":"image/png","created_at":"2021-09-29T02:36:40.957Z","created_by":"blt1e57c6588ae1816e","file_size":"25739","filename":"elastic-blog-googlecloudstorage.png","parent_uid":null,"tags":[],"title":"elastic-blog-googlecloudstorage.png","updated_at":"2021-09-29T02:36:40.957Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:03.166Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd90012c091d42541/6153d1381ea20372528ad145/elastic-blog-googlecloudstorage.png"},"_metadata":{"uid":"cs24dd0b9f56bd7dd3"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"Dataflow","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaa2c3995d6d75aa1"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eGet started\u003c/h2\u003e\n\u003cp\u003eThe best way to demonstrate the GCS ingest functionality is to step through an example. The following example will analyze earthquake data from USGS which catalogs a public dataset that provides information about real-time earthquakes and seismic stats. We’ll use the USGS magnitude \u003ca href=\"https://earthquake.usgs.gov/earthquakes/feed/v1.0/summary/2.5_month.csv\"\u003e2.5+ earthquakes\u003c/a\u003e from the past month as a CSV. Here we’re showing only the first five lines of the file to give you an idea of what the data looks like:\u003c/p\u003e"}],"_metadata":{"uid":"cs6c446be7e58a7efe"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltee0956af688e6fe1","ACL":{},"content_type":"image/png","created_at":"2021-09-29T03:10:30.074Z","created_by":"blt3044324473ef223b70bc674c","file_size":"447344","filename":"elastic-blog-googlecloudstorage-2.png","tags":[],"title":"elastic-blog-googlecloudstorage-2.png","updated_at":"2021-09-29T03:10:30.074Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:00.317Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltee0956af688e6fe1/6153d926947b692d209b8056/elastic-blog-googlecloudstorage-2.png"},"_metadata":{"uid":"csec3e8a293fd28767"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"data file","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs510c39c9effec904"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn the Dataflow page on the Google Cloud Console, select the \u003cstrong\u003eGCS to Elasticsearch template\u003c/strong\u003e. The template creates the schema for the JSON document using one of the following:\u003c/p\u003e\u003col\u003e\u003cli\u003eJavascript UDF (if provided)\u003c/li\u003e\u003cli\u003eJSON schema (if provided)\u003c/li\u003e\u003cli\u003eCSV headers* (default)\u003c/li\u003e\u003c/ol\u003e\n\u003cp\u003eIf either a UDF or JSON schema is provided then it will be used instead of the CSV headers. \u003c/p\u003e"}],"_metadata":{"uid":"cse16ad6b8537e3a6c"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltcd90690751ac2244","ACL":{},"content_type":"image/png","created_at":"2021-09-29T02:38:50.365Z","created_by":"blt1e57c6588ae1816e","file_size":"171141","filename":"elastic-blog-googlecloudstorage-3.png","tags":[],"title":"elastic-blog-googlecloudstorage-3.png","updated_at":"2021-09-29T02:38:50.365Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:02.589Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcd90690751ac2244/6153d1ba69b7947c1b3b015e/elastic-blog-googlecloudstorage-3.png"},"_metadata":{"uid":"csb88ad021c3375ab4"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"cloud staging","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs65bdf002222db630"},"header_style":"H2","paragraph_l10n":"For the first field on the form, enter the parameters that indicate the location of files in GCS. Cloud ID can be found from Elastic Cloud UI as shown below. API Key can be created using the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/security-api-create-api-key.html\"\u003eCreate API key API\u003c/a\u003e."}],"_metadata":{"uid":"cs5b9a65ca82c5a7be"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blte21c59b2ec7701c2","ACL":{},"content_type":"image/png","created_at":"2021-09-29T02:39:48.346Z","created_by":"blt1e57c6588ae1816e","file_size":"157870","filename":"elastic-blog-googlecloudstorage-4.png","tags":[],"title":"elastic-blog-googlecloudstorage-4.png","updated_at":"2021-09-29T02:39:48.346Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:00.102Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte21c59b2ec7701c2/6153d1f469b7947c1b3b0166/elastic-blog-googlecloudstorage-4.png"},"_metadata":{"uid":"cs881ca81fe70e9fd5"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"API Key","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9caa8428cadb2334"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor the \u003ccode\u003eElasticsearch index\u003c/code\u003e field, pick an index name where your data will be loaded. For example, we used the \u003ccode\u003equakes\u003c/code\u003e index.\u003c/p\u003e"}],"_metadata":{"uid":"cs98dbc2c4fe4edc52"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt8a8a4be6a7b18686","ACL":{},"content_type":"image/png","created_at":"2021-09-29T02:41:36.351Z","created_by":"blt1e57c6588ae1816e","file_size":"280180","filename":"elastic-blog-googlecloudstorage-5.png","tags":[],"title":"elastic-blog-googlecloudstorage-5.png","updated_at":"2021-09-29T02:41:36.351Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:03.483Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8a8a4be6a7b18686/6153d2609d27cf7da4ba3685/elastic-blog-googlecloudstorage-5.png"},"_metadata":{"uid":"cs62716b04f4a6e75a"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"cloud staging","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf3578f155042fedf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eClick on \u003cstrong\u003eRun Job\u003c/strong\u003e to start ingesting this earthquake data in GCS to Elasticsearch, all without leaving the Google Cloud console. \u003c/p\u003e\n\u003cp\u003eYou can then navigate to Kibana, create an index pattern, and start visualizing in minutes:\u003c/p\u003e"}],"_metadata":{"uid":"csca1adb9d0419d512"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt78b1de0b29478be0","ACL":{},"content_type":"image/png","created_at":"2021-09-29T02:43:03.555Z","created_by":"blt1e57c6588ae1816e","file_size":"252287","filename":"elastic-blog-googlecloudstorage-6.png","tags":[],"title":"elastic-blog-googlecloudstorage-6.png","updated_at":"2021-09-29T02:43:03.555Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:00.086Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt78b1de0b29478be0/6153d2b769b7947c1b3b016a/elastic-blog-googlecloudstorage-6.png"},"_metadata":{"uid":"cs52a75d0cd853241d"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"Kibana","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs500a4a9982265cb4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSample dashboard that shows presentation of earthquake data:\u003c/p\u003e"}],"_metadata":{"uid":"cs89b9b49f20fea623"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt829d13fc1905e169","ACL":{},"content_type":"image/png","created_at":"2021-09-29T02:44:02.009Z","created_by":"blt1e57c6588ae1816e","file_size":"486740","filename":"elastic-blog-googlecloudstorage-7.png","parent_uid":null,"tags":[],"title":"elastic-blog-googlecloudstorage-7.png","updated_at":"2021-09-29T02:44:02.009Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T15:00:03.575Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt829d13fc1905e169/6153d2f21ea20372528ad14f/elastic-blog-googlecloudstorage-7.png"},"_metadata":{"uid":"cs122750b3f6b3ab96"},"caption_l10n":"\u0026nbsp;","alt_text_l10n":"earthquake map","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6a1bb487ccb5652e"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eWrapping up\u003c/h2\u003eElastic is constantly making it easier for customers to run where they want and use what they want — and this streamlined integration with Google Cloud is the latest example of that. Elastic Cloud extends the value of the Elastic Stack, allowing customers to do more, faster, making it the best way to experience our platform. \u003ca href=\"https://cloud.google.com/dataflow/docs/guides/templates/provided-batch#cloud-storage-to-elasticsearch\" target=\"_self\"\u003eFor more information on the integration, visit Google’s documentation\u003c/a\u003e. To get started using Elastic on Google Cloud, visit the \u003ca href=\"https://console.cloud.google.com/marketplace/product/elastic-prod/elastic-cloud?utm_source=elastic\u0026utm_medium=elastic_blog\u0026utm_campaign=ingest_data_directly_from_google_cloud_storage_into_elastic_using_google_dataflow\" target=\"_self\"\u003eGoogle Cloud Marketplace\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/\" target=\"_self\"\u003eelastic.co\u003c/a\u003e."}],"_metadata":{"uid":"csfdb1cb114aecb74b"}}}],"publish_date":"2021-09-30T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Ingest data directly from Google Cloud Storage into Elastic using Google Dataflow","seo_description_l10n":"Developers, SREs, and security analysts can now ingest data directly from Google Cloud Storage into Elastic using Google Dataflow, accelerating the time required for troubleshooting and analysis.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte0256e5390d036ed","ACL":{},"created_at":"2023-11-06T20:25:43.573Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-migration","label_l10n":"Cloud migration","tags":[],"title":"Cloud migration","updated_at":"2023-11-06T20:25:43.573Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:27.667Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8d7a0b617e08ab37","ACL":{},"created_at":"2023-11-06T21:36:18.085Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"workload-migration","label_l10n":"Workload migration","tags":[],"title":"Workload migration","updated_at":"2023-11-06T21:36:18.085Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.400Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltfda9e7f7ea98808b","ACL":{},"content_type":"image/png","created_at":"2020-01-10T22:30:09.095Z","created_by":"bltf6ab93733e4e3a73","description":"","file_size":"44390","filename":"blog-thumb-cloud-gcp.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-cloud-gcp.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.262Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfda9e7f7ea98808b/5ffe114c7f3df4662710b340/blog-thumb-cloud-gcp.png"},"title":"Ingest data directly from Google Cloud Storage into Elastic using Google Dataflow","title_l10n":"Ingest data directly from Google Cloud Storage into Elastic using Google Dataflow","updated_at":"2025-03-28T17:10:30.066Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/ingest-data-directly-from-google-cloud-storage-into-elastic-using-google-dataflow","publish_details":{"time":"2025-03-28T17:10:35.429Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcb16e8d8e22b23fb","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"In this research piece, we explore BPFDoor — a backdoor payload specifically crafted for Linux in order to gain re-entry into a previously or actively compromised target environment, with insights on how evasion occurs within impacted systems.","author":["bltc1a27bf09861513f"],"category":["bltb79594af7c5b4199"],"created_at":"2022-05-17T21:28:50.781Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscccea74e49d34906"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThreats knock on your door all the time. In this \u003ca href=\"https://www.elastic.co/security-labs/a-peek-behind-the-bpfdoor\" target=\"_self\"\u003eresearch piece\u003c/a\u003e, we explore \u003c/span\u003e\u003ca href=\"https://doublepulsar.com/bpfdoor-an-active-chinese-global-surveillance-tool-54b078f1a896\" target=\"_self\"\u003eBPFDoor\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e — a backdoor payload specifically crafted for Linux in order to gain re-entry into a previously or actively compromised target environment. This payload has been observed across systems for five years, suggesting that the threat actors responsible for operating the malware have been around for some time and have likely operated undetected in many environments.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe threat actors have leveraged a network of VPS servers to act as a controller and access these systems via compromised routers based out of Taiwan, acting as a VPN network for the adversarial group. In the Elastic Security Intelligence and Analytics team’s deep research, we explore the actual payload, the backdoor lifecycle, and the BPF filters that are leveraged to provide you with insights on how evasion occurs within impacted systems.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eIt’s important to know how you can detect this payload threat and understand the sophistication of the loader. Both are covered in \u003ca href=\"https://www.elastic.co/security-labs/a-peek-behind-the-bpfdoor\" target=\"_self\"\u003ethis research\u003c/a\u003e. The Elastic Security Intelligence and Analytics team also shares the actual indicators of compromise.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eIt’s critical to invest the time and resources into ensuring your organization’s workloads remain effectively monitored. Get started with a \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=trail\" target=\"_self\"\u003e\u003cu\u003efree 14-day trial of Elastic Cloud\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e. Or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=download\" target=\"_self\"\u003e\u003cu\u003edownload\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e the self-managed version of the Elastic Stack for free.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1230031f809a807d"}}}],"publish_date":"2022-05-18T07:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Threat protection from BPFDoor","seo_description_l10n":"In this research piece, we explore BPFDoor — a backdoor payload specifically crafted for Linux in order to gain re-entry into a previously or actively compromised target environment, with insights on how evasion occurs within impacted systems.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt8eb410499d8645b9","ACL":{},"content_type":"image/png","created_at":"2021-12-03T15:10:01.483Z","created_by":"blt4349d9729d06d101","file_size":"161741","filename":"blog-security-detection-720x420.png","parent_uid":null,"tags":[],"title":"blog-security-detection-720x420.png","updated_at":"2021-12-03T15:10:01.483Z","updated_by":"blt4349d9729d06d101","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-03T18:35:40.809Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8eb410499d8645b9/61aa334981fe8f3ca269a15f/blog-security-detection-720x420.png"},"title":"A peek behind the BPFDoor","title_l10n":"A peek behind the BPFDoor","updated_at":"2025-03-28T16:56:48.869Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/a-peek-behind-the-bpfdoor","publish_details":{"time":"2025-03-28T16:56:54.499Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3094a90b52527c02","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"See how we’ve been improving the processes that allow us to make updates quickly in response to new information and propagate those protections to our users, with the help of machine learning models. ","author":["bltd3ad28026289add7"],"category":["bltb79594af7c5b4199"],"created_at":"2022-06-07T21:50:17.826Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs879c520bc8599a26"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eCyber attacks on corporate networks were \u003c/span\u003e\u003ca href=\"https://www.forbes.com/sites/chuckbrooks/2022/01/21/cybersecurity-in-2022--a-fresh-look-at-some-very-alarming-stats/?sh=675676ea6b61\" target=\"_self\"\u003e\u003cu\u003eup 50% in 2021\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e, and it’s \u003c/span\u003e\u003ca href=\"https://www.govtech.com/blogs/lohrmann-on-cybersecurity/the-top-22-security-predictions-for-2022\" target=\"_self\"\u003e\u003cu\u003eexpected that 2022 will see more of the same\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/endpoint-security/\" target=\"_self\"\u003e\u003cu\u003eElastic Endpoint Security\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e includes a variety of protection layers to ensure maximum coverage against different types of malware. There have been a few examples recently of the need for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-protects-against-data-wiper-malware-targeting-ukraine-hermeticwiper\" target=\"_self\"\u003e\u003cu\u003efast, accurate updates\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e of user environments in order to protect against the latest malware. Here at Elastic, we’ve been improving the processes that allow us to make updates quickly in response to new information and propagate those protections to our users.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eAs part of our security solution, we use a machine learning model to help us detect malware based on known characteristics. Since machine learning is never perfect, we deploy supplemental artifacts, including lists of known file hashes that range from malicious to benign. There are two scenarios when we might need to update these lists, which we’ll cover here. Using these, teams can experience a much faster response to malware.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e[Related article: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/sandboxing-anti-malware-products-for-fun-and-profit\" target=\"_self\"\u003e\u003cu\u003eSandboxing anti-malware products for fun and profit\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e]\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eScenario 1: The model isn’t perfect\u0026nbsp;\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThis happens pretty rarely, since our model has True Negative rates of 99.8%. But no model is perfect, and our True Positive rates vary from 99% (which is great) down to 97.9%, due to noisy data — particularly large bursts of near-duplicates. In applying machine learning to cybersecurity, data drift is an ever-present challenge and part of what makes it such an interesting problem.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThere are a couple of ways we can find out if our model is doing the wrong thing:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e1) \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eUser feedback.\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eA user sends us an email telling us that a piece of custom software is being flagged as malware, but is actually safe.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e2) \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eTelemetry data coming back from our model running on customers’ machines.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWe look at the volume and velocity of alerts, using Elastic’s Anomaly Detection feature to let us know if there is a sudden spike from a particular file. We also use patterns to help us confirm if an alert is coming from a single noisy machine, a test cluster, or a legitimate threat.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe advantage of using lists as a backstop to machine learning is that it’s a fast and easy way to make sure our customers are protected from new malware, as well as protecting them from unnecessary noise from false positives.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eScenario 2: New forms of malware appear\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWe typically find out about new kinds of malware from either security news/community resources, or our own Security Intelligence and Analytics team identifying new kinds of malware.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWhen this happens, we can easily deploy small changes to lists. We update the model separately, because that takes longer.\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWe’ve been steadily adding more automation to make this process of deploying updated lists to customers smoother and faster, with the goal of making it easy for anyone on the team to create and deploy an update. We’ve also been working on making the process of updating the model easier and faster.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThreats yet discovered…\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003eThe Elastic Security Intelligence and Analytics team continues to research and respond to groundbreaking threats in its mission to help Elastic customers and the broader security community. If you’re using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=elastic+security\" target=\"_self\"\u003e\u003cu\u003eElastic Security\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e already, you can expect to see our latest findings in the newsfeed within the platform. We’ll also post our latest findings on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog\" target=\"_self\"\u003e\u003cu\u003eelastic.co/blog\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003eReady to become part of the Elastic Security community and take advantage of the team’s leading threat research? Get started with a free \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=trail\" target=\"_self\"\u003e\u003cu\u003e14-day trial of Elastic Cloud\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=download\" target=\"_self\"\u003e\u003cu\u003edownload\u003c/u\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);\"\u003e the self-managed version of the Elastic Stack for free.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5e4138fa94612266"}}}],"publish_date":"2022-06-09T07:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Automating the Security Protections rapid response to malware","seo_description_l10n":"See how we’ve been improving the processes that allow us to make updates quickly in response to new information and propagate those protections to our users, with the help of machine learning models. ","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"bltbbb16787f2745266","ACL":{},"content_type":"image/png","created_at":"2022-06-01T19:13:18.460Z","created_by":"blt3044324473ef223b70bc674c","file_size":"110089","filename":"blog-security-endpoint-720x420.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-security-endpoint-720x420.png","updated_at":"2022-06-01T19:13:18.460Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-13T18:59:20.587Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbbb16787f2745266/6297ba4e6634c30f572c8d99/blog-security-endpoint-720x420.png"},"title":"Automating the Security Protections rapid response to malware","title_l10n":"Automating the Security Protections rapid response to malware","updated_at":"2025-03-28T16:56:12.768Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/automating-security-protections-rapid-response-to-malware","publish_details":{"time":"2025-03-28T16:56:19.651Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt741b2e880f9732eb","_version":21,"locale":"en-us","ACL":{},"abstract_l10n":"Running ECK with Kubernertes monitoring and logs integration, cert-manager, ingress controller, SAML and much more.","author":["blt37871c8eba8cdb1e"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-05-20T13:47:07.443Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs43134091483bae0f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis article will guide you on how to spin up an ECK environment ready for production which contains,\u003c/p\u003e\u003cul\u003e\u003cli\u003ededicated stack monitoring,\u003c/li\u003e\u003cli\u003efleet-server \u0026 elastic-agent (with kubernetes integration),\u003c/li\u003e\u003cli\u003eelasticsearch autoscaling,\u003c/li\u003e\u003cli\u003enodeAffinity \u0026 nodeSelector,\u003c/li\u003e\u003cli\u003eSAML with auth0,\u003c/li\u003e\u003cli\u003ehot, warm, cold, frozen architecture,\u003c/li\u003e\u003cli\u003eheartbeat monitor SSL certificate expiration,\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/kubernetes-sigs/external-dns\" target=\"_self\"\u003eexternal-dns \u003c/a\u003e(with CloudFlare integration),\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/cert-manager/cert-manager\" target=\"_self\"\u003ecert-manager \u003c/a\u003e(with let's encrypt integration),\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://kubernetes.github.io/ingress-nginx/\" target=\"_self\"\u003eingress controller \u003c/a\u003e(using Cloudflare to register the endpoints),\u003c/li\u003e\u003cli\u003eOptional: \u003ca href=\"https://esrally.readthedocs.io/en/stable/\"\u003eesrally\u003c/a\u003e to validate autoscaling and run benchmark against es cluster\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eRemember you must have \u003cspan data-type='inlineCode'\u003ebasic\u003c/span\u003e or \u003cspan data-type='inlineCode'\u003eenterprise\u003c/span\u003e license to run ECK.\u003c/p\u003e\u003ch2\u003eDemo\u003c/h2\u003e\u003cp\u003eTo see the demo and files, please access \u003ca href=\"https://github.com/framsouza/eck-ready-for-production\" target=\"_self\"\u003ehttps://github.com/framsouza/eck-ready-for-production\u003c/a\u003e\u003c/p\u003e\u003ch3\u003ecert-manager\u003c/h3\u003e\u003cp\u003ecert-manager adds certificates and certificate issuers as resource types in Kubernetes, and simplifies the process of obtaining, renewing and using those certificates. It's very command Kubernetes administrator use cert-manager to handle certificate, and on this example we are going to use cert-manager with let's encrypt to access Kibana. Remember that, TLS certificates for the Elasticsearch transport layer that are used for internal communications between Elasticsearch nodes are managed by ECK and cannot be changed.\u003c/p\u003e\u003ch3\u003eingress\u003c/h3\u003e\u003cp\u003eIngress controller is specialized load balancer for Kubernetes, which accepts traffic from outside the Kubernetes cluster and balances it to pods.\u003c/p\u003e\u003ch3\u003eexternal-dns\u003c/h3\u003e\u003cp\u003eIt's a addon that configures public DNS servers about exposed Kubernetes services, on this examples we are integrating external-dns with Cloudflare. For each Ingress/Service resource you us, a DNS entry will created on Cloudflare with the respective IP address, on external-dns logs you should be able to see the following:\u003c/p\u003e"}],"_metadata":{"uid":"cs7b36218aa1d26393"}}},{"code":{"code":"level=info msg=\"Using inCluster-config based on serviceaccount-token\"\nlevel=info msg=\"Created Kubernetes client https://10.76.0.1:443\"\nlevel=info msg=\"Changing record.\" action=CREATE record=kibana.framsouza.co ttl=1 type=A zone=4cd4c7c1cb8f7bf3a7482749654ae6fb\nlevel=info msg=\"Changing record.\" action=CREATE record=monitoring.framsouza.co ttl=1 type=TXT zone=4cd4c7c1cb8f7bf3a7482749654ae6fb","_metadata":{"uid":"cs38ca58271231ef62"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs017b8624324c4e48"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003eHow-to setup\u003c/h3\u003e\u003cp\u003eMake sure to respect the commands execution order:\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003eCreate GKE cluster with Kubernetes type hot, warm, cold, frozen for each dedicated node pool, make sure you will have enough resource to run the pods in the nodes.\u003c/li\u003e\u003cli\u003eCreate a cluster role mapping that gives you permission to install ECK operator\u003c/li\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ekubectl create clusterrolebinding cluster-admin-binding --cluster-role=cluster-admin --user=\u0026lt;USERNAME\u0026gt;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cli\u003eInstall ECK operator\u003c/li\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm repo add elastic https://helm.elastic.co \u0026\u0026 helm repo update \u0026\u0026 helm install elastic-operator elastic/eck-operator -n elastic-system --create-namespace\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cli\u003eCreate dedicated storage class by applying files storageclass-hot.yaml and storageclass-warm.yaml\u003c/li\u003e\u003cli\u003eDownload your license and apply it via secret (or apply the \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/license.yaml\" target=\"_self\"\u003elicense.yaml)\u003c/a\u003e\u003c/li\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ekubectl create secret generic eck-license --from-file \u0026lt;LICENSE-PATH\u0026gt; -n elastic-system \u0026\u0026 kubectl label secret eck-license \"license.k8s.elastic.co/scope\"=operator -n elastic-system\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cli\u003eCreate the monitoring cluster (it will create a \u003cspan data-type='inlineCode'\u003ens\u003c/span\u003e call monitoring) by applying \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/monitoring-es.yaml\" target=\"_self\"\u003emonitoring-es.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eCreate elasticsearch resource, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/elasticsearch.yaml\" target=\"_self\"\u003eelasticsearch.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eCreate kibana resource, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/kibana.yaml\" target=\"_self\"\u003ekibana.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eCreate fleet resource, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/fleet.yaml\" target=\"_self\"\u003efleet.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eCreate heartbeat, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/heartbeat.yaml\" target=\"_self\"\u003eheartbeat.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eInstall external-dns\u003c/li\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ekubectl apply -f external-dns.yml\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cli\u003eInstall cert-manager\u003c/li\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ekubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/v1.7.1/cert-manager.yaml\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cli\u003eInstall ingress-nginx ,\u003c/li\u003e\u003cul\u003e\u003cli\u003e\u003cspan data-type='inlineCode'\u003ehelm upgrade --install ingress-nginx ingress-nginx --repo https://kubernetes.github.io/ingress-nginx --namespace ingress-nginx --create-namespace\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cli\u003eCreate ingress resource, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/ingress.yaml\" target=\"_self\"\u003eingress.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eCreate cluster issuer apply, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/clusterissuer.yaml\" target=\"_self\"\u003eclusterissuer.yaml\u003c/a\u003e\u003c/li\u003e\u003cli\u003eCreate let's encrypt certificate, \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/certificate.yaml\" target=\"_self\"\u003ecertificate.yaml\u003c/a\u003e\u003c/li\u003e\u003c/ol\u003e\u003ch3\u003eAccessing\u003c/h3\u003e\u003cp\u003eFor this example, I am using a domain call framsouza.co and as I am using external-dns, the DNS entry will be automatically added to Cloudflare, https://kibana.framsouza.co and https://monitoring.framsouza.co. You can check the connection is safe and we are using a valid certificate by let's encrypt.\u003c/p\u003e\u003cp\u003eIf you want to login using SAML, make sure to adjust the \u003cspan data-type='inlineCode'\u003esaml\u003c/span\u003e session on \u003cspan data-type='inlineCode'\u003eelasticsearch.yml\u003c/span\u003e according to your environment.\u003c/p\u003e\u003ch3\u003eAutoscaling validation\u003c/h3\u003e\u003cp\u003e(Optional)\u003c/p\u003e\u003cp\u003eTo confirm if autoscaling is working as expected, you can use \u003ca href=\"https://esrally.readthedocs.io/en/stable/\" target=\"_self\"\u003eesrally\u003c/a\u003e to test that and run benchmark against your cluster. Make sure to have \u003cspan data-type='inlineCode'\u003eparams-file.json\u003c/span\u003e with the following content:\u003c/p\u003e\u003cp\u003e{\u003c/p\u003e\u003cp\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"number_of_replicas\": 1,\u003c/p\u003e\u003cp\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\"number_of_shards\": 2\u003c/p\u003e\u003cp\u003e}\u003c/p\u003e\u003cp\u003ethen you just need to run and wait a couple of hours until the test is finished.\u003c/p\u003e"}],"_metadata":{"uid":"cs16fa0af20f79b9fb"}}},{"code":{"code":"docker run -v /tmp/params-file.json:/tmp/params-file.json elastic/rally race --track=http_logs --target-hosts=${IP}:9200 --pipeline=benchmark-only --client-options=\"timeout:60,use_ssl:true,verify_certs:false,basic_auth_user:'elastic',basic_auth_password:'${PASSWORD}'\" --track-params=/tmp/params-file.json","_metadata":{"uid":"cs24da6dd46e151822"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs59ffa8900402c778"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eHave a look at \u003ca href=\"https://github.com/framsouza/eck-ready-for-production/blob/main/esrally-result.txt\" target=\"_self\"\u003eesrally-result.txt\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch4\u003eKeep learning about ECK:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/using-eck-with-helm\" target=\"_self\"\u003eECK with helm\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/installing-eck-with-terraform-on-gcp\" target=\"_self\"\u003eInstalling ECK with Terraform on GCP\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs59e615dbd40a2a86"}}}],"publish_date":"2022-05-23","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"Running ECK with Kubernertes monitoring and logs integration, cert-manager, ingress controller, SAML and much more.","seo_image":null,"seo_title_l10n":"ECK in production environment"},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt23bfd15a9c05b228","ACL":{},"_version":1,"content_type":"image/png","created_at":"2020-01-28T19:51:35.869Z","created_by":"bltf6ab93733e4e3a73","file_size":"34449","filename":"eck-blog-thumb.png","is_dir":false,"parent_uid":null,"tags":[],"title":"eck-blog-thumb.png","updated_at":"2020-01-28T19:51:35.869Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-30T16:11:50.504Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt23bfd15a9c05b228/5e3090c7507d2f74fb78c86e/eck-blog-thumb.png"},"title":"ECK in production environment","title_l10n":"ECK in production environment","updated_at":"2025-03-28T16:55:52.288Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/eck-in-production-environment","publish_details":{"time":"2025-03-28T16:55:57.474Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt11fd3e9f23f7732f","_version":9,"locale":"en-us","ACL":{},"abstract_l10n":"We explore using Elastic to extract Cobalt Strike beacon payloads from memory and use open source tools to analyze and group threat activity clusters.","author":["blte6e65ef62d0ef93d","bltc7df7c2cea1deedd","blt2c45cabef3b4013c","bltc1a27bf09861513f"],"category":["bltb79594af7c5b4199"],"created_at":"2022-01-19T17:54:16.395Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0ee4e89c6836f0c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElastic Security engineers \u003ca href=\"https://www.elastic.co/security-labs/collecting-cobalt-strike-beacons-with-the-elastic-stack\" target=\"_self\"\u003ehave documented\u003c/a\u003e a less tedious way to find network beaconing from Cobalt Strike. In their full analysis ([\u003ca href=\"https://www.elastic.co/security-labs/collecting-cobalt-strike-beacons-with-the-elastic-stack\" target=\"_self\"\u003e1\u003c/a\u003e] [\u003ca href=\"https://www.elastic.co/security-labs/extracting-cobalt-strike-beacon-configurations\" target=\"_self\"\u003e2\u003c/a\u003e]), Elastic Security team researchers Andrew Pease, Derek Ditch, and Daniel Stepanic walk users through the Elastic fleet policy, how to collect the beacon, beacon configuration, how to analyze its activity, and how you can set it up in your organization’s environment.\u003c/p\u003e\u003cp\u003eThese two articles ([\u003ca href=\"https://www.elastic.co/security-labs/collecting-cobalt-strike-beacons-with-the-elastic-stack\" target=\"_self\"\u003e1\u003c/a\u003e] [\u003ca href=\"https://www.elastic.co/security-labs/extracting-cobalt-strike-beacon-configurations\" target=\"_self\"\u003e2\u003c/a\u003e]) are ideal for helping security analysts identify, collect, and configure Cobalt Strike beacon payloads from an endpoint using Elastic. It is often difficult to collect the Cobalt Strike beacon payload from memory and extract its configuration to identify observables and cluster group activities, partially due to the tremendous amount of metadata the beacon’s configurations include.\u003c/p\u003e\u003cp\u003eThe early stages of an intrusion usually include initial access, execution, persistence, and command-and-control (C2) beaconing. When structured threats use zero-days, these first two stages are often not detected, and it can often be challenging and time-consuming to identify persistence mechanisms left by an advanced adversary. \u003c/p\u003e\u003cp\u003eThe information helps threat hunters and analysts monitor Cobalt Strike beaconing activity, but also provides useful indicators of compromise (IoCs) with which to start an investigation.\u003c/p\u003e\u003cbr/\u003eIf you don’t have an Elastic Cloud cluster but would like to collect and configure the Cobalt Strike beacon, you can start a \u003ca href=\"https://cloud.elastic.co/registration\" target=\"_self\"\u003efree 14-day trial of Elastic Cloud\u003c/a\u003e today."}],"_metadata":{"uid":"csaeef45c65dcd5558"}}}],"publish_date":"2022-01-20T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Extract and analyze Cobalt Strike beacon payloads with Elastic","seo_description_l10n":"Learn how to extract Cobalt Strike beacon payloads from memory and use open source tools to analyze and group threat activity clusters.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltbf75d98adf3a9e45","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-11-22T21:26:52.053Z","updated_at":"2021-11-22T21:26:52.053Z","content_type":"image/png","file_size":"121441","filename":"illustration-radar-security.png","title":"illustration-radar-security.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-22T21:26:57.740Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf75d98adf3a9e45/619c0b1c1c5e9d77962cd96d/illustration-radar-security.png"},"title":"Bringing home the beacon (from Cobalt Strike)","title_l10n":"Bringing home the beacon (from Cobalt Strike)","updated_at":"2025-03-28T16:55:33.926Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/bringing-home-the-beacon-cobalt-strike","publish_details":{"time":"2025-03-28T16:55:39.228Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf114ba45d6024594","_version":27,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog post, we will look at how to get technical help on one of the Elastic community channels and the information you should include in your queries to get the most comprehensive answers.\n","author":["blt9e68c6310223dacc"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-08-10T13:35:57.485Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2febeec19b435e6f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 14pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 14pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThe Elastic community encompasses developers from different programming backgrounds, security practitioners, and product owners. Our products’ free and open nature helps users build on top and share their feedback with the user community and us at Elastic.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRecently, \u003c/span\u003e\u003ca href=\"https://ela.st/slack\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eElastic Slack Community\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e workspace has crossed 15K members, another active channel besides \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eDiscuss\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, \u003c/span\u003e\u003ca href=\"http://community.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eMeetups\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, and \u003c/span\u003e\u003ca href=\"https://www.youtube.com/c/officialelasticcommunity\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eYouTube\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, where community members engage actively to build and solve problems using Elastic’s products and solutions.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eFrom the creation of our Slack workspace, community members have participated in more than 35K discussions. More than 700 members actively participated every day in the last 30 days. Daily, more than 3,000 people actively participate in discussions on \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003ediscuss.elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, and more than 7,000 people watch our Community YouTube channel.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWe’re so glad that community members are using these channels to build and solve problems using Elastic’s products and solutions. But for those who are new to the community, what's the best way to ask for help or start a conversation?\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eIn this blog post, we will look at:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eHow to get technical help on one of the Elastic community channels\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThe information you should include in your queries to get the most comprehensive answers\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cp\u003e\u003c/p\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e[Related article: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/5-reasons-to-join-the-elastic-contributor-program\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003e5 Reasons to join the Elastic Contributor Program\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e]\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eHow can you get technical help on one of Elastic’s community channels?\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eYou can request help or suggestions on our discussion forums (\u003c/span\u003e\u003ca href=\"https://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003ediscuss.elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e) or \u003c/span\u003e\u003ca href=\"https://ela.st/slack\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eSlack workspace\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e. There are a few differences to keep in mind between each option.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch3\u003e\u003cspan style=\"color: rgb(67, 67, 67);\"\u003eElastic Discuss Forum\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/h3\u003e\u003cp style=\"font-size: 11pt;\"\u003eThe Elastic Discuss forum is extensive. It contains tags that mark your specific question, and sometimes, you might directly receive answers from Elasticians who wrote or worked on that feature. It allows you to ask longer questions, attach stack traces, etc. By asking a question on \u003ca href=\"http://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003ediscuss.elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e, you also make the question searchable for others via Google.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9e4d01b107fd74e2"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltffe90a2935cca901","ACL":{},"content_type":"image/png","created_at":"2022-08-10T14:47:37.637Z","created_by":"blt1dac765f65376b4a","file_size":"394166","filename":"1.png","parent_uid":null,"tags":[],"title":"1.png","updated_at":"2022-08-10T14:47:37.637Z","updated_by":"blt1dac765f65376b4a","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-15T13:00:00.081Z","user":"blt1dac765f65376b4a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltffe90a2935cca901/62f3c5095c954177895b0121/1.png"},"_metadata":{"uid":"csf2f529b3dc134827"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb29250d038aca0b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003e\u003cspan style=\"color: rgb(67, 67, 67);\"\u003eElastic Community Slack\u003c/span\u003e\u003cspan style=\"color: rgb(67, 67, 67);\"\u003e\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eSlack Workspace is a place to have conversations with other community members. There are channels dedicated to each Elastic Stack product and solutions like #stack-elasticsearch, #stack-kibana, and #observability. While Slack is not searchable by search engines, and the free version of Slack only allows storage of messages for the last 90 days, it lets you network with other community members efficiently and ties well into the widespread business use of Slack.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003ePlease remember that we try to answer as many questions as possible, but neither \u003c/span\u003e\u003ca href=\"http://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003ediscuss.elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e nor Slack guarantee any SLA. If you are a customer, the best way to get quick help is through \u003c/span\u003e\u003ca href=\"http://support.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003esupport.elastic.co\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"http://community.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eMeetups\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://www.youtube.com/c/officialelasticcommunity\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eYouTube\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e allow you to comment on events and videos. We reply to all the comments as soon as possible. However, for long-form discussions, \u003c/span\u003e\u003ca href=\"http://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003ediscuss.elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://ela.st/slack\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eSlack\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e are recommended.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat information should you include in your queries?\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eAs we rapidly develop and add more features, including beta/experimental features, we want to ensure that we are on the same page while answering your queries.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eHere are a few details you can provide to help us as we answer questions most effectively:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWhich product are you using, and which version?\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWhat are you performing on the product (i.e., provide step-wise details for efficient reproduction of the issue)?\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eWhat did you expect to happen instead?\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eList of third-party plugins being used\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cbr/\u003e\u003cspan style=\"font-size: 11pt;\"\u003eFor example, a sample question from \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003ediscuss.elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e could look like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc8297df6fd15bcdb"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltcf98b709d4f4b11f","ACL":{},"content_type":"image/jpeg","created_at":"2022-08-10T14:49:26.759Z","created_by":"blt1dac765f65376b4a","file_size":"343489","filename":"2.jpg","parent_uid":null,"tags":[],"title":"2.jpg","updated_at":"2022-08-10T14:49:26.759Z","updated_by":"blt1dac765f65376b4a","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-15T13:00:00.122Z","user":"blt1dac765f65376b4a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcf98b709d4f4b11f/62f3c576e894104b272598ff/2.jpg"},"_metadata":{"uid":"csb5e98ef52a5fd3e3"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt97aa3e751c05102f","ACL":{},"content_type":"image/jpeg","created_at":"2022-08-10T14:49:51.219Z","created_by":"blt1dac765f65376b4a","file_size":"261877","filename":"3.jpg","parent_uid":null,"tags":[],"title":"3.jpg","updated_at":"2022-08-10T14:49:51.219Z","updated_by":"blt1dac765f65376b4a","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-15T13:00:00.148Z","user":"blt1dac765f65376b4a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt97aa3e751c05102f/62f3c58f34f523580f110dfd/3.jpg"},"_metadata":{"uid":"cs6f76cc5f7327c664"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7981df72552e3e2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003eAs you can see, the \u003c/span\u003e\u003ca href=\"https://discuss.elastic.co/t/filebeat-elasticsearch-output-is-not-configured/283637\"\u003e\u003cspan style='font-size: 11pt;'\u003eproblem\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 11pt;'\u003e is explained with the relevant information needed for us to reply. Kindly anonymise the config or remove sensitive data — especially passwords!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003eLikewise, on Slack:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1e4e5a16123e7dc4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltf1ef119476501299","ACL":{},"content_type":"image/jpeg","created_at":"2022-08-10T14:50:40.104Z","created_by":"blt1dac765f65376b4a","file_size":"71352","filename":"4.jpg","parent_uid":null,"tags":[],"title":"4.jpg","updated_at":"2022-08-10T14:50:40.104Z","updated_by":"blt1dac765f65376b4a","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-15T13:00:00.068Z","user":"blt1dac765f65376b4a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf1ef119476501299/62f3c5c07e18987096abbc39/4.jpg"},"_metadata":{"uid":"cs0674f165f6ab9972"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs67fc4b2c4cb68de8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThe use case would be a welcome addition because Elasticsearch can be configured as a time series store or a search engine.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eThat being said, here are some best practices to keep in mind:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eAlways follow the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/community/codeofconduct\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eElastic Community Code of Conduct\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003ePlease do not tag any specific folks in the Discuss forum or Slack workspace.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 11pt;\"\u003eIf you are a customer, kindly use the relevant support channel. None of these community help channels offer you any kind of SLA.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eA growing and learning community\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003eI hope the above tips will serve you well in getting help from the vast Elastic community. And when you’re ready, stay connected by becoming a member on our community channels — and give back by helping others find answers to their questions!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csffe297e8ae3904b9"}}}],"publish_date":"2022-08-15T16:00:00.000Z","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"In this blog post, we will look at how to get technical help on one of the Elastic community channels and the information you should include in your queries to get the most comprehensive answers.","seo_image":null,"seo_title_l10n":"Getting Help on Elastic Community Channels"},"subtitle_l10n":"Newcomers to the Elastic community can access abundant resources to connect and find answers","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltb3c31c5b0260b469","ACL":{},"content_type":"image/jpeg","created_at":"2020-11-04T13:32:36.774Z","created_by":"blt458f9d272024a3ea","description":"","file_size":"54510","filename":"blog-thumb-careers-at-elastic.jpg","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-careers-at-elastic.jpg","updated_at":"2022-02-11T21:03:50.956Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:21.909Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb3c31c5b0260b469/600f179e0cb0aa0ffcdd5333/blog-thumb-careers-at-elastic.jpg"},"title":"How to get technical help on Elastic community channels","title_l10n":"How to get technical help on Elastic community channels","updated_at":"2025-03-28T16:55:05.961Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/getting-help-on-elastic-community-channels","publish_details":{"time":"2025-03-28T16:55:12.751Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf684fb92d679c9bc","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Using Threshold rules to create alerts on your alerts is a great way to maximize your analyst effectiveness without sacrificing visibility. By using these rules, security analysts spend less time investigating false positives.","author":["blt06048a64b0c2b959"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-08-31T22:17:14.464Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs815e3dca5bbc9ad2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs the Threat Detection and Response (TDR) team on Elastic’s internal Infosec team, one of our responsibilities is building, tuning, and maintaining the security detections used to find and stop attacks against Elastic systems. This includes the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e environment, which currently spans 50+ cloud regions and four different cloud providers ingesting more than 1.5 petabytes of data per day.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe also work very closely with our Incident Response team and the analysts triaging alerts so we can feel their pain when detections don’t work as intended. Within Elastic, we call ourselves Customer Zero and we always use the newest versions \u003c/span\u003e\u003ca href=\"https://www.elastic.co/downloads/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eof our products\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. We meet every week with the development teams that are building Elastic products to provide real-world feedback, bug reports, and feature requests to make our products better for customers and ourselves.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eThe problem with noisy rules\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFinding the true positives within the flood of alerts is one of the biggest challenges for any security operations center (SOC). Every SOC has finite resources for dealing with alerts. Most SOCs have expected response times for investigating an alert based on its severity.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor example, a critical severity alert could use PagerDuty to notify an analyst and require an investigation within minutes, while a low severity alert could be included in a daily report and require review within the next working day. The cost of investigating a false positive can increase dramatically with the severity of the alert. If your analysts are investigating a false positive, that’s time spent not investigating a true positive.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne of the best ways to reduce false positives is to update the rule logic or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/detections-ui-exceptions.html#detection-rule-exceptions\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eexception list\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to filter out the known false positive events. The challenge with filtering events is that you have to balance the goal of filtering out noise while still keeping the detection effective.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSometimes, depending on the environment, it’s impossible to completely filter out the false positives without reducing the usefulness of the detection rule. If you overly filter or disable your detection rules, you risk missing a real attack. However, if you leave them on and the alerts are noisy, the analysts will get overwhelmed and overworked. When this happens, they will suffer from alert fatigue. Alert fatigue can lead to analyst burnout, resulting in a higher turnover of personnel and increased risk of not detecting or responding to an attack in time.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThreat actors understand this and often use custom binaries or built-in commands to avoid detection and blend in with the noise. This technique is often referred to as “Living off the Land.” Elastic Security comes with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/prebuilt-rules.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emany built-in detection rules\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to detect these types of actions. The problem is that installed software, updates, admin scripts, and occasional user activity can often run the same commands as an attacker, setting off these alerts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you enable every prebuilt detection from Elastic or any other SIEM on a production network without filtering, you will immediately see the level of noise that SOC analysts have to deal with. You can reduce this noise by constantly tuning and adding exceptions to your detections, but it is impossible to get to zero false positives in a production environment without impacting visibility.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e[Related article: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/why-almost-half-of-organizations-want-to-replace-their-siem\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhy almost half of organizations want to replace their SIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e]\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eThe difference between true and false positives\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSomething the Elastic Infosec Detections team noticed was that, when the false positive alerts are caused by legitimate software or user activity, security analysts will often see a single alert being triggered multiple times on a host without any related alerts. When new software is installed in your network, you may see a single noisy detection rule creating the same alert hundreds of times on multiple hosts without any additional alerts being triggered on those hosts. When this happens, it’s likely that you aren’t under attack, you just need to add a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/detections-ui-exceptions.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enew exception\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to that rule to filter out the changes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn contrast, when you see a real threat or malware activity, it will often trigger several \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003edifferent\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e alerts on a single host or associated with a single user account as the attacker moves through the phases of the \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMITRE ATT\u0026CK\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e matrix corresponding to the attack lifecycle. If the attackers are trying to actively avoid detection, the alerts will often be low severity alerts that analysts don’t normally respond to immediately because they are noisy and resemble normal activity in the network.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs the attacker proceeds from initial access to privilege escalation, establishes persistence, impersonates users, scans internal networks for potential targets, moves laterally, and attempts to steal data from the network, they will set off many high, medium, and low severity alerts along the way.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou can see this behavior in the campaign and malware analysis posts published in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. These reports include the detection rules that are triggered by the threat actors at the end of each report, and there are almost always multiple different alerts. For example, in the recent \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/elastic-security-uncovers-blister-malware-campaign\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBlister malware campaign\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, the attacks potentially triggered five different prebuilt detections. Four of the five detections are medium or low severity and could be overlooked by analysts. However, when several different alerts go off on a single host, you will want to escalate the response to a high or critical severity. If you want to test this out yourself, you can see this by creating a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-build-a-malware-analysis-sandbox-with-elastic-security\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMalware Sandbox with Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and detonating malware on your test environment with the prebuilt rules enabled.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eA solution to having a faster response to this type of activity without overwhelming analysts is to use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-threshold-rule\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethreshold rules\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e within Elastic SIEM to create new alerts when there are multiple different types of alert per entity. To maximize analyst efficiency, we set the noisy rules to a low severity level and create a new high severity alert that the security analysts can prioritize once we have multiple different alerts on a single “entity.” An entity can be a host, a user, an IP address, etc.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe low severity alerts are reviewed in bulk within the SIEM, but we do not send Slack push notifications to the analysts each time a low severity alert triggers. The medium, high, and critical severity alerts use the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#rule-notifications\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eActions\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e feature to push notifications directly to the analysts via Slack. This lets us keep noisy rules enabled and useful without overburdening the analysts with constant push notifications and alarms. If we have a rule that is noisy but challenging to tune, we can keep it enabled but set to low severity.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eReal-world example: Detecting TLS break and inspect activity\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf a threat actor wants to collect the encrypted network traffic from a host, they will need to take multiple actions. The first step is to get between the process making the connection and the destination server. This can be done by using an implanted device (such as an infected router), or by configuring a proxy on the workstation. The next step is to install a root certificate on the host so the applications will trust the malicious proxy and not generate warnings and errors from untrusted certificates.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s prebuilt rules include a rule for MacOS systems to detect \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/webproxy-settings-modification.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emodifications being made to the WebProxy\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e settings. This detection rule will trigger any time a new WebProxy is configured to intercept web traffic from a host. Because there are many legitimate reasons to install proxy software on a system, this detection rule can have a high number of false positives. Often, VPN software will update the WebProxy settings every time the user joins or disconnects from a VPN. Even after filtering out many common VPN products, we still saw 200+ alerts for this rule from around 2,000 MacOS systems over the last year. Because there are so many legitimate reasons to change these settings, this rule should not be configured to send push notifications to SOC analysts. So, we set the severity of this rule to low.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnother prebuilt rule for MacOS will alert when there is an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/attempt-to-install-root-certificate.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAttempt to Install a Root Certificate\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Depending on the environment, this detection rule can generate a lot of false positives from legitimate software installing new root certificates. A common false positive is from document- or code-signing software installing their certificates. For this detection rule, we have seen around 250 alerts in the last year.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOn their own, each of these detection rules is low severity and causes many false positives. However, if both detections are seen on a single host within a 24h time period, there is a much higher chance that something is attempting to intercept the encrypted network traffic from the host. For these two detection rules, we made a special critical severity threshold rule that alerts us when both detections are observed on a single host within the last 24h.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOver the last year, this alert has only triggered once and it was a non-malicious true positive. In this case, it was a software developer installing an application that intercepts encrypted traffic to help troubleshoot a web application they were building. By using threshold rules, we were able to reduce the number of alerts pushed to analysts from 450+ to a single alert. We have included the detection rule below so you can create your own version.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eHow to use Threshold Rules to detect multiple alerts on a host\u003c/h2\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTo get started, navigate to the Rule Management page within the Security app and click \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eCreate New Rule\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Within the Rule creation interface, select Threshold to begin creating a new custom Threshold rule. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/rules-ui-create.html#create-threshold-rule\"\u003e\u003cspan style='font-size: 12pt;'\u003eThreshold Rules\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can be used to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-aggregations.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eaggregate\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e events and generate alerts based on the number of events matching a query exceeding a threshold, or when the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-aggregations-metrics-cardinality-aggregation.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ecardinality\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (number of unique values) is more than a certain value.\u003c/span\u003e"}],"_metadata":{"uid":"csc541a4b6373564f2"}}},{"image":{"image":{"uid":"blt7be7637e46f97f12","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:14:50.506Z","updated_at":"2022-08-31T22:14:50.506Z","content_type":"image/png","file_size":"284283","filename":"1.png","title":"1.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.025Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7be7637e46f97f12/630fdd5a847c967c7c96d38f/1.png"},"_metadata":{"uid":"cs14cd40c22b8a77dd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfb50b0ac89cea6a3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eSetting the index pattern\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll alerts in Elastic Security are written to an index so you can create alerts on your alerts. To do so, you will need to set the index pattern to use the \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003e.siem-signals-*\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e index. If you are using multiple Kibana Spaces with detection rules enabled, you will want to include the space name in the index pattern. For example, use \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003e.siem-signals-SPACENAME*\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e so you don’t mix alerts from different spaces.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eBuilding the Custom query\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter setting the index pattern, you will need to create a query to select only the rules you want to use in your aggregations. You can not leave this blank, so you will need to add a query that returns all of the detections you wish to aggregate. We chose to use the query \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003esignal.rule.name:*\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to do this. This query will return all alerts from the index. In addition to this base query, you will probably want to filter out certain events from the aggregation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt a minimum, you will need to filter out alerts from the threshold rule you are creating. If you don’t filter out these events, your threshold rule could alert on its own past alerts, which could lead to a noisy cascade of redundant alerts. Trust us, we learned this the hard way.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/p\u003e\u003cp\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you are aggregating on a field like \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003ehost.name\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e you will want to filter out alerts from filebeat agents collecting data such as AWS or Okta logs because all events from a filebeat agent have the \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003ehost.name\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e value of the host that filebeat is running on.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/p\u003e\u003cp\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou will want to filter out any events where your ‘Group by’ field doesn’t exist, otherwise you may have unrelated events that are grouped together because they will all have a \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003enull\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e value for that field.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/p\u003e\u003cp\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you want to exempt certain low risk rules from this rule, you could add logic to your query to limit results by \u003c/span\u003e\u003cspan style=\"color: rgb(85, 85, 85);font-size: 12pt;\"\u003erisk_score\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or any other field in the alerts.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaee985133bc9a60d"}}},{"image":{"image":{"uid":"blte3fe5f7f1805de4e","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:15:20.479Z","updated_at":"2022-08-31T22:15:20.479Z","content_type":"image/png","file_size":"65820","filename":"2.png","title":"2.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.030Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte3fe5f7f1805de4e/630fdd788bdc107d4a01c854/2.png"},"_metadata":{"uid":"cscf12948783a13e9d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8c3fb267e9f24a04"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eGroup by and cardinality fields\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter your query is created, \u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003euse the \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eGroup by\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e and \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eThreshold\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e fields to determine which source event field is used as a threshold and also the threshold’s value. For example, if \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eagent.id\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e and\u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003e host.name\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e are used with a threshold value of greater than or equal to 2, it will evaluate any group of alerts where the same\u0026nbsp; \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eagent.id\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e and\u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003e host.name\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e have generated two or more events during the time range of the query. The \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eCount\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e field is then used with the\u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003e signal.rule.name\u003c/span\u003e\u003cspan style='color:rgb(33, 37, 41);font-size: 12pt;'\u003e field to check if there are two or more different alerts on those matching events, and if so a new alert will be created.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs38e67c15ff9c96c3"}}},{"image":{"image":{"uid":"blt41246ab8750b3757","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:15:36.725Z","updated_at":"2022-08-31T22:18:47.917Z","content_type":"image/png","file_size":"62601","filename":"5.png","title":"3.png","ACL":{},"_version":2,"parent_uid":null,"is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.034Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41246ab8750b3757/630fde477066f57e88f6be44/5.png"},"_metadata":{"uid":"cs05fa6632cfd8c083"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbfdcb8e5e002cef4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eScheduling the detection\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter creating the logic of your query, you will need to give the rule a name, set the severity, add some documentation for how analysts should respond to the alerts, and set the schedule for how often the alert will run and how large of a time window will be queried each time.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cbr/\u003e\u003cspan style='font-size: 12pt;'\u003eWhen scheduling these alerts, the first option of \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eRuns every\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e will set how often the rule will run. The second option of \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003eAdditional look-back time\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e will help determine how large of a time window will be queried each time the rule is run. For example, if both options are set to 1 hour, the query will run every hour. Each time it runs, it will query the last 2 hours worth of events.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs35375ecbdbedcdee"}}},{"image":{"image":{"uid":"blt528fd59db1bbae91","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:15:56.412Z","updated_at":"2022-08-31T22:15:56.412Z","content_type":"image/png","file_size":"68581","filename":"4.png","title":"4.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.038Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt528fd59db1bbae91/630fdd9cc13d4a157590acea/4.png"},"_metadata":{"uid":"cs1c21aaeadeaa605b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3dd42ed8d22e828b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are trade-offs to having a larger or smaller lookback time that you will want to consider. Having a larger lookback window of 12 or 24 hours can help you catch the more stealthy attackers that are trying to blend in by going slow; but you have a higher chance of false positives from unrelated low severity alerts. Having a shorter time window of 1 or 2 hours will reduce the number of false positives and help you identify spikes of different alerts on a host; however, there is the chance that a very careful attacker could avoid detection.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou will need to experiment a little with different lookback times to determine one that works for your team and environment. The lookback time you use in your network will primarily be determined by the resources you have available to investigate alerts. If you have a small team, you can use a shorter lookback time to reduce false positives while still detecting spikes. If you have a larger response team, you can have a longer lookback time at the cost of more false positives. You can also create multiple versions of your rule with different lookback times and different severity levels.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eRecommended Threshold Rules\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLuckily, Elastic doesn’t limit the number of queries or detection rules you create. You can fully customize your experience and create several different threshold alerts in your SIEM to generate different detections for different scenarios, create rules with different look-back times and severity levels that fit with your processes, and you can create several threshold detections that group by other field names. Here are some recommended threshold rules that you could apply in your Elastic SIEM:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch3\u003eMultiple different alerts on a single\u003cspan style='color:rgb(85, 85, 85);'\u003e host.name\u003c/span\u003e\u003cspan style='color:rgb(67, 67, 67);'\u003e \u003c/span\u003eand\u003cspan style='color:rgb(67, 67, 67);'\u003e \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);'\u003eagent.id\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe use both the\u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003e agent.id\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003ehost.name\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e fields together for this detection because you will sometimes have multiple hosts with the same name.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf2d5f7a1ae1175e9"}}},{"image":{"image":{"uid":"blt9d09e41588a334b3","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:16:12.921Z","updated_at":"2022-08-31T22:16:12.921Z","content_type":"image/png","file_size":"62601","filename":"5.png","title":"5.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.045Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9d09e41588a334b3/630fddacc593ff7e8241a7fa/5.png"},"_metadata":{"uid":"csa859d481e3170960"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs53b45de7f2d57a79"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eMultiple different alerts on a single\u003cspan style='color:rgb(67, 67, 67);'\u003e \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);'\u003euser.id\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn a Windows domain, the \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003euser.id\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e field is the unique identifier for that user within the domain. This alert could identify a compromised account causing multiple different alerts to trigger. If you are collecting logs that contain the \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003euser.email\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e field such as Okta or AWS logs, you could make a version of this rule using \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003euser.email \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003efield instead.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6f9f8493d7fa665d"}}},{"image":{"image":{"uid":"blt97bf3ccb80b14435","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:16:29.700Z","updated_at":"2022-08-31T22:16:29.700Z","content_type":"image/png","file_size":"58750","filename":"6.png","title":"6.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.048Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt97bf3ccb80b14435/630fddbdc12c8404ed2a853e/6.png"},"_metadata":{"uid":"csc9d6e8de434d5cca"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs44c12a3db0925262"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eMultiple different \u003cspan style='color:rgb(85, 85, 85);'\u003ehost.name\u003c/span\u003e alerts on a single\u003cspan style='color:rgb(67, 67, 67);'\u003e \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);'\u003euser.id\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInstead of checking the \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003esignal.rule.name\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e field for cardinality, this rule uses the \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003ehost.name\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e field. This will alert you when a user’s account is triggering alerts on multiple different hosts in your network. This could be an indication of a compromised account being used for lateral movement. A common false positive could be an administrator or service account that is used to push out updates, so those may need to be filtered out in your query or exceptions, but do that with caution because then you may not detect it if one of those accounts is compromised.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2ac9248de4fc712a"}}},{"image":{"image":{"uid":"bltb06a87360125476a","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:16:46.454Z","updated_at":"2022-08-31T22:16:46.454Z","content_type":"image/png","file_size":"57082","filename":"7.png","title":"7.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.053Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb06a87360125476a/630fddce2d08277c7e733f2a/7.png"},"_metadata":{"uid":"cs41bd5d23176f3408"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6cce649bc7c87da7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eMultiple alerts with different destination.ip for a single source.ip\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you have alerts that use network data, you can use this threshold rule to create a new alert when a single \u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003esource.ip\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e has targeted two or more different\u003c/span\u003e\u003cspan style='color:rgb(85, 85, 85);font-size: 12pt;'\u003e destination.ip\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. This could be an indication of a network attack or scanning.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1dc74632ca2a0513"}}},{"image":{"image":{"uid":"bltcd1a1b485318ad46","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:17:01.817Z","updated_at":"2022-08-31T22:17:01.817Z","content_type":"image/png","file_size":"59291","filename":"8.png","title":"8.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.056Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcd1a1b485318ad46/630fdddd52174f0e0e96fe16/8.png"},"_metadata":{"uid":"cs4edcc36d2ab07f0d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0975e8d026c89fb9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch3\u003eDetecting TLS break and inspect activity\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis detection is the detection rule mentioned above and it works by alerting when both detection rules have been observed during the time window. Because this is looking for two specific detection rules, the time window can be set to a larger size without causing as many false positives.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9d37e5a8fbef4c4c"}}},{"image":{"image":{"uid":"blt96c53f4e44e57dea","created_by":"bltc87e8bcd2aefc255","updated_by":"bltc87e8bcd2aefc255","created_at":"2022-08-31T22:20:40.220Z","updated_at":"2022-08-31T22:20:40.220Z","content_type":"image/png","file_size":"158040","filename":"3.png","title":"3.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-09-09T16:07:20.061Z","user":"bltc87e8bcd2aefc255"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96c53f4e44e57dea/630fdeb852174f0e0e96fe1c/3.png"},"_metadata":{"uid":"cs526bb3e2d982631c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs98e705f1021b4b39"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003ch2\u003eConclusion\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsing Threshold Rules to create alerts on your alerts is a great way to maximize your analyst effectiveness without sacrificing visibility. We have found that by using these rules, our security analysts are spending less time investigating false positives and they are responding faster to the alerts that matter.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd10a27ee8c466908"}}}],"publish_date":"2022-09-07T07:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Maximizing analyst efficiency using Cardinality Threshold rules on your alerts","seo_description_l10n":"Using Threshold rules to create alerts on your alerts is a great way to maximize your analyst effectiveness without sacrificing visibility. By using these rules, security analysts spend less time investigating false positives.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"bltcaf8e3e614fb824e","ACL":{},"content_type":"image/png","created_at":"2022-08-02T15:55:47.372Z","created_by":"bltd9765be97bbed20c","file_size":"45509","filename":"blog-open-security-720x420-A.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-open-security-720x420-A.png","updated_at":"2022-08-02T15:55:47.372Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-01T16:33:59.870Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcaf8e3e614fb824e/62e949032a66d4760f00e2c9/blog-open-security-720x420-A.png"},"title":"Detection engineering — Maximizing analyst efficiency using Cardinality Threshold rules on your alerts","title_l10n":"Detection engineering — Maximizing analyst efficiency using Cardinality Threshold rules on your alerts","updated_at":"2025-03-28T16:54:41.327Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/detection-engineering-maximizing-analyst-efficiency-using-cardinality-threshold-rules-on-your-alerts-","publish_details":{"time":"2025-03-28T16:54:46.089Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd26447b476f84259","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"We recently had a tricky date formatting bug. This is the story of how we traced it back to an error in the JDK date formatting library (now fixed for Java 17 \u0026 18).","author":["blt685a3d05f0dde9cb"],"category":["blte5cc8450a098ce5e"],"created_at":"2021-10-14T14:01:07.926Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs543a86f5b208f60b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBuilding new features gets a lot of excitement, but fixing bugs is an equally important part of building a robust and trustworthy platform. We take even small bugs seriously, and sometimes small bugs lead to surprising places. This is the story of how following a rare test failure led to finding a subtle but real bug in how Java formats date-time values.\u003c/p\u003e\u003ch2\u003eHow we got here\u003c/h2\u003e\n\u003cp\u003eElasticsearch has a feature called Composite Aggregation, which can be used to paginate through aggregation results. It uses a fairly standard pattern for this, where each response includes an “after key”, which is a human readable key (as opposed to a hash value, like the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.14/scroll-api.html\"\u003escroll API\u003c/a\u003e uses) representing the last bucket the aggregation returned in that call. The caller then passes that key back to the next call, and the aggregation picks up at that point. Having the key human readable helps a lot in debugging, and allows for some fancy tricks if you’re feeling cheeky. But it also requires formatting.\u003c/p\u003e\n\u003cp\u003eWe got some weird bugs reported where composite aggregations would “get stuck”, meaning the caller would pass in the after key composite had returned, but get back the same page and after key as they had already gotten. What gives?\u003c/p\u003e\n\u003cp\u003eDate formatting is what gives. It turns out some date formats weren’t “round tripping” correctly; that is to say, the formatted string didn’t parse back to the original value. At first glance, it might seem like every format should be able to round trip correctly, but in practice that isn’t true. For example, in \u003ca href=\"https://github.com/elastic/elasticsearch/issues/72556\"\u003e#72556\u003c/a\u003e, the caller sent the sensible-looking format \u003ccode\u003eYYYY-MM-dd\u003c/code\u003e but that uses \u003ca href=\"https://docs.oracle.com/javase/8/docs/api/java/time/temporal/WeekFields.html#weekBasedYear--\"\u003eweek-based-year\u003c/a\u003e; month-based-year is lowercase \u003ccode\u003eyyyy\u003c/code\u003e. Java is happy to print a week-based-year followed by a month, since it can compute both of those from the internal representation. But when parsing, it doesn’t know how to place a month in a week-based-year, and instead of throwing, it defaults everything it can’t parse to 1. So we’d always get back January 1st of whatever year we initially formatted.\u003c/p\u003e\n\u003cp\u003eIt’s hard to look at a format in isolation and tell if it will round trip correctly, especially since it may depend on the value being formatted. So we did the next best thing. When we go to write the after key in Composite, we \u003ca href=\"https://github.com/elastic/elasticsearch/pull/74252\"\u003etest if we can round trip the exact value we’re trying to write\u003c/a\u003e. If we can’t round trip the value exactly, we fail the query. This prevents a key we can’t parse from creating more problems down the line, like causing a client to miss data or loop forever (following the principle of “Crash Early”).\u003c/p\u003e\n\u003cp\u003eWe also had \u003ca href=\"https://github.com/elastic/elasticsearch/issues/68963\"\u003ea bug\u003c/a\u003e around using epoch_seconds format with composite, which we wanted to support. So as a prerequisite to the round trip check, we added what turned out to be a pretty \u003ca href=\"https://github.com/elastic/elasticsearch/pull/73955\"\u003eeasy fix\u003c/a\u003e for that, and some testing around it. One of my favorite things about working at Elastic is our \u003ca href=\"https://www.elastic.co/blog/elasticsearch-testing-qa-increasing-coverage-randomizing-test-runs\"\u003erobust testing toolkit\u003c/a\u003e. In this example, we made it very easy to write tests that randomize their sample data, and since it was easy, that’s what I did when I wrote it. Turns out that was a good idea.\u003cbr\u003e\u003c/p\u003e\u003ch2\u003eAn unexpected test failure\u003c/h2\u003e\n\u003cp\u003eWe merged the fixes from above, and everything was good for a few weeks. Then, \u003ca href=\"https://github.com/elastic/elasticsearch/issues/75594\"\u003ethe test failed\u003c/a\u003e. It was strange - the failure reproduced locally sometimes, but not others. Eventually, we realized two things: First, that it was flaky depending on if the JVM in question had received the \u003ca href=\"https://mm.icann.org/pipermail/tz-announce/2020-October/000059.html\"\u003e2020b timezone update\u003c/a\u003e, which corrected the time zone for Antarctica/Macquarie, which the test had randomly selected; and second, that the update had moved Antarctica/Macquarie into a time zone that experienced \u003ca href=\"https://en.wikipedia.org/wiki/Daylight_saving_time\"\u003eDaylight Savings Time\u003c/a\u003e. Anything DST related is immediately suspect, and we quickly reproduced the failure with any DST transition where the local time moves back.\u003c/p\u003eOnce we knew how to reproduce the bug, I wrote a unit test case that just did that and threw it in the debugger. I knew we had some \u003ca href=\"https://github.com/elastic/elasticsearch/blob/b7c5293228c32208c267d5ce082f114129163e43/server/src/main/java/org/elasticsearch/common/time/EpochTime.java\"\u003ecustom code around epoch values\u003c/a\u003e, and that was my first suspect. We have an anonymous class method \u003ca href=\"https://github.com/elastic/elasticsearch/blob/b7c5293228c32208c267d5ce082f114129163e43/server/src/main/java/org/elasticsearch/common/time/EpochTime.java#L80-L96\"\u003eMILLIS#resolve()\u003c/a\u003e which looked promising. That’s where we convert milliseconds-since-epoch, which Elasticsearch likes to use internally for dates, to seconds + nanoseconds, which Java likes to use internally for dates. My theory was somehow we were messing this up. So I put some breakpoints in, and stepped through that method, but at the end of it, the \u003ccode\u003efieldValues\u003c/code\u003e map (which is sort of the scratch pad for Java’s date parsing) had the right values in it. I hit the “resume program” button to run to my next breakpoint. When I got there, I looked at my \u003ccode\u003efieldValues\u003c/code\u003e map again, and my correct value had changed! Now it showed the incorrect value.\u003cbr\u003e\u003cbr\u003e\u003ch2\u003eWhatever remains, however unlikely\u003c/h2\u003e\n\u003cp\u003eIt’s hard to suspect that a core component of a widely used, extremely well tested system is the root cause of a bug. You know in your heart of hearts that it’s probably not broken, and you’re probably just calling it wrong. I think every senior developer has probably cried wolf about a library being broken at some point, and \u003ca href=\"https://stackoverflow.com/questions/7065164/how-to-make-a-timezone-aware-datetime-object-in-python#comment8453142_7065242\"\u003efelt quite silly\u003c/a\u003e to learn they were doing it wrong. I wanted to be fully confident this wasn’t something we were doing.\u003c/p\u003e\n\u003cp\u003eI took a look at \u003ccode\u003ejava.time.format.Parsed#resolve()\u003c/code\u003e. Hmm, what’s this ResolverStyle parameter? It has a strict mode and we’re not using it. That must be the problem. But it wasn’t. So I threw some breakpoints on it and ran the debugger again. Just like before, our \u003ccode\u003eMILLIS#resolve()\u003c/code\u003e code put the right value for \u003ccode\u003eINSTANT_SECONDS\u003c/code\u003e in the map. Then we entered \u003ccode\u003eParsed#resolveFields()\u003c/code\u003e and something strange happened. It took \u003ccode\u003eINSTANT_SECONDS\u003c/code\u003e out of the map, and created a zoned date time. It had a timezone, \u003ccode\u003eAmerica/New_York\u003c/code\u003e, but it didn’t have a UTC offset. Strange. Without the offset, it had converted our unambiguous \u003ccode\u003eINSTANT_SECONDS\u003c/code\u003e value to an ambiguous value (That is to say, a local time that occurs twice. For example in the \u003ccode\u003eAmerica/New_York\u003c/code\u003e time zone, the time 2020-11-01 01:00:00 occurs twice, once at UTC+5 and once at UTC+4. We say this time is ambiguous, since just from the time and zone, it isn’t clear which is meant.) A few lines later, \u003ccode\u003eresolveInstant()\u003c/code\u003e put \u003ccode\u003eINSTANT_SECONDS\u003c/code\u003e back on the map, but with the wrong value. Since the zoned date time was ambiguous, it just picked the lower value, which was wrong in this case (and also explained why transitions that moved the clock forward didn’t break). There was our bug.\u003c/p\u003e\n\u003cp\u003eFrom there it wasn’t hard to recreate the problem using just the core JDK. I had to switch from milliseconds to seconds, but otherwise it followed very logically. I tried a few adjacent cases and they didn’t have this issue. I stuffed my work in \u003ca href=\"https://gist.github.com/not-napoleon/7b3adbea80f3fafe16ebae001586a763\"\u003ea gist\u003c/a\u003e and floated it around the team to see if anyone saw something I’d missed. I got some feedback on how best to present the issue, and submitted a \u003ca href=\"https://bugs.openjdk.java.net/browse/JDK-8272473\"\u003eJDK bug\u003c/a\u003e, my first ever (achievement unlocked?). Two weeks later, they fixed it.\u003c/p\u003e\u003ch2\u003eLessons Learned\u003c/h2\u003e\n\u003cp\u003eThere are a few takeaways and things to learn from this experience. First, always test your edge cases, and DST transitions are definitely an edge case for anything having to do with time zones. We could have caught this sooner if we’d done that. Second, test your contracts. We found this because we said to ourselves “The formatter should be able to round trip,” and then we tested that. Third, randomized testing is amazing, it finds edge cases you never thought to look for. Finally, sometimes the library \u003cstrong\u003eis\u003c/strong\u003e broken. Extraordinary claims require extraordinary evidence, but that doesn’t mean they’re wrong.\u003c/p\u003e\n\u003cp\u003eIf this kind of deep dive bug hunting appeals to you, check out our \u003ca href=\"https://www.elastic.co/about/careers/\"\u003ecareers page\u003c/a\u003e and see if you’d like to come work with us.\u003c/p\u003e\n\u003cp\u003e___________________________\u003csup\u003e\u003cbr\u003e\u003c/sup\u003e\u003c/p\u003e\n\u003cp\u003e\u003csup\u003e1\u003c/sup\u003e See \u003cem\u003eThe Pragmatic Programmer\u003c/em\u003e by Andrew Hunt \u0026 Dave Thomas, page 120\u003c/p\u003e"}],"_metadata":{"uid":"csa36a129a673b5fa3"}}}],"publish_date":"2021-10-14T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Elastic traced a formatting bug in Elasticsearch","seo_description_l10n":"We recently had a tricky date formatting bug. This is the story of how we traced it back to an error in the JDK date formatting library (now fixed for Java 17 \u0026 18).","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt4042407cc73afed2","created_by":"bltf6ab93733e4e3a73","updated_by":"bltf6ab93733e4e3a73","created_at":"2020-06-24T04:21:28.961Z","updated_at":"2020-06-24T04:21:28.961Z","content_type":"image/png","file_size":"30628","filename":"blog-thumb-search-charts.png","title":"blog-thumb-search-charts.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T18:04:18.610Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4042407cc73afed2/5ef2d4c87253820a4364f310/blog-thumb-search-charts.png"},"title":"How Elastic traced a formatting bug in Elasticsearch","title_l10n":"How Elastic traced a formatting bug in Elasticsearch","updated_at":"2025-03-28T16:51:54.727Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/how-elastic-traced-a-formatting-bug-in-elasticsearch","publish_details":{"time":"2025-03-28T16:51:59.897Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb4cd51f42b5f0139","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"The Elastic Certified Engineer Exam is one of several certifications available to users of Elastic products. Learn about tips and resources to help you prepare for and succeed with the exam.","author":["blt265422bc68364b2e"],"category":["bltc253e0851420b088"],"created_at":"2022-07-27T19:20:56.059Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9f82122f56b8f611"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eGaining certifications in key technologies is a great way for developers to showcase their skills and progress in their technology careers. The \u003ca href=\"https://www.elastic.co/training/elastic-certified-engineer-exam\" target=\"_self\"\u003eElastic Certified Engineer exam\u003c/a\u003e is one of several certifications that users of Elastic products can complete to flaunt their skills.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eJust like back in school, preparing for certification exams can be a nerve-wracking experience — as members of our community can attest.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eAs a new community advocate, I have been learning about the latest Elastic products, as well as drawing on my previous developer experience on how I would use them. Here I share tips and resources that can help set you up for success with the Elastic Certified Engineer exam.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e[Related article: \u003ca href=\"/blog/becoming-an-elastic-certified-engineer-pays-dividends\" target=\"_self\"\u003eBecoming an Elastic Certified Engineer pays dividends\u003c/a\u003e]\u003c/p\u003e\u003ch2\u003e1) Embrace using multiple content formats\u003c/h2\u003e\u003cp\u003eEveryone processes information at different speeds and via different mediums. Perhaps in your school years, you happily recalled full pages of the textbook you read last week but were unlikely to remember concepts discussed in classroom lectures. Or perhaps like me, learning through practical labs and experimentation works better for you. The reality of learning all technologies, including Elasticsearch, is that using a mixture of resources and practical applications is the best way to go.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eIf you are an established practitioner, building an application using Elasticsearch will likely be the most effective way for you. Perhaps you'll follow in our founder Shay's footsteps and build out a pet project, such as a \u003ca href=\"https://www.elastic.co/about/history-of-elasticsearch\" target=\"_self\"\u003erecipe app\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eFor those just starting out, consider the \u003ca href=\"https://www.elastic.co/training/elasticsearch-engineer\" target=\"_self\"\u003eElasticsearch Engineer training\u003c/a\u003e, which is available in virtual or on-demand formats. This course contains a mixture of video content and lab exercises to give you practical experience using Elasticsearch. Although it might be tempting to try and multitask, don't watch videos and do the labs at the same time. You will find, as I did, that the concepts will not sink in! Instead, consider writing notes of the key points as you go along. This process of encoding the information in your own voice can help reinforce concepts and improve recall.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eEngaging with or contributing to the Elastic community is another valid study tool. Contributing content is a great way to research topics and build a more detailed understanding. Many materials produced by the Community team, or our wide community of Elastic users across the world, can help you find different voices to reinforce your learning. There are many ways to get involved, including:\u0026nbsp;\u003c/p\u003e\u003cul\u003e\u003cli\u003eAsking or answering questions on \u003ca href=\"https://ela.st/slack\" target=\"_self\"\u003eSlack\u003c/a\u003e or \u003ca href=\"https://discuss.elastic.co/\" target=\"_self\"\u003eDiscuss\u003c/a\u003e\u003c/li\u003e\u003cli\u003eWatching content on our YouTube channel, including the \u003ca href=\"https://www.youtube.com/playlist?list=PL_mJOmq4zsHZYAyK606y7wjQtC0aoE6Es\" target=\"_self\"\u003eBeginners Crash Course to Elasticsearch\u003c/a\u003e\u003c/li\u003e\u003cli\u003eAttending a \u003ca href=\"https://community.elastic.co/\" target=\"_self\"\u003emeetup or event\u003c/a\u003e online or near you!\u003c/li\u003e\u003cli\u003eSharing personal content and contributions via the \u003ca href=\"https://www.elastic.co/community/contributor\" target=\"_self\"\u003eElastic Contributor Program\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eI have definitely found using a mixture of content, attending a couple of events, and asking colleagues questions have been beneficial for my own learning. Check out the full list of resources at the end of this post to find some useful learning and exam preparation content.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e[Related article: \u003ca href=\"/blog/5-reasons-to-join-the-elastic-contributor-program\" target=\"_self\"\u003e5 Reasons to join the Elastic Contributor Program\u003c/a\u003e]\u003c/p\u003e\u003ch2\u003e2) Practice, practice, practice!\u003c/h2\u003e\u003cp\u003ePractice makes perfect! There are many exercises you can try out to gain practice on the Elastic stack. If you sign up for the training course, you may want to try the exercises more than once to reinforce your knowledge.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eMany practice exercises are mentioned in \u003ca href=\"https://www.youtube.com/watch?v=JR-6LM3e5_M\" target=\"_self\"\u003eAcing the Elastic Certified Engineer Exam\u003c/a\u003e. Be sure to check the version of Elasticsearch and then overlap with the current course syllabus as well to ensure these resources cover all topics in the exam.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eIrrespective of the exercises undertaken, if you devised a different solution, but obtained the same answer, that’s OK! Make sure to check that the results match, and also try out the suggested solution to reinforce the different approaches. Consider if your solution is optimal. For example, when writing Elasticsearch queries and aggregations over a subset of data, using a filter over match queries will be more efficient \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-cache.html\" target=\"_self\"\u003edue to how query caching works in Elasticsearch\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhen answering questions, type out the queries in labs or exercises rather than copy-pasting samples from the documentation. This is a good technique for building up muscle memory for writing the commands in the exam. It's also important to learn the shortcuts for the Kibana Console, located under Dev Tools, such as keyboard commands, documentation shortcuts, and auto-indentation.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhen completing practice exercises, consider trying them under as close to exam conditions as possible. Try setting yourself a similar time limit to keep track of your pace. Be mindful of the environment you will need to take the exam in, such as the use of a single monitor with a webcam, microphone, speakers, and a clean desk.\u0026nbsp;\u003c/p\u003e\u003ch2\u003e3) Try to correct errors on your own first\u003c/h2\u003e\u003cp\u003eThrough your practice, it's inevitable that you will encounter error messages and make mistakes when writing queries. Developers tend to build strong searching skills with their favorite search engine, allowing them to quickly find the answer to these error messages.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eLack of access to a search engine in your exam will make it challenging to diagnose issues with your solution if you default to this problem-solving approach. Try to read and diagnose issues yourself over defaulting to entering the error message into your favorite search engine, and make sure you are comfortable navigating the Elastic documentation for the version of Elasticsearch used in the exam.\u003c/p\u003e\u003ch2\u003e4) Embrace sleep and Space, Time\u003c/h2\u003e\u003cp\u003eWith any certification, there is much to learn. Anyone new to Elasticsearch will find there is a lot to cover — as has been my experience as a new Elastician. All of us reach a limit on the amount of information we can cram into our brains at one time.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eEven if you have already scheduled your exam and are faced with that looming deadline, or you’re waiting to schedule the exam when you feel more comfortable, it's important to look after yourself while preparing. Especially if you are revising alongside your day job responsibilities and deadlines. Embrace the Space, Time element of the \u003ca href=\"https://www.elastic.co/about/our-source-code\" target=\"_self\"\u003eElastic Source Code\u003c/a\u003e and ensure you have clear study blocks, regular breaks to digest the content, and a good night's sleep to give you time to dream. I have found Elastic’s Shut It Down Days have been a welcome space for me to process my own learnings.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2\u003e5) Validate you have covered all possible exam topics\u003c/h2\u003e\u003cp\u003eBefore the exam, check the topics within the agenda to be sure you have covered them in your learning. Ensure you are comfortable with what the terms are and which screens or API calls they may refer to.\u003c/p\u003e\u003ch2\u003e6) Reach out to the Certifications team for help\u003c/h2\u003e\u003cp\u003eAs your exam date looms closer, you may have questions about logistics. For individuals with disabilities, accommodations or extra time can be arranged. I’ve found that many logistical questions are covered in \u003ca href=\"https://www.youtube.com/watch?v=9UpB-s_ZfNE\" target=\"_self\"\u003ePreparing for the Elastic Certified Engineer Exam - Get Elasticsearch Certified\u003c/a\u003e. Our Certifications team is always happy to help with any clarifications that are needed. Reach out to \u003ca href=\"mailto:certifications@elastic.co\" target=\"_self\"\u003ecertifications@elastic.co\u003c/a\u003e for help.\u0026nbsp;\u003c/p\u003e\u003ch2\u003e7) Celebrate when you pass!\u003c/h2\u003e\u003cp\u003ePassing the Elastic Certified Engineer exam is a huge achievement. All that hard work has paid off. It might feel natural to immediately start planning for one of the other certifications, such as the \u003ca href=\"https://www.elastic.co/training/elastic-certified-analyst-exam\" target=\"_self\"\u003eElastic Certified Analyst\u003c/a\u003e or \u003ca href=\"https://www.elastic.co/training/elastic-certified-observability-engineer\" target=\"_self\"\u003eElastic Certified Observability Engineer\u003c/a\u003e. But it’s important to enjoy the moment. Once you get there, take time to celebrate the win, share your achievement, and give yourself a well-deserved break.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eI just passed the exam recently. Upon reading the news, I celebrated with a victory dance and dinner out with my family.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eGood luck!\u003c/p\u003e"}],"_metadata":{"uid":"cs60e330f2af96060c"}}},{"callout":{"title_l10n":"Resources","_metadata":{"uid":"cs4a3a9f18679b855a"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"/training/elastic-certified-engineer-exam\" target=\"_self\"\u003eElastic Certified Engineer Exam\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/training/elastic-certified-analyst-exam\" target=\"_self\"\u003eElastic Certified Analyst\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/training/elastic-certified-observability-engineer\" target=\"_self\"\u003eElastic Certified Observability Engineer\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/training/certification/faq\" target=\"_self\"\u003eElastic Certification FAQ\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/index.html\" target=\"_self\"\u003eElastic Documentation\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/training/\" target=\"_self\"\u003eTraining\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/community/\" target=\"_self\"\u003eElastic Community\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/training/free\" target=\"_self\"\u003eElastic Quick Starts and How-tos\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.youtube.com/playlist?list=PL_mJOmq4zsHZYAyK606y7wjQtC0aoE6Es\" target=\"_self\"\u003eBeginners Crash Course to Elasticsearch\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/community/contributor\" target=\"_self\"\u003eElastic Contributor Program\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.youtube.com/watch?v=9UpB-s_ZfNE\" target=\"_self\"\u003ePreparing for the Elastic Certified Engineer Exam- Get Elasticsearch Certified\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.youtube.com/watch?v=JR-6LM3e5_M\" target=\"_self\"\u003eAcing the Elastic Certified Engineer Exam\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}}],"publish_date":"2022-08-01","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"","seo_image":null,"seo_title_l10n":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt941960cc2498f467","_content_type_uid":"tags_culture"},{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blte747a556bf93c462","ACL":{},"content_type":"image/png","created_at":"2022-07-27T19:33:43.178Z","created_by":"bltd9765be97bbed20c","file_size":"87035","filename":"blog-certificate-720x420.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-certificate-720x420.png","updated_at":"2022-07-27T19:33:43.178Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-01T13:00:00.112Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte747a556bf93c462/62e193176ab9c47806f8e19d/blog-certificate-720x420.png"},"title":"7 tips and tricks for preparing for the Elastic Certified Engineer Exam","title_l10n":"7 tips and tricks for preparing for the Elastic Certified Engineer Exam","updated_at":"2025-03-28T16:51:19.481Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/7-tips-and-tricks-for-preparing-for-the-elastic-certified-engineer-exam","publish_details":{"time":"2025-03-28T16:51:25.064Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd56d1086bbf2d136","_version":31,"locale":"en-us","ACL":{},"abstract_l10n":"Get metrics and logs from your AWS deployment and Elastic Observability in just minutes! We’ll show you how to use Elastic integrations to quickly monitor and manage the performance of your applications and AWS services to streamline troubleshooting.","author":["blt19aa6eaf05f480b6"],"category":["bltb79594af7c5b4199"],"created_at":"2022-11-21T18:42:23.776Z","created_by":"bltd9765be97bbed20c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cseef28842283fbbeb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe transition to distributed applications is in full swing, driven mainly by our need to be “always-on” as consumers and fast-paced businesses. That need is driving deployments to have more complex requirements along with the ability to be globally diverse and rapidly innovate.\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eCloud is becoming the de facto deployment option for today’s applications. Many cloud deployments choose to host their applications on AWS for the globally diverse set of regions it covers and the myriad of services (for faster development and innovation) available, as well as to drive operational and capital costs down. On AWS, development teams are finding additional value in migrating to Kubernetes on Amazon EKS, testing out the latest serverless options, and improving traditional, tiered applications with better services.\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eElastic Observability offers 30 out-of-the-box integrations for AWS services with more to come.\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eA quick review highlighting some of the integrations and capabilities can be found in a previous post:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"/blog/elastic-and-aws-seamlessly-ingest-logs-and-metrics-into-a-unified-platform-with-ready-to-use-integrations\" target=\"_self\"\u003eElastic and AWS: Seamlessly ingest logs and metrics into a unified platform with ready-to-use integrations\u003c/a\u003e.\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eSome additional posts on key AWS service integrations on Elastic are:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"/blog/observability-apm-aws-lambda-serverless-functions\" target=\"_self\"\u003eAPM (metrics, traces and logs) for serverless functions on AWS Lambda with Elastic\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/blog/elastic-and-aws-serverless-application-repository-speed-time-to-actionable-insights-with-frictionless-log-ingestion-from-amazon-s3\" target=\"_self\"\u003eLog ingestion from AWS Services into Elastic via serverless forwarder on Lambda\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/blog/new-elastic-and-amazon-s3-storage-lens-integration-simplify-management-control-costs-and-reduce-risk\" target=\"_self\"\u003eElastic’s Amazon S3 Storage Lens Integration: Simplify management, control costs, and reduce risk\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/blog/elastic-cloud-with-aws-firelens-accelerate-time-to-insight-with-agentless-data-ingestion\" target=\"_self\"\u003eIngest your container logs into Elastic Cloud with AWS FireLens\u003c/a\u003e\n \u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eA full list of AWS integrations can be found in Elastic’s online documentation:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"https://docs.elastic.co/en/integrations/aws\" target=\"_self\"\u003eFull list of AWS integrations\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eIn addition to our native AWS integrations, Elastic Observability aggregates not only logs but also metrics for AWS services and the applications running on AWS compute services (EC2, Lambda, EKS/ECS/Fargate). All this data can be analyzed visually and more intuitively using Elastic’s advanced machine learning capabilities, which help detect performance issues and surface root causes before end users are affected.\u003c/p\u003e\n\u003cp\u003eFor more details on how Elastic Observability provides application performance monitoring (APM) capabilities such as service maps, tracing, dependencies, and ML based metrics correlations:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003ca href=\"/blog/apm-correlations-elastic-observability-root-cause-transactions\" target=\"_self\"\u003eAPM correlations in Elastic Observability: Automatically identifying probable causes of slow or failed transactions\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/blog/elastic-and-aws-get-the-most-value-from-your-data-sets\" target=\"_self\"\u003eElastic and AWS: Get the most value from your data sets\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eThat’s right, Elastic offers metrics ingest, aggregation, and analysis for AWS services and applications on AWS compute services (EC2, Lambda, EKS/ECS/Fargate). Elastic is more than logs — it offers a unified observability solution for AWS environments.\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eIn this blog, I’ll review how Elastic Observability can monitor metrics for a simple AWS application running on AWS services which include:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eAWS EC2\u003c/li\u003e\n \u003cli\u003eAWS ELB\u003c/li\u003e\n \u003cli\u003eAWS RDS (AuroraDB)\u003c/li\u003e\n \u003cli\u003eAWS NAT Gateways\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eAs you will see, once the integration is installed, metrics will arrive instantly and you can immediately start reviewing metrics.\u003c/p\u003e\n"},{"title_l10n":"Prerequisites and config","_metadata":{"uid":"csae5ea2ec31959044"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIf you plan on following this blog, here are some of the components and details we used to set up this demonstration:\u003c/p\u003e\u003cul\u003e\u003cli\u003eEnsure you have an account on \u003ca href=\"http://cloud.elastic.co\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e and a deployed stack (\u003ca href=\"https://www.elastic.co/guide/en/elastic-stack/current/installing-elastic-stack.html\" target=\"_self\"\u003esee instructions here\u003c/a\u003e).\u003c/li\u003e\u003cli\u003eEnsure you have an AWS account with permissions to pull the necessary data from AWS. \u003ca href=\"https://docs.elastic.co/en/integrations/aws#aws-permissions\" target=\"_self\"\u003eSee details in our documentation\u003c/a\u003e.\u003c/li\u003e\u003cli\u003eWe used \u003ca href=\"https://github.com/aws-samples/aws-three-tier-web-architecture-workshop\" target=\"_self\"\u003eAWS’s three tier app\u003c/a\u003e and installed it as instructed in git.\u003c/li\u003e\u003cli\u003eWe’ll walk through installing the general \u003ca href=\"https://docs.elastic.co/en/integrations/aws\" target=\"_self\"\u003eElastic AWS Integration\u003c/a\u003e, which covers the four services we want to collect metrics for.\u003cbr /\u003e(\u003ca href=\"https://docs.elastic.co/en/integrations/aws#reference\" target=\"_self\"\u003eFull list of services supported by the Elastic AWS Integration\u003c/a\u003e)\u003c/li\u003e\u003cli\u003eWe will \u003cem\u003enot\u003c/em\u003e cover application monitoring given other blogs cover application \u003ca href=\"https://www.elastic.co/observability/aws-monitoring\" target=\"_self\"\u003eAWS monitoring\u003c/a\u003e (metrics, logs, and tracing). Instead we will focus on how AWS services can be easily monitored.\u003c/li\u003e\u003cli\u003eIn order to see metrics, you will need to load the application. We’ve also created a playwright script to drive traffic to the application.\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Three tier application overview","_metadata":{"uid":"cs892b6c3d62a53c95"},"header_style":"H2","paragraph_l10n":"\n\u003cp\u003eBefore we dive into the Elastic configuration, let's review what we are monitoring. If you follow the instructions for \u003ca href=\"https://github.com/aws-samples/aws-three-tier-web-architecture-workshop\" target=\"_self\"\u003eaws-three-tier-web-architecture-workshop\u003c/a\u003e, you will have the following deployed.\u003c/p\u003e"}],"_metadata":{"uid":"cs4548cb9ce976d900"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt224d9426e0bf65de","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:23:25.665Z","created_by":"bltd9765be97bbed20c","file_size":"161680","filename":"blog-elastic-three-tier.png","parent_uid":null,"tags":[],"title":"blog-elastic-three-tier.png","updated_at":"2022-11-21T18:23:25.665Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.112Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt224d9426e0bf65de/637bc21d32130110b279af80/blog-elastic-three-tier.png"},"_metadata":{"uid":"cs6d8bb9cf8e3a2294"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs85beaa8ac92ebd7a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhat’s deployed:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e1 VPC with 6 subnets\u003c/li\u003e\n \u003cli\u003e2 AZs\u003c/li\u003e\n \u003cli\u003e2 web servers per AZ\u003c/li\u003e\n \u003cli\u003e2 application servers per AZ\u003c/li\u003e\n \u003cli\u003e1 External facing application load balancer\u003c/li\u003e\n \u003cli\u003e1 Internal facing application load balancer\u003c/li\u003e\n \u003cli\u003e2 NAT gateways to manage traffic to the application layer\u003c/li\u003e\n \u003cli\u003e1 Internet gateway\u003c/li\u003e\n \u003cli\u003e1 RDS Aurora DB with a read replica\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eAt the end of the blog, we will also provide a Playwright script to implement to load this app. This will help drive metrics to “light up” the dashboards.\u003c/p\u003e\n"},{"title_l10n":"Setting it all up","_metadata":{"uid":"csc0f2787f916c1650"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLet’s walk through the details of how to get the application, AWS integration on Elastic, and what gets ingested.\u003c/p\u003e"},{"title_l10n":"Step 0: Load up the AWS Three Tier application and get your credentials","_metadata":{"uid":"cs14c1a6a98212a368"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eFollow the instructions listed out in \u003ca href=\"https://github.com/aws-samples/aws-three-tier-web-architecture-workshop\" target=\"_self\"\u003eAWS’s Three Tier app\u003c/a\u003e and instructions in the workshop link on git. The workshop is listed \u003ca href=\"https://catalog.us-east-1.prod.workshops.aws/workshops/85cd2bb2-7f79-4e96-bdee-8078e469752a/en-US\" target=\"_self\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eOnce you’ve installed the app, get credentials from AWS. This will be needed for Elastic’s AWS integration.\u003c/p\u003e\u003cp\u003eThere are several options for credentials:\u003c/p\u003e\u003cul\u003e\u003cli\u003eUse access keys directly\u003c/li\u003e\u003cli\u003eUse temporary security credentials\u003c/li\u003e\u003cli\u003eUse a shared credentials file\u003c/li\u003e\u003cli\u003eUse an IAM role Amazon Resource Name (ARN)\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eFor more details on specifics around necessary \u003ca href=\"https://docs.elastic.co/en/integrations/aws#aws-credentials\" target=\"_self\"\u003ecredentials\u003c/a\u003e and \u003ca href=\"https://docs.elastic.co/en/integrations/aws#aws-permissions\" target=\"_self\"\u003epermissions\u003c/a\u003e.\u003c/p\u003e"},{"title_l10n":"Step 1: Get an account on Elastic Cloud","_metadata":{"uid":"cs2cb133d6c36849b5"},"header_style":"H3","paragraph_l10n":"\n\u003cp\u003eFollow the instructions to \u003ca href=\"https://cloud.elastic.co/registration?fromURI=%2Fhome\" target=\"_self\"\u003eget started on Elastic Cloud\u003c/a\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"cscd297375277874c4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt0dd4e2e2f5174976","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:25:02.563Z","created_by":"bltd9765be97bbed20c","file_size":"55470","filename":"blog-elastic-get-an-account.png","parent_uid":null,"tags":[],"title":"blog-elastic-get-an-account.png","updated_at":"2022-11-21T18:25:02.563Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.119Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0dd4e2e2f5174976/637bc27ed56692108527f412/blog-elastic-get-an-account.png"},"_metadata":{"uid":"cs34b6221f1a272b35"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Step 2: Install the Elastic AWS integration","_metadata":{"uid":"cs212a25eba04b066f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eNavigate to the AWS integration on Elastic.\u003c/p\u003e"}],"_metadata":{"uid":"cs7fa69a6c1adf7b2f"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltdc3430379a09f7f9","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:25:32.755Z","created_by":"bltd9765be97bbed20c","file_size":"241842","filename":"blog-elastic-install-aws-integration.png","parent_uid":null,"tags":[],"title":"blog-elastic-install-aws-integration.png","updated_at":"2022-11-21T18:25:32.755Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.070Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc3430379a09f7f9/637bc29ce72c60105ee2ade9/blog-elastic-install-aws-integration.png"},"_metadata":{"uid":"cs292c010871547527"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfa14ea6a0b9f3f6e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSelect \u003cspan data-type='inlineCode'\u003eAdd AWS \u003c/span\u003eintegration.\u003c/p\u003e"}],"_metadata":{"uid":"cscc28c210cdf4e0b4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt283b5ca300f8e6ff","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:26:43.129Z","created_by":"bltd9765be97bbed20c","file_size":"95061","filename":"blog-elastic-add-aws-integration.png","parent_uid":null,"tags":[],"title":"blog-elastic-add-aws-integration.png","updated_at":"2022-11-21T18:26:43.129Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.122Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt283b5ca300f8e6ff/637bc2e35797f6109ea93f38/blog-elastic-add-aws-integration.png"},"_metadata":{"uid":"csb92dbca22e5cd30e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs842b30e62b5236bb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis is where you will add your credentials and it will be stored as a policy in Elastic. This policy will be used as part of the install for the agent in the next step.\u003c/p\u003e\n\u003cp\u003eAs you can see, the general Elastic AWS Integration will collect a significant amount of data from 30 AWS services. If you don’t want to install this general Elastic AWS Integration, you can select individual integrations to install.\u003c/p\u003e\n"},{"title_l10n":"Step 3: Install the Elastic Agent with AWS integration","_metadata":{"uid":"cs157374ceab90db11"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eNow that you have created an integration policy, navigate to the \u003cspan data-type='inlineCode'\u003eFleet\u003c/span\u003e section under \u003cspan data-type='inlineCode'\u003eManagement \u003c/span\u003ein Elastic.\u003c/p\u003e"}],"_metadata":{"uid":"cs179756cd19f53363"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt59b0c6cc493921eb","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:28:03.863Z","created_by":"bltd9765be97bbed20c","file_size":"12956","filename":"blog-elastic-install-elastic-agent.png","parent_uid":null,"tags":[],"title":"blog-elastic-install-elastic-agent.png","updated_at":"2022-11-21T18:28:03.863Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.141Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt59b0c6cc493921eb/637bc3336f703310906d56c7/blog-elastic-install-elastic-agent.png"},"_metadata":{"uid":"cs2ab67399f01910dd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-small: 25%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs01bb244a084aba99"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSelect the name of the policy you created in the last step.\u003c/p\u003e"}],"_metadata":{"uid":"cs230393f82669bef0"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt50469230993f00ee","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:28:28.461Z","created_by":"bltd9765be97bbed20c","file_size":"255723","filename":"blog-elastic-name-policy.png","parent_uid":null,"tags":[],"title":"blog-elastic-name-policy.png","updated_at":"2022-11-21T18:28:28.461Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.122Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt50469230993f00ee/637bc34ccca9f010a904ea58/blog-elastic-name-policy.png"},"_metadata":{"uid":"cs315cb724b31186f7"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs42546739ca193c6e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFollow step 3 in the instructions in the \u003cstrong\u003eAdd\u003c/strong\u003e agent window. This will require you to:\u003c/p\u003e\n\u003cp\u003e1: Bring up an EC2 instance\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan data-type='inlineCode'\u003et2.medium is minimum\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan data-type='inlineCode'\u003eLinux - your choice of which\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan data-type='inlineCode'\u003eEnsure you allow for Open reservation on the EC2 instance when you Launch it\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e2: Log in to the instance and run the commands under \u003cspan data-type='inlineCode'\u003eLinux Tar\u003c/span\u003e tab (below is an example)\u003c/p\u003e"}],"_metadata":{"uid":"cs69d8f1b4ae34fc19"}}},{"code":{"code":"curl -L -O https://artifacts.elastic.co/downloads/beats/elastic-agent/elastic-agent-8.5.0-linux-x86_64.tar.gz\ntar xzvf elastic-agent-8.5.0-linux-x86_64.tar.gz\ncd elastic-agent-8.5.0-linux-x86_64\nsudo ./elastic-agent install --url=https://37845638732625692c8ee914d88951dd96.fleet.us-central1.gcp.cloud.es.io:443 --enrollment-token=jkhfglkuwyvrquevuytqoeiyri","_metadata":{"uid":"cs4e1071b6c9d5127b"}}},{"title_text":{"title_text":[{"title_l10n":"Step 4: Run traffic against the application","_metadata":{"uid":"cs3ebf54e9319159d5"},"header_style":"H3","paragraph_l10n":"\u003cspan\u003eWhile getting the application running is fairly easy, there is nothing to monitor or observe with Elastic unless you add a load on the application.\u003c/span\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eHere is a simple script you can also run using \u003ca href=\"https://playwright.dev/\"\u003ePlaywright\u003c/a\u003e to add traffic to the website for the AWS three tier application:\u003c/p\u003e"}],"_metadata":{"uid":"csedd448f7d5a79a65"}}},{"code":{"code":"import { test, expect } from '@playwright/test';\n\ntest('homepage for AWS Threetierapp', async ({ page }) =\u003e {\n await page.goto('http://web-tier-external-lb-1897463036.us-west-1.elb.amazonaws.com/#/db');\n\n await page.fill('#transactions \u003e tbody \u003e tr \u003e td:nth-child(2) \u003e input', (Math.random()*100).toString())\n await page.fill('#transactions \u003e tbody \u003e tr \u003e td:nth-child(3) \u003e input', (Math.random()*100).toString())\n await page.waitForTimeout(1000)\n await page.click('#transactions \u003e tbody \u003e tr:nth-child(2) \u003e td:nth-child(1) \u003e input[type=button]')\n await page.waitForTimeout(4000)\n\n});","_metadata":{"uid":"cs765735780652a4eb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8682525e392614c2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThis script will launch three browsers, but you can limit this load to one browser in playwright.config.ts file.\u003c/p\u003e\u003cp\u003eFor this exercise, we ran this traffic for approximately five hours with an interval of five minutes while testing the website.\u003c/p\u003e"},{"title_l10n":"Step 5: Go to AWS dashboards","_metadata":{"uid":"csa98e150b8b515de8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eNow that your Elastic Agent is running, you can go to the related AWS dashboards to view what’s being ingested.\u003c/p\u003e\u003cp\u003eTo search for the AWS Integration dashboards, simply search for them in the Elastic search bar. The relevant ones for this blog are:\u003c/p\u003e\u003cul\u003e\u003cli\u003e[Metrics AWS] EC2 Overview\u003c/li\u003e\u003cli\u003e[Metrics AWS] ELB Overview\u003c/li\u003e\u003cli\u003e[Metrics AWS] RDS Overview\u003c/li\u003e\u003cli\u003e[Metrics AWS] NAT Gateway\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csa0173867e6ed0be2"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltae5d178728d5981d","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:32:27.853Z","created_by":"bltd9765be97bbed20c","file_size":"13343","filename":"blog-elastic-search-aws-integration-dashboards.png","parent_uid":null,"tags":[],"title":"blog-elastic-search-aws-integration-dashboards.png","updated_at":"2022-11-21T18:32:27.853Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.119Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltae5d178728d5981d/637bc43b411e3c10e4602705/blog-elastic-search-aws-integration-dashboards.png"},"_metadata":{"uid":"cs5e8294c46afef47e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs69b2348ec9a14940"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eLet's see what comes up!\u003c/p\u003e\n\u003cp\u003eAll of these dashboards are out-of-the-box and for all the following images, we’ve narrowed the views to only the relevant items from our app.\u003c/p\u003e\n\u003cp\u003eAcross all dashboards, we’ve limited the timeframe to when we ran the traffic generator.\u003c/p\u003e"}],"_metadata":{"uid":"cs22785cfca002bb63"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt4a904d25aca79a28","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:32:59.801Z","created_by":"bltd9765be97bbed20c","file_size":"465712","filename":"blog-elastic-dashboard-traffic-generator.png","parent_uid":null,"tags":[],"title":"blog-elastic-dashboard-traffic-generator.png","updated_at":"2022-11-21T18:32:59.801Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.126Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4a904d25aca79a28/637bc45b71c75510a0ca1950/blog-elastic-dashboard-traffic-generator.png"},"_metadata":{"uid":"cs634873a9936d966a"},"caption_l10n":"Elastic Observability EC2 Overview Dashboard","alt_text_l10n":"Elastic Observability EC2 Overview Dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csae65a7bce3d52721"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce we filtered for our 4 EC2 instances (2 web servers and 2 application servers), we can see the following:\u003c/p\u003e\n\u003cp\u003e1: All 4 instances are up and running with no failures in status checks.\u003c/p\u003e\n\u003cp\u003e2: We see the average CPU utilization across the timeframe and nothing looks abnormal.\u003c/p\u003e\n\u003cp\u003e3: We see the network bytes flow in and out, aggregating over time as the database is loaded with rows.\u003c/p\u003e\n\u003cp\u003eWhile this exercise shows a small portion of the metrics that can be viewed, more are available from AWS EC2. The metrics listed on \u003ca href=\"https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/viewing_metrics_with_cloudwatch.html\"\u003eAWS documentation\u003c/a\u003e are all available, including the dimensions to help narrow the search for specific instances, etc.\u003c/p\u003e"}],"_metadata":{"uid":"cs3269210707cc6546"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt0c39f0a7d3b0561a","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:33:45.767Z","created_by":"bltd9765be97bbed20c","file_size":"322918","filename":"blog-elastic-overview-dashboard.png","parent_uid":null,"tags":[],"title":"blog-elastic-overview-dashboard.png","updated_at":"2022-11-21T18:33:45.767Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.140Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0c39f0a7d3b0561a/637bc4894005df1070b00265/blog-elastic-overview-dashboard.png"},"_metadata":{"uid":"cs272c54675ea73502"},"caption_l10n":"Elastic Observability ELB Overview Dashboard","alt_text_l10n":"Elastic Observability ELB Overview Dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csef85012e93341ca8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor the ELB dashboard, we filter for our 2 load balancers (external web load balancer and internal application load balancer).\u003c/p\u003e\n\u003cp\u003eWith the out-of-the-box dashboard, you can see application ELB-specific metrics. A good portion of the application ELB specific metrics listed in \u003ca href=\"https://docs.aws.amazon.com/elasticloadbalancing/latest/application/load-balancer-cloudwatch-metrics.html\"\u003eAWS Docs\u003c/a\u003e are available to add graphs for.\u003c/p\u003e\n\u003cp\u003eFor our two load balancers, we can see:\u003c/p\u003e\n\u003cp\u003e1: Both the hosts (EC2 instances connected to the ELBs) are healthy.\u003c/p\u003e\n\u003cp\u003e2: Load Balancer Capacity Units (how much you are using) and request counts both went up as expected during the traffic generation time frame.\u003c/p\u003e\n\u003cp\u003e3: We picked to show 4XX and 2XX counts. 4XX will help identify issues with the application or connectivity with the application servers.\u003c/p\u003e"}],"_metadata":{"uid":"csd1cc7c6b5035fd3e"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt1419bf8dc01b91cc","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:34:24.525Z","created_by":"bltd9765be97bbed20c","file_size":"268614","filename":"blog-elastic-transaction-blocked.png","parent_uid":null,"tags":[],"title":"blog-elastic-transaction-blocked.png","updated_at":"2022-11-21T18:34:24.525Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.134Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1419bf8dc01b91cc/637bc4b00f2f8f10dd0e5b33/blog-elastic-transaction-blocked.png"},"_metadata":{"uid":"cs81597c3f563ffdfe"},"caption_l10n":"Elastic Observability RDS Overview Dashboard","alt_text_l10n":"Elastic Observability RDS Overview Dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaaa8e26e0451c52e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFor AuroraDB, which is deployed in RDS, we’ve filtered for just the primary and secondary instances of Aurora on the dashboard.\u003c/p\u003e\u003cp\u003eJust as with EC2, ELB, most RDS metrics from Cloudwatch are also available to create new charts and graphs. In this dashboard, we’ve narrowed it down to showing:\u003c/p\u003e\u003cp\u003e1: Insert throughput \u0026amp; Select throughput\u003c/p\u003e\u003cp\u003e2: Write latency\u003c/p\u003e\u003cp\u003e3: CPU usage\u003c/p\u003e\u003cp\u003e4: General number of connections during the timeframe\u003c/p\u003e"}],"_metadata":{"uid":"cs05c5f7baca0f529c"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blte975d2976864374c","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:35:37.030Z","created_by":"bltd9765be97bbed20c","file_size":"646619","filename":"blog-elastic-aws-nat-dashboard.png","parent_uid":null,"tags":[],"title":"blog-elastic-aws-nat-dashboard.png","updated_at":"2022-11-21T18:35:37.030Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.133Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte975d2976864374c/637bc4f92f1aba10d25ac347/blog-elastic-aws-nat-dashboard.png"},"_metadata":{"uid":"cse020c974ba7b985d"},"caption_l10n":" Elastic Observability AWS NAT Dashboard","alt_text_l10n":"Elastic Observability AWS NAT Dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csafa1f7fd01717a41"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe filtered to look only at our 2 NAT instances which are fronting the application servers. As with the other dashboards, other metrics are available to build graphs and /charts as needed.\u003c/p\u003e\n\u003cp\u003eFor the NAT dashboard we can see the following:\u003c/p\u003e\n\u003cp\u003e1: The NAT Gateways are doing well due to no packet drops\u003c/p\u003e\n\u003cp\u003e2: An expected number of active connections from the web server\u003c/p\u003e\n\u003cp\u003e3: Fairly normal set of metrics for bytes in and out\u003c/p\u003e\n\u003cp\u003e\u003cstrong\u003eCongratulations, you have now started monitoring metrics from key AWS services for your application!\u003c/strong\u003e\u003c/p\u003e\n"},{"title_l10n":"What to monitor on AWS next?","_metadata":{"uid":"cs2beab432275089a4"},"header_style":"H2","paragraph_l10n":"\n\n"},{"title_l10n":"Add logs from AWS Services","_metadata":{"uid":"csd67fe4ac4549399b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eNow that metrics are being monitored, you can also now add logging. There are several options for ingesting logs.\u003c/p\u003e\u003cp\u003e1. The AWS Integration in the Elastic Agent has logs setting. Just ensure you turn on what you wish to receive. Let’s ingest the Aurora Logs from RDS. In the Elastic agent policy, we simply turn on Collect logs from CloudWatch (see below). Next, update the agent through the Fleet management UI.\u003c/p\u003e"}],"_metadata":{"uid":"cs2b77e30647296262"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltefa43f40c3c84204","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:36:41.710Z","created_by":"bltd9765be97bbed20c","file_size":"45467","filename":"blog-elastic-collect-logs.png","parent_uid":null,"tags":[],"title":"blog-elastic-collect-logs.png","updated_at":"2022-11-21T18:36:41.710Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.052Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltefa43f40c3c84204/637bc53911407d1056d5fbb1/blog-elastic-collect-logs.png"},"_metadata":{"uid":"cs6bb10010b19ef7ce"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs077548ed57cc4f73"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e2. You can install the \u003ca href=\"https://github.com/elastic/elastic-serverless-forwarder/blob/main/docs/README-AWS.md#deploying-elastic-serverless-forwarder\"\u003eLambda logs forwarder\u003c/a\u003e. This option will pull logs from multiple locations. See the architecture diagram below.\u003c/p\u003e"}],"_metadata":{"uid":"cs32ae5273ba98805e"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt975403f66875474f","ACL":{},"content_type":"image/png","created_at":"2022-11-21T18:37:16.216Z","created_by":"bltd9765be97bbed20c","file_size":"152077","filename":"blog-elastic-lambda-logs-forwarder.png","parent_uid":null,"tags":[],"title":"blog-elastic-lambda-logs-forwarder.png","updated_at":"2022-11-21T18:37:16.216Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-22T15:00:00.214Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt975403f66875474f/637bc55c7a64f810a2986abf/blog-elastic-lambda-logs-forwarder.png"},"_metadata":{"uid":"cs9fda0dde638d92b1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csef2062d25b5eb598"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eA review of this option is also found in the following \u003ca href=\"/blog/elastic-and-aws-serverless-application-repository-speed-time-to-actionable-insights-with-frictionless-log-ingestion-from-amazon-s3\" target=\"_self\"\u003eblog\u003c/a\u003e.\u003c/p\u003e\n"},{"title_l10n":"Analyze your data with Elastic Machine Learning","_metadata":{"uid":"csdc8272431b2fa042"},"header_style":"H3","paragraph_l10n":"\u003cp\u003eOnce metrics and logs (or either one) are in Elastic, start analyzing your data through Elastic’s ML capabilities. A great review of these features can be found here:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/blog/apm-correlations-elastic-observability-root-cause-transactions\" target=\"_self\"\u003eCorrelating APM Telemetry to determine root causes in transactions\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/elasticon/archive/2020/global/machine-learning-and-the-elastic-stack-everywhere-you-need-it\" target=\"_self\"\u003eIntroduction to Elastic Machine Learning\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eAnd there are many more videos and blogs on \u003ca href=\"/blog/\" target=\"_self\"\u003eElastic’s Blog\u003c/a\u003e.\u003c/p\u003e"},{"title_l10n":"Conclusion: Monitoring AWS service metrics with Elastic Observability is easy!","_metadata":{"uid":"csba02803116672f2f"},"header_style":"H2","paragraph_l10n":"\n\u003cp\u003eI hope you’ve gotten an appreciation for how Elastic Observability can help you monitor AWS service metrics, here’s a quick recap of lessons and what you learned:\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003eElastic Observability supports ingest and analysis of AWS service metrics\u003c/li\u003e\n \u003cli\u003eIt’s easy to set up ingest from AWS Services via the Elastic Agent\u003c/li\u003e\n \u003cli\u003eElastic Observability has multiple out-of-the-box (OOTB) AWS service dashboards you can use to preliminarily review information, then modify for your needs\u003c/li\u003e\n \u003cli\u003e30+ AWS services are supported as part of AWS Integration on Elastic Observability, with more services being added regularly\u003c/li\u003e\n \u003cli\u003eAs noted in related blogs, you can analyze your AWS service metrics with Elastic’s machine learning capabilities\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eStart your own \u003ca href=\"https://aws.amazon.com/marketplace/pp/prodview-voru33wi6xs7k?trk=5fbc596b-6d2a-433a-8333-0bd1f28e84da%E2%89%BBchannel=el\"\u003e7-day free trial\u003c/a\u003e by signing up via \u003ca href=\"https://aws.amazon.com/marketplace/pp/prodview-voru33wi6xs7k?trk=d54b31eb-671c-49ba-88bb-7a1106421dfa%E2%89%BBchannel=el\"\u003eAWS Marketplace\u003c/a\u003e and quickly spin up a deployment in minutes on any of the \u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-reference-regions.html#ec_amazon_web_services_aws_regions\"\u003eElastic Cloud regions on AWS\u003c/a\u003e around the world. Your AWS Marketplace purchase of Elastic will be included in your monthly consolidated billing statement and will draw against your committed spend with AWS.\u003c/p\u003e"}],"_metadata":{"uid":"cs519d85b70024348a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4eeda52c6359a387"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csade9c1d07beb4080"}}}],"publish_date":"2022-11-22","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Analyze your application's AWS service metrics with Elastic Observability","seo_description_l10n":"Get metrics and logs from your AWS deployment and Elastic Observability in just minutes! We’ll show you how to use Elastic integrations to quickly monitor and manage the performance of your applications and AWS services to streamline troubleshooting.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbf6fd364f32f8563","ACL":{},"created_at":"2023-11-06T21:50:46.524Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fleet-elastic-agent","label_l10n":"Fleet/Elastic Agent","tags":[],"title":"Fleet/Elastic Agent","updated_at":"2023-11-06T21:50:46.524Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:48:26.489Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"AWS","label_l10n":"AWS","keyword":"aws","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt5da20aee1a072f80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:30.685Z","updated_at":"2023-11-06T20:08:30.685Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:00:52.463Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"bltbd2f262aa33cb60c","ACL":{},"content_type":"image/png","created_at":"2022-06-06T18:07:42.854Z","created_by":"bltd9765be97bbed20c","file_size":"100062","filename":"blog-charts-packages.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-charts-packages.png","updated_at":"2022-06-06T18:07:42.854Z","updated_by":"bltd9765be97bbed20c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-10T09:12:14.092Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbd2f262aa33cb60c/629e426ed0f3ca0f53e0ad7b/blog-charts-packages.png"},"title":"Wait… Elastic Observability monitors metrics for AWS services in just minutes?","title_l10n":"Wait… Elastic Observability monitors metrics for AWS services in just minutes?","updated_at":"2025-03-28T13:40:40.239Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/aws-service-metrics-monitor-observability-easy","publish_details":{"time":"2025-03-28T13:40:46.529Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt37c068f09bb58cb4","_version":15,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog, we will provide background on the Linux process model, a key aspect of how Linux workloads are represented.","author":["bltb1d768de0d3fe74c"],"category":["bltb79594af7c5b4199"],"created_at":"2022-04-14T21:32:40.773Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1736901f64dfef9a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe Linux process model, available within Elastic, allows users to write very targeted alerting rules and gain deeper insight into exactly what is happening on their Linux servers and desktops.\u003c/p\u003e\u003cp\u003eIn this blog, we will provide background on the Linux process model, a key aspect of how Linux workloads are represented.\u003c/p\u003e\u003cp\u003eLinux follows the Unix process model from the 1970's that was augmented with the concept sessions in the 1980's judging from when the setsid() system call was introduced by early \u003ca href=\"https://en.wikipedia.org/wiki/POSIX\" target=\"_self\"\u003ePOSIX documents\u003c/a\u003e\u003c/p\u003e\u003cp\u003eThe Linux process model is a good abstraction for recording computer workloads (which programs are run) and for writing rules to react to these events. It offers a clear representation of who did what when on which server for alerting, compliance and threat hunting.\u003c/p\u003e\u003cp\u003eCapturing process creation, privilege escalation and lifespans offers deep insight into how applications and services are implemented and their normal patterns of program execution. Once normal execution patterns are identified, rules may be written to send alerts when anomalous execution patterns occur.\u003c/p\u003e\u003cp\u003eDetailed process information permits very targeted rules to be written for alerts, which reduces false positives and alert fatigue.\u0026nbsp; It also allows Linux sessions to be categorized as one of:\u003c/p\u003e\u003cul\u003e\u003cul\u003e\u003cli\u003eautonomous services started at boot (e.g. cron)\u003c/li\u003e\u003cli\u003eservices providing remote access (e.g. sshd)\u003c/li\u003e\u003cli\u003einteractive (likely human) remote access (e.g a bash terminal started via ssh)\u003c/li\u003e\u003cli\u003enon-interactive remote access (e.g. Ansible installing software via ssh)\u003c/li\u003e\u003c/ul\u003e\u003c/ul\u003e\u003cp\u003eThese categorizations permit very precise rules and review. For example, one could review all interactive sessions on specific servers in a selected timeframe.\u003c/p\u003e\u003cp\u003eThis article describes how the Linux process model works and will assist in writing alerting and response rules for workload events. An understanding of the Linux process model is also an essential first step to understanding Containers and the namespaces and cgroups from which they are composed.\u003c/p\u003e\u003ch2\u003eProcess model capture vs. system call logs\u003c/h2\u003e\u003cp\u003eCapturing changes to the session model in terms of new processes, new sessions, exiting processes, etc. is simpler and clearer than capturing the \u003ca href=\"https://en.wikipedia.org/wiki/System_call\" target=\"_self\"\u003esystem calls\u003c/a\u003e used to enact those changes. Linux has approximately 400 system calls and does not refactor them once they are released. This approach retains a stable application binary interface (ABI), which means programs compiled to run on Linux years ago should continue to run on Linux today without rebuilding them from source code.\u003c/p\u003e\u003cp\u003eNew system calls are added to improve capabilities or security instead of refactoring existing system calls (avoids breaking the ABI). The upshot is that mapping a time ordered list of system calls and their parameters to the logical actions they perform takes a significant amount of expertise. Additionally, newer system calls, such as those of io_uring, make it possible to read and write files and sockets with no additional system calls by using memory mapped between kernel and user space.\u003c/p\u003e\u003cp\u003eBy contrast, the process model is stable (hasn't changed much since the 1970's) yet still comprehensively covers the actions taken on a system when one includes file access, networking and other logical operations.\u003c/p\u003e\u003ch2\u003eProcess formation: init is the first process after boot\u003c/h2\u003e\u003cp\u003eWhen the Linux kernel has started, it creates a special process called \u003ca href=\"https://en.wikipedia.org/wiki/Init\" target=\"_self\"\u003e“the init process.”\u003c/a\u003e A process embodies the execution of one or more programs. The init process always has the process id (PID) of 1 and is executed with a user id of 0 (root). Most modern Linux distributions use systemd as their init process's executable program.\u003c/p\u003e\u003cp\u003eThe job of init is to start the configured services such as databases, web servers, and remote access services such as sshd. These services are typically encapsulated within their own sessions, which simplifies starting and stopping services by grouping all processes of each service under a single session id (SID).\u003c/p\u003e\u003cp\u003eRemote access, such as via the SSH protocol to an sshd service, will create a new Linux session for the accessing user. This session will initially execute the program the remote user requested — often an interactive shell — and the associated process(es) will all have the same SID.\u003c/p\u003e\u003ch2\u003eThe mechanics of creating a process\u003c/h2\u003e\u003cp\u003eEvery process, except the init process, has a single parent process. Each process has a PPID, the process id of its parent process (0/no-parent in the case of init). Reparenting can occur if a parent process exits in a way that does not also terminate the child process(es).\u003c/p\u003e\u003cp\u003eReparenting usually picks init as the new parent and init has special code to clean up after these adopted children when they exit. Without this adoption and clean up code, orphaned child processes would become \"zombie\" processes (no kidding!). They hang around until their parent reaps them so the parent can examine their exit code — an indicator of whether the child program completed its tasks successfully.\u003c/p\u003e\u003cp\u003eThe advent of \"containers,\" pid namespaces in particular, necessitated the ability to designate processes other than init as \"sub-reapers\" (processes willing to adopt orphaned processes). Typically sub-reapers are the first process in a container. This is done because the processes in the container cannot \"see\" processes in the ancestor pid namespaces (i.e. their PPID value would not make sense if the parent was in an ancestor pid namespace).\u003c/p\u003e\u003cp\u003eTo create a child process, the parent clones itself via the \u003ca href=\"https://en.wikipedia.org/wiki/Fork_(system_call)\" target=\"_self\"\u003efork() or clone() system call\u003c/a\u003e. After the fork/clone, execution immediately continues in \u003cem\u003eboth\u003c/em\u003e the parent \u003cem\u003eand\u003c/em\u003e the child (ignoring vfork() and clone()’s CLONE_VFORK option), but along different code paths by virtue of the return code value from fork()/clone().\u003c/p\u003e\u003cp\u003eYou read that correctly: one fork()/clone() system call provides a return code in two different processes! The parent receives the PID of the child as its return code, and the child receives 0 so the shared code of the parent and child can branch based on that value. There are some cloning nuances with multi-threaded parents and copy-on-write memory for efficiency that do need to be elaborated on here. The child process inherits the memory state of the parent and its open files, network sockets, and the controlling terminal, if any.\u003c/p\u003e\u003cp\u003eTypically, the parent process will capture the PID of the child to monitor its lifecycle (see reaping above). The child process's behavior depends on the program that cloned itself (it provides an execution path to follow based on the return code from fork()).\u003c/p\u003e\u003cp\u003eA web server such as nginx might clone itself, creating a child process to handle http connections. In cases like this, the child process does not execute a new program, but simply runs a different code path in the same program to handle http connections in this case. Recall that the return value from a clone or fork tells the child that it is the child so it can choose this code path.\u003c/p\u003e\u003cp\u003eInteractive shell processes (e.g., one of bash, sh, fish, zsh, etc. with a controlling terminal), possibly from an ssh session, clone themselves whenever a command is entered. The child process, still running a code path from the parent/shell, does a bunch of work setting up file descriptors for IO redirection, setting the process group, and more before the code path in the child calls the \u003ca href=\"https://man7.org/linux/man-pages/man2/execve.2.html\" target=\"_self\"\u003eexecve()\u003c/a\u003e system call or similar to run a different program inside that process.\u003c/p\u003e\u003cp\u003eIf you type ls into your shell, it forks your shell, the setup described above is done by the shell/child and then the ls program (usually from the /usr/bin/ls file) is executed to replace the contents of that process with the machine code for ls. This \u003ca href=\"https://www.gnu.org/software/libc/manual/html_node/Implementing-a-Shell.html\" target=\"_self\"\u003earticle\u003c/a\u003e about implementing shell job control provides great insight into the inner workings of shells and process groups.\u003c/p\u003e\u003cp\u003eIt is important to note that a process can call execve() more than once, and therefore workload capture data models must handle this as well. This means that a process can become many different programs before it exits — not just its parent process program optionally followed by one program. See the shell \u003ca href=\"https://www.man7.org/linux/man-pages/man1/bash.1.html#SHELL_BUILTIN_COMMANDS\" target=\"_self\"\u003eexec builtin command\u003c/a\u003e for a way to do this in a shell (i.e. replace the shell program with another in the same process).\u003c/p\u003e\u003cp\u003eAnother aspect of executing a program in a process is that some open file descriptors (those marked as close-on-exec) may be closed prior to the execution of the new program, while others may remain available to the new program. Recall that a single fork()/clone() call provides a return code in two processes, the parent and the child. The execve() system call is strange as well in that a successful execve() has no return code for success because it results in a new program execution so there's nowhere to return to except when execve() fails.\u003c/p\u003e\u003ch2\u003eCreating new sessions\u003c/h2\u003e\u003cp\u003eLinux currently creates new sessions with a single system call, setsid(), which is called by the process that becomes the new session leader. This system call is often part of the cloned child’s code path run before executing another program in that process (i.e. it’s planned by, and included in, the parent process’s code). All processes within a session share the same SID, which is the same as the PID of the process that is called setsid(), also known as the session leader. In other words, a session leader is any process with a PID that matches its SID. The exit of the session leader process will trigger termination of its immediate children process groups.\u003c/p\u003e\u003ch2\u003eCreating new process groups\u003c/h2\u003e\u003cp\u003eLinux uses process groups to identify a group of processes working together within a session. They will all have the same SID and process group id (PGID). The PGID is the PID of the process group leader. There is no special status for the process group leader; it may exit with no effect on other members of the process group and they retain the same PGID — even though the process with that PID no longer exists.\u003c/p\u003e\u003cp\u003eNote that even with pid-wrap (re-use of a recently used pid on busy systems), the Linux kernel ensures the pid of an exited process group leader is not reused until all members of that process group have exited (i.e. there is no way their PGID could accidentally refer to a new process).\u003c/p\u003e\u003cp\u003eProcess groups are valuable for shell pipeline commands like:\u003c/p\u003e\u003cp\u003ecat foo.txt | grep bar | wc -l\u003c/p\u003e\u003cp\u003eThis creates three processes for three different programs (cat, grep and wc) and connects them with pipes. Shells will create a new process group even for single program commands like ls. The purpose of process groups is to permit targeting of signals to a set of processes and to identify a set of processes — the foreground process group — that are permitted full read and write access to their session’s controlling terminal, if any.\u003c/p\u003e\u003cp\u003eIn other words, control-C in your shell will send an interrupt signal to all processes in the foreground process group (the negative PGID value as the signal’s pid target discriminates between the group versus the process group leader process itself). The controlling terminal association ensures that processes reading input from the terminal don’t compete with each other and cause issues (terminal output may be permitted from non-foreground process groups).\u003c/p\u003e\u003ch2\u003eUsers and groups\u003c/h2\u003e\u003cp\u003eAs mentioned above, the init process has the user id 0 (root). Every process has an associated user and group and these may be used to restrict access to system calls and files. Users and groups have numeric ids and \u003cem\u003emay\u003c/em\u003e have an associated name like root or ms. The root user is the superuser which may do anything, and should only be used when absolutely required for security reasons.\u003c/p\u003e\u003cp\u003eThe Linux kernel only cares about ids. Names are optional and provided for human convenience by the files \u003ca href=\"https://man7.org/linux/man-pages/man5/passwd.5.html\" target=\"_self\"\u003e/etc/passwd\u003c/a\u003e and \u003ca href=\"https://man7.org/linux/man-pages/man5/group.5.html\" target=\"_self\"\u003e/etc/group\u003c/a\u003e. The \u003ca href=\"https://man7.org/linux/man-pages/man5/nsswitch.conf.5.html\" target=\"_self\"\u003eName Service Switch (NSS)\u003c/a\u003e allows these files to be extended with users and groups from LDAP and other directories (use \u003ca href=\"https://man7.org/linux/man-pages/man1/getent.1.html\" target=\"_self\"\u003egetent passwd\u003c/a\u003e if you want to see the combination of /etc/passwd and NSS-provided users).\u003c/p\u003e\u003cp\u003eEach process may have several users and groups associated with it (real, effective, saved, and supplemental groups). See \u003ca href=\"https://man7.org/linux/man-pages/man7/credentials.7.html\" target=\"_self\"\u003eman 7 credentials\u003c/a\u003e for more information.\u003c/p\u003e\u003cp\u003eThe increased use of containers whose root file systems are defined by container images has increased the likelihood of /etc/passwd and /etc/group being absent or missing some names of user and group ids that may be in use. Since the Linux kernel does not care about these names, only the ids, this is fine.\u003c/p\u003e\u003ch2\u003eSummary\u003c/h2\u003e\u003cp\u003eThe Linux process model provides a precise and succinct way of representing server workloads which in turn allows very targeted alerting rules and review. An easy to understand per-session rendering of the process model in your browser would provide great insight into your server workloads.\u003c/p\u003e\u003cp\u003eYou can get started with a free \u003ca href=\"https://cloud.elastic.co/registration?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=trail\" target=\"_self\"\u003e\u003cu\u003e14-day trial of Elastic Cloud\u003c/u\u003e\u003c/a\u003e. Or,\u003ca href=\"https://www.elastic.co/downloads/?utm_source=log4j+hub+blog\u0026utm_medium=embed+link\u0026utm_campaign=log4j_hub_blog\u0026utm_id=log4j\u0026utm_content=download\" target=\"_self\"\u003e\u003cu\u003edownload\u003c/u\u003e\u003c/a\u003e the self-managed version of the Elastic Stack for free.\u003c/p\u003e\u003ch2\u003eLearning more\u003c/h2\u003e\u003cp\u003eLinux man pages are an excellent source of information. The man pages below have details of the Linux process model described above:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man2/fork.2.html\" target=\"_self\"\u003eman 2 fork\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man2/clone.2.html\" target=\"_self\"\u003eman 2 clone\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man2/setsid.2.html\" target=\"_self\"\u003eman 2 setsid\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man2/execve.2.html\" target=\"_self\"\u003eman 2 execve\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man2/_exit.2.html\" target=\"_self\"\u003eman 2 exit\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man7/credentials.7.html\" target=\"_self\"\u003eman 7 credentials\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://man7.org/linux/man-pages/man7/namespaces.7.html\" target=\"_self\"\u003eman 7 namespaces\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.gnu.org/software/libc/manual/html_node/Implementing-a-Shell.html\" target=\"_self\"\u003eprocess groups - implementing shell job control\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.man7.org/linux/man-pages/man1/bash.1.html#SHELL_BUILTIN_COMMANDS\" target=\"_self\"\u003eshell builtin commands\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs6fc4f9b45d796bf9"}}}],"publish_date":"2022-04-18T18:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"The Linux process and session model","seo_description_l10n":"The Linux process model, available within Elastic, allows users to write very target alerting rules and gain deeper insight into exactly what is happening on their Linux servers and desktops.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltbf75d98adf3a9e45","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-11-22T21:26:52.053Z","updated_at":"2021-11-22T21:26:52.053Z","content_type":"image/png","file_size":"121441","filename":"illustration-radar-security.png","title":"illustration-radar-security.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-22T21:26:57.740Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf75d98adf3a9e45/619c0b1c1c5e9d77962cd96d/illustration-radar-security.png"},"title":"The Linux process and session model as part of security alerting and monitoring","title_l10n":"The Linux process and session model as part of security alerting and monitoring","updated_at":"2025-03-28T13:40:04.233Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/linux-process-and-session-model-as-part-of-security-alerting-and-monitoring","publish_details":{"time":"2025-03-28T13:40:09.440Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3c7c1b6f6034e33e","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog post, get to know Giovana do Nascimento Pena. Giovana is a full-stack application developer at IBM and was awarded as a Bronze Contributor in 2022. Additionally, she is the Elastic Community Organizer for the São Paulo user group.","author":["bltfbd888b393c07a6a"],"category":["blte5cc8450a098ce5e"],"created_at":"2023-09-19T14:08:52.768Z","created_by":"blt92c74e5c4edca909","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs521a8b25532b7250"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGiovana do Nascimento Pena is a full-stack application developer at IBM. She graduated with a degree in systems analysis and development from UNASP University and a postgraduate degree in DevOps from PUC Minas Gerais. Giovana is certified in Developer Profession - Level 2 Experienced and IBM Cloud. She's part of the Black Girls Institute, one of the leaders of TLC, and IBM's internal technical community. She was awarded as a Bronze Contributor in 2022 and is the Elastic Community Organizer for the São Paulo user group.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhen did you first embrace Elastic as a technology?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI got to know Elastic in mid-2019 at a meetup, where they talked about observability. I was always interested in exploring topics I had never seen before. In fact, this is a tip I give to everyone: explore new things, be curious to learn about different technologies and see whether or not they can be applied in everyday life. After that, I had the opportunity to participate in an APM workshop and fell in love with Elastic's technologies, and I am always exploring the topics.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhy did you decide to become a community organizer?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirstly for passion: I am passionate about tech communities. Second, I always wanted to make an impact on people's lives. Belonging to a community, you have the opportunity to grow, learn, build a network, and, mostly, get to know yourself. These are pillars that I believe in and that changed my life and can change the lives of other people too.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat is your most memorable moment from being part of the Elastic community?\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere were several, but without a doubt seeing my former Elastic mentor watch my presentation with admiration was something fantastic. That impacted me in many ways. This is something that I reflect on a lot, and seeing many exchanges end up occurring in the community, it's like a never-ending chain of impact we have on each other.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhy did you decide to join the Elastic Contributor Program? What were the most significant benefits you reaped from it?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI joined the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/community/contributor\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Contributor Program\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e after being invited by a few Elasticians because each of them saw my passion and engagement with the community. This made me see the importance of giving back to the community, especially in a post-pandemic world, to bring visibility to Brazil and become a reference in the world when it comes to tech communities. I had training opportunities through Elastic, visibility, gifts like everyone else, and especially technical support, making me stand out in my field.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat are your favorite things about the Elastic community?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI believe it's about finding a safe place to share knowledge. No matter how you help, you will impact other people, and that's wonderful. I learned a lot and gained seniority thanks to the community. The networking and engagement I gained in my career also far exceeded my expectations. For me, the pillars I love most about the community are knowledge, engagement, and especially people.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat does it mean to you to be a woman in tech?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI admit that it is quite a challenge, the weight and effort of my actions, but I know the importance of taking on projects, leadership, and becoming an inspiration for other women in the area. We often forget the impact we have in tech and the importance and power that women in these roles can have. I feel honored to be where I am today, and I know that in the future this will have a global impact on an entire society.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eAny final thoughts you'd like to share?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI wanted to reinforce a message about the importance of communities. Thanks to them, I have a career in tech. However, I know that not all places have the privilege of having communities within their regions, so I would like to challenge everyone reading this post to try to encourage the creation and engagement of communities in the cities where they live. This impacts many professionals and unfortunately, we're still lacking in that. Engaging in a community could be the next step toward a successful career journey.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7598bb9b50f12ee6"}}}],"publish_date":"2023-10-12T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Get to know the Elastic Community series: Meet Giovana do Nascimento","seo_description_l10n":"In this blog post, get to know Giovana do Nascimento Pena. Giovana is a full-stack application developer at IBM and was awarded as a Bronze Contributor in 2022. Additionally, she is the Elastic Community Organizer for the São Paulo user group.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt71431489e0afe88b","ACL":{},"content_type":"image/jpeg","created_at":"2023-09-19T14:28:14.364Z","created_by":"blt92c74e5c4edca909","file_size":"202517","filename":"Screenshot_2023-09-19_at_8.09.38_AM.jpg","parent_uid":null,"tags":[],"title":"Screenshot_2023-09-19_at_8.09.38_AM.jpg","updated_at":"2023-09-19T14:28:14.364Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.456Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt71431489e0afe88b/6509affea53c9dafd6450784/Screenshot_2023-09-19_at_8.09.38_AM.jpg"},"title":"Get to know the Elastic Community series: Meet Giovana do Nascimento","title_l10n":"Get to know the Elastic Community series: Meet Giovana do Nascimento","updated_at":"2025-03-28T13:39:31.344Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/get-to-know-the-elastic-community-series-meet-giovana-do-nascimento","publish_details":{"time":"2025-03-28T13:39:36.645Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2dd3abac99c8e9cb","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"In this blog, we will use the Elasticsearch Python Client to send MyFitnessPal data to Elastic in order to better understand the trends and behaviors surrounding our nutrition.","author":["blt0e731319d585ef5f"],"category":["blte5cc8450a098ce5e"],"created_at":"2023-10-10T16:30:43.564Z","created_by":"blt92c74e5c4edca909","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2024bc09bf556a84"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eBackstory\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThree years after starting my fitness journey, I have the privilege of starting all over again thanks to my obsession with chocolate and pastries. Although these foods aren’t inherently bad, my goal is to make informed decisions based on data from my initial fitness journey.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this blog, we will use the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/python-api/current/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch Python Client\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to send MyFitnessPal data to Elastic\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e in order to better understand the trends and behaviors surrounding our nutrition, with the end result being both a health dashboard in Kibana\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e as well as the ability to run Elasticsearch\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e®\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e queries against our data.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eMyFitnessPal\u003c/h2\u003e\u003cp\u003e\u003ca href=\"https://www.myfitnesspal.com/\"\u003e\u003cspan style='font-size: 12pt;'\u003eMyFitnessPal\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is a calorie tracking tool used to log foods for each meal of the day. Although it’s really helpful in providing a detailed breakdown for each day, I wanted to take this a step further and receive all these same details based on a date range. I also wanted to search for specific foods from previous meal entries based on days, meal type, and macronutrient breakdown. These details can give a better picture of your overall nutrition goals and accomplishments over a given period of time.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat is Elasticsearch?\u003c/h2\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is a data store that allows you to search and analyze your data. It has the ability to ingest and index both structured and unstructured data depending on your use case. And serves as the foundation for all other solutions within the Elastic Stack.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eCreating the health dashboard\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirst, we’ll start by running a Python script that builds on the \u003c/span\u003e\u003ca href=\"https://python-myfitnesspal.readthedocs.io/en/latest/getting_started.html\"\u003e\u003cspan style='font-size: 12pt;'\u003emyfitnesspal-Python\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e library.\u0026nbsp; We will use it to grab our data from MyFitnessPal and send it to Elasticsearch.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce your data is in Elasticsearch, you’ll be able to run queries and aggregations against it, as well as visualize it within Kibana.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere is how your Kibana dashboard should look at the end of this tutorial.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csba295ae27d3cb2d4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt1547f0adaaf1c1a6","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:13:56.265Z","created_by":"blt92c74e5c4edca909","file_size":"482479","filename":"Screenshot_2023-10-10_at_10.13.46_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.13.46_AM.png","updated_at":"2023-10-10T16:13:56.265Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.409Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1547f0adaaf1c1a6/652578445679ebc2736df0ed/Screenshot_2023-10-10_at_10.13.46_AM.png"},"_metadata":{"uid":"cs4ae5846b5aece4a4"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2c478a53b0b8f9a6"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003ePrerequisites\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBefore we begin, you will need:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud account\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to send data to Elasticsearch using the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/python-api/current/index.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch Python Client\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn account for \u003c/span\u003e\u003ca href=\"http://myfitnesspal.com\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMyFitnessPal\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to log in and retrieve food diary data\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.python.org/downloads/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePython\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e installation v3 or higher\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe will be using a library called \u003c/span\u003e\u003ca href=\"https://python-myfitnesspal.readthedocs.io/en/latest/getting_started.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePython-myfitnesspal\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to grab the data from our personal account. All the code from this tutorial is available \u003c/span\u003e\u003ca href=\"https://github.com/arober39/myfitnesspal_diary_entries\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehere\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eData extraction to Elasticsearch\u003c/h2\u003e\u003cp\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFirst, let’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/python-api/current/installation.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003einstall\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/python-api/current/index.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch Python client\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbb81b89d4ec3a25c"}}},{"code":{"code":"Python -m pip install elasticsearch","_metadata":{"uid":"cs008f5892af28fe1c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs23bb551194f9ba24"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNext, we’ll need to install the myfitnesspal package.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd13e5bcff9e0e849"}}},{"code":{"code":"pip install myfitnesspal","_metadata":{"uid":"cs6d6bf5de49678fdd"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb0bac0d878a5faa5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSince the myfitnesspal library uses cookies to login from the terminal, we will have to grant the terminal \u003c/span\u003e\u003ca href=\"https://osxdaily.com/2018/10/09/fix-operation-not-permitted-terminal-error-macos/\"\u003e\u003cspan style='font-size: 12pt;'\u003efull disk access\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Be sure to reverse this access once data has been extracted.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnsure you grant access to a browser you’ve previously used to log in to MyFitnessPal.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsing this library, we will be able to access the food diary, exercises, measurements, and reports as shown \u003c/span\u003e\u003ca href=\"https://python-myfitnesspal.readthedocs.io/en/latest/how_to/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ehere\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. In this post, we’ll be focused only on the diary entries.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo establish a connection to our Elasticsearch cluster, we need to specify our Elastic Cloud ID and authentication credentials. I recommend creating a .ini file and accessing these credentials using a config parser.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs21868acfa3b46ae6"}}},{"code":{"code":"from elasticsearch import Elasticsearch \nimport configparser\n\nconfig = configparser.ConfigParser() \nconfig.read('mfp_elastic.ini')\n\n# Elasticsearch client instance \nes_client = Elasticsearch( \n cloud_id=config['ELASTIC']['cloud_id'], \n basic_auth=(\"elastic\", config['ELASTIC']['password']) \n) \nes_client.info()","_metadata":{"uid":"cs889ba34f3fcb845b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1b31ae419771759f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe’ll also need to import the myfitnesspal library to use the client to access meal entries.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd87c465e57f36c2e"}}},{"code":{"code":"import myfitnesspal\n\nclient = myfitnesspal.Client()","_metadata":{"uid":"cse3e8d3f4aa4d8300"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscd9bbf37fc803396"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, you can pass in your date range using the get_date() function.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2db75d5ed71c4109"}}},{"code":{"code":"def main():\n start_date = date(2020, 10, 1) \n end_date = date(2020, 10, 1) ","_metadata":{"uid":"csaae09bb2975ab112"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa34589f5a147bfe3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFinally, we can send the data to an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/what-is-an-elasticsearch-index\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch index\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e once we replace the index value with the name of the index that will hold all the meals for each day.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf7bc0472221bd45a"}}},{"code":{"code":"# send breakfast, lunch, dinner structs to ES \ndef send_meals_to_elasticsearch(meals_diary_entry): \n es_client.index( \n index='{INDEX_NAME_FOR_EACH_MEAL}', \n document=meals_diary_entry \n) \n\n# send each days overall calories and macros to ES \ndef send_todays_total_to_elasticsearch(total_daily_entry): \n es_client.index( \n index='{INDEX_NAME_FOR_TODAYS_TOTAL_MACROS}', \n document=total_daily_entry \n)","_metadata":{"uid":"cs2a5787acfa8be4b0"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb48b80784d18ca2b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, simply run the code that will log in to MyFitnessPal and send the data to Elasticsearch.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs63ce34f7aad2e0a4"}}},{"code":{"code":"Python myfitnesspal_to_elasticsearch.py","_metadata":{"uid":"cs2f7a912f87203b35"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs86eda3be2ae05413"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAfter running the Python code, we should have two new indices stored in Elasticsearch:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ealexis_myfitnesspal_diary_official_index index\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e ,\u003c/span\u003e\u003cspan style=\"color: rgb(55, 71, 79);font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003econtaining the calories and macros for each meal\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe total daily calories and macros for each day, contained in the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ealexis_daily_myfitnesspal_total_index index\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe output for the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ealexis_myfitnesspal_diary_official_index\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"color: rgb(55, 71, 79);font-size: 12pt;\"\u003eindex\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e should look something like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6a474fdae6c911fe"}}},{"code":{"code":"{\"date\": \"2020-10-01\", \"meal_type\": \"breakfast\", \"total_meal_macros\": {\"calories\": 607.0, \"carbohydrates\": 41.0, \"fat\": 38.0, \"protein\": 34.0, \"sodium\": 423.0, \"sugar\": 23.0}, \"list_of_food_macros\": [{\"food_macros\": {\"calories\": 120.0, \"carbohydrates\": 6.0, \"fat\": 11.0, \"protein\": 2.0, \"sodium\": 5.0, \"sugar\": 0.0}, \"name\": \"Avocado\"}, {\"food_macros\": {\"calories\": 210.0, \"carbohydrates\": 0.0, \"fat\": 14.0, \"protein\": 24.0, \"sodium\": 195.0, \"sugar\": 0.0}, \"name\": \"Hickman's Farm Fresh Egg\"}, {\"food_macros\": {\"calories\": 100.0, \"carbohydrates\": 1.0, \"fat\": 8.0, \"protein\": 6.0, \"sodium\": 180.0, \"sugar\": 0.0}, \"name\": \"Kraft Shredded Cheese Mexican\"}, {\"food_macros\": {\"calories\": 69.0, \"carbohydrates\": 17.0, \"fat\": 0.0, \"protein\": 1.0, \"sodium\": 2.0, \"sugar\": 15.0}, \"name\": \"Medjoul dates Dates\"}, {\"food_macros\": {\"calories\": 63.0, \"carbohydrates\": 16.0, \"fat\": 0.0, \"protein\": 1.0, \"sodium\": 1.0, \"sugar\": 8.0}, \"name\": \"Banana Large 8\\\" 9\\\" Long\"}, {\"food_macros\": {\"calories\": 45.0, \"carbohydrates\": 1.0, \"fat\": 5.0, \"protein\": 0.0, \"sodium\": 40.0, \"sugar\": 0.0}, \"name\": \"Silk Coconut Milk Unsweetened Coconut Milk\"}], \"list_of_foods\": [\"Avocado\", \"Hickman's Farm Fresh Egg\", \"Kraft Shredded Cheese Mexican\", \"Medjoul dates Dates\", \"Banana Large 8\\\" 9\\\" Long\", \"Silk Coconut Milk Unsweetened Coconut Milk\"]}\n\n{\"date\": \"2020-10-01\", \"meal_type\": \"lunch\", \"total_meal_macros\": {\"calories\": 315.0, \"carbohydrates\": 31.0, \"fat\": 3.0, \"protein\": 42.0, \"sodium\": 628.0, \"sugar\": 4.0}, \"list_of_food_macros\": [{\"food_macros\": {\"calories\": 24.0, \"carbohydrates\": 6.0, \"fat\": 0.0, \"protein\": 0.0, \"sodium\": 0.0, \"sugar\": 4.0}, \"name\": \"Homemade Baked Egg Plant\"}, {\"food_macros\": {\"calories\": 140.0, \"carbohydrates\": 0.0, \"fat\": 1.0, \"protein\": 34.0, \"sodium\": 300.0, \"sugar\": 0.0}, \"name\": \"Starkist Chunk Light Tuna Pouch\"}, {\"food_macros\": {\"calories\": 151.0, \"carbohydrates\": 25.0, \"fat\": 2.0, \"protein\": 8.0, \"sodium\": 328.0, \"sugar\": 0.0}, \"name\": \"Right rice Thai curry rice\"}], \"list_of_foods\": [\"Homemade Baked Egg Plant\", \"Starkist Chunk Light Tuna Pouch\", \"Right rice Thai curry rice\"]}\n\n{\"date\": \"2020-10-01\", \"meal_type\": \"dinner\", \"total_meal_macros\": {\"calories\": 345.0, \"carbohydrates\": 29.0, \"fat\": 3.0, \"protein\": 46.0, \"sodium\": 971.0, \"sugar\": 1.0}, \"list_of_food_macros\": [{\"food_macros\": {\"calories\": 15.0, \"carbohydrates\": 2.0, \"fat\": 0.0, \"protein\": 2.0, \"sodium\": 51.0, \"sugar\": 0.0}, \"name\": \"Spinach\"}, {\"food_macros\": {\"calories\": 180.0, \"carbohydrates\": 25.0, \"fat\": 2.0, \"protein\": 10.0, \"sodium\": 390.0, \"sugar\": 0.0}, \"name\": \"Right Rice Cilantro Lime Net Carbs Vegetable Rice\"}, {\"food_macros\": {\"calories\": 140.0, \"carbohydrates\": 0.0, \"fat\": 1.0, \"protein\": 34.0, \"sodium\": 300.0, \"sugar\": 0.0}, \"name\": \"Starkist Chunk Light Tuna Pouch\"}, {\"food_macros\": {\"calories\": 10.0, \"carbohydrates\": 2.0, \"fat\": 0.0, \"protein\": 0.0, \"sodium\": 230.0, \"sugar\": 1.0}, \"name\": \"Cleveland Kraut Whiskey Dill Sauerkraut\"}], \"list_of_foods\": [\"Spinach\", \"Right Rice Cilantro Lime Net Carbs Vegetable Rice\", \"Starkist Chunk Light Tuna Pouch\", \"Cleveland Kraut Whiskey Dill Sauerkraut\"]}\n\n{\"date\": \"2020-10-01\", \"meal_type\": \"snacks\", \"total_meal_macros\": {\"calories\": 248.0, \"carbohydrates\": 31.0, \"fat\": 7.0, \"protein\": 21.0, \"sodium\": 263.0, \"sugar\": 4.0}, \"list_of_food_macros\": [{\"food_macros\": {\"calories\": 38.0, \"carbohydrates\": 8.0, \"fat\": 0.0, \"protein\": 1.0, \"sodium\": 13.0, \"sugar\": 3.0}, \"name\": \"cascadian farms organic fire roasted sweet potatoes\"}, {\"food_macros\": {\"calories\": 210.0, \"carbohydrates\": 23.0, \"fat\": 7.0, \"protein\": 20.0, \"sodium\": 250.0, \"sugar\": 1.0}, \"name\": \"Oh Yeah One Protein Bar Dark Chocolate Sea Salt\"}], \"list_of_foods\": [\"cascadian farms organic fire roasted sweet potatoes\", \"Oh Yeah One Protein Bar Dark Chocolate Sea Salt\"]}","_metadata":{"uid":"cs4787ba2379b6b052"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs97fdea550a4bf453"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd the output for the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ealexis_daily_myfitnesspal_total_index\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e index containing the total macros and calories for the day should look something like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8437998d9a8502ec"}}},{"code":{"code":"{'date': '2020-10-01', 'daily_macros': {'calories': 1515.0, 'carbohydrates': 132.0, 'fat': 51.0, 'protein': 143.0, 'sodium': 2285.0, 'sugar': 32.0}}","_metadata":{"uid":"cs3f7d566dd10807b4"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0075ba3429ef5fd2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNext we need to validate that our data is present in our Elastic Cloud cluster. Once logged in, select the menu panel -\u0026gt; Dev Tools.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csab0b9cca2bbe506a"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltfd70121a4879c382","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:18:53.842Z","created_by":"blt92c74e5c4edca909","file_size":"224634","filename":"Screenshot_2023-10-10_at_10.18.41_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.18.41_AM.png","updated_at":"2023-10-10T16:18:53.842Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.554Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfd70121a4879c382/6525796dc85f13250ccd1704/Screenshot_2023-10-10_at_10.18.41_AM.png"},"_metadata":{"uid":"cs941620216115019f"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2a0605054f06aed1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s ensure we have the data for each meal by running the following search request.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa044d4b17d8c52b1"}}},{"code":{"code":"GET alexis_myfitnesspal_diary_official_index/_search","_metadata":{"uid":"csa141c5069cfb375a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0c26a13396baa6b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOutput:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8157c93173f81269"}}},{"code":{"code":" \"_source\": {\n \"date\": \"2023-7-26\",\n \"meal_type\": \"breakfast\",\n \"total_meal_macros\": {\n \"calories\": 466,\n \"carbohydrates\": 64,\n \"fat\": 15,\n \"protein\": 27,\n \"sodium\": 273,\n \"sugar\": 33\n },\n \"list_of_food_macros\": [\n {\n \"food_macros\": {\n \"calories\": 16,\n \"carbohydrates\": 3,\n \"fat\": 0,\n \"protein\": 2,\n \"sodium\": 55,\n \"sugar\": 0\n },\n \"name\": \"Spinach\"\n },\n {\n \"food_macros\": {\n \"calories\": 30,\n \"carbohydrates\": 1,\n \"fat\": 3,\n \"protein\": 1,\n \"sodium\": 135,\n \"sugar\": 0\n },\n \"name\": \"Silk Unsweetened Almond Milk\"\n },\n {\n \"food_macros\": {\n \"calories\": 80,\n \"carbohydrates\": 2,\n \"fat\": 2,\n \"protein\": 15,\n \"sodium\": 80,\n \"sugar\": 1\n },\n \"name\": \"Garden of Life Sport Organic Protein\"\n },\n {\n \"food_macros\": {\n \"calories\": 121,\n \"carbohydrates\": 31,\n \"fat\": 0,\n \"protein\": 2,\n \"sodium\": 1,\n \"sugar\": 17\n },\n \"name\": \"Banana Large Fresh Banana\"\n },\n {\n \"food_macros\": {\n \"calories\": 150,\n \"carbohydrates\": 10,\n \"fat\": 10,\n \"protein\": 6,\n \"sodium\": 0,\n \"sugar\": 0\n },\n \"name\": \"simply nature chia seeds chia seeds\"\n },\n {\n \"food_macros\": {\n \"calories\": 69,\n \"carbohydrates\": 17,\n \"fat\": 0,\n \"protein\": 1,\n \"sodium\": 2,\n \"sugar\": 15\n },\n \"name\": \"Medjoul dates Dates\"\n }\n ],\n \"list_of_foods\": [\n \"Spinach\",\n \"Silk Unsweetened Almond Milk\",\n \"Garden of Life Sport Organic Protein\",\n \"Banana Large Fresh Banana\",\n \"simply nature chia seeds chia seeds\",\n \"Medjoul dates Dates\"\n ]\n }\n }\n...\n","_metadata":{"uid":"cs6ed22bf351eb4afd"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs308a33b7d77ec826"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis index contains not only the total macros, that is the protein, carbs and fats, for each meal, but also the nutrient breakdown for each food item within each meal. Lastly, it provides a full list of the foods consumed in that meal.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, let’s check the index containing the total or overall daily calories and macros by running the following command.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0d8e4f92a542d0d6"}}},{"code":{"code":"GET alexis_daily_myfitnesspal_total_index/_search","_metadata":{"uid":"csa4a5d9b52ee2d381"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs189ea8ef5f1e7b6c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOutput:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9bad8a2edfca3738"}}},{"code":{"code":"{\n \"hits\": {\n \"total\": {\n \"value\": 213,\n \"relation\": \"eq\"\n },\n \"max_score\": 1,\n \"hits\": [\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"9wBzQ4oBg_eLj9VFLbl4\",\n \"_score\": 1,\n \"_source\": {\n \"date\": \"2020-10-01\",\n \"daily_macros\": {\n \"calories\": 1515,\n \"carbohydrates\": 132,\n \"fat\": 51,\n \"protein\": 143,\n \"sodium\": 2285,\n \"sugar\": 32\n }\n }\n },\n ]\n}","_metadata":{"uid":"cs670a64b039efd2a8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd9e15097e3fe075b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs you can see in the above example, I consumed 1515 calories in total on Oct. 01, 2020.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAlthough retrieving meal entries for a specific day is great, this can be done by simply clicking on a day in the MyFitnessPal app. A more useful way to explore our data is by searching for multiple days over a period of time to gain deeper insight into any possible trends.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s say we wanted to view all meals for a full month. We can run a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-bool-query.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ebool query\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with a given date range. In this case, I chose the month of December, but feel free to choose any month.As you can see in the above example, I consumed 1515 calories in total on Oct. 01, 2020.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAlthough retrieving meal entries for a specific day is great, this can be done by simply clicking on a day in the MyFitnessPal app. A more useful way to explore our data is by searching for multiple days over a period of time to gain deeper insight into any possible trends.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s say we wanted to view all meals for a full month. We can run a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-bool-query.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ebool query\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with a given date range. In this case, I chose the month of December, but feel free to choose any month.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cseddd5ec09d7d8c81"}}},{"code":{"code":"GET alexis_myfitnesspal_diary_official_index/_search\n{\n \"query\": {\n \"bool\": {\n \"filter\": [\n {\n \"range\": {\n \"date\" : {\n \t\"gte\": \"2020-12-01\",\n \t\"lte\": \"2020-12-30\"\n }\n }\n }\n ]\n }\n }\n}","_metadata":{"uid":"csfa51488f893e1da9"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs96fb9a868edd4905"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOutput:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9bb60eaef83b439e"}}},{"code":{"code":"{\n \"took\": 3,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 114,\n \"relation\": \"eq\"\n },\n \"max_score\": 0,\n \"hits\": [\n {\n \"_index\": \"alexis_myfitnesspal_diary_official_index\",\n \"_id\": \"hQB0Q4oBg_eLj9VFoLqY\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-12-01\",\n \"meal_type\": \"breakfast\",\n \"total_meal_macros\": {\n \"calories\": 369,\n \"carbohydrates\": 32,\n \"fat\": 18,\n \"protein\": 24,\n \"sodium\": 184,\n \"sugar\": 11\n },\n \"list_of_food_macros\": [\n {\n \"food_macros\": {\n \"calories\": 4,\n \"carbohydrates\": 1,\n \"fat\": 0,\n \"protein\": 0,\n \"sodium\": 25,\n \"sugar\": 0\n },\n \"name\": \"Lily of the Desert Aloe Vera Juice\"\n },\n {\n \"food_macros\": {\n \"calories\": 160,\n \"carbohydrates\": 9,\n \"fat\": 11,\n \"protein\": 6,\n \"sodium\": 0,\n \"sugar\": 0\n },\n \"name\": \"365 Whole Foods Market Organic Black Chia Seeds\"\n },\n {\n \"food_macros\": {\n \"calories\": 24,\n \"carbohydrates\": 4,\n \"fat\": 0,\n \"protein\": 2,\n \"sodium\": 78,\n \"sugar\": 1\n },\n \"name\": \"Spinach Baby Spinach\"\n },\n {\n \"food_macros\": {\n \"calories\": 40,\n \"carbohydrates\": 0,\n \"fat\": 5,\n \"protein\": 0,\n \"sodium\": 0,\n \"sugar\": 0\n },\n \"name\": \"Carlson Wild Norwegian Cod Liver Oil\"\n },\n {\n \"food_macros\": {\n \"calories\": 80,\n \"carbohydrates\": 2,\n \"fat\": 2,\n \"protein\": 15,\n \"sodium\": 80,\n \"sugar\": 1\n },\n \"name\": \"Garden of Life Sport Organic Protein\"\n },\n {\n \"food_macros\": {\n \"calories\": 61,\n \"carbohydrates\": 16,\n \"fat\": 0,\n \"protein\": 1,\n \"sodium\": 1,\n \"sugar\": 9\n },\n \"name\": \"Banana Large Fresh Banana\"\n }\n ],\n \"list_of_foods\": [\n \"Lily of the Desert Aloe Vera Juice\",\n \"365 Whole Foods Market Organic Black Chia Seeds\",\n \"Spinach Baby Spinach\",\n \"Carlson Wild Norwegian Cod Liver Oil\",\n \"Garden of Life Sport Organic Protein\",\n \"Banana Large Fresh Banana\"\n ]\n }\n },\n...","_metadata":{"uid":"cs773dd755a1a94769"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csae9a524c202374a6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs you can see, we get back all the meals for each day in the month of December starting with the 1st.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow let’s say we wanted to filter by meal type. We can search for all meal entries where the meal_type is set to snack.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf98c1ec48c373a4"}}},{"code":{"code":"GET alexis_myfitnesspal_diary_official_index/_search\n{\n \"query\": {\n \"match\": {\n \"meal_type\": \"snacks\"\n }\n }\n}","_metadata":{"uid":"cs91c6a211cffe8a3c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs40dc4751a1db19bf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOutput:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csceff5e4af15e3289"}}},{"code":{"code":"{\n \"took\": 1,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 212,\n \"relation\": \"eq\"\n },\n \"max_score\": 1.3442461,\n \"hits\": [\n {\n \"_index\": \"alexis_myfitnesspal_diary_official_index\",\n \"_id\": \"-QBzQ4oBg_eLj9VFMLmf\",\n \"_score\": 1.3442461,\n \"_source\": {\n \"date\": \"2020-10-01\",\n \"meal_type\": \"snacks\",\n \"total_meal_macros\": {\n \"calories\": 248,\n \"carbohydrates\": 31,\n \"fat\": 7,\n \"protein\": 21,\n \"sodium\": 263,\n \"sugar\": 4\n },\n \"list_of_food_macros\": [\n {\n \"food_macros\": {\n \"calories\": 38,\n \"carbohydrates\": 8,\n \"fat\": 0,\n \"protein\": 1,\n \"sodium\": 13,\n \"sugar\": 3\n },\n \"name\": \"cascadian farms organic fire roasted sweet potatoes\"\n },\n {\n \"food_macros\": {\n \"calories\": 210,\n \"carbohydrates\": 23,\n \"fat\": 7,\n \"protein\": 20,\n \"sodium\": 250,\n \"sugar\": 1\n },\n \"name\": \"Oh Yeah One Protein Bar Dark Chocolate Sea Salt\"\n }\n ],\n \"list_of_foods\": [\n \"cascadian farms organic fire roasted sweet potatoes\",\n \"Oh Yeah One Protein Bar Dark Chocolate Sea Salt\"\n ]\n }\n },\n...","_metadata":{"uid":"cs5660c12e165650c6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs880438619e818339"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNot only can you search for specific meals, but you can also search for meals within a given meal_type in which a certain food was consumed. For instance, you could search for all the days you consumed black chia seeds for breakfast.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs57a7ed0d86b228dc"}}},{"code":{"code":"GET alexis_myfitnesspal_diary_official_index/_search\n{\n \"query\": {\n \"bool\": {\n \"must\": [\n {\"match\": { \"list_of_foods\": \"Black Chia Seeds\" }}\n ],\n \"filter\": [\n {\"term\" : {\"meal_type\": \"breakfast\"}}\n ]\n }\n }\n}","_metadata":{"uid":"csab089ab9208ae72b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd41ace30663b23f4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOutput:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs592595d491089d19"}}},{"code":{"code":"{\n \"took\": 1,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 60,\n \"relation\": \"eq\"\n },\n \"max_score\": 7.762555,\n \"hits\": [\n {\n \"_index\": \"alexis_myfitnesspal_diary_official_index\",\n \"_id\": \"PQBzQ4oBg_eLj9VFzbrS\",\n \"_score\": 7.762555,\n \"_source\": {\n \"date\": \"2020-10-28\",\n \"meal_type\": \"breakfast\",\n \"total_meal_macros\": {\n \"calories\": 380,\n \"carbohydrates\": 11,\n \"fat\": 23,\n \"protein\": 33,\n \"sodium\": 220,\n \"sugar\": 1\n },\n \"list_of_food_macros\": [\n {\n \"food_macros\": {\n \"calories\": 160,\n \"carbohydrates\": 9,\n \"fat\": 11,\n \"protein\": 6,\n \"sodium\": 0,\n \"sugar\": 0\n },\n \"name\": \"365 Whole Foods Market Organic Black Chia Seeds\"\n },\n {\n \"food_macros\": {\n \"calories\": 80,\n \"carbohydrates\": 2,\n \"fat\": 2,\n \"protein\": 15,\n \"sodium\": 80,\n \"sugar\": 1\n },\n \"name\": \"Garden of Life Sport Organic Protein\"\n },\n {\n \"food_macros\": {\n \"calories\": 140,\n \"carbohydrates\": 0,\n \"fat\": 10,\n \"protein\": 12,\n \"sodium\": 140,\n \"sugar\": 0\n },\n \"name\": \"Nice eggs Eggs\"\n }\n ],\n \"list_of_foods\": [\n \"365 Whole Foods Market Organic Black Chia Seeds\",\n \"Garden of Life Sport Organic Protein\",\n \"Nice eggs Eggs\"\n ]\n }\n },","_metadata":{"uid":"cs2d37199840d9834b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs10614d835cc86194"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs you can see, there are 60 days in my index, where black chia seeds were consumed for breakfast.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile we are searching on a list field, It’s important to note there is no dedicated array data type in Elasticsearch. Therefore, it is best to use the nested data types in cases where you want to be able to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/array.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003equery objects in an array\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e independent from each other.\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlong with querying for specific foods consumed in a certain meal of the day, we can also view our total calories and macros for each day within a month by running the previous command against our \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ealexis_daily_myfitnesspal_total_index\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e index.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1593f5814416c4cb"}}},{"code":{"code":"GET alexis_daily_myfitnesspal_total_index/_search\n{\n \"query\": {\n \"bool\": {\n \"filter\": [\n {\n \"range\": {\n \"date\" : {\n \"gte\": \"2020-12-01\",\n \"lte\": \"2020-12-30\"\n }\n }\n }\n ]\n }\n }\n}","_metadata":{"uid":"cs1664d65e41ed5aaf"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaaebdbbcaa8d16ff"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOutput:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7e1f79e13765788e"}}},{"code":{"code":"{\n \"took\": 0,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 30,\n \"relation\": \"eq\"\n },\n \"max_score\": 0,\n \"hits\": [\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"kg50Q4oBSJjU8Is4oIRw\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-12-01\",\n \"daily_macros\": {\n \"calories\": 1632,\n \"carbohydrates\": 97,\n \"fat\": 69,\n \"protein\": 158,\n \"sodium\": 1075,\n \"sugar\": 33\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"hwB0Q4oBg_eLj9VFprrK\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-12-02\",\n \"daily_macros\": {\n \"calories\": 1622,\n \"carbohydrates\": 90,\n \"fat\": 73,\n \"protein\": 151,\n \"sodium\": 1263,\n \"sugar\": 29\n }\n }\n },","_metadata":{"uid":"cs784f37d09579eb82"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd45c29bd710a6f6c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis is great preparation for the visuals we will create later on this tutorial using this data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn important principle I’ve learned throughout my fitness journey is that I have to keep my calorie intake below my maintenance calories in order to continue to see progress.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo a helpful search in determining how long you’ve consistently accomplished this goal is by seeing the amount of days my calories fell below maintenance. In my case, my maintenance calories were around 1,800 and above. So any days where my calories were below this number would indicate that I was in a caloric deficit.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere, I’ll again use bool query to view all the days my calories fell within a calorie deficit.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscf9d643c6ae05fa8"}}},{"code":{"code":"GET alexis_daily_myfitnesspal_total_index/_search\n{\n \"query\": { \n \"bool\": { \n \"filter\": [ \n { \"range\": { \"daily_macros.calories\": { \"gte\": 1400 }}},\n { \"range\": { \"daily_macros.calories\": { \"lte\": 1800 }}}\n ]\n }\n }\n}","_metadata":{"uid":"cs976b41161927381b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse5e145dd0d84694f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOutput:\u003c/p\u003e"}],"_metadata":{"uid":"cse9dba991612ff6ea"}}},{"code":{"code":"{\n \"took\": 1,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 137,\n \"relation\": \"eq\"\n },\n \"max_score\": 0,\n \"hits\": [\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"9wBzQ4oBg_eLj9VFLbl4\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-01\",\n \"daily_macros\": {\n \"calories\": 1515,\n \"carbohydrates\": 132,\n \"fat\": 51,\n \"protein\": 143,\n \"sodium\": 2285,\n \"sugar\": 32\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"-gBzQ4oBg_eLj9VFNbnD\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-02\",\n \"daily_macros\": {\n \"calories\": 1509,\n \"carbohydrates\": 151,\n \"fat\": 52,\n \"protein\": 131,\n \"sodium\": 1710,\n \"sugar\": 28\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"_gBzQ4oBg_eLj9VFO7mn\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-03\",\n \"daily_macros\": {\n \"calories\": 1504,\n \"carbohydrates\": 135,\n \"fat\": 51,\n \"protein\": 132,\n \"sodium\": 1477,\n \"sugar\": 50\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"9A5zQ4oBSJjU8Is4QYOr\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-04\",\n \"daily_macros\": {\n \"calories\": 1518,\n \"carbohydrates\": 126,\n \"fat\": 65,\n \"protein\": 119,\n \"sodium\": 1481,\n \"sugar\": 31\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"AgBzQ4oBg_eLj9VFR7qI\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-05\",\n \"daily_macros\": {\n \"calories\": 1537,\n \"carbohydrates\": 152,\n \"fat\": 46,\n \"protein\": 126,\n \"sodium\": 2339,\n \"sugar\": 44\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"BQBzQ4oBg_eLj9VFTbrq\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-06\",\n \"daily_macros\": {\n \"calories\": 1497,\n \"carbohydrates\": 127,\n \"fat\": 56,\n \"protein\": 130,\n \"sodium\": 1614,\n \"sugar\": 30\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"-g5zQ4oBSJjU8Is4U4MH\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-07\",\n \"daily_macros\": {\n \"calories\": 1493,\n \"carbohydrates\": 144,\n \"fat\": 53,\n \"protein\": 120,\n \"sodium\": 2114,\n \"sugar\": 32\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"DgBzQ4oBg_eLj9VFWLr7\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-08\",\n \"daily_macros\": {\n \"calories\": 1508,\n \"carbohydrates\": 135,\n \"fat\": 54,\n \"protein\": 113,\n \"sodium\": 2121,\n \"sugar\": 33\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"EQBzQ4oBg_eLj9VFXrre\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-09\",\n \"daily_macros\": {\n \"calories\": 1502,\n \"carbohydrates\": 136,\n \"fat\": 53,\n \"protein\": 128,\n \"sodium\": 1253,\n \"sugar\": 42\n }\n }\n },\n {\n \"_index\": \"alexis_daily_myfitnesspal_total_index\",\n \"_id\": \"_w5zQ4oBSJjU8Is4ZIMH\",\n \"_score\": 0,\n \"_source\": {\n \"date\": \"2020-10-10\",\n \"daily_macros\": {\n \"calories\": 1518,\n \"carbohydrates\": 127,\n \"fat\": 60,\n \"protein\": 125,\n \"sodium\": 2598,\n \"sugar\": 39\n }\n }\n }\n ]\n }\n}","_metadata":{"uid":"csbbc8d98de76778ee"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd3a6b17279a1df0a"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eVisualization with Kibana\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow that we understand our data a little better, we can create a health dashboard showing the trends in our data at a glance.\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUnder the menu tab, select \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDashboard\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e in the Analytics section. Then, click \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCreate dashboard\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to the right.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb6fc13f1dfe3af83"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt843cbb85907882ef","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:25:00.048Z","created_by":"blt92c74e5c4edca909","file_size":"102200","filename":"Screenshot_2023-10-10_at_10.24.48_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.24.48_AM.png","updated_at":"2023-10-10T16:25:00.048Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.164Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt843cbb85907882ef/65257adc0819466c36b3462b/Screenshot_2023-10-10_at_10.24.48_AM.png"},"_metadata":{"uid":"cs39b4e699bf0fb208"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt36057cb578ea9227","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:25:43.762Z","created_by":"blt92c74e5c4edca909","file_size":"87611","filename":"Screenshot_2023-10-10_at_10.25.36_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.25.36_AM.png","updated_at":"2023-10-10T16:25:43.762Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.743Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt36057cb578ea9227/65257b079e3c1b39b8fa286c/Screenshot_2023-10-10_at_10.25.36_AM.png"},"_metadata":{"uid":"cs8fe6c0be60242ab1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt85ecdd8bfdc7ce4b","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:26:06.194Z","created_by":"blt92c74e5c4edca909","file_size":"93507","filename":"Screenshot_2023-10-10_at_10.25.53_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.25.53_AM.png","updated_at":"2023-10-10T16:26:06.194Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.461Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt85ecdd8bfdc7ce4b/65257b1e3488c1fa6720ddf7/Screenshot_2023-10-10_at_10.25.53_AM.png"},"_metadata":{"uid":"csf206db7586c25e78"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5abe88b087ff59f4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt might also be helpful to add your Maintenance Calories to the dashboard to compare the rest of your data. Maintenance calories are the minimum amount of calories your body requires to maintain your current bodyweight. This is determined by metrics like your weight, height, and/or body fat percentage. If you aren’t sure about your specific maintenance calories, you can use this \u003c/span\u003e\u003ca href=\"https://tdeecalculator.net/\"\u003e\u003cspan style='font-size: 12pt;'\u003eonline calculator\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to calculate them.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter inputting your information, you should receive this calorie breakdown.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfa90f92762500242"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt0ac23c5b21e94129","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:26:42.640Z","created_by":"blt92c74e5c4edca909","file_size":"143406","filename":"Screenshot_2023-10-10_at_10.26.30_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.26.30_AM.png","updated_at":"2023-10-10T16:26:42.640Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.161Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0ac23c5b21e94129/65257b42d8b0122e74e97f47/Screenshot_2023-10-10_at_10.26.30_AM.png"},"_metadata":{"uid":"cs4c6590a119213b91"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa031fafe4ef494da"},"header_style":"H2","paragraph_l10n":"\u003cspan style=\"font-size: 12pt;\"\u003eWe can start with the maintenance calories for the Sedentary option. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLet’s manually add this number to our dashboard and save the markdown control.\u003c/span\u003e"}],"_metadata":{"uid":"cs8c51d5a812974be2"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt9c614be62180a0f7","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:27:29.701Z","created_by":"blt92c74e5c4edca909","file_size":"168939","filename":"Screenshot_2023-10-10_at_10.27.16_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.27.16_AM.png","updated_at":"2023-10-10T16:27:29.701Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:01.274Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9c614be62180a0f7/65257b71ea594f45130141eb/Screenshot_2023-10-10_at_10.27.16_AM.png"},"_metadata":{"uid":"cs0bd43805ad78d5c1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs202f1c6636547954"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe last metric we will manually add is our Basal Metabolic Rate. This is the amount of calories we burn at rest. So if we did nothing for an entire day, this is the number of calories we are guaranteed to burn. We can grab this number from the previous online calculator we used located above the maintenance calories.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse379bce6624de9ab"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt994637c9d5aee370","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:28:00.246Z","created_by":"blt92c74e5c4edca909","file_size":"143984","filename":"Screenshot_2023-10-10_at_10.27.50_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.27.50_AM.png","updated_at":"2023-10-10T16:28:00.246Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:01.276Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt994637c9d5aee370/65257b905679eb1cef6df104/Screenshot_2023-10-10_at_10.27.50_AM.png"},"_metadata":{"uid":"cse07e922b7a0bf8f6"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt5a89aea8080abcc1","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:28:22.057Z","created_by":"blt92c74e5c4edca909","file_size":"117074","filename":"Screenshot_2023-10-10_at_10.28.06_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.28.06_AM.png","updated_at":"2023-10-10T16:28:22.057Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.163Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5a89aea8080abcc1/65257ba6fabb8d0e61dc7d7a/Screenshot_2023-10-10_at_10.28.06_AM.png"},"_metadata":{"uid":"csb88e1617fffc6d00"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc8c3a435badee9eb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow let’s create visualizations based on the data we stored in our indices. Be sure to choose the desired date range for your dashboard. In my case, I’ll be viewing the data from my initial fitness journey from October 1, 2020, through May 1, 2021.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs02ce704a4cfc000d"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt66822b7a1caf1ab9","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:28:53.363Z","created_by":"blt92c74e5c4edca909","file_size":"51486","filename":"Screenshot_2023-10-10_at_10.28.40_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.28.40_AM.png","updated_at":"2023-10-10T16:28:53.363Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.168Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt66822b7a1caf1ab9/65257bc57a2689ee7005c5de/Screenshot_2023-10-10_at_10.28.40_AM.png"},"_metadata":{"uid":"cse306477bef3346ec"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6d8aed1366d3a81e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow let’s calculate the average amount of calories consumed over a given time period. As this is a simple statistic, it’s good to use a Metric \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/lens.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eLens visualization\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. For this metric, we’ll be using the index containing our total calories per day.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eAverage Calories metric\u003c/h2\u003e"}],"_metadata":{"uid":"csaa0dc6b1817a0d32"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt1db4ca23c1a8ab0b","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:29:32.077Z","created_by":"blt92c74e5c4edca909","file_size":"42516","filename":"Screenshot_2023-10-10_at_10.29.20_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.29.20_AM.png","updated_at":"2023-10-10T16:29:32.077Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.527Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1db4ca23c1a8ab0b/65257bec9d1a1cf4beb37852/Screenshot_2023-10-10_at_10.29.20_AM.png"},"_metadata":{"uid":"cs52346baf647a0a58"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"video":{"vidyard_uuid":"tQEZLkkcwDGauNASbGq6JQ","_metadata":{"uid":"cs47f1aa49c5c08924"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csed3938845b6c20c2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs you can see, we used the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ealexis_daily_myfitnesspal_total_index\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e index to calculate the average calories consumed over a given period of time. This can be helpful in determining whether the calories consumed on average were generally below or above your maintenance calories.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eCalories Over Time\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003eNow let’s create a line graph that tracks my calories from October 2020 to May 2021.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003eFor this graph, we’ll be using the index containing our total calories and macros per day.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7c3e044ffec1e812"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltbf6f4b6dc86558a5","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:54:41.127Z","created_by":"blt92c74e5c4edca909","file_size":"168243","filename":"Screenshot_2023-10-10_at_10.54.31_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.54.31_AM.png","updated_at":"2023-10-10T16:54:41.127Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.906Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf6f4b6dc86558a5/652581d1600b6569a935b112/Screenshot_2023-10-10_at_10.54.31_AM.png"},"_metadata":{"uid":"csd7bc3a02b9322561"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"video":{"vidyard_uuid":"RMg2DqkENp5QB9VHttajCk","_metadata":{"uid":"cs93c1aef466e74581"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb543903ada3b305f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis graph is helpful for identifying anomalies or spikes in my calories. Further context can be provided as far as whether these spikes correlated with specific holidays, which could attest for a huge surplus in calories. Perhaps, the spikes are a clerical error or the result of disproportionate percentages for important macronutrients such as protein.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn our next graph, we’ll add a line graph representing the trends for protein, carbs, and fats.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor this graph, we’ll be using the index containing our total calories and macros per day.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e\u003cspan\u003eMacros Over Time\u003c/span\u003e\u003c/h2\u003e"}],"_metadata":{"uid":"cs50ef99c977d11a39"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt2ec332618a46f8aa","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:55:56.123Z","created_by":"blt92c74e5c4edca909","file_size":"297028","filename":"Screenshot_2023-10-10_at_10.55.43_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.55.43_AM.png","updated_at":"2023-10-10T16:55:56.123Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.376Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2ec332618a46f8aa/6525821c8332d833390d965b/Screenshot_2023-10-10_at_10.55.43_AM.png"},"_metadata":{"uid":"cs1e4dc941e99a4588"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"video":{"vidyard_uuid":"qTAABJmyqRKZmxnfyt2npj","_metadata":{"uid":"cs77cf8273b23a6acb"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7475f3bfbec06093"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis graph can be helpful in comparison to the calories graph. You can use it to view the macro breakdown for days in which spikes in calories occured.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eNutrition Table\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor the Nutrition Table, we’ll be using the index containing our total calories and macros per day.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfa02801b55663e01"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt594e47d5fbd0b811","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:56:43.480Z","created_by":"blt92c74e5c4edca909","file_size":"166937","filename":"Screenshot_2023-10-10_at_10.56.34_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.56.34_AM.png","updated_at":"2023-10-10T16:56:43.480Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.763Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt594e47d5fbd0b811/6525824b2a3548198da7bc95/Screenshot_2023-10-10_at_10.56.34_AM.png"},"_metadata":{"uid":"csfc12f8940821a7c9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"video":{"vidyard_uuid":"2cLTWfq3U6ogYcVRcVzPVH","_metadata":{"uid":"cs688417ddcdcf33bd"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs20aa5bc518e58904"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDetecting the root cause of a spike in calories can be determined using the graphs, but in some cases having a tabular view of both calories and macronutrients allows for further investigation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor instance, the calorie line graph shows a spike on 2020-11-06. When I compare this spike with the macro table, I see a dramatic increase in my protein is the cause of the spike. After referencing this with my food diary, I was able to see that a protein source was accidentally inputted multiple times causing the spike.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eTotal days in Caloric Deficit / Caloric Surplus\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor the Caloric Deficit / Caloric Surplus graph, we’ll be using the index containing our total calories per day.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9e9393bd2ee364db"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt8cfa1c5167e3ea31","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:57:39.612Z","created_by":"blt92c74e5c4edca909","file_size":"82986","filename":"Screenshot_2023-10-10_at_10.57.28_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.57.28_AM.png","updated_at":"2023-10-10T16:57:39.612Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.916Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8cfa1c5167e3ea31/65258283fabb8d10b1dc7da8/Screenshot_2023-10-10_at_10.57.28_AM.png"},"_metadata":{"uid":"cs9042113d250ae7f1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"video":{"vidyard_uuid":"2WZStvsGiaz9ypdyKdt9a8","_metadata":{"uid":"csa1edded3117759b7"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd251b07446161085"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs you can see, we created a bar graph based on calorie ranges. Since I know both my Maintenance Calories as well as my Basal Metabolic Rate, I can determine the amount of days I was in a calorie deficit compared to the time I ate at maintenance. Lastly, I included the total days for my fitness journey by including all calories 1,400 and above.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis can be helpful during plateaus, which are time periods where you experience little to no progress in fat loss or strength gain. These can sometimes occur after being in a caloric deficit too long. The above graph can be used to determine when it’s time to bring your calories back up to maintenance.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eAverage Calories per Week\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this next graph, we’ll be visualizing the moving average for calories per week. For this graph, we’ll be using the index containing our total calories per day.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd85d2eadc9614fe9"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blta552094221f9409a","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:58:37.266Z","created_by":"blt92c74e5c4edca909","file_size":"138459","filename":"Screenshot_2023-10-10_at_10.58.27_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.58.27_AM.png","updated_at":"2023-10-10T16:58:37.266Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.534Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta552094221f9409a/652582bd5679ebe31b6df130/Screenshot_2023-10-10_at_10.58.27_AM.png"},"_metadata":{"uid":"csa3e54c4dc108eb6e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"video":{"vidyard_uuid":"BYiPkB9M2vF6iPPGnDPWQq","_metadata":{"uid":"cs4dfdea2c31ac170e"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs565b5244d19d5700"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this graph, we are able to view our average amount of calories per week. This again gives us a visual at a glance of where our calories generally fell over a period of time. As you can see, I spent almost five months eating below maintenance.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eTop 10 Most Consumed Foods\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLastly, we’ll be creating a tag cloud to represent the top 10 foods most consumed over a given time period. For this visual, we’ll be using the index containing the individual meals.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs73e6f1cd498917ac"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltab4a688e6d9a2fcd","ACL":{},"content_type":"image/png","created_at":"2023-10-10T16:59:24.239Z","created_by":"blt92c74e5c4edca909","file_size":"194079","filename":"Screenshot_2023-10-10_at_10.59.10_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.59.10_AM.png","updated_at":"2023-10-10T16:59:24.239Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.174Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltab4a688e6d9a2fcd/652582ecd44a28a9a3fdbb68/Screenshot_2023-10-10_at_10.59.10_AM.png"},"_metadata":{"uid":"csfb67a99988945a8b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"video":{"vidyard_uuid":"EAcZraQWvtoVtmw6XNWY4C","_metadata":{"uid":"cs64364a1efad9d692"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1ed380919da00627"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere, we have a tag cloud used to showcase my top foods consumed. This can be modified to include top 5, top 20, or whatever number you think is best. This can be helpful in understanding foods you should maybe decrease or possibly foods you should eat more of in your fitness journey.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYour completed dashboard should look something like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3165594e72ff4b73"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltefef364e27ea32c7","ACL":{},"content_type":"image/png","created_at":"2023-10-10T17:00:11.583Z","created_by":"blt92c74e5c4edca909","file_size":"483070","filename":"Screenshot_2023-10-10_at_10.59.59_AM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-10-10_at_10.59.59_AM.png","updated_at":"2023-10-10T17:00:11.583Z","updated_by":"blt92c74e5c4edca909","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.529Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltefef364e27ea32c7/6525831bfabb8d51dddc7db1/Screenshot_2023-10-10_at_10.59.59_AM.png"},"_metadata":{"uid":"cs30854b65a318d8e7"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs76ff026759b99955"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eLimitations\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSince this approach relies on a library independent of MyFitnessPal and uses cookies to log in, it is only a viable approach as long as the website allows access.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eFuture implementations\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThough the goal of this tutorial was to reflect meal entries for a single user, having data from multiple users will create data on a macro level, especially when considering geo locations, like the typical eating habits of people in a given region in comparison to others. Also, adding data from other apps that track exercise, sleep, or steps would add an additional layer in considering all contributing factors with regard to health.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eLeveraging Elasticsearch to make better health decisions\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUnderstanding the power of Elasticsearch starts with using it to understand real life data. Using Elasticsearch, we were not only able to search for specific foods and meals within a date range, but also visualize trends that can help inform future health and fitness decisions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReady to get started with tracking your own fitness journey with Elastic? Begin a \u003c/span\u003e\u003ca href=\"http://cloud.elastic.co/registration\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efree trial of Elastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs662fdf3161e1d5c4"}}},{"callout":{"title_l10n":"Resources","_metadata":{"uid":"cs7e40a5d2de6d769c"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/client/python-api/current/index.html\"\u003eElasticsearch Python Client\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://python-myfitnesspal.readthedocs.io/en/latest/getting_started.html\"\u003ePython MyFitnessPal documentation\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/dashboard.html\"\u003eKibana dashboard and visualization guide\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd17cbfe13a3746d1"},"header_style":"H2","paragraph_l10n":"\u003cem\u003e\u003c/em\u003e\u003cspan\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e"}],"_metadata":{"uid":"cs7c2bc9283b91bfb6"}}}],"publish_date":"2023-10-12T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Inform your personal fitness journey with Elasticsearch queries and Kibana","seo_description_l10n":"In this blog, we will use the Elasticsearch Python Client to send MyFitnessPal data to Elastic in order to better understand the trends and behaviors surrounding our nutrition.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt4dbe5c8d09c853e9","ACL":{},"content_type":"image/png","created_at":"2022-06-01T19:17:21.589Z","created_by":"blt3044324473ef223b70bc674c","file_size":"145165","filename":"illustration-elastic-search-gear-v2-1680x980.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"illustration-elastic-search-gear-v2-1680x980.png","updated_at":"2022-06-01T19:17:21.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-10-12T13:00:00.920Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4dbe5c8d09c853e9/6297bb4124e98e0f7a82fe8e/illustration-elastic-search-gear-v2-1680x980.png"},"title":"Inform your personal fitness journey with Elasticsearch queries and Kibana","title_l10n":"Inform your personal fitness journey with Elasticsearch queries and Kibana","updated_at":"2025-03-28T13:38:51.788Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/inform-your-personal-fitness-journey-elasticsearch-queries-kibana","publish_details":{"time":"2025-03-28T13:38:58.436Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt44f66caf7dba9813","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"Meet Nicholas Penning in the latest get to know the Elastic Community series. Nicholas has been in the tech industry for about 20 years, and half of this time has been in cybersecurity.","author":["bltfbd888b393c07a6a"],"category":["blte5cc8450a098ce5e"],"created_at":"2023-11-07T13:36:08.665Z","created_by":"blt92c74e5c4edca909","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscfaaa473a78231a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNicholas Penning has been in the tech industry for about 20 years. Half of this time has been in cybersecurity. He is originally from the state of Wyoming, where he got his foundation in computers from countless hours of building computers and networks and cleaning up infected computer systems. Nicholas continued his education at Dakota State University in South Dakota, where he was able to learn about cybersecurity.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhen did you first embrace Elastic as a technology?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAround 2018, I started exploring the ELK Stack and became very familiar with the ability to ingest and search large volumes of data. The open-source nature of the product was very appealing and made it very easy to get started with the platform.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat is the most memorable moment in your career?\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe most memorable moment was being able to wield Elastic® as an open platform that allowed me and my team to fully automate a process that once took 20 hours a month between 2–3 staff. This was not only a huge time saver, but as an added benefit we could now visualize and search on the data for threats in a new capacity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat do you believe are good opportunities for the cybersecurity field to leverage from generative AI? Any use case you'd like to share?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI believe one good use case for generative AI in the cybersecurity field would be the streamlining of reports. For example, imagine an incident response team has engaged with an adversary and performed all of the steps to successfully mitigate a threat leveraging a search and case management platform that contains all of the data pertaining to an incident. Using generative AI, I could see the opportunity to generate a report that would consist of the entire timeline of events that occurred during the incident, what actions were taken, metrics/kpis, diagrams, and even some good hot wash questions that should be considered to improve the incident handling or detect and prevent similar threats in the future.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eHave you spoken at any meetup groups or conferences? If so, how did you like it?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYes. I have spoken at a virtual ElasticON and a meetup or two. They are great opportunities to network with others in the field, and it’s always a great time to share knowledge and experiences.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat are your favorite things about the Elastic community?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMy favorite things about the Elastic community are how involved Elastic employees are and the variety of organizations (small to large) that are always willing to jump in to solve a problem or answer a question. Everything between understanding features and functionality of the stack to gathering feedback from many of the real-world users out there on emergent or significant issues that can be communicated to Elastic to resolve. The ability to ask a question to such a large and diverse audience has proven to add value to the Elastic product stack. The last thing to mention is that the community is very open to using an instant messaging platform to get great discussions going between beginners and experts of the stack.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eWhat would you recommend for folks who want to start their career in cybersecurity?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eI would recommend that anyone getting into cybersecurity should understand the importance of logging computer systems and networks for the purpose of identifying threats. Traditionally this is called a security information and event management system (SIEM), and in my opinion, it is one of the most significant tools in a cybersecurity analyst’s toolkit to be effective in thwarting cyber threats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce the concept of SIEM is understood, I would then recommend learning how to script (using Python or Powershell), how to use regular expressions (regex), and how application programming interfaces (APIs) work. The combination of scripting, regex, and APIs will allow you to build just about anything as a cybersecurity analyst to understand and automate tools that will be a force multiplier for security operations-centered careers. The Elastic Stack will assist with all of these recommendations as it has open APIs and highly versatile enrich capabilities to use regex to break your data down to even more useful capacities.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eAny final thoughts you'd like to share?\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe world needs more cybersecurity professionals. It's an exciting career and there are many disciplines, so don't think you need to focus on just one or have to know them all. Lastly, join the cybersecurity communities out there to get more involved by helping or learning from others. Cybersecurity focused communities are something I wish were more prevalent and open 10 years ago when I started, so take advantage of them!\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e(Note: All of these opinions and views are my own and are not intended to reflect those of my employers.)\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs31d1126d3667d280"}}}],"publish_date":"2023-11-08T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Get to know the Elastic Community series: Meet Nicholas Penning","seo_description_l10n":"Get to know the Elastic Community series: Meet Nicholas Penning","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt396934202512795e","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2023-11-07T13:38:25.246Z","created_by":"blt92c74e5c4edca909","file_size":"168117","filename":"Screenshot_2023-11-07_at_6.37.26_AM.jpeg","parent_uid":null,"tags":[],"title":"Screenshot_2023-11-07_at_6.37.26_AM.jpeg","updated_at":"2023-11-07T13:38:25.246Z","updated_by":"blt92c74e5c4edca909","publish_details":{"time":"2023-11-08T14:00:00.600Z","user":"blt92c74e5c4edca909","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt396934202512795e/654a3dd12e735d040a9fae0b/Screenshot_2023-11-07_at_6.37.26_AM.jpeg"},"title":"Get to know the Elastic Community series: Meet Nicholas Penning","title_l10n":"Get to know the Elastic Community series: Meet Nicholas Penning","updated_at":"2025-03-28T13:37:43.045Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/get-to-know-the-elastic-community-series-meet-nicholas-penning","publish_details":{"time":"2025-03-28T13:37:47.961Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6f3f3c4fcb8379ae","_version":21,"locale":"en-us","ACL":{},"abstract_l10n":"Here we discuss the challenges of identifying duplicate logs from problematic services and how to deduplicate data using Elastic Beats, Logstash, and Elastic Agent.","author":["blt265422bc68364b2e"],"category":["blte5cc8450a098ce5e"],"created_at":"2023-11-02T09:56:04.432Z","created_by":"blt1dac765f65376b4a","markdown_l10n":"","modular_blocks":[{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs1c75de31ea0f4f05"},"header_style":null,"markdown_l10n":"# Log deduplication with Elasticsearch\nSREs get flooded by large volumes of logs from noisy applications every day. In his seminal work [The Mythical Man Month](https://www.goodreads.com/work/quotes/1905885-the-mythical-man-month-essays-on-software-engineering), Frederick P. Brooks said that \"all programmers are optimists.\" This optimism manifests in software engineers not putting in controls to stop their applications from sending continuous logs in exceptional failure situations. In large organizations with centralized logging platforms, this flood of events is being ingested into logging platforms and taking up considerable storage volumes and processing compute. On the people side, it leaves SREs feeling overwhelmed and suffering from alert fatigue as they are engulfed by the wave of messages, a bit like this:\n\n\u0026nbsp; \n\n][1]\n\n\u0026nbsp; \n\nDevelopers building software including microservices and key applications are responsible for ensuring they do not send duplicate log events, and that they are sending the correct log events at the right level. Nevertheless, situations such as the use of third-party solutions or maintenance of ageing services mean we cannot always guarantee responsible logging practices have been applied. Even if we drop unnecessary fields as covered in [this piece on pruning fields from incoming log events](https://www.elastic.co/blog/pruning-incoming-log-volumes-with-elastic), we still have an issue with storing large numbers of duplicate events. \nHere we discuss the challenges of identifying duplicate logs from problematic services and how to deduplicate data using Elastic Beats, Logstash, and Elastic Agent.\n## What is a duplicate log entry?\nBefore diving into the various ways of preventing these duplicates from making it into your logging platform, we need to understand what a duplicate is. In my prior life as a software engineer, I was responsible for developing and maintaining an ecosystem of vast microservices. Some had considered retry logic that, after some time, would shut the service down gracefully and trigger appropriate alerts. However, not all services are built to gracefully handle these cases.\nService misconfiguration can also contribute to event duplication. Inadvertently changing the production log level from `WARN` to `TRACE` can lead to more aggressive event volumes that have to be handled by the logging platform. \n\nElasticsearch automatically generates a unique ID for each document ingested unless a document contains an `_id` field on ingestion. Therefore, if your service is sending repeated alerts, you run the risk of having the same event stored as multiple documents with different IDs.\nAnother cause can be due to retry mechanisms for the tools used for log collection. A notable example is for Filebeat, [where a lost connection or shutdown can cause the retry mechanism of Filebeat to resend an event until the output acknowledges receipt of the event](https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-deduplication.html).\n## Tools Overview\n\nIn this blog we shall examine the tools available in four Elastic tools:\n\n1. [Logstash](https://www.elastic.co/logstash/) is a free and open ETL pipeline tool that allows you to ingest, transform, and output data between a myriad of sources, including ingestion into and output from Elasticsearch. These examples will be used to show the different behaviour of Elasticsearch when generating logs with and without a particular ID.\n2. [Beats](https://www.elastic.co/beats/) are a family of lightweight shippers that allow us to ingest events from a given source into not just Elasticsearch, but also other outputs, including Kafka, Redis, or Logstash.\n3. [Ingest pipelines](https://www.elastic.co/guide/en/elasticsearch/reference/current/ingest.html) allow for transformations and enrichment to be applied to documents ingested into Elasticsearch. It's like running the `filter` part of Logstash directly into Elasticsearch without the need to have another service running. New pipelines can be created either within the **Stack Management \u003e Ingest Pipelines** screen or via the `_ingest` API, [as covered in the documentation](https://www.elastic.co/guide/en/elasticsearch/reference/current/ingest.html#create-manage-ingest-pipelines).\n4. [Elastic Agent](https://www.elastic.co/guide/en/fleet/current/fleet-overview.html) is a single agent that can execute on your host and send logs, metrics, and security data from multiple services and infrastructure to Elasticsearch using the various supported integrations.\nRegardless of the reason for the duplicates, there are several possible courses of action in the Elastic ecosystem.\n## Ingestion without specified IDs\nThe default approach is to ignore and ingest all events. When an ID is not specified on a document, Elasticsearch will auto-generate a new ID for each document it receives.\nLet's take a simple example, available in [this GitHub repository](https://github.com/carlyrichmond/simple-server), using a [simple Express HTTP server](https://github.com/carlyrichmond/simple-server/blob/main/server.js). The server, when run, exposes a single endpoint returning a single log message:\n\n\n [1]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcb726be86c9c8601/6543831208cc0104077cd7d4/gif.gif"}],"_metadata":{"uid":"cs5204589990332fdd"}}},{"code":{"code":"{\"event\":{\"transaction_id\":1,\"data_set\":\"my-logging-app\"},\"message\":\"WARN: Unable to get an interesting response\"}","_metadata":{"uid":"cs4127d6210afeceac"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs169d66d6efaf171e"},"header_style":null,"markdown_l10n":"Using Logstash we can poll the endpoint `http://locahost:3000/` every 60 seconds and send the result to Elasticsearch. Our `logstash.conf` looks like the below:"}],"_metadata":{"uid":"cs7f67665dddf8b030"}}},{"code":{"code":"input {\n http_poller {\n urls =\u003e {\n simple_server =\u003e \"http://localhost:3000\"\n }\n request_timeout =\u003e 60\n schedule =\u003e { cron =\u003e \"* * * * * UTC\"}\n codec =\u003e \"json\"\n }\n}\noutput {\n elasticsearch { \n cloud_id =\u003e \"${ELASTIC_CLOUD_ID}\" \n cloud_auth =\u003e \"${ELASTIC_CLOUD_AUTH}\"\n index =\u003e \"my-logstash-index\"\n }\n}","_metadata":{"uid":"cs91df66236fb8ef5f"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs86d40f30a307100b"},"header_style":null,"markdown_l10n":"Logstash will push each event, and without any ID on the event Elasticsearch will generate a new [`_id`](https://www.elastic.co/guide/en/elasticsearch/reference/current/mapping-id-field.html) field to serve as a unique identifier for each document:"}],"_metadata":{"uid":"cs22f6c4a623264865"}}},{"code":{"code":"GET my-logstash-index/_search\n{\n \"took\": 0,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 11,\n \"relation\": \"eq\"\n },\n \"max_score\": 1,\n \"hits\": [\n {\n \"_index\": \"my-logstash-index\",\n \"_id\": \"-j83XYsBOwNNS8Sc0Bja\",\n \"_score\": 1,\n \"_source\": {\n \"@version\": \"1\",\n \"event\": {\n \"transaction_id\": 1,\n \"original\": \"\"\"{\"event\":{\"transaction_id\":1,\"data_set\":\"my-logging-app\"},\"message\":\"WARN: Unable to get an interesting response\"}\"\"\",\n \"data_set\": \"my-logging-app\"\n },\n \"message\": \"WARN: Unable to get an interesting response\",\n \"@timestamp\": \"2023-10-23T15:47:00.528205Z\"\n }\n },\n {\n \"_index\": \"my-logstash-index\",\n \"_id\": \"NT84XYsBOwNNS8ScuRlO\",\n \"_score\": 1,\n \"_source\": {\n \"@version\": \"1\",\n \"event\": {\n \"transaction_id\": 1,\n \"original\": \"\"\"{\"event\":{\"transaction_id\":1,\"data_set\":\"my-logging-app\"},\"message\":\"WARN: Unable to get an interesting response\"}\"\"\",\n \"data_set\": \"my-logging-app\"\n },\n \"message\": \"WARN: Unable to get an interesting response\",\n \"@timestamp\": \"2023-10-23T15:48:00.314262Z\"\n }\n },\n // Other documents omitted\n ]\n }\n}","_metadata":{"uid":"cs61f3ab8f0acb9115"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs6e6b3808cfd1dc86"},"header_style":null,"markdown_l10n":"This behavior is consistent for Beats, Ingest Pipelines and Elastic Agent as they will send all events received without additional configuration.\n## BYO-ID\nSpecifying a unique ID for each event using an existing ID bypasses the Elasticsearch ID generation step discussed in the previous section. Ingesting a document where this attribute already exists will result in Elasticsearch checking if a document with this ID exists in the index, and updating the document if it does. This does result in an overhead as the index needs to be searched to check if a document with the same `_id` exists.\nExtending our above Logstash example, specifying the value of the document ID in Logstash is achievable by specifying the `document_id` option in the Elasticsearch output plugin, which would be used to ingest events into Elasticsearch:"}],"_metadata":{"uid":"cs8d521bdf4364955d"}}},{"code":{"code":"# http_poller configuration omitted\noutput {\n elasticsearch { \n cloud_id =\u003e \"${ELASTIC_CLOUD_ID}\" \n cloud_auth =\u003e \"${ELASTIC_CLOUD_AUTH}\"\n index =\u003e \"my-unique-logstash-index\"\n document_id =\u003e \"%{[event][transaction_id]}\"\n }\n}","_metadata":{"uid":"cs04c3ed76cd90f73e"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs5f9811c783fdd5cd"},"header_style":null,"markdown_l10n":"This will set the value of the `_id` field to the value of `event.transaction_id`. In our case, this means the new document will replace the existing document on ingestion as both documents have an `_id` of 1:"}],"_metadata":{"uid":"cs742bab3d46b0b464"}}},{"code":{"code":"GET my-unique-logstash-index/_search\n{\n \"took\": 48,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 1,\n \"relation\": \"eq\"\n },\n \"max_score\": 1,\n \"hits\": [\n {\n \"_index\": \"my-unique-logstash-index\",\n \"_id\": \"1\",\n \"_score\": 1,\n \"_source\": {\n \"@timestamp\": \"2023-10-23T16:33:00.358585Z\",\n \"message\": \"WARN: Unable to get an interesting response\",\n \"@version\": \"1\",\n \"event\": {\n \"original\": \"\"\"{\"event\":{\"transaction_id\":1,\"data_set\":\"my-logging-app\"},\"message\":\"WARN: Unable to get an interesting response\"}\"\"\",\n \"data_set\": \"my-logging-app\",\n \"transaction_id\": 1\n }\n }\n }\n ]\n }\n}","_metadata":{"uid":"csa59b39a305d706cb"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs39146341b31ecb45"},"header_style":null,"markdown_l10n":"The ID is specified in various ways depending on the tool, as discussed further in subsequent sections.\n### Beats \nFor JSON documents, which is a common format for many sources of logs, if your event does have a useful and meaningful ID that can be used as the unique ID for a document and prevent duplicate entries, using either the `decode_json_fields` processor or the `json.document_ID` input setting [as recommended in the documentation](https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-deduplication.html). This approach is preferred over generating a key when a natural key is present within a JSON field within our message.\nBoth settings are shown in the below example:"}],"_metadata":{"uid":"csdc2850890f7ff1c4"}}},{"code":{"code":"filebeat.inputs:\n- type: filestream\n id: my-logging-app\n paths:\n - /var/tmp/other.log\n - /var/log/*.log\n json.document_id: \"event.transaction_id\" \n# Alternative approach using decode_json_fields processor\nprocessors:\n - decode_json_fields:\n document_id: \"event.transaction_id\"\n fields: [\"message\"]\n max_depth: 1\n target: \"\"","_metadata":{"uid":"cs1c75a348364c51f1"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"csb8b816f969594d05"},"header_style":null,"markdown_l10n":"### Ingest pipelines \nIn this case, the ID can be set using a [`set` processor](https://www.elastic.co/guide/en/elasticsearch/reference/current/set-processor.html) combined with the `copy_from` option to transfer the value from your unique field to the Elasticsearch `@metadata._id` attribute:"}],"_metadata":{"uid":"cs5181ba8fb75a5dda"}}},{"code":{"code":"PUT _ingest/pipeline/test-pipeline\n{\n \"processors\": [\n {\n \"set\": {\n \"field\": \"_id\",\n \"copy_from\": \"transaction_id\"\n }\n }\n ]\n}","_metadata":{"uid":"csfecd3e470a8bc21e"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"csa305a3b2bdc4e453"},"header_style":null,"markdown_l10n":"### Elastic Agent\nElastic Agent has a similar approach where you can use the `copy_fields` processor to copy the value to the `@metadata._id` attribute in the integration:"}],"_metadata":{"uid":"cse6fa991747b6c94b"}}},{"code":{"code":"- copy_fields:\n fields:\n - from: transaction_id\n to: @metadata._id\n fail_on_error: true\n ignore_missing: true","_metadata":{"uid":"cs29f8206c70eb8739"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs50597aec8480888f"},"header_style":null,"markdown_l10n":"The `fail_on_error` setting when true will result in a return to the prior state by reverting the changes applied by the failing processor. Meanwhile `ignore_missing` will only trigger a failure for a document with a non-existent field when set to `false`.\n## Auto-generated ID\nGenerating a unique ID using techniques such as [fingerprinting](https://en.wikipedia.org/wiki/Fingerprint_(computing)) on a subset of event fields. By hashing a set of fields a unique value is generated that, when matched, will result in an update of the original document on ingest in Elasticsearch.\n[As this handy piece on handing duplicates with Logstash](https://www.elastic.co/blog/logstash-lessons-handling-duplicates) specifically outlines, the [fingerprint filter plugin](https://www.elastic.co/guide/en/logstash/current/plugins-filters-fingerprint.html) can be configured to generate an ID with the specified hashing algorithm to field `@metadata.fingerprint`:"}],"_metadata":{"uid":"cs8322cd79a073940c"}}},{"code":{"code":"filter {\n fingerprint {\n source =\u003e [\"event.start_date\", \"event.data_set\", \"message\"]\n target =\u003e \"[@metadata][fingerprint]\"\n method =\u003e \"SHA256\"\n }\n}\noutput {\n elasticsearch {\n hosts =\u003e \"my-elastic-cluster.com\"\n document_id =\u003e \"%{[@metadata][fingerprint]}\"\n }\n}","_metadata":{"uid":"csa233486625415566"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs29d4dd816b3f9745"},"header_style":null,"markdown_l10n":"If not specified, the default hashing algorithm `SHA256` will be used to hash the combination `|event.start_date|start_date_value|event.data_set|data_set_value|message|message_value|`. If we wanted to use one of the other permitted algorithm options, it can be specified using the `method` option. This will result in Elasticsearch updating the document matching the generated `_id`:"}],"_metadata":{"uid":"csd2d67ecd9883a6aa"}}},{"code":{"code":"GET my-fingerprinted-logstash-index/_search\n{\n \"took\": 8,\n \"timed_out\": false,\n \"_shards\": {\n \"total\": 1,\n \"successful\": 1,\n \"skipped\": 0,\n \"failed\": 0\n },\n \"hits\": {\n \"total\": {\n \"value\": 1,\n \"relation\": \"eq\"\n },\n \"max_score\": 1,\n \"hits\": [\n {\n \"_index\": \"my-fingerprinted-logstash-index\",\n \"_id\": \"b2faceea91b83a610bf64ac2b12e3d3b95527dc229118d8f819cdfaa4ba98af1\",\n \"_score\": 1,\n \"_source\": {\n \"@timestamp\": \"2023-10-23T16:46:00.772480Z\",\n \"message\": \"WARN: Unable to get an interesting response\",\n \"@version\": \"1\",\n \"event\": {\n \"original\": \"\"\"{\"event\":{\"transaction_id\":1,\"data_set\":\"my-logging-app\"},\"message\":\"WARN: Unable to get an interesting response\"}\"\"\",\n \"data_set\": \"my-logging-app\",\n \"transaction_id\": 1\n }\n }\n }\n ]\n }\n}","_metadata":{"uid":"cs406af845e9e98129"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs0a9646f5b40648f1"},"header_style":null,"markdown_l10n":"If your event does not have a single meaningful identifying field, this may be a useful option if you are happy to take the processing overhead of generating the ID, or the potential for collisions where different events resolve to the same generated hash. Similar capabilities are available for other tools, as discussed in subsequent sections. \n### Beats\nThe [`add_id` processor](https://www.elastic.co/guide/en/beats/filebeat/current/add-id.html) for Beats and Elastic Agent will allow for a unique Elasticsearch-compatible ID to be generated. By default, this value will be stored in the `@metadata._id` field which is the ID field for Elasticsearch documents."}],"_metadata":{"uid":"cs4679de13a47f58e1"}}},{"code":{"code":"filebeat.inputs:\n- type: filestream\n ID: my-logging-app\n paths:\n - /var/tmp/other.log\n - /var/log/*.log\n json.document_ID: \"event.transaction_id\" \nprocessors:\n - add_ID: ~\n target_field: @metadata._id","_metadata":{"uid":"cs4756b3e9b55df636"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"csbf5de0ff9e2addaf"},"header_style":null,"markdown_l10n":"Alternatively, the [`fingerprint` processor](https://www.elastic.co/guide/en/beats/filebeat/current/fingerprint.html) generates a hashed value of a concatenation of the specified field name and value pairs separated by the `|` operator."}],"_metadata":{"uid":"csb136493584c1ee11"}}},{"code":{"code":"filebeat.inputs:\n- type: filestream\n ID: my-logging-app\n paths:\n - /var/tmp/other.log\n - /var/log/*.log\nprocessors:\n - fingerprint:\n fields: [\"event.start_date\", \"event.data_set\", \"message\"]\n target_field: \"@metadata._id\"\n method: \"sha256\"\n ignore_missing: false","_metadata":{"uid":"cs7ee8a91e9807e411"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs28ec0ced696ffdcd"},"header_style":null,"markdown_l10n":"In the above example, the default hashing algorithm [`sha256`](https://en.wikipedia.org/wiki/SHA-2) will be used to hash the combination `|event.start_date|start_date_value|event.data_set|data_set_value|message|message_value|`. If we wanted to use one of the other permitted algorithm options, it can be specified using the `method` option. \nError handling is also an important consideration that the `ignore_missing` option assists with. For example, if the `event.start_date` field does not exist on a given document, an error will be raised when `ignore_missing` is set to `false`. This is the default implementation if `ignore_missing` is not explicitly set, but it's common to ignore errors by specifying the value as `true`.\n\n### Elastic Agent\nJust like Beats, Elastic Agent has an [`add_id` processor](https://www.elastic.co/guide/en/fleet/current/add_id-processor.html) that can be used to generate a unique ID, defaulting to `@metadata._id` if the `target_field` attribute is not specified:"}],"_metadata":{"uid":"cs6fed061ed29e958b"}}},{"code":{"code":" - add_id:\n target_field: \"@metadata._id\"","_metadata":{"uid":"cs64d07aea1281a2f3"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs29c535b9a647984d"},"header_style":null,"markdown_l10n":"Alternatively, the [`fingerprint` processor](https://www.elastic.co/guide/en/fleet/current/fingerprint-processor.html) is also available in Elastic Agent and can be applied to any integration segment that includes an advanced configuration section including a processors option. The processor logic looks like the below:"}],"_metadata":{"uid":"cs03c987d8a0669399"}}},{"code":{"code":" - fingerprint:\n fields: [\"event.start_date\", \"event.data_set\", \"message\"]\n target_field: \"@metadata._id\"\n ignore_missing: false\n method: \"sha256\"","_metadata":{"uid":"cs6474a8624ff97561"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs3b6b2c367a71f037"},"header_style":null,"markdown_l10n":"Taking the [Kafka](https://docs.elastic.co/integrations/kafka) integration as an example, the above processor snippet can be applied in the processor segment of the advanced configuration section for the *Collect logs from Kafka brokers*:\n\n\u0026nbsp;\n\n][1]\n\n\u0026nbsp;\n\nJust like Beats, the value that is hashed is constructed as a concatenation of the field name and field value separated by `|`. For example `|field1|value1|field2|value2|`. However, just like in Beats and unlike in Logstash, the `method` value is in lowercase despite supporting the same encoding algorithms.\n### Ingest pipelines\nHere we'll show the sample request to create a pipeline with a [`fingerprint` processor](https://www.elastic.co/guide/en/elasticsearch/reference/current/fingerprint-processor.html) with the `_ingest` API. Note the similarities of the below configuration to our Beats processors:\n\n\n [1]: https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6a63c6db6d13008d/654384290970dd001bd1637d/image_2_kafka.png"}],"_metadata":{"uid":"cs9215f093b0e152b6"}}},{"code":{"code":"PUT _ingest/pipeline/my-logging-app-pipeline\n{\n \"description\": \"Event and field dropping for my-logging-app\",\n \"processors\": [\n {\n \"fingerprint\": {\n fields: [\"event.start_date\", \"event.data_set\", \"message\"]\n target_field: \"@metadata._id\"\n ignore_missing: false\n method: \"SHA-256\"\n }\n }\n ]\n}","_metadata":{"uid":"csaa45b6336524d60f"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"csfe97b63c8f18b73d"},"header_style":null,"markdown_l10n":"## Aggregate Events\nAggregating events together based on common fields is another option, if the tool using supports it. Aggregation of events comes with a tradeoff as the tool needs to keep several events in memory to perform the aggregation rather than immediately forwarding the event over to the output. For this reason, the only tool within the Elastic ecosystem that supports event aggregation is Logstash.\n\nTo implement the aggregation-based approach in Logstash, use the [`aggregate` plugin](https://www.elastic.co/guide/en/logstash/current/plugins-filters-aggregate.html). In our case, it's unlikely that a specific end event will be sent to distinguish between duplicates, meaning specifying a `timeout` as per the below example is needed to control the batching process:"}],"_metadata":{"uid":"cs5796269d276cf1c5"}}},{"code":{"code":"filter {\n grok {\n match =\u003e [ \"message\", %{NOTSPACE:event.start_date} \"%{LOGLEVEL:loglevel} - %{NOTSPACE:user_ID} - %{GREEDYDATA:message}\" ]\n }\n aggregate {\n task_ID =\u003e \"%{event.start_date}%{loglevel}%{user_ID}\"\n code =\u003e \"map['error_count'] ||= 0; map['error_count'] += 1;\"\n push_map_as_event_on_timeout =\u003e true\n timeout_task_ID_field =\u003e \"user_id\"\n timeout =\u003e 600\n timeout_tags =\u003e ['_aggregatetimeout']\n timeout_code =\u003e \"event.set('has_multiple_occurrences', event.get('error_count') \u003e 1)\"\n }\n}","_metadata":{"uid":"csbc8e3a7d44ea8ed4"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cs55e34c40fbeab928"},"header_style":null,"markdown_l10n":"The above example will send an event after 600 seconds, or 10 minutes, adding the `error_count` and `has_multiple_occurrences` attributes to the event to indicate an aggregated event. The `push_map_as_event_on_timeout` option will ensure that the aggregation result is pushed on each timeout, allowing you to reduce the alert volume. When determining the timeout for your data, consider your volume and opt for the lowest timeout you can as Logstash will hold the events in memory until the timeout expires and the aggregate event is pushed."}],"_metadata":{"uid":"cs5d96e404b68bb0e9"}}},{"markdown":{"markdown":[{"title_l10n":"","_metadata":{"uid":"cse0e8c2e75314c322"},"header_style":null,"markdown_l10n":"## Conclusions\nLog volume spikes can quickly overwhelm logging platforms and SRE engineers looking to maintain reliable applications. We have discussed several approaches to handling duplicate events using Elastic Beats, Logstash (which are available in [this GitHub repository](https://github.com/carlyrichmond/simple-server)), and Elastic Agent.\n\nWhen generating IDs via a hashing algorithm using fingerprint processors, or performing aggregates, consider the attributes used carefully to balance preventing a flood and obfuscating legitimate streams pointing to a large-scale problem in your ecosystem. Both approaches have an overhead, either in terms of processing to generate the ID, or memory overhead to store the documents eligible to aggregate.\n\nSelecting an option really depends on the events you consider duplicates and the performance trade-offs. As discussed, when you specify an ID Elasticsearch needs to check for the existence of a document matching that ID before adding the document to the index. This results in a slight delay in ingestion to perform the `_id` existence check. \n\nUsing hashing algorithms to generate the ID adds additional processing time as the ID needs to be generated for each event before it is compared and potentially ingested. Choosing to not specify an ID bypasses this check as Elastic will generate the ID for you, but will result in all events being stored which increases your storage footprint. \n\nDropping full events is a legitimate practice not covered in this piece. If you want to drop log entries to reduce your volume [check out this piece on pruning fields from incoming log events](https://www.elastic.co/blog/pruning-incoming-log-volumes-with-elastic). \n\nIf your favorite way to deduplicate events is not listed here, do let us know!\n\n## Resources\n1. [Elastic Beats](https://www.elastic.co/beats/)\n2. [Filebeat | Fingerprint processor](https://www.elastic.co/guide/en/beats/filebeat/current/fingerprint.html)\n3. [Filebeat | Decode JSON fields processor](https://www.elastic.co/guide/en/beats/filebeat/current/decode-json-fields.html)\n4. [Filebeat | Filebeat deduplication](https://www.elastic.co/guide/en/beats/filebeat/current/filebeat-deduplication.html)\n5. [Logstash](https://www.elastic.co/logstash/)\n6. [Logstash | Fingerprint plugin](https://www.elastic.co/guide/en/logstash/current/plugins-filters-fingerprint.html)\n7. [Logstash | Aggregate plugin](https://www.elastic.co/guide/en/logstash/current/plugins-filters-aggregate.html)\n8. [Elastic Agent](https://www.elastic.co/guide/en/fleet/current/fleet-overview.html)\n9. [Elastic Agent | Fingerprint processor](https://www.elastic.co/guide/en/fleet/current/fingerprint-processor.html)\n10. [Ingest Pipelines](https://www.elastic.co/guide/en/elasticsearch/reference/current/ingest.html) \n11. [Elasticsearch | Ingest pipeline fingerprint processor](https://www.elastic.co/guide/en/elasticsearch/reference/current/fingerprint-processor.html)"}],"_metadata":{"uid":"csbb7e98a5f87d7050"}}}],"publish_date":"2023-11-06T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Log deduplication with Elasticsearch","seo_description_l10n":"Duplicate events from unhealthy application services make log searching tricky. Check out how to handle duplicates using Logstash, Beats, and Elastic Agent.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Duplicate events from unhealthy application services make log searching tricky. Check out how to handle duplicates using Logstash, Beats and Elastic Agent.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8dc7b808d2bc8325","_version":1,"created_by":"blt1dac765f65376b4a","updated_by":"blt1dac765f65376b4a","created_at":"2023-11-02T11:20:40.739Z","updated_at":"2023-11-02T11:20:40.739Z","content_type":"image/png","file_size":"51730","filename":"elasticsearch.png","title":"elasticsearch.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2023-11-16T15:00:51.639Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8dc7b808d2bc8325/65438608a67ffd001b94e85e/elasticsearch.png"},"title":"Log deduplication with Elasticsearch","title_l10n":"Log deduplication with Elasticsearch","updated_at":"2025-03-28T13:34:41.573Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/log-deduplication-with-elasticsearch","publish_details":{"time":"2025-03-28T13:34:52.620Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltdaca797815499610","_version":45,"locale":"en-us","ACL":{},"abstract_l10n":"Building community is one of our top priorities. We want our employees to feel at home in their local office, so we hired local designers to create murals on the walls of each office to bring to life the essence of each Elastic city. ","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2022-12-19T19:05:53.156Z","created_by":"blt084c51ee83c3308f","markdown_l10n":"\n","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs67888d6f6f9f2cc6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’re a distributed, global company (and proud of it), but we do want to give Elasticisians a place to connect face-to-face should they choose. In fact, building community is one of our top priorities here at Elastic. That’s why we have offices in 15 cities around the world. While some Elasticians use them to work and connect, we also use them to host in-person events, like this summer’s Elasticamp.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCurrently, we have offices in: Amsterdam, Arlington, Austin, Bangalore, Berlin, Chicago, Copenhagen, London, Munich, New York, Paris, San Francisco, Singapore, Sydney, and Tokyo.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhat makes our offices special is that each one is designed with its location in mind. We want our employees to feel at home in their local office, so we hired local designers to create murals on the walls of each office to bring to life the essence, vibrancy, and culture of each Elastic city.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’re so thankful that we’re able to showcase these artists’ designs so our employees can enjoy a piece of local, original art.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHere are some of the murals that decorate our office walls:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAmsterdam\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eArtist: Wallnuts, Jessica Smith\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAmsterdam has two murals: one in a corridor that is city-themed with various homages to Amsterdam (like Stroopwafels and bicycles!) and one with the tagline, “You know…for search!”.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse37b05802749a086"}}},{"image":{"image":{"_version":4,"is_dir":false,"uid":"blt3662bc7ebb56f061","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-19T19:08:06.797Z","created_by":"blt084c51ee83c3308f","description":"","file_size":"680655","filename":"IMG_3306-scaled.jpeg","parent_uid":null,"tags":[],"title":"IMG_3306-scaled.jpeg","updated_at":"2022-12-20T17:03:51.059Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.170Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3662bc7ebb56f061/63a1eaf7221b8b684a7b04ef/IMG_3306-scaled.jpeg"},"_metadata":{"uid":"csf260d3cc84d8ade7"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltbe7f8f686b9c2a16","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-20T17:04:13.274Z","created_by":"blt084c51ee83c3308f","file_size":"541577","filename":"IMG_3334-scaled.jpeg","parent_uid":null,"tags":[],"title":"IMG_3334-scaled.jpeg","updated_at":"2022-12-20T17:04:13.274Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.188Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbe7f8f686b9c2a16/63a1eb0d9ee4de0dca30c132/IMG_3334-scaled.jpeg"},"_metadata":{"uid":"cs2e52ff1957a01c5b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd1b1fa34988c3cdc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eArlington\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Kathy Chen\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArlington, Virginia also has two murals, one in reception and one in the work area. Both feature landmarks in the area and typical architecture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5e2441a240243923"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltef5a348dab2a3aee","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:05:16.552Z","created_by":"blt084c51ee83c3308f","file_size":"1906467","filename":"mural-arl-front-lobby-wall-2022-Art-1.png","parent_uid":null,"tags":[],"title":"mural-arl-front-lobby-wall-2022-Art-1.png","updated_at":"2022-12-20T17:05:16.552Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.162Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltef5a348dab2a3aee/63a1eb4c81b6d37de803a5dc/mural-arl-front-lobby-wall-2022-Art-1.png"},"_metadata":{"uid":"csbd1ffa5be9483bf1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"_version":4,"is_dir":false,"uid":"blt5c70994e50dc86a0","ACL":{},"content_type":"image/png","created_at":"2022-12-19T19:15:00.892Z","created_by":"blt084c51ee83c3308f","description":"","file_size":"1139810","filename":"mural-arl-back-wall-2022-Art.png","parent_uid":null,"tags":[],"title":"mural-arl-back-wall-2022-Art.png","updated_at":"2022-12-20T17:04:58.073Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.183Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5c70994e50dc86a0/63a1eb3a38fca911ba5d12f4/mural-arl-back-wall-2022-Art.png"},"_metadata":{"uid":"cs9bc2cc1f568779e3"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs467988e6cbe2e06e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAustin\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Pavlov Visuals\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the seventh floor of our Austin office is a colorful design with aspects of Austin’s culture and landscape.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc4ad9707b04b8886"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltac5c1ffcbac3ac64","ACL":{},"content_type":"image/png","created_at":"2022-12-20T16:52:33.102Z","created_by":"blt084c51ee83c3308f","file_size":"1080904","filename":"Pavlov_Elastic_Mural_Austin_Final_B.png","parent_uid":null,"tags":[],"title":"Pavlov_Elastic_Mural_Austin_Final_B.png","updated_at":"2022-12-20T16:52:33.102Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:01.753Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltac5c1ffcbac3ac64/63a1e851addc6f6850c5a863/Pavlov_Elastic_Mural_Austin_Final_B.png"},"_metadata":{"uid":"cs0415572672a8b286"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3ef507eb7650ea23"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBangalore\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Vijay Machani, Thingswork\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBangalore has two murals, one black and white and one in color that depicts the local area.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003cspan\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc88e91538a923edb"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt0e5c03f1eed58254","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:05:46.905Z","created_by":"blt084c51ee83c3308f","file_size":"1511935","filename":"Wall-4.png","parent_uid":null,"tags":[],"title":"Wall-4.png","updated_at":"2022-12-20T17:05:46.905Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:01.418Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0e5c03f1eed58254/63a1eb6a8f1f170dcb413224/Wall-4.png"},"_metadata":{"uid":"cs9ec6894668b1d298"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt751d50b65a115f24","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:06:02.778Z","created_by":"blt084c51ee83c3308f","file_size":"574462","filename":"Wall-10.png","parent_uid":null,"tags":[],"title":"Wall-10.png","updated_at":"2022-12-20T17:06:02.778Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.343Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt751d50b65a115f24/63a1eb7aa72a6d10b098218a/Wall-10.png"},"_metadata":{"uid":"csb4545abd7568cb6e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf4705f7842c3d63a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBerlin\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: 44Flavours\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBerlin’s abstract wallpaper-esque design is colorful and playful with subtle nods to the city.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8ec5611a89799861"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt5ba7c5df494c666a","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:08:44.020Z","created_by":"blt084c51ee83c3308f","file_size":"122932","filename":"2021011-44flavours_artwork-elastic_wall.png","parent_uid":null,"tags":[],"title":"2021011-44flavours_artwork-elastic_wall.png","updated_at":"2022-12-20T17:08:44.020Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.249Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5ba7c5df494c666a/63a1ec1c8c096610945242c9/2021011-44flavours_artwork-elastic_wall.png"},"_metadata":{"uid":"csd53e5cd794fc40e7"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs78c3c1880dc18642"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eChicago\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eArtist: Jennifer Reeves\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChicago’s city-themed mural has the Bean, modes of transport, and the sport the city loves.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0361c58acc925e06"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt1b5ad298681e175a","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:09:36.260Z","created_by":"blt084c51ee83c3308f","file_size":"4619799","filename":"Chicago-Mural_Final.png","parent_uid":null,"tags":[],"title":"Chicago-Mural_Final.png","updated_at":"2022-12-20T17:09:36.260Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.507Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1b5ad298681e175a/63a1ec50a937a810c29d02ea/Chicago-Mural_Final.png"},"_metadata":{"uid":"cs2193a9e36e736133"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs29193d0f3a440b31"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCopenhagen\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Christine Gan\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCopenhagen’s is also city-themed, with the Danish flag front and center as well as local architecture and monuments.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfd628bf6c884acd0"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7a99192fc3affecb","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:12:59.533Z","created_by":"blt084c51ee83c3308f","file_size":"140351","filename":"Copenhagen.png","parent_uid":null,"tags":[],"title":"Copenhagen.png","updated_at":"2022-12-20T17:12:59.533Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.364Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7a99192fc3affecb/63a1ed1be2224f4e6d32b594/Copenhagen.png"},"_metadata":{"uid":"cscc5b4d3203677c92"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs57ba94dd452692b7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLondon\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Mac McDonald\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLondon has a city-themed one with the iconic landmarks of the capital city.\u003c/span\u003e"}],"_metadata":{"uid":"csb2a3e48a7cb21d8f"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt9adbb9e0f7ccbe0d","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:14:43.419Z","created_by":"blt084c51ee83c3308f","file_size":"410238","filename":"1.png","parent_uid":null,"tags":[],"title":"1.png","updated_at":"2022-12-20T17:14:43.419Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.359Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9adbb9e0f7ccbe0d/63a1ed83a937a810c29d02fc/1.png"},"_metadata":{"uid":"cs524cd00a42de4e5e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs37316bdf8d1ce282"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMunich\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Dustin Haver\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSticking with the theme, Munich’s mural is a cityscape in Elastic’s brand design.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs826c2390d0d4838c"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt64b49a1685f00c4b","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:20:09.458Z","created_by":"blt084c51ee83c3308f","file_size":"2997931","filename":"Munich-Mural.png","parent_uid":null,"tags":[],"title":"Munich-Mural.png","updated_at":"2022-12-20T17:20:09.458Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:01.652Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt64b49a1685f00c4b/63a1eec9d7569411af5deed3/Munich-Mural.png"},"_metadata":{"uid":"cs625f312896710bbd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9523b3966e8aef15"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNew York\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Niege Borges (5th fl) and Jordan E. Moss (4th fl)\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNew York’s office has two murals: one that celebrates the different people and culture in the city and one that showcases New York in all its glory.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfa72efbd1027cf68"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt0cef6340aabe99e4","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:24:00.587Z","created_by":"blt084c51ee83c3308f","file_size":"1291296","filename":"elastic-wall-2NYC-FL5.png","parent_uid":null,"tags":[],"title":"elastic-wall-2NYC-FL5.png","updated_at":"2022-12-20T17:24:00.587Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.407Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0cef6340aabe99e4/63a1efb081b6d37de803a5e8/elastic-wall-2NYC-FL5.png"},"_metadata":{"uid":"cs1b8f8ff2014ce9f9"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt41d631ff3854e1ef","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-20T17:21:57.143Z","created_by":"blt084c51ee83c3308f","file_size":"516195","filename":"Elastic_NYMural_JordanMoss_2-scaled.jpeg","parent_uid":null,"tags":[],"title":"Elastic_NYMural_JordanMoss_2-scaled.jpeg","updated_at":"2022-12-20T17:21:57.143Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.595Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41d631ff3854e1ef/63a1ef35f2b81c35b49ae5d3/Elastic_NYMural_JordanMoss_2-scaled.jpeg"},"_metadata":{"uid":"cs985f6cfcf6bea5f3"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3ef8b6f5e2b2e4e8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eParis\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Jennifer Reeves\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eParis’ mural has a city and food theme, central to French culture.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7e52ad11757495e4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blta19151e284ff63cf","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-20T17:25:38.873Z","created_by":"blt084c51ee83c3308f","file_size":"744746","filename":"Paris-Mural-Photo-scaled.jpeg","parent_uid":null,"tags":[],"title":"Paris-Mural-Photo-scaled.jpeg","updated_at":"2022-12-20T17:25:38.873Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.388Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta19151e284ff63cf/63a1f012eee5ef585b468f1a/Paris-Mural-Photo-scaled.jpeg"},"_metadata":{"uid":"cs7188a64f43e9b29c"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc1079da0fd04becc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSan Francisco\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Gable Company\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur San Francisco office has a mural that is similar to our Amsterdam office, but shows the key landmarks of the city and what makes San Francisco special.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc5b07093a8d15b7d"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt4e996a36d1bc81d6","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:26:45.946Z","created_by":"blt084c51ee83c3308f","file_size":"723567","filename":"Screen_Shot_2022-12-12_at_2.16.49_PM.png","parent_uid":null,"tags":[],"title":"Screen_Shot_2022-12-12_at_2.16.49_PM.png","updated_at":"2022-12-20T17:26:45.946Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.317Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4e996a36d1bc81d6/63a1f0557760ab1f00afed03/Screen_Shot_2022-12-12_at_2.16.49_PM.png"},"_metadata":{"uid":"cs5e47c2d93e76e7d5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7d16935d996b0397"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSingapore\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Somewan\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSingapore’s mural celebrates the city’s diverse food scene.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csafee968dd3978f53"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt8bf6ef86bd133e57","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-20T17:28:14.194Z","created_by":"blt084c51ee83c3308f","file_size":"736803","filename":"Image-from-iOS-5-scaled.jpeg","parent_uid":null,"tags":[],"title":"Image-from-iOS-5-scaled.jpeg","updated_at":"2022-12-20T17:28:14.194Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.475Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8bf6ef86bd133e57/63a1f0ae7335502078c019b3/Image-from-iOS-5-scaled.jpeg"},"_metadata":{"uid":"csed38a214c8df2edd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscfc97de40cf29e79"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSydney\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: James Gulliver Hancock\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSydney has an abstract cityscape mural that also incorporates the city’s flora and fauna.\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb4342fc3dc374228"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt5c7be65ba265e8df","ACL":{},"content_type":"image/png","created_at":"2022-12-20T17:29:05.151Z","created_by":"blt084c51ee83c3308f","file_size":"1468529","filename":"sydney-James-Gulliver-Hancock-2021-1.png","parent_uid":null,"tags":[],"title":"sydney-James-Gulliver-Hancock-2021-1.png","updated_at":"2022-12-20T17:29:05.151Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.995Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5c7be65ba265e8df/63a1f0e1d5ac907c261b174d/sydney-James-Gulliver-Hancock-2021-1.png"},"_metadata":{"uid":"cs9e395af615abd87b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1a6e869fb6455583"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTokyo\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eArtist: Yeka Haski\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTokyo’s mural is two-toned and done in a unique caricature style typical of Japanese culture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd2632df66c7ae44c"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt87e8e751465cb770","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-20T17:29:52.635Z","created_by":"blt084c51ee83c3308f","file_size":"587454","filename":"1-2-scaled.jpeg","parent_uid":null,"tags":[],"title":"1-2-scaled.jpeg","updated_at":"2022-12-20T17:29:52.635Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.946Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt87e8e751465cb770/63a1f110770fe14a53473723/1-2-scaled.jpeg"},"_metadata":{"uid":"cs456d1329bfc05e56"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd336c95bfad0c07b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eWhat mural is your favorite? Apply to work in your local office \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-each-elastic-office-has-its-own-locally-designed-mural\"\u003e\u003cspan style='font-size: 12pt;'\u003ehere\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa0cbc98478da3d10"}}}],"publish_date":"2022-12-21","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt0414045bd4e12b0e","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt2578a51341d487d2","ACL":{},"content_type":"image/jpeg","created_at":"2022-12-19T19:04:40.949Z","created_by":"blt084c51ee83c3308f","file_size":"145821","filename":"12.15-murals-blog-1680x980.jpg","parent_uid":null,"tags":[],"title":"12.15-murals-blog-1680x980.jpg","updated_at":"2022-12-19T19:04:40.949Z","updated_by":"blt084c51ee83c3308f","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-12-21T15:00:00.574Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2578a51341d487d2/63a0b5c881b6d37de803a270/12.15-murals-blog-1680x980.jpg"},"title":"Each Elastic office has its own locally-designed mural. See them all.","title_l10n":"Each Elastic office has its own locally-designed mural. See them all. ","updated_at":"2025-03-28T13:23:12.928Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/culture-each-elastic-office-has-its-own-locally-designed-mural","publish_details":{"time":"2025-03-28T13:23:20.215Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7faeb9b73d655bd1","_version":13,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic CEO Shay Banon explains how the company decided on a vaccine mandate for in-office employees and why: “We’re putting the safety and comfort of our employees first.”","author":["blt4990cfe37610ed0f"],"category":["bltc253e0851420b088"],"created_at":"2021-11-18T14:05:29.751Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa707c7831d0c6b57"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003eThis is an internal email I sent that outlines our approach to vaccine mandates and we are sharing a version here to let everyone know the actions we are taking to ensure the safety and well-being of our employees and community.\u003c/em\u003e\u003c/p\u003e\n\u003cp\u003eWe've thought long and hard about our approach to vaccine mandates. Like most of our decisions on managing COVID-19 to date, we're putting the safety and comfort of our employees first. At the same time, we did not want to be the first out of the gate and rush into decisions. \u003c/p\u003e\n\n\u003cp\u003eWe can all agree that while things are improving globally, we're still seeing concerning developments with new and mutant variants that we feel a strong need to support vaccination programs. After a lot of work by our workplace safety, legal, and HR teams, who carried out very detailed due diligence, risk, and impact assessments, we have decided to put in place a vaccine mandate. This will require all Elasticians to provide proof of full vaccination for the purpose of coming into an Elastic office, and/or to travel or attend events or visit customers. \u003c/p\u003e\n\u003cp\u003eElastic is widely distributed in our workplace approach, so if an Elastician's role doesn't require being in the office, they can continue to work remotely. However, participating in Elastic events or traveling on behalf of Elastic both require vaccination. \u003c/p\u003e\n\u003cp\u003eThe rules and regulations across the globe also vary significantly, so we've tried to be globally consistent but locally relevant with our processes, our questions, and exceptions. \u003c/p\u003e\n\u003cp\u003eTo help guide us through this, we have developed a detailed process to register and provide evidence of vaccination status. It's very likely that we have to repeat the validation process at regular intervals and we may ask Elasticians to go through the same process again.\u003c/p\u003e\n\u003cp\u003eSome business groups will be required to be vaccinated to ensure we comply with relevant regulatory and customer requirements, regardless of their intentions of coming into an Elastic office, carrying out business travel, or attending events. This mostly applies to US Federal team members and our legal team has produced additional guidance and instructions for Elasticians whose work relates to US Federal customer contracts, and they will be notified regarding Federal vaccination requirements. \u003c/p\u003e\n\u003cp\u003eIt's important to note that regulations on wearing masks in the office vary by location. Based on the relevant local authorities' regulations, you may still be required to wear a face cover even if you've been fully vaccinated.\u003c/p\u003e\n\u003cp\u003eWe are sharing the information about the Elastic vaccine mandate so our community, customers, and partners are aware of the actions we are taking to help ensure the safety and well-being of our employees and the people we work with around the world. \u003c/p\u003e\n\u003cp\u003eBe well,\u003cbr\u003eShay\u003c/p\u003e"}],"_metadata":{"uid":"cs9c06137d0167da21"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse79a9e0a2340d950"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cbr\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4166b6c1598b3b89"}}}],"publish_date":"2021-11-18T15:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic puts employee safety first with COVID-19 vaccine mandate","seo_description_l10n":"Elastic CEO Shay Banon explains how the company decided on a vaccine mandate for in-office employees and why: “We’re putting the safety and comfort of our employees first.”","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt6253a47c336e309d","ACL":{},"content_type":"image/png","created_at":"2021-02-02T21:53:25.858Z","created_by":"bltf6ab93733e4e3a73","file_size":"102720","filename":"blog-thumb-covid-19.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-covid-19.png","updated_at":"2022-02-11T21:03:29.215Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:35.981Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6253a47c336e309d/6019c9d53e70bb4c12c6f272/blog-thumb-covid-19.png"},"title":"Elastic puts employee safety first with COVID-19 vaccine mandate","title_l10n":"Elastic puts employee safety first with COVID-19 vaccine mandate","updated_at":"2025-03-28T12:14:11.046Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/culture-elastic-puts-employee-safety-first-with-covid-19-vaccine-mandate","publish_details":{"time":"2025-03-28T12:14:46.639Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4f088654fd2d25aa","_version":21,"locale":"en-us","ACL":{},"abstract_l10n":"Rick Laner has built a career out of relentless focus on the customer, scaling high growth organizations to match their ambitions. Now he brings that experience to Elastic.","author":["blta9cb9a057d08bed0"],"category":["bltc253e0851420b088"],"created_at":"2022-01-14T20:50:15.111Z","created_by":"blt4349d9729d06d101","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs63d7a58ca6528af5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBefore Rick Laner joined Elastic as our new Chief Customer Success\u0026nbsp;Officer, he wanted to confirm if the company was committed to scaling, focusing on the customer experience, and whether\u0026nbsp;the culture is really as advertised. \u003c/p\u003e\n\u003cp\u003e“\u003cem\u003eFirstly, I really dug into the culture and tried to understand, ‘is it really how people operate? Are all the good things I heard true?’ After talking to more than 80 people in my first 8 weeks and observing how teams function, I realized it is absolutely the case,\u003c/em\u003e” said Rick. “\u003cem\u003ePeople take pride in their innovation, uniqueness, making complex tasks simple, taking calculated risks, being humble and respectful. It is truly the way people operate, and the leadership do the same and reward it. It is all true.\u003c/em\u003e”\u003c/p\u003e\n\u003cp\u003eRick has made a career out of customer success, services, pre-sales, and support over the past 30 years, with more recent leadership roles at Mulesoft/Salesforce, Splunk and BMC Software.\u003c/p\u003e\n\u003cp\u003e\u003cem\u003e“At Elastic, everyone’s on this core mission,”\u003c/em\u003e he says, \u003cem\u003e“and that’s a very unique thing, because it can be an incredible catalyst or X-Factor when building the foundations for scale in a fast growing organization. It basically means with strong alignment on a common vision we grow even faster.”\u003c/em\u003e\u003c/p\u003e\n\u003cp\u003eFor Rick, being \u003c/p\u003e\n\u003cp\u003eChief Customer Success Officer\u0026nbsp;at Elastic is first and foremost about satisfaction, service, and value for our customers. Therefore, the customer journey is at the center of how he plans to structure his team, recruit talent, communicate and determine insights into how our customers are using Elastic solutions. From there, he will provide the right activities and knowledge to customers to ensure they are successful.\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cem\u003e“If we look through the eyes of our customers it will ensure we provide a better experience. That is why the Customer Journey is at the\u003c/em\u003e\u003cem\u003e core\u003c/em\u003e\u003cem\u003e of how we will operate.”\u003c/em\u003e he says. \u003cem\u003e“Providing a service to our customers in the Cloud makes the table stakes even higher. \u003c/em\u003e\u003cstrong\u003e\u003cem\u003eWe need to be able to guide a customer to maximize their experience and multiply the value from our platform for their business.\u003c/em\u003e\u003c/strong\u003e\u003cem\u003e As an increasing number of our customers move to the Elastic Cloud, \u003c/em\u003e\u003cem\u003ewe will \u003c/em\u003e\u003cem\u003ebe able to proactively support customers before they even reach out to us. Our platform enables Elastic to derive insights on how our customers are using our solutions–and how we can help them drive even greater value.”\u003c/em\u003e\u003cbr\u003e\u003c/p\u003e\u003cbr\u003e"}],"_metadata":{"uid":"cs96fabd8543ec6b36"}}},{"image":{"image":{"uid":"blta0c75c95b14f01df","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2022-01-15T02:00:19.375Z","updated_at":"2022-01-15T02:00:19.375Z","content_type":"image/png","file_size":"50389","filename":"blog-img-customer-journey.png","title":"blog-img-customer-journey.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-15T02:02:10.223Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta0c75c95b14f01df/61e22ab3b7138d58986f4a3c/blog-img-customer-journey.png"},"_metadata":{"uid":"cs3f6e6f00bbb622b5"},"caption_l10n":"","alt_text_l10n":"customer-journey","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7b6667574cd8ea61"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eAdvancing your career at Elastic\u003c/h2\u003e\n\u003cp\u003e\u003cem\u003e“Elastic already has incredible talent and we have the starting foundations for knowledge sharing, and we will strive to continuously improve and create the ability for millions of people to build careers and skills in Elastic.”\u003c/em\u003e\u003c/p\u003e\n\u003cp\u003eTo advance on his plan, Rick wants to ensure Elastic is fostering career progression, inclusion, and collaboration in our recruitment, retention, and team-building approach. That will include a robust onboarding program, early-in-career support, and expert-level development for seasoned professionals. Roles will range from architects, consultants, delivery managers, CSMs, instructors, content creators, to support engineers and beyond. He says there will be plenty of opportunities for advancement and promotion as Elastic continues to grow.\u003c/p\u003e\n\u003cp\u003eIn addition to this, Rick and the team will dramatically expand our partner ecosystem next year and beyond, so that we have more skills in the market for our customers to leverage.\u003c/p\u003e\n\u003cp\u003eAnd, we’ll continue to collaborate with our Elastic community to create new career paths and support professional development networks. Elastic will be working on a digital platform that will include self service, knowledge articles, videos, access to training and more.\u003c/p\u003e\n\u003cp\u003e\u003cem\u003e“We’re accountable for our customers’ success by accelerating business value,”\u003c/em\u003e said Rick.\u003c/p\u003e\n\u003cp\u003eOutside of work, the Australia native has turned from triathlons to mountain biking to keep active, partly to steer clear of the busy roads around Houston, which he now calls home. Rick also racks up the frequent flyer miles, as his three children chose colleges in California, Tennessee, and North Carolina. “So, you know, the house is pretty quiet right now.”\u003c/p\u003e\n\u003cp\u003eAll the better for his mission: a relentless focus on serving the Elastic customer.\u003c/p\u003e"}],"_metadata":{"uid":"csec4cb126061e66f9"}}}],"publish_date":"2022-01-18T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Chief Customer Success Officer Rick Laner has a map and mission for customer success","seo_description_l10n":"Rick Laner has built a career out of relentless focus on the customer, scaling high growth organizations to match their ambitions. Now he brings that experience to Elastic.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"},{"uid":"blteca7aeb268d33827","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8a6ef250ff6f22b3","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2022-01-15T02:00:04.384Z","updated_at":"2022-01-15T02:00:04.384Z","content_type":"image/png","file_size":"111690","filename":"blog-header-rick-laner-1680x980px.png","title":"blog-header-rick-laner-1680x980px.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-01-15T02:02:10.229Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8a6ef250ff6f22b3/61e22aa4378c6d5896ae0d56/blog-header-rick-laner-1680x980px.png"},"title":"Chief Customer Success Officer Rick Laner has a map and mission for customer success","title_l10n":"Chief Customer Success Officer Rick Laner has a map and mission for customer success","updated_at":"2025-03-28T12:03:58.497Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/culture-elastic-welcomes-rick-laner-as-chief-customer-officer","publish_details":{"time":"2025-03-28T12:04:07.598Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3f2c90c73b057209","_version":22,"locale":"en-us","ACL":{},"abstract_l10n":"ElasticGPT is a private employee assistant built on the Elastic Search AI Platform. It empowers employees to find relevant information, mitigate support tickets, and help field redundant questions and requests across the organization.","author":["bltc377310d5111b252","blt5bab75f2cfb4f62c"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-26T18:40:27.052Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"ElasticGPT — Powered by Elastic, for Elastic","_metadata":{"uid":"cs328a7c0d52971f95"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticGPT is our internal \u003c/span\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (GenAI) assistant built on a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/rag\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieval augmented generation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (RAG) framework. It is meticulously crafted using Elastic’s own technology stack to deliver secure, scalable, and context-aware knowledge discovery for Elasticians.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt its heart lies SmartSource, a private, internally built, and fine-tuned RAG model that retrieves and passes the most relevant context from our internal data sources to an OpenAI large language model (LLM) using Elasticsearch for vector search and data storage. This generative AI application also delivers private, secure access to OpenAI’s GPT-4o and GPT-4o-mini models hosted on a dedicated Azure tenant through Elastic Cloud. This architecture exemplifies the seamless integration and raw power of the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/partners/ai-ecosystem\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI Ecosystem\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — from the backend to the frontend — all monitored and optimized through Elastic’s observability tools.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this post, we’ll peel back the layers of ElasticGPT’s architecture, spotlighting SmartSource, our internal RAG-based LLM framework and model that transforms how we retrieve and discover information from our proprietary internal data sources. We’ll also explore how private access to OpenAI’s GPT-4o and GPT-4o-mini models extends ElasticGPT’s capabilities beyond RAG, enabling broader generative tasks — all while staying true to the customer zero ethos.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbebd285f59358590"}}},{"video":{"vidyard_uuid":"yiifM2QTPUh3r26ZsjpCs3?","_metadata":{"uid":"cs27c18273ce9c3557"},"caption_l10n":"","shadow":false,"video_play_count":"auto","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"The Elastic on Elastic story: Building GenAI apps with our platform","_metadata":{"uid":"cs230a47daad846c1d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs customer zero, building ElasticGPT was not built just to validate our generative AI capabilities and gain key efficiencies in this era of AI, but also to provide feedback to our product teams and share best practices with our customers on how to build a sustainable and future-proof generative AI platform that will scale as your business grows.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticGPT isn’t just another tool — it’s a living showcase of Elastic’s technologies working in unison. We built it from the ground up using solutions and capabilities within the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch powers the data and search backbone\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud ensures effortless scalability\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEUI, Elastic’s in-built design library, delivers a polished frontend\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability provides real-time insights\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis approach ensures that we can provide a secure, performant, and seamless application using the integrated capabilities of Elastic to meet our team's current demands and future expectations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6d44934b987dd6e2"}}},{"video":{"vidyard_uuid":"xcRbAUAETvrg3JWyeDnrxj?","_metadata":{"uid":"csa83bd97e6c16cf07"},"caption_l10n":"","shadow":false,"video_play_count":"auto","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Backend architecture: Elasticsearch as the mighty core","_metadata":{"uid":"cs64ab03eac8a098d6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe backbone of ElasticGPT is \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, a versatile powerhouse that serves as both the vector database for SmartSource’s RAG capabilities and a robust repository for chat data across all models. Hosted on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, this setup offers the flexibility, scalability, and performance needed to support a growing internal user base.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Vector database for SmartSource","_metadata":{"uid":"cs6c6e259bc6f2a784"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSmartSource, our name for our internal model, taps into Elasticsearch’s vector database to store embeddings — numerical representations of our internal data sourced from Elastic’s Wiki, ServiceNow Knowledge Articles, ServiceNow News Articles, and beyond. Using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/es-native-connectors.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s Enterprise Connectors\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we ingest this data effortlessly, break it into searchable chunks, and generate embeddings for semantic search. When a user asks “What’s our Q1 sales target?” SmartSource performs a lightning-fast vector search in Elasticsearch to retrieve the most relevant context — perhaps a snippet from a sales report or meeting notes — and feeds it to GPT-4o for a polished response.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis setup empowers SmartSource to deliver precise, context-aware answers grounded in our proprietary data, all thanks to Elastic’s unparalleled search capabilities.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003e\u003cspan style='color:rgb(67, 67, 67);'\u003eChat data storage for all models\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvery interaction — whether with SmartSource, GPT-4o, or GPT-4o-mini — is meticulously logged in Elasticsearch. This includes user messages, timestamps, feedback, and metadata\u003c/span\u003e\u003cspan style='color:rgb(19, 115, 51);font-size: 12pt;'\u003e.\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eStoring this data in Elasticsearch isn’t just about record-keeping — it’s about continuous improvement. With Elastic’s analytics, we can track usage patterns, pinpoint common queries, and identify areas for refinement. Meanwhile, within \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, application performance monitoring (APM) keeps tabs on performance, reliability, and resource utilization, ensuring response times stay lightning-fast as adoption scales. User chat data is deleted every 30 days, with only metrics saved, enabling us to retain the most relevant data cost effectively.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Frontend architecture: React and EUI for a seamless experience","_metadata":{"uid":"cs3a89ecee734a7e28"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticGPT’s frontend is a sleek blend of React and \u003c/span\u003e\u003ca href=\"https://eui.elastic.co/#/\"\u003e\u003cspan style='font-size: 12pt;'\u003eEUI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, Elastic’s own UI framework, ensuring it feels like a natural extension of our ecosystem. Hosted on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elastic-cloud-kubernetes\"\u003e\u003cspan style='font-size: 12pt;'\u003eKubernetes\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e within Elastic Cloud, it’s built to scale dynamically and integrate effortlessly with our backend.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why EUI? A lesson in flexibility","_metadata":{"uid":"cs5c2eea82243c494c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEarly on, we toyed with Hugging Face’s Chat UI for a quick start, but its limitations became clear when users demanded custom features. Switching to EUI was a no-brainer — it’s purpose-built for Elastic’s products, aligning perfectly with our design system and backend. Now, ElasticGPT’s interface mirrors tools like Kibana, offering a consistent experience while letting us iterate rapidly as generative AI evolves.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key features: Real time and secure","_metadata":{"uid":"cs5bc03a34f51ac177"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe frontend streams responses in real time, so users see answers unfold naturally — think of it like a conversation, not a loading screen. Source attribution and linking builds trust, while simple feedback buttons let users rate answer quality. Security is ironclad, with Elastic’s Okta single sign-on (SSO) for authentication and end-to-end encryption for data protection. Thanks to Elastic Cloud’s Kubernetes orchestration, we can deploy updates without downtime, keeping the user experience smooth and reliable.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"API: The glue between frontend and backend","_metadata":{"uid":"cs171382a9f8c5f11d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticGPT’s API is the unsung hero, bridging the React frontend and Elasticsearch backend with a stateless, streaming design. It’s engineered for efficiency, delivering fast, accurate responses to users in real time.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How it works for SmartSource","_metadata":{"uid":"csb1364d5ab8498fdc"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen a user queries SmartSource, the API triggers a vector search in Elasticsearch to fetch relevant context, sends it to GPT-4o (hosted on Azure), and streams the generated response back to the frontend.\u003cbr /\u003e\u003cbr /\u003eFor GPT-4o and GPT-4o-mini, the API bypasses the RAG pipeline, routing queries directly to the Azure-hosted models for non-contextual tasks like brainstorming or general Q\u0026amp;A.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Monitoring with Elastic APM","_metadata":{"uid":"cs90f6dd7f844f8181"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/application-performance-monitoring\"\u003e\u003cspan style='font-size: 12pt;'\u003eAPM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e tracks every API transaction — query latency, error rates, and more — ensuring we can resolve issues before they affect users. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/kibana\"\u003e\u003cspan style='font-size: 12pt;'\u003eKibana\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e dashboards provide a bird’s-eye view of API performance, model usage, and system health, reinforcing the advantage of a platform approach.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"LangChain: Orchestrating the RAG pipeline","_metadata":{"uid":"cs99c004ecfbc70aa1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/search-labs/integrations/langchain\"\u003e\u003cspan style='font-size: 12pt;'\u003eLangChain\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is the orchestration layer behind SmartSource’s RAG capabilities, tying together Elastic’s vector search with GPT-4o’s generation to deliver accurate, context-rich responses.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e1. What it does: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eLangChain manages the RAG pipeline end-to-end: chunking ingested data, generating embeddings, retrieving context from Elasticsearch, and crafting prompts for GPT-4o. For instance, when a user asks about Q1 sales, LangChain pulls the exact chunk from a sales report — not the entire document — keeping answers concise and relevant.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e2. Why it fits with Elastic: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eLangChain’s flexibility pairs perfectly with the Elastic Stack. Elasticsearch delivers fast, scalable vector search, while Elastic Cloud ensures the infrastructure scales with demand. Plus, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/kibana\"\u003e\u003cspan style='font-size: 12pt;'\u003eKibana\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e lets us monitor LangChain’s performance alongside the rest of the system, creating a cohesive observability strategy.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Extended capabilities: Private access to GPT-4o and GPT-4o-mini","_metadata":{"uid":"cs7d01cbb08731b27d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBeyond SmartSource, ElasticGPT offers secure access to LLMs such as OpenAI’s GPT-4o and GPT-4o-mini models, hosted on a private Azure tenant. These models shine for tasks that don’t require internal data retrieval — think general queries, content drafting, or creative brainstorming. However, since it’s in a secure environment, employees can share private company data without worrying about complying with company policy.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSecure and compliant:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Hosting these models on Azure ensures all interactions meet Elastic’s stringent security and compliance standards. Elasticians can use them with confidence, knowing their data stays private and protected.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTracked in Elasticsearch: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEvery GPT-4o and GPT-4o-mini interaction is logged in Elasticsearch. This unified tracking lets us monitor usage, collect feedback, and maintain consistent observability across all ElasticGPT features.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s IT team is reducing the potential impact of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/avoid-shadow-ai-generative-ai-soc\"\u003e\u003cspan style='font-size: 12pt;'\u003eshadow AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e by delivering secure access to multiple LLMs. The team is currently expanding coverage to other LLMs, such as Anthropic's Claude models and Google's Gemini models.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why a platform approach is a winning formula","_metadata":{"uid":"cs3304d6eb7bb4c787"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eBuilding ElasticGPT on our own platform isn’t just practical — it’s a strategic triumph. Here’s why:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cstrong\u003eSeamless integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eEvery piece — Enterprise Connectors, Elasticsearch, EUI, APM — fits together like a puzzle, eliminating friction and compatibility issues.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cstrong\u003eScalability on demand: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eElastic Cloud’s auto-scaling ensures ElasticGPT grows with us, handling hundreds or thousands of users without missing a beat.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cstrong\u003eSecurity built in: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eSSO, encryption, and Elastic’s security features lock down internal data, ensuring compliance and trust.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003e\u003cstrong\u003eMonitoring in real time: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eElasticsearch, Elastic Observability, and Kibana analytics dashboards reveal how ElasticGPT is used, where it excels, and where it can evolve — fueling continuous enhancement.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(67, 67, 67);font-size: 12pt;\"\u003eThis platform approach has delivered a v1 that’s already slashing redundant IT queries and creating employee efficiencies. And because it’s built on our Elastic Search AI Platform, we’re poised to iterate as fast as generative AI advances.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s next? ","_metadata":{"uid":"csb020f38dd5aecba6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs we advance ElasticGPT, we aim to extensively use our powerful stack, utilizing new features like the \"Semantic Text\" field type, inference endpoints, and LLM observability to continue to utilize and test our latest features.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn parallel, with the increasing prominence of agentic AI, ElasticGPT will evolve to incorporate specialized AI agents designed to streamline workflows, significantly boost productivity, and enhance the daily experience for all Elasticians.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Build generative AI applications today","_metadata":{"uid":"csbe6967183913d3aa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReady to begin a build of your own? Check out our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/demo-gallery/ai-playground\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efree AI playground\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to start building today.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs4f8b533b17f6e3b4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third-party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third-party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs075928b929aa27ce"}}}],"publish_date":"2025-03-26","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt12f69d11c921e1aa","_version":1,"title":"Blog Header Image - ElasticGPT.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-26T18:38:14.715Z","updated_at":"2025-03-26T18:38:14.715Z","content_type":"image/jpeg","file_size":"129278","filename":"Blog_Header_Image_-_ElasticGPT.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-26T19:44:41.527Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt12f69d11c921e1aa/67e44996a9431ff7de414b32/Blog_Header_Image_-_ElasticGPT.jpg"},"title":"Generative AI for Elastic’s workforce: Under the hood of ElasticGPT","title_l10n":"Generative AI for Elastic’s workforce: Under the hood of ElasticGPT","updated_at":"2025-03-27T20:49:44.127Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/generative-ai-elasticgpt","publish_details":{"time":"2025-03-27T20:49:50.021Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3366890e2aa8f37f","_version":3,"locale":"en-us","ACL":{},"abstract_l10n":"Developers create the apps, systems, and tools we use every day. See how J.P. Morgan and Elastic are working together to empower developers to push boundaries in payment processing and provide the resources they need to build the future of payments.","author":["blt9ce725bc73ebd4c0"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-26T19:55:25.460Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2008608b5a824f9d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDevelopers are the heroes behind many of today’s tech innovations. They create the apps, systems, and tools we use every day. Both J.P. Morgan and Elastic understand this and are working together to empower developers to improve payment processing. J.P. Morgan is a leader in payments, and Elastic turns data into results with the power of Search AI. Together, they are giving developers the resources they need to build the future of payments.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Developers and the changing world of payments","_metadata":{"uid":"cs8c4edbb2e53846e3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn recent years, payments have become more than just moving money. People expect transactions to be quick, easy, and safe. The rise of payment apps has shown that people want smooth, hassle-free ways to send and receive money. This shift has had a massive impact on developers, who now have the challenge of creating seamless payment systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePeter Bailey, J.P. Morgan’s product director for developer experiences, explains, “The idea of payments being software has become our area of focus. No longer is it just about exchanging money; it's about creating a whole payments ecosystem where developers build platforms that make it easy for businesses to integrate payments into their operations. This means developers are leading the charge in how payments are made, received, and processed.”\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"J.P. Morgan’s Payments Developer Portal","_metadata":{"uid":"cs29392363e61fc140"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo help developers innovate, J.P. Morgan created the \u003c/span\u003e\u003ca href=\"https://developer.payments.jpmorgan.com/\"\u003e\u003cspan style='font-size: 12pt;'\u003ePayments Developer Portal\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. This portal is a hub where developers can access the tools they need to work with J.P. Morgan’s payment solutions. With self-service access to APIs, documentation, and a sandbox environment, developers can test and experiment with the firm’s systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBailey continues, “We heard from developers that they needed to have self-service access to our documentation, our specifications, and a sandbox to play around with our products.” This feedback from developers was vital in shaping the portal’s design. By providing these resources, J.P. Morgan allows developers to explore, innovate, and figure out how their products can fit into the larger payments landscape.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe growth of the Payments Developer Portal is an accelerator and enabler for developers, as they now have the freedom to test their ideas and build solutions that fit their needs. The Portal is helping them deliver faster, more robust solutions to stakeholders and businesses.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elastic’s role in payments","_metadata":{"uid":"cs46f941ca923ca020"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic plays a big part in making all of this possible. Its powerful search technology, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, is integrated into many J.P. Morgan payment business applications. Elastic helps developers quickly and easily find the data they need, which is essential when working with complex payment systems and processes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBailey explains, \"Elastic has a very well-known product in the Elasticsearch offering. And that's been incorporated into hundreds of applications in J.P. Morgan, specifically within the payments business.\" This integration helps developers ensure that payments run smoothly and data can be accessed quickly. In a world where payments are happening faster than ever, this kind of technology is critical.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Helping developers innovate","_metadata":{"uid":"cs9cf41a64fdc4d9c7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDevelopers are often the ones who devise innovative solutions, find new ways to solve complex problems, and push the boundaries of what’s possible. Their ability to think outside the box allows them to create cutting-edge payment systems and seamless user experiences that others might not have considered.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJ.P. Morgan and Elastic both understand that \u003c/span\u003e\u003ca href=\"https://www.jpmorgan.com/insights/payments/payment-trends/elastic-developer-support-payment-solutions\"\u003e\u003cspan style='font-size: 12pt;'\u003einvesting in developers is vital to driving innovation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Elastic has spent years building tools for developers, and J.P. Morgan is learning from that by creating its developer-friendly environment. Together, they are making it easier for developers to build the future of payments.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBecause developers are at the heart of these changes in payment processing, they build systems that enable payments to happen almost instantly. Whether they are integrating a payment button into a website or creating an app that lets users easily split a bill, developers are simplifying the payment process for everyone. By providing developers with the right tools, like J.P. Morgan’s API and Elastic’s powerful search capabilities, their creativity is unlocked. With these resources, developers can craft innovative solutions that will transform how we make payments for years to come.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Building the future of payments","_metadata":{"uid":"cs1563ff1a1f3d61b1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJ.P. Morgan and Elastic are working together to empower developers and transform the world of payments. As Bailey notes, J.P. Morgan and Elastic are helping to \"open the art of the possible\" for developers everywhere.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy supporting developers, J.P. Morgan and Elastic are ensuring that the future of payments is fast, efficient, and easy. Whether for businesses or individual users, the systems developers build will continue to shape the payments landscape. As technology evolves, developers will be there to create solutions that make payments easier and better for everyone.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.youtube.com/watch?v=djYAsc_x110\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLearn more about how Elastic and J.P. Morgan are driving payments innovation forward\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0ec3b872571e5d3b"}}}],"publish_date":"2025-03-26","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt51b7ed57990a29fb","_version":1,"title":"blogheaderimage-jpmc_177403.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-26T19:54:29.009Z","updated_at":"2025-03-26T19:54:29.009Z","content_type":"image/jpeg","file_size":"157855","filename":"blogheaderimage-jpmc_177403.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-26T20:06:20.171Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt51b7ed57990a29fb/67e45b752e137c7d64b8cabd/blogheaderimage-jpmc_177403.jpg"},"title":"Empowering developers and innovating payment processing at J.P. Morgan","title_l10n":"Empowering developers and innovating payment processing at J.P. Morgan","updated_at":"2025-03-26T20:06:14.821Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/innovating-payment-processing-j-p-morgan","publish_details":{"time":"2025-03-26T20:06:19.911Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2eef12aa396df32b","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Explore how to detect hidden threats with ELK Stack. Learn how adversaries are leveraging T1564 - Hide Artifacts to conceal files, processes, and more. Strengthen your defenses against with actionable insights and tailored ES|QL queries.","author":["bltd7e3256924767ce0"],"category":["blte5cc8450a098ce5e"],"created_at":"2025-03-26T06:30:23.337Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd81748cfce9457de"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAttackers thrive in the shadows, using MITRE ATT\u0026amp;CK® T1564 - Hide Artifacts to cloak their presence with hidden files, concealed processes, and manipulated registry keys. These stealth tactics allow adversaries to evade detection, persist undetected, and escalate their access — all while quietly exfiltrating data or disrupting operations.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs971a27048b4c9256"}}},{"image":{"image":{"uid":"blt1b61694eee800f5d","_version":1,"title":"Hunting-with-Elastic-Security.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-26T06:32:25.374Z","updated_at":"2025-03-26T06:32:25.374Z","content_type":"image/jpeg","file_size":"387016","filename":"Hunting-with-Elastic-Security.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-26T17:05:56.168Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1b61694eee800f5d/67e39f79edf277090f90bdc9/Hunting-with-Elastic-Security.jpg"},"_metadata":{"uid":"csf971828f376fb63e"},"caption_l10n":"","alt_text_l10n":"Hunting with Elastic Security","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-medium: 50%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1fbf27bd65c12267"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImagine files, processes, and even user accounts disappearing in your environment without a trace. Could an adversary be lurking, covering their tracks and evading detection? It’s time to sharpen your tools, hunt for these hidden threats, and expose what’s been left in the dark. Can you prove their presence, or will their artifacts remain unseen? The hunt begins now!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Understanding the technique","_metadata":{"uid":"cs40436fba350bb43f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eT1564 - Hide Artifacts\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is a technique within the \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/\"\u003e\u003cspan style='font-size: 12pt;'\u003eMITRE ATT\u0026amp;CK\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e framework, allowing adversaries to conceal their malicious activities, maintain persistence, and evade detection by defenders. This technique spans a range of sub-techniques, each designed to obscure files, processes, user accounts, or other elements within a system. By hiding their tracks, attackers can avoid triggering alerts and extend their dwell time in an environment, increasing the potential for damage.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Sub-techniques of T1564","_metadata":{"uid":"cse3a52d90110cc52f"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/001/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHidden Files and Directories (T1564.001)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Adversaries may use system utilities or file attributes to hide files and directories critical to their operations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/002/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHidden Users (T1564.002)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Attackers can create or modify user accounts, making them invisible to administrators or standard user enumeration methods.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/004/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNTFS File Attributes (T1564.004)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e NTFS alternate data streams are used to embed malicious content in files, effectively hiding it from plain sight.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/006/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRun Virtual Instance (T1564.006)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Adversaries may use isolated virtual instances to execute malicious code without affecting the host system or triggering standard monitoring tools.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/008/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEmail Hiding Rules (T1564.008)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Attackers manipulate email client rules to redirect or hide email communications, preventing users from noticing key warnings or malicious messages.\u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1564/008/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis technique falls under the \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/tactics/TA0005/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDefense Evasion (TA0005)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e tactic in the MITRE ATT\u0026amp;CK framework, highlighting its role in enabling attackers to bypass detection mechanisms. By hiding artifacts, adversaries ensure that defenders are either unaware of their presence or unable to identify and remediate malicious activities in time.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFailing to detect and respond to T1564 activities can have significant consequences for an organization’s security posture. Hidden files and processes may allow attackers to escalate privileges, exfiltrate sensitive data, or maintain control over compromised systems for extended periods. The resulting impact includes risks to \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003econfidentiality\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, as sensitive data could be accessed or stolen; \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eintegrity\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, as system modifications go unnoticed; and \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eavailability\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, as attackers may disrupt services without being detected.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUnderstanding Hide Artifacts is critical to building robust defenses. By shining a light on hidden activities, you can thwart attackers' attempts to operate in the shadows and secure your environment against evolving threats.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data sources to optimize the hunt","_metadata":{"uid":"csbc1f02f81abda69f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDetecting\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eHide Artifacts requires monitoring a wide range of data sources to uncover the stealthy techniques adversaries use to conceal their activities. By leveraging these data sources, you can identify suspicious behaviors, uncover hidden files and processes, and expose adversaries' attempts to evade detection. Below, we summarize key data sources, what they detect, and recommended \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003eintegrations\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that have been optimized for the Elastic Agent.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e1. File monitoring\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Hidden files and directories, changes to file attributes, and files with suspicious NTFS streams\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Critical for uncovering hidden or manipulated files used to conceal malicious activity\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eUse \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/fim.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eFile Integrity Monitoring\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eor a different integration that collects logging information from a third party\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003efor file integrity monitoring and file access tracking\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTrack file creation and modification events; enable NTFS alternate data stream monitoring on Windows systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e2. Process monitoring\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Hidden processes or processes executing in virtualized instances\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Identifies processes attempting to evade detection or execute in isolated environments\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/windows.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eWindows Integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, or a different\u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003e integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that collects logging information from a third party to monitor process creation events, command-line arguments, and anomalous behavior\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEnable process execution tracking (Event ID 4688 in Windows); enable logging for command-line arguments\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e3. Registry monitoring\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eChanges to registry keys used to hide files, directories, or processes, such as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eHKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run.\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIdentifies attempts to persist malicious artifacts through registry changes\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eUse \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eor a different \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003eintegration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that collects logging information from a third party to detect suspicious changes or access\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Enable \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRegistry Access Auditing\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e (Event ID 4657)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e4. User account monitoring\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Creation or modification of hidden user accounts\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Exposes unauthorized user accounts created for stealthy access\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eUse \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or a different \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003eintegration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that collects logging information from a third party for capturing logs about user account activity\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEnable \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAudit User Account Management\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e (Event ID 4720 - Account Creation, Event ID 4722 - Account Enabled)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e5. Email logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Email rules that hide or redirect communications\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eExposes malicious manipulation of email client rules to prevent detection or alerting\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eYou have numerous integrations to choose from, including \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/proofpoint_on_demand.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eProofpoint On Demand\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://docs.elastic.co/integrations/microsoft_exchange_server\"\u003e\u003cspan style='font-size: 12pt;'\u003eMicrosoft Exchange Server\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/es-connectors-gmail.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eGmail\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/o365.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eMicrosoft Office 365\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/cisco_secure_email_gateway.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCisco Secure Email Gateway\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (For a complete list of available out-of-the-box integrations, visit the\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic Integrations page\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEnable mailbox rule auditing in email systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e6. Memory forensics\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Hidden processes, malicious code in isolated virtual instances, or processes evading termination\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Uncovers in-memory activity that evades standard file-based detection\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eUse \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/windows.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eWindows Integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or a different \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style='font-size: 12pt;'\u003eintegration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that audits for memory analysis\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eRequires memory snapshot analysis\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e7. Audit logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Resource forking, access to hidden file systems, and other filesystem-level manipulations\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Identifies advanced methods of hiding artifacts, particularly on Unix-based systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eUse \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/auditd.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eauditd\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e file access monitoring and audit logging\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEnable auditd on Linux systems for detailed file access logs\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor more on auditd, check out \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/linux-detection-engineering-with-auditd\"\u003e\u003cspan style='font-size: 12pt;'\u003eLinux Detection Engineering with auditd\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e from Elastic Security Labs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e8. Network traffic logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Use of alternative protocols or obfuscated traffic patterns that could indicate hidden activity\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Identifies potential data exfiltration or stealthy communications\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eYou have numerous integrations to choose from, including \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/aws.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eAWS\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/azure.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eAzure Logs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/checkpoint.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCheck Point\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/cisco-intro.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCisco\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/palo-alto-intro.html\"\u003e\u003cspan style='font-size: 12pt;'\u003ePalo Alto\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (For a complete list of available out-of-the-box integrations, visit the\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/index.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic Integrations page\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRequired logging: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEnable DNS, HTTP, and custom protocol analysis\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Threat hunting with ES|QL queries","_metadata":{"uid":"cs633eab95b2ba0e71"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo effectively hunt for adversaries leveraging \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eT1564 - Hide Artifacts\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, we use a combination of Elastic Stack \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e queries and data from various sources such as file access logs, process execution logs, and command execution logs. These queries aim to uncover hidden files, processes, user accounts, and other artifacts that adversaries use to evade detection.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 1: Detect hidden files and directories (T1564.001)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3c180e69dab71191"}}},{"code":{"code":"FROM logs-*\n| WHERE file.attributes == (\"hidden\", \"system\")\n AND NOT file.path == \"/legitimate/system/path/*\"\n| KEEP file.path, file.attributes, user.name, host.name, @timestamp\n","_metadata":{"uid":"csbed964e0d67c90be"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6c7b301b9de9a755"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query identifies files and directories with hidden or system attributes that fall outside known legitimate paths. Attackers often use these attributes to conceal malicious files and evade detection.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo determine what constitutes a \"known legitimate path,\" you should conduct an inventory of system-critical directories and paths commonly used by legitimate applications. For example:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReview configuration documentation for operating systems and applications to identify directories expected to contain hidden or system files.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can use this query in your Elastic environment to identify directories that frequently contain hidden or system files.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs22b62d24cf0409fc"}}},{"code":{"code":"\nFROM logs-*\n| WHERE file.attributes IN (\"hidden\", \"system\")\n| STATS count = count() BY file.directory\n| SORT count DESC\n| LIMIT 100\n","_metadata":{"uid":"cs8303ded0fce08732"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd553a9920cded184"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt might also be fruitful to run a search replacing \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eDESC\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eASC\u003c/span\u003e\u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eto check directories that are less likely to contain hidden files.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConsult with your IT and security teams to compile a list of approved paths used in your organization.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo modify the query to include multiple known legitimate paths, you can expand the condition by adding additional paths using the logical \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAND NOT IN\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e operator or a list of paths. For instance:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs017845b5a90214e2"}}},{"code":{"code":"FROM logs-*\n| WHERE file.attributes IN (\"hidden\", \"system\")\n AND file.path NOT IN (\"C:\\\\legitimate\\\\system\\\\path\", \"C:\\\\another\\\\legitimate\\\\path\", \"D:\\\\yet\\\\another\\\\path\")\n| KEEP file.path, file.attributes, user.name, host.name, @timestamp\n","_metadata":{"uid":"csc62b5a90263b86ba"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs10e8017221843bad"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 2: Monitor registry keys for persistence (T1564.002)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2bebe42e669d47c5"}}},{"code":{"code":"FROM logs-*\n| WHERE registry.path == (\"HKEY_LOCAL_MACHINE\\\\SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Run\") AND registry.value != \"legitimate_key\"\n| KEEP registry.path, registry.value, registry.key, user.name, host.name, @timestamp","_metadata":{"uid":"cs0838607c0e0d722a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs23ce266ce28c2eff"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query detects suspicious registry modifications where attackers may add hidden users or persistence mechanisms. Monitoring these keys is essential to identifying hidden artifact activities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can use a similar technique as explained in query 1 to help determine the values of “legitimate_key.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse0e717b8c35aa95f"}}},{"code":{"code":"FROM logs-*\n| WHERE registry.path == (\"HKEY_LOCAL_MACHINE\\\\SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Run\")\n| STATS count = count() BY registry.key\n| SORT count DESC\n| LIMIT 100\n","_metadata":{"uid":"cs36948c3b91a6dfe8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse1f0100ad8f037eb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 3: Identify NTFS alternate data streams (T1564.004)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa146896e28c8e21a"}}},{"code":{"code":"FROM logs-* \n| WHERE file.path == \"*::$DATA\" AND NOT file.path == \"/known/good/paths\" \n| KEEP file.path, file.attributes, user.name, host.name, @timestamp","_metadata":{"uid":"cse268ee2fe6e2fd44"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4ce8b250f45a26af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e NTFS alternate data streams are used to hide malicious content within legitimate files. This query highlights any NTFS streams not within known legitimate paths.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can use a similar technique as explained in query 1 to help determine the values of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/known/good/paths.\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3732dce0a40d9409"}}},{"code":{"code":"FROM logs-*\n| WHERE file.path LIKE \"*::$DATA\"\n| STATS count = count() BY file.path\n| SORT count DESC\n| LIMIT 100\n","_metadata":{"uid":"csc6630f0f2282bd0a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5997c07b38e35c86"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 4: Detect processes running in virtual instances (T1564.006)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa045dccda58437d1"}}},{"code":{"code":"FROM logs-*\n| WHERE process.name IN (\"vmcompute.exe\", \"VBoxService.exe\")\n AND host.name NOT IN (\"known_virtualized_host\")\n| KEEP process.name, host.name, user.name, @timestamp\n","_metadata":{"uid":"cs61e5b91aa3208ed0"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7f1fed90d5a6815e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Attackers may execute malicious processes within virtual instances to evade detection. This query identifies suspicious virtual machine-related processes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 5: Monitor Email Rules for Concealed Communications (T1564.008)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfd71182d4c7c6369"}}},{"code":{"code":"FROM logs-*\n| WHERE event.category == \"email\"\n| KEEP user.email, email.subject, email.direction, email.to, email.from, email.message_id, email.attachments.file.name, @timestamp\n| SORT @timestamp DESC\n","_metadata":{"uid":"csefc2386d6738be25"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse830dc1ecf984f99"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Attackers manipulate email traffic to evade detection, using deceptive subjects, unexpected senders, or suspicious attachments. This query helps identify unusual email activity by analyzing metadata like subject lines, recipients, and file attachments. Reviewing these patterns daily can help detect potential threats before they escalate.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1e8a62008f192c5b"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 6: Identify resource forking (T1564.009)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csdb252c98a942cb6a"}}],"_metadata":{"uid":"cs8a38784f1b9dff5e"}}},{"code":{"code":"FROM logs-*\n| WHERE file.path LIKE \"*:/*\"\n| KEEP file.path, user.name, host.name, @timestamp\n","_metadata":{"uid":"csb0812c19e57b5396"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Resource forks are used to hide malicious data in file systems. This query identifies resource forks across filesystems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 7: Detect processes ignoring termination signals (T1564.011)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs25c02adc0d0bc3f6"}}],"_metadata":{"uid":"cs7d0bece874718155"}}},{"code":{"code":"FROM logs-*\n| WHERE event.category == \"process\"\n AND event.type == \"termination\"\n AND process.executable != \"\" \n AND process.exit_code == 0\n| KEEP process.name, process.executable, process.exit_code, host.name, user.name, @timestamp\n","_metadata":{"uid":"csb57e50a262b22b4f"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Processes configured to ignore termination signals are often designed to evade manual or automated shutdown attempts. This query flags such behaviors.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 8: Identify hidden users on Linux systems\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csbea1e5533b0c2b23"}}],"_metadata":{"uid":"csa427876b02720085"}}},{"code":{"code":"FROM logs-*\n| WHERE user.name != \"\" \n AND user.id \u003e= 1000\n AND process.command_line NOT LIKE \"*bash*\"\n AND process.command_line NOT LIKE \"*sh*\"\n| KEEP user.name, user.id, process.command_line, host.name, @timestamp\n","_metadata":{"uid":"cs8fe87fa34fa94f67"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eHidden users on Linux systems often have unusual shell paths or UID values. This query highlights potentially malicious user accounts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 9: Detect hidden processes via parent-child relationships\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs0e1aa8adf5253b6b"}}],"_metadata":{"uid":"csd21949fb55fdab54"}}},{"code":{"code":"FROM logs-*\n| WHERE process.name == \"svchost.exe\"\n AND NOT process.parent.name == \"services.exe\"\n| KEEP process.name, process.parent.name, user.name, host.name, @timestamp\n","_metadata":{"uid":"csb138a75602b75626"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Attackers may hide processes by linking them to parent processes that are unusual or unexpected. This query flags such anomalies.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 10: Monitor file access in protected directories\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs7323c42e74a5e9e2"}}],"_metadata":{"uid":"cs99ba16e7bd8d109e"}}},{"code":{"code":"FROM logs-*\n| WHERE file.path IN (\"/etc/shadow\", \"/etc/passwd\")\n AND event.action == \"access\"\n| KEEP file.path, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs57973043ebb13770"}}},{"title_text":{"title_text":[{"title_l10n":"","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Attackers often target sensitive files in protected directories. This query detects unauthorized access attempts.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csb54a393ace76f646"}},{"title_l10n":"The key to strong security posture? Leave no stone unturned","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe shadows in your network have been pushed aside, and what was once hidden has now been brought to light. From concealed files and processes to obscure registry keys — did you unmask the adversary’s tricks, or did your hunt confirm that the shadows were empty? With T1564 - Hide Artifacts in your crosshairs, your focus and detection skills have revealed the true nature of potential threats.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhether you uncovered hidden dangers or validated your defenses, your proactive efforts have fortified your security posture. Every NTFS alternate data stream uncovered, every cloaked process revealed, and every hidden email rule dismantled strengthens your network. The risks of undetected artifacts are significant, but today, you’ve shown that a determined hunter leaves no stone unturned.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWas your network hiding an intruder, or can you confidently declare it secure? Either way, you’ve taken critical steps to limit attackers’ options. Remember, the tactics of concealment evolve, and staying ahead means continuous vigilance. Stay sharp, stay prepared, and keep hunting — because with Elastic, it's always the right time to protect your network. Ready to take your threat hunting to the next level?\u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup\"\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/a\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003eStart a free Elastic Cloud trial today\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and bring light to the shadows before adversaries can hide in them!\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs405ad1e28514f076"}}],"_metadata":{"uid":"cs04c9e0bda29a424a"}}}],"publish_date":"2025-03-26","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt7a4eb1026ba18f63","ACL":{},"created_at":"2023-11-06T20:07:03.185Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"advanced-persistent-threat","label_l10n":"Advanced Persistent Threat (APT)","tags":[],"title":"Advanced Persistent Threat (APT)","updated_at":"2023-11-06T20:07:03.185Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:50.393Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt83da212008a1c956","_version":1,"title":"Blog Header Image- ELK Hunting Series-3-175401.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-26T06:29:23.130Z","updated_at":"2025-03-26T06:29:23.130Z","content_type":"image/jpeg","file_size":"115939","filename":"Blog_Header_Image-_ELK_Hunting_Series-3-175401.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-26T17:05:56.149Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt83da212008a1c956/67e39ec3e5b23a4005948805/Blog_Header_Image-_ELK_Hunting_Series-3-175401.jpg"},"title":"Hunting with Elastic Security: Unmasking concealed artifacts with Elastic Stack insights","title_l10n":"Hunting with Elastic Security: Unmasking concealed artifacts with Elastic Stack insights","updated_at":"2025-03-26T06:50:44.068Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/unmasking-concealed-artifacts-elastic-stack","publish_details":{"time":"2025-03-26T17:05:55.778Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2499c96b6ca36a7d","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"Learn how observability metrics, logs, traces, and profiles enhance monitoring, optimize performance, and support data-driven decisions.","author":["blt83cf0258d983212a"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-25T00:33:16.653Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs19cfe822f9f707a2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eObservability metrics provide insights into the performance, behavior, and health of applications, systems, and infrastructure — enabling observability practices, which is how a system’s internal state is understood by examining its data. As organizations continue to collect more and more data, observability metrics are a key telemetry signal for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eobservability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn modern application development, observability refers to collecting and analyzing \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/telemetry-data\"\u003e\u003cspan style='font-size: 12pt;'\u003etelemetry data\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/log-files\"\u003e\u003cspan style='font-size: 12pt;'\u003elogs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/traces#traces-metrics-logs-and-profiles\"\u003e\u003cspan style='font-size: 12pt;'\u003emetrics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/traces\"\u003e\u003cspan style='font-size: 12pt;'\u003etraces\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — from a variety of sources for detailed insight into the behavior of applications running in your environments. Observability metrics are the telemetry signals that help organizations make sense of their operations and create proactive monitoring processes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy leveraging observability metrics, organizations can obtain a comprehensive view of the performance of their technology stack, improving issue diagnostics and resolution times. When used effectively, observability metrics can provide valuable business insights that drive growth and allow organizations to focus on innovation.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3 pillars of observability","_metadata":{"uid":"cs5d329075d29eacb1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe foundation of observability is often described in terms of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/3-pillars-of-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003ethree pillars: metrics, logs, and traces\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Together, they provide essential visibility into system performance and behavior. As technology continues to advance and observability needs increase, a fourth pillar is emerging: profiles.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Metrics","_metadata":{"uid":"cs1eccd446ce5cf8b2"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMetrics are raw numerical data points collected from hardware, software, and websites. In measuring known knowns, metrics are used for monitoring resource usage, performance, and user behavior. In other words, metrics tell monitoring and observability teams \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ewhat\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is happening in their systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCore types of observability metrics\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eObservability is a practice that gives organizations a 360-degree view of their environments and operations. To do so, observability relies on these core types of metrics:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eApplication metrics: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eApplication metrics are the telemetry data generated by and related to applications within a technology stack. Some examples of commonly used metrics include response times, throughput, request rates, and error counts. These metrics allow engineers to monitor application performance and availability. Application metrics are also used in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/application-performance-monitoring\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eapplication performance monitoring (APM)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSystem metrics: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSystem metrics, also referred to as infrastructure metrics, reflect the health of hardware and operating systems including key components like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/kubernetes-monitoring\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKubernetes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Examples include CPU utilization, disk I/O, network throughput, memory usage, instance uptime, container resource utilization, and service availability. These metrics provide insights into the performance of cloud resources, virtual machines, containers, and other underlying components.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBusiness metrics: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBusiness metrics tie technical and operational performance to business outcomes. For example, metrics like conversion rates, average transaction value, and user retention help correlate system performance with organizational objectives.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn effective observability solution ensures reliability, effective resource allocation, compliance, and security. It also helps plan capacity, optimize performance, improve user experiences, and control costs. Core metrics enable effective observability, and ultimately, data-driven decision-making that translates to better business outcomes. These metrics are typically aggregated and visualized in dashboards for real-time performance monitoring.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Logs","_metadata":{"uid":"cs41ed25562acf5f54"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/log-files\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLogs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e are timestamped entries of specific events generated by systems, applications, networks, and infrastructure. They provide event details and context, allowing engineers to understand \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ewhy\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e issues occur.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNetwork devices, applications, operating systems, applications, IoT devices, and third-party applications emit different types of logs, including (but not limited to):\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSystem logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e These include events like connection attempts, errors, and configuration changes.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eApplication logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e They record software changes, CRUD operations, application authentication, and other events to help diagnose issues.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNetwork logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Network logs record data from events that take place on a network or device, including network traffic, security events, and user activity.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLogs are recorded in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/structured-data\"\u003e\u003cspan style='font-size: 12pt;'\u003estructured\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/unstructured-data\"\u003e\u003cspan style='font-size: 12pt;'\u003eunstructured\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e formats, which represents a storage challenge. They can also be hard to categorize since log data is often siloed in a variety of systems and not automatically correlated.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"},{"title_l10n":"Traces","_metadata":{"uid":"cs14d4e1a18cd55b41"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/traces\"\u003e\u003cspan style='font-size: 12pt;'\u003eTraces\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are telemetry signals that let engineers see applications and services from a user-session perspective. Distributed tracing collects traces of requests that make their way through a distributed architecture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTraces allow engineers to monitor and debug applications, discovering bottlenecks. In other words, traces tell \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/devops\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevOps\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e teams \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ewhere\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e issues are occurring in their environments. They’re the foundation of proactive monitoring. By analyzing traces, engineers can discover which metrics or logs are related to a particular issue, mitigating future issues.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, traces that help identify slow processes include API queries, front-end API traffic, server-to-server workloads, and internal API calls.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile metrics, logs, and traces offer users valuable application and system performance data, these signals don’t always provide the details required for troubleshooting code and performance tuning. This is where profiles come in.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Profiles","_metadata":{"uid":"cs81912b824bc2547a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/observability/universal-profiling\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProfiling\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is the gathering and analysis of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/elastic-profiling-agent-acceptance-opentelemetry\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eprofiles\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — stack traces that help identify issues related to data structures, code visibility, and memory allocation at the kernel and user levels.\u0026nbsp;\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProfiling helps uncover bottlenecks across your system at the code level, another key benefit of modern observability. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/opentelemetry\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOpenTelemetry\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is also adopting profiling as a signal. As a result, profiling is emerging as the fourth and newest pillar of observability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Essential observability metrics: The 4 golden signals for SRE teams","_metadata":{"uid":"cs139eb73cf9a2fab7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile every organization’s monitoring needs are unique, certain observability metrics are universally important. These metrics are sometimes referred to as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ethe four golden signals within the site reliability engineering (SRE) community\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Latency","_metadata":{"uid":"cse91170d63f67ee33"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLatency measures the time it takes for data to travel from one point to another. Latency will signal underlying performance issues. High latency can degrade user experiences by increasing load times, causing application errors, and challenging user expectations.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Traffic","_metadata":{"uid":"cs19fffbbe7985e0bb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTraffic metrics track the volume of requests or transactions an application processes. They help teams understand user behavior and anticipate scaling needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Errors","_metadata":{"uid":"cseb973061f6088489"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eError metrics provide visibility into failed requests or operations. Monitoring error rates and identifying patterns can help address recurring issues.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Saturation","_metadata":{"uid":"cs5085e0b05b119f03"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSaturation metrics indicate how close a system is to its capacity limits. Monitoring resource utilization ensures that engineers can proactively address bottlenecks before they impact performance.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese four golden signals are key to effective observability practices as they provide insights into the health and performance of IT systems. When monitored, correlated, and analyzed, these metrics help IT teams get actionable insights that enable them to take on a more proactive stance around site reliability and performance monitoring.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs06650e3b9d0b2a18"}}},{"banner":{"reference":[{"uid":"blta942865b8cd51e9c","_content_type_uid":"banner"}],"_metadata":{"uid":"cs69ee792b826ddead"}}},{"title_text":{"title_text":[{"title_l10n":"Best practices for implementing observability metrics","_metadata":{"uid":"cs62a3b83e9907f900"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe primary challenge of implementing observability metrics has to do with sorting through the noise — many signals produce a mass of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/telemetry-data\"\u003e\u003cspan style='font-size: 12pt;'\u003etelemetry data\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e that may not all be useful. In addition to this, SREs will often struggle with data heterogeneity. How do you correlate various types of disparate data for easier troubleshooting?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFrom these challenges, we can establish some best practices for implementing observability metrics.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDefine clear objectives: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eSuccessfully implementing observability metrics — and combatting data overwhelm —\u0026nbsp;begins with establishing your goals. To define these objectives, ask yourself what you need your metrics to tell you. You don’t need to monitor everything; you only need to monitor what is important to your organization and systems.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eUse open standards to instrument your applications: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eInstrumentation is the process of generating and collecting telemetry data from applications. To avoid vendor lock-in when you instrument your applications, consider a vendor-neutral framework like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/opentelemetry\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenTelemetry (OTel)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. OTel provides a standardized framework that enables you to collect and compare telemetry data from multiple sources.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLeverage automation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eAutomate data collection, analysis, and alerting to reduce manual effort and enable faster response times.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCustomize visualizations: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIn order to meet your defined objectives, it’s best to customize your dashboards. Default dashboards are only useful to a point — customizing how you visualize your environment is key to successful observability.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Observability metrics with Elastic ","_metadata":{"uid":"csfffdb929f5557d5c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e provides a unified solution for collecting, monitoring, and analyzing observability metrics across your technology stack. With Elastic Observability, you can collect, store, and visualize observability metrics from any source and speed up problem resolution with our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearch AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Observability prevents outages and accelerates problem resolution with search-based relevance, no-compromise data retention, improved operational efficiency and cost, and a future-proofed investment. Get fast, contextual, and unified insights across the broadest data sources with an open, OTel-first solution that seamlessly integrates with your evolving technology ecosystem.\u003cbr /\u003e\u003cbr /\u003eLearn more about \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eobservability with Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs74ae1e6390fabad1"}}},{"callout":{"title_l10n":"Deep dive into more observability metrics resources","_metadata":{"uid":"csfe9d03e5ec824d63"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExplore Elastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/observability/current/apm-metrics.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLook over metrics for APM with Elastic.\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/4-benefits-observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRead about the top benefits of observability\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/observability/opentelemetry\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow trending: OpenTelemetry adoption increases\u003c/span\u003e\u003c/a\u003e\u003ca href=\"https://www.elastic.co/observability/building-data-foundation-modern-observability\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn how to build a data foundation for your observability needs\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/observability/current/explore-metrics.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExplore infrastructure metrics over time\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/observability/current/analyze-metrics.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnalyze metrics\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs399de16cc66cf27b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs733b71496aec3419"}}}],"publish_date":"2025-03-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt85414c8cbf30b724","ACL":{},"created_at":"2023-11-06T21:52:01.987Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"universal-profiling","label_l10n":"Universal profiling","tags":[],"title":"Universal profiling","updated_at":"2023-11-06T21:52:01.987Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.852Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"title":"Monitoring","label_l10n":"Monitoring","keyword":"monitoring","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt018d981515b9a4fd","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:24.931Z","updated_at":"2020-06-17T03:39:59.356Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:24.931Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-02T18:15:31.077Z","user":"bltf6ab93733e4e3a73"}},{"_content_type_uid":"tags_topic","title":"OpenTelemetry","label_l10n":"Open source/standards","keyword":"opentelemetry","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt069bd34528952802","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:44:13.512Z","updated_at":"2023-11-06T20:44:13.512Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.903Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Real user monitoring","label_l10n":"Real user monitoring","keyword":"real-user-monitoring","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt59d92f2f17daff45","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:49:57.287Z","updated_at":"2023-11-06T20:49:57.287Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:27.810Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Synthetic monitoring","label_l10n":"Synthetic monitoring","keyword":"synthetic-monitoring","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb4db9161bbf295bc","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:47.250Z","updated_at":"2023-11-06T21:33:47.250Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.838Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt644c874f72ce70e0","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-25T00:30:15.794Z","created_by":"blte369ea3bcd6ac892","file_size":"167705","filename":"Blog_Header_Image_Understanding_observability_metrics_Types_golden_signals_and_best_practices_176949.jpg","parent_uid":null,"tags":[],"title":"Blog Header Image_Understanding observability metrics Types, golden signals, and best practices_176949.jpg","updated_at":"2025-03-25T00:30:15.794Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-25T14:00:00.495Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt644c874f72ce70e0/67e1f917362ee3b22355cdae/Blog_Header_Image_Understanding_observability_metrics_Types_golden_signals_and_best_practices_176949.jpg"},"title":"Understanding observability metrics: Types, golden signals, and best practices","title_l10n":"Understanding observability metrics: Types, golden signals, and best practices","updated_at":"2025-03-25T15:40:50.328Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/observability-metrics","publish_details":{"time":"2025-03-25T15:41:14.082Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd4e064cad664b3d7","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Elasticsearch transforms data management in the aviation industry by enabling real-time analysis of vast amounts of information. Learn how we enhance customer experience through personalised services and quick data retrieval for customer support.","author":["bltcf42cb9c7bfeca25"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-03T17:00:36.900Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf374fe5304022ead"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDigital customer experience is no longer a luxury but a \u003c/span\u003e\u003ca href=\"https://www.which.co.uk/reviews/airlines/article/best-and-worst-airlines-a5EhC8N851et\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003enecessity for European airlines\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. It drives customer satisfaction, enhances operational efficiency, and creates a sustainable competitive advantage. As the industry continues to evolve, airlines that prioritise investment in cutting-edge digital technologies and platforms will be better positioned to thrive in a dynamic and demanding market.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe ability to store, search, and analyse large volumes of data in real time plays a critical role in operations, customer service, safety, and compliance for airlines.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eStrong adoption and execution of data management help airlines, airports, and service providers enhance operational efficiency, improve customer experiences, and gain competitive advantages. Poor adoption risks being stranded on the ground and a loss of competitive edge.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Real-time search and analytics in a data-heavy industry","_metadata":{"uid":"csaa2bc2a1a14c584c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe aviation industry generates vast amounts of data daily, including flight schedules, passenger information, baggage tracking, aircraft maintenance logs, weather data, and operational metrics. Managing and deriving insights from this data is crucial but complex.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch — an open source, distributed search and analytics engine — has emerged as a transformative technology across industries for its ability to handle large volumes of unstructured data across varied datasets.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn practice, Elasticsearch’s ability to search and index data in real time is invaluable for tracking flight statuses and passenger information. Several European Airlines use Elasticsearch to monitor schedules and provide passengers with real-time updates on delays or gate changes. Similarly, airports deploy Elasticsearch to offer precise baggage tracking by integrating data from IoT-enabled tags and scanners, ensuring smoother operations and reducing lost luggage incidents.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Enhanced customer experience through personalised services","_metadata":{"uid":"cs607f6b1b2f1b914e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eModern passengers expect a seamless travel experience that is often facilitated by personalised digital interactions.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch powers sophisticated recommendation engines by analysing historical travel data, preferences, and real-time booking trends. For example, airlines can suggest ancillary services, such as extra baggage or lounge access, based on a passenger’s past behavior or preferences.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFurthermore, Elasticsearch’s speed and scalability enable airlines to enhance customer service. By integrating Elasticsearch into customer support systems, airlines can quickly retrieve relevant data, such as booking history or frequent flyer status, to provide personalised and timely assistance.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elasticsearch enhances airside, too ","_metadata":{"uid":"csd96eb6e946d137a1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe power of Elasticsearch isn’t limited to landside. Airside, it can enhance predictive maintenance and safety, operational efficiency, and cost savings. Here are some of the use cases:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMaintenance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Aircraft maintenance involves analysing and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/customers/airbus\"\u003e\u003cspan style='font-size: 12pt;'\u003ecentralising information across vast amounts of sensor data\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, maintenance logs, and operational history to identify potential issues before they become critical.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCompliance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eAviation authorities and airlines must be able to quickly search for and retrieve necessary documentation during audits or investigations. Because it can handle structured and unstructured data, Elasticsearch ensures that safety and regulatory compliance processes are both thorough and efficient.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOperational efficiency: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eBy aggregating and analysing airport operations data, such as passenger flow, gate usage, and security line wait times, stakeholders can identify bottlenecks and optimise resource allocation. Airlines can also use Elasticsearch to analyse fuel consumption patterns, optimise routes, and reduce operational costs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, by indexing weather forecasts alongside historical flight data, Elasticsearch can help create models to anticipate and mitigate disruptions caused by adverse weather conditions — lowering costs and improving punctuality.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSafety:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This is the cornerstone of aviation. Elasticsearch contributes to safety by facilitating predictive maintenance. Aircraft maintenance involves analysing vast amounts of sensor data, maintenance logs, and operational history to identify potential issues before they become critical. This is achieved by ingesting and analysing this data in real time, enabling predictive analytics that help schedule maintenance efficiently and avoid costly downtime.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFraud detection and cybersecurity: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWith increased digitisation comes greater susceptibility to fraud and cyber attacks. Elasticsearch’s machine learning capabilities are used by customers in the aviation industry around the world. They use them to detect anomalies in data streams, such as unusual booking patterns or unauthorised access attempts. And real-time alerting systems help mitigate potential threats swiftly, protecting sensitive customer and operational data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elasticsearch gives wings to data management ","_metadata":{"uid":"cs73747a63b08d685d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch is revolutionising how the aviation industry manages and analyses data. Its ability to process vast datasets in real time, provide actionable insights, and enhance both operational and customer-centric processes makes it an invaluable tool for airlines, airports, and other aviation stakeholders.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs the industry continues to embrace digital transformation, Elasticsearch’s role in improving efficiency, safety, and customer satisfaction will only grow — cementing its place as a cornerstone technology in aviation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to start your journey? \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003eSign up for a 14-day free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csfa583e5c3c4a55a7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs86745345abf06cb2"}}}],"publish_date":"2025-03-18","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blte63217e73b24f852","ACL":{},"created_at":"2023-11-06T21:49:35.924Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-frame-analytics","label_l10n":"Data frame analytics","tags":[],"title":"Data frame analytics","updated_at":"2023-11-06T21:49:35.924Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.093Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt7a4eb1026ba18f63","ACL":{},"created_at":"2023-11-06T20:07:03.185Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"advanced-persistent-threat","label_l10n":"Advanced Persistent Threat (APT)","tags":[],"title":"Advanced Persistent Threat (APT)","updated_at":"2023-11-06T20:07:03.185Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:50.393Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdd4b5182721ccd42","ACL":{},"created_at":"2023-11-06T20:38:13.883Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"digital-experience","label_l10n":"Digital experience","tags":[],"title":"Digital experience","updated_at":"2023-11-06T20:38:13.883Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.180Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte6358c0a4368f192","ACL":{},"created_at":"2023-11-06T20:39:12.952Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"end-user-experience","label_l10n":"End user experience","tags":[],"title":"End user experience","updated_at":"2023-11-06T20:39:12.952Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:48.382Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Knowledge base search","label_l10n":"Knowledge base search","keyword":"knowledge-base-search","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2c020c0c24ae64ef","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:41:47.026Z","updated_at":"2023-11-06T20:41:47.026Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.958Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3c3c124c70b20f1e","ACL":{},"created_at":"2023-11-06T20:47:25.066Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"predictive-analytics","label_l10n":"Predictive analytics","tags":[],"title":"Predictive analytics","updated_at":"2023-11-06T20:47:25.066Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:06.368Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Search UI","label_l10n":"Search UI","keyword":"search-ui","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltaea23ea6eafbd6eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:31:21.217Z","updated_at":"2023-11-06T21:31:21.217Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.855Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt3ff56eb3b9c58312","ACL":{},"created_at":"2020-06-17T03:33:18.405Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"business-analytics","label_l10n":"Business analytics","tags":[],"title":"Business analytics","updated_at":"2020-07-06T22:20:18.826Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.556Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt9f3033eaacd184dd","ACL":{},"created_at":"2022-09-13T16:43:44.540Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2022-09-13T16:43:44.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.249Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt3296a54c4e9420ae","_version":1,"title":"174142 - Blog header image- Elasticsearch in the aviation industry-2.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-23T02:08:34.835Z","updated_at":"2025-02-23T02:08:34.835Z","content_type":"image/jpeg","file_size":"180858","filename":"174142_-_Blog_header_image-_Elasticsearch_in_the_aviation_industry-2.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-18T17:50:32.634Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3296a54c4e9420ae/67ba832250b73077e87aec44/174142_-_Blog_header_image-_Elasticsearch_in_the_aviation_industry-2.jpg"},"title":"Elasticsearch in the aviation industry: A game-changer for data management","title_l10n":"Elasticsearch in the aviation industry: A game-changer for data management","updated_at":"2025-03-25T15:33:52.239Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elasticsearch-data-management-aviation","publish_details":{"time":"2025-03-25T15:34:05.139Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltaa065372e6b262e6","_version":1,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["blt469efe6417174bf5"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-03-25T15:29:01.869Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"Version 8.17.4 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.17.4 over the previous version 8.17.3.\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.17/new.html).\n","modular_blocks":[],"publish_date":"2025-03-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8836a5dda86cbfe0","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-01T15:42:09.734Z","updated_at":"2024-04-01T15:42:09.734Z","content_type":"image/png","file_size":"62454","filename":"Patch_release_dark.png","title":"Patch_release_dark.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-02T17:14:25.081Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8836a5dda86cbfe0/660ad5d11b5a5878c8adccbc/Patch_release_dark.png"},"title":"Elastic Stack 8.17.4 released","title_l10n":"Elastic Stack 8.17.4 released","updated_at":"2025-03-25T15:29:01.869Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-stack-8-17-4-released","publish_details":{"time":"2025-03-25T17:02:23.570Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb8541e2b210fc92a","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["blt469efe6417174bf5"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-03-25T15:19:51.467Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"Version 8.16.6 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.16.6 over the previous version 8.16.5.\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.16/new.html).\n","modular_blocks":[],"publish_date":"2025-03-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt720a36f34ba37235","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-08T02:19:40.632Z","updated_at":"2024-04-08T02:19:40.632Z","content_type":"image/png","file_size":"59668","filename":"Patch_release_white.png","title":"Patch_release_white.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-08T20:16:44.015Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt720a36f34ba37235/6613543c0d99458bb1031dca/Patch_release_white.png"},"title":"Elastic Stack 8.16.6 released","title_l10n":"Elastic Stack 8.16.6 released","updated_at":"2025-03-25T15:21:52.049Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-stack-8-16-6-released","publish_details":{"time":"2025-03-25T17:02:30.364Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3df9f5cde799cb8b","_version":15,"locale":"en-us","ACL":{},"abstract_l10n":"Explore how AI and generative AI are transforming government with use cases, examples, and Elastic’s AI-driven solutions for efficiency, transparency, and citizen engagement.","author":["blt6705dad0ae6f1419"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-24T21:45:31.656Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs05a7d5529fb3cafd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArtificial intelligence technologies are everywhere in the private sector. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/ai-in-business\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI in business\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is steadily transforming efficiency, productivity, and profitability. In the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic sector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, however, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-adoption-lessons-from-it-leaders\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI adoption\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e has been slower than in other industries. From state to federal government agencies, AI has the potential to revolutionize public administration by enhancing decision-making, streamlining operations, and improving citizen services. It presents an opportunity to address social challenges like food insecurity, environmental concerns, and public safety.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHowever, AI in government comes with governance considerations that will shape best practices as new technology emerges. This article explores AI's role in government operations, its benefits, and how government agencies and stakeholders can effectively implement AI-driven solutions for more efficient processes for everyone — from federal agencies down to each constituent.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Understanding AI in the public sector","_metadata":{"uid":"csab7fe5c1d0d9bd66"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArtificial intelligence is a set of technologies that enable machines to mimic human intelligence and make efficient and accurate data-driven predictions, recommendations, and decisions. A subset of AI, generative AI, goes a step further. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e features enhanced data processing capabilities and the ability to create new, original content. It enables intuitive, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style='font-size: 12pt;'\u003enatural language\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e interactions with machines, making technology more accessible. Be it traditional AI or generative AI, at its core, AI can leverage and process data more efficiently than humans can.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernment agencies run on vast amounts of data — likely even more data than most private organizations. This data is often highly sensitive and subject to strict privacy laws. As a result, the public sector is challenging. It has to serve the needs of every citizen, and different agencies have digitized differently and at various speeds. The result is overwhelming amounts of digital data, distributed across information silos that government agents — and citizen users — don’t always have the skills to navigate.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLegislation, transactions, records, intelligence, and more form the data pool of government agencies and stakeholders. AI can help conquer big data challenges: breaking down silos, streamlining operations, and enhancing efficiency. By using AI, agencies can reduce costs, improve service delivery, and enhance citizen satisfaction.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs418f7593b12eea2a"}}},{"banner":{"reference":[{"uid":"blt655c8e8e72e9f833","_content_type_uid":"banner"}],"_metadata":{"uid":"cs23ee950ed4984be7"}}},{"title_text":{"title_text":[{"title_l10n":"Government AI applications and use cases","_metadata":{"uid":"cs6c0b39c2b3248a13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernment AI spans all agencies and stakeholders working with and in the government. From data processing to defense technology, AI can be implemented in big and small ways. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/machine-learning\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI and machine learning (ML)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are used to respond to several government data challenges, particularly in improving public service delivery, supporting data-driven decision-making, and improving operational efficiency through automation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernment agencies that focus on healthcare, education, transportation, and critical public services must rely on large, often protected datasets. With AI analytics and automation capabilities, governments can improve the efficiency of public service delivery.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Transportation","_metadata":{"uid":"cs556a47156915a6cb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/manufacturing\"\u003e\u003cspan style='font-size: 12pt;'\u003etransportation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, machine learning algorithms can be used for traffic optimization and predictive maintenance for transportation infrastructure. In the US, organizations are exploring using AI for public transportation applications, reading sensor data, and helping users plan routes and trips and improve roadway safety.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Education","_metadata":{"uid":"cs6169acd85ca50bfd"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/education\"\u003e\u003cspan style='font-size: 12pt;'\u003eeducation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, AI can help close education gaps by democratizing access. According to UNESCO (the United Nations Educational, Scientific and Cultural Organization), AI has the potential to address some of the biggest challenges in education today. It can innovate teaching and learning practices and accelerate progress toward the sustainable development goal of ensuring inclusive and equitable quality education for all. AI also has the potential for offering personalized learning platforms and focused help for students. Some government agencies are already rolling out AI training modules within governments, with the possibility to expand to private citizens.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Healthcare","_metadata":{"uid":"csfda10f7286cadd41"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/healthcare\"\u003e\u003cspan style='font-size: 12pt;'\u003ehealthcare\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, AI-powered tools can improve the overall level of care by accelerating diagnoses and clinical research. AI can support many diagnostic tools and automate administrative processes. It has the potential to improve the collection of clinical data, expediting knowledge-sharing and research efforts across the healthcare sector. Government agencies across the world are also utilizing AI as a predictive analytics tool for disease outbreaks to prevent the next pandemic.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Citizen services","_metadata":{"uid":"csc8eee62e0e66b225"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBeyond prediction and processing, government agencies can use AI to better connect citizens with critical services they need. Consumers expect immediate, efficient, and personal service — and government agencies are often notorious for slow and inefficient processing times. AI can improve the quality of customer service and support to match expectations set by the level of service in the private sector.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the US, the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic sector\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is ranked lowest of 10 industries surveyed for customer satisfaction.\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e1\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e By integrating various AI applications like Search AI, chatbots with 24/7 availability, and automated administrative processes, governments can streamline public information dissemination, offer personalized government services, and improve customer service overall.\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRead more: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/customer-service-government-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eWhy customer service matters for government — and how AI will help\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"},{"title_l10n":"Automating internal processes","_metadata":{"uid":"cs916ec707764fc181"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernments handle vast amounts of paperwork, data, and administrative tasks. Time wasted manually sorting through documents can have real ramifications for citizens. The US government estimates that $140 billion\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e2\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e in potential benefits go unused each year because of outdated or complicated processes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBeyond improving knowledge-sharing, access controls, and overall efficiency, going paperless paves the way for automation and AI. AI is particularly useful for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/information-retrieval\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieving information\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e stored in various formats and locations, making data more accessible and preventing employees from wasting time searching through different files and systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSome estimates predict that the US public sector will collectively experience $519 billion in productivity gains from generative AI by 2033.\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e3\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e By reducing manual workloads, AI helps minimize human error and increases operational efficiency.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the legal field, AI can find information stored in different places and formats. It can automate processes such as document processing and classification; workflow automation for permits, tax filings, and social benefits; and fraud detection in public assistance programs. AI can also simplify and streamline legal processes, including e-discovery, compliance checks, and contract analysis, enhancing accuracy and efficiency.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI can also help sift through large amounts of information in higher education, especially research institutions. Generative AI helps researchers locate and use contextual, relevant information from a variety of sources. This is especially crucial for collaborative research projects that span across departments or universities.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Decision support","_metadata":{"uid":"cs0f17ae8275182ff5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData-driven decision-making is key to optimizing efficiency, services, and outputs. However, recent research showed that only \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/public-sector-leaders-insights-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003e32% of public sector leaders\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e use data insights for daily decisions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI gives its users the unparalleled ability to draw valuable insights from consolidated data that support decision-making. For instance, predictive analytics can forecast trends in crime, public health, and economic shifts, helping governments proactively mitigate and respond to these challenges.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePolicy-makers can also rely on predictive analytics to build simulation models that assess the potential impacts of legislation before it is implemented.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRead more: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/5-generative-ai-insights-for-leaders\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolving challenges with data and AI: 5 insights for public sector leaders\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"},{"title_l10n":"AI governance framework","_metadata":{"uid":"cs0338cc96166c14b4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLike everything in the public sector, AI use must be carefully regulated to ensure ethical deployment, fairness, and transparency. Government agencies work with sensitive data. Establishing robust governance frameworks helps mitigate risks, uphold legal standards, and maintain public trust in government AI initiatives. The latter is key in meeting consumer expectations and improving government services.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Regulations","_metadata":{"uid":"cs2cb19227d9c16b32"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRegulatory bodies have, for the most part, largely struggled to keep up with AI advancement. The speedy adoption of AI in private sectors and an uneven understanding of the technology’s capabilities, benefits, and risks make regulation a challenge.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo respond, governments are establishing ethical standards, legal considerations, and frameworks to ensure responsible AI usage. These regulations aim to promote fairness, accountability, and transparency, ensuring AI applications align with democratic values and human rights. However, compliance with these frameworks varies across regions, influencing how AI is implemented in government agencies.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Compliance requirements","_metadata":{"uid":"cs6f3b9dd2d2fe8429"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOverall, data privacy laws, fairness mandates, and transparency guidelines are at the heart of compliance requirements, which aim to ensure trustworthy and safe AI services.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the US, no current federal, overarching AI regulations exist,\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e4\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and efforts to adopt or reject them are intrinsically tied to the two-party system. Administrations will sway between imposing regulations or removing them altogether in favor of fast-paced innovation. Instead, states create regulations, resulting in a patchwork of legislation and a complicated compliance landscape that government agencies and stakeholders are left to navigate on their own.\u003cbr /\u003e\u003cbr /\u003eOn the other hand, the European Union introduced the \u003c/span\u003e\u003ca href=\"http://www.elastic.co/blog/eu-ai-act\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI Act\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, the first-ever legal framework to guarantee safety, fundamental rights, and human-centric AI and strengthen uptake, investment, and innovation in AI across the EU.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Security considerations","_metadata":{"uid":"cs81975849e2cd7fc8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe greatest security concern in the use of generative AI in government is how to handle sensitive data with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/open-source-llms-guide\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic large language models (LLMs)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, foundational pieces of AI systems that use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style='font-size: 12pt;'\u003enatural language\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Improper use of public LLMs can pose risks such as data leaks, unintended exposure of classified information, and vulnerabilities to adversarial manipulation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI systems often function as black boxes, making security assurance particularly challenging. Their lack of transparency complicates risk assessment and mitigation efforts, increasing vulnerabilities to data breaches and adversarial attacks. Consequently, deploying AI in government presents complex security challenges, particularly in protecting national security interests. Implementing stringent safeguards, such as robust encryption, access controls, and continuous monitoring is essential to mitigate these risks effectively.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo ensure that generative AI is grounded with proper context, organizations can implement \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieval augmented generation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, or RAG, a group of techniques that enable the safe use of proprietary data. This approach helps mitigate risks by ensuring AI models rely on authoritative, up-to-date data rather than solely on potentially biased or outdated training data. By integrating RAG, government agencies can maintain greater control over sensitive information, and rely on more context-aware responses.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Implementation strategies","_metadata":{"uid":"cse2606c0902264a0f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe biggest challenges in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-adoption-lessons-from-it-leaders\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI adoption\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e aren’t just technical. They include a lack of specialized talent and often unclear regulations.\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e5\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Many agencies face resistance due to concerns over \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/data-security\"\u003e\u003cspan style='font-size: 12pt;'\u003edata security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, job displacement, and the complexity of implementation. Successfully integrating AI into government must be a multi-step, strategic process that overcomes these obstacles and fosters a culture of innovation.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnsuring real-time data visibility: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEffective AI implementation depends wholly on agencies having complete, real-time access to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eall\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e relevant data. Without full visibility, AI-driven insights and automation may be incomplete or inaccurate. After all, AI is only as good as the data it uses.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePlanning and governance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e While the lack of regulation may foster innovation, it may hinder government-level adoption of AI. Establishing clear policies, ethical guidelines, and regulatory compliance measures can help ensure fast — and responsible — AI deployment.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIdentifying specific use cases:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Agencies should assess where AI can drive the most impact, whether in public services, automation, or decision-making. Governments should slowly scale these services to impact sector and economy levels.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScaling and security: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eBeyond scaling use cases, agencies should ensure that the technology has the capacity to meet scale and evolving government needs while remaining secure.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIntegration with existing systems: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThough government agencies are at varying levels of technological maturity, ensuring that AI systems seamlessly integrate into existing systems is key to successful implementation.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Government AI initiatives","_metadata":{"uid":"csccfb2782866b9944"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAround the world, government agencies are developing programs to upskill the workforce of government stakeholders and public users on using AI to unlock even more benefits (while mitigating the risks).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe US Department of State AI Inventory 2024 outlines various AI applications in diplomacy, cybersecurity, and administrative functions, aimed at improving public services, efficiency, and decision-making.\u003c/span\u003e\u003cspan style='font-size: 0.6em;'\u003e\u003csup\u003e6\u003c/sup\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.state.gov/artificial-intelligence/\"\u003e\u003cspan style='font-size: 12pt;'\u003eThe U.S. Department of State is using AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to modernize its diplomatic statecraft. The Office of the Under Secretary for Management uses AI technologies within the Department of State to advance traditional diplomatic activities, applying machine learning to internal information technology and management consultant functions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSome other examples of initiatives include:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTranslation of consular content:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e AI translation models work alongside teams to provide consular content on government websites to customers in their preferred language. AI reduces the time and resources typically needed while the human touch ensures accuracy and understanding (AI still struggles with legal jargon!).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eViolence Against Civilians Model:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e A machine learning model that uses open source political, social, and economic datasets to forecast mass civilian killings for the upcoming quarter and year for each country globally in order to inform conflict prevention.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSenturion Alpha:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e A stakeholder/influence-driven model that identifies where key decision-makers fall on an issue spectrum and who influences whom. The simulation analyzes the political dynamics within contexts and estimates how the policy positions of competing interests will evolve over time.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStoryzy:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Improves detected use of synthetic content, which refers to computer-generated data that mimics real-world data.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"AI solutions for government agencies with Elasticsearch","_metadata":{"uid":"cs4c98e0e3cb73dbe6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e offers full search capabilities for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003ebuilding AI apps\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/rag\"\u003e\u003cspan style='font-size: 12pt;'\u003eRAG workflows\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/document-level-security.html\"\u003e\u003cspan style='font-size: 12pt;'\u003edocument-level security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/vector-database\"\u003e\u003cspan style='font-size: 12pt;'\u003ea production-ready vector database\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/elasticsearch-relevance-engine\"\u003e\u003cspan style='font-size: 12pt;'\u003eELSER\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e pretrained retrieval model for more relevant natural language search results, and E5 (multi-language) support. Elastic’s open approach allows your team to integrate your data, securely, with your own or third-party transformer models.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdvanced data analytics:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Real-time insights from structured and unstructured data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced search capabilities:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Improved data retrieval for intelligence and public records\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScalable AI systems:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Flexible infrastructure that adapts to evolving demands\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy leveraging \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, government agencies can enhance transparency, efficiency, and citizen engagement, driving digital transformation at scale.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0653c296b7f1149d"}}},{"video":{"vidyard_uuid":"2YDcbHU6Wbdohkck54q1Ze?","_metadata":{"uid":"cs8f0cbff77133bbb2"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdd81e74d345a733c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/data-mesh-public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLearn more about data mesh for public sector.\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8d871b16c615caba"}}},{"callout":{"title_l10n":"Explore more resources on AI applications and use cases for government agencies","_metadata":{"uid":"cs13b334e7ef71a2df"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"http://elastic.co/industries/public-sector\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDeep dive into Elastic for public sector\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/public-sector-data-stewardship-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePublic sector data stewardship for the AI era\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/data-mesh-public-sector\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eData mesh in public sector: Pillars, architecture, and examples\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/portfolio/operationalizing-generative-ai-strategic-guide\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAn executive’s guide to operationalizing generative AI\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/how-search-ai-transforms-call-centers-citizen-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow Search AI is transforming call centers and citizen support\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/customer-service-government-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhy customer service matters for government — and how AI will help\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd3bc9fe7854d446d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cstrong\u003eSources:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u0026nbsp;1. McKinsey \u0026amp; Company, “\u003c/span\u003e\u003ca href=\"https://www.mckinsey.com/industries/public-sector/our-insights/governments-can-deliver-exceptional-customer-experiences-heres-how\"\u003e\u003cspan style='font-size: 10pt;'\u003eGovernments can deliver exceptional customer experiences—here’s how\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 10pt;'\u003e,” 2022.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e2. The White House, “\u003c/span\u003e\u003ca href=\"https://bidenwhitehouse.archives.gov/omb/briefing-room/2023/09/22/fact-sheet-building-digital-experiences-for-the-american-people/\"\u003e\u003cspan style='font-size: 10pt;'\u003eFACT SHEET: Building Digital Experiences for the American People\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 10pt;'\u003e,” 2023.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e3. Boston Consulting Group, “\u003c/span\u003e\u003ca href=\"https://www.bcg.com/publications/2023/unlocking-genai-opportunities-in-the-government#\"\u003e\u003cspan style='font-size: 10pt;'\u003eGenerative AI for the Public Sector: From Opportunities to Value\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 10pt;'\u003e,” 2023.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e4. Software Improvement Group, “\u003c/span\u003e\u003ca href=\"https://www.softwareimprovementgroup.com/us-ai-legislation-overview/\"\u003e\u003cspan style='font-size: 10pt;'\u003eAI Legislation in the US: A 2025 Overview\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 10pt;'\u003e,” 2025.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e5. McKinsey \u0026amp; Company, “\u003c/span\u003e\u003ca href=\"https://www.mckinsey.com/industries/public-sector/our-insights/the-potential-value-of-ai-and-how-governments-could-look-to-capture-it\"\u003e\u003cspan style='font-size: 10pt;'\u003eThe potential value of AI—and how governments could look to capture it\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 10pt;'\u003e,” 2022.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e6. U.S. Department of State, “\u003c/span\u003e\u003ca href=\"https://2021-2025.state.gov/department-of-state-ai-inventory-2024/\"\u003e\u003cspan style='font-size: 10pt;'\u003eDepartment of State AI Inventory 2024\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 10pt;'\u003e,” 2024.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9df4da83055cbdcb"}}}],"publish_date":"2025-03-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt5c6ac057387f6ba9","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-24T21:43:17.405Z","created_by":"blte369ea3bcd6ac892","file_size":"150931","filename":"Blog_Header_Understanding_AI_in_government_Applications_use_cases_and_examples_176794.jpg","parent_uid":null,"tags":[],"title":"Blog Header Understanding AI in government_ Applications, use cases, and examples 176794.jpg","updated_at":"2025-03-24T21:43:17.405Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-25T14:00:00.548Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5c6ac057387f6ba9/67e1d1f52e137cb4e2b8afd8/Blog_Header_Understanding_AI_in_government_Applications_use_cases_and_examples_176794.jpg"},"title":"Understanding AI in government: Applications, use cases, and implementation","title_l10n":"Understanding AI in government: Applications, use cases, and implementation","updated_at":"2025-03-24T22:34:36.526Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/ai-government","publish_details":{"time":"2025-03-25T14:00:00.534Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt30a3f6bd380b89a4","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":" Explore the role of AI in customer support, from chatbots to virtual assistants, enhancing user experiences and increasing satisfaction without replacing human agents.","author":["blt6705dad0ae6f1419"],"category":["bltc17514bfdbc519df"],"created_at":"2024-09-25T16:38:28.484Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4ff02e8c9c9f3130"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’ve all experienced it: walking into the store and seeing a line at the in-person checkout stations while all the self-checkout stations are free. This is what happens when convenience tools aren’t all that convenient. For a while, that was the case with many customer service “solutions.” Remember early chatbots like Ikea’s \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eAnna\u003c/em\u003e\u003csup\u003e1\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and Alaska Airlines’ \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eAsk Jenn\u003c/em\u003e\u003c/span\u003e\u003csup\u003e2\u003c/sup\u003e\u003cspan style=\"font-size: 12pt;\"\u003e? When tech is more clunky than useful, customers bypass it altogether.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYet, 90% of customers expect an immediate response to customer service issues.\u003csup\u003e3\u003c/sup\u003e Enter artificial intelligence (AI) customer support tools, which have become game changers for businesses hoping to streamline their customer service systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAI integrations in customer support have become essential and expected by customers. Gartner has forecasted that generative AI (GenAI) will power 80% of customer service and support operations by 2028.\u003csup\u003e4\u003c/sup\u003e And it’s not all about customer-facing interactions — AI can assist human agents by providing them with insights to help them give customers a top-notch experience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs AI is increasingly normalized for customer support systems, businesses need to understand how to implement the best tools for the most value. Personalization is the key to effective customer support. By personalizing solutions to your business and your customers, you can anticipate their needs — which is at the core of any good customer experience.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What is AI in customer support?","_metadata":{"uid":"cs87312efbee26bbf6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAI is used in customer support to create smoother, more personalized interactions while lightening the load for human customer service reps. Most commonly, AI is used in chatbots that use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/machine-learning\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003emachine learning (ML)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enatural language processing (NLP)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to mimic human speech and resolve customer issues. But AI in customer support doesn’t begin and end with chatbots. From virtual assistants to AI-powered search, companies can integrate AI into almost every facet of the user experience to support their customer service teams. The goal isn’t to \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003ereplace\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e customer support but to \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eenhance\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhen used to its fullest potential, AI can help customer support teams boost productivity, increase customer satisfaction, and bolster their bottom line. Long-term customers are more profitable and cheaper to retain, and they talk up their favorite brands to peers. Good customer service can turn tentative customers into brand loyalists. But customer expectations are also rising. Users expect frictionless experiences that resolve their issues faster and better than before. And 80% of customers claim that the experience that a company provides is as important as its product and services.\u003csup\u003e5\u003c/sup\u003e So, being behind the curve might mean losing them. Therefore, it’s no surprise that businesses are scrambling to implement AI tools for customer service.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHere’s how to do it right to satisfy customers and streamline customer success operations.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Diverse AI technologies in customer support","_metadata":{"uid":"cs5002aa63b567fa90"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI has significantly expanded what can be automated in customer service. While chatbots are still the most common and most accessible AI tool for customer support, they might not be the best fit for your business. Familiarizing yourself with the landscape can help you decide which AI tool will best serve your teams and your customers.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Chatbots","_metadata":{"uid":"cse9f3d9dcd77182d1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/enhancing-chatbot-capabilities-with-nlp-and-vector-search-in-elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003eChatbots\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e are automated systems that can tackle basic questions and routine tasks, giving customers quick answers and easing the load on human agents. They’re built to handle tons of interactions at once and are a staple for any high-traffic support system.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Virtual assistants","_metadata":{"uid":"cs5335d752664e9a34"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eVirtual assistants can manage more sophisticated queries than chatbots and give customer interactions a more personalized touch. They’re a better option than chatbots if a user needs to be guided through a complex process.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Vector search","_metadata":{"uid":"csebd98115906827ca"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen customers are searching for something but aren’t using the exact keywords, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/vector-search\"\u003e\u003cspan style='font-size: 12pt;'\u003evector search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e can help. Through embeddings — numerical representations of data that capture its context — vector search can identify information that’s conceptually like the search term even when exact matches of keywords aren’t being used.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Hybrid search","_metadata":{"uid":"csd1d96334b2f549d2"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHybrid search combines different search techniques like vector and keyword search to deliver better \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/search-relevance\"\u003e\u003cspan style='font-size: 12pt;'\u003erelevance\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. It blends dense and sparse embeddings to fine-tune the balance between understanding context and matching specific terms.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Natural language processing (NLP)","_metadata":{"uid":"cs02688aae7eba45d0"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style='font-size: 12pt;'\u003eNLP\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is used to interpret and respond to human language with nuanced understanding. It lets chatbots and virtual assistants grasp what a customer is saying and respond in a way that makes sense and feels like a natural conversation.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Machine learning algorithms","_metadata":{"uid":"csc2412e1d62147885"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/machine-learning\"\u003e\u003cspan style='font-size: 12pt;'\u003eMachine learning\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e algorithms are at the heart of AI’s continuous improvement. By analyzing vast amounts of data from previous interactions, machine learning helps AI systems refine and improve their future responses.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Automated response systems (ARS)","_metadata":{"uid":"csc0a949b1beb61cae"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese systems are designed to handle large volumes of customer queries. They automate responses to common questions and issues so that human agents don’t get overwhelmed and can focus on more complex customer issues instead.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"AI-powered analytics","_metadata":{"uid":"cs3e3534e86a5d40d2"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith AI-powered analytics, you can dive deep into customer data and find insights that help you predict what customers want. It also helps you make informed decisions about the best ways to tailor your support strategies in the future.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Implementing AI in customer support","_metadata":{"uid":"cscf67455e62ddad77"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA roadblock for many businesses that want to experiment with AI is the implementation process. Integrating AI into your existing systems doesn’t have to be intimidating. The right tools and the right partners make adding AI integrations intuitive. But to find the right tools, the first step is to establish exactly what your goals are. Only by knowing what your business — and your customers — really need can you make significant improvements to your customer support systems. Here’s how to implement AI in customer support.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 1: Understand your customers well ","_metadata":{"uid":"csd812cbbe6949c555"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhat are their demographics and interests? What are their pain points? Do they respond more positively to voice or digital interactions? By understanding the customer, you can tailor your solutions to proactively address their needs.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 2: Determine if you want AI to improve your self-service tools or support your human agents (chances are you’ll want to do a little of both)","_metadata":{"uid":"cs8ed8973fc478182f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSelf-service\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e provides your customers with tools that’ll help them serve themselves. Virtual agents or chatbots are usually a good choice here. Normally this process requires analyzing customer queries, understanding their intent, and then having a customer service expert create dialogue flows to help the customer get where they need to be. These flows were often time-consuming to create — a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eChoose Your Own Adventure\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e-style of writing that could easily go off course if the customer sends it a curveball. Fortunately, generative AI has made the process a lot simpler. Not only does it make building the flows easier, but it’s also more resilient to digressions and variations during customer interactions.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSupporting your human agents with AI\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is another approach you can take. A new call center agent might be spending a lot of time searching knowledge bases, documentation, and case histories to get the right answer for a customer. GenAI can retrieve information faster and summarize it quickly, cutting down customer wait times in the process. If you’ve ever been on hold for a long time, you know how much this can improve the customer experience. Another way GenAI can help is by automatically drafting responses to customer emails based on what they’re asking and any context available. The customer service rep can then review the email before it’s sent to make sure it makes sense and appropriately handles the query.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 3: Determine what experience you want to create ","_metadata":{"uid":"csc78b4754d098cbb5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou know your audience, and you have a general idea of the ways you’d like to serve them. It’s time to map out your end-to-end customer journeys (chances are you’ll have at least a few) and then look at the best tools to support them. Don’t limit yourself to budget concerns as you brainstorm these journeys — go big. You can rein things in during the next step.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 4: Think about your budget and ROI ","_metadata":{"uid":"cs90bbd6b8e73f074f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFirst, calculate the cost of different AI tools and technologies — and remember to factor in both your upfront investment \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eand\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e ongoing expenses, maintenance, and updates.\u0026nbsp; When you have all that assessed, consider your ROI. Using the in-house data you have, think about the different ways your plan will improve customer satisfaction and how that will affect your bottom line.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 5: Design the customer experience end to end ","_metadata":{"uid":"cs20a2d9e20b7dc6e6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s time to look back at Step 3 with Step 4’s budget in mind. Choose your tools and design strategies that serve both your customers and agents.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 6: Train your customer service team ","_metadata":{"uid":"cs18ff159a0d7ac2f9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCan your customer service reps seamlessly pick up a conversation if a chatbot passes one to them? Do they understand when and where to intervene if a customer is having a poor experience that the AI tools can’t solve? Do they have a basic understanding of how to use the technology correctly during interactions and gather insights from it later? By training your customer service team, you can still succeed in giving customers a personalized experience when AI struggles to provide answers.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Step 7: Review data and iterate ","_metadata":{"uid":"cs5c6c35681e1301c3"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI makes this process easier, too. For example, a big chunk of a call center’s job is documenting conversations. GenAI can make transcripts of every call, which gives time back to the operators. It can also use these transcripts to come up with insights as to why certain calls are taking longer or if certain products or services are having issues that need to be reported to the product and marketing departments.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Challenges of AI in customer support","_metadata":{"uid":"cs61ba2fe25ec12902"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImplementing a new technology comes with its challenges. And despite the potential of AI, some customers — and some teams — might be skeptical. With the right AI tool and the right implementation process, you can get past most of the common obstacles. Here are some of the potential challenges of AI in customer support and how to solve them.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Managing customer expectations","_metadata":{"uid":"cs643fbc4e34421cb3"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccording to a recent Gartner study, some customers may worry that GenAI will just add another barrier between them and a real agent. Others are concerned it’ll provide the wrong answers or possibly even be biased against certain customers.\u003csup\u003e6\u003c/sup\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e It will be up to your business to communicate to customers how AI can make the service experience better. Be upfront: Let customers know when they’re interacting with AI. And never hesitate to escalate complex cases to human agents when AI falls short.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Privacy and security concerns","_metadata":{"uid":"cs11d84693eabd59cd"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAny system that handles customer data is a prime target for hackers, and AI is no exception. These systems often need to process large amounts of personal information, so privacy and security can’t just be an afterthought.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e You’ll need to stay on top of data protection laws and regularly update your security measures to keep up with new threats — it’s crucial for maintaining customer trust.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Technical integration issues","_metadata":{"uid":"csa1bae6e9996b4adf"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMany companies still rely on older systems that weren’t built with AI in mind. This can mean upgrades — often expensive and time-consuming ones.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Start with a thorough assessment of your current systems, looking for areas where AI can fit in smoothly and where upgrades are necessary. Phased rollouts can help minimize disruptions, allowing you to iron out issues before scaling up.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Resistance from support teams","_metadata":{"uid":"cs57ea96ad1f0e9540"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSupport teams might push back against AI integration because they’re resistant to a new way of doing things, or they’re worried that automation will replace them.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The key here is to involve the team from the start, offer plenty of training, and show them how AI can make their jobs easier, not take them away.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Continuous updates and maintenance","_metadata":{"uid":"cs30ec0a4b9e644fca"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI systems need regular updates to keep up with changing customer needs and new tech developments. If companies don’t keep up, they risk their AI falling behind and becoming more of a liability than an asset.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e You’ll want to establish a schedule for regular system reviews and updates as well as invest in ongoing learning for your AI systems by feeding them fresh data and refining their algorithms.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key benefits of AI in customer support","_metadata":{"uid":"cse3ee6a0075ed8d26"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce you’ve pushed through the challenges, you get to reap the benefits of AI in customer support. Here are some of the ways AI in customer support can transform your business:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e24/7 availability:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Customers will have access to assistance around the clock, regardless of time zones or business hours.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInstant response:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e AI delivers immediate answers and solutions and keeps the customer experience smooth and frustration-free.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePersonalized service:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Customer data helps AI tailor its responses and recommendations. This helps it make each customer experience feel personable.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced efficiency:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e AI streamlines support operations by automating routine tasks and inquiries. This lets human agents focus on more complex and nuanced issues.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eReduced costs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Automating processes means less money spent on manual tasks and more streamlined operations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImproved data collection and analysis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e AI digs into every customer interaction to gather valuable insights, helping you understand trends and improve your support strategy.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScalability of support operations:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e AI handles increasing volumes easily so that your business can expand without growing pains.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Case study: How Cisco transformed its support experience","_metadata":{"uid":"cs021533698dadff23"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFounded in 1984, Cisco is the backbone of the global network economy, serving more than 87% of Fortune 500 companies. But with millions of service requests and countless documents to sift through, it faced a real challenge: how to deliver quick and accurate support with such substantial volume.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe solution was an overhaul of Cisco’s search capabilities powered by AI. To do this, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/customers/cisco\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCisco partnered with Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to revamp its customer support system. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, running on\u0026nbsp;\u003c/span\u003e\u003ca href=\"https://www.elastic.co/elastic-cloud-kubernetes\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud on Kubernetes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, is now the engine at the center of Cisco’s new enterprise search architecture. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis new tool, c\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003ealled \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRe-imagined Topic Search, saves Cisco’s support engineers 5,000 hours a month. Now, engineers can quickly pull up relevant documents and similar cases whether they're helping customers over the phone or online.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Feedback from our engineers is extremely positive,” says Sujith Joseph, principal enterprise search and cloud architect at Cisco Systems. “They now use Topic Search to solve 90% of service requests. They can deliver a better customer experience by easily finding on-target information and fixing issues much faster than before.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCisco.com also got a major AI upgrade. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt’s now powered by the Re-imagined Search Platform, an\u0026nbsp;AI\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esearch solution\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ebuilt on\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003ca href=\"https://www.elastic.co/partners/google-cloud\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGoogle Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eservices and Elasticsearch\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. This overhaul has slashed search response times by 73% and boosted user engagement while reducing operational costs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSince rolling out Re-imagined Search across customer support and Cisco.com, Cisco’s search team has also integrated it into more than 50 internal and external apps, including the Cisco intranet.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“Today, people expect instant search access to the information they need,” Joseph adds. “Keeping customers and potential customers aligned with relevant content about our solutions and services is fundamental to these relationships.”\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Harness AI for customer support with Elastic","_metadata":{"uid":"cs8169bf822615fd01"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e combines generative AI with powerful search technology to boost self-service support and streamline agent workflows. It taps into your organization’s own data, knowledge base, and process docs to deliver precise answers and smart recommendations, all while keeping document security tight and costs low.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5b7ea6bba111f2e0"}}},{"callout":{"title_l10n":"AI for customer support resources","_metadata":{"uid":"csdec2749ecaeaf1f6"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"/learn/transform-customer-support-with-ai-powered-search\"\u003eTransform customer support with AI search\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/cloud/generative-ai-trial-overview\"\u003eExplore generative AI in a free trial\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/genai-customer-support-building-proof-of-concept\"\u003eGenAI for customer support - Part 1: Building our proof of concept\u0026nbsp;\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/genai-customer-support-building-a-knowledge-library\"\u003eGenAI for customer support - Part 2: Building a knowledge library\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/genai-elastic-elser-chat-interface\"\u003eGenAI for customer support - Part 3: Designing a chat interface for chatbots\u003c/a\u003e\u0026nbsp;\u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/customer-service-government-ai\"\u003eWhy customer service matters for government — and how AI will help\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/resources/search/ebook/implementing-search-for-your-knowledge-base\" target=\"_self\"\u003eImplementing search and generative AI for your knowledge base\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs959ec36bfa49385a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003csup\u003e1\u003c/sup\u003e \u003ca href=\"https://www.chatbots.org/virtual_assistant/anna3/\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eChatbot Anna\u003c/span\u003e\u003c/a\u003e\u003csup\u003e\u003cbr superscript=\"[object Object]\"/\u003e\u003c/sup\u003e\u003csup\u003e2\u003c/sup\u003e \u003ca href=\"https://www.chatbots.org/virtual_assistant/jenn/\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eChatbot Jenn\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003csup\u003e\u003cbr superscript=\"[object Object]\"/\u003e\u003c/sup\u003e\u003c/span\u003e\u003csup\u003e3\u003c/sup\u003e\u003cspan style=\"font-size: 10pt;\"\u003e Hubspot \u003c/span\u003e\u003ca href=\"https://www.hubspot.com/hubfs/assets/flywheel%20campaigns/HubSpot%20Annual%20State%20of%20Service%20Report%20-%202022.pdf\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eAnnual State of Service\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, 2022\u003cbr /\u003e\u003c/span\u003e\u003csup\u003e4\u003c/sup\u003e \u003ca href=\"https://www.gartner.com/en/newsroom/press-releases/2023-08-30-gartner-reveals-three-technologies-that-will-transform-customer-service-and-support-by-2028\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eGartner Hype Cycle\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, 2023\u003cbr /\u003e\u003c/span\u003e\u003csup\u003e5\u003c/sup\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003csup\u003e\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 10pt;\"\u003e Salesforce, \u003c/span\u003e\u003ca href=\"https://www.salesforce.com/resources/research-reports/state-of-the-connected-customer/\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eState of the Connected Customer\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, 6th Edition\u003cbr /\u003e\u003c/span\u003e\u003csup\u003e\u003c/sup\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003csup\u003e\u003c/sup\u003e\u003c/span\u003e\u003csup\u003e6\u003c/sup\u003e \u003cspan style=\"font-size: 10pt;\"\u003eGartner, \u003c/span\u003e\u003ca href=\"https://www.gartner.com/en/webinar/631278/1394124\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003e4 Key Customer Insights to Guide Your Service CX Strategies\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, 2024\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs82a3c290a844431d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3daa4f9981cbcd4e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2ee0b2a5531ff0d8"}}}],"publish_date":"2024-09-26","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Understanding AI for customer support guide | Elastic","seo_description_l10n":"Explore the role of AI in customer support, from chatbots to virtual assistants, enhancing user experiences and increasing satisfaction without replacing human agents.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3184f3496194138e","ACL":{},"created_at":"2023-11-06T20:36:32.173Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-support","label_l10n":"Customer support","tags":[],"title":"Customer support","updated_at":"2023-11-06T20:36:32.173Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.257Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf04b065d79bd1a12","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-09-25T17:21:40.204Z","created_by":"bltb6c155cd84fc0c1a","file_size":"193635","filename":"elastic-de-142343-blogheader.V2_V1.jpg","parent_uid":null,"tags":[],"title":"elastic-de-142343-blogheader.V2_V1.jpg","updated_at":"2024-09-25T17:21:40.204Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-09-26T14:00:00.249Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf04b065d79bd1a12/66f446a4f9cb26549f43e479/elastic-de-142343-blogheader.V2_V1.jpg"},"title":"Understanding AI for customer support: How AI is transforming customer service","title_l10n":"Understanding AI for customer support: How AI is transforming customer service","updated_at":"2025-03-24T19:52:50.458Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/understanding-ai-customer-support","publish_details":{"time":"2025-03-24T19:52:54.680Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltaf7ec477f5ff8fef","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"In a recent evaluation, Informa TechTarget's Enterprise Strategy Group explored the business value Elastic Security offers. See the report findings, from improved security analytics with ML and AI to lower costs and greater business continuity.","author":["blt14f762eec103604e","blt4381ee7857316e89"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-24T03:50:02.281Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs524b0c81c2de3e15"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity is a complicated industry, with constant changes coming at a breakneck pace. The attack surface, stakeholder needs, adversary tactics, and the very tools you wield are constantly evolving — leaving many security teams unsure whether they’re prepared.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the unending fight, you deserve tools you can trust that also offer a substantial return on investment. Tools that provide unrivaled visibility, reduced risk, and scalability that matches your data needs without breaking the bank.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"A rigorous evaluation ","_metadata":{"uid":"cs9696f2d3e369aa68"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic commissioned Enterprise Strategy Group to provide an economic analysis of the business impact and value Elastic customers realize from Elastic Security. To conduct its study, Enterprise Strategy Group interviewed multiple SOC leaders of both private and public sector organizations that use Elastic, aggregating their experiences and results into a single composite organization: a high-tech enterprise with 5,000 employees, 11,650 endpoints, $900 million per year in revenue, and 3GB daily ingest for security analytics.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Glowing results","_metadata":{"uid":"cs1d59b32022819c29"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEnterprise Strategy Group collected information via customer interviews to compare the costs and benefits of Elastic Security. Three business value themes emerged:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eImproved security analytics with ML and AI: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security enhances organizations’ ability to secure their environments by providing actionable access to their data and insights that deliver a much clearer picture of their ecosystem.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eLower costs: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security introduces efficiencies to both the top and bottom lines of customers. It reduces the time employees spend on fatiguing tasks, delivers cost savings through tool consolidation and resource optimization, and enables some companies, such as MSSPs, to expand their operations and grow their revenue.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eImproved business continuity: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCustomers shared that Elastic enables their business to more effectively prevent and recover from a security event — reducing the likelihood and number of security incidents or breaches.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"}],"_metadata":{"uid":"csbd88dd7de8c73718"}}},{"quotes":{"quote_l10n":"“Since we have moved to Elastic, we are safer and more recoverable. We test\nmore, have deeper insights, and can assure our board of directors that we are\nbetter protected because of Elastic Security.”","_metadata":{"uid":"cs7b36783263f9c82f"},"quote_author_l10n":"Analyzing the Economic Benefits of Elastic Security","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb1f7b00aaedc01b6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy migrating to Elastic Security, customers have seen the following improvements:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e36% reduction in annual risk exposure\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e42%–56% reduction in total cost of ownership\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e74% reclamation of full-time security employees' hours, allowing for more strategic initiatives\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e75% lower false positives with Elastic Security’s machine learning-powered anomaly detection\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReduced mean time to investigate from 300 minutes to 90 minutes and mean time to remediate from 180 minutes to 6 minutes\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e66% faster time to value of new hires and 20% reduction in employee turnover\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e90% reduction in security events and incidents\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"}],"_metadata":{"uid":"cs071948a13e588eb7"}}},{"quotes":{"quote_l10n":"“Protection of our IP is our #1 priority, not cost. That being said, Elastic is almost 35% cheaper than our previous solution and gives us far better insights and protection.”","_metadata":{"uid":"cse58d09a667e961ec"},"quote_author_l10n":"Analyzing the Economic Benefits of Elastic Security","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"Dive deeper","_metadata":{"uid":"cs7dc52a6dddf4d2f1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnterprise Strategy Group’s study has shown that deploying Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven security analytics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e helps organizations gain greater visibility across the environments while reducing costs and driving efficiencies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInterested in learning how your organization could realize business impact with Elastic Security? \u003c/span\u003e\u003ca href=\"http://elastic.co/resources/security/report/analyze-economic-benefits-elastic-security\"\u003e\u003cspan style='font-size: 12pt;'\u003eRead the report\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Want some deeper insights? Our upcoming webinar, Analyzing the economic impact of AI-driven security analytics, features the ESG analyst who wrote the report and one of our customers, Sierra Nevada Corporation. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/analyzing-the-economic-impact-of-ai-driven-security-analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003eSave your spot for this event\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e on April 17, 2025, and see just how big of an impact Elastic Security has had!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8d16ddda2e6a6ca9"}}}],"publish_date":"2025-03-24","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Quantifying economic impact with Enterprise Strategy Group","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt7a4eb1026ba18f63","ACL":{},"created_at":"2023-11-06T20:07:03.185Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"advanced-persistent-threat","label_l10n":"Advanced Persistent Threat (APT)","tags":[],"title":"Advanced Persistent Threat (APT)","updated_at":"2023-11-06T20:07:03.185Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:50.393Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt405e99573a94e858","ACL":{},"created_at":"2023-11-06T20:37:33.009Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-loss-prevention","label_l10n":"Data Loss Prevention (DLP)","tags":[],"title":"Data Loss Prevention (DLP)","updated_at":"2023-11-06T20:37:33.009Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:40.892Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt048e5e01aa446692","ACL":{},"created_at":"2023-11-06T20:38:02.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"devsecops","label_l10n":"DevSecOps","tags":[],"title":"DevSecOps","updated_at":"2023-11-06T20:38:02.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.187Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte41b0699a34eac99","ACL":{},"created_at":"2023-11-06T20:38:53.624Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"edr","label_l10n":"EDR","tags":[],"title":"EDR","updated_at":"2023-11-06T20:38:53.624Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:26.559Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt484a944a3d130219","ACL":{},"created_at":"2023-11-06T20:39:33.494Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fraud-detection","label_l10n":"Fraud detection","tags":[],"title":"Fraud detection","updated_at":"2023-11-06T20:39:33.494Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.155Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd11e6308b4dbe770","ACL":{},"created_at":"2023-11-06T21:32:01.057Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-research","label_l10n":"Security research","tags":[],"title":"Security research","updated_at":"2023-11-06T21:32:01.057Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.638Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte799688802bb242c","ACL":{},"created_at":"2023-11-06T21:32:44.031Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"soar","label_l10n":"SOAR","tags":[],"title":"SOAR","updated_at":"2023-11-06T21:32:44.031Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.584Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt94fd9c3bf14d1f7c","ACL":{},"created_at":"2023-11-06T21:35:54.155Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vulnerability-management","label_l10n":"Vulnerability Management (VM)","tags":[],"title":"Vulnerability Management (VM)","updated_at":"2023-11-06T21:35:54.155Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.168Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt492e90a3579ab172","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-24T03:50:00.803Z","created_by":"blte369ea3bcd6ac892","file_size":"151078","filename":"Blog-header-ESG_Security_Value_Study_Launch-17967.jpg","parent_uid":null,"tags":[],"title":"Blog-header-ESG Security Value Study Launch-17967.jpg","updated_at":"2025-03-24T03:50:00.803Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-24T15:00:01.116Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt492e90a3579ab172/67e0d668314d672a451b7a7a/Blog-header-ESG_Security_Value_Study_Launch-17967.jpg"},"title":"What is the value of AI-driven security analytics?","title_l10n":"What is the value of AI-driven security analytics?","updated_at":"2025-03-24T05:45:34.438Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/value-ai-driven-security-analytics","publish_details":{"time":"2025-03-24T15:00:01.030Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1de8c55f6f6997fd","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic and Tines unveil Tines Workflow Automation, a new product offering available through Elastic that brings orchestration and automation to security and observability teams.","author":["blt91eeaf08ab3d1d6a","bltc2f4d6e97d81ab56","bltcfe4b34171051a0b"],"category":["bltb79594af7c5b4199"],"created_at":"2025-03-18T18:05:31.377Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs705c79d4a74dc858"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic and Tines are unveiling an integrated product offering to transform the crucial work of security and observability teams. We’re excited to introduce Tines Workflow Automation, available directly through Elastic. This seamless package extends Elastic with the orchestration and automation capabilities of Tines, equipping SOC teams with security orchestration, automation, and response (SOAR) and observability teams with incident response automation. Together, Elastic and Tines strengthen defenses and ensure operational resilience, maximizing the return on your existing technology investments.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"From complexity to clarity","_metadata":{"uid":"csbd58d0b135d443a8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eToday’s digital world inundates organizations with a deluge of data, alerts, and issues requiring intervention. Security analysts must tackle threats fast enough to prevent harm, while SREs and DevOps engineers grapple with identifying and resolving performance problems before users are affected. Many of these teams are understaffed and overburdened, and the nature of their work requires coordinating efforts across departments and systems.\u003cbr /\u003e\u003cbr /\u003eThe common thread is that practitioners must be able to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eanalyze\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eact\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e across the IT environment, without data silos or workflow breakdowns blocking the way. They require real-time insights to cut through the noise and automation to keep pace. And they need these capabilities to function seamlessly.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Turn data into insights — and insights into action","_metadata":{"uid":"cs93f975c2fa11fbae"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic and Tines transform security and observability programs by augmenting Elastic’s solutions with Tines’ intuitive, AI-powered workflow orchestration and automation solution.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s Search AI Platform provides groundbreaking log management, advanced analytics, and AI features. You can ingest and normalize information of almost any kind (including \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/automatic-import-ai-data-integration-builder\"\u003e\u003cspan style='font-size: 12pt;'\u003ecustom data in just minutes\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e), swiftly \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/elasticsearch-searchable-snapshots\"\u003e\u003cspan style='font-size: 12pt;'\u003esearch years of archives\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and tackle use cases with machine learning (ML), alerting, and AI.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTines enables teams of all sizes and skill sets to \u003c/span\u003e\u003ca href=\"https://www.tines.com/product/?utm_source=Elastic\u0026utm_medium=partner\u0026utm_campaign=launch\"\u003e\u003cspan style='font-size: 12pt;'\u003ebuild, run, and monitor their most important workflows\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. The \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eAI and workflow orchestration \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eplatform gives teams the tools to enrich data, add contextualization, and \u003c/span\u003e\u003ca href=\"https://www.tines.com/guides/essential-guide-to-workflow-automation/security/?utm_source=Elastic\u0026utm_medium=partner\u0026utm_campaign=launch\"\u003e\u003cspan style='font-size: 12pt;'\u003emeet users where they are\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (natural language, no code, low code, or bring your own code). As a result, they get greater value and experience fewer silos from their disparate data and alerting systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach platform plays a vital role. Elastic delivers real-time insights at unprecedented scale, arming practitioners to ask the right questions, receive relevant answers, and make informed decisions. Tines then propels resulting workflows —\u0026nbsp;from the simplest routine tasks to the most sophisticated multi-stage, multi-system responses.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBoth technologies can be deployed in the cloud or on-premises, and both smoothly scale from the needs of a start-up to the demands of a global enterprise.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Integrate, automate, celebrate","_metadata":{"uid":"cs6909b0e12618e12b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePrebuilt bidirectional connections make it easy to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/tines-action-type.html\"\u003e\u003cspan style='font-size: 12pt;'\u003elink Elastic alerts with Tines\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/tines.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eanalyze data from Tines in Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and connect many other systems in your environment.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow for the fun part. You can quickly find and implement workflows in the \u003c/span\u003e\u003ca href=\"https://www.tines.com/library/tools/elastic/?utm_source=Elastic\u0026utm_medium=partner\u0026utm_campaign=launch\"\u003e\u003cspan style='font-size: 12pt;'\u003eTines library\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, including sequences contributed by Elastic’s SOC team and other community members. Popular automations include enriching alerts, quarantining compromised hosts, and revoking privileged access.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWant to start with a blank slate? Tines offers an intuitive workflow builder that allows you to incorporate your organization’s preexisting processes.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8694ae47ca225149"}}},{"image":{"image":{"uid":"blte8430abcffb35476","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-18T18:43:30.681Z","created_by":"blte369ea3bcd6ac892","file_size":"318764","filename":"tines-workflow-builder.png","parent_uid":null,"tags":[],"title":"tines-workflow-builder.png","updated_at":"2025-03-18T18:43:30.681Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-19T12:30:00.498Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte8430abcffb35476/67d9bed264766010febf2cdc/tines-workflow-builder.png"},"_metadata":{"uid":"cs5908a91a13f5ae15"},"caption_l10n":"","alt_text_l10n":"Tines workflow builder","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse8608930bcfc9e17"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCases\u003c/span\u003e\u003cspan style='color:rgb(29, 28, 29);font-size: 12pt;'\u003e propel investigation and remediation by centralizing critical information and enabling collaboration across your team.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0a6dcecda29f1d31"}}},{"image":{"image":{"uid":"blt67721c105593f69c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-18T18:44:44.347Z","created_by":"blte369ea3bcd6ac892","file_size":"142203","filename":"tines-case.png","parent_uid":null,"tags":[],"title":"tines-case.png","updated_at":"2025-03-18T18:44:44.347Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-19T12:30:00.530Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt67721c105593f69c/67d9bf1ccca70a2e833a0a41/tines-case.png"},"_metadata":{"uid":"csc8f8fec939443b3d"},"caption_l10n":"","alt_text_l10n":"Tine case","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs82aa1f90d6e09b12"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003eDashboards visualize data from Cases and Records, streamlining monitoring and reporting on workflow performance.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs017a7f12ffcfa57e"}}},{"image":{"image":{"uid":"bltfd9ce5b40c28182c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-18T18:45:54.344Z","created_by":"blte369ea3bcd6ac892","file_size":"110713","filename":"tines-dashboard.png","parent_uid":null,"tags":[],"title":"tines-dashboard.png","updated_at":"2025-03-18T18:45:54.344Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-19T12:30:00.513Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfd9ce5b40c28182c/67d9bf62fa2ac21dcc3602f5/tines-dashboard.png"},"_metadata":{"uid":"cs8261aa3045c0f075"},"caption_l10n":"","alt_text_l10n":"Tines dashboard","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"The power of Elastic with Tines Workflow Automation","_metadata":{"uid":"csfc1d7cc503ccc9a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic delivers a robust set of tools designed to propel analysis — and with Tines Workflow Automation, its capabilities reach a whole new level.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eResolve issues faster:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Connect disjointed systems, coordinate across teams, and harness AI to expedite investigation and response.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRaise operational efficiency: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003eBuild workflows and leverage AI features to empower your team to work repetitive tasks faster and more consistently.\u003c/span\u003e\u003cspan style=\"color: rgb(68, 71, 70);font-size: 12pt;\"\u003e\u003cstrong\u003e\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eReduce costs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Mitigate security incidents, avoid costly service disruptions, and handle growing demands with your existing resources.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eExecute consistently:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Standardize operating procedures, foster collaboration, and embed transparency to drive continuous improvement.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csf9bfc20af9932157"}}},{"quotes":{"quote_l10n":"“We can use Elastic and Tines to build workflows that actually fit our needs and help us accomplish what we need to accomplish. And I can’t say the same for a lot of the other software vendor combinations.”","_metadata":{"uid":"cs6f838382fc72ae4f"},"quote_author_l10n":"Braxton Williams, Engineering Manager, Texas A\u0026M System Cyber Operations","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"Elevate your SOC with SOAR","_metadata":{"uid":"cscde0ae0a4f96fea0"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/false-positives-automated-siem-investigations-elastic-tines\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAugment Elastic Security with Tines Workflow Automation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to leverage AI-driven security analytics with SOAR:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eOrchestration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Effortlessly coordinate complex workflows across different systems and business units.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAutomation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Free up valuable analyst time to focus on high-priority threats and strategic initiatives by automating actions across your IT ecosystem.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eResponse:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Minimize the frequency and impact of cyber incidents by tracking and managing fast and effective measures.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Reach your observability goals faster","_metadata":{"uid":"cs6fe6490139ce6154"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.tines.com/blog/elastic-observability-and-tines/?utm_source=Elastic\u0026utm_medium=partner\u0026utm_campaign=launch\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePair Elastic Observability with Tines Workflow Automation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to prevent outages, accelerate problem resolution, and enhance operational efficiency through intelligent orchestration:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eMonitoring:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Seamlessly aggregate and analyze telemetry data across your entire technology stack.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAnalysis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Enable teams to focus on service improvements by automating routine monitoring and investigation tasks.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eResolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Reduce downtime and service degradation through automated troubleshooting and remediation workflows.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Achieve measurable results","_metadata":{"uid":"csb67c910bd9676363"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic and Tines are long-time partners, currently serving over 60 joint customers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“Tines Workflow Automation is a force multiplier,” notes Santosh Krishnan, GM of security and observability at Elastic. “We’re glad to make this strategic offering available publicly in unison with Elastic Security and Elastic Observability.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“The time it takes to turn insights into action often determines the effectiveness of security and observability teams,” said Eoin Hinchy, founder and CEO at Tines. “By connecting real-time analysis and AI-powered workflows, the combined offering from Elastic and Tines minimizes that time. This results in faster issue resolution, reduced costs, and, of course, less stress and workload on practitioners.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic counts on the Tines platform within its SOC. Aaron Jewitt, principal detection engineer at Elastic, estimates that it handles the workload of 95 full-time employees, explaining that “we automate many tasks that would be impossible to complete otherwise.”\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What will you automate first?","_metadata":{"uid":"cs718f0a8e1502cd20"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic and Tines are teaming up to help teams work smarter, respond faster, and achieve more. Explore our unified offering and contact Elastic to unlock the full potential of your security and observability programs:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExperience a free trial of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and connect it with \u003c/span\u003e\u003ca href=\"https://www.tines.com/blog/announcing-the-tines-community-edition/?utm_source=Elastic\u0026utm_medium=partner\u0026utm_campaign=launch\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTines community edition\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSee Tines and Elastic in action in a \u003c/span\u003e\u003ca href=\"https://www.databreachtoday.com/webinars/texas-am-university-system-cyber-operations-drives-efficient-scaling-w-6164?rf=elasticxtines\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecase study webinar\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with Texas A\u0026amp;M University System Cyber Operations.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/contact\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eContact us\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to learn more about Elastic + Tines.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"","_metadata":{"uid":"cs1f794af14248a662"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdbca444744d4ee35"}}}],"publish_date":"2025-03-19","sanity_migration_complete":false,"seo":{"seo_title_l10n":" Elastic and Tines partner to orchestrate and automate team workflows","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Automate your security and observability workflows with Tines Workflow Automation, now available directly from Elastic","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte799688802bb242c","ACL":{},"created_at":"2023-11-06T21:32:44.031Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"soar","label_l10n":"SOAR","tags":[],"title":"SOAR","updated_at":"2023-11-06T21:32:44.031Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.584Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt4c21aa7fe852d60e","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-18T18:05:30.208Z","created_by":"blte369ea3bcd6ac892","file_size":"44660","filename":"Elastic_Tines-announcement_blog.png","parent_uid":null,"tags":[],"title":"Elastic_Tines-announcement_blog.png","updated_at":"2025-03-18T18:05:30.208Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-19T12:30:00.482Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4c21aa7fe852d60e/67d9b5ea1c40c5bb82b21d09/Elastic_Tines-announcement_blog.png"},"title":"Elastic and Tines team up to offer SOAR and AIOps","title_l10n":" Elastic and Tines team up to offer SOAR and AIOps","updated_at":"2025-03-19T01:17:47.131Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-tines-automate-security-observability","publish_details":{"time":"2025-03-19T15:43:22.054Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt86615aaf0ea465be","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"Discover how to detect OS Credential Dumping (T1003) in this comprehensive guide. Learn how to unmask adversaries, protect your credentials, and fortify your defenses with actionable insights and ES|QL queries tailored for detection.","author":["bltd7e3256924767ce0"],"category":["blte5cc8450a098ce5e"],"created_at":"2025-03-17T17:30:51.357Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs23a5c41df52d3427"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the shadowy depths of your network, whispers grow louder — something isn’t right. Adversaries are on the prowl, targeting the very keys to your kingdom: your credentials. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eT1003 - OS Credential Dumping\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is their weapon of choice to steal password hashes and sensitive authentication materials. They quietly harvest secrets to impersonate users, escalate privileges, and move laterally through your environment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2ba24d81556374ad"}}},{"image":{"image":{"uid":"bltf853a5d0fbb413bf","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-17T18:01:59.278Z","created_by":"blte369ea3bcd6ac892","file_size":"1831871","filename":"Hunting-with-Elastic-Security.png","parent_uid":null,"tags":[],"title":"Hunting-with-Elastic-Security.png","updated_at":"2025-03-17T18:01:59.278Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-19T15:00:00.955Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf853a5d0fbb413bf/67d8639702de2038be5a6585/Hunting-with-Elastic-Security.png"},"_metadata":{"uid":"csf59206df4302d610"},"caption_l10n":"","alt_text_l10n":"Hunting-with-Elastic-Security","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs839e6e7528921412"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eProtecting credentials is critical to maintaining the confidentiality, integrity, and availability of your systems. The challenge is to uncover signs of OS Credential Dumping and assess whether an adversary has attempted to harvest sensitive authentication data — or confirm that your defenses are holding strong.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis hunt matters because once credentials are stolen, the door to your infrastructure is left wide open. It’s time to arm yourself, dig into the logs, and expose their movements. The hunt for OS Credential Dumping begins now. Can you track the adversaries lurking within your systems and unmask their tricks? Let’s sharpen our tools and find out!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Understanding the technique","_metadata":{"uid":"cs04c88fba514353f9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/\"\u003e\u003cspan style='font-size: 12pt;'\u003eT1003 - OS Credential Dumping\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is a technique within the \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/\"\u003e\u003cspan style='font-size: 12pt;'\u003eMITRE ATT\u0026amp;CK\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e® framework that adversaries use to obtain credentials stored in operating systems. By extracting password hashes, plaintext passwords, or authentication tokens, attackers gain the ability to impersonate legitimate users, escalate privileges, and move laterally across your environment. The technique is categorized under the \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/tactics/TA0006/\"\u003e\u003cspan style='font-size: 12pt;'\u003eCredential Access tactic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, as it directly targets sensitive credentials to advance an attack.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eT1003 includes several dangerous \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003esub-techniques\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e that highlight the diverse ways adversaries can dump credentials:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/001/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLSASS Memory (T1003.001)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Targeting the LSASS process to retrieve credentials stored in memory (Tools like \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eMimikatz\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e are often used here.)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/002/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSecurity Account Manager (SAM) (T1003.002)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Extracting local account credentials from the SAM registry hive\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/003/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNTDS (T1003.003)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Dumping credentials from the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eNTDS.dit\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file in Active Directory environments, compromising domain accounts\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/004/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLSA Secrets (T1003.004)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Extracting cached credentials and service account information stored in registry keys\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/005/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCached Domain Credentials (T1003.005)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Accessing credentials cached locally on Windows systems to enable offline authentication\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/006/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDCSync (T1003.006)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Simulating domain controller replication to retrieve credentials from Active Directory without running code on the DC\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/007/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eProc Filesystem (T1003.007)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Dumping credentials from Linux systems using the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/proc\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e filesystem\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1003/008/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e/etc/passwd and /etc/shadow (T1003.008)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Retrieving user account details and hashed passwords from Unix-based systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf left undetected, \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOS Credential Dumping\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e can lead to catastrophic consequences. Attackers who gain access to credentials can bypass authentication mechanisms, impersonate privileged users, and maintain Persistence throughout your network. This compromises confidentiality as sensitive accounts and systems are exposed, disrupts integrity by allowing unauthorized access, and jeopardizes availability as attackers escalate privileges to disable critical systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the broader MITRE ATT\u0026amp;CK framework, T1003 is a gateway for attackers to pivot from Credential Access to other phases of an attack, such as Lateral Movement, Persistence, and even Impact. Failing to detect and mitigate this technique can allow adversaries to establish control over your environment, leading to data theft, ransomware deployment, or complete system compromise.\u003cbr /\u003e\u003cbr /\u003eUnderstanding the significance of \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eT1003\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is paramount — hunting for this activity ensures you can protect the keys to your kingdom before attackers use them against you.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data sources to optimize the hunt","_metadata":{"uid":"cs988a996df239b865"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDetecting \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eOS Credential Dumping (T1003)\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e requires leveraging a combination of logs, monitoring tools, and data sources that provide visibility into process execution, file access, registry manipulation, and memory interactions. Below is a breakdown of essential data sources and what they detect, a as well as recommended Elastic integrations to optimize the hunt:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e1. Process monitoring\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Processes interacting with LSASS memory \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e(lsass.exe)\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, tools like Mimikatz, and suspicious process creation events\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Critical for detecting tools or scripts attempting to dump credentials in memory\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/windows.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWindows Integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party to monitor process creation events, command-line arguments, and anomalous behavior.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e2. Windows event logs (security and system)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Unauthorized access to registry hives (SAM, SECURITY), system files \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e(ntds.dit)\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and cached credentials; also flags Privilege Escalation attempts\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Provides insights into adversary access to sensitive files and resources\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUse \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/windows.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eWindows Integration\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003efor to capture relevant Security Event IDs such as: \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEvent ID 4663\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e: Object Access (File or Registry), \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEvent ID 4688\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e: Process Creation, \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEvent ID 4656\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e: Handle Requested for Object Access.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e3. File access logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Attempts to access sensitive files like:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eC:\\\\Windows\\\\System32\\\\config\\\\SAM\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e stores local user account password hashes for authentication\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eC:\\\\Windows\\\\System32\\\\config\\\\SECURITY\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e contains system security policies, including local security authority (LSA) secrets\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eNTDS.dit\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for Active Directory credential dumping\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Helps detect unauthorized attempts to copy or dump system files\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/fim.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFile Integrity Monitoring\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eor another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003efor file integrity monitoring and file access tracking.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e4. Registry monitoring\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Adversaries accessing or exporting registry hives, such as SAM, SECURITY, or SYSTEM, to retrieve credential data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Monitors manipulation of critical registry keys and hive exports using commands like \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ereg save\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eor another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party to detect suspicious changes or access.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e5. Memory forensics\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Tools accessing LSASS memory (e.g., Mimikatz) to extract credentials\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIdentifies in-memory attacks that bypass file-based detection mechanisms\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or tools like \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eVolatility\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to analyze memory dumps for credential access.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e6. Command execution logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Suspicious commands used to dump credentials, such as:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003ereg save\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e exports registry hives, including SAM and SECURITY, which store credential and security policy data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003evssadmin\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e creates a Volume Shadow Copy, often used to access locked system files like NTDS.dit\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003elsass.exe \u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003edumps using tools like \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eprocdump.exe\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Critical for identifying commands or scripts used to trigger credential dumping activities\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party to monitor command-line executions and log PowerShell events.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e7. Audit logs for Active Directory\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Access to the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eNTDS.dit\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e file or abnormal replication activity (DCSync attacks)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Protects domain credentials by monitoring access to key AD data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party for Active Directory logs.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e8. Linux audit logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Attempts to access \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/proc/mem\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/etc/passwd\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/etc/shadow\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e files on Linux systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelevance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Monitors credential dumping attempts on Unix-based systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/endpoint-security.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/fim.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFile Integrity Monitoring\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e, \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eor another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party with File Integrity Monitoring to track access to these sensitive files.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Threat hunting with ES|QL queries","_metadata":{"uid":"cs3a9801463ebb0f5b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eES|QL\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e queries to track down Credential Dumping activities, as we can query and analyze large volumes of security data within Elasticsearch. ES|QL enables analysts to write intuitively, correlate events, and uncover anomalies associated with techniques like OS Credential Dumping. By leveraging ES|QL’s powerful filtering, aggregation, and transformation capabilities, SOC teams can quickly pinpoint suspicious process activities, anomalous file access patterns, or unauthorized registry changes. This approach simplifies complex hunting tasks, making it easier to detect, investigate, and respond to potential threats in real time while leveraging the flexibility and speed of the Elastic Stack.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 1: Detect processes accessing LSASS memory (T1003.001)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc3019d1a9d9b6ee2"}}},{"code":{"code":"FROM logs-*\n| WHERE TO_LOWER(process.name) == \"lsass.exe\"\n AND TO_LOWER(process.parent.name) IN (\"procdump.exe\", \"mimikatz.exe\", \"powershell.exe\")\n| KEEP process.name, process.parent.name, process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs3c913b40568f7413"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd7dd8f66c9d4f1a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query identifies processes interacting with \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003elsass.exe\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, a common target for credential dumping tools like \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eMimikatz\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e or \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eProcdump\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. Accessing LSASS memory is a key indicator of T1003.001.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 2: Monitor registry hive exports (T1003.002)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd2e1da70aa38c107"}}},{"code":{"code":"FROM logs-*\n| WHERE process.command_line LIKE \"*reg save*\" \n AND (process.command_line LIKE \"*\\\\\\\\sam*\" \n OR process.command_line LIKE \"*\\\\\\\\security*\" \n OR process.command_line LIKE \"*\\\\\\\\system*\")\n| KEEP process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs8e4f3c76224f9c5c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1710db267150655c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query flags the use of the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ereg save\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e command, which adversaries use to export the SAM, SECURITY, and SYSTEM registry hives. These files contain credential information.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 3: Detect NTDS.dit access for Active Directory dumping (T1003.003)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs671600cfc112acdb"}}},{"code":{"code":"FROM logs-*\n| WHERE TO_LOWER(file.path) LIKE \"*\\\\\\\\ntds.dit\"\n AND TO_LOWER(event.action) == \"access\"\n| KEEP file.path, user.name, host.name, @timestamp\n\n","_metadata":{"uid":"cs2c52f6585acddb93"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6abddd38aef6d040"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Adversaries dump the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003entds.dit\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file to retrieve domain credentials. This query detects unauthorized access attempts to the NTDS file in Active Directory environments.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 4: Detect suspicious DCSync behavior (T1003.006)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs05e8e332d0dac093"}}},{"code":{"code":"FROM logs-*\n| WHERE event.action == \"replication\" \n AND user.name != \"domain_admin\"\n| KEEP event.action, user.name, host.name, @timestamp\n","_metadata":{"uid":"csb710f0a2cf6f01e4"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs02bca76a89aea0a6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e The DCSync attack allows an adversary to impersonate a domain controller and retrieve credentials. This query looks for abnormal replication requests from non-admin accounts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 5: Monitor access to /etc/passwd and /etc/shadow (T1003.008)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7c1694f0ddbfeb06"}}},{"code":{"code":"FROM logs-*\n| WHERE file.path IN (\"/etc/passwd\", \"/etc/shadow\") AND event.action == \"read\"\n| KEEP file.path, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs3e8687456177a5c5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb1cc45f47d3b7a15"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e On Unix-based systems, attackers dump \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/passwd\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/shadow\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e files to obtain user account information and password hashes. This query detects unauthorized read access.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 6: Identify cached domain credential dumps (T1003.005)\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs42b719ed5f15ef3b"}}},{"code":{"code":"FROM logs-*\n| WHERE process.command_line LIKE \"*reg.exe*\" \n OR process.command_line LIKE \"*HKLM\\\\\\\\SECURITY*\"\n| KEEP process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs860b1ff7994a1f92"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6686287b181677c4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Cached domain credentials are often stored in the SECURITY hive. This query detects attempts to dump cached credentials using registry commands.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 7: Detect Mimikatz execution in command-line\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3939ea8bcfc3045e"}}},{"code":{"code":"\nFROM logs-*\n| WHERE process.command_line LIKE \"*mimikatz*\"\n| KEEP process.name, process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs11da0833bf591a4d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs19daeda9982b937b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Mimikatz is a popular tool for credential dumping. This query flags direct invocations of Mimikatz or similar tools in the command line.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 8: Identify suspicious use of Procdump for LSASS dumping\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9c6fcd90fdc9605a"}}},{"code":{"code":"FROM logs-*\n| WHERE process.command_line LIKE \"*procdump*\" \n AND process.command_line LIKE \"*lsass*\"\n| KEEP process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"csaa4466e6a2529fad"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs58de093bba0a864e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Procdump is sometimes used to dump LSASS memory. This query detects any use of Procdump targeting LSASS.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 9: Detect unusual file access on SAM registry hive\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2f6e263d0ae1a0f0"}}},{"code":{"code":"FROM logs-*\n| WHERE file.path LIKE \"C:\\\\\\\\Windows\\\\\\\\System32\\\\\\\\config\\\\\\\\SAM\"\n AND event.action IN (\"read\", \"access\", \"open\")\n| KEEP file.path, user.name, process.name, host.name, @timestamp\n","_metadata":{"uid":"csc350d6693923f27f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0ddd0ca3d6430d1d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query detects command-line activity indicative of Credential Dumping or data extraction.The SAM registry hive contains hashed credentials. This query detects any unauthorized attempts to read or access the file.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 10: Monitor volume shadow copy usage\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1d9444f707710c0d"}}},{"code":{"code":"FROM logs-*\n| WHERE TO_LOWER(process.command_line) LIKE \"*vssadmin*\" \n AND TO_LOWER(process.command_line) LIKE \"*create shadow*\"\n| KEEP process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"csedcf193eeb4b186b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbe91d1febc942028"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Adversaries create shadow copies to bypass file locks and access sensitive files like \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003entds.dit\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. This query monitors the creation of shadow copies.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 11: Detect tools accessing /proc/mem for credential dumps\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2889c703e8040cd6"}}},{"code":{"code":"FROM logs-*\n| WHERE TO_LOWER(file.path) LIKE \"/proc/*\" \n AND TO_LOWER(process.name) IN (\"gcore\", \"dd\", \"cat\")\n| KEEP file.path, process.name, user.name, host.name, @timestamp\n","_metadata":{"uid":"csdd927dcec0278056"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbcb6cad9a5918b96"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e On Linux, adversaries can dump process memory via the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/proc\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e filesystem. This query identifies suspicious tools accessing \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/proc\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e paths.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 12: Detect large NTDS.dit file transfers\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8ca7064d96494d08"}}},{"code":{"code":"FROM logs-*\n| WHERE network.protocol == \"smb\"\n AND file.name LIKE \"ntds.dit*\"\n| KEEP file.name, source.ip, destination.ip, @timestamp\n","_metadata":{"uid":"csa59e5c45f2d65beb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf17841ab2b72e424"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query detects large SMB file transfers involving \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003entds.dit\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e , indicating possible exfiltration of Active Directory credentials.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 13: Monitor PowerShell scripts targeting LSASS\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4a04de4e734bba31"}}},{"code":{"code":"FROM logs-*\n| WHERE process.command_line LIKE \"*powershell*\" \n AND process.command_line LIKE \"*lsass*\"\n| KEEP process.command_line, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs9ef3ba95bedbdf27"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd84f3ff935ea68d7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Adversaries often use PowerShell scripts to dump LSASS memory. This query detects PowerShell commands targeting LSASS.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 14: Detect attempts to copy sensitive registry hives\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa201487b20345343"}}},{"code":{"code":"FROM logs-*\n| WHERE (file.path LIKE \"*\\\\\\\\SYSTEM\" \n OR file.path LIKE \"*\\\\\\\\SECURITY\" \n OR file.path LIKE \"*\\\\\\\\SAM\")\n AND event.action == \"copy\"\n| KEEP file.path, user.name, host.name, @timestamp\n","_metadata":{"uid":"cs059ac56f6419b49c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9b59c12f50f01685"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Attackers copy registry hives to extract credentials offline. This query detects such attempts.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery 15: Identify new tools writing to sensitive credential files\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2efb532dd5e87c85"}}},{"code":{"code":"FROM logs-*\n| WHERE (file.path == \"/etc/shadow\" \n OR file.path LIKE \"*\\\\\\\\SAM\" \n OR file.path LIKE \"*\\\\\\\\SECURITY\")\n AND event.action == \"write\"\n| KEEP file.path, user.name, process.name, host.name, @timestamp\n","_metadata":{"uid":"cs36d23e84c55a99c9"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb598b77c6f0ba994"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query monitors write operations to critical files like\u0026nbsp;\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/etc/shadow\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e or SAM, which may indicate tampering or malicious credential extraction attempts.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Hunt efficiently","_metadata":{"uid":"cs5a82d909b3e54a5e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe whispers in your network have grown silent, but what did you uncover? Were you able to catch the adversary red-handed, dumping credentials from LSASS memory or exfiltrating the NTDS.dit file under the cover of darkness? Perhaps you followed the trails of registry exports, shadow copies, or suspicious processes trying to claim your keys to the kingdom. Whether you proved the adversary's activity or validated your defenses, you have strengthened your security posture and sharpened your detection capabilities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRemember, OS Credential Dumping (T1003) is relied upon for escalating privileges, impersonating users, and traversing your environment like a ghost in the machine. The hunt for stolen credentials is a critical effort that can expose silent intruders before they wreak havoc. By monitoring LSASS access, registry hives, and file activity, you have not only thwarted today’s threats but also prepared for tomorrow’s battles.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, did you uncover the adversary, or can you confidently prove they weren’t there? Either way, your network is now safer, your defenses stronger, and your tools sharper. But stay vigilant — credential dumping remains a relentless adversarial technique, and the hunt is never truly over.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo elevate your threat hunting capabilities, check out the\u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs/elevate-your-threat-hunting\"\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic Security Labs Threat Hunting package\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Stay ahead of adversaries with advanced detection strategies and keep refining your skills.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKeep hunting, and always stay one step ahead.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cse6d5f443093ef5eb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse06bdb712046c422"}}}],"publish_date":"2025-03-19","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt7a4eb1026ba18f63","ACL":{},"created_at":"2023-11-06T20:07:03.185Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"advanced-persistent-threat","label_l10n":"Advanced Persistent Threat (APT)","tags":[],"title":"Advanced Persistent Threat (APT)","updated_at":"2023-11-06T20:07:03.185Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:50.393Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt8d69fdea14ecdbfc","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-17T17:29:37.511Z","created_by":"blte369ea3bcd6ac892","file_size":"119246","filename":"Blog_Header_Image-_ELK_Hunting_Series-2.jpg","parent_uid":null,"tags":[],"title":"Blog Header Image- ELK Hunting Series-2.jpg","updated_at":"2025-03-17T17:29:37.511Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-19T15:00:00.972Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8d69fdea14ecdbfc/67d85c010c5905ca38fcfca5/Blog_Header_Image-_ELK_Hunting_Series-2.jpg"},"title":"Hunting with Elastic Security: Detecting credential dumping with ES|QL","title_l10n":"Hunting with Elastic Security: Detecting credential dumping with ES|QL","updated_at":"2025-03-18T20:31:02.864Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-security-detecting-credential-dumping","publish_details":{"time":"2025-03-19T15:44:12.052Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb804d682fce266d9","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"Uncover hidden exfiltration attempts in your network with ELK Stack insights. Learn how to detect T1048 - Exfiltration Over Alternative Protocol, safeguard sensitive data, and outsmart adversaries leveraging covert channels.","author":["bltd7e3256924767ce0"],"category":["bltb79594af7c5b4199"],"created_at":"2025-03-12T01:49:04.925Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5c23e1f688d7da5c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNot all network traffic is what it seems. Some flows conceal secrets, quietly exfiltrating sensitive data beyond your defenses. MITRE ATT\u0026amp;CK® T1048 - Exfiltration Over Alternative Protocol is a stealth technique adversaries use to smuggle data out of your environment by bypassing traditional security controls. Whether tunneling through ICMP, abusing DNS, or leveraging obscure application protocols, attackers exploit these alternative pathways to avoid detection and sneak critical information past your defenses.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs050d013626200aa5"}}},{"image":{"image":{"uid":"bltce2619a4ad3a01bf","_version":1,"title":"Hunting-with-Elastic-Security.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-12T01:40:24.759Z","updated_at":"2025-03-12T01:40:24.759Z","content_type":"image/jpeg","file_size":"135999","filename":"Hunting-with-Elastic-Security.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-12T20:41:06.507Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltce2619a4ad3a01bf/67d0e6083d54877c320f034a/Hunting-with-Elastic-Security.jpg"},"_metadata":{"uid":"cs3379f0ccadd997e3"},"caption_l10n":"","alt_text_l10n":"Hunting with Elastic Security","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs74f1a2c4bb45e809"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe risks are severe — intellectual property, credentials, or confidential data could be extracted without a trace. Could these seemingly ordinary data streams hide something more sinister? An adversary may already be using T1048 to outmaneuver your security. DNS queries, ICMP echoes, or unexpected protocol usage might be concealing exfiltrated data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis blog will arm you with the knowledge and tools to detect these covert exfiltration methods. By analyzing logs, dissecting traffic patterns, and leveraging ES|QL, you’ll uncover hidden threats and expose adversarial tactics. Can you stop data from slipping through the cracks, or will exfiltration routes remain undetected? It’s time to find out — the hunt begins now!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Understanding the technique","_metadata":{"uid":"cs7cb3372072e8b03b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1048/\"\u003e\u003cspan style='font-size: 12pt;'\u003eMITRE ATT\u0026amp;CK technique T1048\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, known as \"Exfiltration Over Alternative Protocol,\" involves adversaries transferring stolen data using protocols different from their primary command and control (C2) channels. This method enables attackers to bypass security measures that monitor standard C2 traffic, thereby reducing the likelihood of detection. Commonly exploited protocols include FTP, SMTP, HTTP/S, DNS, and SMB. Adversaries may also employ encryption or obfuscation to further conceal the exfiltration process. (\u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1048/\"\u003e\u003cspan style='font-size: 12pt;'\u003eattack.mitre.org\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e)\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Sub-techniques of T1048","_metadata":{"uid":"csc69dc47e0256fc92"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003e1.\u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1048/001/\"\u003e\u003cspan style='font-size: 11pt;'\u003e \u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eT1048.001: Exfiltration Over Symmetric Encrypted Non-C2 Protocol\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDescription:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Adversaries exfiltrate data over a symmetrically encrypted network protocol distinct from the existing C2 channel. Symmetric encryption uses the same key for both encryption and decryption, necessitating a shared secret between communicating parties.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExample:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Utilizing protocols like HTTPS, where data is encrypted symmetrically after an initial key exchange, to transfer stolen information to a different server\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003e2.\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1048/002/\"\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eT1048.002: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDescription:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e In this method, adversaries exfiltrate data using an asymmetrically encrypted protocol separate from the primary C2 channel. Asymmetric encryption employs a pair of keys — public and private — for encryption and decryption, enhancing security by eliminating the need for a shared secret.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExample:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Leveraging protocols that use asymmetric encryption for secure data transfer to an alternate destination\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003e3.\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 11pt;'\u003e \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1048/003/\"\u003e\u003cspan style='font-size: 11pt;'\u003e\u003cstrong\u003eT1048.003: Exfiltration Over Unencrypted Non-C2 Protocol\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDescription:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Adversaries exfiltrate data over an unencrypted network protocol different from the main C2 channel. This approach may involve obfuscating data within protocols that are typically unencrypted, such as HTTP, FTP, or \u003c/span\u003e\u003ca href=\"https://www.akamai.com/glossary/what-is-dns-tunneling\"\u003e\u003cspan style='font-size: 12pt;'\u003eDNS\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExample:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Embedding stolen data within HTTP requests to a web server controlled by the attacker without employing encryption, relying instead on data obfuscation techniques\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy leveraging alternative protocols, adversaries exploit gaps in security tools and monitoring strategies. For example, ICMP packets typically used for diagnostic purposes can be manipulated to carry data payloads, and DNS requests can be crafted to exfiltrate data under the guise of normal traffic. These tactics create significant challenges for defenders, who must analyze benign-looking traffic for hidden threats.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnderstanding the significance of T1048 and its sub-techniques is critical for building robust defenses. By focusing on suspicious patterns in network traffic and scrutinizing less-monitored protocols, you can expose exfiltration attempts before they succeed. Proactively addressing these threats ensures your organization’s most valuable assets remain secure.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data sources to optimize the hunt","_metadata":{"uid":"cs5f34f7c7dfe62e8b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo effectively detect T1048 activities, consider the following data sources and their respective Elastic integrations:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e1. Application logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Monitor logs from applications handling data transfers.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Unusual file downloads from cloud services like Google Drive or Microsoft OneDrive, such as multiple downloads by a single user in a short period\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/elastic_agent.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Agent\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e can be configured with centrally managed\u0026nbsp; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eintegrations\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and ship application logs to Elastic.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e2. Cloud storage access logs: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTrack access to cloud storage services.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Unusual queries or access patterns, especially from unexpected sources, indicating potential improper permissions or unauthorized access\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/elastic_agent.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Agent\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e can be configured with out-of-the-box \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations?search=cloud%20storage\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eintegrations to collect cloud storage\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e access logs.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e3. Command execution logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Record executed commands and their arguments.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Commands that initiate data transfers, such as \u003cspan data-type='inlineCode'\u003ecurl,\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eftp\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003escp\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e,\u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e which may indicate exfiltration attempts\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e You can leverage one of Elastic’s many \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/index.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eintegrations\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to collect executed commands and their arguments. An integration you could utilize is the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/system.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSystem\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e4. File access logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Monitor access to files, especially sensitive ones.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Access to or modification of files that may be staged for exfiltration\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/fim.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFile Integrity Monitoring Integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/endpoint.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e can track file modification events.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e5. Network traffic logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Analyze network connections and data flows.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e New or unusual network connections, especially to untrusted hosts, and traffic patterns that don't conform to expected protocols\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e For network logs, you can leverage one of Elastic’s many \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/index.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eintegrations\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Most firewall integrations will ingest the required data correctly. You could also utilize the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/network_traffic.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNetwork Packet Capture\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to capture and analyze network traffic.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e6. User activity logs:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Monitor and analyze user activity.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDetects:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Users initiating large or unusual data transfers, which may be precursors to exfiltration\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElastic integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Use \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/endpoint.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Endpoint Security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eor another \u003c/span\u003e\u003ca href=\"https://www.elastic.co/integrations/data-integrations\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic integration\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that collects logging information from a third party for monitoring user activity logs.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Threat hunting with ES|QL queries","_metadata":{"uid":"cs79aec23444ae3e42"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo uncover adversaries leveraging \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/techniques/T1048/\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eT1048 - Exfiltration Over Alternative Protocol\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we need to analyze network behaviors, process activities, and data flows for signs of hidden exfiltration. By leveraging \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/ecs/current/ecs-reference.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic Common Schema (ECS)\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, these data sources are parsed and normalized into a consistent format, ensuring more effective correlation and detection across diverse logs. Below are \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eES|QL queries\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e designed to detect specific aspects of this technique, using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/ecs/current/ecs-ecs.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eECS fields\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to streamline analysis and enhance threat-hunting capabilities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e1. Identify non-standard protocol usage\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdc62669809afbedb"}}},{"code":{"code":"FROM logs-*\n| WHERE network.protocol NOT IN (\"http\", \"https\", \"ftp\") AND network.direction == \"egress\"\n| STATS bytes_out = sum (network.bytes) by source.ip,destination.ip, network.protocol\n","_metadata":{"uid":"csaff1508c2e793b55"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse9ec480d90848088"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query identifies traffic using \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003enon-standard protocols\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, excluding common ones like HTTP, HTTPS, FTP, and SSH. Non-standard protocols are less frequently used for legitimate purposes and are often exploited by adversaries for covert communication or data exfiltration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e2. Cross-reference with firewall logs\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc541ca6f4b89df4d"}}},{"code":{"code":"FROM logs-*\n| WHERE event.outcome == \"success\" AND destination.port IN (53, 123, 69)\n| KEEP destination.ip, rule.name, event.outcome","_metadata":{"uid":"cse0eeba404c06cd8b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc48721a7c007fb35"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e This query identifies \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003efirewall rules\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e that allow traffic on specific ports commonly associated with alternative protocols, such as DNS (port 53), NTP (port 123), or TFTP (port 69). Monitoring these logs helps uncover potential misconfigurations or malicious activity where attackers are leveraging non-standard ports for data exfiltration.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy correlating this data with other logs (e.g., application or host logs), analysts can validate the legitimacy of the traffic and identify malicious activities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e3. Correlate with host-based connections\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc32b21f15d39577d"}}},{"code":{"code":"FROM logs-*\n| WHERE network.protocol == \"dns\" AND network.direction == \"egress\"\n| STATS bytes_out = sum(network.bytes) by source.ip, destination.ip, network.protocol\n","_metadata":{"uid":"csaa38021beb680482"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs641266ad66845247"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThis query focuses on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ehost-based DNS connections\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with a significant amount of outbound traffic. Monitoring host-level DNS activity allows analysts to identify endpoints generating excessive data transfers over DNS, which could signal suspicious behavior such as DNS tunneling for data exfiltration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e4. Detect large outbound DNS queries\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csacacfe9d57ea2e39"}}},{"code":{"code":"FROM logs-*\n| WHERE network.protocol == \"dns\" \n| EVAL dns_length = length(dns.question.name)\n| WHERE dns_length \u003e 100\n| KEEP source.ip, destination.ip, dns.question.name, dns_length, @timestamp","_metadata":{"uid":"cs6c30e13a6bd33c1b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0dbc16eebc8aa4c5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThis query identifies \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003elarge DNS queries\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, which may indicate suspicious activity such as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDNS tunneling\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. DNS is primarily used for resolving domain names into IP addresses, and legitimate DNS queries are typically concise. However, attackers can exploit the DNS protocol to encode and exfiltrate data, resulting in unusually large query lengths.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy monitoring the length of DNS queries and correlating them with known patterns of DNS tunneling, defenders can act quickly to block malicious domains or implement additional restrictions.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis query provides a simple yet powerful mechanism for detecting potential data exfiltration attempts over DNS, allowing organizations to proactively address a common technique used by adversaries.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e5. Identify ICMP traffic with data payloads\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8bae03238f24ace8"}}},{"code":{"code":"FROM logs-*\n| WHERE network.transport == \"icmp\" \n AND network.bytes \u003e 0\n| KEEP source.ip, destination.ip, network.bytes, @timestamp","_metadata":{"uid":"cs48053ae95cbf09ba"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs030a85d63c964c13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThis query detects \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eICMP (Internet Control Message Protocol) traffic\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003enon-empty payload\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. ICMP is primarily used for diagnostic purposes, such as pinging a host to check its availability. Typically, ICMP packets carry minimal or no payload data, so the presence of a payload is unusual and can indicate covert activity.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e6. Monitor outbound FTP connections\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs264e80fddaba66a2"}}},{"code":{"code":"FROM logs-*\n| WHERE process.name == \"ftp\" AND network.direction IN (\"outbound\", \"egress\", \"external\")\n| KEEP user.name, source.ip, destination.ip, network.bytes, @timestamp","_metadata":{"uid":"cs417f72c2a8f49128"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs25ee8a7e1edece4b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThis query focuses on detecting \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eoutbound FTP (File Transfer Protocol) connections\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. FTP is a protocol commonly used for transferring files between systems, both internally and externally. While legitimate in some environments, its use for outbound connections, especially to unknown or untrusted destinations, is a potential indicator of data exfiltration.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e7. Identify outbound SMB traffic\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbe119b0d4a6ae9ce"}}},{"code":{"code":"FROM logs-*\n| WHERE network.protocol == \"smb\" AND network.direction IN (\"outbound\", \"egress\", \"external\")\n| KEEP source.ip, destination.ip\n","_metadata":{"uid":"cs542be39455fc542e"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6f3ce9b517cc1b6b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplanation: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eThis query focuses on detecting \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eoutbound SMB traffic\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, which is often a red flag for potential data exfiltration. SMB (Server Message Block) is a protocol primarily used for file sharing, printer sharing, and other networked resource access within an organization’s internal network.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cstrong\u003e8. Detect abnormal application data transfer activity\u003c/strong\u003e\u003c/p\u003e\u003ch1\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/h1\u003e"}],"_metadata":{"uid":"cs2f61982f39981fdf"}}},{"code":{"code":"FROM logs-*\n| WHERE event.category == \"file\"\n AND process.name IN (\"dropbox\", \"google-drive\", \"onedrive\")\n AND event.action == \"creation\"\n AND file.size \u003e 5000000\n| KEEP user.name, process.name, event.action, file.size, source.ip, destination.ip, @timestamp","_metadata":{"uid":"cs39bd721df6cee496"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6daf263fd85c6032"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eExplanation:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e This query monitors \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eapplication logs\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for abnormal file uploads through popular file-sharing applications like Dropbox, Google Drive, and OneDrive. It flags large file uploads (over 5MB) that could indicate potential data exfiltration.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eCorrelating the process name \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e(process.name)\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with the user \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e(user.name)\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e and upload size \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e(bytes_out)\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e provides deeper context, helping analysts differentiate between normal and suspicious activity.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"The next challenge: Stay vigilant","_metadata":{"uid":"cs34a676c528eb8646"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe hunt for exfiltration pathways has come to an end, but what did you uncover? Were the whispers in your network a false alarm, or did you expose an adversary stealthily siphoning data through alternative protocols? By digging into DNS queries, scrutinizing ICMP payloads, and monitoring less-traveled protocols, you’ve shone a light on hidden streams that could carry sensitive information beyond your defenses.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you found signs of T1048 - Exfiltration Over Alternative Protocol, you’ve taken critical steps to disrupt the adversary’s escape route and protect your organization’s most valuable assets. If not, your proactive approach has validated your defenses, ensuring your network is resilient against covert exfiltration attempts. Either way, your efforts have bolstered your security posture and sharpened your detection capabilities.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe challenge now is to remain vigilant. Adversaries are constantly refining their techniques, seeking new ways to bypass traditional monitoring. Remember, every DNS query, ICMP packet, or unusual protocol is a potential signal of malicious intent. The hunt may be over for today, but the lessons you’ve learned and the tools you’ve honed will serve you in future battles.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, did you catch the adversary in the act, or can you confidently say your defenses held firm? Either way, your network is safer, and your skills as a hunter are sharper. Want to stay ahead of the latest threats? Learn how Elastic Security can help you detect, investigate, and respond to modern attacks with cutting-edge research and techniques. Visit\u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to explore expert insights, real-world threat analysis, and powerful defense strategies.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe logs don’t lie — let them guide your hunt.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs197f31ba8a3743b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa891133737b1ceae"}}}],"publish_date":"2025-03-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt7a4eb1026ba18f63","ACL":{},"created_at":"2023-11-06T20:07:03.185Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"advanced-persistent-threat","label_l10n":"Advanced Persistent Threat (APT)","tags":[],"title":"Advanced Persistent Threat (APT)","updated_at":"2023-11-06T20:07:03.185Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:50.393Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt4ea103fc5647f722","_version":1,"title":"1-175401 - Blog Header Image- ELK Hunting Series-1.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-12T01:38:45.228Z","updated_at":"2025-03-12T01:38:45.228Z","content_type":"image/jpeg","file_size":"97302","filename":"1-175401_-_Blog_Header_Image-_ELK_Hunting_Series-1.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-12T20:41:06.495Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4ea103fc5647f722/67d0e5a5a01ee932970610b1/1-175401_-_Blog_Header_Image-_ELK_Hunting_Series-1.jpg"},"title":"Hunting with Elastic Security: Detecting covert data exfiltration","title_l10n":"Hunting with Elastic Security: Detecting covert data exfiltration","updated_at":"2025-03-14T15:11:07.603Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-security-detecting-covert-data-exfiltration","publish_details":{"time":"2025-03-14T15:11:11.683Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt62a26b9c217a3102","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"This series gives you an inside look at how we're using generative AI in Elastic customer support. Join us as we share our journey in real time!","author":["blt57f0334083eb9790"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-06-27T18:49:32.722Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb3ef354065f10f37"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEmbark on a technical journey from zero to hero as we explore the development of a GenAI app for customer support. T\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/category/inside-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003eInside Elastic blog series\u003c/span\u003e\u003c/a\u003e \u003cspan style=\"font-size: 12pt;\"\u003eshowcases Elastic's internal operations solving real-world business challenges. This specific series will shed light on our journey to integrate generative AI into our customer success and support operations, providing you with a behind-the-scenes look at our process. We’re blogging about this capability as we’re building it, and we’re excited for you to join the ride!\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI: The Next Frontier","_metadata":{"uid":"cs84b3616f4eb2629d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe launch of OpenAI's generative AI tools in late 2022 opened a world of possibilities for AI-generated content. Business leaders quickly sought ways to harness this technology for their unique challenges. This is especially true of our Customer Success and Support teams’ operations, after hearing questions from our leaders at Elastic like:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI improve customer support efficiency and effectiveness?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI enhance the customer experience and satisfaction?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI be integrated with existing customer support systems and processes?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI assist in automating repetitive tasks and free up support agents' time for more complex and strategic activities?\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Field Engineering team, responsible for custom internal tooling, started to investigate generative AI and met at an offsite to brainstorm potential applications. Given we are Elastic, we were aware of our product’s search capabilities and how we integrate into the larger AI technology stack. However, technology alone doesn’t answer any of the questions above.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile discussing the possibilities of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, we landed on two support workflows that we thought could benefit our internal teams and, as a result, our customers:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAutomated case summaries:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Our support engineers spend a significant amount of time providing case summaries for escalation or transitioning a case from one engineer to another. Our hypothesis was that we could use generative AI to automate this process and increase our support team’s efficiency and effectiveness, improve issue resolution, and boost customer satisfaction overall.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDrafting an initial reply:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Service level agreements are a key benefit of our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/support\"\u003e\u003cspan style='font-size: 12pt;'\u003esupport offering\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and ensuring timely response is paramount. We were unsure if the large language model (LLM) was smart enough to offer an accurate, relevant response, but we were convinced that our learnings from this process would be critical in deciding the next use case.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArmed with this decision, we decided to build a scalable proof of concept that would allow us to operationalize these workflows for a subset of our users while including a feedback mechanism to rate and improve quality.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Building a proof of concept for feedback","_metadata":{"uid":"cs2ce87d0283eadfbf"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor context, our Field Engineering team has built our system’s infrastructure on top of \u003c/span\u003e\u003ca href=\"https://cloud.google.com/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eGoogle Cloud Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, with Salesforce \u003c/span\u003e\u003ca href=\"https://www.salesforce.com/service/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eService Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e powering our case management. This existing setup made it straightforward to integrate our initial proof of concept with \u003c/span\u003e\u003ca href=\"https://cloud.google.com/vertex-ai?\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eVertex AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which was already enabled internally and compliant with our security and privacy policies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOf course, we knew Elastic would play a role in our design (and subsequent blogs will speak to that), but at this initial stage we were focused on the LLM itself and applying generative text to the outlined workflow. The very first architecture looked like this:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csac2f8393231913a7"}}},{"image":{"image":{"uid":"bltcb97c512e241c08d","_version":1,"title":"1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:50:02.732Z","updated_at":"2024-06-27T18:50:02.732Z","content_type":"image/png","file_size":"245511","filename":"1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.844Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcb97c512e241c08d/667db45ab113249b1a3a2706/1.png"},"_metadata":{"uid":"cs0fb120c63b220710"},"caption_l10n":"","alt_text_l10n":"architecture","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"banner":{"reference":[{"uid":"bltcd245d630daca83c","_content_type_uid":"banner"}],"_metadata":{"uid":"csd11e1a67b0672411"}}},{"title_text":{"title_text":[{"title_l10n":"Creating a case summary","_metadata":{"uid":"csc9a4c1bf96adc650"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt a high level, we wanted to keep the automation simple. We asked our CRM team to add a custom button on all cases that would call an external endpoint. That external endpoint was a Google \u003c/span\u003e\u003ca href=\"https://cloud.google.com/functions?\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCloud Function\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that did the following:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1.\u0026nbsp; The function accepted the Salesforce unique case ID as input and retrieved the case details as text.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2. The retrieved text would then be automatically sent to Vertex AI combined with the following \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/prompt-engineering\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eengineered prompt\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eWrite the summary of the following customer agent conversation in a paragraph? \\\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eConsidering the conversation below, what are the pending actions by the Agent? Keep the response short.\\\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eUse only the information from the conversation below:\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e${text}\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eProvide the answers in the dictionary format : {Summary:[], Pending Actions:[]}`;\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e3. The AI-generated response was posted to the case via a Salesforce \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eChatter Post\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThat was basically it! The lone exception was for long-running cases, where we had to break down the text into summaries of summaries. Once we landed on a design, we had this up and running in a week.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Automating a draft initial reply","_metadata":{"uid":"csab444269458cbe13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhile a little more complex than case summaries, automating a reply for our support engineers to review was relatively straightforward. We leveraged an existing automation for all newly created cases and called a new Google \u003c/span\u003e\u003ca href=\"https://cloud.google.com/pubsub?\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePub/Sub\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e queue to handle all the incoming requests separately. The Pub/Sub performed the following tasks:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1. It stored the Case ID in the queue for when resources were available.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e2. On execution, it passed the Case ID to a different Google Cloud Function that would extract only the customer’s initial request as text.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e3. The retrieved text would then be automatically sent to Vertex AI combined with the following engineered prompt:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eYou are an expert Elastic Support Engineer, using only Elastic products, provide a \\\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eresponse with resolution to this email by a customer:\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e${text}\u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003e\"\"\"`;\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e4. The AI-generated response was posted to the case via a Salesforce Chatter Post.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAgain, a simple approach to capturing an initial draft reply that was scalable for the subset of cases we were looking at. This took us a few extra days to modify our existing code and the additional Pub/Sub functionality and took us roughly two weeks to complete.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing Vertex AI as our LLM for this proof of concept was an easy decision. We knew we would have plenty to think about related to LLM accuracy (see below), but the ease of connecting it with our existing infrastructure made this process much quicker. Much like search, the relevance of an AI-generated response is a deeper conversation and something we knew we would tackle next.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Capturing user feedback","_metadata":{"uid":"cscd558c80799bdfa3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn example of the previously mentioned Salesforce Chatter post:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb1ce0dcec516afd5"}}},{"image":{"image":{"uid":"blte1ccb7e67d424fc8","_version":1,"title":"2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:50:08.632Z","updated_at":"2024-06-27T18:50:08.632Z","content_type":"image/png","file_size":"115487","filename":"2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.834Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte1ccb7e67d424fc8/667db460abc513cfa45d0981/2.png"},"_metadata":{"uid":"cs7b18f3d25417227f"},"caption_l10n":"","alt_text_l10n":"support automation","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbaeb9ba00c954eca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn both use cases, draft reply and case summary, the decision to use Salesforce Chatter to deliver the AI-generated text was based on the idea that we could use standard Chatter features for \u003c/span\u003e\u003ca href=\"https://help.salesforce.com/s/articleView?id=sf.collab_feed_like.htm\u0026type=5\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003e\"likes\"\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to identify positive sentiment and threaded responses to capture subjective feedback. This was a critical step in the process and reduced friction in the feedback loop as users could work cases and provide their feedback in the same operational system.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere are much more sophisticated techniques for evaluating LLM accuracy, especially when Elasticsearch provides context. Still, we intentionally avoided that for the proof of concept as our data population was manageable, and we wanted to review every comment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Objectively evaluating results and making decisions","_metadata":{"uid":"cs1eb5eb9f37612fe3"},"header_style":"H2","paragraph_l10n":"\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDays Open\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e44\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenerated Content\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e940\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFeedback\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e217\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePositive Sentiment\u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style=\"font-size: 12pt;\"\u003e15.67%\u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eThe initial user feedback yielded a ~16% positive response rate, which was lower than expected. Reviewing subjective feedback revealed that the LLM lacked in-depth knowledge of our products, which hindered its ability to address technical support queries. The model performed much better with generic summaries and responses that didn't require specific product knowledge. This highlighted a content gap, as the LLM was trained on public data and lacked access to key data sources like our product documentation and internal knowledge base articles.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBased on this data, we decided to add two new design principles:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRefine the input data: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe recognized the need for a more explicit input experience to provide clearer, more direct questions to the LLM for improved responses. This is equivalent to the “garbage in, garbage out” statement in data engineering.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSet a higher accuracy/sentiment threshold:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Technical support requires high accuracy, so we aimed for a \u0026gt;80% benchmark and developed systems to measure and enhance accuracy at various stages.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGuided by these principles, we decided that the optimal experience would be to consolidate these and all other potential functions into a unified chat interface. That should help curate the inputs in a consistent way for better workflow and responses. Furthermore, we knew the next evolution would need to include Elasticsearch for improved response accuracy via a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eretrieval augmented generation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e architecture.\u0026nbsp; This should allow us to evaluate accuracy at scale and significantly improve the precision of our responses.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Solving business problems","_metadata":{"uid":"cs40950c394c9b4dce"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArmed with this data-backed understanding of how a large language model responds to our specific workflows and our decision to integrate the solution into a chatbot, we revisited the questions from our business leaders:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI improve customer support efficiency and effectiveness?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe believe we can build a self-service chatbot experience that will answer support related product questions. Support agents’ use of the chatbot will speed up their analysis and investigation, reducing mean time to resolution. In addition, new joiners can learn from the chatbot rather than other members of the team. This can reduce onboarding time and create capacity in existing team members who are fielding these questions today.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI enhance the customer experience and satisfaction?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Technology Services Industry Association (\u003c/span\u003e\u003ca href=\"https://www.tsia.com/who-we-are\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTSIA\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e), which works with thousands of support organizations, has years of research supporting the fact that customers \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eprefer\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e self-service over assisted support. Exposing a similar self-service chatbot can increase both user experience and customer satisfaction as real-time, relevant responses can reduce customer response times to milliseconds and don’t require reading through vast pages of documentation.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI be integrated with existing customer support systems and processes?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur talented team of developers can easily integrate a chat experience into our custom Support Portal at the point where customers are asking these questions and leverage Elasticsearch for knowledge content search.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow can generative AI assist in automating repetitive tasks and free up support agents' time for more complex and strategic activities?\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSupport agents consistently search for product documentation, internal enablement content, and knowledge articles for an answer. Natural language chat is an evolution of these search activities that deliver contextual, relevant responses rather than recommending information to read. The efficiencies gained in search time alone will free up support agent time for other value-add, strategic activities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter a few months of gathering data, we presented our findings, designs, and plans for a chat-based Support AI Assistant to our stakeholders, aligned on the above outcomes, and moved from proof of concept to an approved project.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur customers and our community are at the heart of everything we do. When building any internal or external experience, we keep our Customers, 1st. Investing in this process allowed us to build an informed plan to execute against, keeping our customers front of mind.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What's next?","_metadata":{"uid":"cs8633d8f7e155ba19"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur Field Engineering team is now focused on developing a scalable, secure, and accurate Support AI Chat Assistant. This blog series will continue with regular updates, each installment highlighting a different aspect of our build process. Stay tuned for more insights and inspiration for your own generative AI projects.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTake a sneak peek at our current architecture:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csac5924db3c65fd36"}}},{"image":{"image":{"uid":"blt118be6e915c596fa","_version":1,"title":"3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:50:14.625Z","updated_at":"2024-06-27T18:50:14.625Z","content_type":"image/png","file_size":"141109","filename":"3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.854Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt118be6e915c596fa/667db466c8ca77b311cde359/3.png"},"_metadata":{"uid":"cs385d06149928aa63"},"caption_l10n":"","alt_text_l10n":"current architecture","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"callout":{"title_l10n":"Check out what's next in the series","_metadata":{"uid":"cs040f5fe406b98e35"},"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart 2: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/genai-customer-support-building-a-knowledge-library\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI for Customer Support — Building a Knowledge Library\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart 3: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/genai-elastic-elser-chat-interface\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI for Customer Support — Designing a chat interface for chatbots... for humans\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart 4:\u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elser-rag-search-for-relevance\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e GenAI for Customer Support — Tuning RAG search for relevance\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLaunch blog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/generative-ai-customer-support-elastic-support-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI for customer support - Explore the Elastic Support Assistant\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb51c8571dc7e72c9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eOriginally published June 27, 2024; updated March 13, 2025.\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003e\u003cbr italic=\"[object Object]\"/\u003e\u003cbr italic=\"[object Object]\"/\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6a6327a5ef33e020"}}}],"publish_date":"2025-03-13","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Search UI","label_l10n":"Search UI","keyword":"search-ui","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltaea23ea6eafbd6eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:31:21.217Z","updated_at":"2023-11-06T21:31:21.217Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.855Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltedaba1c436cb0ded","ACL":{},"created_at":"2023-11-06T20:40:47.717Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"information-retrieval","label_l10n":"Information retrieval","tags":[],"title":"Information retrieval","updated_at":"2023-11-06T20:40:47.717Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:37.018Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt4607298d4fd82c81","ACL":{},"created_at":"2020-06-17T03:31:33.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"workplace-search","label_l10n":"Workplace search","tags":[],"title":"Workplace search","updated_at":"2020-07-06T22:19:56.394Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:53.167Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltac88392b5d494907","_version":1,"title":"elastic-de-143903-V2_V1 (1).jpeg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-06-27T18:49:31.019Z","updated_at":"2024-06-27T18:49:31.019Z","content_type":"image/jpeg","file_size":"130759","filename":"elastic-de-143903-V2_V1_(1).jpeg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-06-27T19:01:39.819Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltac88392b5d494907/667db43bbbf7b42e25a74e95/elastic-de-143903-V2_V1_(1).jpeg"},"title":"GenAI for customer support — Part 1: Building our proof of concept","title_l10n":"GenAI for customer support — Part 1: Building our proof of concept","updated_at":"2025-03-14T05:50:57.958Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/genai-customer-support-building-proof-of-concept","publish_details":{"time":"2025-03-14T05:53:48.370Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3833271eee9fa0e8","_version":16,"locale":"en-us","ACL":{},"abstract_l10n":"Discover how Elastic enables data mesh in the public sector with key pillars, architecture, and real-world examples for better data access and governance.","author":["blt6705dad0ae6f1419"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-12T03:18:19.289Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5237fe68c5f54eeb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThink about all the data behind projects like defense intelligence, public health records, urban planning models, and more. Government agencies are generating enormous quantities of data all the time. Things get even more tricky when the data is spread across cloud platforms, on-prem systems, or specialized environments like satellites and emergency response centers. It’s hard to find information, much less use it efficiently. And with different teams working with many different apps and data formats, a real lack of interoperability arises.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDespite their best efforts to build data-driven organizations, the reality is that 65% of public sector leaders still struggle to use data continuously in real time and at scale, according to a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/public-sector-leaders-insights-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003erecent Elastic study\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“It’s taking us longer to do our job, which is not good since most of our work is done in an emergency,” one public sector leader told Elastic. “We need to be able to get information as soon as possible.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe mountain of data is growing. Access to it is bottlenecking. So how can public sector agencies ditch the complexity of those centralized silos? Data mesh offers an alternative way to organize data that could be the answer.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What is data mesh?","_metadata":{"uid":"csb0e253a0885aa251"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePut simply, a data mesh overcomes silos. Data collected from across the entire network is available to be retrieved and analyzed at any or all points of the ecosystem — as long as the user has permission to access it. It provides a unified yet distributed layer that simplifies and standardizes data operations.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf67d54b70186787b"}}},{"video":{"vidyard_uuid":"6sU9zxWp9jECdPkHKndD6C","_metadata":{"uid":"cs26a5e68a4fb63467"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"4 pillars of data mesh","header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData mesh is built on four key principles:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDomain ownership:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e How agencies and departments manage their own data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eData as a product: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eWhere those domain owners make sure their datasets are high quality and easily accessible\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSelf-service platforms:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Let both internal and external teams find and use high-quality data without IT holdups\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFederated governance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Makes sure everything’s working smoothly and securely across systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s look at each of these a little closer.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csb539a0e5300d6071"}},{"title_l10n":"Domain ownership","header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInstead of relying on a central IT team to manage all data, data ownership is distributed across government agencies and departments. Essentially, you’re building technical teams that mirror how the agency itself is composed. You want the people who are most intimately familiar with that data to own it. This can be applied to public health, defense, urban planning, and more — just about any public sector use case.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, the US Cybersecurity and Infrastructure Security Agency (CISA) uses a data mesh approach to gain visibility into security data from hundreds of federal agencies, while allowing each agency to retain control of its data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/cisa-zero-trust-whitepaper\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLearn more about accelerating CISA Zero Trust with Elastic as a unified data layer\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis leads us to the second (and arguably most important) pillar — the one which the other three pillars are designed to support:\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs54fe89aea595bb25"}},{"title_l10n":"Data as a product","header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach dataset is treated as a product with clear documentation and quality standards. The department that owns the data needs to make sure it’s easily accessible and organized for when other departments need it. In other words, they are accountable and responsible for sharing that data as a usable product.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFrom a government perspective, this could be census information, emergency response data, or intelligence reports, for example. It all depends on the structure of the project or government agency. What’s important is that this curated data will be ready to use when other teams come looking for it, and they won’t have to spend time cleaning or verifying it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, you may ask, isn’t this just another way to silo analytical data? What are the nuts and bolts of how other departments can access it? That leads us to our next pillar.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csbea1458ab794ecbc"}},{"title_l10n":"Self-service platforms","header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDepartments are being asked to do a lot here, and they’ll need convenient platforms that make their data accessible to others. Searchable catalogs for easy data discovery, query tools for real-time analysis, and the ability for users to clean and integrate data themselves as well as share insights through dashboards and APIs are all tools that can be used.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThey’ll also need built-in governance to enforce access controls, which leads us to our final pillar.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"cs1db5ab2c30a73a6e"}},{"title_l10n":"Federated computational governance","header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, we’ve established that each department is in control of its own data. However, the data mesh still needs overarching governance protocols to keep it secure and prevent risk.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese security controls should be built into the system that retrieves the data, rather than applied separately by each department. The system should check user permissions as part of the search and make sure people only see the data they’re allowed to access right from the start.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the public sector, this could be anything from privacy regulations in healthcare data to classified information in defense systems.\u003c/span\u003e\u003c/p\u003e","_metadata":{"uid":"csa5591de26070dc51"}}],"_metadata":{"uid":"cs7cf5a5b2415d4180"}}},{"image":{"image":{"uid":"blt31caafdf8b1809bf","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-12T03:17:08.019Z","created_by":"blte369ea3bcd6ac892","file_size":"269507","filename":"Elastic-vision-of-the-data-mesh.png","parent_uid":null,"tags":[],"title":"Elastic-vision-of-the-data-mesh.png","updated_at":"2025-03-12T03:17:08.019Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-12T15:00:07.390Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt31caafdf8b1809bf/67d0fcb484b60342daba05aa/Elastic-vision-of-the-data-mesh.png"},"_metadata":{"uid":"csc643920e9c09c157"},"caption_l10n":"","alt_text_l10n":"Common data layer with unified analytics from Elastic","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"banner":{"reference":[{"uid":"blt23855197ea4f5f29","_content_type_uid":"banner"}],"_metadata":{"uid":"cs87e1e2efd07e5526"}}},{"title_text":{"title_text":[{"title_l10n":"Data mesh architecture","_metadata":{"uid":"csa6b177da2cd766f0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA data mesh architecture is a framework that unites the pillars of data mesh into a process to manage distributed data.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImplementing a data mesh architecture reduces friction in the collaboration process. It’s a game-changer for teams working with domain-specific data for model training and analytics, thanks to its more user-centric approach.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData mesh helps enable more efficient data handling and governance at scale, despite multiple platforms and implementation teams. Data mesh architecture creates more autonomy as well as more democratization of data — if you have scalable, self-serve data observability. Data observability is what lets teams manage all that data under a single pane of glass.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEffective data observability is built into the architecture of a data mesh. It’s what gives teams access to insights they can use from all the data they collect. Think of it this way: Data observability is about having eyes on the health and integrity of the data, while data mesh architectures are about decentralized management of that data. And to manage it, you have to be able to see into it in detail.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data mesh vs. other approaches","_metadata":{"uid":"csc612d9c216512604"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHow does data mesh compare to alternative forms of analytical data architecture and storage? Let’s look at two others that often draw comparisons: data fabric and data lakes.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data mesh vs. data fabric","_metadata":{"uid":"cs6e56743d5256c12d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData mesh and data fabric are similar approaches in that they both take a decentralized approach, collecting data at remote sites. However, a data fabric takes data collected at one site and copies it to another site. This data is shared as individual records and cannot be correlated with other records unless it gets consumed by something that makes sense of it. This approach can often lead to data silos.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA data mesh approach, on the other hand, does not rely on copying data and instead indexes data locally upon ingest into a distributed platform where users can search for data locally and across remote sites. In this model, data is unified at the search platform layer. Data is indexed once and then is available to any authorized user or use case through this unified layer.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data mesh vs. data lake","_metadata":{"uid":"csbdfc11ed0462c056"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou may have noticed that there are a lot of water-related metaphors in data: data streams, data pipelines, etc. Data, like water, can be collected, stored, filtered, and distributed — sometimes efficiently, sometimes chaotically.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the same way that a lake collects water from multiple sources, a data lake collects data and holds it for future use. In other words, it’s a storage environment for any combination of structured, semi-structured, or unstructured data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData lakes can sometimes be helpful to data mesh domain owners as they process and curate their data products. They can use a data lake for long-term storage of large, unstructured datasets (say, satellite imagery or public records) that don’t have a specific purpose yet. But if a data lake becomes disorganized and difficult to navigate, it turns into a data swamp — murky, cluttered, and hard to extract value from.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data mesh and AI","_metadata":{"uid":"csf5d725d70f2a82f1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData mesh can offer a way to democratize \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/machine-learning\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI and machine learning\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for public sector agencies. Traditionally, data science teams have operated as centralized hubs, pulling data from multiple sources to develop machine learning models. However, as noted earlier, this process can cause redundant work and inconsistencies, leading to challenges with model reproducibility.\u003cbr /\u003e\u003cbr /\u003eBy flipping that model around with data mesh and embedding AI development within domain teams, you can clean and refine data at its source and create an AI-driven data product other departments can utilize.\u003cbr /\u003e\u003cbr /\u003eTake national disaster response as an example. AI models embedded in emergency response teams often analyze data like real-time satellite imagery, sensor data, and even social media reports to identify the hardest-hit areas. With data mesh, different agencies ranging from government agencies to first responders could access this information immediately without waiting for centralized processing and improve their response times as a result.\u003cbr /\u003e\u003cbr /\u003eData mesh also improves AI governance because it incorporates it right from the start, standardizing tasks like model validation, bias detection, explainability, and monitoring for model drift.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How to implement data mesh for public sector","_metadata":{"uid":"csf13078117f7904f7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach public sector organization has a unique set of data needs, which is why one-size-fits-all data silos can be slow and stifling to internal and external users. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/public-sector-leaders-insights-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eTwo out of three public sector leaders\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e said that they’re unsatisfied with the data insights available to them.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData mesh can be customized to the unique needs of each public sector agency, from defense to national security or federal, state, and local government.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo get started with data mesh, public sector agencies will need to follow a few steps:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAssign responsibility for data to specific departments.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTreat datasets as well-documented, accessible assets designed for internal and external use and make sure they comply with regulatory requirements.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImplement tools that let agencies, analysts, and policymakers easily access and analyze data without relying on centralized IT teams.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnforce governance across agencies, keeping in mind frameworks like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/fedramp\"\u003e\u003cspan style='font-size: 12pt;'\u003eFedRAMP\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cmmc-compliance\"\u003e\u003cspan style='font-size: 12pt;'\u003eCMMC\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/zero-trust\"\u003e\u003cspan style='font-size: 12pt;'\u003eZero Trust\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd finally, encourage data sharing across organizations to make better decisions and improve public services while maintaining security controls.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Government and defense applications","_metadata":{"uid":"cscd80488c5762c39b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData mesh is a natural fit for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003egovernment\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and defense sectors, where vast, distributed datasets have to be securely accessed and analyzed in real time.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/defense\"\u003e\u003cspan style='font-size: 12pt;'\u003edefense\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, it assists with faster intelligence gathering and asset management so operators in the field can act with the latest data. In \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/healthcare\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic health\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, it can help rapidly integrate epidemiological data from hospitals or research labs to respond to outbreaks. Transportation departments can analyze traffic and weather data across cities. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/education\"\u003e\u003cspan style='font-size: 12pt;'\u003eEducation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e departments can view children’s test scores over the past decade and cross-reference them to other data, such as time spent learning remotely versus in-person.\u003c/span\u003e\u003cbr /\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s take \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/us-navy-digital-keel-search\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis example\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e from the US Navy: Its push for digital modernization hinges on the ability to “securely move any information from anywhere to anywhere” to achieve information superiority. But traditional centralized data storage is too risky, especially in air-gapped and Denied, Degraded, Intermittent, and Limited (DDIL) environments. Here’s a case where a global data mesh can help, allowing data to remain at its source while still being searchable and accessible across the Navy’s vast operational landscape. This decentralized approach keeps ops resilient even if a server or data center fails and provides a unified view of mission-critical data without needing to move or duplicate it.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data mesh in action with Elastic","_metadata":{"uid":"cse6ecf7d227115992"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearch AI Company\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, Elastic’s data analytics platform serves as a powerful global data mesh, offering \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/machine-learning\"\u003e\u003cspan style='font-size: 12pt;'\u003emachine learning\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing\"\u003e\u003cspan style='font-size: 12pt;'\u003enatural language processing\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/semantic-search\"\u003e\u003cspan style='font-size: 12pt;'\u003esemantic search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, alerting, and visualization in a unified system. In other words, Elastic serves a unifying function by giving agencies full visibility into their data as well as the ability to ingest, organize, access, and analyze it.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThree key features set Elastic apart:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-enable-ccs.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCross-cluster search (CCS)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which lets you run a single search request against one or more remote clusters\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/searchable-snapshots.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearchable snapshots\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which provide a cost-effective way for you to access and query infrequently used, historical data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRole-based access control, which provides integrated security\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s data mesh approach also can serve as a foundation for modern security frameworks like \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/zero-trust\"\u003e\u003cspan style='font-size: 12pt;'\u003eZero Trust\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and opens up new possibilities for data-driven operations.\u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e\u003cbr /\u003e\u003cbr /\u003eLearn more about how Elastic helps government, healthcare, and education teams maximize data value with speed, scale, and relevance\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7f3a1b5e5b181123"}}},{"callout":{"title_l10n":"Explore more data mesh in the public sector resources","_metadata":{"uid":"csd6634ad0a73b1029"},"paragraph_l10n":"\n\u003cul\u003e\n \u003cli\u003e\n \u003ca href=\"https://www.elastic.co/blog/elastic-global-data-mesh-security-governance-policy\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing Elastic as a global data mesh: Unify data access with security, governance, and policy\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003ca href=\"https://www.elastic.co/public-sector/accelerating-defense-missions-with-global-data-mesh\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccelerating defense missions with a global data mesh\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003ca href=\"https://www.elastic.co/virtual-events/maximizing-data-value-in-public-sector\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMaximizing data value in public sector\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003ca href=\"https://www.elastic.co/industries/public-sector/cisa-zero-trust-whitepaper\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccelerating CISA Zero Trust with Elastic as a unified data layer\u003c/span\u003e\u003c/a\u003e\n \u003c/li\u003e\n\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3910785f2fd6c146"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third-party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third-party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc30aa1c413ac6947"}}}],"publish_date":"2025-03-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt17630d07558c63f6","ACL":{},"created_at":"2023-11-06T21:33:01.038Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"state-local-government","label_l10n":"State \u0026 local government","tags":[],"title":"State \u0026 local government","updated_at":"2023-11-06T21:33:01.038Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.342Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltf2d5f3033a993cfe","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-12T03:10:10.380Z","created_by":"blte369ea3bcd6ac892","file_size":"162150","filename":"Blog_Header_Image_Public_Sector.jpg","parent_uid":null,"tags":[],"title":"Blog Header Image Public Sector.jpg","updated_at":"2025-03-12T03:10:10.380Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-12T15:00:07.379Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf2d5f3033a993cfe/67d0fb1218b08463aaaabbac/Blog_Header_Image_Public_Sector.jpg"},"title":"Understanding data mesh in public sector: Pillars, architecture, and examples","title_l10n":"Understanding data mesh in public sector: Pillars, architecture, and examples","updated_at":"2025-03-13T21:49:22.512Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/data-mesh-public-sector","publish_details":{"time":"2025-03-13T21:52:32.320Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt91c0befca9468e88","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"The public sector is shifting from imagining the possibilities of generative AI to operationalizing and realizing its value at scale. Learn more about GenAI trends and data preparedness in government and defense agencies and educational institutions.","author":["blt6d82d216763f3c7c"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-12T01:06:05.141Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc31b55df6ea873fd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eArtificial intelligence (AI) and generative AI (GenAI) are rapidly transforming the public sector, moving beyond theoretical possibilities to real-world applications. Proper data preparedness, stewardship, and governance will play critical roles in successful GenAI implementations.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eWe recently hosted a webinar, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/public-sector-data-stewardship-idc\"\u003e\u003cspan style='font-size: 12pt;'\u003ePublic sector data stewardship for the AI era\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, with industry experts Max Klaps, research director at IDC, and Dave Erickson, distinguished architect at Elastic. They explored the current state of GenAI adoption in government, education, and defense and dove into the data challenges and opportunities GenAI presents.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The evolution of AI in government","_metadata":{"uid":"cs268ae25a03cc4123"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere’s been a significant shift in how government agencies and other public sector organizations approach AI. Initially, organizations experimented with various AI tools and pilot projects. However, the focus has now shifted toward identifying specific use cases that deliver tangible value and align with the organization's mission and key performance indicators (KPIs).\u003cbr /\u003e\u003cbr /\u003eAccording to IDC research, about half of public sector organizations are running pilots, and 20% are implementing AI in production. The key question now is where AI can drive the most significant impact. Organizations are prioritizing use cases that enhance operational efficiency, improve resilience, reduce errors, ensure compliance, and provide better observability into their processes. Ultimately, the goal is to leverage AI, particularly GenAI, to achieve better outcomes for the public sector workforce, citizens, and students.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Prioritizing high-impact use cases","_metadata":{"uid":"cs9425bd1a1aaf0e23"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe focus has been on several key use cases, categorized as \"horizon one,\" which aim for early wins and test existing capabilities and future-oriented use cases with higher impact and external focus.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/blog/the-future-of-generative-ai-in-public-sector#the-3-horizons-of-generative-ai-use-cases-in-public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003eHorizon one use cases\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e often involve internal processes, such as critical natural infrastructure protection, financial market oversight, dynamic digital legislation, public communication and notification, and AI research and writing assistance for higher education. These use cases often revolve around content access, summarization, and preparation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLooking ahead, public sector leaders are exploring and scaling use cases that directly impact mission outcomes. These include enhancing service delivery, reducing the burden of tax compliance, ensuring payment integrity and reducing fraud, integrating natural language capabilities into 311 systems, and hyper-personalizing student recruitment and intervention in higher education.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Overcoming challenges and ensuring data readiness","_metadata":{"uid":"cs8d83e5d963b0e199"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImplementing GenAI is not without its challenges, with common obstacles such as:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGovernance\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRisk\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCost control\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eScalability\u0026nbsp;\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eBut one recurring theme is the critical importance of data readiness. Although there's a need for high-quality data, quantity isn’t necessarily the primary concern. Public sector organizations can leverage pretrained models and focus on providing the AI with relevant, curated data for specific use cases. This approach, known as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieval augmented generation (RAG)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, ensures that AI answers are grounded in authoritative information and reduces the risk of inaccurate or biased outputs. The quality of data being fed to the generative models is critical.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csaed0933643543276"}}},{"banner":{"reference":[{"uid":"bltc11264e44c984bd8","_content_type_uid":"banner"}],"_metadata":{"uid":"cs0cde6017f909872b"}}},{"title_text":{"title_text":[{"title_l10n":"RAG: A key pattern for success","_metadata":{"uid":"csd2b0d53ae6f83b27"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eRAG is a crucial workflow for grounding GenAI with proper context. Instead of relying solely on the model’s pre-existing knowledge, RAG involves retrieving relevant data from an organization's proprietary data (e.g., documents, images, audio) and using that data to inform the AI's response. This approach enhances the accuracy, trustworthiness, and explainability of AI-generated answers.\u003cbr /\u003e\u003cbr /\u003eElastic plays a significant role in enabling \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/rag\"\u003e\u003cspan style='font-size: 12pt;'\u003eRAG\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/vector-database\"\u003e\u003cspan style='font-size: 12pt;'\u003evector database\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e enables organizations to store, retrieve, and analyze vast amounts of data, making it easier to ground AI in authoritative information.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Responsible AI and risk mitigation","_metadata":{"uid":"csb49a3094a834b680"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eResponsible AI involves ensuring that AI systems are ethical, explainable, and transparent. Organizations can take several practical steps to promote responsible AI, including:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAssessing and categorizing the risk levels of different use cases\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePrioritizing risk mitigation strategies, such as implementing data security protocols and detecting bias\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEstablishing clear accountability and reporting mechanisms\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEngaging with the public to explain the risks and opportunities of AI\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s essential to use a common language and framework for discussing AI risks, such as the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) in the United States. Another important consideration is separating the compensating controls for responsible AI from the AI itself — in other words, maintaining control over the guardrails you need. Also, continuous evaluation of AI-generated answers is essential for ensuring ongoing public trust.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Preparing the workforce for GenAI","_metadata":{"uid":"csb0dbf54623b1e6d1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePeople are crucial to the successful implementation of GenAI. Organizations need to invest in training and development to ensure that their workforce is prepared for this shift. Key areas of focus include:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEstablishing AI awareness (and risk) training for all employees\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eProviding technical staff with the tools and opportunities to work with AI\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeveraging the expertise of the partner ecosystem, such as academic research institutions and standards bodies\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCreate spaces where staff can experience AI's limitations and learn how to use it effectively as a tool. Emphasize moving away from the mindset of AI as an all-knowing entity and embrace a more practical approach that stresses understanding AI's capabilities and limitations.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Learn more","_metadata":{"uid":"cs191a11cb27927d74"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTune into \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/public-sector-data-stewardship-idc\"\u003e\u003cspan style='font-size: 12pt;'\u003ePublic sector data stewardship for the AI era\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for more insights on capitalizing on the incredible power and potential of GenAI.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs56a97382c9bcfb44"}}},{"callout":{"title_l10n":"Explore additional GenAI resources:","_metadata":{"uid":"csc80e203e2a0d83d5"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic for generative AI\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — GenAI technical details, research, and tutorials\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBlog: \u003c/span\u003e\u003ca href=\"http://www.elastic.co/blog/public-sector-leaders-insights-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e5 insights from public sector leaders: Solving organizational challenges with data and AI\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEbook: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industries/public-sector/how-search-ai-transforms-call-centers-citizen-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow Search AI is transforming call centers and citizen support\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhat is a large language model (LLM)?\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse213e7a5d22a3620"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdfecdeec986d8a47"}}}],"publish_date":"2025-03-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltd6680e0300eee933","ACL":{},"created_at":"2023-11-06T20:37:41.282Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"defense","label_l10n":"Defense","tags":[],"title":"Defense","updated_at":"2023-11-06T20:37:41.282Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.232Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb2519aa4ed213854","ACL":{},"created_at":"2023-11-06T20:39:02.976Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education","label_l10n":"Education","tags":[],"title":"Education","updated_at":"2023-11-06T20:39:02.976Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.189Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb4928f8cf10d2cff","ACL":{},"created_at":"2023-11-06T21:35:16.245Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"vector-search","label_l10n":"Vector search","tags":[],"title":"Vector search","updated_at":"2023-11-06T21:35:16.245Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.491Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt09263c5a3152c7a7","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-12T01:05:53.405Z","created_by":"blte369ea3bcd6ac892","file_size":"71040","filename":"blog_header_image_publicsector_ai_175791.jpg","parent_uid":null,"tags":[],"title":"blog_header_image_publicsector_ai_175791.jpg","updated_at":"2025-03-12T01:05:53.405Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-12T15:00:04.054Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt09263c5a3152c7a7/67d0ddf11aa775f81cb199fd/blog_header_image_publicsector_ai_175791.jpg"},"title":"Public sector data stewardship for the AI era","title_l10n":"Public sector data stewardship for the AI era","updated_at":"2025-03-12T17:09:23.288Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/public-sector-data-stewardship-ai","publish_details":{"time":"2025-03-12T17:10:24.252Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt04a8c1ef59294253","_version":7,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Cloud Serverless on AWS has achieved several industry-recognized security and compliance certifications. This milestone reinforces our commitment to security, privacy, and regulatory compliance. ","author":["blt2b87f31037aed281"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2025-01-21T19:49:56.143Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"Elastic Cloud Serverless on AWS achieves major compliance certifications","_metadata":{"uid":"cs540a68b192b87927"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe are thrilled to announce that Elastic Cloud Serverless on AWS has achieved several significant compliance certifications. This milestone reinforces our commitment to security, privacy, and regulatory compliance. Elastic Cloud Serverless is now audited or certified under the following industry-leading frameworks: SOC 2 Type 2, ISO 27001, ISO 27017, ISO 27018, Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCloud Security Alliance (CSA) Security, Trust, Assurance, and Risk (STAR).\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What this means for you","_metadata":{"uid":"cscd530b3bd4ae87fe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese certifications demonstrate our dedication to maintaining high standards of security, governance, and data protection. Here’s a brief overview of why each framework matters to you:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSOC 2 Type 2:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e The Elastic Cloud Serverless service meets rigorous standards for security, availability, confidentiality, and privacy.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eISO 27001:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic has established, implemented, maintained, and continually improved upon an information security management system (ISMS). Elastic Cloud Serverless is now certified under that ISMS.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eISO 27017 and 27018:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic has implemented security controls applicable to the provision and use of cloud services as well as measures to protect personal data in the cloud.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePCI DSS:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic Cloud Serverless has demonstrated compliance with all applicable PCI DSS requirements.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHIPAA:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic Cloud Serverless satisfies the requirements of the HIPAA Security Rule and Breach Notification Rule.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCSA STAR:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e The CSA STAR certification demonstrates our commitment to cloud security best practices.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Why it matters","_metadata":{"uid":"cs5c2d54851c13cf9b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAchieving these certifications is a testament to our continued investment in comprehensive security practices and our commitment to protecting your data. In addition to a faster, more flexible way to scale search, security, and observability capabilities — introduced with the general availability of Elastic Cloud Serverless — it also meets the highest standards of security and compliance.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Learn more","_metadata":{"uid":"csa6b6fd39ed7116b4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo learn more about our full portfolio of compliance certifications, visit our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/trust\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTrust Center\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe are excited to continue providing you with secure, reliable, and compliant cloud services. We will continue to maintain these certifications and expand our portfolio of supported compliance frameworks to position Elastic Cloud Serverless \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eon AWS\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e as a trusted solution for search, security, and observability applications.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eAs of the publication date, currently Elastic Cloud Serverless on AWS is externally certified and attested to against the above mentioned frameworks and standards. As Elastic Cloud Serverless expands to additional regions and cloud providers, we will work to certify and attest to the new environments at the same level of rigor.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9d5a6e932fc0a060"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3f95493814396f47"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd1744f3cffdd5f5b"}}}],"publish_date":"2025-01-21","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt9fe4026c50b65a9b","_version":1,"title":"serverless-infosec.jpeg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-01-21T19:48:37.301Z","updated_at":"2025-01-21T19:48:37.301Z","content_type":"image/jpeg","file_size":"159422","filename":"serverless-infosec.jpeg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-01-21T20:21:43.352Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9fe4026c50b65a9b/678ffa156f0a081f9c2672fd/serverless-infosec.jpeg"},"title":"Elastic Cloud Serverless on AWS achieves major compliance certifications","title_l10n":"Elastic Cloud Serverless on AWS achieves major compliance certifications","updated_at":"2025-03-11T23:52:23.461Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-cloud-serverless-achieves-major-compliance-certifications","publish_details":{"time":"2025-03-11T23:55:07.464Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt01804ff7ae45ff93","_version":5,"locale":"en-us","ACL":{},"abstract_l10n":"As cyber threats grow in complexity, traditional security models are no longer enough. Zero Trust offers a proactive approach to securing access and sensitive data. See how a unified data layer helps public sector organizations implement Zero Trust.","author":["blt9580becc8544cdfa"],"category":["bltb79594af7c5b4199"],"created_at":"2025-03-11T01:51:29.299Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs776798c6a56d4021"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the evolving and complex cyber landscape, the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/zero-trust\"\u003e\u003cspan style='font-size: 12pt;'\u003eZero Trust\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e approach is instrumental in addressing both internal and external threats. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIt's a comprehensive strategy rather than a single solution\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, demanding the orchestration of multiple components to be genuinely effective.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs data, systems, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/cybersecurity#types-of-cybersecurity-threats\"\u003e\u003cspan style='font-size: 12pt;'\u003ecyber threats\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e continue to grow in complexity, traditional security models are no longer sufficient. This is where Zero Trust (ZT) comes into play — \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003enever trust, always verify\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. It ensures that every request for access, whether internal or external, is authenticated, authorized, and encrypted. This significantly reduces the risk of unauthorized access, insider threats, data breaches, and advanced cyber attacks.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile the US federal government, including defense agencies, is already mandated to adopt Zero Trust architectures, other industries are beginning to follow suit. However, despite its increasing adoption and clear benefits, public sector organizations face significant challenges when trying to implement this security framework.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Challenges of Zero Trust deployment for public sector organizations","_metadata":{"uid":"csd2254e0e9b3ee7f9"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Complexity of implementation","_metadata":{"uid":"cs368f09fe716f9648"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDeploying a Zero Trust\u0026nbsp; architecture across an organization is complex, especially for large enterprises and critical infrastructure. These environments often rely on diverse and legacy systems, requiring significant resources and expertise to integrate ZT principles effectively.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Heterogeneous IT environments","_metadata":{"uid":"cs48b1a97364a00246"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAgencies operate across diverse environments, from on-prem data centers to multiple cloud services and providers — some managed internally, others externally. Navigating these hybrid infrastructures while maintaining security, interoperability, and visibility adds significant complexity.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Legacy tools and limited scalability","_metadata":{"uid":"cs2f635ddd0c4be0b9"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMany federal government agencies rely on decades-old infrastructure that wasn’t designed with Zero Trust principles in mind. Legacy IT systems struggle to keep up, lacking scalability, speed, and cross-environment support.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Balancing security with usability","_metadata":{"uid":"cs5f7935131a7c29cd"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eZero Trust inherently limits access based on user roles, which can sometimes be perceived as a barrier to collaboration and productivity. Organizations must ensure security policies remain effective to prevent unauthorized access without restricting employees’ ability to perform their work.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Siloed data and lack of holistic visibility","_metadata":{"uid":"cs9335636693711108"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach Zero Trust pillar generates data in different formats, often stored in silos without interoperability. This lack of unified data makes it difficult to monitor and analyze risks holistically. Manually correlating data across disparate systems slows down threat detection and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/investigation-response\"\u003e\u003cspan style='font-size: 12pt;'\u003eincident response\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Fragmented security solutions","_metadata":{"uid":"cscea6a5cf2e0aea08"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMany vendors sell separate security tools that should be integrated into a comprehensive solution. This leads to a disconnected user experience, higher security risks, and inefficiencies in data protection.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3f32a498e4d894b1"}}},{"banner":{"reference":[{"uid":"bltf3f60f328ddf7fc5","_content_type_uid":"banner"}],"_metadata":{"uid":"csc67218ab493dace0"}}},{"title_text":{"title_text":[{"title_l10n":"Why traditional security models are failing","_metadata":{"uid":"cs7121488d009c53d5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePublic sector organizations\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehandle massive amounts of sensitive data on a daily basis. Traditionally, sharing this data involved creating copies and transmitting them across networks in an attempt to centralize it. However, in an era where global data amounts to hundreds of exabytes, this method is now outdated and inefficient. In addition, secure access to this data is essential, guaranteeing that only authorized individuals can interact with it without risking its integrity or security.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eData retention \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eis a major concern for public sector agencies. Some are required to store security logs for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-hosted-data-retention-government-compliance\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e365 days or longer\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Ten or twenty years ago, this was manageable, but today’s data explosion makes traditional storage models impractical. Agencies generate terabytes of data daily, and duplicating all of it into a central repository is neither cost-effective nor scalable.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key considerations for public sector when implementing Zero Trust","_metadata":{"uid":"csccee21633cb36183"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA successful Zero Trust strategy depends on an organization’s ability to see and secure all its data. Seamless information discovery enhances user experience, while real-time monitoring, resilient storage, and unified security visibility strengthen defenses. By integrating these elements, agencies can balance security with efficiency and maintain a proactive security posture.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAgencies must overcome complex legacy environments, usability concerns, data silos, and interoperability issues while ensuring compliance with federal mandates. For instance, in the example of critical infrastructure, Zero Trust adoption must be seamless to avoid service disruptions.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo address these barriers, public sector organizations should:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTake a phased approach\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to implementation, focusing on high-risk areas first\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eInvest in tools for consolidation \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ethat provide cross-platform visibility and real-time analytics\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEnsure \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eZero Trust policies\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e that enhance security\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e without disrupting essential operations\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTypically, organizations purchase security products for two reasons: to reduce risk and to optimize costs. However, there’s more to consider beyond just these factors. Effective security requires not only the right tools but also a strategy that ensures efficiency, scalability, and a strong return on investment.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How Elastic’s capabilities support Zero Trust adoption in the public sector","_metadata":{"uid":"csee5fb7a35ed59185"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic supports public sector agencies worldwide in their Zero Trust strategies by offering a unified data layer that connects isolated data, enabling faster, easier, and more secure access to critical information, regardless of format or location, all without requiring centralization.\u003cbr /\u003e\u003cbr /\u003eBy combining the precision of search with the intelligence of AI, Elastic connects data silos for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-turn-data-into-actionable-insights\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ereal time insights, analysis, and automated actions\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that strengthen \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/operational-resilience-pillars\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eoperational resilience\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, mitigate cybersecurity risks, and improve public sector operational efficiency.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Real-world applications and success stories from Zero Trust implementation","_metadata":{"uid":"cs0bf5c653bcf940cc"},"header_style":"H2","paragraph_l10n":""},{"title_l10n":"Data mesh for US federal agencies","_metadata":{"uid":"cs18bf80ae5b4087f5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor US federal agencies, the Elastic data mesh powers the Continuous Diagnostics and Mitigation (CDM) dashboard, enabling multiple US federal agencies to obtain a unified view of security threats and patterns without transferring data ownership to a central repository. This capability is vital for projects where data visibility is necessary but ownership is distributed.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Unified view across multiple data centers ","_metadata":{"uid":"cs986374010ef87b7f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne public sector customer needed a unified view across two data centers, each generating 2.5 terabytes of security data per day. Their initial plan was to replicate all data, doubling storage costs. However, with Elastic’s cross-cluster search, they eliminated the need for replication, drastically reducing infrastructure complexity and costs. Now, they can access a single pane of glass view from either data center — without duplicating data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why do public sector organizations choose Elastic for Zero Trust?","_metadata":{"uid":"cs6060f4f9adb7fa7f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/observability/tool-consolidation\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTool consolidation\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eA single, unified platform for search, security, observability, and analytics\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStorage costs savings: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eEnables frozen tier storage for cost-effective \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-hosted-data-retention-government-compliance\"\u003e\u003cspan style='font-size: 12pt;'\u003elong-term data retention\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, without sacrificing searchability\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOpen, transparent, and flexible: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eBuilt on an open source foundation, offering flexibility and adaptable licensing to avoid dependence on a single provider\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIntegration capabilities: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eSeamlessly integrates with third-party tools and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\"\u003e\u003cspan style='font-size: 12pt;'\u003elarge language models (LLMs)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for compatibility with existing systems\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCost-effective scaling: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eDesigned for easy scalability to meet growing data needs, making it suitable for businesses of all sizes\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eComprehensive support: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eOffers a wealth of support resources, including detailed documentation, training programs, and active community forums\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eElastic helps public sector organizations \u003c/span\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003e\u003cstrong\u003esecure critical data, improve operational resilience, and streamline compliance efforts\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eReady to learn more? Watch our webinar: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/missing-piece-zero-trust-strategy\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eThe missing piece of your Zero Trust strategy\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExplore additional Zero Trust resources:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eDeep dive into the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eFor further reading and hands-on workshops, visit \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security-labs\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security Labs\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eIf you are starting with your Zero Trust strategy, check out: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/zero-trust\"\u003e\u003cspan style='font-size: 12pt;'\u003eWhat is Zero Trust?\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eWhite paper: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/es/does-your-zero-trust-strategy-have-a-unified-data-access-layer\"\u003e\u003cspan style='font-size: 12pt;'\u003eDoes your Zero Trust strategy have a unified data access layer?\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-provides-the-foundation-for-the-dods-pillars-of-zero-trust-networking\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic provides the foundation for the DoD's pillars of Zero Trust Networking\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(49, 51, 63);font-size: 12pt;'\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/querying-a-petabyte-of-cloud-storage-in-10-minutes\"\u003e\u003cspan style='font-size: 12pt;'\u003eQuerying a petabyte of cloud storage in 10 minutes\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/cloud/cloud-trial-overview/security?plcmt=hero\u0026pg=en-security-page\"\u003e\u003cspan style='font-size: 12pt;'\u003eStart your journey with Elastic today with a 14-day free trial\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"","_metadata":{"uid":"csa4556eae62cfecb3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1187b9618657328e"}}}],"publish_date":"2025-03-11","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"How public sector agencies can solve Zero Trust challenges and break down silos with a unified data layer","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltc5bbc20e390f300b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-11T01:51:27.090Z","created_by":"blte369ea3bcd6ac892","file_size":"144273","filename":"Blog_Header_Image_The_Missing_Piece_175402.jpg","parent_uid":null,"tags":[],"title":"Blog Header Image The Missing Piece 175402.jpg","updated_at":"2025-03-11T01:51:27.090Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-11T15:00:03.848Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc5bbc20e390f300b/67cf971fb8764e771be8d4d6/Blog_Header_Image_The_Missing_Piece_175402.jpg"},"title":"The missing piece of your Zero Trust strategy: A unified data layer","title_l10n":"The missing piece of your Zero Trust strategy: A unified data layer ","updated_at":"2025-03-11T02:04:39.460Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/missing-piece-zero-trust-data-layer","publish_details":{"time":"2025-03-11T15:00:03.831Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt21ab91b446588c5b","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"From customer-facing search boxes to database search crawlers, enterprise search technology can strengthen cybersecurity threat and risk management","author":["bltd2df0da99707cbf2"],"category":["bltc17514bfdbc519df"],"created_at":"2022-05-16T07:33:14.459Z","created_by":"bltac225ac457fe0293","markdown_l10n":"","modular_blocks":[{"callout":{"title_l10n":"CISO takeaways","_metadata":{"uid":"cseba173c1509f830b"},"paragraph_l10n":"\u003cul\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eMany enterprises still don’t have a clear or full view of their digital assets\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eSearch tools add a new layer of threat detection to existing cybersecurity defenses\u0026nbsp;\u003c/li\u003e\u003cli dir=\"ltr\" aria-level=\"1\"\u003eSearch applications can also help limit the spread of malware\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf11c395a165c8f0c"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003ca href=\"https://www.elastic.co/what-is/data-security\" target=\"_self\"\u003eData security\u003c/a\u003e is increasingly under threat inside the enterprise amid three converging forces: the proliferation of cloud tools and platforms; the many different types of data that they generate, and the need to correlate all of it for analytics.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eWhile \u003c/span\u003e\u003ca href=\"https://www.elastic.co/cloud\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003ecloud platforms\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e are the critical infrastructure for how technology teams scale and operate today, many companies still don’t have a clear or complete view of all their digital assets in this emerging environment. Advanced \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003eenterprise search capabilitie\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003es, however, can eliminate blind spots and add an important layer of cybersecurity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e“Today, enterprises need to be able to query their environment, and they need to be able to query their data,” says Katie Teitler, senior product marketer at Axonius, a cybersecurity asset management company, and former research chief at TAG Cyber. “They need the ability to have a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003efull-stack view\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e of what’s going on in the network. Without good visibility or search capabilities, they can’t identify and address vulnerabilities.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThat is an important advantage of modern enterprise search. They use machine learning algorithms, natural language processing (NLP) capabilities, and other tools to better understand context and meaning from a wider array of data types and formats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eHere’s a look at three strategies to leverage advanced search to improve security.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eDefine search queries for security needs\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eEffectively searching databases can help enterprises address a range of security concerns, such as risks associated with system integrations, outside attacks, and insider threats. But security teams need to identify and refine their search targets.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e“Organizations must \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-build-and-lead-a-data-driven-organization-and-why-it-matters\" target=\"_self\"\u003econtextualize security data\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e within a business context,” says Jon Oltsik, senior principal analyst and ESG fellow at Enterprise Strategy Group, an IT research and strategy firm. “When I’m investigating suspicious behavior, I may be extra diligent if this behavior takes place in business-critical applications or data,” he says. To search for insider threats, Oltsik adds, security analysts “need to collect data on user access patterns so they can detect anomalous behavior.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eData can help identify if an asset has a known vulnerability, and it can help identify potentially vulnerable devices on a network. “I can find answers to all these questions if I have the data and I have the right query capabilities,” Oltsik says.\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eUse search to accelerate and refine threat detection\u0026nbsp;\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eSearch tools can also help limit the damage of malware attacks. For example, in December 2021, a \u003c/span\u003e\u003ca href=\"https://www.cisa.gov/uscert/ncas/alerts/aa21-356a\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003ecritical security vulnerability\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e was identified in Apache Log4j, a Java tool used by countless applications for recording events into error logs. The vulnerability, called Log4Shell, allowed attackers to \u003c/span\u003e\u003ca href=\"https://www.washingtonpost.com/technology/2021/12/20/log4j-hack-vulnerability-java/\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003erun malicious software\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e, or even potentially take over, a server running Log4j. The challenge for CISOs continues to be how ubiquitous Log4j is.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e“There are millions of applications and services running this library,” explains Mandy Andress, CISO at Elastic. “Dependencies were not easily identifiable, so it was really hard to even tell if you were impacted, if you needed to upgrade, if you needed to patch, or if you didn’t have any issues whatsoever.”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThat’s where robust search came into play. Elastic knew its systems and assets could be vulnerable. And by working with partners and SaaS providers, its InfoSec team was able to identify thousands of potential security holes. But were those vulnerabilities being exploited?\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eThe team then put search to work and was able to search vast amounts of data in mere seconds. A cursory search, across 60 clusters and a petabyte of data, took only 10 seconds, says Andress. A second and more targeted query, based upon those initial findings, delivered another set of results in less than a minute. In the past, that kind of searching could have taken days or even weeks — at which point additional risks would have been identified. Instead, Elastic was able to deploy patches and upgrades within a few hours.\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eRead: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/why-cybersecurity-needs-to-be-everyones-job-and-4-steps-to-get-started\" target=\"_self\"\u003e\u003cstrong\u003eWhy cybsersecurity needs to be everyone's job\u003c/strong\u003e\u003c/a\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003eIncorporate search into long-term security strategy\u003c/strong\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eAttackers have continued to probe other widely used resources. “These attackers are going for the largest targets they can,” says Teitel.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eExisting vulnerabilities will remain risks. “We’ll be seeing attacks in the future that are successful because there are unpatched and still vulnerable Log4j versions out there,” Andress says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eAll of which makes search platforms an increasingly important tool for CISOs. “You can’t just say, ‘What’s in my environment today?’” says Teitel. “You have to search over time: ‘Where was I on April 1? Where am I now on May 1? Where will I be on June 1?”\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eIt’s all part of a game of catch-up with attackers that security teams must continue to improve on, because the volume and complexity of threats will only increase. “Attackers have a lot of patience,” adds Teitel. “Time is on their side.”\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/cybersecurity-solutions-riskier-world?rogue=ebook\u0026baymax=\u0026storm=footer\u0026elektra=socialmedia\" target=\"_self\"\u003e\u003cstrong\u003eCheck out our special report on cybersecurity solutions for a riskier world\u003c/strong\u003e\u003c/a\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaabbbcfbd7416d71"}}}],"publish_date":"2022-05-16T07:22:30.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltac352930d0bd6c7f","ACL":{},"created_at":"2023-11-06T21:36:27.692Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"xdr","label_l10n":"XDR","tags":[],"title":"XDR","updated_at":"2023-11-06T21:36:27.692Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.167Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt518d58c000517b46","created_by":"bltac225ac457fe0293","updated_by":"bltac225ac457fe0293","created_at":"2022-05-16T07:29:10.559Z","updated_at":"2022-05-16T07:29:10.559Z","content_type":"image/jpeg","file_size":"202793","filename":"search-security-1440x840.jpg","title":"search-security-1440x840.jpg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-16T07:44:49.869Z","user":"bltac225ac457fe0293"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt518d58c000517b46/6281fd46a4aac35766f2f0c2/search-security-1440x840.jpg"},"title":"Cybersecurity is a data challenge, and better search technology is key to improving visibility and action","title_l10n":"Cybersecurity is a data challenge, and better search technology is key to improving visibility and action","updated_at":"2025-03-10T09:00:39.945Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/cybersecurity-is-a-data-challenge-and-better-search-technology-is-key-to-improving-visibility-and-action","publish_details":{"time":"2025-03-10T09:00:46.894Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt42e310ee99655fa4","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic recently conducted a survey of telco industry leaders. Here are a few top insights on how they're using data and AI to address business challenges and meet their goals.","author":["blte520dce49f64b517"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-05T00:28:58.688Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3f32cbacd22f5d72"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eThe telecommunications industry is at the forefront of innovation and connectivity, often setting high standards and expectations for customers’ digital experiences. Now, as AI moves past its buzzword phase, telco leaders have been steadily integrating AI into their businesses, further advancing their ability to respond to customer needs and provide high standards of service.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eAt the core of these digital experiences — especially AI — is the ability to strategically use data to meet business goals.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"The importance of data in telecommunications","_metadata":{"uid":"cseabcf7b036a39225"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eTelco companies generate and handle enormous volumes of data daily. This data includes call records, network performance metrics, customer interactions, and more. Efficiently managing and analyzing this data is essential for:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003cstrong\u003eOptimizing network performance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eBy analyzing network data, telco companies can identify and resolve issues quickly, ensuring a seamless experience for their operations and their customers.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003cstrong\u003eEnhancing customer experience:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e Understanding customer behavior and preferences through data analysis helps companies provide more personalized services and boost customer satisfaction.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003cstrong\u003eFraud detection and prevention: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eAnalyzing call patterns and usage data can help to detect fraudulent activities and prevent potential losses.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"","_metadata":{"uid":"csf2ce700ac1a0a009"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eDespite leaders aspiring to build data-driven organizations, the reality is that \u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e\u003cstrong\u003e70% of leaders in telecommunications, technology, and media and entertainment industries still struggle to utilize data continuously — in real time and at scale\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e. Many industry leaders are tackling this gap by using AI and generative AI. But to reach that level of advanced maturity where AI can have maximum value, companies first need a strong data foundation. Going back to data fundamentals ensures that businesses can manage, access, and use exponentially growing data volumes, all while dealing with complex business challenges.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eElastic and Socratic Technologies surveyed 1,005 C-suite, business, and technology leaders on the current state of their business. This research — with data and results specifically from 326 telecommunications, technology, and media and entertainment leaders — highlights several recurring insights about how telco leaders approach business challenges, underlying data problems, and investment priorities (AI, generative AI, and automation) for the near future.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eBelow, we’ll explore a couple of these insights from the report.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Solving data challenges can solve business challenges","_metadata":{"uid":"cs7f545ab79501d2e7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUnderlying data challenges can hinder telco companies’ ability to access critical information for informed real-time decision-making. Without the ability to access relevant data and insights in real time, companies are experiencing consequences such as misinformed and delayed responses to market shifts, customer needs, and operational issues. These challenges can ultimately lead to revenue loss, lowered productivity, heightened risk exposure, decreased customer satisfaction, and escalating operational costs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003eAs one telecommunications C-suite leader noted in the survey, “T\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ehe sheer volume and velocity of incoming data overwhelm traditional processing infrastructures, leading to latency issues and hindering timely decision-making processes.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAcross the board, the study found that leaders are having difficulty getting actionable insights from their data. According to the C-suite executives and decision-makers,\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e 59% are unsatisfied with the data insights they have today, and only 34% are leveraging data insights daily for business decisions\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo solve this problem, executives and leaders are prioritizing data analytics and data science tools as their top technology investment, as noted by 61% of respondents. As companies work toward becoming true data-driven businesses, it’s important to know how and if the tools and systems in their IT environments are able to provide a single, holistic, and connected view of all data types, across their business. Otherwise, it can be easy to run into data sprawl and tool sprawl and lack a “single pane of glass” that multiple teams can rely on for their data-centric use cases.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs53d3a5059561fafb"}}},{"banner":{"reference":[{"uid":"blta3ffaaba0b6a0bd1","_content_type_uid":"banner"}],"_metadata":{"uid":"cs8f97bc9d917ddf26"}}},{"title_text":{"title_text":[{"title_l10n":"GenAI is making an impact, fast","_metadata":{"uid":"cs23e1b47019b97385"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor telco leaders, generative AI is much more than a buzzword, with \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e88% of C-suite executives planning to invest in or having already invested in generative AI\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTelcos are using generative AI for use cases such as customer service chatbots, network optimization, inventory allocation, customer sentiment analysis, and more.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHowever, as seen in the above findings around data utility, the impacts of generative AI will only be as helpful as the data behind it. Being able to organize, access, and analyze all your data — structured and unstructured — with a single tool is essential, especially for telcos using a retrieval augmented generation (RAG) model. In that case, information would first be gathered from your proprietary data for critical context before being passed to a large language model (LLM).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWithout the ability to quickly organize and make sense of all data types in one platform, generative AI will be basing its outputs on incomplete, outdated, or inaccurate information. That’s why it’s critical to spend some time on your data strategy and making sure your entire teams are working with the same tools and information.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Learn more about data and AI in telco","_metadata":{"uid":"csc085ff43021d0c54"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLearn what else telco leaders had to say about data and AI by \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/portfolio/report/solving-business-challenges-data-ai-telecommunications\"\u003e\u003cspan style='font-size: 12pt;'\u003edownloading the full study\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csb1bfb64708ccca81"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third-party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third-party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4fe927d7b42d75cf"}}}],"publish_date":"2025-03-07","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_partner":[],"tags_topic":[{"title":"Customer experience","label_l10n":"Customer experience","keyword":"customer-experience","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt25722919b3bca233","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:27.803Z","updated_at":"2021-12-16T22:34:27.803Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.021Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt5ebb3c17304b01bc","ACL":{},"created_at":"2023-11-06T20:47:38.117Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"privacy-first-ai","label_l10n":"Privacy-first AI","tags":[],"title":"Privacy-first AI","updated_at":"2023-11-06T20:47:38.117Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:58.404Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4732ba20ad170771","ACL":{},"created_at":"2023-11-06T20:48:01.608Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"public-multi-hybrid-cloud","label_l10n":"Public, multi \u0026 hybrid cloud","tags":[],"title":"Public, multi \u0026 hybrid cloud","updated_at":"2023-11-06T20:48:01.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:51.878Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt2555bd3a8871e1aa","_version":1,"title":"blogheaderimage_TelcoIT_175403_.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-07T23:00:55.838Z","updated_at":"2025-03-07T23:00:55.838Z","content_type":"image/jpeg","file_size":"121863","filename":"blogheaderimage_TelcoIT_175403_.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-07T23:03:37.425Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2555bd3a8871e1aa/67cb7aa78c6f4e4b68b842ac/blogheaderimage_TelcoIT_175403_.jpg"},"title":"AI in the telecommunications industry: Overcoming foundational data challenges","title_l10n":"AI in the telecommunications industry: Overcoming foundational data challenges","updated_at":"2025-03-08T00:09:56.348Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/ai-telecommunications-industry-overcoming-data-challenges","publish_details":{"time":"2025-03-08T00:10:05.655Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4656b13e4df19c1f","_version":21,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic has been recognized as a Customers’ Choice in the 2021 Gartner Peer Insights ‘Voice of the Customer’: Security Incident and Event Management (SIEM) report with an overall rating of 4.6 out of 5.","author":["bltb0cc3d711c5c0b3a","blt0dbe04e5acc0f969"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2021-12-03T21:05:07.519Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs39397031c225b7ff"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElastic has been recognized as a Customers’ Choice in the 2021 \u003cem\u003eGartner Peer Insights ‘Voice of the Customer’: Security Incident and Event Management \u003c/em\u003e(\u003cem\u003eSIEM) \u003c/em\u003ereport with an overall rating of 4.6 out of 5 based on 51 reviews as on November 25, 2021.\u003c/p\u003e\u003cp\u003eThe report combines the feedback and experiences of more than 51 \u003ca href=\"https://www.elastic.co/security\"\u003eElastic Security\u003c/a\u003e customers on Gartner Peer Insights™. Elastic’s \u003cem\u003eWillingness to Recommend\u003c/em\u003e score was 98% — the highest of all vendors included in the report.\u003c/p\u003e\u003cp style=\"max-width: 225px;\"\u003e\u003cimg data-image=\"4fc839eftaz9\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt941e632c7863eb19/61aa902f47c677586bb0327f/gartner-peer-insights.jpg\" data-sys-asset-uid=\"blt941e632c7863eb19\" alt=\"gartner-peer-insights.jpg\" width=\"225\" height=\"131\" style=\"width: 225;max-width: 225px;height: 131;\"/\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003eElastic appreciates the wonderful community of security practitioners that use Elastic Security as their SIEM solution, and how readily they provide us with feedback to help make our solution even better.\u003cbr /\u003e\u003c/p\u003e\u003ch2\u003eWhat customers have to say\u003c/h2\u003e"}],"_metadata":{"uid":"cs05f1eb0894596acb"}}},{"quotes":{"quote_l10n":"\"This product is already very mature and the expected features are going in the right direction. We were able to improve our security considerably with it.\"","_metadata":{"uid":"cs8029d5167d05fb0a"},"quote_author_l10n":"\u003ca href=\"https://www.gartner.com/reviews/market/security-information-event-management/vendor/elasticsearch/product/elastic-siem/review/view/3846224\"\u003eSenior Security Manager in the Services industry\u003c/a\u003e","quote_details_l10n":""}},{"quotes":{"quote_l10n":"“The solution provides fast and accurate insight across all the different apps and systems. With the built in tools and functionality correlating events across the environment is really easy and together with the rest of the stack our SOC can continuously monitor, investigate and respond in an intuitive and fast flow.”","_metadata":{"uid":"cs54a606867696f567"},"quote_author_l10n":"\u003ca href=\"https://www.gartner.com/reviews/market/security-information-event-management/vendor/elasticsearch/product/elastic-siem/review/view/3783118\"\u003eTechnical Lead Security Monitoring in the Services industry\u003c/a\u003e","quote_details_l10n":""}},{"quotes":{"quote_l10n":"\"You can't beat the speed and price. Great experience especially with how fast new features are being released. The search speed is incredible that no other product can compete with. Easy to scale and easy to have 100% availability due to distributed architecture.\"","_metadata":{"uid":"cs130dd250a83d1633"},"quote_author_l10n":"\u003ca href=\"https://www.gartner.com/reviews/market/security-information-event-management/vendor/elasticsearch/product/elastic-siem/review/view/3782034\"\u003eSenior Security Analyst in the Communications industry\u003c/a\u003e","quote_details_l10n":""}},{"quotes":{"quote_l10n":"“Have displaced a number of legacy SIEM products, being able to provide longer retention, higher ingest rate and at a reduced price point. Plenty of non vendor training options available that use Elastic as their tool of choice for training making it a great choice for SOCs.”","_metadata":{"uid":"cs2c85417b3d33f35c"},"quote_author_l10n":"\u003ca href=\"https://www.gartner.com/reviews/market/security-information-event-management/vendor/elasticsearch/product/elastic-siem/review/view/3781878\"\u003eIT Security Manager in the Manufacturing industry\u003c/a\u003e","quote_details_l10n":""}},{"quotes":{"quote_l10n":"\"Great option to scale to your needs without blowing your budget - The new wave of SIEM in general is quickly evolving, but I see the most potential to really bring everything together well with Elastic.\"","_metadata":{"uid":"cs20df988a006d7dae"},"quote_author_l10n":"\u003ca href=\"https://www.gartner.com/reviews/market/security-information-event-management/vendor/elasticsearch/product/elastic-siem/review/view/3781786\"\u003eSr InfoSec Ops Engineer in the Retail industry\u003c/a\u003e","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8ca998ffbbd7830a"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eAbout the Gartner Peer Insights Voice of the Customer Report\u003c/h2\u003e\u003cp\u003eCustomer feedback is truly a gift and we are honored. The report is a document that synthesizes Gartner Peer Insights’ reviews into insights for IT decision makers.\u003c/p\u003e\u003cp\u003eGartner Peer Insights is a free peer review and ratings platform designed for enterprise software and services decision makers. Reviews go through a strict validation and moderation process in an effort to ensure they are authentic. The “\u003cem\u003eVoice of the Customer\u003c/em\u003e” document only includes vendors with 20 or more eligible published reviews during the specified 18-month submission period. Reviews from end users of companies with less than $50M in revenue are excluded from this methodology.\u003c/p\u003e\u003cp\u003eVendors placed in the upper-right quadrant of the “Voice of the Customer” quadrants are recognized with the Gartner Peer Insights Customers’ Choice distinction, denoted with a Customers’ Choice badge. The recognized vendors meet or exceed both the market average Overall Rating and the market average User Interest and Adoption.\u003c/p\u003e\u003cp\u003eElastic overall scored as follows:\u003c/p\u003e\u003cul\u003e\u003cli\u003eProduct capabilities (4.5 out 5) based on 49 responses\u003c/li\u003e\u003cli\u003eSales experience (4.5 out of 5) based on 42 responses\u003c/li\u003e\u003cli\u003eDeployment experience (4.5 out of 5) based on 48 responses\u003c/li\u003e\u003cli\u003eSupport experience (4.5 out of 5) based on 46 responses\u003c/li\u003e\u003cli\u003eWillingness for customers to recommend (98%) based on 51 responses\u003c/li\u003e\u003cli\u003e4.6 out of 5 overall rating from customers based on 51 responses\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eThanks to our Elastic Security Community\u003c/h2\u003e\u003cbr /\u003e\u003cp\u003eThe Elastic Security team is motivated by a vision to help protect the world’s data. Our software developers, security researchers, rule developers, data scientists, data engineers, Linux internal experts, product designers, quality assurance, user experience pros, and product managers all strive to bring deep security expertise to Elastic users through the Elastic Security solution.\u003c/p\u003e\u003cp\u003eThe SIEM capability is a key component of Elastic Security, built into the Elastic Stack, along with Endpoint Security and integrations that help identify security events as well as simplify and automate workflows necessary for efficient security operations.\u003c/p\u003e\u003cp\u003eWe are extremely pleased that Elastic Security is helping our SIEM users protect their organizations’ data and systems against cyber threats. We are thankful to our community of users for sharing their feedback, including their successes and challenges, with Elastic, their peers. Join our \u003ca href=\"https://www.elastic.co/community/\"\u003eElastic community\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eNot using Elastic Security yet? Take a look at one of our \u003ca href=\"https://www.elastic.co/webinars/unlock-your-soc-stop-threats-with-limitless-xdr\"\u003elatest demos\u003c/a\u003e and \u003ca href=\"https://cloud.elastic.co/registration\"\u003etry it free\u003c/a\u003e (no credit card required).\u003c/p\u003e\u003cp\u003e*Gartner, “\u003cem\u003eGartner Peer Insights Voice of the Customer: Security Incident and Event Management”, \u003c/em\u003ePeer Contributors, November 25, 2021.\u003c/p\u003e\u003cp\u003eGartner Disclaimer:\u003c/p\u003e\u003cp\u003e\u003cem\u003eGartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.\u003c/em\u003e\u003c/p\u003e\u003cem\u003eThe Gartner Peer Insights Customers’ Choice badge is a trademark and service mark of Gartner, Inc., and/or its affiliates, and is used herein with permission. All rights reserved. Gartner Peer Insights Customers’ Choice constitute the subjective opinions of individual end-user reviews, ratings, and data applied against a documented methodology; they neither represent the views of, nor constitute an endorsement by, Gartner or its affiliates.\u003c/em\u003e"}],"_metadata":{"uid":"cs15c83991c05bfea6"}}}],"publish_date":"2021-12-09T20:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"title":"SIEM","label_l10n":"SIEM","keyword":"siem","hidden_value":false,"tags":[],"locale":"en-us","uid":"blta7a92715fa2dc7aa","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-07-12T21:52:53.275Z","updated_at":"2021-07-12T21:52:53.275Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-07T18:59:30.492Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt64ac6f0006f42861","ACL":{},"content_type":"image/png","created_at":"2021-05-05T14:26:05.870Z","created_by":"blt3e52848e0cb3c394","file_size":"111765","filename":"blog-security-timeseries-radar-720x420.png","tags":[],"title":"blog-security-timeseries-radar-720x420.png","updated_at":"2021-05-05T14:26:05.870Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-05-13T22:00:14.883Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt64ac6f0006f42861/6092aafd162d47104df4b8b9/blog-security-timeseries-radar-720x420.png"},"title":"Elastic Security was recognized as a Customers’ Choice in 2021 Gartner Peer Insights ‘Voice of Customer’: SIEM Report","title_l10n":"Elastic Security was recognized as a Customers’ Choice in 2021 Gartner Peer Insights ‘Voice of Customer’: SIEM Report","updated_at":"2025-03-07T16:01:46.693Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elastic-security-recognized-customers-choice-gartner-peer-insights-report","publish_details":{"time":"2025-03-07T16:01:50.381Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt796edd8c52d4fcf7","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"CISOs must rethink how to manage cyber risk as an organizational priority.","author":["blteeb004d031583a0e"],"category":[],"created_at":"2021-10-29T16:14:15.940Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"callout":{"title_l10n":"","_metadata":{"uid":"csb4a770a8c2de9a47"},"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eKey takeaways:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cul\u003e\u003cli\u003eCyber risks aren’t exotic threats; they are just another form of business risk\u003c/li\u003e\u003cli\u003eCISOs should focus budgets first on people and processes, and then on technology\u003c/li\u003e\u003cli\u003eFostering a culture of openness around security helps organizations better accept and manage risk\u003c/li\u003e\u003c/ul\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7f897a603d921d48"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eEach year, companies pour more money into their cybersecurity budgets — more than $\u003ca href=\"https://cybersecurityventures.com/cybersecurity-spending-2021-2025/\"\u003e262 billion\u003c/a\u003e collectively in 2021, up from just $3.5 billion about 20 years ago. Yet every year, the attacks, breaches, and losses continue to increase. Employing the same tactics while expecting different results is not a rational approach to managing cybersecurity risk.\u0026nbsp;\u003c/p\u003e\u003cp\u003eSome security tactics, of course — defining acceptable levels of risk, using liability insurance to transfer some of that risk, and mitigating damage when it happens — remain important in reducing the impact of attacks. Yet, business leaders need to rethink their organizational strategy. Enterprise security is too important to be the sole purview of a handful of specialists, as it has been for years. It needs to be enmeshed into everyone's job around the enterprise.\u0026nbsp;\u003c/p\u003e\u003cp\u003eHere are four strategies CISOs should consider to help put cyber risk management on a better path.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003e1. It’s time to normalize cybersecurity risk\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eFirst, organizations must change how they think about cyber risks. Cyberattacks have traditionally been seen as a unique, exogenous threat, separate from other aspects of corporate risk management. That needs to change.\u0026nbsp;\u003c/p\u003e\u003cp\u003eCyber risk \u003cem\u003eis\u003c/em\u003e business risk. It needs to be incorporated into every company’s risk-management framework and managed with some of the same methodologies used in financial and operational risk modeling. If CFOs and COOs can sleep decently at night, so too should their security peers in the C-suite.\u003c/p\u003e\u003cp\u003eIn many ways, cybersecurity is not a technology problem, it’s an organizational one. Security processes should be as fundamental to the enterprise as those for onboarding employees or designing great customer experiences. They need to receive the same consideration as every other necessary business function, along with commensurate funding and headcount.\u0026nbsp;\u003c/p\u003e\u003cp\u003eSecurity also needs to be more proactive and less reactive. Just as a company wouldn’t wait to hire sales staff until after a product launch, it shouldn’t wait for a major incident before it funds a cybersecurity team and puts the right processes in place.\u003c/p\u003e\u003cp\u003eIt’s a given that organizations will continue to endure serious breaches; the more important question is whether they took reasonable measures to prevent them, and how effectively they respond.\u0026nbsp;\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003e2. Focus on people, processes, and technology — in that order\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eNext, CISOs need to reconsider where they’re focusing their resources. Their budgets should follow a clearly defined set of priorities, and tech should — in most cases — not be at the top. The first priority is people, and that means investing in training your employees in proper security hygiene, in teaching and reskilling your teams, and in strengthening a security culture.\u003c/p\u003e\u003cp\u003eThe next spending priority should be internal processes. How thoroughly, for example, has the organization rehearsed what it will do in the event of a ransomware attack? Internal and external communications, operational continuity planning, and how (or whether) to engage with the attackers are all best planned before the crisis hits.\u003c/p\u003e\u003cp\u003eThird, only \u003cem\u003eafter\u003c/em\u003e the most pressing issues around people and processes have been addressed, should CISOs invest in technology tools to help reduce and manage threats.\u0026nbsp;\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003e3. More carrots, fewer sticks\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eNearly 9\u003ca href=\"https://cisomag.eccouncil.org/psychology-of-human-error-could-help-businesses-prevent-security-breaches/\"\u003e in 10\u003c/a\u003e data breaches are the result of human error, according to a recent study by Stanford University researchers. And despite the more than $1 billion that companies spend annually on security awareness training, that’s unlikely to change. Companies need to find new ways to reward good security practices.\u003c/p\u003e\u003cp\u003eShaming employees for security slipups, for instance, doesn’t make them more vigilant. More often than not, it just scares them into silence and makes them less likely to speak up. Or they may try to solve the problem on their own and unknowingly make it worse. If they work in a highly regulated industry, that can lead to sanctions.\u003c/p\u003e\u003cp\u003eInstead, organizations need to foster a culture of openness around security, encouraging employees to ask questions and raise red flags. Some companies send out simulated phishing attacks and reward employees who successfully identify them with gift cards and other perks. Others offer public recognition for employees who pass the required security training. Nearly any form of positive acknowledgment is a step in the right direction.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003e4. Make security tools easier to use\u003c/strong\u003e\u003c/h2\u003e\u003cp\u003eMuch of the billions of dollars companies spend on security technology goes toward shelfware that never gets used. In many cases, these are complicated tools that require experts who understand how to use them, and such people are in short supply. With a \u003ca href=\"https://www.zdnet.com/article/the-cybersecurity-jobs-crisis-is-getting-worse-and-companies-are-making-basic-mistakes-with-hiring/\"\u003esecurity labor shortage\u003c/a\u003e that isn’t going away soon, according to the Information Systems Security Association (ISSA) and industry analyst firm Enterprise Strategy Group (ESG), security tech must become easier to use.\u003c/p\u003e\u003cp\u003eSimpler tools would not only enable CISOs to hire more people to handle essential security functions, but also they would open up the workforce to a more diverse array of individuals with different backgrounds and tech expertise. Engineers also need to spend more time providing easy-to-understand dashboards that allow senior executives and other less technical people to understand the current state of risk.\u003c/p\u003e\u003cp\u003eOne of the reasons that my company, Elastic, offers a free and open technology stack is to encourage and enable a vibrant community of contributors. We also believe that opening products to the broader audience of developers makes them more secure.\u003c/p\u003e\u003cp\u003eEnterprise security cannot remain a siloed function handled by a crew of specialists. It needs to be part of everyone’s responsibilities. Making it so can help companies move beyond simply reacting to crises and into a new paradigm where they manage cybersecurity efficiently, like any other risk.\u003c/p\u003e\u003cp\u003e\u003cem\u003eNate Fick is the VP of Security Strategy\u0026nbsp;at Elastic.\u003c/em\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7e639a3fcdf0dbfc"}}}],"publish_date":"2021-11-04T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Why cybersecurity needs to be everyone’s job–and 4 steps to get started","seo_description_l10n":"CISOs must rethink how to manage cyber risk as an organizational priority.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"CISOs must rethink how to manage cyber risk as an organizational priority.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blte0dda6da06a373ab","ACL":{},"content_type":"image/jpeg","created_at":"2021-11-04T00:02:58.661Z","created_by":"blt1e57c6588ae1816e","file_size":"149200","filename":"Normalization_v2_1440x840.jpg","parent_uid":null,"tags":[],"title":"Normalization_v2_1440x840.jpg","updated_at":"2021-11-04T00:02:58.661Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-08T20:00:00.732Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte0dda6da06a373ab/61832332ffff3679072221d6/Normalization_v2_1440x840.jpg"},"title":"Why cybersecurity needs to be everyone’s job–and 4 steps to get started","title_l10n":"Why cybersecurity needs to be everyone’s job–and 4 steps to get started","updated_at":"2025-03-07T13:01:13.326Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/why-cybersecurity-needs-to-be-everyones-job-and-4-steps-to-get-started","publish_details":{"time":"2025-03-07T13:01:17.342Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltecbae6a1e237690a","_version":22,"locale":"en-us","ACL":{},"abstract_l10n":"Observing Kubernetes deployments can be a challenge for an SRE or IT operations professional, but it all starts with the basics: knowing which components are observable, what can be observed, and how to understand and use that telemetry data. ","author":["blt5bd19cc24d46cd2f"],"category":["bltb79594af7c5b4199"],"created_at":"2022-11-08T19:32:11.758Z","created_by":"blt469f34057b68c377","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6754944989345e5b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAn avid bird-watcher once told me that for bird-watching beginners, it’s more important to focus on learning about the birds and identifying their unique songs rather than trying to find the perfect pair of binoculars.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8fb9f1f8603b253d"}}},{"image":{"image":{"uid":"bltaa54b5b2131fe6ca","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-09T15:07:17.448Z","updated_at":"2022-11-09T15:07:17.448Z","content_type":"image/jpeg","file_size":"865874","filename":"observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg","title":"observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:22.888Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaa54b5b2131fe6ca/636bc2252e16be076e6df481/observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg"},"_metadata":{"uid":"cs4c83c0aa3007c534"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3d66025af19470b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne of the aspects that makes Kubernetes such an interesting and dynamic system to observe is that unlike many other pieces of technology, it is not just one big bird always singing the same song but a group of different bird species who happen to sing a variety of amazing songs.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing these metaphors around bird-watching relates well to Kubernetes observability. Let's first learn about the equivalent Kubernetes birds we can observe by looking at the key Kubernetes components and start exploring their bird songs by understanding which signals each one emits.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn this blog, we will focus on observing the infrastructure of Kubernetes over observing applications deployed on Kubernetes, giving us a view from the perspective of a Kubernetes cluster administrator.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2\u003eWhat is observable in Kubernetes?\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKubernetes has four main components that we need to be aware of in order to understand what we will be observing: the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003econtrol plane, nodes, pods, and containers\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8b02526932bcf0b2"}}},{"image":{"image":{"uid":"blt7c73df35b00d1632","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-08T19:29:05.366Z","updated_at":"2022-11-08T19:29:05.366Z","content_type":"image/png","file_size":"47653","filename":"kubernetes-diagram-720x420_2x.png","title":"kubernetes-diagram-720x420_2x.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:22.914Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7c73df35b00d1632/636aae01358231185a7a828d/kubernetes-diagram-720x420_2x.png"},"_metadata":{"uid":"cs707a8fc190ae5fa1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9bc876471ee131cb"},"header_style":"H2","paragraph_l10n":"\u003ch3 style=\"text-align: justify;\"\u003eMonitoring the Kubernetes control plane\u0026nbsp;\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis is a machine (virtual or physical) comprising a collection of items that are mainly focused on dealing with Kubernetes being an orchestrator. The key element of the control plane is the kube-apiserver, and the data we can get through it will enable us to best understand the overall status of the cluster.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eControl plane elements observable through the kube-apiserver are:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli style=\"font-size: 12pt;\"\u003eetcd: \u003cspan style=\"font-size: 12pt;\"\u003ea distributed key value pair database used as a backing store for cluster data\u003c/span\u003e\u003c/li\u003e\u003cli style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ekube-scheduler: the controller responsible for deciding which node to place new pods in\u003c/span\u003e\u003c/li\u003e\u003cli style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ekube-controller-manager: runs all controller processes; logically controllers are separate but to reduce complexity they’re bundled into a single binary and process\u003c/span\u003e\u003c/li\u003e\u003cli style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecloud-controller-manager: the controller responsible for interacting with cloud provider resources via the cloud provider API\u003c/span\u003e\u003cspan\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eA read through the Kubernetes \u003c/span\u003e\u003ca href=\"https://kubernetes.io/docs/concepts/overview/components/#control-plane-components\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is recommended to get into more details of the functions that each of these control plane components is there to perform.\u003c/span\u003e\u003c/p\u003e\u003ch3 style=\"text-align: justify;\"\u003eMonitoring Kubernetes nodes\u0026nbsp;\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNodes give Kubernetes its computing power. They are the (virtual or physical) machines pods run on. Each node contains the following elements:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"font-size: 12pt;\"\u003e\u003c/p\u003e\u003cul\u003e\u003cli style=\"font-size: 12pt;\"\u003ekubelet: an a\u003cspan style=\"font-size: 12pt;\"\u003egent in charge of registering the node with control plane, making sure containers running in each pod are healthy and communicating this information back to the control plane through the kube-apiserver\u003c/span\u003e\u003c/li\u003e\u003cli style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ekube-proxy: a network proxy that runs on each node, making network communication to pods from inside and outside the cluster possible\u003c/span\u003e\u003c/li\u003e\u003cli style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003econtainer\u0026nbsp;runtime: the software that is responsible for running containers\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMore details on each node component can be found in the Kubernetes \u003c/span\u003e\u003ca href=\"https://kubernetes.io/docs/concepts/overview/components/#node-components\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003ch3 style=\"text-align: justify;\"\u003eMonitoring Kubernetes pods and containers\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePods are the smallest deployable computing unit in Kubernetes. We can think of pods as a wrapping for running containers.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe most common model is to have one container per pod, but there can be multiple containers running in a pod for use cases that require them to be tightly coupled or share resources, such as applications with sidecar containers.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eUnderstanding the Kubernetes resource based model\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKubernetes has a declarative model based on resources. The idea is that users provide an intent and Kubernetes acts on that intent to create or modify the resources as requested by the user without requiring further user input.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe will discuss only some examples from the \u003c/span\u003e\u003ca href=\"https://kubernetes.io/docs/reference/kubernetes-api/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efull list of resources\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e available through the Kubernetes API.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch3 style=\"text-align: justify;\"\u003eWorkload resources\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePods can be created using different workload resources, which can provide different patterns of deployment. These can be Deployments, ReplicaSets, StatefulSets, DaemonSets, Jobs, etc.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor example,\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDaemonSets\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eensure that there is an instance of the same pod running on each node.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGrasping \u003c/span\u003e\u003ca href=\"https://kubernetes.io/docs/concepts/workloads/controllers/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edetails of how each workload resource works\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is crucial for a thorough understanding of deployment issues in Kubernetes.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eOther relevant resources\u003c/h3\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003enamespace: a cluster resource that can be used to provide logical boundaries for other resources, enabling a cluster administrator to decide who has access to what or monitoring a group of resources that may be linked with a specific area of the business\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eevent: \u0026nbsp;a report of an event somewhere in the cluster, usually a state change in the system\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eWhat can be observed in each Kubernetes component?\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSimilar to how bird songs are composed of different musical notes, the status of a Kubernetes cluster is derived from the signals it emits. Understanding these signals will get us closer to having music in our ears.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe signals we can get from the Kubernetes components can be categorized within the three pillars of observability: metrics, logs, and traces.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eKubernetes metrics\u0026nbsp;\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMetrics are numerical signals that can help us understand a component's overall behavior over time. For example, we can use metrics to build a dashboard to understand resource usage and answer questions such as “What is the average CPU consumption per pod?”\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd8b1c50691e4dd2c"}}},{"image":{"image":{"uid":"blt252b9d8fbd48eedb","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-09T15:07:39.724Z","updated_at":"2022-11-09T15:07:39.724Z","content_type":"image/jpeg","file_size":"984306","filename":"observingkubernetesbasics-cpuconsumption-3-3.jpeg","title":"observingkubernetesbasics-cpuconsumption-3-3.jpeg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:22.937Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt252b9d8fbd48eedb/636bc23b421feb097ddb607a/observingkubernetesbasics-cpuconsumption-3-3.jpeg"},"_metadata":{"uid":"cs8c1e82035a8713c3"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaa9e7f1cb36cd6da"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMetrics are available in \u003c/span\u003e\u003ca href=\"https://prometheus.io/docs/instrumenting/exposition_formats/\"\u003e\u003cspan style='font-size: 12pt;'\u003ePrometheus format\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which is structured plain text that humans and machines can both read. The majority of Kubernetes components metrics are available on the /metrics endpoint of the HTTP server.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGiven the open source origins of Kubernetes, the Kubernetes community makes the decision to introduce or deprecate metrics as the Kubernetes ecosystem grows and evolves. There is a published \u003c/span\u003e\u003ca href=\"https://github.com/kubernetes/kubernetes/blob/master/test/instrumentation/testdata/stable-metrics-list.yaml\"\u003e\u003cspan style='font-size: 12pt;'\u003elist of stable metrics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to help you stay on top of things.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eKubernetes logs\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLogs are records that help us keep track of what a component is doing at a given time. The information provided by logs when correlated with metrics makes for a powerful combination and provides important insights. While metrics will tell you that a resource is dead, logs will help you understand the exact reason the resource died. The lowest level of logs we can gather from Kubernetes is individual container logs — these are available as standard streams (stdout and stderr).\u003c/span\u003e\u003cbr/\u003e\u003cbr/\u003e\u003cspan style='font-size: 12pt;'\u003eGetting a sneak peek at a pod’s logs using the kubectl cli is as easy as typing the below \u003c/span\u003e\u003ca href=\"https://jamesdefabia.github.io/docs/user-guide/kubectl/kubectl_logs/\"\u003e\u003cspan style='font-size: 12pt;'\u003ekubectl logs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e command.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2f16131b35729ee8"}}},{"code":{"code":"kubectl logs POD ","_metadata":{"uid":"cs90e143e0a57a1106"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3cc3716432df2720"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eExample:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs925b3e6f60383c74"}}},{"code":{"code":"# Return snapshot logs from a pod running Elastic Agent as its only container\n\nkubectl logs elastic-agent-894vs -n kube-system \n","_metadata":{"uid":"cs052a48f30dad6b8c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaba615abbe69010f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe result will contain a number of logs looking similar to the example below.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdbdd11ee58d40d8d"}}},{"code":{"code":"{\"log.level\":\"info\",\"@timestamp\":\"2022-10-03T10:39:28.047Z\",\"log.origin\":{\"file.name\":\"operation/operator.go\",\"file.line\":307},\"message\":\"operation 'operation-start' skipped for filebeat.8.3.1\",\"ecs.version\":\"1.6.0\"}","_metadata":{"uid":"csd539edcd6c056ce5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfa890de0d920cc0c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt is important to be aware that Kubernetes containers’ ephemeral nature means that container logs will only be available for the previous and current instance of a container. Therefore, implementing a cluster-level logging solution is required to guarantee access to logs beyond the lifetime of a pod or even the cluster.\u003c/span\u003e\u003c/p\u003e\u003ch3 style=\"text-align: justify;\"\u003eTraces in Kubernetes\u0026nbsp;\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA trace will record the touchpoints of a request or action as it moves through the different components of a distributed system.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eApplication layer tracing can be implemented with external components in similar fashion to any other distributed system. For tracing of requests between Kubernetes system components, there is a feature in \u003c/span\u003e\u003ca href=\"https://kubernetes.io/docs/concepts/cluster-administration/system-traces/\"\u003e\u003cspan style='font-size: 12pt;'\u003ealpha state\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e aimed at keeping records of latency and relationships between operations in the cluster.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eKubernetes events\u003cspan style='color:rgb(67, 67, 67);'\u003e\u0026nbsp;\u003c/span\u003e\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThere is an area where bird watching significantly diverts from Kubernetes, and that is the ephemeral nature of Kubernetes. Imagine that we’re part of a video game with characters that get killed and respawn automatically with another identity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKeeping track of that happening would be impossible with conventional heartbeat signals. This is where another type of information called Kubernetes events can help us stay on top of changes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhile Kubernetes events are not part of the aforementioned three pillars of observability, they are a resource that has a crucial role in helping us understand the potential causes of issues. Events are a resource type that is automatically generated when other resources have a change of state, an error occurrence, or any other message that is important to broadcast. Each event message is assigned a type (normal, error, warning, etc.) to better help us categorize those we should be more aware of.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvents can be explored by using the kubectl describe pod command or using kubectl get events.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGetting events with kubectl describe pod example:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs21d4d994a479609e"}}},{"code":{"code":"# Explore the events related to a specific Kubernetes pod\nkubectl describe pod elastic-agent-894vs -n kube-system","_metadata":{"uid":"cscddfe59d89de7663"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8063a9fced416207"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe output of describe will have a section at the end containing the events for this specific pod.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs672554fcb16df59e"}}},{"code":{"code":"Events:\n Type Reason Age From Message\n ---- ------ ---- ---- -------\n Warning FailedScheduling 2m (x4886 over 3d16h) default-scheduler 0/3 nodes are available: 1 Insufficient memory, 2 node(s) didn't match Pod's node affinity/selector.\n Normal NotTriggerScaleUp 110s (x31772 over 3d16h) cluster-autoscaler pod didn't trigger scale-up:\n","_metadata":{"uid":"csf5f785ccde8d148d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc451210433c934e6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGetting events with kubectl get events example:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs025a4cdf89a99a56"}}},{"code":{"code":"# Explore the events across the cluster\nkubectl get events -A","_metadata":{"uid":"cs83df2af4a6e5e77b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6062b88125e7db41"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe output of describe will have a section at the end containing the latest cluster wide events.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7f96a49eda6a03cb"}}},{"code":{"code":"LAST SEEN TYPE REASON OBJECT MESSAGE\n49m Warning ContainerdStart node/miguel-cluster1 Starting containerd container runtime...\n49m Warning DockerStart node/miguel-cluster1 Starting Docker Application Container Engine...\n49m Warning KubeletStart node/miguel-cluster1 Started Kubernetes kubelet.\n50m Normal Starting node/miguel-cluster1 Starting kubelet.\n50m Warning InvalidDiskCapacity node/miguel-cluster1 invalid capacity 0 on image filesystem\n50m Normal NodeHasSufficientMemory node/node/miguel-cluster1 Node node/miguel-cluster1 status is now: NodeHasSufficientMemory\n50m Normal NodeHasNoDiskPressure node/miguel-cluster1 Node node/miguel-cluster1 status is now: NodeHasNoDiskPressure\n","_metadata":{"uid":"cs0c10accae1fc0cbb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs286c8ae0c401295d"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eDeducing the status of a Kubernetes cluster from signals\u0026nbsp;\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNow that we are familiar with a variety of musical notes, it is time to create some observability music!\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSimilar to how there is no fixed formula to create songs, there is no unique way to find meaningful correlation in the signals we are gathering. There are, however, best practices that can help us make sure we ask the right questions according to our use case and get the best possible answers.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003eUsing Kubernetes metrics to identify issues\u003c/h3\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe most popular methods for analyzing metrics on distributed systems can help you choose which metrics to gather and how to analyze the performance of your system. Great resources include Google’s SRE book, \u003c/span\u003e\u003ca href=\"https://sre.google/sre-book/monitoring-distributed-systems/#xref_monitoring_golden-signals\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe four golden signals\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, Brendan Gregg’s \u003c/span\u003e\u003ca href=\"https://www.brendangregg.com/usemethod.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUSE method\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or Tom Wilkie’s \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=TJLpYXbnfQ4\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRED method\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing one of these will help us make music by choosing the metrics relevant to our system. There are different tools to help us stay on top of information; the appropriate one will be based on the circumstances.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eVisualizations\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDashboards can help us get a quick visual of the overall status of the metrics we have chosen or help us understand behavior over time. The below example dashboard provides a good overview of the status of the Pod workload resources and Pod resource usage of CPU and memory.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs31bc8843da8a2f66"}}},{"image":{"image":{"uid":"blt2129d020a916ee65","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-09T16:09:56.574Z","updated_at":"2022-11-09T16:09:56.574Z","content_type":"image/jpeg","file_size":"1694059","filename":"observingkubernetesbasics-podresources-4.jpeg","title":"observingkubernetesbasics-podresources-4.jpeg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:22.962Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2129d020a916ee65/636bd0d42e673b30d507d573/observingkubernetesbasics-podresources-4.jpeg"},"_metadata":{"uid":"csbfe18727e362b529"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs42e5abe04d27c917"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStaying on top of your Kubernetes cluster at all times\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor observability practitioners whose goal is to keep Kubernetes up and running at all times, such as an SRE or a CloudOps professional, being stuck to a dashboard with the hope of looking at the right thing at the right time is not a feasible option. Many common use cases can be covered by implementing threshold rules that will trigger informative alerts when a threshold is reached or close to being reached.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, set up an automated rule that will send a Slack message whenever a pod is restarted more than X times within a certain period.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0f2428ecb0bc8481"}}},{"image":{"image":{"uid":"blta7ce7108e9c0a254","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-09T16:10:11.532Z","updated_at":"2022-11-09T16:10:11.532Z","content_type":"image/png","file_size":"243150","filename":"observingkubernetesbasics-rules-5.png","title":"observingkubernetesbasics-rules-5.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:22.987Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta7ce7108e9c0a254/636bd0e3571726758dbe44f7/observingkubernetesbasics-rules-5.png"},"_metadata":{"uid":"cs8bc7f8d829997bdd"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9207d29bc0992d09"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSpotting what you might otherwise miss\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSetting up basic threshold rules will not provide enough coverage given there are behaviors that can only be considered abnormal based on the preceding or surrounding data points. The use of tools like machine learning will enable us to find anomalies in behavior or predict how a Kubernetes component should perform based on trends and with limited guidance required from the user.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor example, using a single metric ML job to identify an anomaly for Kubernetes Pods CPU usage.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbf1f6ad3f79d9211"}}},{"image":{"image":{"uid":"blt32d88b7ae4dc555b","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-09T16:10:23.150Z","updated_at":"2022-11-09T16:10:23.150Z","content_type":"image/png","file_size":"439194","filename":"observingkubernetesbasics-metricviewer-6.png","title":"observingkubernetesbasics-metricviewer-6.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:23.014Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt32d88b7ae4dc555b/636bd0ef120bae1633ca891a/observingkubernetesbasics-metricviewer-6.png"},"_metadata":{"uid":"cs8377ea21d7b5d488"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csad299d885755901f"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003eMoving the investigation from metrics to logs\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAfter metrics have helped us identify issues, logs are great at surfacing granular information with rich local context. Trying to find an issue by looking at logs on their own can be compared to finding a needle in a haystack, but once metrics have helped us to narrow down potential cluster issues to a few components, log analysis will help us understand more details about what has happened. Stored and indexed logs can be visualized with a variety of tools to help you slice and dice them as required.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs132209dfb4aa5281"}}},{"image":{"image":{"uid":"blt642238f034d83d05","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-09T16:10:36.599Z","updated_at":"2022-11-09T16:10:36.599Z","content_type":"image/png","file_size":"643001","filename":"observingkubernetesbasics-logs-7.png","title":"observingkubernetesbasics-logs-7.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:23.037Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt642238f034d83d05/636bd0fc0b5d2311678e5f22/observingkubernetesbasics-logs-7.png"},"_metadata":{"uid":"csd8dfabdcbb6167e1"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc726b0c591967f5d"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003ePutting it all into practice\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that you are familiar with the most common type of Kubernetes birds and their songs, it’s important to actually go and do some Kubernetes watching — this is where finding a good pair of binoculars or a telephoto lens will come in handy.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdea782a09a8737c9"}}},{"image":{"image":{"uid":"bltdc0aa4fc84474ded","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-08T19:30:00.705Z","updated_at":"2022-11-08T19:30:00.705Z","content_type":"image/png","file_size":"215254","filename":"observingkubernetesbasics-binoculars-8.png","title":"observingkubernetesbasics-binoculars-8.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-09T20:09:23.061Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdc0aa4fc84474ded/636aae3809737b2f10270a45/observingkubernetesbasics-binoculars-8.png"},"_metadata":{"uid":"csa59470311fd875f7"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-x-large: 100%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs92d460fca0e756b4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo properly observe Kubernetes, we need reliable software tools to help us gather and store the data we can get from it and more importantly, help us visualize the most comprehensive picture of the status of our Kubernetes clusters and containers running on them.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"font-size: 12pt;\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eExplore how Elastic can provide you with a unified \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/kubernetes-cluster-metrics-logs-monitoring\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKubernetes observability\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e solution to help you store all types of Kubernetes signals from logs, metrics, and traces. Elastic Observability offers a multitude of data analysis tools to help you surface the meaning behind the data, such as cluster overview dashboards, log analysis console, and machine learning based anomaly detection.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs697e39408d62641d"}}}],"publish_date":"2022-11-09","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":{"uid":"blt6074501b9d5f3cca","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-15T12:35:59.892Z","updated_at":"2022-11-15T12:35:59.892Z","content_type":"image/jpeg","file_size":"68550","filename":"observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg","title":"observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-15T13:28:36.553Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6074501b9d5f3cca/637387af3177be104ac20207/observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg"},"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3d6d3cd2ad3fce72","ACL":{},"created_at":"2023-11-06T21:35:37.967Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"visualization","label_l10n":"Visualization","tags":[],"title":"Visualization","updated_at":"2023-11-06T21:35:37.967Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.605Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt81b58809978b575d","created_by":"blt469f34057b68c377","updated_by":"blt469f34057b68c377","created_at":"2022-11-08T19:27:26.155Z","updated_at":"2022-11-10T16:10:17.909Z","content_type":"image/jpeg","file_size":"68550","filename":"observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg","title":"observingkubernetesbasics-podresources-4.png","ACL":{},"_version":3,"parent_uid":null,"is_dir":false,"tags":[],"description":"","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-11-10T16:10:54.717Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt81b58809978b575d/636d22691eced80972fa27bf/observingkubernetesbasics-pexelsrajukhanpathan-1-1.jpeg"},"title":"The basics of observing Kubernetes: A bird-watcher’s perspective","title_l10n":"The basics of observing Kubernetes: A bird-watcher’s perspective","updated_at":"2025-03-07T12:59:52.689Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/monitoring-kubernetes-observability-basics","publish_details":{"time":"2025-03-07T12:59:56.336Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt77d3ec36b4bb3ab1","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic Security has earned the AV-Comparatives Approved Product Award for Enterprise Main-Test Series 2024. It excelled in diverse protection scenarios, demonstrating superior threat protection and system performance while minimizing false alarms.","author":["blt2197c290679d2e28"],"category":["bltb79594af7c5b4199"],"created_at":"2025-03-05T00:53:09.408Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa1db0f0f75bbc578"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security has earned \u003c/span\u003e\u003ca href=\"https://www.av-comparatives.org/av-comparatives-awards-2024-for-elastic/#:~:text=Elastic%20was%20very%20successful%20in,Product%20Award%20for%20both%20runs\"\u003e\u003cspan style='font-size: 12pt;'\u003eAV-Comparatives’ 2024 Approved Product Award in the Enterprise Main-Test Series\u003cwbr\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. The honor reflects its outstanding malware defense, optimal system performance, and minimal false positives. Excelling across protection, performance, and false-positive benchmarks, Elastic Security has proven its ability to safeguard organizations without compromise. This independent recognition underscores our commitment to delivering world-class security solutions for businesses.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Why the test matters","_metadata":{"uid":"csd730de47da588025"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.av-comparatives.org/consumer/\"\u003e\u003cspan style='font-size: 12pt;'\u003eAV-Comparatives\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is a globally respected independent testing lab known for its rigorous evaluations of security software. Its enterprise-focused trials simulate real-world attacks to assess a product’s ability to block threats, maintain system performance, and minimize false positives. Earning the Approved Product award demonstrates that Elastic Security meets these high standards.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Highlights from Elastic Security’s performance","_metadata":{"uid":"cs95830b00c2ab29b0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAV-Comparatives Enterprise Approved Product Award winner:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Recognized for robust protection, high performance, and minimal false positives\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e99.8% malware protection rate:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Effectively detects and mitigates real-world threats\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eZero false positives:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Ensures security teams focus on real threats, not noise\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMinimal system impact:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Proven to maintain performance without slowing business operations\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSeamless integration:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Designed for modern security teams, leveraging the speed and extensibility of the Elastic Search AI Platform\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese outcomes reflect our continuous efforts to enhance security measures and provide reliable protection for businesses of all sizes.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Performance is in our DNA","_metadata":{"uid":"cse05b3669641e658d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn today’s cybersecurity landscape, strong malware protection is essential for ensuring smooth business operations. A sluggish device or high resource consumption can be a warning sign of malicious processes. While advanced security features like behavior-based threat detection, ransomware defense, and AI-driven analytics are vital, overall system performance plays an equally important role in endpoint security.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt Elastic Security, we recognize that effective protection must come without sacrificing speed or stability. We’ve made it our mission to deliver powerful security capabilities with minimal impact on CPU and memory usage — setting a high standard for how the Elastic Agent is developed and maintained. This philosophy has been validated by independent testing: our AV-Comparatives results confirmed that we can keep systems secure without slowing them down.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Get started with Elastic Security","_metadata":{"uid":"csed350ee319256480"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eJoin the growing number of businesses that trust Elastic Security — now recognized by AV-Comparatives as an industry-leading solution — to protect their organization against attacks. Experience the peace of mind that comes with knowing your endpoints (and your organization as a whole) are secure against the latest threats. Start your Elastic Security \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efree trial\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and discover the difference that our protection can make. Visit \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eelastic.co/security\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to learn more and get started.\u003cbr /\u003e\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor more detailed results, see the \u003c/span\u003e\u003ca href=\"https://www.av-comparatives.org/av-comparatives-awards-2024-for-elastic/#:~:text=Elastic%20was%20very%20successful%20in,Product%20Award%20for%20both%20runs\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAV-Comparatives Awards 2024 for Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e report.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs1b8c32be487105bc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs86302c4a0596c579"}}}],"publish_date":"2025-03-06","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Security Achieves AV-Comparatives Enterprise Award 2024","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Awarded for outstanding protection, performance, and minimal false positives.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte41b0699a34eac99","ACL":{},"created_at":"2023-11-06T20:38:53.624Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"edr","label_l10n":"EDR","tags":[],"title":"EDR","updated_at":"2023-11-06T20:38:53.624Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:26.559Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte6358c0a4368f192","ACL":{},"created_at":"2023-11-06T20:39:12.952Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"end-user-experience","label_l10n":"End user experience","tags":[],"title":"End user experience","updated_at":"2023-11-06T20:39:12.952Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:48.382Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltd12745b736426a5f","_version":1,"title":"lake with woman.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-07T00:05:04.998Z","updated_at":"2025-03-07T00:05:04.998Z","content_type":"image/jpeg","file_size":"38797","filename":"lake_with_woman.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-07T00:07:04.138Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd12745b736426a5f/67ca3831045f582d16c0200e/lake_with_woman.jpg"},"title":"Elastic Security wins AV-Comparatives 2024 Enterprise Approved Product Award","title_l10n":"Elastic Security wins AV-Comparatives 2024 Enterprise Approved Product Award","updated_at":"2025-03-07T00:05:25.327Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-security-av-comparatives-award","publish_details":{"time":"2025-03-07T00:07:03.829Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbb7503a3cf33f6aa","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic is excited to announce the technical preview of Elastic Cloud Serverless on Google Cloud. Built on the industry-first Search AI Lake architecture, it combines vast storage, low-latency querying, and advanced AI capabilities. ","author":["blt7969873b62221c94"],"category":["bltb79594af7c5b4199"],"created_at":"2025-03-05T01:19:28.495Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb0336d5279e3fe04"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eToday, we are excited to announce the technical preview of Elastic Cloud Serverless on Google Cloud — now available in the Iowa (us-central1) region. Elastic Cloud Serverless provides the fastest way to start and scale observability, security, and search solutions without managing infrastructure. Built on the industry-first \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/search-ai-lake-elastic-cloud-serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearch AI Lake architecture\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — which leverages Google Cloud Storage — it combines vast storage, separate storage and compute, low-latency querying, and advanced AI capabilities to deliver uncompromising speed and scale.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Start and scale quickly with Elastic Cloud Serverless on Google Cloud","_metadata":{"uid":"cs93d860d26b435649"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNo compromise on speed or scale:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elasticsearch Serverless dynamically scales to accommodate your workload, handling unpredictable traffic spikes automatically — all while delivering low-latency search on boundless object storage.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHassle-free operations:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Say goodbye to managing clusters, provisioning nodes, or fine-tuning performance. Free your team from operational tasks — no need to manage infrastructure, do capacity planning, upgrade, or scale data.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePurpose-built product experience:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic Cloud Serverless offers a streamlined workflow to help you create projects tailored to your unique use cases in observability, security, and search. With guided onboarding, you can use in-product resources and tools that guide you every step of the way, accelerating time to value.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eFlexible usage-based pricing model: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud Serverless offers a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-serverless-pricing-packaging\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eusage-based pricing model\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that scales with your needs. You only pay for what you use — whether it’s for data ingested and retained in Elastic Security and Observability products or for compute resources in Elasticsearch.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Getting started with Elastic Cloud Serverless on Google Cloud","_metadata":{"uid":"cs132d7d4eb4f63a23"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo try Elastic Cloud Serverless, \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/serverless-registration\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esign up\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003elog in\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to the Elastic Cloud console and create a serverless project.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor Observability or Security projects, select Google Cloud as the cloud provider and US Central 1 (Iowa) as the region.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor Elasticsearch projects, choose a use case (“General Purpose” or “Optimized for Vectors”), and then select Google Cloud as the cloud provider and US Central 1 (Iowa) as the region.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eClick \"Create project,” and your Elastic Cloud Serverless project will be provisioned in minutes.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eVisit our \u003ca href=\"https://www.elastic.co/docs/current/serverless\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to learn more.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s next?","_metadata":{"uid":"cs224468dddbac675f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe are just getting started. We are working to expand Elastic Cloud Serverless to additional Google Cloud regions and introduce new features to further enhance performance and usability. Stay tuned for exciting updates as we bring the full power of Elastic’s solutions to Google Cloud users.\u003cbr /\u003e\u003cbr /\u003eThe future of search, security, and observability is here without compromise on speed, scale, or cost. Experience Elastic Cloud Serverless and Search AI Lake to unlock new opportunities with your data. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e about the possibilities of serverless or start your \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/serverless-registration\"\u003e\u003cspan style='font-size: 12pt;'\u003efree trial now\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e on Google Cloud in technical preview.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csd8fa2c1657cb07dc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs67163a49c2eed79c"}}}],"publish_date":"2025-03-10","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Announcing the technical preview of Elastic Cloud Serverless on Google Cloud","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Elastic Cloud Serverless provides the fastest way to start and scale security, observability, and search solutions — without managing infrastructure. ","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltd3330c8b33d68fef","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-03-05T01:15:44.202Z","created_by":"blte369ea3bcd6ac892","file_size":"92385","filename":"175344_-_Blog_Header_Image_Elastic_Cloud_Serverless_1_V1.jpg","parent_uid":null,"tags":[],"title":"175344 - Blog Header Image Elastic Cloud Serverless 1_V1.jpg","updated_at":"2025-03-05T01:15:44.202Z","updated_by":"blte369ea3bcd6ac892","publish_details":{"time":"2025-03-10T13:00:02.047Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd3330c8b33d68fef/67c7a5c05e83f4d0aecb8bad/175344_-_Blog_Header_Image_Elastic_Cloud_Serverless_1_V1.jpg"},"title":"Elastic Cloud Serverless now available in technical preview on Google Cloud","title_l10n":"Elastic Cloud Serverless now available in technical preview on Google Cloud ","updated_at":"2025-03-06T18:01:44.712Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-cloud-serverless-google-cloud-tech-preview","publish_details":{"time":"2025-03-10T13:00:02.030Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltead58fb81fb7307d","_version":37,"locale":"en-us","ACL":{},"abstract_l10n":"With Elastic Observability 8.1, development teams can now get enhanced visibility into AWS Lambda and CI/CD build pipelines, and leverage open standards based instrumentation for unified data ingest and analysis across a wide variety of data types.","author":["blt06813ba62b8b04b9"],"category":["bltfaae4466058cc7d6"],"created_at":"2022-03-02T13:15:24.433Z","created_by":"blt469f34057b68c377","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse916570ae67fc8cd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eTechnologies such as \u003ca href=\"https://www.elastic.co/what-is/serverless-computing\" target=\"_self\"\u003eserverless computing\u003c/a\u003e frameworks and CI/CD automation tools help accelerate software development lifecycles (SDLC) to give development teams a competitive edge in the marketplace. Armed with these technologies, teams can deploy and innovate faster and more frequently by automating repetitive tasks and eliminating the need to manage or provision servers.\u003c/p\u003e\u003cp\u003eWith Elastic Observability 8.1, DevOps and SRE teams can now leverage even better support for these technologies with the ability to capture application traces from AWS Lambda, ingest OpenTelemetry logs, and collect detailed Jenkins build logs using the OpenTelemetry Collector.\u003c/p\u003e\u003cp\u003eThese new features allow customers to:\u003c/p\u003e\u003cul\u003e\u003cli\u003eAccelerate release cycles with observability for AWS Lambda functions and CI/CD build pipelines\u003c/li\u003e\u003cli\u003eStandardize open standards based data collection by ingesting OpenTelemetry logs along with metrics and traces\u003c/li\u003e\u003cli\u003eUnify these data streams with other relevant observability data and easily navigate investigative workflows without losing context\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eElastic Observability 8.1 is \u003ca href=\"https://cloud.elastic.co/registration?elektra=whats-new-elastic-7-13-blog\" target=\"_self\"\u003eavailable now on Elastic Cloud\u003c/a\u003e — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also \u003ca href=\"https://www.elastic.co/downloads/\" target=\"_self\"\u003edownload the Elastic Stack\u003c/a\u003e and our cloud orchestration products, Elastic Cloud Enterprise and Elastic Cloud for Kubernetes, for a self-managed experience.\u003c/p\u003e\u003ch2\u003eGet enhanced visibility into AWS Lambda (Beta)\u003c/h2\u003e\u003cp\u003eGet end-to-end application performance monitoring (APM) visibility and correlate AWS Lambda traces with other Elastic Observability data for faster and more comprehensive root cause analysis.\u0026nbsp;\u003c/p\u003e\u003cp\u003eLambda is a popular high-availability compute service provided by Amazon that lets developers run event-driven functions on a pay-per-use basis without having to provision or manage servers — increasing development efficiency and controlling costs.\u003c/p\u003e\u003cp\u003eWith Elastic Observability 8.1, development teams can now \u003ca href=\"https://www.elastic.co/guide/en/apm/guide/current/monitoring-aws-lambda.html\" target=\"_blank\"\u003ecollect serverless application traces\u003c/a\u003e from Lambda functions written in Node.js, Python and Java. Elastic additionally supports native cloud monitoring with open standards with the ability to collect \u003ca href=\"https://www.elastic.co/blog/tracing-aws-lambdas-with-opentelemetry-and-elastic-observability\" target=\"_blank\"\u003eLambda traces via OpenTelemetry\u003c/a\u003e (Java and Python only).\u003c/p\u003e"}],"_metadata":{"uid":"cs2bc783fa5b9c5c38"}}},{"video":{"vidyard_uuid":"JJHRxzPN11jQWJ1uiFptJh","_metadata":{"uid":"cs933bd22429e9075e"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":true,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb78260f351d55b58"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eAugment CI/CD observability with Jenkins logs\u003c/h2\u003e\n\u003cp\u003eDevelopers around the world rely on Jenkins automation to reliably build, test, and deploy their software. Elastic empowers developers with visibility into their CI/CD pipelines with high level health indicator dashboards and drill-downs, along with intuitive visualizations of critical build activities.\u003c/p\u003eNow, in Technical Preview with Elastic Observability 8.1, teams can improve traceability of their software supply chain process by additionally collecting \u003ca href=\"https://plugins.jenkins.io/opentelemetry/\" target=\"_blank\"\u003edetailed Jenkins logs\u003c/a\u003e, including errors and build execution details, such as test outputs, using the OpenTelemetry Collector."}],"_metadata":{"uid":"cs9ba52b6ae4a18a71"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt55c8587a58bd472f","ACL":{},"content_type":"image/png","created_at":"2022-03-02T17:53:38.458Z","created_by":"blt469f34057b68c377","file_size":"757655","filename":"Image3.png","parent_uid":null,"tags":[],"title":"Image3.png","updated_at":"2022-03-02T17:53:38.458Z","updated_by":"blt469f34057b68c377","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T20:34:55.688Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt55c8587a58bd472f/621faf224428422d082c435a/Image3.png"},"_metadata":{"uid":"cscf2e7581253d8c62"},"caption_l10n":"Troubleshoot Jenkins errors and build execution issues with detailed logs — in combination with high level CI/CD pipeline health dashboards and other intuitive drill-downs.","alt_text_l10n":"Troubleshoot Jenkins errors and build execution issues with detailed logs — in combination with high level CI/CD pipeline health dashboards and other intuitive drill-downs.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs72c4c56b02220372"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eStandardize data collection with OpenTelemetry\u003c/h2\u003e\n\u003cp\u003eElastic Observability users can now also ingest OpenTelemetry logs, in addition to existing support for ingesting OpenTelemetry metrics and traces. With the ability to ingest \u003ca href=\"https://www.elastic.co/observability/opentelemetry\" target=\"_blank\"\u003eOpenTelemetry observability\u003c/a\u003e data into Elastic, DevOps teams can now maintain an open standards-based, vendor-neutral observability architecture while streamlining investigative workflows with contextual navigation across signal types and layers.\u003c/p\u003e"}],"_metadata":{"uid":"cs453e4023c3a8ab65"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt7a563316b21adb86","ACL":{},"content_type":"image/png","created_at":"2022-03-02T17:43:44.449Z","created_by":"blt469f34057b68c377","file_size":"658717","filename":"image_(4).png","parent_uid":null,"tags":[],"title":"image_(4).png","updated_at":"2022-03-02T17:43:44.449Z","updated_by":"blt469f34057b68c377","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-03-08T20:34:55.712Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7a563316b21adb86/621facd068865368951c6443/image_(4).png"},"_metadata":{"uid":"csabd8f615b9002045"},"caption_l10n":"Organizations that already use the OpenTelemetry Collector for tracing and metrics collection can now standardize data collection across a diversity of sources and data types by also using it for log ingest.","alt_text_l10n":"Organizations that already use the OpenTelemetry Collector for tracing and metrics collection can now standardize data collection across a diversity of sources and data types by also using it for log ingest.","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2d941260b8fadcca"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eAccelerate troubleshooting with unified observability\u003c/h2\u003e\n\u003cp\u003eElastic Observability 8.1 extends visibility to additional platforms and data sources, including AWS Lambda traces, OpenTelemetry logs, and Jenkins build details. \u003c/p\u003e\n\u003cp\u003eWith all the data in one place, within \u003ca href=\"https://www.elastic.co/guide/en/ecs/current/ecs-reference.html\" target=\"_blank\"\u003eone common schema\u003c/a\u003e, teams that use Elastic can streamline investigative workflows and easily correlate across and navigate to other relevant observability data for contextual troubleshooting. In addition, leveraging Elastic’s \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/data-tiers.html\" target=\"_blank\"\u003efrozen tier\u003c/a\u003e for cost effective and secure long-term storage enables better root cause analysis and audit trails based on historical data. These advantages, unique to Elastic, are now extended to storing and analyzing OpenTelemetry logs, and troubleshooting CI/CD pipeline anomalies and serverless applications. \u003c/p\u003e\u003ch2\u003eTry it out\u003c/h2\u003e\n\u003cp\u003eExisting Elastic Cloud customers can access many of these features directly from the \u003ca href=\"https://cloud.elastic.co/\"\u003eElastic Cloud console\u003c/a\u003e. If you’re new to Elastic Cloud, take a look at our \u003ca href=\"https://www.elastic.co/training/free#quick-starts\"\u003eQuick Start guides\u003c/a\u003e (bite-sized training videos to get you started quickly) or our \u003ca href=\"https://www.elastic.co/training/free#fundamentals\"\u003efree fundamentals training courses\u003c/a\u003e. You can always get started for free with a \u003ca href=\"http://cloud.elastic.co/registration\"\u003efree 14-day trial of Elastic Cloud\u003c/a\u003e. Or \u003ca href=\"https://www.elastic.co/downloads/\"\u003edownload\u003c/a\u003e the self-managed version of the Elastic Stack for free.\u003c/p\u003e\n\u003cp\u003eRead about these capabilities and more in the \u003ca href=\"https://www.elastic.co/guide/en/observability/8.1/whats-new.html\"\u003eElastic Observability 8.1\u003c/a\u003e release notes, and other Elastic Stack highlights in the \u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-8-1-0\"\u003eElastic 8.1\u003c/a\u003e announcement post.\u003c/p\u003e\n\u003cp\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all. \u003c/em\u003e\u003c/p\u003e\u003cbr\u003e"}],"_metadata":{"uid":"cs0a852d8d5e0150a6"}}}],"publish_date":"2022-03-08T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Observability 8.1: Visibility into AWS Lambda, CI/CD pipelines, and more","seo_description_l10n":"With Elastic Observability 8.1, development teams can now get enhanced visibility into AWS Lambda and CI/CD build pipelines, and leverage open standards based instrumentation for unified data ingest and analysis across a wide variety of data types.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt76a8a9e2ae891569","ACL":{},"created_at":"2023-11-06T21:35:06.844Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tracing","label_l10n":"Tracing","tags":[],"title":"Tracing","updated_at":"2023-11-06T21:35:06.844Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.748Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"AWS","label_l10n":"AWS","keyword":"aws","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt5da20aee1a072f80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:30.685Z","updated_at":"2023-11-06T20:08:30.685Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:00:52.463Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4f7e02463a803fc1","ACL":{},"created_at":"2023-11-06T20:35:19.646Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-native","label_l10n":"Cloud native","tags":[],"title":"Cloud native","updated_at":"2023-11-06T20:35:19.646Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:35:54.838Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Python","label_l10n":"Python","keyword":"python","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6293a0df96e13ba7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:49:39.583Z","updated_at":"2023-11-06T20:49:39.583Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.836Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"OpenTelemetry","label_l10n":"Open source/standards","keyword":"opentelemetry","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt069bd34528952802","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:44:13.512Z","updated_at":"2023-11-06T20:44:13.512Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.903Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt44910d88c864d1cb","ACL":{},"content_type":"image/png","created_at":"2021-01-12T16:51:33.775Z","created_by":"bltf6ab93733e4e3a73","file_size":"5838","filename":"blog-thumb-observability-pattern-color.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-observability-pattern-color.png","updated_at":"2022-02-11T21:04:12.027Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:03.790Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt44910d88c864d1cb/5ffdd3955b28c33f6281ce94/blog-thumb-observability-pattern-color.png"},"title":"Elastic Observability 8.1: Visibility into AWS Lambda, CI/CD pipelines, and more","title_l10n":"Elastic Observability 8.1: Visibility into AWS Lambda, CI/CD pipelines, and more","updated_at":"2025-03-06T12:45:14.228Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/whats-new-elastic-observability-8-1-0","publish_details":{"time":"2025-03-06T12:45:17.764Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5f32c1b70555bc8c","_version":26,"locale":"en-us","ACL":{},"abstract_l10n":"In 8.2, Elastic has newly introduced support for the Elasticsearch query syntax for all Enterprise Search engines which allows you to take it to the next level when your search experience needs extra configurability.","author":["blt5fd2526d9811bef1"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-04-14T19:04:09.519Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3094ce79b097476b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eElastic 8.2 introduces a new search API for App Search. The Elasticsearch Search API, now in beta, brings more of the flexibility and power of Elasticsearch to App Search. Elastic 8.2 also introduces a Search Explain API for App Search, which exposes the Elasticsearch queries generated by App Search. Use these Elasticsearch queries as the basis for your own.\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eIn this post, we'll look at the new APIs and explore the following use cases:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"#case1\" target=\"_self\"\u003eI want to count how many documents would match my query, without the overhead of the search results payload\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"#case2\" target=\"_self\"\u003eI want to count how many documents match my query, grouped by a certain field or fields\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"#case3\" target=\"_self\"\u003eI want to search for documents that are like a specific document in the same index\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"#case4\" target=\"_self\"\u003eI want to use a custom function to calculate document scores\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"#case5\" target=\"_self\"\u003eI want to retrieve a subset of documents without applying any scoring or grouping. These features are not useful to me and make the query slower\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"#case6\" target=\"_self\"\u003eI want to search for an exact match of a word or phrase, not a fuzzy match\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"#case7\" target=\"_self\"\u003eI want to add a runtime field to my documents and return it in my search\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003ch2\u003eThe Elasticsearch Search API for App Search\u003c/h2\u003e\u003cp\u003eIn App Search v8.2, we’ve added a new beta API called Elasticsearch Search API. Using this API, you can query the App Search document indices using free-form Elasticsearch queries.\u003c/p\u003e\u003cp\u003ePerhaps you’ve been using App Search for a while, and although it’s powerful out of the box, you’d like to customize your search queries. App Search makes it very easy to get up and running with search. At the same time, it hides details and makes assumptions. The Elasticsearch Search API can fill this gap by providing direct access to query the underlying indices with Elasticsearch.\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eThe API is available as:\u003c/p\u003e"}],"_metadata":{"uid":"cs08dbd634c0f829f2"}}},{"code":{"code":"GET /api/as/v0/engines/\u003cengine-name\u003e/elasticsearch/_search\nPOST /api/as/v0/engines/\u003cengine-name\u003e/elasticsearch/_search\n\n","_metadata":{"uid":"cs9fbed01c38309c0a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs78a3633597b5dd65"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe API accepts the following parameters:\u003c/p\u003e"}],"_metadata":{"uid":"cs54be143519e1e5ed"}}},{"code":{"code":"request: JSON object with the following properties:\nrequest.body: JSON. This query will be sent as-is to Elasticsearch.\nrequest.query_params: List of parameters. A parameter is an object with a key and a value.\nanalytics: JSON object with the following properties:\nanalytics.query: String. Query associated with this request.\nanalytics.tags: List of tags to attach to this request.\n","_metadata":{"uid":"cs372f60ef013e1338"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs46d7d6204751bc50"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eConfiguration\u003c/h2\u003e\u003cp\u003eThis API is only available via a \u003ca href=\"https://www.elastic.co/guide/en/app-search/current/authentication.html#authentication-private\" target=\"_self\"\u003eprivate key\u003c/a\u003e. In addition, a feature flag \u003ccode\u003efeature_flag.elasticsearch_search_api\u003c/code\u003e should be set to \u003ccode\u003etrue\u003c/code\u003e in the Enterprise Search \u003ca href=\"https://www.elastic.co/guide/en/enterprise-search/current/configuration.html#configuration-file\" target=\"_self\"\u003econfiguration file\u003c/a\u003e.\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eKeep in mind that with this API, results are formatted differently than \u003ca href=\"https://www.elastic.co/guide/en/app-search/current/search.html\" target=\"_self\"\u003eSearch API\u003c/a\u003e results. Documents are returned from Elasticsearch as-is, without applying any additional formatting. This means you can’t use this API as a drop-in replacement for the Search API.\u003c/p\u003e"}],"_metadata":{"uid":"csf1082f24bfb0437f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa9d21600c303e596"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eUse cases\u003c/h2\u003eWhat kind of problems can you solve with this API? We’ll look at a few, using the National Parks sample engine that comes with App Search.\u003ch3 id=\"case1\"\u003eI want to count how many documents would match my query, without the overhead of the search results payload.\u003c/h3\u003e\u003cp\u003eProvide a body to the API, and set the “size” parameter to 0. Example:\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf87a45a36c28601"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\"query\": {\"match_all\": {}}},\n \"query_params\": [\n {\"key\": \"size\", \"value\": \"0\"}\n ]\n }\n}\n","_metadata":{"uid":"csd332537fdbe4d46f"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9e992a9f2a08eb52"},"header_style":"H2","paragraph_l10n":"\u003ch3 id=\"case2\"\u003eI want to count how many documents match my query, grouped by a certain field or fields.\u003c/h3\u003e\u003cbr /\u003e\u003cp\u003eProvide a body with \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/search-aggregations.html\" target=\"_self\"\u003eaggregations\u003c/a\u003e (“aggs”) to the API, and set the “size” to 0. Multiple aggs can be specified. In this example, for brevity, I’m not specifying any query, so aggregations will be applied to all documents in the documents index. In reality, you will want to do some kind of searching and filtering:\u003c/p\u003e"}],"_metadata":{"uid":"csced8424f6e4ca541"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"aggs\": {\n \"top_states\": {\n \"terms\": {\n \"field\": \"states.enum\",\n \"size\": 100\n }\n },\n \"world_heritage_site\": {\n \"terms\": {\n \"field\": \"world_heritage_site.enum\",\n \"size\": 10\n }\n }\n }\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"0\"\n }\n ]\n }\n}\n","_metadata":{"uid":"cs5429acde44a5d8ab"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs56cc9c8249c23145"},"header_style":"H2","paragraph_l10n":"\u003ch3 id=\"case3\"\u003eI want to search for documents that are like a specific document in the same index.\u003c/h3\u003eUse the Elasticsearch’s \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-mlt-query.html\" target=\"_self\"\u003emore_like_this (MLT)\u003c/a\u003e query. Example\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csadf98edec2b5d416"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"query\": {\n \"more_like_this\": {\n \"fields\": [\n \"title\",\n \"description\"\n ],\n \"like\": [\n {\n \"_id\": \"park_sequoia\"\n }\n ],\n \"min_term_freq\": 1,\n \"max_query_terms\": 12\n }\n }\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"100\"\n }\n ]\n }\n}\n","_metadata":{"uid":"cs646947b8ae058133"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs06987fcfdea26afd"},"header_style":"H2","paragraph_l10n":"\u003ch3 id=\"case4\"\u003eI want to use a custom function to calculate document scores.\u003c/h3\u003e\u003cbr /\u003e\u003cp\u003eWhy not? With a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-function-score-query.html\" target=\"_self\"\u003ecustom function\u003c/a\u003e, you can calculate document scores as a function of park square footage and number of visitors:\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8667aa34b9c24684"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"query\": {\n \"function_score\": {\n \"script_score\": {\n \"script\": {\n \"source\": \"Math.log(doc['acres.float'].value * doc['acres.float'].value)\"\n }\n }\n }\n }\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"100\"\n }\n ]\n }\n}\n","_metadata":{"uid":"cs959e54fee90364bf"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs308b5ba84e87d23d"},"header_style":"H2","paragraph_l10n":"\u003ch3 id=\"case5\"\u003eI want to retrieve a subset of documents without applying any scoring or grouping. These features are not useful to me and make the query slower.\u003c/h3\u003e\u003cbr /\u003eThis is what filter context in Elasticsearch is for — you can \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-filter-context.html#filter-context\" target=\"_self\"\u003efilter\u003c/a\u003e the documents using a combination of criteria, but they won’t be scored. The following query selects all national parks in California within 300 miles of San Francisco International airport:\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd7be9a42cc239fbf"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"query\": {\n \"bool\": {\n \"filter\": [\n {\n \"geo_distance\": {\n \"distance\": \"300mi\",\n \"location.location\": {\n \"lat\": 37.62126189231072,\n \"lon\": -122.3790626898805\n }\n }\n },\n {\n \"term\": {\n \"states.enum\": \"California\"\n }\n }\n ]\n }\n }\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"100\"\n }\n ]\n }\n}\n","_metadata":{"uid":"csf84118c3ce27bb61"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs92001754266eef83"},"header_style":"H2","paragraph_l10n":"\u003ch3 id=\"case6\"\u003eI want to search for an exact match of a word or phrase, not a fuzzy match.\u003c/h3\u003e\u003cp\u003eIn its current version, App Search doesn’t make this easy. This is because after text fields are \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/analysis-overview.html#tokenization\" target=\"_self\"\u003etokenized\u003c/a\u003e, the search is not being done on exact terms anymore, but on the resulting tokens. For example, the word “needle-like” will be turned into two tokens: “needle” and “like”. So if you try to use a match query:\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6580c3d23e621d42"}}},{"code":{"code":"{\n \"query\": {\n \"match\": {\n \"description\": \"needle-like\"\n }\n }\n}\n","_metadata":{"uid":"cs61d0c90a83ed4716"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc4ba0610064e7a7f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou will find documents that match “needle” and / or “like”. In our sample National Parks index, this will return three documents. Here is a workaround using a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/runtime.html\"\u003eruntime field\u003c/a\u003e:\u003c/p\u003e"}],"_metadata":{"uid":"cs4a3a2b5079ce54f6"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"query\": {\n \"bool\": {\n \"filter\": {\n \"term\": {\n \"has_exact_word\": true\n }\n }\n }\n },\n \"runtime_mappings\": {\n \"has_exact_word\": {\n \"type\": \"boolean\",\n \"script\": {\n \"source\": \"emit(doc['description.enum'].value.contains('needle-like'))\"\n }\n }\n }\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"100\"\n }\n ]\n }\n}\n","_metadata":{"uid":"cs3a9bf57eddc6e3a8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs73dd749517d10108"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe query above will return only one document, that in fact contains the exact word “needle-like”.\u003c/p\u003e\u003cp\u003eHere is another workaround using a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl-script-query.html\"\u003escript query\u003c/a\u003e:\u003c/p\u003e"}],"_metadata":{"uid":"cs6824a1077a5b86c9"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"query\": {\n \"bool\": {\n \"filter\": {\n \"script\": {\n \"script\": \"doc['description.enum'].value.contains('needle-like')\"\n }\n }\n }\n }\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"100\"\n }\n ]\n }\n}\n","_metadata":{"uid":"cs5fd294cc979ab1f1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse3adefb5c42ba578"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThese workarounds might temporarily solve a legitimate business problem, but performance would be severely degraded. The script query would have to scan every document in the index and, for an index of any significance, this quickly becomes unsustainable. The best way to solve this problem would be to apply a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/analysis-custom-analyzer.html\" target=\"_self\"\u003ecustom analyzer\u003c/a\u003e to your documents index. This ensures that text is tokenized in a way that makes sense for your set of documents.\u003c/p\u003e\u003ch3 id=\"case7\"\u003eI want to add a \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/runtime.html\" target=\"_self\"\u003eruntime field\u003c/a\u003e to my documents and return it in my search.\u003c/h3\u003e\u003cbr /\u003e\u003cp\u003eLet’s add distance to SFO (in miles) to all documents in the National Parks index. The following query adds a runtime field, and includes it in “fields” to ensure it’s being returned in the response:\u003c/p\u003e"}],"_metadata":{"uid":"cse27e670bb9e736cc"}}},{"code":{"code":"{\n \"request\": {\n \"body\": {\n \"runtime_mappings\": {\n \"miles_to_sfo\": {\n \"type\": \"double\",\n \"script\": {\n \"source\": \"emit(0.00062137 * doc['location.location'].planeDistance(37.62126189231072, -122.3790626898805))\"\n }\n }\n },\n \"fields\": [\n \"miles_to_sfo\"\n ]\n },\n \"query_params\": [\n {\n \"key\": \"size\",\n \"value\": \"100\"\n }\n ]\n }\n}\n","_metadata":{"uid":"cs3d1a2467213cc16c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6573a7274494953b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eKeep in mind that, because runtime fields are evaluated at query time, they will naturally be less performant than indexed fields. One thing you can do to improve query performance is ensure you’re only retrieving a subset of documents you actually need, by applying filters on other indexed fields. This means the runtime field doesn’t have to be evaluated for the whole dataset. If this is a query you will be making regularly, and especially if the index contains a lot of documents, you should consider \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/runtime-indexed.html\"\u003epromoting this field\u003c/a\u003e to an indexed field.\u003c/p\u003e\u003ch2\u003eThe Search Explain API for App Search\u003c/h2\u003e\u003cbr/\u003e\u003cp\u003eThe new Search Explain API is another useful tool that will help you write your Elasticsearch queries.\u003c/p\u003eThe Search Explain API accepts the same parameters as the App Search \u003ca href=\"https://www.elastic.co/guide/en/app-search/current/search.html\"\u003eSearch API\u003c/a\u003e. However, instead of running a search and returning results, it builds and returns an Elasticsearch query that App Search would run.\u003cp\u003e\u003c/p\u003e\u003cp\u003eThe API is available as:\u003c/p\u003e"}],"_metadata":{"uid":"cs065814c4f677aa1f"}}},{"code":{"code":"GET /api/as/v0/engines/\u003cengine-name\u003e/search_explain\nPOST /api/as/v0/engines/\u003cengine-name\u003e/search_explain\n","_metadata":{"uid":"cs9902f2a76fcb7325"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs893b7e896f2c3ee0"},"header_style":"H2","paragraph_l10n":"You can see what happens when you search for “everglade” in App Search:"}],"_metadata":{"uid":"csee93aea2510bd221"}}},{"code":{"code":"curl -XPOST 'http://localhost:3002/api/as/v0/engines/national-parks-demo/search_explain' \\\n--header 'Content-Type: application/json' \\\n--header 'Authorization: Bearer private-abcdef' \\\n--data-raw '{\n \"query\": \"everglade\"\n}'\n","_metadata":{"uid":"cse22dded28cd62d68"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa9b660626f186cd3"},"header_style":"H2","paragraph_l10n":"Response:"}],"_metadata":{"uid":"cs8120be8003bb91dd"}}},{"code":{"code":"{\n \"meta\": {\n \"alerts\": [],\n \"warnings\": [],\n \"precision\": 2,\n \"engine\": {\n \"name\": \"national-parks-demo\",\n \"type\": \"default\"\n },\n \"request_id\": \"d3346586-46b0-419f-91a2-e051253ab455\"\n },\n \"query_string\": \"GET enterprise-search-engine-national-parks-demo/_search\",\n \"query_body\": {\n \"query\": {\n \"bool\": {\n \"must\": {\n \"function_score\": {\n \"boost_mode\": \"sum\",\n \"score_mode\": \"sum\",\n \"query\": {\n \"bool\": {\n \"must\": [\n {\n \"bool\": {\n \"should\": [\n {\n \"multi_match\": {\n \"query\": \"everglade\",\n \"minimum_should_match\": \"1\u003c-1 3\u003c49%\",\n \"type\": \"cross_fields\",\n \"fields\": [\n \"world_heritage_site^1.0\",\n \"world_heritage_site.stem^0.95\",\n \"world_heritage_site.prefix^0.1\",\n \"world_heritage_site.joined^0.75\",\n \"world_heritage_site.delimiter^0.4\",\n \"description^2.4\",\n \"description.stem^2.28\",\n \"description.prefix^0.24\",\n \"description.joined^1.8\",\n \"description.delimiter^0.96\",\n \"title^5.0\",\n \"title.stem^4.75\",\n \"title.prefix^0.5\",\n \"title.joined^3.75\",\n \"title.delimiter^2.0\",\n \"nps_link^0.7\",\n \"nps_link.stem^0.665\",\n \"nps_link.prefix^0.07\",\n \"nps_link.joined^0.525\",\n \"nps_link.delimiter^0.28\",\n \"states^2.8\",\n \"states.stem^2.66\",\n \"states.prefix^0.28\",\n \"states.joined^2.1\",\n \"states.delimiter^1.12\",\n \"id^1.0\"\n ]\n }\n },\n {\n \"multi_match\": {\n \"query\": \"everglade\",\n \"minimum_should_match\": \"1\u003c-1 3\u003c49%\",\n \"type\": \"best_fields\",\n \"fuzziness\": \"AUTO\",\n \"prefix_length\": 2,\n \"fields\": [\n \"world_heritage_site.stem^0.1\",\n \"description.stem^0.24\",\n \"title.stem^0.5\",\n \"nps_link.stem^0.07\",\n \"states.stem^0.28\"\n ]\n }\n }\n ]\n }\n }\n ]\n }\n },\n \"functions\": [\n {\n \"script_score\": {\n \"script\": {\n \"source\": \"Math.max(_score + ((1.5 * (doc.containsKey(\\\"visitors.float\\\") \u0026\u0026 !doc[\\\"visitors.float\\\"].empty ? doc[\\\"visitors.float\\\"].value : 0))) - _score, 0)\"\n }\n }\n }\n ]\n }\n }\n }\n },\n \"sort\": [\n {\n \"_score\": \"desc\"\n },\n {\n \"_doc\": \"desc\"\n }\n ],\n \"highlight\": {\n \"fragment_size\": 300,\n \"type\": \"plain\",\n \"number_of_fragments\": 1,\n \"order\": \"score\",\n \"encoder\": \"html\",\n \"require_field_match\": false,\n \"fields\": {}\n },\n \"size\": 10,\n \"from\": 0,\n \"timeout\": \"30000ms\",\n \"_source\": [\n \"visitors\",\n \"square_km\",\n \"world_heritage_site\",\n \"date_established\",\n \"description\",\n \"location\",\n \"id\",\n \"acres\",\n \"title\",\n \"nps_link\",\n \"states\"\n ]\n }\n}\n","_metadata":{"uid":"cse5020c5848b41daa"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse075ff076c24ffa9"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhoa. A lot seems to be happening there. App Search is:\u003cbr/\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003ecombining 2 different multi-match queries, one type of best_fields and another of type cross_fields\u003c/li\u003e\u003cli\u003ecalculating a script score, multiplying the document score returned by Elasticsearch by an additional factor of visitors\u003c/li\u003e\u003cli\u003eapplying field weights and boosts\u003c/li\u003e\u003cli\u003eadding highlighting\u003c/li\u003e\u003cli\u003esumming up the resulting document scores\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eThis query could be used as a starting point, and modified as needed to achieve your search objectives.\u003c/p\u003e\u003ch2\u003eSummary\u003c/h2\u003e\u003cp\u003eIn this blog post, we gave you some tips for using the new Elasticsearch Search API in App Search. We provided several use cases, based on App Search feature requests we have received over time. We also let you take a peek into the inner workings of App Search, with the new Search Explain API.\u003c/p\u003eWe hope that this new API will empower you to build that perfect search experience you’ve always been looking for. Try it out with a free trial on \u003ca href=\"https://cloud.elastic.co/registration\" target=\"_self\"\u003eElastic Cloud\u003c/a\u003e. We’d love to hear what you build with it, and if you have any feedback, don’t hesitate to \u003ca href=\"https://www.elastic.co/contact\" target=\"_self\"\u003elet us know\u003c/a\u003e."}],"_metadata":{"uid":"cs8735b8afcdd57378"}}}],"publish_date":"2022-05-03","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elasticsearch Search API: A new way to locate App Search documents","seo_description_l10n":"In 8.2, Elastic has newly introduced support for the Elasticsearch query syntax for all Enterprise Search engines allow which you to take it to the next level when your search experience needs extra configurability.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltefbcf6957c5e689a","ACL":{},"created_at":"2023-11-06T20:35:45.445Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-search","label_l10n":"Cloud search","tags":[],"title":"Cloud search","updated_at":"2023-11-06T20:35:45.445Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:40:50.742Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1e6d5146b2e18cf1","created_by":"blt3c43ba848c427672","updated_by":"blt3c43ba848c427672","created_at":"2022-02-07T15:00:01.871Z","updated_at":"2022-02-07T15:00:01.871Z","content_type":"image/png","file_size":"43652","filename":"thumb-sea-of-documents.png","title":"thumb-sea-of-documents.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-02-07T15:01:40.509Z","user":"blt3c43ba848c427672"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1e6d5146b2e18cf1/620133f1d96fa00bff5eeb0c/thumb-sea-of-documents.png"},"title":"Elasticsearch Search API: A new way to locate App Search documents","title_l10n":"Elasticsearch Search API: A new way to locate App Search documents","updated_at":"2025-03-06T12:31:50.150Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/elasticsearch-search-api-a-new-way-to-locate-app-search-documents","publish_details":{"time":"2025-03-06T12:31:54.630Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb8d7df8022aa9c7b","_version":15,"locale":"en-us","ACL":{},"abstract_l10n":"In the latest version of Search UI, version 1.10, we introduced a slew of new functionality, including being extended Elasticsearch features as well as Typescript support. Follow along with code samples to get started today.","author":["blt1485ed52f0118421"],"category":["bltb79594af7c5b4199"],"created_at":"2022-04-14T23:06:20.934Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0112c5b6de4beead"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe just published Search UI version \u003ca href=\"https://github.com/elastic/search-ui/releases/tag/v1.10.0\" target=\"_self\"\u003e1.10\u003c/a\u003e, and we're excited to share it with you.\u003c/p\u003e\u003cp\u003eSearch UI 1.10 adds two important features that make building search even easier:\u003c/p\u003e\u003col\u003e\u003cli\u003eFirst-class support for Elasticsearch\u003c/li\u003e\u003cli\u003eTypescript support\u003c/li\u003e\u003c/ol\u003e\u003cp\u003eRead on to learn more.\u003c/p\u003e\u003ch2\u003eWhat is Search UI again?\u003c/h2\u003e\u003cp\u003eThere are two essential parts of building a search experience; managing your data (indexing, relevance tuning, analytics) and creating an interface so that users can search your data. Elastic's \u003ca href=\"https://github.com/elastic/search-ui\" target=\"_self\"\u003eSearch UI\u003c/a\u003e is a purpose-built library that helps you build user-facing search experiences.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eSearch UI is not a new project. In fact, we introduced our \u003ca href=\"https://www.elastic.co/blog/search-ui-1-0-0-released\" target=\"_self\"\u003e1.0\u003c/a\u003e and \u003ca href=\"https://www.elastic.co/blog/search-ui-1-2-0-released\" target=\"_self\"\u003e1.2\u003c/a\u003e releases \u003ca href=\"https://www.elastic.co/blog/search-ui-1-0-0-released\" target=\"_self\"\u003eback in 2019\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp\u003eOne fact that remains as true today as it was in 2019 – Search UI is by far the \u003ca href=\"https://codeburst.io/how-to-build-great-react-search-experiences-quickly-8c69081f328d\" target=\"_self\"\u003efastest way to build a Search Experience with Elastic\u003c/a\u003e, and we’re re-investing in it this year. We want to enhance the developer experience and expand the breadth of use cases we're able to help with. To that end, we're kicking it off with a 1.10 release that’s chock full of useful features. For future reference, bookmark the \u003ca href=\"https://docs.elastic.co/search-ui/tutorials/elasticsearch\" target=\"_self\"\u003eSearch UI tutorial\u003c/a\u003e in our documentation for additional detail.\u003c/p\u003e\u003ch2\u003eSearch UI now has first-class support for Elasticsearch\u003c/h2\u003e\u003cbr /\u003e\u003cp\u003eWhen we built Search UI, we saw a tremendous opportunity to pair it with Elastic's \u003ca href=\"https://www.elastic.co/app-search/service\" target=\"_self\"\u003eApp Search\u003c/a\u003e, which gives you a highly streamlined toolkit for building end-to-end search.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eThe reality is that our customers have varying needs with different grades of complexity. Some development teams use App Search for search applications. Some also use \u003ca href=\"https://www.elastic.co/workplace-search/\" target=\"_self\"\u003eWorkplace Search\u003c/a\u003e for internal enterprise search, and \u003ca href=\"https://www.elastic.co/elasticsearch/\" target=\"_self\"\u003eElasticsearch\u003c/a\u003e for its performance and complete customizability.\u003c/p\u003e\u003cp\u003eThe particular search solution you're using is just an implementation detail as far as search experience is concerned. We like to think of Elastic as a single search solution, and we want the same to be true of Search UI. It shouldn't dictate the experience that you deliver to end-users.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eTo that end, Search UI includes the concept of connectors.\u003c/p\u003e\u003ch2\u003eConnectors let Search UI connect to different backends\u003c/h2\u003e\u003cp\u003eConnectors are pluggable components that connect your search experience to various backends. They tell Search UI how to query your data. So regardless of your backend, you can build your search experience with Search UI and just pop in the appropriate connector.\u003c/p\u003e"}],"_metadata":{"uid":"cs561b37f248ff4c88"}}},{"image":{"image":{"uid":"blt03060ce345e03be0","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-04-14T23:10:49.553Z","updated_at":"2022-04-14T23:10:49.553Z","content_type":"image/png","file_size":"150835","filename":"search-ui-110.png","title":"search-ui-110.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-03T18:08:24.943Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt03060ce345e03be0/6258a9f9899dad4bfa8b232f/search-ui-110.png"},"_metadata":{"uid":"cs36467c476c82d979"},"caption_l10n":"**You can create a custom connector to connect to ANY API. We'll cover this below.","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csffa02350a9a2b46f"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eExample of the Elasticsearch connector in action\u003c/h2\u003e\u003cp\u003e\u003cbr/\u003eHere's an example of a simple search experience built with Search UI that shows a search box and results. It uses an AppSearchAPIConnector to query App Search for search results:\u003c/p\u003e"}],"_metadata":{"uid":"cs220fecf41b7f345c"}}},{"code":{"code":"\nimport AppSearchAPIConnector from \"@elastic/search-ui-app-search-connector\";\nimport { SearchProvider, Results, SearchBox } from \"@elastic/react-search-ui\";\n\nconst connector = new AppSearchAPIConnector({\n searchKey: \"search-371auk61r2bwqtdzocdgutmg\",\n engineName: \"search-ui-examples\",\n endpointBase: \"http://127.0.0.1:3002\"\n});\n\nexport default function App() {\n return (\n \u003cSearchProvider\n config={{\n apiConnector: connector\n }}\n \u003e\n \u003cdiv className=\"App\"\u003e\n \u003cSearchBox /\u003e\n \u003cResults /\u003e\n \u003c/SearchProvider\u003e\n );\n}\n\n","_metadata":{"uid":"csb48dd7618f28c9ea"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdbb17c357eb82942"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eUsing Elasticsearch? No problem, simply change your connector:\u003c/p\u003e"}],"_metadata":{"uid":"cs56dde908736b6756"}}},{"code":{"code":"import ElasticsearchAPIConnector from \"@elastic/search-ui-elasticsearch-connector\";\nimport { SearchProvider, Results, SearchBox } from \"@elastic/react-search-ui\";\n\nconst connector = new ElasticsearchAPIConnector({\n host: \"http://localhost:9200\",\n index: \"search-ui-examples\",\n apiKey: \"apiKeyExample\"\n});\n\nexport default function App() {\n return (\n \u003cSearchProvider\n config={{\n apiConnector: connector\n }}\n \u003e\n \u003cdiv className=\"App\"\u003e\n \u003cSearchBox /\u003e\n \u003cResults /\u003e\n \u003c/SearchProvider\u003e\n );\n}\n\n","_metadata":{"uid":"csb2ae63878fde0ffa"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs62701509f1142387"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe way you build your Search Experience doesn't need to change. Build your search experience and then configure a connector to tell it where to get your data.\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eEasy, right?\u003c/p\u003e\u003ch2\u003eMoving to production\u003c/h2\u003e\u003cp\u003e\u003cbr/\u003eWhat's the catch?\u003c/p\u003e\u003cp\u003eNo catch, really! But there are a couple of considerations you might want to make.\u003c/p\u003e\u003cp\u003eFirstly, this connector code above makes calls directly to Elasticsearch's search endpoint from the browser.\u003c/p\u003e\u003cp\u003eThis is great because it can get you up and running quickly since it doesn't require you to set up any kind of server application. It's just your front-end code making calls directly to an Elasticsearch server that only takes a moment to set up on Elastic Cloud.\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eFor many use cases like internal or non-public applications, this is sufficient. However, there are some precautions that Elastic recommends you consider before taking this setup public. They're outlined \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/es-security-principles.html#security-protect-cluster-traffic\" target=\"_self\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003cp\u003eFor public-facing search use cases, you generally want an application layer to obscure your /_search endpoint so you can restrict queries to Elasticsearch.\u0026nbsp;\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eThankfully, this connector can also run on the server with node.js, so you can easily use it as a base for an application layer.\u003c/p\u003e\u003ch2\u003eRun it on the server\u003c/h2\u003e"}],"_metadata":{"uid":"csaf1f972ce685f398"}}},{"image":{"image":{"uid":"bltec1c444da0b800f9","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2022-04-14T23:13:40.573Z","updated_at":"2022-04-14T23:13:40.573Z","content_type":"image/png","file_size":"131079","filename":"search-ui-110-2.png","title":"search-ui-110-2.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-03T18:08:24.948Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec1c444da0b800f9/6258aaa43531aa4a9d8316e2/search-ui-110-2.png"},"_metadata":{"uid":"cs390766085ccd0b1a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8e9a312e9e718de7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eA \"connector\" in Search UI is just a pure function that accepts the search state (i.e., user input, selected filters, the current page number) and converts that state into an Elasticsearch query.\u003cbr/\u003e\u003c/p\u003e\u003cp\u003eThe Elasticsearch connector is JavaScript. As described above, JavaScript can run in a browser, but it can also run on a server.\u0026nbsp;\u003cbr/\u003e\u003cbr/\u003eThis means that you can create a simple REST API that accepts search state as a parameter and uses this library to convert that search state to Elasticsearch queries on the server.\u003c/p\u003e\u003ch3\u003eServer Code, using Express\u003c/h3\u003e\u003cp\u003eYou could, for example, create a small \u003ca href=\"https://expressjs.com/\" target=\"_self\"\u003eExpress\u003c/a\u003e application that exposes the connector's operations as a REST API.\u003c/p\u003e"}],"_metadata":{"uid":"cs3bb4960595fa27d7"}}},{"code":{"code":"var express = require(\"express\");\nvar APIConnector =\n require(\"@elastic/search-ui-elasticsearch-connector\").default;\nrequire(\"cross-fetch/polyfill\");\nvar app = express();\napp.use(express.json());\napp.use(express.urlencoded({ extended: false }));\nconst connector = new APIConnector(\n {\n host: \"http://localhost:9200\", // host url for the elasticsearch instance\n index: \"search-ui-examples\", // index name where the search documents are contained\n apiKey: \"apiKeyExample\" // Optional. apiKey used to authorize a connection to Elasticsearch instance.\n }\n);\napp.post(\"/search\", async (req, res) =\u003e {\n const { query, options } = req.body;\n const response = await connector.onSearch(query, options);\n res.json(response);\n});\napp.post(\"/autocomplete\", async (req, res) =\u003e {\n const { query, options } = req.body;\n const response = await connector.onAutocomplete(query, options);\n res.json(response);\n});\nvar listener = app.listen(8080, function () {\n console.log(\"Listening on port \" + listener.address().port);\n});\n","_metadata":{"uid":"cs3f7bf5294d4d5a22"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse1c1cd57ea8bcb38"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003eClient Code - using Search UI\u003c/h3\u003eOnce you've exposed your connector on the server with our new REST API, you'll need to consume it in Search UI.\u003cbr/\u003e\u003cp\u003eFor this, you need to use custom connectors. A custom connector lets you implement a connector interface so that you can connect Search UI to any search API.\u003c/p\u003e\u003cp\u003eWe'll modify our previous example and a custom connector to connect to our new REST API.\u003c/p\u003e"}],"_metadata":{"uid":"cse3d760b40755a3da"}}},{"code":{"code":"\nimport { SearchProvider, Results, SearchBox } from \"@elastic/react-search-ui\";\n\nclass CustomConnector {\n constructor(host) {\n this.host = host;\n }\n\n async onSearch(query, options) {\n const response = await fetch(this.host + \"/search\", {\n method: \"POST\",\n headers: {\n \"Content-Type\": \"application/json\"\n },\n body: JSON.stringify({\n query,\n options\n })\n });\n return response.json();\n }\n\n async onAutocomplete(query, options) {\n const response = await fetch(this.host + \"/autocomplete\", {\n method: \"POST\",\n headers: {\n \"Content-Type\": \"application/json\"\n },\n body: JSON.stringify({\n query,\n options\n })\n });\n return response.json();\n }\n}\n\nconst connector = new CustomConnector(\"https://my-api-host/\");\n\nexport default function App() {\n return (\n \u003cSearchProvider\n config={{\n apiConnector: connector\n }}\n \u003e\n \u003cdiv className=\"App\"\u003e\n \u003cSearchBox /\u003e\n \u003cResults /\u003e\n \u003c/SearchProvider\u003e\n );\n}\n\n","_metadata":{"uid":"cs933515068a8629a9"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4a6797dde8be754a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThat's it!. You should see the `CustomConnector` executing requests to the server, providing the search state and configuration in the body. The node.js server will use the Elasticsearch connector to perform a search in Elasticsearch and return results to the client.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eSince you now perform the queries server-side, you've added an additional layer of security and alleviated some of the concerns associated with calling Elasticsearch directly from a browser.\u003c/p\u003e\u003ch2\u003eShare your feedback with us for the Elasticsearch connector Technical Preview\u003c/h2\u003e\u003cp\u003eWhile the Elasticsearch connector is now \u003ca href=\"https://www.npmjs.com/package/@elastic/search-ui-elasticsearch-connector\" target=\"_self\"\u003epublished\u003c/a\u003e and available for use, it is still in Technical Preview. As a result, you'll find a few features that are still unimplemented, and you may even find a bug or two. Rest assured, we’ll continue to improve on it as it reaches maturity.\u003c/p\u003e\u003cp\u003ePlease help us by directing your feedback, questions, or bug reports \u003ca href=\"https://github.com/elastic/search-ui/issues/704\" target=\"_self\"\u003ehere\u003c/a\u003e.\u003c/p\u003e\u003ch2\u003eTypescript support and other quality of life improvements\u003c/h2\u003e\u003cp\u003eLast but not least, this is 2022, not 2019 anymore; Typescript is a modern, scalable way to build frontend applications. To that end, we've converted this project from a JavaScript framework to Typescript with Typescript definitions.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eBetter late than never, right?\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://codesandbox.io/s/search-ui-national-parks-example-ts-k6u5iz?file=/src/App.tsx\" target=\"_self\"\u003eGive it a try in our CodeSandbox\u003c/a\u003e.\u003cbr /\u003e\u003c/p\u003e\u003cp\u003eDeveloper productivity is important to us. We'll continue to release bug fixes and introduce other quality of life features in the future. Stay tuned for more!\u003c/p\u003e"}],"_metadata":{"uid":"cs71aa10e73ddbff29"}}}],"publish_date":"2022-05-03","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Search UI 1.10 makes building search experiences for Elasticsearch even easier","seo_description_l10n":"In the latest version of Search UI, version 1.10, we introduced a slew of new functionality, including being extended Elasticsearch features as well as Typescript support. Follow along with code samples to get started today.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Search UI","label_l10n":"Search UI","keyword":"search-ui","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltaea23ea6eafbd6eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:31:21.217Z","updated_at":"2023-11-06T21:31:21.217Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.855Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt3284cac2b1db6082","ACL":{},"content_type":"image/png","created_at":"2022-04-01T16:42:56.015Z","created_by":"blt3044324473ef223b70bc674c","file_size":"66788","filename":"illustration-search-results-1-608x420.png","parent_uid":null,"tags":[],"title":"illustration-search-results-1-608x420.png","updated_at":"2022-04-01T16:42:56.015Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-04-01T17:50:02.942Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3284cac2b1db6082/62472b9080fcca09d1b99b96/illustration-search-results-1-608x420.png"},"title":"Search UI 1.10 makes building search experiences for Elasticsearch even easier","title_l10n":"Search UI 1.10 makes building search experiences for Elasticsearch even easier","updated_at":"2025-03-06T12:28:35.074Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/search-ui-1-1-0-makes-building-search-experiences-for-elasticsearch-even-easier","publish_details":{"time":"2025-03-06T12:28:39.216Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4f85135f988e8cc1","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"A recent Forbes article showed that 98% of workers want to work remotely at least some of the time, but only 16% of companies operate remotely. Elastic has always operated distributedly — we are distributed by design.","author":["blt7fc3768df8cad1f6"],"category":["bltc253e0851420b088"],"created_at":"2023-08-22T23:14:42.968Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs751998b62c17159e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eA recent \u003c/span\u003e\u003ca href=\"https://www.forbes.com/advisor/business/remote-work-statistics/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eForbes article\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e showed that 98% of workers want to work remotely at least some of the time, but only 16% of companies operate remotely.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eElastic® has always operated distributedly — we are \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-elastic-distributed-by-design\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edistributed by design\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. But, with Elasticians in more than 40 countries around the world it can prove challenging to create an environment where teams can thrive.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eWe asked three team leaders to share their best tips for successfully leading distributed teams.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eEncourage growth\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a manager, you’re at least partially responsible for your team members \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/culture-the-elastic-guide-to-finding-a-company-you-can-grow-with\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecareer progression\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. But ultimately, each Elasitican needs to drive their own career development with their managers there to support and guide them, Diana Jourdan, Senior Manager Software Engineering, says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eStacey King Poling, Director, Software Engineering, asks every one in her organization what their career goals are.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“It’s extremely important if you want to be a successful leader that you support, mentor, and groom successors within your space and to work very hard to promote within,” she says.\u003cbr /\u003e\u003cbr /\u003eBut, it’s also important for team members to take the lead and drive their own growth.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“Be proactive and take responsibility when new opportunities arise,” Diana says. “Share your goals and interests early on with your manager and ask questions.”\u003cbr /\u003e\u003cbr /\u003eGet out of your comfort zone, build a network of people with the same interests and goals, and seek out mentorship, Diana says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“Elastic has a program called peer to peer, where anyone in the company can join and be paired with folks from different organizations with either technical or soft skills they would like to learn from. You could join this program as a mentor or a mentee and it is a great opportunity to get career advice, brainstorm, or just extend the professional network.”\u003cbr /\u003e\u003cbr /\u003eAnd Madhura, Director of Engineering, agrees. She believes every individual is responsible for their own career path.\u003cbr /\u003e\u003cbr /\u003e“It is very important to have regular career conversations with your manager, as well as your team members,” she says. “The action after those conversations is different depending on your role. Set clear and simple goals for yourself, discuss and update them after your conversations with your manager.”\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1d85cd3d4aaba99a"}}},{"video":{"vidyard_uuid":"M31yAC9Tmo5VJXrSfBcdSf?","_metadata":{"uid":"cs9310e3eb90d2341f"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf7b4e386c193dd73"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eCelebrate differences\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEspecially when a team is spread across time zones, cultures, and countries, celebrating their differences but also their similarities can help bring a team closer together.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eAs a leader, you have to speak your team’s language, Stacey says.\u003cbr /\u003e\u003cbr /\u003e“Try to find answers to questions like the following: What language does your team speak collectively? What is the preferred communication method for every member of your team? What is your own preferred method of communication? How can you find the best possible middle ground?,” she says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eMadhura Chopda, Director of Engineering, believes that everyone should come as they are.\u003cbr /\u003e\u003cbr /\u003e“I genuinely believe that one can bring the most value if they come in as they are, with an open mind to adapt to various situations. There is no one solution that fits all,” she says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eStacey agrees, saying, “I try to look at the best in people and believe that if I have an open, transparent, continuous dialogue with my team members, they will genuinely support us.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eBe open\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic has teams spread over different time zones, so communication, whether synchronous or asynchronous is key.\u003cbr /\u003e\u003cbr /\u003eDiana’s team is split over 3 time zones, with the majority of team members in EMEA.\u003cbr /\u003e\u003cbr /\u003e“We value working out in the open and keeping the team Slack channel active,” she says. “Discussions happen in documents, Github, and emails.”\u003cbr /\u003e\u003cbr /\u003eAnd collaboration and brainstorming can come from asynchronous communication, says Madhura.\u003cbr /\u003e\u003cbr /\u003e“I have seen discussions and brainstorming be successful when they are run through shared docs. As a leader, I can moderate the discussion by asking questions that motivate preparation and research to be done before answering them,” she says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eBut, teams or individuals are encouraged to get on a call when a discussion gets too long or there may be a misunderstanding.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“One of the Elastic values is to assume no malice and try to understand what the others’ perspective is,” Diana says.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003eA distributed environment doesn’t mean it’s all work and no play. For non-work related stuff, Diana’s team has a shenanigans Slack channel and a weekly slot in everyone's calendar for people to share about their families, hobbies, or the latest article or joke they read, she says.\u003cbr /\u003e\u003cbr /\u003eBut in the end, it’s all about being understanding, especially when you’re not face to face.\u0026nbsp;\u003cbr /\u003e\u003cbr /\u003e“One thing that has worked with me is always trying to lead with empathy, even at times when emotions run high,” Madhura says.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003eLooking to join a company that’s distributed by design? \u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/careers/?baymax=web\u0026elektra=culture-lead-distributed-team\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBrowse open roles\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs49e8618d5dad61c4"}}}],"publish_date":"2023-08-23","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt0414045bd4e12b0e","_content_type_uid":"tags_culture"},{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"},{"uid":"bltc1899ef5008b2218","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt7759d55af6e70783","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2023-08-22T23:08:00.012Z","updated_at":"2023-08-22T23:08:00.012Z","content_type":"image/jpeg","file_size":"168396","filename":"128099_-_How_to_lead_a_distributed_team_Blog_Banner-01_V1.jpg","title":"128099_-_How_to_lead_a_distributed_team_Blog_Banner-01_V1.jpg","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T15:47:35.544Z","user":"blte369ea3bcd6ac892"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7759d55af6e70783/64e53fd07b6375b01c417442/128099_-_How_to_lead_a_distributed_team_Blog_Banner-01_V1.jpg"},"title":"How to successfully lead a team in a distributed workplace","title_l10n":"How to successfully lead a team in a distributed workplace","updated_at":"2025-03-06T12:26:33.718Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/culture-lead-distributed-team","publish_details":{"time":"2025-03-06T12:26:37.879Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte60f486821bf2935","_version":20,"locale":"en-us","ACL":{},"abstract_l10n":"Byte Buddy makes it easy to write Java agents without bytecode know-how. But class loaders and other complexities can still ruin your day. Here's a novel invokedynamic-based architecture that simplifies agent development.","author":["blt124a19c640fd9c5e","blt85c73920ec923a06"],"category":[],"created_at":"2021-11-15T14:59:04.564Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf19e9e48345e314f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOne of the nicest things about Byte Buddy is that it allows you to write a Java agent without manually having to deal with byte code. To instrument a method, agent authors can simply write the code they want to inject in pure Java. This makes writing Java agents much more accessible and avoids complicated on-boarding requirements.\u003c/p\u003e\n\u003cp\u003eAfter the first successful experiments, agent authors often get hit by a wall of complexity that the JVM throws at them: class loaders (OSGi, oh my!), class visibility, dependence on internal APIs, class path scanners, and version conflicts to name a few. \u003c/p\u003e\n\u003cp\u003eIn this article, we'll look at a relatively novel approach to break through this wall of complexity. The architecture, which is based on the invokedynamic bytecode instruction, a bytecode that is best known for leveraging Java’s lambda expressions, allows for a simple mental model when writing instrumentations. As a bonus, this also enables updating to a newer version of the agent at runtime, without having to restart the instrumented application.\u0026nbsp;The Elastic APM Java agent started the \u003ca href=\"https://github.com/elastic/apm-agent-java/issues/1337\"\u003emigration to this invokedynamic-based architecture\u003c/a\u003e over a year ago and recently completed the migration.\u003c/p\u003e\u003ch2\u003eIssues with traditional advice dispatching approaches\u003c/h2\u003e\n\u003cp\u003eLet's consider a simple example of an agent that wants to measure the response time of Java servlets. In so-called advice methods, one can define code that should run before or after the actual method. It's also possible to get access to the arguments of the instrumented method.\u003c/p\u003e"}],"_metadata":{"uid":"cs1a5254da6e27704a"}}},{"code":{"code":"@Advice.OnMethodEnter\npublic static long enter() {\n return System.nanoTime();\n}\n\n@Advice.OnMethodExit\npublic static void exit(\n @Advice.Argument(0) HttpServletRequest request,\n @Advice.Enter long startTime) {\n System.out.printf(\n \"Request to %s took %d ns%n\",\n request.getRequestURI(),\n System.nanoTime() - startTime);\n}","_metadata":{"uid":"cs43b71bd003b89b51"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5f464ea8dc6244d9"},"header_style":"H2","paragraph_l10n":"In Byte Buddy, there are two main ways how advice gets applied to an instrumented method.\u003cbr /\u003e\u003ch2\u003eInlined advice\u003c/h2\u003e\u003cp\u003eBy default, the enter and exit advice is copied into the target methods, as if the original author of the class had added the agent’s code into the method. The instrumented method, if written in plain Java, would then look something like this:\u003c/p\u003e"}],"_metadata":{"uid":"cs202e88ad5d183aa7"}}},{"code":{"code":"protected void service(HttpServletRequest req, HttpServletResponse resp) {\n long startTime = System.nanoTime();\n // original method body\n System.out.printf(\n \"Request to %s took %d ns%n\",\n request.getRequestURI(),\n System.nanoTime() - startTime);\n}","_metadata":{"uid":"cs0d9566108497f369"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9f2ded6761ae33d6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe advantage is that the advice has access to any value or type that is normally reachable from the instrumented method. In the above example, this allows accessing \u003ccode\u003ejavax.servlet.http.HttpServletRequest\u003c/code\u003e, even though the agent does not itself ship with that interface. As the agent’s code is run within the targeted method, it simply picks up the type definition that is already available to the method itself.\u003c/p\u003e\n\u003cp\u003eOn the downside, the advice code is no longer executed in the context that it is defined within. As a result, you can, for example, not set a breakpoint in an advice method, because it is never actually called. Remember: the methods are merely used as a template.\u003c/p\u003e\n\u003cp\u003eBut the real issue is that factoring code out of the advice methods or calling any methods that are normally reachable from advice is no longer possible. Since all code is now executed from the instrumented method, the agent might run on an entirely different class loader with no connection to the instrumented method, so even public methods might not be invokable from the instrumented code. We'll see more of this issue in the next section. \u003c/p\u003e\u003ch2\u003eDelegated advice\u003c/h2\u003eFor a similar but still very different approach, it is possible to instruct Byte Buddy to delegate to the advice methods instead. This can be controlled via the advice annotation attribute \u003ccode\u003e@Advice.OnMethodEnter(inline = false)\u003c/code\u003e. By default, Byte Buddy will delegate to an advice method via a static method call. The instrumented method would then look like this:"}],"_metadata":{"uid":"cse5317b3033a1a9b8"}}},{"code":{"code":"protected void service(HttpServletRequest req, HttpServletResponse resp) {\n long startTime = AdviceClass.enter();\n // original method body\n AdviceClass.exit(req, startTime);\n}","_metadata":{"uid":"cs39e3dd5952a96d1a"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs965d50ca112e2e9c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eSimilarly to before, it is up to the agent’s developer to ensure that the advice code is visible to the instrumented method. If the instrumented method does not share a class loader hierarchy with the agent’s code, this instrumentation would yield a \u003ccode\u003eNoClassDefFoundError\u003c/code\u003e upon reaching the above method. And even if the delegated advice is reachable from the agent, argument types such as \u003ccode\u003eHttpServletRequest\u003c/code\u003e might not be available to the agent’s class loader. This would then only move the error to the agent’s code upon its advice invocation.\u003c/p\u003e\u003ch2\u003eClass loader issues\u003c/h2\u003e\n\u003cp\u003eBy default, agents get added to the system class loader when they are attached to the JVM and the \u003ccode\u003ejava.lang.instrument.Instrumentation\u003c/code\u003e interface offers ways to add the agent to the bootstrap class loader. In theory, adding classes to the bootstrap class loader makes them visible everywhere. However, some class loaders (such as OSGi) only allow certain classes (such as \u003ccode\u003ejava.*, com.sun.*\u003c/code\u003e) to be loaded from the system or bootstrap class loader. A common solution is to instrument all class loaders and explicitly redirect class loading of classes in certain packages directly to the bootstrap loader.\u003c/p\u003e\n\u003cp\u003eBut adding classes to the system class loader and the bootstrap class loader also comes with downsides. The additional classes can slow down class path scanners or even cause failures that prevent the application from starting. See \u003ca href=\"https://github.com/elastic/apm-agent-java/pull/364\"\u003eelastic/apm-agent-java#364\u003c/a\u003e for an example. Also, it's not possible to unload classes of such a persistent class loader, which is an issue when designing an agent that wants to offer the possibility of its own removal during runtime.\u003c/p\u003e\n\u003cp\u003eConceptually, there are only two approaches to overcoming these class loader issues where an advice class wants to invoke different methods that are normally shipped with the agents but where these methods might not be reachable. Either this code must be injected into the instrumented class' class loader such that they can be looked up directly from there. Or, a new class loader must be defined as a child of this former class loader where any additional types can now be located by implementing such a custom class loader.\u003c/p\u003e\n\u003cp\u003eFor the first approach, Byte Buddy comes with utilities that allow classes to be injected into any class loader \u003ccode\u003e(net.bytebuddy.dynamic.loading.ClassInjector)\u003c/code\u003e. While this seems like a straightforward fix, it comes with major drawbacks. The more flexible injectors are built on top of internal APIs such as \u003ccode\u003esun.misc.Unsafe / jdk.internal.misc.Unsafe\u003c/code\u003e. And also safer-sounding class injector strategies like \u003ccode\u003eUsingReflection\u003c/code\u003e use clever workarounds to circumvent the safeguards that have been introduced in recent Java versions that usually disallow accessing private fields using \u003ccode\u003eUnsafe::putBoolean\u003c/code\u003e. As of today, it's a cat-and-mouse game between Oracle who restricts access to internal APIs and enforces visibility in the reflection API, and the discovery of new loopholes that can circumvent these. At the same time, the official gateway of using a method handle lookup is barely compatible with agents and its integration is an open issue (\u003ca href=\"https://bugs.openjdk.java.net/browse/JDK-8200559\"\u003ehttps://bugs.openjdk.java.net/browse/JDK-8200559\u003c/a\u003e). Therefore, it seems rather risky to build a whole agent architecture using the currently unsafe APIs that Oracle is aiming to lock down further.\u003c/p\u003e\n\u003cp\u003eWith the second approach, all advice and helper classes are loaded in a child class loader. This works without relying on unsafe API because the class loader is implemented by the agent developer and because a class loader can get access to all types that are defined by its parent class loader.\u003c/p\u003e\n\u003cp\u003eAnother advantage of loading helper classes in a dedicated class loader as opposed to injecting them into the instrumented class's class loader is that it is possible to unload these classes. This allows to fully detach the agent from the application and to attach a new version of the agent without leaving any trace of the previous version, also known as live-updating the agent. Byte Buddy already allows reverting all the instrumentations it has applied via re-transformation. When no other references to the agent helper class loaders are leaked, this makes all its objects, classes, and even the entire class loader eligible for garbage collection.\u003c/p\u003e\n\u003cp\u003eOne complication with this approach is that the advice class is not visible to the instrumented class. The instrumented method \u003ccode\u003eHttpServlet::service\u003c/code\u003e from the previous example calls \u003ccode\u003eAdviceClass\u003c/code\u003e via a static method call. This would lead to a \u003ccode\u003eNoClassDefFoundError\u003c/code\u003e at runtime, as \u003ccode\u003eAdviceClass\u003c/code\u003e is not visible in the context of the \u003ccode\u003eHttpServlet::service method\u003c/code\u003e. That's because \u003ccode\u003eAdviceClass\u003c/code\u003e is loaded by a child class loader of the instrumented class \u003ccode\u003e(HttpServlet)\u003c/code\u003e. While \u003ccode\u003eAdviceClass\u003c/code\u003e can access classes that are visible to the instrumented class, such as the \u003ccdoe\u003eHttpServletRequest argument, the reverse is not true. \u003c/cdoe\u003e\u003c/p\u003e\u003ch2\u003eIntroducing an invokedynamic-based advice dispatching approach\u003c/h2\u003e\n\u003cp\u003eThere's another, lesser-known alternative to dispatching advice via a static method call. With \u003ccode\u003enet.bytebuddy.asm.Advice.WithCustomMapping::bootstrap\u003c/code\u003e, you can instruct Byte Buddy to insert an \u003ccode\u003einvokedynamic\u003c/code\u003e bytecode instruction into the instrumented methods. This instruction was added in Java 7 with the goal of better support for dynamic languages in the JVM, such as Groovy and JRuby. \u003c/p\u003e\n\u003cp\u003eIn a nutshell, an \u003ccode\u003einvokedynamic\u003c/code\u003e invocation consists of two phases: looking up a \u003ccode\u003eCallSite\u003c/code\u003e and then invoking the \u003ccode\u003eMethodHandle\u003c/code\u003e the \u003ccode\u003eCallSite\u003c/code\u003e holds. If the same invokedynamic instruction is executed another time, \u003ccode\u003eCallSite\u003c/code\u003e from the initial lookup will be invoked.\u003c/p\u003e\n\u003cp\u003eThe following example shows how an invokedynamic instruction looks like in the bytecode of a method.\u003c/p\u003e\n\u003cp\u003e\u003ccode\u003e// InvokeDynamic #1:exit:(Ljavax/servlet/ServletRequest;long)V\u0026lt;/p\u0026gt;\n\u0026lt;p\u0026gt;invokedynamic #1076, 0 \u003c/code\u003e\u003c/p\u003e\u003cbr\u003eThe lookup of the \u003ccode\u003eCallSite\u003c/code\u003e happens within a so-called bootstrap method. This method receives a couple of arguments for the lookup, such as the advice class name, method name, and the advice's \u003ccode\u003eMethodType\u003c/code\u003e that represents the arguments and return type. The following example shows how the bootstrap method is declared within the bytecode of a class."}],"_metadata":{"uid":"cs505c82d5062668be"}}},{"code":{"code":"BootstrapMethods:\n 1: #1060 REF_invokeStatic java/lang/IndyBootstrapDispatcher.bootstrap:(Ljava/lang/invoke/MethodHandles$Lookup;Ljava/lang/String;Ljava/lang/invoke/MethodType;[Ljava/lang/Object;)Ljava/lang/invoke/CallSite\n Method arguments:\n #1049 org.example.ServletAdvice\n #1050 1\n #12 javax/servlet/http/HttpServlet\n #1072 service\n #1075 REF_invokeVirtual javax/servlet/http/HttpServlet.service:(Ljavax/servlet/HttpServletRequest;Ljavax/servlet/HttpServletResponse;)V","_metadata":{"uid":"cs679706426ac018de"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5c714c6c23c4107f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe class that contains the bootstrap method (in this case \u003ccode\u003ejava/lang/IndyBootstrapDispatcher.bootstrap)\u003c/code\u003e; must be visible from any instrumented class. Therefore, this class needs to be added to the bootstrap class loader. To ensure compatibility with filtering class loaders, such as OSGi loaders, the class is placed into the \u003ccode\u003ejava.lang\u003c/code\u003e package.\u003c/p\u003e\n\u003cp\u003eWhile this approach doesn't completely avoid class injection, injecting only a single class does result in a reduced surface of eternal classes that are added by the agent and reduces the need to refactor an existing agent if future releases of the JDK no longer allow for such injection.\u003c/p\u003e\n\u003cp\u003eIn the Elastic APM Java agent, the bootstrap method will create a new class loader whose parent is the class loader of the instrumented class and load the advice and any amount of helpers from it. We can then load the advice class from this newly created class loader given the advice class name that is provided as an argument to the bootstrap method \u003ccode\u003e(Method arguments: org.example.ServletAdvice)\u003c/code\u003e.\u003c/p\u003e\n\u003cp\u003eUsing the other arguments of the bootstrap method, we can construct a \u003ccode\u003eMethodHandle\u003c/code\u003e and a \u003ccode\u003eCallSite\u003c/code\u003e that represents the advice method within the child class loader we created. For our needs, the target method is always the same. Thus, a \u003ccode\u003eConstantCallSite\u003c/code\u003e can be returned that allows the JIT to inline the advice method.\u003c/p\u003e\n\u003cp\u003eNow that we only rely on exactly one class to be visible from the instrumented methods (\u003ccode\u003ejava.lang.IndyBootstrapDispatcher\u003c/code\u003e), we can further isolate the agent by loading its classes that aren't specific to a particular library it instruments from a dedicated class loader. As described in the previous section, hiding the agent's classes from the regular class loader hierarchy avoids compatibility issues, for example with class path scanners. It also allows the agent to ship any dependencies, such as Byte Buddy or a logging library, without having to shade (aka relocate) the dependencies to the agent's namespace. This makes debugging the agent that much easier. Due to the isolated class loader, there is no concern about conflicting classes that may be present in the application's class loader hierarchy. More details on the implementation of one such isolated class loader can be found in the Elastic APM Java agent's source code for \u003ca href=\"https://github.com/elastic/apm-agent-java/blob/43b0e11917a4f6eddb38b02bfe7a5917985058d9/elastic-apm-agent/src/main/java/co/elastic/apm/agent/premain/ShadedClassLoader.java#L1\"\u003eShadedClassLoader\u003c/a\u003e.\u003c/p\u003e\n\u003cp\u003eThe resulting class loader hierarchy looks like this:\u003c/p\u003e"}],"_metadata":{"uid":"cs0e827f908d8eb3e3"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"blt272e6c07cfb98930","ACL":{},"content_type":"image/png","created_at":"2021-11-15T15:05:23.998Z","created_by":"blt1e57c6588ae1816e","file_size":"7892","filename":"blog-elastic-invokedynamic-1.png","parent_uid":null,"tags":[],"title":"blog-elastic-invokedynamic-1.png","updated_at":"2021-11-15T15:05:23.998Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-11-22T18:00:00.549Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt272e6c07cfb98930/6192773434c0aa7f9f958e57/blog-elastic-invokedynamic-1.png"},"_metadata":{"uid":"csf3b6729d295cfc68"},"caption_l10n":"","alt_text_l10n":"Class loader hierarchy","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs43cecf4c2963aae6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNote that the agent helper class loader, which loads the advice and library-specific helper classes, has two parents: The class loader of the instrumented class (such as the class loader that servlet containers create for each web application) and the agent class loader. That allows advice and helper classes to access both types that are visible from the instrumented class' class loader and the agent class loader. While having multiple parents is not offered by the built-in class loaders, it is relatively straightforward to implement it oneself. Byte Buddy also comes with an implementation called\u0026nbsp;\u003ccode\u003enet.bytebuddy.dynamic.loading.MultipleParentClassLoader\u003c/code\u003e.\u0026nbsp;\u003cbr\u003e\u003c/p\u003e\n\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003eIn summary, this section described how the \u003cstrong\u003einvokedynamic instruction can be used to call an advice method that is loaded from a child class loader of the instrumented class' defining class loader\u003c/strong\u003e. As a result, this allows the agent to hide its classes from the application while providing a way to invoke the isolated methods from the application classes it instruments. This is useful because the advice and all other classes loaded by this class loader can access the instrumented libraries' classes while the advice code is still executed as regular code. It also avoids injecting the advice and helper classes into the target class loader directly, which is only possible today by using internal APIs that Oracle is aiming to increasingly lock down.\u003c/p\u003e\u003ch2\u003eAssignReturned\u003c/h2\u003e\n\u003cp\u003eWhile advice that uses either inlining or delegation is implemented by the same API, and seems rather similar as a result, there are differences. Delegation advice cannot easily write values in the scope of the instrumented method. When advice is inlined, the advice method can simply assign values to annotated parameters which Byte Buddy then translates to a replacement of the represented value during the inlining process. As an example, the following inlined advice would replace the first argument of an instrumented method - here a Runnable - with a wrapper instance that also implements the Runnable interface, which reports any future invocations back to the agent:\u003c/p\u003e"}],"_metadata":{"uid":"csf92aa7e6dcb19824"}}},{"code":{"code":"@Advice.OnMethodEnter\npublic static void enter(\n @Advice.Argument(value = 0, readOnly = false) Runnable callback) {\n callback = new TracingRunnable(callback);\n}","_metadata":{"uid":"cs5cddd92299799db2"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0354be126dc46847"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs the above code is inlined, the advice simply replaces the value that is assigned to the first argument of the instrumented method. As a result, the instrumented method is now executed as if its caller had already passed the \u003cspan data-type='inlineCode'\u003eTracingRunnable\u003c/span\u003e to it.\u003c/p\u003e\u003cp\u003eWhen using delegation, this does not work, unfortunately. With delegation, the new value would only be assigned to the parameter of the advice method, without affecting the instrumented method’s assignment which would still carry the original runnable after the advice method was executed.\u003c/p\u003e\u003cp\u003eTo offer such assignments when using delegating advice, Byte Buddy recently introduced the Advice.AssignReturned post-processor. Advice post processors are handlers that are invoked after an advice method was dispatched, to allow for additional operations that are independent of the advice that was applied. But most importantly, post processors always generate code that is inlined into the instrumented method, even if the advice itself is invoked via delegation. This allows for writing values in the scope of the instrumented method if these values were returned from the advice method. With post processors being an extension to the regular Advice implementation, they need to first be registered manually by calling:\u003c/p\u003e"}],"_metadata":{"uid":"cs3201090a301b1d10"}}},{"code":{"code":"Advice.withCustomBinding()\n .with(new Advice.AssignReturned.Factory());","_metadata":{"uid":"cs609abe6d88d446bd"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa6faaf2b6d22a701"},"header_style":"H2","paragraph_l10n":"As the name suggests, this post-processor allows an \nassignment of the value that is returned from an advice method to \nparameters of the instrumented method. To implement the above example, \none would, for example, instruct the post-processor to assign the \nreturned value to the instrumented method’s first argument as it was \ndone before:\u003cbr\u003e"}],"_metadata":{"uid":"cs518de51234170b6b"}}},{"code":{"code":"@Advice.OnMethodEnter(inline = false)\n@Advice.AssignReturned.ToArguments(@ToArgument(0))\npublic static Runnable enter(@Advice.Argument(0) Runnable callback) {\n return new TracingRunnable(callback);\n}","_metadata":{"uid":"cs96b84dac42b56166"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf9dca34186a4b797"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eJust as in the inlined example, the instrumented method would now observe the \u003ccode\u003eTracingRunnable\u003c/code\u003e\n as its first argument as it was replaced by the post-processor. And \nbesides assigning argument values, it is also possible to assign values \nto fields, to the method’s return value, its thrown exception and even \nto its \u003cem\u003ethis\u003c/em\u003e reference if the method is non-static.\u003c/p\u003e\n\n\u003cp\u003eIn some cases, it might however be required to assign more than one \nvalue. With inlined advice, this is straightforward to implement by \nassigning multiple values within the advice method directly to each \nannotated parameter. With delegating advice, multiple assignments are \nhowever similarly easy to implement by returning an array as a return \ntype and by specifying what index of the returned array contains what \nvalue.\u003c/p\u003e\n\u003cp\u003eTo extend the hypothetical example, assuming that the instrumented \nmethod also requires an executor service as a second argument, we could \nenforce the usage of a freshly created cached thread pool by providing \nit as a second argument to an advice method’s returned array. When \nannotating the advice method’s assignments, every assignment now only \nneeds to indicate what array index represents which of the assigned \nvalues.\u003c/p\u003e"}],"_metadata":{"uid":"csa18c04e611774ac6"}}},{"code":{"code":"@Advice.OnMethodEnter(inline = false)\n@Advice.AssignReturned.ToArguments(\n @ToArgument(value = 0, index = 0, typing = DYNAMIC),\n @ToArgument(value = 1, index = 1, typing = DYNAMIC))\npublic static Runnable enter(@Advice.Argument(0) Runnable callback) {\n return new Object[] {\n new TracingRunnable(callback),\n Executors.newCachedThreadPool()\n };\n}","_metadata":{"uid":"cs0b419cbf466d3901"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2839777f12a59432"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFinally, as \u003ccode\u003eObject-typed\u003c/code\u003e arrays might contain non-assignable values, the annotations must specify that dynamic typing is to be used. Doing so, Byte Buddy attempts a type-casting of values prior to assigning. To avoid the potential \u003ccode\u003eClassCastExceptions\u003c/code\u003e from affecting the instrumented application, the post processor can be configured to suppress these exceptions.\u003c/p\u003e"}],"_metadata":{"uid":"csb6d01cc3a62d86a6"}}},{"code":{"code":"new Advice.AssignReturned().Factory()\n .withSuppressed(ClassCastException.class)","_metadata":{"uid":"cs6423722539a73037"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csdb05f662b56f872e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFailing to configure dynamic typing in cases when the array contains non-assignable values would lead to an exception during the instrumenting of a class. Aside from loss of instrumentation, the application will not be affected.\u003c/p\u003e\u003ch2\u003eTrade-offs\u003c/h2\u003e\n\u003cp\u003eOne of the limitations of this architecture is that it's not possible to support Java 6 applications as it relies on the \u003ccode\u003einvokedynamic bytecode\u003c/code\u003e instruction that has been added in Java 7. As the Elastic APM Java agent never supported Java 6, this was not an issue in that case. Many other agents don't even support Java 7 anymore, whose market share is just around 1-5%, depending on what study is considered.\u003c/p\u003e\n\u003cp\u003eIn addition to the requirement of Java 7+, the instrumented class has to be at bytecode level 51, meaning that it has to be compiled with a target of Java 7 or later. That's because it's not possible to use \u003ccode\u003einvokedynamic\u003c/code\u003e instructions for older class file versions. Some libraries, in particular older JDBC drivers, which an agent may want to instrument, are sometimes compiled with quite old class file versions. There's a relatively simple workaround, though. Using a \u003ccode\u003eClassVisitor\u003c/code\u003e, we can let ASM re-write the bytecode to class file version 51 (Java 7). This has proven to be a stable and reliable way since this has been introduced in the Elastic APM Java agent. It does come with a bit of a performance penalty but we only need to do that for the relatively rare occasion where the class file version of the instrumented class is lower than 51.\u003c/p\u003eAnother thing to keep in mind is that early versions of Java 7 (before update 60, which released in May 2014) and Java 8 (before update 40, which released in March 2015) have bugs in their \u003ccode\u003einvokedynamic\u003c/code\u003e and \u003ccode\u003eMethodHandle\u003c/code\u003e support. For that reason, the Elastic APM Java agent disables itself if it's detected to run on these JVM versions.\u003cbr\u003e\u003cbr\u003e\u003ch2\u003eNext Steps\u003c/h2\u003e\n\u003cp\u003eHave a look at the \u003ca href=\"https://www.elastic.co/guide/en/apm/agent/java/current/intro.html\"\u003edocs\u003c/a\u003e to find out more about the Elastic APM Java Agent and how it can help you to identify and fix performance issues in your application. If you want to build your own Java agent, visit \u003ca href=\"https://bytebuddy.net\"\u003ebytebuddy.net\u003c/a\u003e to learn more.\u003c/p\u003e"}],"_metadata":{"uid":"cs33d17829c1bac146"}}}],"publish_date":"2021-11-22T14:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Embracing invokedynamic to tame class loaders in Java agents","seo_description_l10n":"Byte Buddy makes it easy to write Java agents without bytecode know-how. But class loaders and other complexities can still ruin your day. Here's a novel invokedynamic-based architecture that simplifies agent development.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt2ad8c87e6be56a66","ACL":{},"content_type":"image/png","created_at":"2020-06-18T00:07:58.016Z","created_by":"bltf6ab93733e4e3a73","file_size":"61385","filename":"blog-thumb-ml-anomaly-laptop.png","tags":[],"title":"blog-thumb-ml-anomaly-laptop.png","updated_at":"2020-06-18T00:07:58.016Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-22T15:00:00.000Z","user":"bltf6ab93733e4e3a73"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2ad8c87e6be56a66/5eeab05e7bcaf625d820e601/blog-thumb-ml-anomaly-laptop.png"},"title":"Embracing invokedynamic to tame class loaders in Java agents","title_l10n":"Embracing invokedynamic to tame class loaders in Java agents","updated_at":"2025-03-06T12:21:23.612Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/embracing-invokedynamic-to-tame-class-loaders-in-java-agents","publish_details":{"time":"2025-03-06T12:21:27.983Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8a3a98d212becf67","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Hello from the Elastic DevRel team! In this newsletter, we cover the first pre-release of Elasticsearch and the Elastic Stack 9.0, the availability of Elastic Cloud Serverless on Azure, the latest blogs and videos, and upcoming events.","author":["blt45e4796f6aeab23a"],"category":["bltc17514bfdbc519df"],"created_at":"2025-03-04T08:28:47.482Z","created_by":"blt96ac6007eba0a223","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3cf37c76981816a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(38, 38, 38);font-size: 12pt;'\u003eHello from the Elastic DevRel team! \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIn this newsletter, we cover the first pre-release of Elasticsearch and the Elastic Stack 9.0, the availability of Elastic Cloud Serverless on Azure, the latest blogs and videos, and upcoming events, including ElasticONs in Sydney and Singapore.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdb3bd3ba9d5f1a5a"}}},{"title_text":{"title_text":[{"title_l10n":"What’s new","_metadata":{"uid":"cscfb0d60bd39449e3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003eThe first 9.0 pre-release, 9.0.0-beta1, of \u003c/span\u003e\u003ca href=\"https://github.com/elastic/elasticsearch/releases/tag/v9.0.0-beta1\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://github.com/elastic/kibana/releases/tag/v9.0.0-beta1\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eKibana\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003e, and the rest of the Elastic Stack \u003c/span\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003eis now available\u003c/span\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003e. Give it a try, let us know what works and what doesn't, and please don't use it in production (yet).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003eThe easiest way to try it out today is through start-local: \u003c/span\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003ecurl -fsSL https://elastic.co/start-local | sh -s -- -v 9.0.0-beta1\u003c/span\u003e \u003c/span\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 11pt;\"\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003eWe'll dive into more features in the following (pre-) releases, but for beta1, here is an overview of what's now available in ES|QL, the new piped query language.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5d90010ab3741bf4"}}},{"title_text":{"title_text":[{"title_l10n":"1. Lookup joins","_metadata":{"uid":"csa030b335d292c28f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLookup joins, a highly requested feature, are the first of many planned join commands. These joins function like SQL LEFT OUTER JOINs, enabling the direct joining of data or event streams with lookup indices. The ES|QL editor suggests lookup indices and conditions to expedite query construction.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6e2e284ae44af890"}}},{"title_text":{"title_text":[{"title_l10n":"2. KQL filtering inside ES|QL queries","_metadata":{"uid":"csf75f6915464ea3eb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eKQL filtering, the Kibana Query Language, is integrated within ES|QL queries. This integration allows for the combination of KQL's expressive filtering capabilities with ES|QL's transformation features, resulting in faster query execution and improved precision.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9cb3e8be358f7fef"}}},{"title_text":{"title_text":[{"title_l10n":"3. Inference API, MATCH, and more","_metadata":{"uid":"cs656958a6422b6f49"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSemantic search is expanded with access to the Inference API, enabling more accurate AI-driven search experiences. The MATCH command now supports a wider range of field types, query parameters, and optimizations for enhanced accuracy.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa0a5cc27b8a5f203"}}},{"title_text":{"title_text":[{"title_l10n":"4. New functions and commands for statistical analysis","_metadata":{"uid":"cs7616a6944e26de2f"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Standard Deviation function is natively available in ES|QL. A new categorization function automatically groups similar log messages to highlight patterns. Additionally, a failure store for debugging purposes is introduced to store query failures, facilitating pattern analysis and improved reliability.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdbe2378e29cd407c"}}},{"title_text":{"title_text":[{"title_l10n":"5. Performance enhancements","_metadata":{"uid":"csdb7ab52070b3ced6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eES|QL includes several internal improvements to enhance query performance: acceleration of case-insensitive matching using TO_UPPER/TO_LOWER pushdowns, smarter field capabilities detection for optimized query execution, and memory reductions for faster response times and lower resource usage.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor a complete list of features and changes, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elastic-stack/9.0/release-notes-elasticsearch-9.0.0.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003echeck out the release notes\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(68, 68, 68);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1c209575299dfcd9"}}},{"title_text":{"title_text":[{"title_l10n":"Elastic Cloud Serverless: Technical preview on Microsoft Azure","_metadata":{"uid":"cs5daf835493cae403"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that Elastic Cloud Serverless has gone GA on AWS, we’re starting to expand to other cloud providers. The first one is\u003c/span\u003e\u003cspan style='color:rgb(68, 68, 68);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-serverless-microsoft-azure-tech-preview\"\u003e\u003cspan style='font-size: 12pt;'\u003eMicrosoft Azure\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, where we have just added the first region as a technical preview.For an in-depth, external look at it, read Arnold Van Wijnbergen’s\u003c/span\u003e\u003cspan style='color:rgb(68, 68, 68);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://qensus.com/elastic/partner-news-evaluation-of-elastic-cloud-serverless-on-microsoft-azure-technical-preview/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eEvaluation of Elastic Cloud Serverless on Microsoft Azure (Technical Preview)\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(68, 68, 68);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfbbe05f64f93324a"}}},{"title_text":{"title_text":[{"title_l10n":"Blogs, videos, and interesting links","_metadata":{"uid":"csd1230d88ce64022e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDeepSeek R1: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eLearn how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/deepseek-rag-ollama-playground\"\u003e\u003cspan style='font-size: 12pt;'\u003erun a local instance of DeepSeek and connect to it from within Kibana\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Dave Erickson and Jakob Reiter.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eVector search: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eValentin Crettaz provides a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/introduction-to-vector-search\"\u003e\u003cspan style='font-size: 12pt;'\u003equick introduction to vector search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, explains how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/vector-search-set-up-elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003eset up vector search in Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and shows how to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/hybrid-search-elasticsearch\"\u003e\u003cspan style='font-size: 12pt;'\u003ecraft hybrid search queries\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSearch relevance: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ePeter Straßer discusses the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/compound-word-search\"\u003e\u003cspan style='font-size: 12pt;'\u003esearch challenges that come with compound words and how to address them\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOpenTelemetry:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Follow Bahubali Shetti as he \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/openai-tracing-langtrace-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003etraces a RAG-based Chatbot with Elastic distributions of OpenTelemetry and Langtrace\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSecurity:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-detect-malicious-browser-extensions-using-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003eDetect malicious browser extensions using Elastic\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Aaron Jewitt.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eElastic APM: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eHaidar Braimaanie explains \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/opentelemetry-cpp-elastic\"\u003e\u003cspan style='font-size: 12pt;'\u003ehow to monitor your C++ applications with Elastic APM\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCLIP: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eJeffrey Rengifo and Tomás Murúa explore \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/openai-clip-alternatives\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenAI CLIP (Contrastive Language–Image Pre-training) alternatives\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFaceted search:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/faceted-search-examples-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eUse facet search in Elasticsearch to narrow down options within categories\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with Andre Luiz.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCheck out these videos:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.youtube.com/watch?v=oKDR90456SM\"\u003e\u003cspan style='font-size: 12pt;'\u003eBuilding AI search: Live insights from Elastic engineering\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.youtube.com/watch?v=CyNJScJA-ZY\u0026t=258s\"\u003e\u003cspan style='font-size: 12pt;'\u003eOTel for Python: Traces with custom spans — Daily Elastic Byte S06E04\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e by Jessica Garson\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.youtube.com/live/2hI9HjEKORg\"\u003e\u003cspan style='font-size: 12pt;'\u003eOTel for Java (Traces) — Daily Elastic Byte S06E05\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e by Piotr Przybyl\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFeatured blogs and projects from the community:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBuild an \u003c/span\u003e\u003ca href=\"https://www.linkedin.com/pulse/building-ai-powered-search-system-using-rag-vh-chaudhary-veesf/?trackingId=bGxndRqyRLy2B9s1vPpIbA%3D%3D\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-Powered Search System using RAG and Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with VH Chaudhary\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://medium.com/newsdatahub/from-redis-to-elasticsearch-when-simple-solutions-hit-their-limits-b7fa095b2232\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eWhen Redis hit the wall: Scaling search from thousands to millions of articles\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e by Olga\u003c/span\u003e\u003ca href=\"https://medium.com/newsdatahub/from-redis-to-elasticsearch-when-simple-solutions-hit-their-limits-b7fa095b223\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp;\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://blog.telary.io/migrating-off-app-entreprise-search/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMigrating off AppSearch / EntrepriseSearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, where Constant Deschietere provides some tips for moving data and queries\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://github.com/githubesson/csves/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCSVES (CSV to Elasticsearch)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e: A flexible tool for importing CSV data into Elasticsearch with automatic field detection and mapping\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs571230018608da7d"}}},{"title_text":{"title_text":[{"title_l10n":"Upcoming events ","_metadata":{"uid":"csd0ba4a9f3f8e2e83"},"header_style":"H2","paragraph_l10n":""}],"_metadata":{"uid":"cs52eea8be94c41211"}}},{"title_text":{"title_text":[{"title_l10n":"Americas","_metadata":{"uid":"cs15c5f36f254268f5"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eBoston: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elasticsearch-boston/events/306012449/?recId=4a63a4e6-36f0-4a3e-a97e-90a6e1ba65d1\u0026recSource=keyword_search\u0026searchId=2851a10a-81c9-423d-a80c-501c363adffb\u0026eventOrigin=find_page$all\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch, Vectors, and Hybrid: The new era of Search\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 6\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSilicon Valley: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-silicon-valley-user-group/events/306124074/?eventOrigin=group_upcoming_events\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic AI: Agentic Workflows \u0026amp; LLMs + Research for Real-World Impact\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 6\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePhoenix: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-phoenix-user-group/events/306159187/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eConfluent x Elastic joint meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 6\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eWashington DC:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/washington-dc-elastic-fantastics/events/306010528/?recSource=chapter-search\u0026recId=65d5ea73-ee6e-41c0-8dc9-f9e0a8b03f47\u0026searchId=884bc49f-e3fa-4070-88bd-e0d1a82eb5ec\u0026eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eThe new era of Search, Search: a new era\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e —\u0026nbsp; March 12\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDurham:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://allthingsopen.ai/about\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eAll Things Open AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — March 17–18\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDallas: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-dallas-user-group/events/306239185/?slug=elastic-dallas-user-group\u0026eventId=306239185\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearch in a Digital Thread using eQube DaaS platform \u0026amp; Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — March 18\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLancaster:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/lancaster-elastic-user-group/events/pnqvjtyhcfbzb/?eventOrigin=find_page$all\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCommunity Monthly meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e —\u0026nbsp; March 19\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eChicago:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-chicago-user-group/events/305542818/?eventOrigin=group_events_list\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic User Group Meetup\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 20\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSeattle:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/big-data-bellevue-bdb/events/305472422/?eventOrigin=group_upcoming_events\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic + Big Data Bellevue\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp; \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 20\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eToronto:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-toronto-user-group/events/306015499/?slug=elastic-toronto-user-group\u0026eventId=301883000\u0026isFirstPublish=true\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003edo MORE with stateLESS Elasticsearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp; March 20\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSanta Clara: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.usenix.org/conference/srecon25americas\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSRECon Americas\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e —\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 25–27\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eVirtual Meetup:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-united-states-and-canada-virtual/events/305135329/?slug=elastic-united-states-and-canada-virtual\u0026eventId=305135329\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eReal-Time Log Monitoring and Visualization Using ELK and Kafka\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 27\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSeattle:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://lu.ma/seattle-startup-summit\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSeattle Startup Summit\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e—\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e March 28\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf6e54d5d6664c91f"}}},{"title_text":{"title_text":[{"title_l10n":"Europe, Middle East, and Africa","_metadata":{"uid":"cs729ad98a408ecf91"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eZurich: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://devopsdays.org/events/2025-zurich/welcome/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eDevOpsDays Zurich\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp; \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 12–13\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eParis: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elasticfr/events/303824144/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eLa crème de la crème\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u0026nbsp; \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 13\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAmsterdam: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/elastic-nl/events/305919766\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic and Hopsworks meetup, LLM usage in building pipelines\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 13\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStockholm: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.meetup.com/stockholm-elastic-fantastics/events/306131300\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eTracking abuse using intelligence with Elastic \u0026amp; Tele2\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 13\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eWroclaw:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://2025.boilingfrogs.pl\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eBoilingFrogs\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 15\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAmsterdam:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://webdevcon.nl/session/observability-for-javascript-engineers/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eWebdevcon\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 21\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFlorence: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://osday.dev/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eOpenSourceDay\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 21\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSaint-Herblain: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.lacantine.co/agenda/event/25-03-2025-enitechfest/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eENI Tech Fest Saint-Herblain\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (France) \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 25\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTurin:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://2025.cloudconf.it/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eCloud Conf\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 26\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLondon:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://sreday.com/2025-london-q1/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eSREDay London\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 27–28\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs15b5c765139aeba8"}}},{"title_text":{"title_text":[{"title_l10n":"Asia-Pacific","_metadata":{"uid":"cs3638c1f212f00d57"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAhmedabad: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://laracon.in\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eLaracon India\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(34, 34, 34);font-size: 12pt;'\u003e— \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMarch 8–9\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf3cdcb84cd214fe4"}}},{"title_text":{"title_text":[{"title_l10n":"ElasticON Tour","_metadata":{"uid":"cs6d08e5cf07764619"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic's free, one-day conference series is coming to you. Join us to learn what's hot at Elastic right now, watch talks or demos, and visit the ask-me-anything booth. And we have a dedicated community track with talks from Elastic engineers and community members.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSydney:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/events/elasticon/sydney?utm_campaign=elasticon-tour-sydney\u0026utm_source=community\u0026utm_medium=email\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticON\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — March 6\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs61e6cb5925c4a8d9"}}},{"image":{"image":{"uid":"blt4c090d140106492a","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-03-04T08:28:00.777Z","created_by":"blt96ac6007eba0a223","file_size":"259117","filename":"elastic_on.png","parent_uid":null,"tags":[],"title":"elastic on.png","updated_at":"2025-03-04T08:28:00.777Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2025-03-06T15:20:56.285Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4c090d140106492a/67c6b990938bf546e9f9e56e/elastic_on.png"},"_metadata":{"uid":"csc20cc2e05660b4ab"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csee6531edbcaf982f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eJoin your \u003c/span\u003e\u003ca href=\"https://community.elastic.co/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003elocal Elastic User Group\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e chapter for the latest news on upcoming events! You can also find us on \u003c/span\u003e\u003ca href=\"https://www.meetup.com/pro/elastic/\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003eMeetup.com\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. If you’re interested in presenting at a meetup, send an email to \u003c/span\u003e\u003ca href=\"mailto:meetups@elastic.co\"\u003e\u003cspan style='font-size: 12pt;'\u003emeetups@elastic.co\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs363275f6b3632329"}}}],"publish_date":"2025-03-06","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Community","label_l10n":"Community","keyword":"community","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt9c74c5bb18c95a80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-07-14T13:45:14.579Z","updated_at":"2020-07-14T13:45:14.579Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-07-14T13:45:14.579Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-08-13T15:01:07.164Z","user":"bltc87e8bcd2aefc255"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt696883955f9c5c66","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-04-18T15:45:26.219Z","created_by":"blt96ac6007eba0a223","file_size":"154834","filename":"community-blog-series-04_(1)_(1).png","parent_uid":null,"tags":[],"title":"community-blog-series-04_(1)_(1).png","updated_at":"2024-04-18T15:45:26.219Z","updated_by":"blt96ac6007eba0a223","publish_details":{"time":"2024-04-19T07:38:52.718Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt696883955f9c5c66/66214016b8b5ce078fdbef6e/community-blog-series-04_(1)_(1).png"},"title":"DevRel newsletter — March 2025","title_l10n":"DevRel newsletter — March 2025","updated_at":"2025-03-05T09:27:36.344Z","updated_by":"blt96ac6007eba0a223","url":"/blog/devrel-newsletter-march-2025","publish_details":{"time":"2025-03-06T15:20:56.205Z","user":"blt96ac6007eba0a223","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2423137547555089","_version":1,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.\n","author":["blta248c27b7b7978db"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-03-04T17:20:58.101Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"Version 8.17.3 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.17.3 over the previous versions 8.17.2\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.17/new.html).","modular_blocks":[],"publish_date":"2025-03-04","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt720a36f34ba37235","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-08T02:19:40.632Z","updated_at":"2024-04-08T02:19:40.632Z","content_type":"image/png","file_size":"59668","filename":"Patch_release_white.png","title":"Patch_release_white.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-08T20:16:44.015Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt720a36f34ba37235/6613543c0d99458bb1031dca/Patch_release_white.png"},"title":"Elastic Stack 8.17.3 released","title_l10n":"Elastic Stack 8.17.3 released ","updated_at":"2025-03-04T17:20:58.101Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-stack-8-17-3-released","publish_details":{"time":"2025-03-04T17:21:48.418Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4289c9140f54be09","_version":1,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.\n","author":["blta248c27b7b7978db"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-03-04T17:17:31.005Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"Version 8.16.5 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 8.16.5 over the previous version 8.16.4\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/8.16/new.html).","modular_blocks":[],"publish_date":"2025-03-04","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8836a5dda86cbfe0","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-01T15:42:09.734Z","updated_at":"2024-04-01T15:42:09.734Z","content_type":"image/png","file_size":"62454","filename":"Patch_release_dark.png","title":"Patch_release_dark.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-02T17:14:25.081Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8836a5dda86cbfe0/660ad5d11b5a5878c8adccbc/Patch_release_dark.png"},"title":"Elastic Stack 8.16.5 released","title_l10n":"Elastic Stack 8.16.5 released ","updated_at":"2025-03-04T17:17:31.005Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-stack-8-16-5-released","publish_details":{"time":"2025-03-04T17:18:36.008Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9fbb0868540deae9","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Gain full visibility into your Elasticsearch Service costs with the Elasticsearch Service Billing integration. Learn how to deploy it, customize spending attribution per team, and get Kibana alerts to track budget thresholds and prevent overspending.","author":["blt60f0f6a133431d16"],"category":["blte5cc8450a098ce5e"],"created_at":"2025-03-04T01:58:06.925Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd177d569ddf5f1bb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMonitoring and managing your Elasticsearch Service (ESS) usage and costs is crucial for efficient operations. The \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/ess_billing.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eElasticsearch Service Billing integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e offers a streamlined approach to collect, visualize, and act upon your billing data. In this article, I'll guide you through deploying this integration, customizing it to align with your organizational structure, and setting up alerts to monitor team-specific expenditures.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Deploying the Elasticsearch Service Billing integration","_metadata":{"uid":"cs3b29037825d7ad64"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo begin, identify an Elasticsearch cluster with an attached Fleet-enabled Elastic Agent where the integration can be deployed. This agent will need internet access, as it will poll Elastic billing APIs and parse the resulting data, allowing you to leverage the preconfigured dashboards. Your monitoring cluster on Elastic Cloud Hosted could be a prime candidate for this.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Pre-flight checks","_metadata":{"uid":"cs2234101a0fa735e8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBefore installing the integration and adding it to an agent policy, you will need to retrieve some information for your organization:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eThe organization ID:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Navigate to your \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/account/members\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud organization page\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to find your organization identifier.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eA billing API key:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e On the\u003c/span\u003e\u003ca href=\"https://cloud.elastic.co\"\u003e \u003cspan style=\"font-size: 12pt;\"\u003eAPI keys page\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, create an API key with the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003eBilling admin\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e role.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Deploying the integration","_metadata":{"uid":"csc426bea22f6c744d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOn the Integrations page in Kibana, search for the \"Elasticsearch Service Billing\" integration and click on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd Elasticsearch Service Billing\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2cb57eac585a7d69"}}},{"image":{"image":{"uid":"bltd26c5efc03001341","_version":1,"title":"elasticsearch-service-billing.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:07:55.796Z","updated_at":"2025-03-04T02:07:55.796Z","content_type":"image/png","file_size":"533305","filename":"elasticsearch-service-billing.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.042Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd26c5efc03001341/67c6607bc4605a465943ed3e/elasticsearch-service-billing.png"},"_metadata":{"uid":"csb32006cfb41aeb2e"},"caption_l10n":"","alt_text_l10n":"Elasticsearch service billing","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7fab27dfec50397c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFill in the requested information, which you collected in the previous step. You can also customize how far back the billing data should be collected during the first run (one year by default) and how often the collection should occur. Please note, however, that the billing data is collected with a daily granularity, so changing the default frequency of 24 hours will bring little benefit.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa517ee2e3428f626"}}},{"image":{"image":{"uid":"blt17e105d0c43911c4","_version":1,"title":"Elasticsearch-service-billing-metrics.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:09:11.447Z","updated_at":"2025-03-04T02:09:11.447Z","content_type":"image/png","file_size":"180854","filename":"Elasticsearch-service-billing-metrics.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:57.998Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17e105d0c43911c4/67c660c7c1fe96639d5515d3/Elasticsearch-service-billing-metrics.png"},"_metadata":{"uid":"cs48f8f0ca700fa72a"},"caption_l10n":"","alt_text_l10n":"Elasticsearch service billing metrics","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs60607a3fe4a306fa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAlso note that the second dataset (Elasticsearch Service Credits) requires an active commercial commitment with Elastic to collect data properly.\u003cbr /\u003e\u003cbr /\u003eFinally, deploy the integration to the agent policy of your choice. With version 1.2.0 of the integration, and underlying stack version 8.17.0+, it is also possible to deploy this integration \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eagentless\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0698ea77ede6b5ff"}}},{"image":{"image":{"uid":"blt2ba776cdf96e2d20","_version":1,"title":"adding-intergration.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:10:02.415Z","updated_at":"2025-03-04T02:10:02.415Z","content_type":"image/png","file_size":"71553","filename":"adding-intergration.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.063Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2ba776cdf96e2d20/67c660fa1a2ab560ff1129ec/adding-intergration.png"},"_metadata":{"uid":"csfa400d723ad29d17"},"caption_l10n":"","alt_text_l10n":"Adding integration","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Visualizing ECU use","_metadata":{"uid":"cs59c88d1d20af3571"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce deployed, the integration will start polling Elastic billing APIs until your configured lookbehind period is fully onboarded. This can take a few minutes — be patient after the initial install, or change the time picker to whatever lookbehind value you used during install to see the progress in real time.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdfc727ddf17f973f"}}},{"image":{"image":{"uid":"blt199cf393eaae1f12","_version":1,"title":"quarterly-cost-overview.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:10:57.105Z","updated_at":"2025-03-04T02:10:57.105Z","content_type":"image/png","file_size":"745596","filename":"quarterly-cost-overview.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:57.986Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt199cf393eaae1f12/67c661315108fbe44d36003d/quarterly-cost-overview.png"},"_metadata":{"uid":"csc35fd437558b1b94"},"caption_l10n":"","alt_text_l10n":"Quarterly cost overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Drilling down: Defining deployment ownership","_metadata":{"uid":"cs97b2a660caa3c1cc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that you are collecting billing information for the entire organization, you will want to attribute the costs related to specific deployments to the teams that own them.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor this purpose, create an @custom pipeline for the integration, where you can define your logic.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor my example, I will use the following logic:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAll deployments with “test” in their name will be attributed to the QA team.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAll deployments with “security” in their name will be attributed to the Security team.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAll other deployments will be attributed to the Development team.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Creating the custom template and ingest pipeline","_metadata":{"uid":"cs74155f632567083c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eImplementing this logic requires declaring new fields in the custom template and then creating the ingest pipeline:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3c8aa420aa0a4292"}}},{"code":{"code":"PUT /_component_template/metrics-ess_billing.billing@custom\n{\n \"template\": {\n \"mappings\": {\n \"properties\": {\n \"team\": {\n \"type\": \"keyword\"\n }\n }\n }\n }\n}\n\n\nPUT /_ingest/pipeline/metrics-ess_billing.billing@custom\n{\n \"processors\": [\n {\n \"set\": {\n \"field\": \"team\",\n \"value\": \"development\"\n }\n },\n {\n \"set\": {\n \"field\": \"team\",\n \"value\": \"security\",\n \"if\": \"ctx.ess.billing.deployment_name ==~ /.*security.*/\"\n }\n },\n {\n \"set\": {\n \"field\": \"team\",\n \"value\": \"QA\",\n \"if\": \"ctx.ess.billing.deployment_name ==~ /.*test.*/\"\n }\n }\n ]\n}\n","_metadata":{"uid":"cs6deefbdb32893fd7"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfab9e3916407c6e5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eYou could also use the \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/ingest-enriching-data.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eenrich processor\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e to create a “join” with a reference base, thereby linking each deployment to its owner.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Altering historical data","_metadata":{"uid":"cs9c620af9329e47ed"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt is likely that you added the above ingest pipeline after the initial data pull, in which case a lot of the data is currently missing the newly defined field. You can “fix” your data by manually updating the mapping for the indices that already exist and performing an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docs-update-by-query.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eupdate by query\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse0dddcd19d60fa7f"}}},{"code":{"code":"PUT metrics-ess_billing.billing-*/_mapping\n{\n \"properties\": {\n \"team\": {\n \"type\": \"keyword\"\n }\n }\n}\n\n\nPOST /metrics-ess_billing.billing-*/_update_by_query?pipeline=metrics-ess_billing.billing@custom\u0026wait_for_completion=false","_metadata":{"uid":"cs4185baf562032378"}}},{"title_text":{"title_text":[{"title_l10n":"Viewing the results","_metadata":{"uid":"csfa3147532b9b0d4d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can now analyse the spending trends of your teams, thanks to this freshly created field. Let’s use some ES|QL for this purpose:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(0, 113, 194);font-size: 10.5pt;'\u003e\u003cstrong\u003eFROM\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e metrics-ess_billing.billing-*\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e| \u003c/span\u003e\u003cspan style='color:rgb(196, 64, 124);font-size: 10.5pt;'\u003e\u003cstrong\u003eSTATS\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e `Team spending`=\u003c/span\u003e\u003cspan style='color:rgb(0, 113, 194);font-size: 10.5pt;'\u003eSUM(\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003eess.billing.total_ecu\u003c/span\u003e\u003cspan style='color:rgb(0, 113, 194);font-size: 10.5pt;'\u003e)\u003c/span\u003e\u003cbr /\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e\u0026nbsp;\u0026nbsp;\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003cspan style='color:rgb(196, 64, 124);font-size: 10.5pt;'\u003e\u003cstrong\u003eBY\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e \u003c/span\u003e\u003cspan style='color:rgb(0, 113, 194);font-size: 10.5pt;'\u003eBUCKET(\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e@timestamp,\u003c/span\u003e\u003cspan style='color:rgb(0, 126, 119);font-size: 10.5pt;'\u003e\"1 month\"\u003c/span\u003e\u003cspan style='color:rgb(0, 113, 194);font-size: 10.5pt;'\u003e)\u003c/span\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 10.5pt;'\u003e, team\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs05667aa497f1a976"}}},{"image":{"image":{"uid":"blt838771c1fc7ad544","_version":1,"title":"Analyze-spending-trends.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:16:27.851Z","updated_at":"2025-03-04T02:16:27.851Z","content_type":"image/png","file_size":"86399","filename":"Analyze-spending-trends.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.140Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt838771c1fc7ad544/67c6627b1a2ab5658f1129f9/Analyze-spending-trends.png"},"_metadata":{"uid":"cs9964c24f3a8d5666"},"caption_l10n":"","alt_text_l10n":"Analyze spending trends","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2f224e5a20ffd252"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIt looks like the trend is fairly stable, except for this large bill in November. Maybe I should configure some alerting to identify the spending trend faster next time.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5693bec99522d106"}}},{"title_text":{"title_text":[{"title_l10n":"Setting up alerts for team spending","_metadata":{"uid":"cs859bd1432bbdea84"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMonitoring team expenditures is vital for budget management. With Kibana's alerting features, you can configure notifications to alert you when a team's spending trend surpasses a predefined threshold — let’s prevent this November fluke from happening again.\u003cbr /\u003e\u003cbr /\u003eSince I already queried for the data and wrote the ES|QL query, most of the work is already done! I can simply click on the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAlerts\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e button at the top of my screen and change my configuration and threshold to match my goals.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs88f2472b1eb36486"}}},{"image":{"image":{"uid":"blt67dcf6d4e119f97e","_version":1,"title":"Setting-up-alerts.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:18:08.839Z","updated_at":"2025-03-04T02:18:08.839Z","content_type":"image/png","file_size":"350687","filename":"Setting-up-alerts.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.053Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt67dcf6d4e119f97e/67c662e086795f05fa8e5050/Setting-up-alerts.png"},"_metadata":{"uid":"cs098e09c229c2c971"},"caption_l10n":"","alt_text_l10n":"Setting up alerts","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa70a78e09dc5dfbe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn my case, I will refine the granularity to daily spending and set a per-team budget of 1,000 ECUs:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs29e2ce0f94563427"}}},{"image":{"image":{"uid":"bltd44cf16bd5725ccb","_version":1,"title":"Elasticsearch-query.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:19:40.149Z","updated_at":"2025-03-04T02:19:40.149Z","content_type":"image/png","file_size":"255428","filename":"Elasticsearch-query.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.031Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd44cf16bd5725ccb/67c6633c54cf2f00de766719/Elasticsearch-query.png"},"_metadata":{"uid":"cs784e352f3e74cb02"},"caption_l10n":"","alt_text_l10n":"Elasticserach query","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd2a066e85ea26091"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNotice how I can live-test my query and confirm that this would indeed have triggered in November, when my Development team blew the budget.\u003cbr /\u003e\u003cbr /\u003eThe final step is to configure the action you want Kibana to run on alert trigger. In my case, this will certainly be an email, but you can refer to the documentation for more details about all available \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/action-types.html\"\u003e\u003cspan style='font-size: 12pt;'\u003econnector types\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa952fee06a41e3a9"}}},{"image":{"image":{"uid":"blt8903cf9a6eb3f1ec","_version":1,"title":"Connector-types.png","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T02:21:17.625Z","updated_at":"2025-03-04T02:21:17.625Z","content_type":"image/png","file_size":"123902","filename":"Connector-types.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.073Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8903cf9a6eb3f1ec/67c6639dd1b1de5bfbca8184/Connector-types.png"},"_metadata":{"uid":"cs8577de5c38c4f6c8"},"caption_l10n":"","alt_text_l10n":"Connector types","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Take control of your Elasticsearch Service costs","_metadata":{"uid":"cs99b060f8f1a75da7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy integrating the Elasticsearch Service Billing data into your observability pipeline, you gain real-time visibility into your cloud spending, ensuring financial accountability across teams. With custom tagging and alerting in Kibana, you can track expenses, enforce budget policies, and prevent unexpected cost overruns.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to take control of your Elasticsearch Service costs? \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/integrations/current/ess_billing.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eDeploy the integration\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e today, customize it to match your team structure, and set up alerts to stay ahead of budget surprises.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs4be85facdda0a3a6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7fad702a8f9c7a91"}}}],"publish_date":"2025-03-04","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Track and control Elasticsearch Service costs with billing integration","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Track, customize, and alert on Elasticsearch Service expenses using Elasticsearch service billing integration.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Alerting","label_l10n":"Alerting","keyword":"alerting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd8e03b8972ecf817","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:20.375Z","updated_at":"2020-06-17T03:38:20.375Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:20.374Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:49:19.650Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}},{"title":"Optimizing","label_l10n":"Optimizing","keyword":"optimizing","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt7731091cfa6e23e8","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:40:15.070Z","updated_at":"2020-06-17T03:40:15.070Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:40:15.069Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:51.089Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt3ff56eb3b9c58312","ACL":{},"created_at":"2020-06-17T03:33:18.405Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"business-analytics","label_l10n":"Business analytics","tags":[],"title":"Business analytics","updated_at":"2020-07-06T22:20:18.826Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.556Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt1d8cc8db9be8d4d1","_version":1,"title":"-27-ridges.jpg","created_by":"blte369ea3bcd6ac892","updated_by":"blte369ea3bcd6ac892","created_at":"2025-03-04T01:56:54.745Z","updated_at":"2025-03-04T01:56:54.745Z","content_type":"image/jpeg","file_size":"108901","filename":"-27-ridges.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-03-04T17:26:58.129Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1d8cc8db9be8d4d1/67c65de6d3f86d3f57ec5287/-27-ridges.jpg"},"title":"Monitor Elasticsearch Service costs with billing integration and alerts","title_l10n":"Monitor Elasticsearch Service costs with billing integration and alerts","updated_at":"2025-03-04T17:11:12.570Z","updated_by":"bltd9765be97bbed20c","url":"/blog/monitor-elasticsearch-costs-billing-integration","publish_details":{"time":"2025-03-04T17:26:57.482Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9ecc9aab330ebf84","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"GenAI has been a big win for security teams worldwide. While it’s unlikely to take cybersecurity jobs, it is bringing forth a powerful level of automation that uplevels the traditional day-to-day workload of practitioners. Learn how GenAI can help.","author":["blt1f84830916c3ddfe"],"category":["bltc17514bfdbc519df"],"created_at":"2025-02-18T21:44:19.247Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs73bcedf08f8b15c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/what-is/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenerative AI (GenAI)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is quickly becoming an essential part of everyday security workflows. So … is it a partner or competitor?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe wide-ranging implementation of GenAI technologies into virtually every aspect of the security stack has, on the whole, helped security teams work more efficiently to mitigate threats. GenAI is providing security practitioners access and analysis to data they otherwise would never have had — making their work even more impactful than it’s ever been.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the same time, GenAI has also expanded the attack surface — whether through adversaries’ abilities to scale production of malicious code, the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/llm-safety-report?utm_source=releaseblog\"\u003e\u003cspan style='font-size: 12pt;'\u003erisks associated with employees’ use of large language models (LLMs)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, or increasingly sophisticated social engineering campaigns.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, how does all this affect today’s security professionals?\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How GenAI is helping security professionals","_metadata":{"uid":"csb2253f02e20b1e4a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith GenAI on board, security practitioners’ daily scope of work is changing in real time. Here are some of the traditional tasks by role and how exactly GenAI is alleviating burdensome processes for each.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Security engineers and architects","_metadata":{"uid":"csdfd439a8af470d85"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTask:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Collect and normalize a new data source.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenAI helps by:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eAutomating the development of custom data integrations; creating a fully fledged integration (pipeline, mappings, templates, and integration package)\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTask:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Create or convert a detection rule.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenAI helps by:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Creating and converting detection rules; explaining alerts\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Security analysts","_metadata":{"uid":"cs72ca7cef262b0d38"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTask:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Triage alerts.\u003cbr /\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eGenAI helps by:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Automating triage by correlating related alerts into attack-level findings\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTask: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eMonitor security alerts.\u003c/span\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eGenAI helps by:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Automating alert triage by filtering out false positives and prioritizing genuine threats based on severity and potential impact\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTask:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Investigate a threat.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenAI helps by:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Performing key investigation steps like providing a detailed description of the attack, summarizing hosts and users, displaying related \u003c/span\u003e\u003ca href=\"https://attack.mitre.org/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eMITRE ATT\u0026amp;CK®\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e tactics, and more (Built-in AI assistants can also create step-by-step remediation plans and streamline ad-hoc analysis and enrichment by generating preferred program language queries.)\u003cbr /\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTask:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Respond to an incident.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenAI helps by: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSuggesting remediation steps and helping document incidents\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"SOC leaders","_metadata":{"uid":"cs8024226502658b37"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTask: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eManage\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eteam performance.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenAI helps by: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTracking and summarizing metrics on response time, alert volume per analyst, team fatigue levels, and more\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eTask: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReport metrics and insights to executives.\u003cbr /\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eGenAI helps by: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAggregating and visualizing security metrics, generating concise summaries, and providing predictive insights to better communicate with stakeholders\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1fd6c06448c6cc0c"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs06f497f681166c49"},"paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSee a detailed breakdown of how \u003c/span\u003e\u003ca href=\"https://www.elastic.co/lp/how-is-ai-changing-the-cybersecurity-landscape\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI is changing the cybersecurity landscape\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"AI-driven security analytics","_metadata":{"uid":"cs665bcd6846219de2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the help of GenAI, security teams can more easily prioritize critical incidents, reduce alert fatigue, and accelerate investigations through real-time integrated threat intelligence, automated triage, and LLM-enhanced workflows. AI-driven security analytics transform security operations into a more proactive, adaptive, and efficient function — allowing organizations to stay ahead of today’s threat actors (who themselves are also using GenAI) and respond with greater speed and accuracy.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere are some estimates on how much time security teams can expect to save with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI-driven security analytics\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc00fc417352bd86e"}}},{"image":{"image":{"uid":"blta25f739e96047c29","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-02-18T21:43:53.661Z","created_by":"bltb6c155cd84fc0c1a","file_size":"295135","filename":"image2.png","parent_uid":null,"tags":[],"title":"image2.png","updated_at":"2025-02-18T21:43:53.661Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2025-02-19T14:55:00.393Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta25f739e96047c29/67b4ff196e2f9543f50a89af/image2.png"},"_metadata":{"uid":"cs7b26335f98a09a46"},"caption_l10n":"","alt_text_l10n":"time savings of ai","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Today’s AI-equipped security professional","_metadata":{"uid":"cs5e116c6e5893a7a5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOK, so GenAI is elevating efficiency, productivity, and overall defense capabilities … but how might it help you in \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eyour\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e role? Check out this resume from the perspective of a humble-yet-powerful AI assistant and see why \u003c/span\u003e\u003ca href=\"https://www.elastic.co/lp/security/ai-assistant-resume\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI is the newest team member you need\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbfee1b92d43f3fb4"}}},{"image":{"image":{"uid":"blt0990b67517845319","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2025-02-18T21:43:14.118Z","created_by":"bltb6c155cd84fc0c1a","file_size":"634871","filename":"image1.png","parent_uid":null,"tags":[],"title":"image1.png","updated_at":"2025-02-18T21:43:14.118Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2025-02-19T14:55:00.491Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0990b67517845319/67b4fef284b0c2201fdea3a9/image1.png"},"_metadata":{"uid":"cs6a173e9b64400424"},"caption_l10n":"","alt_text_l10n":"security ai assistant resume","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs06e01840f3c6fc3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI has been a big win for security teams worldwide. While it’s unlikely to take cybersecurity professionals’ jobs, it is bringing forth a powerful level of automation that uplevels the traditional day-to-day workload of practitioners — shifting their role to adopt more strategic focus and creative problem-solving.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy automating away many of the time-intensive and mundane tasks that have burned out many security analysts and admins, security teams can now focus on the priorities that truly matter and further strengthen overall security posture.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCheck out our webinar on \u003c/span\u003e\u003ca href=\"https://www.elastic.co/virtual-events/2025-cybersecurity-trends\"\u003e\u003cspan style='font-size: 12pt;'\u003esecurity trends for 2025\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to gain further insight into the relationship between practitioner and AI, and see how \u003c/span\u003e\u003ca href=\"https://www.elastic.co/lp/security/ai-assistant-resume\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI can help your team accomplish more\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2f506b6cf4ec5175"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6a9d8da7f247fbf0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs345b75c8266ff5ce"}}}],"publish_date":"2025-03-03","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"No, but it’s fundamentally changing them.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt9085022a5c6c87e9","ACL":{},"created_at":"2023-11-06T20:41:57.778Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"large-language-models","label_l10n":"Large language models","tags":[],"title":"Large language models","updated_at":"2023-11-06T20:42:13.486Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:28.432Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt3c3c124c70b20f1e","ACL":{},"created_at":"2023-11-06T20:47:25.066Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"predictive-analytics","label_l10n":"Predictive analytics","tags":[],"title":"Predictive analytics","updated_at":"2023-11-06T20:47:25.066Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:06.368Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltfb1e89b001674db9","ACL":{},"created_at":"2023-11-06T21:30:17.252Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"relevance","label_l10n":"Relevance","tags":[],"title":"Relevance","updated_at":"2023-11-06T21:30:17.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.339Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blte799688802bb242c","ACL":{},"created_at":"2023-11-06T21:32:44.031Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"soar","label_l10n":"SOAR","tags":[],"title":"SOAR","updated_at":"2023-11-06T21:32:44.031Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.584Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blta0522675d5f80636","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-02-18T21:29:34.454Z","created_by":"bltb6c155cd84fc0c1a","file_size":"156662","filename":"174118_-_Blog_header_image-_Will_AI_start_taking_cybersecurity_jobs_-1.jpg","parent_uid":null,"tags":[],"title":"174118 - Blog header image- Will AI start taking cybersecurity jobs?-1.jpg","updated_at":"2025-02-18T21:29:34.454Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2025-02-19T14:55:00.476Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta0522675d5f80636/67b4fbbec063ceb01d3c6413/174118_-_Blog_header_image-_Will_AI_start_taking_cybersecurity_jobs_-1.jpg"},"title":"Will AI start taking cybersecurity jobs?","title_l10n":"Will AI start taking cybersecurity jobs?","updated_at":"2025-03-03T20:23:00.301Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/will-ai-start-taking-cybersecurity-jobs","publish_details":{"time":"2025-03-03T20:26:23.880Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5030aa9a2be4a79c","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"US federal agencies have made progress in adhering to M-21-31’s cyber threat response requirements but lag in advanced event logging requirements. Learn how Elastic can help agencies overcome three major challenges slowing M-21-31 logging compliance.","author":["blte520dce49f64b517","blt7d037363482c18a8"],"category":["bltc17514bfdbc519df"],"created_at":"2023-12-19T15:33:29.201Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs890d8d71f916070c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor the past four years or so, US federal agencies have been working to comply with the requirements set out in OMB M-21-31. Released in 2021, the Office of Management and Budget (OMB)’s M-21-31 memorandum provided guidance and requirements for federal agencies in order to improve centralized visibility into logging data before, during, and after cybersecurity incidents. The memo outlined a logging maturity model with four tiers (E0-3) to guide agencies in their compliance process.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn a December 2023 study, the US Government Accountability Office (GAO) found that most agencies were not on track to meet deadlines for advanced logging. The study highlighted \u003c/span\u003e\u003ca href=\"https://www.gao.gov/products/gao-24-105658\"\u003e\u003cspan style='font-size: 12pt;'\u003ethree challenges\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e agencies face as they work to meet M-21-31 event logging requirements: lack of staff, event logging technical challenges, and limitations in cyber event information sharing.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThese challenges are still very much relevant in 2025. In addition, agencies are increasingly focused on cost efficiencies and interoperability. The good news, however, is that advancements in AI and logging have made M-21-31 compliance more achievable by US government agencies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this post, we’ll walk through common M-21-31 logging compliance challenges and share how we’ve seen US federal customers address them using Elasticsearch.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Using Elasticsearch to solve M-21-31 challenges","_metadata":{"uid":"cs65e193f948d2e44b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSeveral federal agencies have been using Elastic’s Search AI Platform to meet M-21-31 requirements — taking a unified approach that includes both logging and threat response. Based on these agencies’ experience using Elastic for M-21-31, we recommend the following ways to overcome common M-21-31 challenges.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Limited budgets","_metadata":{"uid":"csebc04c95564b944a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs federal agencies prioritize cost savings and interoperability, there is increasing scrutiny toward technology investments and budgets. Since M-21-31 was introduced in 2021, Elastic continues to offer even more opportunity for agencies to save on costs and store data affordably.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAffordable data tiering model: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eElastic's data tiering approach optimizes data management by categorizing data into storage tiers based on access frequency and cost. For example, agencies can \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-hosted-data-retention-government-compliance\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estore longer term or historical data\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e in Elastic’s frozen tier. Ideal for long-term retention, the frozen tier enables data to be stored in object storage for two years or longer.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003cstrong\u003eSearchable snapshots: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eThe unique searchable snapshots capability enables direct searches for data \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003ewithout any rehydration, maintaining fast search performance. (Elastic's cold and frozen tiers perform with search speeds that are comparable to our competitors' hot tiers.)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eElasticsearch logsdb index mode: \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/whats-new-elastic-8-17-0#elasticsearch-logsdb-index-mode\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch logsdb index mode\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e is designed to significantly reduce data storage costs by efficiently storing and searching essential log data. Logsdb index mode can \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elasticsearch-logsdb-index-mode\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecut data storage costs by up to 65%\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, making it an ideal choice for federal agencies aiming to optimize their data management budgets while complying with M-21-31.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"2. Skills gap and lack of staff","_metadata":{"uid":"csbdec99d84d5679b1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFederal agencies are leveraging the AI and machine learning (ML) capabilities built into the Elastic Search AI Platform to automate time-consuming tasks and uncover data insights in real time. Instead of hiring more employees or re-skilling existing teams, agencies are benefiting from Elastic’s democratized approach to insights and the accessible capabilities built into the platform. A few of the functionalities helping agencies address the skills gap include:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003cstrong\u003eConsolidated view into data: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlign teams and roles around common datasets, providing a unified view of infrastructure performance and enriched by threat intelligence. This consolidated access makes it easier and faster to consume and act on data, no matter where it’s located.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003cstrong\u003eDrag-and-drop visualizations\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnalyze logging and cybersecurity data through Elasticsearch’s intuitive, visual \u003c/span\u003e\u003ca href=\"https://www.elastic.co/kibana\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edrag-and-drop dashboards\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. These dashboards surface insights generated from Elastic’s ML and AI capabilities, allowing everyone access to this information in real time — as opposed to having to wait on a data scientist with specialized knowledge or access.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAI capabilities: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLeverage the power of Elastic’s Search AI Platform to streamline tasks, reduce manual data correlation, and triage security alerts. \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/ai-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e integrates generative AI to simplify tasks and help users find context and information for understanding anomalies and threats faster, speeding problem resolution. And Elastic’s Attack Discovery feature can automatically cut through hundreds of noisy alerts in order to surface the ones that matter most to your agency. As a result, your team can save time by quickly understanding the presented attacks, take immediate follow-up action, and more.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"3. Event logging technical challenges","_metadata":{"uid":"cs39a36f9257eae63b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOne of the roadblocks in logging compliance is not having access to \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003eall \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003elogging data. Without streamlined visibility into all data types and sources, the ability to accurately pinpoint threats and patterns is significantly limited. Many organizations are challenged with the high costs involved in managing and storing large quantities of disparate logging data. Elastic’s approach simplifies data ingest and analysis, while our resource-based pricing gives teams the flexibility to pay for what they need.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eStreamlined data ingest:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIngesting different types of data from different sources typically requires multiple tools and processes (and high costs). Using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elastic-agent\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Agent\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to ingest all your logs, metrics, and traces can eliminate dependency on external plugins and integrations that may require you to give up control of sensitive data.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eUnified schema: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo organize and make sense of all types of ingested data, Elastic uses an open source, community-driven schema known as the\u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/common-schema\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic Common Schema\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, or ECS. This common data structure unifies all modes of analysis available in Elastic, including search, drill-down and pivoting, data visualization, ML-based anomaly detection, detection rules, and alerting. ECS is also part of OpenTelemetry, offering agencies yet more opportunity for building efficiencies and interoperability.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"4. Limitations in cyber event information sharing","_metadata":{"uid":"csd072c5f9295dc277"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eM-21-31 called for agencies to share logging data with one another, “as needed and appropriate, to accelerate incident response efforts.” Traditionally, sharing data outside an agency introduced significant risk for already-sensitive data, as well as potential costs and time required to copy data or move it to a central source.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsing Elasticsearch, however, agencies can securely share data across agencies, teams, and projects. In fact, federal agencies are probably already familiar with the cyber intelligence data provided by CISA; Elasticsearch \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/public-sector-cdms-data-strategy\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003epowers CISA’s CDM Dashboard\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, giving CISA centralized visibility into 100+ agencies’ cybersecurity data when needed. CISA, and other federal agencies, have been relying on Elasticsearch for its:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eDistributed approach: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-enable-ccs.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic cross-cluster search\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-enable-ccs.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e cross-cluster replication\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e capabilities, agencies can securely share their data outside their agency without moving it. In addition to reducing the risk, time, and costs involved with moving data, this approach enables each agency to retain control of their data in its original secure location.\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eData privacy controls: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWorking hand in hand with cross-cluster search and replication, Elastic’s\u003c/span\u003e\u003cspan style=\"color: rgb(33, 37, 41);font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-security-role-based-access-control-rbac\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003erole and attribute-based access control\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(33, 37, 41);font-size: 12pt;\"\u003e (RBAC/ABAC) security lets you decide who at your agency can access what data — down to the document level. These security permissions are applied locally, where the data resides. This allows you to create secure dynamic data access policies for certain classification levels and functional areas.\u003c/span\u003e\u003cp\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Get started: Accelerate M-21-31 compliance","_metadata":{"uid":"cs402abecd9bd6b72b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more about how Elastic can provide integrated, cost-effective support for M-21-31 compliance, from log storage, management, and cybersecurity capabilities within our unified AI-powered platform:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhite paper: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/industry-brief-the-executive-order-on-improving-the-nations-cybersecurity\"\u003e\u003cspan style='font-size: 12pt;'\u003eM-21-31 industry brief\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-hosted-data-retention-government-compliance\"\u003e\u003cspan style='font-size: 12pt;'\u003eOptimizing long-term storage costs for government compliance\u0026nbsp;\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/its-time-for-government-to-move-beyond-monitoring-and-into-observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eIt’s time for government to move beyond monitoring and into observability\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/contact/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003eContact the Elastic federal team\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cse7011fc37f50ad22"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscfdde844049cd69f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eOriginally published December 19, 2023; updated March 3, 2025.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"csf771f8925b3f2d12"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0cfb8ac7ab92dd1e"}}},{"image":{"image":null,"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null},"_metadata":{"uid":"cs0afbdfb4ff275f05"}}}],"publish_date":"2025-03-03","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"How US federal agencies can better meet advanced event logging requirements","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt284682f193d93481","ACL":{},"created_at":"2023-11-06T20:07:36.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-ml-models","label_l10n":"AI/ML models","tags":[],"title":"AI/ML models","updated_at":"2023-11-06T20:07:36.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:37.071Z","user":"blt06083bb707628f5c"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4eb0f5c53cfcb73a","ACL":{},"created_at":"2023-11-06T20:43:57.712Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-source-standards","label_l10n":"Open source/standards","tags":[],"title":"Open source/standards","updated_at":"2023-11-06T20:43:57.712Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:21.485Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"parent_uid":"blta8bbe6455dcfdb35","uid":"blt6380424f89934f96","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-05-30T20:13:32.007Z","updated_at":"2023-05-30T20:13:32.007Z","content_type":"image/jpeg","file_size":"167019","filename":"log-management-720x420_(2).jpeg","title":"log-management-720x420_(2).jpeg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-30T20:43:47.376Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6380424f89934f96/647658ecec2233010651bf95/log-management-720x420_(2).jpeg"},"title":"M-21-31 logging compliance: Where are we now?","title_l10n":"M-21-31 logging compliance: Where are we now?","updated_at":"2025-03-03T18:18:43.377Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/m-21-31-logging-compliance-challenges","publish_details":{"time":"2025-03-03T18:18:47.799Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt681b190feb3f4561","_version":13,"locale":"en-us","ACL":{},"abstract_l10n":"In an exciting update to our Operation Giving Back program, we are thrilled to share that Elastic is now offering one year of free virtual, on-demand training for all U.S. veterans and active duty military personnel.","author":["bltcfa45c6824a1e807"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2021-09-30T14:32:57.187Z","created_by":"blt1e57c6588ae1816e","markdown_l10n":"","modular_blocks":[{"callout":{"title_l10n":"","_metadata":{"uid":"cs178d2f61ff9b8f9e"},"paragraph_l10n":"","callout_reference":["blt47d0de7b45a59baa"],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7d7eaf768f1b02d5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIn an exciting update to our Operation Giving Back program, we are thrilled to share that Elastic is now offering one year of free virtual, on-demand training for all U.S. veterans and active duty military personnel. We are operationalizing the program in the U.S. \nfirst, but will be working on ways to expand it to other countries in \nthe future.\u003c/p\u003e\n\u003cp\u003eElastic skills are in high demand across public and private industries. We’re proud to be offering the individuals who have devoted themselves to their country with an opportunity to prepare for bright new futures, wherever life may take them. \u003c/p\u003e\n\u003cp\u003e“Veterans bring a wealth of knowledge and skills to the workforce,” says Hector Perez, Senior Director, CRM applications at Elastic. “With this no-cost training from Elastic, military veterans can open up new career paths for themselves in high-demand industries.” \u003c/p\u003e\n\u003cp\u003eYou can learn more about the program and sign up to access free training on our \u003ca href=\"http://elastic.co/veterans\"\u003eOperation Giving Back web page\u003c/a\u003e. \u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eMilitary roots at Elastic are at the heart of this program\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eProviding free training for veterans is particularly meaningful for me as a member of a military family. Both my dad and husband are veterans, so I was encouraged to see how Elastic was already supporting the Department of Defense (DOD) and their mission when I joined the company nearly four years ago. Meeting users in the DOD who embraced Elastic’s free and open roots and built a thriving community around them galvanized the team and I to start Operation Giving Back. Elastic’s \u003ca href=\"https://www.elastic.co/about/our-source-code\"\u003esource code\u003c/a\u003e values, including Space, Time and Progress, Simple Perfection, have been essential in giving us the time and encouragement to take an idea like this and build it into an entire program supporting a community that we’re passionate about. I’m hopeful that there will be much more to come for our military community members through this program.\u003c/p\u003e\u003ch2\u003e\u003cstrong\u003eTraining, guidance, and support for our military users\u003c/strong\u003e\u003c/h2\u003e\n\u003cp\u003eFor our veterans and active duty military personnel who are interested in taking advantage of this program, getting started with your free Elastic training subscription is as simple as verifying your ID to begin one year of access.\u003c/p\u003e\n\u003cp\u003eWith Quick Start guides, training fundamentals, field guides, and our popular Data Analysis for Kibana course, this subscription provides everything veterans need to get started with the Elastic platform or to build on existing skills to achieve mastery. \u003c/p\u003e\n\u003cp\u003e“As a veteran who works with many veterans at Elastic, I am glad to see us make this commitment of time and resources to support veterans outside the company as well,” said Kevin Keeney, Army Mission Support at Elastic. “When they leave the service, veterans often need to retool their skills. This program gives them an easy path to develop an in-demand skill set for the global job market.”\u003c/p\u003e\n\u003cp\u003eAlong with access to the training, the Elastic team is providing support to new and existing users every step of the way. For new users, we’ll be in touch to share recommended course paths and additional resources for getting familiar with Elastic technology. And for our seasoned users looking to deepen their expertise, we will offer assistance with preparing for Elastic certification, mastering a new skill, or diving deeper into niche topics. \u003c/p\u003e\n\u003cp\u003eAs part of this program, we’re excited to continue partnering with organizations like \u003ca href=\"https://vetsintech.co/\"\u003eVetsinTech\u003c/a\u003e to offer training, mentorship, and professional development opportunities for personnel transitioning from military to civilian life. \u003c/p\u003e\n\u003cp\u003eWe’re honored and excited to be supporting the military community that’s been such a meaningful part of both the Elastic story and our personal stories. \u003c/p\u003eTo learn more about the program and sign up for access to free training, \u003ca href=\"http://elastic.co/veterans\"\u003evisit our veterans web page today\u003c/a\u003e."}],"_metadata":{"uid":"csa29ec3967f7ca372"}}}],"publish_date":"2021-09-30T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Free Elastic training for U.S. veterans and active duty military personnel","seo_description_l10n":"In an exciting update to our Operation Giving Back program, we are thrilled to share that Elastic is now offering one year of free virtual, on-demand training for all U.S. veterans and active duty military personnel.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[{"uid":"blt6d563296d3ba4a70","_content_type_uid":"tags_culture"},{"uid":"blt791379bc935f6af0","_content_type_uid":"tags_culture"}],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","uid":"bltc6e3d049760fc06a","title":"Government","label_l10n":"Government","keyword":"government","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:32.959Z","updated_at":"2023-11-06T20:40:32.959Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.338Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt8ba81aec5f3106e1","created_by":"blt1e57c6588ae1816e","updated_by":"blt1e57c6588ae1816e","created_at":"2021-09-30T19:21:49.565Z","updated_at":"2021-09-30T19:21:49.565Z","content_type":"image/png","file_size":"36130","filename":"Blog_Thumbnail-training-for-vets-720x420.png","title":"Blog_Thumbnail-training-for-vets-720x420.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-30T19:22:03.810Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8ba81aec5f3106e1/61560e4d9c76234dd174b91b/Blog_Thumbnail-training-for-vets-720x420.png"},"title":"Free Elastic training for U.S. veterans and active duty military personnel","title_l10n":"Free Elastic training for U.S. veterans and active duty military personnel","updated_at":"2025-02-27T11:02:50.512Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/free-elastic-training-for-us-veterans-and-active-duty-military-personnel","publish_details":{"time":"2025-02-27T11:02:57.800Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltecfaf12e755817a4","_version":28,"locale":"en-us","ACL":{},"abstract_l10n":"Using named entity recognition (NER) as an example, this blog describes the process for getting up and running using deep learning models for natural language processing (NLP) in Elasticsearch.","author":["bltf5e67aa275b15da9"],"category":["blte5cc8450a098ce5e"],"created_at":"2022-04-06T19:46:08.011Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs32aec6d0f29fd880"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs part of our \u003ca href=\"/blog/how-to-deploy-natural-language-processing-nlp-getting-started\" target=\"_self\"\u003emulti-blog series on natural language processing (NLP)\u003c/a\u003e, we will walk through an example using a named entity recognition (NER) NLP model to locate and extract predefined categories of entities in unstructured text fields. Using a publicly available model, we will show you how to deploy that model to Elasticsearch, find named entities in text with the new _infer API, and use the NER model in an ingest pipeline to extract entities as documents are ingested into Elasticsearch.\u003c/p\u003e\u003cp\u003eNER models are useful for using natural language to extract entities like people, places, and organizations from full text fields.\u003c/p\u003e\u003cp\u003eIn this example we will run the paragraphs of the book \u003ca href=\"https://en.wikipedia.org/wiki/Les_Mis%C3%A9rables\" target=\"_self\"\u003eLes Misérables\u003c/a\u003e, through an NER model and use the model to extract the characters and locations from the text and visualize the relationships between them.\u003c/p\u003e"},{"title_l10n":"Deploying an NER model to Elasticsearch","_metadata":{"uid":"cs0481055660bb05a1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eFirst we need to select an NER model that can extract the names of the characters and locations from text fields. Fortunately there are a few NER models available on \u003ca href=\"http://huggingface.co\" target=\"_self\"\u003eHugging Face\u003c/a\u003e we can choose from, and checking the \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/current/ml-nlp-model-ref.html#ml-nlp-model-ref-ner\" target=\"_self\"\u003eElastic documentation\u003c/a\u003e, we see one for an \u003ca href=\"https://huggingface.co/elastic/distilbert-base-uncased-finetuned-conll03-english\" target=\"_self\"\u003euncased NER model from Elastic\u003c/a\u003e to try out.\u003c/p\u003e\n\u003cp\u003eNow that we have selected the NER model to use, we can use Eland to install the model. In this example we will run the Eland command via a docker image, but first we must build the docker image by cloning the \u003ca href=\"https://github.com/elastic/eland\" target=\"_self\"\u003eEland\u003c/a\u003e GitHub repository and create a docker image of Eland on your client system:\u003c/p\u003e"}],"_metadata":{"uid":"cs3549522214587f08"}}},{"code":{"code":"git clone git@github.com:elastic/eland.git\ncd eland\ndocker build -t elastic/eland .\n","_metadata":{"uid":"cs0ce5d70cb5f00faf"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7917b287ef49f6ca"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNow that our eland docker client is ready we can install the NER model by executing the \u003ccode\u003eeland_import_hub_model\u003c/code\u003e command in the new docker image with the following command:\u003c/p\u003e"}],"_metadata":{"uid":"csb4e9fd1e0c1fc658"}}},{"code":{"code":"docker run -it --rm elastic/eland \\\n eland_import_hub_model \\\n --url $ELASTICSEARCH_URL \\\n --hub-model-id elastic/distilbert-base-uncased-finetuned-conll03-english \\\n --task-type ner \\\n --start","_metadata":{"uid":"csabeea0ce3a0a42c6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csab2af550d25c5201"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eYou will need to replace the ELASTICSEACH_URL with the URL for your Elasticsearch cluster. For authentication purposes you will need to include an administrator username and password in the URL in the format \u003cem\u003ehttps://username:password@host:port\u003c/em\u003e. For Elasticsearch Service, use port 9243.\u003c/p\u003e\u003cp\u003eSince we used the --start option at the end of the eland import command, Elasticsearch will deploy the model to all available machine learning nodes and load the model in memory. If we had multiple models and wanted to select which model to deploy, we could use Kibana's Machine Learning \u0026gt; Model Management user interface to manage the start and stopping of models.\u003c/p\u003e"}],"_metadata":{"uid":"cs1ff6791663d0e058"}}},{"title_text":{"title_text":[{"title_l10n":"Testing out the NER model","_metadata":{"uid":"cs507a6d69b00b3268"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eDeployed models can be evaluated using the new \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.0/infer-trained-model-deployment.html\" target=\"_self\"\u003e_infer\u003c/a\u003e API. The input is the string we wish to analyze. In the request below, \u003ccode\u003etext_field\u003c/code\u003e is the field name where the model expects to find the input, as defined in the model configuration. By default, if the model was uploaded via Eland, the input field is \u003ccode\u003etext_field\u003c/code\u003e.\u003c/p\u003e\u003cp\u003eTry this example in Kibana’s Dev Tools Console:\u003c/p\u003e"}],"_metadata":{"uid":"csafaa98927d865659"}}},{"code":{"code":"POST _ml/trained_models/elastic__distilbert-base-uncased-finetuned-conll03-english/deployment/_infer\n{\n \"docs\": [\n {\n \"text_field\": \"Hi my name is Josh and I live in Berlin\"\n }\n ]\n}\n","_metadata":{"uid":"cse3caaee9ae79f993"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs16f066a92308d1b6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe model found two entities: the person \"Josh\" and the location \"Berlin\".\u003c/p\u003e"}],"_metadata":{"uid":"cs97415c75f1abc018"}}},{"code":{"code":"{\n \"predicted_value\" : \"Hi my name is [Josh](PER\u0026Josh) and I live in [Berlin](LOC\u0026Berlin)\", \n \"entities\" : {\n \"entity\" : \"Josh\",\n \"class_name\" : \"PER\",\n \"class_probability\" : 0.9977303419824,\n \"start_pos\" : 14,\n \"end_pos\" : 18\n },\n {\n \"entity\" : \"Berlin\",\n \"class_name\" : \"LOC\",\n \"class_probability\" : 0.9992474323902818,\n \"start_pos\" : 33,\n \"end_pos\" : 39\n }\n ]\n}\n","_metadata":{"uid":"cs33282ab2267ddbfc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs158738286d63d50a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ccode\u003epredicted_value\u003c/code\u003e is the input string in \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/plugins/8.0/mapper-annotated-text-usage.html\" target=\"_self\"\u003eAnnotated Text\u003c/a\u003e format, \u003ccode\u003eclass_name\u003c/code\u003e is the predicted class, and \u003ccode\u003eclass_probability\u003c/code\u003e indicates the level of confidence in the prediction. \u003ccode\u003estart_pos\u003c/code\u003e and \u003ccode\u003eend_pos\u003c/code\u003e are the starting and ending character positions of the identified entity.\u003c/p\u003e"}],"_metadata":{"uid":"cs74c241debfb81d93"}}},{"banner":{"reference":[{"uid":"blt05d957a5a4398c02","_content_type_uid":"banner"}],"_metadata":{"uid":"cs91c116cb56029163"}}},{"title_text":{"title_text":[{"title_l10n":"Adding the NER model to an inference ingest pipeline","_metadata":{"uid":"csc96185849a6877c7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe _infer API is a fun and easy way to get started, but it accepts only a single input and the detected entities are not stored in Elasticsearch. An alternative is to perform bulk inference on documents as they are ingested via an ingest pipeline with the \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.0/inference-processor.html\"\u003eInference processor\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\n\u003cp\u003eYou can define an ingest pipeline in the \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/current/ml-nlp-inference.html#ml-nlp-inference-processor\"\u003eStack Management UI\u003c/a\u003e or configure it in Kibana Console; this one contains multiple ingest processors:\u003c/p\u003e"}],"_metadata":{"uid":"csfbe817753f159ce1"}}},{"code":{"code":"PUT _ingest/pipeline/ner\n{\n \"description\": \"NER pipeline\",\n \"processors\": [\n {\n \"inference\": {\n \"model_id\": \"elastic__distilbert-base-uncased-finetuned-conll03-english\",\n \"target_field\": \"ml.ner\",\n \"field_map\": {\n \"paragraph\": \"text_field\"\n }\n }\n },\n {\n \"script\": {\n \"lang\": \"painless\",\n \"if\": \"return ctx['ml']['ner'].containsKey('entities')\",\n \"source\": \"Map tags = new HashMap(); for (item in ctx['ml']['ner']['entities']) { if (!tags.containsKey(item.class_name)) tags[item.class_name] = new HashSet(); tags[item.class_name].add(item.entity);} ctx['tags'] = tags;\"\n }\n }\n ],\n \"on_failure\": [\n {\n \"set\": {\n \"description\": \"Index document to 'failed-\u003cindex\u003e'\",\n \"field\": \"_index\",\n \"value\": \"failed-{{{ _index }}}\"\n }\n },\n {\n \"set\": {\n \"description\": \"Set error message\",\n \"field\": \"ingest.failure\",\n \"value\": \"{{_ingest.on_failure_message}}\"\n }\n }\n ]\n}\n","_metadata":{"uid":"cs033a734d1ec4b9bc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs71e2d762578a54fd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eStarting with the \u003ccode\u003einference\u003c/code\u003e processor, the purpose of \u003ccode\u003efield_map\u003c/code\u003e is to map \u003ccode\u003eparagraph\u003c/code\u003e (the field to analyze in the source documents) to text_field (the name of the field the model is configured to use). \u003ccode\u003etarget_field\u003c/code\u003e is the name of the field to write the inference results to.\u003c/p\u003e\n\u003cp\u003eThe \u003ccode\u003escript\u003c/code\u003e processor pulls out the entities and groups them by type. The end result is lists of people, locations, and organizations detected in the input text. We are adding this painless script so that we can build visualizations from the fields that are created.\u003c/p\u003e\n\u003cp\u003eThe \u003ccode\u003eon_failure\u003c/code\u003e clause is there to catch errors. It defines two actions. First, it sets the \u003ccode\u003e_index\u003c/code\u003e meta field to a new value, and the document will now be stored there. Secondly, the error message is written to a new field: \u003ccode\u003eingest.failure\u003c/code\u003e. Inference can fail for a number of easily fixable reasons. Perhaps the model has not been deployed, or the input field is missing in some of the source documents. By redirecting the failed documents to another index and setting the error message, those failed inferences are not lost and can be reviewed later. Once the errors are fixed, reindex from the failed index to recover the unsuccessful requests.\u003c/p\u003e"}],"_metadata":{"uid":"cs002baa0982b6151d"}}},{"title_text":{"title_text":[{"title_l10n":"Selecting the text fields for Inference","_metadata":{"uid":"cscfd7e688e84d4733"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNER can be applied to many datasets. As an example I've picked Victor Hugo’s classic 1862 novel \u003ccite\u003eLes Misérables\u003c/cite\u003e. You can upload the \u003ccite\u003eLes Misérables\u003c/cite\u003e paragraphs of our \u003ca href=\"https://github.com/grabowskit/nlp-data/blob/main/les-miserables-nd.json\" target=\"_self\"\u003esample json file\u003c/a\u003e using \u003ca href=\"https://www.elastic.co/guide/en/kibana/current/connect-to-elasticsearch.html#upload-data-kibana\" target=\"_self\"\u003eKibana's file upload\u003c/a\u003e feature. The text is split into 14,021 JSON documents each containing a single paragraph. Taking a random paragraph as an example:\u003c/p\u003e"}],"_metadata":{"uid":"cs3268ac2375d7ae1a"}}},{"code":{"code":"{\n \"paragraph\": \"Father Gillenormand did not do it intentionally, but inattention to proper names was an aristocratic habit of his.\",\n \"line\": 12700\n}\n","_metadata":{"uid":"cscf9f0db4ab10aabb"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaa8ee285b75f143a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOnce the paragraph is ingested through the NER pipeline, the resulting document stored in Elasticsearch is marked up with one identified person.\u003c/p\u003e"}],"_metadata":{"uid":"cs698a94af4898ab52"}}},{"code":{"code":"{\n \"paragraph\": \"Father Gillenormand did not do it intentionally, but inattention to proper names was an aristocratic habit of his.\",\n \"@timestamp\": \"2020-01-01T17:38:25\",\n \"line\": 12700,\n \"ml\": {\n \"ner\": {\n \"predicted_value\": \"Father [Gillenormand](PER\u0026Gillenormand) did not do it intentionally, but inattention to proper names was an aristocratic habit of his.\",\n \"entities\": [{\n \"entity\": \"Gillenormand\",\n \"class_name\": \"PER\",\n \"class_probability\": 0.9806354093873283,\n \"start_pos\": 7,\n \"end_pos\": 19\n }],\n \"model_id\": \"elastic__distilbert-base-cased-finetuned-conll03-english\"\n }\n },\n \"tags\": {\n \"PER\": [\n \"Gillenormand\"\n ]\n }\n}\n","_metadata":{"uid":"csd25e57523000555d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs530bdc4d73376955"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eA tag cloud is a visualization that scales words by the frequency at which they occur and is the perfect infographic for viewing the entities found in \u003ccite\u003eLes Misérables\u003c/cite\u003e. Open Kibana and create a new aggregation-based visualization and then pick Tag Cloud. Select the index containing the NER results and add a terms aggregation on the \u003ccode\u003etags.PER.keyword\u003c/code\u003e field.\u003c/p\u003e"}],"_metadata":{"uid":"cs760f9db0898253f4"}}},{"image":{"image":{"_version":1,"is_dir":false,"uid":"bltc450643fc30ff5fc","ACL":{},"content_type":"image/png","created_at":"2022-04-06T19:42:58.855Z","created_by":"blt3044324473ef223b70bc674c","file_size":"263766","filename":"nlp-getting-started-part2-les-miserables-entities-tag-cloud.png","parent_uid":null,"tags":[],"title":"nlp-getting-started-part2-les-miserables-entities-tag-cloud.png","updated_at":"2022-04-06T19:42:58.855Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-27T17:50:49.658Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc450643fc30ff5fc/624ded42c674a505586e2cb2/nlp-getting-started-part2-les-miserables-entities-tag-cloud.png"},"_metadata":{"uid":"cs4e74a86778b545bb"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs09b081c69ba17508"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIt is easy to see from the visualization that Cosette, Marius, and Jean Valjean are the most frequently mentioned characters in the book.\u003c/p\u003e"}],"_metadata":{"uid":"cs9374cec416bac5a5"}}},{"title_text":{"title_text":[{"title_l10n":"Tuning the deployment","_metadata":{"uid":"cs14827f6d31e6c027"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eReturning to the Model Management UI, under Deployment stats you will find the \u003cstrong\u003eAvg Inference Time\u003c/strong\u003e. This is the time measured by the native process to perform inference on a single request. When \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/start-trained-model-deployment.html\" target=\"_self\"\u003estarting a deployment\u003c/a\u003e there are two parameters that control how CPU resources are used: inference_threads and model_threads.\u003c/p\u003e\n\u003cp\u003einference_threads is the number of threads used to run the model per request. Increasing inference_threads directly reduces average inference time. The number of requests that are evaluated in parallel is controlled by model_threads. This setting will not reduce average inference time but increases throughput.\u003c/p\u003e\n\u003cp\u003eIn general, tune for latency by increasing the number of inference_threads and increase throughput by raising the number of model_threads. Both the settings default to one thread, so there is plenty of performance to be gained by modifying them. The effect is demonstrated using the NER model.\u003c/p\u003e\n\u003cp\u003eTo change one of the thread settings, the deployment must be stopped and restarted. The ?force=true parameter is passed to the stop API because the deployment is referenced by an ingest pipeline which would normally prevent stopping.\u003c/p\u003e"}],"_metadata":{"uid":"cs44c50808a177e085"}}},{"code":{"code":"POST _ml/trained_models/elastic__distilbert-base-uncased-finetuned-conll03-english/deployment/_stop?force=true\n","_metadata":{"uid":"cs3eaf78fee0cbc91b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs28b5484a9b123ba5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAnd restart with four inference threads. Average inference time is reset when the deployment is restarted.\u003c/p\u003e"}],"_metadata":{"uid":"cs764ab92f6b05d719"}}},{"code":{"code":"POST _ml/trained_models/elastic__distilbert-base-uncased-finetuned-conll03-english/deployment/_start?inference_threads=4","_metadata":{"uid":"csd6bd6c7bbf546205"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs38d28115a53b72b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhen processing the \u003ccite\u003eLes Misérables\u003c/cite\u003e paragraphs, average inference time falls to 55.84 milliseconds per request compared to 173.86 milliseconds for one thread.\u003c/p\u003e"}],"_metadata":{"uid":"cscf33055186b7a9cf"}}},{"title_text":{"title_text":[{"title_l10n":"Learning more and trying it out","_metadata":{"uid":"cs5ee1ce81e831dd28"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eNER is just one of the NLP tasks ready to use now. Text classification, zero shot classification and text embeddings are also available. More examples can be found in the NLP \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/8.0/ml-nlp.html\" target=\"_self\"\u003edocumentation\u003c/a\u003e along with a by-no-means-exhaustive \u003ca href=\"https://www.elastic.co/guide/en/machine-learning/8.0/ml-nlp-model-ref.html\" target=\"_self\"\u003elist of models\u003c/a\u003e deployable to the Elastic Stack.\u003c/p\u003e\u003cp\u003eNLP is a major new feature in the Elastic Stack for 8.0 with an exciting roadmap. Discover new features and keep up with the latest developments by building your cluster in Elastic Cloud. Sign up for a \u003ca href=\"https://cloud.elastic.co/registration\" target=\"_self\"\u003efree 14-day trial\u003c/a\u003e today and try the examples in this blog.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch4\u003eIf you want more NLP reads:\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/how-to-deploy-nlp-text-embeddings-and-vector-search\" target=\"_blank\"\u003eHow to deploy NLP text embeddings and vector search\u2028\u2028\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-deploy-nlp-sentiment-analysis-example\" target=\"_blank\"\u003eHow to deploy NLP sentiment analysis\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-deploy-natural-language-processing-nlp-getting-started\" target=\"_blank\"\u003eHow to deploy natural language processing: Getting started\u2028\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"cs9cab90fbdd895489"}}}],"publish_date":"2022-05-20","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How to deploy NLP: Named entity recognition (NER) example","seo_description_l10n":"Using named entity recognition (NER) as an example, this blog describes the process for getting up and running using deep learning models for natural language processing (NLP) in Elasticsearch.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"Natural Language Processing (NLP)","label_l10n":"Natural Language Processing (NLP)","keyword":"natural-language-processing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt97696fc6e9921c30","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:43:16.119Z","updated_at":"2023-11-06T20:43:16.119Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:23:24.704Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9149a5fda79fd708","ACL":{},"created_at":"2023-11-06T20:37:49.356Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"deployment","label_l10n":"Deployment","tags":[],"title":"Deployment","updated_at":"2023-11-06T20:37:49.356Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.169Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt03343e31035d9e73","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2023-05-11T16:19:15.142Z","updated_at":"2023-05-11T16:19:15.142Z","content_type":"image/png","file_size":"135153","filename":"illustration-campaign-ansof-1680x980.png","title":"illustration-campaign-ansof-1680x980.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-11T16:20:52.502Z","user":"bltd9765be97bbed20c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt03343e31035d9e73/645d15830830e25a5ced06de/illustration-campaign-ansof-1680x980.png"},"title":"How to deploy NLP: Named entity recognition (NER) example","title_l10n":"How to deploy NLP: Named entity recognition (NER) example","updated_at":"2025-02-25T22:39:35.130Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/how-to-deploy-nlp-named-entity-recognition-ner-example","publish_details":{"time":"2025-02-25T22:48:05.589Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0882d1df226e052d","_version":13,"locale":"en-us","ACL":{},"abstract_l10n":"Get started with ES|QL and learn how to use it to analyze, visualize, and get insights from your data. ES|QL accelerates your workflows by allowing you to create visualizations, calculations, and aggregations directly from one screen.","author":["blt66fc5c9958656092"],"category":[],"created_at":"2023-10-31T15:26:03.809Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"What is ES|QL (Elasticsearch Query Language)?","_metadata":{"uid":"csb27621934e380759"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eES|QL (Elasticsearch Query Language) is Elastic®'s new innovative piped query language, designed to speed up your data analysis and investigation processes by offering powerful computing and aggregation capabilities.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eNavigate through the complexities of identifying unfolding cyber attacks or pinpointing production issues with enhanced ease and efficiency.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eES|QL not only simplifies searching, aggregating, and visualizing massive data sets but also empowers users with advanced features like lookups and real-time processing, all from a single screen in Discover.\u003c/p\u003e"},{"title_l10n":"ES|QL adds 3 powerful capabilities to the Elastic Stack","_metadata":{"uid":"cscf656d0444a5b7c7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003c/p\u003e\n\u003col\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eA new and fast Distributed \u0026amp; Dedicated Query Engine\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that powers \u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003e_query\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe new ES|QL query engine delivers advanced search capabilities with concurrent processing, improving speed and efficiency irrespective of data source and structure\u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e.\u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe performance of the new engine is measured and is public. Follow along with performance benchmarking in \u003c/span\u003e\u003ca href=\"https://elasticsearch-benchmark-analytics.elastic.co/app/dashboards#/view/0f02d4a0-e02c-11ed-8269-e92d5d639852?_g=(refreshInterval%3A(pause%3A!t%2Cvalue%3A60000)%2Ctime%3A(from%3Anow-15d%2Cto%3Anow))\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethis public dashboard\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eA new and powerful piped language. \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eES|QL is Elastic’s new piped language that transforms, enriches, and simplifies data investigations. Learn more about ES|QL language’s capabilities in \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethe documentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eA new and unified data exploration/investigation experience\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that accelerates resolution by creating aggregations and visualizations from one screen delivering an uninterrupted workflow.\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n\u003c/ol\u003e"}],"_metadata":{"uid":"cs7bbf072be2057d14"}}},{"title_text":{"title_text":[{"title_l10n":"Why did we invest time and effort into ES|QL?","_metadata":{"uid":"cs5d5dc5c2204537bc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur users need agile tools that not only present data but also offer efficient methods to make sense of it, as well as the ability to act on insights in real time and post ingest data processing.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s commitment to enhancing users’ data exploration experience drove us to invest in ES|QL. It is designed to be accessible for beginners and powerful for experts. With ES|QL’s intuitive interface, users can start quickly and dive deep into their data without steep learning curves. The auto-complete and in-app documentation ensure that crafting advanced queries becomes a straightforward workflow.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMoreover, ES|QL doesn’t just show you numbers; it brings them to life. Contextual visualizations powered by Lens suggestion engine automatically adapt to the nature of your queries, providing a clear view of your insights.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdditionally, a direct integration into Dashboards and Alerting functionalities reflects our vision of a cohesive, end-to-end experience.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn essence, our investment in ES|QL was a direct response to the evolving needs of our community — a step toward a more interconnected, insightful, and efficient workflow.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Delving deeper into security and observability use cases","_metadata":{"uid":"csc72121aab83371dd"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOur commitment to ES|QL also stems from a deep understanding of the challenges faced by our users (e.g., site reliability engineers (SREs), DevOps, and threat hunters).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSREs\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e,\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eobservability is essential. Every second of downtime or glitch can have a cascading effect on user experience and, consequently, the bottom line. An example of that is ES|QL’s Alerting feature: with its emphasis on highlighting meaningful trends over isolated incidents, SREs can proactively pinpoint and address system inefficiencies or failures. This reduces the noise and ensures they are reacting to genuine threats to system stability, making their response more timely and effective.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eDevOps\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e teams are consistently in a race against time, deploying multiple updates, patches, and new features. With ES|QL’s new and powerful data exploration and data visualization, they can quickly assess the impact of every deployment, monitor system health, and receive real-time feedback. This not only enhances the quality of deployments but also ensures rapid course correction, if needed.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ethreat hunters\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, the security landscape is constantly evolving and changing. An example of how ES|QL empowers them in this changing landscape is the ENRICH feature. This feature allows them to look up data across different data sets, thereby unveiling hidden patterns or anomalies that might indicate a security threat. Additionally, contextual visualizations mean they don’t just see raw data but get actionable insights, presented visually. This drastically reduces the time taken to discern potential threats, ensuring quicker reactions to vulnerabilities.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhether you’re an SRE trying to decipher a spike in server load, a DevOps professional assessing the impact of the latest release, or a threat hunter investigating a potential breach, ES|QL complements the user, rather than complicating the journey.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe next sections of the blog post will help you get started with ES|QL and showcase some tangible examples of how powerful it is when exploring your data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How to get started with ES|QL in Kibana","_metadata":{"uid":"cs2d898b30d1237955"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo begin using ES|QL, navigate to Discover and simply select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTry ES|QL\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e from the data-view picker. It’s user-friendly and straightforward.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5a626c1b1cc5cf57"}}},{"image":{"image":{"uid":"bltf1ba0812b74b1ada","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:45:29.863Z","created_by":"bltb6c155cd84fc0c1a","file_size":"284665","filename":"elastic-blog-1-how-to-get-started.png","parent_uid":null,"tags":[],"title":"elastic-blog-1-how-to-get-started.png","updated_at":"2023-11-01T17:45:29.863Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.494Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf1ba0812b74b1ada/65428eb908cc0104077cd28a/elastic-blog-1-how-to-get-started.png"},"_metadata":{"uid":"cs947fc9a3938761a3"},"caption_l10n":"","alt_text_l10n":"1 - get started","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4ea73e103c0751e0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis will get you into ES|QL mode in Discover.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Efficient and easy query building","_metadata":{"uid":"cs6fc054d4aabc462c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL in Discover offers auto-complete and in-app documentation, making it easy to craft powerful queries right from the query bar.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs62b7285da6c176b6"}}},{"image":{"image":{"uid":"blt8aa55c995836851c","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:45:50.201Z","created_by":"bltb6c155cd84fc0c1a","file_size":"108122","filename":"elastic-blog-2-efficient-and-easy-query.png","parent_uid":null,"tags":[],"title":"elastic-blog-2-efficient-and-easy-query.png","updated_at":"2023-11-01T17:45:50.201Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.567Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8aa55c995836851c/65428ecea67ffd001b94e2fa/elastic-blog-2-efficient-and-easy-query.png"},"_metadata":{"uid":"csa15e6d13e4a3a468"},"caption_l10n":"Auto-complete in the query bar to help you complete a query fast","alt_text_l10n":"2 - Auto-complete in the query bar to help you complete a query fast","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"uid":"blt2bdf80a2c1c06c70","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:45:58.900Z","created_by":"bltb6c155cd84fc0c1a","file_size":"352533","filename":"elastic-blog-3-in-app-documentation.png","parent_uid":null,"tags":[],"title":"elastic-blog-3-in-app-documentation.png","updated_at":"2023-11-01T17:45:58.900Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.702Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2bdf80a2c1c06c70/65428ed6d8b7e20407a868a8/elastic-blog-3-in-app-documentation.png"},"_metadata":{"uid":"cse36e7885e2d7ed20"},"caption_l10n":"In-app documentation, right there to help you learn ES|QL!","alt_text_l10n":"3 - In-app documentation, right there to help you learn ES|QL!","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"How to analyze and visualize data with ES|QL","_metadata":{"uid":"cs5e343587bc54d83d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith ES|QL, you can do comprehensive and powerful data exploration.\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIt allows you to conduct ad-hoc data exploration within Discover, create aggregations, transform data, enrich data sets, and more, directly from the query builder. Results are presented in a tabular format or as visualizations — it depends on the query you are executing.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow you will find examples of ES|QL queries for observability and how the results are represented in both a tabular format and as a visual representation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eES|QL query with metrics use case:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8a6acd462db4827d"}}},{"code":{"code":"from metrics* \n| stats max_cpu = max(kubernetes.pod.cpu.usage.node.pct), max_mem = max(kubernetes.pod.memory.usage.bytes) by kubernetes.pod.name \n| sort max_cpu desc \n| limit 10","_metadata":{"uid":"cs653da0eb40f35a66"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs93d2d5f30e1bd07a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe above query is showcasing how you can utilize following source command, aggregation functions, and processing commands:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003efrom \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003esource command (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-from\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003efrom metrics*: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis initiates a query from index patterns that match the pattern “metrics*.” The asterisk(*) acts as a wildcard, meaning it will select data from all index patterns whose names start with “metrics.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003estats…by \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eaggregations (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-stats-by\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e), \u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003emax \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e(\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-functions-operators.html#esql-agg-max\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e), and \u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003eby\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-stats-by\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis segment aggregates data based on specific statistics. It breaks down as follows:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003emax_cpu=max(kubernetes.pd.cpu.usage.node.pct): \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor each distinct “kubernetes.pod.name,” it finds the maximum CPU usage percentage and stores that value in a new column named “max_cpu.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003emax_mem = max(kubernettes.pod.memory.usage.bytes): For each distinct “kubernetes.pod.name,” it finds the maximum memory usage in bytes and stores that value in a new column named “avg_mem.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eProcessing commands (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003esort\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-sort\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003elimit\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-limit\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003esort max_cpu desc:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e This sorts the resulting data rows by the “max_cpu” column in descending order. This means the row with the highest “max_cpu” value will be at the top.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003elimit 10: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis limits the output to the top 10 rows after sorting.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eIn summary, the query:\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGroups data from all metric indices using an index pattern\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAggregates the data to find the maximum CPU usage percentage and maximum memory usage for each distinct Kubernetes pod\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSorts the aggregated data by the maximum CPU usage in descending order\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOutputs only the top 10 rows with the highest CPU usage\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eContextual visualizations: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWhen writing ES|QL queries in Discover, you’ll receive visual representations powered by the Lens suggestion engine. Your query’s nature determines the type of visualization you get, whether it’s a Metric, Histogram Heatmap, etc.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBelow is a visual representation in the form of a bar chart and a table representation of the above query with columns max_cpu, avg_mem, and kubernetes.pod.name:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs99cd46561258cd0c"}}},{"image":{"image":{"uid":"blt203fb89ae7c2c361","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:46:12.210Z","created_by":"bltb6c155cd84fc0c1a","file_size":"267601","filename":"elastic-blog-4-several-bar-graphs.png","parent_uid":null,"tags":[],"title":"elastic-blog-4-several-bar-graphs.png","updated_at":"2023-11-01T17:46:12.210Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.763Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt203fb89ae7c2c361/65428ee42149b10407ad85e5/elastic-blog-4-several-bar-graphs.png"},"_metadata":{"uid":"csd1315e5049e39ff0"},"caption_l10n":"","alt_text_l10n":"4 - several bar graphs","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs08166c0097ed6ed7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eExample of an ES|QL query with Observability and time-series data use case:\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6c9ec1513a98f0c4"}}},{"code":{"code":"from apache-logs |\nwhere url.original == \"/login\" |\neval time_buckets = auto_bucket(@timestamp, 50, \"2023-09-11T21:54:05.000Z\", \"2023-09-12T00:40:35.000Z\") |\nstats login_attempts = count(user.name) by time_buckets, user.name |\nsort login_attempts desc","_metadata":{"uid":"cs0169640615a6b10c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2ba8009cf89de7d2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe above query is showcasing how you can utilize the following source command, aggregation functions, processing commands, and functions.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003efrom \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003esource command (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-from\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003efrom apache-logs: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis initiates a query from an index named “apache-logs.” This index contains log entries related to Apache web server traffic.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003ewhere\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-where\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ewhere url.original==”/login”: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFilters the records to only those where the “url.original” field equals “/login.” This means we are only interested in log entries pertaining to login attempts or accesses to the login page.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003eeval\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-eval\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e) \u0026amp; \u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003eauto_bucket\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-functions-operators.html#esql-auto_bucket\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eeval time_buckets =... : \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis creates a new column named “time_buckets.”\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eauto_bucket” \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003efunction creates human-friendly buckets and returns a datetime value for each row that corresponds to the resulting bucket the row falls into.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“@timestamp”\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is the field containing the timestamp of each log entry.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“50” \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eis the number of buckets.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“2023-09-11T21:54:05.000Z”: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStart time for bucketing\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“2023-09-12T00:40:35.000Z”: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEnd time for bucketing\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis means that log entries from “2023-09-11T21:54:05.000Z” to “2023-09-12T00:40:35.000Z” will be divided into 50 equally spaced intervals, and each entry will be associated with a specific interval based on its timestamp.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe goal isn’t to provide exactly the target number of buckets, it’s to pick a range that you are comfortable with that provides at most the target number of buckets. If you ask for more buckets, then \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eauto_bucket \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecan pick a smaller range.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003estats…by \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eaggregations (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-stats-by\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e), \u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003ecount\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-functions-operators.html#esql-agg-count\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e), and \u003c/span\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003eby\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-stats-by\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003estats login_attempts = count(user.name) by time_buckets, user.name: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAggregates the data to calculate the number of login attempts. It does this by counting the occurrences of \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“user.name”\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (representing unique users attempting to log in).\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe count is grouped by both the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“time_buckets”\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (the time intervals we created) and \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“user.name.” \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis means for each time bucket, we will see how many times each user attempted to log in.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"color: rgb(56, 118, 29);font-size: 12pt;\"\u003e\u003cstrong\u003esort\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-sort\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e)\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSort login_attempts desc: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFinally, the aggregated results are sorted by the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e“login_attempts” \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecolumn in descending order. This means the result will show the highest number of login attempts at the top.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eIn summary, the query:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSelects data from the “apache-logs” index\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFilters for log entries related to the login page\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBuckets these entries into specific time intervals\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCounts the number of login attempts for each user in each of those time intervals\u003c/span\u003e\u003c/li\u003e\n \u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOutputs the results sorted by the highest number of login attempts first\u003c/span\u003e\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBelow is a visual representation in the form of a bar chart and a table representation of the above query with columns login_attempts, time_buckets, and user.name.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1cd6b02f09e41056"}}},{"image":{"image":{"uid":"blt350adfd5153b0e80","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:46:35.545Z","created_by":"bltb6c155cd84fc0c1a","file_size":"274873","filename":"elastic-blog-5-colored-graphs.png","parent_uid":null,"tags":[],"title":"elastic-blog-5-colored-graphs.png","updated_at":"2023-11-01T17:46:35.545Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.662Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt350adfd5153b0e80/65428efbaadaa1001b1093ac/elastic-blog-5-colored-graphs.png"},"_metadata":{"uid":"cs1b8c9cd929eaa429"},"caption_l10n":"","alt_text_l10n":"5 - color graphs","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"In-line visualization editing in Discover \u0026 Dashboard","_metadata":{"uid":"cs8a782d27d042638a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEdit ES|QL visualizations directly within Discover and Dashboards. No need to navigate to Lens for quick edits; you can make changes seamlessly.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow you can see a video of an end-to-end workflow or read the step-by-step guide:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWriting an ES|QL query\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGetting contextual visualization based on the nature of the query\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn-line edit the visualization\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSave it to a Dashboard\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBe able to edit the visualization from a Dashboard\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"}],"_metadata":{"uid":"cs6cb01e38decde1c4"}}},{"video":{"vidyard_uuid":"MuuxB5dwHjcha9i4op3UmC","_metadata":{"uid":"cs59d3761ed45c302e"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb27e67bafa8bfb87"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eStep 1. Writing an ES|QL query.\u003c/strong\u003e\u003c/span\u003e \u003cspan style=\"font-size: 12pt;\"\u003eQuery example that produces a metric visualization:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs260b224b6872c7c3"}}},{"code":{"code":"from apache-logs\n| stats avgbytes = avg(http.response.body.bytes)\n| eval roundbytes = round(avgbytes)\n| drop avgbytes","_metadata":{"uid":"cs80a1c8480a4ef96d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs393085e80555adb0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 2. Getting contextual visualization (in this case a metric visualization) based on the nature of the query. \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eYou can then select the pencil icon to go into in-line editing mode.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csba553e54dac00b43"}}},{"image":{"image":{"uid":"blt9ca9cef70e1f64e9","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:46:55.646Z","created_by":"bltb6c155cd84fc0c1a","file_size":"120430","filename":"elastic-blog-6-15137.png","parent_uid":null,"tags":[],"title":"elastic-blog-6-15137.png","updated_at":"2023-11-01T17:46:55.646Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.508Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9ca9cef70e1f64e9/65428f0f2797e3040709d23a/elastic-blog-6-15137.png"},"_metadata":{"uid":"csde3542a87f61cd22"},"caption_l10n":"","alt_text_l10n":"6","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6cd7c4d6dd99671f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 3. Editing the visualization using in-line editing mode\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbe45d1c7833c3208"}}},{"image":{"image":{"uid":"blt61e365cece326df9","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:47:04.565Z","created_by":"bltb6c155cd84fc0c1a","file_size":"244264","filename":"elastic-blog-7-15137.png","parent_uid":null,"tags":[],"title":"elastic-blog-7-15137.png","updated_at":"2023-11-01T17:47:04.565Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.582Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt61e365cece326df9/65428f1808cc0104077cd292/elastic-blog-7-15137.png"},"_metadata":{"uid":"csb4a9363dce5e606f"},"caption_l10n":"","alt_text_l10n":"7","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs59269c985971ab90"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the above case, we want the visualization to be in dynamic color mode, so we switch it to “Dynamic.”\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7608b9d995bdeb71"}}},{"image":{"image":{"uid":"blt123edfb052aa943f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:47:16.700Z","created_by":"bltb6c155cd84fc0c1a","file_size":"233205","filename":"elastic-blog-8-gold-bar-graph.png","parent_uid":null,"tags":[],"title":"elastic-blog-8-gold-bar-graph.png","updated_at":"2023-11-01T17:47:16.700Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.715Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt123edfb052aa943f/65428f248b3f8e001b7aec04/elastic-blog-8-gold-bar-graph.png"},"_metadata":{"uid":"cs317c8983b1001dde"},"caption_l10n":"","alt_text_l10n":"8","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd4dadea5edbcd6e2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe also have the opportunity to define the color ranges we want to use:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7450af801932a573"}}},{"image":{"image":{"uid":"blt00874e115e7dd3c0","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:47:27.862Z","created_by":"bltb6c155cd84fc0c1a","file_size":"224701","filename":"elastic-blog-9-gold-bar-graph.png","parent_uid":null,"tags":[],"title":"elastic-blog-9-gold-bar-graph.png","updated_at":"2023-11-01T17:47:27.862Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.777Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt00874e115e7dd3c0/65428f2fa036750407c8314b/elastic-blog-9-gold-bar-graph.png"},"_metadata":{"uid":"csc2e517343cf3a00c"},"caption_l10n":"","alt_text_l10n":"9","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0aa8c06b2e6cdab2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 4. Saving to a Dashboard\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7761391b6ba5784b"}}},{"image":{"image":{"uid":"bltbe1422cdfcdbc953","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:47:38.504Z","created_by":"bltb6c155cd84fc0c1a","file_size":"116011","filename":"elastic-blog-10-bar-graph-saving-to-dashboard.png","parent_uid":null,"tags":[],"title":"elastic-blog-10-bar-graph-saving-to-dashboard.png","updated_at":"2023-11-01T17:47:38.504Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.676Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbe1422cdfcdbc953/65428f3a36795e040703dc94/elastic-blog-10-bar-graph-saving-to-dashboard.png"},"_metadata":{"uid":"cs5faac3e19486e755"},"caption_l10n":"","alt_text_l10n":"10","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"bltb970816bf07da660","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:47:49.185Z","created_by":"bltb6c155cd84fc0c1a","file_size":"149813","filename":"elastic-blog-11-save-lens-vis.png","parent_uid":null,"tags":[],"title":"elastic-blog-11-save-lens-vis.png","updated_at":"2023-11-01T17:47:49.185Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.523Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb970816bf07da660/65428f4520567d001b0915c0/elastic-blog-11-save-lens-vis.png"},"_metadata":{"uid":"cs803166f525a91bf7"},"caption_l10n":"","alt_text_l10n":"11","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csaf21b6aca8e16496"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 5. Be able to edit the visualization from a Dashboard\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f1c91544a5e4b89"}}},{"image":{"image":{"uid":"blt1516bd02e3161f54","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:48:02.113Z","created_by":"bltb6c155cd84fc0c1a","file_size":"126764","filename":"elastic-blog-12-roundbytes.png","parent_uid":null,"tags":[],"title":"elastic-blog-12-roundbytes.png","updated_at":"2023-11-01T17:48:02.113Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.596Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1516bd02e3161f54/65428f52a036750407c83154/elastic-blog-12-roundbytes.png"},"_metadata":{"uid":"csa63f77c65311e359"},"caption_l10n":"","alt_text_l10n":"12 - roundbytes","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blta3517e76be216fdf","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:55:18.840Z","created_by":"bltb6c155cd84fc0c1a","file_size":"191503","filename":"elastic-blog-13-gold-roundbytes-15137.png","parent_uid":null,"tags":[],"title":"elastic-blog-13-gold-roundbytes-15137.png","updated_at":"2023-11-01T17:55:18.840Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.728Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta3517e76be216fdf/6542910662f244001b7d9e21/elastic-blog-13-gold-roundbytes-15137.png"},"_metadata":{"uid":"cs4cd591dd4bc7e547"},"caption_l10n":"","alt_text_l10n":"13","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Creating an ES|QL alert directly from Discover","_metadata":{"uid":"csf28dc732cd5df5a7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can utilize ES|QL for observability and security alerts, setting aggregated values as thresholds. Enhance detection accuracy and receive actionable notifications by emphasizing meaningful trends over isolated incidents, reducing false positives.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBelow, we will focus on how to create an ES|QL alert rule type from Discover.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe new alert rule type is available under the existing Elasticsearch rule type. This rule type brings all the new functionalities that are available within ES|QL and unlocks new alerting use cases.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith the new type, users will be able to generate a single alert based on a defined ES|QL query and preview the query result before saving the rule. When the query returns an empty result, no alerts will be generated.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eQuery example for an alert:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8a54f63e42d3eed0"}}},{"code":{"code":"from metrics-pods |\nstats max_cpu = max(kubernetes.pod.cpu.usage.node.pct) by kubernetes.pod.name|\nsort max_cpu desc | limit 10\n","_metadata":{"uid":"cs9634388fc4f721d7"}}},{"title_text":{"title_text":[{"title_l10n":"How to create an alert from Discover","_metadata":{"uid":"cs8d63d408c04e7e1a"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 1. Click on “Alerts” and then “Create search threshold rule.” \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eYou can start creating your ES|QL alert rule type either after you have defined your ES|QL query in the query bar or before you have defined your ES|QL query. The benefit of doing it after you have defined it is that the query automatically gets pasted into the “Create Alert” flyout.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6cf014252e368654"}}},{"image":{"image":{"uid":"blt6960b893560a5546","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:55:31.409Z","created_by":"bltb6c155cd84fc0c1a","file_size":"125921","filename":"elastic-blog-14-red-box.png","parent_uid":null,"tags":[],"title":"elastic-blog-14-red-box.png","updated_at":"2023-11-01T17:55:31.409Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.791Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6960b893560a5546/65429113d822120407106f4d/elastic-blog-14-red-box.png"},"_metadata":{"uid":"cs80170ee3ff493bb5"},"caption_l10n":"","alt_text_l10n":"14","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs970a7faff8e2b1b3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 2. Start defining your ES|QL alert rule type\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaf2893a301b6e821"}}},{"image":{"image":{"uid":"bltd27aa14576d2920b","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:55:42.787Z","created_by":"bltb6c155cd84fc0c1a","file_size":"280925","filename":"elastic-blog-15-create-rule.png","parent_uid":null,"tags":[],"title":"elastic-blog-15-create-rule.png","updated_at":"2023-11-01T17:55:42.787Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.689Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd27aa14576d2920b/6542911eaadaa1001b1093db/elastic-blog-15-create-rule.png"},"_metadata":{"uid":"cse8f8e1a3b8ad6c1f"},"caption_l10n":"","alt_text_l10n":"15","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd7f947f222c6e2f5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 3. Test your alert rule type query. \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eYou can iterate on the ES|QL query that is pasted in and test it by clicking on “Test query.” This will give you a preview of the results in a table.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse40e7fed5f1ce948"}}},{"image":{"image":{"uid":"blt4634f9d751ed194f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:55:53.089Z","created_by":"bltb6c155cd84fc0c1a","file_size":"136219","filename":"elastic-blog-16-create-rule.png","parent_uid":null,"tags":[],"title":"elastic-blog-16-create-rule.png","updated_at":"2023-11-01T17:55:53.089Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.537Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4634f9d751ed194f/65429129d8b7e20407a868c8/elastic-blog-16-create-rule.png"},"_metadata":{"uid":"cs36228f1582ba4f64"},"caption_l10n":"","alt_text_l10n":"16 - create rule","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"image":{"image":{"uid":"blt13d79f3cafffd085","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:56:05.156Z","created_by":"bltb6c155cd84fc0c1a","file_size":"114790","filename":"elastic-blog-17-test-query.png","parent_uid":null,"tags":[],"title":"elastic-blog-17-test-query.png","updated_at":"2023-11-01T17:56:05.156Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.609Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt13d79f3cafffd085/6542913562f244001b7d9e26/elastic-blog-17-test-query.png"},"_metadata":{"uid":"csfade9f7dddab6e44"},"caption_l10n":"","alt_text_l10n":"17 - test query","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs58c067afd08fe7d0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eStep 4. Set up your connector and “Save.” \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eYou have now successfully created an ES|QL alert rule type!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csea3680f34aac29c8"}}},{"image":{"image":{"uid":"blt6ba535d136bedd1f","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:13:36.943Z","created_by":"bltb6c155cd84fc0c1a","file_size":"133346","filename":"Screenshot_2023-11-01_at_1.13.16_PM.png","parent_uid":null,"tags":[],"title":"Screenshot_2023-11-01_at_1.13.16_PM.png","updated_at":"2023-11-01T17:13:36.943Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.742Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ba535d136bedd1f/6542874008cc0104077cd248/Screenshot_2023-11-01_at_1.13.16_PM.png"},"_metadata":{"uid":"csbe63dc94341ff645"},"caption_l10n":"","alt_text_l10n":"18","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"Enrich your query data set with fields from another data set","_metadata":{"uid":"cs2051f7413f99336c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou can use the enrich command (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-enrich\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e) to enhance your query data set with fields from another data set, complete with in-context suggestions for the selected policy (i.e., hinting the matching field and enriched columns).\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eQuery example using \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eENRICH\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e,\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003ewhere a enrich policy :”servers-to-project” is being utilized via the query to enrich the data set with name, server_hostname, and cost:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdb6b937ea7227e53"}}},{"code":{"code":"from projects* | limit 10 |\nenrich servers-to-project on project_id with name, server_hostname, cost |\nstats num_of_servers = count(server_hostname), total_cost = sum(cost) by project_id |\nsort total_cost desc","_metadata":{"uid":"csa7fa961ae02d848a"}}},{"image":{"image":{"uid":"bltd237c9c2672c99c2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:56:48.525Z","created_by":"bltb6c155cd84fc0c1a","file_size":"157817","filename":"elastic-blog-20-bar-graphs.png","parent_uid":null,"tags":[],"title":"elastic-blog-20-bar-graphs.png","updated_at":"2023-11-01T17:56:48.525Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.803Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd237c9c2672c99c2/65429160a184e7001b4f9493/elastic-blog-20-bar-graphs.png"},"_metadata":{"uid":"csbd786bb2d0e98ece"},"caption_l10n":"Tabular results and visual representation of the query with ENRICH above","alt_text_l10n":"20","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs845ddc5ff1acdb9c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe have also made it easy for users to create enrich policies by adding an overview and a wizard to create enrich policies.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo find an overview of enrich policies, navigate to Stack Management ⇒ Index Management, and there you will see a tab called \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnrich Policies\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1ace311b634c3be0"}}},{"image":{"image":{"uid":"bltd81a7d99b203e7e2","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:57:03.631Z","created_by":"bltb6c155cd84fc0c1a","file_size":"266827","filename":"elastic-blog-21-index-mgmt.png","parent_uid":null,"tags":[],"title":"elastic-blog-21-index-mgmt.png","updated_at":"2023-11-01T17:57:03.631Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.816Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd81a7d99b203e7e2/6542916fa036750407c83169/elastic-blog-21-index-mgmt.png"},"_metadata":{"uid":"csbf5ef70b16bdef04"},"caption_l10n":"","alt_text_l10n":"21","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc4b2b98d7140dda5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHere is the enrich policy used in above query: “servers-to-project”:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs008f3dee16ce429d"}}},{"image":{"image":{"uid":"blt0acaf44bcd3aca75","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:57:16.139Z","created_by":"bltb6c155cd84fc0c1a","file_size":"247851","filename":"elastic-blog-22-servers-to-project.png","parent_uid":null,"tags":[],"title":"elastic-blog-22-servers-to-project.png","updated_at":"2023-11-01T17:57:16.139Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.551Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0acaf44bcd3aca75/6542917c0970dd001bd15e96/elastic-blog-22-servers-to-project.png"},"_metadata":{"uid":"cscbc29c74a5795029"},"caption_l10n":"","alt_text_l10n":"22","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csea34a40a5ba38020"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can easily start creating a new enrich policy by clicking on \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCreate enrich policy\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. As soon as you have created and executed one, it can then be used in an ES|QL query in Discover.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs48bacf430a2ac714"}}},{"image":{"image":{"uid":"blt32012e4b1efbc1a9","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-01T17:57:28.171Z","created_by":"bltb6c155cd84fc0c1a","file_size":"237767","filename":"elastic-blog-23-create-enrich-policy.png","parent_uid":null,"tags":[],"title":"elastic-blog-23-create-enrich-policy.png","updated_at":"2023-11-01T17:57:28.171Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.621Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt32012e4b1efbc1a9/654291880970dd001bd15e9a/elastic-blog-23-create-enrich-policy.png"},"_metadata":{"uid":"cs2cfdd6e676296f76"},"caption_l10n":"","alt_text_l10n":"23 - create enrich policy","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3cc77469d719bb3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn more about enrich policies \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-enrich-data.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehere\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and about the ENRICH command in ES|QL \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql-commands.html#esql-enrich\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehere\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Elevating data exploration: The power and promise of ES|QL","_metadata":{"uid":"csa91525e0ccb594cc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL is Elastic’s latest innovation to advance data analysis and exploration. It’s not just about showing data; it’s about making it understandable, actionable, and visually appealing. Powered by a fast, distributed, and dedicated query engine, designed as a new piped language and wrapped in a unified data exploration experience, ES|QL meets the challenges of users such as site reliability engineers, DevOps, threat hunters, and other types of analysts.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL empowered SREs to tackle system inefficiencies effectively, aids DevOps in ensuring quality deployments, and provides threat hunters with tools to quickly discern potential security threats. Its direct integration into Dashboards, in-line visualization editing, alert functionalities, and abilities like enrich commands provide a seamless and efficient workflow. The ES|QL interface combines both power and user-friendliness, allowing users to dive deep into their data, making their analysis simpler and more insightful. The launch of ES|QL is just a continuation of Elastic’s journey around enhancing data exploration experiences and addressing the evolving needs of our user community.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou can try all of the capabilities of ES|QL today! To do so, sign up for an \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic trial account\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or test it out on our \u003c/span\u003e\u003ca href=\"https://esql.demo.elastic.co\"\u003e\u003cspan style='font-size: 12pt;'\u003epublic demo environment\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbdaf14a85f143def"}}}],"publish_date":"2023-11-07","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Shorten your time to insights by creating aggregations, visualizations, and alerts directly from Discover with ES|QL","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt4667af6ab5dfbc82","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-10-31T15:08:18.007Z","created_by":"bltb6c155cd84fc0c1a","file_size":"76555","filename":"ES_QL_blog-720x420-07.png","parent_uid":null,"tags":[],"title":"ES_QL_blog-720x420-07.png","updated_at":"2023-10-31T15:08:18.007Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:01.649Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4667af6ab5dfbc82/65411862c2b34d001be73bfa/ES_QL_blog-720x420-07.png"},"title":"Getting started with ES|QL (Elasticsearch Query Language)","title_l10n":"Getting started with ES|QL (Elasticsearch Query Language) ","updated_at":"2025-02-25T21:50:46.411Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/getting-started-elasticsearch-query-language","publish_details":{"time":"2025-02-25T21:50:56.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt60b7a8d9cb8c22b3","_version":8,"locale":"en-us","ACL":{},"abstract_l10n":"Introducing ES|QL: Elastic's piped query language. Transform, enrich, and simplify data investigations with concurrent processing, efficient searches across data, and all-in-one screen aggregations and visualizations delivering iterative workflows.","author":["blt59e7f7049d793705","blt19aa6eaf05f480b6","blt91eeaf08ab3d1d6a"],"category":["blt0c9f31df4f2a7a2b"],"created_at":"2023-11-02T16:45:13.837Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs222fe93da4825778"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eToday, we are pleased to announce the technical preview of Elastic®’s new piped query language, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/esql.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eES|QL\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e (Elasticsearch Query Language), which transforms, enriches, and simplifies data investigations. Powered by a new query engine, ES|QL delivers advanced search capabilities with concurrent processing, improving speed and efficiency irrespective of data source and structure. Quickly resolve issues by creating aggregations and visualizations all from a single screen for an iterative and smooth workflow.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9dffee14040495c6"}}},{"video":{"vidyard_uuid":"B7awk5TY43Dq9VpQxbvmxA","_metadata":{"uid":"cs009e76748c563af9"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":true}},{"title_text":{"title_text":[{"title_l10n":"Evolution in Elasticsearch","_metadata":{"uid":"cs197c429163a56ea5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOver the past 13 years, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch®\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e has significantly evolved, adapting to user needs and the shifting digital landscape. Originally for full-text search, Elasticsearch expanded to support a broader set of use cases based on user feedback. Throughout this journey, the Elasticsearch \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/query-dsl.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eQuery DSL\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, our first adopted search language, provided a rich set of queries for filters, aggregations, and other operations. This JSON-based DSL ultimately became the foundation of our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/8.10/search-search.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e_search\u003c/span\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e API endpoint.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThrough the years and the diversification of needs, it became evident that users wanted more than what Query DSL provided. We began to adopt and weave in additional DSLs under our Query DSL for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/painless/current/painless-contexts.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003escripting\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e or for \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/eql-apis.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eevents\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e in security investigations and much more. However, as versatile as these additions were, they didn't entirely cover some of the requirements of our users.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUsers wanted a query language that could:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSimplify threat and security investigations while observing and resolving production issues through a single query that delivers a comprehensive and iterative approach\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eStreamline data investigations by searching, enriching, aggregating, and visualizing plus more, all from a single interface\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUse advanced search capabilities like lookups with concurrent processing improving speed and efficiency to query vast amounts of data irrespective of source and structure\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"From pipe dreams to reality — Introducing ES|QL","_metadata":{"uid":"cs739139b681a5e1c8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWe listened and are proud to introduce \u003ca href=\"https://www.elastic.co/blog/getting-started-elasticsearch-query-language\"\u003eElasticsearch Query Language (ES|QL)\u003c/a\u003e, our new innovative piped query language — a single unified method and language to interact with data in Elasticsearch while removing the costly need to transfer it to external systems for specialized processing. Unlike other languages Elastic has adopted over the years like Query DSL, ES|QL is designed and purpose built from the ground up to greatly simplify data investigations and be accessible for beginners while being powerful for experts.\u0026nbsp;\u003c/p\u003e\u003cp\u003e\u003cem\u003eES|QL example command:\u003c/em\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs04670210ba5e42cd"}}},{"code":{"code":"from logstash-*\n| stats avg_bytes = avg(bytes) by geo.src\n| eval avg_bytes_kb = round(avg_bytes/1024, 2)\n| enrich geo-data on geo.src with country, continent\n| keep avg_bytes_kb, geo.src, country, continent \n| limit 4","_metadata":{"uid":"cs834eb08b45840476"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1f7334849b863511"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eES|QL example output:\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003ctable\u003e\u003ctbody\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eavg_bytes_kb\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003egeo.src\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003ecountry\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003econtinent\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e8.84\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eBD\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eBangladesh\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eAsia\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e6.92\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eBR\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eBrazil\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eAmericas\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e2.75\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCI\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCôte d'Ivoire\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eAfrica\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003ctr\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e4.55\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eCL\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eChile\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003ctd\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eAmericas\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e \u003c/span\u003e\u003c/td\u003e\u003c/tr\u003e\u003c/tbody\u003e\u003c/table\u003e\u003cp\u003e\u003c/p\u003e"},{"title_l10n":"Streamlined simplicity: A UI tailored for enhanced and iterative workflows ","_metadata":{"uid":"cs632005fd40cdbacb"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eConnecting the dots of an unfolding attack or navigating through observability data requires you to filter, search, transform, and aggregate across an extraordinary amount of data. ES|QL delivers this functionality from a single query.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs31e57e44273c117b"}}},{"image":{"image":{"uid":"bltfa80b86cb375b9da","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-02T16:36:06.520Z","created_by":"bltb6c155cd84fc0c1a","file_size":"203328","filename":"elastic-esql-announcement.png","parent_uid":null,"tags":[],"title":"elastic-esql-announcement.png","updated_at":"2023-11-02T16:36:06.520Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:02.372Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfa80b86cb375b9da/6543cff6a036750407c83950/elastic-esql-announcement.png"},"_metadata":{"uid":"csfd05a4b557ba811a"},"caption_l10n":"","alt_text_l10n":"Streamlined simplicity","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1e125b8cf8146c20"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eContext switching or trying to find what you are looking for from many screens can slow you down and be frustrating. From a unified display, ES|QL provides autocomplete syntax, integrates product documentation, and visualizes search outcomes, ensuring an uninterrupted and efficient workflow for data inquiries. Whether for security, observability, or search, ES|QL enhances efficiency, speed, and the depth of data exploration.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"ES|QL concurrency — Two threads are better than one","_metadata":{"uid":"cs38fa14a1aff22148"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePowered by a robust query engine, ES|QL offers advanced search capabilities with concurrent processing, enabling users to seamlessly query across diverse data sources and structure.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThere is no translation or transpliations to Query DSL; instead, each query in ES|QL is initially broken down, interpreted for its meaning, validated for accuracy, and then enhanced for best performance. Then a process is laid out for executing the query across various nodes within the cluster. The target nodes handle the query, making on-the-fly adjustments to the execution plan using the framework provided by ES|QL. The result is lightning fast queries that you get out of the box. As an example, view \u003c/span\u003e\u003ca href=\"https://elasticsearch-benchmarks.elastic.co/#tracks/esql/nightly/default/30d\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ethe nightly benchmarks\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for comparison.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4447eafd0e1b6c8c"}}},{"banner":{"reference":[{"uid":"blt6d98a581fc6972d6","_content_type_uid":"banner"}],"_metadata":{"uid":"csbff4b0be769be0d1"}}},{"title_text":{"title_text":[{"title_l10n":"Platform innovation drives Elastic solutions benefits","_metadata":{"uid":"csa9673bb974a22aea"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s solutions — \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearch\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability\"\u003e\u003cspan style='font-size: 12pt;'\u003eObservability\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='font-size: 12pt;'\u003eSecurity\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — all benefit from features and innovations that are delivered within Elasticsearch and Kibana®. ES|QL fundamentally changes the experience of using these solutions and provides a simple but powerful data investigation workflow.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"ES|QL enhances Elastic Security","_metadata":{"uid":"cs0cc21de07179557b"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL fundamentally changes how analysts pursue threats and strengthens detection. Built in answer to rich community input, it unleashes the power of piped queries at the speed of Elasticsearch, enhancing the SIEM, endpoint security, and cloud security capabilities of Elastic Security.\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSearch quickly and iteratively:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Following the breadcrumbs of an emerging threat requires quick action and a language that delivers an iterative workflow.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEnrich results with context:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e ES|QL enables analysts to correlate suspicious IP addresses with known threat intelligence databases, providing immediate clarity on potential threats.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eTransform data:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e ES|QL empowers users to manipulate their data by defining new fields or parsing non-normalized data, ensuring data clarity and relevance.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAggregate data:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Results can be consolidated and aggregated, paving the way for deeper analysis and insight extraction.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic is the only search platform to pair the efficiency of a schema-on-write architecture with the iterative search experience of a schema-on-read piped query language. With incredibly fast search — and query output in full sight — analysts can draw closer to their target with each successive pipe.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL also enhances Elastic Security’s powerful detection engine. To reduce alarm fatigue, improve alert relevance, and provide another avenue for behavioral detection, organizations can incorporate aggregated values within detection rules. With inline evaluation, practitioners can iteratively develop and hone ES|QL-based rules. Queries are formatted in plaintext, simplifying collaboration and supporting detection-as-code.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"ES|QL impacts Elastic Observability","_metadata":{"uid":"csb5a8ab761d6d8ece"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSREs using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability-labs/blog/opentelemetry-kubernetes-esql\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Observability\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e can leverage ES|QL to analyze logs, metrics, traces, and profiling data, enabling them to pinpoint performance bottlenecks and system issues with a single query. SREs gain the following advantages when managing high dimensionality and high cardinality data with ES|QL in Elastic Observability:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRemove signal noise:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e With ES|QL alerting, enhance detection precision by focusing on significant trends rather than individual incidents, minimizing false alarms, and delivering actionable notifications. SREs can manage these alerts through the Elastic API and integrate them into DevOps processes.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eEnhanced analysis with insights:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e ES|QL can process diverse observability data, including application, infrastructure, business data, and more, regardless of the source and structure. ES|QL can easily enrich the data with additional fields and context, allowing the creation of visualizations for dashboards or issue analysis with a single query.\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eReduced mean time to resolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e ES|QL, when combined with Elastic Observability's AIOps and AI Assistant, enhances detection accuracy by identifying trends, isolating incidents, and reducing false positives. This improvement in context facilitates troubleshooting and the quick pinpointing and resolution of issues.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eES|QL in Elastic Observability not only enhances an SRE's ability to manage the customer experience, an organization's revenue, and SLOs more effectively but also facilitates collaboration with developers and DevOps by providing contextualized aggregated data.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"ES|QL advances Elastic Search","_metadata":{"uid":"csb76831ef608b17a8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith ES|QL, you can retrieve, aggregate, calculate, and transform data in a single query. It boasts key features, such as the ability to define fields at the time of query, perform data enrichment lookups, and process queries concurrently. Understand and explore your data with ES|QL in various ways. From utilizing clients for direct API/code integration to visualizing results directly from one screen, ES|QL streamlines your data investigations, ensuring you get the most out of your data sets with ease and simplicity.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eES|QL’s design focus is evident in its capability to reduce code complexity, ultimately leading to cost and time savings. By facilitating the reuse of query results in subsequent searches, ES|QL minimizes computational overhead, eliminating the need for convoluted scripts and redundant queries. ES|QL is not just an API but a simple and powerful way to transform your approach to search.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Embark on your ES|QL journey","_metadata":{"uid":"cs0f05f64d80a306a6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe future of data exploration and manipulation is here. Elastic invites security analysts, SREs, and developers to experience this transformative language firsthand and unlock new horizons in their data tasks. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/piped-query-language\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more about the possibilities with ES|QL\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, or \u003c/span\u003e\u003ca href=\"http://ela.st/startnow\"\u003e\u003cspan style='font-size: 12pt;'\u003estart your free trial\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e now in technical preview.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs14331b010fbe896a"}}}],"publish_date":"2023-11-07","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Announcing Elastic’s piped query language, ES|QL","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltaa08115c1a4c99d9","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2023-11-02T16:21:32.477Z","created_by":"bltb6c155cd84fc0c1a","file_size":"72479","filename":"ES_QL_blog-720x420-06.png","parent_uid":null,"tags":[],"title":"ES_QL_blog-720x420-06.png","updated_at":"2023-11-02T16:21:32.477Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2023-11-07T13:45:02.384Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaa08115c1a4c99d9/6543cc8c36795e040703e45e/ES_QL_blog-720x420-06.png"},"title":"From pipe dreams to reality: Announcing Elastic’s piped query language, ES|QL","title_l10n":"From pipe dreams to reality: Announcing Elastic’s piped query language, ES|QL","updated_at":"2025-02-25T21:27:46.614Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/esql-elasticsearch-piped-query-language","publish_details":{"time":"2025-02-25T21:31:20.477Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb1ec879086c2333a","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"This blog provides tips and resources for troubleshooting Elasticsearch memory allocation. See the top allocation management theory links our Support team sends to users and where they direct users to resolve their resource allocation issues.","author":["bltddff0459e563bc78"],"category":["blte5cc8450a098ce5e"],"created_at":"2024-09-30T23:55:13.531Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csddb37782b8c035d1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith Elastic Cloud delivering solutions like Observability, Security, and Search, we've broadened the users who use Elastic Cloud beyond full ops teams to include data engineers, security teams, and consultants. As an Elastic support representative, I’ve enjoyed engaging with a diverse range of users and use cases.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWith a wider audience, I’m seeing more questions about managing resource allocation, in particular troubleshooting allocation health and avoiding circuit breakers. I get it! When I started with Elasticsearch, I had the same questions. It was my first intro to managing Java heap and time series database shards and scaling my own infrastructure.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen I joined Elastic, I loved that on top of documentation, we had blogs and tutorials so I could onboard quickly. But then I struggled my first month to correlate my theoretical knowledge to the errors users would send through my ticket queue. Eventually I figured out, like other support reps, that a lot of the reported errors were just symptoms of allocation issues and the same seven-ish links would bring users up to speed to successfully manage their resource allocation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSpeaking as a support rep, I’m going to go over the top allocation management theory links we send users, the top symptoms we see, and where we direct users to update their configurations to resolve their resource allocation issues.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Theory","_metadata":{"uid":"cs96737da32e053960"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a Java application, Elasticsearch requires some logical memory (heap) allocation from the system’s physical memory. This should be up to half of the physical RAM, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/heap-sizing.html#compressed_oops\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecapping at 32GB\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Setting higher heap usage is usually \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-memory-pressure.html#ec-memory-pressure-causes\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ein response\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to expensive queries and larger data storage. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/circuit-breaker.html#parent-circuit-breaker\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eParent circuit breaker\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e defaults to 95%, but we recommend scaling resources once consistently \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/found-understanding-memory-pressure-indicator#conclusion\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehitting 85%\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eI highly recommend these overview articles for more info:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/blog/a-heap-of-trouble\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eA heap of trouble\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/guide/current/heap-sizing.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHeap: Sizing and swapping\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Configuration","_metadata":{"uid":"cs0a3c0dfb50f3d590"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOut of the box, Elasticsearch’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/advanced-configuration.html#setting-jvm-heap-size\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003edefault settings\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e automatically size your JVM heap based on node role and total memory. However, as needed, you can configure it directly in the following three ways:\u003c/span\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e1. Directly in your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/advanced-configuration.html#setting-jvm-heap-size\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003econfig \u0026gt; jvm.options\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e file of your local Elasticsearch files:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7d32b0304fa4ceee"}}},{"code":{"code":"## JVM configuration\n\n################################################################\n## IMPORTANT: JVM heap size\n################################################################\n\n…\n\n# Xms represents the initial size of total heap space\n# Xmx represents the maximum size of total heap space\n\n-Xms4g\n-Xmx4g","_metadata":{"uid":"cs5e46cac24287aae6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs179308ec437fc051"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e2. As an Elasticsearch environment variable \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.12/docker.html#docker-cli-run-prod-mode\"\u003e\u003cspan style='font-size: 12pt;'\u003ein your docker-compose\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csaa56425613c18df4"}}},{"code":{"code":"version: '2.2'\nservices:\n es01:\n\timage: docker.elastic.co/elasticsearch/elasticsearch:7.12.0\n\tenvironment:\n \t- node.name=es01\n \t- cluster.name=es\n \t- bootstrap.memory_lock=true\n \t- \"ES_JAVA_OPTS=-Xms4g -Xmx4g\"\n \t- discovery.type=single-node\n\tulimits:\n \tmemlock:\n \tsoft: -1\n \thard: -1\n\tports:\n \t- 9200:9200","_metadata":{"uid":"cs5b51e140ab5a3dc3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs04d10efb1f56f8ef"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e3. Via our Elastic Cloud Hosted \u0026gt; Deployment \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-customize-deployment-components.html#ec-cluster-size\"\u003e\u003cspan style='font-size: 12pt;'\u003eEdit view\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eNote:\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e The drop down assigns physical memory and roughly half will be allotted to the heap.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs78e99b5fdadbfb62"}}},{"image":{"image":{"uid":"blt21fba1109675bda8","_version":1,"title":"blog-elasticsearch-hot-data-content-tier.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-04T16:39:06.647Z","updated_at":"2024-11-04T16:39:06.647Z","content_type":"image/png","file_size":"53163","filename":"blog-elasticsearch-hot-data-content-tier.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.566Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt21fba1109675bda8/6728f8aa9b78e715d553807f/blog-elasticsearch-hot-data-content-tier.png"},"_metadata":{"uid":"cs6e45ad401ec63e10"},"caption_l10n":"","alt_text_l10n":"elasticsearch hot data and content tier","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Troubleshooting","_metadata":{"uid":"cs6c6ce5ece703a5af"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you’re currently experiencing performance issues with your cluster, it will most likely come down to the usual suspects:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eConfiguration issues:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Undersized master nodes, no \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/getting-started-index-lifecycle-management.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eILM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e policy\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eVolume induced:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e High request pace/load, overlapping expensive queries/writes\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll following cURL/API requests can be made in the Elastic Cloud Hosted \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-api-console.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch API Console\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, as a cURL to the Elasticsearch API, or under Kibana \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/console-kibana.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDev Tools\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e"},{"title_l10n":"Allocation health","_metadata":{"uid":"csf5a226700d58d1c6"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eData indices \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html\"\u003e\u003cspan style='font-size: 12pt;'\u003estore into sub-shards\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, which use heap for maintenance and during search/write requests. Shard size should \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.16/size-your-shards.html#shard-size-recommendation\"\u003e\u003cspan style='font-size: 12pt;'\u003ebe no larger than 50GB\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;Taking the above Elastic Cloud Hosted example with 8GB of physical memory across two zones (which will allocate two nodes in total), let’s join this to an example:\u0026nbsp; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-allocation.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cat/allocation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csea592384116ee716"}}},{"code":{"code":"GET /_cat/allocation?v=true\u0026h=shards,node\nshards node\n 41 instance-0000000001\n 41 instance-0000000000","_metadata":{"uid":"cs7a4fc3e94009b7e8"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs13128b83dbcedffd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAnd to: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-health.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cluster/health\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs10c4578db37a0e7a"}}},{"code":{"code":"GET /_cluster/health?filter_path=status,*_shards\n\n{\n \"status\": \"green\",\n \"unassigned_shards\": 0,\n \"initializing_shards\": 0,\n \"active_primary_shards\": 41,\n \"relocating_shards\": 0,\n \"active_shards\": 82,\n \"delayed_unassigned_shards\": 0\n}","_metadata":{"uid":"cs722f975aa1ac1b16"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs47238668db1c604d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf any shards report \u0026gt;0 outside \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eactive_shards\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e or \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eactive_primary_shards\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, you’ve pinpointed a cause for performance issues.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMost commonly if this reports an issue, it will be \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eunassigned_shards\u0026gt;0\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. If these shards are primary, your cluster will report as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estatus:red\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, and if only replicas, it will report as \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estatus:yellow\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e. (This is why \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html#dynamic-index-settings\"\u003e\u003cspan style='font-size: 12pt;'\u003esetting replicas on indices\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is important — if the cluster encounters an issue, it can recover rather than experience data loss.)Let’s pretend we have a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estatus:yellow\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e with a single unassigned shard. To investigate, we’d take a look at which index shard is having trouble via \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-shards.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cat/shards\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csdf67115e87eda65f"}}},{"code":{"code":"GET _cat/shards?v=true\u0026s=state\nindex \tshard prirep state \tdocs store ip \tnode\nlogs \t0 \tp \tSTARTED \t2 10.1kb 10.42.255.40 instance-0000000001\nlogs \t0 \tr \tUNASSIGNED\nkibana_sample_data_logs \t0 \tp \tSTARTED \t14074 10.6mb 10.42.255.40 instance-0000000001\n.kibana_1 \t0 \tp \tSTARTED \t2261 3.8mb 10.42.255.40 instance-0000000001","_metadata":{"uid":"cs84e42325ae42db40"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csca5d90f4a5828a1f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo this will be for our non-system index logs, which have an unassigned replica shard. Let’s see what’s giving it grief by running \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/7.12/cluster-allocation-explain.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cluster/allocation/explain\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. (Pro tip: When you escalate to support, this is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eexactly\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e what we do.)\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e\u003cstrong\u003eGET _cluster/allocation/explain?pretty\u0026amp;filter_path=index,node_allocation_decisions.node_name,node_allocation_decisions.deciders.*\u003c/strong\u003e\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs65ac3aef7b729bff"}}},{"code":{"code":"{ \"index\": \"logs\",\n \"node_allocation_decisions\": [{\n \"node_name\": \"instance-0000000005\",\n \"deciders\": [{\n \"decider\": \"data_tier\",\n \"decision\": \"NO\",\n \"explanation\": \"node does not match any index setting [index.routing.allocation.include._tier] tier filters [data_hot]\"\n}]}]}","_metadata":{"uid":"cscd314239f3b38b03"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csa11d35edc31eb51d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis error message points to \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003edata_hot\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, which is part of an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-lifecycle-management.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eindex lifecycle management\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e (ILM) policy and indicates that our ILM policy is incongruent with our current index settings. In this case, the cause of this error is from setting up a hot-warm ILM policy without having designated hot-warm nodes. (I needed to guarantee something would fail, so this is me forcing error examples for y’all. For more information, see \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=5z3n2VgusLE\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003ethis example troubleshooting video\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for resolution walkthrough.)\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you run this command when you don’t have any unassigned shards, you’ll get a 400 error saying \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eunable to find any unassigned shards to explain\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e because nothing’s wrong to report on\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e.\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eIf you get a non-logic cause (e.g., a temporary network error like \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003enode left cluster during allocation\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e), then you can use Elastic’s handy-dandy \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-reroute.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cluster/reroute\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4cd3226d26e7e91e"}}},{"code":{"code":"POST /_cluster/reroute","_metadata":{"uid":"cs5b9f4c3fa34d1459"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs99c4e50e27efe068"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis request without customizations starts an asynchronous background process that attempts to allocate all current \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003estate:UNASSIGNED\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e shards. (Don’t be like me and not wait for it to finish before you contact dev, because I thought it would be instantaneous and coincidentally escalate just in time for them to say nothing’s wrong because nothing was anymore.) For more information, see this \u003c/span\u003e\u003ca href=\"https://www.youtube.com/watch?v=v2mbeSd1vTQ\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003etroubleshooting video for monitoring Allocation Health\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Circuit breakers","_metadata":{"uid":"csac7cc6875626f46c"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMaxing out your heap allocation can cause requests to your cluster to time out or error and frequently will cause your cluster to experience circuit breaker exceptions. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/circuit-breaker-errors.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eCircuit breaking errors\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e causes elasticsearch.log events like:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa6123b2fe5541ffc"}}},{"code":{"code":"Caused by: org.elasticsearch.common.breaker.CircuitBreakingException: [parent] Data too large, data for [\u003ctransport_request\u003e] would be [num/numGB], which is larger than the limit of [num/numGB], usages [request=0/0b, fielddata=num/numKB, in_flight_requests=num/numGB, accounting=num/numGB]","_metadata":{"uid":"csf328c98fcbe15688"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9b748bf9e85a9c6a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTo investigate, take a look at your \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003eheap.percent\u003c/em\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, either by looking at \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-nodes.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_cat/nodes\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc0ddb373e182df0d"}}},{"code":{"code":"GET /_cat/nodes?v=true\u0026h=name,node*,heap*\n# heap = JVM (logical memory reserved for heap)\n# ram = physical memory\n\nname node.role heap.current heap.percent heap.max\ntiebreaker-0000000002 mv 119.8mb 23 508mb\ninstance-0000000001 himrst 1.8gb 48 3.9gb\ninstance-0000000000 himrst 2.8gb 73 3.9gb","_metadata":{"uid":"cs9759079a5c9a1d05"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs43d6daa2b506e8ec"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOr if you’ve previously enabled it, navigate to Kibana \u0026gt; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/xpack-monitoring.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eStack Monitoring\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse328c6f3be61bb8a"}}},{"image":{"image":{"uid":"bltaf9ad3a2547c12d3","_version":1,"title":"blog-elasticsearch-nodes.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-05T14:47:17.903Z","updated_at":"2024-11-05T14:47:17.903Z","content_type":"image/png","file_size":"235581","filename":"blog-elasticsearch-nodes.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.577Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltaf9ad3a2547c12d3/672a2ff510ff855dc625ebea/blog-elasticsearch-nodes.png"},"_metadata":{"uid":"cs14509603c7e1b0b9"},"caption_l10n":"","alt_text_l10n":"elasticsearch nodes","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4e4577eca5d5bc3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eIf you've confirmed you're hitting your memory circuit breakers, you'll want to consider increasing heap temporarily to give yourself breathing room to investigate. When investigating root cause, look through your \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/enable-audit-logging.html\" target=\"_self\"\u003eaudit logging\u003c/a\u003e, \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules-slowlog.html\" target=\"_self\"\u003eslow logging\u003c/a\u003e, \u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/logging.html\" target=\"_self\"\u003eclusterlogs,\u003c/a\u003e or elasticsearch.log for the preceding consecutive events. You'll be looking for:\u003c/p\u003e\u003cul\u003e\u003cli\u003eExpensive queries, especially:\u003cul\u003e\u003cli\u003eHigh bucket aggregations\u003cul\u003e\u003cli\u003eI felt so silly when I found out that searches temporarily allocate a certain portion of your heap \u003cem\u003ebefore\u003c/em\u003e they run the query based on the search \u003cem\u003esize\u003c/em\u003e or bucket dimensions, so setting 10,000,000 really was giving my ops team heartburn.\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003enon-optimized mappings\u003cul\u003e\u003cli\u003eThe second reason to feel silly was when I thought doing hierarchical reporting would search better than flattened out data (it does not).\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003c/ul\u003e\u003c/li\u003e\u003cli\u003eRequest volume/pace: Usually batch or async queries\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Time to scale","_metadata":{"uid":"cs72cf02f7ec1a4126"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf this isn’t your first time hitting circuit breakers or you suspect it’ll be an ongoing issue (e.g., consistently hitting 85%, so it’s time to look at scaling resources), you’ll want to take a closer look at \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/found-understanding-memory-pressure-indicator\"\u003e\u003cspan style='font-size: 12pt;'\u003ethe JVM Memory Pressure\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as your long-term heap indicator. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-memory-pressure.html\"\u003e\u003cspan style='font-size: 12pt;'\u003eYou can check this\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e in Elastic Cloud Hosted \u0026gt; Deployment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7018b9cbeb694290"}}},{"image":{"image":{"uid":"bltec76d550fd75d35e","_version":1,"title":"blog-elasticsearch-instances.png","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-05T14:47:40.198Z","updated_at":"2024-11-05T14:47:40.198Z","content_type":"image/png","file_size":"216097","filename":"blog-elasticsearch-instances.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.556Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltec76d550fd75d35e/672a300cec690346cf80e426/blog-elasticsearch-instances.png"},"_metadata":{"uid":"csb75de8bf4d1709e5"},"caption_l10n":"","alt_text_l10n":"elasticsearch instances","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf716fd6b8c98aa10"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOr you can calculate it from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/cluster-nodes-stats.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e_nodes/stats\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc93cc273ccc95595"}}},{"code":{"code":"GET /_nodes/stats?filter_path=nodes.*.jvm.mem.pools.old\n\n{\"nodes\": { \"node_id\": { \"jvm\": { \"mem\": { \"pools\": { \"old\": {\n \"max_in_bytes\": 532676608,\n \"peak_max_in_bytes\": 532676608,\n \"peak_used_in_bytes\": 104465408,\n \"used_in_bytes\": 104465408\n}}}}}}}","_metadata":{"uid":"csb712d2db038a6552"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs545ca4bd1034b922"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhere:\u003c/p\u003e"}],"_metadata":{"uid":"cs642a356c6aa18794"}}},{"code":{"code":"JVM Memory Pressure = used_in_bytes / max_in_bytes","_metadata":{"uid":"csd2dd7d82cab97b76"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7a8edb0eb547da34"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA potential symptom of this is high frequency and long duration from garbage collector (gc) events in your elasticsearch.log:\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3e7a869654542ce1"}}},{"code":{"code":"[timestamp_short_interval_from_last][INFO ][o.e.m.j.JvmGcMonitorService] [node_id] [gc][number] overhead, spent [21s] collecting in the last [40s]","_metadata":{"uid":"cs645946facbfa844c"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8c029cedd156f990"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you confirm this scenario, you’ll need to take a look either at scaling your cluster or at reducing the demands hitting it. You’ll want to investigate/consider:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIncreasing heap resources (heap/node; number of nodes)\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDecreasing shards (delete unnecessary/old data; \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/getting-started-index-lifecycle-management.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003euse ILM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to put data into \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/hot-warm-architecture\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ewarm/cold storage\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e so you can \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/ilm-shrink.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eshrink it\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e; turn off replicas for data you don’t care if you lose)\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"We're here to help","_metadata":{"uid":"cs2c3078cac9273079"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWooh! From what I see in Elastic support, that’s the rundown of most common user tickets: unassigned shards, unbalanced shard-heap, circuit breakers, high garbage collection, and allocation errors. All are symptoms of the core resource allocation management conversation. Hopefully, you now know the theory and resolution steps, too.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt this point, though, if you’re stuck resolving an issue, feel free to reach out. We’re here and happy to help! Contact us:\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"http://discuss.elastic.co/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eElastic Discuss\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://join.slack.com/t/elasticstack/shared_invite/zt-o4sdlhb7-OGXEcy4iry_CsxVyJLGYag\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003eElastic community Slack\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/consulting\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic consulting\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/training\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic training\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic support\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCheers to our ability to self-manage the Elastic Stack’s resource allocation as non-Ops (love Ops, too)!\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2b374506db2111d2"}}},{"callout":{"title_l10n":"Additional resources:","_metadata":{"uid":"cs8dad7e458d5e92c8"},"paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDocs: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-monitoring-setup.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow to set up monitoring\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-set-up-elastic-cloud-advice-from-elastic-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHow to set up Elastic Cloud: Advice from Elastic support\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csf3986fc457801d5d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003eOriginally published April 27, 2021; updated November 5, 2024.\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb8fdc17e83ea105f"}}}],"publish_date":"2024-11-05T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"bltc65e91f68e28d7dc","_version":1,"title":"Office-building (4).jpg","created_by":"bltd9765be97bbed20c","updated_by":"bltd9765be97bbed20c","created_at":"2024-11-04T16:58:32.748Z","updated_at":"2024-11-04T16:58:32.748Z","content_type":"image/jpeg","file_size":"127924","filename":"Office-building_(4).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-11-05T15:06:14.539Z","user":"bltd9765be97bbed20c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc65e91f68e28d7dc/6728fd38e404ee40f9f6c79a/Office-building_(4).jpg"},"title":"Managing and troubleshooting Elasticsearch memory","title_l10n":"Managing and troubleshooting Elasticsearch memory","updated_at":"2025-02-25T21:20:26.966Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/managing-and-troubleshooting-elasticsearch-memory","publish_details":{"time":"2025-02-25T21:21:13.969Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt164cc603cf9b0288","_version":34,"locale":"en-us","ACL":{},"abstract_l10n":"In part one of this two-part series, we’ll dive into configuring the components of a standard Elastic Stack consisting of Elasticsearch, Logstash, Kibana, and Beats (ELK-B), on which we can immediately begin developing.","author":["blt096405e08d51c7ce"],"category":["bltb79594af7c5b4199"],"created_at":"2023-05-17T16:36:25.211Z","created_by":"blt92c74e5c4edca909","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csae476b8a58cdcb3a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs the Elastic Stack has grown over the years and the feature sets have increased, so has the complexity of getting started or attempting a proof-of-concept (POC) locally. And while \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is still the fastest and easiest way to get started with Elastic, the need for local development and testing is still widely abundant. As developers, we are drawn to quick setups and rapid development with low-effort results. Nothing screams fast setup and POC quite like Docker — which is what we’ll be focusing on to get started with an entire Elastic Stack build-out for your local enjoyment.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn part one of this two-part series, we’ll dive into configuring the components of a standard Elastic Stack consisting of Elasticsearch, Logstash, Kibana, and Beats (ELK-B), on which we can immediately begin developing.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn part two, we’ll enhance our base configuration and add many of the different features that power our evolving stack, such as APM, Agent, Fleet, Integrations, and Enterprise Search. We will also look at instrumenting these in our new local environment for development and POC purposes.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor those who have been through some of this before, you're welcome to \u003c/span\u003e\u003ca href=\"https://github.com/elkninja/elastic-stack-docker-part-one\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTL;DR and head over to the repo to grab the files\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAs a prerequisite, \u003c/span\u003e\u003ca href=\"https://docs.docker.com/get-docker/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDocker Desktop or Docker Engine\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e with \u003c/span\u003e\u003ca href=\"https://docs.docker.com/get-started/08_using_compose/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDocker-Compose\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e will need to be installed and configured. For this tutorial, we will be using Docker Desktop.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOur focus for these Docker containers will primarily be Elasticsearch and Kibana. However, we’ll be utilizing Metricbeat to give us some cluster insight as well as Filebeat and Logstash for some ingestion basics.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csac231957c6be793b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs95ee301df3686e70"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eFile structure\u003c/h2\u003e\u003cp\u003eFirst, let's start by defining the outline of our file structure.\u003c/p\u003e\u003cp\u003e├── .env\u003c/p\u003e\u003cp\u003e├── docker-compose.yml\u003c/p\u003e\u003cp\u003e├── filebeat.yml\u003c/p\u003e\u003cp\u003e├── logstash.conf\u003c/p\u003e\u003cp\u003e└── metricbeat.yml\u003c/p\u003e\u003cp\u003eWe’ll keep it simple initially. Elasticsearch and Kibana will be able to start from the docker-compose file, while Filebeat, Metricbeat, and Logstash will all need additional configuration from yml files.\u0026nbsp;\u003c/p\u003e\u003ch2\u003eEnvironment file\u003c/h2\u003e\u003cp\u003eNext, we’ll define variables to pass to the docker-compose via the .env file. These parameters will help us establish ports, memory limits, component versions, etc.\u003c/p\u003e\u003ch3\u003e.env\u003c/h3\u003e"}],"_metadata":{"uid":"cs8ee3cf303335b3cc"}}},{"code":{"code":"# Project namespace (defaults to the current folder name if not set)\n#COMPOSE_PROJECT_NAME=myproject\n\n\n# Password for the 'elastic' user (at least 6 characters)\nELASTIC_PASSWORD=changeme\n\n\n# Password for the 'kibana_system' user (at least 6 characters)\nKIBANA_PASSWORD=changeme\n\n\n# Version of Elastic products\nSTACK_VERSION=8.7.1\n\n\n# Set the cluster name\nCLUSTER_NAME=docker-cluster\n\n\n# Set to 'basic' or 'trial' to automatically start the 30-day trial\nLICENSE=basic\n#LICENSE=trial\n\n\n# Port to expose Elasticsearch HTTP API to the host\nES_PORT=9200\n\n\n# Port to expose Kibana to the host\nKIBANA_PORT=5601\n\n\n# Increase or decrease based on the available host memory (in bytes)\nES_MEM_LIMIT=1073741824\nKB_MEM_LIMIT=1073741824\nLS_MEM_LIMIT=1073741824\n\n\n# SAMPLE Predefined Key only to be used in POC environments\nENCRYPTION_KEY=c34d38b3a14956121ff2170e5030b471551370178f43e5626eec58b04a30fae2\n","_metadata":{"uid":"csf32f35554b3f4ad4"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs196221e52072e89d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNote that the placeholder word “changeme” for all the passwords and the sample key are used for demonstration purposes only. These should be changed even for your local POC needs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs you can see here, we specify ports 9200 and 5601 for Elasticsearch and Kibana respectively. This is also where you can change from “basic” to “trial” license type in order to test additional features.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe make use of the `STACK_VERSION' environment variable here in order to pass it to each of the services (containers) in our \u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003edocker-compose.yml\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file. When using Docker, opting to hard-code the version number as opposed to using something like the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e:latest\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tag is a good way to maintain positive control over the environment. For components of the Elastic Stack, the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e:latest\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e tag is not supported and we require version numbers to pull the images.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eSetup and Elasticsearch node\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOne of the first bits of trouble that's often run into when getting started is security configuration. As of 8.0, security is enabled by default. Therefore, we'll need to make sure we have the certificate CA setup correctly by utilizing a \"setup\" node to establish the certificates. Having \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/secure-cluster.html\"\u003e\u003cspan style='font-size: 12pt;'\u003esecurity enabled is a recommended practice\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and should not be disabled, even in POC environments.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003edocker-compose.yml (‘setup’ container)\u003c/h3\u003e"}],"_metadata":{"uid":"cs6dfcfa17ebad19d9"}}},{"code":{"code":"version: \"3.8\"\n\n\nvolumes:\n certs:\n driver: local\n esdata01:\n driver: local\n kibanadata:\n driver: local\n metricbeatdata01:\n driver: local\n filebeatdata01:\n driver: local\n logstashdata01:\n driver: local\n\n\nnetworks:\n default:\n name: elastic\n external: false\n\n\nservices:\n setup:\n image: docker.elastic.co/elasticsearch/elasticsearch:${STACK_VERSION}\n volumes:\n - certs:/usr/share/elasticsearch/config/certs\n user: \"0\"\n command: \u003e\n bash -c '\n if [ x${ELASTIC_PASSWORD} == x ]; then\n echo \"Set the ELASTIC_PASSWORD environment variable in the .env file\";\n exit 1;\n elif [ x${KIBANA_PASSWORD} == x ]; then\n echo \"Set the KIBANA_PASSWORD environment variable in the .env file\";\n exit 1;\n fi;\n if [ ! -f config/certs/ca.zip ]; then\n echo \"Creating CA\";\n bin/elasticsearch-certutil ca --silent --pem -out config/certs/ca.zip;\n unzip config/certs/ca.zip -d config/certs;\n fi;\n if [ ! -f config/certs/certs.zip ]; then\n echo \"Creating certs\";\n echo -ne \\\n \"instances:\\n\"\\\n \" - name: es01\\n\"\\\n \" dns:\\n\"\\\n \" - es01\\n\"\\\n \" - localhost\\n\"\\\n \" ip:\\n\"\\\n \" - 127.0.0.1\\n\"\\\n \" - name: kibana\\n\"\\\n \" dns:\\n\"\\\n \" - kibana\\n\"\\\n \" - localhost\\n\"\\\n \" ip:\\n\"\\\n \" - 127.0.0.1\\n\"\\\n \u003e config/certs/instances.yml;\n bin/elasticsearch-certutil cert --silent --pem -out config/certs/certs.zip --in config/certs/instances.yml --ca-cert config/certs/ca/ca.crt --ca-key config/certs/ca/ca.key;\n unzip config/certs/certs.zip -d config/certs;\n fi;\n echo \"Setting file permissions\"\n chown -R root:root config/certs;\n find . -type d -exec chmod 750 \\{\\} \\;;\n find . -type f -exec chmod 640 \\{\\} \\;;\n echo \"Waiting for Elasticsearch availability\";\n until curl -s --cacert config/certs/ca/ca.crt https://es01:9200 | grep -q \"missing authentication credentials\"; do sleep 30; done;\n echo \"Setting kibana_system password\";\n until curl -s -X POST --cacert config/certs/ca/ca.crt -u \"elastic:${ELASTIC_PASSWORD}\" -H \"Content-Type: application/json\" https://es01:9200/_security/user/kibana_system/_password -d \"{\\\"password\\\":\\\"${KIBANA_PASSWORD}\\\"}\" | grep -q \"^{}\"; do sleep 10; done;\n echo \"All done!\";\n '\n healthcheck:\n test: [\"CMD-SHELL\", \"[ -f config/certs/es01/es01.crt ]\"]\n interval: 1s\n timeout: 5s\n retries: 120","_metadata":{"uid":"csb4db8250e54458ed"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs4608293bd0fad237"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt the top of the \u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003edocker-compose.yml \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ewe set the compose version, followed by the volumes and default networking configuration that will be used throughout our different containers.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe also see that we're standing up a container labeled “setup” with some bash magic to specify our cluster nodes. This allows us to call the elasticsearch-certutil, passing the server names in yml format in order to create the CA cert and node certs. If you wanted to have more than one Elasticsearch node in your stack, this is where you would add the server name to allow the cert creation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNote: In a future post, we’ll adopt the recommended method of using a keystore to keep secrets, but for now, this will allow us to get the cluster up and running.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis setup container will start up first, wait for the ES01 container to come online, and then use our environment variables to set up the passwords we want in our cluster. We’re also saving all certificates to the “certs” volume so that all other containers can have access to them.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSince the Setup container is dependent on the ES01 container, let's take a quick look at the next configuration so we can start them both up:\u003c/span\u003e\u003c/p\u003e\u003ch3\u003edocker-compose.yml (‘es01’ container)\u003c/h3\u003e"}],"_metadata":{"uid":"cs2decb3207302bae6"}}},{"code":{"code":" es01:\n depends_on:\n setup:\n condition: service_healthy\n image: docker.elastic.co/elasticsearch/elasticsearch:${STACK_VERSION}\n labels:\n co.elastic.logs/module: elasticsearch\n volumes:\n - certs:/usr/share/elasticsearch/config/certs\n - esdata01:/usr/share/elasticsearch/data\n ports:\n - ${ES_PORT}:9200\n environment:\n - node.name=es01\n - cluster.name=${CLUSTER_NAME}\n - discovery.type=single-node\n - ELASTIC_PASSWORD=${ELASTIC_PASSWORD}\n - bootstrap.memory_lock=true\n - xpack.security.enabled=true\n - xpack.security.http.ssl.enabled=true\n - xpack.security.http.ssl.key=certs/es01/es01.key\n - xpack.security.http.ssl.certificate=certs/es01/es01.crt\n - xpack.security.http.ssl.certificate_authorities=certs/ca/ca.crt\n - xpack.security.transport.ssl.enabled=true\n - xpack.security.transport.ssl.key=certs/es01/es01.key\n - xpack.security.transport.ssl.certificate=certs/es01/es01.crt\n - xpack.security.transport.ssl.certificate_authorities=certs/ca/ca.crt\n - xpack.security.transport.ssl.verification_mode=certificate\n - xpack.license.self_generated.type=${LICENSE}\n mem_limit: ${ES_MEM_LIMIT}\n ulimits:\n memlock:\n soft: -1\n hard: -1\n healthcheck:\n test:\n [\n \"CMD-SHELL\",\n \"curl -s --cacert config/certs/ca/ca.crt https://localhost:9200 | grep -q 'missing authentication credentials'\",\n ]\n interval: 10s\n timeout: 10s\n retries: 120","_metadata":{"uid":"csf52ff6b7e8999493"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs546bcd2e188d8706"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThis will be the single-node cluster of Elasticsearch that we’re using for testing.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNotice we’ll be using the CA cert and node certificates that were generated.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou will also notice that we’re storing the Elasticsearch data in a volume outside of the container by specifying \u003cspan data-type='inlineCode'\u003e- esdata01:/usr/share/elasticsearch/data\u003c/span\u003e The two primary reasons for this are performance and data persistence. If we were to leave the data directory inside the container, we would see a significant degradation in the performance of our Elasticsearch node, as well as lose data anytime we needed to change the configuration of the container within our docker-compose file.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith both configurations in place, we can perform our first `docker-compose up` command.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs41df3dd83111d786"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs92e73ae3933fdb6e"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003eDocker Compose tips\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you’re new to Docker Compose or it’s been a while since you’ve had to \u003c/span\u003e\u003ca href=\"https://docs.docker.com/engine/reference/commandline/compose/#child-commands\"\u003e\u003cspan style='font-size: 12pt;'\u003eremember some of the commands\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, let’s quickly review the primary ones you will want to know for this adventure.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou will want to run all these commands in a terminal while in the same folder in which your \u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003edocker-compose.yml\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file resides. My example folder:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs51829e3c5edff568"}}},{"image":{"image":{"uid":"blt18e2b714d1be05fb","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-31T19:53:57.140Z","updated_at":"2023-05-31T19:53:57.140Z","content_type":"image/png","file_size":"60880","filename":"Screenshot_2023-05-31_at_1.53.44_PM.png","title":"Screenshot_2023-05-31_at_1.53.44_PM.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-02T20:39:30.729Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt18e2b714d1be05fb/6477a5d514eef6dcbb88421e/Screenshot_2023-05-31_at_1.53.44_PM.png"},"_metadata":{"uid":"cs5f75b4defe8bf69b"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs059ff356d212aeda"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet’s take a look at those commands.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs227f3e3891a79aec"}}},{"image":{"image":{"uid":"blt82c0a221326eecf1","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-31T19:54:49.124Z","updated_at":"2023-05-31T19:54:49.124Z","content_type":"image/png","file_size":"158901","filename":"Screenshot_2023-05-31_at_1.54.32_PM.png","title":"Screenshot_2023-05-31_at_1.54.32_PM.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-02T20:39:30.752Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt82c0a221326eecf1/6477a60904cf0c4308c497ab/Screenshot_2023-05-31_at_1.54.32_PM.png"},"_metadata":{"uid":"csd8b20894f19085cf"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscbf223a77b7de4f2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, lets run `docker-compose up`.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs6b16557eab607b33"}}},{"image":{"image":{"uid":"blt828cbfd7ac8b0e37","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-31T19:55:54.839Z","updated_at":"2023-05-31T19:55:54.839Z","content_type":"image/png","file_size":"343198","filename":"Screenshot_2023-05-31_at_1.55.45_PM.png","title":"Screenshot_2023-05-31_at_1.55.45_PM.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-02T20:39:30.779Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt828cbfd7ac8b0e37/6477a64a43f559ac23b7d6dc/Screenshot_2023-05-31_at_1.55.45_PM.png"},"_metadata":{"uid":"cs285ac485d5f4be85"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs275a9cefc385331e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAt this point, if the syntax is correct, Docker will begin to download all images and build the environment that is listed in the \u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003edocker-compose.yml\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file. This may take a few minutes depending on the speed of your internet. If you want to see the images outside of Docker Desktop, you can always find them in the \u003c/span\u003e\u003ca href=\"https://www.docker.elastic.co/\"\u003e\u003cspan style='font-size: 12pt;'\u003eofficial Elastic Docker Hub\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7bc4db1d04a7061b"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0688d3a7301619c9"},"header_style":"H2","paragraph_l10n":"\u003ch3\u003eTroubleshooting Virtual Memory misconfigurations\u003c/h3\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen starting up the Elasticsearch node for the first time, many users get stuck on the Virtual Memory configuration and receive an error message such as:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1abf4dc2c0eafa0b"}}},{"code":{"code":"{\"@timestamp\":\"2023-04-14T13:16:22.148Z\", \"log.level\":\"ERROR\", \"message\":\"node validation exception\\n[1] bootstrap checks failed. You must address the points described in the following [1] lines before starting Elasticsearch.\\nbootstrap check failure [1] of [1]: max virtual memory areas vm.max_map_count [65530] is too low, increase to at least [262144]\", \"ecs.version\": \"1.2.0\",\"service.name\":\"ES_ECS\",\"event.dataset\":\"elasticsearch.server\",\"process.thread.name\":\"main\",\"log.logger\":\"org.elasticsearch.bootstrap.Elasticsearch\",\"elasticsearch.node.name\":\"es01\",\"elasticsearch.cluster.name\":\"docker-cluster\"}","_metadata":{"uid":"cs39409e43c91199d3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs59408e7a901f896c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe key takeaway here is \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003emax virtual memory areas vm.max_map_count [65530] is too low, increase to at least [262144]. \u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUltimately, the command \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003esysctl -w vm.max_map_count=262144\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e needs to be run where the containers are being hosted.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the case of Mac, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html#_macos_with_docker_for_mac\"\u003e\u003cspan style='font-size: 12pt;'\u003echeck these instructions\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e for Docker for Mac. Follow \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html#_windows_and_macos_with_docker_desktop\"\u003e\u003cspan style='font-size: 12pt;'\u003ethese instructions for Docker Desktop\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. For Linux users, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html#_linux\"\u003e\u003cspan style='font-size: 12pt;'\u003esee these instructions\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Windows users, if you have Docker Desktop, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html#_windows_and_macos_with_docker_desktop\"\u003e\u003cspan style='font-size: 12pt;'\u003eyou can try these instructions\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. However, if you’re \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html#_windows_with_docker_desktop_wsl_2_backend\"\u003e\u003cspan style='font-size: 12pt;'\u003eusing WSLv2 with Docker Desktop, take a look here\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce complete, you can reboot Docker Desktop and retry your \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003edocker-compose up\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e command.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5cf8b7cd48550683"}}},{"image":{"image":{"uid":"blt96b117aab6a0cde3","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:23:33.651Z","updated_at":"2023-05-17T16:23:33.651Z","content_type":"image/png","file_size":"111427","filename":"image7.png","title":"image7.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.528Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96b117aab6a0cde3/6464ff85e0f341103f57bda8/image7.png"},"_metadata":{"uid":"cs8e35cfbfe465b076"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc7dccca4872a9b3c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRemember, the Setup container will exit on purpose after it has completed generating the certs and passwords.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSo far so good, but let's test.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe can use a command to copy the \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003eca.crt \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eout of the es01-1 container. Remember, the name of the set of containers is based on the folder from which the \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003edocker-compose.yml\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e is running. For example, my directory is “elasticstack_docker” therefore, my command would look like this, based on the screenshot above:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003edocker cp \u003c/span\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cp style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003eelasticstack_docker-es01-1:/usr/share/elasticsearch/config/certs/ca/ca.crt /tmp/.\u003c/span\u003e\u003c/p\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOnce the certificate is downloaded, run a curl command to query the Elasticsearch node:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cspan data-type='inlineCode'\u003ecurl --cacert /tmp/ca.crt -u elastic:changeme https://localhost:9200\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc3d378497a9f85b2"}}},{"image":{"image":{"uid":"blt399aad04378e03f8","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:25:16.465Z","updated_at":"2023-05-17T16:25:16.465Z","content_type":"image/png","file_size":"44081","filename":"image4.png","title":"image4.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.553Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt399aad04378e03f8/6464ffec61e0446fcb14f9a6/image4.png"},"_metadata":{"uid":"cs51478baeb459f7d5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csfd806638460448ef"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSuccess!\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNotice that we’re accessing Elasticsearch using \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003elocalhost\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e:9200. This is thanks to the port, which has been specified via the \u003cspan data-type='inlineCode'\u003eports\u003c/span\u003e section of \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003edocker-compose.yml\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. This setting maps ports on the container to ports on the host and allows traffic to pass through your machine and into the docker container with that port specified.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs7b7a70af80190eee"}}},{"banner":{"reference":[{"uid":"blt6d98a581fc6972d6","_content_type_uid":"banner"}],"_metadata":{"uid":"cs8f141e4d784cc4b5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs29723e1d07a50f8e"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eKibana\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor the Kibana config, we will utilize the certificate output from earlier. We will also specify that this node doesn't start until it sees that the Elasticsearch node above is up and running correctly.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003edocker-compose.yml (‘kibana’ container)\u003c/h3\u003e"}],"_metadata":{"uid":"cs849d255f0afec5b1"}}},{"code":{"code":"kibana:\n depends_on:\n es01:\n condition: service_healthy\n image: docker.elastic.co/kibana/kibana:${STACK_VERSION}\n labels:\n co.elastic.logs/module: kibana\n volumes:\n - certs:/usr/share/kibana/config/certs\n - kibanadata:/usr/share/kibana/data\n ports:\n - ${KIBANA_PORT}:5601\n environment:\n - SERVERNAME=kibana\n - ELASTICSEARCH_HOSTS=https://es01:9200\n - ELASTICSEARCH_USERNAME=kibana_system\n - ELASTICSEARCH_PASSWORD=${KIBANA_PASSWORD}\n - ELASTICSEARCH_SSL_CERTIFICATEAUTHORITIES=config/certs/ca/ca.crt\n - XPACK_SECURITY_ENCRYPTIONKEY=${ENCRYPTION_KEY}\n - XPACK_ENCRYPTEDSAVEDOBJECTS_ENCRYPTIONKEY=${ENCRYPTION_KEY}\n - XPACK_REPORTING_ENCRYPTIONKEY=${ENCRYPTION_KEY}\n mem_limit: ${KB_MEM_LIMIT}\n healthcheck:\n test:\n [\n \"CMD-SHELL\",\n \"curl -s -I http://localhost:5601 | grep -q 'HTTP/1.1 302 Found'\",\n ]\n interval: 10s\n timeout: 10s\n retries: 120","_metadata":{"uid":"cs10f472b15f9ae020"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbbc6218ede4fd378"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNotice in our `environment` section that we’re specifying \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003eELASTICSEARCH_HOSTS=https://es01:9200\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e We’re able to specify the container name here for our ES01 Elasticsearch container since we’re utilizing the \u003c/span\u003e\u003ca href=\"https://docs.docker.com/compose/networking/\"\u003e\u003cspan style='font-size: 12pt;'\u003eDocker default networking\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. All containers that are using the “elastic” network that was specified at the beginning of our \u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003edocker-compose.yml\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file will be able to properly resolve other container names and communicate with each other.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet's load up Kibana and see if we can access it.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs99369e2c38fd1f59"}}},{"image":{"image":{"uid":"blt61b57182e9ecb7ce","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:26:30.760Z","updated_at":"2023-05-17T16:26:30.760Z","content_type":"image/png","file_size":"146607","filename":"image5.png","title":"image5.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.576Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt61b57182e9ecb7ce/64650036ce0b9185f3e81ca8/image5.png"},"_metadata":{"uid":"csfd63ea71af865d6d"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs66bb15bd1f291224"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe containers are green. We should now be able to reach \u003c/span\u003e\u003ca href=\"http://localhost:5601\"\u003e\u003cspan style='font-size: 12pt;'\u003ehttp://localhost:5601\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs93c79b54df178639"}}},{"image":{"image":{"uid":"bltf990c5d8d32fd57e","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:27:09.977Z","updated_at":"2023-05-17T16:27:09.977Z","content_type":"image/png","file_size":"45007","filename":"image3.png","title":"image3.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.603Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf990c5d8d32fd57e/6465005d6ff7c0a9f72bce2f/image3.png"},"_metadata":{"uid":"cs20c8751bad739ee5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":"width-large: 75%"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csef885f2320fa0bc0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA quick login with the username and password that was specified should drop us right into a brand-new instance of Kibana. Excellent!\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eMetricbeat\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that we have Kibana and Elasticsearch up and running and communicating, let’s configure Metricbeat to help us keep an eye on things. This will require both configuration in our docker-compose file, and also in a standalone \u003c/span\u003e\u003cspan style='color:rgb(24, 128, 56);font-size: 12pt;'\u003emetricbeat.yml\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e file.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNote:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e For Logstash, Filebeat, and Metricbeat, the configuration files are using \u003c/span\u003e\u003ca href=\"https://docs.docker.com/storage/bind-mounts/\"\u003e\u003cspan style='font-size: 12pt;'\u003ebind mounts\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Bind mounts for files will retain the same permissions and ownership within the container that they have on the host system. Be sure to set permissions such that the files will be readable and, ideally, not writeable by the container’s user. You will receive an error in the container otherwise. Removing the write permissions on your host may suffice.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003edocker-compose.yml (‘metricbeat01’ container)\u003c/h3\u003e"}],"_metadata":{"uid":"cs71d9afdb5fa66098"}}},{"code":{"code":" metricbeat01:\n depends_on:\n es01:\n condition: service_healthy\n kibana:\n condition: service_healthy\n image: docker.elastic.co/beats/metricbeat:${STACK_VERSION}\n user: root\n volumes:\n - certs:/usr/share/metricbeat/certs\n - metricbeatdata01:/usr/share/metricbeat/data\n - \"./metricbeat.yml:/usr/share/metricbeat/metricbeat.yml:ro\"\n - \"/var/run/docker.sock:/var/run/docker.sock:ro\"\n - \"/sys/fs/cgroup:/hostfs/sys/fs/cgroup:ro\"\n - \"/proc:/hostfs/proc:ro\"\n - \"/:/hostfs:ro\"\n environment:\n - ELASTIC_USER=elastic\n - ELASTIC_PASSWORD=${ELASTIC_PASSWORD}\n - ELASTIC_HOSTS=https://es01:9200\n - KIBANA_HOSTS=http://kibana:5601\n - LOGSTASH_HOSTS=http://logstash01:9600","_metadata":{"uid":"cs63a058952d67d141"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc8f94d53de267336"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHere, we’re exposing host information regarding processes, filesystem, and the docker daemon to the Metricbeat container in a read-only fashion. This enables Metricbeat to collect the data to send to Elasticsearch.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003emetricbeat.yml\u003c/h3\u003e"}],"_metadata":{"uid":"csb8c33c1668fc2089"}}},{"code":{"code":"metricbeat.config.modules:\n path: ${path.config}/modules.d/*.yml\n reload.enabled: false\n\n\nmetricbeat.modules:\n- module: elasticsearch\n xpack.enabled: true\n period: 10s\n hosts: ${ELASTIC_HOSTS}\n ssl.certificate_authorities: \"certs/ca/ca.crt\"\n ssl.certificate: \"certs/es01/es01.crt\"\n ssl.key: \"certs/es01/es01.key\"\n username: ${ELASTIC_USER}\n password: ${ELASTIC_PASSWORD}\n ssl.enabled: true\n\n\n- module: logstash\n xpack.enabled: true\n period: 10s\n hosts: ${LOGSTASH_HOSTS}\n\n\n- module: kibana\n metricsets:\n - stats\n period: 10s\n hosts: ${KIBANA_HOSTS}\n username: ${ELASTIC_USER}\n password: ${ELASTIC_PASSWORD}\n xpack.enabled: true\n\n\n- module: docker\n metricsets:\n - \"container\"\n - \"cpu\"\n - \"diskio\"\n - \"healthcheck\"\n - \"info\"\n #- \"image\"\n - \"memory\"\n - \"network\"\n hosts: [\"unix:///var/run/docker.sock\"]\n period: 10s\n enabled: true\n\n\nprocessors:\n - add_host_metadata: ~\n - add_docker_metadata: ~\n\n\noutput.elasticsearch:\n hosts: ${ELASTIC_HOSTS}\n username: ${ELASTIC_USER}\n password: ${ELASTIC_PASSWORD}\n ssl:\n certificate: \"certs/es01/es01.crt\"\n certificate_authorities: \"certs/ca/ca.crt\"\n key: \"certs/es01/es01.key\"","_metadata":{"uid":"cs1626f7dab4d34af4"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc57538b5bbfe2661"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOur Metricbeat is dependent on ES01 and Kibana nodes being healthy before starting. The notable configurations here are in the \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003emetricbeat.yml\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e file. We have enabled four modules for gathering metrics including Elasticsearch, Kibana, Logstash, and Docker.\u003c/span\u003e \u003cspan style=\"font-size: 12pt;\"\u003eThis means, once we verify Metricbeat is up, we can hop into Kibana and \u003c/span\u003e\u003ca href=\"http://localhost:5601/app/monitoring\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enavigate to “Stack Monitoring”\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to see how things look.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csa276d47cb9ddfbdb"}}},{"image":{"image":{"uid":"bltd26e79829c568c13","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:28:38.740Z","updated_at":"2023-05-17T16:28:38.740Z","content_type":"image/png","file_size":"183573","filename":"image9.png","title":"image9.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.625Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd26e79829c568c13/646500b6bb5054db5d0ff13f/image9.png"},"_metadata":{"uid":"cs822800c302c1b9f5"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse328239b5a33edfb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDon't forget to set up your out-of-the-box rules!\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs80378bb011e70f4c"}}},{"image":{"image":{"uid":"blt925df5f044d604de","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:29:17.985Z","updated_at":"2023-05-17T16:29:17.985Z","content_type":"image/png","file_size":"50902","filename":"image10.png","title":"image10.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.649Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt925df5f044d604de/646500dd01974d3ef9d68ba4/image10.png"},"_metadata":{"uid":"cs220b430fc7a1499e"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt92390cf6b273991b","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:29:48.455Z","updated_at":"2023-05-17T16:29:48.455Z","content_type":"image/png","file_size":"165054","filename":"image12.png","title":"image12.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.675Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt92390cf6b273991b/646500fc42f57a80484124f9/image12.png"},"_metadata":{"uid":"cs875178d687b7c95a"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc4e6c3927957dfb5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMetricbeat is also configured for monitoring the container’s host through \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cspan data-type='inlineCode'\u003e/var/run/docker.sock\u003c/span\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Checking Elastic Observability allows you to see metrics coming in from your host.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3b089e2557ecca2e"}}},{"image":{"image":{"uid":"blt9ed46c43547b1d6c","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:30:44.653Z","updated_at":"2023-05-17T16:30:44.653Z","content_type":"image/png","file_size":"106267","filename":"image8.png","title":"image8.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.698Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9ed46c43547b1d6c/64650134f21a355221cf6fd2/image8.png"},"_metadata":{"uid":"cs7df8de35fb1e00df"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs751c7c3eed1077c1"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eFilebeat\u003c/h2\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow that the cluster is stable and monitored with Metricbeat, let’s look at Filebeat for log ingestion. Here, our Filebeat will be utilized in two different ways:\u003c/span\u003e\u003c/p\u003e\u003ch3\u003edocker-compose.yml (‘filebeat01’ container)\u003c/h3\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs03a0e171882c8e54"}}},{"code":{"code":" filebeat01:\n depends_on:\n es01:\n condition: service_healthy\n image: docker.elastic.co/beats/filebeat:${STACK_VERSION}\n user: root\n volumes:\n - certs:/usr/share/filebeat/certs\n - filebeatdata01:/usr/share/filebeat/data\n - \"./filebeat_ingest_data/:/usr/share/filebeat/ingest_data/\"\n - \"./filebeat.yml:/usr/share/filebeat/filebeat.yml:ro\"\n - \"/var/lib/docker/containers:/var/lib/docker/containers:ro\"\n - \"/var/run/docker.sock:/var/run/docker.sock:ro\"\n environment:\n - ELASTIC_USER=elastic\n - ELASTIC_PASSWORD=${ELASTIC_PASSWORD}\n - ELASTIC_HOSTS=https://es01:9200\n - KIBANA_HOSTS=http://kibana:5601\n - LOGSTASH_HOSTS=http://logstash01:9600","_metadata":{"uid":"csc36fcdeb37653474"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs282e96cd81520c3d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 14pt;'\u003efilebeat.yml\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs75638784e3d3b29b"}}},{"code":{"code":"filebeat.inputs:\n- type: filestream\n id: default-filestream\n paths:\n - ingest_data/*.log\n\n\nfilebeat.autodiscover:\n providers:\n - type: docker\n hints.enabled: true\n\n\nprocessors:\n- add_docker_metadata: ~\n\n\nsetup.kibana:\n host: ${KIBANA_HOSTS}\n username: ${ELASTIC_USER}\n password: ${ELASTIC_PASSWORD}\n\n\noutput.elasticsearch:\n hosts: ${ELASTIC_HOSTS}\n username: ${ELASTIC_USER}\n password: ${ELASTIC_PASSWORD}\n ssl.enabled: true\n ssl.certificate_authorities: \"certs/ca/ca.crt\"","_metadata":{"uid":"cs0e5d58b26a37a699"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2e0bbd938d70bafa"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFirst, we set a bind mount to map the folder “filebeat_ingest_data” into the container. If this folder doesn't exist on your host, it will be created when the container spins up. If you’d like to test the \u003c/span\u003e\u003ca href=\"http://localhost:5601/app/logs/stream\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLogs Stream\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e viewer within Elastic Observability for your custom logs, you can easily drop any file with a \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e.log\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e extension into \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/filebeat_ingest_data/\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and the logs will be read into the default Filebeat Datastream.\u003cbr/\u003e\u003c/span\u003e\u003cbr/\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAlongside this, we also map in \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/var/lib/docker/containers\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/var/run/docker.sock\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e which, combined with the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003efilebeat.autodiscover\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e section and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/current/configuration-autodiscover-hints.html#_docker_3\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ehints-based autodiscover\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, allows Filebeat to pull in the logs for all the containers. These logs will also be found in the Logs Stream viewer mentioned above.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb47185d5cf91d7ee"}}},{"image":{"image":{"uid":"blta02e6bd272df383d","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:32:45.966Z","updated_at":"2023-05-17T16:32:45.966Z","content_type":"image/png","file_size":"364589","filename":"image13.png","title":"image13.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.720Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta02e6bd272df383d/646501adf55683f99fe00dd4/image13.png"},"_metadata":{"uid":"cs1521e276ff693164"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3bb8f391d6ea189e"},"header_style":"H2","paragraph_l10n":"\u003ch2\u003eLogstash\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOur final container to bring to life is none other than Logstash.\u003c/span\u003e\u003c/p\u003e\u003ch3\u003edocker-compose.yml (‘logstash01’ container)\u003c/h3\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscf6031ad3ca1b1ca"}}},{"code":{"code":" logstash01:\n depends_on:\n es01:\n condition: service_healthy\n kibana:\n condition: service_healthy\n image: docker.elastic.co/logstash/logstash:${STACK_VERSION}\n labels:\n co.elastic.logs/module: logstash\n user: root\n volumes:\n - certs:/usr/share/logstash/certs\n - logstashdata01:/usr/share/logstash/data\n - \"./logstash_ingest_data/:/usr/share/logstash/ingest_data/\"\n - \"./logstash.conf:/usr/share/logstash/pipeline/logstash.conf:ro\"\n environment:\n - xpack.monitoring.enabled=false\n - ELASTIC_USER=elastic\n - ELASTIC_PASSWORD=${ELASTIC_PASSWORD}\n - ELASTIC_HOSTS=https://es01:9200","_metadata":{"uid":"cs0166b53afdcf90b4"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs3bb66012a7b688e0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 14pt;'\u003elogstash.conf\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb59c5db0006fd37b"}}},{"code":{"code":"input {\n file {\n #https://www.elastic.co/guide/en/logstash/current/plugins-inputs-file.html\n #default is TAIL which assumes more data will come into the file.\n #change to mode =\u003e \"read\" if the file is a compelte file. by default, the file will be removed once reading is complete -- backup your files if you need them.\n mode =\u003e \"tail\"\n path =\u003e \"/usr/share/logstash/ingest_data/*\"\n }\n}\n\n\nfilter {\n}\n\n\noutput {\n elasticsearch {\n index =\u003e \"logstash-%{+YYYY.MM.dd}\"\n hosts=\u003e \"${ELASTIC_HOSTS}\"\n user=\u003e \"${ELASTIC_USER}\"\n password=\u003e \"${ELASTIC_PASSWORD}\"\n cacert=\u003e \"certs/ca/ca.crt\"\n }\n}\n","_metadata":{"uid":"cse3767ab8fcc1bbce"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5c40ab49d8662a18"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe Logstash configuration is very similar to the Filebeat configuration. Again we’re using a bind mount and mapping a folder called \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/logstash_ingest_data/\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e from the host into the Logstash container. Here, you can test out some of the many \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/input-plugins.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003einput plugins\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/filter-plugins.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efilter plugins\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e by modifying the \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003elogstash.yml\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e file. Then drop your data into the \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cspan data-type='inlineCode'\u003e/logstash_ingest_data/\u003c/span\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e folder. You may need to restart your Logstash container after modifying the \u003c/span\u003e\u003cspan style=\"color: rgb(24, 128, 56);font-size: 12pt;\"\u003elogstash.yml\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e file.\u003cbr /\u003e\u003c/span\u003e\u003cbr /\u003e\u003cspan style=\"font-size: 12pt;\"\u003eNote, the Logstash output index name is \"logstash-%{+YYYY.MM.dd}\". To see the data, you will \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/data-views.html#settings-create-pattern\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eneed to create a Data View\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for the “logstash-*” pattern, as seen below.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfe5783e57ad22d85"}}},{"image":{"image":{"uid":"blt0fc9a442d3edc36d","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:34:22.481Z","updated_at":"2023-05-17T16:34:22.481Z","content_type":"image/png","file_size":"88489","filename":"image11.png","title":"image11.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.747Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0fc9a442d3edc36d/6465020e01974da3aed68ba8/image11.png"},"_metadata":{"uid":"cs6d4f444acc295452"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt1a274d4779996251","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:34:41.860Z","updated_at":"2023-05-17T16:34:41.860Z","content_type":"image/png","file_size":"369132","filename":"image14.png","title":"image14.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.767Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt1a274d4779996251/646502216606ca504e95e905/image14.png"},"_metadata":{"uid":"csfd94f18d6bed8735"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs60fb56062a47e393"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, with Filebeat and Logstash both up and running, if you navigate back to Cluster Monitoring you will see Logstash being monitored, as well as some metrics and links for Elasticsearch Logs.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs610e670a6d22b5cd"}}},{"image":{"image":{"uid":"blt965f471c668c7bf1","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:35:17.951Z","updated_at":"2023-05-17T16:35:17.951Z","content_type":"image/png","file_size":"189720","filename":"image6.png","title":"image6.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.789Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt965f471c668c7bf1/646502456606cad52295e909/image6.png"},"_metadata":{"uid":"cs22af6833a41959fe"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Conclusion","_metadata":{"uid":"cs96032cc843ab1e9f"},"header_style":"H2","paragraph_l10n":""}],"_metadata":{"uid":"csc5c9954357329b03"}}},{"image":{"image":{"uid":"blt9ef7719ea4353141","created_by":"blt92c74e5c4edca909","updated_by":"blt92c74e5c4edca909","created_at":"2023-05-17T16:35:52.841Z","updated_at":"2023-05-17T16:35:52.841Z","content_type":"image/png","file_size":"94379","filename":"image1.png","title":"image1.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-05-17T16:59:15.813Z","user":"blt92c74e5c4edca909"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9ef7719ea4353141/646502689c40aa66a40754d1/image1.png"},"_metadata":{"uid":"csc1cc1d0159f2a613"},"caption_l10n":"","alt_text_l10n":"","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs14f9c4f431d888c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003ePart one of this series has covered a full active cluster with monitoring and ingestion as the foundation of our stack. This will act as your local playground to test some of the features of the Elastic ecosystem.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReady to learn more? \u003ca href=\"https://www.elastic.co/blog/getting-started-with-the-elastic-stack-and-docker-compose-part-2\" target=\"_self\"\u003eCheck out part two\u003c/a\u003e! We dive into optimizing this foundation, along with setting up additional features such as APM Server, Elastic Agents, Elastic Integrations, and Elastic Search. We also deploy and test an application that you can instrument with some of these pieces.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAll files discussed here \u003c/span\u003e\u003ca href=\"https://github.com/elkninja/elastic-stack-docker-part-one\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eare available on GitHub\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e along with some sample data to ingest for Filebeat and Logstash.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/webinars/introduction-elk-stack\" target=\"_self\"\u003e\u003cspan\u003eWatch the introduction to Elastic Stack\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs0da2ed3e0122b559"}}},{"callout":{"title_l10n":"Additional resources","_metadata":{"uid":"cs1d9c69d2e7d2113d"},"paragraph_l10n":"\u003col\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/elasticsearch/reference/current/docker.html#docker-compose-file\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRunning Elasticsearch on Docker\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/kibana/current/docker.html\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRunning Kibana on Docker\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/metricbeat/current/running-on-docker.html\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRunning Metricbeat on Docker\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/beats/filebeat/current/running-on-docker.html\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRunning Filebeat on Docker\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/docker-config.html\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003eRunning Logstash on Docker\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ol\u003e","callout_reference":[],"callout_type":"Information (info)"}}],"publish_date":"2023-05-17T13:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Getting started with the Elastic Stack and Docker-Compose","seo_description_l10n":"In part one of this two-part series, we’ll dive into configuring the components of a standard Elastic Stack consisting of Elasticsearch, Logstash, Kibana, and Beats (ELK-B), on which we can immediately begin developing.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltdeb5e512cabf0e10","ACL":{},"created_at":"2023-11-03T17:34:50.549Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"platform","label_l10n":"Platform","tags":[],"title":"Platform","updated_at":"2023-11-03T17:34:53.443Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.235Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt3a21a598b13dcba0","ACL":{},"content_type":"image/png","created_at":"2021-01-12T16:50:35.641Z","created_by":"bltf6ab93733e4e3a73","file_size":"50983","filename":"blog-thumb-charts-laptop.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-charts-laptop.png","updated_at":"2022-02-11T21:04:12.027Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:03.577Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3a21a598b13dcba0/5ffdd35b092adc41f184bad4/blog-thumb-charts-laptop.png"},"title":"Getting started with the Elastic Stack and Docker Compose: Part 1","title_l10n":"Getting started with the Elastic Stack and Docker Compose: Part 1","updated_at":"2025-02-25T20:49:53.016Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/getting-started-with-the-elastic-stack-and-docker-compose","publish_details":{"time":"2025-02-25T20:52:32.914Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5b91d5a19b0f708d","_version":1,"locale":"en-us","ACL":{},"abstract_l10n":"Read about the updates and bug fixes that have been included in this release.","author":["blta248c27b7b7978db"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-02-25T18:58:20.860Z","created_by":"blte369ea3bcd6ac892","markdown_l10n":"Version 7.17.28 of the Elastic Stack was released today. We recommend you [upgrade to this latest version](https://www.elastic.co/downloads). We recommend 7.17.28 over the previous version 7.17.27\n\nFor details of the issues that have been fixed and a full list of changes for each product in this version, please refer to [the release notes](https://www.elastic.co/guide/en/starting-with-the-elasticsearch-platform-and-its-solutions/7.17/new.html).","modular_blocks":[],"publish_date":"2025-02-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[],"tags_use_case":[],"thumbnail_image":{"uid":"blt8836a5dda86cbfe0","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-04-01T15:42:09.734Z","updated_at":"2024-04-01T15:42:09.734Z","content_type":"image/png","file_size":"62454","filename":"Patch_release_dark.png","title":"Patch_release_dark.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-04-02T17:14:25.081Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8836a5dda86cbfe0/660ad5d11b5a5878c8adccbc/Patch_release_dark.png"},"title":"Elastic Stack 7.17.28 released","title_l10n":"Elastic Stack 7.17.28 released ","updated_at":"2025-02-25T18:58:20.860Z","updated_by":"blte369ea3bcd6ac892","url":"/blog/elastic-stack-7-17-28-released","publish_details":{"time":"2025-02-25T22:09:11.745Z","user":"blte369ea3bcd6ac892","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt12a751f492100461","_version":4,"locale":"en-us","ACL":{},"abstract_l10n":"The Logstash integration has incorporated data from new and improved reporting APIs into dashboards that make monitoring and troubleshooting your Logstash deployment simple and straightforward.","author":["blt80b226b35f93d8c4"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-02-25T17:43:20.282Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs032371abb893a03a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLogstash is a powerful tool for ingesting, transforming, and shipping data from various sources. Visibility into Logstash is critical for optimizing performance and troubleshooting issues related to data ingestion. We’ve greatly improved the Logstash integration to display the status of your Logstash nodes and pipelines at a glance. The integration is now powered by Elastic Agent, which queries Logstash monitoring APIs for data that populates managed dashboards.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThis blog will guide you through the visualizations available from the integration, how to configure and install them, and the underlying APIs that provide the data. See the health of your Logstash nodes at a glance with the updated integration.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Monitoring with the Logstash integration","_metadata":{"uid":"cs62a0ef67cfa231a0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe dashboards available through the integration completely break open the black box. Insights that would take extensive queries are available at your fingertips in the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOverview\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e dashboard. Here, you can see what matters at a high level, the number of events Logstash has received, how many it has processed and sent, and how long it took.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs23e795b64e3a88c3"}}},{"image":{"image":{"uid":"blt7a22c155f8777943","_version":1,"title":"image1.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:46:51.637Z","updated_at":"2025-02-25T17:46:51.637Z","content_type":"image/png","file_size":"330989","filename":"image1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.109Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7a22c155f8777943/67be020b304ea9d77b82bf05/image1.png"},"_metadata":{"uid":"cs2c129bff5c9fb413"},"caption_l10n":"","alt_text_l10n":"overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0d8297b0e9a5158d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor the performance of a single node, the \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNode Overview\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e dashboard provides details on system and process health. This helps to determine if an issue is localized to an individual host or if it is pervasive throughout a deployment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfef3f669564d5f62"}}},{"image":{"image":{"uid":"blte883f0223a220a45","_version":1,"title":"image15.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:46:41.214Z","updated_at":"2025-02-25T17:46:41.214Z","content_type":"image/png","file_size":"434575","filename":"image15.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.383Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte883f0223a220a45/67be0201cdb05afe2b5de90d/image15.png"},"_metadata":{"uid":"cs21ebad383ee5ea31"},"caption_l10n":"","alt_text_l10n":"node overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse50cc3502a504dba"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePipelines are where the work in Logstash really occurs, and we have no shortage of insights related to pipeline performance. The \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ePipeline Overview\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e dashboard provides high-level details on pipeline activity across your entire deployment to quickly surface problems and assess performance. Broken down by pipeline, you can see the average time an event takes to process, which is how long it takes pushing to queue. Items that are outside the allotted tolerance are bolded in red to quickly attract attention and direct users to take action.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9f8010f25306673f"}}},{"image":{"image":{"uid":"bltb35edde2f3ab8b32","_version":1,"title":"image3.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:46:25.682Z","updated_at":"2025-02-25T17:46:25.682Z","content_type":"image/png","file_size":"278551","filename":"image3.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.200Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb35edde2f3ab8b32/67be01f1c1fe9665f354cf18/image3.png"},"_metadata":{"uid":"cs22fe6dc66decef67"},"caption_l10n":"","alt_text_l10n":"pipeline overview","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csb6469888dc36942f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs you drill down into individual pipelines, you’ll see details on worker utilization and processing over time. This is invaluable in determining the cause of problems. Isolating spikes in time makes it easier to correlate with configuration changes or external events.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs9cd1be50602de922"}}},{"image":{"image":{"uid":"blte35852dc45b881b9","_version":1,"title":"image10.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:46:12.890Z","updated_at":"2025-02-25T17:46:12.890Z","content_type":"image/png","file_size":"173737","filename":"image10.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.312Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte35852dc45b881b9/67be01e4d1b1de0b10ca3c45/image10.png"},"_metadata":{"uid":"cs1bbdf7fd2891dc86"},"caption_l10n":"","alt_text_l10n":"blank graphs","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs027ab0768a630f87"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBut you shouldn’t stop at pipelines. A huge benefit of using Logstash is the vast ecosystem of plugins. That strength does introduce variability, which can make troubleshooting more difficult. Thankfully, the integration addresses that problem by providing plugin details by type, enabling users to drill down further.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf4c670adc3b36f5d"}}},{"image":{"image":{"uid":"blte33a19e9c0affcff","_version":1,"title":"image5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:45:53.312Z","updated_at":"2025-02-25T17:45:53.312Z","content_type":"image/png","file_size":"193441","filename":"image5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.291Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte33a19e9c0affcff/67be01d1c660314b201ffbb7/image5.png"},"_metadata":{"uid":"cs5422c86f13b5a637"},"caption_l10n":"","alt_text_l10n":"1 - ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"bltd62af84e144458e3","_version":1,"title":"image11.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:45:44.034Z","updated_at":"2025-02-25T17:45:44.034Z","content_type":"image/png","file_size":"366958","filename":"image11.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.121Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd62af84e144458e3/67be01c85c5329184331644f/image11.png"},"_metadata":{"uid":"cseb123b629c2c0a65"},"caption_l10n":"","alt_text_l10n":"2 - ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"image":{"image":{"uid":"blt252f140bc88098e3","_version":1,"title":"image14.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:45:36.356Z","updated_at":"2025-02-25T17:45:36.356Z","content_type":"image/png","file_size":"251842","filename":"image14.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.393Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt252f140bc88098e3/67be01c0d1b1de841cca3c3f/image14.png"},"_metadata":{"uid":"cs9981d9168248ad5f"},"caption_l10n":"","alt_text_l10n":"3 - ","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"See what’s new","_metadata":{"uid":"cs424f55154817eff6"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe health report dashboards are the newest addition, and the amount of information they can quickly convey will make every Logstash operator’s life easier. One quick look is all you need to see if there are problems with your Logstash deployment.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf93ec32bdd4af42b"}}},{"image":{"image":{"uid":"blta09f356567518bdb","_version":1,"title":"image13.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:45:08.014Z","updated_at":"2025-02-25T17:45:08.014Z","content_type":"image/png","file_size":"177841","filename":"image13.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.214Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta09f356567518bdb/67be01a4959e4e3c29e47109/image13.png"},"_metadata":{"uid":"cs21b8dc7cf8647d0f"},"caption_l10n":"","alt_text_l10n":"orange bar graph","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8b485d895e5ac4bd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003ePipeline health provides more detailed data as well as actionable insights on troubleshooting steps.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfbdee871df3f4cec"}}},{"image":{"image":{"uid":"bltcc8fc8badf48c124","_version":1,"title":"image12.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:44:59.950Z","updated_at":"2025-02-25T17:44:59.950Z","content_type":"image/png","file_size":"284375","filename":"image12.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.322Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcc8fc8badf48c124/67be019b959e4e6115e47105/image12.png"},"_metadata":{"uid":"csa519a52907ca0d91"},"caption_l10n":"","alt_text_l10n":"yellow, orange, green bar graph","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"Logstash integration with Elastic Agent ","_metadata":{"uid":"cs8d791e6303db81a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eInstalling the integration can be done in minutes, and the data you get will save you hours of troubleshooting. Here are the steps to install the integration and deploy agents to your Logstash instances that will collect and transform the data from Logstash monitoring APIs.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e1. \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/dashboard-monitoring-with-elastic-agent.html#add-agent-to-fleet-ead\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd the Logstash integration to monitor your deployment\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cbr /\u003e\u003cspan style='font-size: 12pt;'\u003eFrom the integrations page, search for Logstash. Click \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd Logstash\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, and you’ll be guided through the configuration options on how an Elastic Agent can collect monitoring data from your instance.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs746fd2a1cb0056b8"}}},{"image":{"image":{"uid":"bltbbce2bee42e31a9b","_version":1,"title":"image2.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:44:50.217Z","updated_at":"2025-02-25T17:44:50.217Z","content_type":"image/png","file_size":"215816","filename":"image2.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.301Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbbce2bee42e31a9b/67be019262af0c0cd88a19be/image2.png"},"_metadata":{"uid":"cs496ec7972b745e0a"},"caption_l10n":"","alt_text_l10n":"logstash","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs52f77b6af0c205a7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBe sure to select \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMetrics (Elastic Agent)\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to get the most data and our newest dashboards. You can specify what data to collect and the API polling intervals or stick with our defaults. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHealth Reporting\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e is disabled by default, but you’ll want to enable it to get the most out of the integration. If you have modified your Logstash configuration to listen on a different port, specify it here.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs92a407c08e435f55"}}},{"image":{"image":{"uid":"bltb067333638b3bfc6","_version":1,"title":"image9.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:44:27.486Z","updated_at":"2025-02-25T17:44:27.486Z","content_type":"image/png","file_size":"242904","filename":"image9.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.180Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb067333638b3bfc6/67be017b959e4e0e70e47101/image9.png"},"_metadata":{"uid":"cscd80dceb13f2ceeb"},"caption_l10n":"","alt_text_l10n":"add logstash integration","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse3353dc764e6b774"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e2. \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/dashboard-monitoring-with-elastic-agent.html#add-agent-to-fleet-ead\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eConfigure and install Elastic Agents on Logstash nodes\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou will likely be deploying this to new agents. Create a name that is meaningful, and then save and continue. If you already have agents monitoring your Logstash deployment, you can add this policy to existing hosts.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csecfc974cc192b693"}}},{"image":{"image":{"uid":"bltcb8d8034fb84aa41","_version":1,"title":"image7.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:50:23.102Z","updated_at":"2025-02-25T17:50:23.102Z","content_type":"image/png","file_size":"98968","filename":"image7.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.403Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcb8d8034fb84aa41/67be02df1a2ab55a0a10e325/image7.png"},"_metadata":{"uid":"cs74aeef1c2ca97552"},"caption_l10n":"","alt_text_l10n":"where to add this integration?","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5ea9e9b4194209c1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eYou will be prompted to add Elastic Agent to your Logstash nodes.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs93c266910b723949"}}},{"image":{"image":{"uid":"blte9fc3e03f467a1b6","_version":1,"title":"image8.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:50:07.793Z","updated_at":"2025-02-25T17:50:07.793Z","content_type":"image/png","file_size":"71818","filename":"image8.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.229Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte9fc3e03f467a1b6/67be02cf5ac38d956c8fef06/image8.png"},"_metadata":{"uid":"csf016ffa1184406a4"},"caption_l10n":"","alt_text_l10n":"logstash integration added","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5d44d20d4591835d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eChoose \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAdd Elastic Agent to your hosts\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e, and you’ll be guided through Fleet enrollment, agent installation, and verification.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csf06d61544aeff175"}}},{"image":{"image":{"uid":"blte72b303e41565076","_version":1,"title":"image4.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:49:53.981Z","updated_at":"2025-02-25T17:49:53.981Z","content_type":"image/png","file_size":"256944","filename":"image4.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.373Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte72b303e41565076/67be02c162af0c67cf8a19d0/image4.png"},"_metadata":{"uid":"cs478f7c7ea00e3bc1"},"caption_l10n":"","alt_text_l10n":"add agent","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cscbeb301caaee4c50"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOnce you’ve verified that agents are communicating with Fleet, the data will start flowing in and populate the dashboards.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Data available through Logstash monitoring APIs","_metadata":{"uid":"cs458c9ec0f87fa481"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLogstash exposes several monitoring APIs that give extensive visibility into single instances. The Logstash integration uses these APIs with the Elastic Agent to parse and deliver these data to your monitoring cluster. Customers that wish to create a custom integration for Logstash monitoring can query these APIs according to their requirements.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/node-stats-api.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eNode Stats\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cbr /\u003eProvides detailed information at a node and pipeline level for a wide range of resources, events, and utilization. In version 8.5, we added an additional data type — Flow Stats — which includes derivative measures of performance, including throughput, backpressure, and worker concurrency.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/guide/en/logstash/current/logstash-health-report-api.html\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eHealth Report\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cbr /\u003eNew in 8.16, the Logstash health report returns a color coded health status for your Logstash instance based on various indicators, such as pipeline status and worker utilization. The indicators include symptom details. You can also view unhealthy results, which include potential impacts, diagnoses, and suggested actions to address the problem.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Get started today","_metadata":{"uid":"cs75918543fb57c3e0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eReady to get started? Explore now in a \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/registration\"\u003e\u003cspan style='font-size: 12pt;'\u003efree 14-day trial\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(52, 55, 65);font-size: 12pt;'\u003e on Elastic Cloud\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e — the hosted Elasticsearch service that includes all of the latest features.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cseeecea03a99193f1"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs5915fb0f37ebdb13"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs711ce6c0b39e35e5"}}}],"publish_date":"2025-02-25","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt39140cf3e2cd4550","ACL":{},"created_at":"2023-11-06T21:51:00.583Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"integrations","label_l10n":"Integrations","tags":[],"title":"Integrations","updated_at":"2023-11-06T21:51:00.583Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.083Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"_content_type_uid":"tags_topic","uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"tags_topic","uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"blt9f3033eaacd184dd","ACL":{},"created_at":"2022-09-13T16:43:44.540Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2022-09-13T16:43:44.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.249Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"bltb302c1813086b3cd","_version":1,"title":"158175 - Blog header image_Prancheta 1-04 (2).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-25T17:43:15.906Z","updated_at":"2025-02-25T17:43:15.906Z","content_type":"image/jpeg","file_size":"171236","filename":"158175_-_Blog_header_image_Prancheta_1-04_(2).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-25T17:51:06.281Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb302c1813086b3cd/67be01335ac38d53798feee3/158175_-_Blog_header_image_Prancheta_1-04_(2).jpg"},"title":"Easy, comprehensive Logstash monitoring with Elastic Agent","title_l10n":"Easy, comprehensive Logstash monitoring with Elastic Agent","updated_at":"2025-02-25T17:50:59.520Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/logstash-monitoring-elastic-agent","publish_details":{"time":"2025-02-25T17:51:05.608Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltc08afab7cf86ee84","_version":17,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic is the best developer platform for building AI search and generative AI apps with expanded ecosystem partners, full document vector search, a proprietary ML model for semantic search now in GA, and a simple API-first developer experience. ","author":["blt6f8c1e29600b488b"],"category":[],"created_at":"2023-11-30T15:44:11.111Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9dc013da917071ff"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn this blog, we want to share the investments that Elastic® is making to simplify your experience as you build AI applications. We know that developers have to stay nimble in today’s fast-evolving AI environment. Yet, common challenges make building generative AI applications needlessly rigid and complicated. To name just a few:\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eVectors — from how many to which ones you can use and how to chunk large passages of text\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEvaluating, swapping, and managing large language models (LLMs)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSetting up effective semantic search (particularly if your development team has limited resources or skill gaps)\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeveraging existing investments and current architectures while balancing tech debt\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eScaling from proof-of-concept to production\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMaking sure that end-user applications are fast and cost-effective and reflect secure, up-to-date proprietary data in responses to queries\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFragmented and complex implementation\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFlexible tools help you adapt quickly, respond to changes, and accelerate your projects. This is why Elastic is building on its foundation in Apache Lucene to offer the best open code vector database and search engine available. Elastic is also actively partnering across the ecosystem to expand support for transformer and foundation models.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMoreover, we’re making it easier to get highly relevant semantic search out of the box with Elastic’s proprietary Learned Sparse EncodeR model, ELSER — now in GA. We’re reducing the costs and processing time associated with retrieval augmented generation (RAG), the retrieval process that provides relevant responses to natural language queries from proprietary data sources to LLMs, for custom use cases. And, we’re streamlining the developer experience across Elasticsearch®, so that implementation is simple and straightforward.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eDevelopers are actively shaping the future of generative AI apps. Elastic’s ground-breaking investments (and many more to come) reflect why our AI-powered search analytics platform is the best choice for a new generation of search workloads.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"All in on Apache Lucene","_metadata":{"uid":"cs03d7b75b1a159737"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIt all started with \u003c/span\u003e\u003ca href=\"/celebrating-lucene\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eApache Lucene\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, an open source search engine software library that has stood the test of time and provides the basis for Elasticsearch. While Elasticsearch has grown to be recognized as the most downloaded vector database with its innovations in vector search, scalability, and performance, the strength of our platform originates from the fact that Elastic and Lucene’s communities invest in these advancements in Apache Lucene first. In fact, Elastic has a history of enhancing Lucene’s capabilities, such as numeric and geospatial search capabilities, Weak AND support, and improved columnar storage. Advancing the Lucene community means everyone goes farther, faster. Being the driver for these investments means Elastic users receive the value first, tailored to their search needs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAt Elastic, we know that Lucene has potential beyond full-text search: developers need a full scope of features to build search apps and generative AI experiences including aggregations, filtering, faceting, etc. Ultimately we are on track to make Lucene the most leading-edge vector database in the world and to share its capabilities with millions of Elasticsearch users across the globe. That’s why Elastic’s developers regularly commit code to Lucene and leverage its foundational code for new projects, such as:\u003c/span\u003e\u003c/p\u003e\n\u003cul\u003e\n \u003cli\u003e\n \u003cp\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/lucene-bringing-maximum-inner-product-to-lucene\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBringing maximum-inner-product to Lucene\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003ca href=\"/blog/accelerating-vector-search-simd-instructions\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAccelerating vector search with SIMD instructions\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/adding-passage-vector-search-to-lucene\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDelivering full document vector search for allowing documents to have multiple vectors within one field, ranked by the most similar vectors\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e — handling the complexity of properly scoring vectors derived from long passages of text in order to address a common challenge — maintaining the overall context of large documents when using text embeddings\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/articles/vector-similarity-computations-fma-style\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFused Multiply-Add (FMA) in Lucene\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSince Elasticsearch is built on top of Lucene, when you \u003c/span\u003e\u003ca href=\"/blog/whats-new-elasticsearch-platform-8-11-0\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eupgrade to our latest release\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, you automatically benefit from all of the latest improvements. And we’ve already started to contribute the next foundational investments our customers will need by adding \u003c/span\u003e\u003ca href=\"/search-labs/blog/scalar-quantization-in-lucene\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003escalar quantization support to Lucene\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, a key cost savings capability.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Second to none in semantic search and RAG","_metadata":{"uid":"cscd3aae40d3f634a2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eDevelopers are tasked with building search and generative AI applications that are relevant, performant, and cost-effective. Quite simply, you need to be able to retrieve data from all your proprietary data sources to build RAG to deliver the best, most pertinent results. To that end, we’ve added \u003ca href=\"/enterprise-search/data-ingestion\" target=\"_self\"\u003emore native connectors and connector clients\u003c/a\u003e for enterprise databases and popular productivity tools, and content sources like OneDrive, Google Drive, GitHub, ServiceNow, Sharepoint, Teams, Slack, and plenty of others.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEven more notably with \u003c/span\u003e\u003ca href=\"/blog/whats-new-elasticsearch-platform-8-11-0\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s 8.11 release\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, we’ve announced the general availability of Elastic Learned Sparse EncodeR (ELSER). It’s our proprietary AI model for delivering world-class semantic search. ELSER is a pre-trained, text retrieval model that provides highly relevant results across domains and lets you implement semantic search by \u003c/span\u003e\u003ca href=\"/getting-started/enterprise-search/build-a-semantic-search-experience\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003efollowing a few simple steps\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. Since \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/introducing-elasticsearch-relevance-engine-esre\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eits technical preview in May\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, ELSER has had wide adoption, allowing us to make improvements based on customer feedback. Our GA ELSER model brings increased relevance and reduced ingest and retrieval time. You can \u003c/span\u003e\u003ca href=\"https://github.com/elastic/elasticsearch-labs/blob/bc36bfa5d1ce56dc1e7412bc8a91db5ba1c36751/notebooks/model-upgrades/upgrading-index-to-use-elser.ipynb\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eupgrade now\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to take advantage of these enhancements.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAnother obstacle that comes with generative AI territory: higher compute costs and slower response times. Generative LLM calls incur costs per token and require additional processing, which takes time. However, with the power of embeddings and fast k-Nearest Neighbors algorithms (kNN), Elastic can be used as a \u003c/span\u003e\u003ca href=\"https://elastic.co/search-labs/blog/elasticsearch-as-a-genai-caching-layer\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecaching layer for generative AI applications\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, readily identifying similar queries and responses and providing quicker, more cost-effective answers. With respect to cost efficiencies, \u003c/span\u003e\u003cspan style=\"color: rgb(29, 28, 29);font-size: 12pt;\"\u003eon AWS, we now also offer \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/cloud/current/ec-default-aws-configurations.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ea vector search optimized Elastic Cloud hardware profile\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(29, 28, 29);font-size: 12pt;\"\u003e with an optimal default RAM ratio for a price effective ability to store more vectors.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThe better Elastic is at making semantic search and RAG simple to use together, the faster developers can make great generative AI experiences for end users. That’s why we’re laser-focused on making the technology easy and practical for developers to use.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Choice and flexibility across the ecosystem","_metadata":{"uid":"csfff1115bf6ca1b09"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHelping you respond to change quickly in the AI era with an open platform where you can use a variety of tools and consistent standards is key to accelerating generative AI projects. That’s why developers have flexibility to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/elastic-machine-learning-models\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003euse and host a variety of transformer models\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e within Elasticsearch, including private and public \u003c/span\u003e\u003ca href=\"https://www.docker.elastic.co/r/eland/eland:latest\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eHugging Face models\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e. You can also store vectors in Elasticsearch generated by third-party services like AWS SageMaker, Google Vertex AI, Cohere, OpenAI, and more.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’re also expanding our support for ecosystem tools so you can easily use Elasticsearch as your \u003c/span\u003e\u003ca href=\"https://integrations.langchain.com/vectorstores\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003evector database with LangChain\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and \u003c/span\u003e\u003ca href=\"https://gpt-index.readthedocs.io/en/stable/examples/vector_stores/ElasticsearchIndexDemo.html\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLlamaIndex\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIn fact, we recently collaborated with the LangChain team on \u003c/span\u003e\u003ca href=\"/blog/elasticsearch-langchain-production-ready-rag-templates\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLangChain Templates\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to help developers build production-ready generative AI apps. Thanks to our community, Elastic is already one of the most popular vector stores on LangChain. Now with the new \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eRAG template\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, you can create production-level capabilities with LangSmith and Elasticsearch.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"A simple developer experience","_metadata":{"uid":"csc21a1d6dd4ca9322"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’re dedicated to creating a simplified developer experience. We’re releasing streamlined commands that abstract away the complexity of inference and model management work streams that you can use behind one simple API. We’re improving default settings for dense vectors and providing automatic mappings too. With one call, you can summarize results or embed text as vectors from any model, reducing the time it takes for you to build and learn.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSoon, we’ll introduce \u003c/span\u003e\u003ca href=\"/blog/elastic-serverless-architecture\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic’s new serverless architecture\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, a new deployment option for developers who want to focus on creating innovative experiences, not managing their underlying infrastructure. We’re focused on giving you all of the tools you need, so we’re adding new language clients in our serverless architecture for Python, PHP, JavaScript, Ruby, Java, .Net, and Go.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWe’re also well aware that it can be challenging to get started with fast-changing, new technologies, which is why we’re offering simple onboarding with inline guidance and code across every one of Elastic’s deployment options, including \u003c/span\u003e\u003ca href=\"https://www.elastic.co/search-labs/tutorials/examples\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ereal-world examples\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e to help you spin up new projects quickly.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThere’s never been a better time to be an Elasticsearch developer. Our recent research and development efforts are making Lucene the best vector database in the world. We’re ensuring that semantic search and RAG are unparalleled when it comes to ease of use, relevance, speed, scale, and cost efficiency. And we’re putting ecosystem openness, flexibility, and simplicity at the heart of developer experience.\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eReady to start building next-generation search on Elasticsearch? Try the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/esre/current/index.html\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElasticsearch Relevance Engine™\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, our suite of developer tools for building AI search apps.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd79b48f52edf80b5"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs8fc82eec8399be72"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8fed689b9137958b"}}}],"publish_date":"2023-11-30","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Elastic’s innovative investments to support an open ecosystem and a simpler developer experience","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt02ec7fa8864f17dd","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-11-30T16:18:30.450Z","updated_at":"2023-11-30T16:18:30.450Z","content_type":"image/png","file_size":"155558","filename":"elastic-de-135742-blogheader-pav_V1.png","title":"elastic-de-135742-blogheader-pav_V1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2023-11-30T20:27:48.736Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt02ec7fa8864f17dd/6568b5d67c56dd34b8a618b4/elastic-de-135742-blogheader-pav_V1.png"},"title":"Paving the way for modern search workflows and generative AI apps","title_l10n":"Paving the way for modern search workflows and generative AI apps","updated_at":"2025-02-25T17:11:57.493Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/modern-search-workflows-generative-ai-apps","publish_details":{"time":"2025-02-25T17:12:01.366Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt7aab1ff88e7ae0f5","_version":12,"locale":"en-us","ACL":{},"abstract_l10n":"The payments industry is changing. There are new apps and technologies being used to send money seemingly every day. But banks have advantages in scale and sophistication that they use to innovate and compete.","author":["blt9b0dc3587c08e259"],"category":[],"created_at":"2021-12-07T21:31:25.343Z","created_by":"blt4349d9729d06d101","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs76c2e4e54ec1c916"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe payments industry has evolved dramatically over the past decade. Traditional payment vehicles still make up the majority of transaction flows, but new apps and startups continue to grow in popularity, and billions of dollars move through their systems.\u003c/p\u003e\n\u003cp\u003eAccording to a recent \u003ca href=\"https://www.jpmorgan.com/solutions/treasury-payments/payments-are-eating-the-world\"\u003eJPMorgan study\u003c/a\u003e, of the $240 trillion in global payments in 2020, ~$54 trillion can be attributed to emerging mega-themes; that is, trends that are reshaping the way money changes hands. These themes include super apps, e-commerce, digital wallets, wearables, BNPL (buy now, pay later), connected cars, and other payment vehicles. This environment has generated a rush of excitement for customers. However, it has also created a significant level of complexity that the financial community and regulators are grappling with.\u003c/p\u003e\n\u003cp\u003eTo a great extent, fintech providers have proven to be the leaders of innovation in this space, jumping on emerging market needs and creating digital applications to meet customers where they are. Thus, while it is true that long gone are the days of banks being a one-stop shop for payments, banks still have a reason to try to remain competitive and innovative.\u003c/p\u003e\n\u003cp\u003eAccording to \u003ca href=\"https://www.ey.com/en_gl/banking-capital-markets/how-banks-can-win-at-payments\"\u003eEY\u003c/a\u003e, payments generate between 20% and 30% of the typical bank's profit directly or indirectly. It's therefore essential for banks to assert their expertise and history in this space. Possibly even more critical, transactions create key data points that enable banks to personalize other purchase experiences. With \u003ca href=\"https://www.bcg.com/publications/2019/what-does-personalization-banking-really-mean\"\u003eBCG\u003c/a\u003e finding that only 30% of customers think their bank is personalizing their service—there is a significant opportunity for expansion in this area.\u003c/p\u003e\n\u003cp\u003eBanks should create an environment that enables them to be the perfect source or partner for transactions. Here are a few things banks can do to support a winning payments experience.\u003c/p\u003e\n"},{"title_l10n":"Complete, Real-time search ","_metadata":{"uid":"cs23e21c0fe8ac72d7"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eEnabling a \u003ca href=\"/blog/rabobank-enhancing-the-online-banking-experience-with-elasticsearch\"\u003ereal-time search experience\u003c/a\u003e across accounts and solutions types is still a struggle for many providers. Particularly in the institutional space, it can be difficult with multiple payment types (Wires, ACH, Same Day ACH, RTP) running on legacy systems and rails to deliver this holistic picture back to the client. This situation often feels frustrating for clients as they need to access multiple screens or run several reports across modules. This can also create downstream issues with servicing customers. According to \u003ca href=\"https://www.capgemini.com/wp-content/uploads/2021/04/World-Retail-Banking-Report-2021.pdf\" target=\"_self\"\u003eCapgemini\u003c/a\u003e, having a successful omnichannel experience is the most crucial component for banking customers. That starts with empowering employees with complete datasets and\u0026nbsp;enabling them to respond to customer inquiries quickly. For banks that are still struggling with this challenge, it is worth exploring tools to drive searchability and break down data silos to unlock a better experience.\u003c/p\u003e"},{"title_l10n":"Create a tech foundation for innovation","_metadata":{"uid":"cs2650742572895558"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThe world of payments will continue to evolve. New foundational changes with the introduction of 5G coupled with advances in artificial intelligence (AI) algorithms, quantum computing, and blockchain will give life to advances in the payments space, according to \u003ca href=\"https://www.jpmorgan.com/solutions/treasury-payments/payments-are-eating-the-world\"\u003eJPM\u003c/a\u003e. It's therefore crucial that banks offer their developers the means to innovate. Faster application development can be achieved via \u003ca href=\"/observability\"\u003eunified visibility\u003c/a\u003e across time series data and with tools that have built-in machine learning. Exploring new ways to streamline IT (e.g., mainframe offloading, application consolidation) helps reduce costs and enables banks to reinvest in digital transformation.\u003c/p\u003e"},{"title_l10n":"Harness data to lead the way in fraud detection","_metadata":{"uid":"cs023d85edfb1248fc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBanks have a clear advantage over fintech and niche payment providers when it comes to their potential to address fraud proactively. Traditional banks sit on a wealth of real-time information about customers, enabling them to paint a more holistic picture of their profiles. Understanding customer habits to accurately detect potential fraud events \u0026amp; protect their assets. While also not creating roadblocks for legitimate transactions. Search platforms can empower Fraud teams with unified data sets, enabling \u003ca href=\"/customers/pscu\" target=\"_blank\"\u003equick decisioning \u003c/a\u003efor the end customer \u0026amp; merchants. By deploying machine learning and alerting features, fraud teams can proactively detect and stamp out financial fraud before it impacts accounts.\u003c/p\u003e\u003cp\u003eEven as the payments space becomes more fragmented, there is still an opportunity for banks to be the trusted partner for clients to get their most important answers. Elastic is the leading platform for search-powered solutions, delivering powerful insights across financial services. We help organizations search, solve, and succeed — no matter the mission.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eRead more stories about how our financial services customers use Elastic\u003c/strong\u003e \u003ca href=\"/industries/financial-services\"\u003ehere\u003c/a\u003e.\u003c/p\u003e"}],"_metadata":{"uid":"cs69153ba70ba07637"}}}],"publish_date":"2021-12-09T17:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Elastic can help banks compete in the booming payments industry","seo_description_l10n":"The payments industry is changing. There are new apps and technologies being used to send money seemingly every day. But banks have advantages in scale and sophistication that they use to innovate and compete.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt86414c2c190e35ba","created_by":"blt4349d9729d06d101","updated_by":"blt4349d9729d06d101","created_at":"2021-12-07T21:35:36.573Z","updated_at":"2021-12-07T21:35:36.573Z","content_type":"image/png","file_size":"25937","filename":"4d7d178b.png","title":"4d7d178b.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-09T19:26:23.969Z","user":"blt4349d9729d06d101"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt86414c2c190e35ba/61afd3a81a1be33b1b23fe22/4d7d178b.png"},"title":"How Elastic can help banks compete in the booming payments industry","title_l10n":"How Elastic can help banks compete in the booming payments industry","updated_at":"2025-02-25T15:39:52.426Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/how-elastic-can-help-banks-compete-payment-experience-payments-industry","publish_details":{"time":"2025-02-25T15:43:14.735Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1b2760ff8d03ddff","_version":11,"locale":"en-us","ACL":{},"abstract_l10n":"In a recently concluded third-party survey managed and analyzed by Socratic Technologies, over 1,400 Elastic customers shared their observability experiences. Take a look at the key takeaways from the survey.","author":["bltac4c94c5765cc633"],"category":["bltc17514bfdbc519df"],"created_at":"2022-07-08T19:40:10.144Z","created_by":"blt36060ca1dddf191e","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs088d80ab7d830612"},"header_style":"H2","paragraph_l10n":"\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003eCorrelating\u0026nbsp;data across multiple silos and applications to derive meaningful and actionable insights is an ongoing struggle. These challenges are only set to increase as high-speed connectivity becomes more ubiquitous and enables data-heavy, digital experiences.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003eIn a recent third-party survey managed and analyzed by Socratic Technologies, \u003c/span\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003eover 1,400 Elastic customers shared their observability experiences, revealing quantifiable benefits that directly contributed to business outcomes. \u003c/span\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003eElastic Observability is the world’s most widely deployed \u003ca href=\"https://www.elastic.co/observability\" target=\"_self\"\u003eobservability platform\u003c/a\u003e, built on the proven Elastic Stack — to break down silos and enable near real-time actionable insights.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e[\u003c/span\u003e\u003ca href=\"/explore/devops-observability/forrester-total-economic-impact-observability\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);\"\u003e\u003cu\u003eDownload the complete report for Elastic Observability\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e.]\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);\"\u003e66% improved MTTx metrics brought by unified visibility\u003c/span\u003e\u003c/h2\u003e\n\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003eCustomer experiences are directly tied to reduced application downtime, minimized friction across touchpoints, and improved service resilience. Organizations across industries strive to achieve these capabilities. Elastic Observability empowers them with end-to-end visibility into applications, systems, and infrastructure improving application and service resilience as measured by MTTx metrics.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n\u003cp\u003e\u003c/p\u003e\n\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003eOur customers reduced the number of incidents by 61%, which, in turn, reduced revenue loss due to downtime by 62%. At the same time, unified visibility can facilitate better collaboration across teams to prevent issues from occurring in the first place, building more resilient applications and services. All of these factors helped to improve MTTx KPIs and drove customer satisfaction higher for Elastic Observability users.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs617e5f105e6cfcc5"}}},{"quotes":{"quote_l10n":"With the Elastic solutions, we have implemented an observability platform to measure technical efficiency and enrich business dashboards. We also plan to integrate it with our Security solution (SOC).","_metadata":{"uid":"cs12c3c192c45be7d3"},"quote_author_l10n":"Elastic Observability customer | Industry - Telecommunications","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2801fc48b0c6b313"},"header_style":"H2","paragraph_l10n":"\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(0, 0, 0);font-size: undefined;'\u003eDriving faster innovations with actionable insights\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: undefined;'\u003eLack of skilled labor is a growing concern across most industries. Organizations are constantly seeking ways to enhance efficiency. Survey respondents shared how Elastic helps them improve efficiency and minimize time to market for new products and features.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style='color:rgb(14, 16, 26);font-size: undefined;'\u003eWith unified visibility, distributed systems and applications can be designed to be more resilient, reducing the number of incidents and allowing more time for developers and IT staff to focus on building new products and adding capabilities. Improved resilience not only improved efficiency but also helped build customer stickiness, and survey respondents reported seeing reduced customer churn up to 90%. Not surprisingly, customers cited Elastic Observability for driving operational efficiency and its ease of use.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse3a8dac85765f040"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"csdc66c6b6794b7971"},"paragraph_l10n":"\u003ch3\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003eUp to \u003c/span\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003e\u003cstrong\u003e88%\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 16, 26);\"\u003e acceleration in time-to-market of new products and features\u003c/span\u003e\u003c/h3\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0d157d3716753add"},"header_style":"H2","paragraph_l10n":"\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);font-size: undefined;\"\u003eEnsuring business critical services operate seamlessly, at scale\u0026nbsp;\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003eWe know how technology advancements in connectivity, cloud and data analytics, AI, and machine learning are redefining industries and changing how they do business. At Elastic, we are committed to building new capabilities that can help our customers position themselves well for the challenges of today and for the future.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003eWith organizational efficiency being top of mind for businesses and organizations, the majority of respondents to the survey cited \u003c/span\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003e\u003cstrong\u003elog analytic capabilities and near real-time actionable insights \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003eas critical in improving developer and operational efficiency\u003c/span\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003e\u003cstrong\u003e.\u0026nbsp;\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003e[Related article: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/driving-quantified-success-with-elastic-enterprise-search\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);font-size: undefined;\"\u003e\u003cu\u003eDriving quantified success with Elastic Enterprise Search\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003e]\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);font-size: undefined;\"\u003eAccelerate business results with Elastic across any cloud\u003c/span\u003e\u003c/h2\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003eA common theme that stood out from the survey was that deploying Elastic on the cloud provided an accelerated path to realizing business objectives. In fact, 95%of Elastic Cloud customers affirmed that they would use as much or more Elastic Cloud in the coming year.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003eThey cited ease of use and impact on cost as the most common reasons to deploy Elastic Cloud. For our customers, Elastic Cloud simplified their solution management and accelerated their time to market with improved operational efficiency while also reducing risks and overhead costs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003e[Related article: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/nucleus-research-elastic-data-management-observability-cloud\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);font-size: undefined;\"\u003e\u003cu\u003eLeveraging Elastic to improve data management and observability in the cloud\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(14, 16, 26);font-size: undefined;\"\u003e]\u003c/span\u003e\u003c/p\u003e\u003ch2 style=\"text-align: left;\"\u003e\u003cspan style=\"color: rgb(0, 0, 0);font-size: undefined;\"\u003eDownload the full report\u0026nbsp;\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(0, 0, 0);font-size: undefined;\"\u003eIn this blog post, we captured the highlights of the survey for Elastic Observability. Download the \u003c/span\u003e\u003ca href=\"/explore/devops-observability/forrester-total-economic-impact-observability\" target=\"_self\"\u003e\u003cspan style=\"color: rgb(17, 85, 204);font-size: undefined;\"\u003e\u003cu\u003efull report\u003c/u\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(0, 0, 0);font-size: undefined;\"\u003e for a closer look at the quantified benefits across solutions and we encourage you to share with your team.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs5bced0d1dd7b01d7"}}}],"publish_date":"2022-07-12","sanity_migration_complete":false,"seo":{"noindex":false,"canonical_tag":"","seo_description_l10n":"In a recently concluded third-party survey managed and analyzed by Socratic Technologies, over 1,400 Elastic customers shared their observability experiences. Take a look at the key takeaways from the survey.","seo_image":null,"seo_title_l10n":"Building resilience for applications and services with Elastic Observability"},"subtitle_l10n":"Insights from the 2022 Results That Matter study","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"bltc3067ddccda555c1","ACL":{},"created_at":"2023-11-06T21:50:08.806Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elastic-cloud","label_l10n":"Elastic Cloud","tags":[],"title":"Elastic Cloud","updated_at":"2023-11-06T21:50:08.806Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.096Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt17abd238870bda42","ACL":{},"content_type":"image/png","created_at":"2022-05-17T00:36:34.268Z","created_by":"blt1e57c6588ae1816e","file_size":"179861","filename":"illustration-machine-learning-anomaly-1680x980.png","parent_uid":null,"tags":[],"title":"illustration-machine-learning-anomaly-1680x980.png","updated_at":"2022-05-17T00:36:34.268Z","updated_by":"blt1e57c6588ae1816e","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-18T13:00:00.071Z","user":"blt1e57c6588ae1816e"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt17abd238870bda42/6282ee123b9b8554904a04f2/illustration-machine-learning-anomaly-1680x980.png"},"title":"Building resilience for applications and services with Elastic Observability","title_l10n":"Building resilience for applications and services with Elastic Observability","updated_at":"2025-02-24T22:35:24.441Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/building-resilience-for-applications-and-services-with-elastic-observability","publish_details":{"time":"2025-02-24T22:35:28.543Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt842663de774fde04","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"The observability experts at Elastic predict and review industry trends for this fast-evolving DevOps discipline. From kubernetes to CI/CD pipelines and TCO, these 12 trends are likely to impact your future observability strategy and deployment.","author":["bltde0a0be05534cebf"],"category":["bltc17514bfdbc519df"],"created_at":"2022-02-04T23:38:25.414Z","created_by":"blt3044324473ef223b70bc674c","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9ef37bd9bbb1204d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs businesses accelerate digital transformations and cloud adoption to better serve customers and employees in the face of the global pandemic, operational complexity has also mounted. To untangle these complexities and enable executive visibility into IT ecosystem , business leaders are increasingly looking to observability solutions as a strategic investment. \u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs3b6237dbd3b369bc"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eThroughout this unprecedented time, \u003ca href=\"/blog/look-back-at-elastic-observability-in-2021\"\u003eElastic has been uniquely positioned\u003c/a\u003e to help our customers succeed in their digital transformation journeys, and drive their observability initiatives. We’ve been part of thousands of customer conversations and efforts to manage digital transformation. Here’s what we’ve learned and predict for the years ahead.\u003c/p\u003e"}],"_metadata":{"uid":"csb7456926d028e2d6"}}},{"title_text":{"title_text":[{"title_l10n":"1. Observability is a critical business initiative","_metadata":{"uid":"cs6cf5ea9685ea9c2b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWith customers and employees increasingly going digital, businesses need to innovate faster with increased adoption of cloud and cloud-native technologies. Keeping cloud applications running effectively has also become significantly more difficult. Organizations continue to struggle with a lot of data, but few are able to extract actionable insights. Observability connects the dots in your telemetry data, provides visibility into application performance, and enables accelerated digital transformation.\u003c/p\u003e\u003cp\u003eAs a result, the criticality of full-stack observability efforts to accelerate digital transformation has now been deemed a strategic initiative for the C-suite. Observability is moving from being a buzzword to becoming mainstream. Executives will continue to expect observability solutions to increasingly connect business and operational KPIs. \u003ca href=\"/observability/ema-allstar-award-ai-assisted-observability\" target=\"_self\"\u003eAccording to EMA Research\u003c/a\u003e, microservices, containerization, public cloud, and application transformation has lifted observability to the top of enterprise priorities and is the #1 challenge for DevOps teams.\u003c/p\u003e"}],"_metadata":{"uid":"cs9fc32ca7cd99280a"}}},{"title_text":{"title_text":[{"title_l10n":"2. Kubernetes visibility and the emergence of eBPF","_metadata":{"uid":"cs69728501aeb90520"},"header_style":"H2","paragraph_l10n":"Container and kubernetes-led adoption continues to grow rapidly. However, the newer, ephemeral, cloud technologies have also introduced several operational and visibility challenges. As the number of kubernetes clusters increase, so does the management complexity related to scaling and monitoring. Emerging technologies such as \u003ca href=\"/blog/elastic-and-cmd-join-forces-to-help-you-take-command-of-your-cloud-workloads\"\u003eeBPF\u003c/a\u003e represent a big leap forward to provide visibility into complex Kubernetes environments with minimal overhead. eBPF also delivers the ability to provide visibility from the infrastructure to the application without the complexity and overhead of service meshes and will continue to see increased adoption. Expect increased focus on managing Kubernetes as well as the adoption of eBPF."}],"_metadata":{"uid":"cs7a9da73bdb2a7b0d"}}},{"title_text":{"title_text":[{"title_l10n":"3. Increasing need for visibility across hybrid and multi-cloud environments","_metadata":{"uid":"csb70dca3fbb3bfcc9"},"header_style":"H2","paragraph_l10n":"As organizations continue to rapidly evolve in their digital transformation journey, the adoption of the public cloud is a critical component. To facilitate and accelerate digital transformation, teams need visibility across hybrid and multi-cloud environments which are becoming increasingly complex. \u003ca href=\"/virtual-events/cloud-trends-and-observability\"\u003eAccording to 451 Research\u003c/a\u003e, over 70% of respondents say that the public cloud has increased complexity in their IT organization. Observability solutions that can provide visibility across hybrid and multi-cloud environments will be the solution of choice as organizations look for unified and comprehensive visibility across legacy technology as well as modern cloud environments."}],"_metadata":{"uid":"cs99df1591dedd5d83"}}},{"title_text":{"title_text":[{"title_l10n":"4. Machine learning will improve and deliver actionable insights","_metadata":{"uid":"csf474e4fb16dea2c8"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWith the amount of observability data exponentially growing, it’s harder for teams to manually sift and sort through the data to detect outliers and trends. In fact, infrequently occurring anomalies can be quite disruptive to the business but can be difficult to detect. According to \u003ca href=\"/observability/ema-allstar-award-ai-assisted-observability\" target=\"_self\"\u003eEMA Research\u003c/a\u003e, 45% of SRE time is spent on searching for actionable data. Operations and development teams are looking for ways in which machine learning can help identify anomalies as well as any outlier trends and patterns to accelerate root cause analysis and reduce downtime.\u003c/p\u003e"}],"_metadata":{"uid":"csf23637a4759f1a55"}}},{"title_text":{"title_text":[{"title_l10n":"5. Ad hoc analytics and data visualization in observability","_metadata":{"uid":"cs42d4d8a1f59d96a3"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhile machine learning and automated troubleshooting will continue to improve, DevOps and SRE teams will still need the ability to analyze and segment their observability data to answer the unknown unknowns. Ad hoc analytics along with data visualization enables collaboration between teams as they seek answers to trends and understand patterns to isolate application issues, along with the resulting business impact. These advanced capabilities will require observability solutions that can store large amounts of data with custom metrics and contextual data from a variety of sources and treat all data as a first class citizen. Observability is all about the data and storing it at the granularity needed for true insights.\u003c/p\u003e\n\u003cp\u003eExpect customers to increasingly focus on these advanced observability requirements as they continue to tie operational performance to business impact. \u003c/p\u003e"}],"_metadata":{"uid":"cs63842c34bde33ed3"}}},{"title_text":{"title_text":[{"title_l10n":"6. Increasing adoption and reliance on open standards","_metadata":{"uid":"cs581184d0d159c580"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs the observability technology ecosystem gets more complex, DevOps teams continue to converge on technologies based upon open standards. Adopting open standards help organizations avoid vendor lock-in while also unlocking community-driven innovation. We will continue to see the evolution of OpenTelemetry standards support for traces, metrics, and logs. Increased adoption of Prometheus for metrics and Apache Kafka for data streaming. DevOps teams are increasingly choosing observability solutions that support these open standards to provide organizations the ability to integrate and observe their heterogeneous application ecosystems.\u003c/p\u003e"}],"_metadata":{"uid":"csa7a49d1486cecbec"}}},{"title_text":{"title_text":[{"title_l10n":"7. Simple, transparent, consumption-based pricing","_metadata":{"uid":"cs923405b9f4f61a12"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs observability has continued to evolve and broaden its capabilities along with supporting more data types, observability pricing models have gotten increasingly complex. Each vendor offers multiple pricing levels along with a lot of fine print making observability deployments and their budgets, difficult to predict. Organizations will favor observability solutions that deliver value with costs based on consumption, providing teams the flexibility to adopt a model that works for them financially. Consumption-based pricing models that don’t artificially constrain customers from monitoring different environments, offer data retention and storage flexibility while still maintaining performance will be commonplace.\u003c/p\u003e"}],"_metadata":{"uid":"cs357b0276b011ca40"}}},{"title_text":{"title_text":[{"title_l10n":"8. A focus on observability TCO for the long-term","_metadata":{"uid":"cs125db05916c4e40b"},"header_style":"H2","paragraph_l10n":"With the exponential growth in operational complexity, organizations are increasingly faced with choosing between improved TCO vs. best of breed solutions. Too many solutions lead to tool sprawl resulting in fragmentation and data silos impacting operational visibility and hampering the ability to correlate data. According to \u003ca href=\"/virtual-events/cloud-trends-and-observability\"\u003e451 Research\u003c/a\u003e, 76% of organizations use more than one cloud provider. With over 800 services now being offered between AWS, Google Cloud, and Azure (according to EMA research), tool sprawl and complexity rises exponentially. Piecing together diagnostic information from multiple tools (otherwise known as the swivel chair effect) leads to increased time to root cause, reduced productivity, and slower innovation. Organizations will continue to consolidate multiple tools on a single platform that offers the best TCO for today and for tomorrow."}],"_metadata":{"uid":"csb693778b451a71f6"}}},{"title_text":{"title_text":[{"title_l10n":"9. A holistic approach requiring the right skills, processes, and technology","_metadata":{"uid":"cs3914ba615ef9f4fe"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eObservability is not just about tools. Proper observability requires building the right skillset and mindset in an organization. A team that is well versed in modern software development processes, as well as operating in a cloud environment. A team that follows observability best practices, right from the start of the development process: adding informative tags to packages, adding logging to their code, and enabling instrumentation for traces. Observability best practices need to be embedded in the development process from start to finish, not an afterthought.\u003c/p\u003e"}],"_metadata":{"uid":"csab2988b28a2281b9"}}},{"title_text":{"title_text":[{"title_l10n":"10. Tighter collaboration between operations and development teams","_metadata":{"uid":"cs12cc9f501987e3b2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eOrganizations continue to adopt DevOps practices as the rate of software development accelerates. To be effective, there needs to be increased collaboration between development and operations teams. All teams need to be analyzing the same data to be able to effectively collaborate and resolve problems quickly. In addition, besides adopting multiple tools within production environments, teams are also forced to adopt different tools used in their dev and stage environments, mostly due to cost constraints. Tool silos in different stages present a fragmented view of the entire pipeline. Organizations will continue to integrate their entire development environment on a single, \u003ca href=\"https://www.elastic.co/observability\" target=\"_self\"\u003eobservability platform\u003c/a\u003e to improve collaboration across teams, each analyzing the same data to reduce downtime.\u003c/p\u003e"}],"_metadata":{"uid":"cs9b2d93f7e7970ecc"}}},{"title_text":{"title_text":[{"title_l10n":"11. The rise of CI/CD observability","_metadata":{"uid":"csb6e17556525eaab5"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eBuild tools are critical to ensuring the delivery of software from development to production and are often extremely complex. To get insights and visibility into this pipeline, the CI/CD community has leveraged OpenTelemetry to start instrumenting build tools (e.g. Jenkins, Maven, JUnit, Ansible, etc). These initiatives went beyond the expectations of troubleshooting CI/CD platforms and has also helped accelerate software deployment. 2022 will continue to see the rise of an ecosystem of OpenTelemetry, native devops tools transforming CI/CD pipelines into gold mines of metrics on the software delivery lifecycle. Critical information that will support an ever growing range of use cases from troubleshooting and optimizing CI/CD pipelines, to test optimization, cost accounting, engineering process monitoring, and much more.\u003c/p\u003e"}],"_metadata":{"uid":"cs0bbd15496564ef54"}}},{"title_text":{"title_text":[{"title_l10n":"12. Observability and security working together more closely","_metadata":{"uid":"csd9e50bff717658f4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eAs the application development process accelerates with enterprises deploying code multiple times a day or week, it’s important to ensure the security of the application as well as the infrastructure. CIOs and CISOs are looking to embed security and observability teams together so they can ensure that security isn’t compromised while delivering innovation for their customers. Recent \u003ca href=\"/blog/cios-are-changing-who-is-responsible-for-cybersecurity-devsecops-observability-securitytools\"\u003esurvey data from 451 Research\u003c/a\u003e shows a major shift in who is using application security tools, suggesting that DevSecOps is not just an idea, but a growing reality. IT decision-makers allocated application security tools to 48% of development teams in 2020, compared to just 29% in 2015, a significant leap forward.\u003c/p\u003e\n\u003cp\u003eAccording to the report, “Opportunities abound for security to become more directly integrated into DevOps efforts, with CIOs leading the charge.” The report continues to say: “Security teams must become better versed in DevOps practices and tools, while DevOps pros must increasingly embrace the integration of security practices and technology.” Expect increased requirements from enterprises for solutions that allow observability and security teams to collaborate on the same platform.\u003c/p\u003e"}],"_metadata":{"uid":"cs1fe235807c486a71"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs1bcd81ebfa13c63a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003eWhile there has been a lot of hype around observability, organizations are starting to understand the criticality of it to ensure successful digitization and cloud adoption. These changes are driving significant and rapid business and operational needs. As you move from traditional monitoring to observability, the end goal of a great, reliable digital experience is what full-stack observability will ultimately bring about. Which is why an observability initiative is an important journey to embark on in 2022.\u003c/p\u003e\n\u003cp\u003eTo learn more and discuss these future observability trends, join us for a virtual event on March 22, 2022 - \u003ca href=\"https://www.elastic.co/virtual-events/observability-trends-2022\"\u003e\u003cstrong\u003eObservability trends for 2022: A look into the future! \u003c/strong\u003e\u003c/a\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f99d5f6aa5d44f9"}}}],"publish_date":"2022-02-04T23:42:52.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"From eBPF to CI/CD: 12 emerging trends in observability","seo_description_l10n":"The observability experts at Elastic predict and review industry trends for this fast-evolving DevOps discipline. From kubernetes to CI/CD pipelines and TCO, these 12 trends are likely to impact your future observability strategy and deployment.","noindex":false,"canonical_tag":"","seo_image":null},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","title":"AWS","label_l10n":"AWS","keyword":"aws","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt5da20aee1a072f80","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:30.685Z","updated_at":"2023-11-06T20:08:30.685Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:00:52.463Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt8617d65f559b9a82","ACL":{},"created_at":"2023-11-06T20:42:46.365Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"microsoft-azure","label_l10n":"Microsoft Azure","tags":[],"title":"Microsoft Azure","updated_at":"2023-11-06T20:42:46.365Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:39:19.197Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","title":"Google Cloud","label_l10n":"Google Cloud","keyword":"google-cloud","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbf617849beaf10fe","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:39:59.168Z","updated_at":"2023-11-06T20:40:14.658Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:39.796Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9e37344acd64cf5a","ACL":{},"created_at":"2023-11-06T20:38:34.272Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ebpf","label_l10n":"eBPF","tags":[],"title":"eBPF","updated_at":"2023-11-06T20:38:34.272Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.250Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt048e5e01aa446692","ACL":{},"created_at":"2023-11-06T20:38:02.694Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"devsecops","label_l10n":"DevSecOps","tags":[],"title":"DevSecOps","updated_at":"2023-11-06T20:38:02.694Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.187Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","_content_type_uid":"tags_topic","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt4732ba20ad170771","ACL":{},"created_at":"2023-11-06T20:48:01.608Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"public-multi-hybrid-cloud","label_l10n":"Public, multi \u0026 hybrid cloud","tags":[],"title":"Public, multi \u0026 hybrid cloud","updated_at":"2023-11-06T20:48:01.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:51.878Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdd4b5182721ccd42","ACL":{},"created_at":"2023-11-06T20:38:13.883Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"digital-experience","label_l10n":"Digital experience","tags":[],"title":"Digital experience","updated_at":"2023-11-06T20:38:13.883Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.180Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":2,"locale":"en-us","uid":"blt5f2c0926801ce9c6","ACL":{},"created_at":"2023-11-06T21:28:52.513Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kubernetes","label_l10n":"Kubernetes","tags":[],"title":"Kubernetes","updated_at":"2023-11-06T21:28:54.645Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.349Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"OpenTelemetry","label_l10n":"Open source/standards","keyword":"opentelemetry","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt069bd34528952802","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:44:13.512Z","updated_at":"2023-11-06T20:44:13.512Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.903Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":2,"is_dir":false,"uid":"bltd44d2f0e1f4f4b7d","ACL":{},"content_type":"image/png","created_at":"2020-02-14T21:07:01.894Z","created_by":"bltc87e8bcd2aefc255","description":"","file_size":"37777","filename":"blog-thumb-elastic-on-elastic.png","parent_uid":"blta8bbe6455dcfdb35","tags":[],"title":"blog-thumb-elastic-on-elastic.png","updated_at":"2022-02-11T21:03:58.816Z","updated_by":"bltf6ab93733e4e3a73","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-24T17:27:15.343Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltd44d2f0e1f4f4b7d/5ffe0f637c627d662d7fd996/blog-thumb-elastic-on-elastic.png"},"title":"From eBPF to CI/CD: 12 emerging trends in observability","title_l10n":"From eBPF to CI/CD: 12 emerging trends in observability","updated_at":"2025-02-24T22:33:44.330Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/from-ebpf-to-ci-cd-12-emerging-trends-in-observability","publish_details":{"time":"2025-02-24T22:33:49.858Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0807a52ad0dfe8c3","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Elastic is excited to announce the technical preview of Elastic Cloud Serverless on Microsoft Azure. Built on the industry-first Search AI Lake architecture, it combines vast storage, low-latency querying, and advanced AI capabilities. ","author":["bltf6c23ea28fef643d"],"category":["bltfaae4466058cc7d6"],"created_at":"2025-01-30T23:42:54.691Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs0d316df54c520e38"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eToday, we are excited to announce the technical preview of Elastic Cloud Serverless on Microsoft Azure — now available in the EastUS region. Elastic Cloud Serverless provides the fastest way to start and scale security, observability, and search solutions without managing infrastructure. Built on the industry-first \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/search-ai-lake-elastic-cloud-serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eSearch AI Lake architecture\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — which relies on Azure Blob Storage — it combines vast storage, separate storage and compute, low-latency querying, and advanced AI capabilities to deliver uncompromising speed and scale.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Start and scale quickly with Elastic Cloud Serverless on Azure","_metadata":{"uid":"cs9f69a50150392887"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eNo compromise on speed or scale:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elasticsearch Serverless dynamically scales to accommodate your workload, handling unpredictable traffic and data spikes automatically — all while offering low-latency search on boundless object storage.\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eHassle-free operations:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Say goodbye to managing clusters, provisioning nodes, or fine-tuning performance. Free your team from operational tasks — no need to manage infrastructure, do capacity planning, upgrade, or scale data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ePurpose-built product experience:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic Cloud Serverless provides a new, streamlined workflow to help you create projects tailored to your unique use cases in search, observability, and security. With guided onboarding, you can use in-product resources and tools that guide you every step of the way, accelerating time to value.\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \u003cli\u003e\n \u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSimplified pricing model: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Cloud Serverless offers a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/elastic-cloud-serverless-pricing-packaging\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eflexible, usage-based pricing model\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e that scales with your needs. The solution-specific pricing aligns costs with actual usage, offering greater flexibility and cost predictability. Pay only for what you use — whether it’s for data ingested and retained in Elastic Security and Observability products or for compute resources in Elasticsearch.\u003c/span\u003e\u003c/p\u003e\n \u003c/li\u003e\n \n\u003c/ul\u003e"},{"title_l10n":"Getting started with Elastic Cloud Serverless on Azure","_metadata":{"uid":"cs08f7968de3c2001d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWhen you \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/serverless-registration\"\u003e\u003cspan style='font-size: 12pt;'\u003esign up\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e or \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/\"\u003e\u003cspan style='font-size: 12pt;'\u003elog in\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to the Elastic Cloud console, you can create a serverless project by specifying the type of project you want (Elasticsearch, Elastic Observability, or Elastic Security). If you choose an Observability or Security project, select Azure as the cloud provider and EastUS as the region. For an Elasticsearch project, choose the use case (“General Purpose” or “Optimized for Vectors”), and then select Azure as the cloud provider and EastUS as the region. After clicking \"Create project,\" your Elastic Cloud Serverless project will be provisioned within minutes.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eVisit our \u003c/span\u003e\u003ca href=\"https://www.elastic.co/docs/current/serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003edocumentation\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to learn more.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"What’s next?","_metadata":{"uid":"csbe77f81968acc0a4"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eWe are just getting started. As we continue enhancing Elastic Cloud Serverless on Azure, we plan to expand its availability across additional Azure regions and introduce new features to further enhance performance and usability. Stay tuned for exciting updates as we bring the full power of Elastic’s solutions to Azure users.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe future of search, security, and observability is here without compromise on speed, scale, or cost. Experience Elastic Cloud Serverless and Search AI Lake to unlock new opportunities with your data. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/serverless\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn more\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e about the possibilities of serverless or start your \u003c/span\u003e\u003ca href=\"https://cloud.elastic.co/serverless-registration\"\u003e\u003cspan style='font-size: 12pt;'\u003efree trial now\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e on Azure in technical preview.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs32cc9d79f383ad21"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs87cfb40e0240d8de"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csb9d44b0601af6280"}}}],"publish_date":"2025-02-06","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Announcing the technical preview of Elastic Cloud Serverless on Azure","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"Elastic Cloud Serverless provides the fastest way to start and scale security, observability, and search solutions — without managing infrastructure.","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[],"tags_partner":[{"uid":"bltada2311dae66943e","_content_type_uid":"tags_partner"}],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blte5366a60bd5ae8af","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2025-02-06T01:25:19.754Z","created_by":"bltb6c155cd84fc0c1a","file_size":"33874","filename":"blog-serverless-azure-tech-preview_1-blog_header.jpg","parent_uid":null,"tags":[],"title":"blog-serverless-azure-tech-preview_1-blog header.jpg","updated_at":"2025-02-06T01:25:19.754Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2025-02-06T10:55:01.030Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte5366a60bd5ae8af/67a40f7fc0a3735f7f40ada6/blog-serverless-azure-tech-preview_1-blog_header.jpg"},"title":"Elastic Cloud Serverless now available in technical preview on Microsoft Azure","title_l10n":"Elastic Cloud Serverless now available in technical preview on Microsoft Azure","updated_at":"2025-02-24T18:16:52.529Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/elastic-cloud-serverless-microsoft-azure-tech-preview","publish_details":{"time":"2025-02-24T18:16:56.361Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5e74a3e65d6b8255","_version":2,"locale":"en-us","ACL":{},"abstract_l10n":"For US organizations that need to comply with CMMC, Elastic’s Search AI Platform can help. With its comprehensive security, observability, and search capabilities, Elastic gives a foundation to help achieve and maintain CMMC compliance efficiently.","author":["blt08b4b5ab12c65210"],"category":["bltc17514bfdbc519df"],"created_at":"2025-02-24T16:31:35.591Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7a6e45f84ecd45cd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe Cybersecurity Maturity Model Certification (CMMC) is a framework established by the US Department of Defense (DoD) to ensure that organizations handling Controlled Unclassified Information (CUI) implement robust cybersecurity measures. As CMMC becomes a key requirement for defense contractors, higher education institutions engaged in research or contracts with the DoD must also comply with its standards.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic’s Search AI Platform — with its comprehensive security, observability, and search capabilities — provides a powerful foundation to help organizations achieve and maintain CMMC compliance efficiently.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Understanding CMMC requirements","_metadata":{"uid":"cs37eea3afcec3c8fd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCMMC 2.0 consists of three levels with each increasing in complexity and security controls:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLevel 1:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Foundational cybersecurity practices, including basic safeguarding of Federal Contract Information (FCI)\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLevel 2:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Advanced security controls aligned with NIST 800-171, required for organizations handling CUI\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eLevel 3:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Expert-level cybersecurity measures that align with NIST 800-172 and are necessary for highly sensitive operations\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEach level mandates stringent monitoring, logging, and threat detection, which Elastic can help automate and streamline.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How Elastic enables CMMC compliance","_metadata":{"uid":"cs01f48ef8b1d59e3f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eElastic provides a \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003emodern platform with security and observability solutions\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e that aligns with CMMC’s core requirements, helping organizations efficiently \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003ecollect, analyze, and act on security-relevant data\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e in real time.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Centralized log management and SIEM","_metadata":{"uid":"cs7cac5d8e96ea1184"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCMMC mandates \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eaudit logging, continuous monitoring, and incident response\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e capabilities. Elastic Security provides a security information and event management (SIEM) solution that enables organizations to:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIngest and centralize logs\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e from multiple sources (endpoints, networks, applications, and cloud services).\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMonitor system and user activities\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to detect unauthorized access and potential threats.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eMeet retention requirements\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e by securely and affordably storing logs long term for forensic investigations.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"2. Continuous threat detection and response","_metadata":{"uid":"cs6e228429aaa90ab8"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCMMC requires proactive threat hunting and anomaly detection to ensure network security. Elastic’s machine learning-based detection capabilities empower security teams to:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eIdentify\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e anomalous user behavior and insider threats.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eAutomate \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ereal-time threat detection with prebuilt security rules and MITRE ATT\u0026amp;CK coverage.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRespond swiftly \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ewith\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003ecase management and automated remediation workflows.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"3. Endpoint security and Zero Trust implementation","_metadata":{"uid":"cs6e87cf7424628fe4"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAs organizations implement Zero Trust architectures, organizations must secure their endpoints and networks as well as ensure that they can see across the entire security ecosystem. Elastic can provide:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA unified data layer to connect Zero Trust pillars and systems, enabling end-to-end visibility\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBehavioral and signature-based malware prevention\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAdvanced endpoint detection and response (EDR) to stop threats before they escalate\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIntegration with Zero Trust frameworks by enabling continuous monitoring and identity-based access controls\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"4. Data protection and integrity monitoring","_metadata":{"uid":"cs145ce7c79fd95711"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCMMC emphasizes data protection through encryption, access controls, and integrity monitoring. Elastic helps enforce data security with:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eRole-based access controls (RBAC)\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to restrict unauthorized access to logs and sensitive data\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFile integrity monitoring (FIM)\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to detect unauthorized changes to critical files\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEncryption at rest and in transit\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e to ensure compliance with data protection requirements\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"5. Cloud security and compliance automation","_metadata":{"uid":"cs97f631c29a402ab1"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eHigher education institutions and defense contractors often use cloud-based environments. Elastic enables cloud-native security by:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eProviding real-time monitoring for AWS, Azure, and Google Cloud environments\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSupporting FedRAMP and CMMC-aligned security benchmarks\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAutomating compliance audits through Kibana dashboards and reporting features\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":" Why choose Elastic for CMMC compliance?","_metadata":{"uid":"cse1e873e38d4fb901"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e \u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eCost-effective compliance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic’s affordable data tiering provides powerful capabilities for cost-conscious organizations.\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eScalability and performance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic is built to handle massive volumes of security data while maintaining high-speed search and analytics.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eFlexibility:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic supports on-prem, hybrid, and cloud deployments, giving organizations the flexibility to meet compliance without vendor lock-in.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eOpen and extensible:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e Elastic’s open-source technology integrates with existing security tools and frameworks, enhancing security operations center (SOC) capabilities.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Next steps","_metadata":{"uid":"cs5bf1bc6e838809dd"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eCMMC compliance is critical for organizations working with the DoD, including universities engaged in defense research. Using Elastic’s Search AI Platform, organizations can efficiently meet CMMC’s rigorous security and monitoring requirements while enhancing overall cyber resilience.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBy using Elastic’s centralized logging, real-time threat detection, and cloud security capabilities, organizations can simplify compliance efforts and focus on their core mission while ensuring data protection and operational security.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIf you're looking to streamline CMMC compliance, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/contact/public-sector\"\u003e\u003cspan style='font-size: 12pt;'\u003econtact us to learn more\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e about implementing a tailored solution for your organization.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csbe1764eb20ced264"}}},{"callout":{"title_l10n":"","_metadata":{"uid":"cs6671dc91d014bb80"},"paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRelated resources:\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBlog: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/zero-trust-requires-unified-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eZero Trust requires unified data\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u0026nbsp;\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eEbook: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/public-sector/security-in-action-in-public-sector\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security: Public sector success stories\u003c/span\u003e\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","callout_reference":[],"callout_type":"Information (info)"}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs9216b84fb4398318"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csc5a408d112010966"}}}],"publish_date":"2025-02-24","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt4ce45bbfeeff0638","ACL":{},"created_at":"2021-07-12T21:53:30.326Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logs","label_l10n":"Logs","tags":[],"title":"Logs","updated_at":"2021-07-12T21:53:30.326Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.411Z","user":"blt4b2e1169881270a8"}}],"tags_industry":[{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}}],"tags_partner":[],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt811c827f06179c84","_version":1,"title":"Elastic Banner_6 (1).jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2025-02-24T16:31:33.206Z","updated_at":"2025-02-24T16:31:33.206Z","content_type":"image/jpeg","file_size":"158056","filename":"Elastic_Banner_6_(1).jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-24T16:45:09.054Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt811c827f06179c84/67bc9ee570e1ff66d373fe02/Elastic_Banner_6_(1).jpg"},"title":"How Elastic can help organizations achieve CMMC compliance","title_l10n":"How Elastic can help organizations achieve CMMC compliance","updated_at":"2025-02-24T16:31:59.527Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/elastic-cmmc-compliance","publish_details":{"time":"2025-02-24T16:45:08.641Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt172264fcf45db151","_version":6,"locale":"en-us","ACL":{},"abstract_l10n":"Generative AI is all the buzz, but what’s actually possible with this emerging technology? We’ll dive into 15 generative AI use cases to show what’s possible today — and provide inspiration to get you started with your own generative AI use cases.","author":["blt2914a3798eec2d59"],"category":["bltc17514bfdbc519df"],"created_at":"2024-06-24T01:51:36.498Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs62ce1898ad8c29c0"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(13, 13, 13);font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eThere’s a lot of chatter about \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e and what it can (and can’t) do. Generative AI, such as \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\"\u003e\u003cspan style='font-size: 12pt;'\u003elarge language models (LLMs\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e), creates original content by utilizing the patterns and structures it learned from extensive training data without storing the data itself. That includes creating things like text, software code, and art. While it can create content, it won’t be \u003c/span\u003e\u003ca href=\"https://www.fastcompany.com/91140608/the-next-phase-of-generative-ai-presents-a-golden-opportunity-for-businesses\"\u003e\u003cspan style='font-size: 12pt;'\u003ereplacing humans\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e any time soon.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eStill, it is reshaping the landscape of industries worldwide from enhancing cybersecurity defenses to personalizing customer experiences. In fact, 99% of surveyed organizations say that \u003c/span\u003e\u003ca href=\"https://www.elastic.co/pdf/platform/global-generative-ai-adoption-study.pdf\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI has the potential to drive change\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e in their organization.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLet's delve into ways \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/unlock-business-growth-data-driven-insights\" target=\"_self\"\u003e\u003cspan style='font-size: 12pt;'\u003egenerative AI unlocks new possibilities\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and transforms everyday business operations by assisting the humans who use it.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cimg alt=\"15 generative AI use cases for the enterprise\" src=\"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbeb7982f65e90086/669a8ba21e4e7e5aeab6a7ab/15-gen-ai.png\" height=\"auto\"/\u003e\u003cp\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI bolsters cybersecurity defenses","_metadata":{"uid":"csa8a303cc63c2141d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eGenerative AI acts as a force multiplier for cybersecurity teams. It makes advanced security measures more accessible to junior analysts through intuitive natural language interfaces, allowing them to learn and apply complex security concepts without needing to be an expert in code or mathematics. And it helps senior analysts combat the ever-growing threat landscape that is being \u003c/span\u003e\u003ca href=\"https://www.fastcompany.com/91125893/generative-ai-for-cybersecurity-is-it-right-for-your-organization\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003efueled by generative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eHere are some ways generative AI is transforming cybersecurity in threat detection, investigation, and response (TDIR):\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eThreat hunting: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eSay an analyst is trying to traverse through hundreds of alerts. What alerts are actual threats that need to be addressed? With generative AI, a security analyst can use the click of a button to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-driven-security-analytics\"\u003e\u003cspan style='font-size: 12pt;'\u003etriage hundreds of alerts\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e down to a few attacks.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced detection: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eAI models enhance the detection of anomalous behaviors through pattern recognition, behavioral analysis, and more. Using natural language, an analyst can ask if there are unusual login attempts, irregular file access, or other indicators of malicious activity.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003ePredictive analysis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e AI-driven systems can predict and identify potential vulnerabilities, suggesting proactive defenses before threats have a chance to make it through to your systems.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eAutomated reporting:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e In the event of a security incident, generative AI can automatically compile incident reports, including the nature of the incident, affected systems, potential impact, and recommended remediation steps. This empowers security analysts to take appropriate next steps.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/security/ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eDeep dive into AI for SecOps\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI improves operational resilience","_metadata":{"uid":"csbe9538683c3ac780"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eGenerative AI can also enhance how businesses monitor and understand their operational data through \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/aiops\"\u003e\u003cspan style='font-size: 12pt;'\u003eAIOps\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e — using AI to automate and streamline IT operations. Generative AI translates complex data sets into understandable insights through natural language, making it easier for non-experts and experts to make informed decisions, conduct root cause analysis, and limit downtime. Some key applications include:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eExplainability:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e For those needing domain-specific knowledge quickly, generative AI with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieval augmented generation (RAG)\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e capabilities can explain functions, logs, or traces in simple terms.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"}],"_metadata":{"uid":"csc0d932609284fd73"}}},{"image":{"image":{"uid":"blt3e42c95c7b008b10","_version":1,"is_dir":false,"ACL":{},"content_type":"image/png","created_at":"2024-06-24T01:50:34.233Z","created_by":"bltb6c155cd84fc0c1a","file_size":"628980","filename":"rag.png","parent_uid":null,"tags":[],"title":"rag.png","updated_at":"2024-06-24T01:50:34.233Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-06-27T13:00:00.915Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3e42c95c7b008b10/6678d0eab00d391b53e040c1/rag.png"},"_metadata":{"uid":"cscc69d66a8bd00ea3"},"caption_l10n":"","alt_text_l10n":"How retrieval augmented generation works","disable_lightbox":false,"remove_shadow":false,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cse67c0430a4cc9df3"},"header_style":"H2","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(13, 13, 13);font-size: 12pt;\"\u003e\u003cstrong\u003ePredictive maintenance:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(13, 13, 13);font-size: 12pt;\"\u003e In industries like automotive manufacturing, AI-driven predictive maintenance tools can help foresee and address system issues. Before a machine malfunctions, AI can predict and alert workers to address the problem before it affects the manufacturing process.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"color: rgb(13, 13, 13);font-size: 12pt;\"\u003e\u003cstrong\u003eData synthesis:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"color: rgb(13, 13, 13);font-size: 12pt;\"\u003e Data indicating application issues can come from many sources. Site reliability engineers can use AI tools to help synthesize information from various sources into actionable reports, streamlining data and root cause analysis.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/portfolio/operationalizing-generative-ai-strategic-guide\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGet the steps to implement generative AI at your organization\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI enhances customer experiences","_metadata":{"uid":"csdb8288bd93d56a0d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eGenerative AI is revolutionizing customer experiences by personalizing interactions and simplifying customers' information discovery process. Here are some ways generative AI is impacting the user experience:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eEnhanced search tools:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI search tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e help users quickly find precise information, whether they are customers seeking product recommendations or service reps needing protocol guidelines to help a customer. When users can find what they’re looking for, satisfaction increases.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eInteractive digital manuals: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eFor industries like consumer products (say, a video doorbell), AI chatbots can provide real-time, interactive guidance on product features and troubleshooting. This can improve user satisfaction and reduce support calls.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003ePersonalized recommendation systems:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e Generative AI can tailor product recommendations based on individual customer queries, enhancing personalization and satisfaction. In fact, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/improving-digital-customer-experiences/personalizations-critical-role-in-converting-ecommerce-searches-into-sales\"\u003e\u003cspan style='font-size: 12pt;'\u003e88% of online shoppers\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e are more likely to continue shopping on a retailer website that offers a personalized experience, including 96%of Gen Zers and 97% of millennials.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/learn/transform-customer-support-with-ai-powered-search\"\u003e\u003cspan style='font-size: 12pt;'\u003eTransform customer support with AI-powered search\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e"},{"title_l10n":"Generative AI use cases in action","_metadata":{"uid":"cs60b0829f733bdff1"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eOrganizations across industries are already benefiting from generative AI:\u003c/span\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eRetail: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eCustomers can type a project they’re working on like “building a cat tree” into a home improvement site’s search bar and receive a complete list of necessary supplies — getting expert recommendations while streamlining their buying experience.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eTelecom:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e Generative AI can proactively recommend and remediate network issues. Site reliability engineers can ask questions about network health and get answers in real time. This will reduce network downtime and emergency repair costs.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eFinancial services:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e Institutions can improve the accuracy and speed of fraud detection while reducing costs through task automation. By learning what behavior patterns to look out for, generative AI tools can help detect fraud while it’s happening in real time and suggest a next best action to the analyst to remediate.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003eTech: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eGenerative AI can accelerate product prototyping and design by augmenting the brainpower of humans to come up with more ideas, faster. This can help when creating new products, expanding services, and solving problems. Sales teams can use generative AI to create emails, summarize prospect interactions, and more. AI-assisted coding can help detect bugs in real time to lessen time to production.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e\u003cstrong\u003ePublic sector: \u003c/strong\u003e\u003c/span\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eGenerative AI can significantly accelerate mission outcomes, improve citizen services, and better connect government analysts and security professionals to the right data at the right time by securely connecting generative AI with agency data.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/customers/cisco\"\u003e\u003cspan style='font-size: 12pt;'\u003eLearn how Cisco creates AI-powered search experiences with Elastic on Google Cloud\u003c/span\u003e\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"https://www.elastic.co/generative-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eGenerative AI\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e is not about replacing human capabilities but enhancing and extending them. By improving processes across cybersecurity, observability, and customer experience, generative AI allows organizations in any industry to operate more efficiently, proactively, and responsively. As these technologies continue to evolve, the potential for transformative applications across industries seems boundless.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003eMake these use cases a reality. \u003c/span\u003e\u003ca href=\"https://www.elastic.co/portfolio/operationalizing-generative-ai-strategic-guide\"\u003e\u003cspan style='font-size: 12pt;'\u003eGet the steps to implement generative AI at your organization\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(13, 13, 13);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cscbdd94d5d20c231d"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs2cf89efc63bfc739"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cse68124c9f2d33d8f"}}}],"publish_date":"2024-06-27","sanity_migration_complete":false,"seo":{"seo_title_l10n":"15 enterprise generative AI use cases","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt8c57bf8be43a8f34","_version":1,"is_dir":false,"ACL":{},"content_type":"image/jpeg","created_at":"2024-06-24T01:51:34.908Z","created_by":"bltb6c155cd84fc0c1a","file_size":"148715","filename":"Office-building.jpg","parent_uid":null,"tags":[],"title":"Office-building.jpg","updated_at":"2024-06-24T01:51:34.908Z","updated_by":"bltb6c155cd84fc0c1a","publish_details":{"time":"2024-06-27T13:00:00.928Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt8c57bf8be43a8f34/6678d1263641c75d8a13a193/Office-building.jpg"},"title":"15 generative AI use cases for the enterprise","title_l10n":"15 generative AI use cases for the enterprise","updated_at":"2025-02-23T01:57:42.820Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/15-generative-ai-use-cases-enterprise","publish_details":{"time":"2025-02-23T01:57:48.246Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte31dda2d51acc398","_version":10,"locale":"en-us","ACL":{},"abstract_l10n":"The secret to sustainable business growth? Data-driven insights. We interviewed and surveyed 1,005 IT leaders to discover what it takes to continue to grow your business with the help of your data and AI strategy. ","author":["blt14f762eec103604e","blt2914a3798eec2d59"],"category":["bltc17514bfdbc519df"],"created_at":"2024-09-30T13:16:47.984Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc9d5a64db7f665ed"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eMaintaining a competitive edge can feel like a constant struggle as \u003c/span\u003e\u003ca href=\"https://docs.google.com/document/d/13TwXg33ekjP2-qekJfqBh5fSabF6Sb_6FKCT6hdgP7U/edit?tab=t.0\"\u003e\u003cspan style='font-size: 12pt;'\u003eIT leaders race to adopt artificial intelligence (AI)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e to solve their IT challenges and drive innovation. But with the right tools, processes, and strategies, your organization can make the most of your proprietary data and harness the power of data-driven insights and AI to accelerate your business forward.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUsing your data in real time at scale is key to driving business value. More than 80% of C-suite executives expect data and AI to improve productivity and revenue. But to get to those results, it is critical to invest in a strong data foundation that can manage exponentially growing data volumes and uncover insights on your customers, operations, products, and services.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAI and generative AI (GenAI) can be used to optimize your systems and experiences. But before reaching these next-generation technologies, you should focus on getting access to relevant real-time insights at scale to guide your decision-making.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBut don’t just take it from us. Here are \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003efive lessons from 1,005 IT leaders\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e on how to unlock business growth with data and AI.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 1: Prioritize data-driven insights to accelerate business innovation","_metadata":{"uid":"cs286709b0b73862db"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYour business runs on vast amounts of data. Everything in your operational environment continuously consumes and creates data from various sources: your applications, systems, services, and infrastructure. A data-driven approach is crucial for solving key business challenges and driving innovation — you can’t create exceptional customer experiences without understanding what your customers expect and want.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo outmaneuver competitors and truly accelerate business innovation, you need to understand your current state of operations and promising growth opportunities. This is achieved by not only collecting and analyzing your relevant data but also deriving data-driven insights from it. These \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-turn-data-into-actionable-insights\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eactionable insights\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e help you improve resilience, increase your productivity, and ultimately accelerate innovation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eFor example, you might get insight into customers abandoning their carts when they add a certain product. You can look into this and discover that the product listing had a bug and wasn’t allowing people to checkout.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eUnless you analyze it, all this useful information can get lost in storage, often leading to lost revenue opportunities or high operational costs. Creating a culture of data-driven, strategic decision-making needs to happen across the organization from every step of the process to uncover and solve existing business challenges and uncover value-creation opportunities that enable new revenue streams, enhance competitive advantage, and boost business growth. “Problems with \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ereal-time, scalable data utilization\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e impact business efficiency,” explains one technology decision-maker.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eAdopting a strategy to prioritize a culture of using data-driven insights across your organization lays the foundation for innovation.\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Transforming your data into actionable insights starts with reducing data silos and enabling data accessibility, which can lead to faster decision-making, increased productivity, and the edge to outperform your competitors.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 2: Make sure you’re satisfied with your data insights","_metadata":{"uid":"cs6b9e29189d8e8d32"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eNow, you may be getting insights from your data, but are you satisfied with those insights? Three out of five C-suite executives and decision-makers are \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eunsatisfied with the data insights available to them\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Delivering meaningful and actionable data analytics comes down to defining clear objectives and managing data volume. Too much data results in noise, but not enough data stretched across multiple silos makes \u003c/span\u003e\u003ca href=\"https://www.fastcompany.com/91140608/the-next-phase-of-generative-ai-presents-a-golden-opportunity-for-businesses\" target=\"_blank\"\u003e\u003cspan style='font-size: 12pt;'\u003econnecting the dots\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e very difficult.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfca5e94b76e4b148"}}},{"quotes":{"quote_l10n":"If data cannot be processed and analyzed quickly, it can lead to delayed decision-making, affecting critical aspects like customer service, product development, and marketing strategies.","_metadata":{"uid":"cs71d7bd83aa99f6b0"},"quote_author_l10n":"C-suite tech executive","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs7e2f32c45222a64e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSo, how do you make sure you’re satisfied with your data insights? Identify the areas of your organization where you would most benefit from having accurate, real-time insights. Focus first on solving any \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eunderlying data challenges\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e in these impact-making areas and then work on refining those insights with accuracy top of mind. The more accurate these insights are, the more helpful and valuable in a business context. \u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eImproved data insights can enhance decision-making, reduce risks, and increase operational efficiency.\u003c/strong\u003e\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 3: Take time to evaluate and enhance your data maturity","_metadata":{"uid":"csb7b14893672a150a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe hard truth is that 78% of C-suite leaders and IT decision-makers believe their organization is \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003emore advanced in data analytics and intelligence than their peers\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. In reality, there is a significant disconnect between the perceived and actual data maturity levels across organizations. Data maturity — how well an organization leverages data for business — can be broken down into \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/where-are-you-on-your-data-maturity-journey\"\u003e\u003cspan style='font-size: 12pt;'\u003efour stages\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e: capture, analyze, automate, and transform. By identifying where your organization stands in the data maturity framework, you can uncover the best ways to use your data and technology to achieve your business goals.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs2e82e6195a88d716"}}},{"quotes":{"quote_l10n":"We have data silos where different parts of the organization store data separately. This makes it hard to access and use data across departments.","_metadata":{"uid":"csec6ab1da9fcaacfb"},"quote_author_l10n":"Technology decision-maker in the public sector","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs6b8b417559b7289a"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eIf you’re facing a similar challenge, it’s likely your organization hasn’t reached the more advanced stages of the data maturity journey. And even if you have, the journey doesn’t end. It’s a constant quest to continuously innovate and operationalize with the power of your data. To begin your organization’s data maturity assessment, look to your data challenges: Are you dealing with excessive or insufficient volumes of data? Is it difficult to find information within your organization? Is your data taxonomy working for you?\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eBy \u003c/strong\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/advance-data-maturity-journey\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eevaluating and advancing through your data maturity\u003c/strong\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003e journey, you’re building a robust data foundation that aligns with your business goals.\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Aligning to business objectives is crucial to enable more informed and strategic decision-making and \u003ca href=\"https://www.elastic.co/lp/whats-possible-with-genai\" target=\"_self\"\u003euncover opportunities to use AI\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 4: Understand that GenAI comes second to good data practices","_metadata":{"uid":"csfdaf57cb496f3185"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/generative-ai/\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eGenAI\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e comes with the potential to unlock new automation capabilities, enhance your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/search-applications\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esearch applications\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, improve your \u003c/span\u003e\u003ca href=\"https://www.elastic.co/enterprise-search/customer-support\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003ecustomer experience\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, and give your employees time back to focus on strategic activities. It’s impressive and impossible to ignore — so, you’re probably under pressure from your board or leadership to implement new generative AI applications as soon as possible.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBut getting value out of GenAI starts with quality data practices. Your GenAI outputs are dependent upon the data you input. Quality in, quality out. Without the right data and without robust data practices, GenAI won’t help you move the needle, and you won’t see the benefits. The opposite is also true. With rich data inputs and streamlined organizational processes, you’ll glean equally rich insights.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eObtaining quality data begins with making use of your data — across environments, no matter the type of data (\u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/structured-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003estructured\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/unstructured-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eunstructured\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/structured-data#difference-between-structured-semistructured-and-unstructured-data\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003esemi-structured\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e). Building on a foundation of solid data practices, look for a solution that can process all your types of data from across your distributed architecture. Remember: \u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003ewith better data, you will get better AI outputs\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Lesson 5: Embrace GenAI for a competitive advantage","_metadata":{"uid":"cs3f301e348cc16286"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“AI is the future. Without it, we are dinosaurs. GenAI will allow our company to make smarter and more efficient decisions without having to sacrifice anything. GenAI is smart, constantly learning and evolving, and it can tell us what we are missing, where to look, and what to do,” says a technology decision-maker in the manufacturing industry. Recent developments in GenAI have added a whole new wave of dizzying GenAI-powered possibilities, and those who are able to embrace it will gain a host of advantages.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eOrganizations worldwide feel it: \u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003e93% of C-suite executives plan to invest or have already invested in\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e GenAI to improve productivity, operational resilience, customer experience and more.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eEarly (relatively speaking) adoption of GenAI can position your business ahead of competitors by creating new opportunities and driving innovation. \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eTo stay ahead of the adoption curve you first must have good data ready to go. Then, identify a high-impact use case that can benefit from the value of a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/open-source-llms-guide\"\u003e\u003cspan style='font-size: 12pt;'\u003elarge language model (LLM)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGetting the best results securely requires feeding your proprietary data to a generative AI algorithm using \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/retrieval-augmented-generation\"\u003e\u003cspan style='font-size: 12pt;'\u003eretrieval augmented generation (RAG\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e). This technique contextualizes the output of your organization, resulting in more accurate and relevant results.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Key takeaways from IT leaders","_metadata":{"uid":"cs1e32c57d6dbe12ee"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTo compete, grow, and innovate, organizations need a solid data foundation to accelerate the adoption of GenAI technologies. Your data and GenAI strategy should empower your customers and employees to make informed, data-driven decisions confidently.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eLearn what other IT leaders have had to say about their data and AI strategies\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csfcf950764c1273b3"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csd1686a36a9234b2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 10pt;'\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs76d0228983d2b772"}}}],"publish_date":"2024-10-09","sanity_migration_complete":false,"seo":{"seo_title_l10n":"Unlock business growth with data-driven insights: 5 lessons from IT leaders","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt2b0f2e0f79bee06a","_version":1,"title":"161778 - 2 Blog header images IT Wrapped Report blogs D2 copy_Option 5.png","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-09T13:52:26.075Z","updated_at":"2024-10-09T13:52:26.075Z","content_type":"image/png","file_size":"202006","filename":"161778_-_2_Blog_header_images_IT_Wrapped_Report_blogs_D2_copy_Option_5.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-10-09T16:30:40.711Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2b0f2e0f79bee06a/67068a9af2fbee375fe60337/161778_-_2_Blog_header_images_IT_Wrapped_Report_blogs_D2_copy_Option_5.png"},"title":"Unlock business growth with data-driven insights: 5 lessons from IT leaders","title_l10n":"Unlock business growth with data-driven insights: 5 lessons from IT leaders","updated_at":"2025-02-23T01:51:22.736Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/unlock-business-growth-data-driven-insights","publish_details":{"time":"2025-02-23T01:51:28.390Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt05d717ba5c495082","_version":14,"locale":"en-us","ACL":{},"abstract_l10n":"CIOs face mounting IT challenges like data silos and manual processes, hindering business growth. GenAI and data-driven solutions offer relief, but leaders must address their data management issues to unlock GenAI's full potential for innovation.","author":["blt14f762eec103604e","blt2914a3798eec2d59"],"category":["bltc17514bfdbc519df"],"created_at":"2024-10-08T02:22:35.913Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csbc8734cb465d8215"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eAmid budget constraints, labor shortages, and the need to do “more with less,” CIOs and IT leaders are facing common IT problems that transcend industries. From poor data accessibility to changing customer expectations, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/ai-adoption-lessons-from-it-leaders\"\u003e\u003cspan style='font-size: 12pt;'\u003eIT leaders are turning to generative AI (GenAI)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as an answer to their problems.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eContinuous investments in GenAI promise companies new ways to solve key business problems and build revenue-generating streams. But for most, the key to reaping the benefits of GenAI is hidden in plain sight: data. Data is at the heart of IT innovation, but most businesses today aren’t using their data to its full potential. Investing in a robust data foundation is critical to leverage GenAI to optimize business workflows and innovate. Read on to discover what other challenges IT leaders are facing.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Difficulty getting insights from data","_metadata":{"uid":"cs2ccc9ca2d5c159e2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eA substantial 69% of C-suite executives and decision-makers cite the \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003einability to use data continuously\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — in real time and at scale — as a significant hurdle contributing to their company’s business challenges. The result is a lack of real-time insights that forces leaders to rely on their intuitions rather than evidence. This hinders decision-making and stifles growth and efficiency. Operationalizing data isn’t a one-time job. You need tools that can grow as your data does while giving you visibility into your systems.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e“We have data silos across the business and are not able to consolidate [them to] have a single pane of glass to make decisions,” explains a \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003etelecommunications C-suite executive\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e.\u0026nbsp;\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eThe feeling is supported by data: 60% of organizations are \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eunsatisfied with the data insights they have today\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e with only 35% leveraging data insights daily for business decisions. The inability to make real-time, data-driven business decisions is due to underlying data challenges, with 98% of leaders struggling with some combination of data problems. Notably, 67% of organizations are struggling with separate data solutions for different environments, and in most cases, this is due to inefficient data management. This is partly caused by a lack of adequate tools to manage disparate systems and software — another challenge IT leaders face today.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003cbr /\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eGetting insights from data is resource-intensive. It requires time, expertise, and clear objectives and must be integrated into IT development processes. Once you’ve collected relevant data, it takes data analytics and analysis, often with GenAI, to get \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/how-to-turn-data-into-actionable-insights\"\u003e\u003cspan style='font-size: 12pt;'\u003eactionable insights\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Actionable insights offer specific measures and steps that can help you achieve a goal by telling you what to do based on your data. With the precision of search and the intelligence of AI —\u0026nbsp; including \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/machine-learning\"\u003e\u003cspan style='font-size: 12pt;'\u003emachine learning (ML)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/natural-language-processing#:~:text=NLP%20techniques%20help%20computers%20analyze,a%20subspecialty%20of%20computational%20linguistics.\"\u003e\u003cspan style='font-size: 12pt;'\u003enatural language processing (NLP)\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — you can transform raw proprietary data into actionable insights to accelerate your business outcomes.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"2. Lack of adequate tools","_metadata":{"uid":"cs5c04fdcdfbac300c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eTraditionally, organizations have continued to invest in tools that serve a specific purpose based on the needs of the business. However, this conventional technical investment process leads to unplanned isolation and/or duplication of data, information, work, and costs. The result of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/tool-consolidation\"\u003e\u003cspan style='font-size: 12pt;'\u003etool sprawl\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e further inhibits cross-functional collaboration, disables end-to-end visibility of your current environment, and overall creates organizational silos.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLegacy systems can also play a part in tool sprawl. Organizations must balance the cost of phasing these systems out with the cost of keeping them active. And because phasing them out can prove much more expensive, companies remain reliant on legacy systems. As a result, their teams might get stuck with tools that aren’t the most performant and useful for their use cases today. This may mean that all the tools don’t “connect” and speak to each other, ultimately hindering access to real-time, relevant information and digital transformation.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eIn the case of observability and security — practices that share data — redundant work and disparate tools can be detrimental to operations, compromising productivity and security while negatively impacting revenue.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBottom line: inefficient tools and processes create bottlenecks, leading to slower workflows, wasted resources, and increased operational costs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cbr /\u003eIn response to this challenge, 56% of C-suite executives \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eprioritize investment in data tools and technology\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e as a top solution. More specifically, you have everything to gain from \u003c/span\u003e\u003ca href=\"https://www.elastic.co/observability/tool-consolidation\"\u003e\u003cspan style='font-size: 12pt;'\u003econsolidating your tools\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e and investing in ones that can democratize access to data from multiple environments across organizational silos.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"3. Too much time spent on manual work and analysis","_metadata":{"uid":"csda9d7ff280b3d50c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e“If data cannot be processed and analyzed quickly, it can lead to delayed decision-making, affecting critical aspects like customer service, product development, and marketing strategies,” explains a technology company C-suite executive. Inefficiencies hinder productivity and even slow down innovation while IT departments bear the brunt of tool sprawl and data silos.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWithout the right easy-to-use tools and processes, teams often spend a lot of time on excessive manual work and analysis to get the output they need. Not only does this stifle efficiency and productivity, but it also often hinders innovation.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eYou hire the best people — why keep them stuck doing inefficient tasks instead of innovating? If teams had the right tools, they could save time on manual routine tasks and instead focus on more value-added activities that drive business growth. Repetition and inefficiencies can often lead to \u003c/span\u003e\u003ca href=\"https://www.elastic.co/interactive/cybersecurity-analyst-burnout-quiz\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eburnout\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e and can exacerbate valuable talent. Building solutions and tools that allow teams to quickly approach laborious tasks and integrate with existing workflows can lead to better employee satisfaction,\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e*\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e retention, and business efficiency. Using tools that do not support your teams can lead to a loss of productivity, reputation, and revenue.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003cstrong\u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eTaking a people, processes, and technology (PPT) approach to investing in technology and tools can help you build better workflows that prioritize automating repetitive tasks, ultimately leading to increased efficiency, cost savings, and a more agile, innovative organization. By analyzing and redesigning workflows, organizations can identify bottlenecks and inefficiencies, creating streamlined processes that are documented and standardized for consistency.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSelecting the right tools that integrate seamlessly with existing systems and leveraging advanced technologies like GenAI and machine learning further optimize automation capabilities. This approach not only improves accuracy and reduces costs but also enhances organizational agility and employee satisfaction, ultimately providing a competitive advantage in the market.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"4. Lack of operational resilience","_metadata":{"uid":"csdf275f59a3a93542"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOutages are a business's worst nightmare — especially considering the average cost of downtime can be as high as $9,000 a minute.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e*\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/operational-resilience\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eOperational resilience\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e helps businesses weather disruptions by minimizing downtime and preventing potential crises. Resilient companies adapt faster to market changes and outperform competitors during and after a crisis.\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003csup\u003e*\u003c/sup\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e In other words, operational resilience is good for business.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eSuccessful data management and practices are at the heart of operational resilience, yet establishing it is a challenge for many businesses. Without the proper tools, practices, and experts, business data is a burdensome anchor rather than a sail. As a result, organizations are vulnerable to frequent disruptions, delays, and downtime, which impact resilience, increase business risk, reduce productivity, and drive up costs.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eSolution:\u003c/strong\u003e\u003cstrong\u003e\u003cbr bold=\"[object Object]\"/\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWithout the ability to proactively get ahead of disruptions and outages, organizations are locked in a reactive stance and forced to play catch-up. AI can put you ahead of the game with predictive resilience models. By analyzing trends in your data, it can spot potential issues before they occur. Putting out fires big and small ultimately affects end-user productivity and revenue from customer-facing services.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAchieving operational resilience begins with a robust data foundation rather than a disparate collection of fragmented tools and systems. By prioritizing data infrastructure, you can empower your teams with actionable, real-time insights to take on a proactive approach that drives business growth and ensures that your revenue-generating applications are up and running.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"5. Not able to effectively mitigate cybersecurity threats","_metadata":{"uid":"cs5353daa763534bd2"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eGenAI has many potential advantages, but it has also fostered the rise of a new generation of cyber threats. The use of GenAI in both official and unofficial capacities has also intensified and fueled these \u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/cyber-threat-research\"\u003e\u003cspan style='font-size: 12pt;'\u003ecybersecurity threats\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e. Often understaffed in the security domain or underskilled in the face of rapidly evolving AI technologies, organizations see negative business impacts: reactive measures lead to high-risk exposure, financial loss, legal issues, reputational damage, and lost customer trust.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eEffectively mitigating these cybersecurity threats requires specialized skills that are in high demand and very difficult to come by. Organizations must also update security monitoring practices to reach across data silos and offer security teams a 360° view into their systems and operations.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs3f583fd508cadc0d"}}},{"quotes":{"quote_l10n":"Market is trending, technology is dynamic, and it gives rise to new-gen digital crimes. We want [to] be up to the mark per industry standards by equipping ourselves with the latest cybersecurity knowledge and implementations.","_metadata":{"uid":"cs6516caba71853163"},"quote_author_l10n":"C-suite executive, technology industry","quote_details_l10n":""}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs92347fdcd431911c"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003eSolution:\u003cbr /\u003e\u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003eSo, while GenAI may be exacerbating the challenge of keeping up with new threats, it may also be the solution to mitigating them more effectively. More than half (59%) of leaders have already invested in \u003c/span\u003e\u003ca href=\"http://www.elastic.co/resources/portfolio/report/5-insights-csuite-leaders-data-ai\"\u003e\u003cspan style='font-size: 12pt;'\u003eAI and ML-driven security automation technologies\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, and 96% believe that using GenAI security assistants that can proactively detect and remediate network issues and threats will drive value to their organizations. Generative AI has the potential to help close the expertise gap in the security sector and fill security roles when applied to a robust data infrastructure.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eUltimately, it all comes down to data. Leaders are dealing with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/\"\u003e\u003cspan style='font-size: 12pt;'\u003edata challenges\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e — from sprawl and silos to a lack of adequate tools and an insufficient workforce — which compound observability, security, and resilience challenges. It’s no wonder then that C-suite executives and leaders are prioritizing GenAI solutions and data analytics tools as their top technology investments.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"Take the data and AI assessment","_metadata":{"uid":"cs76ccb25e6aa2537b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eLeaders across many organizations struggle with similar business and data challenges, all while looking to AI and GenAI for new opportunities. To identify areas of improvement and investment, reflecting on existing challenges and understanding your competitors is the best place to start to develop a strategic plan to stay competitive.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/resources/interactive/data-and-ai-strategy-assessment\"\u003e\u003cspan style='font-size: 12pt;'\u003eSee how you stack up against your peers in AI investments, business challenges, and opportunities\u003c/span\u003e\u003c/a\u003e\u003cspan style='color:rgb(37, 99, 235);font-size: 12pt;'\u003e.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs76a74120492272e6"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs503ef0b072aeb72b"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cem\u003eOriginally published on October 8, 2024; Updated on December 12, 2024.\u003c/em\u003e\u003c/p\u003e"},{"title_l10n":"","_metadata":{"uid":"cs15423df415b4bf9e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e*\u003ca href=\"https://www.salesforce.com/blog/automation-trend-employee-experience/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003e89% Of Your Employees Could Benefit With This One Change\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, Salesforce. 2022.\u003cbr /\u003e\u003c/span\u003e*\u003ca href=\"https://www.forbes.com/councils/forbestechcouncil/2024/04/10/the-true-cost-of-downtime-and-how-to-avoid-it/\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eThe true cost of downtime (and how to avoid it)\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, Forbes. 2024.\u003cbr /\u003e\u003c/span\u003e*\u003ca href=\"https://www.mckinsey.com/capabilities/risk-and-resilience/our-insights/resilience-for-sustainable-inclusive-growth\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 10pt;\"\u003eResilience for sustainable, inclusive growth\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 10pt;\"\u003e, McKinsey. 2022.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eIn this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 10pt;\"\u003e\u003cem\u003eElastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1ae42d25568a3208"}}}],"publish_date":"2024-12-12","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[],"thumbnail_image":{"uid":"blt4b8871540ff04df3","_version":1,"title":"161778 - 2 Blog header images_ IT Wrapped Report blogs 2.jpg","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-10-08T01:34:02.761Z","updated_at":"2024-10-08T01:34:02.761Z","content_type":"image/jpeg","file_size":"161652","filename":"161778_-_2_Blog_header_images_IT_Wrapped_Report_blogs_2.jpg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-12-12T18:54:58.555Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4b8871540ff04df3/67048c0a5ff78d32dc8f0977/161778_-_2_Blog_header_images_IT_Wrapped_Report_blogs_2.jpg"},"title":"Top 5 IT challenges leaders are facing (and solutions to them)","title_l10n":"Top 5 IT challenges leaders are facing (and solutions to them)","updated_at":"2025-02-23T01:47:26.428Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/top-5-it-challenges-leaders-face-solutions","publish_details":{"time":"2025-02-23T01:47:31.355Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt8fe894b6a0645be6","_version":18,"locale":"en-us","ACL":{},"abstract_l10n":"If you aren’t able to replace your existing SIEM outright, that doesn’t mean you can’t supplement its capabilities with a more performant solution. Elastic allows all users to try out a new, powerful SIEM with little to no upfront cost.","author":["blt1f84830916c3ddfe"],"category":["bltc17514bfdbc519df"],"created_at":"2022-10-12T21:04:03.885Z","created_by":"bltc87e8bcd2aefc255","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"csc6feb1ba5f37d50d"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eSecurity teams with an existing security information and event management (SIEM) investment may find themselves having to pay more to their vendor in order to ingest and index more of their data. In fact, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/explore/security-without-limits/cybersecurity-solutions-riskier-world\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003enearly half\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e (44%) of organizations want to augment or replace their current SIEM solution.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIt may be time to replace your SIEM.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eFortunately, Elastic allows all users to try out a new, powerful SIEM with little to no upfront cost. The solution takes an \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/why-the-best-kind-of-cybersecurity-is-open-security\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eopen approach\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, and data is free to ingest — empowering teams to experience what it feels like to gather unlimited data under a single solution.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eAnd with \u003c/span\u003e\u003ca href=\"https://www.elastic.co/elasticsearch/ai-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, security practitioners of every skill level benefit from automated threat protection, alert investigation, incident response, and more. It also makes the SIEM migration process much easier for teams to execute.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eSo do you need to replace? Here we establish five pain points that may confirm your need for SIEM replacement.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e1. Ingesting and storing data is cost-prohibitive\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf your current SIEM vendor is charging you for data storage, you’re likely leaving a lot of vital contextual data untapped for the sake of budget. Unfortunately, without fast access to activity data and context, your team’s ability to properly protect your organization is limited.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e2. Investigations are running slow\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf your team’s queries are taking hours, it’s time to consider a more modern tool to help get the answers you need in real-time. Thanks to the rapid advancement of \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/large-language-models\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003elarge language models\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, the rest of the world is able to summon responses to queries for just about any request in seconds. You should expect a SIEM solution that does the same for your investigations.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e3. Stagnant platform\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eMany legacy SIEMs weren’t built to adjust to your team’s specific style of work and have a hard time adapting to the latest breed of threat types. While the flexibility to build custom integrations, dashboards, and workflows for a variety of outcomes is a strong plus, the need to defend against a new landscape of AI-intensified threats is essential. Rather than resting on past laurels, be sure your SIEM vendor is dedicated to constant innovation in an environment of quick change.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e4. On-prem only\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eIf your current SIEM solution can’t keep pace with a multi-cloud world, you’ll need a complementary tool to help you achieve the scalability and automation that only a modern SIEM can provide.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003e5. Limited user community\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eWithout an open approach to security, your vendor may not be integrating input from the broader user community. This inhibits contributions and feedback that would otherwise ensure the SIEM is continuously innovating to meet an ever-evolving landscape of cyber threats.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eLegacy SIEMs just don’t cut it\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eMany of the challenges teams are experiencing with their current SIEM offerings stem from the foundational infrastructure those SIEMs were built upon. The requirements of SIEM have vastly outgrown the traditionally static collection, storage, and analysis of security data. Organizations need dynamic and actionable insights into that data, environment-wide correlations, integrated threat intelligence, and real-time investigative capabilities to drill down into areas of concern.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eWith teams continuously integrating cloud services, the attack vector further expands. Now, monitoring across users, apps, behavior, and much more is all part of practitioners’ daily routine.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e“As workloads migrate to the cloud, monitoring cloud deployments becomes essential to the business,” said Mandy Andress, CISO at Elastic. “Some older SIEMs needed a lot of care and feeding. Today's IT environments provide a firehose of data. While traditional SIEMs can ingest a lot of data, they don't embed analytics; it could take hours or days to analyze that data, which impacts the ability to quickly investigate suspicious activity.”\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eMoving forward with replacement\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eOnce you’ve decided to replace your SIEM, the natural next step is to find a highly scalable and flexible platform with which to collect, visualize, and analyze all security-related event logs. This new solution also has to have the ability to selectively forward the raw and/or converted logs back to your existing SIEM in order to satisfy compliance requirements.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eThe replacement approach does not immediately eliminate the need for your original SIEM, as it still provides the complex correlation rules, case workflow and incident response management, and compliance reporting capabilities you’ve established over months or years of fine-tuning.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith Elastic \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003ealongside your existing SIEM, \u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eyour team can modernize security operations — harnessing data at cloud speed and scale to effectively detect, investigate, and respond to evolving threats. With Elastic’s \u003c/span\u003e\u003ca href=\"https://www.elastic.co/pricing/philosophy\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eresource-based pricing philosophy\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e, users don’t need to pay for ingesting data, thereby lowering the barrier to entry for teams looking to feel out the solution before investing further resources.\u003c/span\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch2\u003eReal-world use case\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eUSAA augmented its SIEM using Elastic and immediately started noticing results. USAA’s first quick win occurred during an interactive investigation wherein the team was analyzing web proxy bandwidth consumers. They quickly noticed excessive bandwidth consumption and, within a couple minutes, identified the source of network misuse.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eUSAA’s second quick win came from near-real-time investigation afforded by the \u003c/span\u003e\u003ca href=\"https://www.elastic.co/what-is/elk-stack\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003espeed Elastic is renowned for\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e. The team detected a customer-facing app that was being scanned over the network and identified the source of port scanning activity within 2–3 minutes. The existing SIEM, by comparison, was only 2% complete with the initial search within the same timeframe.\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eFrom this shift in passive data gathering to active investigation, USAA transformed its team from security “gatherers” to “hunters” by using Elastic. Advance your own team’s security maturity on a \u003c/span\u003e\u003ca href=\"https://www.elastic.co/siem/\" target=\"_self\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eunified, open platform for SIEM\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e and \u003ca href=\"https://www.elastic.co/security/siem\" target=\"_self\"\u003esecurity analytics\u003c/a\u003e.\u003c/span\u003e\u003c/p\u003e\u003ch2\u003eLet’s get you up to speed\u003c/h2\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003eSIEM replacement is a process, and our security experts are here to see you through it and help you achieve the results you’re hoping for.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 12pt;\"\u003e\u003ca href=\"https://www.elastic.co/blog/how-elastic-security-drive-value-organization\" target=\"_self\"\u003eLearn how Elastic Security delivers business impact.\u003c/a\u003e \u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"color: rgb(29, 28, 29);font-size: 12pt;\"\u003e\u003cem\u003eOriginally published October 19, 2022; updated February 22, 2025.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1fe59011ff839cdc"}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs401ec3be09eccdcb"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"color: rgb(52, 55, 65);font-size: 10pt;\"\u003e\u003cem\u003eThe release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"csd9173c02a3841f03"}}}],"publish_date":"2024-01-16T16:00:00.000Z","sanity_migration_complete":false,"seo":{"seo_title_l10n":"How to replace your SIEM","seo_description_l10n":"If you aren’t able to replace your existing SIEM outright, that doesn’t mean you can’t supplement its capabilities with a more performant solution. Elastic allows all users to try out a new, powerful SIEM with little to no upfront cost.","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}},{"title":"SIEM","label_l10n":"SIEM","keyword":"siem","hidden_value":false,"tags":[],"locale":"en-us","uid":"blta7a92715fa2dc7aa","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-07-12T21:52:53.275Z","updated_at":"2021-07-12T21:52:53.275Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-10-07T18:59:30.492Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt0e7c39f65cbd3755","ACL":{},"created_at":"2023-11-06T20:37:20.943Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"data-ingestion","label_l10n":"Data ingestion","tags":[],"title":"Data ingestion","updated_at":"2023-11-06T20:37:20.943Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.173Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt47414afcde70b058","ACL":{},"created_at":"2023-11-06T20:43:45.793Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-security","label_l10n":"Open security","tags":[],"title":"Open security","updated_at":"2023-11-06T20:43:45.793Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:27.618Z","user":"blt06083bb707628f5c"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Anomaly detection","label_l10n":"Anomaly detection","keyword":"anomaly-detection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7478459fe32592c5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:06.777Z","updated_at":"2023-11-06T20:08:06.777Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.738Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"uid":"blt020047acd65b5e53","_version":1,"created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2024-02-01T15:28:08.204Z","updated_at":"2024-02-01T15:28:08.204Z","content_type":"image/png","file_size":"116720","filename":"elastic_de_140615_blogheaderimage_isittimetoreplaceyoursiem_D1_V1.png","title":"elastic_de_140615_blogheaderimage_isittimetoreplaceyoursiem_D1_V1.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-02-01T15:28:15.675Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt020047acd65b5e53/65bbb8885cdaec00163b9e6d/elastic_de_140615_blogheaderimage_isittimetoreplaceyoursiem_D1_V1.png"},"title":"Is it time to replace your SIEM?","title_l10n":"Is it time to replace your SIEM?","updated_at":"2025-02-23T01:14:38.915Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/five-signs-you-need-to-replace-your-siem","publish_details":{"time":"2025-02-23T01:14:45.211Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfd16d81e69072c5e","_version":19,"locale":"en-us","ACL":{},"abstract_l10n":"With our new Elastic Security Value Calculator, you can easily estimate how Elastic can drive financial gains for your organization. Based on your results, you’ll know how Elastic Security creates efficiencies for you.","author":["blteeaceaae851afa34","blt8f7db4157fab33b3","blt14f762eec103604e"],"category":["bltc17514bfdbc519df"],"created_at":"2023-06-29T17:40:37.694Z","created_by":"bltb6c155cd84fc0c1a","markdown_l10n":"","modular_blocks":[{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs98ca95e1bd689c01"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003ca href=\"https://www.elastic.co/security\"\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e is used by more than 50% of Fortune 500 companies, minimizes TCO, and delivers a modern approach to detection, investigation, and response to increase security team efficiency. For organizations looking to strengthen defenses by getting access to real-time insights, Elastic Security, \u003c/span\u003e\u003ca href=\"https://www.elastic.co/platform\"\u003e\u003cspan style='font-size: 12pt;'\u003ebuilt on a Search AI Platform\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e, offers visibility across the entire attack surface to help you meet your business objectives.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How Elastic leverages Elastic Security","_metadata":{"uid":"cs5b35d6838f065c52"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eBefore explaining the value drivers, let's hear from our Elastic CISO Mandy Andress.\u0026nbsp; Mandy compares her viewpoint and experiences consolidating tech stacks for a Fortune 100 firm and Elastic with an 87.5% faster time-to-market.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs4627103be9ba622d"}}},{"video":{"vidyard_uuid":"SEZoJSYdjsqg5mNSYnMyWb","_metadata":{"uid":"cs2f68aaee064f2c58"},"caption_l10n":"","shadow":false,"video_play_count":"","muted":false,"loop_video":false,"hide_controls":false,"looping_animation":false}},{"code":{"code":"Video transcript:\n\nHi, all. I'm Mandy, Elastic’s CISO. Before I compare the above outcomes, let me first share my perspective for context. Fundamentally, I see security as a data problem, and I'm often asked, what keeps you up at night? I always give the same answer: what do I not know? There are so many things changing and happening in the global threat environments and our overall environment that I'm always concerned about what we are missing. What actions should we be taking that we don't have the visibility or are just not looking at with the correct perspective? With that in mind, I try to build a diverse team that brings different skills and different perspectives and stays really connected with the community.\n\nBut there will always be things that we don't know. And how do we learn that? How do we apply Elastic and the power of the ELK stack to provide us that visibility? Elastic helps our organization uncover some of those unknown unknowns with data. There are so many great stories I can tell you about how Elastic enables organizations to do that. But fundamentally, it's a mindset shift. How do you transition from focusing on discrete activities that you don't want to see happening in your environment to really understanding the baseline of how your environment should be behaving and what anomalous activities are occurring that you should investigate? With today's scale and overall significant amounts of data. Elastic provides the ability to quickly process significant amounts of data at scale. That speed, combined with our machine learning and generative AI capabilities, means we don't have to do it the same way. When you replace the tech stack for your SOC. These combined capabilities are some of the most powerful I have seen and some of the easiest to configure just out of the box, turning on machine learning rules. We gain significantly more insight than organizations can achieve with the traditional SIEM. We're all awaiting the addition of Elastic Security Assistant that utilizes generative AI to shorten the learning curve of analysts.\n\nBefore Elastic, I was working at a Fortune 100 firm. We wanted to completely rebuild our SOC and expand to provide global 24x7 support. We were ingesting daily about five terabytes of data with 50,000 events per second. Additionally, we had daily bursts, occasionally reaching 100,000 events per second. We knew we wanted detection and analysis with some behavioral analytics. We wanted to start moving into anomalous behavior. Understanding what was suspicious about our environment, whether it was a user or a machine. Getting all of that stood up took us three tools, 24 months, millions of dollars in licenses, and even millions of dollars more in services. And after 24 months, we were functional, but we still had a lot of work to do to get us to our desired end state. \n\nWhen I started at Elastic, I was looking to achieve the same thing, and we were able to do that with one product and one license, Elastic. We’re known to Elasticians as customer zero. We start testing and consuming capabilities as soon as possible. In that first three months, we were ingesting about 32 terabytes of data daily, 350,000 events per second. And we only had four SOC analysts distributed across the globe. From an information security perspective, we were up and running in three months versus 24. Not to mention that our current architecture is ingesting daily 200 terabytes of data, but this story doesn't tell us the rest of the power across the environment. Utilizing cross-cluster search on petabytes of data across multi-cloud and on-prem environments, searching many, many petabytes of data in just under 30 seconds. \n\nThis provides insights allowing us to respond to real-time events like Log4j and helps us provide data analysis to answer some of those questions to help ensure that we're knowing what's happening in our environment and identifying, as best we can, those unknown unknowns. With elastic security, we've seen clear productivity gains, risk reductions, and cost savings, and we look forward to continuing on this journey to improve the security of elastic. I encourage you to evaluate the gains your organization can achieve using elastic. Thank you.","_metadata":{"uid":"cs8bdf533f21337cdf"}}},{"title_text":{"title_text":[{"title_l10n":"Video transcript:","_metadata":{"uid":"cs63681349deefa00d"},"header_style":"H3","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eHi, all. I'm Mandy, Elastic’s CISO. Before I compare the above outcomes, let me first share my perspective for context. Fundamentally, I see security as a data problem, and I'm often asked, what keeps you up at night? I always give the same answer: what do I not know? There are so many things changing and happening in the global threat environments and our overall environment that I'm always concerned about what we are missing. What actions should we be taking that we don't have the visibility or are just not looking at with the correct perspective? With that in mind, I try to build a diverse team that brings different skills and different perspectives and stays really connected with the community.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eBut there will always be things that we don't know. And how do we learn that? How do we apply Elastic and the power of the ELK stack to provide us that visibility? Elastic helps our organization uncover some of those unknown unknowns with data. There are so many great stories I can tell you about how Elastic enables organizations to do that. But fundamentally, it's a mindset shift.\u0026nbsp; How do you transition from focusing on discrete activities that you don't want to see happening in your environment to really understanding the baseline of how your environment should be behaving and what anomalous activities are occurring that you should investigate? With today's scale and overall significant amounts of data. Elastic provides the ability to quickly process significant amounts of data at scale. That speed, combined with our \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003emachine learning\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e and \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003egenerative AI\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e capabilities, means we don't have to do it the same way. When you replace the tech stack for your SOC. These combined capabilities are some of the most powerful I have seen and some of the easiest to configure just out of the box, turning on machine learning rules. \u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003ca href=\"https://www.elastic.co/blog/security-teams-prebuilt-protections\" target=\"_self\"\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eWe gain significantly more insight\u003c/em\u003e\u003c/span\u003e\u003cem\u003e\u003c/em\u003e\u003c/a\u003e\u003cem\u003e\u003c/em\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e than organizations can achieve with the traditional SIEM. We're all awaiting the addition of \u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/guide/en/security/current/security-assistant.html\" target=\"_self\"\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eElastic Security Assistant\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e that utilizes generative AI to shorten the learning curve of analysts.\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eBefore Elastic, I was working at a Fortune 100 firm. We wanted to completely rebuild our SOC and expand to provide global 24x7 support. We were ingesting daily about five terabytes of data with 50,000 events per second. Additionally, we had daily bursts, occasionally reaching 100,000 events per second. We knew we wanted detection and analysis with some behavioral analytics. We wanted to start moving into anomalous behavior. Understanding what was suspicious about our environment, whether it was a user or a machine. Getting all of that stood up took us \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003ethree tools\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e, \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e24 months\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e, \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003emillions of dollars in licenses\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e, and even \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003emillions of dollars more in services\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e. And after 24 months, we were functional, but we still had a lot of work to do to get us to our desired end state.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eWhen I started at Elastic, I was looking to achieve the same thing, and we were able to do that with one product and one license, Elastic. We’re known to Elasticians as customer zero. We start testing and consuming capabilities as soon as possible. In that first three months, we were ingesting about \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e32\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e terabytes\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eof data daily, \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e350,000\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003eevents per second\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e. And we only had \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003efour SOC analysts\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e distributed across the globe. From an information security perspective, we were up and running in \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003ethree months\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e versus 24. Not to mention that our current architecture is ingesting daily \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e200 terabytes\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e of data, but this story doesn't tell us the rest of the power across the environment. Utilizing \u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003ecross-cluster search\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e on petabytes of data across multi-cloud and on-prem environments, searching many, many petabytes of data in just under 30 seconds.\u0026nbsp;\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e\u003cp\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003eThis provides insights allowing us to respond to real-time events like Log4j and helps us provide data analysis to answer some of those questions to help ensure that we're knowing what's happening in our environment and identifying, as best we can, those unknown unknowns. With elastic security, we've seen clear productivity gains, risk reductions, and cost savings, and we look forward to continuing on this journey to improve the security of elastic. I encourage you to evaluate the gains your organization can achieve using elastic. Thank you.\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003c/em\u003e\u003c/span\u003e\u003cspan style=\"font-size: 11pt;\"\u003e\u003cem\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs60439709366aea45"}}},{"image":{"image":{"uid":"blt918f8a12fe2e4b13","created_by":"bltb6c155cd84fc0c1a","updated_by":"bltb6c155cd84fc0c1a","created_at":"2023-06-29T17:08:28.171Z","updated_at":"2023-06-29T17:08:28.171Z","content_type":"image/png","file_size":"198437","filename":"elastic-blog-24-3-months.png","title":"elastic-blog-24-3-months.png","ACL":{},"_version":1,"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-29T19:52:44.659Z","user":"bltb6c155cd84fc0c1a"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt918f8a12fe2e4b13/649dba8c4a3adf2f8b0532ec/elastic-blog-24-3-months.png"},"_metadata":{"uid":"cs95f9028f8f215450"},"caption_l10n":"","alt_text_l10n":"24 months 3 months chart","disable_lightbox":false,"remove_shadow":true,"sizing":{"sizing_options":null}}},{"title_text":{"title_text":[{"title_l10n":"","_metadata":{"uid":"cs39807285793f8f2f"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eCurious to see how your team compares?\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003ca href=\"https://www.elastic.co/security/value-calculator\"\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cstrong\u003e \u003c/strong\u003e\u003c/span\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003eTry out our interactive value calculator\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e\u003cem\u003e\u003cstrong\u003e.\u003c/strong\u003e\u003c/em\u003e\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs1f6e870dc4778bc1"}}},{"title_text":{"title_text":[{"title_l10n":"Value drivers for security teams","_metadata":{"uid":"cs5937075ed2bcc2ae"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eModern security solutions typically drive values in these four primary areas:\u003c/span\u003e\u003c/p\u003e\u003col\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eCosts savings:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e This includes any monetary savings from reducing the total cost of ownership of technology that directly impacts the bottom line.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRisk reduction:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Here, we quantify the value of reducing the likelihood and severity of security incidents with Elastic. Elastic looks to identify potential risks before they occur, allowing your organization to uncover any additional financial benefits that allow you to retain losses.\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eProductivity gains:\u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003e Elastic boosts productivity by accelerating analysis, facilitating collaboration, and automating key steps. These gains improve efficiency, accelerate decision-making, and allow organizations to redistribute resources to new projects.\u0026nbsp;\u003c/span\u003e\u003c/p\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003e\u003cstrong\u003eRevenue recovery: \u003c/strong\u003e\u003c/span\u003e\u003cspan style=\"font-size: 12pt;\"\u003eService downtime and customer experience issues can impact revenue and customer retention. This area reflects the bottom-line value of reducing these risks.\u003c/span\u003e\u003c/li\u003e\u003c/ol\u003e"},{"title_l10n":"Value drivers of Elastic Security","_metadata":{"uid":"cs668cce5848b2c14e"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eFor Elastic Security specifically, we define value in the following categories:\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"1. Security team efficiency improvement","_metadata":{"uid":"csb3895eafd8ded3c1"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security drives productivity gains across security analysts, engineers, and management personnel from a business analysis perspective. We begin by accounting for the economic value of improving the productivity of every SOC’s most valuable resource: its skilled practitioners. If time is money, how much can your team expect to save by automating threat detection and streamlining investigation and incident response?\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eBy centralizing data, security teams can analyze information faster and accelerate response with embedded case management and automated actions. This allows teams to quickly determine root cause and reduce escalations. By improving mean time to investigate, detect, and respond (MTTX) and reducing false-positive alerts and escalations, teams can reduce their overall cost per incident.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"2. Security technology consolidation and optimization","_metadata":{"uid":"cs324d7a36d155bcb2"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic Security unifies several vital technologies — SIEM, endpoint, and cloud security — on a single platform. In this calculation, we estimate the value of lowering licensing and infrastructure costs, reducing technical overhead, and simplifying the implementation of new use cases.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"3. Business disruption risk reduction","_metadata":{"uid":"cs30ae1d9495d57155"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eAny disruption to your business by security incidents — whether internal or external — can cost your organization. Elastic Security allows you to improve visibility, eliminate blind spots, increase automation, and reduce the number of incidents. In this calculation, we consider downtime associated with internal and customer-facing services and applications. This can bring productivity gains for employees and recover revenue previously lost to downtime, SLA violations, and customer churn.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"4. Incident risk reduction","_metadata":{"uid":"cs96ffc5e8779d6d62"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 12pt;\"\u003eWith robust \u003ca href=\"https://www.elastic.co/security/endpoint-security\" target=\"_self\"\u003eendpoint security solutions\u003c/a\u003e and capabilities, Elastic Security prevents and detects ransomware, malware, phishing, and other attacks, and enables automated response environment-wide. Here, we measure the impact of reducing these risks and measure potential financial savings based on IBM’s \u003c/span\u003e\u003ca href=\"https://www.ibm.com/downloads/cas/3R8N1DZJ\" target=\"_blank\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eCost of a Data Breach Report\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"5. Incident cost avoidance","_metadata":{"uid":"cs2a5dfb64de0336f3"},"header_style":"H3","paragraph_l10n":"\u003cul\u003e\u003cli\u003e\u003cspan style='font-size: 12pt;'\u003eElastic Security modernizes SecOps, equipping practitioners to protect, detect, and respond to complex attacks. With an open and transparent platform — and an agent that stops ransomware and advanced threats alike — it helps organizations reduce risk, advance SecOps maturity, and harden DevSecOps processes. Here we take into account post-incident cost savings, including system reimaging and hours spent by an external incident response firm.\u003c/span\u003e\u003c/li\u003e\u003c/ul\u003e"},{"title_l10n":"Elastic AI Assistant","_metadata":{"uid":"cs62a5581a7542a530"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style=\"font-size: 12pt;\"\u003eThese calculations don’t reflect the value delivered in the recently introduced \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/introducing-elastic-ai-assistant\"\u003e\u003cspan style=\"font-size: 12pt;\"\u003eElastic AI Assistant\u003c/span\u003e\u003c/a\u003e\u003cspan style=\"font-size: 12pt;\"\u003e for Elastic Security. AI helps practitioners harness the rapidly shifting LLM landscape to address various security use cases. It provides guidance on topics as varied as alert summarization, triage steps, query conversion, and custom data ingestion. These capabilities streamline analyst workflows, reducing mean time to investigate, detect, and respond.\u003c/span\u003e\u003c/p\u003e"},{"title_l10n":"How does Elastic Security drive value for our customers?","_metadata":{"uid":"cs30dbf5d0c6fc8501"},"header_style":"H2","paragraph_l10n":"\u003cp\u003e\u003cspan style='font-size: 12pt;'\u003eSee how \u003c/span\u003e\u003ca href=\"https://www.elastic.co/blog/transforming-cybersecurity-elastic-search-ai-proficio\"\u003e\u003cspan style='font-size: 12pt;'\u003eProficio\u003c/span\u003e\u003c/a\u003e\u003cspan style='font-size: 12pt;'\u003e turned to Elastic Security and used Elastic AI Assistant to reduce investigation time by 34% and project cost savings.\u003c/span\u003e\u003c/p\u003e"}],"_metadata":{"uid":"cs8f1fc5fd631b3025"}}}],"publish_date":"2023-06-29","sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_image":null,"noindex":false,"canonical_tag":""},"subtitle_l10n":"","table_of_contents":{"blog_series":[]},"tags":[],"tags_culture":[],"tags_elastic_stack":[],"tags_industry":[],"tags_partner":[],"tags_topic":[{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt43ad419de732b584","ACL":{},"created_at":"2023-11-06T21:31:46.367Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-analytics","label_l10n":"Security analytics","tags":[],"title":"Security analytics","updated_at":"2023-11-06T21:31:46.367Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.534Z","user":"blt4b2e1169881270a8"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","_content_type_uid":"tags_topic","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"tags_topic","title":"Investigation \u0026 incident response","label_l10n":"Investigation \u0026 incident response","keyword":"investigation-incident-response","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt43660d1624e728b9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:40:59.781Z","updated_at":"2023-11-06T20:41:24.521Z","ACL":{},"_version":2,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.865Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"bltb1d5b7df835c3535","ACL":{},"created_at":"2023-11-06T21:38:33.456Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"continuous-monitoring","label_l10n":"Continuous monitoring","tags":[],"title":"Continuous monitoring","updated_at":"2023-11-06T21:38:33.456Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.388Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"AIOps","label_l10n":"AIOps","keyword":"aiops","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2690a3f48e0fb443","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:07:47.588Z","updated_at":"2023-11-06T20:07:47.588Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.779Z","user":"blt4b2e1169881270a8"}},{"_content_type_uid":"tags_topic","title":"Cybersecurity","label_l10n":"Cybersecurity","keyword":"cybersecurity","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt276db992db94ced9","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:37:07.408Z","updated_at":"2023-11-06T20:37:07.408Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T10:22:02.082Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"thumbnail_image":{"_version":1,"is_dir":false,"uid":"blt539f8b977e5a814a","ACL":{},"content_type":"image/png","created_at":"2022-06-01T19:17:49.043Z","created_by":"blt3044324473ef223b70bc674c","file_size":"108540","filename":"illustration-currency-value-scale-1680x980-white.png","parent_uid":"bltbe197e1b26d08536","tags":[],"title":"illustration-currency-value-scale-1680x980-white.png","updated_at":"2022-06-01T19:17:49.043Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-10-10T08:10:49.241Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt539f8b977e5a814a/6297bb5dbf05100f50a8c01f/illustration-currency-value-scale-1680x980-white.png"},"title":"How does Elastic Security drive value to your organization?","title_l10n":"How does Elastic Security drive value to your organization?","updated_at":"2025-02-23T01:00:40.300Z","updated_by":"bltb6c155cd84fc0c1a","url":"/blog/how-elastic-security-drive-value-organization","publish_details":{"time":"2025-02-23T01:00:45.607Z","user":"bltb6c155cd84fc0c1a","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1239],"videoEntries":[[{"uid":"blt66c873acf90254cd","_version":7,"locale":"en-us","ACL":{},"created_at":"2025-03-24T17:32:41.018Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Elastic Cloud scaling: Optimizing for growth","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eThis webinar will guide Elastic Cloud customers through proven strategies for efficiently scaling Elastic clusters. Learn directly from our experts in this session designed for organizations experiencing growth.\u003c/p\u003e\u003cp\u003eDiscover how to optimize your Elastic Cloud deployment for performance and cost efficiency. In this practical webinar, you'll learn essential scaling techniques and best practices from our Customer Engineering team to support your growing workloads.\u003c/p\u003e\u003ch4\u003eBenefits\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eOptimize\u003c/strong\u003e cluster performance as your data volume increases\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eScale smart\u003c/strong\u003e with intelligent configuration strategies\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eMaximize\u003c/strong\u003e cluster efficiency and architecture\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eRegister now and learn how to take the stress away from scaling your deployments.\u003c/p\u003e","presentation_date":"2025-04-10T15:00:00.000Z","presenter":["bltf0873aaa01d921b9","bltf981a9d560ebc5df"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Cloud scaling: Optimizing for growth","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Elastic Cloud scaling: Optimizing for growth","token":"","translated_date_l10n":"","translated_time_l10n":"11:00 a.m. EDT","updated_at":"2025-03-31T17:30:54.706Z","updated_by":"blt7ee4b4a4026b9c0b","url":"/virtual-events/scaling-for-growth","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-31T17:31:01.394Z","user":"blt7ee4b4a4026b9c0b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd96ca5e8ce3b1d50","_version":12,"locale":"en-us","ACL":{},"created_at":"2025-03-26T09:26:57.534Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"2025 ElasticON Tour Syndey On Demand","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eElasticON Sydney 2025 was a groundbreaking event focused on \u003cstrong\u003eSupercharging \u0026lt;anything\u0026gt; with Search AI.\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhile the event itself has come to a close, the opportunity to learn and grow doesn't have to. We're offering on-demand access to exclusive sessions, insights, and innovations from some of the brightest minds in the industry. Whether you missed the event or want to relive the highlights, dive into a wealth of valuable content now. The action packed day highlighted the breadth of our technologies, strength of our community, and the depth of our customer and partner relationships.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cstrong\u003eLearn the latest advancements in Elastic:\u003c/strong\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eSearch:\u003c/strong\u003e Build generative AI applications faster than ever before. Deploy and scale across any environment (whether you're on-prem, in the cloud, or somewhere in between)\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eObservability:\u003c/strong\u003e Accelerate problem resolution and improve operational efficiency with Elastic's full stack Search AI-powered observability — fast, contextual, and intelligent observability across the broadest data sources.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eSecurity:\u003c/strong\u003e Detect sooner, investigate faster, and remediate before threats have a chance with Search AI-driven security analytics on the Elastic Search AI Platform.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-03-06T03:30:00.000Z","presenter":["blt99b00fd2496f838e","blt56500a97294fab28","blt6d194548ac42b2dc","bltd8c662f02c05199b","blt9f1e1cacd8fbd682","blt478d09976ac97420","blt98833041240bcd05","blt447838d009a3e1f4","blt0896400660d3af74","blt2430c9dcf8b77248","blt4997fec702d2a043","blt3f40228a9a953e07","bltfe527589b3edba86","bltc02c6104e3bb74eb","blt33c7df8b6c6cc48d","blt2843c397def9f319","blt849afd8f13e08832","blt6c6a8b2857cf88e8"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"2025 ElasticON Tour Sydney On Demand","seo_description_l10n":"This on-demand access is to access exclusive sessions, insights, and innovations from some of the brightest minds in the industry. ","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Line of Business","label_l10n":"Line of Business","keyword":"line-of-business","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc7c3b39e2e489f59","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:29.169Z","updated_at":"2021-12-16T23:50:29.169Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:54.975Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Executive","label_l10n":"Executive","keyword":"executive","hidden_value":false,"tags":[],"locale":"en-us","uid":"blte90f70f3321c02eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:16.927Z","updated_at":"2021-12-16T23:50:16.927Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.025Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"title":"DevOps","label_l10n":"DevOps","keyword":"devops","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd2296d539450bf20","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T22:34:41.888Z","updated_at":"2021-12-16T22:34:41.888Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.169Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"2025 ElasticON Tour Sydney On Demand","token":"k36ytdcznt","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-29T16:02:38.085Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/2025-elasticon-tour-sydney-on-demand","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-29T16:02:45.010Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb3f58cad07a409f4","_version":1,"locale":"en-us","ACL":{},"created_at":"2025-03-28T15:15:55.884Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Conversation with Michael Johnson from Citigroup","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eJoin Elastic's David Hope and Citigroup’s Michael Johnson to hear about current observability challenges in FinServ and how Elastic has helped Citigroup overcome these hurdles.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eCurrent observability challenges in financial services\u003c/li\u003e\u003cli\u003eHow Elastic helped overcome observability hurdles\u003c/li\u003e\u003cli\u003eThe importance of OpenTelemetry\u003c/li\u003e\u003cli\u003eThe observability data mesh with cross cluster search\u003c/li\u003e\u003cli\u003eFuture milestones for the successful implementation of generative AI\u003c/li\u003e\u003cli\u003eHow Elastic can help support future initiatives\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eWant to stay in the loop on all things Elastic?\u003c/h4\u003e\u003cp\u003e\u003ca href=\"/events?tab=1\" target=\"_self\"\u003eJoin us\u003c/a\u003e at our upcoming events or check out \u003ca href=\"/events/elasticon/archive\" target=\"_self\"\u003eElasticON's video archive\u003c/a\u003e.\u003c/p\u003e\u003cp\u003e\u003ca href=\"/community\" target=\"_self\"\u003eGet connected\u003c/a\u003e to find help from the Elastic community.\u003c/p\u003e","presentation_date":"2024-11-13T17:01:00.000Z","presenter":["bltd516a87082210f90","blt2faab086170635af"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":true},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"ElasticON 2024/2025 - Conversation with Michael Johnson from Citigroup","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-28T15:15:55.884Z","updated_by":"blt3044324473ef223b70bc674c","url":"/events/elasticon/archive/observability-problem-resolution-citigroup","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"iE71y1uAZdGoVbPuiNnZWq","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-28T15:15:59.653Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4d9a0c2b7e325c57","_version":10,"locale":"en-us","ACL":{},"created_at":"2021-10-05T19:10:28.579Z","created_by":"bltde77f2161b811714","disclaimer":["blt8a57ffe00cd69ec3"],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":null,"main_header":{"title_l10n":"Enable real time insights at scale for telco to solve","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"marketo_load_id":"14430","gdpr_text":["bltd8d585d4734a50f6"],"fallback":"","gdpr_load_id":"","subtitle_l10n":"","success_message_l10n":"","title_l10n":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eBreaking down traditional telco silos drives faster time to market, reduction in customer acquisition costs, and more. High-resolution insights in real-time at telco scale is an undertaking that requires Elastic’s search and data platform. Join this session to learn how you can maximize data utility and solve these challenges.\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eOther references\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/webinars/new-challenges-and-benefits-brought-by-open-ran-and-5g\" target=\"_self\"\u003eWatch the on-demand webinar: New challenges and benefits brought by Open RAN and 5G\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/webinars/elastic-telco-day-applications-and-operational-highlights-from-telco-environments\" target=\"_self\"\u003eWatch the on-demand webinar: Applications and operational highlights from telco environments\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2021-10-05T19:30:00.000Z","presenter":["blteeaceaae851afa34","blt1e0a451c28c70d3b"],"sanity_migration_complete":false,"seo":{"noindex":false,"seo_description_l10n":"","seo_image":null,"seo_keywords_l10n":"","seo_title_l10n":""},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Enable real time insights at scale for telco to solve","token":"unpwh7a8nb","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-27T15:46:27.282Z","updated_by":"blt3e52848e0cb3c394","url":"/elasticon/archive/2021/global/enable-real-time-insights-at-scale-for-telco-to-solve","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"thKETHATTsZv69o1o4auve","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-27T15:46:32.627Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt98b71123abf65157","_version":9,"locale":"en-us","ACL":{},"created_at":"2025-03-17T09:46:42.529Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Query Quest: Transforming Splunk SPL to Elastic ES|QL","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12248","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eThis multi-part workshop will show you how to transform familiar Splunk® SPL queries into Elastic ES|QL with ease. By bridging these platforms with real-world examples, you’ll learn how the Elastic ES|QL query language can be applied to SPL based use cases.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eThis series will empower you to understand how Elastic can fit into your organization’s evolving cybersecurity landscape, helping you make informed decisions.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eHighlights:\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e• Live Demos: Demonstration of Elastic AI Assistant for seamless query conversion.\u003c/p\u003e\u003cp\u003e• Query Techniques and Best Practices: Leverage ES|QL to convert SPL queries, understanding when and why to use specific ES|QL commands.\u003c/p\u003e\u003cp\u003e• Actionable Skills: Master converting SPL to ES|QL queries to achieve desired outcomes with Elastic Security\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cstrong\u003e\u003c/strong\u003e\u003cstrong\u003ePrerequisites:\u003c/strong\u003e\u003cstrong\u003e\u003c/strong\u003e• Experience working in Security Operations• Familiar with Splunk SPL query language• Basic understanding of Elastic Security solutions","presentation_date":"2025-05-06T05:00:00.000Z","presenter":["blt0555a58731a0323f"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Query Quest: Transforming Splunk SPL to Elastic ES|QL","seo_description_l10n":"This series will empower you to understand how Elastic can fit into your organization’s evolving cybersecurity landscape, helping you make informed decisions.","seo_keywords_l10n":"Security, Elastic ES|QL, Elasticsearch","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Line of Business","label_l10n":"Line of Business","keyword":"line-of-business","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc7c3b39e2e489f59","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:29.169Z","updated_at":"2021-12-16T23:50:29.169Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:54.975Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Consideration","label_l10n":"Consideration","keyword":"consideration","hidden_value":true,"tags":[],"locale":"en-us","uid":"bltcc21b70ba839da7d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:48.154Z","updated_at":"2021-12-16T23:51:48.154Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.006Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Query Quest: Transforming Splunk SPL to Elastic ES|QL","token":"e21qgzz1k8","translated_date_l10n":"","translated_time_l10n":"10:30 a.m. IST / 1 p.m. SGT / 3 p.m. AEST ","updated_at":"2025-03-27T09:01:30.433Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/transforming-splunk-spl-to-elastic-esql","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-27T09:01:37.347Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3ce2645e05e72ae9","_version":2,"locale":"en-us","ACL":{},"created_at":"2025-03-25T23:47:46.843Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"AI for SOC teams: What's real and what's next","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eAMER: 9:00 a.m. PDT, 12:00 p.m EDT\u003c/p\u003e\u003cp\u003eEMEA: 11:00 a.m. CEST, 2:30 p.m. IST\u003c/p\u003e\u003cp\u003eAPJ: 11:00 a.m. SGT, 1:00 p.m. AEDT\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eGenerative AI is transforming security operations, empowering practitioners to detect sooner, investigate faster, and respond decisively.\u003c/p\u003e\u003cp\u003eElastic Security's AI features solve real-world challenges: quickly onboard custom data sources, migrate SIEMs without manually rebuilding content, automate alert triage, and more.\u003c/p\u003e\u003cp\u003eThis webinar will include product demos, customer case studies, and expert insights on how to strengthen defenses with AI.\u003c/p\u003e\u003cp\u003eJoin this session to see how you can transform your security operations with AI.\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/security/ai\"\u003eAI for SecOps\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/virtual-events/accelerate-your-soc-with-ai\"\u003eWebinar: Fight smarter: Accelerate your SOC with AI\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/security/ema-siem-ai-security-analytics-impact-brief\"\u003eEMA Impact Brief: Revolutionizing SIEM with AI-driven security analytics\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-05-22T16:00:00.000Z","presenter":["blt0f29d73fc8cc4651","blt47281ee31f9b7aa9"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"AI for SOC teams: What’s real and what’s next","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"AI for SOC teams: What's real and what's next","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-26T19:36:41.521Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/ai-for-soc-teams-whats-real-and-whats-next","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-26T19:36:57.668Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcefa7d9c7c2427de","_version":8,"locale":"en-us","ACL":{},"created_at":"2025-01-28T22:43:25.210Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Accelerating action with AI","paragraph_l10n":"\u003cp\u003eSponsored by Kyndryl, Microsoft, and Elastic\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eIndustry leaders from Kyndryl, Microsoft, and Elastic join us for an insightful webinar on how AI is revolutionizing business operations and promoting diversity in tech. Our speakers will discuss AI-driven solutions that accelerate decision-making, optimize processes, and enhance customer experiences, fostering an inclusive culture that empowers all voices. Discover how advocating for diversity not only enriches collaboration but also drives innovation and impactful outcomes.\u003c/p\u003e\u003ch4\u003eAdditional resource\u003c/h4\u003e\u003cp\u003eExcited about AI and want to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=microsoft-elastic-Kyndryl-Accelerating-Action\" target=\"_self\"\u003eAzure Marketplace listing\u003c/a\u003e.\u003c/p\u003e","presentation_date":"2025-03-18T21:00:00.000Z","presenter":["blt3d8ed5edce9ead9c","blt5ac86a82351a5aa1","blt0d1be058a59e7827","blt3323f40b67886e38"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Accelerating action with AI","token":"03182025","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-26T00:05:25.703Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/microsoft-elastic-kyndryl-accelerating-action","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"P48rBfrP4XVjAEe2Rykuv3","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-26T00:05:29.471Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1f0b42ac70824c90","_version":7,"locale":"en-us","ACL":{},"created_at":"2025-02-25T01:08:05.248Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Delivering ROI on AI: How AI creates workforce efficiency","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eGenerative AI can be a complex, costly undertaking. One of the important foundational questions is: \"Can I build this myself, or should I buy an off-the-shelf solution?\" The answer is, \"It depends.\"\u003c/p\u003e\u003cp\u003eIn this webinar, our panel of experts from Elastic, IDC, and Microsoft will explore key considerations for when and why an organization might want to invest in a \"build\" approach to generative AI technology.\u003c/p\u003e\u003cp\u003eJoin this webinar to learn how to create a centralized foundation for generative AI experiences. Gain insights and best practices to build your generative AI strategy to stay ahead of the competition. Learn how Elastic and Microsoft stay ahead of the curve and create employee efficiencies with AI.\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eExcited about AI and ready to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=microsoft-elasticgpt-workforce-efficiency\" target=\"_self\"\u003eAzure Marketplace listing\u003c/a\u003e.\u003c/li\u003e\u003cli\u003e\u003ca href=\"/portfolio/operationalizing-generative-ai-strategic-guide\" target=\"_self\"\u003eAn executive's guide to operationalizing generative AI\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/platform\" target=\"_self\"\u003eLearn how to use your data in real time with the Elastic Search AI Platform\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-03-25T21:00:00.000Z","presenter":["bltc377310d5111b252","blte0652df2f117e695","blt089f6ddbd5d28a07"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Delivering ROI on AI: How AI creates workforce efficiency","token":"0325","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-26T00:02:06.031Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/idc-microsoft-elasticgpt-workforce-efficiency","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"Cd3QZV45AV76CzTqRicHSB","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-26T00:02:09.276Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2a55bdc0acc2a095","_version":5,"locale":"en-us","ACL":{},"created_at":"2025-02-18T10:58:05.223Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"How AI is Influencing Fraud in Financial Services","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAs fraudsters increasingly weaponize AI, financial institutions must leverage the same technology to strengthen their defenses. In this session, \u003cstrong\u003eElastic's Deputy CISO, Anthony Scarfe\u003c/strong\u003e, and \u003cstrong\u003epetaFuel CTO, Ludwig Adam\u003c/strong\u003e, discuss how AI is reshaping fraud detection and prevention in financial services.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eAI’s dual impact: \u003c/strong\u003eAI powers real-time fraud detection but also enables cybercriminals to scale attacks.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eEvolving threats:\u003c/strong\u003e Generative AI tools like FraudGPT accelerate phishing campaigns and cross-ecosystem attacks.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eModern fraud prevention: \u003c/strong\u003eCombining machine learning for statistical analysis with generative AI for real-time incident qualification.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eData security \u0026amp; AI training: \u003c/strong\u003eEffective implementation requires integrating multiple data sources while ensuring data privacy.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eWatch the session to learn how financial institutions can detect fraud in real-time, integrate AI-powered analysis into security frameworks, and protect financial operations in an AI-driven landscape.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["bltcd361651714738a0","blt9ebdbc61667c595c"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How AI is Influencing Fraud Detection in Financial Services","seo_description_l10n":"Discover how AI is being used for both fraud prevention and cyberattacks in financial services. Learn real-time detection strategies from Elastic and petaFuel experts. Watch the session now.","seo_keywords_l10n":"AI, financial services, fraud prevention, fraud detection, cyberattacks","seo_image":{"uid":"blt5cd22460921a3c5b","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Ludwig Adam.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T10:57:47.178Z","updated_at":"2025-02-18T10:57:47.178Z","content_type":"image/png","file_size":"94035","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Ludwig_Adam.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T21:09:30.629Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt5cd22460921a3c5b/67b467ab9bea6d115b4901f9/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Ludwig_Adam.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt484a944a3d130219","ACL":{},"created_at":"2023-11-06T20:39:33.494Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fraud-detection","label_l10n":"Fraud detection","tags":[],"title":"Fraud detection","updated_at":"2023-11-06T20:39:33.494Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.155Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - How AI is Influencing Fraud in Financial Services","token":"24IMA6RNF0","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:32:39.514Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/how-ai-is-influencing-fraud-in-financial-services","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"eCHagpRJWV82Cf4hpb28QR","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:32:45.365Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6340070245711ca0","_version":6,"locale":"en-us","ACL":{},"created_at":"2025-02-18T15:35:20.545Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Driving Operational Resilience: Observability and Security in Financial Services","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAs financial institutions defend against cyber threats, operational resilience is more critical than ever. In this session, Ken Exner, Chief Product Officer at Elastic, explores how integrating security and observability enhances performance and strengthens defenses.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eThe convergence of security \u0026amp; observability: \u003c/strong\u003eBoth rely on shared log data, metrics, and real-time monitoring to protect financial institutions.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eRegulatory-driven resilience:\u003c/strong\u003e New compliance mandates push firms to strengthen operational resilience, as customers equate IT outages with security failures.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eEnhanced threat detection: \u003c/strong\u003eElastic’s integrated security and observability platform helps organizations detect and respond to threats faster.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eAI-powered insights: \u003c/strong\u003eAI bridges skill gaps by automating root cause analysis and improving detection capabilities for teams of all experience levels.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eLearn how financial organizations can build a secure, resilient operational framework with integrated observability and security. Watch now to explore strategies for strengthening financial services resilience.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt0896400660d3af74"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Financial Services Can Strengthen Operational Resilience with Security \u0026 Observability","seo_description_l10n":"Discover how financial institutions use integrated security and observability to enhance resilience and meet regulatory demands. Watch the session now.","seo_keywords_l10n":"financial services, security, observability, Operational Resilience","seo_image":{"uid":"blt0b3b89fee878785e","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Ken Exner.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T15:28:10.298Z","updated_at":"2025-02-18T15:28:10.298Z","content_type":"image/png","file_size":"107158","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Ken_Exner.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T21:36:19.045Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0b3b89fee878785e/67b4a70a07cf0fb87dca9c57/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Ken_Exner.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Driving Operational Resilience: Observability and Security in Financial Services","token":"TZYR2W0RR0","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:31:57.159Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/driving-operational-resilience-observability-and-security-in-financial-services","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"tZuCGiwEdhoV2S4QSWajQA","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:32:03.092Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf197d3da4c4a0bf3","_version":5,"locale":"en-us","ACL":{},"created_at":"2025-02-18T10:31:50.525Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Enhancing efficiency with unified search at Allianz Technology","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eHow can financial institutions manage complex data environments while ensuring fast, secure search capabilities? \u003cstrong\u003eChristian Hoffmann, \u003c/strong\u003eand \u003cstrong\u003eMarcel Zeininger\u003c/strong\u003e, \u003cstrong\u003eElasticsearch System Specialist\u003c/strong\u003e at \u003cstrong\u003eAllianz Technology,\u003c/strong\u003e share insights with \u003cstrong\u003eOliver Oursin\u003c/strong\u003e, \u003cstrong\u003eVP of Solutions Architecture at Elastic\u003c/strong\u003e, on optimizing enterprise search.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eBeyond traditional databases: \u003c/strong\u003eRelational databases struggle with modern search demands in financial services.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eHuman vs. automated search: \u003c/strong\u003eDifferent approaches are needed to balance efficiency and accuracy.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBuilt-in security and permissions: \u003c/strong\u003eSearch must integrate role-based access to protect sensitive data.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eCentralized search portal: \u003c/strong\u003eSimplifies developer access and ensures consistent search handling.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eUser-first approach: \u003c/strong\u003eDesigning search based on user behavior leads to better outcomes than relying solely on data structures.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eGain practical strategies from industry leaders on streamlining search, improving data access, and enhancing security in financial services. \u003cstrong\u003eWatch now\u003c/strong\u003e to discover how Allianz Technology optimized enterprise search.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt7b10545443a38377","blt74db67b6a7aaad0b","blt05dbd9cd7f2f3a17"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Allianz Technology Optimized Enterprise Search for Financial Services","seo_description_l10n":"Discover how Allianz Technology enhanced enterprise search, improving security, efficiency, and data access in financial services. Watch the session now.","seo_keywords_l10n":"enterprise search, data management, Allianz, financial services","seo_image":{"uid":"blt248b5a500cf5483d","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Marcel Zeininger.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T10:28:21.441Z","updated_at":"2025-02-18T10:28:21.441Z","content_type":"image/png","file_size":"100392","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Marcel_Zeininger.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T20:34:41.969Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt248b5a500cf5483d/67b460c5d235094c14a28612/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Marcel_Zeininger.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"title":"Knowledge base search","label_l10n":"Knowledge base search","keyword":"knowledge-base-search","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt2c020c0c24ae64ef","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:41:47.026Z","updated_at":"2023-11-06T20:41:47.026Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:49.958Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Enhancing efficiency with unified search at Allianz Technology","token":"LGUAWV9WOU","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:30:55.127Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/enhancing-efficiency-with-unified-search-at-allianz-technology","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"wYUQMAWgdbgh8ikBZMauBz","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:31:01.097Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3093c173a88f72dd","_version":5,"locale":"en-us","ACL":{},"created_at":"2025-02-18T14:15:45.334Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"AI, compliance, and innovation: a roadmap for FSIs","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eHow can financial institutions adopt AI while staying compliant with evolving regulations? Elastic’s CIO, Matt Minetola, Senior Director of Global Government Affairs, Bill Wright, and Microsoft’s Senior Director of Industry Cloud—Financial Services, Thomas Mathew explore strategies for balancing AI innovation with regulatory requirements.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eRegulatory impact: \u003c/strong\u003eGlobal compliance laws, including the EU AI Act, are reshaping AI adoption, requiring built-in privacy and security safeguards.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eImplementation challenges: \u003c/strong\u003eFinancial services firms must address scalability, system consistency, and heightened regulatory scrutiny as AI-driven automation expands.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eStrategic approach: \u003c/strong\u003eSuccess depends on data quality, open standards for flexibility, integrated observability for reporting, and selecting partners that support both AI implementation and compliance.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eDiscover how Elastic’s centralized AI-powered data platform helps financial institutions scale operations while maintaining compliance and security. \u003cstrong\u003eWatch the session \u003c/strong\u003eto learn how FSIs can navigate AI and regulatory complexity.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt91aefbbce7bce7d9","blt4912a365604f6024","bltb4b3824f12a98d9f"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"AI and Compliance in Financial Services: Strategies for Scalable, Secure Innovation","seo_description_l10n":"Learn how financial institutions can implement AI while staying compliant with evolving regulations. Watch industry leaders discuss scalable, secure AI adoption.","seo_keywords_l10n":"AI, financial services, compliance, fsi regulations, security","seo_image":{"uid":"blt72c057d2e47e634c","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Matt Minetola.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T14:14:55.946Z","updated_at":"2025-02-18T14:14:55.946Z","content_type":"image/png","file_size":"98832","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Matt_Minetola.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T21:15:48.854Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt72c057d2e47e634c/67b495df9594de2ea70ec634/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Matt_Minetola.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt484a944a3d130219","ACL":{},"created_at":"2023-11-06T20:39:33.494Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fraud-detection","label_l10n":"Fraud detection","tags":[],"title":"Fraud detection","updated_at":"2023-11-06T20:39:33.494Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.155Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt5ebb3c17304b01bc","ACL":{},"created_at":"2023-11-06T20:47:38.117Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"privacy-first-ai","label_l10n":"Privacy-first AI","tags":[],"title":"Privacy-first AI","updated_at":"2023-11-06T20:47:38.117Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:58.404Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - AI, compliance, and innovation: a roadmap for FSIs","token":"UF7C93SHJQ","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:30:04.535Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/ai-compliance-innovation-roadmap-for-financial-services","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"f4padUGXUphmBG6kyxPRUV","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:30:10.892Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb440c8289b782aeb","_version":5,"locale":"en-us","ACL":{},"created_at":"2025-02-18T09:32:31.227Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Shaping the Future of Financial Services with Elastic","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAt the Financial Services Summit, Elastic’s senior leadership, \u003cstrong\u003eCEO Ash Kulkarni,\u003c/strong\u003e \u003cstrong\u003eCIO Matthew Minetola\u003c/strong\u003e, and \u003cstrong\u003eCISO Mandy Andress\u003c/strong\u003e, explored how financial institutions can harness AI while ensuring resilience, security, and compliance. The discussion focuses on leveraging vast amounts of unstructured data while maintaining customer trust and staying ahead of cyber threats.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eAI in Financial Services: \u003c/strong\u003eGenAI presents an opportunity to automate document analysis and decision-making processes in financial services, improving analysis of everything from loan origination to risk assessment.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eData accessibility \u0026amp; quality: \u003c/strong\u003eEnsuring real-time access to proprietary business data for AI success.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eSimplification \u0026amp; scalability: \u003c/strong\u003eCIOs should consolidate fragmented systems into unified, cost-effective platforms.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eAI \u0026amp; security: \u003c/strong\u003eAdapting security strategies to AI-driven changes while maintaining transparency and compliance.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eComprehensive observability: \u003c/strong\u003eReal-time insights across operations, security, and applications for resilience.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eThe road ahead:\u003c/strong\u003e Moving AI projects into production, scaling capabilities, and maintaining trust in 2025.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWatch now to explore the future of AI in financial services.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["bltfe609b8b6054e6ac","blt91aefbbce7bce7d9","blt8f7db4157fab33b3"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How AI is Transforming Financial Services – Insights from Elastic’s Leadership","seo_description_l10n":"Discover how AI, observability, and security are shaping the future of financial services. Watch Elastic’s senior leaders share strategies for success.","seo_keywords_l10n":"AI, observability, security, compliance, financial services","seo_image":{"uid":"blt93aa77f52a81bdcd","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_1200x627.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T09:24:37.538Z","updated_at":"2025-02-18T09:24:37.538Z","content_type":"image/png","file_size":"639140","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_1200x627.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T20:08:40.276Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt93aa77f52a81bdcd/67b451d5c9003fce9573f471/169165_-_Ad_Banners_for_FSI_Sunmmit_1200x627.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltdf59d18fa27d1692","ACL":{},"created_at":"2023-11-06T21:34:55.381Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"tool-consolidation","label_l10n":"Tool consolidation","tags":[],"title":"Tool consolidation","updated_at":"2023-11-06T21:34:55.381Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.747Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt38a3af2dfebcb772","ACL":{},"created_at":"2024-06-06T15:02:14.821Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retrieval-augmented-generation-rag","label_l10n":"Retrieval augmented generation (RAG)","tags":[],"title":"Retrieval augmented generation (RAG)","updated_at":"2024-06-06T15:02:14.821Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-06T15:02:17.473Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Shaping the Future of Financial Services with Elastic","token":"0Q1QZ2VVTS","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:26:11.103Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/shaping-the-future-of-financial-services-with-elastic","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"H1VwvBaqnShy4frLuJh4HW","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:26:16.743Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd8d0643d5690c9e4","_version":6,"locale":"en-us","ACL":{},"created_at":"2025-02-18T08:58:30.362Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Modern security trends in Financial Services. How PayPlug tackles today's cyber threats","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAs cyber threats grow more sophisticated and regulations tighten, payment companies must protect their systems without compromising speed and efficiency. For PayPlug, with numerous exposed endpoints, the challenge was clear: How can they guard against threats while ensuring seamless payment processing? Join \u003cstrong\u003eVictor Listrat, Head of Security Operations at PayPlug,\u003c/strong\u003e and \u003cstrong\u003eMandy Andress, CISO at Elastic\u003c/strong\u003e, as they explore how AI and automation are transforming security strategies in financial services.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eAI-powered threat detection: \u003c/strong\u003eHow machine learning helps PayPlug identify abnormal behavior and respond to threats faster.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eAutomated security: \u003c/strong\u003eThe role of Elastic agents in monitoring critical data and strengthening endpoint protection.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eUnified security platform: \u003c/strong\u003eThe benefits of consolidating security tools for real-time visibility and automated workflows.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBalancing AI and compliance: \u003c/strong\u003eHow financial firms navigate AI-driven security while meeting evolving regulations like the EU AI Act.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eGain practical insights into protecting financial data and staying ahead of cyber threats with real-world strategies from payment industry leaders. Watch now to see how modern security tools keep financial services secure.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt8f7db4157fab33b3","blt2b463a692a3ffbfd"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Financial Services Use AI and Automation to Strengthen Cybersecurity - The PayPlug use case","seo_description_l10n":"Learn how PayPlug uses AI-driven security and automation to protect financial data, detect threats, and meet compliance standards. Watch the discussion now.","seo_keywords_l10n":"AI, threat detection, compliance, financial services","seo_image":{"uid":"bltc78740532a300bb7","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Victor Listrat.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T08:55:12.498Z","updated_at":"2025-02-18T08:55:12.498Z","content_type":"image/png","file_size":"90442","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Victor_Listrat.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T20:00:58.230Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc78740532a300bb7/67b44af0fd5f93bc50fcc013/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Victor_Listrat.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltc76ab818663a30de","ACL":{},"created_at":"2023-11-06T21:31:31.473Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security-compliance","label_l10n":"Security \u0026 compliance","tags":[],"title":"Security \u0026 compliance","updated_at":"2023-11-06T21:31:31.473Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:54.295Z","user":"blt4b2e1169881270a8"}},{"title":"Automated threat protection","label_l10n":"Automated threat protection","keyword":"automated-threat-protection","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt49e356fcb7971aca","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:08:22.822Z","updated_at":"2023-11-06T20:08:22.822Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:37.794Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Modern Security trends in Financial Services","token":"8NZL02YDKJ","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:25:34.959Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/modern-security-trends-in-financial-services-payplug-case","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"XikAxc11A3PtbmnXEvVnzu","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:25:43.572Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltcffa0abb9d691da4","_version":4,"locale":"en-us","ACL":{},"created_at":"2025-02-18T15:24:11.987Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Driving Innovation: GenAI Use cases in Banking","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eGenerative AI is transforming financial services, helping banks enhance customer experiences, streamline operations, and strengthen fraud detection. In this session, \u003cstrong\u003eElastic’s Senior Director of Solutions Architecture, Steve Mayzak\u003c/strong\u003e, explores how financial institutions are adopting GenAI to drive innovation.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eConversational AI for financial data: \u003c/strong\u003eAI enables natural interactions with transaction and investment data, improving research and decision-making.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eGradual AI implementation: \u003c/strong\u003eBanks start with internal tools to refine AI models before customer deployment.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eData quality matters: \u003c/strong\u003eAI’s effectiveness depends on clean, structured financial data.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eFraud prevention: \u003c/strong\u003eAI detects unusual spending patterns, helping prevent fraud in real time.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eAccuracy \u0026amp; reliability: \u003c/strong\u003eAI systems handling financial data must provide consistent and trustworthy insights.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eDiscover how financial institutions are successfully integrating GenAI to enhance banking services. \u003cstrong\u003eWatch the session\u003c/strong\u003e to explore real-world GenAI strategies in banking.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt9d00569d44cf03ea"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Banks Are Using GenAI to Improve Services, Decision-Making, and Fraud Prevention","seo_description_l10n":"Discover how banks use GenAI to enhance customer interactions, streamline operations, and prevent fraud. Watch the session for expert insights.","seo_keywords_l10n":"financial services, genai, fraud prevention","seo_image":{"uid":"bltc78d46ce9db85bba","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Steve Mayzak.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T15:23:53.757Z","updated_at":"2025-02-18T15:23:53.757Z","content_type":"image/png","file_size":"96820","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Steve_Mayzak.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T21:32:34.410Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltc78d46ce9db85bba/67b4a6095dcb771d70dcd1c4/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Steve_Mayzak.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Driving Innovation: GenAI Use cases in Banking","token":"W1OST2XL9C","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:24:57.696Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/driving-innovation-genai-use-cases-in-banking","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"mT4oktWQ3KViirznxefuiY","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:25:05.253Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta61c6ff24d51cde9","_version":6,"locale":"en-us","ACL":{},"created_at":"2025-02-17T18:04:29.551Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Modernizing payment infrastructure at a global scale. The Swift case","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eWhen SWIFT’s support teams took 12 minutes to access client data and up to four days to resolve cases, they knew their legacy systems needed a transformation. With billions of transactions flowing daily, how could they modernize while ensuring unmatched reliability? Hear from \u003cstrong\u003eSWIFT’s Head of Customer Success, Stefan De Moerloose,\u003c/strong\u003e and \u003cstrong\u003eElastic’s Principal Solutions Architect, Arno van de Velde\u003c/strong\u003e, as they reveal how real-time observability and AI-driven analytics revolutionized SWIFT’s operations.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eUnified data platform: \u003c/strong\u003eA single source of truth for seamless operations across hundreds of applications.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eCustomer service improvements: \u003c/strong\u003eCase resolution slashed from days to 30 minutes, with response times cut to instant.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eOperational excellence: \u003c/strong\u003eLearn how Elastic's common schema and real-time correlation capabilities help SWIFT maintain five-nines availability across its global network.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eInnovation in action: \u003c/strong\u003eHow generative AI is enhancing automation and customer experience.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eDiscover practical strategies to modernize payment infrastructure while scaling securely. \u003cstrong\u003eWatch the session\u003c/strong\u003e and learn how observability transforms payment operations from reactive to proactive.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2024-06-05T09:00:00.000Z","presenter":["bltde106efafe80ec99","blt02a5fd757bab520a"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How SWIFT Transformed Payment Infrastructure with Real-Time Observability","seo_description_l10n":"Discover how SWIFT modernized its payment infrastructure, reducing case resolution times from days to 30 minutes with Elastic’s real-time observability and AI-driven analytics. Watch now to learn how to scale payment operations securely. Watch the session","seo_keywords_l10n":"payment infrastructure, observability, AI, payments, Swift","seo_image":{"uid":"blt6f791ed7e292da65","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_1200x627_Stefan De Moerloose.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-17T17:58:44.624Z","updated_at":"2025-02-17T17:58:44.624Z","content_type":"image/png","file_size":"617023","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_1200x627_Stefan_De_Moerloose.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T19:49:02.236Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6f791ed7e292da65/67b378d4f178482dd72be84f/169165_-_Ad_Banners_for_FSI_Sunmmit_1200x627_Stefan_De_Moerloose.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Modernizing payment infrastructure at a global scale. The Swift case","token":"8AGMHTMVNW","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:24:19.974Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/modernizing-payment-infrastructure-globally-swift","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"WiiqKFPZZbk7PwZDusx6HS","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:24:26.850Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltfc25368f81dcf6d2","_version":4,"locale":"en-us","ACL":{},"created_at":"2025-02-18T09:44:45.665Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Optimizing Cloud Transformation in Financial Services: Strategies for 2025 and Beyond","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAs financial institutions modernize their cloud infrastructure, they must manage growing security events, 45 billion daily at JPMorgan, while navigating data silos, compliance challenges, and a cybersecurity talent shortage. In this session, \u003cstrong\u003eJohnny Bylen, Elastic’s Director of Value Engineering\u003c/strong\u003e, shares strategies for optimizing cloud transformation while balancing innovation, cost, and security.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eData visibility \u0026amp; access: \u003c/strong\u003eUnify siloed data while maintaining compliance with cross-cluster search.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eRegulatory compliance \u0026amp; retention: \u003c/strong\u003eManage complex data retention policies cost-effectively with searchable snapshots.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReducing technical debt: \u003c/strong\u003eConsolidate legacy systems and tools to lower costs and improve compliance.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eInfrastructure modernization: \u003c/strong\u003eBridge gaps between cloud and on-premises environments while controlling costs.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eFinancial institutions need practical solutions to balance data management, security, and efficiency. Learn how Elastic’s unified platform reduces fragmentation, enhances security, and supports AI-driven innovation. Watch the session.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt6685fe25f1ce26c9"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Cloud Transformation Strategies for Financial Services in 2025 and Beyond","seo_description_l10n":"Learn how financial institutions optimize cloud transformation while balancing security, compliance, and cost. Watch the session with Elastic’s expert now.","seo_keywords_l10n":"cloud transformation, financial services, security, compliance, tech debt","seo_image":{"uid":"blt9dbad11f3afc6d73","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Johnny Bylen.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T09:42:46.268Z","updated_at":"2025-02-18T09:42:46.268Z","content_type":"image/png","file_size":"97221","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Johnny_Bylen.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T20:14:04.262Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9dbad11f3afc6d73/67b456166044a182e0f7bdd4/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Johnny_Bylen.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Beginner","label_l10n":"Beginner","keyword":"beginner","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltb615bb59f2a540ed","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2021-08-24T12:52:37.481Z","updated_at":"2021-08-24T12:52:37.481Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-01T14:18:24.950Z","user":"blt86e7fb24ab3b9a29"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt4732ba20ad170771","ACL":{},"created_at":"2023-11-06T20:48:01.608Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"public-multi-hybrid-cloud","label_l10n":"Public, multi \u0026 hybrid cloud","tags":[],"title":"Public, multi \u0026 hybrid cloud","updated_at":"2023-11-06T20:48:01.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:51.878Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blte0256e5390d036ed","ACL":{},"created_at":"2023-11-06T20:25:43.573Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-migration","label_l10n":"Cloud migration","tags":[],"title":"Cloud migration","updated_at":"2023-11-06T20:25:43.573Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:27.667Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt2d51fc8cada40465","ACL":{},"created_at":"2023-11-06T20:35:57.040Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud-security","label_l10n":"Cloud security","tags":[],"title":"Cloud security","updated_at":"2023-11-06T20:35:57.040Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.295Z","user":"blt4b2e1169881270a8"}},{"title":"Cloud monitoring","label_l10n":"Cloud monitoring","keyword":"cloud-monitoring","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt4f82459203f5a666","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:35:08.968Z","updated_at":"2023-11-06T20:35:08.968Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.872Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Optimizing Cloud Transformation in Financial Services: Strategies for 2025 and Beyond","token":"969EW8BVE0","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:23:46.184Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/optimizing-cloud-transformation-in-financial-services-in-2025","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"6ZyJj2hVtm8yog1QDEbYhu","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:23:53.668Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0dc2a6fc4d033ebd","_version":4,"locale":"en-us","ACL":{},"created_at":"2025-02-18T14:28:45.174Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"How Financial Services Institutions Can Promote Modern, Interoperable Ecosystems: The Société Générale case","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eFinancial services firms must break down data silos and integrate legacy and cloud-based systems to ensure seamless operations, regulatory compliance, and customer satisfaction. In this session, Elastic’s \u003cstrong\u003eCIO, Matt Minetola\u003c/strong\u003e, \u003cstrong\u003eSociété Générale’s Senior Technical Architect, Stephane Lopes,\u003c/strong\u003e and \u003cstrong\u003eObservability Lead, Thibaut Barrault\u003c/strong\u003e, share strategies for building connected, scalable financial technology ecosystems.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eConnected systems for better banking: \u003c/strong\u003eInteroperability is essential for delivering seamless customer experiences and meeting regulatory standards.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eManaging hybrid environments: \u003c/strong\u003eSolutions must integrate cloud and on-premises systems while maintaining unified monitoring and observability.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eScalable, open platforms: \u003c/strong\u003eFuture-ready banking requires cost-effective, vendor-neutral solutions that support open standards.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eKeys to success: \u003c/strong\u003eHigh-quality data, flexible technology, and scalable architecture are critical for long-term growth.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eWatch the session to learn how Société Générale modernized its banking infrastructure with OpenTelemetry and Elastic, gaining full visibility across traditional and cloud systems.\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt91aefbbce7bce7d9","blt47fb2cc9648e1778","blt5a131df558af4a1e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Financial Services Can Build Scalable, Interoperable Ecosystems – A Société Générale Case Study","seo_description_l10n":"Discover how financial institutions can break data silos, integrate cloud and on-premises systems, and scale efficiently. Watch Société Générale’s insights now.","seo_keywords_l10n":"financial services, open telemetry, data silos, societe generale","seo_image":{"uid":"bltdeca29ebd055aeac","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Stephane Lopes.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T14:26:04.172Z","updated_at":"2025-02-18T14:26:04.172Z","content_type":"image/png","file_size":"97398","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Stephane_Lopes.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T21:23:26.034Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdeca29ebd055aeac/67b4987c309a926961aebd45/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Stephane_Lopes.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltc8e4f4eb4eed3ccd","ACL":{},"created_at":"2023-11-06T21:42:18.209Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"infrastructure-monitoring","label_l10n":"Infrastructure monitoring","tags":[],"title":"Infrastructure monitoring","updated_at":"2023-11-06T21:42:18.209Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.160Z","user":"blt4b2e1169881270a8"}},{"title":"OpenTelemetry","label_l10n":"Open source/standards","keyword":"opentelemetry","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt069bd34528952802","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:44:13.512Z","updated_at":"2023-11-06T20:44:13.512Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:35.903Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt4eb0f5c53cfcb73a","ACL":{},"created_at":"2023-11-06T20:43:57.712Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"open-source-standards","label_l10n":"Open source/standards","tags":[],"title":"Open source/standards","updated_at":"2023-11-06T20:43:57.712Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:38:21.485Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - How Financial Services Institutions Can Promote Modern, Interoperable Ecosystems. With Société Générale","token":"0KJVXV0YLM","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:23:14.286Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/how-fsis-can-promote-modern-interoperable-ecosystems-societe-generale-case","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"GbSXa5SFFcLPk8qJkX21eu","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:23:20.782Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1fbdab06fc0dc4cb","_version":14,"locale":"en-us","ACL":{},"created_at":"2025-02-18T10:51:29.796Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"How unified data and AI transforms compliance oversight \u0026 risk detection at Fingerprint","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAs regulatory demands increase, financial institutions must modernize their compliance processes to detect fraud and misconduct across complex digital communication networks. In this session, \u003cstrong\u003eFounder \u0026amp; CEO, James Hogbin\u003c/strong\u003e and \u003cstrong\u003eHead of Marketing, Brielle Hewitt at Fingerprint,\u003c/strong\u003e and \u003cstrong\u003eElastic’s VP, Massimo Merlo\u003c/strong\u003e, explore how unified data and AI enhance compliance oversight.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eStronger regulatory compliance: \u003c/strong\u003eAutomating compliance processes and updating risk detection methods are now essential.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eUnified data for fraud detection: \u003c/strong\u003eFinancial crime is rarely identifiable through a single event; data integration helps reduce blind spots.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eAI-powered risk monitoring: \u003c/strong\u003eAutomated systems allow compliance teams to analyze all communications, far beyond manual review limits.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBehavioral analysis in compliance: \u003c/strong\u003eMonitoring channel switching and language changes helps detect misconduct.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBalancing internal \u0026amp; external risks: \u003c/strong\u003eFinancial services must address both employee misconduct and fraud threats like social media scams.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eScalable, cost-effective solutions: \u003c/strong\u003eAI-driven compliance requires efficient data storage and integration to manage oversight at scale.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003e\u003c/strong\u003e\u003c/p\u003e\u003cp\u003eWatch now the session to learn how financial institutions can unify data, leverage AI, and automate compliance to stay ahead of evolving risks.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt35592877a9476de9","blt86c6fef96b5726e0","blt77609d2202ad9922"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How AI and Unified Data Strengthen Compliance \u0026 Risk Detection in Financial Services","seo_description_l10n":"Discover how AI and unified data approaches help financial institutions automate compliance, detect fraud, and reduce risk. Watch the session now.","seo_keywords_l10n":"AI, unified data, financial services, risk detection, fraud detection","seo_image":{"uid":"blt3555ccca068da23f","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_James Hogbin.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T10:49:45.562Z","updated_at":"2025-02-18T10:49:45.562Z","content_type":"image/png","file_size":"99077","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_James_Hogbin.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T20:59:04.866Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt3555ccca068da23f/67b465c99bea6dd5534901e0/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_James_Hogbin.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"blt240c2986db0ba465","ACL":{},"created_at":"2023-11-06T21:31:10.051Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"search-applications","label_l10n":"Search applications","tags":[],"title":"Search applications","updated_at":"2023-11-06T21:31:10.051Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:31:38.331Z","user":"blt4b2e1169881270a8"}},{"title":"Threat hunting","label_l10n":"Threat hunting","keyword":"threat-hunting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltba572dcfa2880a69","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:33:57.466Z","updated_at":"2023-11-06T21:33:57.466Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T05:40:31.696Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt484a944a3d130219","ACL":{},"created_at":"2023-11-06T20:39:33.494Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"fraud-detection","label_l10n":"Fraud detection","tags":[],"title":"Fraud detection","updated_at":"2023-11-06T20:39:33.494Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:33:19.155Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - How unified data and AI transforms compliance oversight \u0026 risk detection at Fingerprint","token":"BIV1P5C61I","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:22:29.961Z","updated_by":"blt0786d8f6f2d1f60b","url":"/virtual-events/how-unified-data-and-ai-transforms-compliance-and-risk-detection","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"usMAo2XSbh27LLxzBDCZXY","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:22:35.242Z","user":"blt0786d8f6f2d1f60b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt92a13d327c8389ac","_version":5,"locale":"en-us","ACL":{},"created_at":"2025-02-18T08:45:09.000Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"Enhancing customer experiences with genAI in Financial Services - The Elastic enabled bank","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eTraditional banking interfaces frustrate customers with impersonal interactions, clunky transaction searches, and static chatbots. How can banks transform these pain points into seamless, personalized experiences? Join \u003cstrong\u003eTim Brophy\u003c/strong\u003e, \u003cstrong\u003ePrincipal Solutions Architect at Elastic,\u003c/strong\u003e as he explores how semantic search and generative AI improve banking operations and customer engagement.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eSmarter transaction search: \u003c/strong\u003eMove beyond keyword matching with AI-powered semantic search for accurate, intent-driven results.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eIntelligent customer support: \u003c/strong\u003eCreate dynamic, real-time chatbot interactions that replace static FAQ-based systems.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eHyper-personalization: \u003c/strong\u003eDeliver tailored recommendations and offers using AI-driven insights.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eFraud detection \u0026amp; compliance: \u003c/strong\u003eStrengthen fraud prevention with AI models designed for financial security and regulatory compliance\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eDiscover how banks are using GenAI to enhance customer experiences, streamline operations, and drive engagement.\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blte3f7364e8671cd09"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Banks Use GenAI to Enhance Customer Experiences and Streamline Operations","seo_description_l10n":"Explore how Elastic’s GenAI-powered solutions improve banking experiences through smarter search, AI-driven chatbots, and personalized services. Watch the webinar now.","seo_keywords_l10n":"generative AI, genAI, banking experience, AI","seo_image":{"uid":"blt81689e34ccd9bb16","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_Tim Brophy.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T08:43:14.070Z","updated_at":"2025-02-18T08:43:14.070Z","content_type":"image/png","file_size":"95407","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Tim_Brophy.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T19:56:54.326Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt81689e34ccd9bb16/67b44822fd5f931c2cfcbfee/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_Tim_Brophy.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt9fb9f67ee7bb5c15","ACL":{},"created_at":"2023-11-06T20:50:46.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"real-time-analysis","label_l10n":"Real-time analysis","tags":[],"title":"Real-time analysis","updated_at":"2023-11-06T20:50:46.256Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:37:43.334Z","user":"blt06083bb707628f5c"}},{"_version":1,"locale":"en-us","uid":"bltf4c040a3cb414ac0","ACL":{},"created_at":"2023-11-06T21:32:35.092Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"semantic-search","label_l10n":"Semantic search","tags":[],"title":"Semantic search","updated_at":"2023-11-06T21:32:35.092Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.425Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Enhancing customer experiences with genAI in Financial Services - The Elastic enabled bank","token":"A9IDKBSSZD","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:16:06.269Z","updated_by":"blt0ef3bb174de02441","url":"/virtual-events/enhancing-cx-with-genAI-in-financial-services","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"EYjXg9FFT5nf558Ayq3JwE","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:16:10.638Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6b65bd3a23c39589","_version":6,"locale":"en-us","ACL":{},"created_at":"2025-02-18T10:04:13.291Z","created_by":"blt0ef3bb174de02441","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"Financial Services Summit","title_l10n":"How BBVA transformed data search and applications with Elastic","paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eON DEMAND\u003c/strong\u003e\u003c/p\u003e","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eIn 2014, BBVA’s transaction data was scattered across multiple systems, limiting customers’ access to real-time banking services. The bank needed a way to unify data, improve search performance, and enhance customer experiences. In this session, \u003cstrong\u003eDavid Jiménez Ausin, Strategy Senior Manager of NoSQL \u0026amp; SQL Operational Databases at BBVA,\u003c/strong\u003e shares how Elastic helped BBVA turn a simple search engine into a functional banking platform.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eFrom fragmented to unified data: \u003c/strong\u003eBBVA expanded from 9 to over 50 integrated services, giving customers access to 20 years of transaction history instead of just one.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eLightning-fast search: \u003c/strong\u003eQueries that once took over 3 seconds now run in milliseconds, even for complex calculations.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eReducing technical debt: \u003c/strong\u003eConsolidate legacy systems and tools to lower costs and improve compliance.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eScalability at enterprise level: \u003c/strong\u003eThe system manages 45 billion data points across 120 TB, handling records with over 400 fields of information.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eDiscover how BBVA leveraged Elastic to enhance data search, optimize performance, and improve banking services at scale. Watch the session now.\u003c/p\u003e\u003cp\u003e\u003cem\u003e\u003cstrong\u003eNote: The session is in spanish with english captions\u003c/strong\u003e\u003c/em\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong \u003e\u003cbr bold=\"[object Object]\" italic=\"[object Object]\"/\u003e\u003c/strong\u003eContinue your journey—watch more sessions from the \u003ca href=\"https://www.elastic.co/events/fsi-summit-2025\" target=\"_self\"\u003eElastic Financial Services Summit\u003c/a\u003e\u003c/p\u003e","presentation_date":"2025-02-18T09:00:00.000Z","presenter":["blt131120489494c51f","bltd84d22abcf22f7f4"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How BBVA Used Elastic to Transform Data Search and Banking Applications","seo_description_l10n":"Learn how BBVA improved banking services with Elastic, achieving real-time search, scalable data management, and seamless customer experiences. Watch the session now.","seo_keywords_l10n":"real time search, banking applications, BBVA","seo_image":{"uid":"blt41bb768cbc6fb450","_version":1,"title":"169165 - Ad Banners for FSI Sunmmit_300x250_David Jimenez Ausin.png","created_by":"blt0ef3bb174de02441","updated_by":"blt0ef3bb174de02441","created_at":"2025-02-18T09:47:43.724Z","updated_at":"2025-02-18T09:47:43.724Z","content_type":"image/png","file_size":"86857","filename":"169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_David_Jimenez_Ausin.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2025-02-18T22:00:14.513Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt41bb768cbc6fb450/67b4573f9bea6dcaed49014f/169165_-_Ad_Banners_for_FSI_Sunmmit_300x250_David_Jimenez_Ausin.png"},"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}}],"tags_language":[{"_version":5,"locale":"en-us","uid":"bltfb7f539f677adbca","ACL":{},"created_at":"2019-10-23T21:44:06.532Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"spanish","label_l10n":"Spanish","tags":[],"title":"Spanish","updated_at":"2020-07-06T22:14:16.119Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:15:17.236Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Latin America","label_l10n":"Latin America","keyword":"latin-america","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltbcf2a1fc6eee5847","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-11-13T00:08:45.508Z","updated_at":"2020-11-13T00:08:45.508Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-01T23:23:58.886Z","user":"blt36e890d06c5ec32c"}},{"uid":"bltccf54d4afac13158","ACL":{},"_version":1,"created_at":"2020-11-13T00:06:52.343Z","created_by":"blt3044324473ef223b70bc674c","keyword":"americas","label_l10n":"Americas","locale":"en-us","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-12-24T13:12:41.684Z","user":"blt3e52848e0cb3c394"},"tags":[],"title":"Americas","updated_at":"2020-11-13T00:06:52.343Z","updated_by":"blt3044324473ef223b70bc674c"}],"tags_role":[],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[{"title":"Intermediate","label_l10n":"Intermediate","keyword":"intermediate","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt09c5429e20d2ba41","created_by":"blt3e52848e0cb3c394","updated_by":"bltcb593abdd43b4039","created_at":"2021-08-24T12:52:59.050Z","updated_at":"2021-09-01T13:06:12.802Z","ACL":{},"_version":3,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-03T12:16:01.953Z","user":"blta4706a7723d386a4"}}],"tags_topic":[{"uid":"bltf38f037a2b6ecb4e","title":"Log monitoring","label_l10n":"Log monitoring","keyword":"log-monitoring","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:29:28.882Z","updated_at":"2023-11-06T21:29:28.882Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.371Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt4a47bf681100e8ca","title":"Log management","label_l10n":"Log management","keyword":"log-management","hidden_value":false,"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T20:42:23.694Z","updated_at":"2023-11-06T20:42:23.694Z","ACL":{},"_version":1,"publish_details":{"time":"2023-11-09T17:49:08.358Z","user":"bltd2a3eb4e4d2bc159","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"title":"Search analytics","label_l10n":"Search analytics","keyword":"search-analytics","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt6c991eb897ec7277","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-11-06T21:30:57.427Z","updated_at":"2023-11-06T21:30:57.427Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-04T12:28:49.147Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbaad5df00a89fcb2","ACL":{},"created_at":"2023-11-06T20:07:17.254Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"ai-search-applications","label_l10n":"AI search applications","tags":[],"title":"AI search applications","updated_at":"2023-11-06T20:07:17.254Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:41:43.822Z","user":"blt06083bb707628f5c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"FSI Summit - Empowering real-time banking: How BBVA transformed data search and applications with Elastic","token":"LF9MJPURRD","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T12:06:56.843Z","updated_by":"blt0ef3bb174de02441","url":"/virtual-events/bbva-transformed-data-search-and-applications-with-elastic","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"NQwfkzksdXhYA6sT52VGgu","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T12:07:01.593Z","user":"blt0ef3bb174de02441","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf0bcaadf262656d4","_version":27,"locale":"en-us","ACL":{},"created_at":"2025-03-18T06:58:19.061Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"2025 ElasticON Tour Singapore On Demand","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":[],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eTo skip ahead or choose which session you'd like to watch, click on the drop down menu in the top left corner of the playlist and see all the videos in the playlist.\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eElasticON Singapore 2025 was a groundbreaking event focused on \u003cstrong\u003eSupercharging \u0026lt;anything\u0026gt; with Search AI\u003c/strong\u003e.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhile the event itself has come to a close, the opportunity to learn and grow doesn't have to. We're offering on-demand access to exclusive sessions, insights, and innovations from some of the brightest minds in the industry. Whether you missed the event or want to relive the highlights, dive into a wealth of valuable content now. The action packed day highlighted the breadth of our technologies, strength of our community, and the depth of our customer and partner relationships.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003cstrong\u003eLearn the latest advancements in Elastic:\u003c/strong\u003e\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eSearch:\u003c/strong\u003e Build generative AI applications faster than ever before. Deploy and scale across any environment (whether you're on-prem, in the cloud, or somewhere in between)\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eObservability:\u003c/strong\u003e Accelerate problem resolution and improve operational efficiency with Elastic's full stack Search AI-powered observability — fast, contextual, and intelligent observability across the broadest data sources.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eSecurity:\u003c/strong\u003e Detect sooner, investigate faster, and remediate before threats have a chance with Search AI-driven security analytics on the Elastic Search AI Platform.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-03-04T00:00:00.000Z","presenter":["blt4990cfe37610ed0f","blt2430c9dcf8b77248","bltacd296962b184324","blte077751d388a38eb","blt598430dd66dec40d","blt8059b98a363c4188","bltd5fa52ed63b5c368","bltc2ab0be4acd23ab3","bltd4bc606cc96f4705","blt961d8d8769dbda90","blt31907cc8d673f59c","bltcdeff3671846f191","bltaed173dcaf595e32","bltbe8d6059b59aa777","blt0555a58731a0323f","blt69ada0b40c53529a","blt6bf9ccfdc624f123","blt5d2e8b61a6606cc4","blt2a4c77b305324183"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"ElasticON Tour Singapore On Demand","seo_description_l10n":"Missed out or interested in reliving the experience? Gain access to exclusive content from our diverse range of speakers.","seo_keywords_l10n":"Elasticsearch, Security","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"_version":3,"locale":"en-us","uid":"blt1671c05cb4d5e1af","ACL":{},"created_at":"2020-06-17T03:41:39.784Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticon","label_l10n":"ElasticON","tags":[],"title":"ElasticON","updated_at":"2021-03-04T18:54:01.311Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-01-25T09:15:42.772Z","user":"blt3e52848e0cb3c394"}}],"tags_event_type_delivery":[],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Line of Business","label_l10n":"Line of Business","keyword":"line-of-business","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc7c3b39e2e489f59","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:29.169Z","updated_at":"2021-12-16T23:50:29.169Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:54.975Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Executive","label_l10n":"Executive","keyword":"executive","hidden_value":false,"tags":[],"locale":"en-us","uid":"blte90f70f3321c02eb","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:16.927Z","updated_at":"2021-12-16T23:50:16.927Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.025Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Awareness","label_l10n":"Awareness","keyword":"awareness","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt07282f7110d8ad35","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:33.855Z","updated_at":"2021-12-16T23:51:33.855Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.099Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte007e1c9cef6ad6b","ACL":{},"created_at":"2020-06-17T03:32:48.898Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2020-07-06T22:20:15.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.357Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt6f00e40aaa5c6f0e","ACL":{},"created_at":"2020-06-17T03:32:57.128Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"siem","label_l10n":"SIEM","tags":[],"title":"SIEM","updated_at":"2020-07-06T22:20:05.385Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.450Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"2025 ElasticON Tour Singapore On Demand","token":"jpxkje13y9","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-25T03:14:58.021Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/2025-elasticon-tour-singapore-on-demand","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"WVWDemuLAMZsoTmUGzhyyf","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-25T03:15:04.019Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt49da9fb24e4f10b7","_version":3,"locale":"en-us","ACL":{},"created_at":"2025-03-24T10:46:54.925Z","created_by":"blte04802f0330f25f7","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"What's new: Elastic 9.0 for GenAI, Security, and Observability | Spring 2025","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eJoin us for an exclusive webinar as we introduce the latest advancements in Elastic with the upcoming release of 9.0 and 8.18. Our experts will provide highlights and demos of the key new features and enhancements designed to help you drive critical business outcomes with GenAI, Security, and Observability.\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003eWhether you are a current user looking to upgrade or are new to Elastic, this webinar will provide insights to help you maximize the potential of your deployment. Don't miss this opportunity to stay ahead of the curve and see the full power of Elastic innovations!\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003cp\u003e\u003c/p\u003e\u003ch4\u003e\u003cstrong\u003eWhy attend?\u003c/strong\u003e\u003c/h4\u003e\u003cul\u003e\u003cli\u003eExpert insights: Gain knowledge from Elastic experts on how to leverage the latest features.\u003c/li\u003e\u003cli\u003eLive demos: Watch live demonstrations of new capabilities.\u003c/li\u003e\u003cli\u003eQ\u0026amp;A: Get your questions answered by Elastic experts.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-04-16T05:00:00.000Z","presenter":["blte02541aa8488cd2e","blt86d32979f49901de","blt4bd459fcb13e2f4d","blt91eeaf08ab3d1d6a","bltde0a0be05534cebf"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"What's new: Elastic 9.0 for GenAI, Security, and Observability | Spring 2025","seo_description_l10n":"In this webinar we introduce the latest advancements in Elastic with the upcoming release of 9.0 and 8.18. Our experts will provide highlights and demos of the key new features and enhancements designed to help you drive critical business outcomes with GenAI, Security, and Observability.","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":3,"locale":"en-us","uid":"blta3fd0168b354a680","ACL":{},"created_at":"2023-11-06T21:50:30.740Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elk-elastic-stack","label_l10n":"ELK/Elastic Stack","tags":[],"title":"ELK/Elastic Stack","updated_at":"2024-03-12T21:21:08.589Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-03-12T21:21:14.279Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt6446d17b56e60042","ACL":{},"created_at":"2021-07-12T21:53:04.840Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"endpoint-security","label_l10n":"Endpoint security","tags":[],"title":"Endpoint security","updated_at":"2021-07-12T21:53:04.840Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:22.409Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[{"title":"Virtual","label_l10n":"Virtual","keyword":"virtual","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltc3a97789fa82c0a5","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2022-04-21T19:17:57.147Z","updated_at":"2022-04-21T19:17:57.147Z","_content_type_uid":"tags_event_delivery","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-05-12T18:15:27.370Z","user":"blt36e890d06c5ec32c"}}],"tags_industry":[{"_version":1,"locale":"en-us","uid":"blt3185b1f0e9eed8d1","ACL":{},"created_at":"2021-09-20T22:40:25.614Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"public-sector","label_l10n":"Public Sector","tags":[],"title":"Public Sector","updated_at":"2021-09-20T22:40:25.614Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.530Z","user":"blt4b2e1169881270a8"}},{"_version":6,"locale":"en-us","uid":"blt250fefd1c4d36a4c","ACL":{},"created_at":"2020-06-17T03:22:54.278Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"education-nonprofit","label_l10n":"Education \u0026 non profit","tags":[],"title":"Education \u0026 non-profit","updated_at":"2020-08-13T16:41:17.070Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.286Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt5c7c769c44d0a39f","ACL":{},"created_at":"2020-06-17T03:22:38.187Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"automotive-manufacturing","label_l10n":"Automotive \u0026 manufacturing","tags":[],"title":"Automotive \u0026 manufacturing","updated_at":"2020-07-06T22:17:51.159Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.604Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte0b2951800682f39","ACL":{},"created_at":"2020-06-17T03:23:08.064Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"energy-utilities","label_l10n":"Energy \u0026 utilities","tags":[],"title":"Energy \u0026 utilities","updated_at":"2020-07-06T22:17:47.822Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.528Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7898c57653ca2b6e","ACL":{},"created_at":"2020-06-17T03:23:20.767Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"financial-services","label_l10n":"Financial services","tags":[],"title":"Financial services","updated_at":"2020-07-06T22:17:46.176Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.532Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt34aaba843e1a6a56","ACL":{},"created_at":"2020-06-17T03:23:40.011Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"food-beverage-hospitality","label_l10n":"Food \u0026 beverage/hospitality","tags":[],"title":"Food \u0026 beverage/hospitality","updated_at":"2020-07-06T22:17:44.469Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.320Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt62646ad19dd7b0b8","ACL":{},"created_at":"2020-06-17T03:23:52.847Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"government","label_l10n":"Government","tags":[],"title":"Government","updated_at":"2020-07-06T22:17:42.931Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.550Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt3f3639d673966a36","ACL":{},"created_at":"2020-06-17T03:24:07.151Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"healthcare","label_l10n":"Healthcare","tags":[],"title":"Healthcare","updated_at":"2020-07-06T22:17:41.344Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.540Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt58f4c3eca4afb6ad","ACL":{},"created_at":"2020-06-17T03:24:20.486Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"media-entertainment","label_l10n":"Media \u0026 entertainment","tags":[],"title":"Media \u0026 entertainment","updated_at":"2020-07-06T22:17:39.186Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.848Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt55fcdf707cf978c2","ACL":{},"created_at":"2020-06-17T03:24:33.455Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"professional-services","label_l10n":"Professional services","tags":[],"title":"Professional services","updated_at":"2020-07-06T22:17:37.861Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.832Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt371b46b1f7be39e3","ACL":{},"created_at":"2020-06-17T03:24:44.114Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"retail","label_l10n":"Retail","tags":[],"title":"Retail","updated_at":"2020-07-06T22:17:35.972Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.835Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltad849a44c42eea31","ACL":{},"created_at":"2020-06-17T03:25:54.912Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"software-technology","label_l10n":"Software \u0026 technology","tags":[],"title":"Software \u0026 technology","updated_at":"2020-07-06T22:17:33.856Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.842Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt7e757baff4a3fec6","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:24.553Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:24.553Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"telecommunication","label_l10n":"Telecommunication","tags":[],"title":"Telecommunication","updated_at":"2020-07-06T22:17:31.608Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}},{"_version":2,"locale":"en-us","uid":"bltdc295116bb7f305e","ACL":{},"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:26:08.977Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"created_at":"2020-06-17T03:26:08.977Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"travel-transportation","label_l10n":"Travel \u0026 transportation","tags":[],"title":"Travel \u0026 transportation","updated_at":"2020-07-06T22:17:27.413Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T22:18:10.949Z","user":"blt3044324473ef223b70bc674c"}}],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[{"title":"Practitioner","label_l10n":"Practitioner","keyword":"practitioner","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt945c4bcb7423a5db","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:50:43.688Z","updated_at":"2021-12-16T23:50:43.688Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:33:43.186Z","user":"blt3044324473ef223b70bc674c"}}],"tags_stage":[{"title":"Consideration","label_l10n":"Consideration","keyword":"consideration","hidden_value":true,"tags":[],"locale":"en-us","uid":"bltcc21b70ba839da7d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2021-12-16T23:51:48.154Z","updated_at":"2021-12-16T23:51:48.154Z","ACL":{},"_version":1,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T00:15:55.006Z","user":"blt3044324473ef223b70bc674c"}}],"tags_technical_level":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt99b075caf3df4ca7","ACL":{},"created_at":"2023-11-06T21:41:39.171Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"generative-ai","label_l10n":"Generative AI","tags":[],"title":"Generative AI","updated_at":"2023-11-06T21:41:39.171Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.390Z","user":"blt4b2e1169881270a8"}}],"tags_use_case":[{"_version":1,"locale":"en-us","uid":"bltbc86a233655f4b8e","ACL":{},"created_at":"2022-09-13T16:43:08.111Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2022-09-13T16:43:08.111Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.253Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"APAC Whats New Elastic 9.0","token":"v5gpl64gnd","translated_date_l10n":"","translated_time_l10n":"10:30 a.m. IST / 1 p.m. SGT / 3 p.m. AEST ","updated_at":"2025-03-24T11:25:25.739Z","updated_by":"blte04802f0330f25f7","url":"/virtual-events/apac-whats-new-elastic-9-0","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-31T15:39:43.256Z","user":"blte04802f0330f25f7","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd3acdef08d556348","_version":3,"locale":"en-us","ACL":{},"created_at":"2025-01-29T02:57:47.773Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Introduction to Elastic Observability: Built for the future with Search AI","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAre you ready for the next generation of observability? Find out how Elastic Observability delivers simplified onboarding and automated insights to help you detect and resolve issues faster. Take advantage of our comprehensive visibility powered by Search AI. This webinar will cover all of Elastic Observability's core capabilities (logging, metrics, APM, synthetic monitoring, profiling) along with how to apply generative AI and SLOs on our unified platform.\u003c/p\u003e\u003cp\u003eWe'll also review how Elastic Observability future-proofs your organization and how customers are seeing real and measurable benefits today. Find out you can increase operational efficiency and team performance in this fast-paced webinar introducing Elastic Observability.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003eIn-depth demonstration of Elastic Observability's capabilities\u003c/li\u003e\u003cli\u003eHow Elastic Observability delivers improvements for IT operations and a better customer experience\u003c/li\u003e\u003cli\u003eHow to future-proof your observability\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/virtual-events/live-elastic-observability-demo\"\u003eHands-on Elastic Observability demo\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/cloud/observability-trial-overview\"\u003eElastic cloud registration\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/lp/observability-maturity-assessment\" target=\"_self\"\u003eObservability maturity assessment\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-03-13T17:00:00.000Z","presenter":["blt6595654c09e95d22","blt29599372767963e8"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Introduction to Elastic Observability: Build for the future with Search AI","seo_description_l10n":"Find out why the next generation of observability will require a new era of speed, scale, and simplicity: Elastic Observability. From open standards to simplified onboarding and automated insights, Elastic helps you detect and resolve issues, faster. Watch this webinar to learn more. ","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Elastic Observability: Built for the future with Search AI","token":"8211527597","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-19T15:25:26.796Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/introduction-to-elastic-observability","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"L2oHWJhEHvDvBzQUkkPonr","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-19T15:25:30.691Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3e3177ed003f2791","_version":3,"locale":"en-us","ACL":{},"created_at":"2025-03-05T19:29:44.157Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":" How Cypris built an AI research platform for production scale on Elastic","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eAMER: 9:00 a.m. PDT, 12:00 p.m. EDT\u003c/p\u003e\u003cp\u003eEMEA: 11:00 a.m. CEST, 2:30 p.m. IST\u003c/p\u003e\u003cp\u003eAPJ: 11:00 a.m. SGT, 1:00 p.m. AEDT\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eR\u0026amp;D teams operate in a high-stakes environment where speed and accuracy are critical. Cypris, an AI-driven research platform, has transformed how organizations analyze technical and market data — delivering insights in minutes instead of weeks.\u003c/p\u003e\u003cp\u003eJoin this webinar to explore how Cypris built an advanced search and research platform that processes over 500 million data points using Elastic. Learn how the team harnessed vector search, Better Binary Quantization (BBQ), and retrieval-augmented generation (RAG) to optimize relevance, reduce development costs, and scale for rapid enterprise growth.\u003c/p\u003e\u003cp\u003eIf you're working with AI search, vector databases, or retrieval-augmented generation, this session will provide deep technical insights from a real-world, production-scale implementation.\u003c/p\u003e\u003ch4\u003eWhat you'll learn\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eOptimizing AI search at scale:\u003c/strong\u003e How Cypris delivers relevant results across vast data sets with dense vector search.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBuilding a production-ready RAG workflow:\u003c/strong\u003e Key considerations for integrating generative AI into research applications.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eTechnical decisions that drive efficiency:\u003c/strong\u003e Why Cypris chose Elastic for real-time indexing, query performance, and cost-effective scaling.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eMeasurable business impact:\u003c/strong\u003e How these optimizations accelerated report generation and reduced in-house AI development costs.\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/what-is/vector-search\"\u003eWhat is vector search?\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/search-labs/blog/thin-indexing-shards-elasticsearch-serverless\"\u003e[Featured blog]\u003c/a\u003e Introducing Serverless Thin Indexing Shards\u003c/li\u003e\u003cli\u003e\u003ca href=\"/customers/cypris\"\u003e[Customer story]\u003c/a\u003e Cypris puts Elastic vector search and RAG technologies at the heart of its AI-powered research platform\u003c/li\u003e\u003cli\u003e\u003ca href=\"https://landing.cypris.ai/introduction-to-cypris\"\u003e[Intro to Cypris]\u003c/a\u003e Learn more about Cypris, an AI-powered research platform\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-04-17T16:00:00.000Z","presenter":["blt2cd6f9b6f7e5b592","bltfc4880a0d9930918","blt8e30adfb69293636"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"How Cypris built an AI research platform for production scale on Elastic","seo_description_l10n":"Discover the transformative journey of Cypris, an AI-powered research platform, as it scales its operations using vector search with Elastic.","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"How Cypris built an AI research platform for production scale on Elastic","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-11T20:16:06.267Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/how-cypris-built-an-ai-research-platform-on-elastic","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-11T20:18:03.540Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltbd5321a530d5b0c6","_version":5,"locale":"en-us","ACL":{},"created_at":"2025-01-10T21:26:13.124Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Solving business challenges with data and AI: Insights from 1,000+ C-Suite Leaders","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eHarnessing the power of data and AI is crucial to solving business challenges, driving innovation, and staying ahead of the competition. Despite significant investments in technology 7 in 10 C-suite executives still struggle to make real-time data-driven decisions in confidence.\u003c/p\u003e\u003cp\u003eIn this webinar, we will discuss the \u003cstrong\u003e5 key insights from 1000+ c-suite, business, and technology leaders\u003c/strong\u003e from our recent research study. Learn about your peer's top business challenges, data problems, and investment priorities (especially AI and generative AI) to see how you can get ahead. Discover why prioritising your data foundation is key to leveraging AI to drive business value.\u003c/p\u003e\u003ch4\u003eKey highlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eBusiness challenges:\u003c/strong\u003e Learn what challenges C-suite leaders across all industries face.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eData challenges:\u003c/strong\u003e Discover why 60% of leaders are unsatisfied with the data insights your company generates.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eData maturity:\u003c/strong\u003e See why 2 in 3 leaders are behind on data maturity and identify steps to enhance your capabilities.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eBusiness impact of data and AI:\u003c/strong\u003e 80% of C-suite executives believe using AI data-driven insights increases revenue. See how data and AI capabilities drive business value.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eGenAI and AI investments:\u003c/strong\u003e Hear from the 93% of executives already investing or planning to invest in generative AI.\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cstrong\u003eDon't miss out—attend the webinar to get the full insights!\u003c/strong\u003e\u003c/p\u003e\u003cp\u003e\u003ca href=\"/resources/portfolio/report/5-insights-csuite-leaders-data-ai\" target=\"_self\"\u003eRead the research report to learn more\u003c/a\u003e.\u003c/p\u003e","presentation_date":"2025-02-19T16:00:00.000Z","presenter":["blt14f762eec103604e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Solving business challenges with data and AI: Insights from 1,000+ C-Suite Leaders","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Solving business challenges with data and AI: Insights from 1,000+ C-Suite Leaders","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-11T17:36:31.621Z","updated_by":"blt7ee4b4a4026b9c0b","url":"/virtual-events/ai-insights-from-thousand-executive-leaders","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"caxyVvkSJowVQp5CqxC9FM","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-11T17:36:37.914Z","user":"blt7ee4b4a4026b9c0b","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb0e0bad931802dd6","_version":7,"locale":"en-us","ACL":{},"created_at":"2025-02-21T23:47:28.008Z","created_by":"blt36e890d06c5ec32c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Delivering ROI on AI: How AI transforms security operations","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"Thank you!","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cul\u003e\u003cli\u003eEurope \u0026amp; India: April 1, 2025, at 2:00 p.m. CEST / 6:30 p.m. IST\u003c/li\u003e\u003cli\u003eAmericas: April 1, 2025, at 1:00 p.m. PDT / 4:00 p.m. EDT\u003c/li\u003e\u003cli\u003eAsia-Pacific: April 1, 2025, at 11:00 a.m. SGT / 2:00 p.m. AEDT\u003c/li\u003e\u003c/ul\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eCyber threats are an ongoing concern for businesses across industries — especially with the speed of AI evolution. Environments and threats are changing rapidly, posing the question: How can AI accelerate security operations?\u003c/p\u003e\n\u003cp\u003eIn this webinar, our panel of experts from Elastic and Microsoft will explore key considerations for investing in AI-driven security analytics. They'll discuss ways organizations can gain greater efficiency and accuracy within security workflows while improving their security posture.\u003c/p\u003e\n\u003cp\u003eGain insights and best practices on building your security AI strategy to stay ahead of threats and attacks. Learn how Elastic and Microsoft are realizing business impact with security AI Assistants for threat intelligence reporting, investigation, and more.\u003c/p\u003e\n\u003ch4\u003eAdditional resources\u003c/h4\u003e\n\n\u003cul\u003e\n \u003cli\u003eExcited about AI and ready to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=idc-microsoft-security-operations\"\u003eAzure Marketplace listing\u003c/a\u003e.\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/portfolio/operationalizing-generative-ai-strategic-guide\"\u003eAn executive's guide to operationalizing generative AI\u003c/a\u003e\u003c/li\u003e\n \u003cli\u003e\u003ca href=\"/platform\"\u003eLearn how to use your data in real time with the Elastic Search AI Platform\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2025-04-01T08:00:00.000Z","presenter":["bltaa21b392f1697213","blt089f6ddbd5d28a07"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Delivering ROI on AI: How AI transforms security operations","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-11T00:07:43.211Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/idc-microsoft-security-operations","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-13T01:56:23.119Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt3a2eb4cb63616c25","_version":18,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:10:49.867Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"title":"pic.png","uid":"blt9c3715d9e5bb29d5","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-01-05T07:08:33.277Z","updated_at":"2019-01-05T07:08:33.277Z","content_type":"image/png","file_size":"80896","filename":"pic.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:40:51.565Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9c3715d9e5bb29d5/5c3057f16d4494e30b7b5563/pic.png"},"main_header":{"title_l10n":"Elastic App Search Overview and Demo","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"6648","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"6648","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eThe Swiftype team at Elastic introduces a powerful new search product for developers. The new product is called App Search, and it’s a search-as-a-service solution that simplifies the process of building rich search experiences for software applications of every kind — from ecommerce websites, to SaaS applications, to mobile apps.\n\u003c/p\u003e\n\u003cp\u003eRegister for our on-demand recording for an\u0026nbsp;overview and demo of Elastic App Search and gain access to a set of robust APIs and tools for building modern, relevant, user-facing search experiences, all backed by the Elastic Stack.\n\u003c/p\u003e\n\u003cul\u003e\n\t\u003cli\u003eBuilt on the Elastic Stack and powered by Elasticsearch\u003c/li\u003e\n\t\u003cli\u003eAdd a new search engine to your custom application in minutes\u003c/li\u003e\n\t\u003cli\u003eRobust APIs for indexing content and managing your search engine\u003c/li\u003e\n\t\u003cli\u003eFine-tune results through an intuitive interface\u003c/li\u003e\n\t\u003cli\u003eAdjust search relevance to meet your specific needs\u003c/li\u003e\n\u003c/ul\u003e\n\u003cp\u003eAdditional Resources (Related content)\n\u003c/p\u003e\n\u003cul\u003e\n\t\u003cli\u003e\u003ca href=\"/app-search/service?elektra=app-search-overview-demo-webinar\"\u003eFree 14-Day App Search Trial\u003c/a\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://swiftype.com/documentation/app-search/getting-started\"\u003eApp Search Documentation\u003c/a\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"/blog/elastic-app-search-is-now-generally-available\"\u003eApp Search GA Blog Post\u003c/a\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://info.elastic.co/app-search-request-demo.html?baymax=web\u0026elektra=app-search-overview-webinar\"\u003eTalk to a search expert\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2018-06-06T16:00:00.000Z","presenter":[],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["app","swiftype"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"title":"Optimizing","label_l10n":"Optimizing","keyword":"optimizing","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt7731091cfa6e23e8","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:40:15.070Z","updated_at":"2020-06-17T03:40:15.070Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:40:15.069Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:51.089Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blte1906c436045dbef","ACL":{},"created_at":"2020-06-17T03:31:19.243Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"app-search","label_l10n":"App search","tags":[],"title":"App search","updated_at":"2020-07-06T22:20:20.511Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.547Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Elastic App Search Overview and Demo","token":"n3mochofrb","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-10T16:44:14.526Z","updated_by":"blt3044324473ef223b70bc674c","url":"/webinars/elastic-app-search-overview-and-demo","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"CZHfZQTSg5BVtY6edfuuRA","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-10T16:45:22.620Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt203719faf31d8266","_version":14,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:09:23.816Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"title":"schema.jpg","uid":"blt382664fd579c9334","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T06:09:23.935Z","updated_at":"2019-02-04T06:09:23.935Z","content_type":"image/jpeg","file_size":"152780","filename":"schema.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-05T09:34:07.341Z","user":"blt0ac59771801e2eb09befe680"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt382664fd579c9334/5c57d713516e21cf0b2a0f83/schema.jpg"},"main_header":{"title_l10n":"Introducing the Elastic Common Schema","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"4797","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWhether you’re conducting security analytics, operations analytics, or a different use case altogether, you likely perform centralized analysis of data from diverse sources. Wouldn’t it be useful if you could apply a common data model to all that data to simplify the cross-source analysis and correlation? Say hello to the Elastic Common Schema!\u003cbr\u003e\u003c/p\u003e\u003cp\u003eThe Elastic Common Schema (ECS) defines a common set of fields and naming guidelines for ingesting data into Elasticsearch, helping you correlate data from diverse vendors and technologies (e.g., Apache web logs, Cisco NetFlow, Tanium endpoint events). Whether you’re searching your data, exploring it with Kibana, configuring a machine learning job, or configuring an alert, ECS will enhance your productivity and power.\u003c/p\u003e\u003cp\u003eThis webinar will include:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003cspan style=\"font-size: 1em;\"\u003eAn overview of ECS and its benefits\u003c/span\u003e\u003c/li\u003e\u003cli\u003e\u003cspan style=\"font-size: 1em;\"\u003e\u003c/span\u003eA demo for implementing ECS\u003c/li\u003e\u003cli\u003eBest practices for using ECS for your data\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eResources:\u003c/p\u003e\u003cul\u003e\u003cli\u003eView the \u003ca href=\"https://github.com/elastic/ecs\"\u003eECS GitHub repository\u003c/a\u003e to find a list of standard fields, a contribution guide, and more\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2019-02-12T17:00:00.000Z","presenter":["blt0dbe04e5acc0f969","bltb94a4ee45f7fae74","blt16a7e55c02b91c17"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Introducing the Elastic Common Schema","seo_description_l10n":"The Elastic Common Schema (ECS) defines a common set of fields and naming guidelines for ingesting data into Elasticsearch, helping you correlate data from diverse vendors and technologies (e.g., Apache web logs, Cisco NetFlow, Tanium endpoint events). Whether you’re searching your data, exploring it with Kibana, configuring a machine learning job, or configuring an alert, ECS will enhance your productivity and power.","seo_keywords_l10n":"Elastic, Elasticsearch, ELK, ELK Stack, Elastic Stack, Common, Schema, Elastic Common Schema, ECS, Apache web logs, Cisco NetFlow, Tanium endpoint events, Kibana, machine learning, alert","seo_image":null,"noindex":false},"tags":["elasticsearch"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"title":"Visualizing","label_l10n":"Visualizing","keyword":"visualizing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt365f9ed2d77755c7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:12.101Z","updated_at":"2020-06-17T03:38:12.101Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:12.100Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:48:22.629Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Introducing the Elastic Common Schema","token":"ii8gpwywiy","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-10T16:43:16.455Z","updated_by":"blt3044324473ef223b70bc674c","url":"/webinars/introducing-the-elastic-common-schema","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"9nCdkV5oM64cQp3hDqbDup","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-10T16:43:58.123Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt5ed46b2c2f2f513c","_version":23,"locale":"en-us","ACL":{},"created_at":"2019-02-21T14:01:35.642Z","created_by":"blt5280857d9e24912bc99a2478","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"bltae230213b0a8297c","created_by":"blt5280857d9e24912bc99a2478","updated_by":"blt5280857d9e24912bc99a2478","created_at":"2019-02-27T00:34:06.372Z","updated_at":"2019-02-27T00:34:06.372Z","content_type":"image/png","file_size":"165579","filename":"uptime.png","title":"uptime.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-27T21:47:47.711Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltae230213b0a8297c/5c75dafe2b22f9f161d6f994/uptime.png"},"main_header":{"title_l10n":"Elastic Uptime: Actively Monitor the Availability of Your Systems and Services","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4342","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"6083","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWeb applications continue to rely on an increasing number of services, both internal and external. Operation teams face a wider footprint of things to monitor that are not all in their control. By using the new Elastic Uptime solution, they can detect when services are down or responding slowly. With alerting, they can get proactively notified even before those services are called by the application. If you are already sending logs and metrics to Elasticsearch, the new Uptime solution expands your observability effort into a new dimension. If you’re new to the Elastic Stack, Elastic Uptime is a great way to get started with observability.\u003cbr\u003e\u003c/p\u003e\u003cp\u003eIn this video you'll learn:\u003c/p\u003e\u003cul\u003e\u003cli\u003eThe benefits of actively monitoring the services you rely on\u003c/li\u003e\u003cli\u003eAn overview of the Elastic Uptime solution\u003c/li\u003e\u003cli\u003eHow to configure Heartbeat to send uptime data to your Elasticsearch cluster (on prem or in Elastic Cloud)\u003c/li\u003e\u003cli\u003eHow to take advantage of machine learning and alerting with your uptime data\u003c/li\u003e\u003c/ul\u003e\u003cp\u003eRelated Content:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"/beats/heartbeat\"\u003eHeartbeat - Lightweight Shipper for Uptime Monitoring\u003c/a\u003e \u003c/li\u003e\u003cli\u003e\u003ca href=\"/blog/uptime-monitoring-with-heartbeat-and-the-elastic-stack\"\u003eUptime Monitoring with Heartbeat and the Elastic Stack\u003c/a\u003e \u003c/li\u003e\u003cli\u003e\u003ca href=\"/guide/en/beats/heartbeat/6.6/heartbeat-overview.html\"\u003eHeartbeat Overview\u003c/a\u003e \u003c/li\u003e\u003cli\u003e\u003ca href=\"/webinars/using-elastic-beats-and-apm-to-monitor-your-openshift-data\"\u003eUsing Elasticsearch, Beats and Elastic APM to monitor your OpenShift Data\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2019-03-27T16:00:00.000Z","presenter":["blt7b7f066c1eeda22d"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Elastic Uptime: Actively Monitor the Availability of Your Systems and Services","seo_description_l10n":"Web applications continue to rely on an increasing number of services, both internal and external. Operation teams face a wider footprint of things to monitor that are not all in their control. By using the new Elastic Uptime solution, they can detect when services are down or responding slowly. With alerting, they can get proactively notified even before those services are called by the application. If you are already sending logs and metrics to Elasticsearch, the new Uptime solution expands your observability effort into a new dimension. If you’re new to the Elastic Stack, Elastic Uptime is a great way to get started with observability.","seo_keywords_l10n":"Elastic, Elastic Stack, ELK, ELK Stack, Elasticsearch, monitor, monitoring, Elastic Uptime, uptime, Heartbeat, Elasticsearch cluster, machine learning, alerting","seo_image":{"uid":"bltae230213b0a8297c","created_by":"blt5280857d9e24912bc99a2478","updated_by":"blt5280857d9e24912bc99a2478","created_at":"2019-02-27T00:34:06.372Z","updated_at":"2019-02-27T00:34:06.372Z","content_type":"image/png","file_size":"165579","filename":"uptime.png","title":"uptime.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-27T21:47:47.711Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltae230213b0a8297c/5c75dafe2b22f9f161d6f994/uptime.png"},"noindex":false},"tags":["uptime","monitoring","machine learning","alerting"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltb5a7ebf330c5002e","ACL":{},"created_at":"2020-06-17T03:36:14.548Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2020-06-17T03:36:14.548Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.244Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Getting started","label_l10n":"Getting started","keyword":"getting-started","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt30953f4176054d3f","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:25.148Z","updated_at":"2020-06-17T03:37:25.148Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:25.148Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-01-07T18:03:25.028Z","user":"blt36e890d06c5ec32c"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"title":"Alerting","label_l10n":"Alerting","keyword":"alerting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd8e03b8972ecf817","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:20.375Z","updated_at":"2020-06-17T03:38:20.375Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:20.374Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:49:19.650Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt2e5ece40473e6b0a","ACL":{},"created_at":"2020-06-17T03:32:06.756Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"log-analytics","label_l10n":"Log analytics","tags":[],"title":"Log analytics","updated_at":"2020-07-06T22:20:10.220Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.397Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt60e4f8c6c19cebb7","ACL":{},"created_at":"2020-06-17T03:32:19.868Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"metrics","label_l10n":"Metrics","tags":[],"title":"Metrics","updated_at":"2020-07-06T22:20:08.577Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.406Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltb249a1eeba77b317","ACL":{},"created_at":"2020-06-17T03:31:53.522Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"apm","label_l10n":"APM","tags":[],"title":"APM","updated_at":"2020-07-06T22:20:22.552Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.550Z","user":"blt4b2e1169881270a8"}},{"_version":7,"locale":"en-us","uid":"bltab0bd43c3f7d586d","ACL":{},"created_at":"2020-06-17T03:32:33.672Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"uptime-monitoring","label_l10n":"Uptime monitoring","tags":[],"title":"Uptime monitoring","updated_at":"2021-04-09T06:48:48.376Z","updated_by":"bltcb593abdd43b4039","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.250Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Elastic Uptime: Actively monitor the availability of your systems and services","token":"jrytc6fjue","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-10T16:42:38.310Z","updated_by":"blt3044324473ef223b70bc674c","url":"/webinars/elastic-uptime-monitoring-actively-monitor-the-availability-of-your-systems-and-services","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"yWFcwqWjuLfqScvFCVRtmE","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-10T16:42:55.600Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6e440239b7e08cf1","_version":29,"locale":"en-us","ACL":{},"created_at":"2019-04-05T14:54:08.925Z","created_by":"blt5280857d9e24912bc99a2478","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"bltbe089d60ac2113e2","created_by":"blt5280857d9e24912bc99a2478","updated_by":"blt5280857d9e24912bc99a2478","created_at":"2019-04-08T16:56:52.877Z","updated_at":"2019-04-08T16:56:52.877Z","content_type":"image/jpeg","file_size":"183096","filename":"spotting-security-anomalies.jpg","title":"spotting-security-anomalies.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-08T16:58:15.816Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbe089d60ac2113e2/5cab7d54037f9c9d783e6dd3/spotting-security-anomalies.jpg"},"main_header":{"title_l10n":"Spotting Security Anomalies with the new Elasticsearch Maps and Uptime features in the Elastic (ELK) Stack","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4342","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"6083","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWith the launch of \"\u003ca href=\"/solutions/maps\"\u003eMaps\u003c/a\u003e\" and \"\u003ca href=\"/solutions/uptime-monitoring\"\u003eUptime\u003c/a\u003e\", we’ve given users of the Elastic Stack even more ways of analysing data sets and spotting issues within their environments. The use of these features may be fairly obvious in a network operations, business analytics or operational analytics context - but what about security operations?\u003cbr\u003e\n\u003c/p\u003e\u003cp\u003eElastic’s lightweight heartbeat agent can periodically monitor several network services such as http(s), TCP and ICMP endpoints. Within seconds, the data finds its way into Elasticsearch and is immediately viewable in the new curated uptime UI. We have other beats such as Filebeat and Packetbeat, as well as logstash plugins, which can gather data sources with IP addresses and enrich them with geo location information. Now, with a dedicated UI for maps, we can layer several different data sources which contain geo points, aggregate them, correlate against other metrics, and more.\n\u003c/p\u003e\u003cp\u003eIn this webinar, James Spiteri, Elastic Solutions Architect, Cyber Security Specialist, and Nicholas Palmer, Elastic Solutions Architect, show you how one can use the Maps and Uptime features to spot anomalies in security data sets.\u0026nbsp;\n\u003c/p\u003e\u003cp\u003eThis\u0026nbsp;demo will show:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eHow to use heartbeat and uptime to spot potential security anomalies (WAF failures, TLS certificate expiry, irregular latency etc).\u003c/li\u003e\n\t\u003cli\u003eUsing maps to layer several different security data sources with geo points\u003c/li\u003e\n\t\u003cli\u003eCreate machine learning jobs and alerts based on the heartbeat datasets\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003eAdditional Resources:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eDocs\n\t\u003cul\u003e\n\t\t\u003cli\u003e\u003ca href=\"/guide/en/beats/heartbeat/current/heartbeat-getting-started.html\"\u003eGetting Started with Heartbeat\u003c/a\u003e \u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\t\u003cli\u003eBlog\n\t\u003cul\u003e\n\t\t\u003cli\u003e\u003ca href=\"/blog/elastic-uptime-monitoring-solution-released\"\u003eUptime Introduction Blog\u003c/a\u003e\u003c/li\u003e\n\t\u003c/ul\u003e\n\t\u003cul\u003e\n\t\t\u003cli\u003e\u003ca href=\"/blog/elastic-maps-beta-released\"\u003eElastic Maps Released\u003c/a\u003e\u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\t\u003cli\u003eVideos\n\t\u003cul\u003e\n\t\t\u003cli\u003e\u003ca href=\"/webinars/elastic-maps-for-geospatial-analysis\"\u003eElastic Maps for Geospatial Analysis\u003c/a\u003e\u003c/li\u003e\n\t\t\u003cli\u003e\u003ca href=\"/webinars/elastic-uptime-monitoring-actively-monitor-the-availability-of-your-systems-and-services\"\u003eElastic Uptime: Actively Monitor the Availability of Your Systems and Services\u003c/a\u003e\u003c/li\u003e\n\t\u003c/ul\u003e\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2019-04-18T08:00:00.000Z","presenter":["blt47281ee31f9b7aa9","bltcf0784b64eb8a96d"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Spotting Security Anomalies with the new Elasticsearch Maps and Uptime features in the Elastic (ELK) Stack","seo_description_l10n":"Elastic’s lightweight heartbeat agent can periodically monitor several network services such as http(s), TCP and ICMP endpoints. Within seconds, the data finds its way into Elasticsearch and is immediately viewable in the new curated uptime UI. We have other beats such as Filebeat and Packetbeat, as well as logstash plugins, which can gather data sources with IP addresses and enrich them with geo location information. Now, with a dedicated UI for maps, we can layer several different data sources which contain geo points, aggregate them, correlate against other metrics, and more.","seo_keywords_l10n":"ELK, ELK Stack, Elastic, Elasticsearch, elasticsearch, TCP, ICMP, Filebeat, Uptime, UI, Packbeat, logstash, geo, maps","seo_image":{"uid":"bltbe089d60ac2113e2","created_by":"blt5280857d9e24912bc99a2478","updated_by":"blt5280857d9e24912bc99a2478","created_at":"2019-04-08T16:56:52.877Z","updated_at":"2019-04-08T16:56:52.877Z","content_type":"image/jpeg","file_size":"183096","filename":"spotting-security-anomalies.jpg","title":"spotting-security-anomalies.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-04-08T16:58:15.816Z","user":"blt5280857d9e24912bc99a2478"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbe089d60ac2113e2/5cab7d54037f9c9d783e6dd3/spotting-security-anomalies.jpg"},"noindex":false},"tags":["security","uptime","maps"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltb5a7ebf330c5002e","ACL":{},"created_at":"2020-06-17T03:36:14.548Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2020-06-17T03:36:14.548Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.244Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"title":"Visualizing","label_l10n":"Visualizing","keyword":"visualizing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt365f9ed2d77755c7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:12.101Z","updated_at":"2020-06-17T03:38:12.101Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:12.100Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:48:22.629Z","user":"blt3044324473ef223b70bc674c"}},{"title":"Machine learning","label_l10n":"Machine learning","keyword":"machine-learning","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt65b9df038275be61","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:34.860Z","updated_at":"2020-06-17T03:38:46.799Z","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:34.860Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-01T17:16:32.546Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt8a7a5ea52ac5d888","ACL":{},"created_at":"2020-06-17T03:30:37.843Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"observability","label_l10n":"Observability","tags":[],"title":"Observability","updated_at":"2020-07-06T22:20:06.879Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:33.411Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt569b48df66a9ba5d","ACL":{},"created_at":"2020-06-17T03:30:49.259Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"security","label_l10n":"Security","tags":[],"title":"Security","updated_at":"2020-07-06T22:20:03.211Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:19.430Z","user":"blt4b2e1169881270a8"}},{"_version":7,"locale":"en-us","uid":"bltab0bd43c3f7d586d","ACL":{},"created_at":"2020-06-17T03:32:33.672Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":true,"keyword":"uptime-monitoring","label_l10n":"Uptime monitoring","tags":[],"title":"Uptime monitoring","updated_at":"2021-04-09T06:48:48.376Z","updated_by":"bltcb593abdd43b4039","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.250Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltd609f5ed6cf2db23","ACL":{},"created_at":"2020-06-17T03:33:07.306Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"geospatial","label_l10n":"Geospatial","tags":[],"title":"Geospatial","updated_at":"2020-07-06T22:20:11.933Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.430Z","user":"blt36e890d06c5ec32c"}}],"timezone":{"title_l10n":"","url":""},"title":"Spotting Security Anomalies with the new Elasticsearch Maps and Uptime features in the Elastic (ELK) Stack","token":"fmqr00vzy5","translated_date_l10n":"","translated_time_l10n":"9 am BST / 10 am CEST / 4 pm SGT","updated_at":"2025-03-10T16:41:54.604Z","updated_by":"blt3044324473ef223b70bc674c","url":"/webinars/spotting-security-anomalies-with-the-new-elasticsearch-maps-and-uptime-features-in-the-elastic-elk-stack","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"9NDWfDhacSpXt1gCKefyQe","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-10T16:42:15.159Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltdc1d04aeda803ff2","_version":25,"locale":"en-us","ACL":{},"created_at":"2019-05-02T22:15:02.564Z","created_by":"blta5fd9e464c6ed162","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt643d8df6107ea0b3","created_by":"blta5fd9e464c6ed162","updated_by":"blta5fd9e464c6ed162","created_at":"2019-05-06T20:29:48.262Z","updated_at":"2019-05-06T20:29:48.262Z","content_type":"image/jpeg","file_size":"175683","filename":"IMAGE1-elastic-enterprise-search-ui-better.jpg","title":"IMAGE1-elastic-enterprise-search-ui-better.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-05-06T20:56:11.900Z","user":"blta5fd9e464c6ed162"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt643d8df6107ea0b3/5cd0993cdce922a269a6129c/IMAGE1-elastic-enterprise-search-ui-better.jpg"},"main_header":{"title_l10n":"Getting started with Elastic Enterprise Search (Beta)","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eNote (January 27, 2020):\u003c/strong\u003e The Elastic Enterprise Search product has been renamed to Elastic Workplace Search. Our suite of search products — \u003ca href=\"https://www.elastic.co/app-search\" target=\"_blank\"\u003eApp Search\u003c/a\u003e, \u003ca href=\"https://www.elastic.co/site-search\" target=\"_blank\"\u003eSite Search\u003c/a\u003e, and \u003ca href=\"https://www.elastic.co/workplace-search\" target=\"_blank\"\u003eWorkplace Search\u003c/a\u003e — are now a part of our broader \u003ca href=\"https://www.elastic.co/enterprise-search\" target=\"_blank\"\u003eElastic Enterprise Search\u003c/a\u003e solution.\n\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWith its ease of deployment, pre-tuned relevance, intuitive interface, and hassle-free administration, Elastic Enterprise Search (Beta) provides a powerful yet simple way to apply the relevance, scale, and speed of Elasticsearch to your organizational search needs. When you create a single source of truth, people can spend less time finding and more time doing.\u003cbr\u003e\u003c/p\u003e\u003cp\u003eLearn how to spin up the all-new Elastic Enterprise Search on your own hardware at no charge during the beta period, and start instantly indexing content across a variety of common cloud applications (Salesforce, Dropbox, Drive, GitHub, or connect to any source with the Custom Source API).\n\u003c/p\u003e\u003cp\u003eWebinar Highlights:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003eGet a rundown of downloading, prerequisites, and beta details \u003c/li\u003e\n\t\u003cli\u003eReview common cloud and enterprise data sources\u003c/li\u003e\n\t\u003cli\u003eUnderstand different search capabilities: weights, autocomplete, facets, and more\u003c/li\u003e\n\t\u003cli\u003eMonitor and customize the search experience\u003c/li\u003e\n\t\u003cli\u003eLearn how to get involved in the Elastic community\u003c/li\u003e\n\u003c/ul\u003e\u003cp\u003e\u003cbr\u003e\u003c/p\u003e\u003cp\u003eAdditional Resources:\n\u003c/p\u003e\u003cul\u003e\n\t\u003cli\u003e\u003ca href=\"https://elastic.co/downloads/enterprise-search\"\u003eDownload Enterprise Search Beta\u003c/a\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://swiftype.com/documentation/enterprise-search\"\u003eDocumentation\u003c/a\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://elastic.co/blog/elastic-enterprise-search-beta1-released\"\u003eBlog post\u003c/a\u003e\u003c/li\u003e\n\t\u003cli\u003e\u003ca href=\"https://elastic.co/solutions/enterprise-search\"\u003eEnterprise Search Solution\u003c/a\u003e\u003c/li\u003e\n\u003c/ul\u003e","presentation_date":"2019-06-05T16:00:00.000Z","presenter":["blt6f8c1e29600b488b","blt70c76c99e0846d48"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Getting started with Elastic Enterprise Search (Beta)","seo_description_l10n":"With its ease of deployment, pre-tuned relevance, intuitive interface, and hassle-free administration, Elastic Enterprise Search (Beta) provides a powerful yet simple way to apply the relevance, scale, and speed of Elasticsearch to your organizational search needs.","seo_keywords_l10n":"enterprise search, elastic enterprise search","seo_image":null,"noindex":false},"tags":["enterprise search"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[{"_version":3,"locale":"en-us","uid":"blt10eb11313dc454f1","ACL":{},"created_at":"2020-06-17T03:30:26.497Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"enterprise-search","label_l10n":"Search","tags":[],"title":"Search","updated_at":"2023-07-19T16:04:51.718Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.232Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"blt4607298d4fd82c81","ACL":{},"created_at":"2020-06-17T03:31:33.256Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"workplace-search","label_l10n":"Workplace search","tags":[],"title":"Workplace search","updated_at":"2020-07-06T22:19:56.394Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:28:53.167Z","user":"blt4b2e1169881270a8"}}],"timezone":{"title_l10n":"","url":""},"title":"Getting started with Elastic Enterprise Search (Beta)","token":"hDHHoz425V","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-10T16:40:57.654Z","updated_by":"blt3044324473ef223b70bc674c","url":"/webinars/getting-started-with-elastic-enterprise-search-beta","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"LLzZy8WpabFk1DdjB9XPvY","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-10T16:41:19.531Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt473a16a5cbcef8e7","_version":12,"locale":"en-us","ACL":{},"created_at":"2024-11-06T00:22:14.963Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Delivering ROI on AI: How AI transforms customer support efficiency","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eDiscover how a leading technology company built an AI assistant to increase customer and support efficiency and realized a return on investment in less than four months.\u003c/p\u003e\u003cp\u003eExperts from Microsoft, Elastic, and IDC discuss business and technical considerations of optimizing large language models (LLMs) for generative AI applications to deliver business value.\u003c/p\u003e\u003cp\u003eThis discussion will highlight the importance of cost-tracking, AI KPIs, and key business metrics, offering a clear roadmap to returns on your AI investment.\u003c/p\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eJoin our \u003ca href=\"http://events.elastic.co/microsoftworkshopshub/webinar\"\u003eMarch roundtables\u003c/a\u003e for an in-depth, in-person exploration. Meet experts and gain insights!\u003c/li\u003e\u003cli\u003eExcited about AI and like to get started? Visit our \u003ca href=\"https://azuremarketplace.microsoft.com/en-us/marketplace/apps/elastic.ec-azure-pp?ocid=microsoft-elastic-support-assistant\"\u003eAzure Marketplace listing.\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/portfolio/operationalizing-generative-ai-strategic-guide\" target=\"_self\"\u003eAn executive's guide to operationalizing generative AI\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/pdf/elastic-on-elastic-support-assistant.pdf\" target=\"_self\"\u003eElastic on Elastic: Support Assistant Case Study\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/platform\" target=\"_self\"\u003eLearn how to use your data in real time with the Elastic Search AI Platform\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-01-28T21:00:00.000Z","presenter":["blt53f53e1c547f2110","blt57f0334083eb9790","blte0652df2f117e695","blt089f6ddbd5d28a07"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":1,"locale":"en-us","uid":"bltf4c15a435ded5722","ACL":{},"created_at":"2021-04-13T17:54:31.202Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"europe","label_l10n":"Europe","tags":[],"title":"Europe","updated_at":"2021-04-13T17:54:31.202Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-10T12:13:00.412Z","user":"blt3e52848e0cb3c394"}},{"_version":1,"locale":"en-us","uid":"bltdabf9ea82c489dad","ACL":{},"created_at":"2023-06-27T17:09:23.025Z","created_by":"blt36e890d06c5ec32c","hidden_value":false,"keyword":"india","label_l10n":"India","tags":[],"title":"India","updated_at":"2023-06-27T17:09:23.025Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-06-27T17:09:25.693Z","user":"blt36e890d06c5ec32c"}},{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Delivering ROI on AI: How AI transforms customer support efficiency","token":"5346","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-10T16:22:01.618Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/microsoft-elastic-support-assistant","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"KFJherZAs6jxzV7EyaAUVn","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-10T16:22:07.028Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6bcafd2e9d5c3727","_version":11,"locale":"en-us","ACL":{},"created_at":"2025-01-03T22:49:55.229Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"2025 technical trends: Embracing the era of choice to bring GenAI into production","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"12485","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eAs the landscape of artificial intelligence continues to evolve at an unprecedented pace, 2025 is poised to be the year where choices redefine the future of technology.\u003c/p\u003e\u003cp\u003eOur upcoming virtual event delves into the emerging technical trends in search and highlights the transformative potential of generative AI (GenAI) as ideas move from experimentation to production. Join industry leaders, AI pioneers, and technical experts as we explore the critical decisions that will shape the deployment of GenAI in the coming year.\u003c/p\u003e\u003cp\u003eThis event is designed for technical leaders, data scientists, AI practitioners, and developers who are keen on understanding the pivotal trends and choices that will drive GenAI in 2025. Learn how to stay ahead of the curve by successfully bringing GenAI solutions into production, heralding a new era of technological innovation and operational excellence.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cul\u003e\u003cli\u003e\u003cstrong\u003eChoice of AI Providers:\u003c/strong\u003e Examine the expanding ecosystem of GenAI technology, comparing offerings from various providers. Understand the implications of choosing the right model based on factors such as performance, cost, and ethical considerations.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eWorkflow Customization:\u003c/strong\u003e Discover innovative tools and frameworks that enable streamlined creation and deployment of AI workflows like retrieval augmented generation (RAG). Learn how to meet specific business needs with tailored solutions that ensure scalability and efficiency.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eIntegrations:\u003c/strong\u003e Identify best practices for integrating GenAI into existing systems and workflows. Explore strategies to ensure compatibility and seamless operation across environments.\u003c/li\u003e\u003cli\u003e\u003cstrong\u003eFuture-Proofing AI Investments:\u003c/strong\u003e Learn how to make strategic decisions that safeguard your AI investments against rapid technological changes and market shifts.\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eLooking for more general GenAI trends? Check out the \u003ca href=\"/resources/search/analyst-report/idc-how-advances-ai-changed-game\"\u003elatest research from IDC\u003c/a\u003e on how search has advanced in the era of AI.\u003c/li\u003e\u003cli\u003eExplore the \u003ca href=\"/partners/ai-ecosystem\"\u003eElastic AI Ecosystem,\u003c/a\u003e which offers developers prebuilt Elasticsearch vector database \u003ca href=\"https://www.elastic.co/search-labs/integrations\"\u003eintegrations\u003c/a\u003e from a trusted network of industry-leading AI companies.\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-02-27T17:00:00.000Z","presenter":["blt22c162f71dbc7943","blt6cc24a383769a34f","blt96df47be2dea5b85","blt9d00569d44cf03ea"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"2025 technical trends: Embracing the era of choice to bring GenAI into production","seo_description_l10n":"As organizations bring their GenAI experiences from experimentation to production, 2025 is poised to be the year where choices redefine the future of technology. ","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"2025 technical trends: Embracing the era of choice to bring GenAI into production","token":"9456508911","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T19:15:11.222Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/2025-technical-search-trends","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"d8pTymFG6ocuTdUpt8S11z","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-07T19:15:14.954Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0dcd30a4d5512c65","_version":2,"locale":"en-us","ACL":{},"created_at":"2025-03-06T19:28:15.985Z","created_by":"blt3044324473ef223b70bc674c","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"email_merchandising_placement_number":null,"description":""},"hour_time_format":false,"image":null,"main_header":{"topic_heading_l10n":"","title_l10n":"Analyzing the economic impact of AI-driven security analytics","paragraph_l10n":"","cta_list":{"cta_type":null,"cta_title_l10n":"","url":""}},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"16474","cta_title_l10n":"","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":""},"message_for_attendee":"","note":{"paragraph_l10n":"\u003cp\u003eAMER: 9:00 a.m. PDT, 12:00 p.m EDT \u003c/p\u003e\u003cp\u003eEMEA: 11:00 a.m. CEST, 2:30 p.m. IST \u003c/p\u003e\u003cp\u003eAPJ: 11:00 a.m. SGT, 2:00 p.m. AEDT\u003c/p\u003e"},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":"default"},"paragraph_l10n":"\u003cp\u003eEmpowering security team members to accelerate their operations is critical to the success of your SOC. But how is this possible when data volumes, attack surface, and costs are constantly growing? You need AI-driven security analytics.\u003c/p\u003e\u003cp\u003eJoin us in this webinar to explore how Sierra Nevada Corporation unlocked efficiencies with Elastic Security's AI-driven security analytics. Plus, learn about the economic impact Elastic Security is providing to teams through analysis from Informa TechTarget's Enterprise Strategy Group. You'll come away with best practices to share with your team, including tools and assets to substantiate your security investments.\u003c/p\u003e\u003ch4\u003eHighlights\u003c/h4\u003e\u003cp\u003eLearn how Elastic Security customers, including Sierra Nevada Corporation, realized the following:\u003c/p\u003e\u003cul\u003e\u003cli\u003e74% of full-time security employees' hours reclaimed\u003c/li\u003e\u003cli\u003e42%–56% reduction in the total cost of ownership\u003c/li\u003e\u003cli\u003e36% reduction in annual risk exposure\u003c/li\u003e\u003c/ul\u003e\u003ch4\u003eAdditional resources\u003c/h4\u003e\u003cul\u003e\u003cli\u003eIDC analyst report: \u003ca href=\"/explore/security-without-limits/elastic-ai-assistant-analyst-report\"\u003eThe Elastic AI Assistant Advantage\u003c/a\u003e\u003c/li\u003e\u003cli\u003eEMA analyst report: \u003ca href=\"/security/elastic-ai-assistant-simplifies-cybersecurity\"\u003eAI at your fingertips: How Elastic AI Assistant simplifies cybersecurity\u003c/a\u003e\u003c/li\u003e\u003cli\u003e\u003ca href=\"/lp/security/ai-assistant-resume\"\u003eElastic AI Assistant resume\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2025-04-16T17:00:00.000Z","presenter":["blt14f762eec103604e","blt02410229abe49649","bltc0a74c17a24dca91"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"Analyzing the economic impact of AI-driven security analytics","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[{"_version":7,"locale":"en-us","uid":"blt01715789a7031adc","ACL":{},"created_at":"2019-10-23T21:42:58.467Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"english","label_l10n":"English","tags":[],"title":"English","updated_at":"2020-12-02T19:17:31.532Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:44:09.411Z","user":"blt3044324473ef223b70bc674c"}}],"tags_region":[{"_version":4,"locale":"en-us","uid":"blt800f3049a517c000","ACL":{},"created_at":"2021-04-13T17:51:50.053Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"north-america","label_l10n":"North America","tags":[],"title":"North America","updated_at":"2024-04-17T07:38:48.383Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:47:41.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt0c39553861919e12","ACL":{},"created_at":"2020-11-13T00:08:13.750Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"emea","label_l10n":"EMEA","tags":[],"title":"EMEA","updated_at":"2020-11-13T00:08:13.750Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:45:29.115Z","user":"blt3044324473ef223b70bc674c"}},{"_version":8,"locale":"en-us","uid":"blt25a1df5963785e04","ACL":{},"created_at":"2022-09-07T08:10:02.602Z","created_by":"blt3e52848e0cb3c394","hidden_value":false,"keyword":"apac","label_l10n":"Asia/Pacific","tags":[],"title":"Asia/Pacific","updated_at":"2024-04-16T19:59:05.617Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-06T18:46:36.098Z","user":"blt3044324473ef223b70bc674c"}}],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Analyzing the economic impact of AI-driven security analytics","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T17:24:48.171Z","updated_by":"blt3044324473ef223b70bc674c","url":"/virtual-events/analyzing-the-economic-impact-of-ai-driven-security-analytics","video_type":["blt321a8ac0bef65269"],"vidyard":{"uuid":"","video_has_playlist":false,"data_chapter":""},"zoom_id":"","publish_details":{"time":"2025-03-11T20:03:32.774Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1e376f7b498fe403","_version":9,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:20:28.161Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"title":"New Geo Capabilities with 5.0.png","uid":"blt68edc0d86ef94edb","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T13:59:06.247Z","updated_at":"2019-02-04T13:59:06.247Z","content_type":"image/png","file_size":"27244","filename":"New_Geo_Capabilities_with_5.0.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:32:31.785Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt68edc0d86ef94edb/5c58452aeab90dd80b53f1f4/New_Geo_Capabilities_with_5.0.png"},"main_header":{"title_l10n":"New Geo Capabilities with 5.0","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","gdpr_load_id":"","success_message_l10n":"","cta_title_l10n":"","fallback":"","gdpr_text":[]},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eThe Elastic Stack 5.0 is released and part of the release was improved geo capabilities. \u0026nbsp;This webinar will cover everything you wanted to know about geo and Elasticsearch. Get advice on field mapping strategies, learn about geo aggregations and visualizations for exploratory spatial data analysis, as well as get insights into new spatial data structures being added to Lucene and Elasticsearch.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eAgenda Includes:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eElastic Stack 5.1 Overview\u003c/li\u003e\u003cli dir=\"ltr\"\u003eGeo field types\u003c/li\u003e\u003cli dir=\"ltr\"\u003eGeo indexing\u003c/li\u003e\u003cli dir=\"ltr\"\u003eGeo search\u003c/li\u003e\u003cli dir=\"ltr\"\u003eGeo aggregations\u003c/li\u003e\u003cli dir=\"ltr\"\u003eLive Q\u0026amp;A\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eIf you can’t join us live, register anyway and we’ll ship you the recording and slides.\u003c/p\u003e\u003cdiv\u003e\u003cbr /\u003e\u003c/div\u003e","presentation_date":"2016-12-20T17:00:00.000Z","presenter":["blt0683a897e123952b","blt33bd88de6b213c4f"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"blt8b37b4b3ec0fe838","ACL":{},"created_at":"2020-06-17T03:36:06.107Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"kibana","label_l10n":"Kibana","tags":[],"title":"Kibana","updated_at":"2020-06-17T03:36:06.107Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.315Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Visualizing","label_l10n":"Visualizing","keyword":"visualizing","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt365f9ed2d77755c7","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:12.101Z","updated_at":"2020-06-17T03:38:12.101Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:12.100Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:48:22.629Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"bltd609f5ed6cf2db23","ACL":{},"created_at":"2020-06-17T03:33:07.306Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"geospatial","label_l10n":"Geospatial","tags":[],"title":"Geospatial","updated_at":"2020-07-06T22:20:11.933Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-03-23T17:30:22.430Z","user":"blt36e890d06c5ec32c"}}],"timezone":{"title_l10n":"","url":""},"title":"New Geo Capabilities with 5.0","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:28:38.715Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/new-geo-capabilities-for-elasticsearch-5.0","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"Hr4Y8ULHJ72RMZT4xPggTc","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:28:42.735Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd0e3be58c183881d","_version":8,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:10:47.828Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt028a8c04c57dab3a","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-10T09:55:49.409Z","updated_at":"2018-10-10T09:55:49.409Z","content_type":"image/jpeg","file_size":"66614","filename":"ingesting-more-with-elastic-webinar.jpg","title":"ingesting-more-with-elastic-webinar.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:40:51.565Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt028a8c04c57dab3a/5bbdcca520bcc78f36235ee5/ingesting-more-with-elastic-webinar.jpg"},"main_header":{"title_l10n":"Ingesting More with the Elastic Stack","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","gdpr_load_id":"","success_message_l10n":"","cta_title_l10n":"","fallback":"","gdpr_text":[]},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWe realize you have acres of data, and Elastic has the right tools to ingest and unify everything to your desire. Come join us to learn more about the Elastic ingestion suite and some use cases you can leverage to drive additional value. \u0026nbsp;We’ll stitch together popular data sources and show how to keep your in-flight data safe with our security features and integrations.\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eThe data ingestion journey with the Elastic Stack\u003c/li\u003e\u003cli dir=\"ltr\"\u003eLogstash and Beats use cases - you know, for ingest...\u003c/li\u003e\u003cli dir=\"ltr\"\u003eSecuring your data flow from end-to-end\u003c/li\u003e\u003cli dir=\"ltr\"\u003eHadoop \u0026amp; friends\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2016-05-25T16:00:00.000Z","presenter":["bltfe1fd513e0662fbc","bltac9c8eef342a33ed"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}},{"_version":1,"locale":"en-us","uid":"bltb5a7ebf330c5002e","ACL":{},"created_at":"2020-06-17T03:36:14.548Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"beats","label_l10n":"Beats","tags":[],"title":"Beats","updated_at":"2020-06-17T03:36:14.548Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.244Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Ingesting More with the Elastic Stack","token":"w1wpj5kemk","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:27:40.562Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/ingesting-more-with-the-elastic-stack","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"Z718CF23A5nRz7wQk4T52G","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:27:44.198Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt1d87eb8bf2bce5ca","_version":6,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:12:55.949Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt0cdbabdfd2a3893b","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T08:55:56.546Z","updated_at":"2018-10-09T08:55:56.546Z","content_type":"image/png","file_size":"20893","filename":"video-level-up-your-cluster.png","title":"video-level-up-your-cluster.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:39:13.630Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0cdbabdfd2a3893b/5bbc6d1cbecc14715d488a86/video-level-up-your-cluster.png"},"main_header":{"title_l10n":"Level Up Your Cluster: Upgrading Elasticsearch","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","gdpr_load_id":"","success_message_l10n":"","cta_title_l10n":"","fallback":"","gdpr_text":[]},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eFor some, upgrading can be the bane of their job. Does the latest version fix any bugs that affect my cluster? Will the new minor release break my system?\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"margin-top: 0pt;margin-bottom: 0pt;\" rel=\"margin-top: 0pt; margin-bottom: 0pt;\"\u003eOften, users decide to upgrade based on a new feature they need, or a bug fix that affects them. But upgrading can have other benefits, like improved performance and decreased index size. In this webinar, Ryan Ernst, Elastic Developer and Lucene Committer,\u0026nbsp;will explore why upgrading can help you, what questions to ask yourself before\u0026nbsp;upgrading, and how to actually perform that pesky upgrade with minimal misery.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eWatch now and download the latest version of \u003ca href=\"https://www.elastic.co/downloads/elasticsearch\" target=\"_blank\"\u003eElasticsearch\u003c/a\u003e.\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAlso, simplify your upgrade process and stay on the latest version of the stack by switching to Elasticsearch Service\u0026nbsp;with a \u003ca href=\"https://www.elastic.co/cloud/elasticsearch-service/signup?elektra=level-up-cluster-video\"\u003efree 14 day trial.\u003c/a\u003e\u0026nbsp;\u003c/p\u003e","presentation_date":"2015-06-30T16:00:00.000Z","presenter":["bltd9feb033b1349273"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["elasticsearch","webinar","developing"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Level Up Your Cluster: Upgrading Elasticsearch","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:26:34.009Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/upgrading-elasticsearch","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"VQhSCfkZuEQVXER4QT5zRf","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:26:37.930Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blta365672e5efc6a5d","_version":6,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:09:39.801Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt9d4080a08757453b","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T09:35:11.728Z","updated_at":"2018-10-09T09:35:11.728Z","content_type":"image/png","file_size":"11492","filename":"video-open-source-trends-insights.png","title":"video-open-source-trends-insights.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:41:37.717Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9d4080a08757453b/5bbc764f831347c0148ae69e/video-open-source-trends-insights.png"},"main_header":{"title_l10n":"Open Source Trends and Insights - A Conversation with the Experts","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"","gdpr_load_id":"","success_message_l10n":"","cta_title_l10n":"","fallback":"","gdpr_text":[]},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eJoin Elastic and 451 Research for a discussion on trends and developments in the open source landscape. Gaurav Gupta (Vice-President of Product Management, Elastic), Steve Mayzak (Senior Director of Worldwide Solutions Architecture at Elastic), and Jay Lyman (Research Manager at 451 Research) will cover growing top-down adoption of Open Source technologies, why companies buy subscriptions, trends in Shadow IT, and commercial drivers in Open Source.\u003c/p\u003e","presentation_date":"2015-09-16T16:00:00.000Z","presenter":["bltf8a28ed7f286abad","bltf7bd920c871e639e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Open Source Trends and Insights - A Conversation with the Experts","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:25:24.162Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/open-source-trends-and-insights","video_type":["blt0d07966d0c7cc2b8"],"vidyard":{"uuid":"yzLMNHCN7Uxr6AokdFRDfz","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:25:31.544Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd7206cb6bbeceb26","_version":7,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:58.241Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blteb61e45cffff3151","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T08:56:00.600Z","updated_at":"2018-10-09T08:56:00.600Z","content_type":"image/png","file_size":"10143","filename":"video-launch-evolve-elasticsearch-deployment.png","title":"video-launch-evolve-elasticsearch-deployment.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:21.189Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blteb61e45cffff3151/5bbc6d2063ed239936a7d91c/video-launch-evolve-elasticsearch-deployment.png"},"main_header":{"title_l10n":"Launch and Evolve Your Elasticsearch Deployment","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eIt’s no secret that Elasticsearch is easy to get up and running. Often, users get started solving one problem, say application search, and find they can tackle many more use cases, like log analytics, multi-language search, geospatial applications, and more. That’s what makes us, you know, elastic. \u0026nbsp;\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.499999942779541;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.499999942779541;margin-top:0pt;margin-bottom:0pt;\"\u003eIn this webinar, Christian Dahlqvist, Elastic Solutions Architect, will present best practices on how to easily get up and running with Elasticsearch. Salvatore Vadacca, Technical Team Leader, at JobRapido, will showcase real life examples about how JobRapido leveraged and expanded their Elasticsearch usage, from storing key values to:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.499999942779541;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.499999942779541;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eSearching across multiple languages (18 languages in 58 countries)\u003c/li\u003e\u003cli dir=\"ltr\"\u003eUsing the Elasticsearch percolator feature for\u0026nbsp;job classification\u003c/li\u003e\u003cli dir=\"ltr\"\u003eManaging and organizing job locations\u0026nbsp;with path analyzers\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2015-07-08T16:00:00.000Z","presenter":["blt9c76b7f20a136f34","blte305d0d8f427e122"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["elasticsearch","webinar","analytics","technology","scaling"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Launch and Evolve Your Elasticsearch Deployment","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:16:35.226Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/launch-and-evolve-your-es-deployment","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"wNHzmi6mqvqLMkYGG26hqY","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:16:38.759Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt9c0084614b17d7dc","_version":8,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:52.231Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt2aa48f474a83198c","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T09:17:44.638Z","updated_at":"2018-10-09T09:17:44.638Z","content_type":"image/png","file_size":"18978","filename":"video-elasticsearch-netsuite-speed-scale-security.png","title":"video-elasticsearch-netsuite-speed-scale-security.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:21.189Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt2aa48f474a83198c/5bbc72383bd14fb77f741b5c/video-elasticsearch-netsuite-speed-scale-security.png"},"main_header":{"title_l10n":"Elasticsearch at NetSuite: Speed, Scale, and Security","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eJoin us for a live webinar to hear Bryan Washer, Principal Site Reliability Engineer at NetSuite, discuss how NetSuite is scaling their Elasticsearch deployment to better serve their clients and internal needs.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eTopics covered:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eNetSuite’s Elasticsearch architecture to ingest 3 billion daily events\u003c/li\u003e\u003cli dir=\"ltr\"\u003eScale to handle a petabyte of data\u003c/li\u003e\u003cli dir=\"ltr\"\u003eMeet security needs like HIPAA, EU, PACRIM, PCI/DSS with Shield\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eBryan will be joined by Marty Messer, VP of Customer Care, and Steve Kearns, Director of Product Management.\u0026nbsp;\u003c/p\u003e","presentation_date":"2015-08-12T16:00:00.000Z","presenter":["bltda363d8e512a1c1e","blta88061c105b8011d","bltb068a3d5b604f364"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Monitoring","label_l10n":"Monitoring","keyword":"monitoring","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt018d981515b9a4fd","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:24.931Z","updated_at":"2020-06-17T03:39:59.356Z","ACL":{},"_version":2,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:24.931Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-02T18:15:31.077Z","user":"bltf6ab93733e4e3a73"}},{"title":"Scaling","label_l10n":"Scaling","keyword":"scaling","hidden_value":true,"tags":[],"locale":"en-us","uid":"bltbafe1bd178271a4e","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:40:27.127Z","updated_at":"2020-06-17T03:40:27.127Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:40:27.127Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-23T10:32:18.015Z","user":"blt3e52848e0cb3c394"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Elasticsearch at NetSuite: Speed, Scale, and Security","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:15:26.935Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/speed-scale-and-security","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"HMYWhzkDPc17KkGyopEtJx","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:15:30.543Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt342acba62c7f0c3d","_version":8,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:50.238Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt4b8b5f5984744f1f","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T09:17:35.139Z","updated_at":"2018-10-09T09:17:35.139Z","content_type":"image/png","file_size":"11298","filename":"video-logstash-plugins1-5.png","title":"video-logstash-plugins1-5.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:21.189Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt4b8b5f5984744f1f/5bbc722f7498f42b0c1a6275/video-logstash-plugins1-5.png"},"main_header":{"title_l10n":"Logstash Plugins Ecosystem and Security","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eJoin Logstash creator, Jordan Sissel and Logstash\u0026nbsp;Team Lead, Suyog Rao for a presentation and discussion on what’s new with Logstash 1.5 including:\u003cbr /\u003e\u003c/p\u003e\u0026gt;\u003cul\u003e\u003cli dir=\"ltr\"\u003eNew Plugin Ecosystem with Examples\u003c/li\u003e\u003cli dir=\"ltr\"\u003eIntegrating Logstash with Security\u0026nbsp;\u003c/li\u003e\u003cli dir=\"ltr\"\u003eAlerting and Logstash\u003c/li\u003e\u003c/ul\u003e\u003cp\u003e\u003cspan style=\"line-height: 1.6em;background-color: initial;\"\u003eDownload and start playing around with the latest version, \u003c/span\u003e\u003ca href=\"http://www.elastic.co/downloads/logstash\"\u003eLogstash 5.2.0\u003c/a\u003e\u003cbr /\u003e\u003c/p\u003e","presentation_date":"2015-08-19T16:00:00.000Z","presenter":["blt8ba74c7c0a468fe7","bltac9c8eef342a33ed"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["logstash","webinar"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt7bb6b1e9a797738f","ACL":{},"created_at":"2020-06-17T03:36:25.048Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"logstash","label_l10n":"Logstash","tags":[],"title":"Logstash","updated_at":"2020-06-17T03:36:25.048Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:19:34.237Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt8adcbb1adf4f30dc","ACL":{},"created_at":"2020-06-17T03:37:36.199Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack-security","label_l10n":"Stack security","tags":[],"title":"Stack security","updated_at":"2020-06-17T03:37:36.199Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-10-07T20:06:58.974Z","user":"blt36e890d06c5ec32c"}},{"title":"Ingesting","label_l10n":"Ingesting","keyword":"ingesting","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt886805f7b26ef356","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:37:57.513Z","updated_at":"2020-06-17T03:37:57.513Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:37:57.513Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-29T17:20:06.688Z","user":"bltea6cbb86fea188be"}},{"title":"Alerting","label_l10n":"Alerting","keyword":"alerting","hidden_value":false,"tags":[],"locale":"en-us","uid":"bltd8e03b8972ecf817","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:38:20.375Z","updated_at":"2020-06-17T03:38:20.375Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:38:20.374Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-07-06T00:49:19.650Z","user":"blt3044324473ef223b70bc674c"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Logstash Plugins Ecosystem and Security","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:14:31.911Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/logstash-1-5-plugins","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"nhSdvGYYuSW32NNLU2hz1k","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:14:36.152Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltd03ec406767eb1f6","_version":6,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:48.242Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt26f0a738c045b57d","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T09:35:09.651Z","updated_at":"2018-10-09T09:35:09.651Z","content_type":"image/png","file_size":"11376","filename":"video-kafka-integration.png","title":"video-kafka-integration.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:21.189Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt26f0a738c045b57d/5bbc764d63ed239936a7d9f2/video-kafka-integration.png"},"main_header":{"title_l10n":"Kafka Integration with the ELK Stack and its Use at LinkedIn","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eJoin LinkedIn Senior Site Reliability Engineer, Tin Le, and Elastic developer, Tal Levy, for a presentation and discussion on ways of using Kafka with Logstash \u0026amp; Elasticsearch.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eLearn how to scale Logstash using Kafka, including architecture and configuration, and hear from LinkedIn about how they are using Kafka with Elasticsearch to monitor their services.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eThis webinar will also cover:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eLogstash 1.5 Kafka input/output plugins\u003c/li\u003e\u003cli dir=\"ltr\"\u003eMonitoring Kafka JMX reporter statistics using the Elasticsearch, Logstash, and Kibana\u003c/li\u003e\u003cli dir=\"ltr\"\u003eLive Kibana demo to collect and analyze Kafka JMX bean statistics\u003c/li\u003e\u003cli dir=\"ltr\"\u003eLinkedIn’s use of Kafka and set-up to scale them to 875 billion daily messages and 700 TB/day\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2015-09-10T16:00:00.000Z","presenter":["blt62c6943dd5314c8c","blt4a614fc6690e9fb0","bltcf0a69ce766b1421"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Kafka Integration with the ELK Stack and its Use at LinkedIn","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:13:26.078Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/kafka-integration-with-elk","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"9Cfdo2X4A8kJ1ky4Sw7Bf5","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:13:29.916Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf90a3cae55393a6b","_version":6,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:38.231Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"bltce1ba7613020badf","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T10:42:18.033Z","updated_at":"2018-10-09T10:42:18.033Z","content_type":"image/png","file_size":"9736","filename":"video-whats-new-shield-watcher.png","title":"video-whats-new-shield-watcher.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:21.189Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltce1ba7613020badf/5bbc860ab160bf6a367eb83b/video-whats-new-shield-watcher.png"},"main_header":{"title_l10n":"What’s New with Shield and Watcher 2.0","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWe're thrilled to announce the release of Shield and Watcher 2.0. This is the first release of these extensions that is compatible with \u003ca href=\"https://www.elastic.co/blog/elasticsearch-2-0-0-released\" target=\"_blank\"\u003eElasticsearch 2.0\u003c/a\u003e. Beyond Elasticsearch 2.0 compatibility, Shield and Watcher 2.0 introduce several new and exciting features, expanding the security and alerting capabilities respectively.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 2.025;margin-top: 0pt;margin-bottom: 11pt;\" rel=\"line-height:2.025;margin-top:0pt;margin-bottom:11pt;\"\u003eJoin Uri Boness, Commercial Products Engineering Lead, for a webinar and Q\u0026amp;A session covering what’s new with Shield and Watcher 2.0 including:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 2.025;margin-top: 0pt;margin-bottom: 11pt;\"\u003e\u003cstrong\u003eShield\u003c/strong\u003e (for security)\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eExtensible Realms\u003c/li\u003e\u003cli dir=\"ltr\"\u003eField and Document ACL\u003c/li\u003e\u003cli dir=\"ltr\"\u003eUser Impersonation\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 2.025;margin-top: 0pt;margin-bottom: 11pt;\"\u003e\u003cstrong\u003eWatcher\u003c/strong\u003e (for alerting)\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eSlack and HipChat Integration\u003c/li\u003e\u003cli dir=\"ltr\"\u003eArray Compare Condition\u003c/li\u003e\u003cli dir=\"ltr\"\u003eWatch De/activation\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2015-12-02T17:00:00.000Z","presenter":["blta0594facbc6d6cf0"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"What’s New with Shield and Watcher 2.0","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:12:26.896Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/what-is-new-with-shield-and-watcher-2-0","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"YhZSTGdR5arWfytZ76Shpk","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:12:31.126Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt87fc6f165aaceb13","_version":7,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:34.219Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blta281dfdb1eeaed49","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T12:12:55.328Z","updated_at":"2018-10-09T12:12:55.328Z","content_type":"image/png","file_size":"16193","filename":"video-kibana-galaxy.png","title":"video-kibana-galaxy.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:37.490Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta281dfdb1eeaed49/5bbc9b4763ed239936a7db68/video-kibana-galaxy.png"},"main_header":{"title_l10n":"The Contributor's Guide to the Kibana Galaxy (Jan 2016)","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eExploring the expanse\u0026nbsp;of the Kibana galaxy alone can be daunting, but join us to discover the answer to the greatest question - how does it all work? We will venture into the belly of the beast to discover how Kibana works, and how you can modify and extend it.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 2.025;margin-top: 0pt;margin-bottom: 11pt;\" rel=\"line-height:2.025;margin-top:0pt;margin-bottom:11pt;\"\u003eIn this video, we will cover:\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eSetting up Kibana for Development\u003c/li\u003e\u003cli dir=\"ltr\"\u003eNavigating the expanse (source code)\u003c/li\u003e\u003cli dir=\"ltr\"\u003eSlaying space bugs\u003c/li\u003e\u003cli dir=\"ltr\"\u003ePreserving our prime directive (testing)\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 2.025;margin-top: 0pt;margin-bottom: 11pt;\"\u003eAttendees will leave this presentation with a deep understanding of how to tweak Kibana, how to spot it’s weaknesses and fix them, and how to share their efforts with the rest of the community via Github.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 2.025;margin-top: 0pt;margin-bottom: 11pt;\"\u003eAdditional Kibana Video:\u003c/p\u003e\u003cul\u003e\u003cli\u003e\u003ca href=\"https://www.elastic.co/webinars/kibana-101-get-started-with-visualizations\" target=\"_blank\"\u003eKibana 101: Getting Started with Visualizations\u003c/a\u003e\u003c/li\u003e\u003c/ul\u003e\u003cbr /\u003e","presentation_date":"2016-01-27T17:00:00.000Z","presenter":["blt2d395623cc3472a3"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["kibana","webinar","videos"],"tags_elastic_stack":[],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"The Contributor's Guide to the Kibana Galaxy (Jan 2016)","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:10:56.799Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/the-contributors-guide-to-the-kibana-galaxy","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"CU288duhB5kC7ekf5nfiDU","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:11:00.770Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt04b32cd4970ad8b6","_version":12,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:10:52.156Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt6911ca14acc20fd0","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-09T13:24:32.441Z","updated_at":"2018-10-09T13:24:32.441Z","content_type":"image/png","file_size":"29353","filename":"video-xpack-webinar.png","title":"video-xpack-webinar.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:50.744Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6911ca14acc20fd0/5bbcac107498f42b0c1a64ae/video-xpack-webinar.png"},"main_header":{"title_l10n":"Security Overview, Roadmap, and Demo","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4342","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eLearn about \u003ca href=\"https://www.elastic.co/products/x-pack/open\" target=\"_blank\"\u003eopening x-pack\u003c/a\u003e and our updated \u003ca href=\"https://www.elastic.co/subscriptions\" target=\"_blank\"\u003esubscription features.\u003c/a\u003e\u0026nbsp;\u003c/p\u003e\u003cp\u003eYour data is too important not to protect. Security is the best way to secure your cluster and your work. Join Jay Modi, Team Lead for Security, for a webinar and Q\u0026amp;A session covering an overview of security, sneak peek at what’s to come, and a live demo showing users how to migrate to X-Pack.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eSimple Security\u003c/p\u003e\u003cul class=\"list-black\"\u003e\u003cli dir=\"ltr\"\u003eUsername/password protection\u003c/li\u003e\u003c/ul\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eAdvanced Security When Needed\u003c/p\u003e\u003cul class=\"list-black\"\u003e\u003cli dir=\"ltr\"\u003eLDAP, Active Directory, and PKI Integration\u003c/li\u003e\u003cli dir=\"ltr\"\u003eRole-based access control\u003c/li\u003e\u003cli dir=\"ltr\"\u003eField and document level security\u003c/li\u003e\u003cli dir=\"ltr\"\u003eEncrypted communication\u003c/li\u003e\u003cli dir=\"ltr\"\u003eAuditing\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2016-04-26T16:00:00.000Z","presenter":["blt4aa00d198bbdaf6e"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["security"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"_version":1,"locale":"en-us","uid":"blt8adcbb1adf4f30dc","ACL":{},"created_at":"2020-06-17T03:37:36.199Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack-security","label_l10n":"Stack security","tags":[],"title":"Stack security","updated_at":"2020-06-17T03:37:36.199Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-10-07T20:06:58.974Z","user":"blt36e890d06c5ec32c"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Security Overview, Roadmap, and Demo","token":"r4g7kgstdd","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:09:26.957Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/x-pack-security-overview-roadmap-demo","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"3t3CC6ctFaAyxB3L4pJjV8","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:09:30.631Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt034705c4860f8894","_version":9,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:10:07.830Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"blt99a1909b9bb97234","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:06:17.834Z","updated_at":"2018-10-11T05:06:17.834Z","content_type":"image/png","file_size":"56885","filename":"video-proven-architectural-patterns.png","title":"video-proven-architectural-patterns.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:41:15.562Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt99a1909b9bb97234/5bbeda49c863b8e614126e50/video-proven-architectural-patterns.png"},"main_header":{"title_l10n":"Proven Architectural Patterns for Mature Elastic Stack Deployments","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4342","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eThe Elastic Stack is used to address a variety of needs, ranging dramatically in both complexity and scale. Components from Elastic can be deployed and configured uniquely for each implementation, so architecting a solution based on proven practices can both accelerate and de-risk projects. \u0026nbsp;Join Elasticsearch Solution Architects as they present reference architectures and proven practices in Elasticsearch deployments, ranging from high-volume log analytics to embedded search applications. \u0026nbsp; \u0026nbsp;\u0026nbsp;\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003eCommon patterns to be covered include:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eGetting started quickly-- show results in minutes\u003c/li\u003e\u003cli dir=\"ltr\"\u003eScaling to meet (the inevitable!) increasing demand\u003c/li\u003e\u003cli dir=\"ltr\"\u003eSupporting high-availability operations and resiliency\u003c/li\u003e\u003cli dir=\"ltr\"\u003eConsidering multiple data centers\u003c/li\u003e\u003cli dir=\"ltr\"\u003eCommon approaches to embedded and enterprise search\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2016-10-20T16:00:00.000Z","presenter":["blt446c17b51322cc82","blt29236ae1d2f00217"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[{"title":"Architecture","label_l10n":"Architecture","keyword":"architecture","hidden_value":true,"tags":[],"locale":"en-us","uid":"blt91896b1dfcbd6413","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:39:38.693Z","updated_at":"2020-06-17T03:39:38.693Z","ACL":{},"_version":1,"_workflow":{"uid":"blte3b720fd9661d254","updated_at":"2020-06-17T03:39:38.693Z","updated_by":"blt3044324473ef223b70bc674c","version":1},"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-06-24T15:31:11.375Z","user":"bltf6ab93733e4e3a73"}}],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Proven Architectural Patterns for Mature Elastic Stack Deployments","token":"r6hha2k8el","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:08:13.443Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/proven-architectural-patterns-for-mature-elastic-stack-deployments","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"anvSSq6EqWJ4GBXceVytdK","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:08:18.495Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltb432d0bac3d736da","_version":8,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:21:28.219Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"uid":"bltb55b137bf7560d9b","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2018-10-11T05:12:57.452Z","updated_at":"2018-10-11T05:12:57.452Z","content_type":"image/jpeg","file_size":"56584","filename":"elastic-stack-5-0-virtual-event.jpg","title":"elastic-stack-5-0-virtual-event.jpg","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:31:37.490Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb55b137bf7560d9b/5bbedbd911df34800cd949c6/elastic-stack-5-0-virtual-event.jpg"},"main_header":{"title_l10n":"Elastic Stack 5.0 Virtual Event","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4737","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eWith 5.0, everything you love about Elastic just got better. 5.0 is about our products working beautifully together, a simplified getting started experience, and a lot of great new features. In this video, the creators of the Elastic Stack tell the story behind 5.0 and introduce all the new and glorious features that make version 5.0 our biggest release yet.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eHighlights include:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eThe 5.0 Story with Shay\u003c/li\u003e\u003cli dir=\"ltr\"\u003eElasticsearch 5.0: What You Need to Know\u003c/li\u003e\u003cli dir=\"ltr\"\u003eKibana 5: It’s More Than Charts and Graphs\u003c/li\u003e\u003cli dir=\"ltr\"\u003eTimelion: Exploring Time Series Data\u003c/li\u003e\u003cli dir=\"ltr\"\u003eIngestion 5.0 Style with Logstash and Beats\u003c/li\u003e\u003cli dir=\"ltr\"\u003eExtend the Elastic Stack with X-Pack\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2016-11-03T15:00:00.000Z","presenter":["blt4990cfe37610ed0f","blta14bb0509c1528d3","blt717d62571a49ab4e","blt08a3f527ab2f0397","blt8ba74c7c0a468fe7","blt392d0d33022a47e8","blta88061c105b8011d"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Elastic Stack 5.0 Virtual Event","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:07:16.921Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/elastic-stack-5-0-virtual-event","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"hLhcWkMx2iNrzWKK3j5YSh","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:07:20.699Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"bltf8023a0ef28940d3","_version":7,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:10:43.846Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"title":"Tales from the field- Elastic Stack and Hadoop.png","uid":"blt9bbbead9d0cf031e","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T13:59:12.253Z","updated_at":"2019-02-04T13:59:12.253Z","content_type":"image/png","file_size":"33134","filename":"Tales_from_the_field-_Elastic_Stack_and_Hadoop.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:40:51.565Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9bbbead9d0cf031e/5c584530dfaabbd40b9c2c76/Tales_from_the_field-_Elastic_Stack_and_Hadoop.png"},"main_header":{"title_l10n":"Tales from the field: Elastic Stack and Hadoop","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"4642","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eHadoop is a great platform for storing and processing massive amounts of data. Elasticsearch is an ideal solution for real-time analytics and visualization of the same data. Join us to learn how you can leverage the full power of both platforms to maximize the value of your data. Learn about the ES-Hadoop connector and some common design patterns from real-world implementations.\u003cbr /\u003e\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eThis webinar will cover several use cases for using Elasticsearch with Hadoop including:\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\"\u003e\u003cbr /\u003e\u003c/p\u003e\u003cul\u003e\u003cli dir=\"ltr\"\u003eLambda Architecture\u003c/li\u003e\u003cli dir=\"ltr\"\u003eReal-time Architecture\u003c/li\u003e\u003cli dir=\"ltr\"\u003eMonitoring Hadoop\u003c/li\u003e\u003cli dir=\"ltr\"\u003eHDFS as back-up store\u003c/li\u003e\u003c/ul\u003e","presentation_date":"2017-02-28T17:00:00.000Z","presenter":["blt8344ec6cc0ffae54","bltef7fcd39f3071b57"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":["videos"],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Tales from the field: Elastic Stack and Hadoop","token":"zzyf1pcknr","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:05:42.705Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/elasticsearch-hadoop","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"8HH3EhUWkboRZPhe1AHhEt","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:05:46.410Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt6c428d61e5a27640","_version":10,"locale":"en-us","ACL":{},"created_at":"2019-02-05T07:20:40.185Z","created_by":"sys_blt57a423112de8a853","disclaimer":[],"do_not_display_on_overview_page":false,"email_merchandising":{"description":"","email_merchandising_placement_number":null},"hour_time_format":false,"image":{"title":"Painless - Secure Scripting Language for Elasticsearch | Elastic 2017-07-13 09-25-01.png","uid":"bltcbb4065ab422d574","created_by":"sys_blt57a423112de8a853","updated_by":"sys_blt57a423112de8a853","created_at":"2019-02-04T14:02:12.366Z","updated_at":"2019-02-04T14:02:12.366Z","content_type":"image/png","file_size":"28019","filename":"Painless_-_Secure_Scripting_Language_for_Elasticsearch_Elastic_2017-07-13_09-25-01.png","ACL":{},"_version":1,"is_dir":false,"tags":[],"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2019-02-11T09:32:09.607Z","user":"sys_blt57a423112de8a853"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltcbb4065ab422d574/5c5845e4eab90dd80b53f206/Painless_-_Secure_Scripting_Language_for_Elasticsearch_Elastic_2017-07-13_09-25-01.png"},"main_header":{"title_l10n":"Painless - Secure Scripting Language for Elasticsearch","cta_list":{"cta_title_l10n":"","cta_type":null,"url":""},"paragraph_l10n":"","topic_heading_l10n":""},"marketo":{"title_l10n":"","subtitle_l10n":"","marketo_load_id":"3819","success_message_l10n":"","fallback":"","gdpr_text":["bltd8d585d4734a50f6"],"gdpr_load_id":"","cta_title_l10n":""},"message_for_attendee":"","note":{"paragraph_l10n":""},"override_hosted_by_copy_l10n":"","page_layout":{"page_layout":null},"paragraph_l10n":"\u003cp\u003eBack in the pre-5.0 dark ages, Elasticsearch lacked a secure scripting language. And the people were sad! But our hero Painless came in 5.0, the shining new default, careful, quick, and kind. Ever watchful of its whitelist and loop counters, Painless protects Elasticsearch from malign mandate, inadvertent or iniquitous.\u003c/p\u003e\u003cp dir=\"ltr\" style=\"line-height: 1.38;margin-top: 0pt;margin-bottom: 0pt;\" rel=\"line-height:1.38;margin-top:0pt;margin-bottom:0pt;\"\u003eGather and hear of Painless' guiding principles, see the features they represent, and, time permitting, discuss Painless' future.\u003c/p\u003e\u003cdiv\u003e\u003cbr /\u003e\u003c/div\u003e","presentation_date":"2017-04-19T16:00:00.000Z","presenter":["blta5b9a463201a679d"],"sanity_migration_complete":false,"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null,"noindex":false},"tags":[],"tags_elastic_stack":[{"_version":1,"locale":"en-us","uid":"blt3d820a0eae1c9158","ACL":{},"created_at":"2020-06-17T03:35:53.368Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"elasticsearch","label_l10n":"Elasticsearch","tags":[],"title":"Elasticsearch","updated_at":"2020-06-17T03:35:53.368Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:24:20.290Z","user":"blt4b2e1169881270a8"}}],"tags_event_type":[{"title":"Webinars","label_l10n":"Webinars","keyword":"webinar","hidden_value":false,"tags":[],"locale":"en-us","uid":"blt7449a6fa428f966d","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2020-06-17T03:42:00.222Z","updated_at":"2022-08-25T18:09:24.790Z","ACL":{},"_version":10,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-26T01:40:17.963Z","user":"bltf020187e3918e5de"}}],"tags_event_type_delivery":[],"tags_industry":[],"tags_language":[],"tags_region":[],"tags_role":[],"tags_stage":[],"tags_technical_level":[],"tags_topic":[],"tags_use_case":[],"timezone":{"title_l10n":"","url":""},"title":"Painless - Secure Scripting Language for Elasticsearch","token":"","translated_date_l10n":"","translated_time_l10n":"","updated_at":"2025-03-07T15:04:25.652Z","updated_by":"blt3e52848e0cb3c394","url":"/webinars/painless-secure-scripting-language-for-elasticsearch","video_type":["bltdcadaef5bdccac7e"],"vidyard":{"uuid":"6GqgmseJ9u3V5WjZ7GipFA","data_chapter":"","video_has_playlist":false},"zoom_id":"","publish_details":{"time":"2025-03-07T15:04:29.235Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1532],"apiContent":{},"translateContent":[[{"uid":"bltfb44eb6e899331a4","_version":1,"locale":"en-us","ACL":{},"created_at":"2024-11-13T23:43:06.196Z","created_by":"blt36e890d06c5ec32c","english_content":"Or","tags":[],"title":"Or","translate_content_l10n":"Or","updated_at":"2024-11-13T23:43:06.196Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-11-13T23:44:21.198Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2aeecde6c1729945","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:02.610Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more","tags":[],"title":"Load more","translate_content_l10n":"Load more","updated_at":"2024-09-03T16:41:46.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-03T16:42:00.289Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt6f3ad4a078adc611","ACL":{},"created_at":"2024-05-28T12:47:25.539Z","created_by":"blt3e52848e0cb3c394","english_content":"Overview","tags":[],"title":"Overview","translate_content_l10n":"Overview","updated_at":"2024-05-28T12:47:25.539Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-28T12:47:29.022Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt3b08c089ffd331e6","ACL":{},"created_at":"2023-01-26T21:09:09.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","tags":[],"title":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","translate_content_l10n":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content.","updated_at":"2023-12-18T21:59:16.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:59:19.133Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt7a2b7e50bb030ed8","ACL":{},"created_at":"2023-01-26T21:09:00.746Z","created_by":"blt36e890d06c5ec32c","english_content":"You'll also receive an email with related content.","tags":[],"title":"You'll also receive an email with related content","translate_content_l10n":"You'll also receive an email with related content.","updated_at":"2023-12-18T21:58:39.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:58:43.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt7a2ecc87e95e0fed","ACL":{},"created_at":"2023-08-23T22:51:28.540Z","created_by":"blt36e890d06c5ec32c","english_content":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","tags":[],"title":"Newsletter GDPR Text","translate_content_l10n":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","updated_at":"2023-08-23T22:51:28.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T22:52:42.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16f2676801e3267e","ACL":{},"created_at":"2023-08-22T17:00:20.812Z","created_by":"blt36e890d06c5ec32c","english_content":"Speakers","tags":[],"title":"Speakers","translate_content_l10n":"Speakers","updated_at":"2023-08-22T17:00:20.812Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-22T17:01:19.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0cbc24c249b9fd54","ACL":{},"created_at":"2023-07-11T21:21:11.001Z","created_by":"blt3044324473ef223b70bc674c","english_content":"Close","tags":[],"title":"Close","translate_content_l10n":"Close","updated_at":"2023-07-11T21:21:11.001Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-11T21:22:26.797Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt20243cb3a8c574f6","ACL":{},"created_at":"2023-04-27T22:46:08.141Z","created_by":"blt36e890d06c5ec32c","english_content":"See more insights","tags":[],"title":"See more insights","translate_content_l10n":"See more insights","updated_at":"2023-04-27T22:46:08.141Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-27T22:47:17.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt5e35f797b223487b","ACL":{},"created_at":"2023-04-25T22:44:26.727Z","created_by":"blt36e890d06c5ec32c","english_content":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","tags":[],"title":"The content on this page is not available in the selected language.","translate_content_l10n":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","updated_at":"2023-04-25T22:50:03.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-25T22:50:49.263Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt95f1076dfef4f727","ACL":{},"created_at":"2023-04-03T16:58:30.945Z","created_by":"blt36e890d06c5ec32c","english_content":"Author","tags":[],"title":"Author","translate_content_l10n":"Author","updated_at":"2023-04-03T16:58:30.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:02:04.749Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltb9e7436e790dc1e1","ACL":{},"created_at":"2023-01-26T21:09:01.075Z","created_by":"blt36e890d06c5ec32c","english_content":"Learn more","tags":[],"title":"Learn more","translate_content_l10n":"Learn more","updated_at":"2023-03-23T23:23:32.443Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:25:05.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte80ec2bf93203454","ACL":{},"created_at":"2023-03-23T23:20:05.096Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now (no PT)","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:20:05.096Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:23:03.467Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt0b2b84aede5a5e1a","ACL":{},"created_at":"2023-01-26T21:09:00.911Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:17:38.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:19:07.965Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ad9978de13cb3c","ACL":{},"created_at":"2023-03-20T19:38:56.211Z","created_by":"blt36e890d06c5ec32c","english_content":"See all top stories","tags":[],"title":"See all top stories","translate_content_l10n":"See all top stories","updated_at":"2023-03-20T19:38:56.211Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:40:01.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0aeca091079429a4","ACL":{},"created_at":"2023-03-20T19:37:29.708Z","created_by":"blt36e890d06c5ec32c","english_content":"Related content","tags":[],"title":"Related content","translate_content_l10n":"Related content","updated_at":"2023-03-20T19:37:29.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:38:35.986Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltdedcc90f4b9d495c","ACL":{},"created_at":"2023-03-13T17:42:26.422Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All (no PT translation)","translate_content_l10n":"All","updated_at":"2023-03-13T18:12:39.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T18:13:09.648Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdafd9e19f8a295c9","ACL":{},"created_at":"2023-03-13T16:44:58.960Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact information","tags":[],"title":"Contact information","translate_content_l10n":"Contact information","updated_at":"2023-03-13T16:44:58.960Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:46:31.937Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d189cf8b1b80402","ACL":{},"created_at":"2023-03-13T16:43:08.761Z","created_by":"blt36e890d06c5ec32c","english_content":"Press Release","tags":[],"title":"Press Release","translate_content_l10n":"Press Release","updated_at":"2023-03-13T16:43:08.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:44:42.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb031798c593cf2aa","ACL":{},"created_at":"2023-03-06T17:39:15.553Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Reddit","tags":[],"title":"Share on Reddit","translate_content_l10n":"Share on Reddit","updated_at":"2023-03-06T17:39:15.553Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-06T17:40:52.751Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltc449b2f75825b408","ACL":{},"created_at":"2023-01-26T21:09:01.238Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories","tags":[],"title":"More stories","translate_content_l10n":"More stories","updated_at":"2023-02-23T22:39:49.208Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-23T22:40:59.356Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte38439477acb192e","ACL":{},"created_at":"2023-01-26T21:09:00.049Z","created_by":"blt36e890d06c5ec32c","english_content":"Articles by","tags":[],"title":"Articles by","translate_content_l10n":"Articles by","updated_at":"2023-02-23T22:11:25.304Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T16:57:47.130Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4b99c93b5338acdd","ACL":{},"created_at":"2023-02-16T17:26:10.103Z","created_by":"blt36e890d06c5ec32c","english_content":"Share this story","tags":[],"title":"Share this story","translate_content_l10n":"Share this story","updated_at":"2023-02-16T17:26:10.103Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-16T17:27:39.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte2e658dd90716f9f","ACL":{},"created_at":"2023-01-26T21:09:06.325Z","created_by":"blt36e890d06c5ec32c","english_content":"Share by Email","tags":[],"title":"Share by Email","translate_content_l10n":"Share by email","updated_at":"2023-02-14T18:05:54.924Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-14T18:06:40.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt622e2e6d3a2e469f","ACL":{},"created_at":"2023-01-26T21:09:09.950Z","created_by":"blt36e890d06c5ec32c","english_content":"Read less","tags":[],"title":"Read less","translate_content_l10n":"Read less","updated_at":"2023-01-26T21:09:09.950Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6e126363fe0669f","ACL":{},"created_at":"2023-01-26T21:09:09.794Z","created_by":"blt36e890d06c5ec32c","english_content":"Search Integrations","tags":[],"title":"Search Integrations","translate_content_l10n":"Search Integrations","updated_at":"2023-01-26T21:09:09.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.579Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfc60ac5a8053094c","ACL":{},"created_at":"2023-01-26T21:09:09.641Z","created_by":"blt36e890d06c5ec32c","english_content":"All Solutions","tags":[],"title":"All Solutions","translate_content_l10n":"All Solutions","updated_at":"2023-01-26T21:09:09.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.477Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c2c6a4e8cb5c2f0","ACL":{},"created_at":"2023-01-26T21:09:09.435Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for registering. We will send you a confirmation email soon.","tags":[],"title":"Thank you for registering. We will send you a confirmation email soon.","translate_content_l10n":"Thank you for registering. We will send you a confirmation email soon.","updated_at":"2023-01-26T21:09:09.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b837e25d93f5d3","ACL":{},"created_at":"2023-01-26T21:09:09.095Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for your interest!","tags":[],"title":"Thank you for your interest!","translate_content_l10n":"Thank you for your interest!","updated_at":"2023-01-26T21:09:09.095Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.784Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteecbf46e81d0d29d","ACL":{},"created_at":"2023-01-26T21:09:08.915Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Youtube","tags":[],"title":"Follow us on Youtube","translate_content_l10n":"Follow us on Youtube","updated_at":"2023-01-26T21:09:08.915Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.451Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dd2bbe9b12abe26","ACL":{},"created_at":"2023-01-26T21:09:08.754Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Twitter","tags":[],"title":"Follow us on Twitter","translate_content_l10n":"Follow us on Twitter","updated_at":"2023-01-26T21:09:08.754Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.917Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35eafbb82d26a869","ACL":{},"created_at":"2023-01-26T21:09:08.594Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on LinkedIn","tags":[],"title":"Follow us on LinkedIn","translate_content_l10n":"Follow us on LinkedIn","updated_at":"2023-01-26T21:09:08.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9667a9e201b264e5","ACL":{},"created_at":"2023-01-26T21:09:08.424Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Facebook","tags":[],"title":"Follow us on Facebook","translate_content_l10n":"Follow us on Facebook","updated_at":"2023-01-26T21:09:08.424Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.149Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafd12f73d268d939","ACL":{},"created_at":"2023-01-26T21:09:08.254Z","created_by":"blt36e890d06c5ec32c","english_content":"Headshot of","tags":[],"title":"Headshot of","translate_content_l10n":"Headshot of","updated_at":"2023-01-26T21:09:08.254Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.217Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteeffcd504c337777","ACL":{},"created_at":"2023-01-26T21:09:08.073Z","created_by":"blt36e890d06c5ec32c","english_content":"Table of contents","tags":[],"title":"Table of contents","translate_content_l10n":"Table of contents","updated_at":"2023-01-26T21:09:08.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.878Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1c9c25fdd610a988","ACL":{},"created_at":"2023-01-26T21:09:07.459Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All","translate_content_l10n":"All","updated_at":"2023-01-26T21:09:07.459Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.849Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcc368963ef15efcf","ACL":{},"created_at":"2023-01-26T21:09:07.299Z","created_by":"blt36e890d06c5ec32c","english_content":"Reset all","tags":[],"title":"Reset all","translate_content_l10n":"Reset all","updated_at":"2023-01-26T21:09:07.299Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.712Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf9e2c7ddef1476c","ACL":{},"created_at":"2023-01-26T21:09:07.138Z","created_by":"blt36e890d06c5ec32c","english_content":"Filters","tags":[],"title":"Filters","translate_content_l10n":"Filters","updated_at":"2023-01-26T21:09:07.138Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.405Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8186c36bcb7238","ACL":{},"created_at":"2023-01-26T21:09:06.974Z","created_by":"blt36e890d06c5ec32c","english_content":"Global Virtual Event","tags":[],"title":"Global Virtual Event","translate_content_l10n":"Global Virtual Event","updated_at":"2023-01-26T21:09:06.974Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.270Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4972bcd17a9589e","ACL":{},"created_at":"2023-01-26T21:09:06.815Z","created_by":"blt36e890d06c5ec32c","english_content":"View more posts","tags":[],"title":"View more posts","translate_content_l10n":"View more posts","updated_at":"2023-01-26T21:09:06.815Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.716Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7784639e8213f1de","ACL":{},"created_at":"2023-01-26T21:09:06.656Z","created_by":"blt36e890d06c5ec32c","english_content":"Print","tags":[],"title":"Print","translate_content_l10n":"Print","updated_at":"2023-01-26T21:09:06.656Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.409Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd160052884c85597","ACL":{},"created_at":"2023-01-26T21:09:06.489Z","created_by":"blt36e890d06c5ec32c","english_content":"Continue reading","tags":[],"title":"Continue reading","translate_content_l10n":"Continue reading","updated_at":"2023-01-26T21:09:06.489Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.383Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa2fe12d75e222b7","ACL":{},"created_at":"2023-01-26T21:09:06.160Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Facebook","tags":[],"title":"Share on Facebook","translate_content_l10n":"Share on Facebook","updated_at":"2023-01-26T21:09:06.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.521Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c65ce5e43c44d1e","ACL":{},"created_at":"2023-01-26T21:09:05.989Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on LinkedIn","tags":[],"title":"Share on LinkedIn","translate_content_l10n":"Share on LinkedIn","updated_at":"2023-01-26T21:09:05.989Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.207Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa64468770539e99","ACL":{},"created_at":"2023-01-26T21:09:05.807Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Twitter","tags":[],"title":"Share on Twitter","translate_content_l10n":"Share on Twitter","updated_at":"2023-01-26T21:09:05.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbf19c4f1958b7010","ACL":{},"created_at":"2023-01-26T21:09:05.653Z","created_by":"blt36e890d06c5ec32c","english_content":"Share","tags":[],"title":"Share","translate_content_l10n":"Share","updated_at":"2023-01-26T21:09:05.653Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.603Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd3ca82669f533596","ACL":{},"created_at":"2023-01-26T21:09:05.494Z","created_by":"blt36e890d06c5ec32c","english_content":"Small image for","tags":[],"title":"Small image for","translate_content_l10n":"Small image for","updated_at":"2023-01-26T21:09:05.494Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.766Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt665205a37a7b1a98","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:05.336Z","created_by":"blt36e890d06c5ec32c","english_content":"Video for","tags":[],"title":"Video for","translate_content_l10n":"Video for","updated_at":"2023-01-26T21:09:05.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:39:50.482Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt33215a82788dd3f2","ACL":{},"created_at":"2023-01-26T21:09:05.174Z","created_by":"blt36e890d06c5ec32c","english_content":"Explore similar demos","tags":[],"title":"Explore similar demos","translate_content_l10n":"Explore similar demos","updated_at":"2023-01-26T21:09:05.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt59af0058e6f2ab2c","ACL":{},"created_at":"2023-01-26T21:09:05.013Z","created_by":"blt36e890d06c5ec32c","english_content":"Register now","tags":[],"title":"Register now","translate_content_l10n":"Register now","updated_at":"2023-01-26T21:09:05.013Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.297Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt44f6c020ef294d34","ACL":{},"created_at":"2023-01-26T21:09:04.854Z","created_by":"blt36e890d06c5ec32c","english_content":"View next","tags":[],"title":"View next","translate_content_l10n":"View next","updated_at":"2023-01-26T21:09:04.854Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.641Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc455c56e1db3258","ACL":{},"created_at":"2023-01-26T21:09:04.701Z","created_by":"blt36e890d06c5ec32c","english_content":"Upcoming webinar","tags":[],"title":"Upcoming webinar","translate_content_l10n":"Upcoming webinar","updated_at":"2023-01-26T21:09:04.701Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.739Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt9e655ee3d1dbcd42","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.537Z","created_by":"blt36e890d06c5ec32c","english_content":"On-demand webinar","tags":[],"title":"On-demand webinar","translate_content_l10n":"On-demand webinar","updated_at":"2023-01-26T21:09:04.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:46:22.076Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd00860fb1d6f389b","ACL":{},"created_at":"2023-01-26T21:09:04.379Z","created_by":"blt36e890d06c5ec32c","english_content":"Featured webinar","tags":[],"title":"Featured webinar","translate_content_l10n":"Featured webinar","updated_at":"2023-01-26T21:09:04.379Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.328Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt335688b477b632cf","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.218Z","created_by":"blt36e890d06c5ec32c","english_content":"Highlights","tags":[],"title":"Highlights","translate_content_l10n":"Highlights","updated_at":"2023-01-26T21:09:04.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:31:29.622Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd90374b721d95342","ACL":{},"created_at":"2023-01-26T21:09:03.895Z","created_by":"blt36e890d06c5ec32c","english_content":"See when this webinar starts in my time zone","tags":[],"title":"See when this webinar starts in my time zone","translate_content_l10n":"See when this webinar starts in my time zone","updated_at":"2023-01-26T21:09:03.895Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.820Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt60fa8518500aa04e","ACL":{},"created_at":"2023-01-26T21:09:03.734Z","created_by":"blt36e890d06c5ec32c","english_content":"Related workshops","tags":[],"title":"Related workshops","translate_content_l10n":"Related workshops","updated_at":"2023-01-26T21:09:03.734Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.354Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fa14ebb51d2154f","ACL":{},"created_at":"2023-01-26T21:09:03.577Z","created_by":"blt36e890d06c5ec32c","english_content":"Hosted by","tags":[],"title":"Hosted by","translate_content_l10n":"Hosted by","updated_at":"2023-01-26T21:09:03.577Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.873Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltace88e420eb1dedb","ACL":{},"created_at":"2023-01-26T21:09:03.419Z","created_by":"blt36e890d06c5ec32c","english_content":"Agenda","tags":[],"title":"Agenda","translate_content_l10n":"Agenda","updated_at":"2023-01-26T21:09:03.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.193Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4e07248dad773e78","ACL":{},"created_at":"2023-01-26T21:09:03.260Z","created_by":"blt36e890d06c5ec32c","english_content":"Location","tags":[],"title":"Location","translate_content_l10n":"Location","updated_at":"2023-01-26T21:09:03.260Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd047722739355567","ACL":{},"created_at":"2023-01-26T21:09:03.106Z","created_by":"blt36e890d06c5ec32c","english_content":"Date","tags":[],"title":"Date","translate_content_l10n":"Date","updated_at":"2023-01-26T21:09:03.106Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.355Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt97cf5566d151b2d8","ACL":{},"created_at":"2023-01-26T21:09:02.936Z","created_by":"blt36e890d06c5ec32c","english_content":"More","tags":[],"title":"More","translate_content_l10n":"More","updated_at":"2023-01-26T21:09:02.936Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltda408b2b71cd18d9","ACL":{},"created_at":"2023-01-26T21:09:02.777Z","created_by":"blt36e890d06c5ec32c","english_content":"View more learning opportunities","tags":[],"title":"View more learning opportunities","translate_content_l10n":"View more learning opportunities","updated_at":"2023-01-26T21:09:02.777Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.807Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5c1c4900cfdb547","ACL":{},"created_at":"2023-01-26T21:09:02.430Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more press releases","tags":[],"title":"Load more press releases","translate_content_l10n":"Load more press releases","updated_at":"2023-01-26T21:09:02.430Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.293Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta759219421b27a99","ACL":{},"created_at":"2023-01-26T21:09:02.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more news","tags":[],"title":"Load more news","translate_content_l10n":"Load more news","updated_at":"2023-01-26T21:09:02.267Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-14T16:29:48.588Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04d58d965fb73d4b","ACL":{},"created_at":"2023-01-26T21:09:02.102Z","created_by":"blt36e890d06c5ec32c","english_content":"Read more","tags":[],"title":"Read more","translate_content_l10n":"Read more","updated_at":"2023-01-26T21:09:02.102Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.159Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcecc4cb33d2f12d1","ACL":{},"created_at":"2023-01-26T21:09:01.933Z","created_by":"blt36e890d06c5ec32c","english_content":"What to explore next...","tags":[],"title":"What to explore next...","translate_content_l10n":"What to explore next...","updated_at":"2023-01-26T21:09:01.933Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.762Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt536f120184d5f82f","ACL":{},"created_at":"2023-01-26T21:09:01.766Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories from Elastic Customers","tags":[],"title":"More stories from Elastic Customers","translate_content_l10n":"More stories from Elastic Customers","updated_at":"2023-01-26T21:09:01.766Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.267Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt4b67bf09270df98e","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:01.597Z","created_by":"blt36e890d06c5ec32c","english_content":"See All Posts","tags":[],"title":"See All Posts","translate_content_l10n":"See all posts","updated_at":"2023-01-26T21:09:01.597Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:34:33.604Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt76ad53f0811383e0","ACL":{},"created_at":"2023-01-26T21:09:01.432Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact Info","tags":[],"title":"Contact Info","translate_content_l10n":"Contact information","updated_at":"2023-01-26T21:09:01.432Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd24b268000310a17","ACL":{},"created_at":"2023-01-26T21:09:00.572Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Watch","tags":[],"title":"Register to Watch","translate_content_l10n":"Register to watch","updated_at":"2023-01-26T21:09:00.572Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc387be0be6c7bba6","ACL":{},"created_at":"2023-01-26T21:09:00.393Z","created_by":"blt36e890d06c5ec32c","english_content":"Sign In to Attend","tags":[],"title":"Sign In to Attend","translate_content_l10n":"Sign in to attend","updated_at":"2023-01-26T21:09:00.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.633Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd778a9bdcafbbc41","ACL":{},"created_at":"2023-01-26T21:09:00.219Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Attend","tags":[],"title":"Register to Attend","translate_content_l10n":"Register to attend","updated_at":"2023-01-26T21:09:00.219Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.790Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f3c4d1f3f7a64fe","ACL":{},"created_at":"2023-01-26T21:08:59.859Z","created_by":"blt36e890d06c5ec32c","english_content":"More posts","tags":[],"title":"More posts","translate_content_l10n":"More posts","updated_at":"2023-01-26T21:08:59.859Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:14:57.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e366458d1dd1e0c","ACL":{},"created_at":"2023-01-26T21:08:59.675Z","created_by":"blt36e890d06c5ec32c","english_content":"By","tags":[],"title":"By","translate_content_l10n":"By","updated_at":"2023-01-26T21:08:59.675Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.125Z","user":"blt36e890d06c5ec32c"}}],75],"entryLocale":"en","isEntryLocalized":false,"translateContentRedesign":[{"uid":"bltfb44eb6e899331a4","_version":1,"locale":"en-us","ACL":{},"created_at":"2024-11-13T23:43:06.196Z","created_by":"blt36e890d06c5ec32c","english_content":"Or","tags":[],"title":"Or","translate_content_l10n":"Or","updated_at":"2024-11-13T23:43:06.196Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-11-13T23:44:21.198Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2aeecde6c1729945","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:02.610Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more","tags":[],"title":"Load more","translate_content_l10n":"Load more","updated_at":"2024-09-03T16:41:46.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-03T16:42:00.289Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt6f3ad4a078adc611","ACL":{},"created_at":"2024-05-28T12:47:25.539Z","created_by":"blt3e52848e0cb3c394","english_content":"Overview","tags":[],"title":"Overview","translate_content_l10n":"Overview","updated_at":"2024-05-28T12:47:25.539Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-28T12:47:29.022Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt3b08c089ffd331e6","ACL":{},"created_at":"2023-01-26T21:09:09.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","tags":[],"title":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","translate_content_l10n":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content.","updated_at":"2023-12-18T21:59:16.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:59:19.133Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt7a2b7e50bb030ed8","ACL":{},"created_at":"2023-01-26T21:09:00.746Z","created_by":"blt36e890d06c5ec32c","english_content":"You'll also receive an email with related content.","tags":[],"title":"You'll also receive an email with related content","translate_content_l10n":"You'll also receive an email with related content.","updated_at":"2023-12-18T21:58:39.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:58:43.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt7a2ecc87e95e0fed","ACL":{},"created_at":"2023-08-23T22:51:28.540Z","created_by":"blt36e890d06c5ec32c","english_content":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","tags":[],"title":"Newsletter GDPR Text","translate_content_l10n":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","updated_at":"2023-08-23T22:51:28.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T22:52:42.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16f2676801e3267e","ACL":{},"created_at":"2023-08-22T17:00:20.812Z","created_by":"blt36e890d06c5ec32c","english_content":"Speakers","tags":[],"title":"Speakers","translate_content_l10n":"Speakers","updated_at":"2023-08-22T17:00:20.812Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-22T17:01:19.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0cbc24c249b9fd54","ACL":{},"created_at":"2023-07-11T21:21:11.001Z","created_by":"blt3044324473ef223b70bc674c","english_content":"Close","tags":[],"title":"Close","translate_content_l10n":"Close","updated_at":"2023-07-11T21:21:11.001Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-11T21:22:26.797Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt20243cb3a8c574f6","ACL":{},"created_at":"2023-04-27T22:46:08.141Z","created_by":"blt36e890d06c5ec32c","english_content":"See more insights","tags":[],"title":"See more insights","translate_content_l10n":"See more insights","updated_at":"2023-04-27T22:46:08.141Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-27T22:47:17.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt5e35f797b223487b","ACL":{},"created_at":"2023-04-25T22:44:26.727Z","created_by":"blt36e890d06c5ec32c","english_content":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","tags":[],"title":"The content on this page is not available in the selected language.","translate_content_l10n":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","updated_at":"2023-04-25T22:50:03.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-25T22:50:49.263Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt95f1076dfef4f727","ACL":{},"created_at":"2023-04-03T16:58:30.945Z","created_by":"blt36e890d06c5ec32c","english_content":"Author","tags":[],"title":"Author","translate_content_l10n":"Author","updated_at":"2023-04-03T16:58:30.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:02:04.749Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltb9e7436e790dc1e1","ACL":{},"created_at":"2023-01-26T21:09:01.075Z","created_by":"blt36e890d06c5ec32c","english_content":"Learn more","tags":[],"title":"Learn more","translate_content_l10n":"Learn more","updated_at":"2023-03-23T23:23:32.443Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:25:05.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte80ec2bf93203454","ACL":{},"created_at":"2023-03-23T23:20:05.096Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now (no PT)","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:20:05.096Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:23:03.467Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt0b2b84aede5a5e1a","ACL":{},"created_at":"2023-01-26T21:09:00.911Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:17:38.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:19:07.965Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ad9978de13cb3c","ACL":{},"created_at":"2023-03-20T19:38:56.211Z","created_by":"blt36e890d06c5ec32c","english_content":"See all top stories","tags":[],"title":"See all top stories","translate_content_l10n":"See all top stories","updated_at":"2023-03-20T19:38:56.211Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:40:01.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0aeca091079429a4","ACL":{},"created_at":"2023-03-20T19:37:29.708Z","created_by":"blt36e890d06c5ec32c","english_content":"Related content","tags":[],"title":"Related content","translate_content_l10n":"Related content","updated_at":"2023-03-20T19:37:29.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:38:35.986Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltdedcc90f4b9d495c","ACL":{},"created_at":"2023-03-13T17:42:26.422Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All (no PT translation)","translate_content_l10n":"All","updated_at":"2023-03-13T18:12:39.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T18:13:09.648Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdafd9e19f8a295c9","ACL":{},"created_at":"2023-03-13T16:44:58.960Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact information","tags":[],"title":"Contact information","translate_content_l10n":"Contact information","updated_at":"2023-03-13T16:44:58.960Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:46:31.937Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d189cf8b1b80402","ACL":{},"created_at":"2023-03-13T16:43:08.761Z","created_by":"blt36e890d06c5ec32c","english_content":"Press Release","tags":[],"title":"Press Release","translate_content_l10n":"Press Release","updated_at":"2023-03-13T16:43:08.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:44:42.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb031798c593cf2aa","ACL":{},"created_at":"2023-03-06T17:39:15.553Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Reddit","tags":[],"title":"Share on Reddit","translate_content_l10n":"Share on Reddit","updated_at":"2023-03-06T17:39:15.553Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-06T17:40:52.751Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltc449b2f75825b408","ACL":{},"created_at":"2023-01-26T21:09:01.238Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories","tags":[],"title":"More stories","translate_content_l10n":"More stories","updated_at":"2023-02-23T22:39:49.208Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-23T22:40:59.356Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte38439477acb192e","ACL":{},"created_at":"2023-01-26T21:09:00.049Z","created_by":"blt36e890d06c5ec32c","english_content":"Articles by","tags":[],"title":"Articles by","translate_content_l10n":"Articles by","updated_at":"2023-02-23T22:11:25.304Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T16:57:47.130Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4b99c93b5338acdd","ACL":{},"created_at":"2023-02-16T17:26:10.103Z","created_by":"blt36e890d06c5ec32c","english_content":"Share this story","tags":[],"title":"Share this story","translate_content_l10n":"Share this story","updated_at":"2023-02-16T17:26:10.103Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-16T17:27:39.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte2e658dd90716f9f","ACL":{},"created_at":"2023-01-26T21:09:06.325Z","created_by":"blt36e890d06c5ec32c","english_content":"Share by Email","tags":[],"title":"Share by Email","translate_content_l10n":"Share by email","updated_at":"2023-02-14T18:05:54.924Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-14T18:06:40.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt622e2e6d3a2e469f","ACL":{},"created_at":"2023-01-26T21:09:09.950Z","created_by":"blt36e890d06c5ec32c","english_content":"Read less","tags":[],"title":"Read less","translate_content_l10n":"Read less","updated_at":"2023-01-26T21:09:09.950Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6e126363fe0669f","ACL":{},"created_at":"2023-01-26T21:09:09.794Z","created_by":"blt36e890d06c5ec32c","english_content":"Search Integrations","tags":[],"title":"Search Integrations","translate_content_l10n":"Search Integrations","updated_at":"2023-01-26T21:09:09.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.579Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfc60ac5a8053094c","ACL":{},"created_at":"2023-01-26T21:09:09.641Z","created_by":"blt36e890d06c5ec32c","english_content":"All Solutions","tags":[],"title":"All Solutions","translate_content_l10n":"All Solutions","updated_at":"2023-01-26T21:09:09.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.477Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c2c6a4e8cb5c2f0","ACL":{},"created_at":"2023-01-26T21:09:09.435Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for registering. We will send you a confirmation email soon.","tags":[],"title":"Thank you for registering. We will send you a confirmation email soon.","translate_content_l10n":"Thank you for registering. We will send you a confirmation email soon.","updated_at":"2023-01-26T21:09:09.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b837e25d93f5d3","ACL":{},"created_at":"2023-01-26T21:09:09.095Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for your interest!","tags":[],"title":"Thank you for your interest!","translate_content_l10n":"Thank you for your interest!","updated_at":"2023-01-26T21:09:09.095Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.784Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteecbf46e81d0d29d","ACL":{},"created_at":"2023-01-26T21:09:08.915Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Youtube","tags":[],"title":"Follow us on Youtube","translate_content_l10n":"Follow us on Youtube","updated_at":"2023-01-26T21:09:08.915Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.451Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dd2bbe9b12abe26","ACL":{},"created_at":"2023-01-26T21:09:08.754Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Twitter","tags":[],"title":"Follow us on Twitter","translate_content_l10n":"Follow us on Twitter","updated_at":"2023-01-26T21:09:08.754Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.917Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35eafbb82d26a869","ACL":{},"created_at":"2023-01-26T21:09:08.594Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on LinkedIn","tags":[],"title":"Follow us on LinkedIn","translate_content_l10n":"Follow us on LinkedIn","updated_at":"2023-01-26T21:09:08.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9667a9e201b264e5","ACL":{},"created_at":"2023-01-26T21:09:08.424Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Facebook","tags":[],"title":"Follow us on Facebook","translate_content_l10n":"Follow us on Facebook","updated_at":"2023-01-26T21:09:08.424Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.149Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafd12f73d268d939","ACL":{},"created_at":"2023-01-26T21:09:08.254Z","created_by":"blt36e890d06c5ec32c","english_content":"Headshot of","tags":[],"title":"Headshot of","translate_content_l10n":"Headshot of","updated_at":"2023-01-26T21:09:08.254Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.217Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteeffcd504c337777","ACL":{},"created_at":"2023-01-26T21:09:08.073Z","created_by":"blt36e890d06c5ec32c","english_content":"Table of contents","tags":[],"title":"Table of contents","translate_content_l10n":"Table of contents","updated_at":"2023-01-26T21:09:08.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.878Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1c9c25fdd610a988","ACL":{},"created_at":"2023-01-26T21:09:07.459Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All","translate_content_l10n":"All","updated_at":"2023-01-26T21:09:07.459Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.849Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcc368963ef15efcf","ACL":{},"created_at":"2023-01-26T21:09:07.299Z","created_by":"blt36e890d06c5ec32c","english_content":"Reset all","tags":[],"title":"Reset all","translate_content_l10n":"Reset all","updated_at":"2023-01-26T21:09:07.299Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.712Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf9e2c7ddef1476c","ACL":{},"created_at":"2023-01-26T21:09:07.138Z","created_by":"blt36e890d06c5ec32c","english_content":"Filters","tags":[],"title":"Filters","translate_content_l10n":"Filters","updated_at":"2023-01-26T21:09:07.138Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.405Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8186c36bcb7238","ACL":{},"created_at":"2023-01-26T21:09:06.974Z","created_by":"blt36e890d06c5ec32c","english_content":"Global Virtual Event","tags":[],"title":"Global Virtual Event","translate_content_l10n":"Global Virtual Event","updated_at":"2023-01-26T21:09:06.974Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.270Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4972bcd17a9589e","ACL":{},"created_at":"2023-01-26T21:09:06.815Z","created_by":"blt36e890d06c5ec32c","english_content":"View more posts","tags":[],"title":"View more posts","translate_content_l10n":"View more posts","updated_at":"2023-01-26T21:09:06.815Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.716Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7784639e8213f1de","ACL":{},"created_at":"2023-01-26T21:09:06.656Z","created_by":"blt36e890d06c5ec32c","english_content":"Print","tags":[],"title":"Print","translate_content_l10n":"Print","updated_at":"2023-01-26T21:09:06.656Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.409Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd160052884c85597","ACL":{},"created_at":"2023-01-26T21:09:06.489Z","created_by":"blt36e890d06c5ec32c","english_content":"Continue reading","tags":[],"title":"Continue reading","translate_content_l10n":"Continue reading","updated_at":"2023-01-26T21:09:06.489Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.383Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa2fe12d75e222b7","ACL":{},"created_at":"2023-01-26T21:09:06.160Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Facebook","tags":[],"title":"Share on Facebook","translate_content_l10n":"Share on Facebook","updated_at":"2023-01-26T21:09:06.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.521Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c65ce5e43c44d1e","ACL":{},"created_at":"2023-01-26T21:09:05.989Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on LinkedIn","tags":[],"title":"Share on LinkedIn","translate_content_l10n":"Share on LinkedIn","updated_at":"2023-01-26T21:09:05.989Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.207Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa64468770539e99","ACL":{},"created_at":"2023-01-26T21:09:05.807Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Twitter","tags":[],"title":"Share on Twitter","translate_content_l10n":"Share on Twitter","updated_at":"2023-01-26T21:09:05.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbf19c4f1958b7010","ACL":{},"created_at":"2023-01-26T21:09:05.653Z","created_by":"blt36e890d06c5ec32c","english_content":"Share","tags":[],"title":"Share","translate_content_l10n":"Share","updated_at":"2023-01-26T21:09:05.653Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.603Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd3ca82669f533596","ACL":{},"created_at":"2023-01-26T21:09:05.494Z","created_by":"blt36e890d06c5ec32c","english_content":"Small image for","tags":[],"title":"Small image for","translate_content_l10n":"Small image for","updated_at":"2023-01-26T21:09:05.494Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.766Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt665205a37a7b1a98","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:05.336Z","created_by":"blt36e890d06c5ec32c","english_content":"Video for","tags":[],"title":"Video for","translate_content_l10n":"Video for","updated_at":"2023-01-26T21:09:05.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:39:50.482Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt33215a82788dd3f2","ACL":{},"created_at":"2023-01-26T21:09:05.174Z","created_by":"blt36e890d06c5ec32c","english_content":"Explore similar demos","tags":[],"title":"Explore similar demos","translate_content_l10n":"Explore similar demos","updated_at":"2023-01-26T21:09:05.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt59af0058e6f2ab2c","ACL":{},"created_at":"2023-01-26T21:09:05.013Z","created_by":"blt36e890d06c5ec32c","english_content":"Register now","tags":[],"title":"Register now","translate_content_l10n":"Register now","updated_at":"2023-01-26T21:09:05.013Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.297Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt44f6c020ef294d34","ACL":{},"created_at":"2023-01-26T21:09:04.854Z","created_by":"blt36e890d06c5ec32c","english_content":"View next","tags":[],"title":"View next","translate_content_l10n":"View next","updated_at":"2023-01-26T21:09:04.854Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.641Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc455c56e1db3258","ACL":{},"created_at":"2023-01-26T21:09:04.701Z","created_by":"blt36e890d06c5ec32c","english_content":"Upcoming webinar","tags":[],"title":"Upcoming webinar","translate_content_l10n":"Upcoming webinar","updated_at":"2023-01-26T21:09:04.701Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.739Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt9e655ee3d1dbcd42","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.537Z","created_by":"blt36e890d06c5ec32c","english_content":"On-demand webinar","tags":[],"title":"On-demand webinar","translate_content_l10n":"On-demand webinar","updated_at":"2023-01-26T21:09:04.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:46:22.076Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd00860fb1d6f389b","ACL":{},"created_at":"2023-01-26T21:09:04.379Z","created_by":"blt36e890d06c5ec32c","english_content":"Featured webinar","tags":[],"title":"Featured webinar","translate_content_l10n":"Featured webinar","updated_at":"2023-01-26T21:09:04.379Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.328Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt335688b477b632cf","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.218Z","created_by":"blt36e890d06c5ec32c","english_content":"Highlights","tags":[],"title":"Highlights","translate_content_l10n":"Highlights","updated_at":"2023-01-26T21:09:04.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:31:29.622Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd90374b721d95342","ACL":{},"created_at":"2023-01-26T21:09:03.895Z","created_by":"blt36e890d06c5ec32c","english_content":"See when this webinar starts in my time zone","tags":[],"title":"See when this webinar starts in my time zone","translate_content_l10n":"See when this webinar starts in my time zone","updated_at":"2023-01-26T21:09:03.895Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.820Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt60fa8518500aa04e","ACL":{},"created_at":"2023-01-26T21:09:03.734Z","created_by":"blt36e890d06c5ec32c","english_content":"Related workshops","tags":[],"title":"Related workshops","translate_content_l10n":"Related workshops","updated_at":"2023-01-26T21:09:03.734Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.354Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fa14ebb51d2154f","ACL":{},"created_at":"2023-01-26T21:09:03.577Z","created_by":"blt36e890d06c5ec32c","english_content":"Hosted by","tags":[],"title":"Hosted by","translate_content_l10n":"Hosted by","updated_at":"2023-01-26T21:09:03.577Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.873Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltace88e420eb1dedb","ACL":{},"created_at":"2023-01-26T21:09:03.419Z","created_by":"blt36e890d06c5ec32c","english_content":"Agenda","tags":[],"title":"Agenda","translate_content_l10n":"Agenda","updated_at":"2023-01-26T21:09:03.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.193Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4e07248dad773e78","ACL":{},"created_at":"2023-01-26T21:09:03.260Z","created_by":"blt36e890d06c5ec32c","english_content":"Location","tags":[],"title":"Location","translate_content_l10n":"Location","updated_at":"2023-01-26T21:09:03.260Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd047722739355567","ACL":{},"created_at":"2023-01-26T21:09:03.106Z","created_by":"blt36e890d06c5ec32c","english_content":"Date","tags":[],"title":"Date","translate_content_l10n":"Date","updated_at":"2023-01-26T21:09:03.106Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.355Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt97cf5566d151b2d8","ACL":{},"created_at":"2023-01-26T21:09:02.936Z","created_by":"blt36e890d06c5ec32c","english_content":"More","tags":[],"title":"More","translate_content_l10n":"More","updated_at":"2023-01-26T21:09:02.936Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltda408b2b71cd18d9","ACL":{},"created_at":"2023-01-26T21:09:02.777Z","created_by":"blt36e890d06c5ec32c","english_content":"View more learning opportunities","tags":[],"title":"View more learning opportunities","translate_content_l10n":"View more learning opportunities","updated_at":"2023-01-26T21:09:02.777Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.807Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5c1c4900cfdb547","ACL":{},"created_at":"2023-01-26T21:09:02.430Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more press releases","tags":[],"title":"Load more press releases","translate_content_l10n":"Load more press releases","updated_at":"2023-01-26T21:09:02.430Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.293Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta759219421b27a99","ACL":{},"created_at":"2023-01-26T21:09:02.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more news","tags":[],"title":"Load more news","translate_content_l10n":"Load more news","updated_at":"2023-01-26T21:09:02.267Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-14T16:29:48.588Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04d58d965fb73d4b","ACL":{},"created_at":"2023-01-26T21:09:02.102Z","created_by":"blt36e890d06c5ec32c","english_content":"Read more","tags":[],"title":"Read more","translate_content_l10n":"Read more","updated_at":"2023-01-26T21:09:02.102Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.159Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcecc4cb33d2f12d1","ACL":{},"created_at":"2023-01-26T21:09:01.933Z","created_by":"blt36e890d06c5ec32c","english_content":"What to explore next...","tags":[],"title":"What to explore next...","translate_content_l10n":"What to explore next...","updated_at":"2023-01-26T21:09:01.933Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.762Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt536f120184d5f82f","ACL":{},"created_at":"2023-01-26T21:09:01.766Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories from Elastic Customers","tags":[],"title":"More stories from Elastic Customers","translate_content_l10n":"More stories from Elastic Customers","updated_at":"2023-01-26T21:09:01.766Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.267Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt4b67bf09270df98e","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:01.597Z","created_by":"blt36e890d06c5ec32c","english_content":"See All Posts","tags":[],"title":"See All Posts","translate_content_l10n":"See all posts","updated_at":"2023-01-26T21:09:01.597Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:34:33.604Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt76ad53f0811383e0","ACL":{},"created_at":"2023-01-26T21:09:01.432Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact Info","tags":[],"title":"Contact Info","translate_content_l10n":"Contact information","updated_at":"2023-01-26T21:09:01.432Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd24b268000310a17","ACL":{},"created_at":"2023-01-26T21:09:00.572Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Watch","tags":[],"title":"Register to Watch","translate_content_l10n":"Register to watch","updated_at":"2023-01-26T21:09:00.572Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc387be0be6c7bba6","ACL":{},"created_at":"2023-01-26T21:09:00.393Z","created_by":"blt36e890d06c5ec32c","english_content":"Sign In to Attend","tags":[],"title":"Sign In to Attend","translate_content_l10n":"Sign in to attend","updated_at":"2023-01-26T21:09:00.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.633Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd778a9bdcafbbc41","ACL":{},"created_at":"2023-01-26T21:09:00.219Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Attend","tags":[],"title":"Register to Attend","translate_content_l10n":"Register to attend","updated_at":"2023-01-26T21:09:00.219Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.790Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f3c4d1f3f7a64fe","ACL":{},"created_at":"2023-01-26T21:08:59.859Z","created_by":"blt36e890d06c5ec32c","english_content":"More posts","tags":[],"title":"More posts","translate_content_l10n":"More posts","updated_at":"2023-01-26T21:08:59.859Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:14:57.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e366458d1dd1e0c","ACL":{},"created_at":"2023-01-26T21:08:59.675Z","created_by":"blt36e890d06c5ec32c","english_content":"By","tags":[],"title":"By","translate_content_l10n":"By","updated_at":"2023-01-26T21:08:59.675Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.125Z","user":"blt36e890d06c5ec32c"}}]},"primeNav":[[{"_version":121,"locale":"en-us","uid":"blta694a81b23d8d1b6","ACL":{},"actions_nav_items":[{"link_type":"icon-link-with-dropdown","icon_name":"language-picker","title_l10n":"Language","_metadata":{"uid":"cs4d57cace9f8b81be"},"url":"","display_in_mobile_footer":true,"dropdown":[{"title_l10n":"Deutsch","_metadata":{"uid":"cs6b8052e8e3d6eeff"},"url":"/de/"},{"title_l10n":"English","_metadata":{"uid":"cs3e739da0e5dd755c"},"url":"/"},{"title_l10n":"Español","_metadata":{"uid":"cs6abb4025e07ad795"},"url":"/es/"},{"title_l10n":"Français","_metadata":{"uid":"csf1d3e66812e0bf02"},"url":"/fr/"},{"title_l10n":"日本語","_metadata":{"uid":"csc55ffdf988121f1a"},"url":"/jp/"},{"title_l10n":"한국어","_metadata":{"uid":"cs12fd960301a768cf"},"url":"/kr/"},{"title_l10n":"简体中文","_metadata":{"uid":"csa94cdb113d29264c"},"url":"/cn/"},{"title_l10n":"Português","_metadata":{"uid":"cs785765bc8a8317b4"},"url":"/pt/"}]},{"link_type":"search","icon_name":"search","title_l10n":"Search","_metadata":{"uid":"cs9e5210a44cd35e0e"},"url":"","display_in_mobile_footer":false,"dropdown":[]},{"link_type":"icon-link","icon_name":"login","title_l10n":"Login","_metadata":{"uid":"cs8256bccc1ea2456e"},"url":"https://cloud.elastic.co","display_in_mobile_footer":true,"dropdown":[]},{"link_type":"primary","icon_name":null,"title_l10n":"Start free trial","_metadata":{"uid":"cs27d6c530946181b6"},"url":"https://cloud.elastic.co/registration","display_in_mobile_footer":true,"dropdown":[]},{"link_type":"secondary","icon_name":null,"title_l10n":"Contact Sales","_metadata":{"uid":"cs6492748b6ed9ff24"},"url":"/contact","display_in_mobile_footer":true,"dropdown":[]}],"alert_bar":[],"created_at":"2023-04-20T14:14:37.626Z","created_by":"blt3e52848e0cb3c394","logo":{"elastic_logo":null,"url":"/"},"nav_items":[{"title_l10n":"Platform","_metadata":{"uid":"cs67c33f9bf7891f56"},"title_id":"nav-item-platform","url":"","sections":[{"title_l10n":"Elasticsearch Platform + ELK Stack","_metadata":{"uid":"cs28455439cc50fde8"},"background_style":"Gray","reference":[{"_content_type_uid":"site_navigation_reference","_version":33,"locale":"en-us","uid":"blte130d9e7e04c68ce","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Partner overview","_metadata":{"uid":"cs287bd794fe8c916d"},"url":"/partners","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs97e60956b4c77e82"},"footnote_l10n":""}}],"column_modular_blocks":[{"title":{"title_l10n":"The Search AI Company","_metadata":{"uid":"cs8a188450384d411d"},"url":"/platform"}},{"image":{"type":"thumbnail-fill container","file":{"uid":"bltb72b02d269f3201a","_version":1,"title":"nav-platform.png","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-14T15:34:13.950Z","updated_at":"2024-05-14T15:34:13.950Z","content_type":"image/png","file_size":"48119","filename":"nav-platform.png","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-05-15T12:50:43.247Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltb72b02d269f3201a/6643847599f5a8667dc35ac7/nav-platform.png"},"_metadata":{"uid":"cs6d350f035dacb270"},"alt_text_l10n":"Search, Security, Observability"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eBuild tailored experiences with Elastic.\u003c/p\u003e","_metadata":{"uid":"cscf9c3c37ecef1469"}}},{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Elastic Search AI Platform overview","_metadata":{"uid":"cs65261558f229f943"},"url":"/platform","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"csd2c7e2a0dcf7c4ee"},"footnote_l10n":""}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cse5d465d6bcfbf132"}}},{"paragraph":{"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eScale your business with Elastic Partners\u003c/strong\u003e\u003c/p\u003e","_metadata":{"uid":"cs361ee4966b199f0c"}}},{"sublinks":{"sublinks":[{"title_l10n":"Find a partner","_metadata":{"uid":"cs01f018b8e6c2aa61"},"url":"https://partners.elastic.co/findapartner/"},{"title_l10n":"Become a partner","_metadata":{"uid":"cs5f07508f60c9c0fe"},"url":"/partners/become-a-partner"}],"_metadata":{"uid":"cs6e2d31658c521070"}}}],"created_at":"2023-06-04T11:59:07.519Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Ghost card"},"tags":[],"title":"Platform - Elasticsearch Platform","title_l10n":"","updated_at":"2024-05-15T18:25:30.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-15T18:25:42.923Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"site_navigation_reference","uid":"blt6fe143a8799b1d7b","_version":17,"locale":"en-us","ACL":{},"below_column_modular_blocks":[],"column_modular_blocks":[{"image":{"type":null,"file":{"_version":3,"is_dir":false,"uid":"blt0090c6239e64faf8","ACL":{},"content_type":"image/svg+xml","created_at":"2019-06-18T00:09:05.515Z","created_by":"blt3044324473ef223b70bc674c","description":"\"all\": \"Elastic Stack\"","file_size":"379","filename":"logo-stack-32-color.svg","parent_uid":"blt3dd6454f65ccc34c","tags":[],"title":"logo-stack-32-color.svg","updated_at":"2022-06-15T16:32:00.813Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-06-15T16:32:09.806Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0090c6239e64faf8/62aa0980c949fd5059e8aebc/logo-stack-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt0090c6239e64faf8/logo-stack-32-color.svg"},"_metadata":{"uid":"cs56b531fd46473960"},"alt_text_l10n":""}},{"title":{"title_l10n":"ELK Stack","_metadata":{"uid":"csb2b0c9d496752b81"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eSearch and analytics, data ingestion, and visualization – all at your fingertips.\u003c/p\u003e","_metadata":{"uid":"cse32f929fa3057408"}}},{"sublinks":{"sublinks":[{"title_l10n":"Kibana","_metadata":{"uid":"csc13bf0787bfe64c3"},"url":"/kibana"},{"title_l10n":"Elasticsearch","_metadata":{"uid":"cs800aa8a08413ff75"},"url":"/elasticsearch"},{"title_l10n":"Integrations","_metadata":{"uid":"csac6f26e4d9dc92bf"},"url":"/integrations"}],"_metadata":{"uid":"csc0eb9aae95a2d760"}}},{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"ELK Stack overview","_metadata":{"uid":"cs8a81059a67502f8f"},"url":"/elastic-stack","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs1d19ed20cdaf80ba"},"footnote_l10n":""}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cseed81fb40af11110"}}},{"paragraph":{"paragraph_l10n":"\u003cp\u003e\u003cstrong\u003eBy developers, for developers\u003c/strong\u003e\u003c/p\u003e","_metadata":{"uid":"csf65c9e004a53da0b"}}},{"sublinks":{"sublinks":[{"title_l10n":"Try the world's most used vector database","_metadata":{"uid":"csa74c6a42e5c25b13"},"url":"/elasticsearch/vector-database"},{"title_l10n":"Scale with the low-latency Search AI Lake","_metadata":{"uid":"cs79e8262c7a671730"},"url":"/blog/search-ai-lake-elastic-cloud-serverless"},{"title_l10n":"Join our community","_metadata":{"uid":"cs462063e2c301a820"},"url":"/community"}],"_metadata":{"uid":"cs4f61a5b050f66f94"}}}],"created_at":"2023-06-04T12:03:38.980Z","created_by":"blt3e52848e0cb3c394","sanity_migration_complete":false,"style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Platform - ELK Stack","title_l10n":"","updated_at":"2024-12-04T20:16:54.644Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-12-04T20:16:59.029Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]},{"title_l10n":"Elastic Cloud","_metadata":{"uid":"cs6c2a742c3201f02f"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt2b4f1f6c89ecd6b2","_version":17,"locale":"en-us","ACL":{},"below_column_modular_blocks":[],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":2,"is_dir":false,"uid":"bltdb0f38c35ae455dc","ACL":{},"content_type":"image/svg+xml","created_at":"2019-06-17T19:56:54.761Z","created_by":"blt3044324473ef223b70bc674c","description":"\"all\": \"Elastic Cloud\"","file_size":"1716","filename":"logo-cloud-24-color.svg","tags":[],"title":"logo-cloud-24-color.svg","updated_at":"2021-12-17T19:41:38.654Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-12-17T19:46:22.193Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdb0f38c35ae455dc/5d07f086877575d0584760a3/logo-cloud-24-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltdb0f38c35ae455dc/logo-cloud-24-color.svg"},"_metadata":{"uid":"cs03ac8608840d234a"},"alt_text_l10n":""}},{"title":{"title_l10n":"Elastic Cloud","_metadata":{"uid":"cse27182bd72de81f8"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eUnlock the power of real-time insights with Elastic on your preferred cloud provider.\u003c/p\u003e","_metadata":{"uid":"cs6cfc29a0530d445e"}}},{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Elastic Cloud overview","_metadata":{"uid":"cs9e1ba22a61156b8e"},"url":"/cloud","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs50a5b2b008340d9e"},"footnote_l10n":""}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csee961bd984575808"}}},{"sublinks":{"sublinks":[{"title_l10n":"Elastic Cloud Serverless","_metadata":{"uid":"cs974ba013957fd92b"},"url":"/cloud/serverless"},{"title_l10n":"Elastic Cloud Serverless pricing","_metadata":{"uid":"csa49e9903f1b062f6"},"url":"/pricing/serverless-search"},{"title_l10n":"Search AI Lake","_metadata":{"uid":"csd24af6c48b144268"},"url":"/cloud/serverless/search-ai-lake"}],"_metadata":{"uid":"csc5efe659a4339dfd"}}}],"created_at":"2023-06-04T12:03:32.338Z","created_by":"blt3e52848e0cb3c394","sanity_migration_complete":false,"style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Platform - Elastic Cloud","title_l10n":"","updated_at":"2025-01-16T23:57:39.534Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2025-01-16T23:59:39.913Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Solutions","_metadata":{"uid":"cs1538385775c98efd"},"title_id":"nav-item-solutions","url":"","sections":[{"title_l10n":"Generative AI","_metadata":{"uid":"cs8f79c87796141d46"},"background_style":"Gray","reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt2b5b716b730e7095","_version":17,"locale":"en-us","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Generative AI overview ","_metadata":{"uid":"cs43afe4a5eb95776a"},"url":"/generative-ai","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs78bf3b3fd7424010"},"footnote_l10n":""}}],"column_modular_blocks":[{"title":{"title_l10n":"Generative AI","_metadata":{"uid":"cs18b2763e43ebbbea"},"url":"/generative-ai"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003ePrototype and integrate with LLMs faster using search AI.\u003c/p\u003e","_metadata":{"uid":"csc2b19500d60f1812"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search AI Lake","_metadata":{"uid":"cs35466fb715f2ee26"},"url":"/cloud/serverless/search-ai-lake"},{"title_l10n":"Elastic AI Assistant","_metadata":{"uid":"csa826ec74cb488fda"},"url":"/elasticsearch/ai-assistant"},{"title_l10n":"Retrieval Augmented Generation","_metadata":{"uid":"cscdbdc699afde4a02"},"url":"/enterprise-search/rag"}],"_metadata":{"uid":"csb397b8fbfeb59c8d"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csdfa77237ae8319e6"}}},{"sublinks":{"sublinks":[{"title_l10n":"Generative AI blogs","_metadata":{"uid":"csa1f8add36e960f17"},"url":"/blog/category/generative-ai"},{"title_l10n":"Search Labs tutorials","_metadata":{"uid":"cs6e6cd221ea191f9c"},"url":"https://www.elastic.co/search-labs/tutorials"},{"title_l10n":"Elastic Community","_metadata":{"uid":"cs9f83e06b285c3f47"},"url":"/community"}],"_metadata":{"uid":"cs67c6e2303b42bb57"}}}],"created_at":"2024-05-10T22:33:22.668Z","created_by":"blt3044324473ef223b70bc674c","sanity_migration_complete":false,"style":{"type":"Ghost card"},"tags":[],"title":"Solutions - Generative AI","title_l10n":"","updated_at":"2024-12-03T17:26:30.015Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-12-03T17:26:35.047Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]},{"title_l10n":"Search, Security, Observability","_metadata":{"uid":"csdd81ddba0bf8cc4b"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","_version":13,"locale":"en-us","uid":"bltc3a1cd40e0416b2c","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Search overview","_metadata":{"uid":"csbd5496aa3d1b0190"},"url":"/enterprise-search","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs44eaadf5237824b3"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"uid":"blt549f7d977c2a88f4","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt36e890d06c5ec32c","created_at":"2019-06-18T00:15:48.602Z","updated_at":"2022-07-14T22:30:12.657Z","content_type":"image/svg+xml","file_size":"1812","filename":"logo-enterprise-search-32-color.svg","title":"logo-enterprise-search-32-color.svg","ACL":{},"_version":4,"is_dir":false,"tags":[],"description":"image_alternative_text: blt4c95fef51f752b47","parent_uid":"blt3dd6454f65ccc34c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-16T22:51:05.584Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt549f7d977c2a88f4/5d082d34616162aa5a85707d/logo-enterprise-search-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt549f7d977c2a88f4/logo-enterprise-search-32-color.svg"},"_metadata":{"uid":"cs170d33ec56ceac69"},"alt_text_l10n":""}},{"title":{"title_l10n":"Search","_metadata":{"uid":"cs775478cd77e6d292"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eDiscover a world of AI possibilities — built with the power of search.\u003c/p\u003e","_metadata":{"uid":"cs5a4b902119bba40f"}}},{"sublinks":{"sublinks":[{"title_l10n":"Vector database","_metadata":{"uid":"csed77c651fdd3174c"},"url":"/elasticsearch/vector-database"},{"title_l10n":"Relevance","_metadata":{"uid":"cs80141cb427dee0c1"},"url":"/enterprise-search/relevance"},{"title_l10n":"Search applications","_metadata":{"uid":"cs9d714be4e38ada8a"},"url":"/enterprise-search/search-applications"},{"title_l10n":"Ecommerce","_metadata":{"uid":"cs7963bae02344b71b"},"url":"/enterprise-search/ecommerce"},{"title_l10n":"Website search","_metadata":{"uid":"cs7836f56c55ba3cfe"},"url":"/enterprise-search/site-search"},{"title_l10n":"Workplace search","_metadata":{"uid":"csf4a77adc63248830"},"url":"/enterprise-search/workplace-search"},{"title_l10n":"Customer support","_metadata":{"uid":"cs445feacc70664066"},"url":"/enterprise-search/customer-support"}],"_metadata":{"uid":"csf4d2d6f3005e3796"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csbd1e64a45bcdc466"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search Labs","_metadata":{"uid":"cs361d5d1595a1b47f"},"url":"https://www.elastic.co/search-labs"}],"_metadata":{"uid":"cs64700fb4732c0bd3"}}}],"created_at":"2023-06-04T12:03:13.040Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Solutions - Search","title_l10n":"","updated_at":"2024-07-11T21:27:34.509Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-07-11T21:28:38.978Z","user":"blt3044324473ef223b70bc674c"}},{"_content_type_uid":"site_navigation_reference","uid":"blt63c42ebb62439573","_version":11,"locale":"en-us","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Security overview","_metadata":{"uid":"cs607609172da7b010"},"url":"/security","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs5975061ef819456a"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":2,"is_dir":false,"uid":"bltf58b7c8e04706979","ACL":{},"content_type":"image/svg+xml","created_at":"2020-01-16T23:28:40.015Z","created_by":"blt3044324473ef223b70bc674c","description":"\"all\": \"Elastic Security\"","file_size":"915","filename":"logo-security-32-color.svg","tags":[],"title":"logo-security-32-color.svg","updated_at":"2022-02-08T19:17:13.406Z","updated_by":"blt36e890d06c5ec32c","parent_uid":"blt3dd6454f65ccc34c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-03T20:41:01.783Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf58b7c8e04706979/5e20f1a8132ead1155e8d0a4/logo-security-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf58b7c8e04706979/logo-security-32-color.svg"},"_metadata":{"uid":"cs3fd34bcf6bd4aa1e"},"alt_text_l10n":""}},{"title":{"title_l10n":"Security","_metadata":{"uid":"cs6bfb6459afd01091"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eProtect, investigate, and respond to cyber threats with AI-driven security analytics.\u003c/p\u003e","_metadata":{"uid":"cs5cd48eb76a2507c5"}}},{"sublinks":{"sublinks":[{"title_l10n":"SIEM","_metadata":{"uid":"csca3f3d9c18e2a70b"},"url":"/security/siem"},{"title_l10n":"AI for the SOC","_metadata":{"uid":"cs423503ab8b0c29e9"},"url":"/security/ai"},{"title_l10n":"Threat Research","_metadata":{"uid":"csb0b9fd0791e6e0bb"},"url":"/security/cyber-threat-research"}],"_metadata":{"uid":"cs0f0079b9e8827b1a"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"csf3e74156baa03a98"}}},{"sublinks":{"sublinks":[{"title_l10n":"Security Labs","_metadata":{"uid":"csd59f826a7734c6e5"},"url":"https://www.elastic.co/security-labs"}],"_metadata":{"uid":"csad4ae4404fd4fb84"}}}],"created_at":"2023-06-04T17:00:41.862Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Solutions - Security","title_l10n":"","updated_at":"2024-07-26T21:43:38.678Z","updated_by":"blt27204bf9f7abb7fd","publish_details":{"time":"2024-07-29T14:22:51.164Z","user":"blt27204bf9f7abb7fd","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"bltb6f106dd636862a0","_version":20,"locale":"en-us","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Observability overview","_metadata":{"uid":"cs1fd681e6a529b1d7"},"url":"/observability","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs3d2c913e15258d90"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":3,"is_dir":false,"uid":"bltbf6ba0d0e0e1e5ab","ACL":{},"content_type":"image/svg+xml","created_at":"2020-01-16T23:28:26.433Z","created_by":"blt3044324473ef223b70bc674c","description":"image_alternative_text: blt6e3875f2cb65b010","file_size":"854","filename":"logo-observability-32-color.svg","parent_uid":"blt3dd6454f65ccc34c","tags":[],"title":"logo-observability-32-color.svg","updated_at":"2022-06-23T22:18:33.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2022-08-03T20:41:01.766Z","user":"blt36e890d06c5ec32c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf6ba0d0e0e1e5ab/5e20f19a2aa8e40a75136318/logo-observability-32-color.svg","permanent_url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltbf6ba0d0e0e1e5ab/logo-observability-32-color.svg"},"_metadata":{"uid":"cs6d88bb24abedd2e3"},"alt_text_l10n":""}},{"title":{"title_l10n":"Observability","_metadata":{"uid":"cs67387a91562b3205"},"url":"/observability"}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eUnify app and infrastructure visibility to proactively resolve issues.\u003c/p\u003e","_metadata":{"uid":"cs88a641ffc2911203"}}},{"sublinks":{"sublinks":[{"title_l10n":"Log monitoring and analytics","_metadata":{"uid":"cs1dd5fa6336795a30"},"url":"/observability/log-monitoring"},{"title_l10n":"OpenTelemetry","_metadata":{"uid":"cs519e0baebee3d9cb"},"url":"/observability/opentelemetry"},{"title_l10n":"Application performance monitoring","_metadata":{"uid":"cs94aa837d61a0762c"},"url":"/observability/application-performance-monitoring"},{"title_l10n":"Infrastructure monitoring","_metadata":{"uid":"cs4f06f89314df2822"},"url":"/observability/infrastructure-monitoring"},{"title_l10n":"Synthetic monitoring","_metadata":{"uid":"cs32572e3664317fa4"},"url":"/observability/synthetic-monitoring"},{"title_l10n":"Real user monitoring","_metadata":{"uid":"cs6c9d63696d568c3b"},"url":"/observability/real-user-monitoring"},{"title_l10n":"Universal Profiling","_metadata":{"uid":"csc17955dd2f2e9772"},"url":"/observability/universal-profiling"},{"title_l10n":"AIOps","_metadata":{"uid":"cs378204c3874ca8e0"},"url":"/observability/aiops"}],"_metadata":{"uid":"cs85b2751f40f3e527"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cs64367ecef14bcb75"}}},{"sublinks":{"sublinks":[{"title_l10n":"Observability Labs","_metadata":{"uid":"cs922d2c431301758e"},"url":"https://www.elastic.co/observability-labs"}],"_metadata":{"uid":"csd9188663d72fdd62"}}}],"created_at":"2023-06-04T12:03:24.813Z","created_by":"blt3e52848e0cb3c394","sanity_migration_complete":false,"style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Solutions - Observability","title_l10n":"","updated_at":"2024-12-02T09:38:00.463Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2024-12-02T09:38:05.590Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Customers","_metadata":{"uid":"cs02fc8bc99a63871c"},"title_id":"nav-item-customers","url":"","sections":[{"title_l10n":"Customers - By solution and by industry","_metadata":{"uid":"cs37e49237bd8c8b6a"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt8a06ade8f3124e88","title":"Customers - By solution","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"bltacc5e178e52f430e","ACL":{},"content_type":"image/svg+xml","created_at":"2023-06-04T17:40:11.179Z","created_by":"blt3e52848e0cb3c394","file_size":"2499","filename":"icon-checkmark-decorative-border.svg","parent_uid":null,"tags":[],"title":"icon-checkmark-decorative-border.svg","updated_at":"2023-06-04T17:40:11.179Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:34:54.206Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltacc5e178e52f430e/647ccc7b6be35fb5eabd2100/icon-checkmark-decorative-border.svg"},"_metadata":{"uid":"cs4dd1fca9f5f44f70"},"alt_text_l10n":""}},{"title":{"title_l10n":"By solution","_metadata":{"uid":"cs5da14c808687a24e"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eSee how customers search, solve, and succeed — all on one Search AI Platform.\u003c/p\u003e","_metadata":{"uid":"cs232ddd0cf2230d2d"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search","_metadata":{"uid":"cs5b14b1b43ac9d8c6"},"url":"/customers/success-stories?usecase=enterprise-search\u0026industry=All"},{"title_l10n":"Security","_metadata":{"uid":"csc5d7c70d48ca90ae"},"url":"/customers/success-stories?usecase=security-analytics\u0026industry=All"},{"title_l10n":"Observability","_metadata":{"uid":"cse86ef1e2be61f194"},"url":"/customers/success-stories?usecase=elastic-observability\u0026industry=All"}],"_metadata":{"uid":"cs24cb1db1f15de1c4"}}}],"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"All customer stories","_metadata":{"uid":"cs0ce277db9b7e5ae7"},"url":"/customers","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"cs165f459ec9fb4aa5"},"footnote_l10n":""}}],"tags":[],"locale":"en-us","style":{"type":"Illustration Grid - two column"},"title_l10n":"","created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-06-04T12:02:51.393Z","updated_at":"2024-05-10T23:00:02.210Z","ACL":{},"_version":9,"publish_details":{"time":"2024-05-15T12:50:42.894Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","_version":3,"locale":"en-us","uid":"blt1d401e05c1cb52ce","ACL":{},"below_column_modular_blocks":[{"cta_group":{"alignment":"left","width":"block","list":[{"type":"tertiary","title_l10n":"Industries overview","_metadata":{"uid":"cs11ae98a64026023e"},"url":"/industries","icon_file":null,"icon_direction":null}],"_metadata":{"uid":"csa93a1ad9dbde01ba"},"footnote_l10n":""}}],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt9f634b6f74878698","ACL":{},"content_type":"image/svg+xml","created_at":"2023-06-04T17:39:46.794Z","created_by":"blt3e52848e0cb3c394","file_size":"1595","filename":"icon-briefcase.svg","parent_uid":null,"tags":[],"title":"icon-briefcase.svg","updated_at":"2023-06-04T17:39:46.794Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:36:29.443Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt9f634b6f74878698/647ccc625637890f19859454/icon-briefcase.svg"},"_metadata":{"uid":"cs8466139a3eb018b6"},"alt_text_l10n":""}},{"title":{"title_l10n":"Industries","_metadata":{"uid":"cs15073e3c310d94e5"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eExceed customer expectations and go to market faster.\u003c/p\u003e","_metadata":{"uid":"csd8f00d1e3c8e0ed4"}}},{"sublinks":{"sublinks":[{"title_l10n":"Public sector","_metadata":{"uid":"cs51ef52ec6b54b410"},"url":"/industries/public-sector"},{"title_l10n":"Financial services","_metadata":{"uid":"cs22eff93153cc2fbe"},"url":"/industries/financial-services"},{"title_l10n":"Telecommunications","_metadata":{"uid":"csacac8855fc00c0f8"},"url":"/industries/telecommunications"},{"title_l10n":"Retail","_metadata":{"uid":"csa363462a65d751a1"},"url":"/industries/retail-ecommerce"},{"title_l10n":"Manufacturing","_metadata":{"uid":"cs38a6bfd8d2f6022e"},"url":"/industries/manufacturing"}],"_metadata":{"uid":"cs9983d6253e2017aa"}}}],"created_at":"2024-05-10T22:59:23.362Z","created_by":"blt3044324473ef223b70bc674c","style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Customers - Industries","title_l10n":"","updated_at":"2024-05-15T18:10:31.550Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-15T18:11:29.679Z","user":"blt3044324473ef223b70bc674c"}}]},{"title_l10n":"Customer spotlight","_metadata":{"uid":"csb4ca6ac5082711d7"},"background_style":"Gray","reference":[{"_content_type_uid":"site_navigation_reference","uid":"bltf4eeed992c6383a2","_version":15,"locale":"en-us","ACL":{},"below_column_modular_blocks":[],"column_modular_blocks":[{"title":{"title_l10n":"Customer spotlight","_metadata":{"uid":"cs69b04a73066109e4"},"url":""}},{"card":{"type":null,"image":{"type":"thumbnail-128","file":{"_version":1,"is_dir":false,"uid":"blt652fec920f2b1a14","ACL":{},"content_type":"image/svg+xml","created_at":"2023-09-21T10:40:07.365Z","created_by":"blt3e52848e0cb3c394","file_size":"64960","filename":"logo-nav-dropdown-48x48-cisco.svg","parent_uid":null,"tags":[],"title":"logo-nav-dropdown-48x48-cisco.svg","updated_at":"2023-09-21T10:40:07.365Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-29T17:10:07.068Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt652fec920f2b1a14/650c1d87aa86c13fa1cc288c/logo-nav-dropdown-48x48-cisco.svg"},"alt_text_l10n":"Cisco logo"},"_metadata":{"uid":"cs5f973141d5cc1738"},"title_l10n":"","paragraph_l10n":"\u003cp\u003eCisco saves 5,000 support engineer hours per month\u003c/p\u003e","cta":[{"title_l10n":"Read more","_metadata":{"uid":"csf06d2489c4bd37ef"},"url":"/customers/cisco"}]}},{"card":{"type":null,"image":{"type":"thumbnail-128","file":{"uid":"blte788c0f923f209a3","_version":1,"title":"logo-dropdown-48x48-sitecore.svg","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-07-08T20:20:05.367Z","updated_at":"2024-07-08T20:20:05.367Z","content_type":"image/svg+xml","file_size":"4873","filename":"logo-dropdown-48x48-sitecore.svg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-07-08T20:21:17.641Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte788c0f923f209a3/668c49f5534bb913eb26e9e8/logo-dropdown-48x48-sitecore.svg"},"alt_text_l10n":"Sitecore logo"},"_metadata":{"uid":"csa2a078ccf29d695e"},"title_l10n":"","paragraph_l10n":"\u003cp\u003eSitecore automates 96 percent of security workflows with Elastic\u003c/p\u003e","cta":[{"title_l10n":"Read more","_metadata":{"uid":"csd53cb4b361d76ca2"},"url":"/customers/sitecore-security"}]}},{"card":{"type":null,"image":{"type":"thumbnail-128","file":{"_version":1,"is_dir":false,"uid":"blt90a52ed02808cbc1","ACL":{},"content_type":"image/svg+xml","created_at":"2023-09-21T10:40:45.741Z","created_by":"blt3e52848e0cb3c394","file_size":"47721","filename":"logo-nav-dropdown-48x48-comcast.svg","parent_uid":null,"tags":[],"title":"logo-nav-dropdown-48x48-comcast.svg","updated_at":"2023-09-21T10:40:45.741Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-09-29T17:10:28.064Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt90a52ed02808cbc1/650c1dadb25642d90add1e4e/logo-nav-dropdown-48x48-comcast.svg"},"alt_text_l10n":"Comcast logo"},"_metadata":{"uid":"csc9c0ac125da0e92b"},"title_l10n":"","paragraph_l10n":"\u003cp\u003eComcast transforms customer experiences with Elastic Observability\u003c/p\u003e","cta":[{"title_l10n":"Read more","_metadata":{"uid":"csada0ee69c800d1e2"},"url":"/customers/comcast"}]}}],"created_at":"2023-06-04T17:04:44.752Z","created_by":"blt3e52848e0cb3c394","style":{"type":"Customer spotlight"},"tags":[],"title":"Customers - Customer spotlight","title_l10n":"Customer Spotlight","updated_at":"2024-07-08T21:10:17.479Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-07-08T21:10:20.899Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Resources","_metadata":{"uid":"cs6d6faf906902f3c2"},"title_id":"nav-item-resources","url":"","sections":[{"title_l10n":"Research, Build, Learn, Connect","_metadata":{"uid":"csac521faabda66147"},"background_style":null,"reference":[{"_content_type_uid":"site_navigation_reference","uid":"blt2da6064728802db5","_version":3,"locale":"en-us","ACL":{},"below_column_modular_blocks":[],"column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cse8a0cd9936682cef"},"alt_text_l10n":""}},{"title":{"title_l10n":"Research","_metadata":{"uid":"cscb627b8efa82cba0"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eStay at the forefront of innovation with technical tips from the experts.\u003c/p\u003e","_metadata":{"uid":"csddfb11d93d95bad7"}}},{"sublinks":{"sublinks":[{"title_l10n":"Search Labs","_metadata":{"uid":"cs58dba67e336edf8b"},"url":"https://www.elastic.co/search-labs"},{"title_l10n":"Security Labs","_metadata":{"uid":"csffc4aa7973e5ffba"},"url":"https://www.elastic.co/security-labs"},{"title_l10n":"Observability Labs","_metadata":{"uid":"cs5a301cabb223025d"},"url":"https://www.elastic.co/observability-labs"}],"_metadata":{"uid":"cs1ac1fdfa36126b2f"}}}],"created_at":"2024-05-10T23:09:27.197Z","created_by":"blt3044324473ef223b70bc674c","sanity_migration_complete":false,"style":{"type":"Illustration Grid - two column"},"tags":[],"title":"Resources - Research","title_l10n":"","updated_at":"2024-12-02T09:41:27.963Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2024-12-02T09:41:32.349Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"blt74484ccc1b85172f","title":"Resources - Build","style":{"type":"Illustration Grid - two column"},"title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cs44c67d7b9a7d1650"},"alt_text_l10n":""}},{"title":{"title_l10n":"Build","_metadata":{"uid":"cse60ed914d4f01062"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eCode with other developers to create a better Elastic, together.\u003c/p\u003e","_metadata":{"uid":"csc56a3cd59fe094f5"}}},{"sublinks":{"sublinks":[{"title_l10n":"Community","url":"/community","_metadata":{"uid":"csd88d4c1cd46edc5d"}},{"title_l10n":"Forum","url":"https://discuss.elastic.co","_metadata":{"uid":"csb90d3bb62af3a70b"}},{"title_l10n":"Downloads","url":"/downloads","_metadata":{"uid":"cs7d47f2c7085e8b89"}},{"title_l10n":"Documentation","url":"/guide","_metadata":{"uid":"csd9f5895ad4598f70"}}],"_metadata":{"uid":"cs0ac4399ed28c210f"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-10T23:10:45.764Z","updated_at":"2024-05-10T23:10:45.764Z","ACL":{},"_version":1,"publish_details":{"time":"2024-05-15T12:50:42.957Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"blt934060d9e8d39d63","title":"Resources - Learn","title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cs5ed8e58e5dfaca72"},"alt_text_l10n":""}},{"title":{"title_l10n":"Learn","_metadata":{"uid":"cs019e09cee63b6044"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eUnleash the possibilities of your data and grow your skill set.\u003c/p\u003e","_metadata":{"uid":"cs2dd1ed4ed0245fb1"}}},{"sublinks":{"sublinks":[{"title_l10n":"Getting started","_metadata":{"uid":"csfc9cb80c881cd24a"},"url":"/getting-started"},{"title_l10n":"Elastic resources","_metadata":{"uid":"cs397c877c7fb56827"},"url":"/learn"},{"title_l10n":"Consulting services","_metadata":{"uid":"csbfa8b33d458721f6"},"url":"/consulting"},{"title_l10n":"Trainings \u0026 certifications","_metadata":{"uid":"csd9ec8c412f31120a"},"url":"/training"}],"_metadata":{"uid":"cs9cc31abd8fb24ad8"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","style":{"type":"Illustration Grid - two column"},"created_by":"blt3e52848e0cb3c394","updated_by":"blt3044324473ef223b70bc674c","created_at":"2023-06-04T12:01:35.685Z","updated_at":"2024-05-10T23:12:02.296Z","ACL":{},"_version":8,"publish_details":{"time":"2024-05-15T12:50:43.025Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_content_type_uid":"site_navigation_reference","uid":"blt845ebfe78aed4d5e","title":"Resources - Connect/Have questions","style":{"type":"Illustration Grid - two column"},"title_l10n":"","column_modular_blocks":[{"image":{"type":"icon-32","file":{"_version":1,"is_dir":false,"uid":"blt96bf0c70d7851e7d","ACL":{},"content_type":"image/svg+xml","created_at":"2023-07-18T17:36:03.382Z","created_by":"blt36e890d06c5ec32c","file_size":"1939","filename":"icon-code-self-closing.svg","parent_uid":null,"tags":[],"title":"icon-code-self-closing.svg","updated_at":"2023-07-18T17:36:03.382Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-09T17:35:38.133Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt96bf0c70d7851e7d/64b6cd8378402d4f9cc28b43/icon-code-self-closing.svg"},"_metadata":{"uid":"cse56c42201943cd81"},"alt_text_l10n":""}},{"title":{"title_l10n":"Connect","_metadata":{"uid":"cs06fc73baa9cc0e3a"},"url":""}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eKeep informed about the latest tech and news from Elastic.\u003c/p\u003e","_metadata":{"uid":"cs6b31c90db1e2a16c"}}},{"sublinks":{"sublinks":[{"title_l10n":"Blog","_metadata":{"uid":"csf3d7822d155dba5f"},"url":"/blog"},{"title_l10n":"Events","_metadata":{"uid":"csb66cf41564a89c85"},"url":"/events"}],"_metadata":{"uid":"cs1fef3e4e9c6dbed8"}}},{"divider":{"color":"darkGray","height":"1px","_metadata":{"uid":"cse01f8ca7bd6510d5"}}},{"paragraph":{"paragraph_l10n":"\u003cp\u003eHave questions?\u003c/p\u003e","_metadata":{"uid":"cs5a829b57a618798d"}}},{"sublinks":{"sublinks":[{"title_l10n":"Contact sales","_metadata":{"uid":"cs96d4362517c2285c"},"url":"/contact?storm=global-header-en"},{"title_l10n":"Get support","_metadata":{"uid":"cs7aa5c4baaaef5c7d"},"url":"/support"}],"_metadata":{"uid":"cs04b8e73b8815803a"}}}],"below_column_modular_blocks":[],"tags":[],"locale":"en-us","created_by":"blt3044324473ef223b70bc674c","updated_by":"blt3044324473ef223b70bc674c","created_at":"2024-05-10T23:18:50.596Z","updated_at":"2024-05-14T02:49:41.602Z","ACL":{},"_version":5,"publish_details":{"time":"2024-05-15T12:50:42.982Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}]}],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Pricing","_metadata":{"uid":"csaf6025f268634b11"},"title_id":"nav-item-pricing","url":"/pricing","sections":[],"dropdown_footer":{"title_l10n":"","cards":[]}},{"title_l10n":"Docs","_metadata":{"uid":"cs4989d0473c51cc69"},"title_id":"nav-item-docs","url":"https://www.elastic.co/docs","sections":[],"dropdown_footer":{"title_l10n":"","cards":[]}}],"tags":[],"title":"Site Navigation","updated_at":"2024-08-14T18:26:51.120Z","updated_by":"blt3044324473ef223b70bc674c","url":"/","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-14T18:27:02.197Z","user":"blt3044324473ef223b70bc674c"}}],1],"footer":{"uid":"blt269f572cdb5d93d5","_version":29,"locale":"en-us","ACL":{},"bottom_nav":[{"assigned_to_column":"1","title_l10n":"About us","_metadata":{"uid":"cs6cd917a10b9de1ff"},"url":"","sub_nav":[{"title_l10n":"About Elastic","_metadata":{"uid":"cs57853e838eec1fb4"},"url":"/about/","label":""},{"title_l10n":"Leadership","_metadata":{"uid":"cs7b59ceb017ff22bd"},"url":"/about/leadership","label":""},{"title_l10n":"DE\u0026I","_metadata":{"uid":"csb0b86d236613965f"},"url":"/careers/diversity-and-inclusion","label":""},{"title_l10n":"Blog","_metadata":{"uid":"cs3246df6b3f8161fe"},"url":"/blog","label":""},{"title_l10n":"Newsroom","_metadata":{"uid":"cs3d227dcae1bb8384"},"url":"/about/press","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"1","title_l10n":"Join us","_metadata":{"uid":"cs4d22a4582aebc90c"},"url":"","sub_nav":[{"title_l10n":"Careers","_metadata":{"uid":"csca2cc3d07a6b7d36"},"url":"/careers","label":""},{"title_l10n":"Career portal","_metadata":{"uid":"cs53d10ad225a44f28"},"url":"https://jobs.elastic.co/#/","label":""},{"title_l10n":"How we hire","url":"/careers/how-we-hire","label":"","_metadata":{"uid":"cs832de86dbf975c63"}}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"2","title_l10n":"Partners","_metadata":{"uid":"cs5fef14456079028c"},"url":"","sub_nav":[{"title_l10n":"Find a partner","_metadata":{"uid":"cse2fd098c7efded04"},"url":"https://partners.elastic.co/findapartner/","label":""},{"title_l10n":"Partner login","_metadata":{"uid":"cs95528fa33120b654"},"url":"https://login.elastic.co/login/partner","label":""},{"title_l10n":"Request access","_metadata":{"uid":"cs30282070e0411be1"},"url":"https://partners.elastic.co/English/register_email.aspx","label":""},{"title_l10n":"Become a partner","_metadata":{"uid":"cs0792dcf8683f5042"},"url":"/partners/become-a-partner","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"2","title_l10n":"Trust \u0026 Security","_metadata":{"uid":"cs676bf9d92ab4cab2"},"url":"","sub_nav":[{"title_l10n":"Trust center","_metadata":{"uid":"cs0e067ac5cdb67f07"},"url":"/trust","label":""},{"title_l10n":"EthicsPoint portal","_metadata":{"uid":"csa5a6f1f0f4ad6561"},"url":"https://secure.ethicspoint.com/domain/media/en/gui/74447/index.html","label":""},{"title_l10n":"ECCN report","_metadata":{"uid":"cs10977a5ef048e0ee"},"url":"/trust/business-integrity#international-trade-compliance—eccn-information","label":""},{"title_l10n":"Ethics email","_metadata":{"uid":"cs3e9bd0524b74e154"},"url":"mailto:ethics@elastic.co","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"3","title_l10n":"Investor relations","_metadata":{"uid":"cs12f93a5521bcc919"},"url":"","sub_nav":[{"title_l10n":"Investor resources","_metadata":{"uid":"cs0f53f841a7406963"},"url":"https://ir.elastic.co/home/default.aspx","label":""},{"title_l10n":"Governance","_metadata":{"uid":"cs372c8a459d030d80"},"url":"https://ir.elastic.co/governance/corporate-governance/default.aspx","label":""},{"title_l10n":"Financials","_metadata":{"uid":"cs44c6147db9c45464"},"url":"https://ir.elastic.co/financials/quarterly-results/default.aspx","label":""},{"title_l10n":"Stock","_metadata":{"uid":"csdceab8cb42b2e8e6"},"url":"https://ir.elastic.co/stock/stock-quote/default.aspx","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]},{"assigned_to_column":"3","title_l10n":"Excellence Awards","_metadata":{"uid":"csef48ff6cc0c8017f"},"url":"","sub_nav":[{"title_l10n":"Previous winners","_metadata":{"uid":"cs0033483bf17111bb"},"url":"/blog/2022-elastic-excellence-awards-winners","label":""},{"title_l10n":"ElasticON Tour","_metadata":{"uid":"csd7af0a9be8c75c8c"},"url":"/elasticon","label":""},{"title_l10n":"Become a sponsor","_metadata":{"uid":"cse46c08157caa313e"},"url":"/events/sponsor","label":""},{"title_l10n":"All events","_metadata":{"uid":"csa8aadaa647b40c37"},"url":"/events/","label":""}],"title2_l10n":"","url2":"","sub_nav2":[]}],"copyright_l10n":"\u003cp\u003e© \u003cspan class=\"copyright-year\"\u003e\u003c/span\u003e. Elasticsearch B.V. All Rights Reserved\u003c/p\u003e","created_at":"2023-07-12T17:40:07.721Z","created_by":"blt36e890d06c5ec32c","footnote_l10n":"\u003cp\u003eElastic, Elasticsearch and other related marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries.\u003c/p\u003e\u003cp\u003eApache, Apache Lucene, Apache Hadoop, Hadoop, HDFS and the yellow elephant logo are trademarks of the \u003ca href=\"https://www.apache.org/\"\u003eApache Software Foundation\u003c/a\u003e in the United States and/or other countries. All other brand names, product names, or trademarks belong to their respective owners.\u003c/p\u003e","legal_links":[{"title_l10n":"Trademarks","_metadata":{"uid":"csc3a92ddcd1567637"},"url":"/legal/trademarks"},{"title_l10n":"Terms of Use","_metadata":{"uid":"cs244688727f583112"},"url":"/legal/terms-of-use"},{"title_l10n":"Privacy","_metadata":{"uid":"cs227108640c2a1b4b"},"url":"/legal/privacy-statement"},{"title_l10n":"Sitemap","_metadata":{"uid":"cs01d3fe43dedf205c"},"url":"/sitemap"}],"logo":{"uid":"bltf8467a95eaa27e4a","_version":1,"created_by":"blt27204bf9f7abb7fd","updated_by":"blt27204bf9f7abb7fd","created_at":"2024-05-06T13:15:06.525Z","updated_at":"2024-05-06T13:15:06.525Z","content_type":"image/svg+xml","file_size":"18710","filename":"logo-tagline_secondary_all_white-177.svg","title":"logo-tagline_secondary_all_white-177.svg","ACL":{},"parent_uid":null,"is_dir":false,"tags":[],"publish_details":{"time":"2024-05-06T14:16:52.270Z","user":"blt27204bf9f7abb7fd","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltf8467a95eaa27e4a/6638d7da0d02e4e98155aaa3/logo-tagline_secondary_all_white-177.svg"},"sanity_migration_complete":false,"social_media_label_l10n":"Follow us","social_media_links":[{"title_l10n":"LinkedIn","_metadata":{"uid":"cs8281b766eac50225"},"url":"https://www.linkedin.com/company/elastic-co","image":{"uid":"blte7cfb1a091901ce1","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:34.613Z","updated_at":"2020-05-04T12:37:38.030Z","content_type":"image/svg+xml","file_size":"1528","filename":"footer-icon-linkedin.svg","title":"footer-icon-linkedin.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte7cfb1a091901ce1/5eb00c925751b2150e57a9d6/footer-icon-linkedin.svg"},"hover_icon":null,"tracking_id":"footer_linkedin"},{"title_l10n":"YouTube","_metadata":{"uid":"cs0a7ef0f38baa3dc4"},"url":"https://www.youtube.com/user/elasticsearch","image":{"uid":"blt7c28b18be98b1af8","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:59.474Z","updated_at":"2020-05-04T12:38:01.471Z","content_type":"image/svg+xml","file_size":"1890","filename":"footer-icon-youtube.svg","title":"footer-icon-youtube.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt7c28b18be98b1af8/5eb00ca908d37e6d82ef7655/footer-icon-youtube.svg"},"hover_icon":null,"tracking_id":"footer_youtube"},{"title_l10n":"Facebook","_metadata":{"uid":"csbe2c2f5c606f8c8d"},"url":"https://www.facebook.com/elastic.co","image":{"uid":"blt75566c5278ad68da","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:02.511Z","updated_at":"2020-05-04T12:36:41.395Z","content_type":"image/svg+xml","file_size":"1143","filename":"footer-icon-facebook.svg","title":"footer-icon-facebook.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt75566c5278ad68da/5eb00c59d238e314f259fbea/footer-icon-facebook.svg"},"hover_icon":null,"tracking_id":"footer_facebook"},{"title_l10n":"Twitter","_metadata":{"uid":"csac0b218be6f14543"},"url":"https://www.twitter.com/elastic","image":{"uid":"blt341fed86979a9fbb","created_by":"blt3e52848e0cb3c394","updated_by":"blt3e52848e0cb3c394","created_at":"2019-06-26T13:41:18.715Z","updated_at":"2020-05-04T12:37:10.251Z","content_type":"image/svg+xml","file_size":"2572","filename":"footer-icon-twitter.svg","title":"footer-icon-twitter.svg","ACL":{},"_version":2,"is_dir":false,"tags":[],"description":"","parent_uid":null,"publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2020-05-05T11:51:40.866Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt341fed86979a9fbb/5eb00c76b8a6356e4ddc1180/footer-icon-twitter.svg"},"hover_icon":null,"tracking_id":"footer_twitter"},{"title_l10n":"GitHub","_metadata":{"uid":"cs3f871c12d50cb1c4"},"url":"https://github.com/elastic","image":{"_version":1,"is_dir":false,"uid":"blt6ef5841a45696d80","ACL":{},"content_type":"image/svg+xml","created_at":"2023-08-02T10:05:35.275Z","created_by":"blt3e52848e0cb3c394","file_size":"1327","filename":"icon-footer-github.svg","parent_uid":null,"tags":[],"title":"icon-footer-github.svg","updated_at":"2023-08-02T10:05:35.275Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-06-26T23:47:50.075Z","user":"blt3044324473ef223b70bc674c"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blt6ef5841a45696d80/64ca2a6fc530871313bc3822/icon-footer-github.svg"},"hover_icon":null,"tracking_id":""}],"tags":[],"title":"Footer Redesign 2023","updated_at":"2024-11-07T21:46:07.252Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-11-09T02:07:26.435Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},"headers":{"country-code":"IN"},"subNav":[[{"uid":"bltaa9e8ef97db20945","_version":179,"locale":"en-us","ACL":{},"collapse_menu":{"title_l10n":"Collapse menu"},"created_at":"2022-03-15T00:28:09.929Z","created_by":"blt3044324473ef223b70bc674c","level_2":[{"title_l10n":"About","_metadata":{"uid":"cs8e091c3682d07b9f"},"url":"/about","level_3":[{"title_l10n":"Leadership","_metadata":{"uid":"cs51a59c6870a53681"},"url":"/about/leadership","level_4":[]},{"title_l10n":"Board","_metadata":{"uid":"cs93163805bdd45c96"},"url":"/about/board","level_4":[]},{"title_l10n":"Open source","_metadata":{"uid":"cs23a3f05026c3f3aa"},"url":"/about/open-source","level_4":[]},{"title_l10n":"Media","_metadata":{"uid":"cs0b695b5ccd67dfe7"},"url":"/about/press","level_4":[]},{"title_l10n":"ESG","_metadata":{"uid":"csfc5459e2272d8169"},"url":"/about/esg","level_4":[]},{"title_l10n":"Trust","_metadata":{"uid":"cs854223d2b53a055d"},"url":"/trust","level_4":[]}],"unlisted":[{"title_l10n":"Source Code","_metadata":{"uid":"cse7f28813f700063b"},"url":"/about/our-source-code"},{"title_l10n":"Distributed","_metadata":{"uid":"cs4069554cd5f6b28a"},"url":"/about/distributed"}]},{"title_l10n":"Blog","_metadata":{"uid":"cs15a678df84fd56c2"},"url":"/blog","level_3":[{"title_l10n":"Solutions","_metadata":{"uid":"cs4207ff196bc706b1"},"url":"/blog/category/solutions","level_4":[]},{"title_l10n":"Stack + Cloud","_metadata":{"uid":"cs5441abdada9821d3"},"url":"/blog/category/stack-cloud","level_4":[]},{"title_l10n":"News","_metadata":{"uid":"cs1e85870f77b92cd6"},"url":"/blog/category/company-news","level_4":[]},{"title_l10n":"Customers","_metadata":{"uid":"cs825404bee91003c3"},"url":"/blog/category/customers","level_4":[]},{"title_l10n":"Generative AI","_metadata":{"uid":"csaa7aa42e834f4477"},"url":"/blog/category/generative-ai","level_4":[]},{"title_l10n":"Culture","_metadata":{"uid":"csef703334f6243895"},"url":"/blog/category/culture","level_4":[]}],"unlisted":[]},{"title_l10n":"Careers","_metadata":{"uid":"cs969077f437917ab2"},"url":"/careers/","level_3":[{"title_l10n":"Our values","_metadata":{"uid":"cs4b8d5b0e5636d8f3"},"url":"/careers/our-values","level_4":[]},{"title_l10n":"Diversity","_metadata":{"uid":"cs9e9e3af649cdca99"},"url":"/careers/diversity-and-inclusion","level_4":[]},{"title_l10n":"Apply now","_metadata":{"uid":"cs40392061bf97b03f"},"url":"https://jobs.elastic.co/all-openings#/","level_4":[]},{"title_l10n":"How we hire","_metadata":{"uid":"csd4df1b5e6f6e2202"},"url":"/careers/how-we-hire","level_4":[]}],"unlisted":[]},{"title_l10n":"Community","_metadata":{"uid":"csa7c1026c5be4ea6e"},"url":"/community","level_3":[{"title_l10n":"Meetups","_metadata":{"uid":"cs5f78ad934ea2205a"},"url":"https://www.meetup.com/pro/elastic/","level_4":[]},{"title_l10n":"Forums","_metadata":{"uid":"csdbb9e951df255450"},"url":"https://discuss.elastic.co/","level_4":[]},{"title_l10n":"Contributors","_metadata":{"uid":"csd075c05386901a0f"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs26101e3bed0a4d02"},"url":"/community/contributor"},{"title_l10n":"Rules","_metadata":{"uid":"cs22e3a8ac4fe28ce5"},"url":"/community/contributor/rules"},{"title_l10n":"Submissions","_metadata":{"uid":"cscb9adc71046046b8"},"url":"/community/contributor/submissions"},{"title_l10n":"Awards","_metadata":{"uid":"cs4b5f2e050fad550b"},"url":"/community/contributor/awards"},{"title_l10n":"FAQ","_metadata":{"uid":"cs59205ebe12a7ec2d"},"url":"/community/contributor/faq"},{"title_l10n":"Contributor portal","_metadata":{"uid":"cs2e8a2af70005fb4c"},"url":"https://contributor-program.app.elstc.co/"}]},{"title_l10n":"Code of conduct","_metadata":{"uid":"csa8ceb4bdb0d19c1d"},"url":"/community/codeofconduct","level_4":[]},{"title_l10n":"Newsletter","_metadata":{"uid":"cscbc9596811de7ad0"},"url":"/community/newsletter","level_4":[]},{"title_l10n":"Help","_metadata":{"uid":"cs1a30f9e3c4d47a24"},"url":"/community/help","level_4":[]}],"unlisted":[]},{"title_l10n":"Consulting","_metadata":{"uid":"cs0048b24adf49ac89"},"url":"/consulting","level_3":[{"title_l10n":"Boost services","_metadata":{"uid":"cs93b353c225c34e62"},"url":"/consulting/boost-services","level_4":[]},{"title_l10n":"Cloud migration","_metadata":{"uid":"cs267573d97e318669"},"url":"/consulting/cloud-migration-services","level_4":[]},{"title_l10n":"Advisory services","_metadata":{"uid":"cs60ffc2c0967469de"},"url":"/consulting/advisory-services","level_4":[]},{"title_l10n":"Contact","_metadata":{"uid":"csa6ac6c2c01f8e140"},"url":"/consulting/contact","level_4":[]}],"unlisted":[]},{"title_l10n":"Customers","_metadata":{"uid":"csc0ea258b71fc82b0"},"url":"/customers","level_3":[{"title_l10n":"Use cases","_metadata":{"uid":"cs070e1aed0e6b3d61"},"url":"","level_4":[{"title_l10n":"Search","_metadata":{"uid":"csc49f7b01bd1f922f"},"url":"/customers/success-stories?usecase=enterprise-search\u0026industry=All"},{"title_l10n":"Observability","_metadata":{"uid":"csc67dd4db7de37244"},"url":"/customers/success-stories?usecase=elastic-observability\u0026industry=All"},{"title_l10n":"Security","_metadata":{"uid":"cs399d89851a0da445"},"url":"/customers/success-stories?usecase=security-analytics\u0026industry=All"}]},{"title_l10n":"Value","_metadata":{"uid":"csf92f4d053140915f"},"url":"/customers/value","level_4":[]}],"unlisted":[{"title_l10n":"Customer value","_metadata":{"uid":"csdc32877d2588370d"},"url":"/customers/value"}]},{"title_l10n":"Elastic Cloud","_metadata":{"uid":"csadc9ecd5d3ccbc57"},"url":"/cloud","level_3":[{"title_l10n":"Serverless","_metadata":{"uid":"csc13d13e75a303990"},"url":"/cloud/serverless","level_4":[{"title_l10n":"Serverless roadmap","_metadata":{"uid":"csb4626fd3abd2508f"},"url":"/cloud/serverless/roadmap"},{"title_l10n":"Search AI Lake","_metadata":{"uid":"cs1451f73495a09dda"},"url":"/cloud/serverless/search-ai-lake"}]},{"title_l10n":"Regions","_metadata":{"uid":"csd395063dddd8845c"},"url":"/cloud/regions","level_4":[]},{"title_l10n":"Docs","_metadata":{"uid":"cs0601c60d26f18c69"},"url":"https://www.elastic.co/guide/en/cloud/current/index.html","level_4":[]},{"title_l10n":"Shared responsibility","_metadata":{"uid":"cs78cfc0cc33a0f07a"},"url":"/cloud/shared-responsibility","level_4":[]},{"title_l10n":"Cloud migration","_metadata":{"uid":"cs99559229bb453ba4"},"url":"","level_4":[{"title_l10n":"Developers","_metadata":{"uid":"cs6b23c5745eabd086"},"url":"/cloud/platform-migration-dev/"},{"title_l10n":"Business Leaders","_metadata":{"uid":"csa656e7b98e93ec8f"},"url":"/cloud/platform-migration"},{"title_l10n":"Consulting services","_metadata":{"uid":"cs505e18ed277cc6ce"},"url":"/cloud/cloud-migration-services"}]}],"unlisted":[{"title_l10n":"Elastic Cloud Enterprise","_metadata":{"uid":"csad2dd1950db00c3a"},"url":"/ece"},{"title_l10n":"Elastic Cloud on Kubernetes","_metadata":{"uid":"cs116ae0b80627d3bd"},"url":"/elastic-cloud-kubernetes"},{"title_l10n":"Elastic App Search Service","_metadata":{"uid":"csb105633fb925c2f6"},"url":"/app-search/service"},{"title_l10n":"App Search Service pricing","_metadata":{"uid":"cs714085379fda18e6"},"url":"/app-search/service/pricing"},{"title_l10n":"Elastic Site Search Service","_metadata":{"uid":"cscd76d7fa04786f14"},"url":"/site-search/service"},{"title_l10n":"Site Search Service pricing","_metadata":{"uid":"cseafb7630188819b8"},"url":"/site-search/service/pricing"}]},{"title_l10n":"Elastic Stack","_metadata":{"uid":"cs60a7b8db425ecda6"},"url":"/elastic-stack","level_3":[{"title_l10n":"Features","_metadata":{"uid":"cs4c2b753f00e29c11"},"url":"/elastic-stack/features","level_4":[]},{"title_l10n":"Capabilities","_metadata":{"uid":"cs0ac881f9652ac2dc"},"url":"","level_4":[{"title_l10n":"Stack security","_metadata":{"uid":"csb16e64ebe7794179"},"url":"/what-is/elastic-stack-security"},{"title_l10n":"Machine learning","_metadata":{"uid":"cse6053162c8526c10"},"url":"/what-is/elasticsearch-machine-learning"},{"title_l10n":"Geospatial","_metadata":{"uid":"cscdff16895437806c"},"url":"/geospatial"},{"title_l10n":"Vector database","_metadata":{"uid":"cse48968b090b6807f"},"url":"/elasticsearch/vector-database"},{"title_l10n":"AutoOps","_metadata":{"uid":"cs42bff71c0925503d"},"url":"/platform/autoops"}]},{"title_l10n":"Elasticsearch","_metadata":{"uid":"cs6928bf21a330389c"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs08cabb5a3b90ede9"},"url":"/elasticsearch"},{"title_l10n":"Features","_metadata":{"uid":"cs03c3242fafe8f43c"},"url":"/elasticsearch/features"},{"title_l10n":"Elasticsearch Service","_metadata":{"uid":"cs9847a5cb39480166"},"url":"/elasticsearch/service"},{"title_l10n":"Elasticsearch searchable snapshots","_metadata":{"uid":"csf47888fa25ecb5f2"},"url":"/elasticsearch/elasticsearch-searchable-snapshots"},{"title_l10n":"Elasticsearch runtime fields","_metadata":{"uid":"cs1f99c5679876f78f"},"url":"/elasticsearch/elasticsearch-runtime-fields"},{"title_l10n":"Elasticsearch Relevance Engine","_metadata":{"uid":"cs404ad7d9e4de8ada"},"url":"/elasticsearch/elasticsearch-relevance-engine"}]},{"title_l10n":"Kibana","_metadata":{"uid":"cs78304ca2eada29b7"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs0eb09309d8eb60e8"},"url":"/kibana"},{"title_l10n":"Features","_metadata":{"uid":"cs29c3df77aa69834b"},"url":"/kibana/features"},{"title_l10n":"Kibana Canvas","_metadata":{"uid":"csb2c5fc936c9d37e9"},"url":"/what-is/kibana-canvas"},{"title_l10n":"Kibana Lens","_metadata":{"uid":"cs81b16f5b629c6734"},"url":"/kibana/kibana-lens"},{"title_l10n":"Kibana dashboard","_metadata":{"uid":"cs37cc1272dc9d1e79"},"url":"/kibana/kibana-dashboard"},{"title_l10n":"Kibana alerting","_metadata":{"uid":"csdca15c27859f48ca"},"url":"/what-is/kibana-alerting"},{"title_l10n":"Elastic Maps","_metadata":{"uid":"cs8f301712e95044fe"},"url":"/maps"},{"title_l10n":"Elastic Maps Service","_metadata":{"uid":"csf728be400b42cd60"},"url":"/elastic-maps-service"}]},{"title_l10n":"Integrations","_metadata":{"uid":"cs7e4a2f68f369617b"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"cs85db9ea3ae40465e"},"url":"/integrations"},{"title_l10n":"Data integrations","_metadata":{"uid":"csfcd0e63e8f2ee96a"},"url":"/integrations/data-integrations"},{"title_l10n":"Elastic Agent","_metadata":{"uid":"cs2751f90a3cec66f9"},"url":"/elastic-agent"},{"title_l10n":"Beats","_metadata":{"uid":"cscba27789614477d8"},"url":"/beats"},{"title_l10n":"Logstash","_metadata":{"uid":"cs3fd37ce923d20d9b"},"url":"/logstash"},{"title_l10n":"Web crawler","_metadata":{"uid":"csaf5ad6e3c2c8d43a"},"url":"/web-crawler"},{"title_l10n":"Content connectors","_metadata":{"uid":"cs3f2fc425a0ee4265"},"url":"/workplace-search/content-sources"}]},{"title_l10n":"Docs","_metadata":{"uid":"cs50ae00c58f827097"},"url":"https://www.elastic.co/guide/en/elastic-stack/current/index.html","level_4":[]}],"unlisted":[{"title_l10n":"What is Elasticsearch","_metadata":{"uid":"csf97903f364909b99"},"url":"/what-is/elasticsearch"},{"title_l10n":"Open X-Pack","_metadata":{"uid":"csc78be312aaff7a28"},"url":"/what-is/open-x-pack"},{"title_l10n":"What is the ELK Stack","_metadata":{"uid":"csdffef2c490972db8"},"url":"/what-is/elk-stack"},{"title_l10n":"Elasticsearch SQL","_metadata":{"uid":"cs404c333ec7ec4952"},"url":"/what-is/elasticsearch-sql"},{"title_l10n":"Elasticsearch-Hadoop","_metadata":{"uid":"cs6c24a5a40f30dfd4"},"url":"/what-is/elasticsearch-hadoop"},{"title_l10n":"Elasticsearch business analytics","_metadata":{"uid":"cs8fd31c81ae759787"},"url":"/what-is/elasticsearch-business-analytics"},{"title_l10n":"Elasticsearch graph","_metadata":{"uid":"cs8e205d91ee02bb96"},"url":"/what-is/elasticsearch-graph"},{"title_l10n":"Elasticsearch monitoring","_metadata":{"uid":"cs8bb9c4f6d47f9844"},"url":"/what-is/elasticsearch-monitoring"},{"title_l10n":"Elastic Common Schema","_metadata":{"uid":"cs7b1c798a93d36629"},"url":"/what-is/ecs"},{"title_l10n":"AWS Elasticsearch Service","_metadata":{"uid":"csc3872252e7286b8b"},"url":"/aws-elasticsearch-service"},{"title_l10n":"OpenSearch","_metadata":{"uid":"cs1b26f037931beadd"},"url":"/what-is/opensearch"},{"title_l10n":"What is Kibana","_metadata":{"uid":"csa66c8bfb9eeb7d64"},"url":"/what-is/kibana"},{"title_l10n":"Kibana feedback","_metadata":{"uid":"csa1f9cce921215858"},"url":"/kibana/feedback"},{"title_l10n":"Kibana ask us questions","_metadata":{"uid":"cs123bbb4d6f52c352"},"url":"/kibana/ask-elastic"},{"title_l10n":"Kibana reporting","_metadata":{"uid":"csa143fdde145d7da8"},"url":"/what-is/kibana-reporting"},{"title_l10n":"ServiceNow and Elastic","_metadata":{"uid":"cs23b5bf47ce54388e"},"url":"/what-is/servicenow"},{"title_l10n":"Help","_metadata":{"uid":"csca062d77a79f2faf"},"url":"/help"}]},{"title_l10n":"Search","_metadata":{"uid":"cs815dbfdfcb5d665d"},"url":"/enterprise-search","level_3":[{"title_l10n":"Capabilities","_metadata":{"uid":"csae031a6128f7400f"},"url":"","level_4":[{"title_l10n":"Data ingestion","_metadata":{"uid":"cs1840c4df996b35ab"},"url":"/enterprise-search/data-ingestion"},{"title_l10n":"Search UI","_metadata":{"uid":"cs2bfeb97c747a96a7"},"url":"/enterprise-search/search-ui"},{"title_l10n":"Search analytics","_metadata":{"uid":"csb97709dfb73eab49"},"url":"/enterprise-search/search-analytics"},{"title_l10n":"Provisioning","_metadata":{"uid":"cs802968c46c6d4a90"},"url":"/enterprise-search/deployment"},{"title_l10n":"Relevance","_metadata":{"uid":"csdb072364aaa5fb4b"},"url":"/enterprise-search/relevance"},{"title_l10n":"Machine learning","_metadata":{"uid":"cse1133a3fb4606c9a"},"url":"/enterprise-search/machine-learning"},{"title_l10n":"Vector database","_metadata":{"uid":"cse18cb18a810a2b13"},"url":"/elasticsearch/vector-database"},{"title_l10n":"Retrieval Augmented Generation","_metadata":{"uid":"cs5bb2a1c8ad475327"},"url":"/enterprise-search/rag"}]},{"title_l10n":"Use cases","_metadata":{"uid":"cs232455854532744c"},"url":"","level_4":[{"title_l10n":"Search applications","_metadata":{"uid":"cs9f7fba4ad3dd44bb"},"url":"/enterprise-search/search-applications"},{"title_l10n":"Ecommerce","_metadata":{"uid":"cs91e93b3cb71b94b2"},"url":"/enterprise-search/ecommerce"},{"title_l10n":"Website","_metadata":{"uid":"cs127db46d15150d15"},"url":"/enterprise-search/site-search"},{"title_l10n":"Workplace search","_metadata":{"uid":"csadc4b4c5dd21b53f"},"url":"/enterprise-search/workplace-search"},{"title_l10n":"Customer support","_metadata":{"uid":"cscb4a04887f303e5d"},"url":"/enterprise-search/customer-support"}]},{"title_l10n":"Docs","_metadata":{"uid":"cs1a6f89380c0872c8"},"url":"https://www.elastic.co/guide/en/enterprise-search/current/index.html","level_4":[]}],"unlisted":[]},{"title_l10n":"Events","_metadata":{"uid":"csbcb9840ba1d9acdb"},"url":"/events","level_3":[{"title_l10n":"Event videos","_metadata":{"uid":"csef7fae775cb448ac"},"url":"/events/videos","level_4":[]},{"title_l10n":"Elastic Excellence Awards","_metadata":{"uid":"csce1bc3f82e76e201"},"url":"/events/awards","level_4":[]},{"title_l10n":"Sponsor","_metadata":{"uid":"cs1029354d0af20664"},"url":"/events/sponsor","level_4":[]}],"unlisted":[]},{"title_l10n":"Getting started","_metadata":{"uid":"cs81808631706d95aa"},"url":"/getting-started","level_3":[{"title_l10n":"Data ingest","_metadata":{"uid":"cs4551c049b5bce4a9"},"url":"/customer-success/data-ingestion","level_4":[]},{"title_l10n":"Search Guides","_metadata":{"uid":"cs4dd23a7a841db1b3"},"url":"","level_4":[{"title_l10n":"Build an AI-powered search experience","_metadata":{"uid":"csf73f8655be7769c1"},"url":"/getting-started/enterprise-search/build-a-semantic-search-experience"},{"title_l10n":"Search across databases and business systems","_metadata":{"uid":"cs94f1e8b406cae10c"},"url":"/getting-started/enterprise-search/search-across-business-systems-and-software"},{"title_l10n":"Add search to your website","_metadata":{"uid":"cs7c73d9c5e1b9c693"},"url":"/getting-started/enterprise-search/add-search-to-your-website"},{"title_l10n":"Set up vector search","_metadata":{"uid":"cs45277c6abe450b02"},"url":"/getting-started/enterprise-search/vector-search"},{"title_l10n":"Build an application on top of Elasticsearch","_metadata":{"uid":"csb5c046a7df26ed60"},"url":"/getting-started/enterprise-search/build-an-application-on-top-of-elasticsearch"}]},{"title_l10n":"Observability Guides","_metadata":{"uid":"cse4691fd58cd3e1fe"},"url":"","level_4":[{"title_l10n":"Collect and analyze logs","_metadata":{"uid":"cs0fdbe552cdda5d84"},"url":"/getting-started/observability/collect-and-analyze-logs"},{"title_l10n":"Application performance monitoring","_metadata":{"uid":"cse9bc3f5a66245f0a"},"url":"/getting-started/observability/monitor-your-application-performance"},{"title_l10n":"Monitor your hosts","_metadata":{"uid":"cs50a6e0ab8c07d2fb"},"url":"/getting-started/observability/monitor-your-hosts"},{"title_l10n":"Kubernetes monitoring","_metadata":{"uid":"cs5bbc668d4f1ef63e"},"url":"/getting-started/observability/monitor-kubernetes-clusters"},{"title_l10n":"Synthetic monitoring","_metadata":{"uid":"cs61ca4004d8aab0e4"},"url":"/getting-started/observability/create-synthetic-monitor"}]},{"title_l10n":"Security Guides","_metadata":{"uid":"cs338104439ba04d75"},"url":"","level_4":[{"title_l10n":"SIEM","_metadata":{"uid":"cs06bf6cebc83287a7"},"url":"/getting-started/security/detect-threats-in-my-data-with-siem"},{"title_l10n":"Endpoint Security","_metadata":{"uid":"cs77396d612fe76685"},"url":"/getting-started/security/secure-my-hosts-with-endpoint-security"},{"title_l10n":"Cloud Security Posture Management","_metadata":{"uid":"cs35a5d9c5449f4ac5"},"url":"/getting-started/security/secure-my-cloud-assets-with-cloud-security-posture-management"}]},{"title_l10n":"Cloud providers","_metadata":{"uid":"cse05b315407095d1b"},"url":"","level_4":[{"title_l10n":"AWS","_metadata":{"uid":"csa16e918cc9bffb18"},"url":"/getting-started/aws"},{"title_l10n":"Google Cloud","_metadata":{"uid":"cs81ea6102c539d232"},"url":"/getting-started/google-cloud"},{"title_l10n":"Microsoft Azure","_metadata":{"uid":"csdbcf27b684e503ee"},"url":"/getting-started/microsoft-azure"}]}],"unlisted":[{"title_l10n":"Resources","_metadata":{"uid":"cs6dd493af724f798a"},"url":"/customer-success/resources"},{"title_l10n":"Customer success","_metadata":{"uid":"cs9f7d53a4c318df4d"},"url":"/customer-success/"}]},{"title_l10n":"Learn","_metadata":{"uid":"cs8bb13f85f00dddcd"},"url":"/learn","level_3":[{"title_l10n":"Videos","_metadata":{"uid":"cs653df48587680973"},"url":"/videos","level_4":[]},{"title_l10n":"White paper","_metadata":{"uid":"csb7a951170183ca96"},"url":"/learn/exploration-center","level_4":[]}],"unlisted":[]},{"title_l10n":"Observability","_metadata":{"uid":"cse4e0fb50dd4e95fd"},"url":"/observability","level_3":[{"title_l10n":"Capabilities","_metadata":{"uid":"csc296f379a0602ce1"},"url":"","level_4":[{"title_l10n":"Application performance monitoring","_metadata":{"uid":"cseab0aa3128578bc9"},"url":"/observability/application-performance-monitoring"},{"title_l10n":"Log monitoring","_metadata":{"uid":"csd03474cbaf4902ce"},"url":"/observability/log-monitoring"},{"title_l10n":"Infrastructure monitoring","_metadata":{"uid":"cs46ef7fc35494bfa7"},"url":"/observability/infrastructure-monitoring"},{"title_l10n":"Real user monitoring","_metadata":{"uid":"csea9acd1bbbbfde95"},"url":"/observability/real-user-monitoring"},{"title_l10n":"Synthetic monitoring","_metadata":{"uid":"cs44921c274725fe6d"},"url":"/observability/synthetic-monitoring"},{"title_l10n":"Universal profiling","_metadata":{"uid":"csace62291bb813cd4"},"url":"/observability/ebpf-continuous-code-profiling"}]},{"title_l10n":"Use cases","_metadata":{"uid":"cs64047eecb6ef228c"},"url":"","level_4":[{"title_l10n":"Cloud monitoring","_metadata":{"uid":"cs805172c3209d1b54"},"url":"/observability/cloud-monitoring"},{"title_l10n":"DevOps","_metadata":{"uid":"cs90631dd39dad3a1a"},"url":"/observability/devops"},{"title_l10n":"Cloud migration","_metadata":{"uid":"csc12e5aecf32ec016"},"url":"/observability/cloud-migration"},{"title_l10n":"Cloud native","_metadata":{"uid":"cs8a37f3b2b907608f"},"url":"/observability/cloud-native"},{"title_l10n":"Kubernetes monitoring","_metadata":{"uid":"csd55c740f313186b9"},"url":"/observability/kubernetes-monitoring"},{"title_l10n":"Serverless monitoring","_metadata":{"uid":"csb93f6b68cd95688f"},"url":"/observability/serverless-monitoring"},{"title_l10n":"OpenTelemetry","_metadata":{"uid":"cs67530af55fe9b32c"},"url":"/observability/opentelemetry"},{"title_l10n":"AIOps","_metadata":{"uid":"csf4a5b4cccd8b4420"},"url":"/observability/aiops"},{"title_l10n":"Digital experience","_metadata":{"uid":"csd3064a183915f3cb"},"url":"/observability/digital-experience-monitoring"},{"title_l10n":"Tool Consolidation","_metadata":{"uid":"csdd3038cf0d5189bd"},"url":"/observability/tool-consolidation"}]},{"title_l10n":"Integrations","_metadata":{"uid":"cs242e973705950a46"},"url":"/integrations/data-integrations?solution=observability","level_4":[]},{"title_l10n":"Docs","_metadata":{"uid":"cs98524b345bd61a42"},"url":"https://www.elastic.co/guide/en/observability/current/index.html","level_4":[]}],"unlisted":[{"title_l10n":"Prometheus monitoring","_metadata":{"uid":"cs8a431f6fa437a2d9"},"url":"/elasticsearch/prometheus-monitoring"}]},{"title_l10n":"Partners","_metadata":{"uid":"cs3155ab73235c8389"},"url":"/partners","level_3":[{"title_l10n":"Become a partner","_metadata":{"uid":"cs7701e9efdd695240"},"url":"/partners/become-a-partner","level_4":[]},{"title_l10n":"Support","_metadata":{"uid":"cs65a1c96e522aabd8"},"url":"","level_4":[{"title_l10n":"Contact us","_metadata":{"uid":"cs1fee03324e45ae1e"},"url":"/partners/contact"},{"title_l10n":"Program guide","_metadata":{"uid":"cs2f056d86678ebfc4"},"url":"/partners/program"}]},{"title_l10n":"Partner account","_metadata":{"uid":"cs236419f427ae708f"},"url":"","level_4":[{"title_l10n":"Login","_metadata":{"uid":"csf3e5ca80df9a2ec4"},"url":"https://login.elastic.co/login/partner"},{"title_l10n":"Request access","_metadata":{"uid":"csd1d246815afdb7da"},"url":"https://partners.elastic.co/English/register_email.aspx"}]}],"unlisted":[]},{"title_l10n":"Platform","_metadata":{"uid":"cs3dab20cab2c29923"},"url":"/products","level_3":[{"title_l10n":"What's new","_metadata":{"uid":"cs8a308f98f32daacf"},"url":"/whats-new","level_4":[]}],"unlisted":[]},{"title_l10n":"Pricing","_metadata":{"uid":"csfc63cdfc1c06399d"},"url":"/pricing","level_3":[{"title_l10n":"Elastic Cloud Serverless","_metadata":{"uid":"csb8a4fdb9c3bc4300"},"url":"","level_4":[{"title_l10n":"Elasticsearch Serverless","_metadata":{"uid":"csd97bc438bdc6d807"},"url":"/pricing/serverless-search"},{"title_l10n":"Elastic Security Serverless","_metadata":{"uid":"cs936f5653e401ba68"},"url":"/pricing/serverless-security"},{"title_l10n":"Elastic Observability Serverless","_metadata":{"uid":"csc47cb6fcee6a3718"},"url":"/pricing/serverless-observability"}]},{"title_l10n":"Benefits","_metadata":{"uid":"csb5cd64003b72b082"},"url":"/pricing/benefits","level_4":[]},{"title_l10n":"FAQ","_metadata":{"uid":"cs689e5f5ca8e039b0"},"url":"/pricing/faq","level_4":[]},{"title_l10n":"Features","_metadata":{"uid":"csc2015a372acc1084"},"url":"","level_4":[{"title_l10n":"Elastic Cloud","_metadata":{"uid":"csf1bb052541fd91ef"},"url":"/subscriptions/cloud"},{"title_l10n":"Self-managed","_metadata":{"uid":"cs21f845b2fe5757d2"},"url":"/subscriptions"}]}],"unlisted":[]},{"title_l10n":"Security","_metadata":{"uid":"cs16cbda02c3601d34"},"url":"/security/","level_3":[{"title_l10n":"Capabilities","_metadata":{"uid":"cseae0b1e586ba8fac"},"url":"","level_4":[{"title_l10n":"SIEM","_metadata":{"uid":"csa7c6619304d5d43e"},"url":"/security/siem"},{"title_l10n":"AI for the SOC","_metadata":{"uid":"csec7f9985bfa7acd1"},"url":"/security/ai"},{"title_l10n":"Security research","_metadata":{"uid":"cs48b56bae35f752ac"},"url":"https://www.elastic.co/security-labs"}]},{"title_l10n":"Features","_metadata":{"uid":"cs0106c99cab044dee"},"url":"","level_4":[{"title_l10n":"Endpoint Security","_metadata":{"uid":"csd2a677bc227c9b5c"},"url":"/security/endpoint-security"},{"title_l10n":"Cloud Security","_metadata":{"uid":"cs6ba30fd6994fd441"},"url":"/security/cloud-security"},{"title_l10n":"XDR","_metadata":{"uid":"cs8f2e4665d3e05358"},"url":"/security/xdr"},{"title_l10n":"CDR","_metadata":{"uid":"csfedb5e2871b95180"},"url":"/security/cloud-detection-and-response"}]},{"title_l10n":"Use cases","_metadata":{"uid":"cs501631844000d8ff"},"url":"","level_4":[{"title_l10n":"Continuous Monitoring","_metadata":{"uid":"cs516d9e75901b9e2f"},"url":"/security/continuous-monitoring"},{"title_l10n":"Threat Hunting","_metadata":{"uid":"cse59e1656166da3c2"},"url":"/security/threat-hunting"},{"title_l10n":"Streamlined investigation \u0026 response","_metadata":{"uid":"cse5d322ffe4da2123"},"url":"/security/investigation-response"},{"title_l10n":"Automated Threat Protection","_metadata":{"uid":"cs923005404e1e9a58"},"url":"/security/automated-threat-protection"}]},{"title_l10n":"Value calculator","_metadata":{"uid":"cs2d4170dce7f39ad5"},"url":"/security/value-calculator","level_4":[]},{"title_l10n":"Docs","_metadata":{"uid":"csce035df42beb2608"},"url":"https://www.elastic.co/guide/en/security/current/index.html","level_4":[]}],"unlisted":[]},{"title_l10n":"Security Labs","_metadata":{"uid":"csf6824d930aad376a"},"url":"/security-labs","level_3":[{"title_l10n":"About","_metadata":{"uid":"csb2589ed0d7b2a427"},"url":"/security-labs/about","level_4":[]},{"title_l10n":"Topics","_metadata":{"uid":"cse25a23f2a3af802a"},"url":"","level_4":[{"title_l10n":"Security Research","_metadata":{"uid":"cs7b629f746bd8afc2"},"url":"/security-labs/security-research"},{"title_l10n":"Malware Analysis","_metadata":{"uid":"cs2f3f082807873a63"},"url":"/security-labs/malware-analysis"},{"title_l10n":"Campaign","_metadata":{"uid":"cs1efed0ff19b6cb7d"},"url":"/security-labs/campaign"},{"title_l10n":"Groups \u0026 Tactics","_metadata":{"uid":"csb10dafb9c8538737"},"url":"/security-labs/groups-and-tactics"},{"title_l10n":"Detection Science","_metadata":{"uid":"csed887fc3ed3cacf6"},"url":"/security-labs/detection-science"}]},{"title_l10n":"Vuln updates","_metadata":{"uid":"csdc16bf239e9db7a9"},"url":"/security-labs/vulnerability-updates","level_4":[]},{"title_l10n":"Reports","_metadata":{"uid":"cs9f95eb60b65c9ec6"},"url":"/security-labs/reports","level_4":[]},{"title_l10n":"Tools","_metadata":{"uid":"cs424a38936637b3fb"},"url":"/security-labs/tools","level_4":[]}],"unlisted":[]},{"title_l10n":"Support","_metadata":{"uid":"cs32a26731618404a3"},"url":"/support","level_3":[{"title_l10n":"Support matrix","_metadata":{"uid":"csf95633f0f6b12cc7"},"url":"/support/matrix","level_4":[]},{"title_l10n":"Submit ticket","_metadata":{"uid":"cs7977b44b540d7211"},"url":"https://support.elastic.co/","level_4":[]}],"unlisted":[]},{"title_l10n":"Training","_metadata":{"uid":"csa5adc240a715c659"},"url":"/training","level_3":[{"title_l10n":"Private","_metadata":{"uid":"csb2c5866403d9a976"},"url":"/training/private-training","level_4":[]},{"title_l10n":"Subscriptions","_metadata":{"uid":"cs4303c8ed367f3d2b"},"url":"/training/subscriptions","level_4":[]},{"title_l10n":"Certifications","_metadata":{"uid":"csaf4321a2ffd12544"},"url":"/training/certification","level_4":[]},{"title_l10n":"Schedule","_metadata":{"uid":"cs03d21c9ad4b35af1"},"url":"/training/schedule","level_4":[]},{"title_l10n":"FAQ","_metadata":{"uid":"cscb69ba6d9cbf9d6c"},"url":"/training/faq","level_4":[]}],"unlisted":[]},{"title_l10n":"Use cases","_metadata":{"uid":"cse0705b3c33d28245"},"url":"/explore","level_3":[{"title_l10n":"Key topics","_metadata":{"uid":"csceafd77b846bc398"},"url":"","level_4":[{"title_l10n":"Power of Elastic","_metadata":{"uid":"cs6d22610e017ebb12"},"url":"/explore/succeed-with-power-of-elastic"},{"title_l10n":"Improving digital customer experiences","_metadata":{"uid":"csdfc902ad0d1715b4"},"url":"/explore/improving-digital-customer-experiences"},{"title_l10n":"Evolving the DevOps lifecycle","_metadata":{"uid":"csb48ace3e2e1fc0c1"},"url":"/explore/devops-observability"},{"title_l10n":"Security without limits","_metadata":{"uid":"csfba99822996d03cf"},"url":"/explore/security-without-limits"}]},{"title_l10n":"Industry","_metadata":{"uid":"cs9857d2f16dc7d396"},"url":"","level_4":[{"title_l10n":"Overview","_metadata":{"uid":"csc66e758d15ae6bdf"},"url":"/industries"},{"title_l10n":"Public Sector","_metadata":{"uid":"cs2a9e6c29d73574ce"},"url":"/industries/public-sector"},{"title_l10n":"Financial services","_metadata":{"uid":"cs69a77a95be8ae670"},"url":"/industries/financial-services"},{"title_l10n":"Telecommunications","_metadata":{"uid":"cs442027d0d054f2f5"},"url":"/industries/telecommunications"},{"title_l10n":"Healthcare","_metadata":{"uid":"cs41f069ee8826f3cc"},"url":"/industries/healthcare"},{"title_l10n":"Technology","_metadata":{"uid":"cs10d2a61d7bf2dfea"},"url":"/industries/technology"},{"title_l10n":"Retail and ecommerce","_metadata":{"uid":"csfd0f8c6ead313dba"},"url":"/industries/retail-ecommerce"},{"title_l10n":"Media and entertainment","_metadata":{"uid":"cs24a39eb8ab182103"},"url":"/industries/media-entertainment"},{"title_l10n":"Manufacturing and automotive","_metadata":{"uid":"csea5e7766a5458ef5"},"url":"/industries/manufacturing"}]}],"unlisted":[]},{"title_l10n":"Observability Labs","_metadata":{"uid":"cs311ec910bc2c0842"},"url":"/observability-labs","level_3":[{"title_l10n":"About","_metadata":{"uid":"cs48c8c88ed6540a13"},"url":"/observability-labs/about","level_4":[]},{"title_l10n":"Topics","_metadata":{"uid":"cs39efd75bc1968340"},"url":"","level_4":[{"title_l10n":"Topic 2","_metadata":{"uid":"cs1a209b9755f3df0f"},"url":"/observability-labs/topic-2"},{"title_l10n":"Topic 3","_metadata":{"uid":"cs11a1889686d577b4"},"url":"/observability-labs/topic-3"}]}],"unlisted":[]}],"tags":[],"title":"Sub Navigation","updated_at":"2025-03-11T14:34:07.364Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2025-03-11T14:34:13.344Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],1],"translateContentRedesign":[[{"uid":"bltfb44eb6e899331a4","_version":1,"locale":"en-us","ACL":{},"created_at":"2024-11-13T23:43:06.196Z","created_by":"blt36e890d06c5ec32c","english_content":"Or","tags":[],"title":"Or","translate_content_l10n":"Or","updated_at":"2024-11-13T23:43:06.196Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-11-13T23:44:21.198Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt2aeecde6c1729945","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:02.610Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more","tags":[],"title":"Load more","translate_content_l10n":"Load more","updated_at":"2024-09-03T16:41:46.744Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-03T16:42:00.289Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt6f3ad4a078adc611","ACL":{},"created_at":"2024-05-28T12:47:25.539Z","created_by":"blt3e52848e0cb3c394","english_content":"Overview","tags":[],"title":"Overview","translate_content_l10n":"Overview","updated_at":"2024-05-28T12:47:25.539Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-05-28T12:47:29.022Z","user":"blt3e52848e0cb3c394"}},{"_version":4,"locale":"en-us","uid":"blt3b08c089ffd331e6","ACL":{},"created_at":"2023-01-26T21:09:09.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","tags":[],"title":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content","translate_content_l10n":"Can't make it? Register and we'll send you the recording. You'll also receive an email with related content.","updated_at":"2023-12-18T21:59:16.399Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:59:19.133Z","user":"blt3044324473ef223b70bc674c"}},{"_version":4,"locale":"en-us","uid":"blt7a2b7e50bb030ed8","ACL":{},"created_at":"2023-01-26T21:09:00.746Z","created_by":"blt36e890d06c5ec32c","english_content":"You'll also receive an email with related content.","tags":[],"title":"You'll also receive an email with related content","translate_content_l10n":"You'll also receive an email with related content.","updated_at":"2023-12-18T21:58:39.250Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-18T21:58:43.929Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt7a2ecc87e95e0fed","ACL":{},"created_at":"2023-08-23T22:51:28.540Z","created_by":"blt36e890d06c5ec32c","english_content":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","tags":[],"title":"Newsletter GDPR Text","translate_content_l10n":"\u003cp\u003eBy submitting you acknowledge that you've read and agree to our \u003ca href=\"/legal/elastic-cloud-account-terms\" target=\"_blank\"\u003eTerms of Service\u003c/a\u003e, and that Elastic may \u003ca href=\"/legal/privacy-statement#how-we-use-the-information\" target=\"_blank\"\u003econtact you\u003c/a\u003e about our related products and services, using the details you provide above. See \u003ca href=\"/legal/privacy-statement/\" target=\"_blank\"\u003eElastic’s Privacy Statement\u003c/a\u003e for more details or to opt-out at any time.\u003c/p\u003e","updated_at":"2023-08-23T22:51:28.540Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-23T22:52:42.175Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt16f2676801e3267e","ACL":{},"created_at":"2023-08-22T17:00:20.812Z","created_by":"blt36e890d06c5ec32c","english_content":"Speakers","tags":[],"title":"Speakers","translate_content_l10n":"Speakers","updated_at":"2023-08-22T17:00:20.812Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-08-22T17:01:19.248Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0cbc24c249b9fd54","ACL":{},"created_at":"2023-07-11T21:21:11.001Z","created_by":"blt3044324473ef223b70bc674c","english_content":"Close","tags":[],"title":"Close","translate_content_l10n":"Close","updated_at":"2023-07-11T21:21:11.001Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-07-11T21:22:26.797Z","user":"blt3044324473ef223b70bc674c"}},{"_version":1,"locale":"en-us","uid":"blt20243cb3a8c574f6","ACL":{},"created_at":"2023-04-27T22:46:08.141Z","created_by":"blt36e890d06c5ec32c","english_content":"See more insights","tags":[],"title":"See more insights","translate_content_l10n":"See more insights","updated_at":"2023-04-27T22:46:08.141Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-27T22:47:17.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt5e35f797b223487b","ACL":{},"created_at":"2023-04-25T22:44:26.727Z","created_by":"blt36e890d06c5ec32c","english_content":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","tags":[],"title":"The content on this page is not available in the selected language.","translate_content_l10n":"The content on this page is not available in the selected language. As Elastic grows globally, we continue to support content in multiple languages.","updated_at":"2023-04-25T22:50:03.458Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-25T22:50:49.263Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt95f1076dfef4f727","ACL":{},"created_at":"2023-04-03T16:58:30.945Z","created_by":"blt36e890d06c5ec32c","english_content":"Author","tags":[],"title":"Author","translate_content_l10n":"Author","updated_at":"2023-04-03T16:58:30.945Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:02:04.749Z","user":"blt36e890d06c5ec32c"}},{"_version":3,"locale":"en-us","uid":"bltb9e7436e790dc1e1","ACL":{},"created_at":"2023-01-26T21:09:01.075Z","created_by":"blt36e890d06c5ec32c","english_content":"Learn more","tags":[],"title":"Learn more","translate_content_l10n":"Learn more","updated_at":"2023-03-23T23:23:32.443Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:25:05.498Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blte80ec2bf93203454","ACL":{},"created_at":"2023-03-23T23:20:05.096Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now (no PT)","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:20:05.096Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:23:03.467Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blt0b2b84aede5a5e1a","ACL":{},"created_at":"2023-01-26T21:09:00.911Z","created_by":"blt36e890d06c5ec32c","english_content":"Watch now","tags":[],"title":"Watch now","translate_content_l10n":"Watch now","updated_at":"2023-03-23T23:17:38.751Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-23T23:19:07.965Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt45ad9978de13cb3c","ACL":{},"created_at":"2023-03-20T19:38:56.211Z","created_by":"blt36e890d06c5ec32c","english_content":"See all top stories","tags":[],"title":"See all top stories","translate_content_l10n":"See all top stories","updated_at":"2023-03-20T19:38:56.211Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:40:01.652Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0aeca091079429a4","ACL":{},"created_at":"2023-03-20T19:37:29.708Z","created_by":"blt36e890d06c5ec32c","english_content":"Related content","tags":[],"title":"Related content","translate_content_l10n":"Related content","updated_at":"2023-03-20T19:37:29.708Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-20T19:38:35.986Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltdedcc90f4b9d495c","ACL":{},"created_at":"2023-03-13T17:42:26.422Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All (no PT translation)","translate_content_l10n":"All","updated_at":"2023-03-13T18:12:39.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T18:13:09.648Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdafd9e19f8a295c9","ACL":{},"created_at":"2023-03-13T16:44:58.960Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact information","tags":[],"title":"Contact information","translate_content_l10n":"Contact information","updated_at":"2023-03-13T16:44:58.960Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:46:31.937Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt8d189cf8b1b80402","ACL":{},"created_at":"2023-03-13T16:43:08.761Z","created_by":"blt36e890d06c5ec32c","english_content":"Press Release","tags":[],"title":"Press Release","translate_content_l10n":"Press Release","updated_at":"2023-03-13T16:43:08.761Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-13T16:44:42.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb031798c593cf2aa","ACL":{},"created_at":"2023-03-06T17:39:15.553Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Reddit","tags":[],"title":"Share on Reddit","translate_content_l10n":"Share on Reddit","updated_at":"2023-03-06T17:39:15.553Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-06T17:40:52.751Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"bltc449b2f75825b408","ACL":{},"created_at":"2023-01-26T21:09:01.238Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories","tags":[],"title":"More stories","translate_content_l10n":"More stories","updated_at":"2023-02-23T22:39:49.208Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-23T22:40:59.356Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte38439477acb192e","ACL":{},"created_at":"2023-01-26T21:09:00.049Z","created_by":"blt36e890d06c5ec32c","english_content":"Articles by","tags":[],"title":"Articles by","translate_content_l10n":"Articles by","updated_at":"2023-02-23T22:11:25.304Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T16:57:47.130Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4b99c93b5338acdd","ACL":{},"created_at":"2023-02-16T17:26:10.103Z","created_by":"blt36e890d06c5ec32c","english_content":"Share this story","tags":[],"title":"Share this story","translate_content_l10n":"Share this story","updated_at":"2023-02-16T17:26:10.103Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-16T17:27:39.093Z","user":"blt36e890d06c5ec32c"}},{"_version":2,"locale":"en-us","uid":"blte2e658dd90716f9f","ACL":{},"created_at":"2023-01-26T21:09:06.325Z","created_by":"blt36e890d06c5ec32c","english_content":"Share by Email","tags":[],"title":"Share by Email","translate_content_l10n":"Share by email","updated_at":"2023-02-14T18:05:54.924Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-02-14T18:06:40.021Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt622e2e6d3a2e469f","ACL":{},"created_at":"2023-01-26T21:09:09.950Z","created_by":"blt36e890d06c5ec32c","english_content":"Read less","tags":[],"title":"Read less","translate_content_l10n":"Read less","updated_at":"2023-01-26T21:09:09.950Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.384Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltb6e126363fe0669f","ACL":{},"created_at":"2023-01-26T21:09:09.794Z","created_by":"blt36e890d06c5ec32c","english_content":"Search Integrations","tags":[],"title":"Search Integrations","translate_content_l10n":"Search Integrations","updated_at":"2023-01-26T21:09:09.794Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.579Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltfc60ac5a8053094c","ACL":{},"created_at":"2023-01-26T21:09:09.641Z","created_by":"blt36e890d06c5ec32c","english_content":"All Solutions","tags":[],"title":"All Solutions","translate_content_l10n":"All Solutions","updated_at":"2023-01-26T21:09:09.641Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.477Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt0c2c6a4e8cb5c2f0","ACL":{},"created_at":"2023-01-26T21:09:09.435Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for registering. We will send you a confirmation email soon.","tags":[],"title":"Thank you for registering. We will send you a confirmation email soon.","translate_content_l10n":"Thank you for registering. We will send you a confirmation email soon.","updated_at":"2023-01-26T21:09:09.435Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.184Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd7b837e25d93f5d3","ACL":{},"created_at":"2023-01-26T21:09:09.095Z","created_by":"blt36e890d06c5ec32c","english_content":"Thank you for your interest!","tags":[],"title":"Thank you for your interest!","translate_content_l10n":"Thank you for your interest!","updated_at":"2023-01-26T21:09:09.095Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.784Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteecbf46e81d0d29d","ACL":{},"created_at":"2023-01-26T21:09:08.915Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Youtube","tags":[],"title":"Follow us on Youtube","translate_content_l10n":"Follow us on Youtube","updated_at":"2023-01-26T21:09:08.915Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.451Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2dd2bbe9b12abe26","ACL":{},"created_at":"2023-01-26T21:09:08.754Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Twitter","tags":[],"title":"Follow us on Twitter","translate_content_l10n":"Follow us on Twitter","updated_at":"2023-01-26T21:09:08.754Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.917Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt35eafbb82d26a869","ACL":{},"created_at":"2023-01-26T21:09:08.594Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on LinkedIn","tags":[],"title":"Follow us on LinkedIn","translate_content_l10n":"Follow us on LinkedIn","updated_at":"2023-01-26T21:09:08.594Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.993Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt9667a9e201b264e5","ACL":{},"created_at":"2023-01-26T21:09:08.424Z","created_by":"blt36e890d06c5ec32c","english_content":"Follow us on Facebook","tags":[],"title":"Follow us on Facebook","translate_content_l10n":"Follow us on Facebook","updated_at":"2023-01-26T21:09:08.424Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.149Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltafd12f73d268d939","ACL":{},"created_at":"2023-01-26T21:09:08.254Z","created_by":"blt36e890d06c5ec32c","english_content":"Headshot of","tags":[],"title":"Headshot of","translate_content_l10n":"Headshot of","updated_at":"2023-01-26T21:09:08.254Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.217Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blteeffcd504c337777","ACL":{},"created_at":"2023-01-26T21:09:08.073Z","created_by":"blt36e890d06c5ec32c","english_content":"Table of contents","tags":[],"title":"Table of contents","translate_content_l10n":"Table of contents","updated_at":"2023-01-26T21:09:08.073Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.878Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1c9c25fdd610a988","ACL":{},"created_at":"2023-01-26T21:09:07.459Z","created_by":"blt36e890d06c5ec32c","english_content":"All","tags":[],"title":"All","translate_content_l10n":"All","updated_at":"2023-01-26T21:09:07.459Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.849Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcc368963ef15efcf","ACL":{},"created_at":"2023-01-26T21:09:07.299Z","created_by":"blt36e890d06c5ec32c","english_content":"Reset all","tags":[],"title":"Reset all","translate_content_l10n":"Reset all","updated_at":"2023-01-26T21:09:07.299Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.712Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltdf9e2c7ddef1476c","ACL":{},"created_at":"2023-01-26T21:09:07.138Z","created_by":"blt36e890d06c5ec32c","english_content":"Filters","tags":[],"title":"Filters","translate_content_l10n":"Filters","updated_at":"2023-01-26T21:09:07.138Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.405Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbd8186c36bcb7238","ACL":{},"created_at":"2023-01-26T21:09:06.974Z","created_by":"blt36e890d06c5ec32c","english_content":"Global Virtual Event","tags":[],"title":"Global Virtual Event","translate_content_l10n":"Global Virtual Event","updated_at":"2023-01-26T21:09:06.974Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.270Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta4972bcd17a9589e","ACL":{},"created_at":"2023-01-26T21:09:06.815Z","created_by":"blt36e890d06c5ec32c","english_content":"View more posts","tags":[],"title":"View more posts","translate_content_l10n":"View more posts","updated_at":"2023-01-26T21:09:06.815Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.716Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7784639e8213f1de","ACL":{},"created_at":"2023-01-26T21:09:06.656Z","created_by":"blt36e890d06c5ec32c","english_content":"Print","tags":[],"title":"Print","translate_content_l10n":"Print","updated_at":"2023-01-26T21:09:06.656Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.409Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd160052884c85597","ACL":{},"created_at":"2023-01-26T21:09:06.489Z","created_by":"blt36e890d06c5ec32c","english_content":"Continue reading","tags":[],"title":"Continue reading","translate_content_l10n":"Continue reading","updated_at":"2023-01-26T21:09:06.489Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.383Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa2fe12d75e222b7","ACL":{},"created_at":"2023-01-26T21:09:06.160Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Facebook","tags":[],"title":"Share on Facebook","translate_content_l10n":"Share on Facebook","updated_at":"2023-01-26T21:09:06.160Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.521Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt2c65ce5e43c44d1e","ACL":{},"created_at":"2023-01-26T21:09:05.989Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on LinkedIn","tags":[],"title":"Share on LinkedIn","translate_content_l10n":"Share on LinkedIn","updated_at":"2023-01-26T21:09:05.989Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.207Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltaa64468770539e99","ACL":{},"created_at":"2023-01-26T21:09:05.807Z","created_by":"blt36e890d06c5ec32c","english_content":"Share on Twitter","tags":[],"title":"Share on Twitter","translate_content_l10n":"Share on Twitter","updated_at":"2023-01-26T21:09:05.807Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.548Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbf19c4f1958b7010","ACL":{},"created_at":"2023-01-26T21:09:05.653Z","created_by":"blt36e890d06c5ec32c","english_content":"Share","tags":[],"title":"Share","translate_content_l10n":"Share","updated_at":"2023-01-26T21:09:05.653Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.603Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd3ca82669f533596","ACL":{},"created_at":"2023-01-26T21:09:05.494Z","created_by":"blt36e890d06c5ec32c","english_content":"Small image for","tags":[],"title":"Small image for","translate_content_l10n":"Small image for","updated_at":"2023-01-26T21:09:05.494Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.766Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt665205a37a7b1a98","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:05.336Z","created_by":"blt36e890d06c5ec32c","english_content":"Video for","tags":[],"title":"Video for","translate_content_l10n":"Video for","updated_at":"2023-01-26T21:09:05.336Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:39:50.482Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt33215a82788dd3f2","ACL":{},"created_at":"2023-01-26T21:09:05.174Z","created_by":"blt36e890d06c5ec32c","english_content":"Explore similar demos","tags":[],"title":"Explore similar demos","translate_content_l10n":"Explore similar demos","updated_at":"2023-01-26T21:09:05.174Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.940Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt59af0058e6f2ab2c","ACL":{},"created_at":"2023-01-26T21:09:05.013Z","created_by":"blt36e890d06c5ec32c","english_content":"Register now","tags":[],"title":"Register now","translate_content_l10n":"Register now","updated_at":"2023-01-26T21:09:05.013Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.297Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt44f6c020ef294d34","ACL":{},"created_at":"2023-01-26T21:09:04.854Z","created_by":"blt36e890d06c5ec32c","english_content":"View next","tags":[],"title":"View next","translate_content_l10n":"View next","updated_at":"2023-01-26T21:09:04.854Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.641Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltbc455c56e1db3258","ACL":{},"created_at":"2023-01-26T21:09:04.701Z","created_by":"blt36e890d06c5ec32c","english_content":"Upcoming webinar","tags":[],"title":"Upcoming webinar","translate_content_l10n":"Upcoming webinar","updated_at":"2023-01-26T21:09:04.701Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.739Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt9e655ee3d1dbcd42","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.537Z","created_by":"blt36e890d06c5ec32c","english_content":"On-demand webinar","tags":[],"title":"On-demand webinar","translate_content_l10n":"On-demand webinar","updated_at":"2023-01-26T21:09:04.537Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:46:22.076Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd00860fb1d6f389b","ACL":{},"created_at":"2023-01-26T21:09:04.379Z","created_by":"blt36e890d06c5ec32c","english_content":"Featured webinar","tags":[],"title":"Featured webinar","translate_content_l10n":"Featured webinar","updated_at":"2023-01-26T21:09:04.379Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.328Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt335688b477b632cf","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:04.218Z","created_by":"blt36e890d06c5ec32c","english_content":"Highlights","tags":[],"title":"Highlights","translate_content_l10n":"Highlights","updated_at":"2023-01-26T21:09:04.218Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:31:29.622Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"bltd90374b721d95342","ACL":{},"created_at":"2023-01-26T21:09:03.895Z","created_by":"blt36e890d06c5ec32c","english_content":"See when this webinar starts in my time zone","tags":[],"title":"See when this webinar starts in my time zone","translate_content_l10n":"See when this webinar starts in my time zone","updated_at":"2023-01-26T21:09:03.895Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.820Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt60fa8518500aa04e","ACL":{},"created_at":"2023-01-26T21:09:03.734Z","created_by":"blt36e890d06c5ec32c","english_content":"Related workshops","tags":[],"title":"Related workshops","translate_content_l10n":"Related workshops","updated_at":"2023-01-26T21:09:03.734Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.354Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt1fa14ebb51d2154f","ACL":{},"created_at":"2023-01-26T21:09:03.577Z","created_by":"blt36e890d06c5ec32c","english_content":"Hosted by","tags":[],"title":"Hosted by","translate_content_l10n":"Hosted by","updated_at":"2023-01-26T21:09:03.577Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:37.873Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltace88e420eb1dedb","ACL":{},"created_at":"2023-01-26T21:09:03.419Z","created_by":"blt36e890d06c5ec32c","english_content":"Agenda","tags":[],"title":"Agenda","translate_content_l10n":"Agenda","updated_at":"2023-01-26T21:09:03.419Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.193Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt4e07248dad773e78","ACL":{},"created_at":"2023-01-26T21:09:03.260Z","created_by":"blt36e890d06c5ec32c","english_content":"Location","tags":[],"title":"Location","translate_content_l10n":"Location","updated_at":"2023-01-26T21:09:03.260Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.039Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd047722739355567","ACL":{},"created_at":"2023-01-26T21:09:03.106Z","created_by":"blt36e890d06c5ec32c","english_content":"Date","tags":[],"title":"Date","translate_content_l10n":"Date","updated_at":"2023-01-26T21:09:03.106Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.355Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt97cf5566d151b2d8","ACL":{},"created_at":"2023-01-26T21:09:02.936Z","created_by":"blt36e890d06c5ec32c","english_content":"More","tags":[],"title":"More","translate_content_l10n":"More","updated_at":"2023-01-26T21:09:02.936Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.435Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltda408b2b71cd18d9","ACL":{},"created_at":"2023-01-26T21:09:02.777Z","created_by":"blt36e890d06c5ec32c","english_content":"View more learning opportunities","tags":[],"title":"View more learning opportunities","translate_content_l10n":"View more learning opportunities","updated_at":"2023-01-26T21:09:02.777Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.807Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc5c1c4900cfdb547","ACL":{},"created_at":"2023-01-26T21:09:02.430Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more press releases","tags":[],"title":"Load more press releases","translate_content_l10n":"Load more press releases","updated_at":"2023-01-26T21:09:02.430Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.293Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blta759219421b27a99","ACL":{},"created_at":"2023-01-26T21:09:02.267Z","created_by":"blt36e890d06c5ec32c","english_content":"Load more news","tags":[],"title":"Load more news","translate_content_l10n":"Load more news","updated_at":"2023-01-26T21:09:02.267Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-03-14T16:29:48.588Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt04d58d965fb73d4b","ACL":{},"created_at":"2023-01-26T21:09:02.102Z","created_by":"blt36e890d06c5ec32c","english_content":"Read more","tags":[],"title":"Read more","translate_content_l10n":"Read more","updated_at":"2023-01-26T21:09:02.102Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.159Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltcecc4cb33d2f12d1","ACL":{},"created_at":"2023-01-26T21:09:01.933Z","created_by":"blt36e890d06c5ec32c","english_content":"What to explore next...","tags":[],"title":"What to explore next...","translate_content_l10n":"What to explore next...","updated_at":"2023-01-26T21:09:01.933Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:48.762Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt536f120184d5f82f","ACL":{},"created_at":"2023-01-26T21:09:01.766Z","created_by":"blt36e890d06c5ec32c","english_content":"More stories from Elastic Customers","tags":[],"title":"More stories from Elastic Customers","translate_content_l10n":"More stories from Elastic Customers","updated_at":"2023-01-26T21:09:01.766Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.267Z","user":"blt36e890d06c5ec32c"}},{"uid":"blt4b67bf09270df98e","_version":1,"locale":"en-us","ACL":{},"created_at":"2023-01-26T21:09:01.597Z","created_by":"blt36e890d06c5ec32c","english_content":"See All Posts","tags":[],"title":"See All Posts","translate_content_l10n":"See all posts","updated_at":"2023-01-26T21:09:01.597Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"time":"2024-09-27T18:34:33.604Z","user":"blt36e890d06c5ec32c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"_version":1,"locale":"en-us","uid":"blt76ad53f0811383e0","ACL":{},"created_at":"2023-01-26T21:09:01.432Z","created_by":"blt36e890d06c5ec32c","english_content":"Contact Info","tags":[],"title":"Contact Info","translate_content_l10n":"Contact information","updated_at":"2023-01-26T21:09:01.432Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.103Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd24b268000310a17","ACL":{},"created_at":"2023-01-26T21:09:00.572Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Watch","tags":[],"title":"Register to Watch","translate_content_l10n":"Register to watch","updated_at":"2023-01-26T21:09:00.572Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.740Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltc387be0be6c7bba6","ACL":{},"created_at":"2023-01-26T21:09:00.393Z","created_by":"blt36e890d06c5ec32c","english_content":"Sign In to Attend","tags":[],"title":"Sign In to Attend","translate_content_l10n":"Sign in to attend","updated_at":"2023-01-26T21:09:00.393Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.633Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"bltd778a9bdcafbbc41","ACL":{},"created_at":"2023-01-26T21:09:00.219Z","created_by":"blt36e890d06c5ec32c","english_content":"Register to Attend","tags":[],"title":"Register to Attend","translate_content_l10n":"Register to attend","updated_at":"2023-01-26T21:09:00.219Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:44.790Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt5f3c4d1f3f7a64fe","ACL":{},"created_at":"2023-01-26T21:08:59.859Z","created_by":"blt36e890d06c5ec32c","english_content":"More posts","tags":[],"title":"More posts","translate_content_l10n":"More posts","updated_at":"2023-01-26T21:08:59.859Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-04-03T17:14:57.905Z","user":"blt36e890d06c5ec32c"}},{"_version":1,"locale":"en-us","uid":"blt7e366458d1dd1e0c","ACL":{},"created_at":"2023-01-26T21:08:59.675Z","created_by":"blt36e890d06c5ec32c","english_content":"By","tags":[],"title":"By","translate_content_l10n":"By","updated_at":"2023-01-26T21:08:59.675Z","updated_by":"blt36e890d06c5ec32c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-01-27T20:51:38.125Z","user":"blt36e890d06c5ec32c"}}],75],"blogCategoryDetail":[[{"uid":"blt79ab512346c0eec7","_version":12,"locale":"en-us","ACL":{},"carousel":[],"category":[{"uid":"blte5cc8450a098ce5e","_version":4,"locale":"en-us","ACL":{},"created_at":"2023-11-02T21:51:15.490Z","created_by":"blt3044324473ef223b70bc674c","key":"how-to","label_l10n":"How to","tags":[],"title":"How to","updated_at":"2024-05-10T13:44:25.495Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.353Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-09-24T00:29:13.783Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[],"tags_elastic_stack":[],"tags_topic":[]},"footer_cta_reference":[],"gallery":{"title_l10n":"More on Tech Topics"},"hero":[{"uid":"bltab2d957fab7fcfb1","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_elastic_stack":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Tech Topics","updated_at":"2024-06-12T15:57:19.637Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/technical-topics","publish_details":{"time":"2024-10-16T12:24:16.366Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt0b8a092baa2d643f","_version":39,"locale":"en-us","ACL":{},"carousel":[],"category":[],"created_at":"2021-09-21T18:30:40.097Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Customers","featured_blog":[],"author":[],"category":[],"tags_blog_type":[],"tags_topic":[],"tags_elastic_stack":[{"uid":"blt6f3b5313b04c2729","_content_type_uid":"tags_elastic_stack"}]},"footer_cta_reference":[{"uid":"bltb02649945991225b","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[{"title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration","_metadata":{"uid":"csd06fb2a856adee86"}}],"icon_text_card":[],"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2025-03-17T09:05:02.976Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-03-17T09:05:05.600Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"gallery":{"title_l10n":"More on customers"},"hero":[{"uid":"blt2b94c476a7e69ac9","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_elastic_stack":[{"_content_type_uid":"tags_elastic_stack","_version":1,"locale":"en-us","uid":"blt6f3b5313b04c2729","ACL":{},"created_at":"2023-11-06T21:49:22.691Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"customer-story","label_l10n":"Customer story","tags":[],"title":"Customer story","updated_at":"2023-11-06T21:49:22.691Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:18.115Z","user":"blt4b2e1169881270a8"}}],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Customers","updated_at":"2024-05-07T16:27:28.325Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/customers","publish_details":{"time":"2024-10-16T12:22:32.272Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte4a5ee5e2481c636","_version":9,"locale":"en-us","ACL":{},"carousel":[],"category":[{"_version":5,"locale":"en-us","uid":"blt0c9f31df4f2a7a2b","ACL":{},"created_at":"2018-08-27T12:32:48.561Z","created_by":"sys_blt57a423112de8a853","key":"company-news","label_l10n":"News","tags":[],"title":"News","updated_at":"2024-05-10T13:44:22.885Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2024-08-29T20:00:07.956Z","user":"blt27204bf9f7abb7fd"}}],"created_at":"2021-09-21T18:32:10.309Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[],"tags_elastic_elk_stack":[],"tags_topic":[]},"footer_cta_reference":[{"uid":"bltb02649945991225b","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[{"title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration","_metadata":{"uid":"csd06fb2a856adee86"}}],"icon_text_card":[],"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2025-03-17T09:05:02.976Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-03-17T09:05:05.600Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"gallery":{"title_l10n":"More on company news"},"hero":[{"uid":"blt11b85590199dd40d","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_elastic_elk_stack":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Company news","updated_at":"2024-04-25T19:56:48.937Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/company-news","publish_details":{"time":"2024-10-16T12:32:14.544Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt77601f62cf0c6252","_version":16,"locale":"en-us","ACL":{},"carousel":[],"category":[{"uid":"bltfaae4466058cc7d6","_version":8,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:47:03.147Z","created_by":"sys_blt57a423112de8a853","key":"releases","label_l10n":"Product release","tags":[],"title":"Product release","updated_at":"2024-05-10T13:44:16.955Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.629Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2018-11-22T06:22:22.201Z","created_by":"sys_blt57a423112de8a853","display_latest_blog_posts":true,"featured_blog":{"author":[],"category":[],"featured_blog":[],"topic_heading_l10n":"","tags_blog_type":[]},"footer_cta_reference":[{"uid":"bltb02649945991225b","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[{"title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration","_metadata":{"uid":"csd06fb2a856adee86"}}],"icon_text_card":[],"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2025-03-17T09:05:02.976Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-03-17T09:05:05.600Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"gallery":{"title_l10n":"Releases"},"hero":[{"uid":"blt244541ff164d2b1c","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Releases","updated_at":"2024-04-25T19:42:34.910Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/releases","publish_details":{"time":"2024-10-16T12:27:14.782Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt957ce7a950db551e","_version":32,"locale":"en-us","ACL":{},"carousel":[{"icon":{"_version":1,"is_dir":false,"uid":"bltfd50cc17d6fa3667","ACL":{},"content_type":"image/svg+xml","created_at":"2021-01-26T11:54:03.941Z","created_by":"blt3e52848e0cb3c394","file_size":"1836","filename":"enterprise-search-logo-color-32px.svg","tags":[],"title":"enterprise-search-logo-color-32px.svg","updated_at":"2021-01-26T11:54:03.941Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-28T14:58:16.769Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/bltfd50cc17d6fa3667/601002db96de49101cfb4c30/enterprise-search-logo-color-32px.svg"},"_metadata":{"uid":"cs9314448a9b4c9a83"},"title_l10n":"Search","tags_use_case":["blt10eb11313dc454f1"],"tags_elastic_elk_stack":[],"display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Elastic Search","featured_blog":[]},"posts":[],"gallery":{"title_l10n":"More on Elastic Search"}},{"icon":{"_version":1,"is_dir":false,"uid":"blta89419c24b753828","ACL":{},"content_type":"image/svg+xml","created_at":"2021-07-19T08:04:15.433Z","created_by":"blt63e521894b971259","file_size":"401","filename":"observability-color.svg","parent_uid":null,"tags":[],"title":"observability-color.svg","updated_at":"2021-07-19T08:04:15.433Z","updated_by":"blt63e521894b971259","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-28T14:58:16.740Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blta89419c24b753828/60f531ff3f40e5481e85a752/observability-color.svg"},"_metadata":{"uid":"cs6bc3a97a635d5697"},"title_l10n":"Observability","tags_use_case":["blt8a7a5ea52ac5d888"],"tags_elastic_elk_stack":[],"display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Elastic Observability","featured_blog":[]},"posts":[],"gallery":{"title_l10n":"More on Elastic Observability"}},{"icon":{"_version":1,"is_dir":false,"uid":"blte046ae7d78156afb","ACL":{},"content_type":"image/svg+xml","created_at":"2021-01-26T20:54:17.021Z","created_by":"blt3e52848e0cb3c394","file_size":"991","filename":"security-logo-color-32px.svg","tags":[],"title":"security-logo-color-32px.svg","updated_at":"2021-01-26T20:54:17.021Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2021-09-28T14:58:16.755Z","user":"blt3e52848e0cb3c394"},"url":"https://images.contentstack.io/v3/assets/bltefdd0b53724fa2ce/blte046ae7d78156afb/601081790839e910126d7653/security-logo-color-32px.svg"},"_metadata":{"uid":"csdffb4405d5195ea7"},"title_l10n":"Security","tags_use_case":["blt569b48df66a9ba5d"],"tags_elastic_elk_stack":[],"display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"Elastic Security","featured_blog":[]},"posts":[],"gallery":{"title_l10n":"More on Elastic Security"}}],"category":[],"created_at":"2021-09-21T18:39:20.131Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[{"uid":"bltb02649945991225b","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[{"title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration","_metadata":{"uid":"csd06fb2a856adee86"}}],"icon_text_card":[],"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2025-03-17T09:05:02.976Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-03-17T09:05:05.600Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"gallery":{"title_l10n":""},"hero":[{"uid":"bltafc1a9945479fe16","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Solutions","updated_at":"2024-04-25T19:41:39.446Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/solutions","publish_details":{"time":"2024-10-16T12:28:16.626Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blte470cd0f47832b94","_version":28,"locale":"en-us","ACL":{},"carousel":[],"category":[{"uid":"bltc253e0851420b088","_version":4,"locale":"en-us","ACL":{},"created_at":"2018-08-27T12:45:23.873Z","created_by":"sys_blt57a423112de8a853","key":"culture","label_l10n":"Culture","tags":[],"title":"Culture","updated_at":"2024-05-10T13:44:28.145Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"time":"2024-05-10T13:44:53.214Z","user":"blt3044324473ef223b70bc674c","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"created_at":"2021-09-21T18:33:05.397Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[{"uid":"bltb02649945991225b","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[{"title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration","_metadata":{"uid":"csd06fb2a856adee86"}}],"icon_text_card":[],"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2025-03-17T09:05:02.976Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-03-17T09:05:05.600Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"gallery":{"title_l10n":"More on culture"},"hero":[{"uid":"blt40f02945da0d4949","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[],"tags_use_case":[],"title":"Blog Category - Culture","updated_at":"2024-04-25T19:37:36.516Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/culture","publish_details":{"time":"2024-10-16T12:25:56.276Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt98f03da8444253c4","_version":19,"locale":"en-us","ACL":{},"carousel":[],"category":[],"created_at":"2023-06-21T20:59:14.074Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[{"uid":"bltb02649945991225b","_version":6,"locale":"en-us","ACL":{},"created_at":"2021-09-16T18:47:06.607Z","created_by":"blt3044324473ef223b70bc674c","cta":{"cta_title_l10n":"","url":""},"cta_group":[{"title_l10n":"Start free trial","url":"https://cloud.elastic.co/registration","_metadata":{"uid":"csd06fb2a856adee86"}}],"icon_text_card":[],"paragraph_l10n":"\u003cp\u003eSpin up a fully loaded deployment on the cloud provider you choose. As the company behind \u003ca href=\"/elasticsearch\"\u003eElasticsearch\u003c/a\u003e, we bring our features and support to your Elastic clusters in the cloud.\u003c/p\u003e","tags":[],"title":"Blog Footer CTA","title_l10n":"Sign up for Elastic Cloud free trial","updated_at":"2025-03-17T09:05:02.976Z","updated_by":"blt3e52848e0cb3c394","publish_details":{"time":"2025-03-17T09:05:05.600Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],"gallery":{"title_l10n":"More on Generative AI"},"hero":[{"uid":"bltbcfe080c422717bb","_content_type_uid":"hero"}],"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_topic":[{"uid":"blt99b075caf3df4ca7","_content_type_uid":"tags_topic"}],"tags_use_case":[],"title":"Blog Category - Generative AI","updated_at":"2024-04-25T19:36:28.188Z","updated_by":"blt3044324473ef223b70bc674c","url":"/blog/category/generative-ai","publish_details":{"time":"2024-10-16T12:29:57.776Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}},{"uid":"blt47677f49600645bd","_version":33,"locale":"en-us","ACL":{},"carousel":[],"category":[],"created_at":"2021-09-24T16:08:27.777Z","created_by":"blt3044324473ef223b70bc674c","display_latest_blog_posts":true,"featured_blog":{"topic_heading_l10n":"","featured_blog":[],"author":[],"category":[],"tags_blog_type":[]},"footer_cta_reference":[],"gallery":{"title_l10n":"More on Elastic Stack + Cloud"},"hero":[{"uid":"blt44ed576d81624808","_content_type_uid":"hero"}],"main_header":{"topic_heading_l10n":"","title_l10n":"Elastic Stack + Cloud","subtitle_l10n":"","paragraph_l10n":"\u003cp\u003eLearn more about the Elastic Search Platform, including Elasticsearch, Kibana, and Elastic Cloud.\u003c/p\u003e"},"posts":[],"seo":{"seo_title_l10n":"","seo_description_l10n":"","seo_keywords_l10n":"","seo_image":null},"tags":[],"tags_blog_type":[],"tags_use_case":[{"_version":2,"locale":"en-us","uid":"blt38a6c014d6bd5ecb","ACL":{},"created_at":"2021-06-02T15:27:49.854Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"stack","label_l10n":"Stack","tags":[],"title":"Stack","updated_at":"2021-07-13T22:00:22.378Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T15:50:17.258Z","user":"blt4b2e1169881270a8"}},{"_version":2,"locale":"en-us","uid":"bltcb543cd010a1e2a8","ACL":{},"created_at":"2020-06-17T03:33:30.831Z","created_by":"blt3044324473ef223b70bc674c","hidden_value":false,"keyword":"cloud","label_l10n":"Cloud","tags":[],"title":"Cloud","updated_at":"2020-07-06T22:20:17.019Z","updated_by":"blt3044324473ef223b70bc674c","publish_details":{"environment":"blt835e2c3b7e9eb7fb","locale":"en-us","time":"2023-12-08T16:05:21.552Z","user":"blt4b2e1169881270a8"}}],"title":"Blog Category - Stack + Cloud","updated_at":"2024-02-26T10:57:21.311Z","updated_by":"blt3e52848e0cb3c394","url":"/blog/category/stack-cloud","publish_details":{"time":"2024-10-16T12:31:22.574Z","user":"blt3e52848e0cb3c394","environment":"blt835e2c3b7e9eb7fb","locale":"en-us"}}],8],"gdprData":{"ip":"0.0.0.0","country_code":"US","city":"unknown","in_eu":true,"lang":"en-US,en;q=0.5"},"contentFound":true,"__N_SSP":true},"page":"/default_detail","query":{},"buildId":"Lxlpn6lP1AzvlD3efONO4","runtimeConfig":{"public":"public","env":"production"},"isFallback":false,"gssp":true,"customServer":true,"appGip":true,"scriptLoader":[]}</script></body></html>
